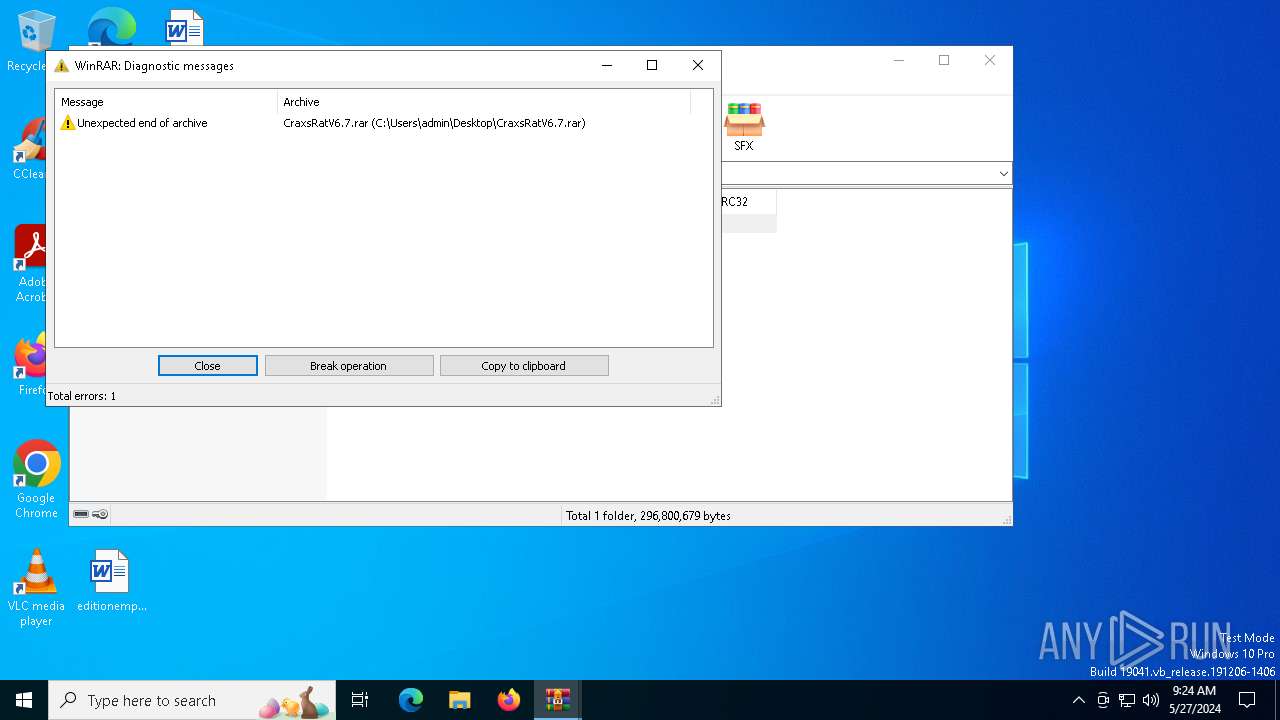
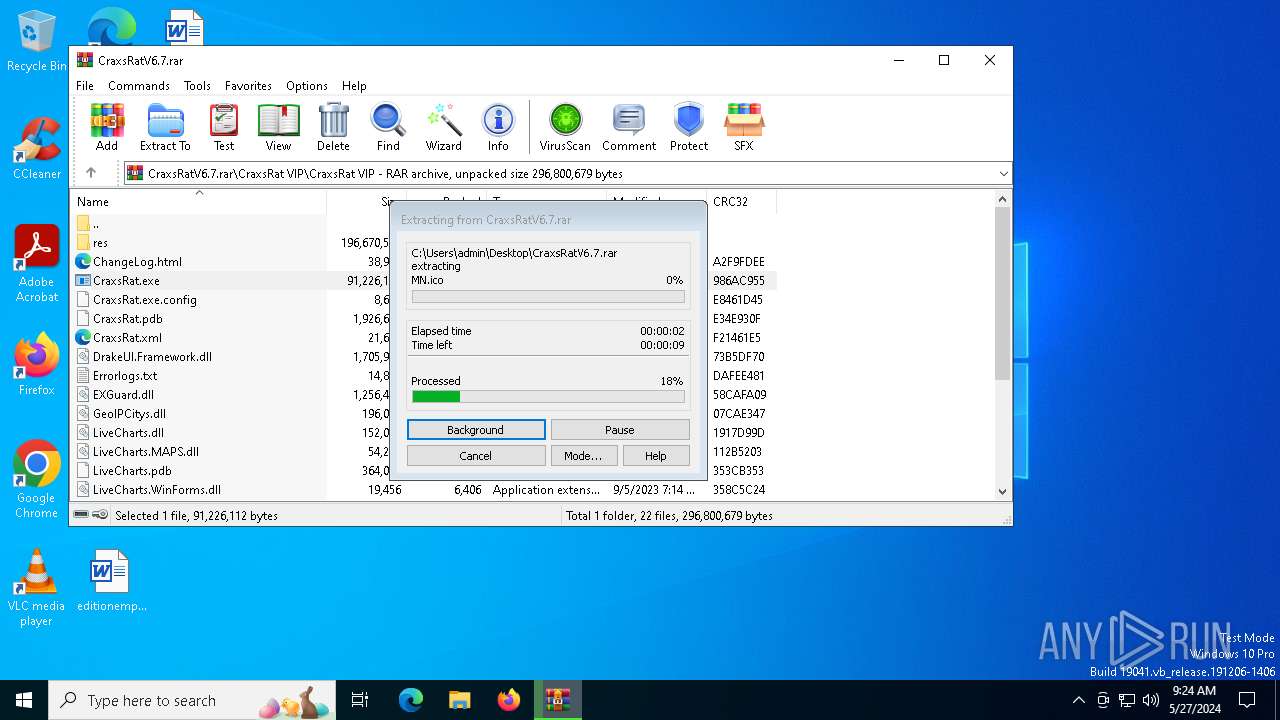
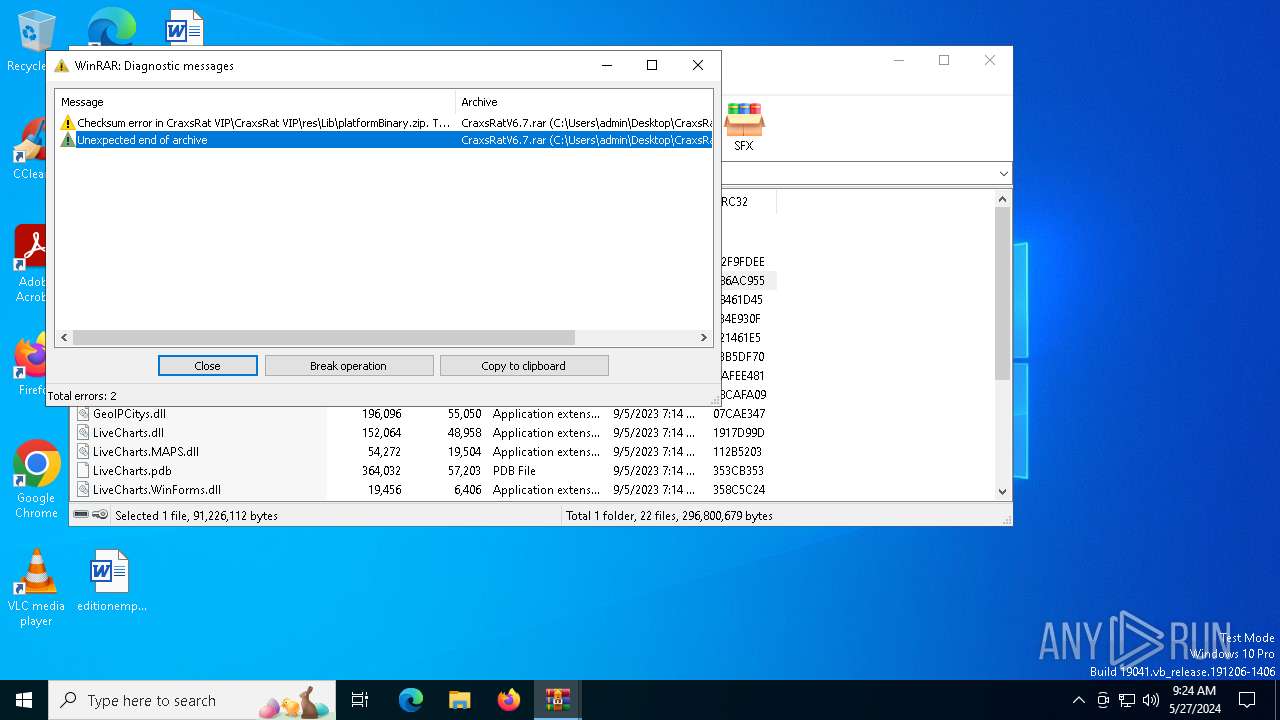
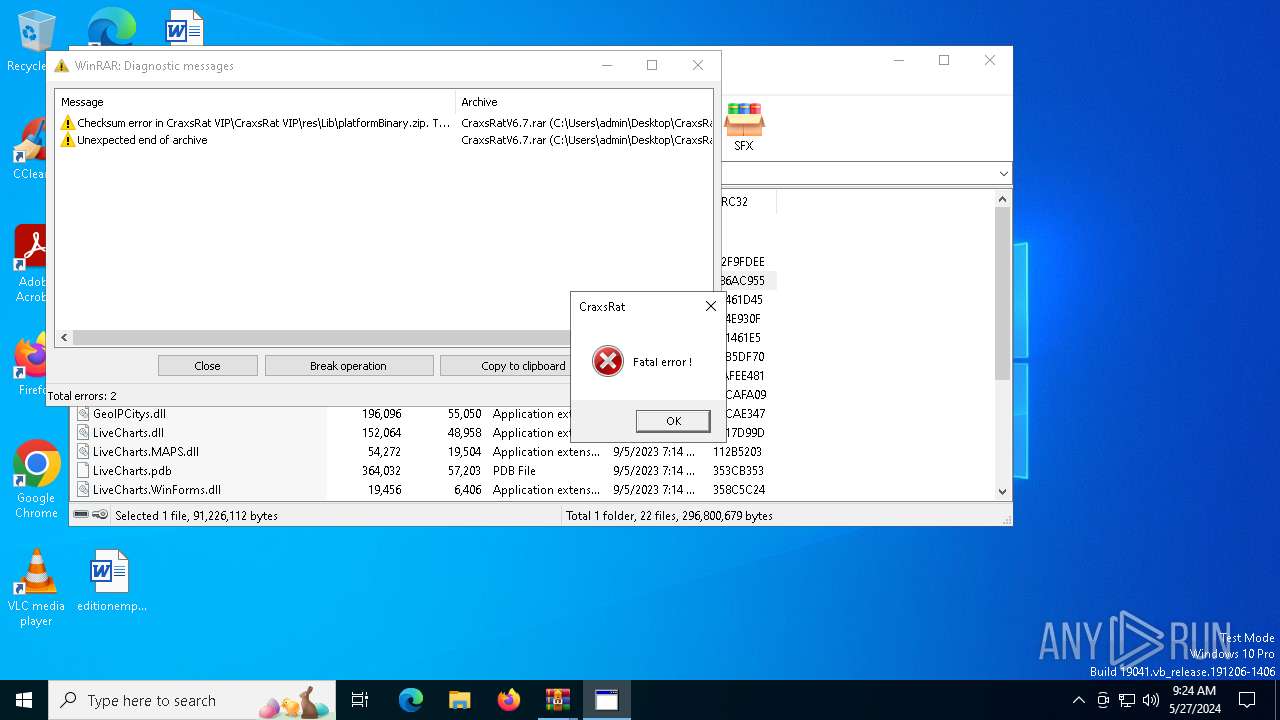
| File name: | CraxsRatV6.7.rar |
| Full analysis: | https://app.any.run/tasks/1a908b20-defe-4ce6-b30b-a8a0f75ee3d4 |
| Verdict: | Malicious activity |
| Threats: | Blank Grabber is an infostealer written in Python. It is designed to steal a wide array of data, such as browser login credentials, crypto wallets, Telegram sessions, and Discord tokens. It is an open-source malware, with its code available on GitHub and regularly receiving updates. Blank Grabber builder’s simple interface lets threat actors even with basic skills to deploy it and conduct attacks. |
| Analysis date: | May 27, 2024, 09:23:35 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v5 |
| MD5: | 4B69081A9CDA05D04CB136BBE3A7B6EB |
| SHA1: | FBC6F19E1285F1E664809D890574CB7D47E59BB8 |
| SHA256: | AAEEBEABC0B7692D3ED3DFB5E6EFB8966C87D89C5B32617EBA72829D9174C26A |
| SSDEEP: | 393216:e7kiZLkQS9SeTzPzdN9UWLI+u/FvZfYv3ehVeNeE77ZVi3ZJpJouLHAQMjdMKj9X:cWBZ51u9WvOhV/EZg6uLgRMeqlC3 |
MALICIOUS
Drops the executable file immediately after the start
- CraxsRat.exe (PID: 6732)
- CraxsRat.exe (PID: 4004)
- csc.exe (PID: 1100)
BlankGrabber has been detected
- CraxsRat.exe (PID: 6732)
- CraxsRat.exe (PID: 4004)
Bypass User Account Control (Modify registry)
- reg.exe (PID: 6932)
Bypass User Account Control (ComputerDefaults)
- ComputerDefaults.exe (PID: 3700)
Create files in the Startup directory
- CraxsRat.exe (PID: 4752)
Adds path to the Windows Defender exclusion list
- cmd.exe (PID: 4940)
- cmd.exe (PID: 6192)
- CraxsRat.exe (PID: 4752)
Antivirus name has been found in the command line (generic signature)
- cmd.exe (PID: 2620)
- MpCmdRun.exe (PID: 2796)
Windows Defender preferences modified via 'Set-MpPreference'
- cmd.exe (PID: 2620)
Bypass execution policy to execute commands
- powershell.exe (PID: 6224)
Changes powershell execution policy (Bypass)
- cmd.exe (PID: 4548)
GROWTOPIA has been detected (YARA)
- CraxsRat.exe (PID: 4752)
DISCORDGRABBER has been detected (YARA)
- CraxsRat.exe (PID: 4752)
BLANKGRABBER has been detected (SURICATA)
- CraxsRat.exe (PID: 4752)
Starts CMD.EXE for self-deleting
- CraxsRat.exe (PID: 4752)
Actions looks like stealing of personal data
- CraxsRat.exe (PID: 4752)
SUSPICIOUS
Starts a Microsoft application from unusual location
- CraxsRat.exe (PID: 6732)
- CraxsRat.exe (PID: 6752)
- CraxsRat.exe (PID: 4004)
- CraxsRat.exe (PID: 4752)
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 6532)
Process drops legitimate windows executable
- CraxsRat.exe (PID: 6732)
- CraxsRat.exe (PID: 4004)
Drops 7-zip archiver for unpacking
- WinRAR.exe (PID: 6532)
The process drops C-runtime libraries
- CraxsRat.exe (PID: 6732)
- CraxsRat.exe (PID: 4004)
Executable content was dropped or overwritten
- CraxsRat.exe (PID: 6732)
- CraxsRat.exe (PID: 4004)
- csc.exe (PID: 1100)
Process drops python dynamic module
- CraxsRat.exe (PID: 6732)
- CraxsRat.exe (PID: 4004)
Application launched itself
- CraxsRat.exe (PID: 6732)
- CraxsRat.exe (PID: 4004)
Starts CMD.EXE for commands execution
- CraxsRat.exe (PID: 6752)
- CraxsRat.exe (PID: 4752)
Uses WEVTUTIL.EXE to query events from a log or log file
- cmd.exe (PID: 5204)
- cmd.exe (PID: 6960)
Uses REG/REGEDIT.EXE to modify registry
- cmd.exe (PID: 6772)
- cmd.exe (PID: 6868)
- cmd.exe (PID: 4704)
Changes default file association
- reg.exe (PID: 6932)
Found strings related to reading or modifying Windows Defender settings
- CraxsRat.exe (PID: 6752)
- CraxsRat.exe (PID: 4752)
Loads Python modules
- CraxsRat.exe (PID: 4752)
Starts POWERSHELL.EXE for commands execution
- cmd.exe (PID: 4940)
- cmd.exe (PID: 2620)
- cmd.exe (PID: 6192)
- cmd.exe (PID: 6908)
- cmd.exe (PID: 4548)
- cmd.exe (PID: 6376)
- cmd.exe (PID: 2308)
- cmd.exe (PID: 6324)
- cmd.exe (PID: 6392)
Script disables Windows Defender's IPS
- cmd.exe (PID: 2620)
Script disables Windows Defender's real-time protection
- cmd.exe (PID: 2620)
Script adds exclusion path to Windows Defender
- cmd.exe (PID: 4940)
- cmd.exe (PID: 6192)
Uses ATTRIB.EXE to modify file attributes
- cmd.exe (PID: 5720)
Get information on the list of running processes
- CraxsRat.exe (PID: 4752)
- cmd.exe (PID: 6836)
- cmd.exe (PID: 6788)
- cmd.exe (PID: 7020)
The process bypasses the loading of PowerShell profile settings
- cmd.exe (PID: 4548)
Uses NETSH.EXE to obtain data on the network
- cmd.exe (PID: 7080)
Starts application with an unusual extension
- cmd.exe (PID: 7012)
- cmd.exe (PID: 6400)
- cmd.exe (PID: 6712)
- cmd.exe (PID: 6404)
- cmd.exe (PID: 4708)
- cmd.exe (PID: 7116)
Uses WMIC.EXE to obtain Windows Installer data
- cmd.exe (PID: 6904)
- cmd.exe (PID: 7000)
BASE64 encoded PowerShell command has been detected
- cmd.exe (PID: 4548)
Base64-obfuscated command line is found
- cmd.exe (PID: 4548)
Accesses antivirus product name via WMI (SCRIPT)
- WMIC.exe (PID: 4128)
The executable file from the user directory is run by the CMD process
- rar.exe (PID: 6208)
Uses WMIC.EXE to obtain computer system information
- cmd.exe (PID: 1752)
Uses WMIC.EXE to obtain operating system information
- cmd.exe (PID: 3172)
Accesses operating system name via WMI (SCRIPT)
- WMIC.exe (PID: 6968)
Accesses product unique identifier via WMI (SCRIPT)
- WMIC.exe (PID: 5528)
Checks for external IP
- CraxsRat.exe (PID: 4752)
Accesses video controller name via WMI (SCRIPT)
- WMIC.exe (PID: 3740)
Device Retrieving External IP Address Detected
- CraxsRat.exe (PID: 4752)
Uses WMIC.EXE to obtain a list of video controllers
- cmd.exe (PID: 6804)
Runs PING.EXE to delay simulation
- cmd.exe (PID: 4024)
Hides command output
- cmd.exe (PID: 4024)
INFO
Create files in a temporary directory
- CraxsRat.exe (PID: 6732)
- CraxsRat.exe (PID: 6752)
- CraxsRat.exe (PID: 4004)
- CraxsRat.exe (PID: 4752)
- MpCmdRun.exe (PID: 2796)
- csc.exe (PID: 1100)
- cvtres.exe (PID: 5612)
- rar.exe (PID: 6208)
Checks supported languages
- CraxsRat.exe (PID: 6732)
- CraxsRat.exe (PID: 6752)
- CraxsRat.exe (PID: 4004)
- CraxsRat.exe (PID: 4752)
- MpCmdRun.exe (PID: 2796)
- tree.com (PID: 6176)
- tree.com (PID: 4544)
- tree.com (PID: 6444)
- tree.com (PID: 2308)
- tree.com (PID: 6816)
- tree.com (PID: 4924)
- csc.exe (PID: 1100)
- cvtres.exe (PID: 5612)
- rar.exe (PID: 6208)
Reads the computer name
- CraxsRat.exe (PID: 6732)
- CraxsRat.exe (PID: 4004)
- CraxsRat.exe (PID: 4752)
- MpCmdRun.exe (PID: 2796)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 6532)
Drops the executable file immediately after the start
- WinRAR.exe (PID: 6532)
Reads the machine GUID from the registry
- CraxsRat.exe (PID: 6752)
- CraxsRat.exe (PID: 4752)
- csc.exe (PID: 1100)
- rar.exe (PID: 6208)
Reads security settings of Internet Explorer
- ComputerDefaults.exe (PID: 3700)
- WMIC.exe (PID: 4128)
- WMIC.exe (PID: 6968)
- WMIC.exe (PID: 5528)
- WMIC.exe (PID: 1008)
- WMIC.exe (PID: 3740)
Reads Microsoft Office registry keys
- ComputerDefaults.exe (PID: 3700)
Creates files in the program directory
- CraxsRat.exe (PID: 4752)
Script raised an exception (POWERSHELL)
- powershell.exe (PID: 3624)
- powershell.exe (PID: 6228)
- powershell.exe (PID: 1120)
- powershell.exe (PID: 4996)
- powershell.exe (PID: 6848)
The Powershell gets current clipboard
- powershell.exe (PID: 6740)
Reads Internet Explorer settings
- mshta.exe (PID: 6180)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v5.0) (61.5) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (38.4) |
Total processes
230
Monitored processes
122
Malicious processes
9
Suspicious processes
5
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 72 | tasklist /FO LIST | C:\Windows\System32\tasklist.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Lists the current running tasks Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1008 | wmic computersystem get totalphysicalmemory | C:\Windows\System32\wbem\WMIC.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: WMI Commandline Utility Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1100 | "C:\Windows\Microsoft.NET\Framework64\v4.0.30319\csc.exe" /noconfig /fullpaths @"C:\Users\admin\AppData\Local\Temp\hfnk4vx0\hfnk4vx0.cmdline" | C:\Windows\Microsoft.NET\Framework64\v4.0.30319\csc.exe | powershell.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Visual C# Command Line Compiler Exit code: 0 Version: 4.8.9037.0 built by: NET481REL1 Modules
| |||||||||||||||
| 1120 | powershell -Command Add-MpPreference -ExclusionPath 'C:\ProgramData\Microsoft\Windows\Start Menu\Programs\StartUp\ .scr' | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1176 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1204 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1208 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1728 | attrib +h +s "C:\Users\admin\AppData\Local\Temp\Rar$EXa6532.16118\CraxsRat VIP\CraxsRat VIP\CraxsRat.exe" | C:\Windows\System32\attrib.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Attribute Utility Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1728 | systeminfo | C:\Windows\System32\systeminfo.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Displays system information Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1752 | C:\WINDOWS\system32\cmd.exe /c "wmic computersystem get totalphysicalmemory" | C:\Windows\System32\cmd.exe | — | CraxsRat.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
73 920
Read events
73 874
Write events
42
Delete events
4
Modification events
| (PID) Process: | (6532) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (6532) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (6532) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\GoogleChromeEnterpriseBundle64.zip | |||
| (PID) Process: | (6532) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\CraxsRatV6.7.rar | |||
| (PID) Process: | (6532) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (6532) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (6532) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (6532) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (6532) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (6532) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
Executable files
52
Suspicious files
35
Text files
508
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6532 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa6532.16118\CraxsRat VIP\CraxsRat VIP\CraxsRat.exe | — | |
MD5:— | SHA256:— | |||
| 6532 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa6532.16118\CraxsRat VIP\CraxsRat VIP\LiveCharts.Wpf.pdb | binary | |
MD5:F209A4302B929A36DD534DC48DFDC617 | SHA256:718FF471C7CCFA31E9CF905DFA01C9925D692835EA646E95754FD801A5EE4CA8 | |||
| 6532 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa6532.16118\CraxsRat VIP\CraxsRat VIP\LiveCharts.xml | xml | |
MD5:5BE563DCD4B0F60D71384CB31D44AAE7 | SHA256:CE3283E4AFD74377D313F9C1D247AFE8164E626C95F710F928734DA6CFAB9311 | |||
| 6532 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa6532.16118\CraxsRat VIP\CraxsRat VIP\LiveCharts.Wpf.xml | xml | |
MD5:9CBC27F6B1AFBC7F43A9ED07F784A73D | SHA256:C18A11B019A56EC8E5916042A9F23A8655EA199BF2A4319573B18B7E035E3914 | |||
| 6532 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa6532.16118\CraxsRat VIP\CraxsRat VIP\Newtonsoft.Json.dll | executable | |
MD5:195FFB7167DB3219B217C4FD439EEDD6 | SHA256:E1E27AF7B07EEEDF5CE71A9255F0422816A6FC5849A483C6714E1B472044FA9D | |||
| 6532 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa6532.16118\CraxsRat VIP\CraxsRat VIP\ChangeLog.html | text | |
MD5:68BE5F2305D89845AE9C4E81E5B493EF | SHA256:6B7FECCC3C61F99C5DB7890187C9564BE846253A09FEE88B599B7D7EC14F9713 | |||
| 6532 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa6532.16118\CraxsRat VIP\CraxsRat VIP\LiveCharts.MAPS.dll | executable | |
MD5:DFEE15E4C6EFA37E6645D8B47C8581E0 | SHA256:5B8A9A04F454A2C4DA5989FA454A0138D3E5C40712816600F90111B7BF045C40 | |||
| 6532 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa6532.16118\CraxsRat VIP\CraxsRat VIP\GeoIPCitys.dll | executable | |
MD5:C070F2421851420E832E4F5989A775A2 | SHA256:D54FD6C5903EEA49A75D620D4BA232F8EFFB1863F5F9C974E4AC0A8FB1904131 | |||
| 6532 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa6532.16118\CraxsRat VIP\CraxsRat VIP\Errorlogs.txt | text | |
MD5:8FE4B6ABB11E41CA939AF1BFEDF93226 | SHA256:AB18414DDE41BC4662FCF05F01EE83FC8CDF48CA1D31E149DBAC3E7C8EF1565B | |||
| 6532 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa6532.16118\CraxsRat VIP\CraxsRat VIP\CraxsRat.xml | xml | |
MD5:20D9FE07B999EE8A2A161CAF409091BE | SHA256:7F0D970F59B74CE707AA9A3E9695B8889560201D1A2C94D1C8298E32643EBE67 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
10
TCP/UDP connections
25
DNS requests
7
Threats
4
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5228 | svchost.exe | GET | 200 | 2.20.68.220:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | unknown |
— | — | GET | 200 | 2.20.68.220:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | unknown |
5140 | MoUsoCoreWorker.exe | GET | 200 | 2.20.68.220:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | unknown |
5228 | svchost.exe | GET | — | 2.17.245.133:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | unknown |
— | — | GET | 200 | 2.17.245.133:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | unknown |
5140 | MoUsoCoreWorker.exe | GET | 200 | 2.17.245.133:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | unknown |
— | — | GET | 204 | 142.250.184.227:443 | https://gstatic.com/generate_204 | unknown | — | — | unknown |
4752 | CraxsRat.exe | GET | 200 | 208.95.112.1:80 | http://ip-api.com/json/?fields=225545 | unknown | — | — | unknown |
2908 | OfficeClickToRun.exe | POST | — | 52.182.143.214:443 | https://self.events.data.microsoft.com/OneCollector/1.0/ | unknown | — | — | unknown |
4752 | CraxsRat.exe | POST | 404 | 162.159.136.232:443 | https://discord.com/api/webhooks/1193297764734480404/KUzaY4KCWj1VFSHjqDcOcwuGOmHzx9c2YCWgq2T7_qupTk0xmZu3ZEcRqwiXXKSMtMv1 | unknown | binary | 45 b | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 239.255.255.250:1900 | — | — | — | unknown |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
5228 | svchost.exe | 2.20.68.220:80 | crl.microsoft.com | Telkom-Internet | ZA | unknown |
— | — | 2.20.68.220:80 | crl.microsoft.com | Telkom-Internet | ZA | unknown |
5140 | MoUsoCoreWorker.exe | 2.20.68.220:80 | crl.microsoft.com | Telkom-Internet | ZA | unknown |
— | — | 2.17.245.133:80 | www.microsoft.com | Akamai International B.V. | NL | unknown |
5228 | svchost.exe | 2.17.245.133:80 | www.microsoft.com | Akamai International B.V. | NL | unknown |
5140 | MoUsoCoreWorker.exe | 2.17.245.133:80 | www.microsoft.com | Akamai International B.V. | NL | unknown |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
gstatic.com |
| whitelisted |
ip-api.com |
| shared |
discord.com |
| whitelisted |
self.events.data.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2184 | svchost.exe | Misc activity | ET INFO Observed Discord Domain in DNS Lookup (discord .com) |
4752 | CraxsRat.exe | Device Retrieving External IP Address Detected | ET POLICY External IP Lookup ip-api.com |
4752 | CraxsRat.exe | A Network Trojan was detected | STEALER [ANY.RUN] BlankGrabber (SkochGrabber) Generic External IP Check |
4752 | CraxsRat.exe | Misc activity | ET INFO Observed Discord Domain (discord .com in TLS SNI) |