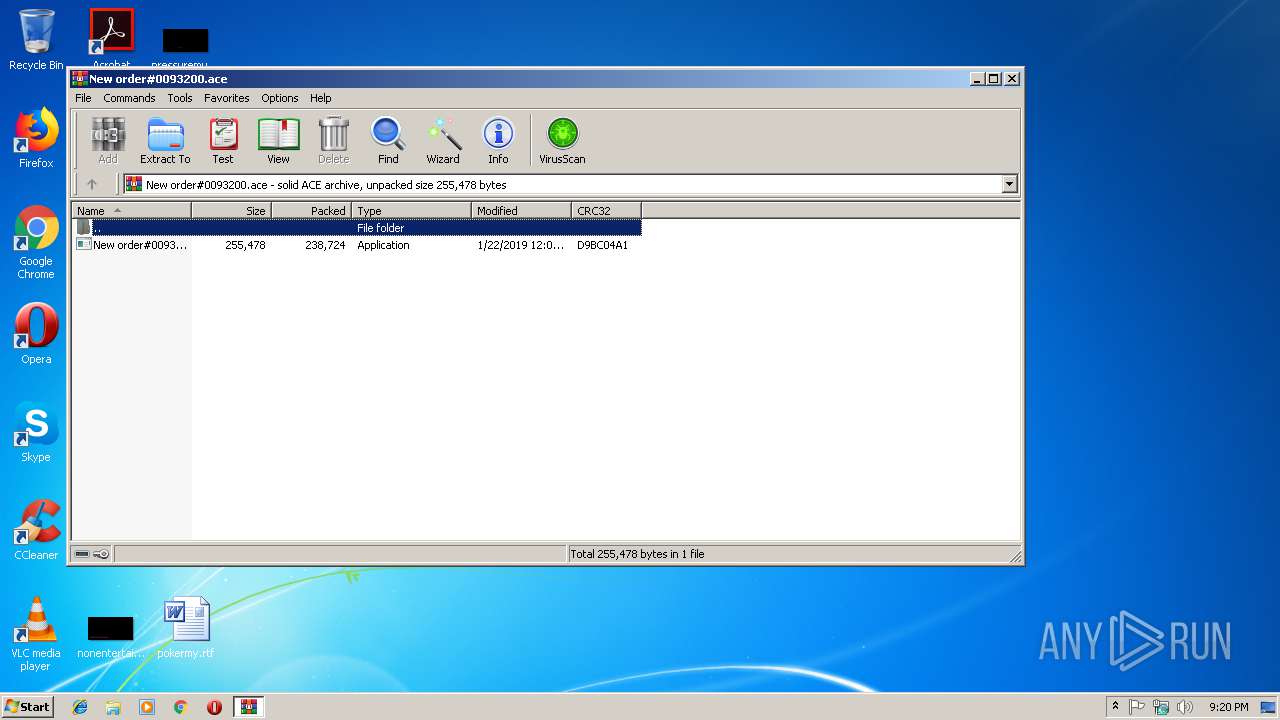
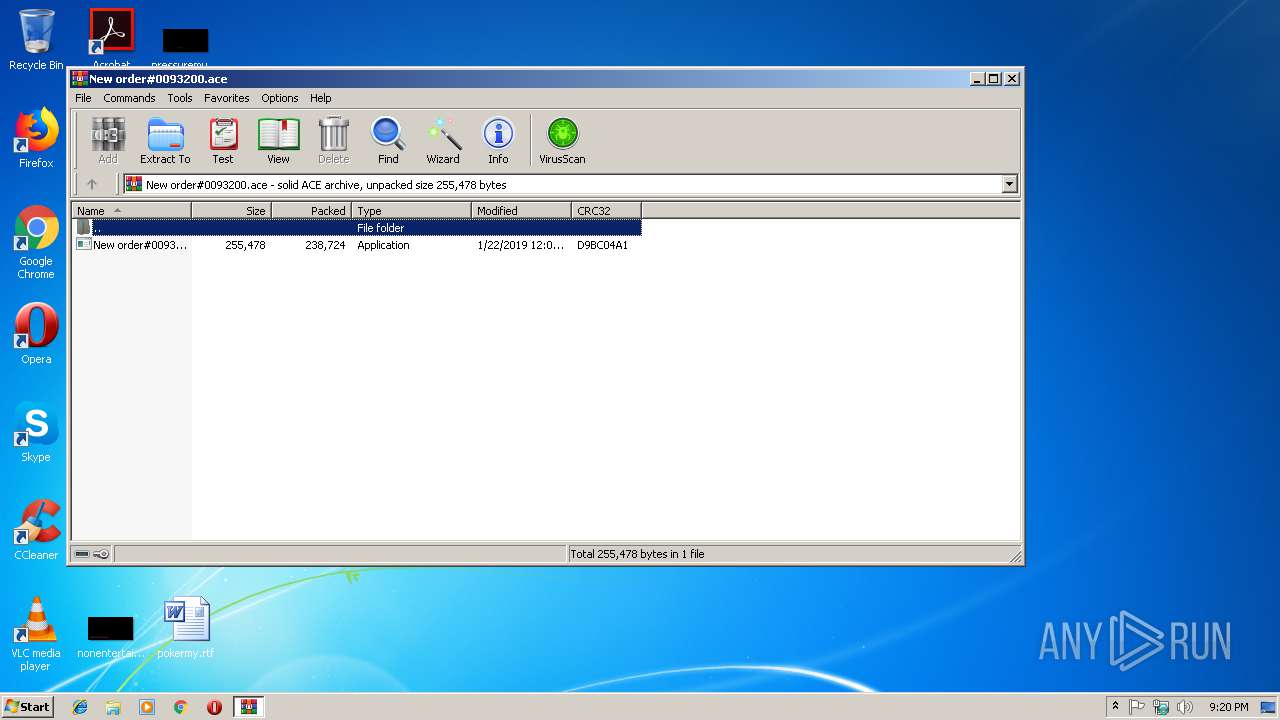
| File name: | New order#0093200.ace |
| Full analysis: | https://app.any.run/tasks/fbba09a6-f7dd-4660-be8c-2ec98c5f70ae |
| Verdict: | Malicious activity |
| Threats: | LokiBot was developed in 2015 to steal information from a variety of applications. Despite the age, this malware is still rather popular among cybercriminals. |
| Analysis date: | January 22, 2019, 21:19:37 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/octet-stream |
| File info: | ACE archive data version 20, from Win/32, version 20 to extract, solid |
| MD5: | 45F84A3212DAA421E66670F88508BCAD |
| SHA1: | F4C31BD3C22E1708C316586D940B608A5F6A3913 |
| SHA256: | AB49E35BF7B484958EA8104B3F348C160554824136C213539D22DB4DFC400A11 |
| SSDEEP: | 6144:H/uGFQnV8x9/Bi9hiLbdkRVFIB3SBISH/euMZ:H/udn4+RQBCBPGjZ |
MALICIOUS
Application was dropped or rewritten from another process
- New order#0093200.exe (PID: 2736)
Loads dropped or rewritten executable
- New order#0093200.exe (PID: 2736)
SUSPICIOUS
Executable content was dropped or overwritten
- New order#0093200.exe (PID: 2736)
- WinRAR.exe (PID: 2976)
INFO
No info indicators.
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .ace | | | ACE compressed archive (100) |
|---|
Total processes
31
Monitored processes
2
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2736 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa2976.847\New order#0093200.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa2976.847\New order#0093200.exe | WinRAR.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 2976 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\New order#0093200.ace" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
Total events
812
Read events
773
Write events
39
Delete events
0
Modification events
| (PID) Process: | (2976) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (2976) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (2976) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\5F\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2976) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\New order#0093200.ace | |||
| (PID) Process: | (2976) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (2976) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (2976) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (2976) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (2976) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\ACE Compression Software\ActiveAce\2.0 |
| Operation: | write | Name: | Count |
Value: 0 | |||
| (PID) Process: | (2976) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\ACE Compression Software\ActiveAce\2.0 |
| Operation: | write | Name: | Name |
Value: 542D4B42647265644B76737A7E794B566767537663764B5B7874767B4B43727A674B5972603778657372653427272E24252727397674721717171717171717171717171717171717171717171717171717171717171717171717171717171717171717171717171717171717171717171717171717171717171717171717171717171717171717171717171717171717171717171717171717171717171717171717171717171717171717171717171717171717171717171717171717171717171717171717171717171717171717171717171717171717171717171717171717171717171717171717171717171717171717171717171717171717171717171717171717171717171717171717171717171717171717171717171717171717171717171717171717171717171717171717171717171717171717171717171700 | |||
Executable files
2
Suspicious files
0
Text files
0
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
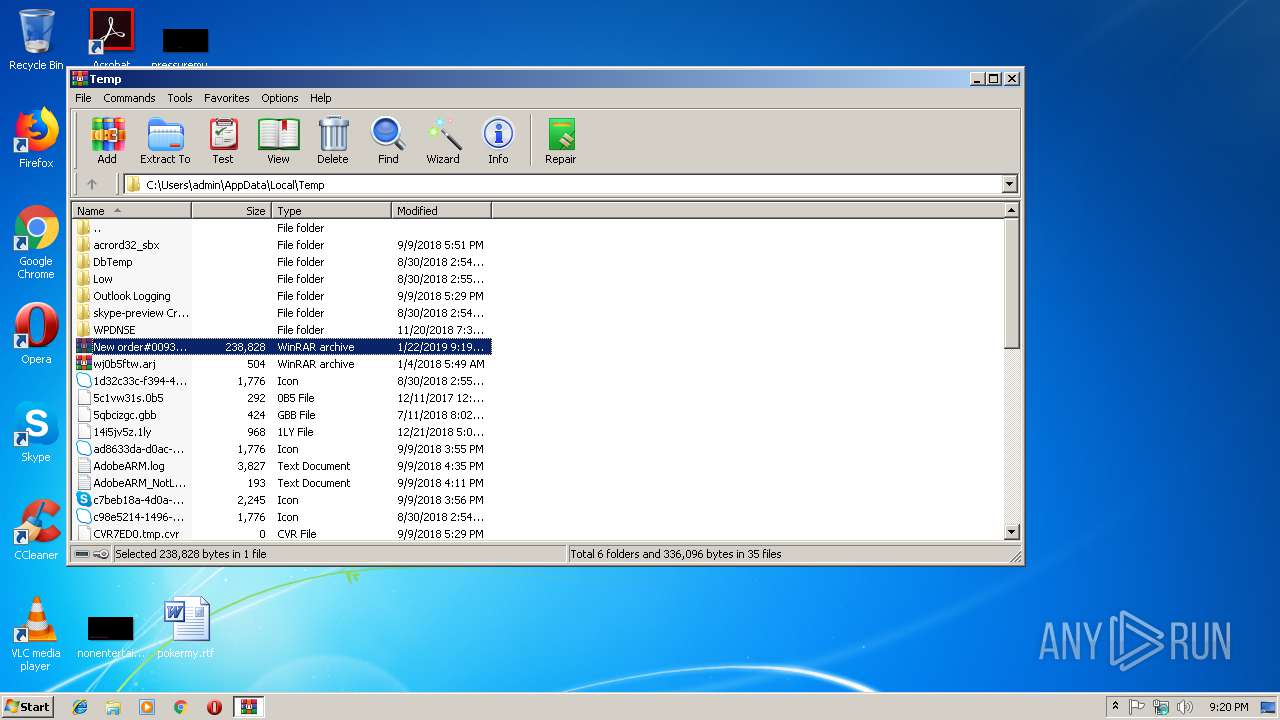
| 2976 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa2976.847\New order#0093200.exe | executable | |
MD5:— | SHA256:— | |||
| 2736 | New order#0093200.exe | C:\Users\admin\AppData\Local\Temp\nssA123.tmp\InstallOptions.dll | executable | |
MD5:8D5A5529462A9BA1AC068EE0502578C7 | SHA256:E625DCD0188594B1289891B64DEBDDEB5159ACA182B83A12675427B320BF7790 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
3
TCP/UDP connections
4
DNS requests
2
Threats
22
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | POST | 404 | 193.238.47.115:80 | http://ivytechbulk.com/atoz/encode.php | unknown | text | 15 b | malicious |
— | — | POST | 404 | 193.238.47.115:80 | http://ivytechbulk.com/atoz/encode.php | unknown | binary | 23 b | malicious |
— | — | POST | 404 | 193.238.47.115:80 | http://ivytechbulk.com/atoz/encode.php | unknown | binary | 23 b | malicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 193.238.47.115:80 | ivytechbulk.com | — | — | malicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
ivytechbulk.com |
| malicious |
Threats
PID | Process | Class | Message |
|---|---|---|---|
— | — | A Network Trojan was detected | ET TROJAN LokiBot User-Agent (Charon/Inferno) |
— | — | A Network Trojan was detected | ET TROJAN LokiBot Checkin |
— | — | A Network Trojan was detected | ET TROJAN LokiBot Application/Credential Data Exfiltration Detected M1 |
— | — | A Network Trojan was detected | ET TROJAN LokiBot Application/Credential Data Exfiltration Detected M2 |
— | — | A Network Trojan was detected | MALWARE [PTsecurity] Loki Bot Check-in M2 |
— | — | A Network Trojan was detected | ET TROJAN LokiBot User-Agent (Charon/Inferno) |
— | — | A Network Trojan was detected | ET TROJAN LokiBot Checkin |
— | — | A Network Trojan was detected | ET TROJAN LokiBot Application/Credential Data Exfiltration Detected M1 |
— | — | A Network Trojan was detected | ET TROJAN LokiBot Application/Credential Data Exfiltration Detected M2 |
— | — | A Network Trojan was detected | MALWARE [PTsecurity] Loki Bot Check-in M2 |