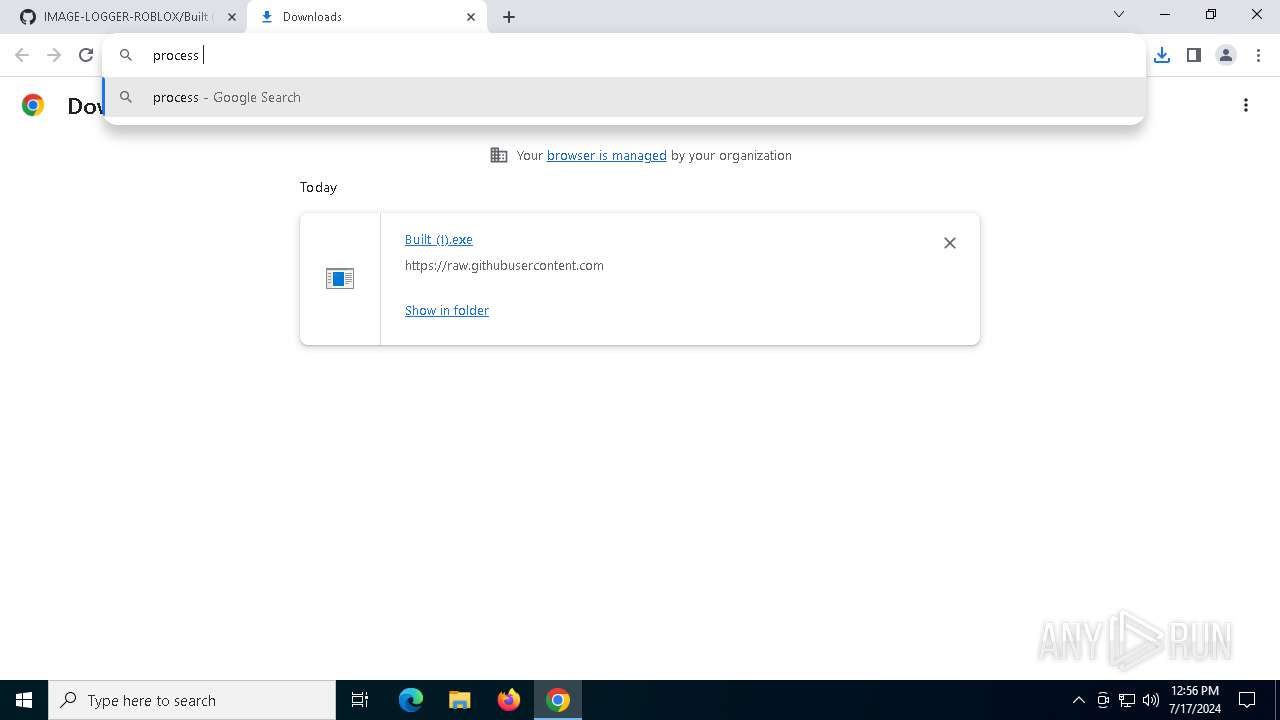
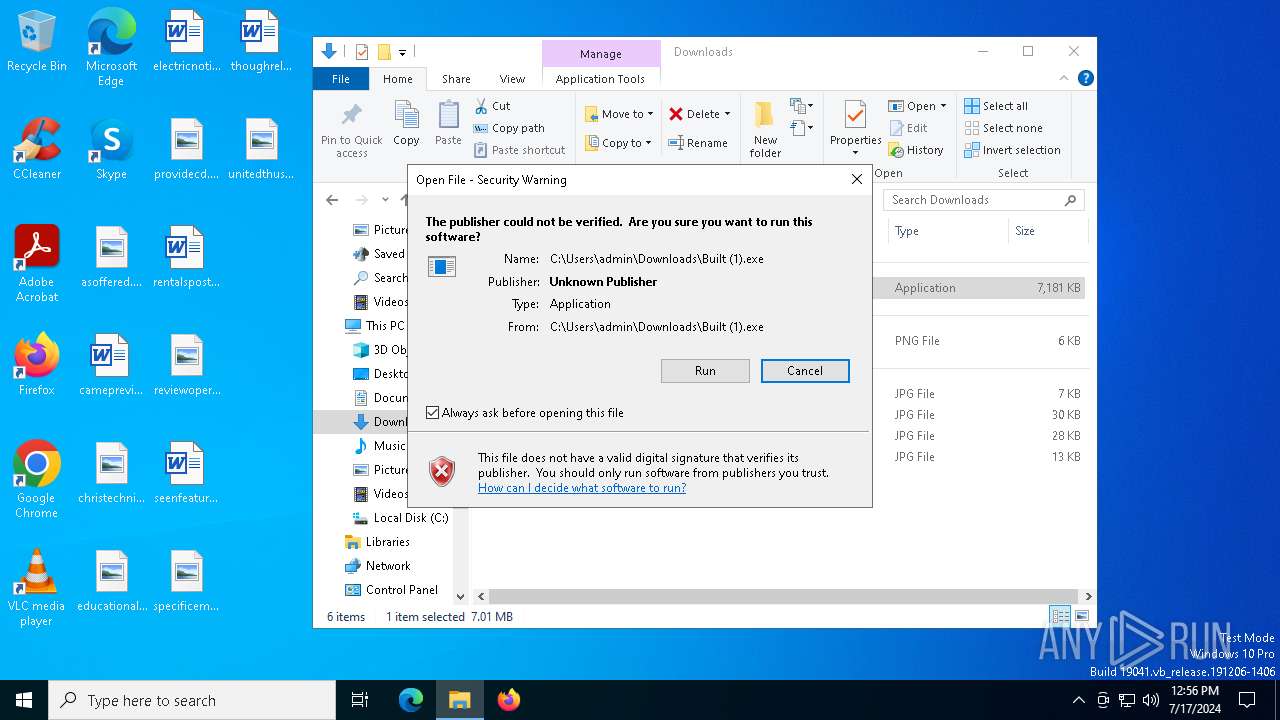
| URL: | https://github.com/Beamingtools/IMAGE-LOGGER-ROBLOX/blob/main/Built%20(1).exe |
| Full analysis: | https://app.any.run/tasks/7083f75f-e8d6-4d88-ad5e-51043647520d |
| Verdict: | Malicious activity |
| Threats: | Blank Grabber is an infostealer written in Python. It is designed to steal a wide array of data, such as browser login credentials, crypto wallets, Telegram sessions, and Discord tokens. It is an open-source malware, with its code available on GitHub and regularly receiving updates. Blank Grabber builder’s simple interface lets threat actors even with basic skills to deploy it and conduct attacks. |
| Analysis date: | July 17, 2024, 12:55:43 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MD5: | 68F4FA83585032BB9078AAC96EB4BC0C |
| SHA1: | 55C6492AB3DC5B493AFD21FE242BC352313E422E |
| SHA256: | AA02790D453C5E818AB43C8C66AEE841ED3C62CB55D9B5567D8BA33920BBDEE3 |
| SSDEEP: | 3:N8tEdQdWKXEW3It4MERZKVNaA:2u2dWK09tTsANL |
MALICIOUS
Drops the executable file immediately after the start
- Built (1).exe (PID: 4148)
- Built (1).exe (PID: 5440)
- Built (1).exe (PID: 2848)
- csc.exe (PID: 7192)
- processhacker-2.39-setup.exe (PID: 7240)
- processhacker-2.39-setup.exe (PID: 7540)
- processhacker-2.39-setup.tmp (PID: 7916)
Adds path to the Windows Defender exclusion list
- Built (1).exe (PID: 2848)
- cmd.exe (PID: 1328)
- cmd.exe (PID: 6892)
Windows Defender preferences modified via 'Set-MpPreference'
- cmd.exe (PID: 7076)
Create files in the Startup directory
- Built (1).exe (PID: 2848)
Changes powershell execution policy (Bypass)
- cmd.exe (PID: 7832)
Bypass execution policy to execute commands
- powershell.exe (PID: 8132)
BLANKGRABBER has been detected (SURICATA)
- Built (1).exe (PID: 2848)
Starts CMD.EXE for self-deleting
- Built (1).exe (PID: 2848)
Stealers network behavior
- Built (1).exe (PID: 2848)
Actions looks like stealing of personal data
- Built (1).exe (PID: 2848)
SUSPICIOUS
Process drops legitimate windows executable
- chrome.exe (PID: 5844)
- Built (1).exe (PID: 4148)
- Built (1).exe (PID: 5440)
- Built (1).exe (PID: 2848)
- processhacker-2.39-setup.tmp (PID: 7916)
Application launched itself
- Built (1).exe (PID: 4148)
- Built (1).exe (PID: 5440)
- Built (1).exe (PID: 4536)
Reads security settings of Internet Explorer
- Built (1).exe (PID: 4536)
- processhacker-2.39-setup.tmp (PID: 7324)
- ProcessHacker.exe (PID: 7556)
The process drops C-runtime libraries
- Built (1).exe (PID: 4148)
- Built (1).exe (PID: 5440)
Cleans NTFS data stream (Zone Identifier)
- explorer.exe (PID: 4612)
Process drops python dynamic module
- Built (1).exe (PID: 4148)
- Built (1).exe (PID: 5440)
Executable content was dropped or overwritten
- Built (1).exe (PID: 4148)
- Built (1).exe (PID: 5440)
- Built (1).exe (PID: 2848)
- csc.exe (PID: 7192)
- processhacker-2.39-setup.exe (PID: 7240)
- processhacker-2.39-setup.tmp (PID: 7916)
- processhacker-2.39-setup.exe (PID: 7540)
Loads Python modules
- Built (1).exe (PID: 4536)
- Built (1).exe (PID: 2848)
Starts CMD.EXE for commands execution
- Built (1).exe (PID: 2848)
Reads the date of Windows installation
- Built (1).exe (PID: 4536)
- processhacker-2.39-setup.tmp (PID: 7324)
Get information on the list of running processes
- Built (1).exe (PID: 2848)
- cmd.exe (PID: 5652)
- cmd.exe (PID: 7208)
- cmd.exe (PID: 7408)
- cmd.exe (PID: 7224)
Starts POWERSHELL.EXE for commands execution
- cmd.exe (PID: 1328)
- cmd.exe (PID: 7076)
- cmd.exe (PID: 6892)
- cmd.exe (PID: 7376)
- cmd.exe (PID: 7832)
- cmd.exe (PID: 7956)
- cmd.exe (PID: 8016)
- cmd.exe (PID: 7384)
- cmd.exe (PID: 8040)
Script disables Windows Defender's IPS
- cmd.exe (PID: 7076)
Script disables Windows Defender's real-time protection
- cmd.exe (PID: 7076)
Accesses product unique identifier via WMI (SCRIPT)
- WMIC.exe (PID: 4028)
- WMIC.exe (PID: 7884)
Checks for external IP
- Built (1).exe (PID: 2848)
Script adds exclusion path to Windows Defender
- cmd.exe (PID: 1328)
- cmd.exe (PID: 6892)
Uses WMIC.EXE to obtain Windows Installer data
- cmd.exe (PID: 4392)
- cmd.exe (PID: 7356)
- cmd.exe (PID: 8008)
Accesses video controller name via WMI (SCRIPT)
- WMIC.exe (PID: 6684)
- WMIC.exe (PID: 6420)
- WMIC.exe (PID: 7836)
Uses ATTRIB.EXE to modify file attributes
- cmd.exe (PID: 2808)
Uses WMIC.EXE to obtain a list of video controllers
- cmd.exe (PID: 6372)
- cmd.exe (PID: 884)
- cmd.exe (PID: 7436)
Uses NETSH.EXE to obtain data on the network
- cmd.exe (PID: 7624)
Starts application with an unusual extension
- cmd.exe (PID: 7592)
- cmd.exe (PID: 8000)
- cmd.exe (PID: 7844)
- cmd.exe (PID: 6816)
- cmd.exe (PID: 6428)
- cmd.exe (PID: 7916)
The process bypasses the loading of PowerShell profile settings
- cmd.exe (PID: 7832)
Base64-obfuscated command line is found
- cmd.exe (PID: 7832)
BASE64 encoded PowerShell command has been detected
- cmd.exe (PID: 7832)
Searches for installed software
- reg.exe (PID: 8112)
Accesses antivirus product name via WMI (SCRIPT)
- WMIC.exe (PID: 7792)
The executable file from the user directory is run by the CMD process
- rar.exe (PID: 7788)
Uses WMIC.EXE to obtain operating system information
- cmd.exe (PID: 7572)
Accesses operating system name via WMI (SCRIPT)
- WMIC.exe (PID: 7920)
Uses WMIC.EXE to obtain computer system information
- cmd.exe (PID: 7724)
Hides command output
- cmd.exe (PID: 7492)
Runs PING.EXE to delay simulation
- cmd.exe (PID: 7492)
Reads the Windows owner or organization settings
- processhacker-2.39-setup.tmp (PID: 7916)
Drops a system driver (possible attempt to evade defenses)
- processhacker-2.39-setup.tmp (PID: 7916)
Checks Windows Trust Settings
- ProcessHacker.exe (PID: 7556)
INFO
Application launched itself
- chrome.exe (PID: 5844)
- firefox.exe (PID: 6296)
- firefox.exe (PID: 3228)
Reads Microsoft Office registry keys
- chrome.exe (PID: 5844)
- firefox.exe (PID: 3228)
The process uses the downloaded file
- chrome.exe (PID: 2120)
- explorer.exe (PID: 4612)
- firefox.exe (PID: 3228)
Drops the executable file immediately after the start
- chrome.exe (PID: 5844)
- firefox.exe (PID: 3228)
Reads security settings of Internet Explorer
- explorer.exe (PID: 4612)
- WMIC.exe (PID: 4028)
- WMIC.exe (PID: 6684)
- WMIC.exe (PID: 6420)
- WMIC.exe (PID: 7792)
- WMIC.exe (PID: 7920)
- WMIC.exe (PID: 1700)
- WMIC.exe (PID: 7884)
- WMIC.exe (PID: 7836)
- Taskmgr.exe (PID: 1972)
Executable content was dropped or overwritten
- chrome.exe (PID: 5844)
- firefox.exe (PID: 3228)
Reads the computer name
- Built (1).exe (PID: 4536)
- Built (1).exe (PID: 4148)
- Built (1).exe (PID: 5440)
- Built (1).exe (PID: 2848)
- processhacker-2.39-setup.tmp (PID: 7324)
- processhacker-2.39-setup.tmp (PID: 7916)
- ProcessHacker.exe (PID: 7556)
Checks proxy server information
- explorer.exe (PID: 4612)
- ProcessHacker.exe (PID: 7556)
Creates files or folders in the user directory
- explorer.exe (PID: 4612)
Checks supported languages
- Built (1).exe (PID: 4148)
- Built (1).exe (PID: 4536)
- Built (1).exe (PID: 5440)
- Built (1).exe (PID: 2848)
- csc.exe (PID: 7192)
- tree.com (PID: 8052)
- cvtres.exe (PID: 7868)
- tree.com (PID: 7260)
- tree.com (PID: 6416)
- tree.com (PID: 8024)
- tree.com (PID: 7608)
- tree.com (PID: 7400)
- rar.exe (PID: 7788)
- processhacker-2.39-setup.exe (PID: 7240)
- processhacker-2.39-setup.tmp (PID: 7324)
- processhacker-2.39-setup.exe (PID: 7540)
- processhacker-2.39-setup.tmp (PID: 7916)
- ProcessHacker.exe (PID: 7556)
Create files in a temporary directory
- Built (1).exe (PID: 4148)
- Built (1).exe (PID: 5440)
- Built (1).exe (PID: 2848)
- csc.exe (PID: 7192)
- cvtres.exe (PID: 7868)
- rar.exe (PID: 7788)
- processhacker-2.39-setup.exe (PID: 7240)
- processhacker-2.39-setup.exe (PID: 7540)
- processhacker-2.39-setup.tmp (PID: 7916)
Reads the software policy settings
- explorer.exe (PID: 4612)
- ProcessHacker.exe (PID: 7556)
Process checks computer location settings
- Built (1).exe (PID: 4536)
- processhacker-2.39-setup.tmp (PID: 7324)
Script raised an exception (POWERSHELL)
- powershell.exe (PID: 3800)
- powershell.exe (PID: 2632)
- powershell.exe (PID: 884)
- powershell.exe (PID: 7200)
- powershell.exe (PID: 8112)
Creates files in the program directory
- Built (1).exe (PID: 2848)
- processhacker-2.39-setup.tmp (PID: 7916)
The Powershell gets current clipboard
- powershell.exe (PID: 7820)
Reads the machine GUID from the registry
- csc.exe (PID: 7192)
- rar.exe (PID: 7788)
- ProcessHacker.exe (PID: 7556)
Attempting to use instant messaging service
- Built (1).exe (PID: 2848)
Creates a software uninstall entry
- processhacker-2.39-setup.tmp (PID: 7916)
Reads Environment values
- ProcessHacker.exe (PID: 7556)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
305
Monitored processes
161
Malicious processes
10
Suspicious processes
4
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 752 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 752 | C:\WINDOWS\system32\SppExtComObj.exe -Embedding | C:\Windows\System32\SppExtComObj.Exe | — | svchost.exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: KMS Connection Broker Version: 10.0.19041.3996 (WinBuild.160101.0800) | |||||||||||||||
| 884 | C:\WINDOWS\system32\cmd.exe /c "wmic path win32_VideoController get name" | C:\Windows\System32\cmd.exe | — | Built (1).exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 884 | powershell -Command Add-MpPreference -ExclusionPath 'C:\ProgramData\Microsoft\Windows\Start Menu\Programs\StartUp\ .scr' | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1328 | C:\WINDOWS\system32\cmd.exe /c "powershell -Command Add-MpPreference -ExclusionPath 'C:\Users\admin\Downloads\Built (1).exe'" | C:\Windows\System32\cmd.exe | — | Built (1).exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1700 | wmic computersystem get totalphysicalmemory | C:\Windows\System32\wbem\WMIC.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: WMI Commandline Utility Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1764 | C:\WINDOWS\System32\rundll32.exe C:\WINDOWS\System32\shell32.dll,SHCreateLocalServerRunDll {9aa46009-3ce0-458a-a354-715610a075e6} -Embedding | C:\Windows\System32\rundll32.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1972 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1972 | "C:\WINDOWS\system32\taskmgr.exe" /4 | C:\Windows\System32\Taskmgr.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Task Manager Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2056 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=chrome.mojom.UtilReadIcon --lang=en-US --service-sandbox-type=icon_reader --disable-quic --no-appcompat-clear --mojo-platform-channel-handle=5260 --field-trial-handle=1868,i,9157686818593150771,1213378947431775440,262144 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction --variations-seed-version /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 122.0.6261.70 Modules
| |||||||||||||||
Total events
109 290
Read events
109 153
Write events
133
Delete events
4
Modification events
| (PID) Process: | (5844) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (5844) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (5844) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\ThirdParty |
| Operation: | write | Name: | StatusCodes |
Value: | |||
| (PID) Process: | (5844) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\ThirdParty |
| Operation: | write | Name: | StatusCodes |
Value: 01000000 | |||
| (PID) Process: | (5844) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (5844) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Update\ClientState\{8A69D345-D564-463c-AFF1-A69D9E530F96} |
| Operation: | write | Name: | dr |
Value: 1 | |||
| (PID) Process: | (5844) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\StabilityMetrics |
| Operation: | write | Name: | user_experience_metrics.stability.exited_cleanly |
Value: 0 | |||
| (PID) Process: | (5844) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome |
| Operation: | write | Name: | UsageStatsInSample |
Value: 0 | |||
| (PID) Process: | (5844) chrome.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Google\Update\ClientStateMedium\{8A69D345-D564-463C-AFF1-A69D9E530F96} |
| Operation: | write | Name: | usagestats |
Value: 0 | |||
| (PID) Process: | (5844) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Update\ClientState\{8A69D345-D564-463c-AFF1-A69D9E530F96} |
| Operation: | write | Name: | metricsid |
Value: | |||
Executable files
89
Suspicious files
281
Text files
142
Unknown types
17
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 5844 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\discounts_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 5844 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\commerce_subscription_db\LOG.old~RF1cfe6c.TMP | — | |
MD5:— | SHA256:— | |||
| 5844 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\chrome_cart_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 5844 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\commerce_subscription_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 5844 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\parcel_tracking_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 5844 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\coupon_db\LOG.old~RF1cfe9b.TMP | — | |
MD5:— | SHA256:— | |||
| 5844 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\coupon_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 5844 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\PersistentOriginTrials\LOG.old | — | |
MD5:— | SHA256:— | |||
| 5844 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\f06a1db6-7739-43f9-98dc-65cea83ab66b.tmp | binary | |
MD5:5058F1AF8388633F609CADB75A75DC9D | SHA256:— | |||
| 5844 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Site Characteristics Database\LOG.old | text | |
MD5:19D1A06251A8678F85D8DE5BFAB83807 | SHA256:AA6E55DCF84CDAF0BD3F913E7B837F65500E9B71A5A7AA773D02FFBC18C7FF01 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
73
TCP/UDP connections
309
DNS requests
330
Threats
12
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1928 | MoUsoCoreWorker.exe | GET | 200 | 23.48.23.143:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
4656 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
3228 | firefox.exe | POST | 200 | 195.138.255.24:80 | http://r11.o.lencr.org/ | unknown | — | — | unknown |
3656 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
4020 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
1928 | MoUsoCoreWorker.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
4612 | explorer.exe | GET | 200 | 104.18.38.233:80 | http://ocsp.comodoca.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBRTtU9uFqgVGHhJwXZyWCNXmVR5ngQUoBEKIz6W8Qfs4q8p74Klf9AwpLQCEEj8k7RgVZSNNqfJionWlBY%3D | unknown | — | — | whitelisted |
4612 | explorer.exe | GET | 200 | 104.18.38.233:80 | http://ocsp.sectigo.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSdE3gf41WAic8Uh9lF92%2BIJqh5qwQUMuuSmv81lkgvKEBCcCA2kVwXheYCEDPXCKiRQFMZ4qW70zm5rW4%3D | unknown | — | — | whitelisted |
2124 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
2124 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4656 | SearchApp.exe | 184.86.251.18:443 | www.bing.com | Akamai International B.V. | DE | unknown |
900 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1856 | RUXIMICS.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4656 | SearchApp.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
1928 | MoUsoCoreWorker.exe | 23.48.23.143:80 | crl.microsoft.com | Akamai International B.V. | DE | unknown |
1928 | MoUsoCoreWorker.exe | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | unknown |
1928 | MoUsoCoreWorker.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4032 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.bing.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
login.live.com |
| whitelisted |
github.com |
| shared |
accounts.google.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
6424 | chrome.exe | Not Suspicious Traffic | INFO [ANY.RUN] Attempting to access raw user content on GitHub |
6424 | chrome.exe | Not Suspicious Traffic | INFO [ANY.RUN] Attempting to access raw user content on GitHub |
2168 | svchost.exe | Device Retrieving External IP Address Detected | INFO [ANY.RUN] External IP Check (ip-api .com) |
2168 | svchost.exe | Device Retrieving External IP Address Detected | ET INFO External IP Lookup Domain in DNS Lookup (ip-api .com) |
2848 | Built (1).exe | Device Retrieving External IP Address Detected | ET POLICY External IP Lookup ip-api.com |
2168 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Cloudflare content delivery network (cdnjs .cloudflare .com) |
2168 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] An application monitoring request to newrelic .com |
2168 | svchost.exe | Device Retrieving External IP Address Detected | ET INFO External IP Lookup Domain in DNS Lookup (ip-api .com) |
2168 | svchost.exe | Misc activity | ET INFO Observed Discord Domain in DNS Lookup (discord .com) |
2848 | Built (1).exe | Device Retrieving External IP Address Detected | ET POLICY External IP Lookup ip-api.com |