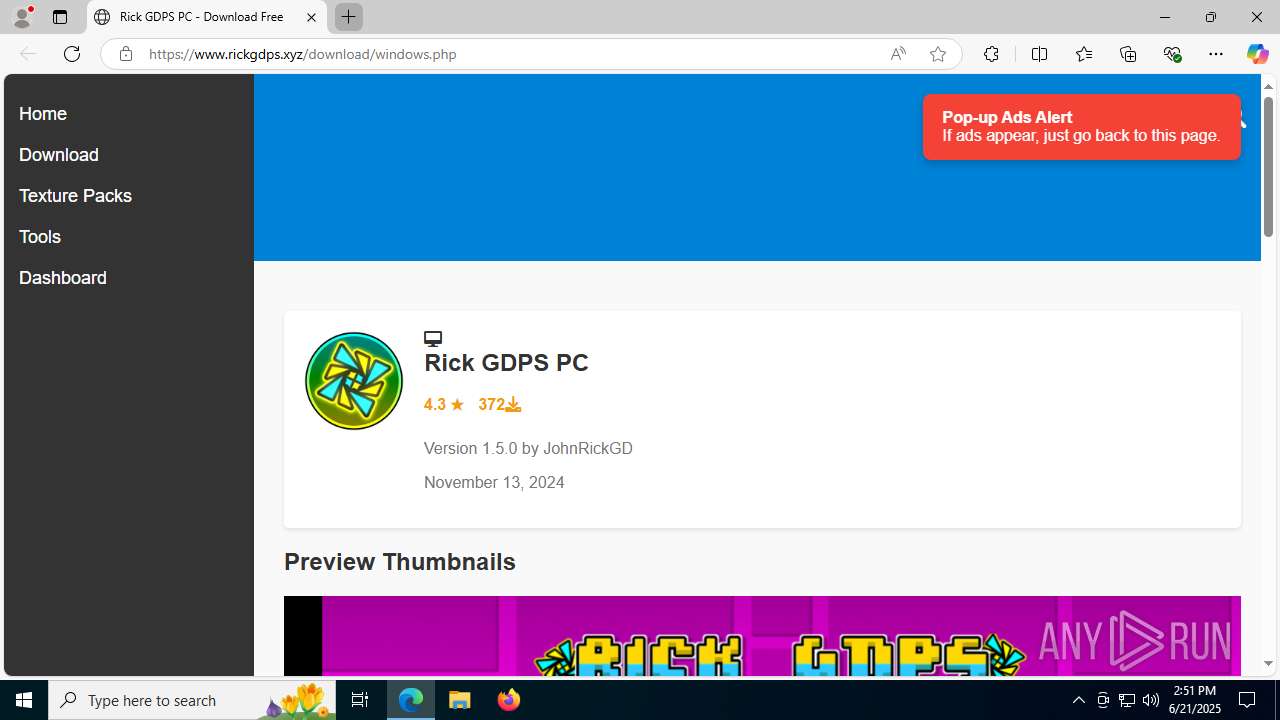
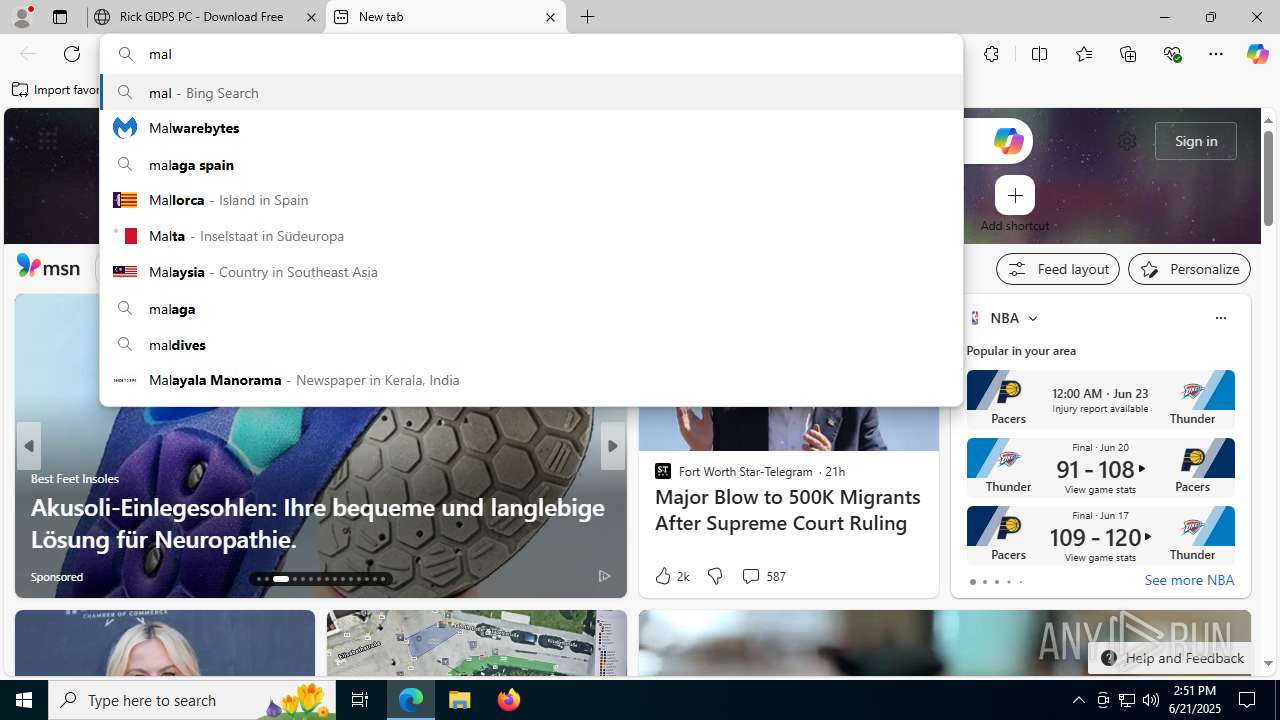
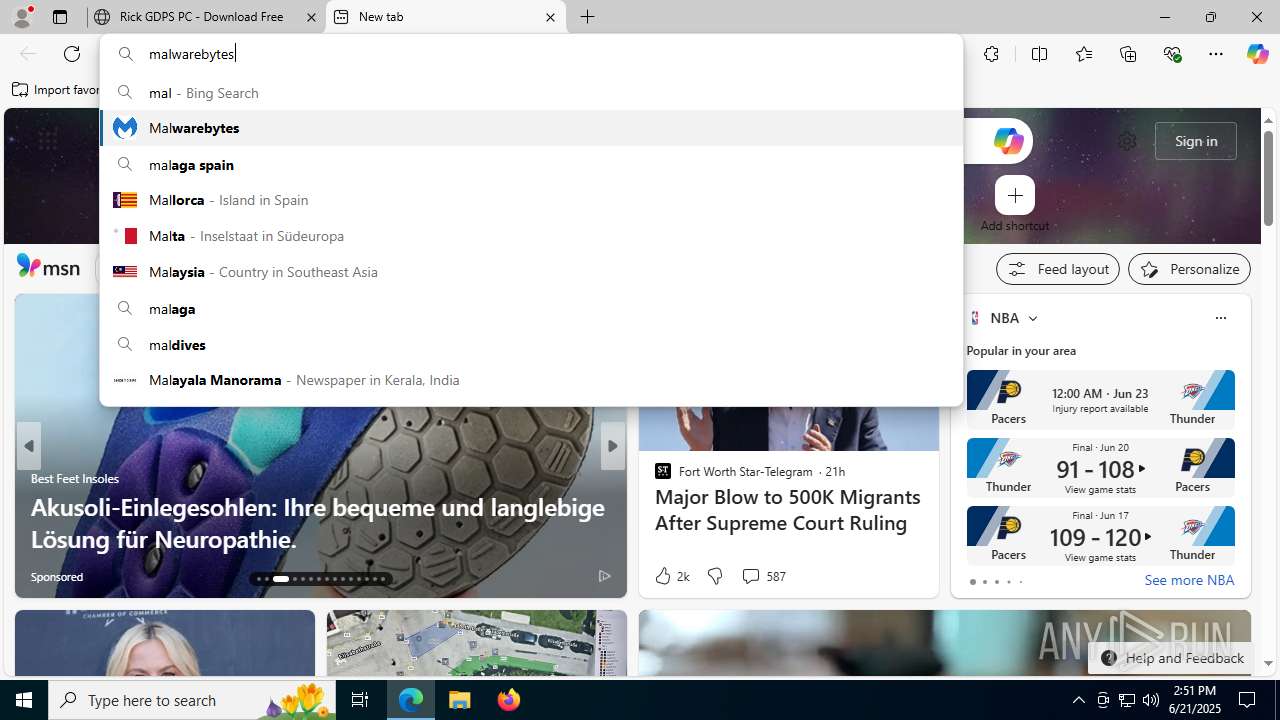
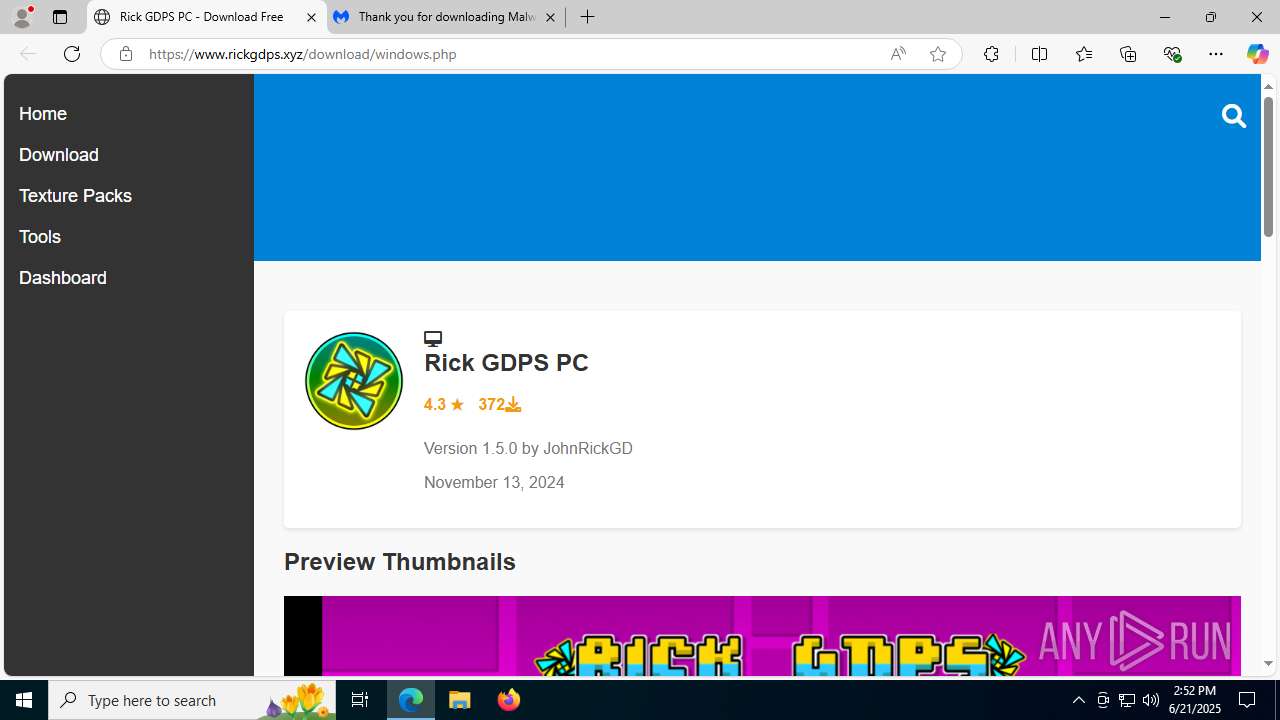
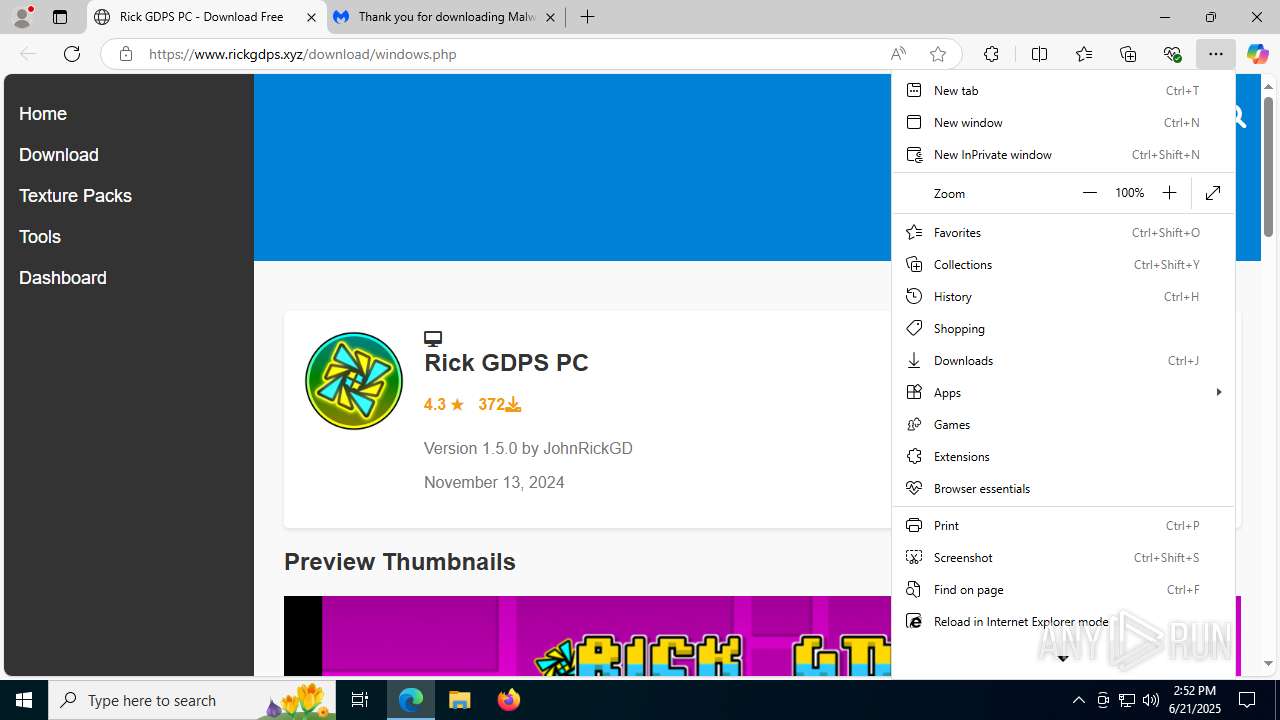
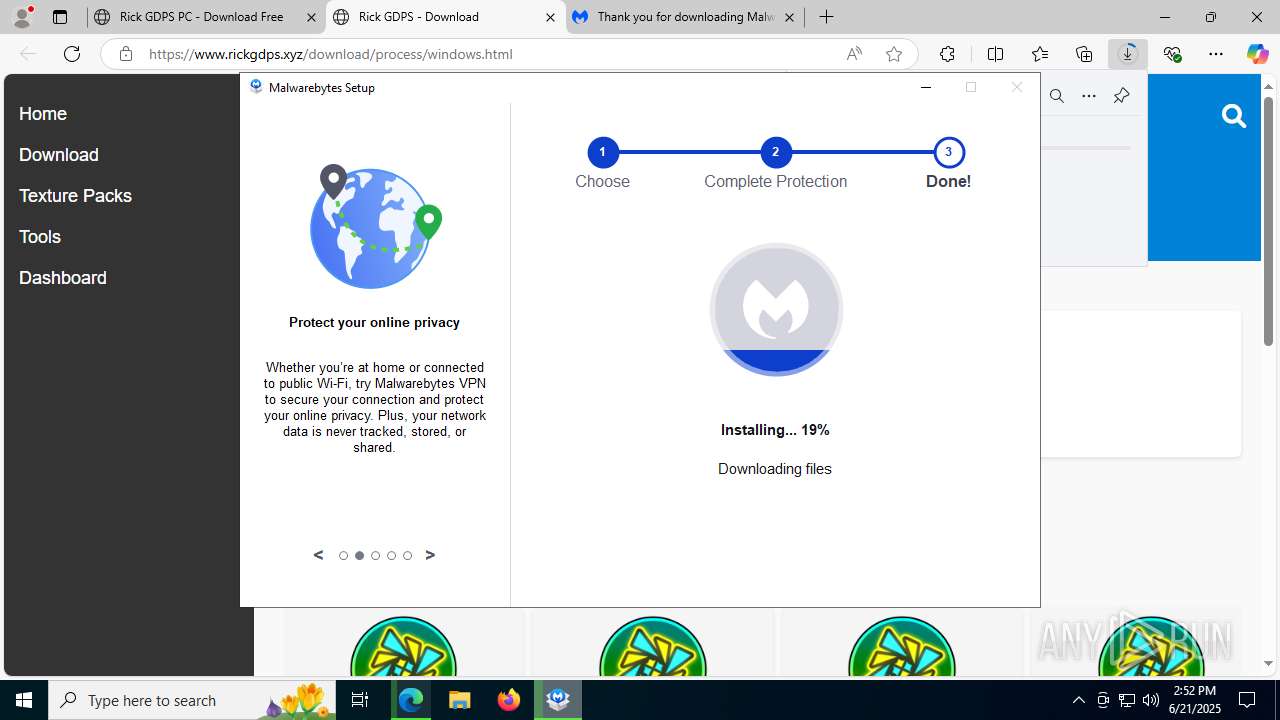
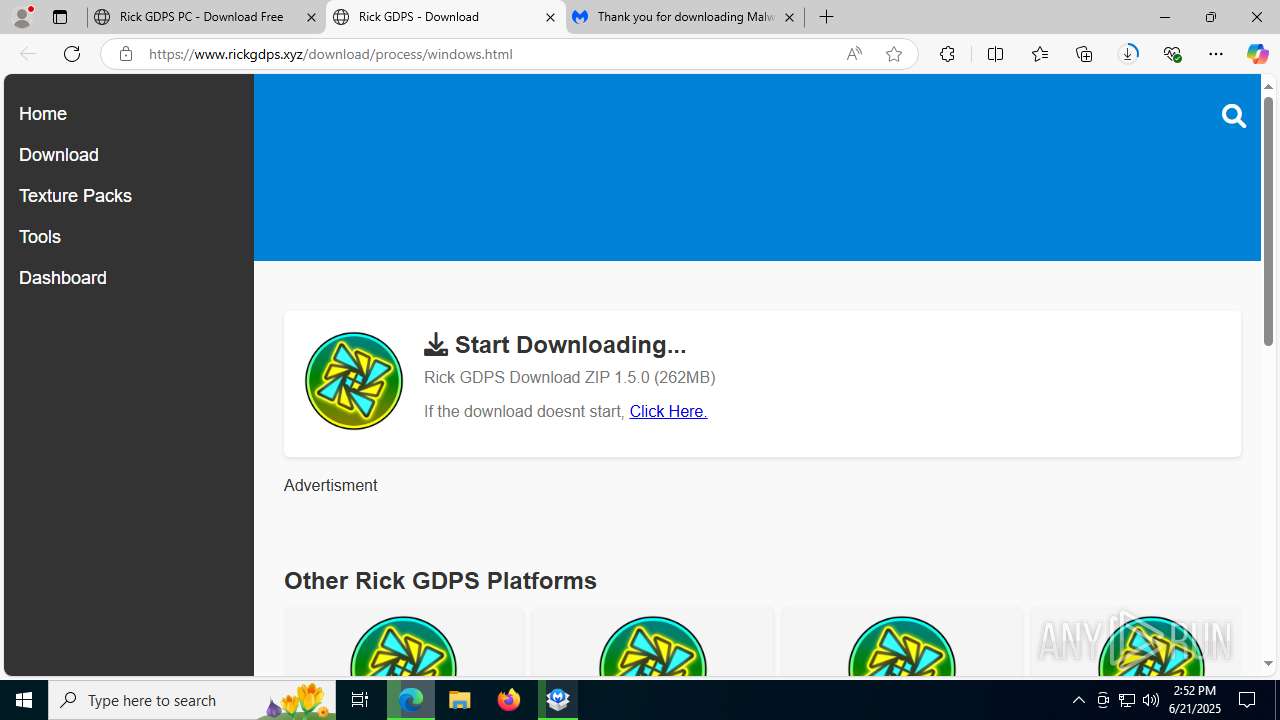
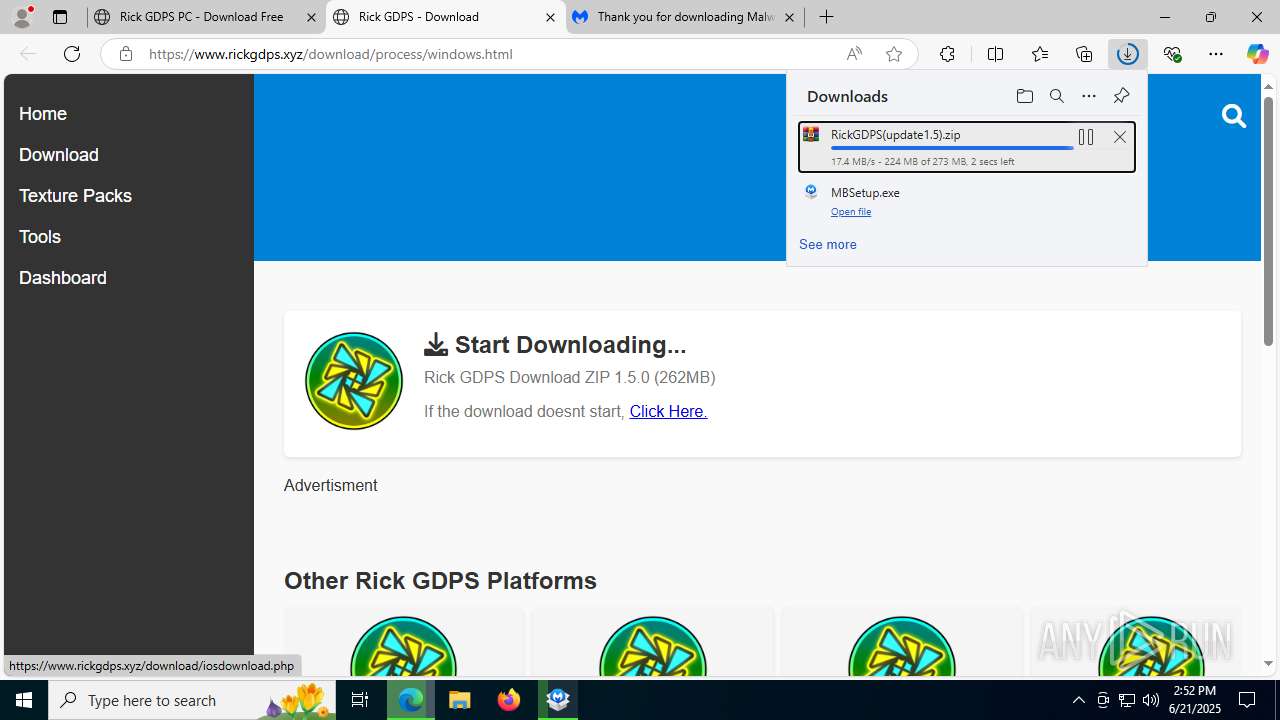
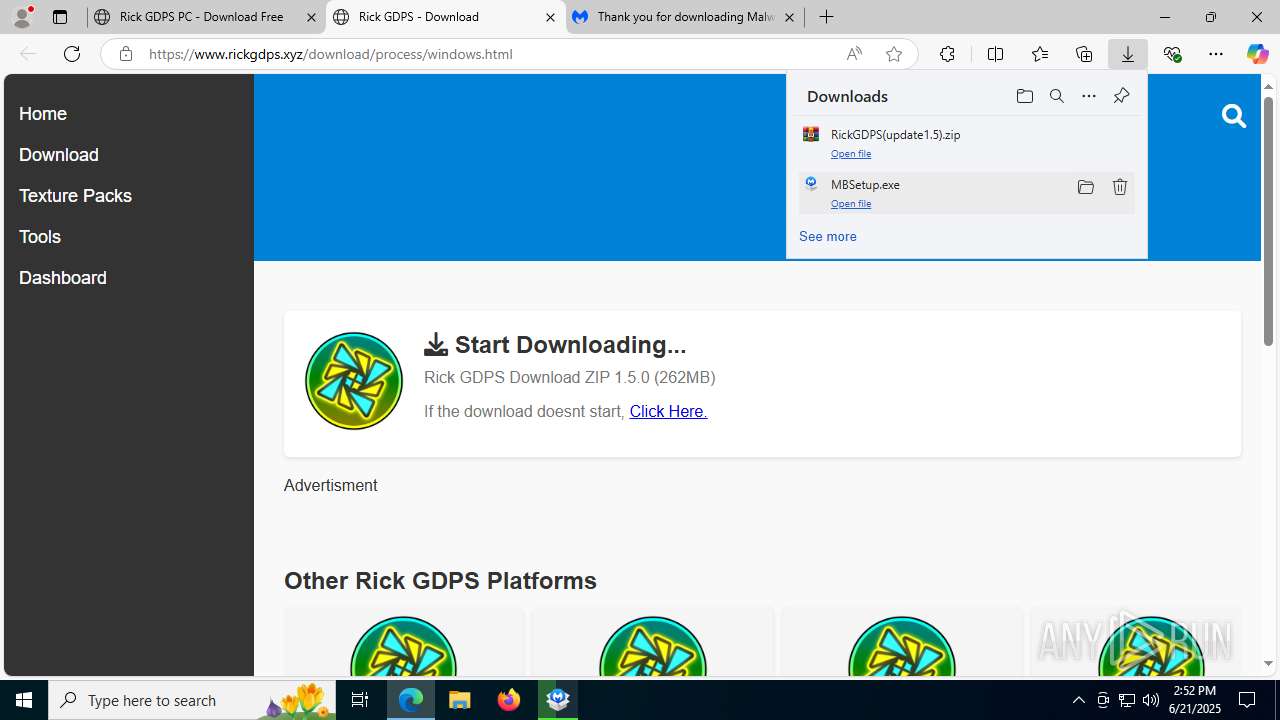
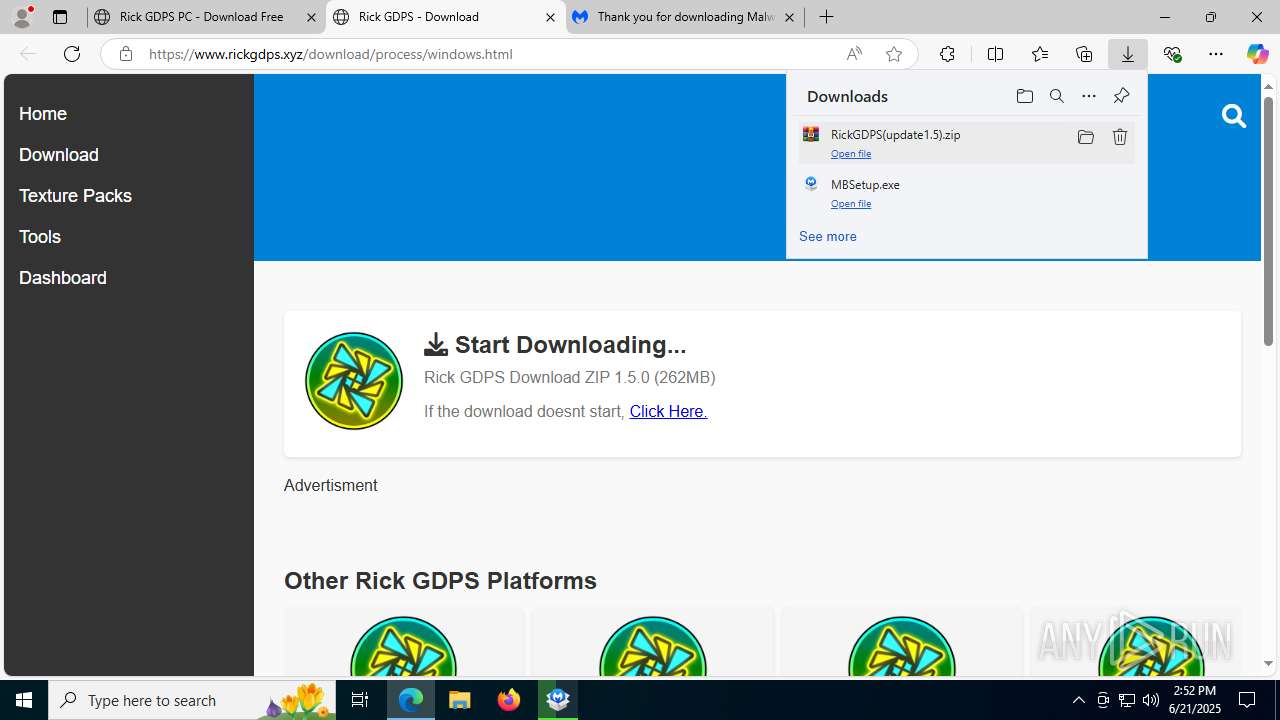
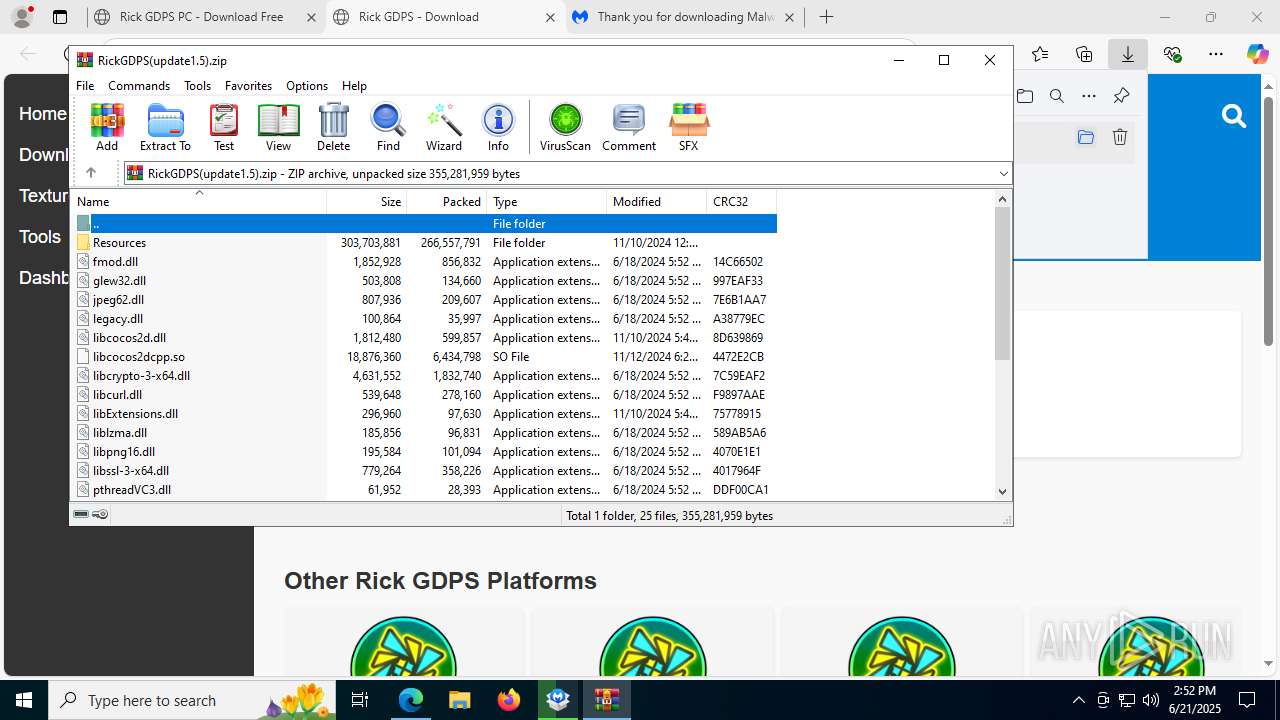
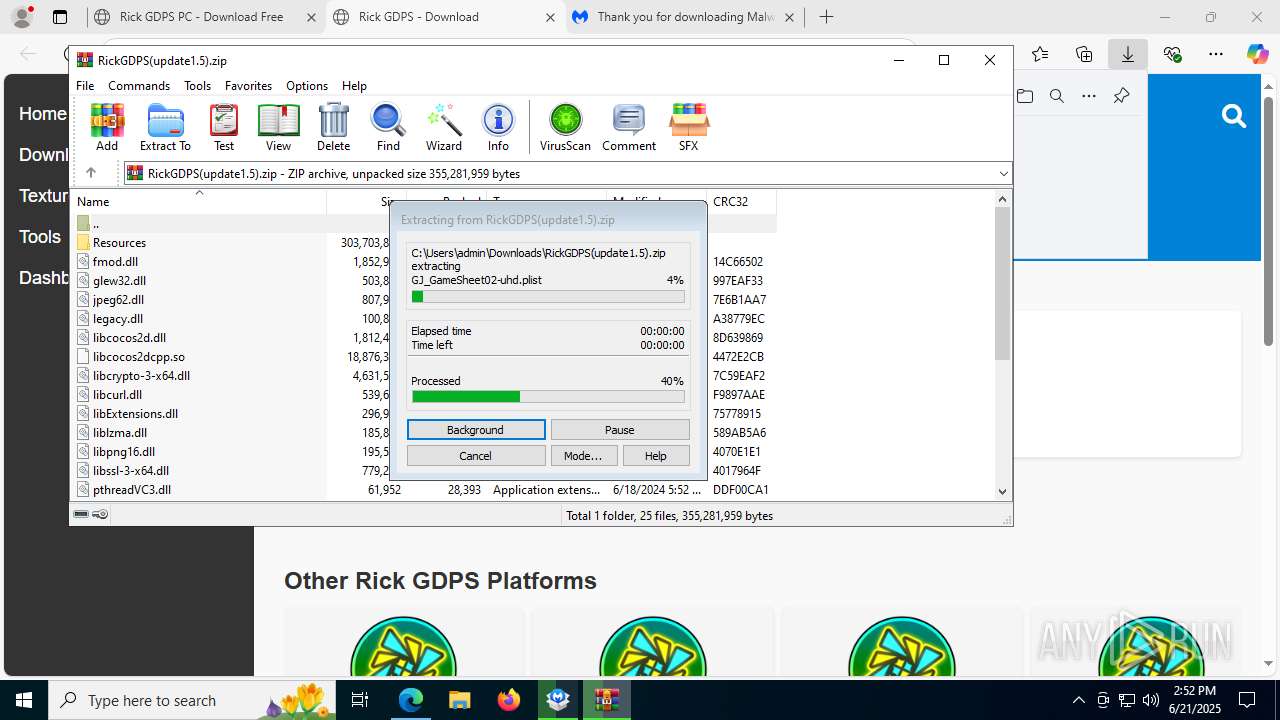
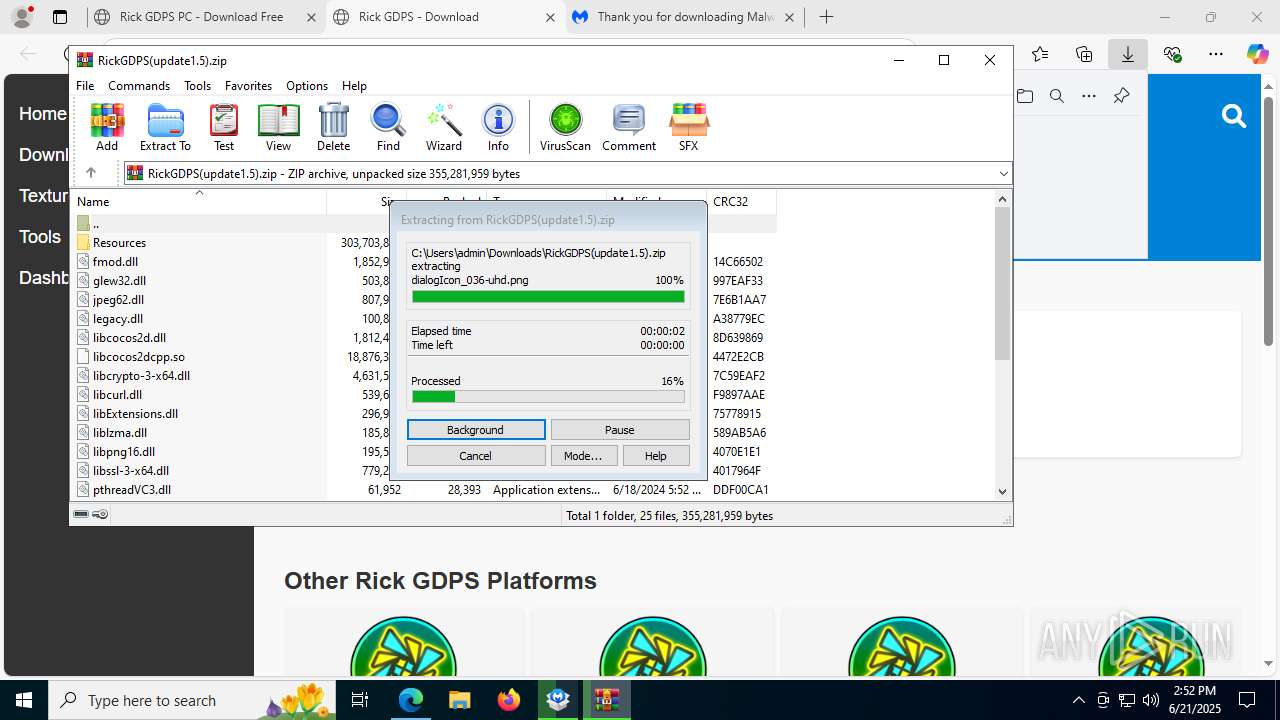
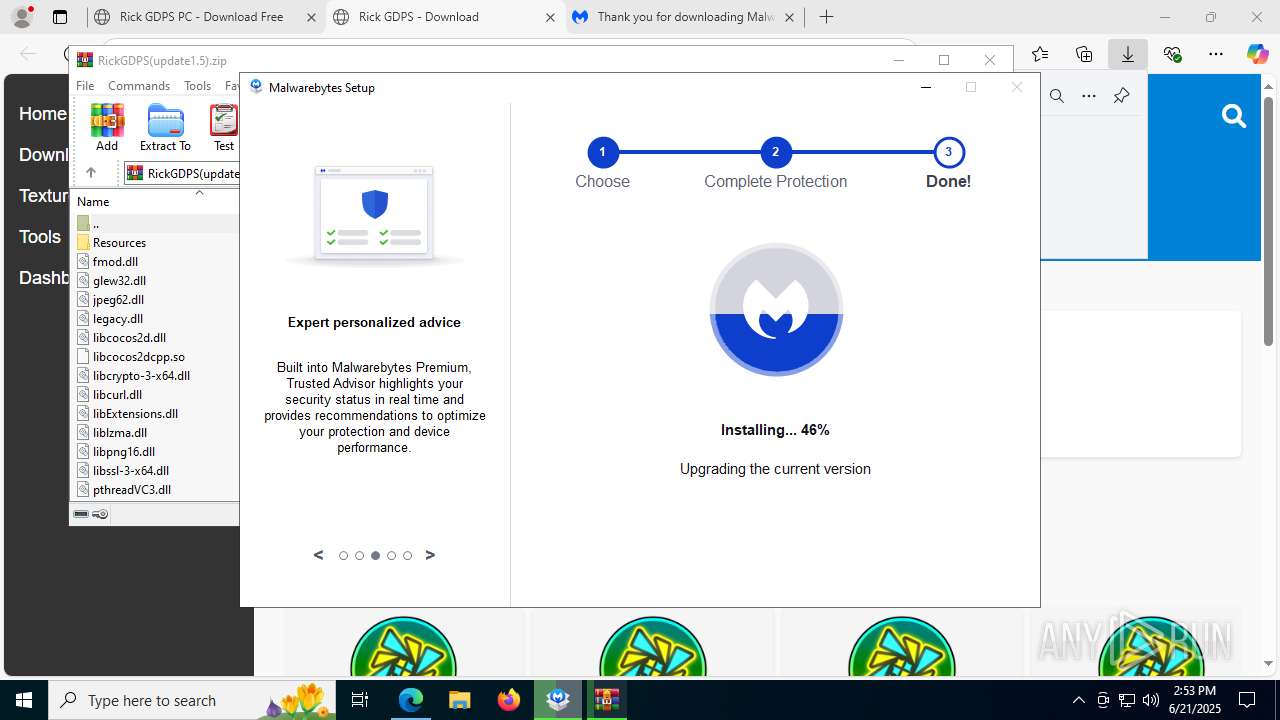
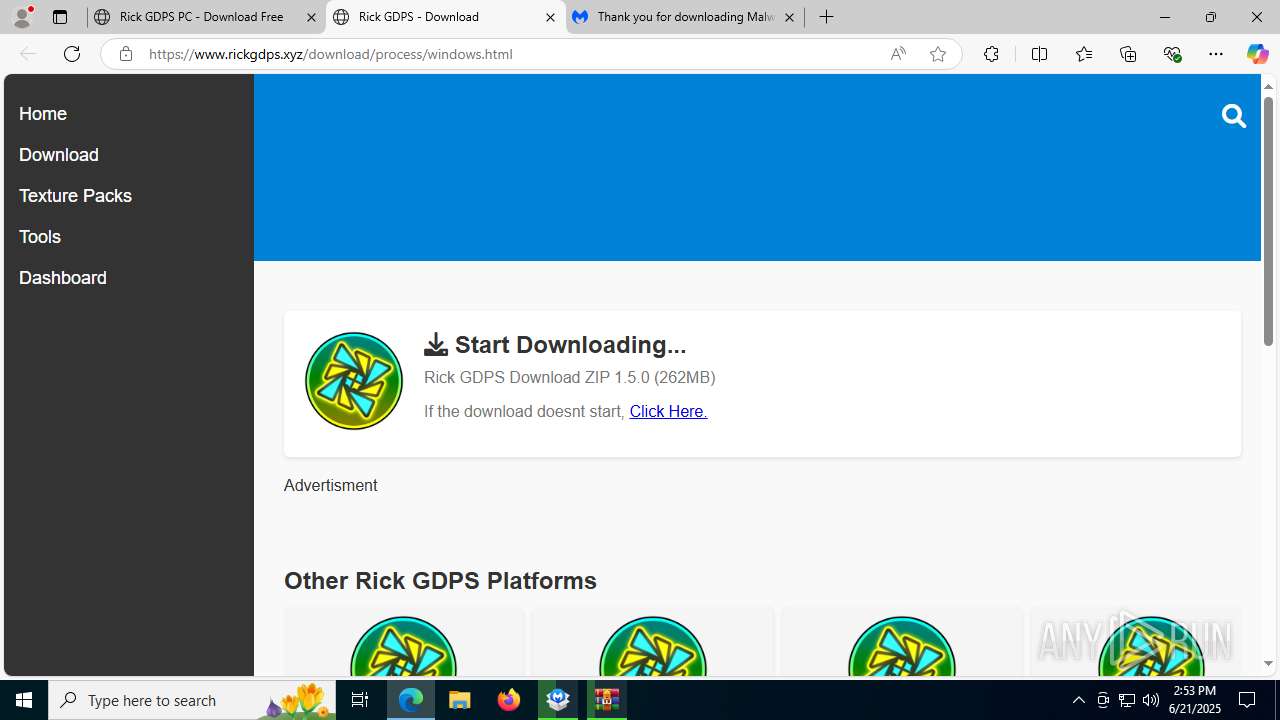
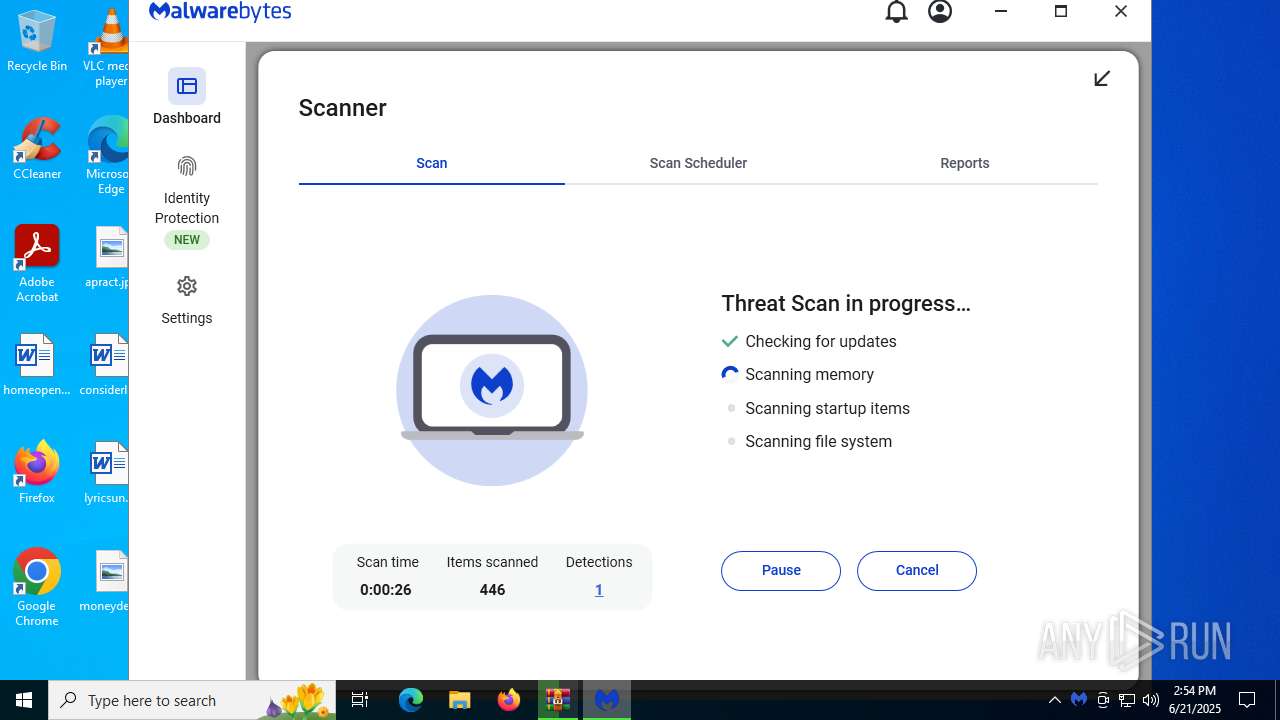
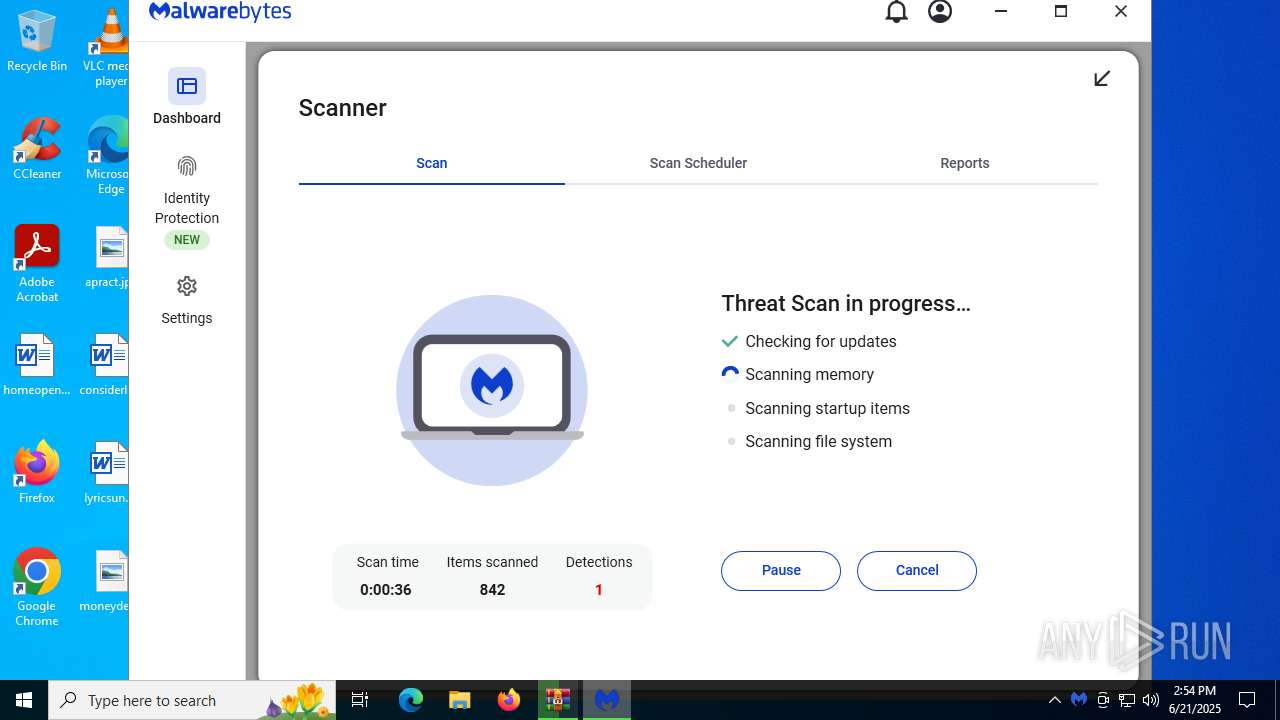
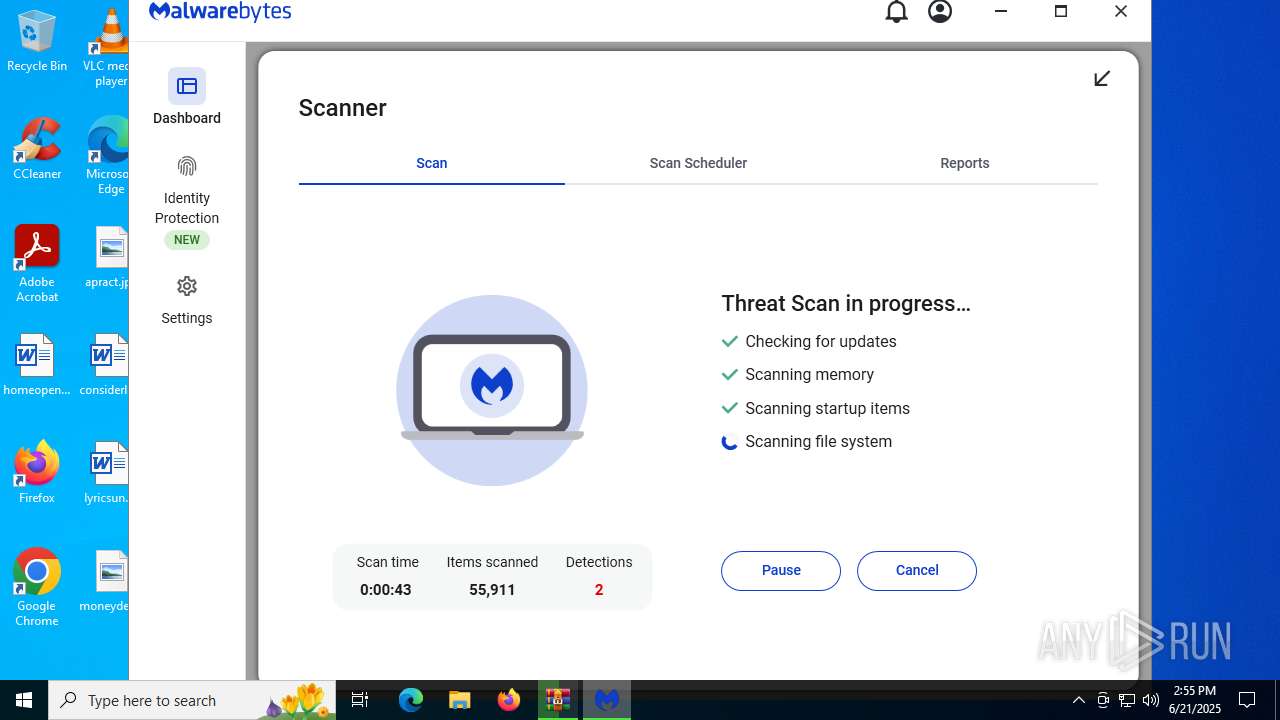
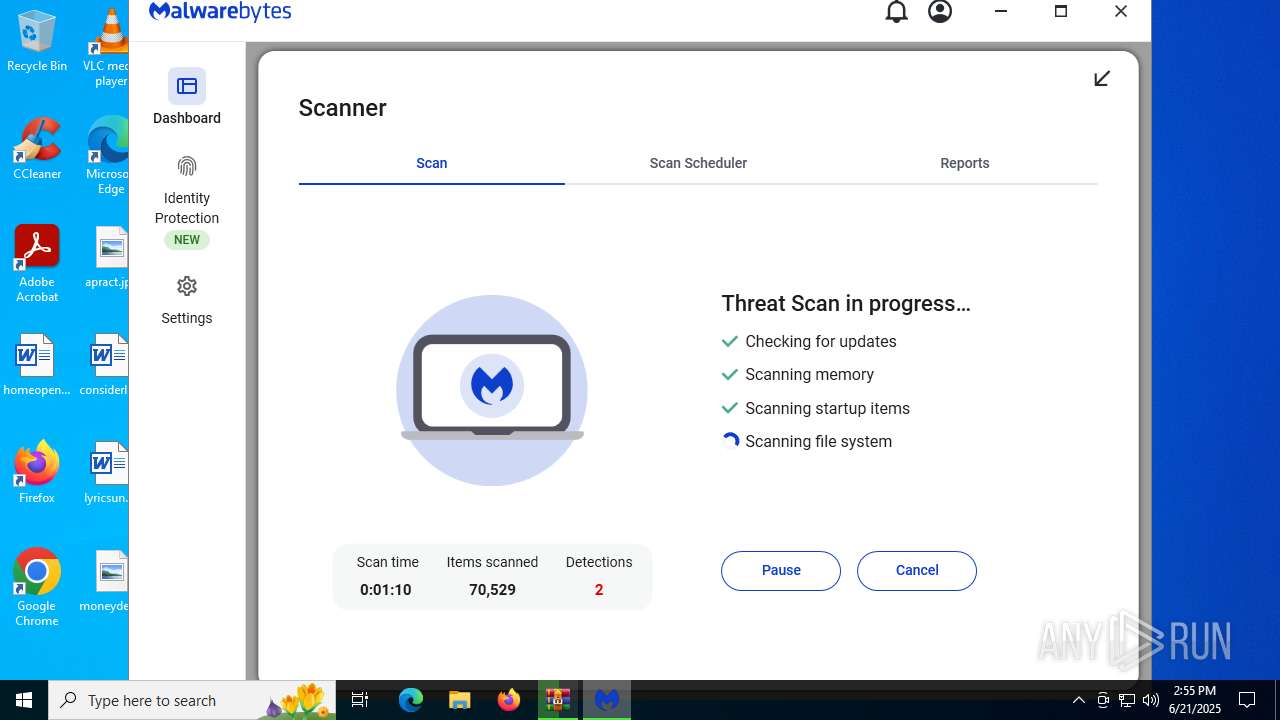
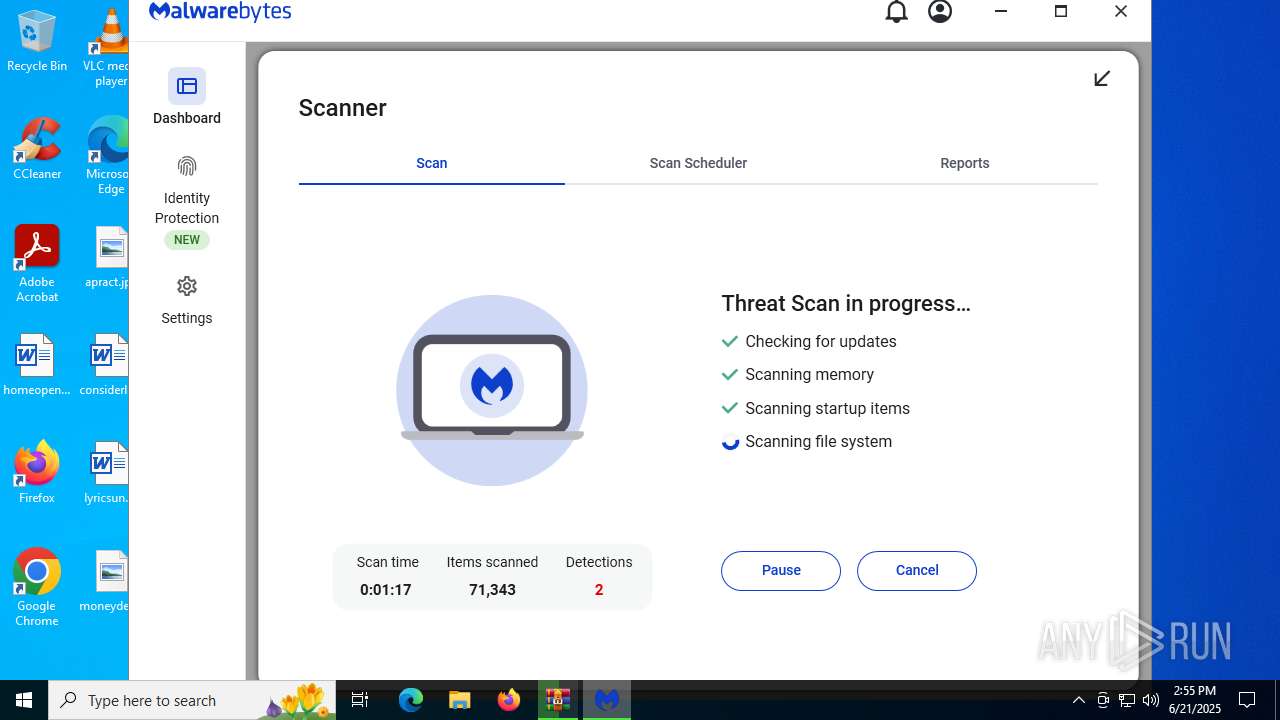
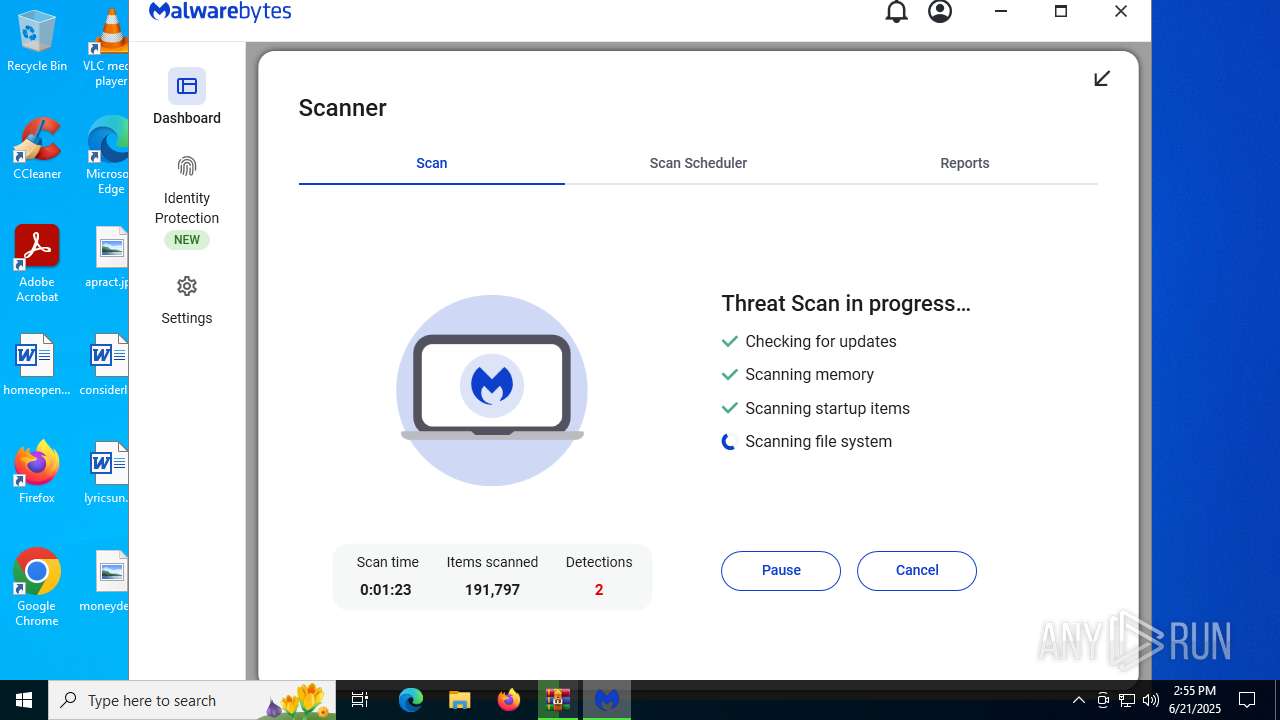
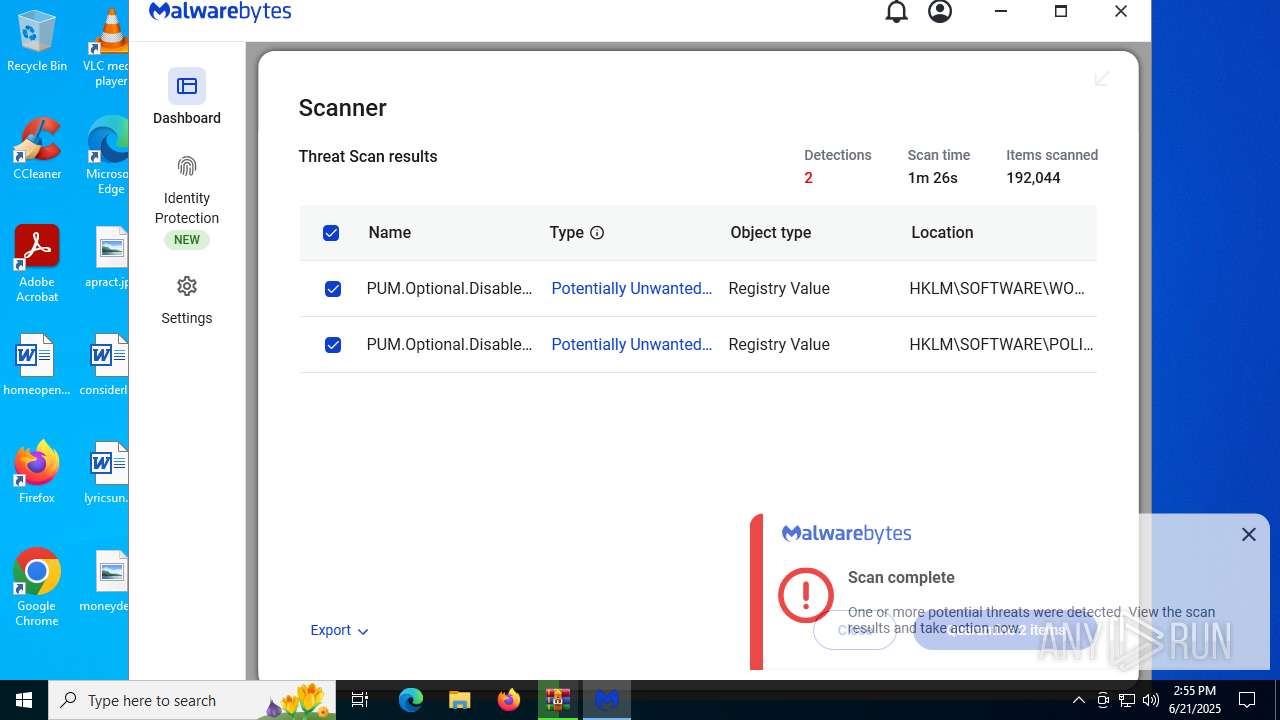
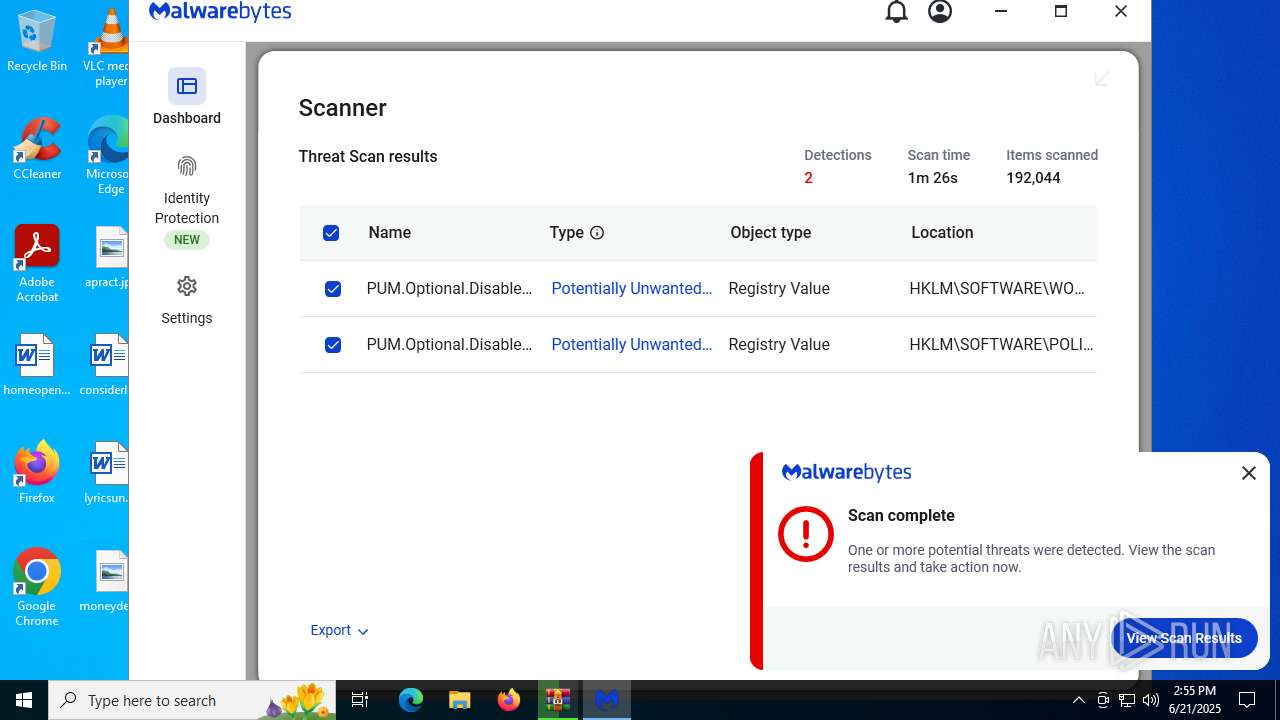
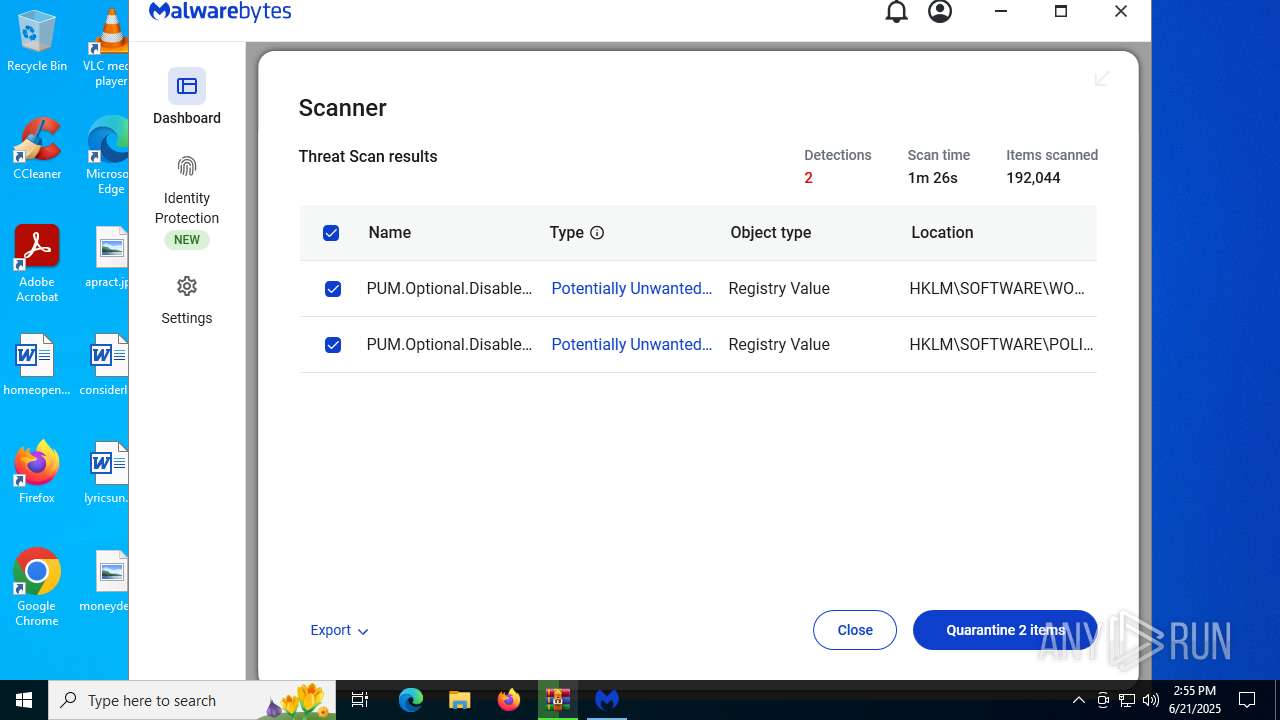
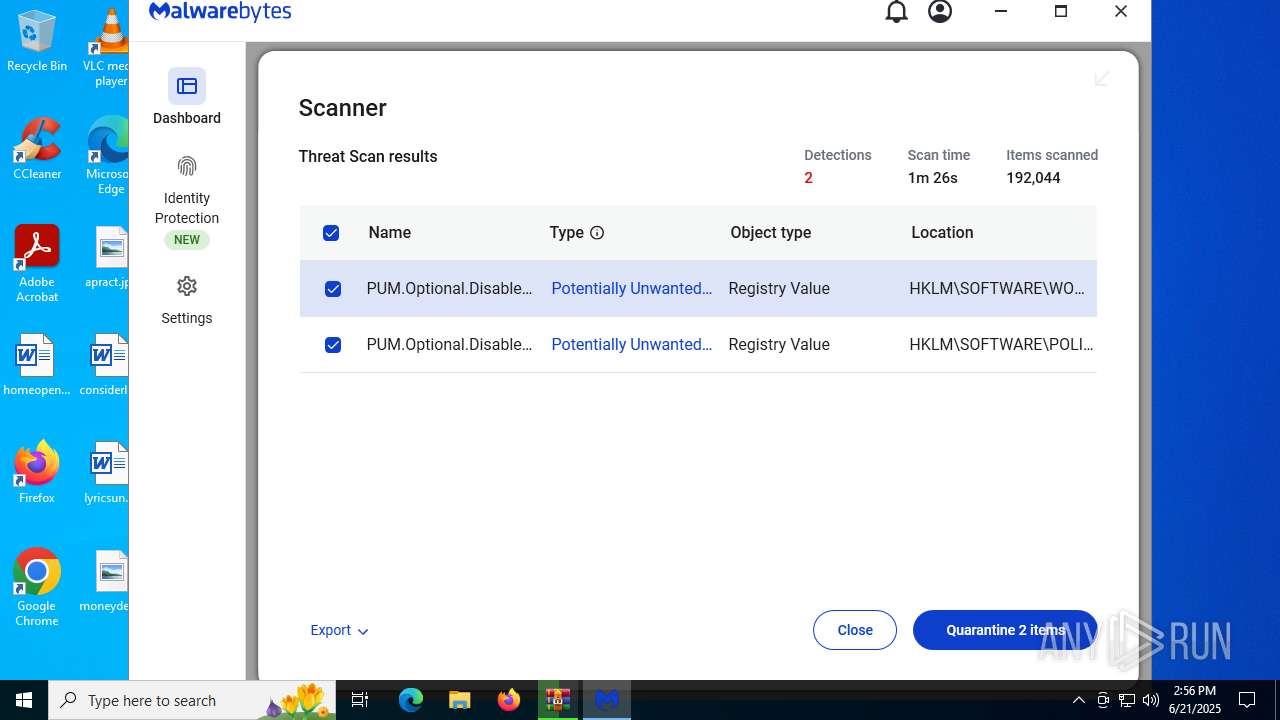
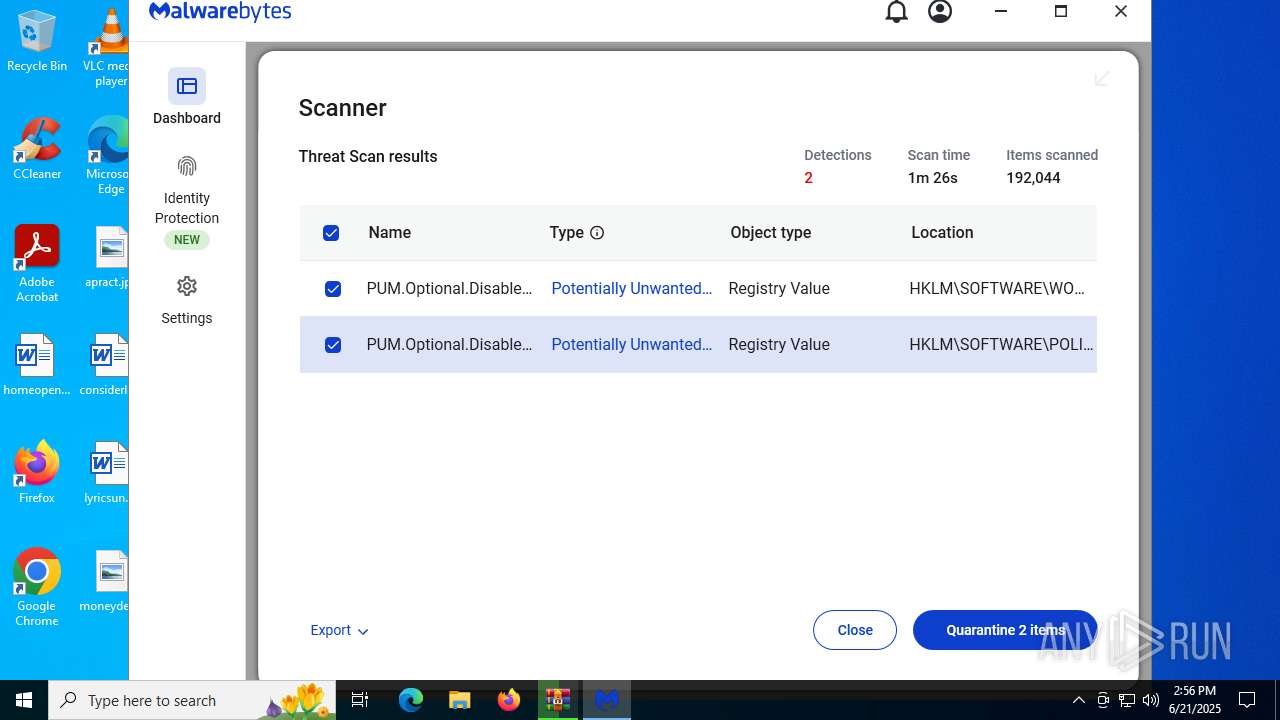
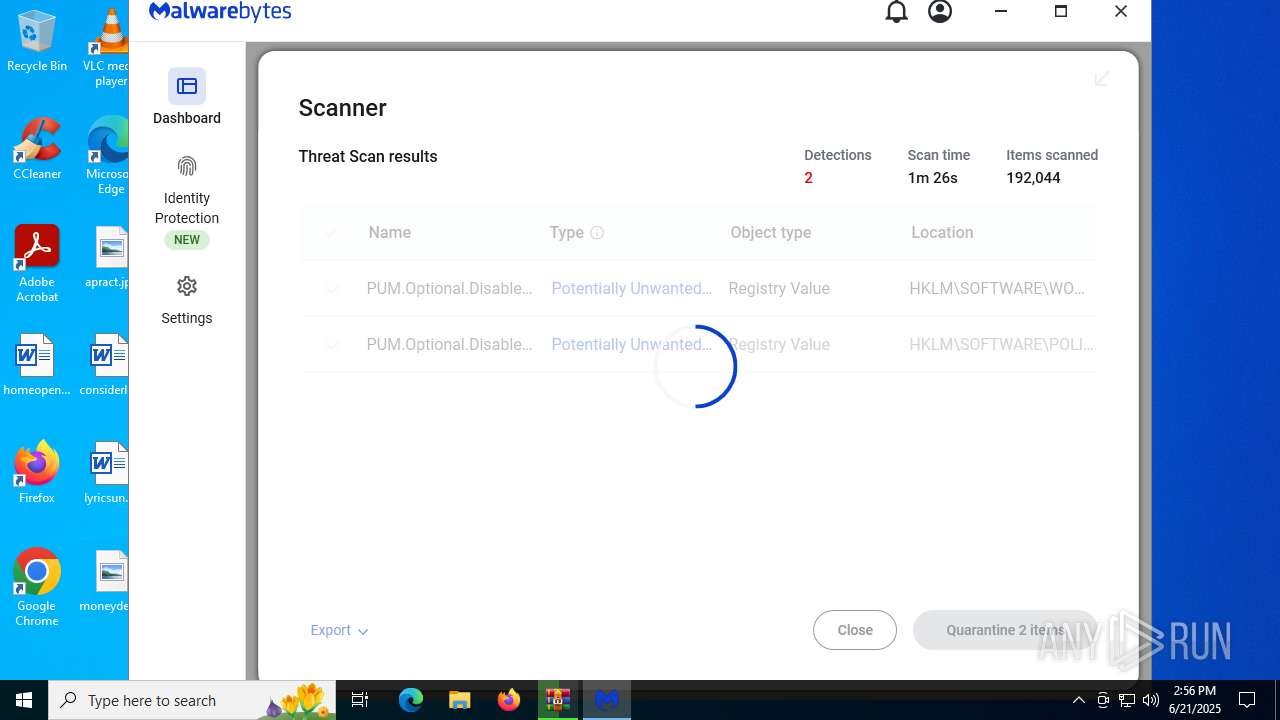
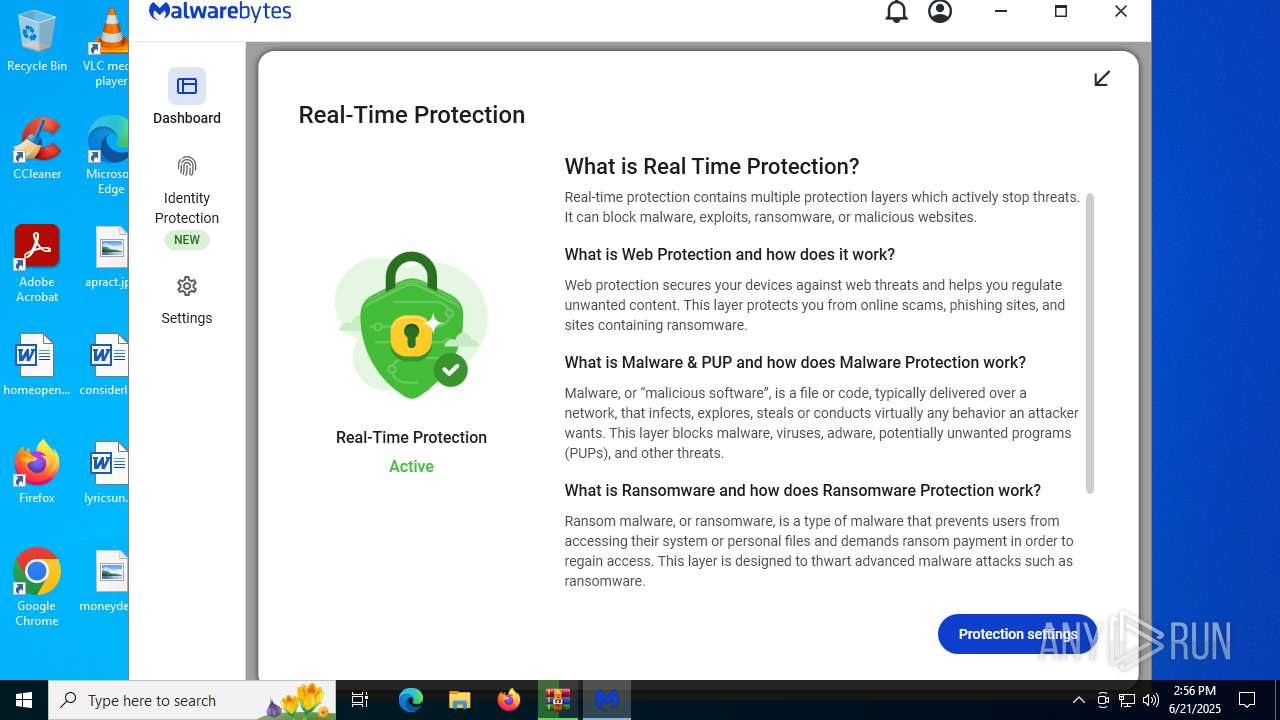
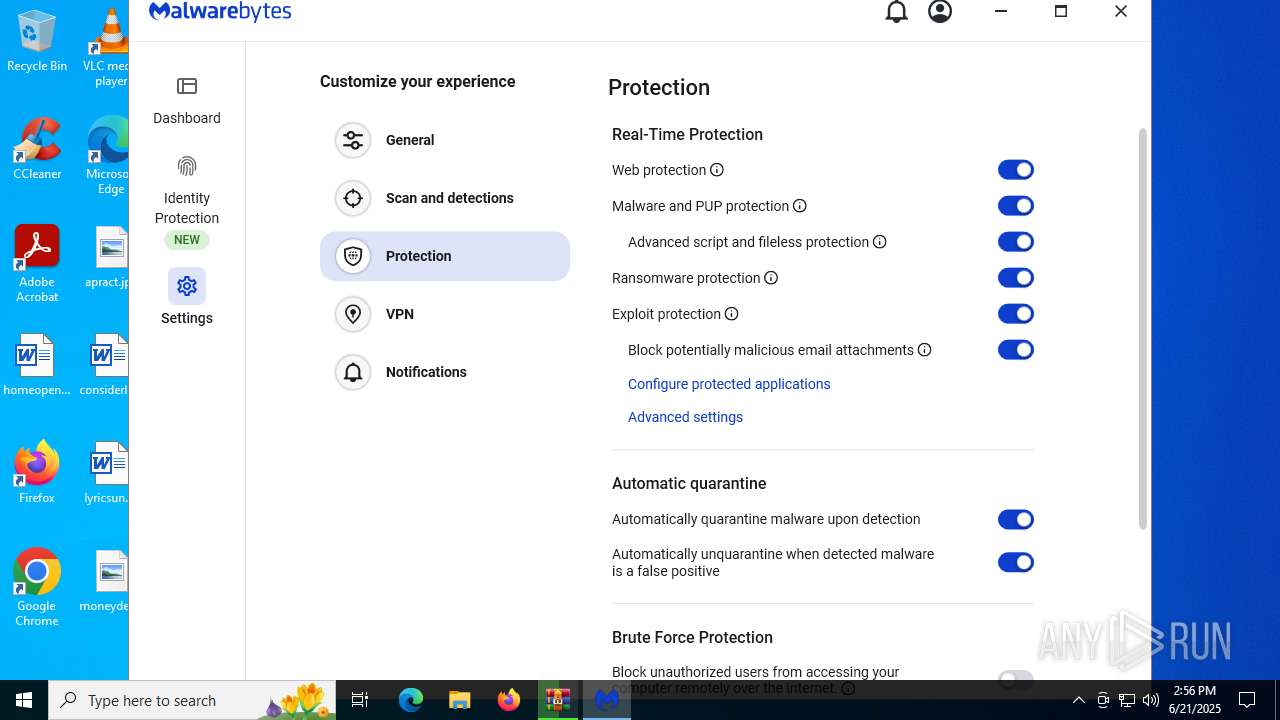
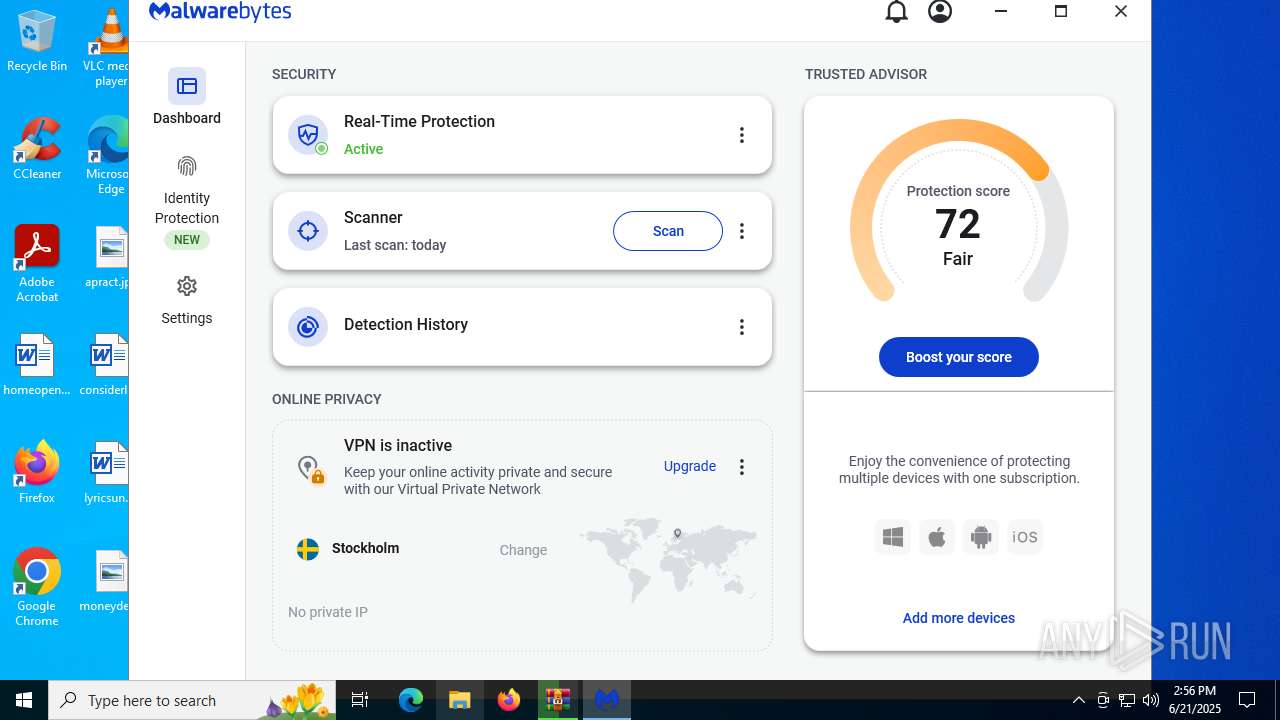
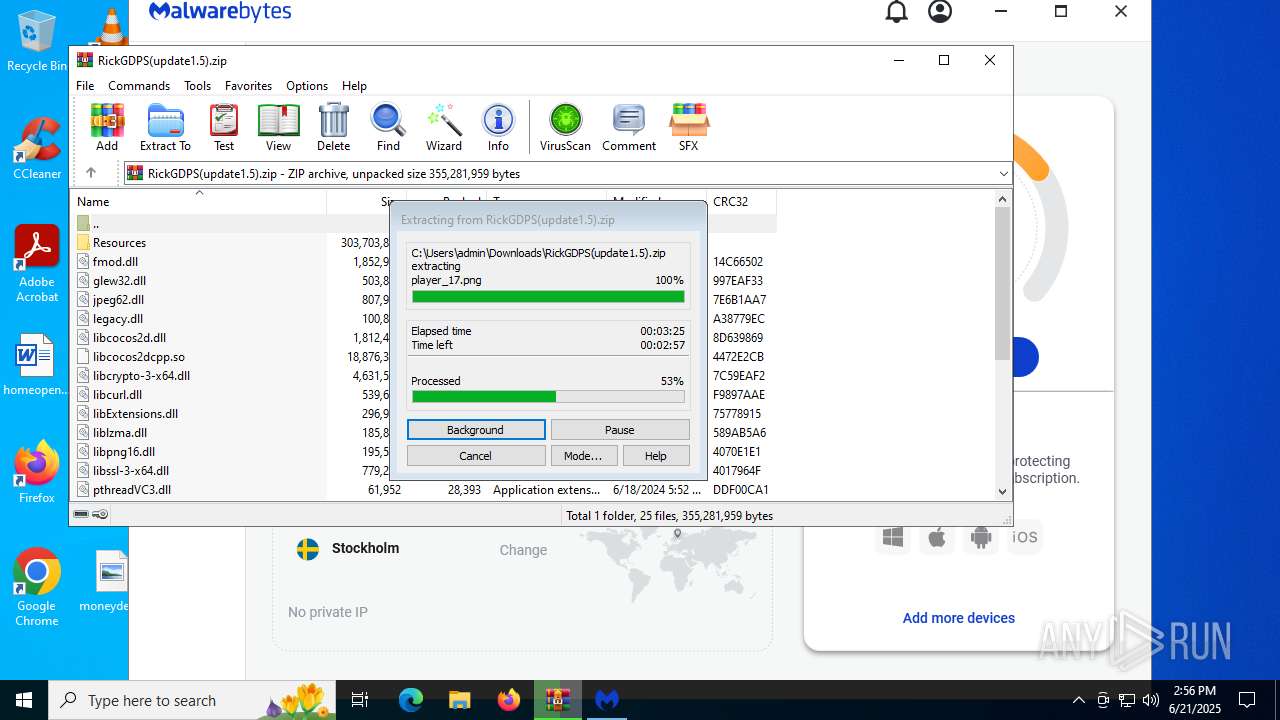
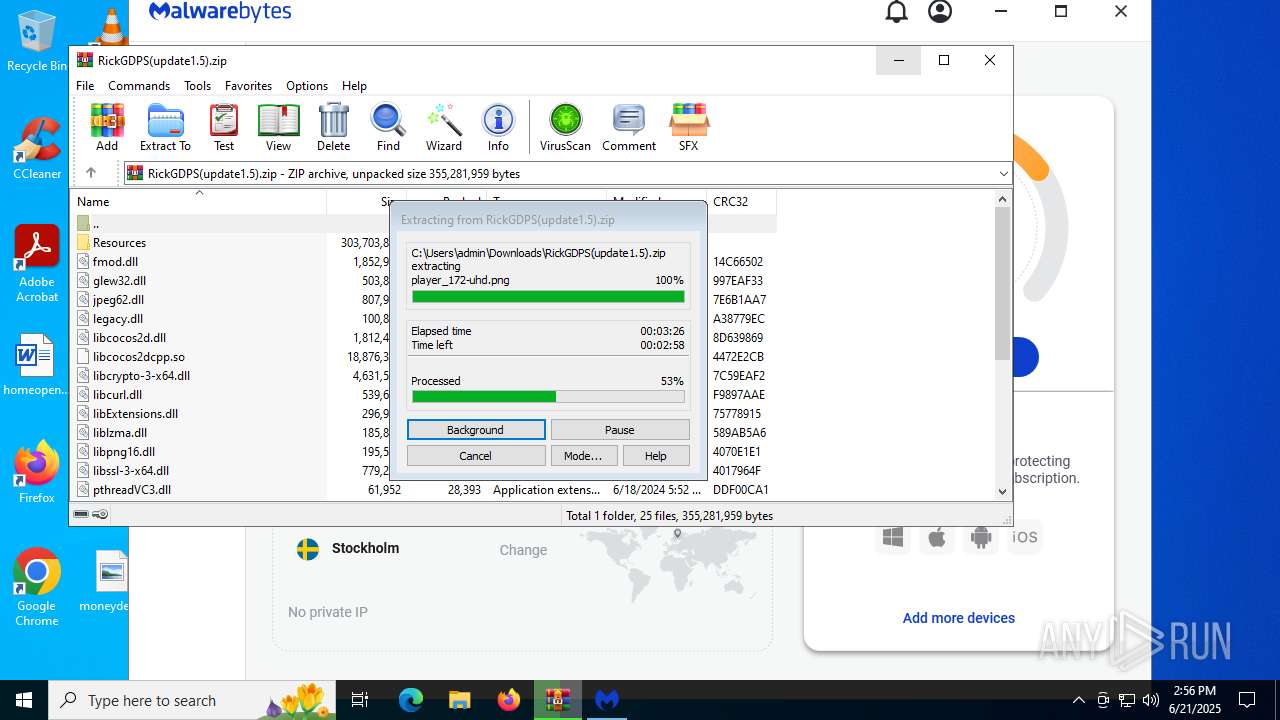
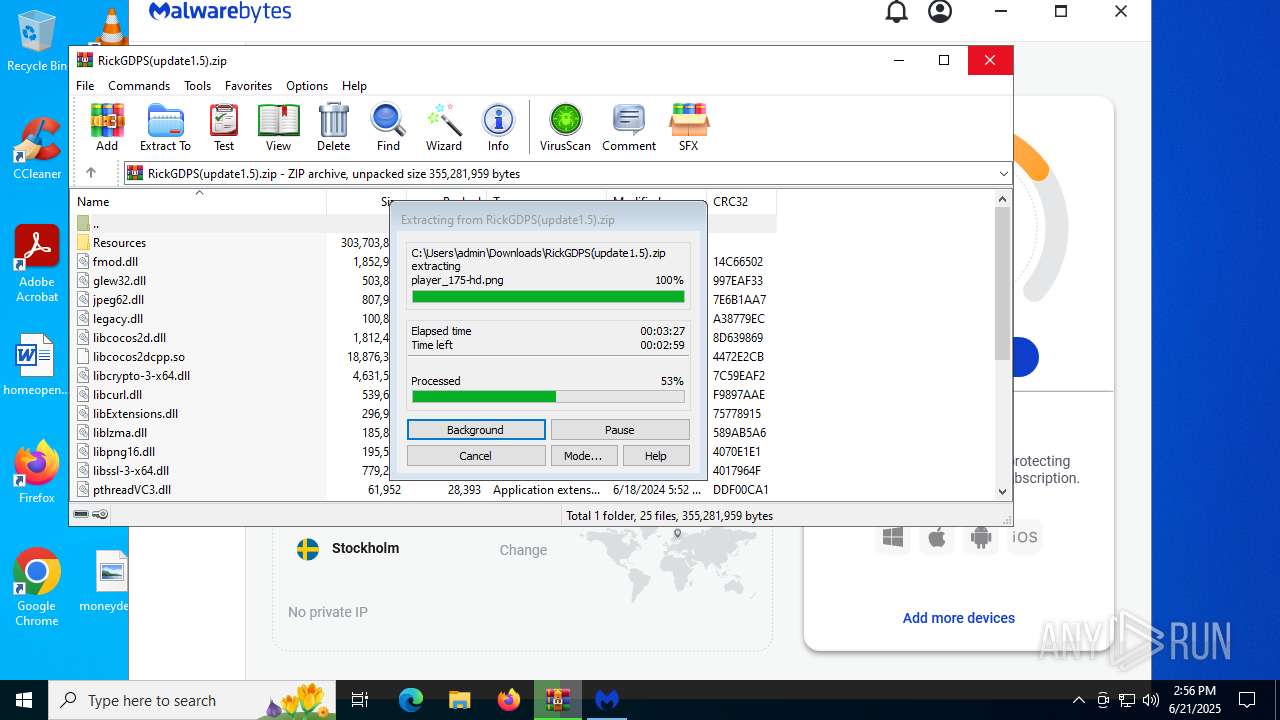
| URL: | https://www.rickgdps.xyz/download/windows.php |
| Full analysis: | https://app.any.run/tasks/2c19bd72-2dfa-4f5e-9d1f-9c21ab1fadfa |
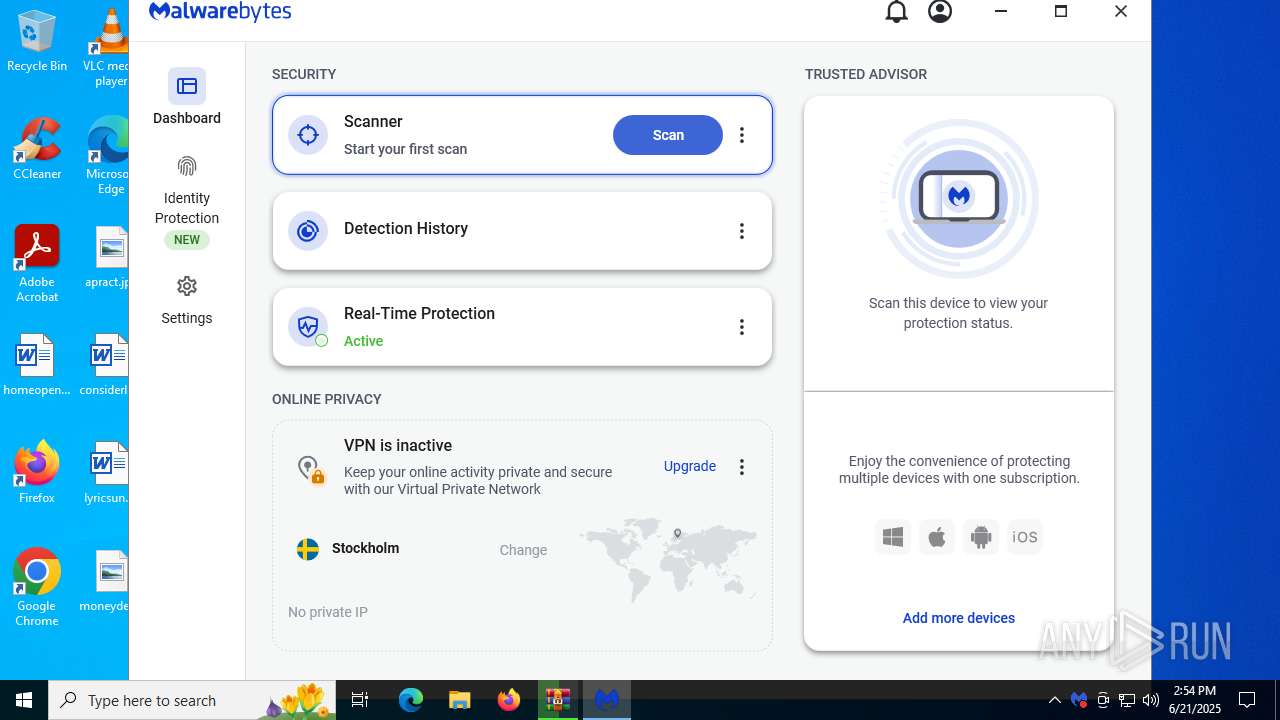
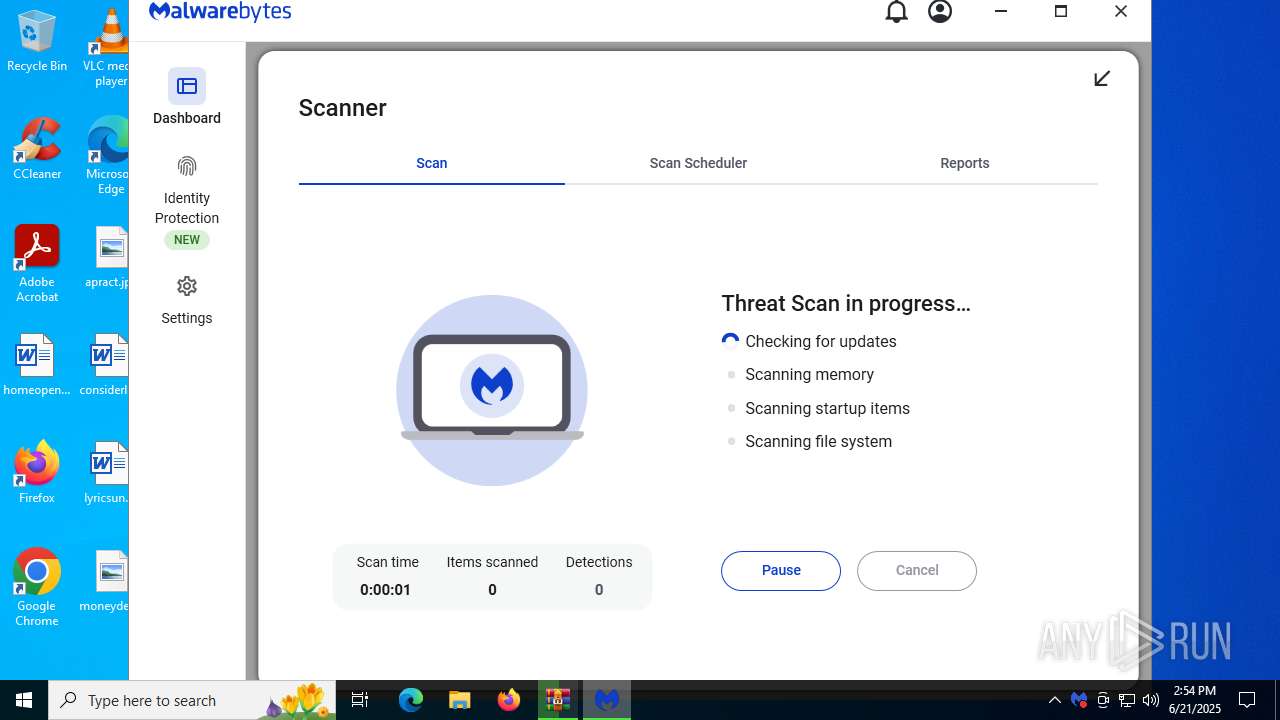
| Verdict: | Malicious activity |
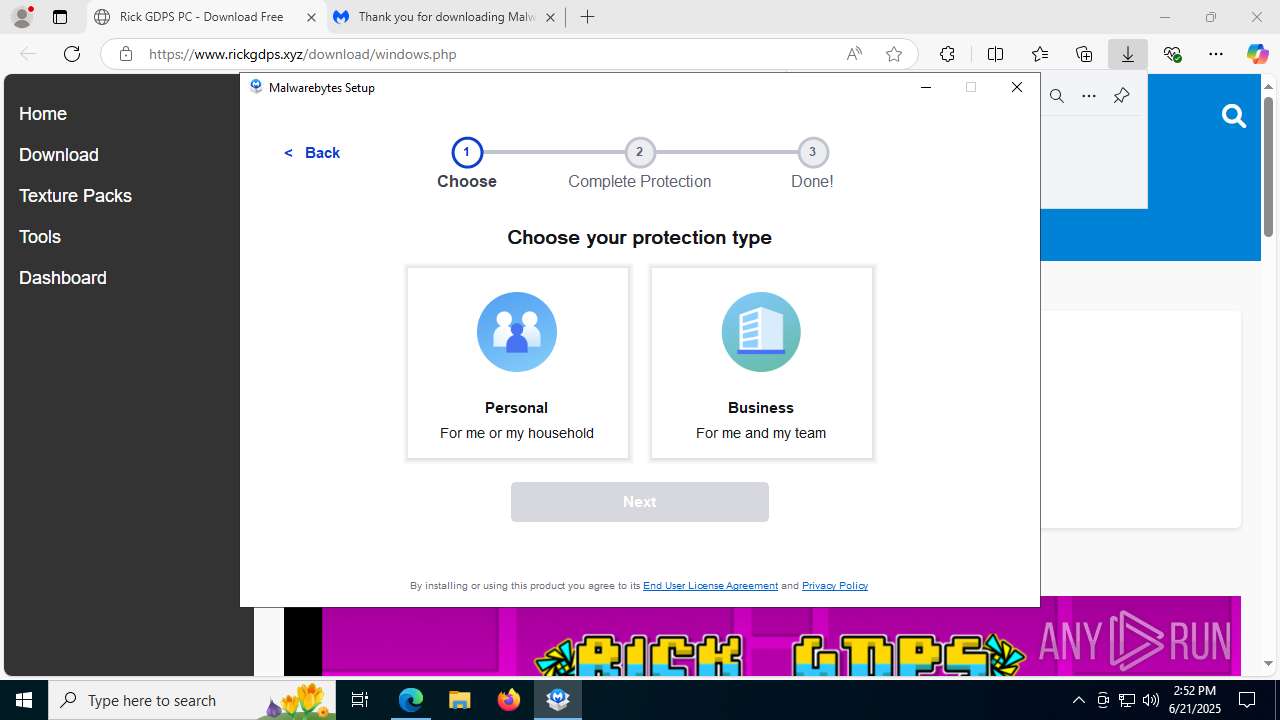
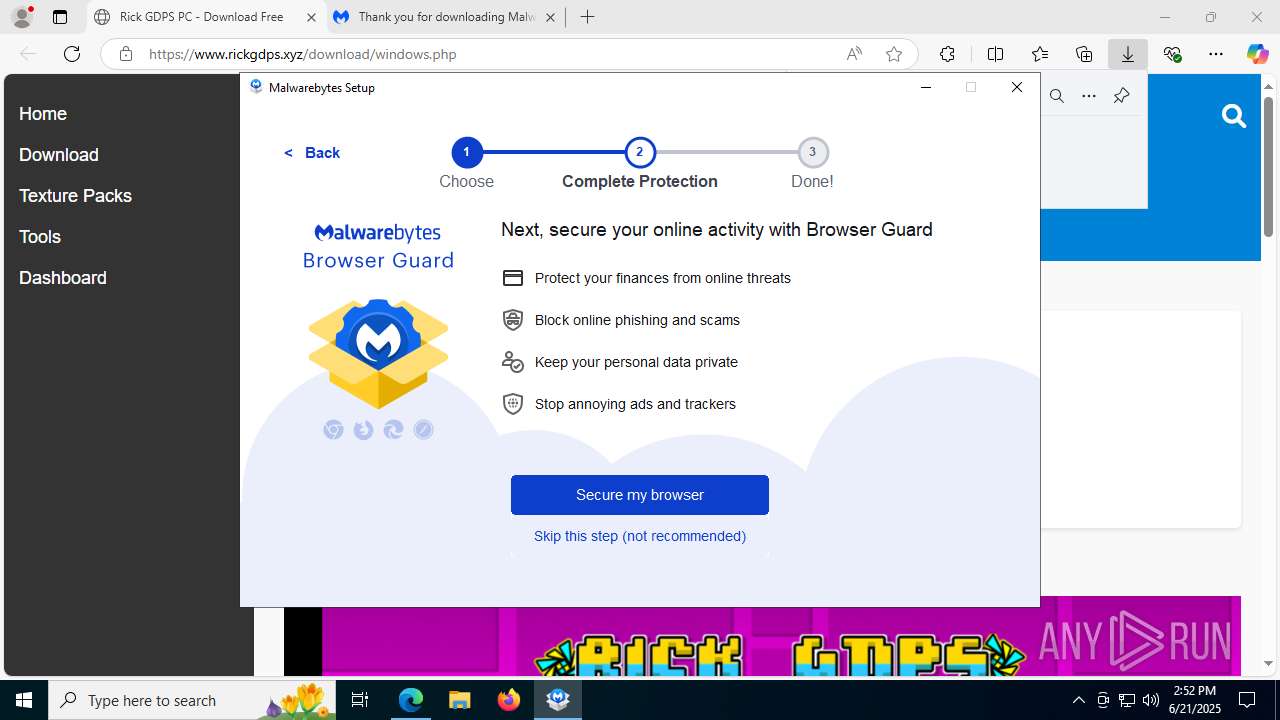
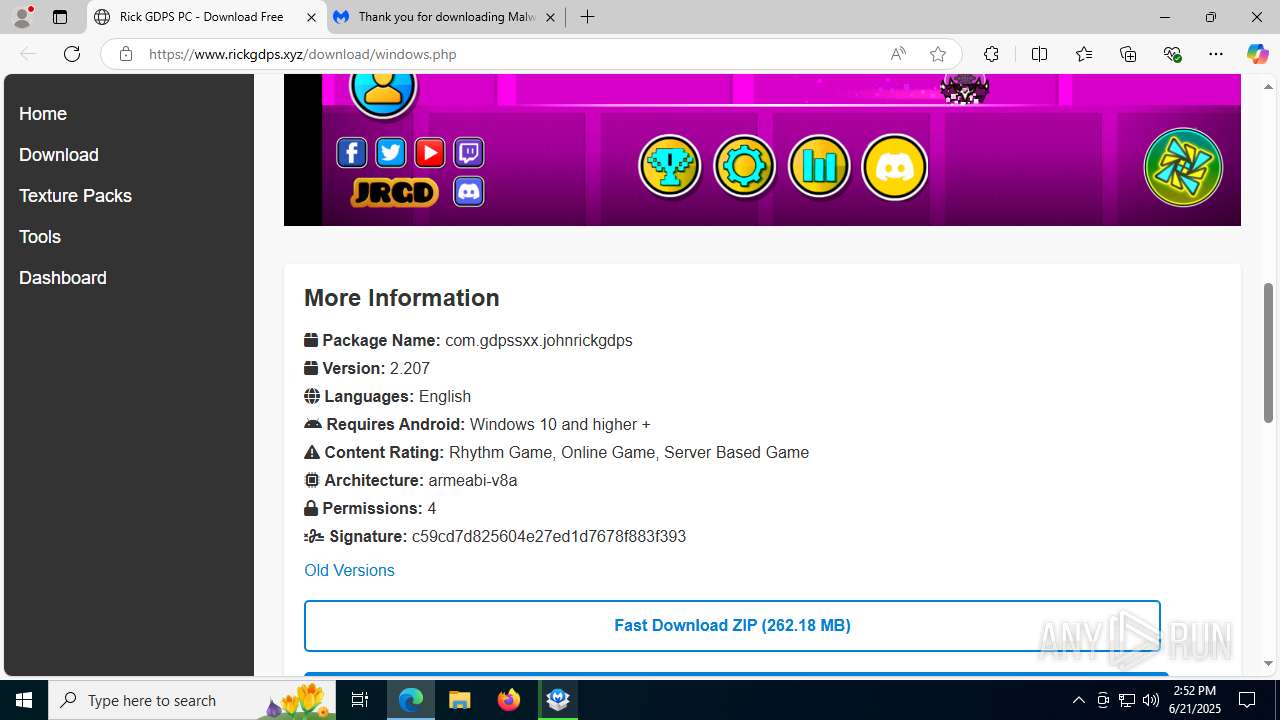
| Threats: | Agent Tesla is spyware that collects information about the actions of its victims by recording keystrokes and user interactions. It is falsely marketed as a legitimate software on the dedicated website where this malware is sold. |
| Analysis date: | June 21, 2025, 14:51:25 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MD5: | 769BAFFF84B76E45A5026C3E4A81C0BE |
| SHA1: | 68356AFD7D12F732FDE0706513448A14E54AD039 |
| SHA256: | ABE849AF5F84C695EEB458A6966CF7EC640123B77E594F2AF317A37DBF836CEA |
| SSDEEP: | 3:N8DSLczMaJCda:2OLczMPa |
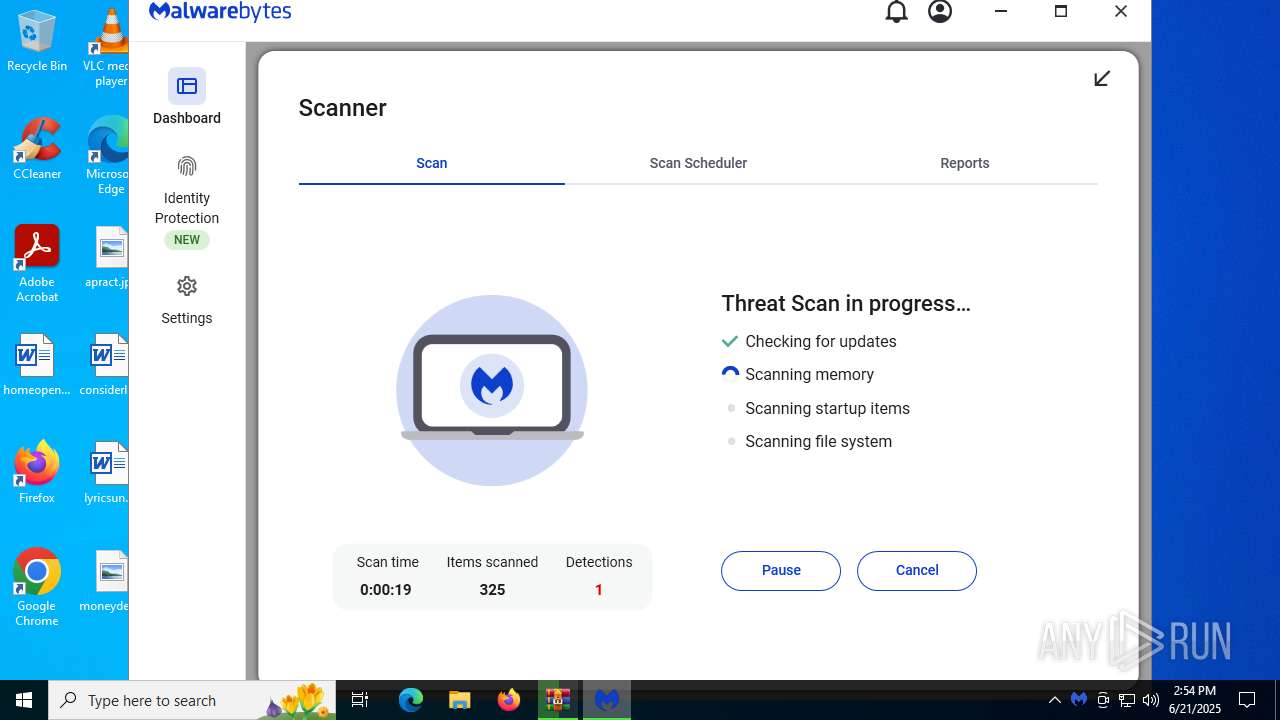
MALICIOUS
PHISHING has been detected (SURICATA)
- msedge.exe (PID: 4920)
Actions looks like stealing of personal data
- MBAMService.exe (PID: 7916)
AGENTTESLA is detected
- MBAMService.exe (PID: 7916)
Steals credentials from Web Browsers
- MBAMService.exe (PID: 7916)
SUSPICIOUS
Searches for installed software
- MBSetup.exe (PID: 1872)
- MBSetup.exe (PID: 4168)
- MBAMInstallerService.exe (PID: 7708)
- MBAMService.exe (PID: 7916)
- Malwarebytes.exe (PID: 2716)
Reads the BIOS version
- MBSetup.exe (PID: 1872)
- MBAMService.exe (PID: 7916)
- mbupdatrV5.exe (PID: 6068)
Creates files in the driver directory
- MBSetup.exe (PID: 1872)
- MBAMInstallerService.exe (PID: 7708)
- MBVpnTunnelService.exe (PID: 7460)
- MBAMService.exe (PID: 3972)
- drvinst.exe (PID: 2348)
- MBAMService.exe (PID: 7916)
Executable content was dropped or overwritten
- MBSetup.exe (PID: 1872)
- MBAMInstallerService.exe (PID: 7708)
- MBVpnTunnelService.exe (PID: 7460)
- drvinst.exe (PID: 2348)
- MBAMService.exe (PID: 3972)
- MBAMService.exe (PID: 7916)
Executes as Windows Service
- MBAMInstallerService.exe (PID: 7708)
- MBAMService.exe (PID: 7916)
The process verifies whether the antivirus software is installed
- MBAMInstallerService.exe (PID: 7708)
- MBSetup.exe (PID: 1872)
- MBVpnTunnelService.exe (PID: 7460)
- drvinst.exe (PID: 2348)
- MBAMService.exe (PID: 3972)
- MBAMService.exe (PID: 7916)
- MBAMWsc.exe (PID: 5552)
- Malwarebytes.exe (PID: 2716)
- Malwarebytes.exe (PID: 2760)
- Malwarebytes.exe (PID: 4664)
- MBAMWsc.exe (PID: 5716)
- mbupdatrV5.exe (PID: 6068)
Drops a system driver (possible attempt to evade defenses)
- MBAMInstallerService.exe (PID: 7708)
- MBVpnTunnelService.exe (PID: 7460)
- MBAMService.exe (PID: 3972)
- drvinst.exe (PID: 2348)
- MBAMService.exe (PID: 7916)
Process drops legitimate windows executable
- MBAMInstallerService.exe (PID: 7708)
- MBAMService.exe (PID: 7916)
The process creates files with name similar to system file names
- MBAMInstallerService.exe (PID: 7708)
The process drops C-runtime libraries
- MBAMInstallerService.exe (PID: 7708)
- MBAMService.exe (PID: 7916)
Drops 7-zip archiver for unpacking
- MBAMInstallerService.exe (PID: 7708)
Adds/modifies Windows certificates
- MBAMInstallerService.exe (PID: 7708)
- MBAMService.exe (PID: 7916)
Changes Internet Explorer settings (feature browser emulation)
- MBAMInstallerService.exe (PID: 7708)
- MBAMService.exe (PID: 7916)
The process checks if it is being run in the virtual environment
- MBAMService.exe (PID: 3972)
- MBAMService.exe (PID: 7916)
Creates/Modifies COM task schedule object
- MBAMService.exe (PID: 7916)
Reads security settings of Internet Explorer
- MBAMService.exe (PID: 7916)
- ig.exe (PID: 7220)
- Malwarebytes.exe (PID: 2716)
Creates or modifies Windows services
- MBAMService.exe (PID: 3972)
- MBAMService.exe (PID: 7916)
Creates a software uninstall entry
- MBAMInstallerService.exe (PID: 7708)
Application launched itself
- Malwarebytes.exe (PID: 2760)
Starts application from unusual location
- MBAMService.exe (PID: 7916)
There is functionality for taking screenshot (YARA)
- Malwarebytes.exe (PID: 2716)
Read startup parameters
- MBAMService.exe (PID: 7916)
Creates file in the systems drive root
- MBAMService.exe (PID: 7916)
Reads browser cookies
- MBAMService.exe (PID: 7916)
INFO
Executable content was dropped or overwritten
- msedge.exe (PID: 1720)
- msedge.exe (PID: 4920)
Reads the computer name
- identity_helper.exe (PID: 7832)
- identity_helper.exe (PID: 8092)
- MBSetup.exe (PID: 1872)
- MBAMInstallerService.exe (PID: 7708)
- identity_helper.exe (PID: 4892)
- MBVpnTunnelService.exe (PID: 7460)
- MBAMService.exe (PID: 3972)
- drvinst.exe (PID: 2348)
- MBAMService.exe (PID: 7916)
- identity_helper.exe (PID: 4500)
- ig.exe (PID: 7220)
- MBAMWsc.exe (PID: 5552)
- Malwarebytes.exe (PID: 2716)
- Malwarebytes.exe (PID: 4664)
- Malwarebytes.exe (PID: 2760)
- MBAMWsc.exe (PID: 5716)
- mbupdatrV5.exe (PID: 6068)
- ig.exe (PID: 2028)
Reads Environment values
- identity_helper.exe (PID: 7832)
- identity_helper.exe (PID: 8092)
- identity_helper.exe (PID: 4892)
- identity_helper.exe (PID: 4500)
- MBAMService.exe (PID: 7916)
Application launched itself
- msedge.exe (PID: 1720)
- msedge.exe (PID: 4860)
Checks supported languages
- identity_helper.exe (PID: 8092)
- MBSetup.exe (PID: 4168)
- MBAMInstallerService.exe (PID: 7708)
- MBSetup.exe (PID: 1872)
- MBVpnTunnelService.exe (PID: 7460)
- identity_helper.exe (PID: 4892)
- MBAMService.exe (PID: 3972)
- drvinst.exe (PID: 2348)
- MBAMService.exe (PID: 7916)
- identity_helper.exe (PID: 4500)
- ig.exe (PID: 7220)
- MBAMWsc.exe (PID: 5552)
- Malwarebytes.exe (PID: 2716)
- Malwarebytes.exe (PID: 2760)
- Malwarebytes.exe (PID: 4664)
- mbupdatrV5.exe (PID: 6068)
- MBAMWsc.exe (PID: 5716)
- ig.exe (PID: 2028)
- identity_helper.exe (PID: 7832)
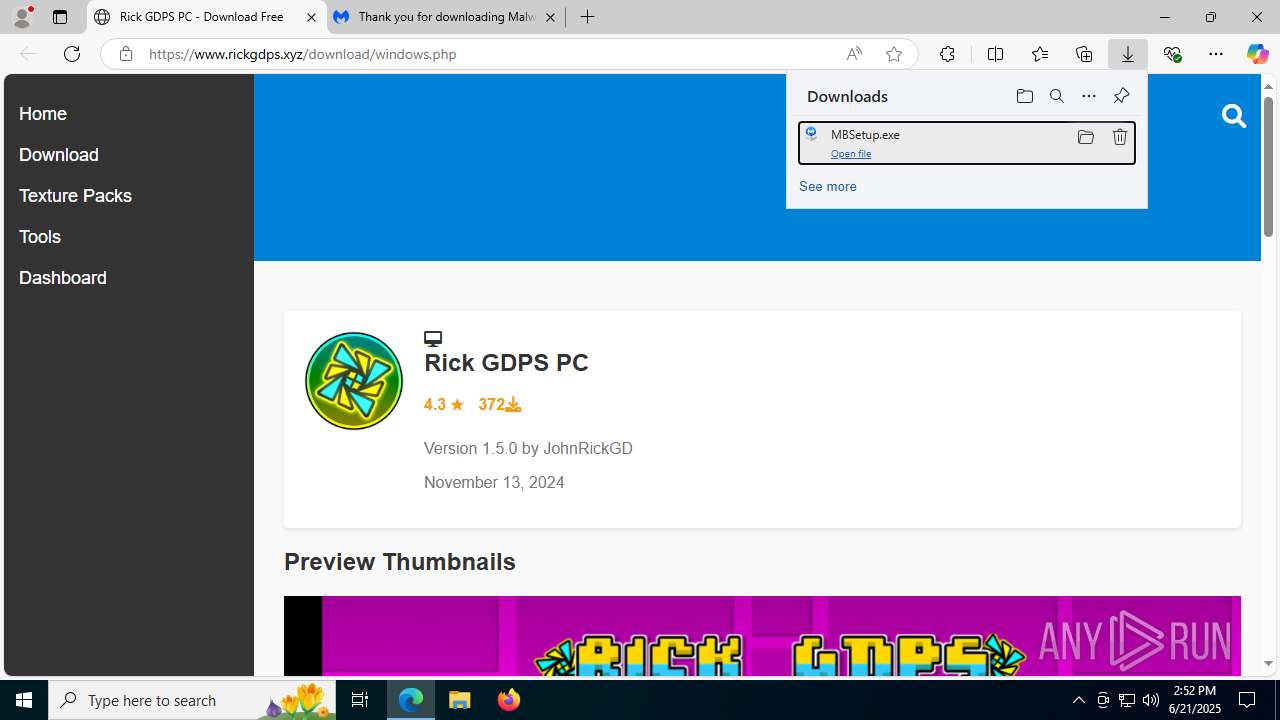
Launching a file from the Downloads directory
- msedge.exe (PID: 1720)
Create files in a temporary directory
- MBSetup.exe (PID: 1872)
Reads the machine GUID from the registry
- MBSetup.exe (PID: 1872)
- MBAMInstallerService.exe (PID: 7708)
- drvinst.exe (PID: 2348)
- MBAMService.exe (PID: 7916)
- mbupdatrV5.exe (PID: 6068)
The sample compiled with english language support
- msedge.exe (PID: 4920)
- MBSetup.exe (PID: 1872)
- MBAMInstallerService.exe (PID: 7708)
- MBVpnTunnelService.exe (PID: 7460)
- drvinst.exe (PID: 2348)
- MBAMService.exe (PID: 3972)
- MBAMService.exe (PID: 7916)
- msedge.exe (PID: 1720)
Creates files in the program directory
- MBSetup.exe (PID: 1872)
- MBAMInstallerService.exe (PID: 7708)
- MBVpnTunnelService.exe (PID: 7460)
- MBAMService.exe (PID: 7916)
- Malwarebytes.exe (PID: 2716)
- mbupdatrV5.exe (PID: 6068)
Checks proxy server information
- MBSetup.exe (PID: 1872)
- slui.exe (PID: 4100)
- Malwarebytes.exe (PID: 2716)
Reads the software policy settings
- MBSetup.exe (PID: 1872)
- MBAMInstallerService.exe (PID: 7708)
- slui.exe (PID: 4100)
- drvinst.exe (PID: 2348)
- MBAMService.exe (PID: 7916)
- Malwarebytes.exe (PID: 2716)
The sample compiled with spanish language support
- MBAMInstallerService.exe (PID: 7708)
Reads Microsoft Office registry keys
- msedge.exe (PID: 1720)
Adds/modifies Windows certificates
- drvinst.exe (PID: 2348)
Reads the time zone
- MBAMService.exe (PID: 7916)
Reads CPU info
- MBAMService.exe (PID: 7916)
CONNECTWISE has been detected
- MBAMService.exe (PID: 7916)
Creates files or folders in the user directory
- Malwarebytes.exe (PID: 2716)
- ig.exe (PID: 2028)
Manual execution by a user
- Malwarebytes.exe (PID: 2760)
Process checks whether UAC notifications are on
- Malwarebytes.exe (PID: 2716)
Process checks computer location settings
- Malwarebytes.exe (PID: 2716)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
261
Monitored processes
107
Malicious processes
14
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 436 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=renderer --string-annotations --disable-gpu-compositing --video-capture-use-gpu-memory-buffer --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=29 --always-read-main-dll --field-trial-handle=5368,i,11833383006937702095,6056433281393424313,262144 --variations-seed-version --mojo-platform-channel-handle=5384 /prefetch:1 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 133.0.3065.92 Modules
| |||||||||||||||
| 436 | ig.exe reseed | C:\Program Files\Malwarebytes\Anti-Malware\ig.exe | — | MBAMService.exe | |||||||||||
User: admin Company: MalwareBytes Integrity Level: LOW Description: Malware Scanner Exit code: 12976128 Version: 1.0.4.8 Modules
| |||||||||||||||
| 516 | "C:\Program Files (x86)\Microsoft\Edge\Application\133.0.3065.92\identity_helper.exe" --type=utility --utility-sub-type=winrt_app_id.mojom.WinrtAppIdService --lang=en-US --service-sandbox-type=none --disable-quic --string-annotations --subproc-heap-profiling --always-read-main-dll --field-trial-handle=1944,i,8430230786467317482,13089712978568152962,262144 --variations-seed-version --mojo-platform-channel-handle=4536 /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\133.0.3065.92\identity_helper.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: PWA Identity Proxy Host Exit code: 3221226029 Version: 133.0.3065.92 Modules
| |||||||||||||||
| 888 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --disable-quic --string-annotations --always-read-main-dll --field-trial-handle=5556,i,11833383006937702095,6056433281393424313,262144 --variations-seed-version --mojo-platform-channel-handle=6492 /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 133.0.3065.92 Modules
| |||||||||||||||
| 1040 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=renderer --string-annotations --extension-process --renderer-sub-type=extension --pdf-upsell-enabled --video-capture-use-gpu-memory-buffer --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=5 --always-read-main-dll --field-trial-handle=3672,i,8430230786467317482,13089712978568152962,262144 --variations-seed-version --mojo-platform-channel-handle=3644 /prefetch:2 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 133.0.3065.92 Modules
| |||||||||||||||
| 1080 | ig.exe reseed | C:\Program Files\Malwarebytes\Anti-Malware\ig.exe | — | MBAMService.exe | |||||||||||
User: admin Company: MalwareBytes Integrity Level: LOW Description: Malware Scanner Exit code: 8650752 Version: 1.0.4.8 Modules
| |||||||||||||||
| 1132 | ig.exe reseed | C:\Program Files\Malwarebytes\Anti-Malware\ig.exe | — | MBAMService.exe | |||||||||||
User: admin Company: MalwareBytes Integrity Level: LOW Description: Malware Scanner Exit code: 6422528 Version: 1.0.4.8 Modules
| |||||||||||||||
| 1204 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=renderer --string-annotations --extension-process --renderer-sub-type=extension --video-capture-use-gpu-memory-buffer --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=7 --always-read-main-dll --field-trial-handle=4280,i,11833383006937702095,6056433281393424313,262144 --variations-seed-version --mojo-platform-channel-handle=4268 /prefetch:2 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 133.0.3065.92 Modules
| |||||||||||||||
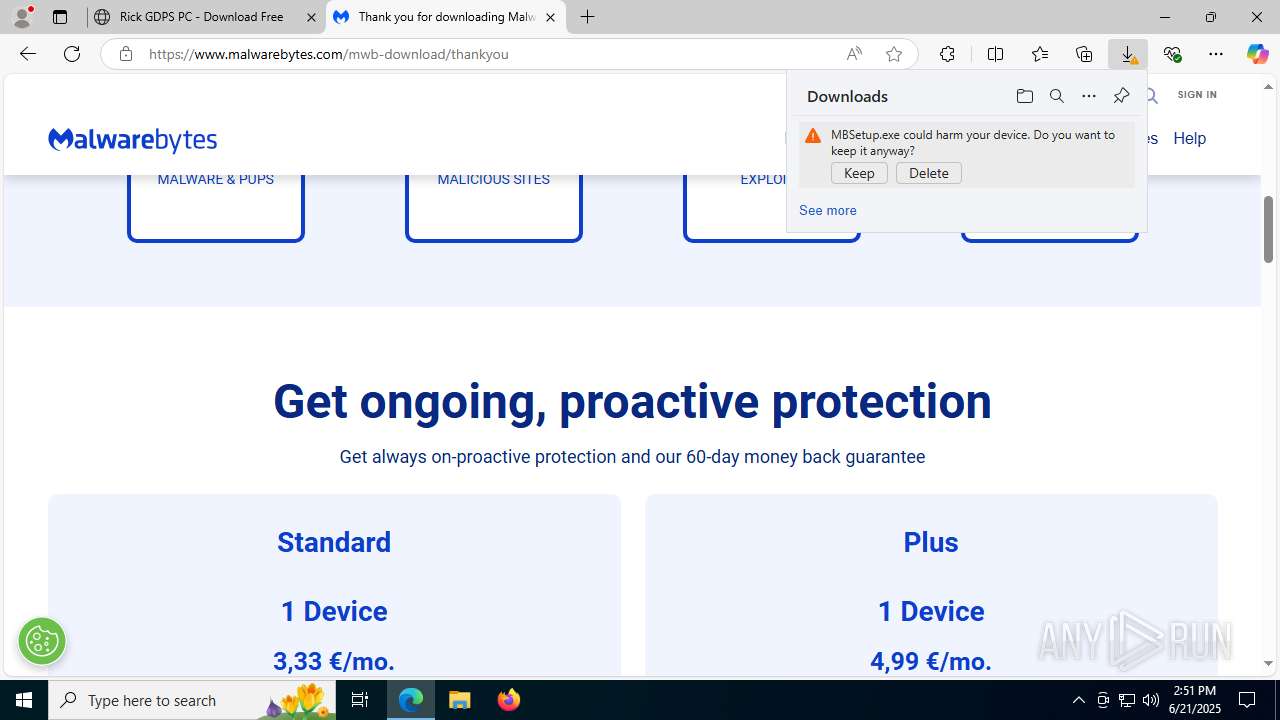
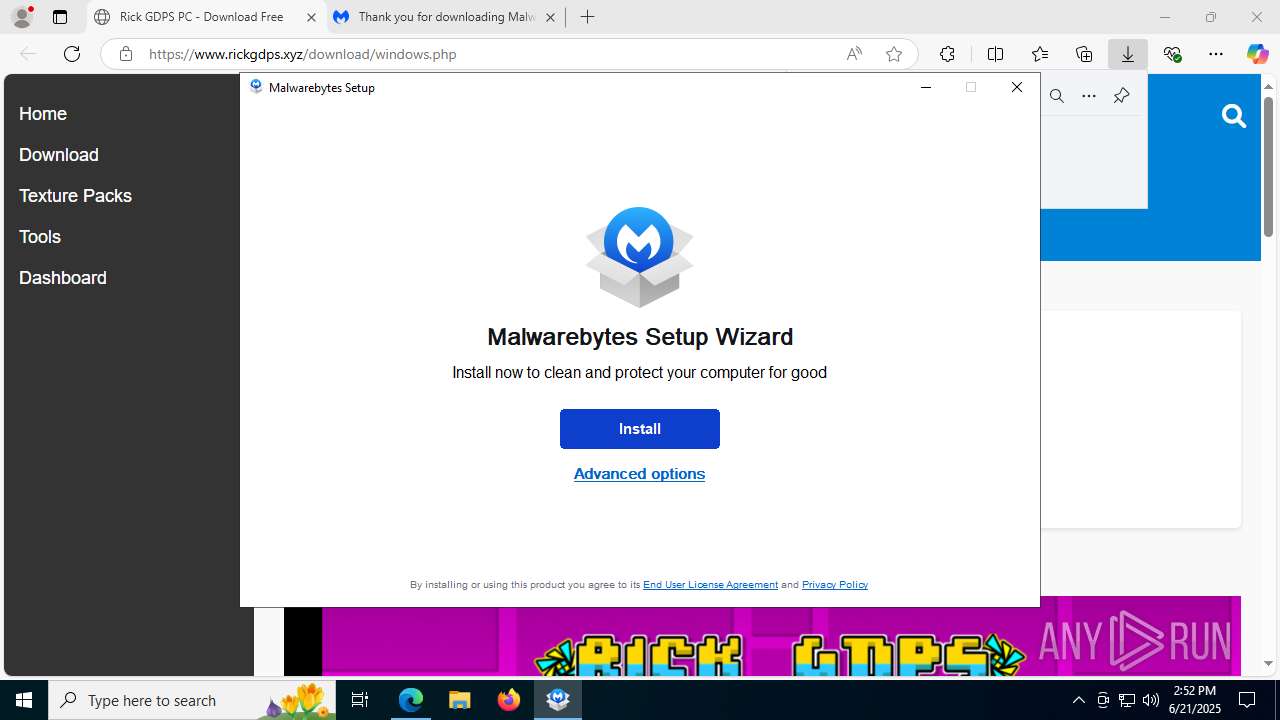
| 1332 | "C:\Users\admin\Downloads\MBSetup.exe" | C:\Users\admin\Downloads\MBSetup.exe | — | msedge.exe | |||||||||||
User: admin Company: Malwarebytes Integrity Level: MEDIUM Description: Malwarebytes Setup Exit code: 3221226540 Version: 5.3.1.129 Modules
| |||||||||||||||
| 1512 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=renderer --string-annotations --disable-gpu-compositing --video-capture-use-gpu-memory-buffer --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=17 --always-read-main-dll --field-trial-handle=5856,i,11833383006937702095,6056433281393424313,262144 --variations-seed-version --mojo-platform-channel-handle=5732 /prefetch:1 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 133.0.3065.92 Modules
| |||||||||||||||
Total events
340 225
Read events
339 147
Write events
1 034
Delete events
44
Modification events
| (PID) Process: | (1720) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (1720) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (1720) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\ThirdParty |
| Operation: | write | Name: | StatusCodes |
Value: | |||
| (PID) Process: | (1720) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\ThirdParty |
| Operation: | write | Name: | StatusCodes |
Value: 01000000 | |||
| (PID) Process: | (1720) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (1720) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\StabilityMetrics |
| Operation: | write | Name: | user_experience_metrics.stability.exited_cleanly |
Value: 0 | |||
| (PID) Process: | (1720) msedge.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\EdgeUpdate\ClientStateMedium\{56EB18F8-B008-4CBD-B6D2-8C97FE7E9062}\LastWasDefault |
| Operation: | write | Name: | S-1-5-21-1693682860-607145093-2874071422-1001 |
Value: 0C8CC465AC962F00 | |||
| (PID) Process: | (1720) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\WindowProperties\459530 |
| Operation: | write | Name: | WindowTabManagerFileMappingId |
Value: {4F3835BE-0C76-455D-8449-022CA77BE324} | |||
| (PID) Process: | (1720) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\WindowProperties\459530 |
| Operation: | write | Name: | WindowTabManagerFileMappingId |
Value: {73A0CB95-E392-45B1-B7CD-82E3B058D8E4} | |||
| (PID) Process: | (1720) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\WindowProperties\459530 |
| Operation: | write | Name: | WindowTabManagerFileMappingId |
Value: {6F0C1996-2176-4E4E-AE3C-3575874E773F} | |||
Executable files
1 355
Suspicious files
1 157
Text files
3 690
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1720 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\PersistentOriginTrials\LOG.old~RF176205.TMP | — | |
MD5:— | SHA256:— | |||
| 1720 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\PersistentOriginTrials\LOG.old | — | |
MD5:— | SHA256:— | |||
| 1720 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old~RF176205.TMP | — | |
MD5:— | SHA256:— | |||
| 1720 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 1720 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\discounts_db\LOG.old~RF176205.TMP | — | |
MD5:— | SHA256:— | |||
| 1720 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\discounts_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 1720 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\ClientCertificates\LOG.old~RF1761f6.TMP | — | |
MD5:— | SHA256:— | |||
| 1720 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\ClientCertificates\LOG.old | — | |
MD5:— | SHA256:— | |||
| 1720 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\EdgePushStorageWithConnectTokenAndKey\LOG.old~RF176244.TMP | — | |
MD5:— | SHA256:— | |||
| 1720 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\EdgePushStorageWithConnectTokenAndKey\LOG.old | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
60
TCP/UDP connections
228
DNS requests
249
Threats
14
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
4920 | msedge.exe | GET | 200 | 150.171.28.11:80 | http://edge.microsoft.com/browsernetworktime/time/1/current?cup2key=2:-ANScqjvF8ElgVzTp9dAQ2cUUvUB0tsBmmcxWRqGl3U&cup2hreq=e3b0c44298fc1c149afbf4c8996fb92427ae41e4649b934ca495991b7852b855 | unknown | — | — | whitelisted |
2632 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 23.53.40.178:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
4648 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
4648 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
7996 | svchost.exe | HEAD | 200 | 23.50.131.72:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/bf8090eb-6e5c-4c51-9250-5bf9b46cf160?P1=1750785808&P2=404&P3=2&P4=CpoCuSW4p0xSoa33onQAZx2Cnn%2bRDneni%2fwG9vwb1At6iRsYFXtcxymDgQVGBaOpz%2bdTBytu3UC9UgndRhcYaA%3d%3d | unknown | — | — | whitelisted |
7996 | svchost.exe | GET | 206 | 23.50.131.72:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/bf8090eb-6e5c-4c51-9250-5bf9b46cf160?P1=1750785808&P2=404&P3=2&P4=CpoCuSW4p0xSoa33onQAZx2Cnn%2bRDneni%2fwG9vwb1At6iRsYFXtcxymDgQVGBaOpz%2bdTBytu3UC9UgndRhcYaA%3d%3d | unknown | — | — | whitelisted |
7996 | svchost.exe | GET | 206 | 23.50.131.72:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/bf8090eb-6e5c-4c51-9250-5bf9b46cf160?P1=1750785808&P2=404&P3=2&P4=CpoCuSW4p0xSoa33onQAZx2Cnn%2bRDneni%2fwG9vwb1At6iRsYFXtcxymDgQVGBaOpz%2bdTBytu3UC9UgndRhcYaA%3d%3d | unknown | — | — | whitelisted |
7996 | svchost.exe | GET | 200 | 23.50.131.72:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/4c4fdee0-d69c-42b7-bf5c-3ec046e9dfc9?P1=1750785810&P2=404&P3=2&P4=Ltumg4AIcojr5dBnMlLj5sbzjugOt5EUTmNmtaj50pyMZLxHQpUX7GSyL2z8HT82H7XiK34kArUZk7vXUDfrPQ%3d%3d | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
1268 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
5944 | MoUsoCoreWorker.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4156 | RUXIMICS.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4920 | msedge.exe | 150.171.28.11:80 | edge.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
4920 | msedge.exe | 13.107.42.16:443 | config.edge.skype.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
4920 | msedge.exe | 104.21.16.1:443 | www.rickgdps.xyz | CLOUDFLARENET | — | unknown |
4920 | msedge.exe | 150.171.28.11:443 | edge.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
4920 | msedge.exe | 92.123.104.45:443 | copilot.microsoft.com | Akamai International B.V. | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
edge.microsoft.com |
| whitelisted |
config.edge.skype.com |
| whitelisted |
www.rickgdps.xyz |
| unknown |
copilot.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
pl26139469.effectiveratecpm.com |
| unknown |
cdnjs.cloudflare.com |
| whitelisted |
www.highperformanceformat.com |
| unknown |
Threats
PID | Process | Class | Message |
|---|---|---|---|
4920 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] Cloudflare content delivery network (cdnjs .cloudflare .com) |
4920 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] Cloudflare content delivery network (cdnjs .cloudflare .com) |
4920 | msedge.exe | Possible Social Engineering Attempted | PHISHING [ANY.RUN] Suspected Phishing Domain (highperformanceformat .com) |
4920 | msedge.exe | Possible Social Engineering Attempted | PHISHING [ANY.RUN] Suspected Phishing Domain (highperformanceformat .com) |
4920 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] Cloudflare Network Error Logging (NEL) |
4920 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] Cloudflare Network Error Logging (NEL) |
4920 | msedge.exe | Possible Social Engineering Attempted | PHISHING [ANY.RUN] Suspected Phishing Domain (highperformanceformat .com) |
4920 | msedge.exe | Possible Social Engineering Attempted | PHISHING [ANY.RUN] Suspected Phishing Domain (highperformanceformat .com) |
4920 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] Google Tag Manager analytics (googletagmanager .com) |
4920 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] Google Tag Manager analytics (googletagmanager .com) |
Process | Message |
|---|---|
Malwarebytes.exe | Profiler was prevented from loading notification profiler due to app settings.
Process ID (decimal): 2716. Message ID: [0x2509].
|
Malwarebytes.exe | Profiler was prevented from loading notification profiler due to app settings.
Process ID (decimal): 2760. Message ID: [0x2509].
|
Malwarebytes.exe | Profiler was prevented from loading notification profiler due to app settings.
Process ID (decimal): 4664. Message ID: [0x2509].
|