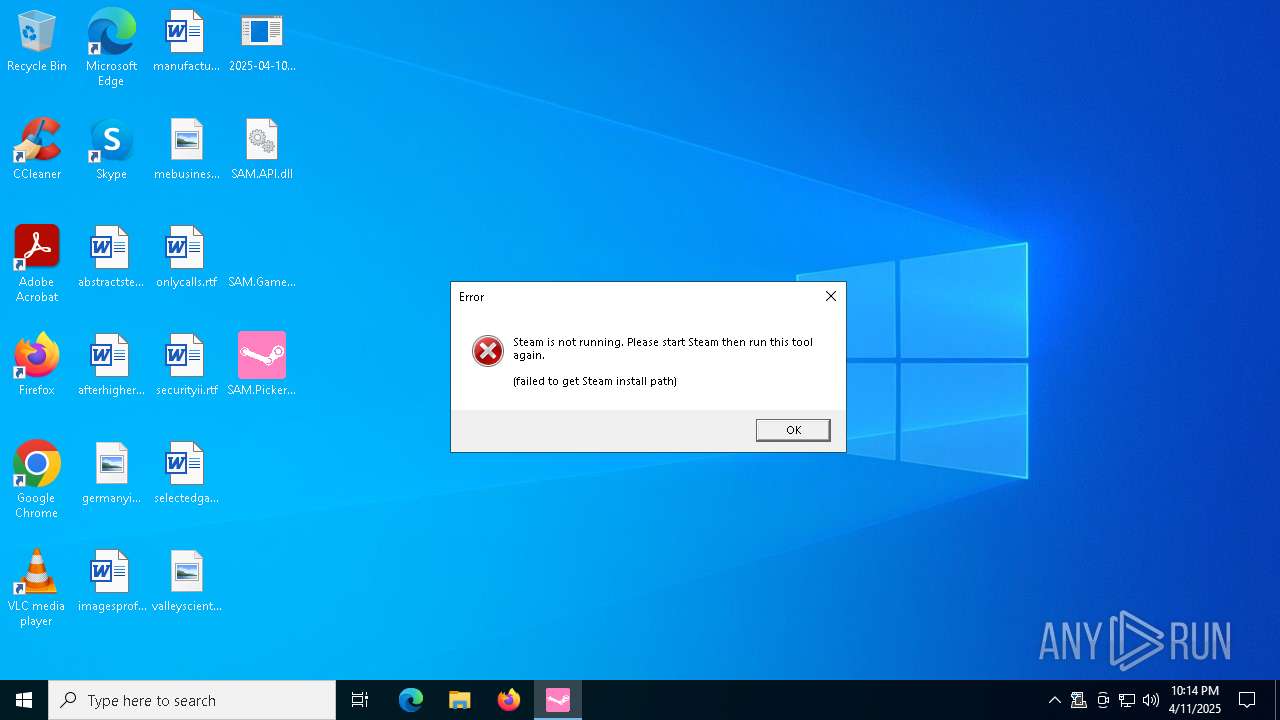
| File name: | 2025-04-10_0d31f30eb5d1a4fbe0584b9220513a1b_black-basta_elex_luca-stealer |
| Full analysis: | https://app.any.run/tasks/bc8888c4-0d8d-4cb1-987f-ea54d983e581 |
| Verdict: | Malicious activity |
| Threats: | Orcus is a modular Remote Access Trojan with some unusual functions. This RAT enables attackers to create plugins using a custom development library and offers a robust core feature set that makes it one of the most dangerous malicious programs in its class. |
| Analysis date: | April 11, 2025, 22:14:34 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386 Mono/.Net assembly, for MS Windows, 3 sections |
| MD5: | 0D31F30EB5D1A4FBE0584B9220513A1B |
| SHA1: | 9BA055F8D90F99DB5AD107BA037E9FC41F1EB5CD |
| SHA256: | AB9373E1F9EF62FEB386ED608B49C81D0469ADEE2CDDA9335BCC46F26DFAADED |
| SSDEEP: | 98304:7cr9NFwsXTqw9kaP4BP49kAabo00tW4buGHbVZE7u84CifZG:+/ |
MALICIOUS
Uses Task Scheduler to run other applications
- cmd.exe (PID: 7392)
- cmd.exe (PID: 6032)
ORCUS has been detected (YARA)
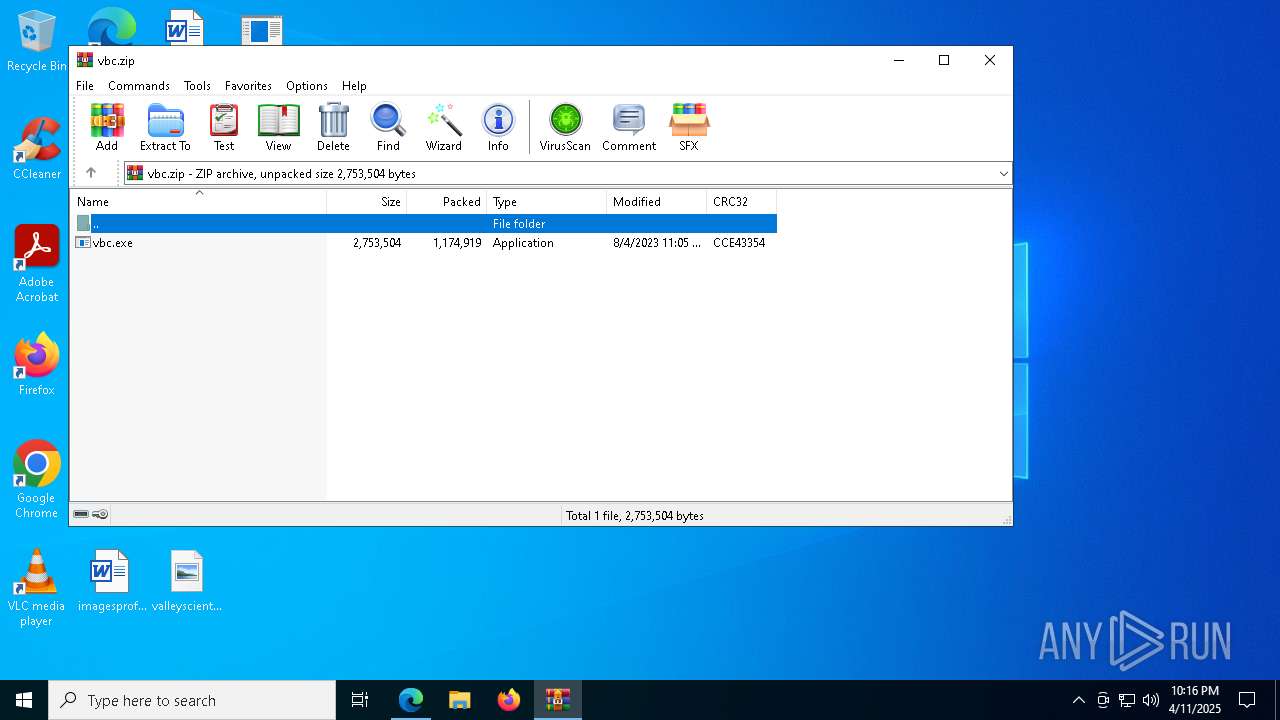
- vbc.exe (PID: 7516)
Orcus is detected
- vbc.exe (PID: 2432)
- vbc.exe (PID: 7516)
SUSPICIOUS
Likely accesses (executes) a file from the Public directory
- OneDrive.exe (PID: 7372)
- cmd.exe (PID: 7392)
- schtasks.exe (PID: 7464)
- OneDrive.exe (PID: 7192)
- cmd.exe (PID: 6032)
- schtasks.exe (PID: 3884)
Starts CMD.EXE for commands execution
- OneDrive.exe (PID: 7372)
- OneDrive.exe (PID: 7192)
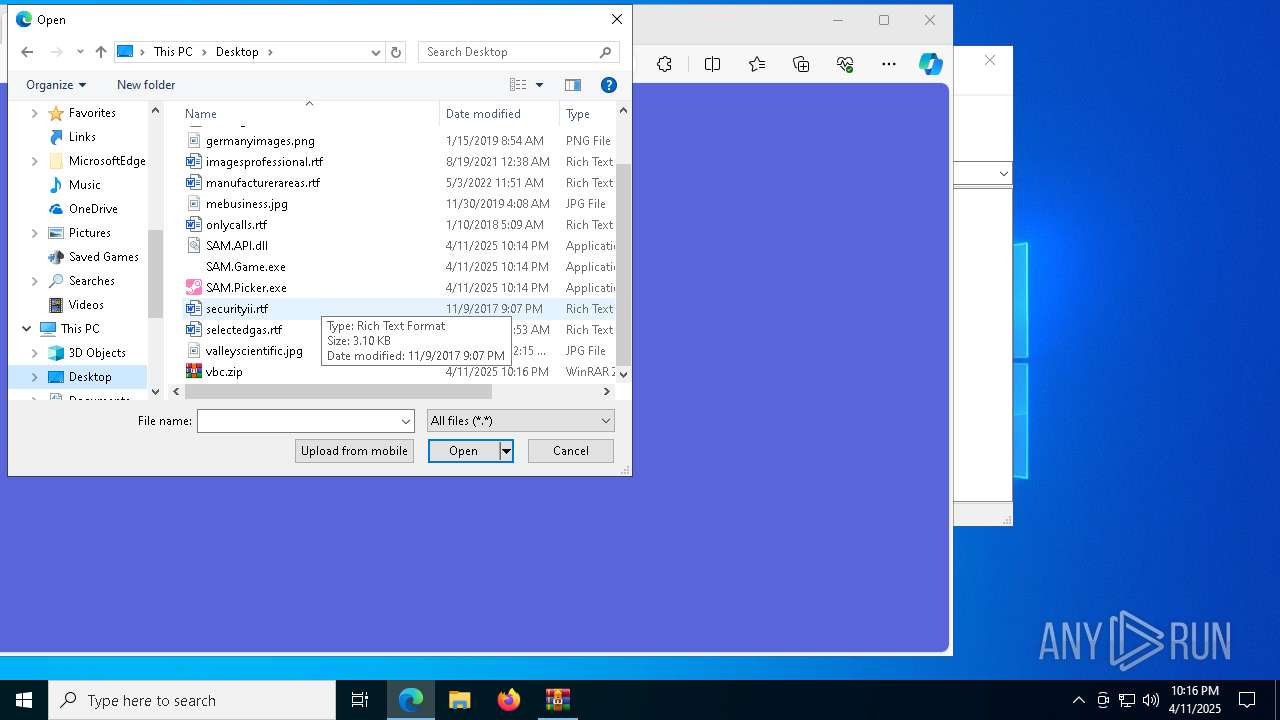
Executable content was dropped or overwritten
- 2025-04-10_0d31f30eb5d1a4fbe0584b9220513a1b_black-basta_elex_luca-stealer.exe (PID: 7312)
Reads security settings of Internet Explorer
- 2025-04-10_0d31f30eb5d1a4fbe0584b9220513a1b_black-basta_elex_luca-stealer.exe (PID: 7312)
- 2025-04-10_0d31f30eb5d1a4fbe0584b9220513a1b_black-basta_elex_luca-stealer.exe (PID: 6436)
- SAM.Game.exe (PID: 7280)
- SAM.Game.exe (PID: 7436)
- WinRAR.exe (PID: 4164)
There is functionality for taking screenshot (YARA)
- vbc.exe (PID: 7516)
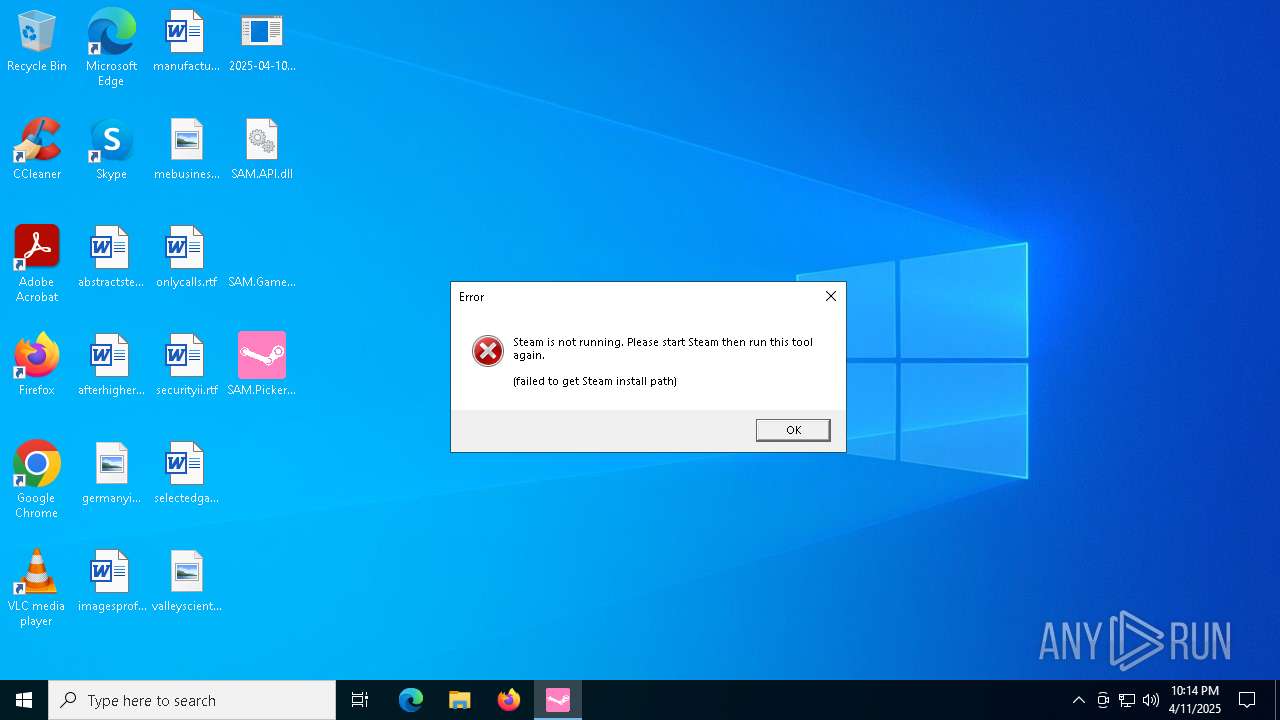
Possible Social Engineering Attempted
- msedge.exe (PID: 7996)
Application launched itself
- WinRAR.exe (PID: 4164)
Process drops legitimate windows executable
- WinRAR.exe (PID: 3124)
- WinRAR.exe (PID: 5216)
Connects to unusual port
- vbc.exe (PID: 7516)
INFO
Reads the computer name
- 2025-04-10_0d31f30eb5d1a4fbe0584b9220513a1b_black-basta_elex_luca-stealer.exe (PID: 7312)
- SAM.Game.exe (PID: 7436)
- SAM.Picker.exe (PID: 7564)
- 2025-04-10_0d31f30eb5d1a4fbe0584b9220513a1b_black-basta_elex_luca-stealer.exe (PID: 6436)
- SAM.Game.exe (PID: 7280)
- SAM.Picker.exe (PID: 6540)
- vbc.exe (PID: 2432)
- vbc.exe (PID: 7516)
- identity_helper.exe (PID: 6300)
Checks supported languages
- 2025-04-10_0d31f30eb5d1a4fbe0584b9220513a1b_black-basta_elex_luca-stealer.exe (PID: 7312)
- OneDrive.exe (PID: 7372)
- SAM.Game.exe (PID: 7436)
- SAM.Picker.exe (PID: 7564)
- OneDrive.exe (PID: 7192)
- 2025-04-10_0d31f30eb5d1a4fbe0584b9220513a1b_black-basta_elex_luca-stealer.exe (PID: 6436)
- SAM.Game.exe (PID: 7280)
- SAM.Picker.exe (PID: 6540)
- vbc.exe (PID: 2432)
- vbc.exe (PID: 7516)
- identity_helper.exe (PID: 6300)
Process checks computer location settings
- 2025-04-10_0d31f30eb5d1a4fbe0584b9220513a1b_black-basta_elex_luca-stealer.exe (PID: 7312)
- 2025-04-10_0d31f30eb5d1a4fbe0584b9220513a1b_black-basta_elex_luca-stealer.exe (PID: 6436)
- SAM.Game.exe (PID: 7280)
- SAM.Game.exe (PID: 7436)
Manual execution by a user
- vbc.exe (PID: 7516)
- 2025-04-10_0d31f30eb5d1a4fbe0584b9220513a1b_black-basta_elex_luca-stealer.exe (PID: 6436)
- vbc.exe (PID: 2432)
- msedge.exe (PID: 5156)
- WinRAR.exe (PID: 4164)
- WinRAR.exe (PID: 5216)
Reads security settings of Internet Explorer
- dllhost.exe (PID: 7224)
- dllhost.exe (PID: 5772)
Reads the machine GUID from the registry
- vbc.exe (PID: 2432)
- vbc.exe (PID: 7516)
Reads the software policy settings
- slui.exe (PID: 7692)
- slui.exe (PID: 516)
Application launched itself
- msedge.exe (PID: 5156)
Reads Environment values
- identity_helper.exe (PID: 6300)
The sample compiled with english language support
- WinRAR.exe (PID: 3124)
- WinRAR.exe (PID: 5216)
- dllhost.exe (PID: 5772)
- msedge.exe (PID: 2800)
Checks proxy server information
- slui.exe (PID: 516)
Executable content was dropped or overwritten
- msedge.exe (PID: 2800)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Orcus
(PID) Process(7516) vbc.exe
C2 (1)196.251.117.118:10134
Keys
AESdf8eccec99ea0ef2ddb53977812cfff4e61c11eabc379561710c0a572601f9e6
Salt
Options
AutostartBuilderProperty
AutostartMethodDisable
TaskSchedulerTaskNameOrcus
TaskHighestPrivilegestrue
RegistryHiddenStarttrue
RegistryKeyNameOrcus
TryAllAutostartMethodsOnFailtrue
ChangeAssemblyInformationBuilderProperty
ChangeAssemblyInformationfalse
AssemblyTitlenull
AssemblyDescriptionnull
AssemblyCompanyNamenull
AssemblyProductNamenull
AssemblyCopyrightnull
AssemblyTrademarksnull
AssemblyProductVersion1.0.0.0
AssemblyFileVersion1.0.0.0
ChangeCreationDateBuilderProperty
IsEnabledfalse
NewCreationDate2025-04-09T13:18:00
ChangeIconBuilderProperty
ChangeIconfalse
IconPathnull
ClientTagBuilderProperty
ClientTaggvelond
DataFolderBuilderProperty
Path%appdata%\Orcus
DefaultPrivilegesBuilderProperty
RequireAdministratorRightsfalse
DisableInstallationPromptBuilderProperty
IsDisabledfalse
FrameworkVersionBuilderProperty
FrameworkVersionNET45
HideFileBuilderProperty
HideFilefalse
InstallationLocationBuilderProperty
Path%programfiles%\Orcus\Orcus.exe
InstallBuilderProperty
Installfalse
KeyloggerBuilderProperty
IsEnabledfalse
MutexBuilderProperty
Mutexdf923e33bf0f4447a5034d5ddb8c42b0
ProxyBuilderProperty
ProxyOptionNone
ProxyAddressnull
ProxyPort1080
ProxyType2
ReconnectDelayProperty
Delay10000
RequireAdministratorPrivilegesInstallerBuilderProperty
RequireAdministratorPrivilegestrue
RespawnTaskBuilderProperty
IsEnabledfalse
TaskNameOrcus Respawner
ServiceBuilderProperty
Installfalse
SetRunProgramAsAdminFlagBuilderProperty
SetFlagfalse
WatchdogBuilderProperty
IsEnabledfalse
NameOrcusWatchdog.exe
WatchdogLocationAppData
PreventFileDeletionfalse
Plugins (0)
TRiD
| .exe | | | Generic CIL Executable (.NET, Mono, etc.) (56.7) |
|---|---|---|
| .exe | | | Win64 Executable (generic) (21.3) |
| .scr | | | Windows screen saver (10.1) |
| .dll | | | Win32 Dynamic Link Library (generic) (5) |
| .exe | | | Win32 Executable (generic) (3.4) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2085:03:04 13:02:49+00:00 |
| ImageFileCharacteristics: | Executable, Large address aware |
| PEType: | PE32 |
| LinkerVersion: | 48 |
| CodeSize: | 1807360 |
| InitializedDataSize: | 2048 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x1bb34e |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 6 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 1.0.0.0 |
| ProductVersionNumber: | 1.0.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
| Comments: | - |
| CompanyName: | - |
| FileDescription: | Loaderr |
| FileVersion: | 1.0.0.0 |
| InternalName: | Loaderr.exe |
| LegalCopyright: | Copyright © 2025 |
| LegalTrademarks: | - |
| OriginalFileName: | Loaderr.exe |
| ProductName: | Loaderr |
| ProductVersion: | 1.0.0.0 |
| AssemblyVersion: | 1.0.0.0 |
Total processes
228
Monitored processes
86
Malicious processes
2
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 240 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=chrome.mojom.UtilWin --lang=en-US --service-sandbox-type=none --no-appcompat-clear --mojo-platform-channel-handle=4208 --field-trial-handle=2396,i,4507333540107788036,11532467678257589342,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 300 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=asset_store.mojom.AssetStoreService --lang=en-US --service-sandbox-type=asset_store_service --no-appcompat-clear --mojo-platform-channel-handle=5848 --field-trial-handle=2396,i,4507333540107788036,11532467678257589342,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 516 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 644 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=5684 --field-trial-handle=2396,i,4507333540107788036,11532467678257589342,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 668 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=5344 --field-trial-handle=2396,i,4507333540107788036,11532467678257589342,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Version: 122.0.2365.59 Modules
| |||||||||||||||
| 924 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=renderer --no-appcompat-clear --disable-gpu-compositing --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=17 --mojo-platform-channel-handle=6684 --field-trial-handle=2396,i,4507333540107788036,11532467678257589342,262144 --variations-seed-version /prefetch:1 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1244 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=5824 --field-trial-handle=2396,i,4507333540107788036,11532467678257589342,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1328 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=gpu-process --disable-gpu-sandbox --use-gl=disabled --gpu-vendor-id=5140 --gpu-device-id=140 --gpu-sub-system-id=0 --gpu-revision=0 --gpu-driver-version=10.0.19041.3636 --no-appcompat-clear --gpu-preferences=WAAAAAAAAADoAAAMAAAAAAAAAAAAAAAAAABgAAAAAAA4AAAAAAAAAAAAAABEAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAGAAAAAAAAAAYAAAAAAAAAAgAAAAAAAAACAAAAAAAAAAIAAAAAAAAAA== --mojo-platform-channel-handle=4264 --field-trial-handle=2396,i,4507333540107788036,11532467678257589342,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1812 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=7352 --field-trial-handle=2396,i,4507333540107788036,11532467678257589342,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1912 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=7756 --field-trial-handle=2396,i,4507333540107788036,11532467678257589342,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
Total events
14 889
Read events
14 771
Write events
115
Delete events
3
Modification events
| (PID) Process: | (5156) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (5156) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (5156) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (5156) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\StabilityMetrics |
| Operation: | write | Name: | user_experience_metrics.stability.exited_cleanly |
Value: 0 | |||
| (PID) Process: | (5156) msedge.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\EdgeUpdate\ClientStateMedium\{56EB18F8-B008-4CBD-B6D2-8C97FE7E9062}\LastWasDefault |
| Operation: | write | Name: | S-1-5-21-1693682860-607145093-2874071422-1001 |
Value: 86C160531E912F00 | |||
| (PID) Process: | (5156) msedge.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\EdgeUpdate\ClientStateMedium\{56EB18F8-B008-4CBD-B6D2-8C97FE7E9062}\LastWasDefault |
| Operation: | write | Name: | S-1-5-21-1693682860-607145093-2874071422-1001 |
Value: 26D968531E912F00 | |||
| (PID) Process: | (5156) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\WindowProperties\131832 |
| Operation: | write | Name: | WindowTabManagerFileMappingId |
Value: {8E487228-F2E3-4371-B377-60BF4C4E18A1} | |||
| (PID) Process: | (5156) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\WindowProperties\131832 |
| Operation: | write | Name: | WindowTabManagerFileMappingId |
Value: {EEC72AF3-2715-4C92-9DD0-E49F7471DC61} | |||
| (PID) Process: | (5156) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\WindowProperties\131832 |
| Operation: | write | Name: | WindowTabManagerFileMappingId |
Value: {1B3CA205-715F-45B0-9B4C-E051B7D7749D} | |||
| (PID) Process: | (5156) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\WindowProperties\131832 |
| Operation: | write | Name: | WindowTabManagerFileMappingId |
Value: {9297B597-2219-4CE6-9363-C53116F4A429} | |||
Executable files
49
Suspicious files
922
Text files
144
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 5156 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\parcel_tracking_db\LOG.old~RF119f69.TMP | — | |
MD5:— | SHA256:— | |||
| 5156 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\parcel_tracking_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 5156 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\PersistentOriginTrials\LOG.old~RF119f69.TMP | — | |
MD5:— | SHA256:— | |||
| 5156 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old~RF119f79.TMP | — | |
MD5:— | SHA256:— | |||
| 5156 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\PersistentOriginTrials\LOG.old | — | |
MD5:— | SHA256:— | |||
| 5156 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 5156 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\discounts_db\LOG.old~RF119f79.TMP | — | |
MD5:— | SHA256:— | |||
| 5156 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\discounts_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 5156 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Variations | binary | |
MD5:6971E42ED64D2BE125547F021EB852B1 | SHA256:B46CFDC4106DF566F71AA34D6F10B53767C561DFD17DD07A5930A18E67BB344B | |||
| 5156 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\EdgePushStorageWithConnectTokenAndKey\LOG.old~RF119fa8.TMP | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
53
TCP/UDP connections
226
DNS requests
122
Threats
7
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1072 | SIHClient.exe | GET | 200 | 23.218.209.163:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 2.16.164.18:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
7748 | svchost.exe | GET | 206 | 208.89.74.29:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/5d32607d-eea9-44fc-ac55-77800b9862a5?P1=1744954408&P2=404&P3=2&P4=D88NJJMaAPeBQlVJGNxSn1IQ0A7xqcs918s28dAkH%2b2TPVhwr0uGWCAIzKQXupcF0EkXl5KNyy1TvV%2fX5AWQ7g%3d%3d | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
1072 | SIHClient.exe | GET | 200 | 23.218.209.163:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
7748 | svchost.exe | HEAD | 200 | 208.89.74.29:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/5d32607d-eea9-44fc-ac55-77800b9862a5?P1=1744954408&P2=404&P3=2&P4=D88NJJMaAPeBQlVJGNxSn1IQ0A7xqcs918s28dAkH%2b2TPVhwr0uGWCAIzKQXupcF0EkXl5KNyy1TvV%2fX5AWQ7g%3d%3d | unknown | — | — | whitelisted |
7748 | svchost.exe | GET | 206 | 208.89.74.29:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/5d32607d-eea9-44fc-ac55-77800b9862a5?P1=1744954408&P2=404&P3=2&P4=D88NJJMaAPeBQlVJGNxSn1IQ0A7xqcs918s28dAkH%2b2TPVhwr0uGWCAIzKQXupcF0EkXl5KNyy1TvV%2fX5AWQ7g%3d%3d | unknown | — | — | whitelisted |
7748 | svchost.exe | GET | 206 | 208.89.74.29:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/5d32607d-eea9-44fc-ac55-77800b9862a5?P1=1744954408&P2=404&P3=2&P4=D88NJJMaAPeBQlVJGNxSn1IQ0A7xqcs918s28dAkH%2b2TPVhwr0uGWCAIzKQXupcF0EkXl5KNyy1TvV%2fX5AWQ7g%3d%3d | unknown | — | — | whitelisted |
7748 | svchost.exe | GET | 206 | 208.89.74.29:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/5d32607d-eea9-44fc-ac55-77800b9862a5?P1=1744954408&P2=404&P3=2&P4=D88NJJMaAPeBQlVJGNxSn1IQ0A7xqcs918s28dAkH%2b2TPVhwr0uGWCAIzKQXupcF0EkXl5KNyy1TvV%2fX5AWQ7g%3d%3d | unknown | — | — | whitelisted |
7748 | svchost.exe | GET | 206 | 208.89.74.29:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/5d32607d-eea9-44fc-ac55-77800b9862a5?P1=1744954408&P2=404&P3=2&P4=D88NJJMaAPeBQlVJGNxSn1IQ0A7xqcs918s28dAkH%2b2TPVhwr0uGWCAIzKQXupcF0EkXl5KNyy1TvV%2fX5AWQ7g%3d%3d | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 2.16.164.18:80 | crl.microsoft.com | Akamai International B.V. | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
7516 | vbc.exe | 196.251.117.118:10134 | — | xneelo | SC | malicious |
3216 | svchost.exe | 172.211.123.249:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
6544 | svchost.exe | 20.190.159.73:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6544 | svchost.exe | 2.23.77.188:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
2104 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
1072 | SIHClient.exe | 52.149.20.212:443 | slscr.update.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
config.edge.skype.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
7516 | vbc.exe | Misc Attack | ET DROP Spamhaus DROP Listed Traffic Inbound group 39 |
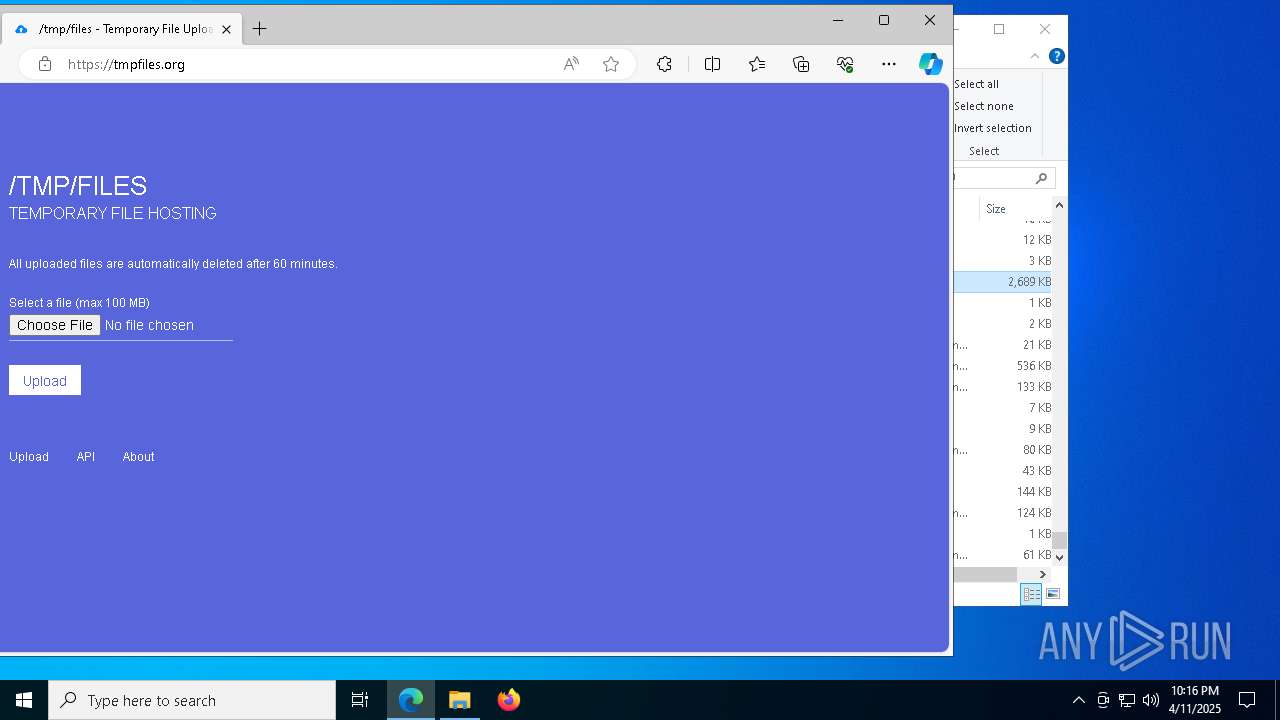
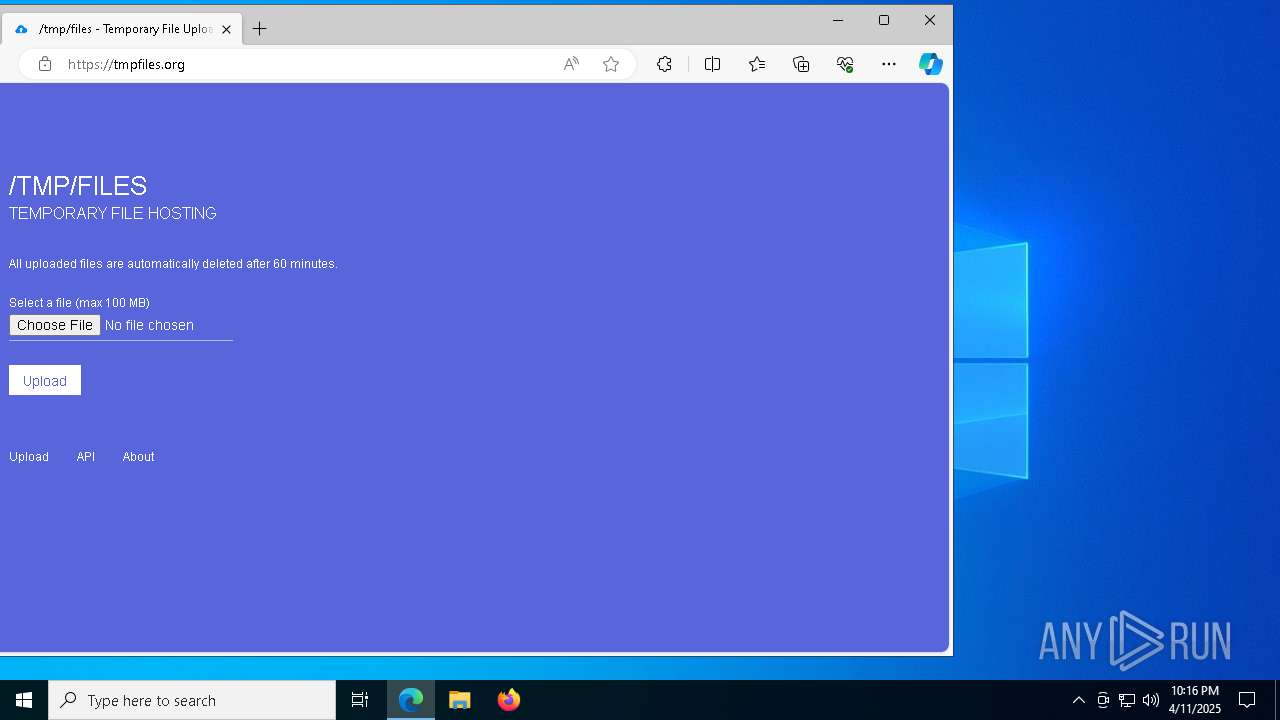
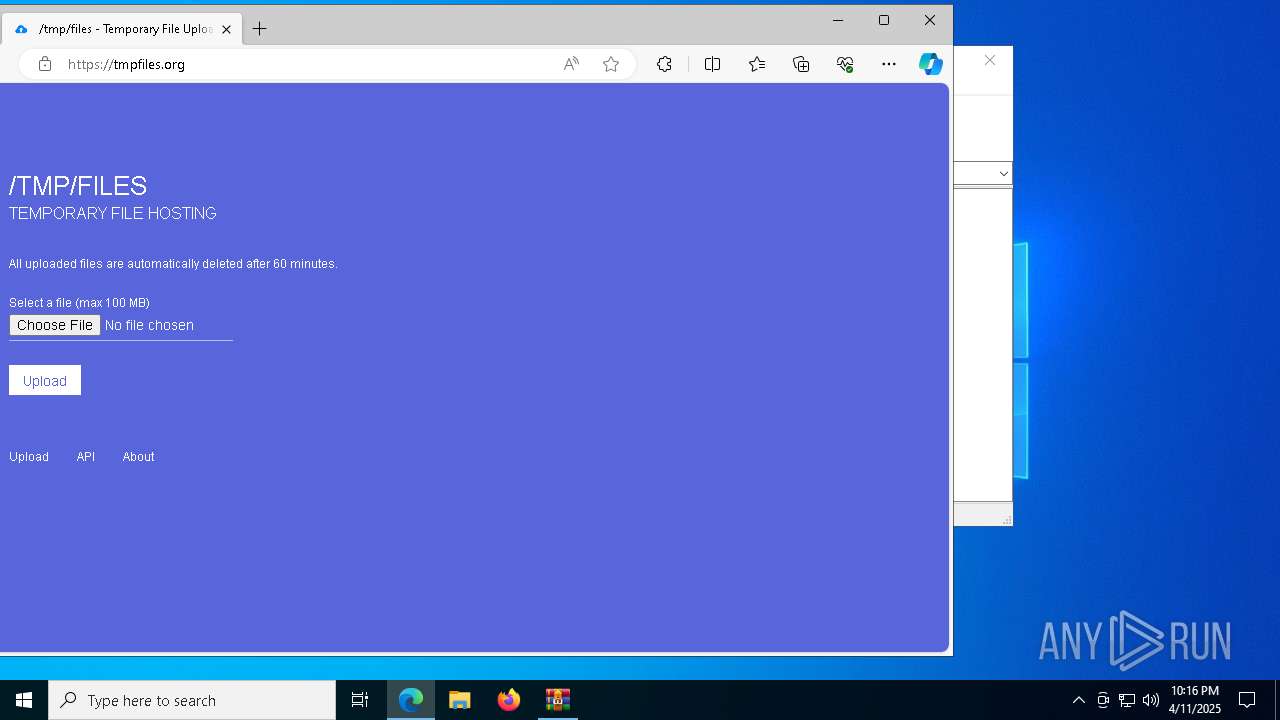
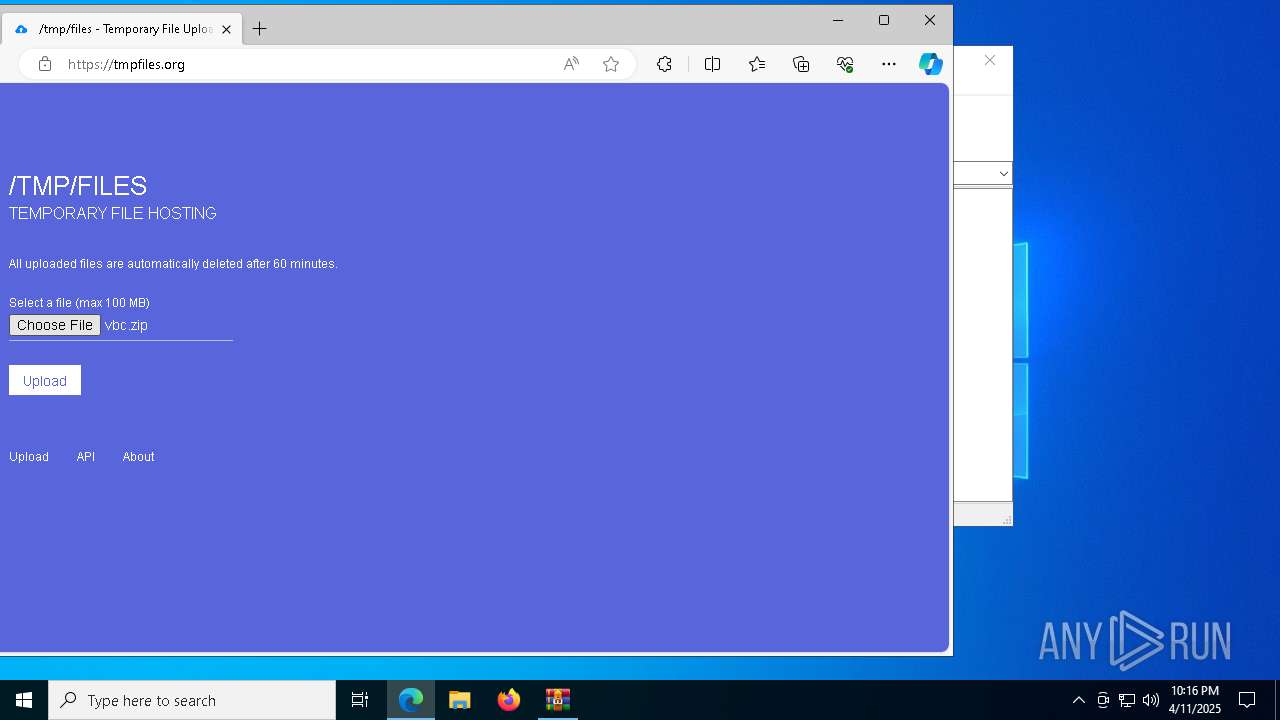
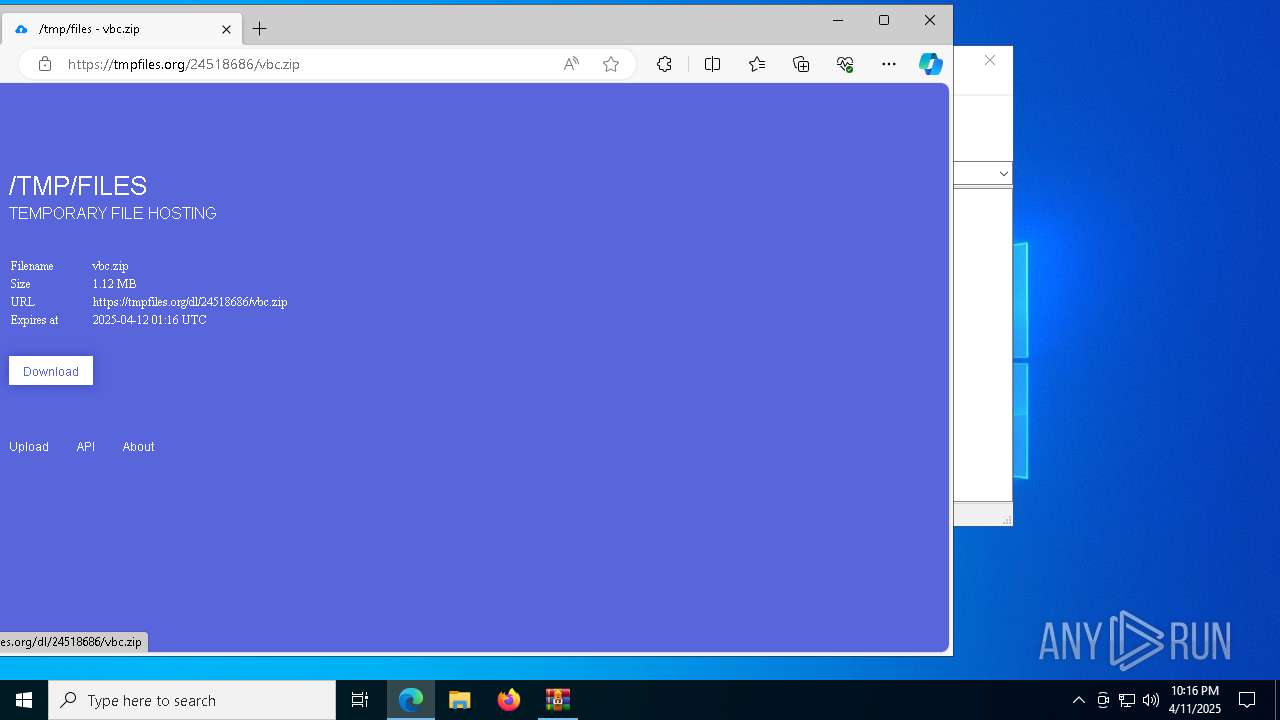
7996 | msedge.exe | Misc activity | ET INFO Temporary File Hosting Domain in DNS Lookup (tmpfiles .org) |
7996 | msedge.exe | Misc activity | ET INFO Temporary File Hosting Domain in DNS Lookup (tmpfiles .org) |
7996 | msedge.exe | Possible Social Engineering Attempted | SUSPICIOUS [ANY.RUN] Domain Marked as Malicious (tmpfiles .org) |
7996 | msedge.exe | Possible Social Engineering Attempted | SUSPICIOUS [ANY.RUN] Domain Marked as Malicious (tmpfiles .org) |
7996 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] Cloudflare Network Error Logging (NEL) |
7996 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] Cloudflare Network Error Logging (NEL) |