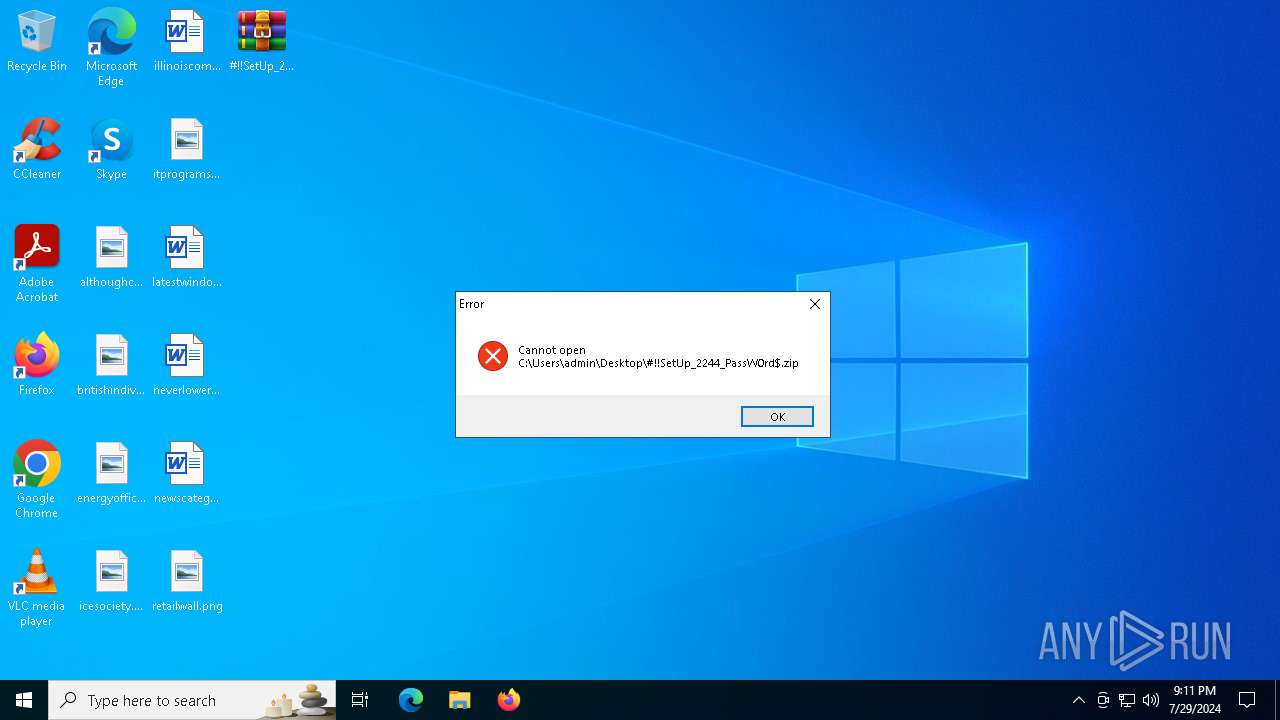
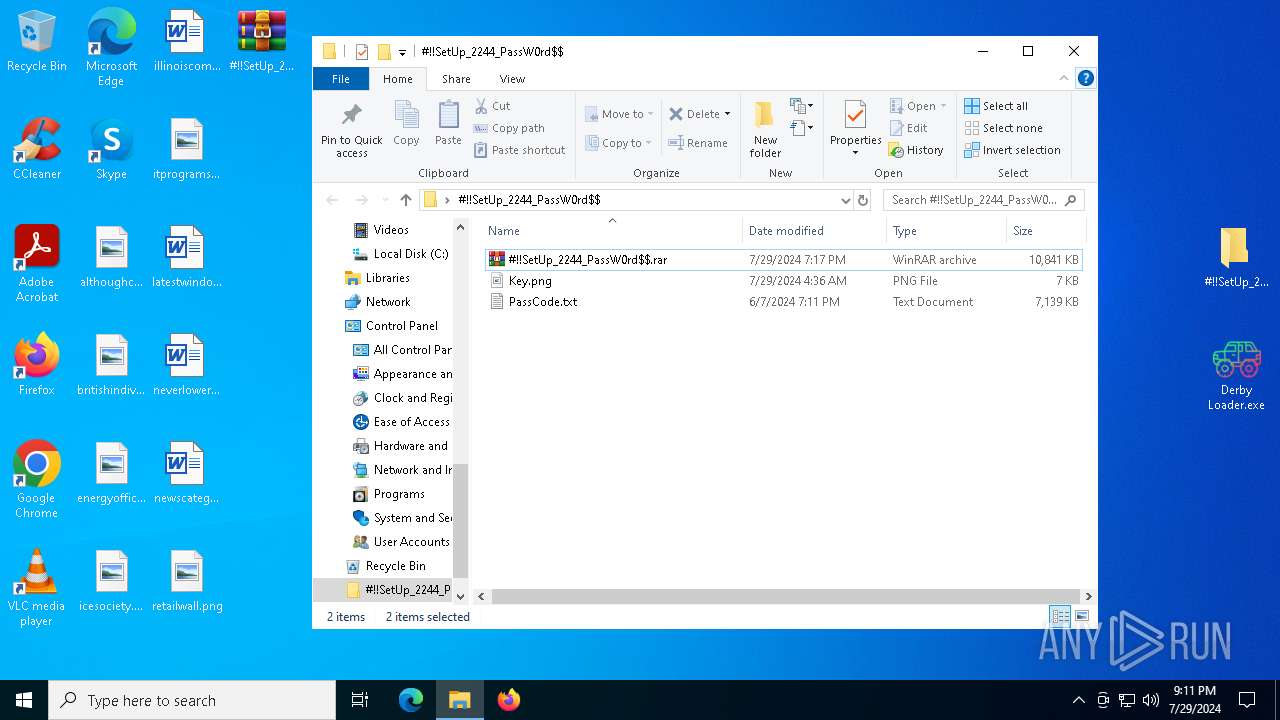
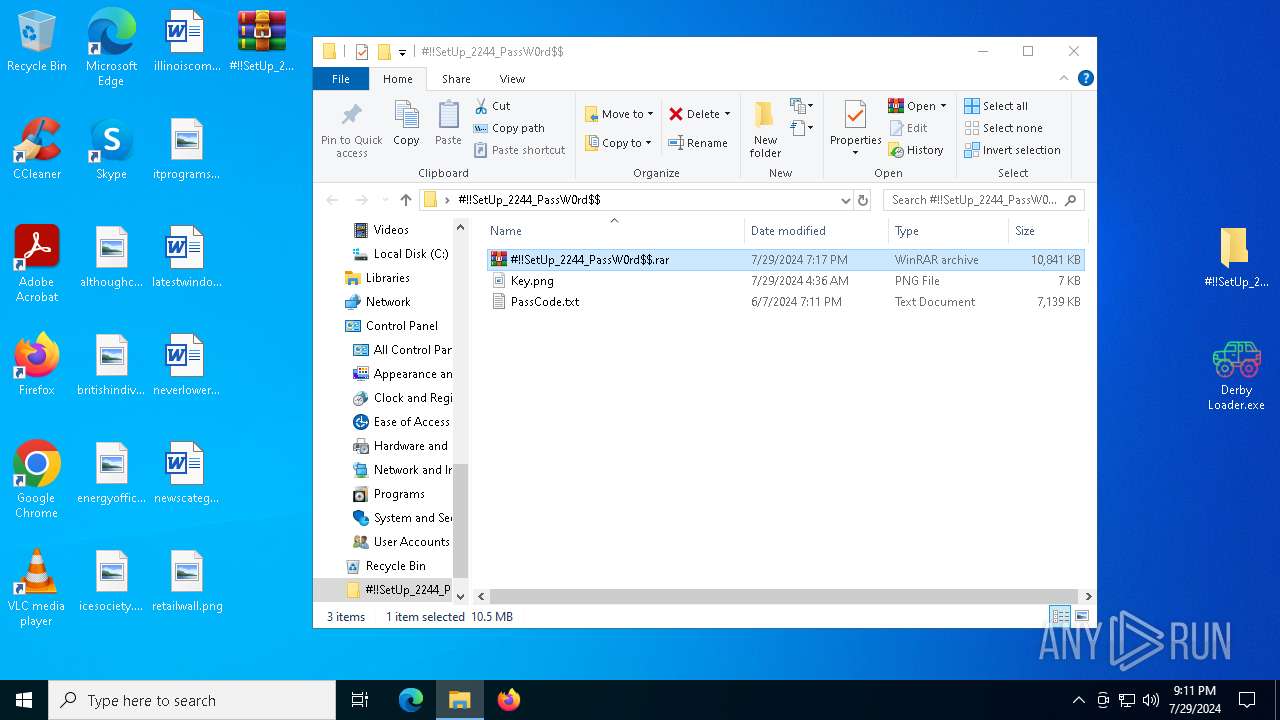
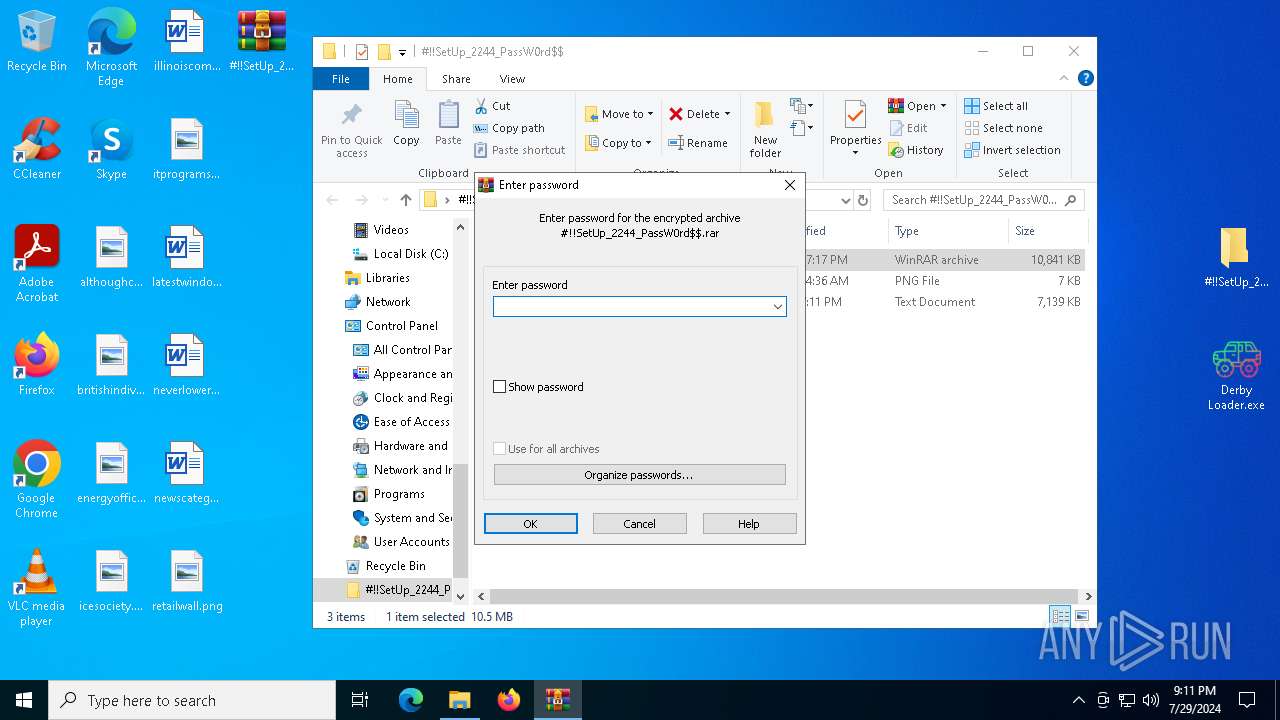
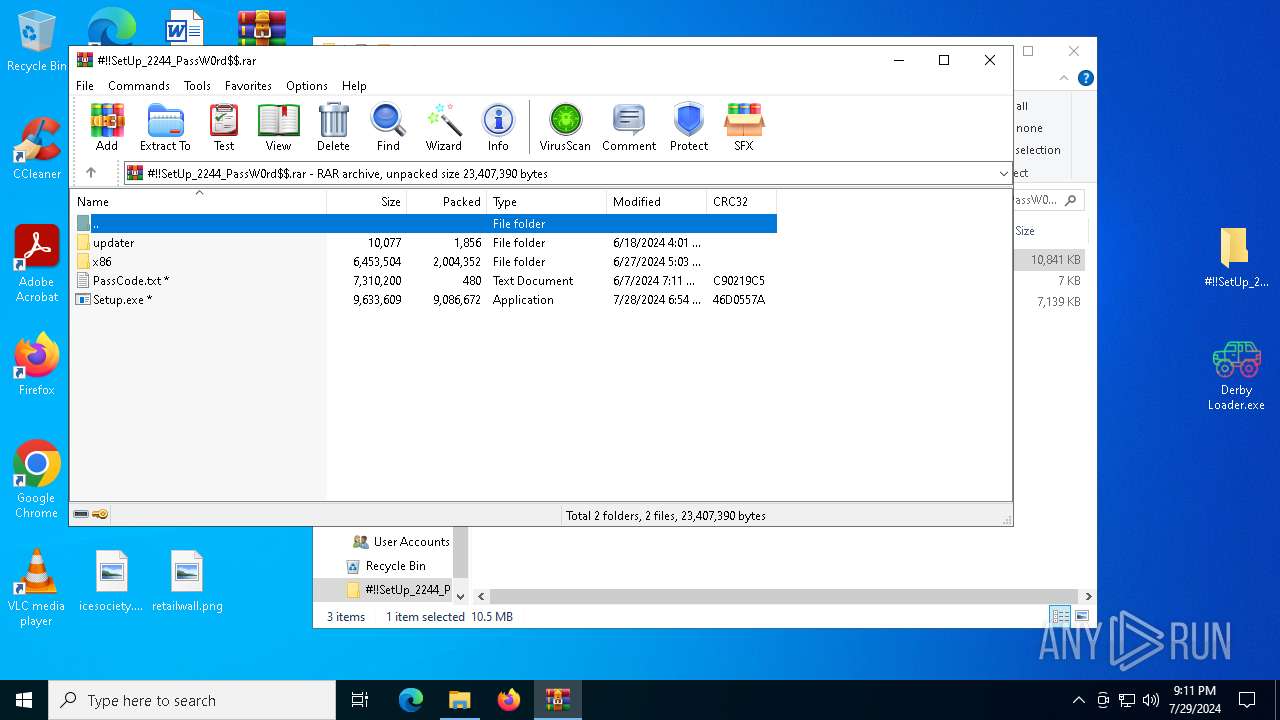
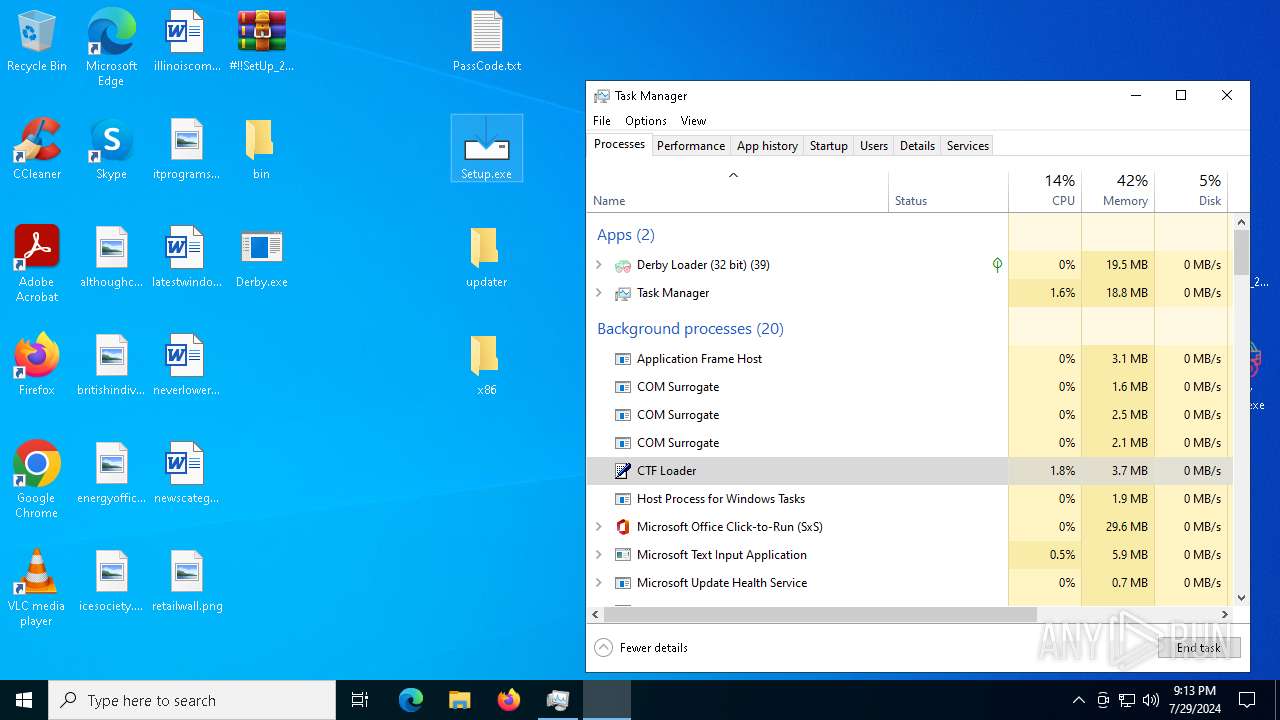
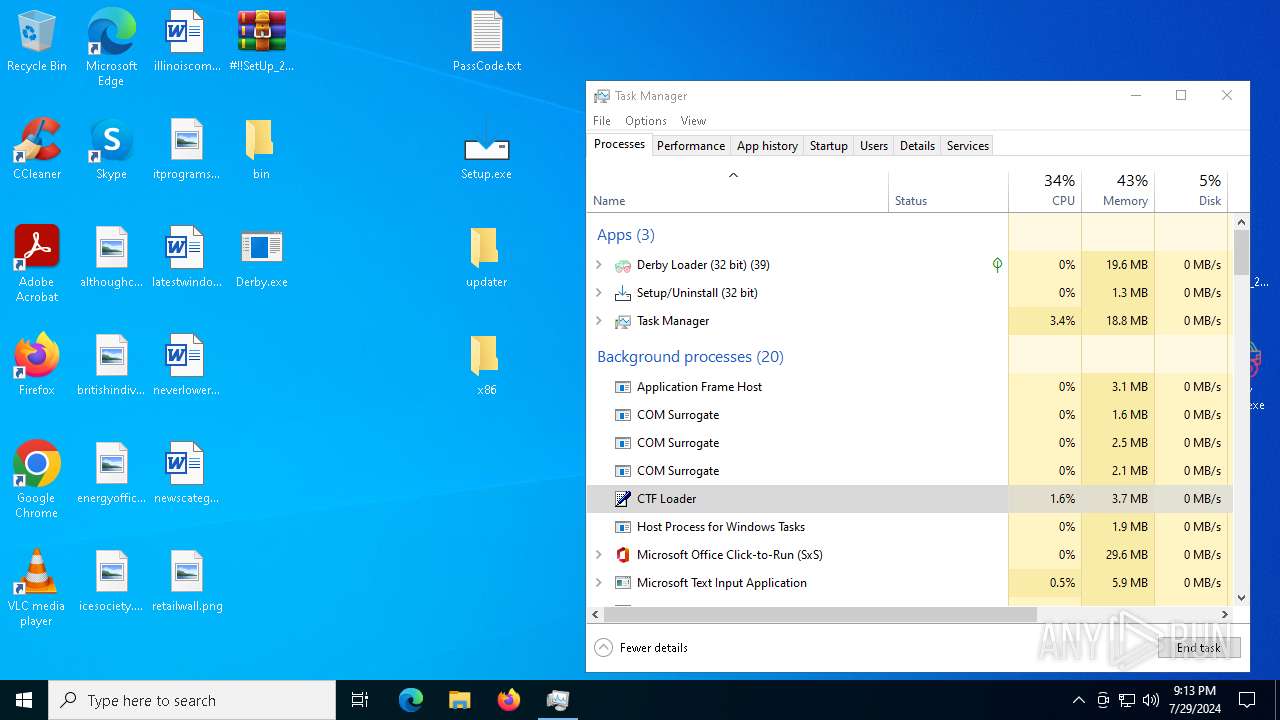
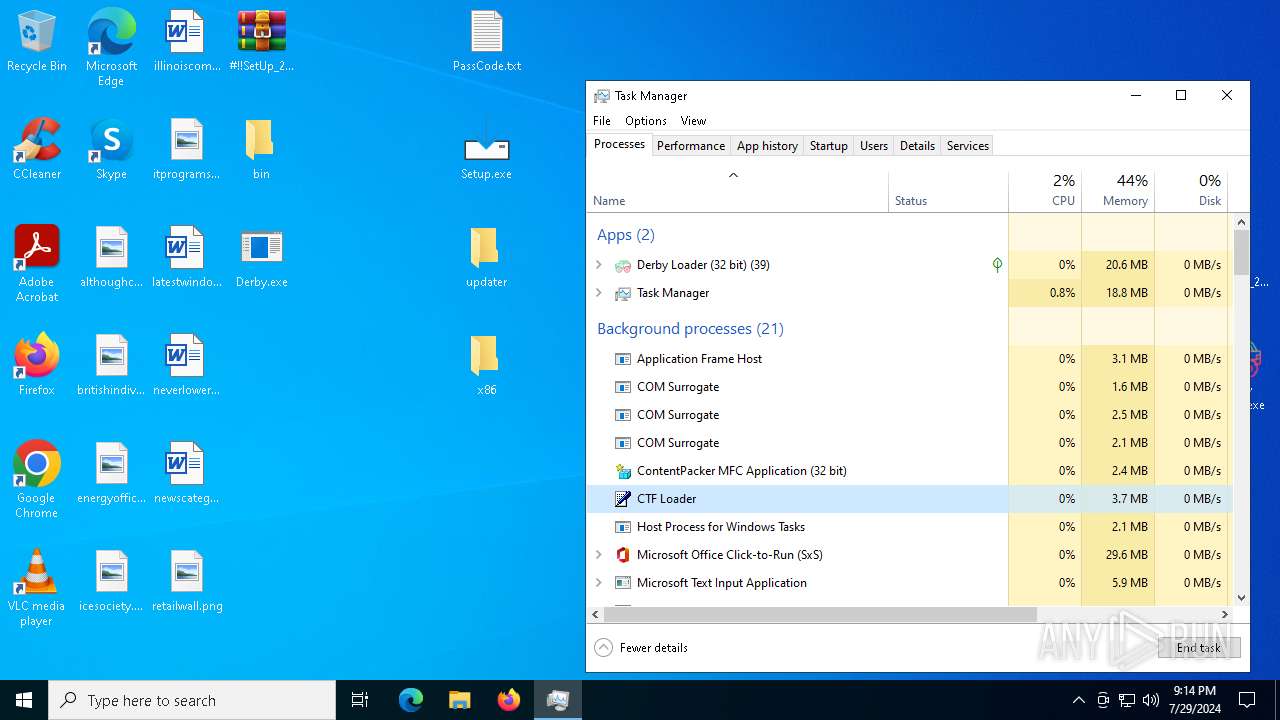
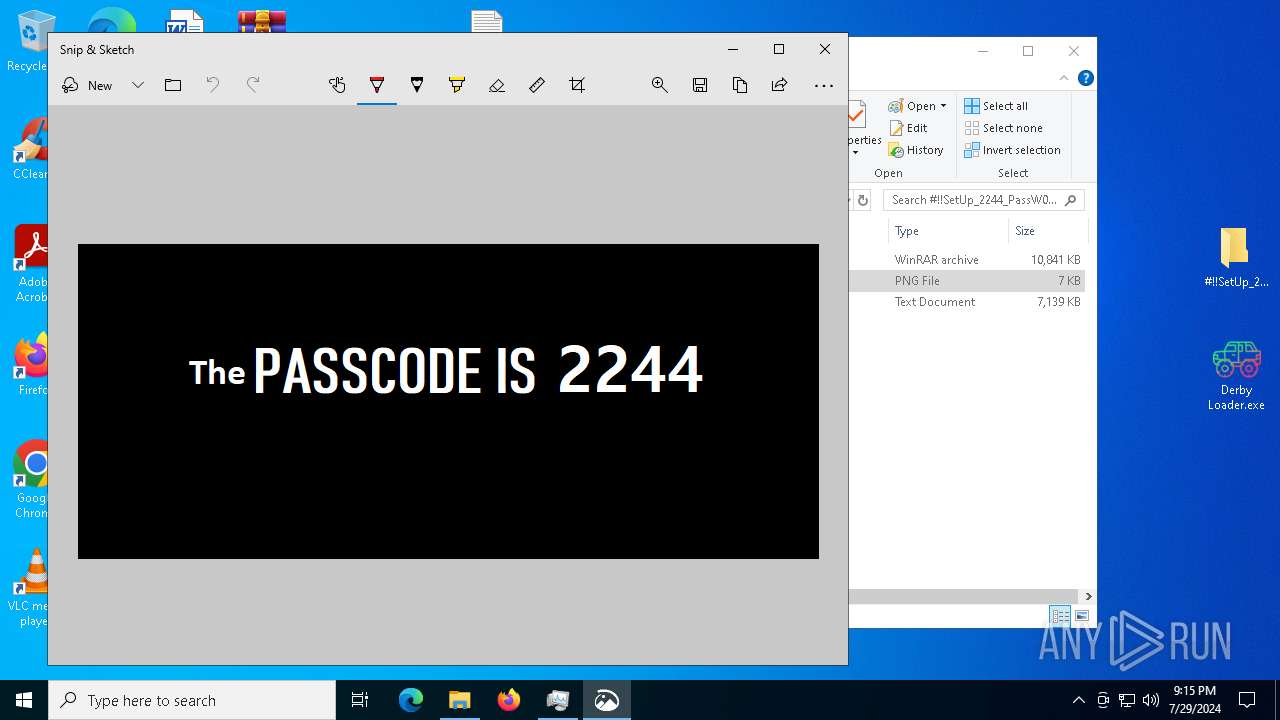
| File name: | #!!SetUp_2244_PassW0rd$.zip |
| Full analysis: | https://app.any.run/tasks/e7387d01-189d-4f28-a7ad-363202f95dcc |
| Verdict: | Malicious activity |
| Threats: | Lumma is an information stealer, developed using the C programming language. It is offered for sale as a malware-as-a-service, with several plans available. It usually targets cryptocurrency wallets, login credentials, and other sensitive information on a compromised system. The malicious software regularly gets updates that improve and expand its functionality, making it a serious stealer threat. |
| Analysis date: | July 29, 2024, 21:11:14 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v1.0 to extract, compression method=store |
| MD5: | 393C305049A3AFC418E588C595675A04 |
| SHA1: | ACF87E4BADE45AF007274E25723440C351B4E632 |
| SHA256: | AB9898C7C1C76610AB6083070909DF728FF102A708BF1A919D49E8A970CF9BB7 |
| SSDEEP: | 98304:dIwuK3u3PQGiEdjHKtJo+UDvaaSXvw5Z5Uzj7IYl3zVB9lBdmZ7lv+OMEu40uPHw:ptS/6nfyR5dh1fNeEjl9CT73pTt |
MALICIOUS
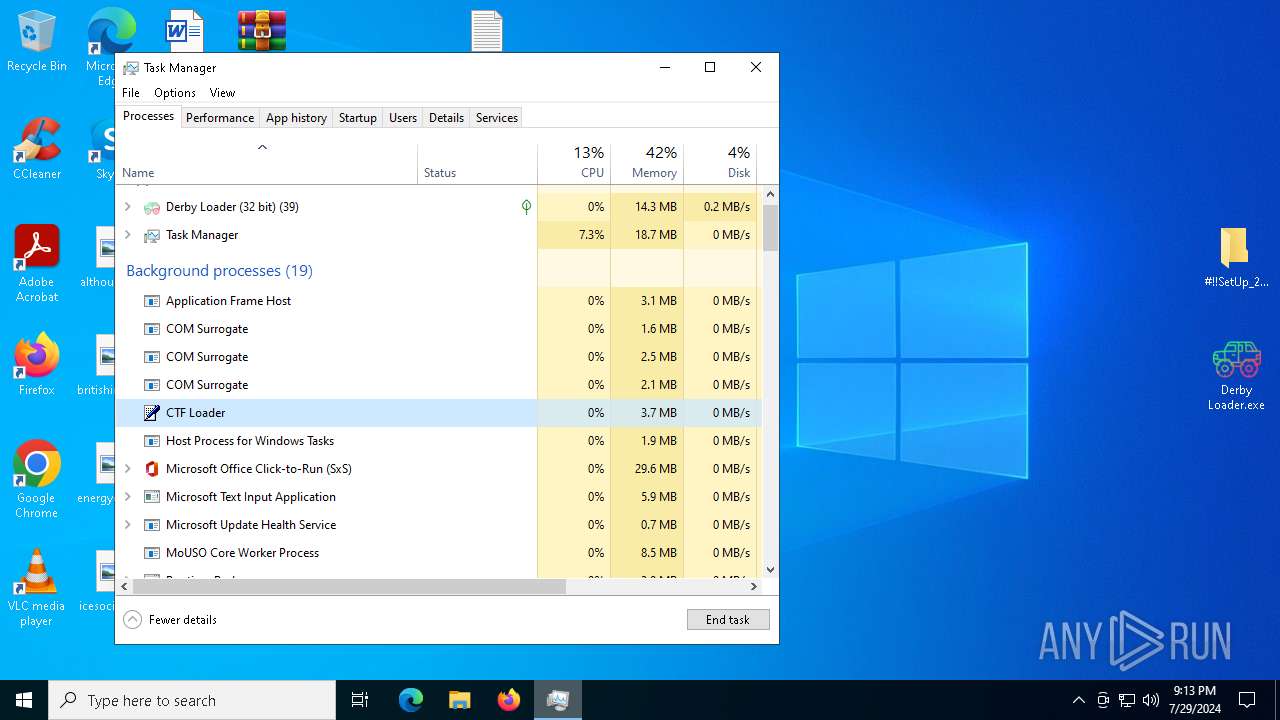
Drops the executable file immediately after the start
- WinRAR.exe (PID: 3392)
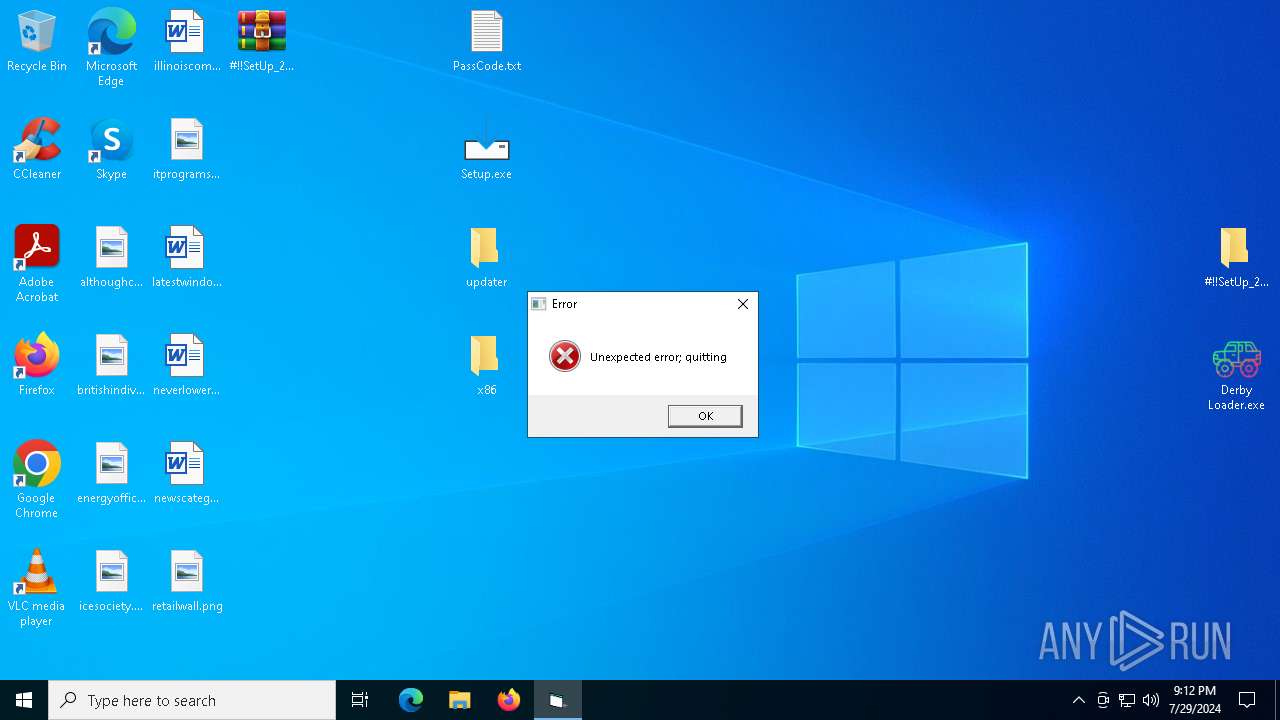
- Setup.exe (PID: 6352)
- Setup.tmp (PID: 3112)
- Setup.exe (PID: 7164)
- Setup.tmp (PID: 4476)
- ImPackr.exe (PID: 4940)
- ImPackr.exe (PID: 7096)
- Derby Loader.exe (PID: 396)
- Setup.exe (PID: 7328)
- Setup.tmp (PID: 7360)
- Setup.exe (PID: 5936)
- Setup.tmp (PID: 4236)
Antivirus name has been found in the command line (generic signature)
- cmd.exe (PID: 6592)
- cmd.exe (PID: 812)
- find.exe (PID: 3704)
- tasklist.exe (PID: 2824)
- find.exe (PID: 4192)
- cmd.exe (PID: 1720)
- tasklist.exe (PID: 4288)
- find.exe (PID: 6324)
- cmd.exe (PID: 7052)
- tasklist.exe (PID: 7112)
- tasklist.exe (PID: 6396)
- find.exe (PID: 6592)
- find.exe (PID: 996)
- tasklist.exe (PID: 4316)
- cmd.exe (PID: 4104)
- avp.exe (PID: 2996)
- avengine.exe (PID: 6056)
- avgemc.exe (PID: 4436)
- ashServ.exe (PID: 4092)
- navapsvc.exe (PID: 7096)
- mcshield.exe (PID: 5828)
- f-prot.exe (PID: 6064)
- cmd.exe (PID: 6232)
- tasklist.exe (PID: 7732)
- find.exe (PID: 7676)
- tasklist.exe (PID: 7860)
- cmd.exe (PID: 7784)
- tasklist.exe (PID: 7576)
- tasklist.exe (PID: 7832)
- find.exe (PID: 7600)
- cmd.exe (PID: 3804)
- find.exe (PID: 3140)
- cmd.exe (PID: 7488)
- cmd.exe (PID: 7508)
- find.exe (PID: 7064)
- find.exe (PID: 1080)
- tasklist.exe (PID: 7132)
Connects to the CnC server
- svchost.exe (PID: 2284)
LUMMA has been detected (SURICATA)
- svchost.exe (PID: 2284)
- explorer.exe (PID: 7224)
Actions looks like stealing of personal data
- explorer.exe (PID: 7224)
SUSPICIOUS
Process drops legitimate windows executable
- WinRAR.exe (PID: 1912)
- Setup.tmp (PID: 4476)
- ImPackr.exe (PID: 7096)
- Setup.tmp (PID: 4236)
Executable content was dropped or overwritten
- Setup.exe (PID: 6352)
- Setup.tmp (PID: 3112)
- Setup.exe (PID: 7164)
- Setup.tmp (PID: 4476)
- ImPackr.exe (PID: 7096)
- ImPackr.exe (PID: 4940)
- Derby Loader.exe (PID: 396)
- Setup.tmp (PID: 7360)
- Setup.exe (PID: 7328)
- Setup.exe (PID: 5936)
- Setup.tmp (PID: 4236)
Reads the date of Windows installation
- Setup.tmp (PID: 3112)
- Setup.tmp (PID: 4476)
- Setup.tmp (PID: 7360)
- Setup.tmp (PID: 4236)
Creates file in the systems drive root
- Setup.tmp (PID: 3112)
- Setup.tmp (PID: 7360)
Reads the Windows owner or organization settings
- Setup.tmp (PID: 4476)
- Setup.tmp (PID: 3112)
- Setup.tmp (PID: 7360)
- Setup.tmp (PID: 4236)
Reads security settings of Internet Explorer
- Setup.tmp (PID: 3112)
- Setup.tmp (PID: 4476)
- Setup.tmp (PID: 7360)
- Setup.tmp (PID: 4236)
- ScreenSketch.exe (PID: 1884)
Get information on the list of running processes
- cmd.exe (PID: 6592)
- Setup.tmp (PID: 4476)
- cmd.exe (PID: 188)
- cmd.exe (PID: 812)
- cmd.exe (PID: 1720)
- cmd.exe (PID: 7052)
- cmd.exe (PID: 4104)
- Setup.tmp (PID: 4236)
- cmd.exe (PID: 6232)
- cmd.exe (PID: 7264)
- cmd.exe (PID: 7784)
- cmd.exe (PID: 3804)
- cmd.exe (PID: 7488)
- cmd.exe (PID: 7508)
Starts CMD.EXE for commands execution
- Setup.tmp (PID: 4476)
- Setup.tmp (PID: 4236)
The process drops C-runtime libraries
- Setup.tmp (PID: 4476)
- ImPackr.exe (PID: 7096)
- Setup.tmp (PID: 4236)
Runs PING.EXE to delay simulation
- Setup.tmp (PID: 4476)
- Setup.tmp (PID: 4236)
Starts itself from another location
- ImPackr.exe (PID: 7096)
- ImPackr.exe (PID: 7608)
Starts application with an unusual extension
- ImPackr.exe (PID: 4940)
- ImPackr.exe (PID: 1148)
The process creates files with name similar to system file names
- Derby Loader.exe (PID: 396)
Contacting a server suspected of hosting an CnC
- svchost.exe (PID: 2284)
- explorer.exe (PID: 7224)
INFO
Drops the executable file immediately after the start
- WinRAR.exe (PID: 1912)
- WinRAR.exe (PID: 5696)
Manual execution by a user
- WinRAR.exe (PID: 1912)
- WinRAR.exe (PID: 5696)
- Setup.exe (PID: 6352)
- Taskmgr.exe (PID: 1596)
- Taskmgr.exe (PID: 6124)
- Derby Loader.exe (PID: 396)
- Setup.exe (PID: 7328)
- mspaint.exe (PID: 7760)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 1912)
- WinRAR.exe (PID: 5696)
Checks proxy server information
- slui.exe (PID: 2708)
Checks supported languages
- Setup.exe (PID: 6352)
- Setup.tmp (PID: 3112)
- Setup.exe (PID: 7164)
- Setup.tmp (PID: 4476)
- ImPackr.exe (PID: 7096)
- ImPackr.exe (PID: 4940)
- StrCmp.exe (PID: 5304)
- more.com (PID: 3228)
- Derby Loader.exe (PID: 396)
- Setup.exe (PID: 7328)
- Setup.tmp (PID: 7360)
- Setup.exe (PID: 5936)
- Setup.tmp (PID: 4236)
- ImPackr.exe (PID: 7608)
- ImPackr.exe (PID: 1148)
- StrCmp.exe (PID: 7664)
- more.com (PID: 7728)
- ScreenSketch.exe (PID: 1884)
Reads the software policy settings
- slui.exe (PID: 2708)
- explorer.exe (PID: 7224)
Create files in a temporary directory
- Setup.exe (PID: 6352)
- Setup.tmp (PID: 3112)
- Setup.exe (PID: 7164)
- Setup.tmp (PID: 4476)
- ImPackr.exe (PID: 4940)
- more.com (PID: 3228)
- Setup.tmp (PID: 7360)
- Setup.exe (PID: 7328)
- Setup.exe (PID: 5936)
- Setup.tmp (PID: 4236)
- ImPackr.exe (PID: 1148)
- more.com (PID: 7728)
Reads Environment values
- Setup.exe (PID: 6352)
- Setup.tmp (PID: 3112)
- Setup.exe (PID: 7164)
- Setup.tmp (PID: 4476)
- Setup.tmp (PID: 7360)
- Setup.exe (PID: 7328)
- Setup.exe (PID: 5936)
- Setup.tmp (PID: 4236)
Reads the computer name
- Setup.tmp (PID: 3112)
- Setup.tmp (PID: 4476)
- ImPackr.exe (PID: 4940)
- ImPackr.exe (PID: 7096)
- more.com (PID: 3228)
- StrCmp.exe (PID: 5304)
- Derby Loader.exe (PID: 396)
- Setup.tmp (PID: 7360)
- Setup.tmp (PID: 4236)
- ImPackr.exe (PID: 7608)
- StrCmp.exe (PID: 7664)
- ImPackr.exe (PID: 1148)
- more.com (PID: 7728)
- ScreenSketch.exe (PID: 1884)
Process checks computer location settings
- Setup.tmp (PID: 3112)
- Setup.tmp (PID: 4476)
- Setup.tmp (PID: 7360)
- Setup.tmp (PID: 4236)
Creates files or folders in the user directory
- Setup.tmp (PID: 4476)
- ImPackr.exe (PID: 7096)
- ImPackr.exe (PID: 4940)
- Setup.tmp (PID: 4236)
- ScreenSketch.exe (PID: 1884)
Reads security settings of Internet Explorer
- Taskmgr.exe (PID: 6124)
Reads the machine GUID from the registry
- Derby Loader.exe (PID: 396)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 10 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | None |
| ZipModifyDate: | 2024:07:29 23:10:18 |
| ZipCRC: | 0x00000000 |
| ZipCompressedSize: | - |
| ZipUncompressedSize: | - |
| ZipFileName: | #!!SetUp_2244_PassW0rd$/ |
Total processes
363
Monitored processes
217
Malicious processes
15
Suspicious processes
11
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 188 | "cmd.exe" /C tasklist /FI "IMAGENAME eq opssvc.exe" /FO CSV /NH | find /I "opssvc.exe" | C:\Windows\System32\cmd.exe | — | Setup.tmp | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 204 | "C:\Users\admin\Desktop/bin/joeboxcontrol.exe" | C:\Users\admin\Desktop\bin\joeboxcontrol.exe | — | Derby Loader.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: Version: 0.0.0.0 Modules
| |||||||||||||||
| 208 | "C:\Users\admin\Desktop/bin/nod32krn.exe" | C:\Users\admin\Desktop\bin\nod32krn.exe | — | Derby Loader.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: Version: 0.0.0.0 Modules
| |||||||||||||||
| 396 | "C:\Users\admin\Desktop\Derby Loader.exe" | C:\Users\admin\Desktop\Derby Loader.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Description: Derby Loader Version: 1.0.0.0 Modules
| |||||||||||||||
| 504 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | joeboxcontrol.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 4294967295 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 524 | "C:\Users\admin\Desktop/bin/coreServiceShell.exe" | C:\Users\admin\Desktop\bin\coreServiceShell.exe | — | Derby Loader.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: Version: 0.0.0.0 Modules
| |||||||||||||||
| 788 | "C:\Users\admin\Desktop/bin/prl_tools.exe" | C:\Users\admin\Desktop\bin\prl_tools.exe | — | Derby Loader.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: Version: 0.0.0.0 Modules
| |||||||||||||||
| 812 | "cmd.exe" /C tasklist /FI "IMAGENAME eq avastui.exe" /FO CSV /NH | find /I "avastui.exe" | C:\Windows\System32\cmd.exe | — | Setup.tmp | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 920 | "C:\Users\admin\Desktop/bin/prl_cc.exe" | C:\Users\admin\Desktop\bin\prl_cc.exe | — | Derby Loader.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: Version: 0.0.0.0 Modules
| |||||||||||||||
| 996 | find /I "sophoshealth.exe" | C:\Windows\System32\find.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Find String (grep) Utility Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
35 238
Read events
35 080
Write events
136
Delete events
22
Modification events
| (PID) Process: | (3392) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (3392) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (3392) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\General |
| Operation: | write | Name: | LastFolder |
Value: C:\Users\admin\Desktop | |||
| (PID) Process: | (3392) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3392) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3392) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (3392) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (3392) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\General\Toolbar\Layout |
| Operation: | write | Name: | Band76_0 |
Value: 4C000000730100000402000000000000F0F0F00000000000000000000000000000000000000000004204090000000000000000003B000000B402000000000000000000000000000001000000 | |||
| (PID) Process: | (3392) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\General\Toolbar\Layout |
| Operation: | write | Name: | Band76_1 |
Value: 4C000000730100000500000000000000F0F0F000000000000000000000000000000000000000000028020E000000000000000000180000002A00000000000000000000000000000002000000 | |||
| (PID) Process: | (3392) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\General\Toolbar\Layout |
| Operation: | write | Name: | Band76_2 |
Value: 4C000000730100000400000000000000F0F0F0000000000000000000000000000000000000000000DE0210000000000000000000180000006400000000000000000000000000000003000000 | |||
Executable files
199
Suspicious files
13
Text files
13
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 5696 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa5696.30494\#!!SetUp_2244_PassW0rd$\#!!SetUp_2244_PassW0rd$\#!!SetUp_2244_PassW0rd$.rar | — | |
MD5:— | SHA256:— | |||
| 5696 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa5696.30494\#!!SetUp_2244_PassW0rd$\#!!SetUp_2244_PassW0rd$\PassCode.txt | — | |
MD5:— | SHA256:— | |||
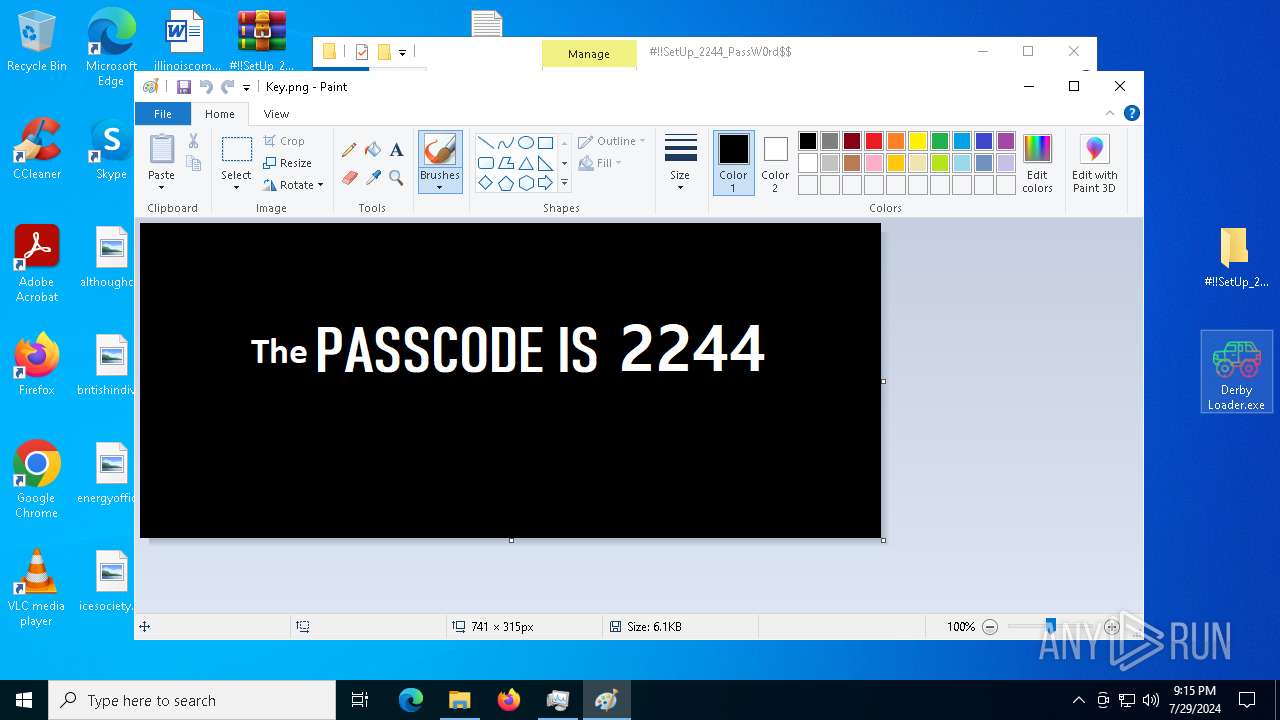
| 5696 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa5696.30494\#!!SetUp_2244_PassW0rd$\#!!SetUp_2244_PassW0rd$\Key.png | image | |
MD5:322CFA2F21842153ACDEDCC58DE91389 | SHA256:941A0B3C595E841BCC19D272FA1BB7A86E7EE348B37EF5E2177AC7286EF601E9 | |||
| 1912 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb1912.32879\x86\api-ms-win-core-processthreads-l1-1-1.dll | executable | |
MD5:29001F316CCFC800E2246743DF9B15B3 | SHA256:E5EA2C21FB225090F7D0DB6C6990D67B1558D8E834E86513BC8BA7A43C4E7B36 | |||
| 1912 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb1912.32879\x86\api-ms-win-core-profile-l1-1-0.dll | executable | |
MD5:6EE66DCA31C5CCE57740D677C85B4CE7 | SHA256:D00A0EDACE14715BF79DBD17B715D8A74A2300F0ADB1F3FC137EDFB7074C9B0A | |||
| 1912 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb1912.32879\updater\manager\ks_tyres.ini | text | |
MD5:47F6571C7884DA6C743551AC724186D4 | SHA256:894D3C57598ECB22C769CC3EA8219859A95E22740E72394A474012EA2119B3D9 | |||
| 1912 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb1912.32879\x86\api-ms-win-core-string-l1-1-0.dll | executable | |
MD5:2E5C29FC652F432B89A1AFE187736C4D | SHA256:3807DB7ACF1B40C797E4D4C14A12C3806346AE56B25E205E600BE3E635C18D4F | |||
| 1912 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb1912.32879\x86\api-ms-win-core-synch-l1-2-0.dll | executable | |
MD5:659E4FEBC208545A2E23C0C8B881A30D | SHA256:9AC63682E03D55A5D18405D336634AF080DD0003B565D12A39D6D71AAA989F48 | |||
| 1912 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb1912.32879\x86\api-ms-win-core-sysinfo-l1-1-0.dll | executable | |
MD5:CEF4B9F680FAAE322170B961A3421C5B | SHA256:1FE918979F1653D63BB713D4716910D192CD09F50017A6ECB4CE026ED6285DF9 | |||
| 1912 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb1912.32879\PassCode.txt | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
5
TCP/UDP connections
45
DNS requests
26
Threats
5
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
4424 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
5368 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
3676 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
4132 | OfficeClickToRun.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
504 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 40.91.76.224:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
— | — | 131.253.33.254:443 | a-ring-fallback.msedge.net | MICROSOFT-CORP-MSN-AS-BLOCK | US | unknown |
— | — | 92.123.104.52:443 | www.bing.com | Akamai International B.V. | DE | unknown |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
3952 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
2432 | slui.exe | 40.91.76.224:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
3488 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
2708 | slui.exe | 40.91.76.224:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
t-ring-fdv2.msedge.net |
| unknown |
a-ring-fallback.msedge.net |
| unknown |
www.bing.com |
| whitelisted |
google.com |
| whitelisted |
fp-afd-nocache-ccp.azureedge.net |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
th.bing.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2284 | svchost.exe | Domain Observed Used for C2 Detected | ET MALWARE Lumma Stealer Related CnC Domain in DNS Lookup (horizonvxjis .shop) |
2284 | svchost.exe | Domain Observed Used for C2 Detected | ET MALWARE Lumma Stealer Related CnC Domain in DNS Lookup (horizonvxjis .shop) |
7224 | explorer.exe | Domain Observed Used for C2 Detected | ET MALWARE Observed Lumma Stealer Related Domain (horizonvxjis .shop in TLS SNI) |
7224 | explorer.exe | Domain Observed Used for C2 Detected | ET MALWARE Observed Lumma Stealer Related Domain (horizonvxjis .shop in TLS SNI) |
7224 | explorer.exe | Domain Observed Used for C2 Detected | ET MALWARE Observed Lumma Stealer Related Domain (horizonvxjis .shop in TLS SNI) |