| File name: | .redtail |
| Full analysis: | https://app.any.run/tasks/6dcf570e-df95-4cf2-ab23-71bcfbab069e |
| Verdict: | Malicious activity |
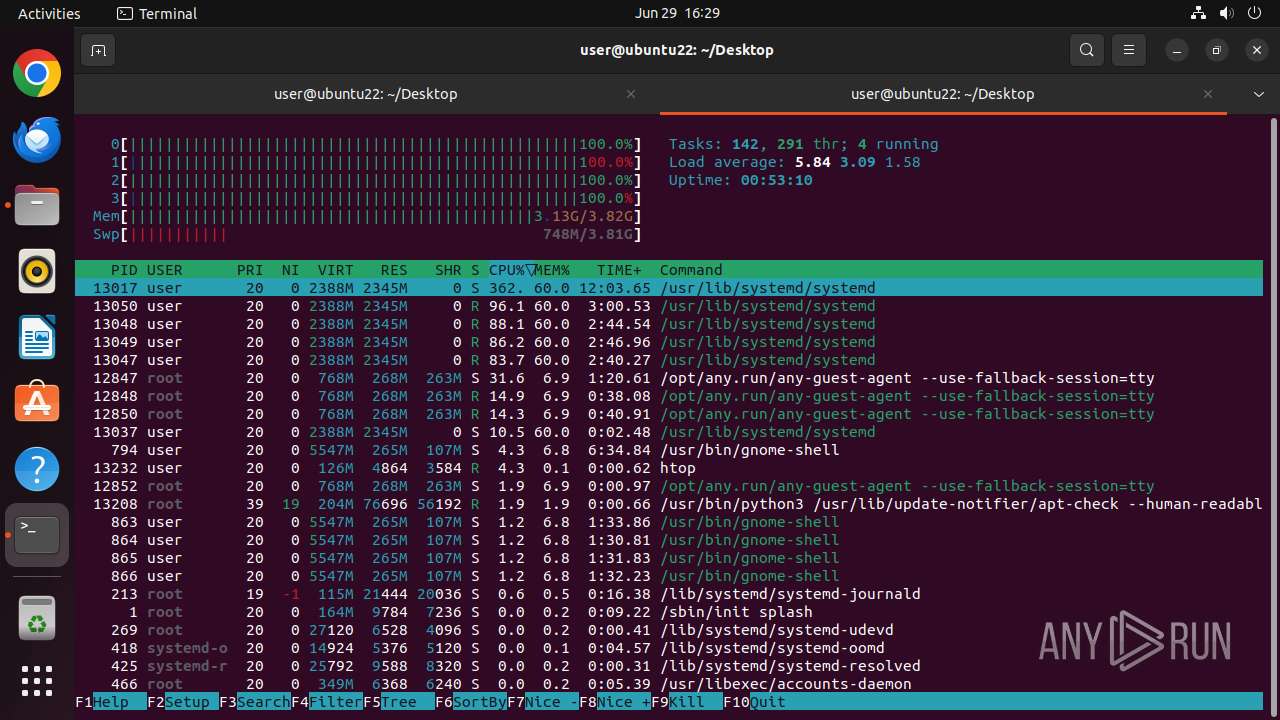
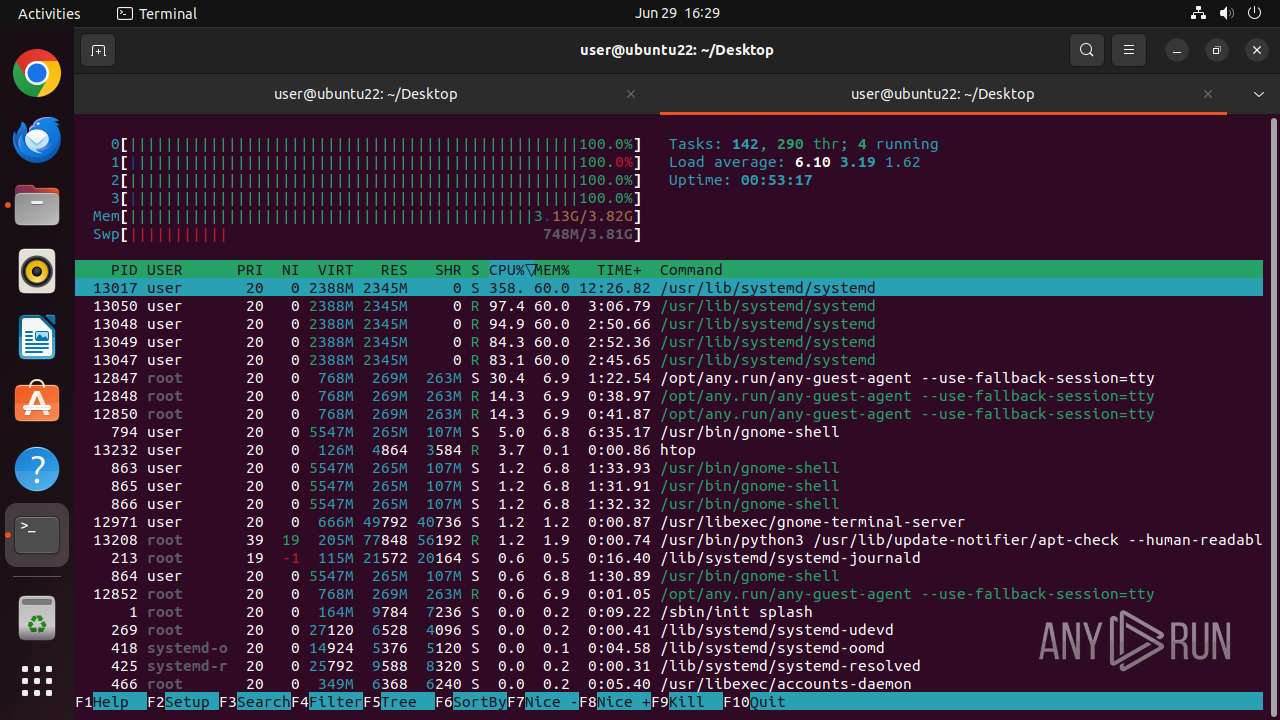
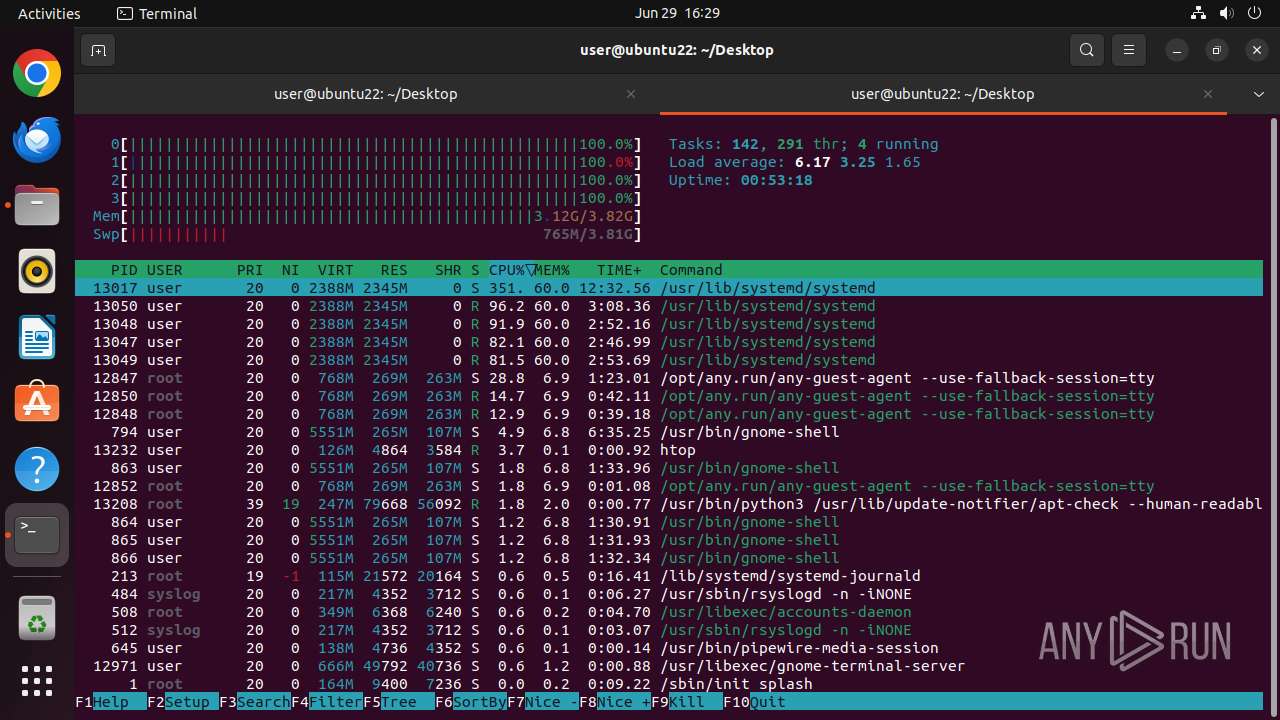
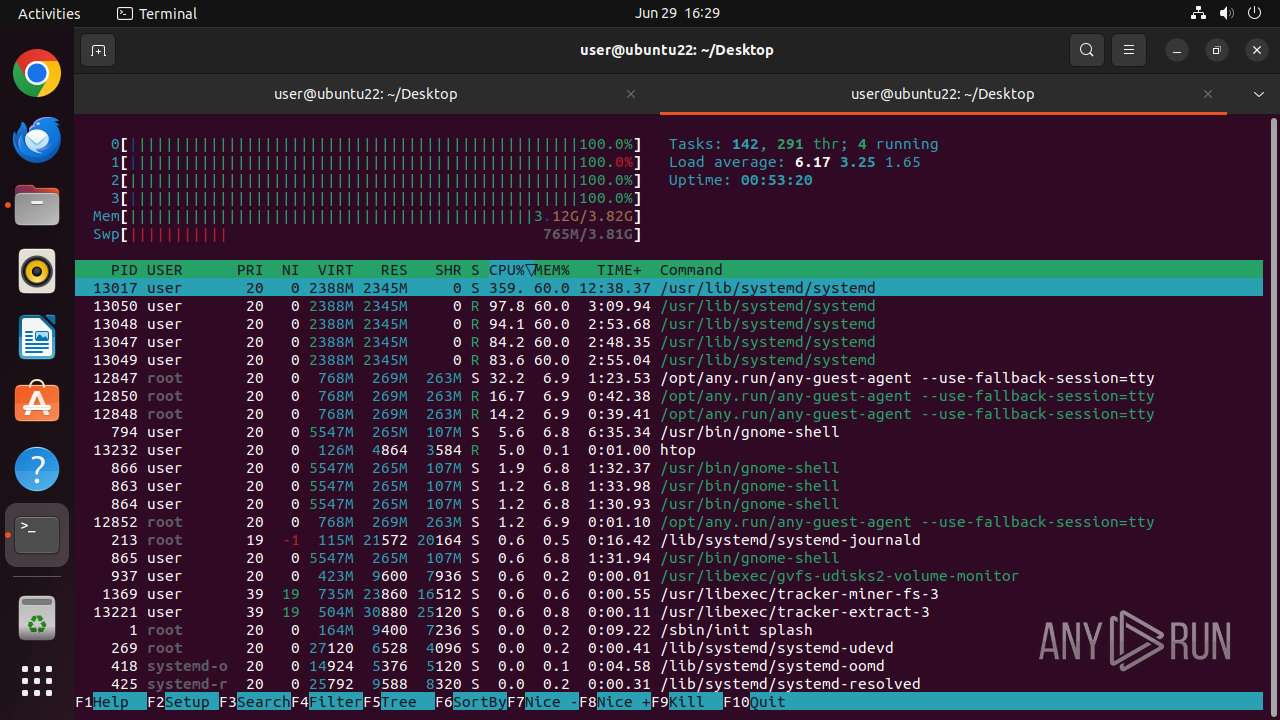
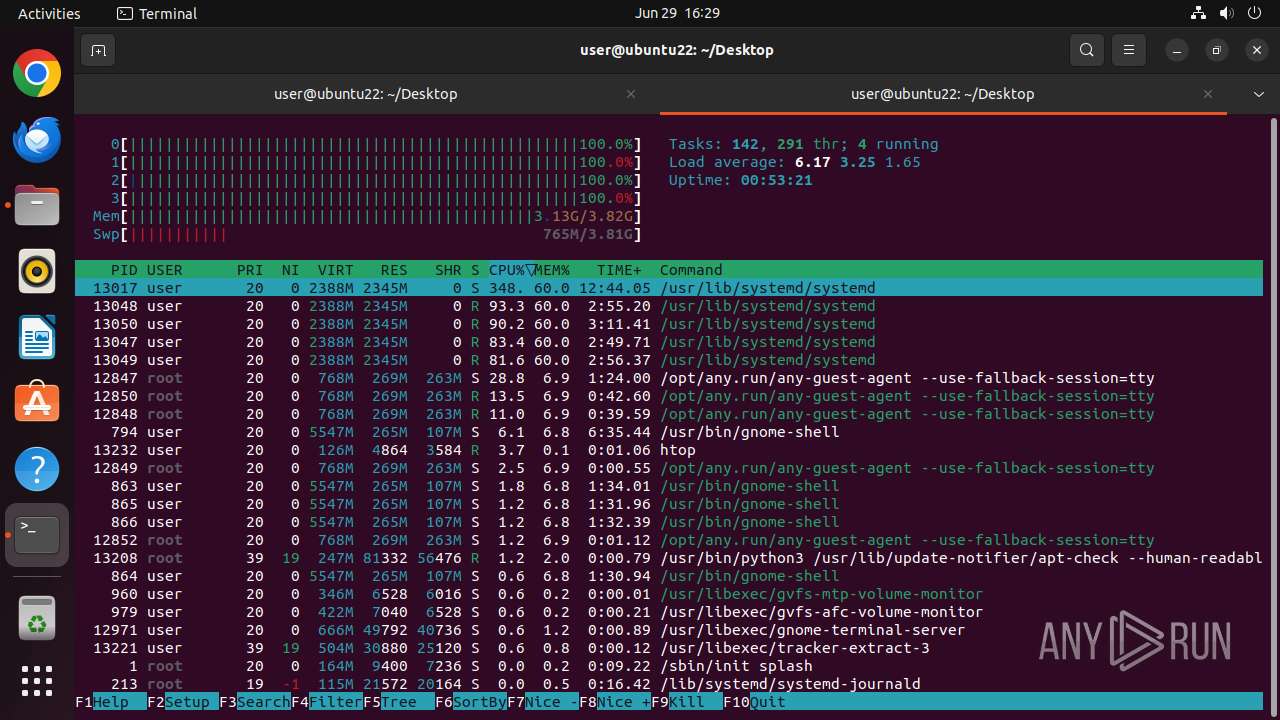
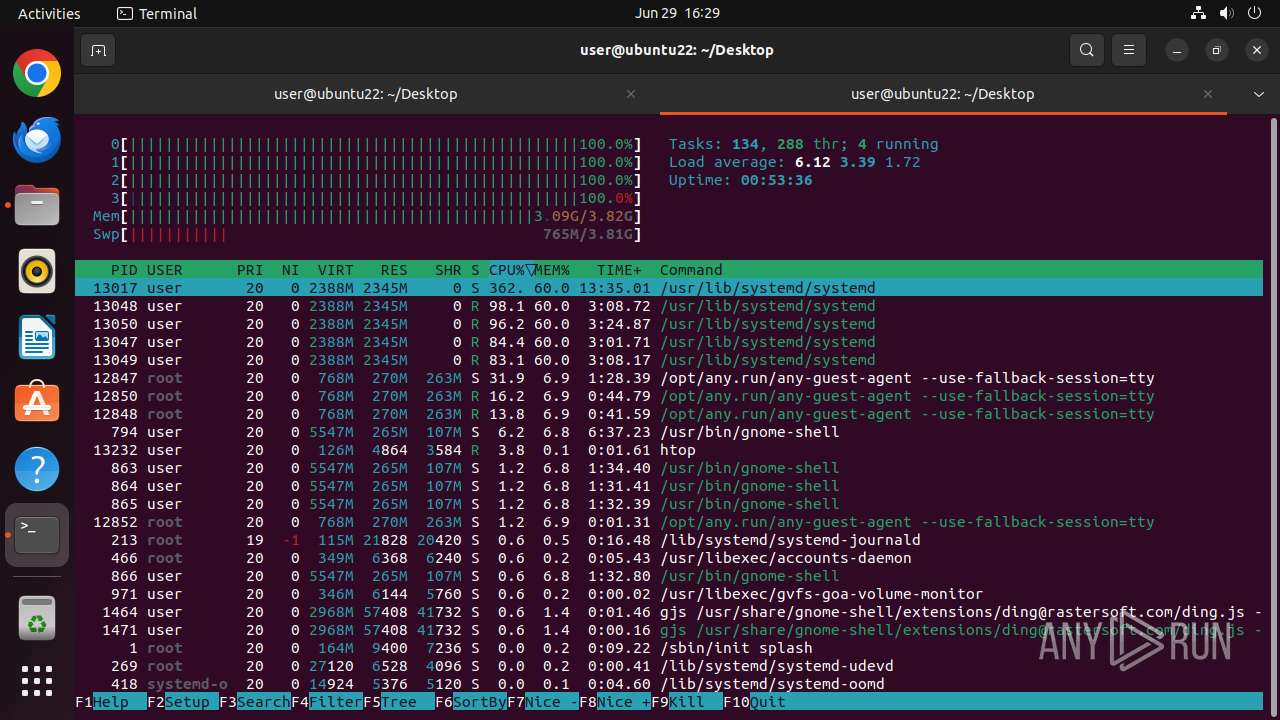
| Threats: | Crypto mining malware is a resource-intensive threat that infiltrates computers with the purpose of mining cryptocurrencies. This type of threat can be deployed either on an infected machine or a compromised website. In both cases the miner will utilize the computing power of the device and its network bandwidth. |
| Analysis date: | June 29, 2024, 15:24:55 |
| OS: | Ubuntu 22.04.2 |
| Tags: | |
| Indicators: | |
| MIME: | application/x-sharedlib |
| File info: | ELF 64-bit LSB shared object, x86-64, version 1 (SYSV), statically linked, no section header |
| MD5: | 07DB7C34621453DB287722245085C5B4 |
| SHA1: | 9D4F2640B89C148E70953D49EB6D7D1867C182D2 |
| SHA256: | AB897157FDEF11B267E986EF286FD44A699E3699A458D90994E020619653D2CD |
| SSDEEP: | 49152:8rp/g+ezhxfndt+1H5PdNpwT9Z5BJqiSk/DHtPaqBBCMNGOfDX879DVxCT5SRMVh:OpY+khxf7cZFNW9BJqPk/7tyqBlNGOfJ |
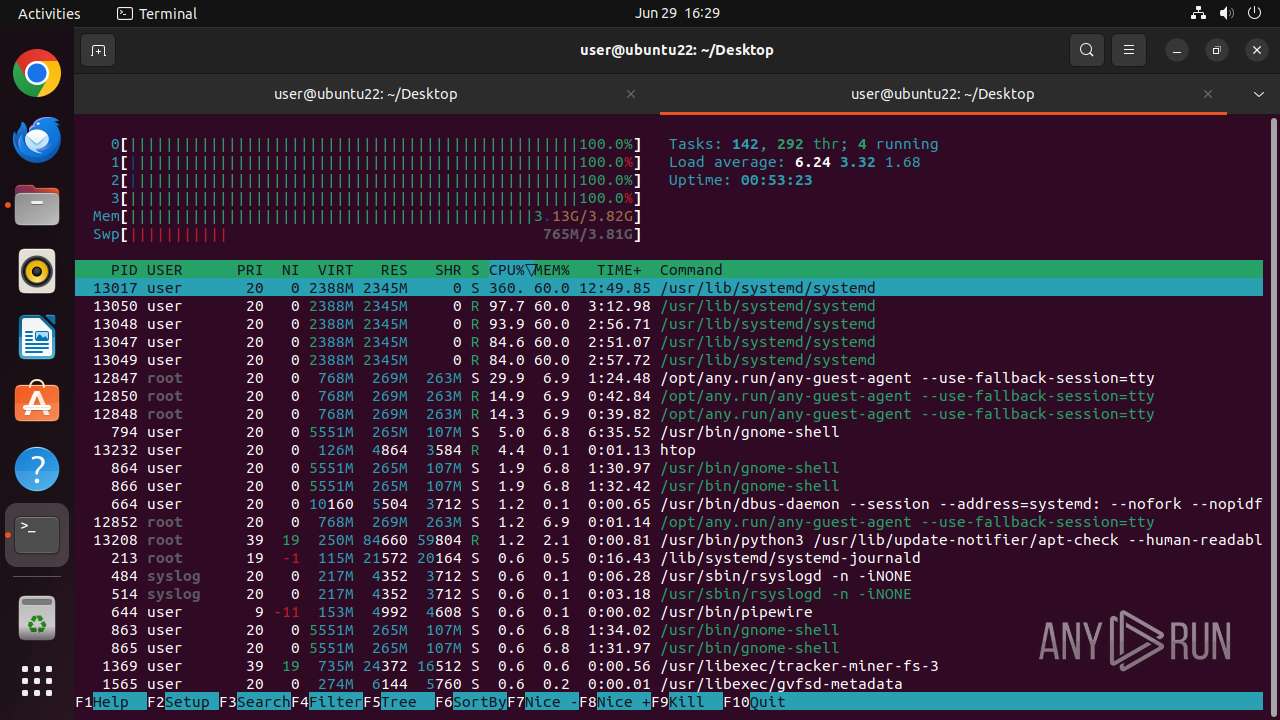
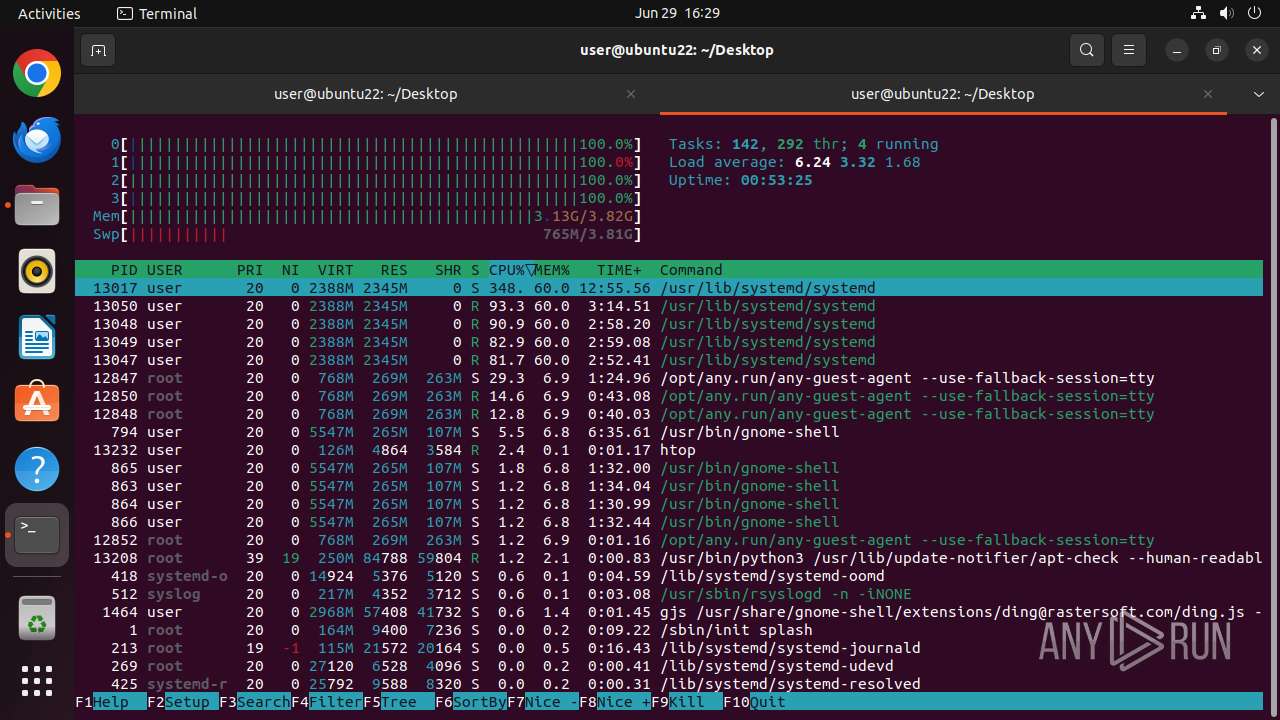
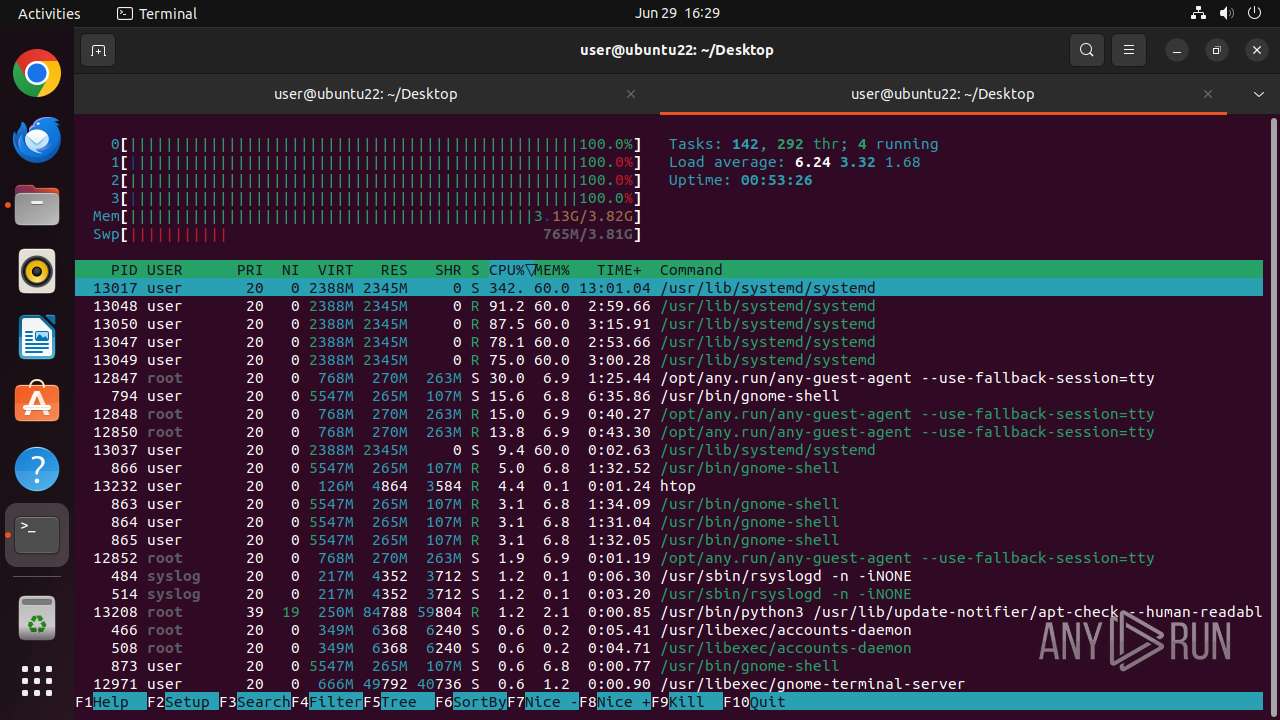
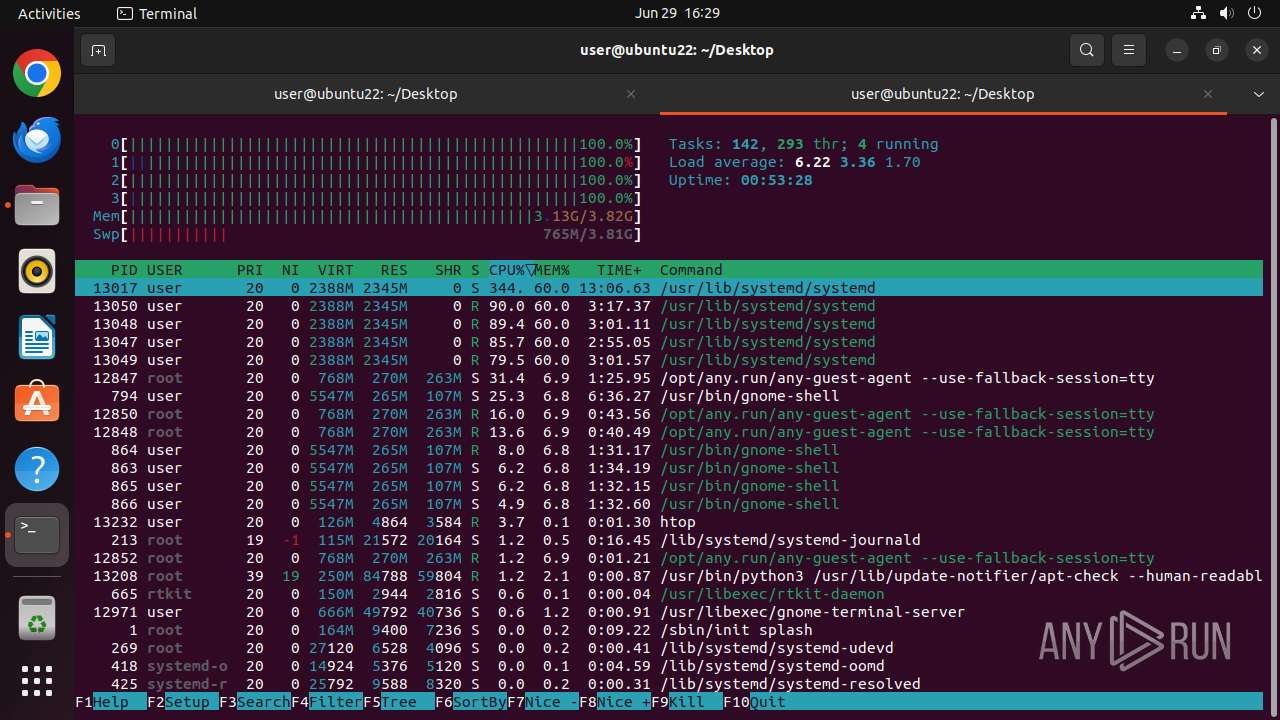
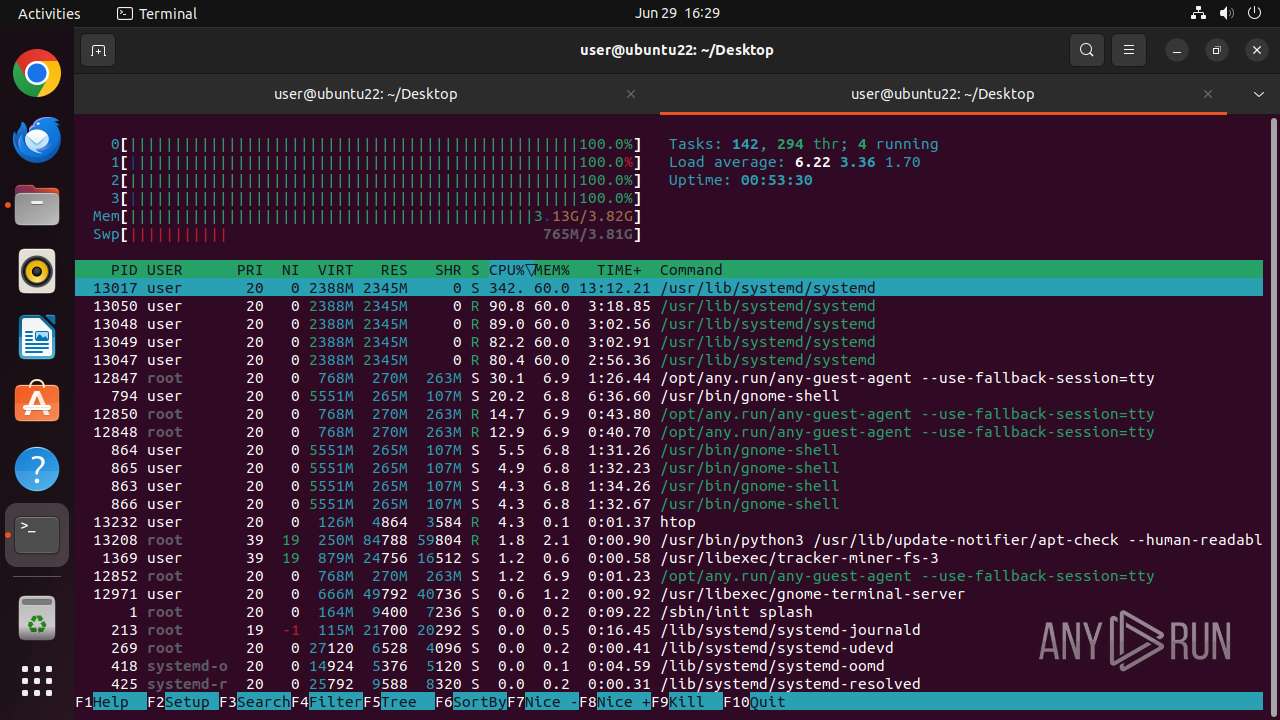
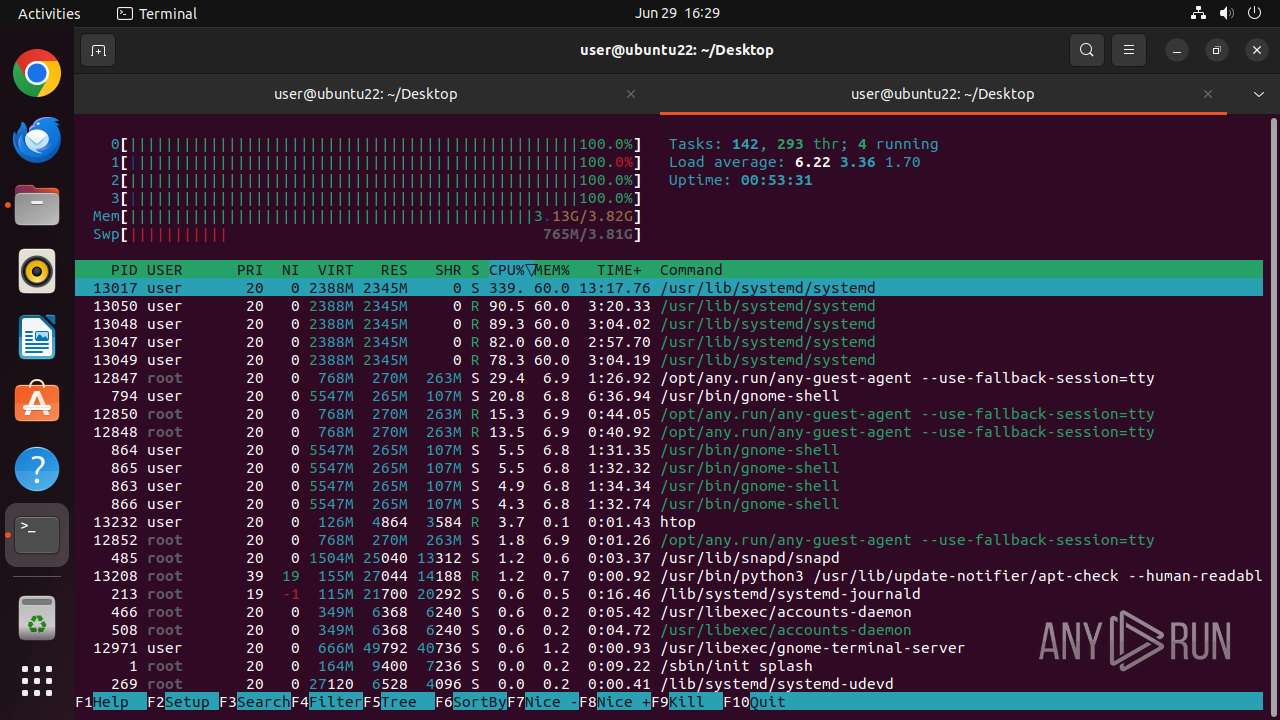
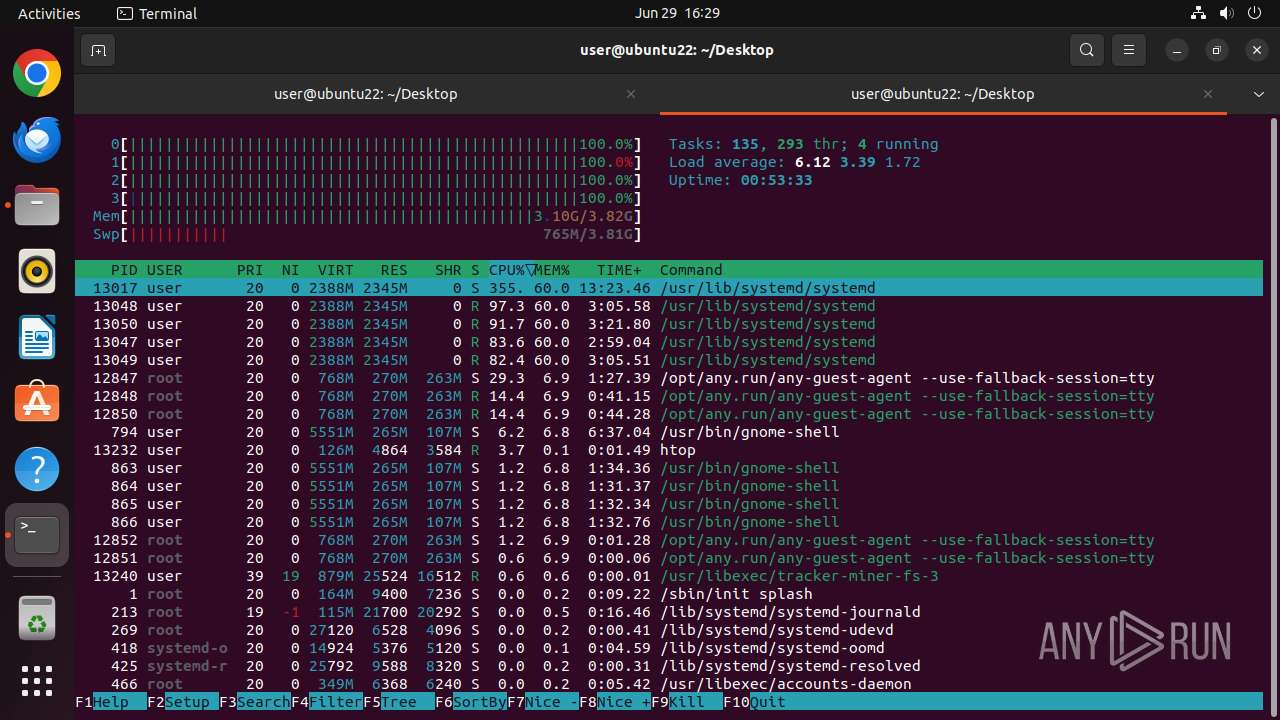
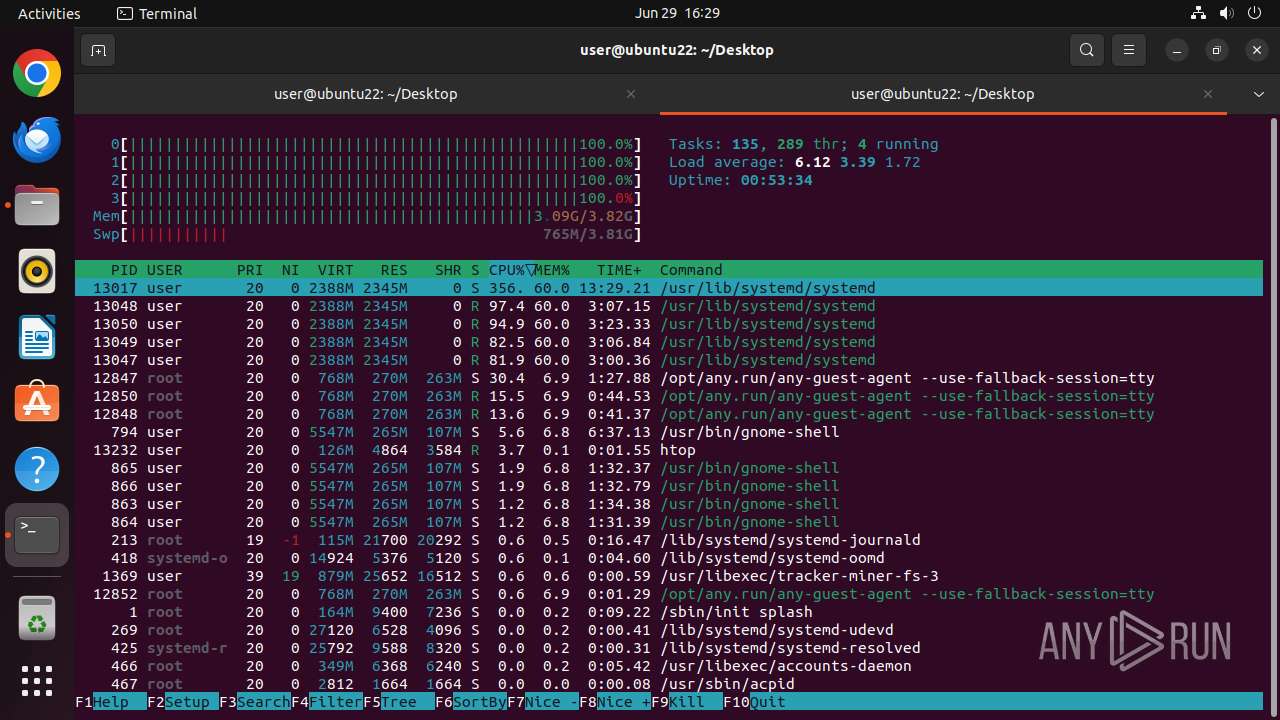
MALICIOUS
MINER has been detected (SURICATA)
- 6dcf570e-df95-4cf2-ab23-71bcfbab069e.o (PID: 13017)
Connects to the CnC server
- 6dcf570e-df95-4cf2-ab23-71bcfbab069e.o (PID: 13017)
SUSPICIOUS
Executes commands using command-line interpreter
- gnome-terminal-server (PID: 12971)
- 6dcf570e-df95-4cf2-ab23-71bcfbab069e.o (PID: 13017)
- update-notifier (PID: 13054)
- cron (PID: 13268)
- apt (PID: 13092)
- dpkg-preconfigure (PID: 13149)
- apt (PID: 13188)
Checks DMI information (probably VM detection)
- systemd-hostnamed (PID: 12953)
- 6dcf570e-df95-4cf2-ab23-71bcfbab069e.o (PID: 13016)
- udevadm (PID: 13026)
Reads /proc/mounts (likely used to find writable filesystems)
- 6dcf570e-df95-4cf2-ab23-71bcfbab069e.o (PID: 13016)
- check-new-release-gtk (PID: 13056)
Manipulating modules (likely to execute programs on system boot)
- modprobe (PID: 13025)
Modifies Cron jobs
- sh (PID: 13019)
Connects to unusual port
- 6dcf570e-df95-4cf2-ab23-71bcfbab069e.o (PID: 13017)
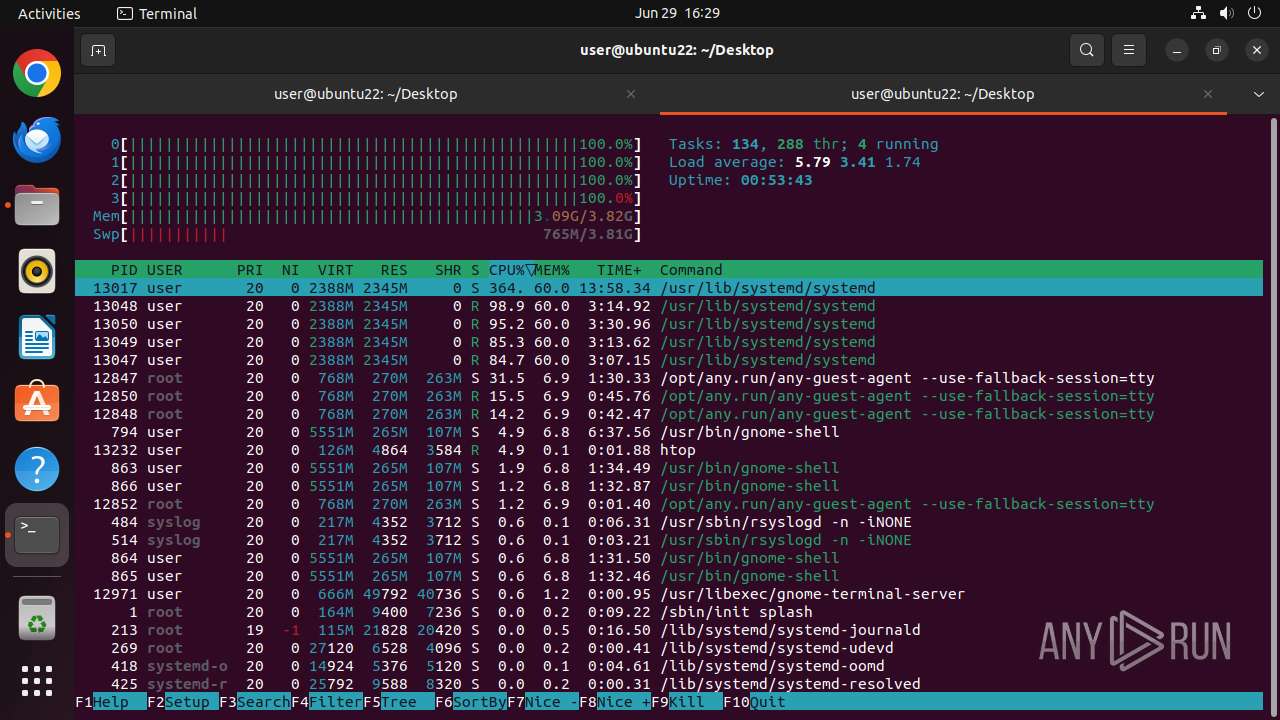
Crypto Currency Mining Activity Detected
- 6dcf570e-df95-4cf2-ab23-71bcfbab069e.o (PID: 13017)
Potential Corporate Privacy Violation
- 6dcf570e-df95-4cf2-ab23-71bcfbab069e.o (PID: 13017)
Changes time attribute to hide new files or make changes to the existing one
- sh (PID: 13192)
Executes the "rm" command to delete files or directories
- update-motd-updates-available (PID: 13194)
- dpkg (PID: 13164)
Checks the user who created the process
- cron (PID: 13268)
Creates or rewrites file in the "bin" folder
- dpkg (PID: 13164)
INFO
No info indicators.
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .o | | | ELF Executable and Linkable format (generic) (100) |
|---|
EXIF
EXE
| CPUArchitecture: | 64 bit |
|---|---|
| CPUByteOrder: | Little endian |
| ObjectFileType: | Shared object file |
| CPUType: | AMD x86-64 |
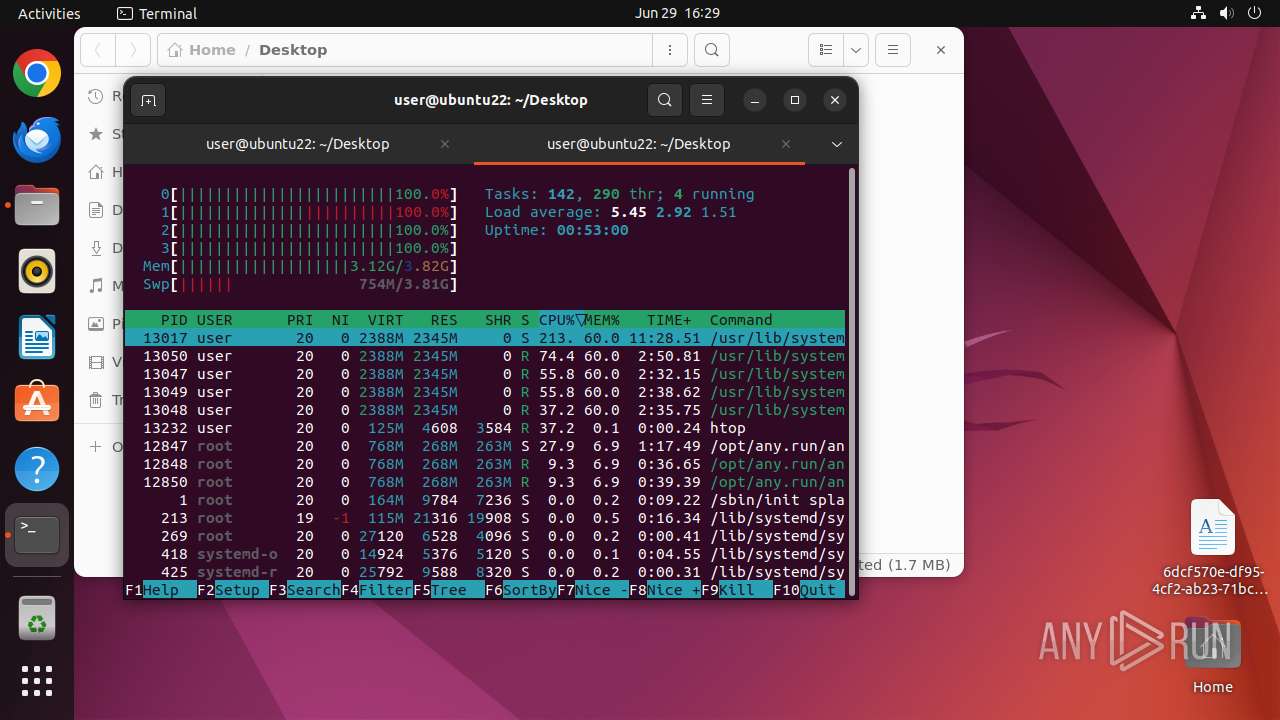
Total processes
370
Monitored processes
154
Malicious processes
3
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process |
|---|---|---|---|---|
| 12936 | /bin/sh -c "DISPLAY=:0 sudo -iu user nautilus /home/user/Desktop/6dcf570e-df95-4cf2-ab23-71bcfbab069e\.o " | /bin/sh | — | any-guest-agent |
User: user Integrity Level: UNKNOWN | ||||
| 12937 | sudo -iu user nautilus /home/user/Desktop/6dcf570e-df95-4cf2-ab23-71bcfbab069e.o | /usr/bin/sudo | — | sh |
User: user Integrity Level: UNKNOWN | ||||
| 12938 | nautilus /home/user/Desktop/6dcf570e-df95-4cf2-ab23-71bcfbab069e.o | /usr/bin/nautilus | — | sudo |
User: user Integrity Level: UNKNOWN | ||||
| 12939 | /usr/bin/locale-check C.UTF-8 | /usr/bin/locale-check | — | nautilus |
User: user Integrity Level: UNKNOWN Exit code: 0 | ||||
| 12953 | /lib/systemd/systemd-hostnamed | /lib/systemd/systemd-hostnamed | — | systemd |
User: root Integrity Level: UNKNOWN Exit code: 1195 | ||||
| 12959 | systemctl --user --global is-enabled snap.snapd-desktop-integration.snapd-desktop-integration.service | /usr/bin/systemctl | — | snapd |
User: root Integrity Level: UNKNOWN Exit code: 482 | ||||
| 12960 | systemctl --user --global is-enabled snap.snapd-desktop-integration.snapd-desktop-integration.service | /usr/bin/systemctl | — | snapd |
User: root Integrity Level: UNKNOWN Exit code: 482 | ||||
| 12962 | systemctl --user --global is-enabled snap.snapd-desktop-integration.snapd-desktop-integration.service | /usr/bin/systemctl | — | snapd |
User: root Integrity Level: UNKNOWN Exit code: 482 | ||||
| 12963 | systemctl --user --global is-enabled snap.snapd-desktop-integration.snapd-desktop-integration.service | /usr/bin/systemctl | — | snapd |
User: root Integrity Level: UNKNOWN Exit code: 482 | ||||
| 12964 | /usr/bin/python3 /usr/bin/gnome-terminal | /usr/bin/gnome-terminal | — | gnome-shell |
User: user Integrity Level: UNKNOWN Exit code: 213 | ||||
Executable files
0
Suspicious files
35
Text files
74
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 13149 | dpkg-preconfigure | /var/cache/debconf/config.dat | text | |
MD5:— | SHA256:— | |||
| 13149 | dpkg-preconfigure | /var/cache/debconf/templates.dat | text | |
MD5:— | SHA256:— | |||
| 13056 | check-new-release-gtk | /tmp/#6029334 (deleted) | text | |
MD5:— | SHA256:— | |||
| 13056 | check-new-release-gtk | /tmp/#6029335 (deleted) | text | |
MD5:— | SHA256:— | |||
| 13056 | check-new-release-gtk | /tmp/#6029359 (deleted) | text | |
MD5:— | SHA256:— | |||
| 13056 | check-new-release-gtk | /tmp/#6029364 (deleted) | text | |
MD5:— | SHA256:— | |||
| 13056 | check-new-release-gtk | /tmp/#6029378 (deleted) | text | |
MD5:— | SHA256:— | |||
| 13056 | check-new-release-gtk | /tmp/#6029379 (deleted) | text | |
MD5:— | SHA256:— | |||
| 13056 | check-new-release-gtk | /home/user/.cache/update-manager-core/meta-release-lts | text | |
MD5:— | SHA256:— | |||
| 13088 | apt | /tmp/#6029334 (deleted) | text | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
3
TCP/UDP connections
25
DNS requests
24
Threats
10
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 204 | 91.189.91.98:80 | http://connectivity-check.ubuntu.com/ | unknown | — | — | unknown |
473 | NetworkManager | GET | 204 | 91.189.91.98:80 | http://connectivity-check.ubuntu.com/ | unknown | — | — | unknown |
13147 | http | GET | 200 | 185.125.190.83:80 | http://archive.ubuntu.com/ubuntu/pool/main/h/htop/htop_3.0.5-7build2_amd64.deb | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
470 | avahi-daemon | 224.0.0.251:5353 | — | — | — | unknown |
— | — | 91.189.91.98:80 | connectivity-check.ubuntu.com | Canonical Group Limited | US | unknown |
— | — | 185.125.190.97:80 | connectivity-check.ubuntu.com | Canonical Group Limited | GB | unknown |
— | — | 195.181.170.19:443 | odrs.gnome.org | Datacamp Limited | DE | unknown |
485 | snapd | 185.125.188.55:443 | api.snapcraft.io | Canonical Group Limited | GB | malicious |
485 | snapd | 185.125.188.54:443 | api.snapcraft.io | Canonical Group Limited | GB | unknown |
485 | snapd | 185.125.188.59:443 | api.snapcraft.io | Canonical Group Limited | GB | unknown |
13017 | 6dcf570e-df95-4cf2-ab23-71bcfbab069e.o | 95.215.19.53:853 | — | ab stract | FI | unknown |
13017 | 6dcf570e-df95-4cf2-ab23-71bcfbab069e.o | 1.1.1.1:853 | — | CLOUDFLARENET | — | malicious |
13017 | 6dcf570e-df95-4cf2-ab23-71bcfbab069e.o | 217.160.70.42:853 | — | IONOS SE | DE | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
connectivity-check.ubuntu.com |
| unknown |
odrs.gnome.org |
| unknown |
api.snapcraft.io |
| unknown |
44.100.168.192.in-addr.arpa |
| unknown |
proxies.internetshadow.org |
| unknown |
changelogs.ubuntu.com |
| unknown |
_http._tcp.archive.ubuntu.com |
| unknown |
archive.ubuntu.com |
| unknown |
Threats
PID | Process | Class | Message |
|---|---|---|---|
13017 | 6dcf570e-df95-4cf2-ab23-71bcfbab069e.o | Misc Attack | ET COMPROMISED Known Compromised or Hostile Host Traffic group 7 |
13017 | 6dcf570e-df95-4cf2-ab23-71bcfbab069e.o | Misc Attack | ET DROP Spamhaus DROP Listed Traffic Inbound group 38 |
13017 | 6dcf570e-df95-4cf2-ab23-71bcfbab069e.o | Misc Attack | ET 3CORESec Poor Reputation IP group 6 |
13017 | 6dcf570e-df95-4cf2-ab23-71bcfbab069e.o | Crypto Currency Mining Activity Detected | MINER [ANY.RUN] CoinMiner Agent CnC Initial Connection |
13017 | 6dcf570e-df95-4cf2-ab23-71bcfbab069e.o | Potential Corporate Privacy Violation | ET POLICY Cryptocurrency Miner Checkin |
13017 | 6dcf570e-df95-4cf2-ab23-71bcfbab069e.o | Misc Attack | ET DROP Spamhaus DROP Listed Traffic Inbound group 14 |
13017 | 6dcf570e-df95-4cf2-ab23-71bcfbab069e.o | Misc Attack | ET 3CORESec Poor Reputation IP group 12 |
13017 | 6dcf570e-df95-4cf2-ab23-71bcfbab069e.o | Potential Corporate Privacy Violation | ET POLICY Cryptocurrency Miner Checkin |
13147 | http | Not Suspicious Traffic | ET POLICY GNU/Linux APT User-Agent Outbound likely related to package management |
1 ETPRO signatures available at the full report