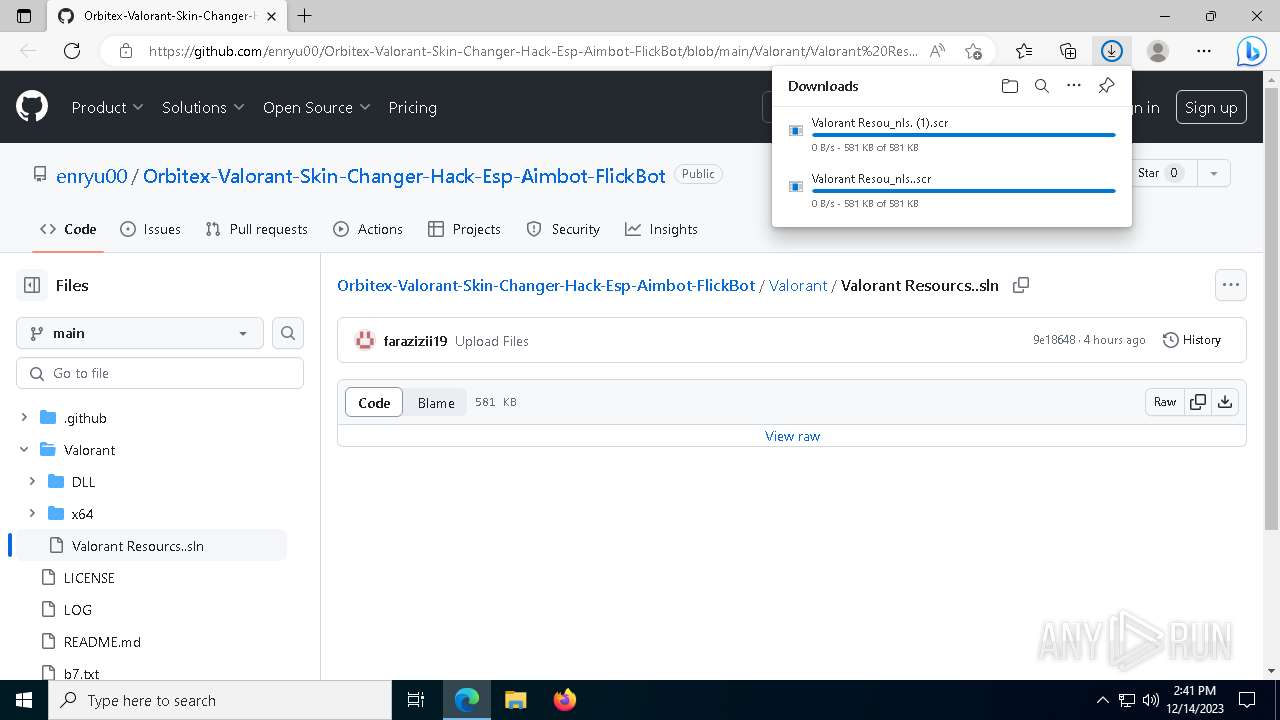
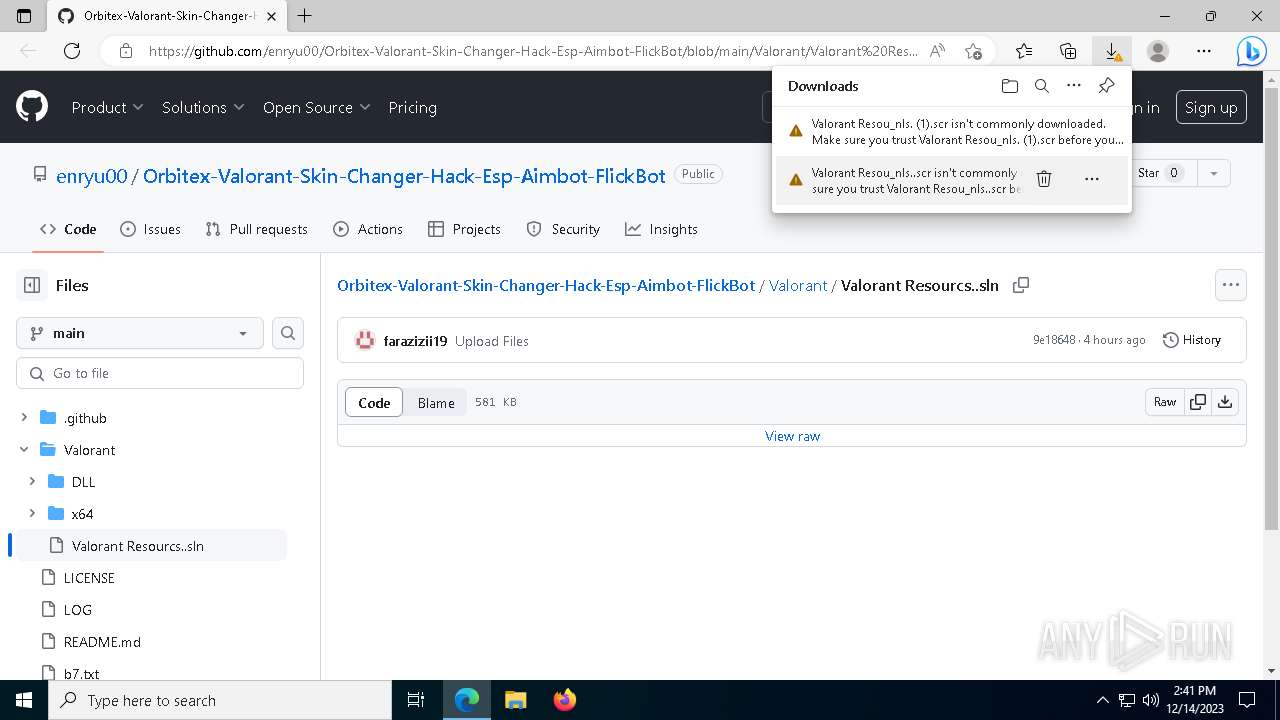
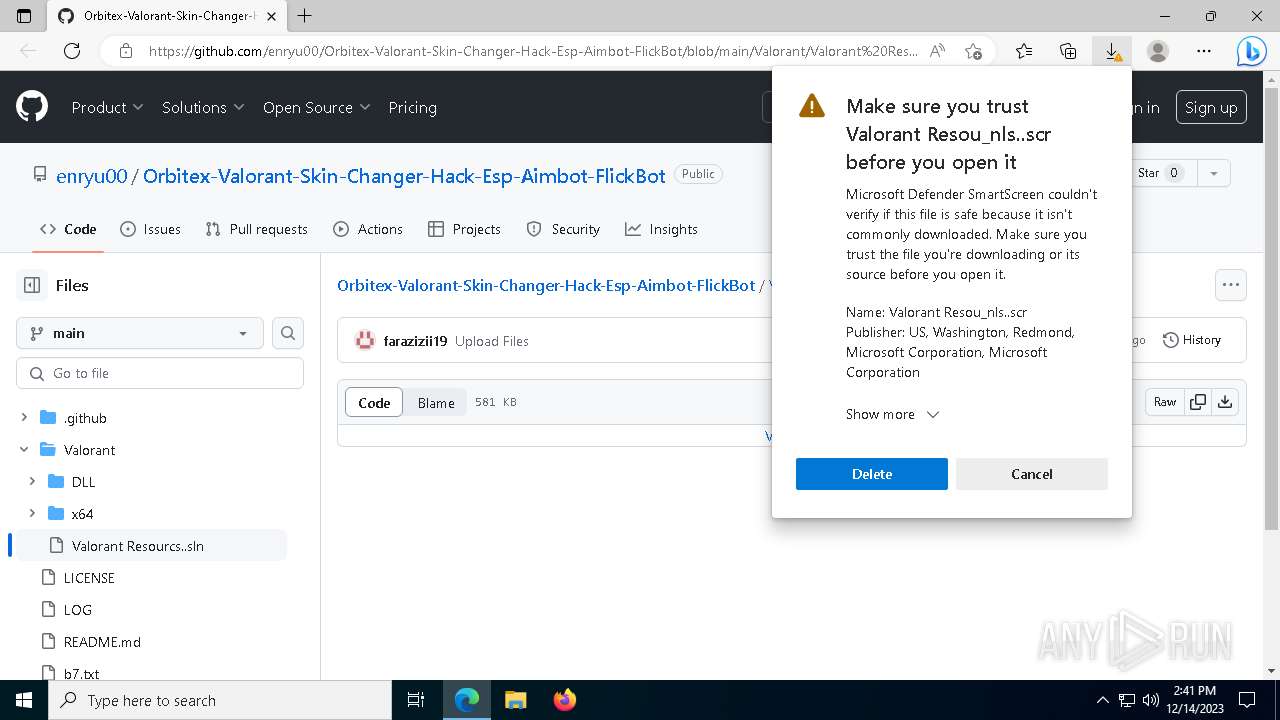
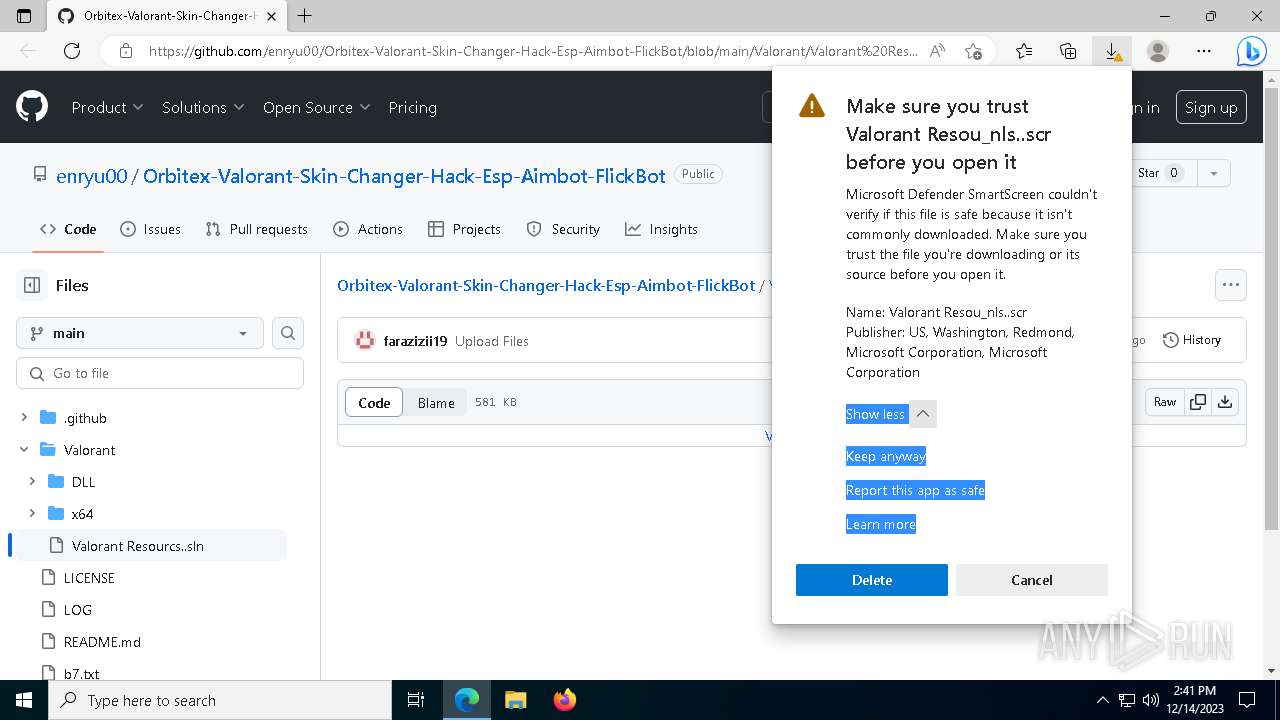
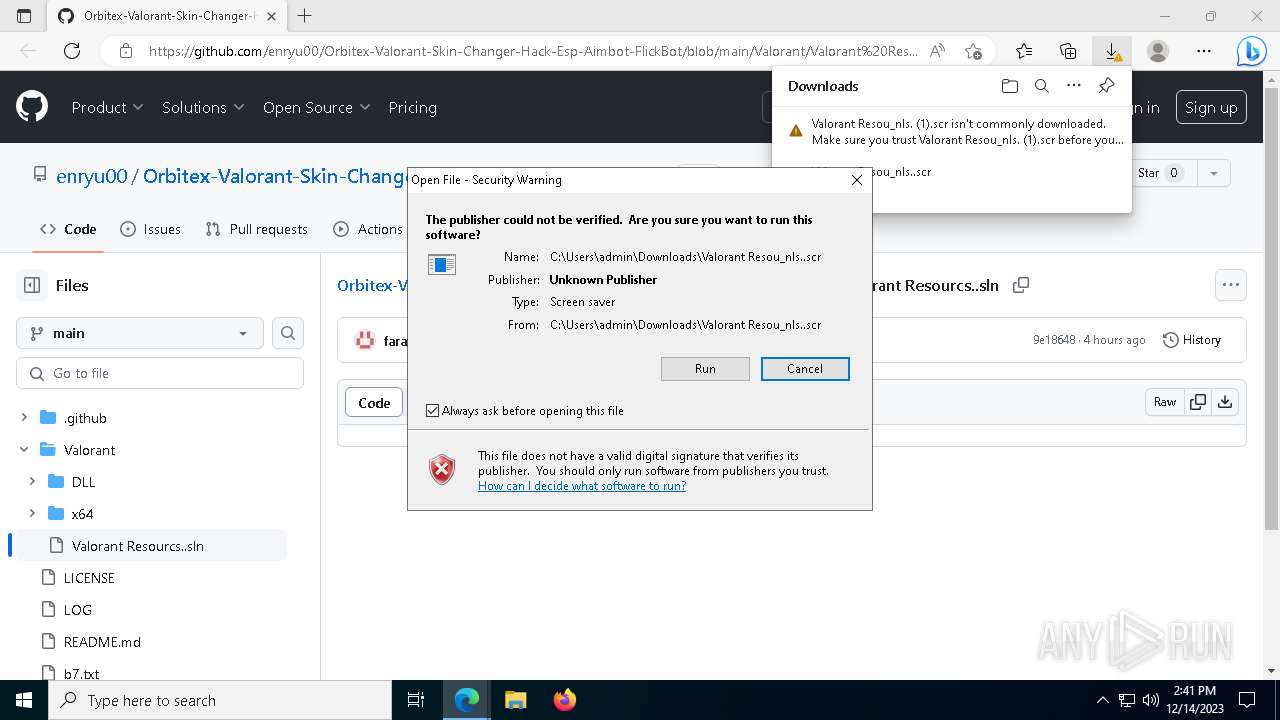
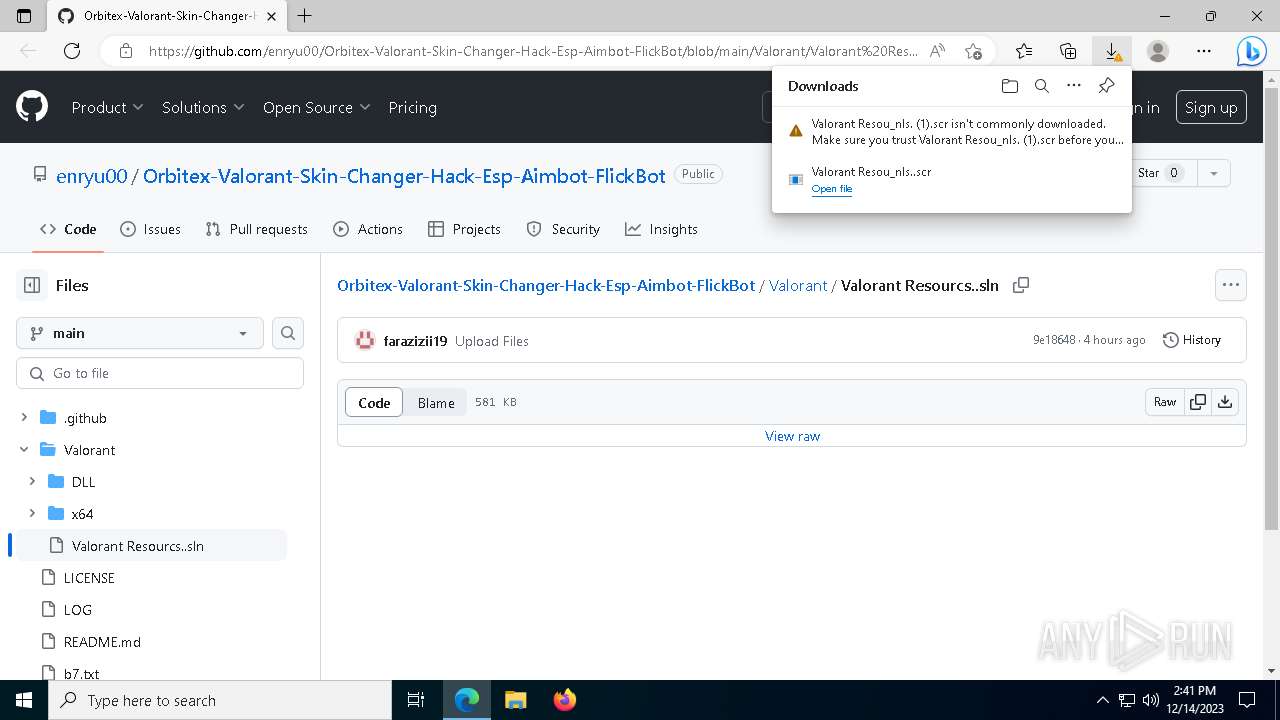
| URL: | https://github.com/enryu00/Orbitex-Valorant-Skin-Changer-Hack-Esp-Aimbot-FlickBot/blob/main/Valorant/Valorant%20Resou%E2%80%AEnls..scr |
| Full analysis: | https://app.any.run/tasks/52e77c50-56d3-44e7-9c6c-d497b854fef8 |
| Verdict: | Malicious activity |
| Threats: | AsyncRAT is a RAT that can monitor and remotely control infected systems. This malware was introduced on Github as a legitimate open-source remote administration software, but hackers use it for its many powerful malicious functions. |
| Analysis date: | December 14, 2023, 14:41:21 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MD5: | 6933F7AC0B7E3FAF7B07520ADBFFBB35 |
| SHA1: | D53B59DBEF2946F7EC358B9E85D56100C36342AA |
| SHA256: | AB009B279C2A59B19488E1AA35263EA42100A77771537B6C9198B08B080197B0 |
| SSDEEP: | 3:N8tEdwgQ/KVA6i86ELDbqMIHTjFFHKIERTXy6iyV0zQkD:2umgQ/Oxv7+THTsTXlrV0zQa |
MALICIOUS
Drops the executable file immediately after the start
- Valorant Resou_nls..scr (PID: 7920)
- b8023kjlkh2.exe (PID: 8064)
- powershell.exe (PID: 3240)
- powershell.exe (PID: 7484)
- b80jkhkfddasa23kjlkh2.exe (PID: 6464)
- b80jkhkfdda23kjlkh2.exe (PID: 6372)
- powershell.exe (PID: 8160)
- powershell.exe (PID: 6672)
- powershell.exe (PID: 7892)
- b80jkh876yhsdda23kjlkh2.exe (PID: 5396)
- Runtime Broker.exe (PID: 7916)
- JFUEOCN2.exe (PID: 2764)
Uses Task Scheduler to run other applications
- cmd.exe (PID: 892)
- cmd.exe (PID: 7388)
ASYNCRAT has been detected (YARA)
- RegAsm.exe (PID: 7624)
- RegAsm.exe (PID: 6680)
- b80jkhkfddasa23kjlkh2.exe (PID: 5092)
Steals credentials from Web Browsers
- Runtime Broker.exe (PID: 7916)
Actions looks like stealing of personal data
- Runtime Broker.exe (PID: 7916)
SUSPICIOUS
Starts application with an unusual extension
- msedge.exe (PID: 3128)
- cmd.exe (PID: 8032)
Starts CMD.EXE for commands execution
- Valorant Resou_nls..scr (PID: 7920)
- b8023kjlkh2.exe (PID: 8064)
- b80jkhkfdda23kjlkh2.exe (PID: 6372)
- Runtime Broker.exe (PID: 7916)
BASE64 encoded PowerShell command has been detected
- eNHmiraJ5p.exe (PID: 2764)
- gYfLVVfGK1.exe (PID: 6220)
- ikR4QDdPW5.exe (PID: 7136)
- k0JkW1Tx32.exe (PID: 7832)
- G6Hx9AeRx9.exe (PID: 8120)
- w7SFcC9are.exe (PID: 4344)
Starts POWERSHELL.EXE for commands execution
- eNHmiraJ5p.exe (PID: 2764)
- G6Hx9AeRx9.exe (PID: 8120)
- k0JkW1Tx32.exe (PID: 7832)
- w7SFcC9are.exe (PID: 4344)
- b8023kjlkh2.exe (PID: 8064)
- b80jkhkfdda23kjlkh2.exe (PID: 6372)
- gYfLVVfGK1.exe (PID: 6220)
- ikR4QDdPW5.exe (PID: 7136)
Base64-obfuscated command line is found
- eNHmiraJ5p.exe (PID: 2764)
- gYfLVVfGK1.exe (PID: 6220)
- ikR4QDdPW5.exe (PID: 7136)
- k0JkW1Tx32.exe (PID: 7832)
- G6Hx9AeRx9.exe (PID: 8120)
- w7SFcC9are.exe (PID: 4344)
The process creates files with name similar to system file names
- powershell.exe (PID: 8112)
- JFUEOCN2.exe (PID: 2764)
Unusual connection from system programs
- powershell.exe (PID: 3240)
- powershell.exe (PID: 7740)
- powershell.exe (PID: 6672)
- powershell.exe (PID: 7484)
- powershell.exe (PID: 7892)
- powershell.exe (PID: 8160)
The Powershell connects to the Internet
- powershell.exe (PID: 7740)
- powershell.exe (PID: 6672)
- powershell.exe (PID: 3240)
- powershell.exe (PID: 7484)
- powershell.exe (PID: 7892)
- powershell.exe (PID: 8160)
Connects to unusual port
- RegAsm.exe (PID: 7624)
- b80jkhkfddasa23kjlkh2.exe (PID: 5092)
- RegAsm.exe (PID: 6680)
- b80jkh876yhsdda23kjlkh2.exe (PID: 5396)
Process drops legitimate windows executable
- powershell.exe (PID: 7484)
- b80jkhkfddasa23kjlkh2.exe (PID: 6464)
- powershell.exe (PID: 6672)
- JFUEOCN2.exe (PID: 2764)
Application launched itself
- b80jkhkfddasa23kjlkh2.exe (PID: 6464)
- Runtime Broker.exe (PID: 7916)
Drops 7-zip archiver for unpacking
- JFUEOCN2.exe (PID: 2764)
Malware-specific behavior (creating "System.dll" in Temp)
- JFUEOCN2.exe (PID: 2764)
Get information on the list of running processes
- cmd.exe (PID: 1424)
- Runtime Broker.exe (PID: 7916)
Uses TASKKILL.EXE to kill Browsers
- cmd.exe (PID: 7400)
Checks for external IP
- Runtime Broker.exe (PID: 7916)
Uses WMIC.EXE to obtain computer system information
- cmd.exe (PID: 7984)
Uses WMIC.EXE to obtain a list of video controllers
- cmd.exe (PID: 7240)
Accesses video controller name via WMI (SCRIPT)
- WMIC.exe (PID: 2936)
Process communicates with Telegram (possibly using it as an attacker's C2 server)
- Runtime Broker.exe (PID: 7916)
The process executes via Task Scheduler
- b80jkhkdsa23kjlkh2.exe (PID: 7136)
Uses WMIC.EXE to obtain Windows Installer data
- cmd.exe (PID: 7076)
Accesses antivirus product name via WMI (SCRIPT)
- WMIC.exe (PID: 6260)
INFO
Application launched itself
- msedge.exe (PID: 3128)
Checks supported languages
- identity_helper.exe (PID: 6096)
- Valorant Resou_nls..scr (PID: 7920)
- eNHmiraJ5p.exe (PID: 2764)
- gYfLVVfGK1.exe (PID: 6220)
- ikR4QDdPW5.exe (PID: 7136)
- k0JkW1Tx32.exe (PID: 7832)
- G6Hx9AeRx9.exe (PID: 8120)
- w7SFcC9are.exe (PID: 4344)
- b8023kjlkh2.exe (PID: 8064)
- RegAsm.exe (PID: 7624)
- b80jkhkfddasa23kjlkh2.exe (PID: 5092)
- b80jkhkfddasa23kjlkh2.exe (PID: 6464)
- RegAsm.exe (PID: 6680)
- b80jkhkfdda23kjlkh2.exe (PID: 6372)
- b80jkhkdsa23kjlkh2.exe (PID: 6916)
- b80jkh876yhsdda23kjlkh2.exe (PID: 5396)
- InstallUtil.exe (PID: 448)
- Runtime Broker.exe (PID: 7916)
- JFUEOCN2.exe (PID: 2764)
- Runtime Broker.exe (PID: 7860)
- Runtime Broker.exe (PID: 4868)
- chcp.com (PID: 7536)
- b80jkhkdsa23kjlkh2.exe (PID: 7136)
Reads the computer name
- identity_helper.exe (PID: 6096)
- Valorant Resou_nls..scr (PID: 7920)
- eNHmiraJ5p.exe (PID: 2764)
- gYfLVVfGK1.exe (PID: 6220)
- ikR4QDdPW5.exe (PID: 7136)
- k0JkW1Tx32.exe (PID: 7832)
- G6Hx9AeRx9.exe (PID: 8120)
- w7SFcC9are.exe (PID: 4344)
- b8023kjlkh2.exe (PID: 8064)
- RegAsm.exe (PID: 7624)
- b80jkhkfddasa23kjlkh2.exe (PID: 5092)
- b80jkhkfddasa23kjlkh2.exe (PID: 6464)
- b80jkhkfdda23kjlkh2.exe (PID: 6372)
- b80jkhkdsa23kjlkh2.exe (PID: 6916)
- RegAsm.exe (PID: 6680)
- b80jkh876yhsdda23kjlkh2.exe (PID: 5396)
- InstallUtil.exe (PID: 448)
- JFUEOCN2.exe (PID: 2764)
- Runtime Broker.exe (PID: 7860)
- Runtime Broker.exe (PID: 4868)
- Runtime Broker.exe (PID: 7916)
- b80jkhkdsa23kjlkh2.exe (PID: 7136)
Drops the executable file immediately after the start
- msedge.exe (PID: 6044)
- msedge.exe (PID: 3128)
The process uses the downloaded file
- msedge.exe (PID: 3128)
- msedge.exe (PID: 7808)
Checks proxy server information
- Valorant Resou_nls..scr (PID: 7920)
- powershell.exe (PID: 3240)
- powershell.exe (PID: 7740)
- powershell.exe (PID: 6672)
- powershell.exe (PID: 7484)
- powershell.exe (PID: 8160)
- powershell.exe (PID: 7892)
- Runtime Broker.exe (PID: 7916)
Reads the software policy settings
- Valorant Resou_nls..scr (PID: 7920)
Create files in a temporary directory
- Valorant Resou_nls..scr (PID: 7920)
- JFUEOCN2.exe (PID: 2764)
- Runtime Broker.exe (PID: 7916)
The executable file from the user directory is run by the CMD process
- eNHmiraJ5p.exe (PID: 2764)
- gYfLVVfGK1.exe (PID: 6220)
- ikR4QDdPW5.exe (PID: 7136)
- k0JkW1Tx32.exe (PID: 7832)
- G6Hx9AeRx9.exe (PID: 8120)
- w7SFcC9are.exe (PID: 4344)
Process checks computer location settings
- eNHmiraJ5p.exe (PID: 2764)
- ikR4QDdPW5.exe (PID: 7136)
- k0JkW1Tx32.exe (PID: 7832)
- G6Hx9AeRx9.exe (PID: 8120)
- w7SFcC9are.exe (PID: 4344)
- gYfLVVfGK1.exe (PID: 6220)
- Runtime Broker.exe (PID: 7916)
Creates files or folders in the user directory
- eNHmiraJ5p.exe (PID: 2764)
- gYfLVVfGK1.exe (PID: 6220)
- G6Hx9AeRx9.exe (PID: 8120)
- ikR4QDdPW5.exe (PID: 7136)
- k0JkW1Tx32.exe (PID: 7832)
- w7SFcC9are.exe (PID: 4344)
- b8023kjlkh2.exe (PID: 8064)
- b80jkhkfddasa23kjlkh2.exe (PID: 6464)
- b80jkhkfdda23kjlkh2.exe (PID: 6372)
- b80jkhkdsa23kjlkh2.exe (PID: 6916)
- b80jkh876yhsdda23kjlkh2.exe (PID: 5396)
- InstallUtil.exe (PID: 448)
- Runtime Broker.exe (PID: 7916)
The executable file from the user directory is run by the Powershell process
- b8023kjlkh2.exe (PID: 8064)
- b80jkhkfddasa23kjlkh2.exe (PID: 6464)
- b80jkhkfdda23kjlkh2.exe (PID: 6372)
- b80jkhkdsa23kjlkh2.exe (PID: 6916)
- b80jkh876yhsdda23kjlkh2.exe (PID: 5396)
- JFUEOCN2.exe (PID: 2764)
Reads the machine GUID from the registry
- b8023kjlkh2.exe (PID: 8064)
- RegAsm.exe (PID: 7624)
- b80jkhkfddasa23kjlkh2.exe (PID: 6464)
- b80jkhkfddasa23kjlkh2.exe (PID: 5092)
- b80jkhkfdda23kjlkh2.exe (PID: 6372)
- b80jkhkdsa23kjlkh2.exe (PID: 6916)
- RegAsm.exe (PID: 6680)
- b80jkh876yhsdda23kjlkh2.exe (PID: 5396)
- InstallUtil.exe (PID: 448)
- Runtime Broker.exe (PID: 7916)
- b80jkhkdsa23kjlkh2.exe (PID: 7136)
Reads Environment values
- Runtime Broker.exe (PID: 7916)
Reads CPU info
- Runtime Broker.exe (PID: 7916)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
AsyncRat
(PID) Process(7624) RegAsm.exe
C2 (1)46.1.103.124
Ports (1)2341
BotnetWinlozb
Version0.5.7B
Options
AutoRunfalse
MutexWinlozb
InstallFolder%AppData%
BSoDfalse
AntiVMfalse
Certificates
Cert1MIIE4jCCAsqgAwIBAgIQAJmupDKFEn4QYTi6VNAu5zANBgkqhkiG9w0BAQ0FADASMRAwDgYDVQQDDAd3YXJyaW9yMCAXDTIyMDEzMDE3MzkzNFoYDzk5OTkxMjMxMjM1OTU5WjASMRAwDgYDVQQDDAd3YXJyaW9yMIICIjANBgkqhkiG9w0BAQEFAAOCAg8AMIICCgKCAgEA1p1heFXbFVfmtOd5Qw+jVCq6buTiUXzCHJ9ogNwGpJyyNyN70miKC4VIi30fCZ1IXcc8rAM4ODRzPV6HEPOKw29lKaG6kXtr...
Server_SignatureckNqvK0/SthCg5274QJEpcIu5XEcHCmue0Th7WQ38LKBXHXl1dUP6rhHGU3AdSp3te3/HDffDPJqNzPtIcscDMVldP2hO7NTJofiZmScZm94atR9WYY7Y3WuSjj4ZV/59vY3Qumu+eyk9F51b6W4eN6ZG3QOucgwPIQs1ZPNSgU+3pJnmErqItuDyOeHdgVn5t8VBPP66YVu8cLjS5m16oVUkgW7Ty5NkWVyP43dc20aE7PIsx8G60qzhuTMseaQqygBHDlMFeugYv7yez9w+fN01T3+d+kfyWR150SasLfq...
Keys
AESb04bfb1471c3c1d4dd53c3e485e87647901aff797b9996eaa9e6cd66d2c1fba9
Saltbfeb1e56fbcd973bb219022430a57843003d5644d21e62b9d4f180e7e6c33941
(PID) Process(5092) b80jkhkfddasa23kjlkh2.exe
C2 (1)46.1.103.124
Ports (1)2341
BotnetWinlogoew
Version0.5.7B
Options
AutoRunfalse
MutexWinlogore
InstallFolder%AppData%
BSoDfalse
AntiVMfalse
Certificates
Cert1MIIE4jCCAsqgAwIBAgIQAJmupDKFEn4QYTi6VNAu5zANBgkqhkiG9w0BAQ0FADASMRAwDgYDVQQDDAd3YXJyaW9yMCAXDTIyMDEzMDE3MzkzNFoYDzk5OTkxMjMxMjM1OTU5WjASMRAwDgYDVQQDDAd3YXJyaW9yMIICIjANBgkqhkiG9w0BAQEFAAOCAg8AMIICCgKCAgEA1p1heFXbFVfmtOd5Qw+jVCq6buTiUXzCHJ9ogNwGpJyyNyN70miKC4VIi30fCZ1IXcc8rAM4ODRzPV6HEPOKw29lKaG6kXtr...
Server_SignatureA+3TJep01BGn6AVt9nWMHZbbBXtudcFoU6SnRL6BLcB6Q0yElhK3G39frXXGgHqfXeAljzmAd54jjB9NYfH/JrJ9iWjITFtogkkNqsxq5OyHW80pCvcAADGn7zNH3HmXTHJ2G2Ha386HCdyKbGgkTk6cG5Vo2kTzPG9biPgxbrGkTFfhzsWz2SI8dhuXoreJd/t5vPCzrF8PaO9jp0/sZ/Q/6HGq/vTbD44eSrrzJRcwZXlyVT9vQ1ZHCIDmYCWXGedL5AxgPovGTx/7W3W1a1+YwlSxgzxWgCyt9ODIZLjF...
Keys
AES61266296432464ae96b05e63bcb419d17cd293233d7ccafe06c169fade41180d
Saltbfeb1e56fbcd973bb219022430a57843003d5644d21e62b9d4f180e7e6c33941
(PID) Process(6680) RegAsm.exe
C2 (1)46.1.103.124
Ports (1)9371
BotnetWinlogoewg
Version0.5.7B
Options
AutoRunfalse
MutexWinlogoreg
InstallFolder%AppData%
BSoDfalse
AntiVMfalse
Certificates
Cert1MIIE4jCCAsqgAwIBAgIQAJmupDKFEn4QYTi6VNAu5zANBgkqhkiG9w0BAQ0FADASMRAwDgYDVQQDDAd3YXJyaW9yMCAXDTIyMDEzMDE3MzkzNFoYDzk5OTkxMjMxMjM1OTU5WjASMRAwDgYDVQQDDAd3YXJyaW9yMIICIjANBgkqhkiG9w0BAQEFAAOCAg8AMIICCgKCAgEA1p1heFXbFVfmtOd5Qw+jVCq6buTiUXzCHJ9ogNwGpJyyNyN70miKC4VIi30fCZ1IXcc8rAM4ODRzPV6HEPOKw29lKaG6kXtr...
Server_SignaturepQ7HIldXdKRVxfNBOGy9zDH8McrWCtaBHw7/eKDeVV+k8Ne2+lW/q34WghfZwZ6iNijJHs3Ctk+vVmy5y8mChJYsGMprkXALhDH5/FW3MwfmLQDmADAmaBZuIbcWKp5DBXNnsa7IZkz8FLYEhTxgrL+oBHPklOqS+5vZxpZaIzl/t3bfzvTvcGyhSOSPS+OsioNr158fPuZYLpV7G88llkCZ987BSIaLF0v5WWo6ueAbQTf7INMIRPRrlzNJMcmDqONxTQVg9Ldnpr9ZEAVVO9Rj94TV00la395Z+mb6SvTr...
Keys
AESfa99d6bdeecdbad82a0cc902e7c7bd1e1b39cd45146cddd6a10375ea8fc9570d
Saltbfeb1e56fbcd973bb219022430a57843003d5644d21e62b9d4f180e7e6c33941
Total processes
237
Monitored processes
107
Malicious processes
20
Suspicious processes
8
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 448 | "C:\Windows\Microsoft.NET\Framework\v4.0.30319\InstallUtil.exe" | C:\Windows\Microsoft.NET\Framework\v4.0.30319\InstallUtil.exe | — | b80jkhkdsa23kjlkh2.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: .NET Framework installation utility Exit code: 0 Version: 4.8.9037.0 built by: NET481REL1 Modules
| |||||||||||||||
| 892 | "cmd" /C schtasks /create /tn \F2g3 /tr "C:\Users\admin\AppData\Roaming\F2g3\F2g3.exe" /st 00:00 /du 9999:59 /sc once /ri 60 /f | C:\Windows\SysWOW64\cmd.exe | — | b8023kjlkh2.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.746 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1188 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --mojo-platform-channel-handle=5244 --field-trial-handle=1872,i,9998176645964812560,9897145181821403543,131072 /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 111.0.1661.62 Modules
| |||||||||||||||
| 1424 | C:\WINDOWS\system32\cmd.exe /d /s /c "tasklist" | C:\Windows\SysWOW64\cmd.exe | — | Runtime Broker.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.746 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1568 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --mojo-platform-channel-handle=4200 --field-trial-handle=1872,i,9998176645964812560,9897145181821403543,131072 /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 111.0.1661.62 Modules
| |||||||||||||||
| 1784 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2652 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2764 | C:\Users\admin\AppData\Local\Temp\eNHmiraJ5p.exe | C:\Users\admin\AppData\Local\Temp\eNHmiraJ5p.exe | — | cmd.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: Exit code: 0 Version: 0.0.0.0 Modules
| |||||||||||||||
| 2764 | "C:\Users\admin\AppData\Local\Temp\JFUEOCN2.exe" | C:\Users\admin\AppData\Local\Temp\JFUEOCN2.exe | — | powershell.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Version: 1.3.3 Modules
| |||||||||||||||
| 2880 | "cmd" /C C:\Users\admin\AppData\Local\Temp\ikR4QDdPW5.exe | C:\Windows\System32\cmd.exe | — | Valorant Resou_nls..scr | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
61 063
Read events
60 887
Write events
175
Delete events
1
Modification events
| (PID) Process: | (3128) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (3128) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (3128) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\ThirdParty |
| Operation: | write | Name: | StatusCodes |
Value: 01000000 | |||
| (PID) Process: | (3128) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (3128) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\EdgeUpdate\ClientState\{56EB18F8-B008-4CBD-B6D2-8C97FE7E9062} |
| Operation: | write | Name: | dr |
Value: 1 | |||
| (PID) Process: | (3128) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\StabilityMetrics |
| Operation: | write | Name: | user_experience_metrics.stability.exited_cleanly |
Value: 0 | |||
| (PID) Process: | (3128) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge |
| Operation: | write | Name: | UsageStatsInSample |
Value: 1 | |||
| (PID) Process: | (3128) msedge.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\EdgeUpdate\ClientStateMedium\{56EB18F8-B008-4CBD-B6D2-8C97FE7E9062} |
| Operation: | write | Name: | usagestats |
Value: 0 | |||
| (PID) Process: | (3128) msedge.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\EdgeUpdate\ClientStateMedium\{56EB18F8-B008-4CBD-B6D2-8C97FE7E9062} |
| Operation: | write | Name: | urlstats |
Value: 0 | |||
| (PID) Process: | (3128) msedge.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\EdgeUpdate\ClientStateMedium\{56EB18F8-B008-4CBD-B6D2-8C97FE7E9062}\LastWasDefault |
| Operation: | write | Name: | S-1-5-21-1693682860-607145093-2874071422-1001 |
Value: BC8CC635B5602F00 | |||
Executable files
44
Suspicious files
336
Text files
79
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3128 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\EdgePushStorageWithConnectTokenAndKey\LOG.old~RF14dc26.TMP | — | |
MD5:— | SHA256:— | |||
| 3128 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\EdgePushStorageWithConnectTokenAndKey\LOG.old | — | |
MD5:— | SHA256:— | |||
| 3128 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old~RF14dc35.TMP | — | |
MD5:— | SHA256:— | |||
| 3128 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 3128 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\LOG.old~RF14dc74.TMP | — | |
MD5:— | SHA256:— | |||
| 3128 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\LOG.old | — | |
MD5:— | SHA256:— | |||
| 3128 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\Site Characteristics Database\LOG.old~RF14dc26.TMP | text | |
MD5:D480C74EE54A756F9A0AE4C42DC88EE1 | SHA256:61F10687C404E33B9D61AB49E0B9FCD809F3DA06E7471164BF8DA209A05DFF78 | |||
| 3128 | msedge.exe | C:\USERS\ADMIN\APPDATA\LOCAL\MICROSOFT\EDGE\USER DATA\CRASHPAD\SETTINGS.DAT | binary | |
MD5:AE78610F57A24ED740046B2A7CBE0272 | SHA256:7155BB73DA7368FB1A65E29E58B36988C7DEA30362619803908D7CFD955C22E9 | |||
| 3128 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Last Version | text | |
MD5:D6DB6EA02FE506F2DA98F1C137243587 | SHA256:126173A7D7D0F54A9FCE5465180BC49DB023E723A41BB55A0F9497BE76FBAA28 | |||
| 3128 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Local State~RF14dbe7.TMP | binary | |
MD5:24FF6E5F1AF64C692D70F012A3E20124 | SHA256:58CCCC4BB42783B62792010C13BA4A724FCB140F082D7996626F17E533E20452 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
19
TCP/UDP connections
126
DNS requests
77
Threats
17
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5388 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | binary | 471 b | unknown |
3128 | msedge.exe | GET | 200 | 23.216.77.28:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | binary | 1.11 Kb | unknown |
6916 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEA177el9ggmWelJjG4vdGL0%3D | unknown | binary | 471 b | unknown |
3128 | msedge.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicCodSigPCA2011_2011-07-08.crl | unknown | binary | 1.05 Kb | unknown |
7712 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | binary | 418 b | unknown |
7712 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | binary | 409 b | unknown |
7016 | svchost.exe | HEAD | 200 | 23.32.238.105:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/4643befd-79b8-4e0c-a2fb-c0e3ee78dcd5?P1=1703068398&P2=404&P3=2&P4=YJBxv8EH0c6DYL4TIV85N7SnDKWlcX0emeqtOQzO7nW0%2b1DejK8QToZndSqd7S7yRPEwg3kbNGllz8SuxHx3Ew%3d%3d | unknown | — | — | unknown |
7016 | svchost.exe | GET | 206 | 23.32.238.105:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/4643befd-79b8-4e0c-a2fb-c0e3ee78dcd5?P1=1703068398&P2=404&P3=2&P4=YJBxv8EH0c6DYL4TIV85N7SnDKWlcX0emeqtOQzO7nW0%2b1DejK8QToZndSqd7S7yRPEwg3kbNGllz8SuxHx3Ew%3d%3d | unknown | binary | 1.09 Kb | unknown |
2344 | svchost.exe | GET | 200 | 23.216.77.6:80 | http://crl.microsoft.com/pki/crl/products/MicWinPCA_2010-07-06.crl | unknown | binary | 552 b | unknown |
2344 | svchost.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20Time-Stamp%20PCA%202010(1).crl | unknown | binary | 814 b | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
6044 | msedge.exe | 13.107.43.16:443 | config.edge.skype.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
3764 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
3128 | msedge.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
6044 | msedge.exe | 140.82.121.4:443 | github.com | GITHUB | US | unknown |
6044 | msedge.exe | 20.103.180.120:443 | nav-edge.smartscreen.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | unknown |
2052 | MoUsoCoreWorker.exe | 4.231.128.59:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6044 | msedge.exe | 185.199.108.154:443 | github.githubassets.com | FASTLY | US | unknown |
6044 | msedge.exe | 185.199.108.133:443 | avatars.githubusercontent.com | FASTLY | US | unknown |
6044 | msedge.exe | 104.126.37.131:443 | www.bing.com | Akamai International B.V. | DE | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
github.com |
| shared |
config.edge.skype.com |
| whitelisted |
nav-edge.smartscreen.microsoft.com |
| whitelisted |
data-edge.smartscreen.microsoft.com |
| whitelisted |
github.githubassets.com |
| whitelisted |
avatars.githubusercontent.com |
| whitelisted |
github-cloud.s3.amazonaws.com |
| shared |
user-images.githubusercontent.com |
| whitelisted |
www.bing.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
7920 | Valorant Resou_nls..scr | Potentially Bad Traffic | ET INFO Pastebin-style Service (textbin .net in TLS SNI) |
2092 | svchost.exe | Misc activity | ET INFO Observed Discord Domain in DNS Lookup (discordapp .com) |
7920 | Valorant Resou_nls..scr | Misc activity | ET INFO Observed Discord Domain (discordapp .com in TLS SNI) |
2092 | svchost.exe | Misc activity | ET INFO Pastebin Service Domain in DNS Lookup (rentry .co) |
7920 | Valorant Resou_nls..scr | Misc activity | ET INFO Observed Pastebin Service Domain (rentry .co in TLS SNI) |
7916 | Runtime Broker.exe | Device Retrieving External IP Address Detected | ET POLICY Possible External IP Lookup Domain Observed in SNI (ipinfo. io) |
2092 | svchost.exe | Potentially Bad Traffic | ET INFO Online File Storage Domain in DNS Lookup (gofile .io) |
2092 | svchost.exe | Misc activity | ET HUNTING Telegram API Domain in DNS Lookup |
7916 | Runtime Broker.exe | Misc activity | ET INFO File Sharing Related Domain in TLS SNI (gofile .io) |
7916 | Runtime Broker.exe | Misc activity | ET HUNTING Observed Telegram API Domain (api .telegram .org in TLS SNI) |