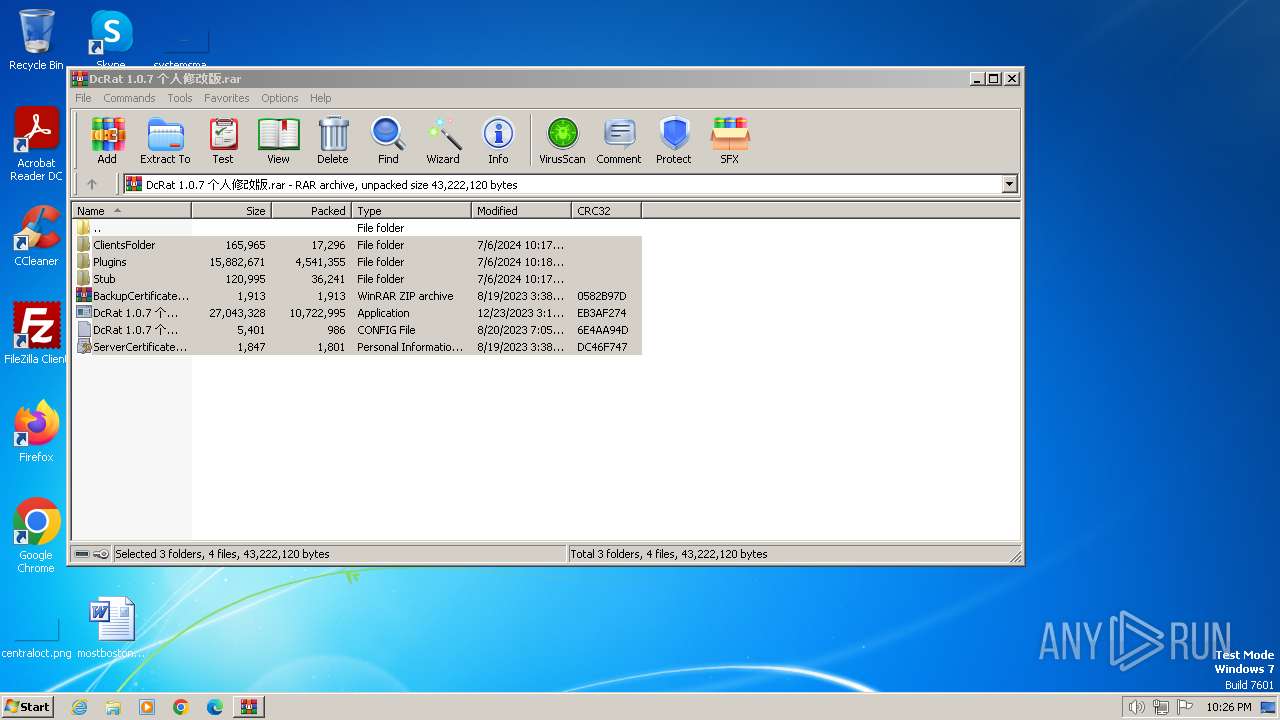
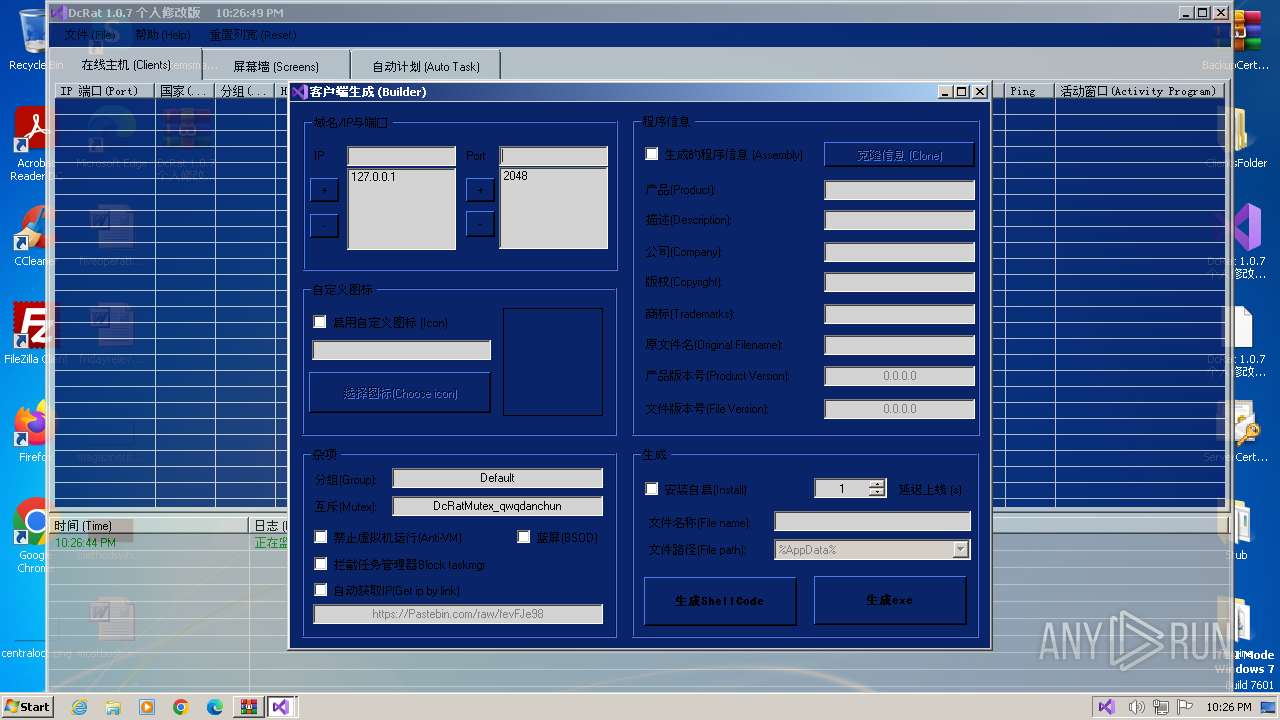
| File name: | DcRat 1.0.7 个人修改版.rar |
| Full analysis: | https://app.any.run/tasks/fcd2b171-8488-4eb9-b289-d4bfcf0175f9 |
| Verdict: | Malicious activity |
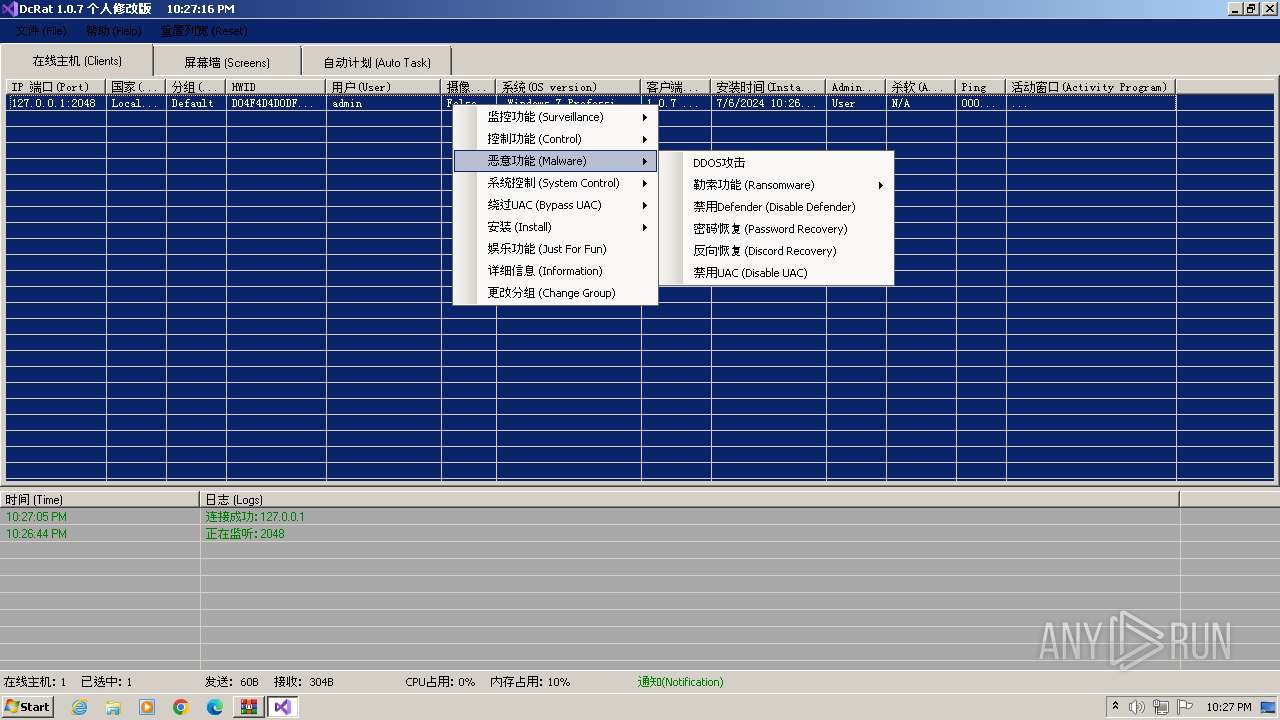
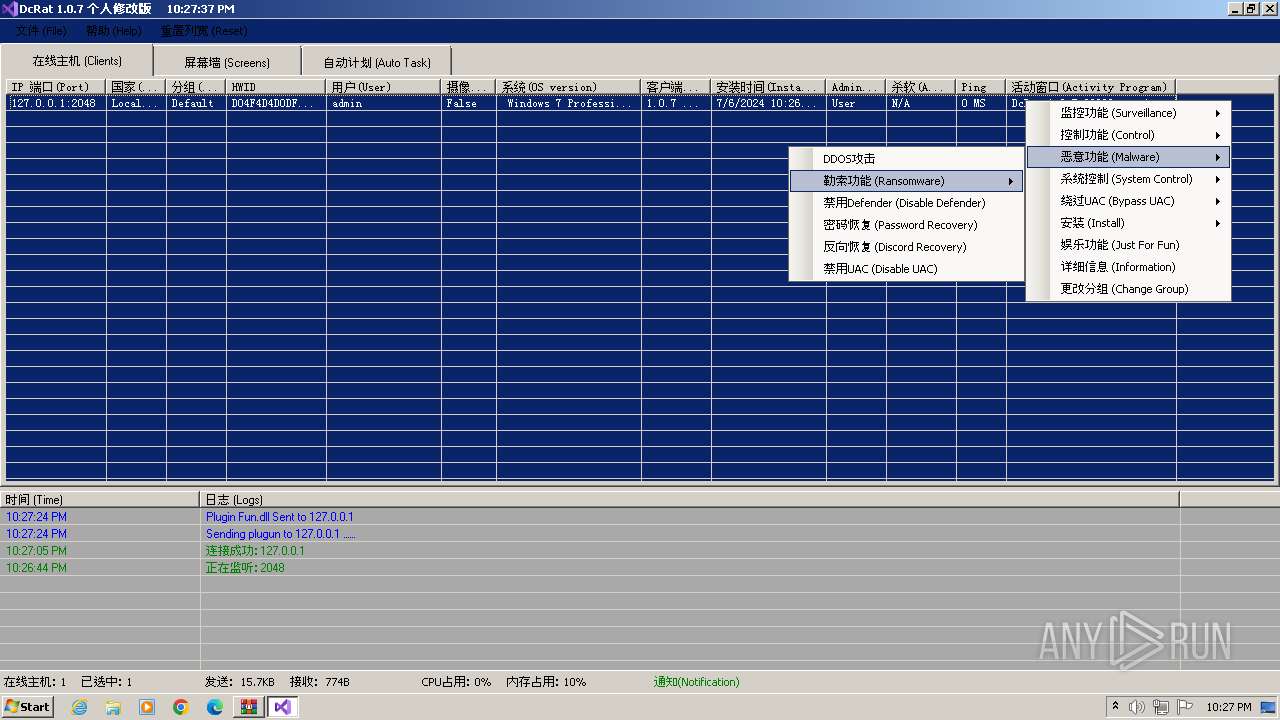
| Threats: | AsyncRAT is a RAT that can monitor and remotely control infected systems. This malware was introduced on Github as a legitimate open-source remote administration software, but hackers use it for its many powerful malicious functions. |
| Analysis date: | July 06, 2024, 21:26:04 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v5 |
| MD5: | 7976A102F3F13170096A83FBE5F86DAB |
| SHA1: | EE6942A430F8E89AF207393A25F4FDA103F988E5 |
| SHA256: | AB6711F82F53F14AB98577F70941B104267FBC06F401A06A4504C5A5B409A973 |
| SSDEEP: | 196608:oZoVA8JB73SKhdsf9DJPNYBES0ETupbeno:oZP8JBeKhk9JPWF0Eno |
MALICIOUS
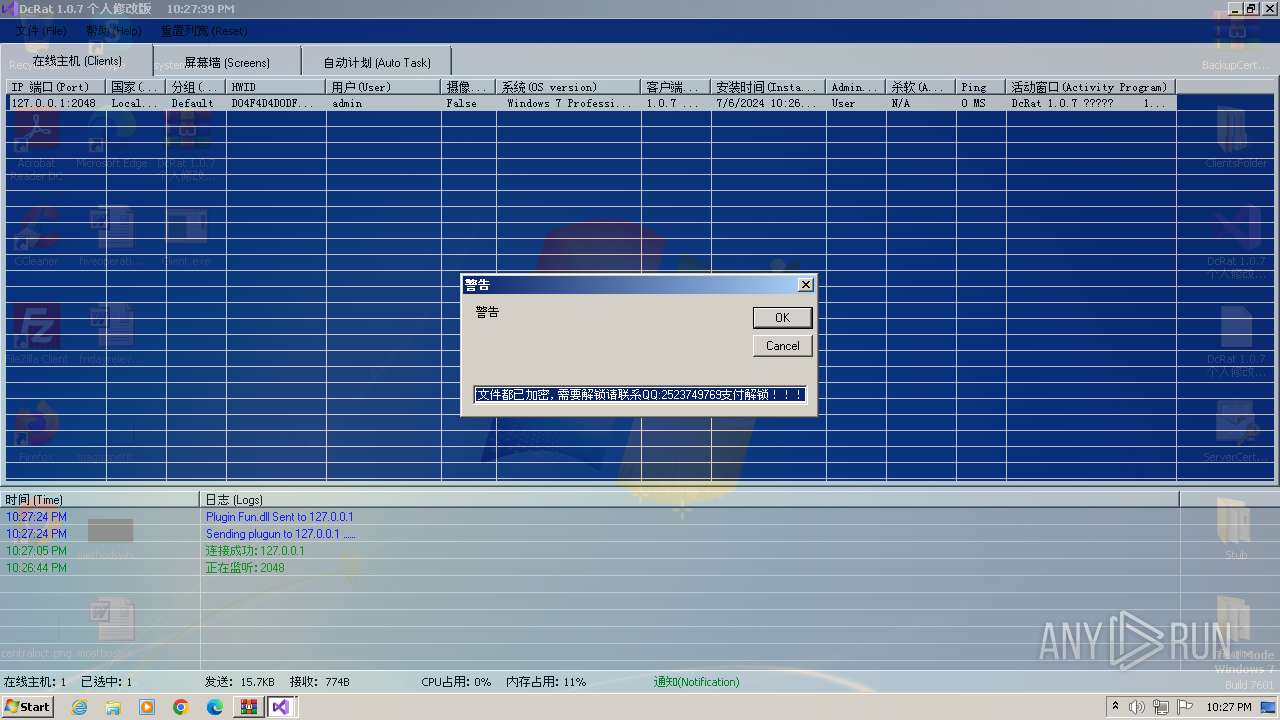
Actions looks like stealing of personal data
- WinRAR.exe (PID: 3344)
- DcRat 1.0.7 个人修改版.exe (PID: 540)
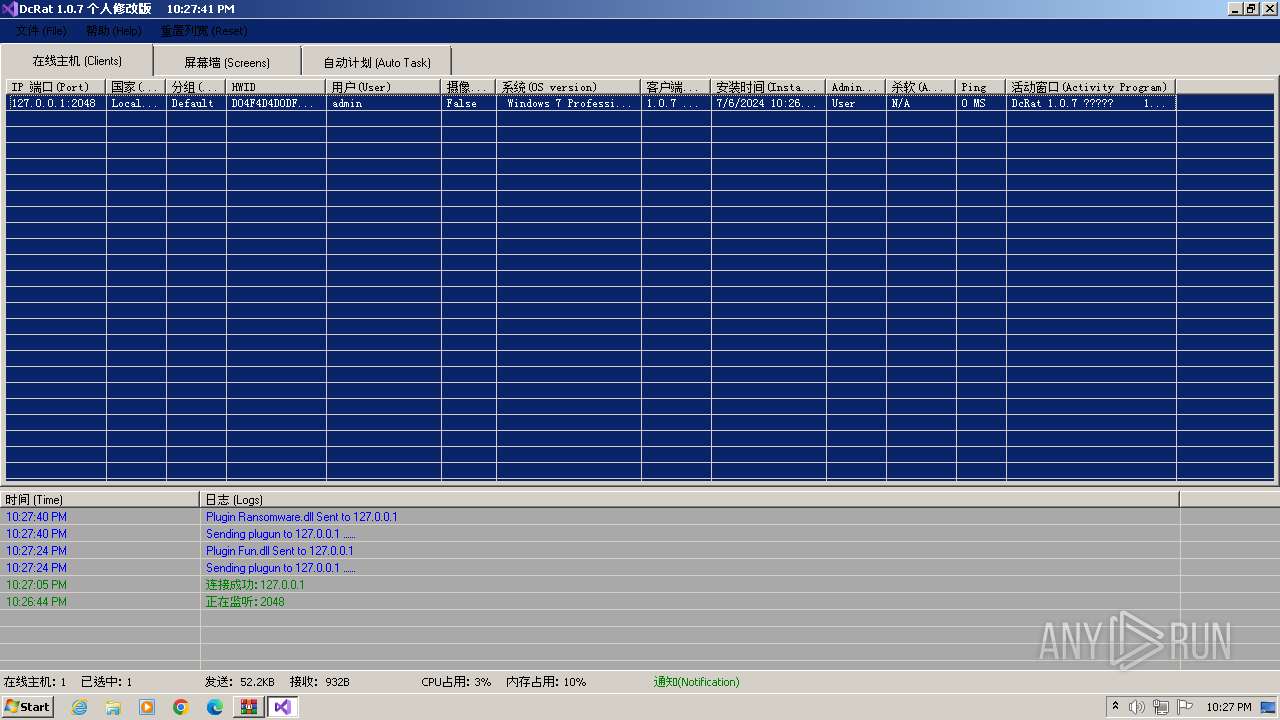
Drops the executable file immediately after the start
- WinRAR.exe (PID: 3344)
- DcRat 1.0.7 个人修改版.exe (PID: 540)
ASYNCRAT has been detected (YARA)
- DcRat 1.0.7 个人修改版.exe (PID: 540)
- Client.exe (PID: 3672)
LimeRAT is detected
- Client.exe (PID: 3672)
SUSPICIOUS
The process creates files with name similar to system file names
- WinRAR.exe (PID: 3344)
Reads the Internet Settings
- DcRat 1.0.7 个人修改版.exe (PID: 540)
Reads security settings of Internet Explorer
- DcRat 1.0.7 个人修改版.exe (PID: 540)
Executable content was dropped or overwritten
- DcRat 1.0.7 个人修改版.exe (PID: 540)
Reads settings of System Certificates
- Client.exe (PID: 3672)
INFO
Executable content was dropped or overwritten
- WinRAR.exe (PID: 3344)
Checks supported languages
- DcRat 1.0.7 个人修改版.exe (PID: 540)
- Client.exe (PID: 3672)
Reads the computer name
- DcRat 1.0.7 个人修改版.exe (PID: 540)
- Client.exe (PID: 3672)
Reads the machine GUID from the registry
- DcRat 1.0.7 个人修改版.exe (PID: 540)
- Client.exe (PID: 3672)
Reads Microsoft Office registry keys
- DcRat 1.0.7 个人修改版.exe (PID: 540)
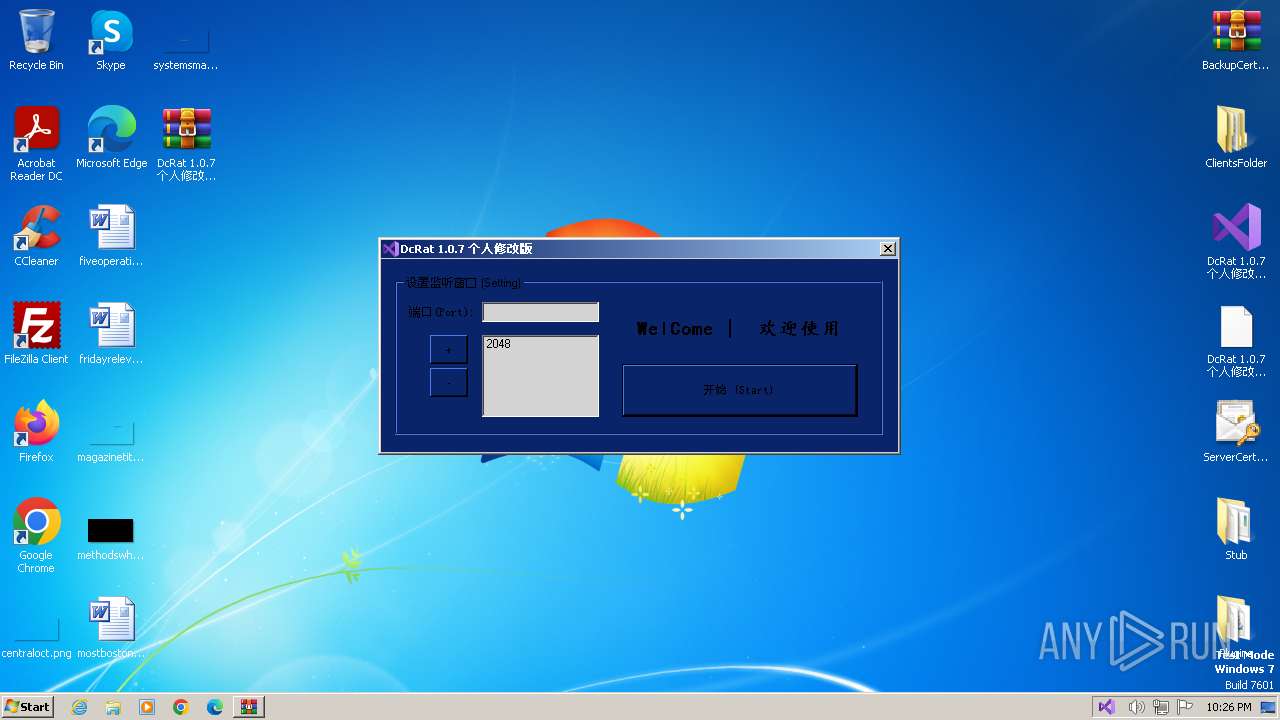
Manual execution by a user
- DcRat 1.0.7 个人修改版.exe (PID: 540)
- Client.exe (PID: 3672)
Reads Environment values
- DcRat 1.0.7 个人修改版.exe (PID: 540)
- Client.exe (PID: 3672)
Creates files or folders in the user directory
- DcRat 1.0.7 个人修改版.exe (PID: 540)
Reads the software policy settings
- Client.exe (PID: 3672)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
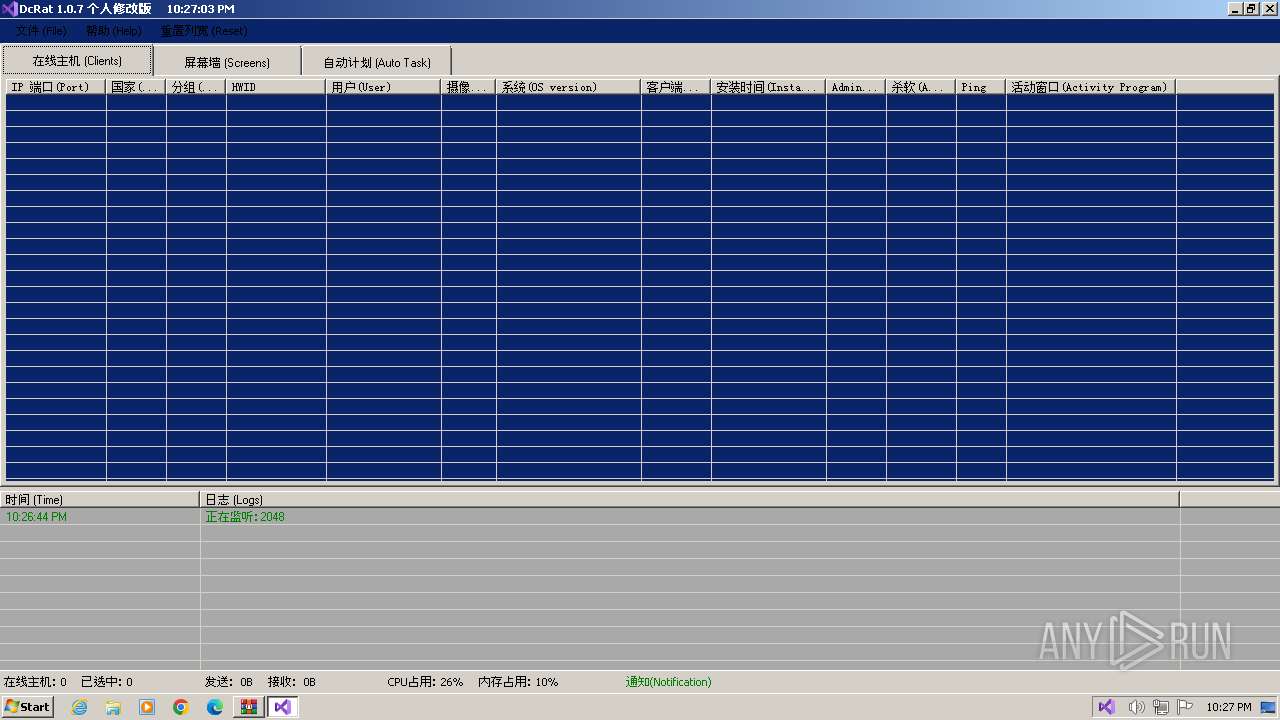
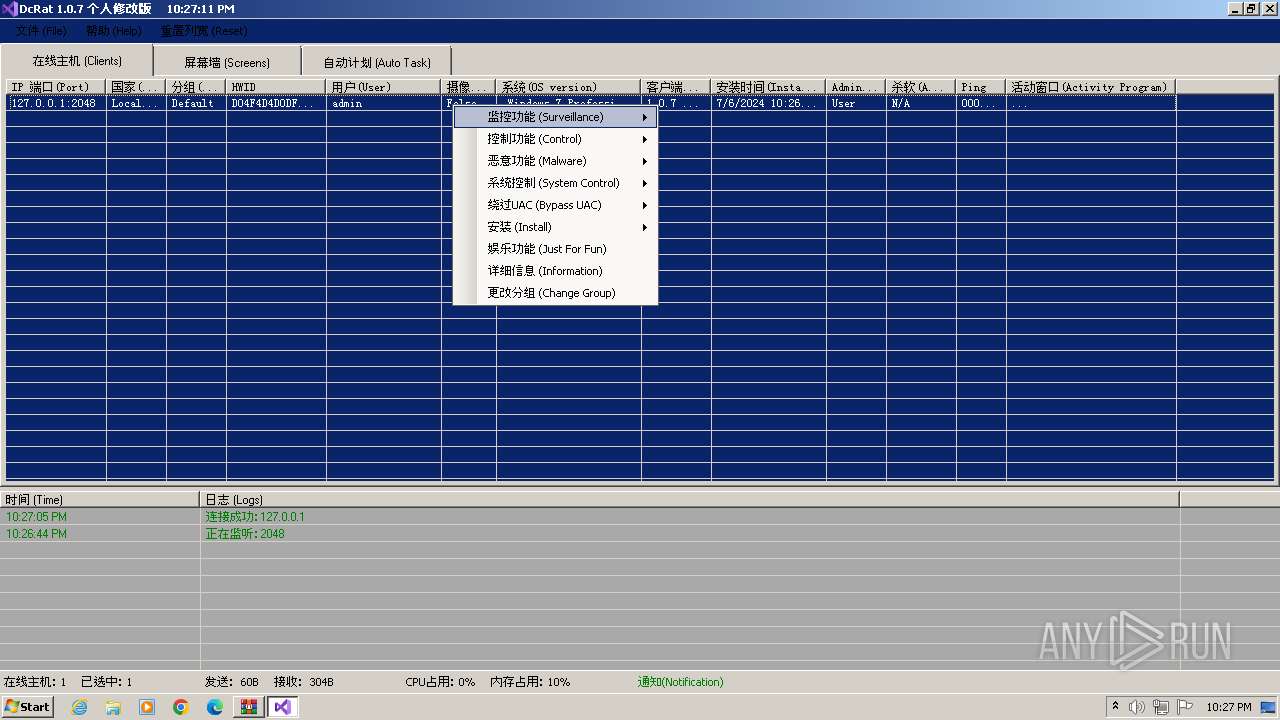
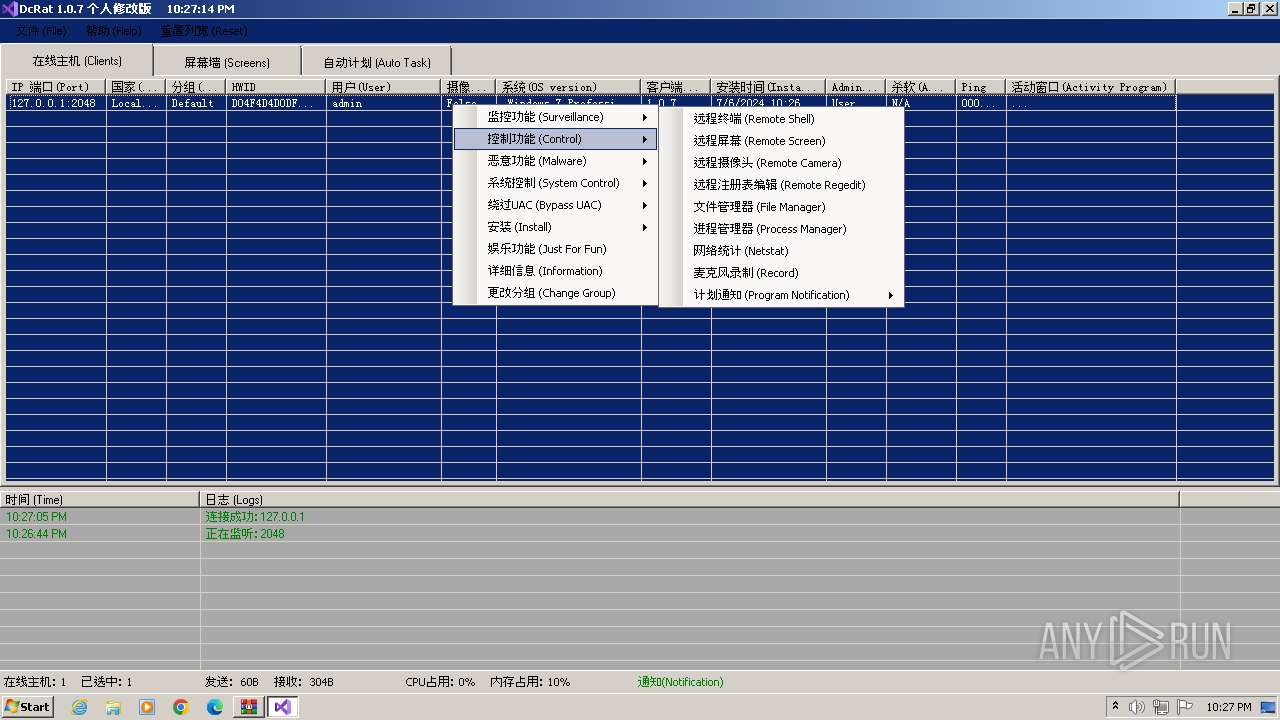
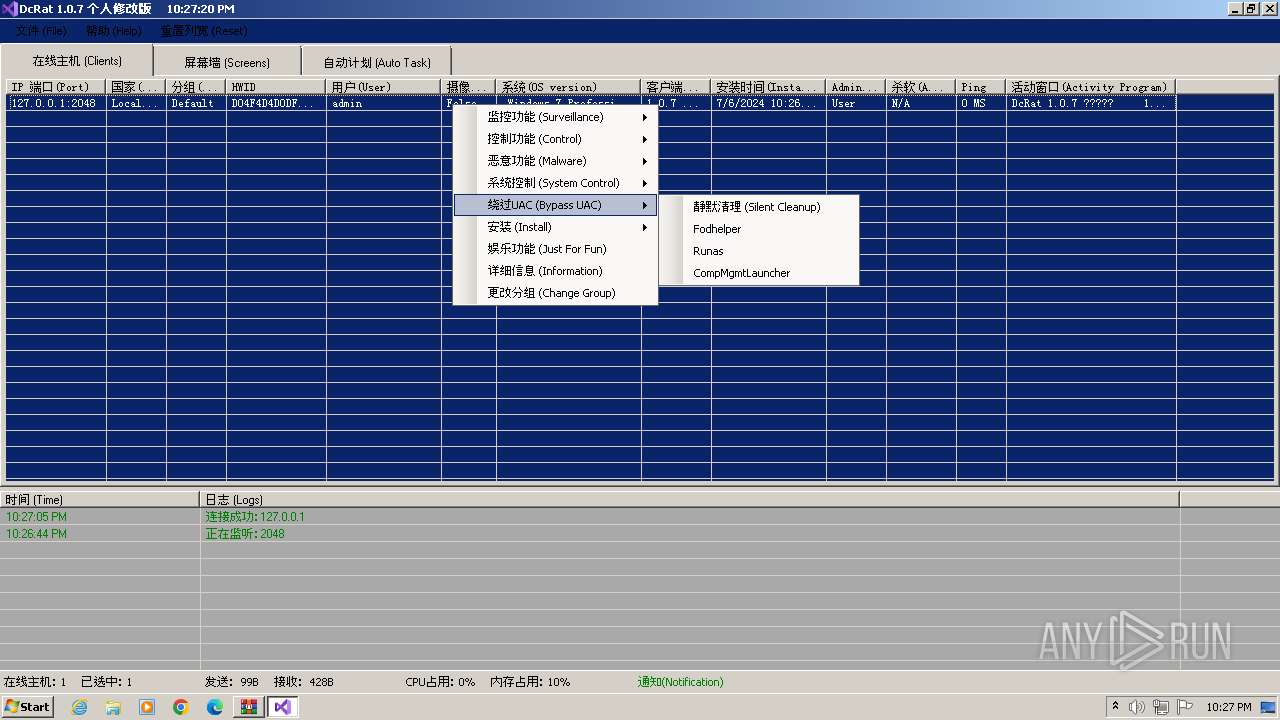
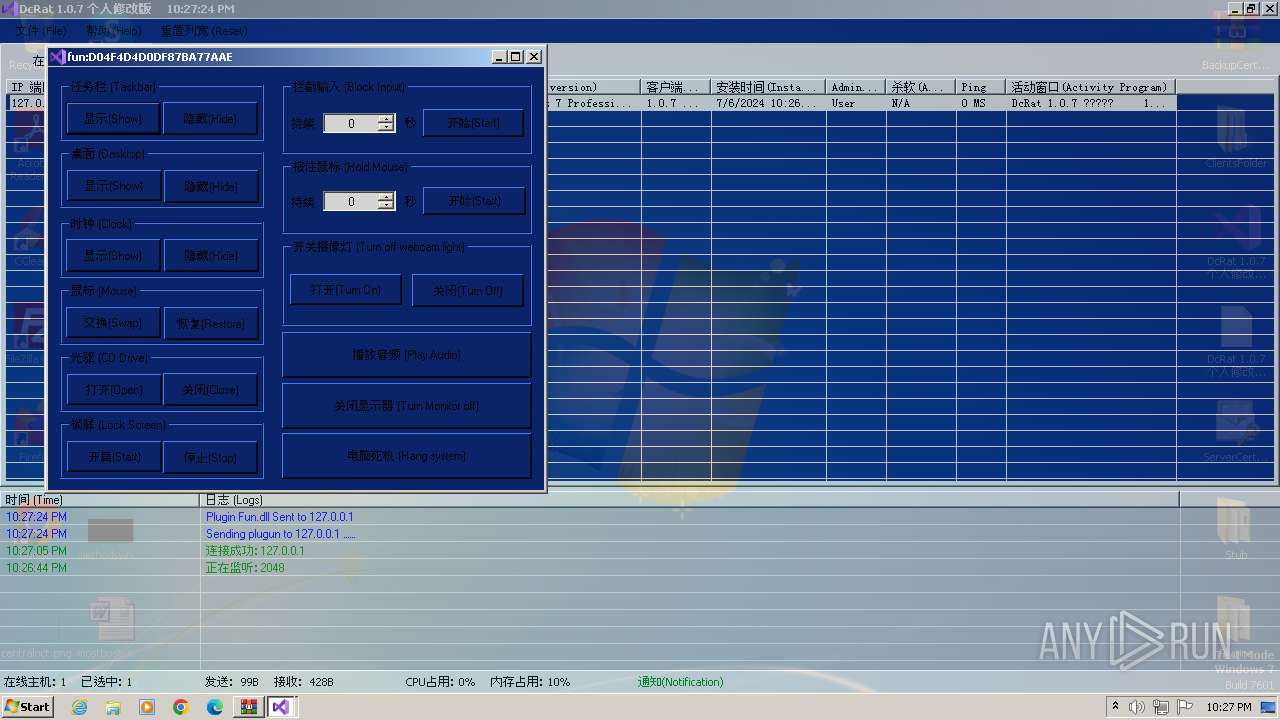
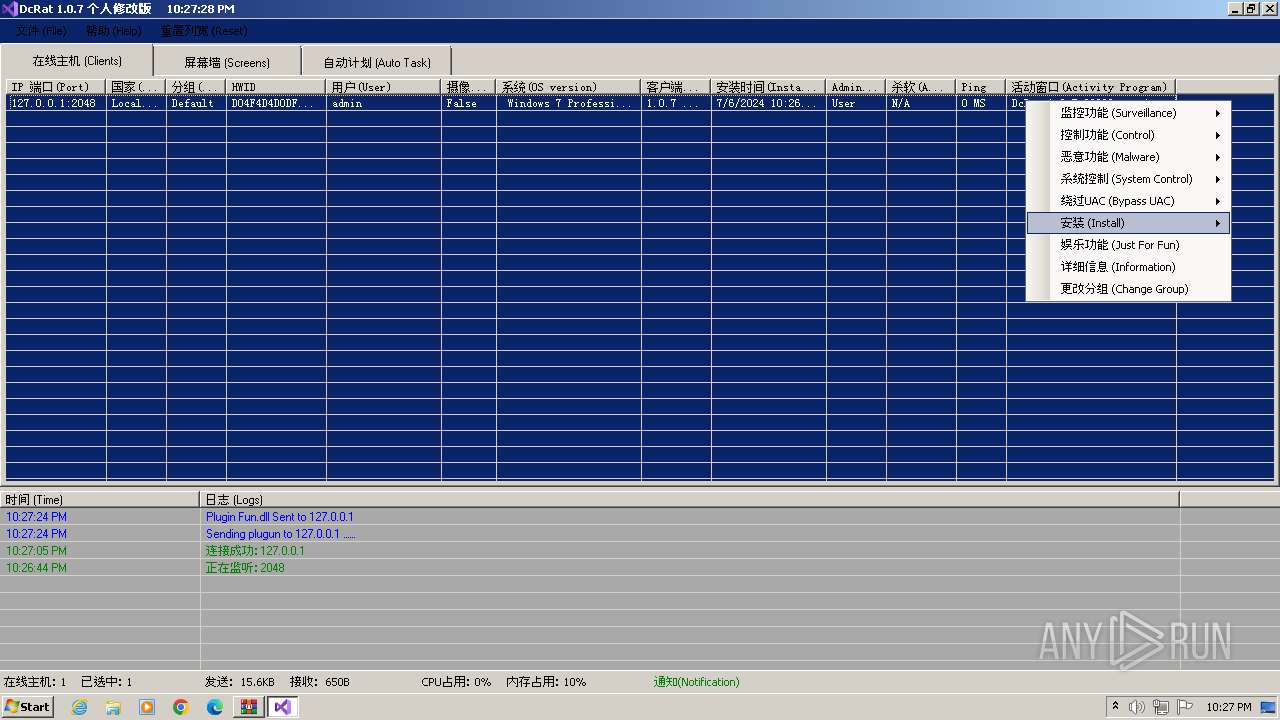
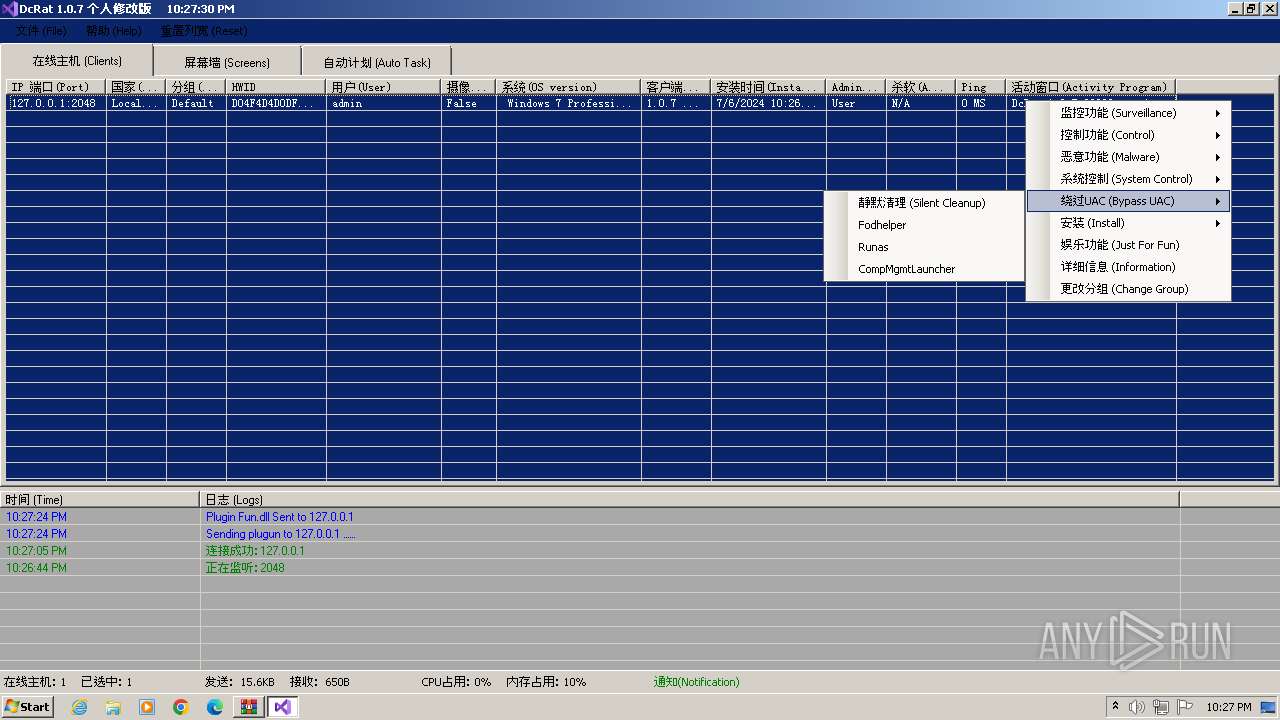
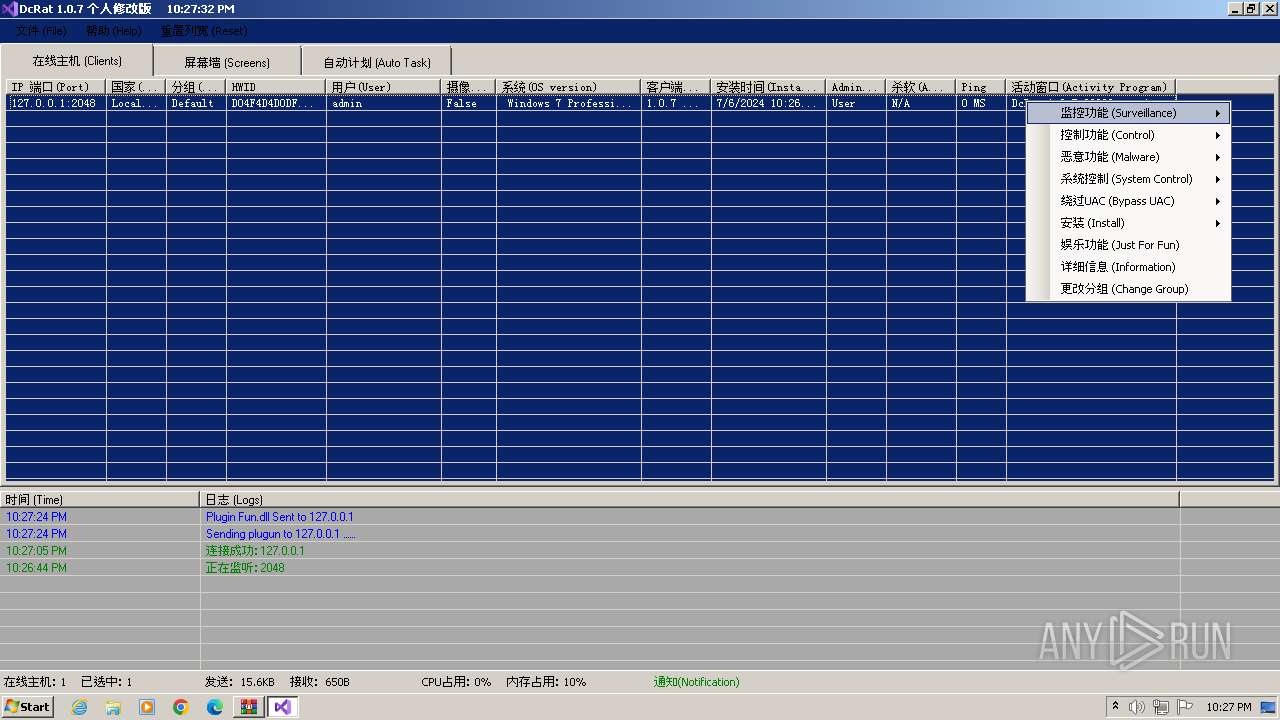
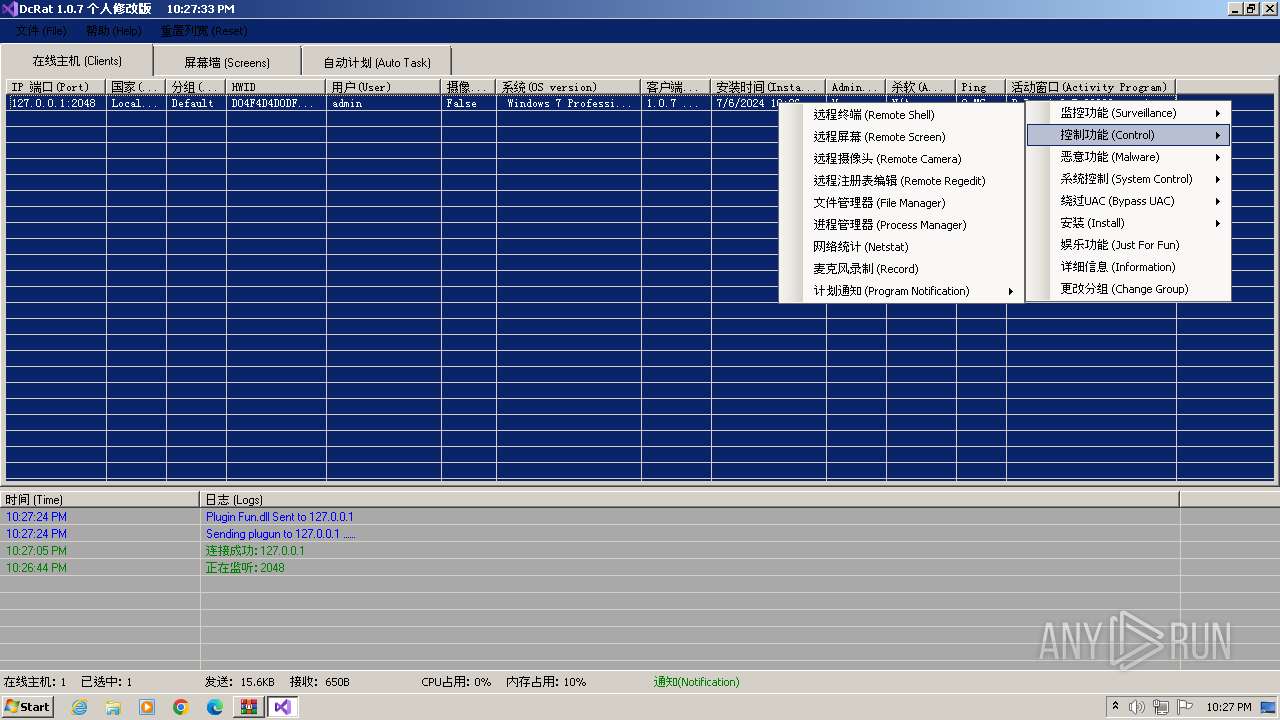
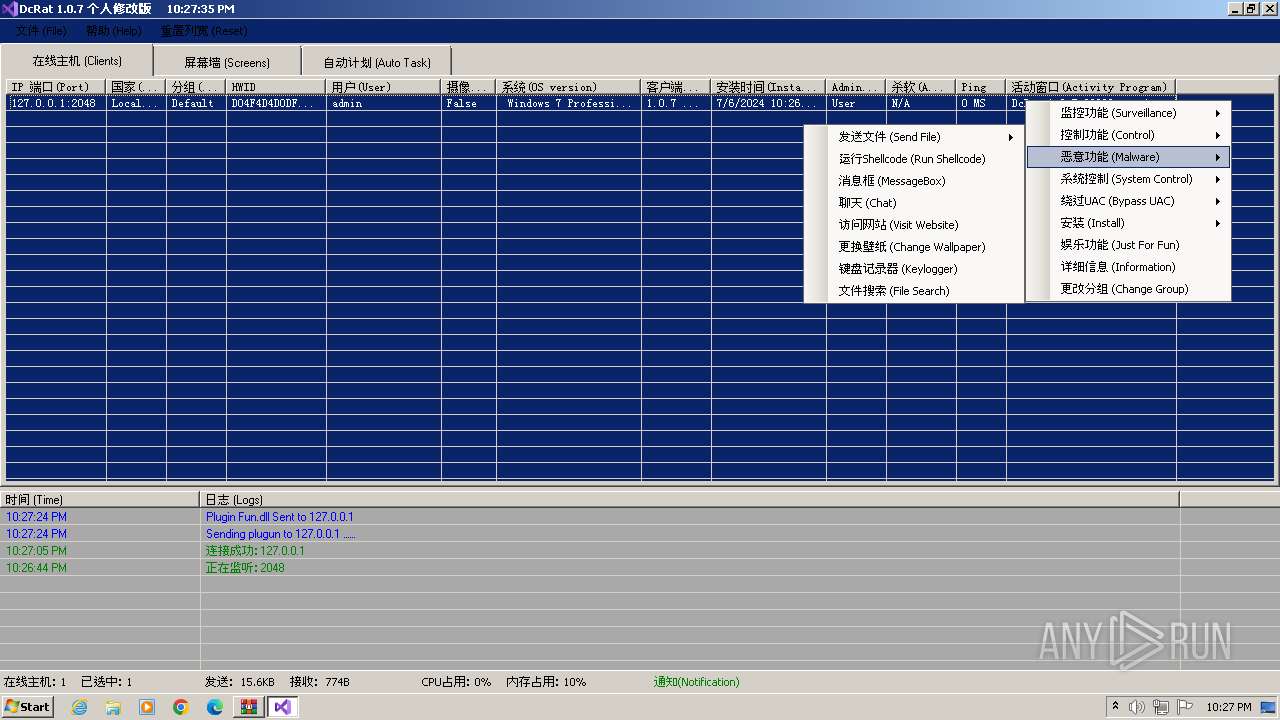
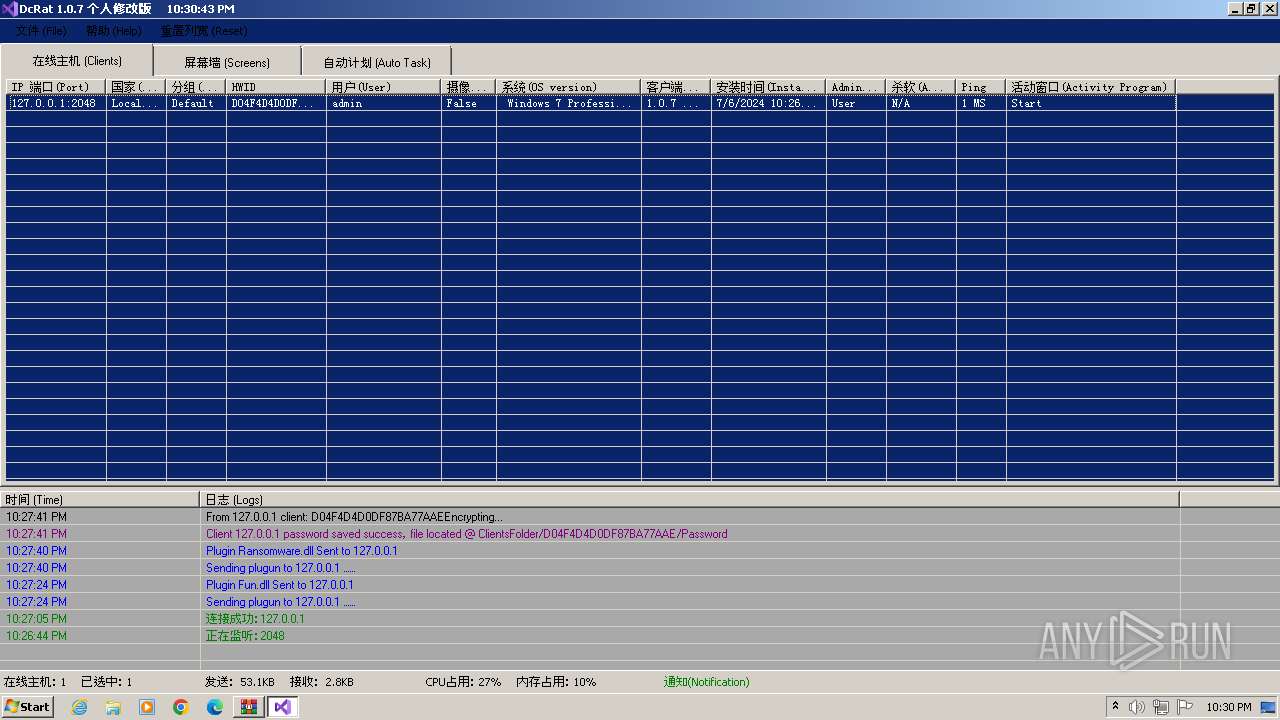
AsyncRat
(PID) Process(3672) Client.exe
C2 (1)127.0.0.1
Ports (1)2048
Version1.0.7 个人修改版
Options
AutoRunfalse
MutexDcRatMutex_qwqdanchun
InstallFolder%AppData%
Certificates
Cert1MIICVzCCAcCgAwIBAgIVALY1OZ5x62bQr7lmG9mvM+4XD+N7MA0GCSqGSIb3DQEBDQUAMH4xJDAiBgNVBAMMG0RjUmF0IDEuMC43IOS4quS6uuS/ruaUueeJiDEbMBkGA1UECwwSQm9iJ3MgQ29uc3RydWN0aW9uMR8wHQYDVQQKDBZCb2IncyBDb25zdHJ1Y3Rpb24gTExDMQswCQYDVQQHDAJOVjELMAkGA1UEBhMCVVMwHhcNMjIxMTA3MTQzODM4WhcNMzMwODE2MTQzODM4WjAdMRswGQYDVQQDDBJC...
Server_SignaturevavuWj7rwnKcXOQSYxydY8Uhjgtl55+jnwTI1ZZvd/jq+fPaNddZ16QfP8MdGyvU46wcReqhxo+sraMgF9lWlAuypVDrFZYzMXZgxYliskRkTGSKDHAy4orCac6BbYdJ7R0giPPEcQKlzXkXkdAScpoE/JWaOQD4pNPsx5LQ01g=
Keys
AES5b07bd913a3d9acfdbdba7af716e6da8de55e0278dfbc9c474eb5b8606c80ea7
SaltQ3JlYXRlZEJ5aWNlLXd6bC4u
TRiD
| .rar | | | RAR compressed archive (v5.0) (61.5) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (38.4) |
Total processes
45
Monitored processes
3
Malicious processes
3
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 540 | "C:\Users\admin\Desktop\DcRat 1.0.7 个人修改版.exe" | C:\Users\admin\Desktop\DcRat 1.0.7 个人修改版.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Description: DcRat 1.0.7 个人修改版 Version: 1.0.7.0 Modules
| |||||||||||||||
| 3344 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\Desktop\DcRat 1.0.7 个人修改版.rar" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
| 3672 | "C:\Users\admin\Desktop\Client.exe" | C:\Users\admin\Desktop\Client.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Version: 1.0.7.0 Modules
AsyncRat(PID) Process(3672) Client.exe C2 (1)127.0.0.1 Ports (1)2048 Version1.0.7 个人修改版 Options AutoRunfalse MutexDcRatMutex_qwqdanchun InstallFolder%AppData% Certificates Cert1MIICVzCCAcCgAwIBAgIVALY1OZ5x62bQr7lmG9mvM+4XD+N7MA0GCSqGSIb3DQEBDQUAMH4xJDAiBgNVBAMMG0RjUmF0IDEuMC43IOS4quS6uuS/ruaUueeJiDEbMBkGA1UECwwSQm9iJ3MgQ29uc3RydWN0aW9uMR8wHQYDVQQKDBZCb2IncyBDb25zdHJ1Y3Rpb24gTExDMQswCQYDVQQHDAJOVjELMAkGA1UEBhMCVVMwHhcNMjIxMTA3MTQzODM4WhcNMzMwODE2MTQzODM4WjAdMRswGQYDVQQDDBJC... Server_SignaturevavuWj7rwnKcXOQSYxydY8Uhjgtl55+jnwTI1ZZvd/jq+fPaNddZ16QfP8MdGyvU46wcReqhxo+sraMgF9lWlAuypVDrFZYzMXZgxYliskRkTGSKDHAy4orCac6BbYdJ7R0giPPEcQKlzXkXkdAScpoE/JWaOQD4pNPsx5LQ01g= Keys AES5b07bd913a3d9acfdbdba7af716e6da8de55e0278dfbc9c474eb5b8606c80ea7 SaltQ3JlYXRlZEJ5aWNlLXd6bC4u | |||||||||||||||
Total events
17 106
Read events
17 000
Write events
100
Delete events
6
Modification events
| (PID) Process: | (3344) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (3344) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (3344) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3344) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\phacker.zip | |||
| (PID) Process: | (3344) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (3344) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\curl-8.5.0_1-win32-mingw.zip | |||
| (PID) Process: | (3344) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\DcRat 1.0.7 个人修改版.rar | |||
| (PID) Process: | (3344) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3344) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3344) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
Executable files
26
Suspicious files
448
Text files
9
Unknown types
19
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3344 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3344.268\Plugins\ip2region.db | — | |
MD5:— | SHA256:— | |||
| 3344 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3344.268\Plugins\Audio.pdb | pdb | |
MD5:4394D071ECDFB1574BC41301441166E0 | SHA256:4A68A2545DD48F66F0D024E2057288F53A8CACAA1516331AA811AE2BA06D8DA3 | |||
| 3344 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3344.268\Plugins\Audio.dll | executable | |
MD5:BE913C2282654CE9A706B9201B06BD38 | SHA256:536A21082AAD83A89E0E937F949C06086EB9D4570C0834C606AD1662E30EB15C | |||
| 3344 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3344.268\Plugins\Extra.pdb | pdb | |
MD5:B60C4B08E1E7720350DE99FE52575F59 | SHA256:03E6BE2E97D6A6E700DBCA1A7451644039A5C59A023827F00046D9B69D38E1E5 | |||
| 3344 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3344.268\Plugins\Extra.dll | executable | |
MD5:AACFD5D2AE2E725972100FF9A1EE8C1C | SHA256:263405A794EFDFBF8E8555B502B6FC02ED4AA0721AF12D34CDB9424D3311BDE1 | |||
| 3344 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3344.268\Plugins\FileManager.dll | executable | |
MD5:657A7D8AE378EF31662A6DA97D1F46B3 | SHA256:DA969B6965E388F1C6884D8616BA31837A6FA4953362AE288B95737C1DD5A96D | |||
| 3344 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3344.268\ClientsFolder\D050D116CBC42AACA698\Information\Information.txt | text | |
MD5:B85CAEB7CA06F4798ABC35B8416E207F | SHA256:A5197546EEE284146BD7DB651638FBC7A6996AD6B66E2012099B512097B5F494 | |||
| 3344 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3344.268\Plugins\Chat.pdb | pdb | |
MD5:CA9F0650BC2572552AF6B50AF1D6154B | SHA256:AE69E27807E91358A925348E25EDAE04342AA0023764574C043C8A1F4FF75D18 | |||
| 3344 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3344.268\Plugins\Discord.dll | executable | |
MD5:F395CFA16CD537FB9F2B93ECDD949D4C | SHA256:65099A26DCB5D1571BD35E05186BA5FC8DAC35795F59F00B085B55BAADAE6AB2 | |||
| 3344 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3344.268\Plugins\Chat.dll | executable | |
MD5:1B0C856F3E251B6D549A8B328CC03198 | SHA256:12EF9587410553DF4A77C00D63871DA38D82AB33FCA58B39E96E7013193215F0 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
5
TCP/UDP connections
13
DNS requests
5
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1372 | svchost.exe | GET | 304 | 23.50.131.206:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?33775f6043c93e33 | unknown | — | — | unknown |
1372 | svchost.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | unknown |
1060 | svchost.exe | GET | 304 | 199.232.210.172:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?a9f83325acc8ca75 | unknown | — | — | unknown |
480 | lsass.exe | GET | 200 | 199.232.210.172:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab?cfa3fea8103cb675 | unknown | — | — | unknown |
1372 | svchost.exe | GET | 200 | 23.48.23.166:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
1372 | svchost.exe | 51.124.78.146:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
2564 | svchost.exe | 239.255.255.250:3702 | — | — | — | whitelisted |
1060 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1372 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
1372 | svchost.exe | 23.50.131.206:80 | ctldl.windowsupdate.com | Akamai International B.V. | DE | unknown |
1372 | svchost.exe | 23.48.23.166:80 | crl.microsoft.com | Akamai International B.V. | DE | unknown |
1372 | svchost.exe | 23.35.229.160:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
1060 | svchost.exe | 199.232.210.172:80 | ctldl.windowsupdate.com | FASTLY | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
ctldl.windowsupdate.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |