| File name: | aaa7799edfd86b52438a9e0d71f8069cbcbe1988036b95888fcdc553e729b7b9.exe |
| Full analysis: | https://app.any.run/tasks/8280b055-e369-4c6d-ae3f-cc695a429f25 |
| Verdict: | Malicious activity |
| Threats: | Akira Ransomware emerged in March 2023 and compromised over 250 organizations by January 2024 with approximately $42 million in ransom payments. It employs double extortion tactics exfiltrating data before encryption and threatening to publish it on a dedicated website. |
| Analysis date: | November 06, 2024, 21:13:48 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32+ executable (GUI) x86-64, for MS Windows, 7 sections |
| MD5: | FEB81A8D7E0F91D6F74B440CDD3C2F28 |
| SHA1: | 8C479629F45D8D9EA5E6ED48A3EEB9917FB7AD07 |
| SHA256: | AAA7799EDFD86B52438A9E0D71F8069CBCBE1988036B95888FCDC553E729B7B9 |
| SSDEEP: | 24576:6RzFgrQfysXMLTZ28J3rGVuZ0EmjBfmxo:6RarQfyscLTZ28J3aVuZ0EmjBfmm |
MALICIOUS
AKIRA has been detected (YARA)
- aaa7799edfd86b52438a9e0d71f8069cbcbe1988036b95888fcdc553e729b7b9.exe (PID: 640)
SUSPICIOUS
The process executes via Task Scheduler
- AppHostRegistrationVerifier.exe (PID: 5716)
Executed via WMI
- powershell.exe (PID: 2112)
INFO
Reads the computer name
- aaa7799edfd86b52438a9e0d71f8069cbcbe1988036b95888fcdc553e729b7b9.exe (PID: 640)
Checks supported languages
- aaa7799edfd86b52438a9e0d71f8069cbcbe1988036b95888fcdc553e729b7b9.exe (PID: 640)
Reads security settings of Internet Explorer
- AppHostRegistrationVerifier.exe (PID: 5716)
Checks proxy server information
- AppHostRegistrationVerifier.exe (PID: 5716)
Manual execution by a user
- notepad.exe (PID: 6624)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win64 Executable (generic) (87.3) |
|---|---|---|
| .exe | | | Generic Win/DOS Executable (6.3) |
| .exe | | | DOS Executable Generic (6.3) |
EXIF
EXE
| MachineType: | AMD AMD64 |
|---|---|
| TimeStamp: | 2024:08:21 11:09:01+00:00 |
| ImageFileCharacteristics: | Executable, Large address aware |
| PEType: | PE32+ |
| LinkerVersion: | 14.37 |
| CodeSize: | 831488 |
| InitializedDataSize: | 249856 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x8d058 |
| OSVersion: | 6 |
| ImageVersion: | - |
| SubsystemVersion: | 6 |
| Subsystem: | Windows GUI |
Total processes
138
Monitored processes
7
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 640 | "C:\Users\admin\Desktop\aaa7799edfd86b52438a9e0d71f8069cbcbe1988036b95888fcdc553e729b7b9.exe" | C:\Users\admin\Desktop\aaa7799edfd86b52438a9e0d71f8069cbcbe1988036b95888fcdc553e729b7b9.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Modules
| |||||||||||||||
| 1716 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2112 | powershell.exe -Command "Get-WmiObject Win32_Shadowcopy | Remove-WmiObject" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | WmiPrvSE.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3972 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5716 | "C:\WINDOWS\system32\AppHostRegistrationVerifier.exe" | C:\Windows\System32\AppHostRegistrationVerifier.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: App Uri Handlers Registration Verifier Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6560 | "C:\WINDOWS\SystemApps\MicrosoftWindows.Client.CBS_cw5n1h2txyewy\TextInputHost.exe" -ServerName:InputApp.AppXjd5de1g66v206tj52m9d0dtpppx4cgpn.mca | C:\Windows\SystemApps\MicrosoftWindows.Client.CBS_cw5n1h2txyewy\TextInputHost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Version: 123.26505.0.0 Modules
| |||||||||||||||
| 6624 | "C:\WINDOWS\system32\NOTEPAD.EXE" C:\Users\admin\Desktop\Log-06-11-2024-22-14-01.txt | C:\Windows\System32\notepad.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
6 077
Read events
6 049
Write events
22
Delete events
6
Modification events
| (PID) Process: | (5716) AppHostRegistrationVerifier.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (5716) AppHostRegistrationVerifier.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (5716) AppHostRegistrationVerifier.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (5716) AppHostRegistrationVerifier.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\CurrentVersion\AppModel\SystemAppData\Microsoft.ZuneMusic_8wekyb3d8bbwe\AppUriHandlers\mediaredirect.microsoft.com |
| Operation: | write | Name: | LastValidationAttemptTime |
Value: C095BACE9030DB01 | |||
| (PID) Process: | (5716) AppHostRegistrationVerifier.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\CurrentVersion\AppModel\SystemAppData\Microsoft.ZuneMusic_8wekyb3d8bbwe\AppUriHandlers\mediaredirect.microsoft.com |
| Operation: | write | Name: | FailedValiationCount |
Value: 5 | |||
| (PID) Process: | (640) aaa7799edfd86b52438a9e0d71f8069cbcbe1988036b95888fcdc553e729b7b9.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\RestartManager\Session0001 |
| Operation: | write | Name: | Owner |
Value: 800200007B4A41CD9030DB01 | |||
| (PID) Process: | (640) aaa7799edfd86b52438a9e0d71f8069cbcbe1988036b95888fcdc553e729b7b9.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\RestartManager\Session0001 |
| Operation: | write | Name: | SessionHash |
Value: F7C33EF949EC4A0BFDA9B6125E4E668DDD78A8A89403B6CDD963F395A979E227 | |||
| (PID) Process: | (640) aaa7799edfd86b52438a9e0d71f8069cbcbe1988036b95888fcdc553e729b7b9.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\RestartManager\Session0001 |
| Operation: | write | Name: | Sequence |
Value: 1 | |||
| (PID) Process: | (640) aaa7799edfd86b52438a9e0d71f8069cbcbe1988036b95888fcdc553e729b7b9.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\RestartManager\Session0001 |
| Operation: | write | Name: | RegFiles0000 |
Value: C:\Users\admin\AppData\Local\ConnectedDevicesPlatform\L.admin\ActivitiesCache.db-shm | |||
| (PID) Process: | (640) aaa7799edfd86b52438a9e0d71f8069cbcbe1988036b95888fcdc553e729b7b9.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\RestartManager\Session0001 |
| Operation: | write | Name: | RegFilesHash |
Value: F4C10188727FDC269FA75AB0BC0FEACEC36CF5BD87E696E75697D31B2090A01A | |||
Executable files
9
Suspicious files
2 661
Text files
770
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
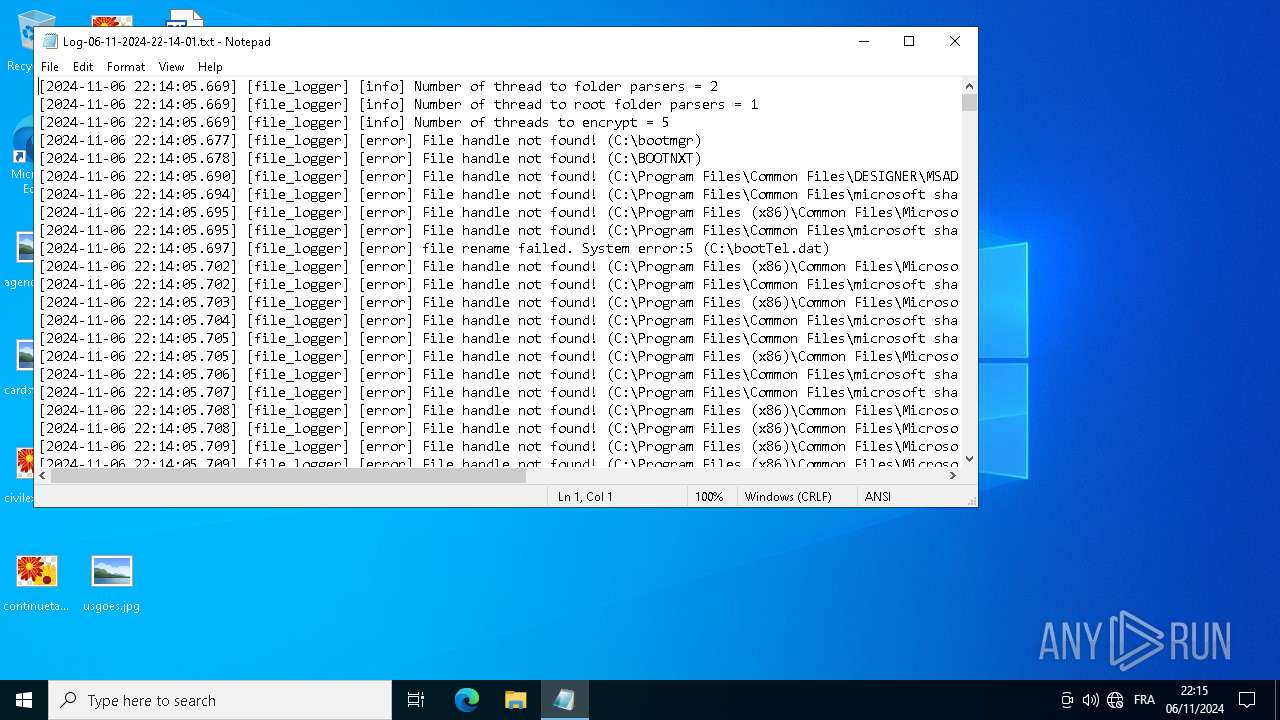
| 640 | aaa7799edfd86b52438a9e0d71f8069cbcbe1988036b95888fcdc553e729b7b9.exe | C:\Users\admin\akira_readme.txt | text | |
MD5:08F762538499795B3FABC40857F2CAEA | SHA256:6DD6401DA86A4FA1E8B74802FA9417B573DEC2C29BEAA8827494702F07024C4B | |||
| 640 | aaa7799edfd86b52438a9e0d71f8069cbcbe1988036b95888fcdc553e729b7b9.exe | C:\Users\admin\AppData\akira_readme.txt | text | |
MD5:08F762538499795B3FABC40857F2CAEA | SHA256:6DD6401DA86A4FA1E8B74802FA9417B573DEC2C29BEAA8827494702F07024C4B | |||
| 2112 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_1feqvvs3.0zr.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 640 | aaa7799edfd86b52438a9e0d71f8069cbcbe1988036b95888fcdc553e729b7b9.exe | C:\Users\admin\AppData\Local\Comms\Unistore\akira_readme.txt | text | |
MD5:08F762538499795B3FABC40857F2CAEA | SHA256:6DD6401DA86A4FA1E8B74802FA9417B573DEC2C29BEAA8827494702F07024C4B | |||
| 2112 | powershell.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\PowerShell\StartupProfileData-NonInteractive | binary | |
MD5:39E9DD242E68F590AA175BAD9B264CA0 | SHA256:BD878F8069EEC9B2B6FB72334E18CB2E6EBA1251D70792ABDD361521E5951700 | |||
| 640 | aaa7799edfd86b52438a9e0d71f8069cbcbe1988036b95888fcdc553e729b7b9.exe | C:\Users\admin\AppData\Local\akira_readme.txt | text | |
MD5:08F762538499795B3FABC40857F2CAEA | SHA256:6DD6401DA86A4FA1E8B74802FA9417B573DEC2C29BEAA8827494702F07024C4B | |||
| 2112 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_berpslqr.agq.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 640 | aaa7799edfd86b52438a9e0d71f8069cbcbe1988036b95888fcdc553e729b7b9.exe | C:\Users\admin\AppData\Local\Comms\UnistoreDB\USS.jcp.akira | binary | |
MD5:C04E7E6C41C0160CEAFAC680E3834DA2 | SHA256:5120A5E87D6F1E9CBDD481D20FA990CDEF3B22A76B162151AA7D68181AD02BDB | |||
| 640 | aaa7799edfd86b52438a9e0d71f8069cbcbe1988036b95888fcdc553e729b7b9.exe | C:\Users\admin\AppData\Local\Comms\Unistore\data\AggregateCache.uca.akira | binary | |
MD5:5C3A40CE8E52DAA9507C6F1243457603 | SHA256:89FC5F520F17C81F2A7CCED0DF55C984D05E1F6CCB0E796A7D43E4E4808A3E55 | |||
| 640 | aaa7799edfd86b52438a9e0d71f8069cbcbe1988036b95888fcdc553e729b7b9.exe | C:\Users\admin\AppData\Local\Comms\UnistoreDB\b4133b527b8fa6b1ee66d6c37d0f7442.arika | binary | |
MD5:EF8243CE5EF4A88F3C7F5E6E0C2417B9 | SHA256:8CECA2C3E9BE7F52432E6AA68AFD5FD4BBBCF0EA0F9A8FF587CF79A6C389FC0B | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
2
DNS requests
4
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2512 | slui.exe | 40.91.76.224:443 | activation-v2.sls.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
3972 | slui.exe | 40.91.76.224:443 | activation-v2.sls.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
mediaredirect.microsoft.com |
| whitelisted |
activation-v2.sls.microsoft.com |
| whitelisted |
self.events.data.microsoft.com |
| whitelisted |