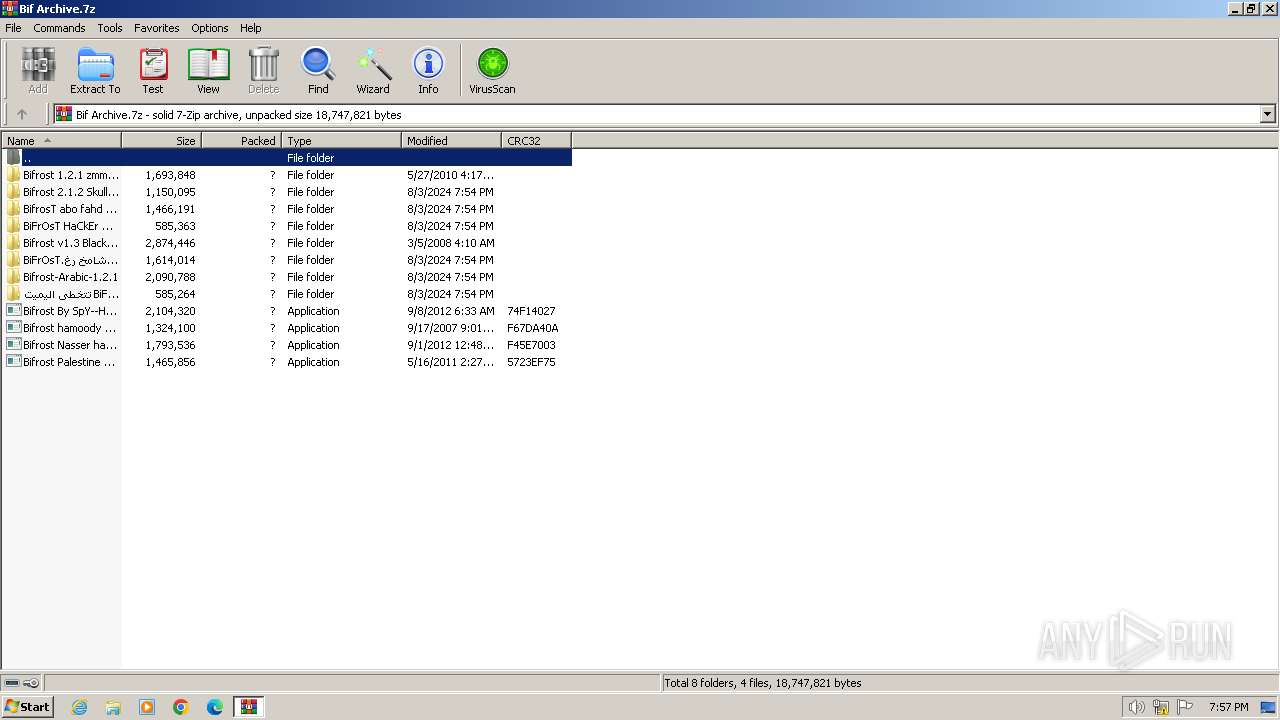
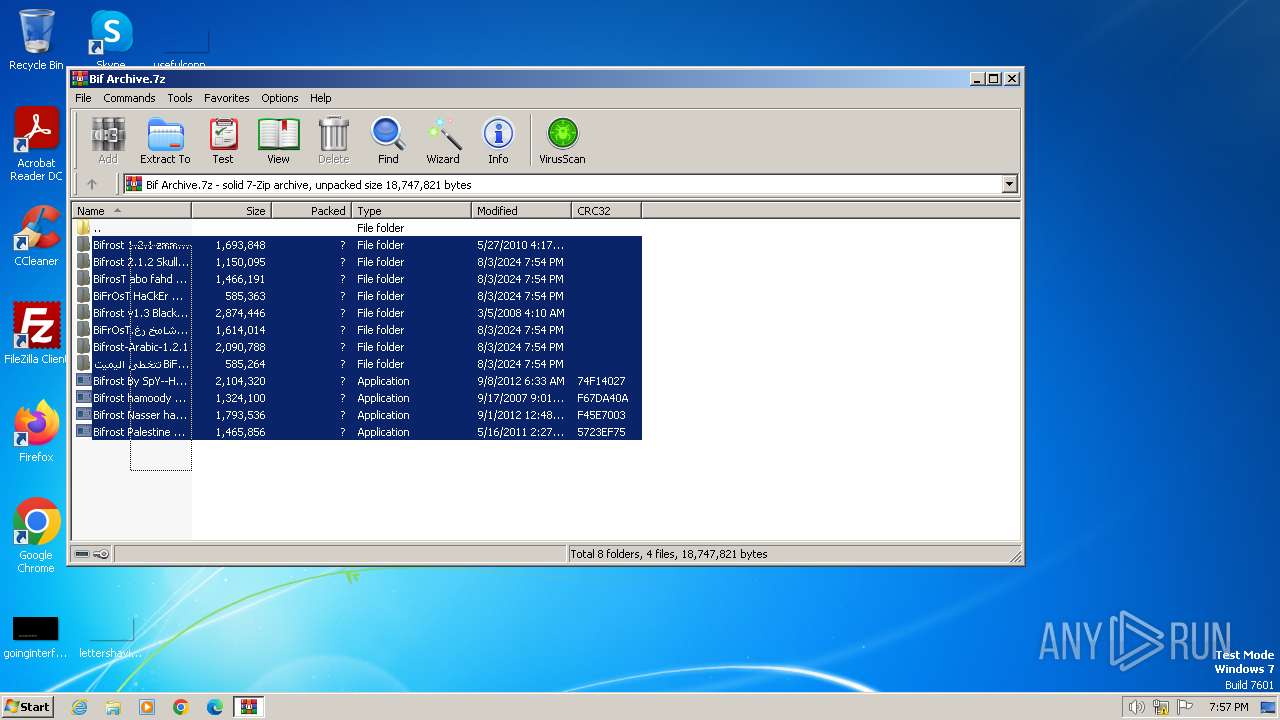
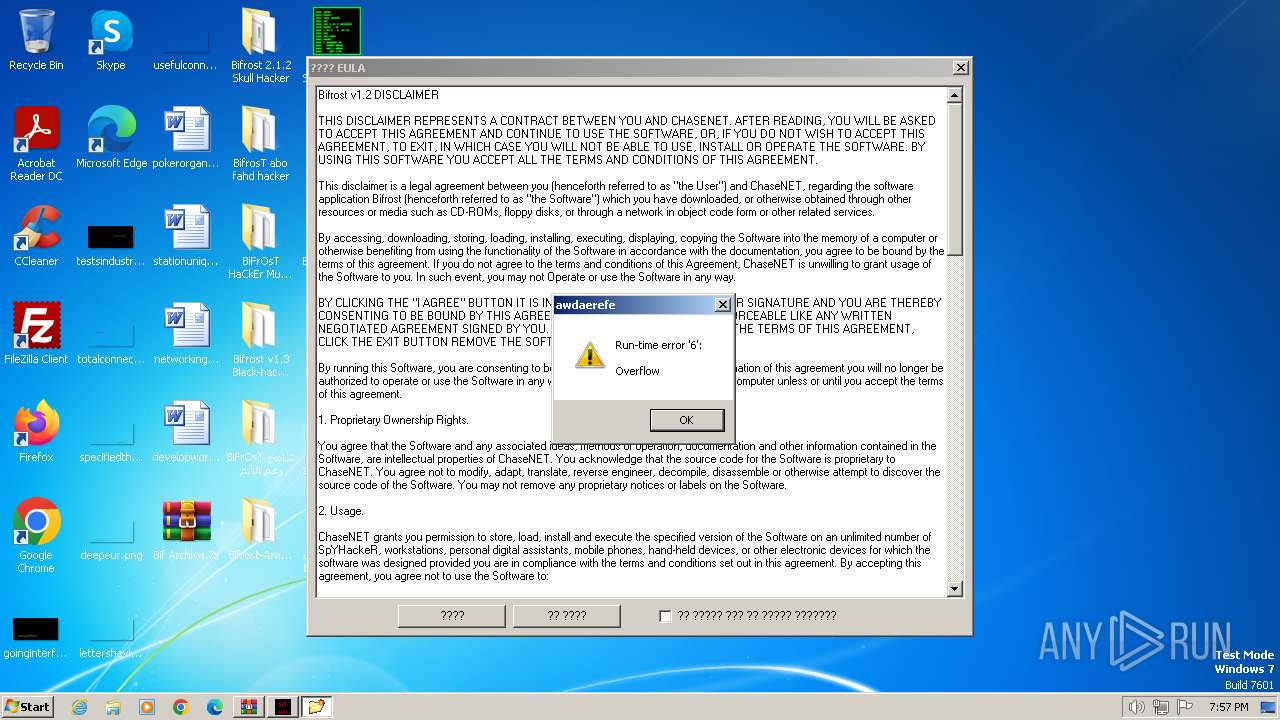
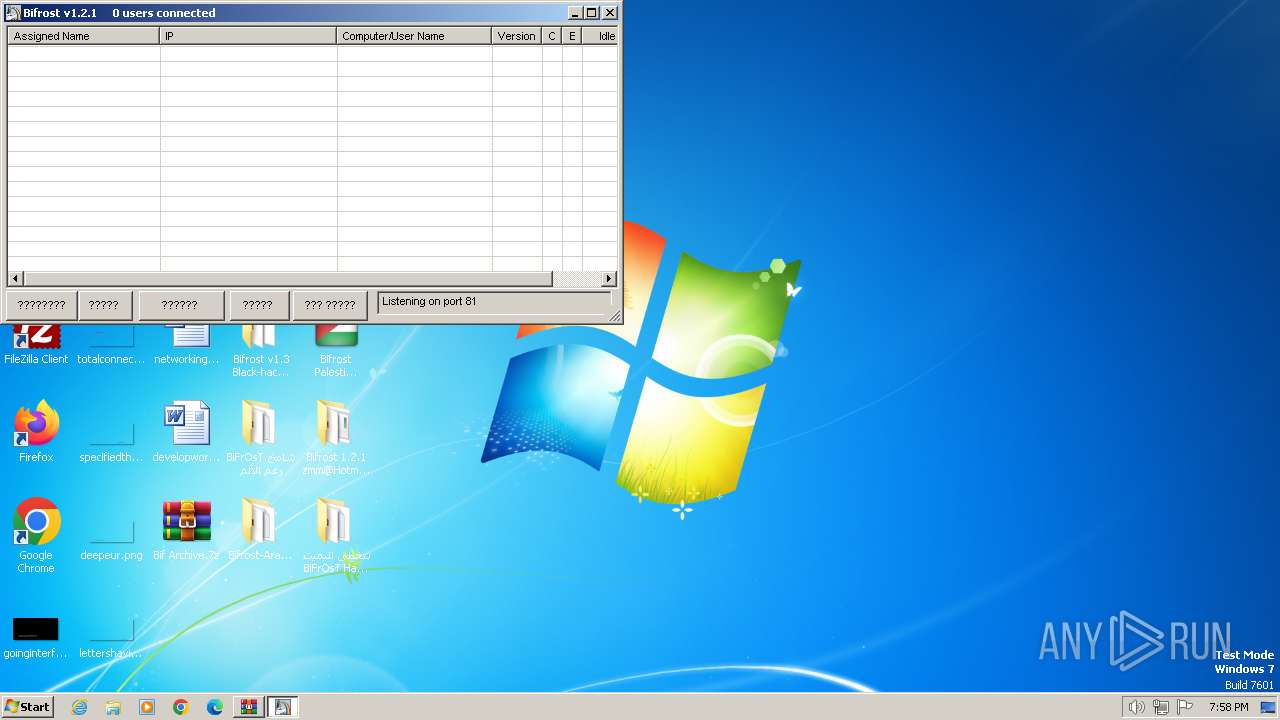
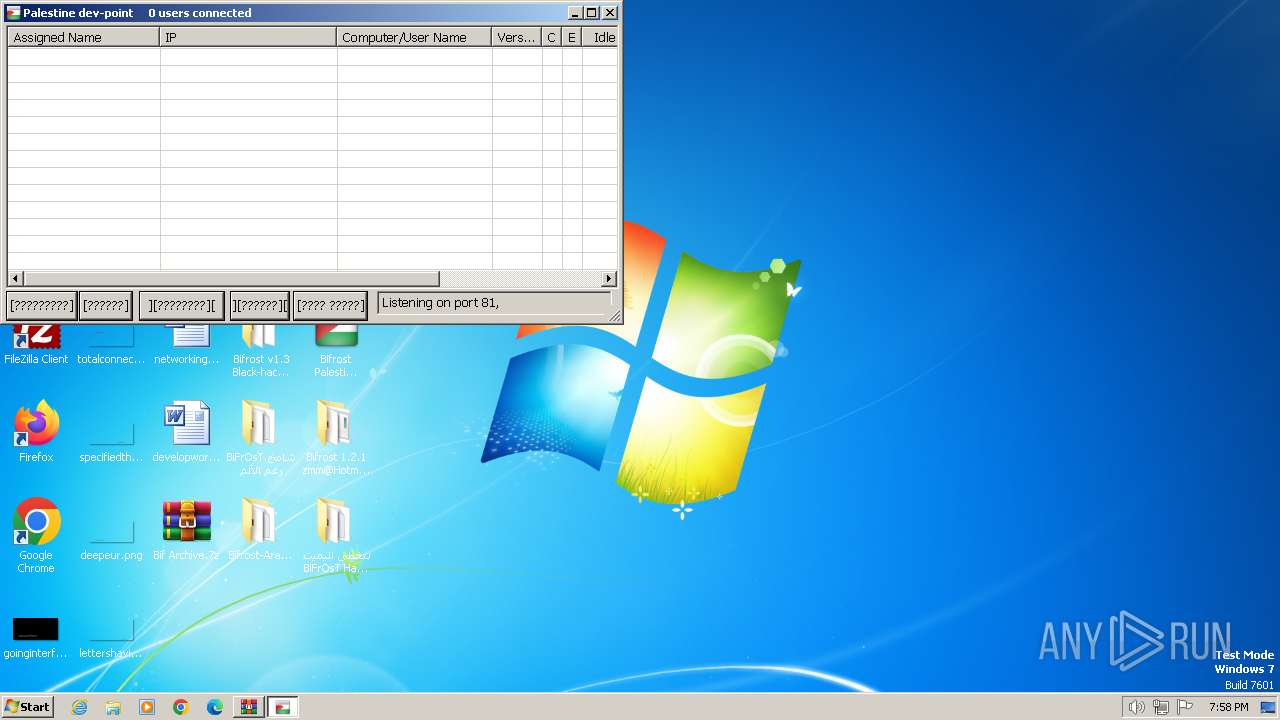
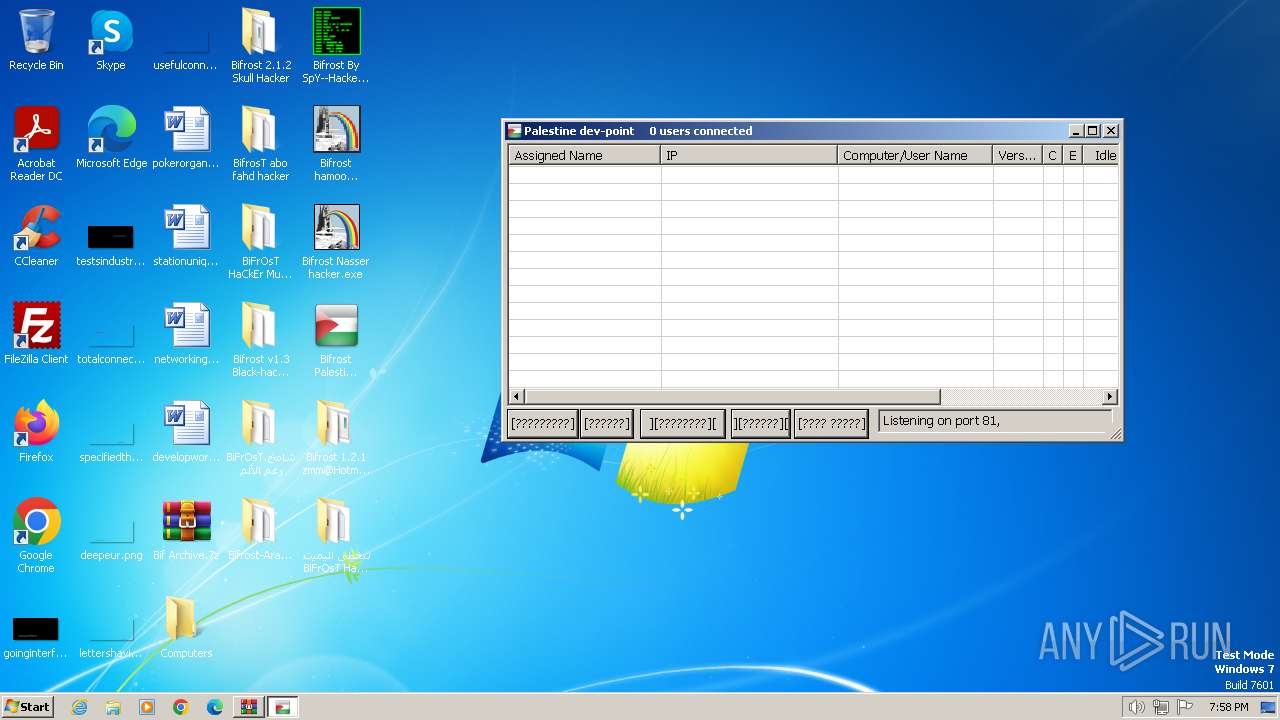
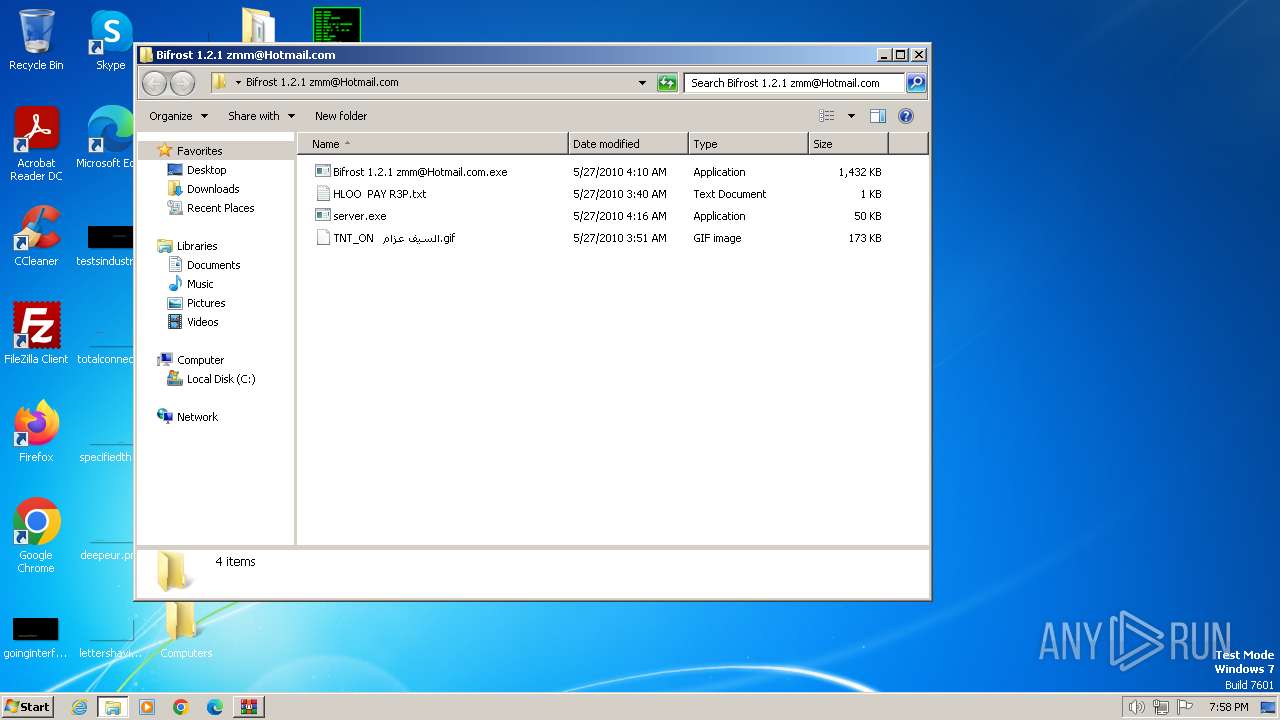
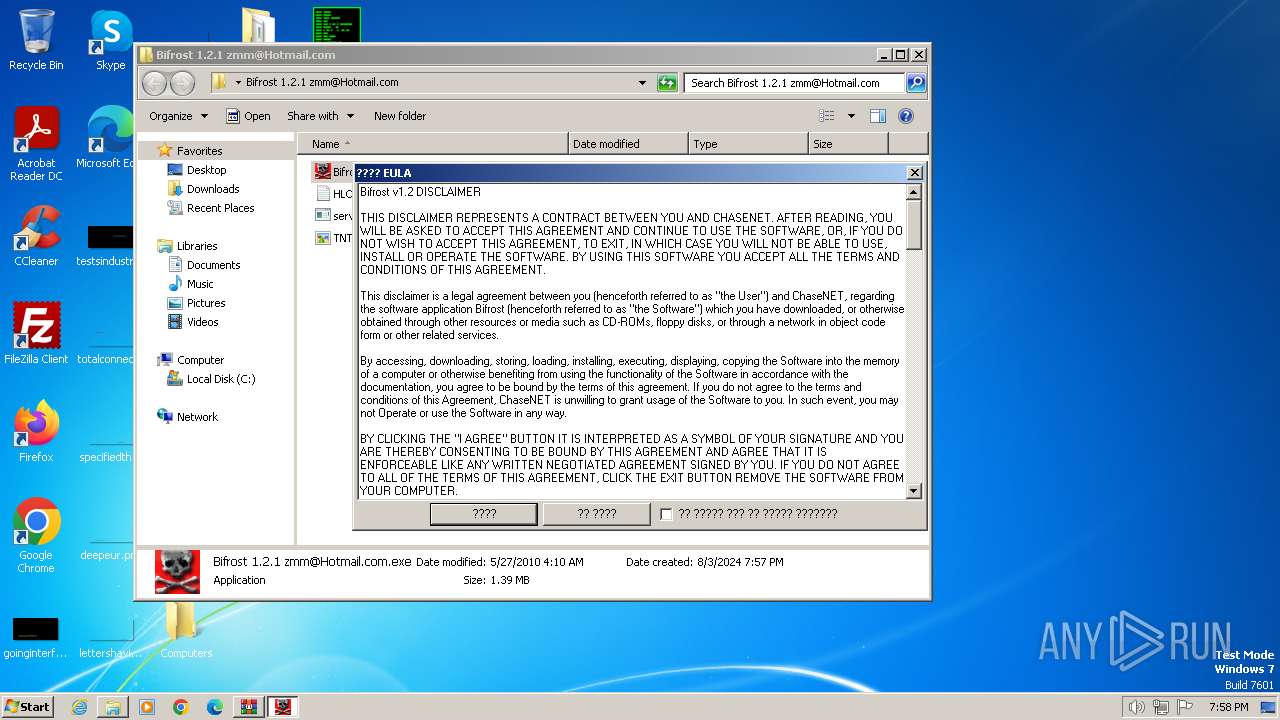
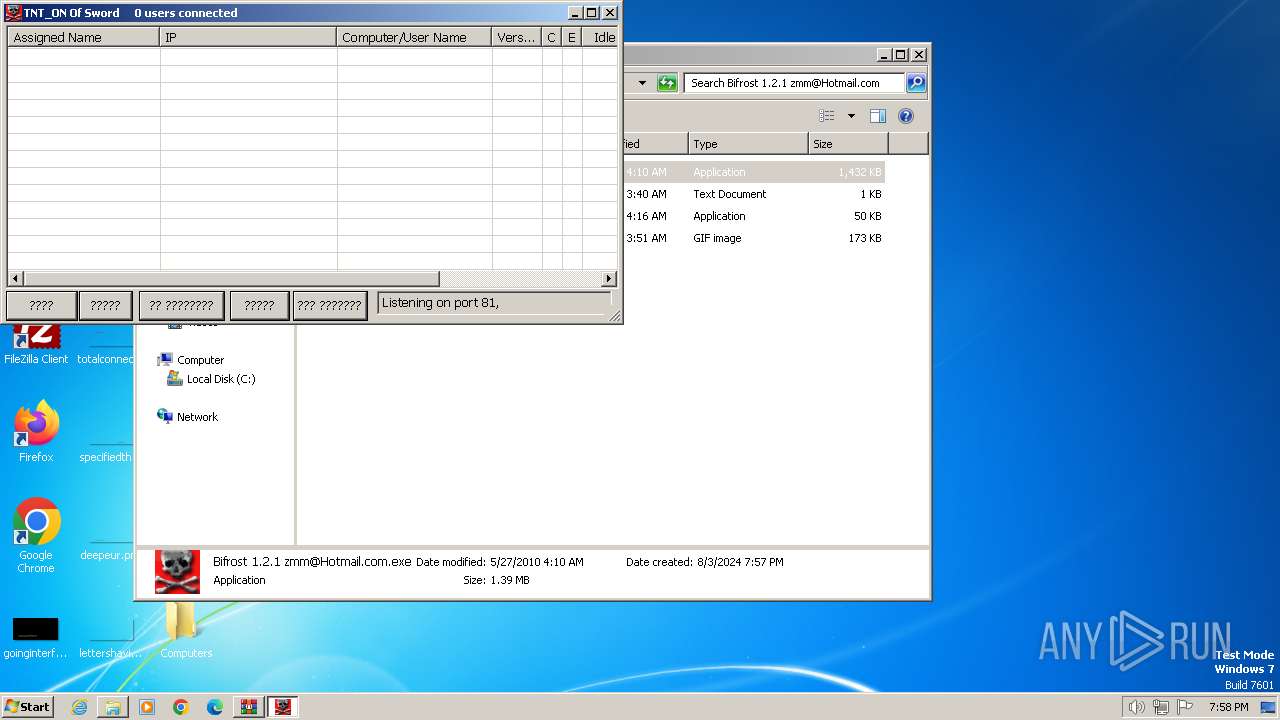
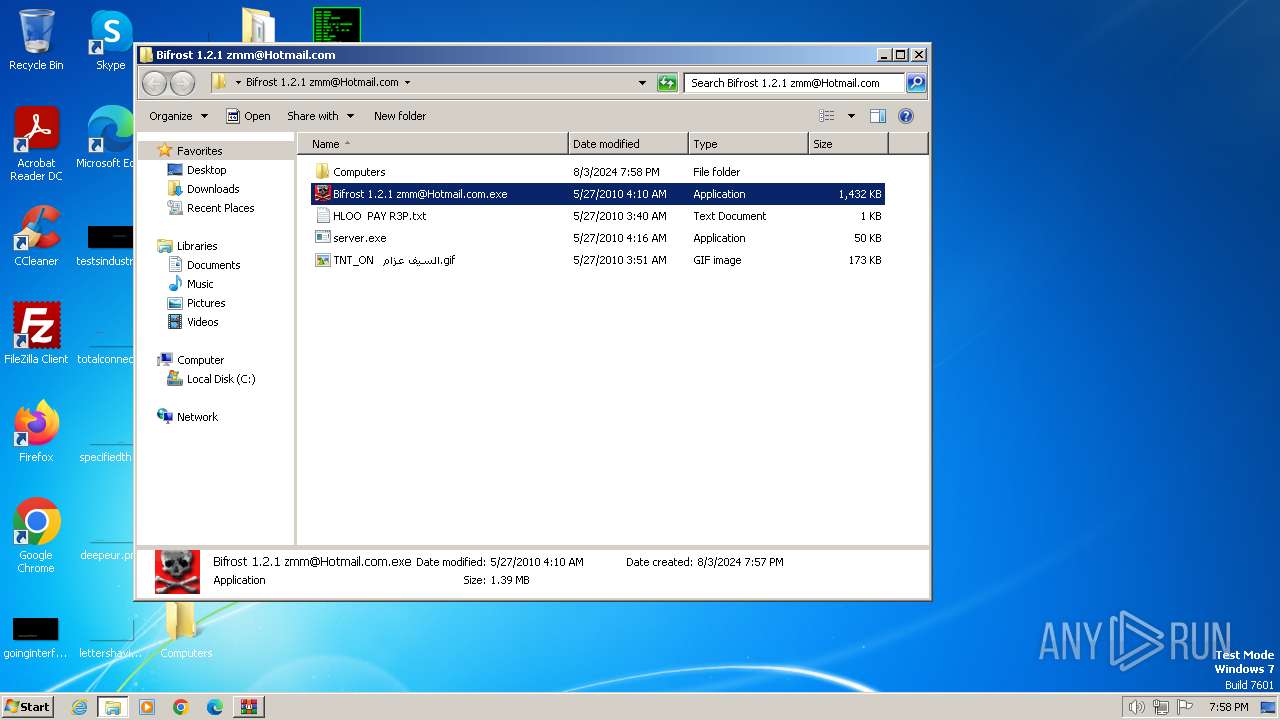
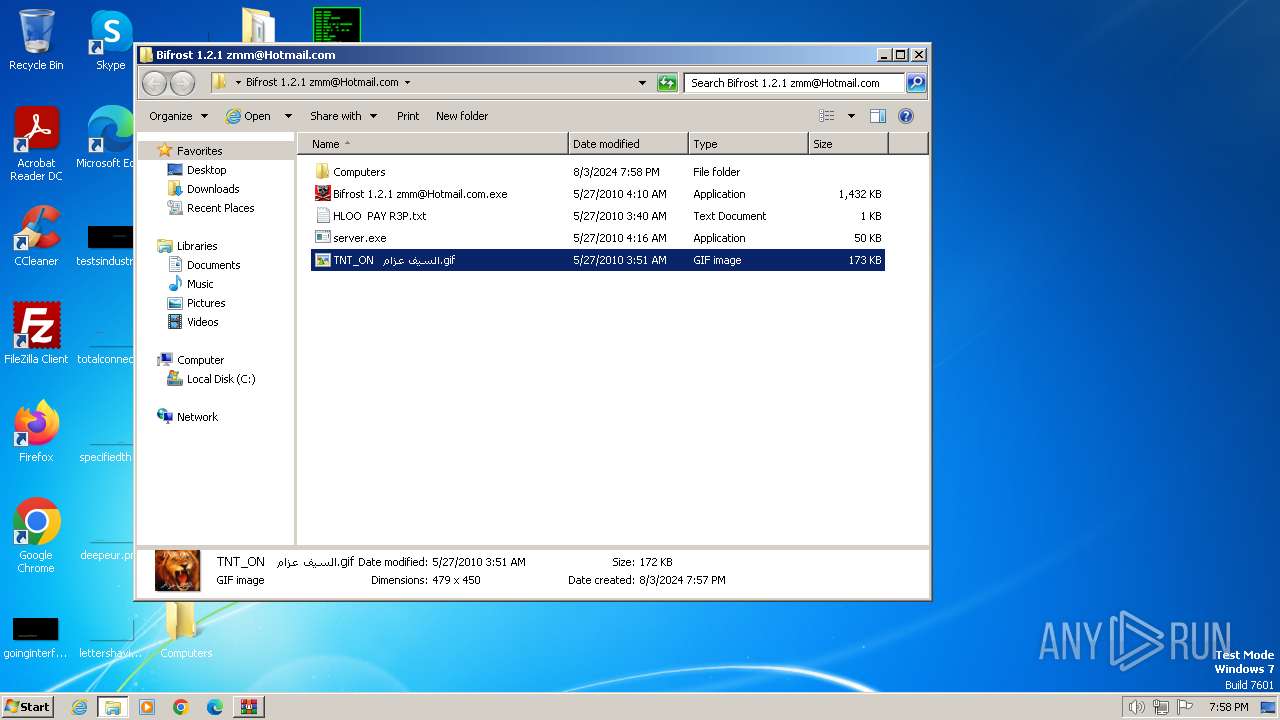
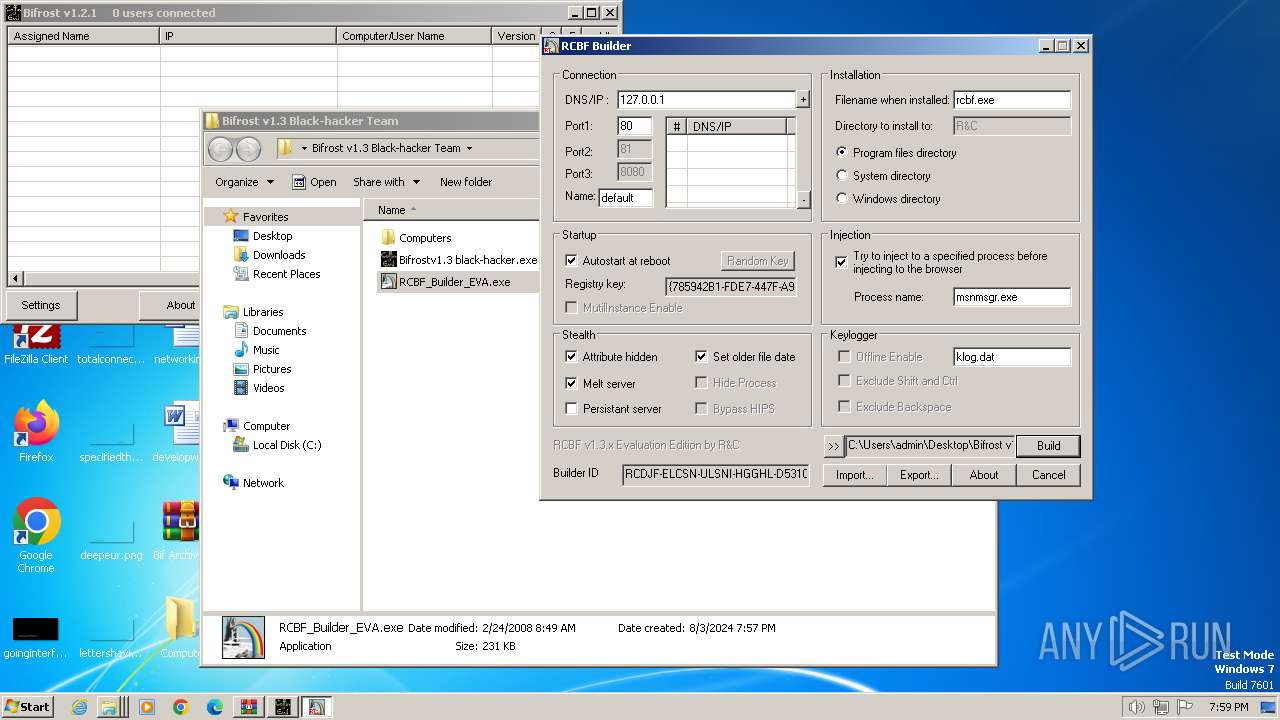
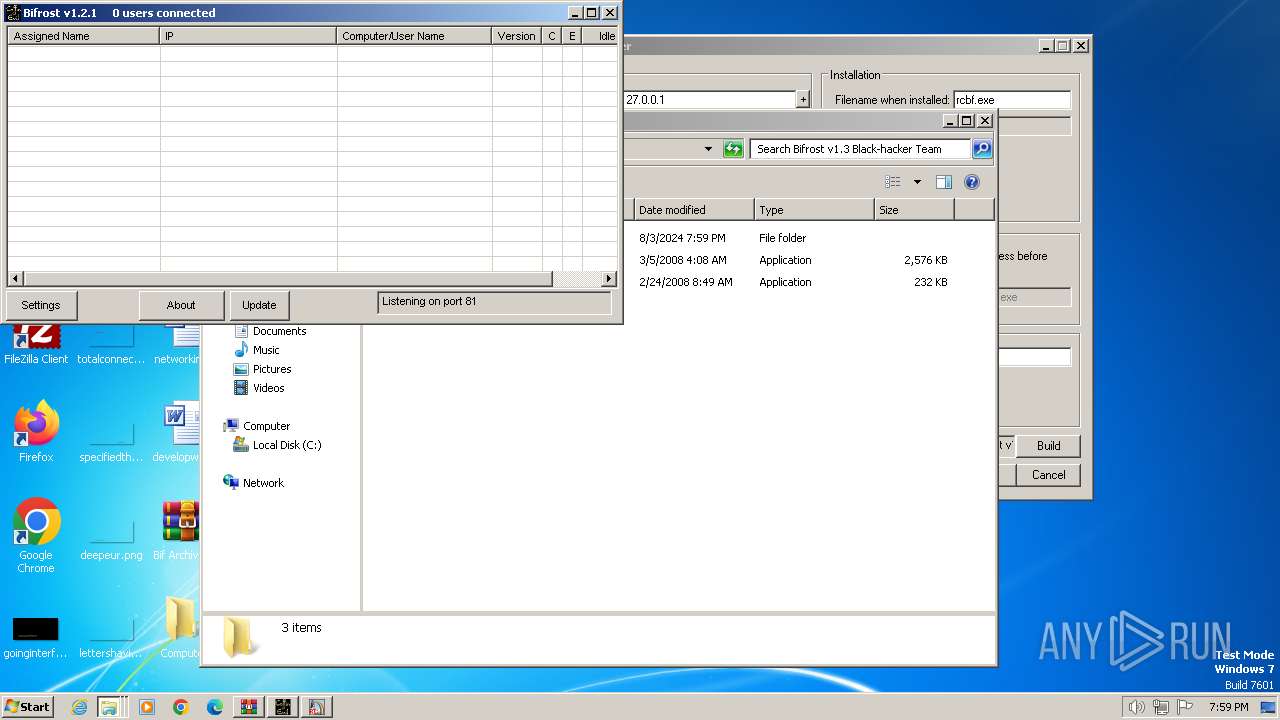
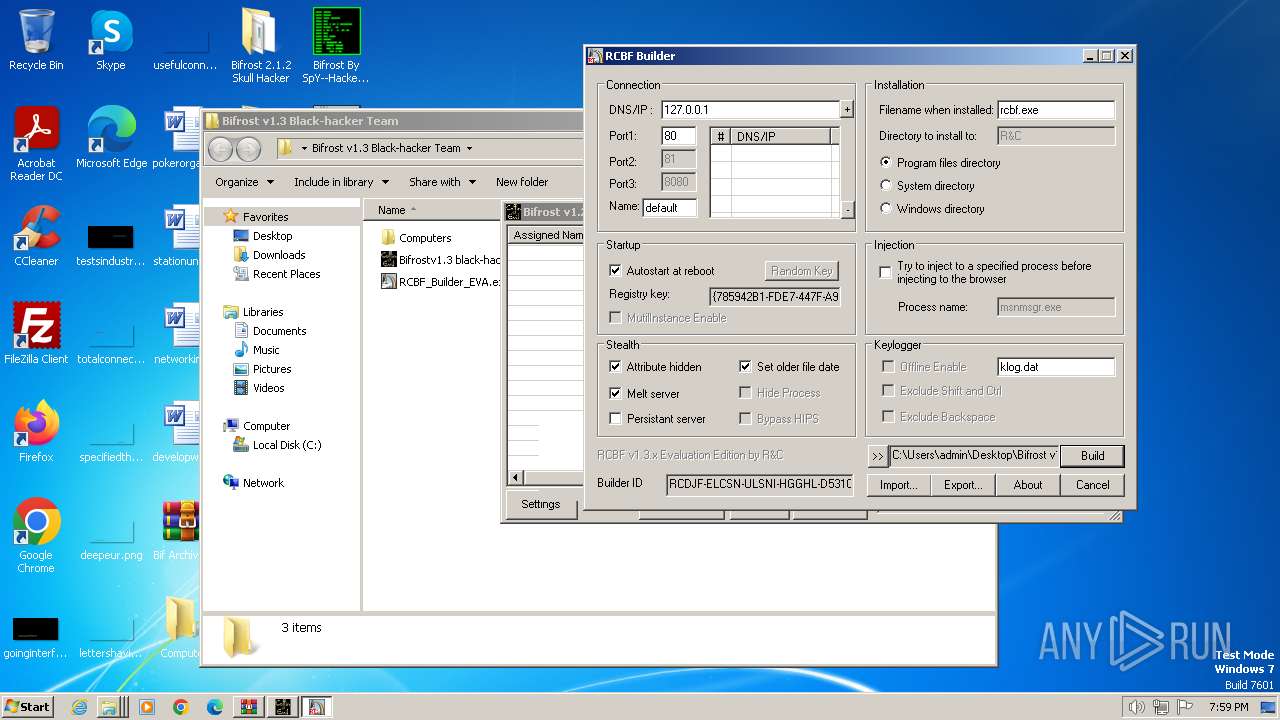
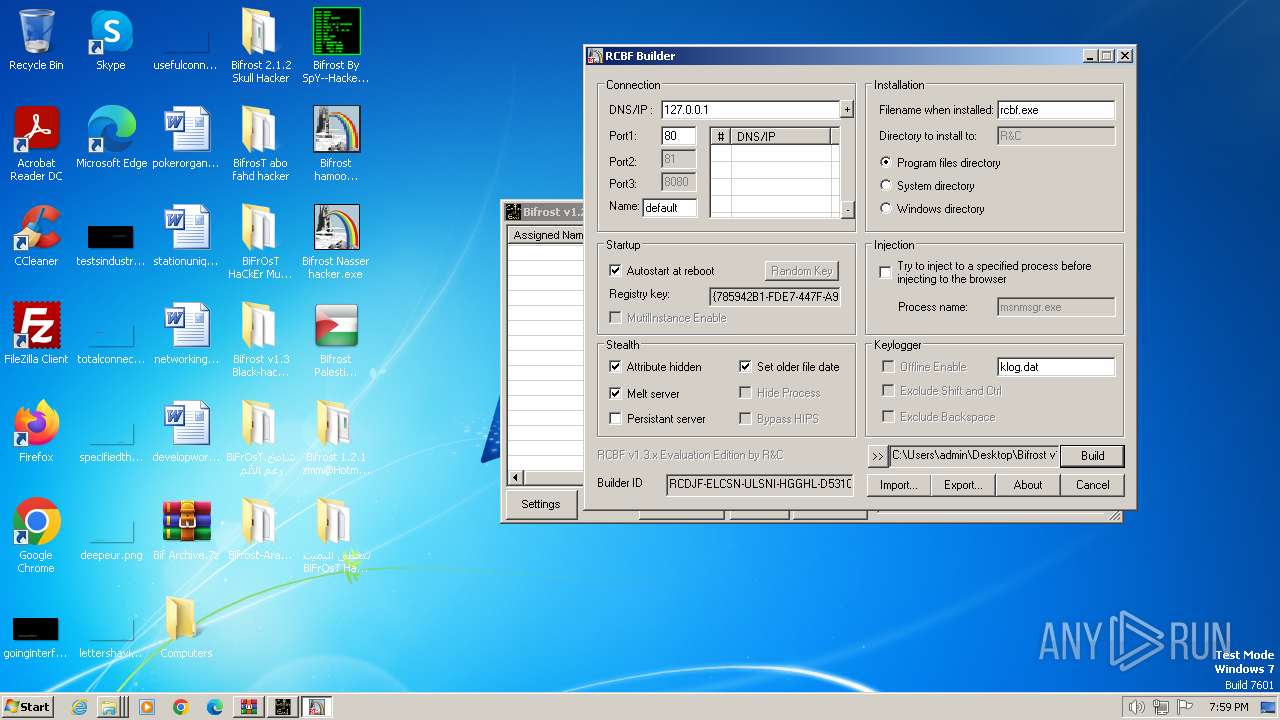
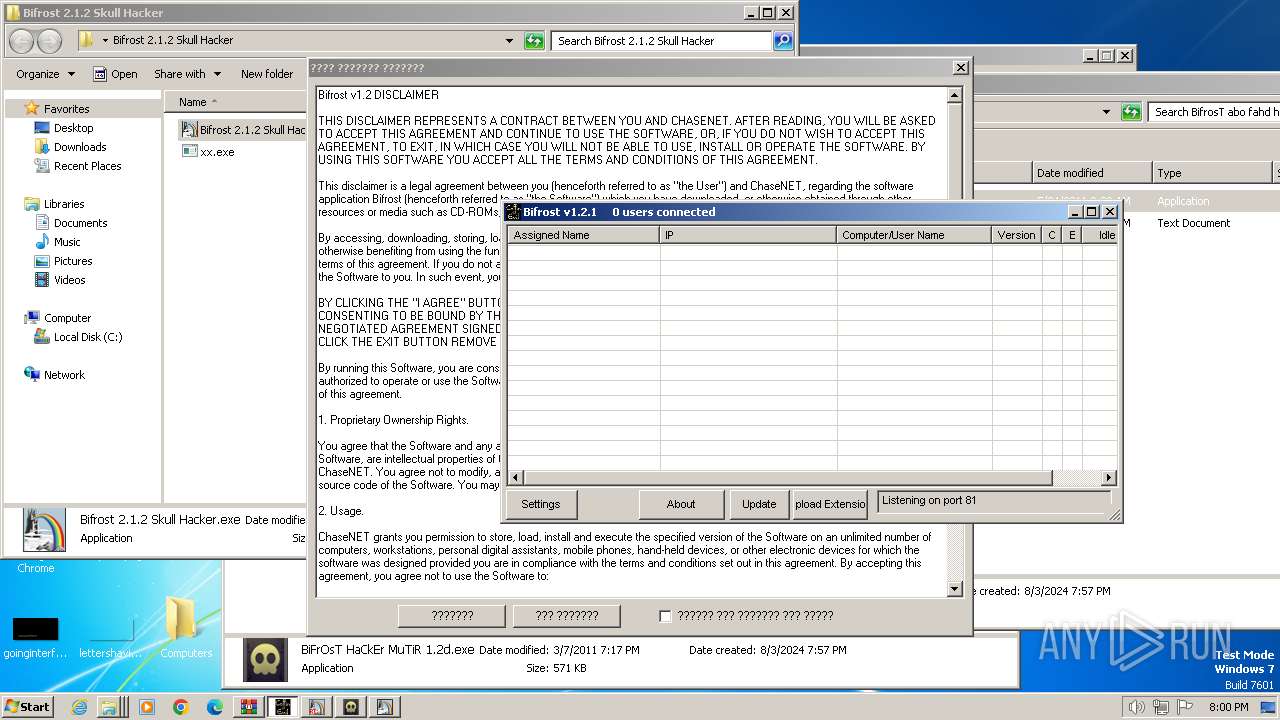
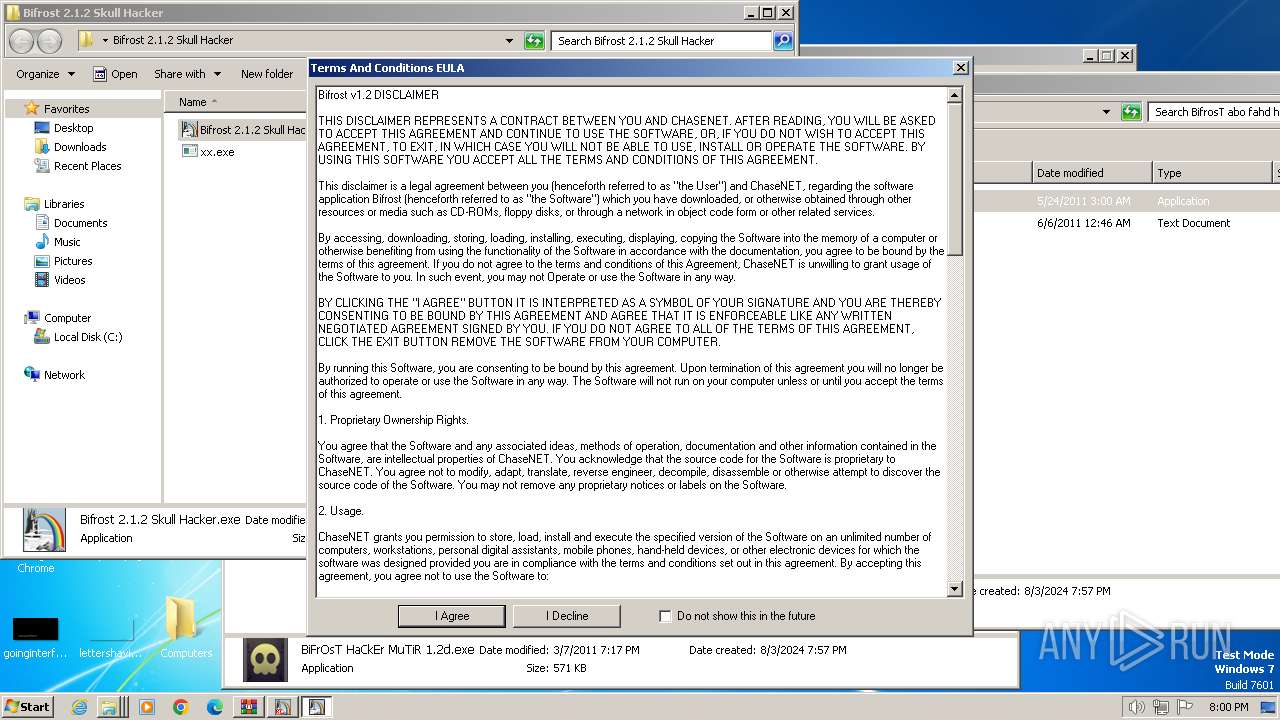
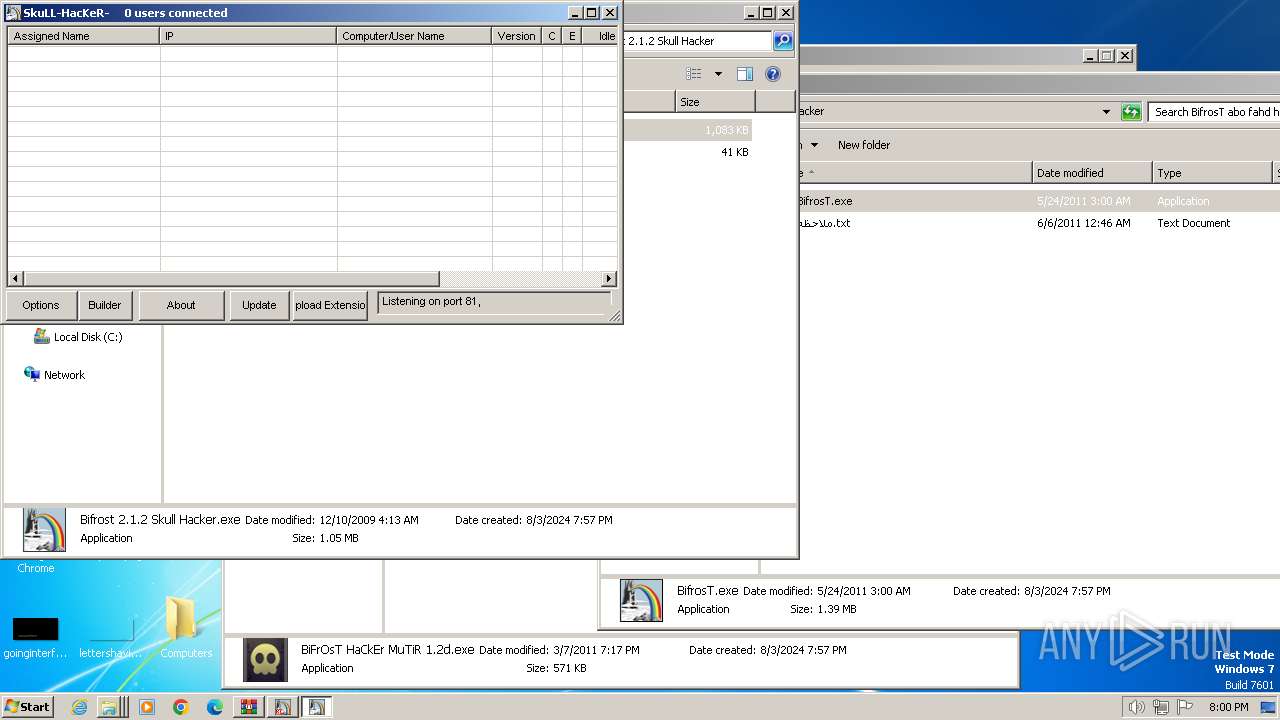
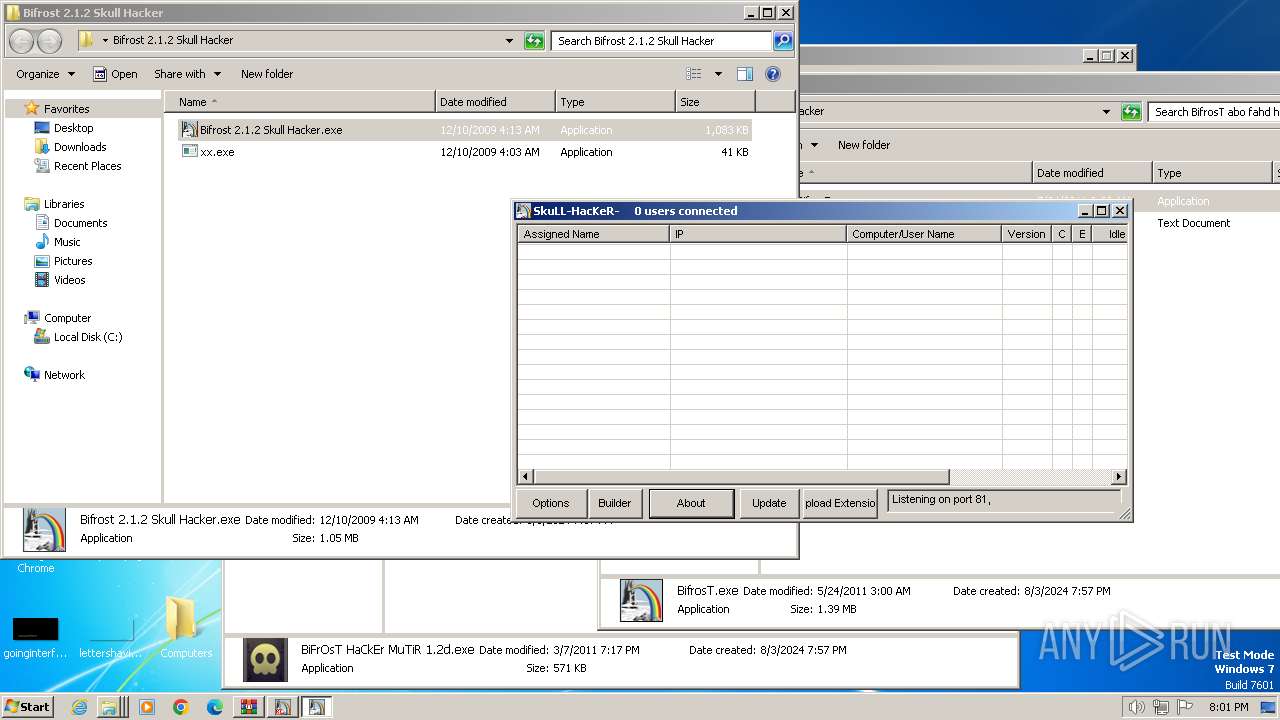
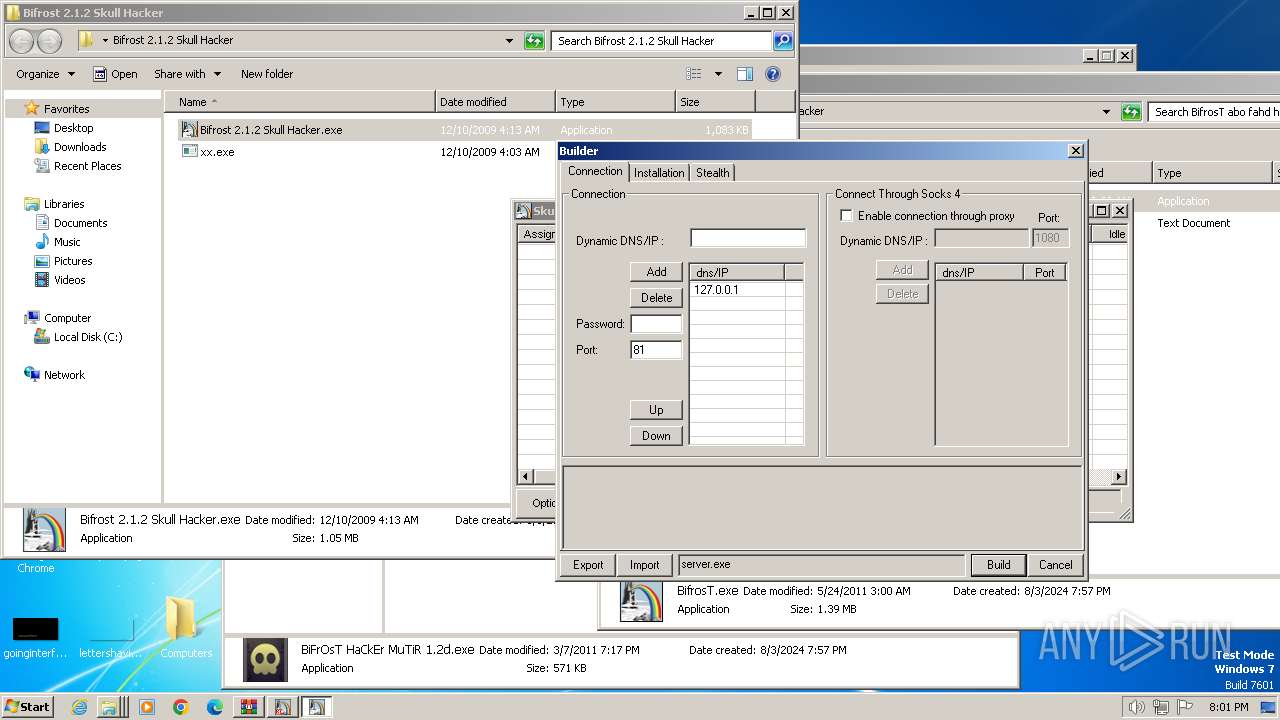
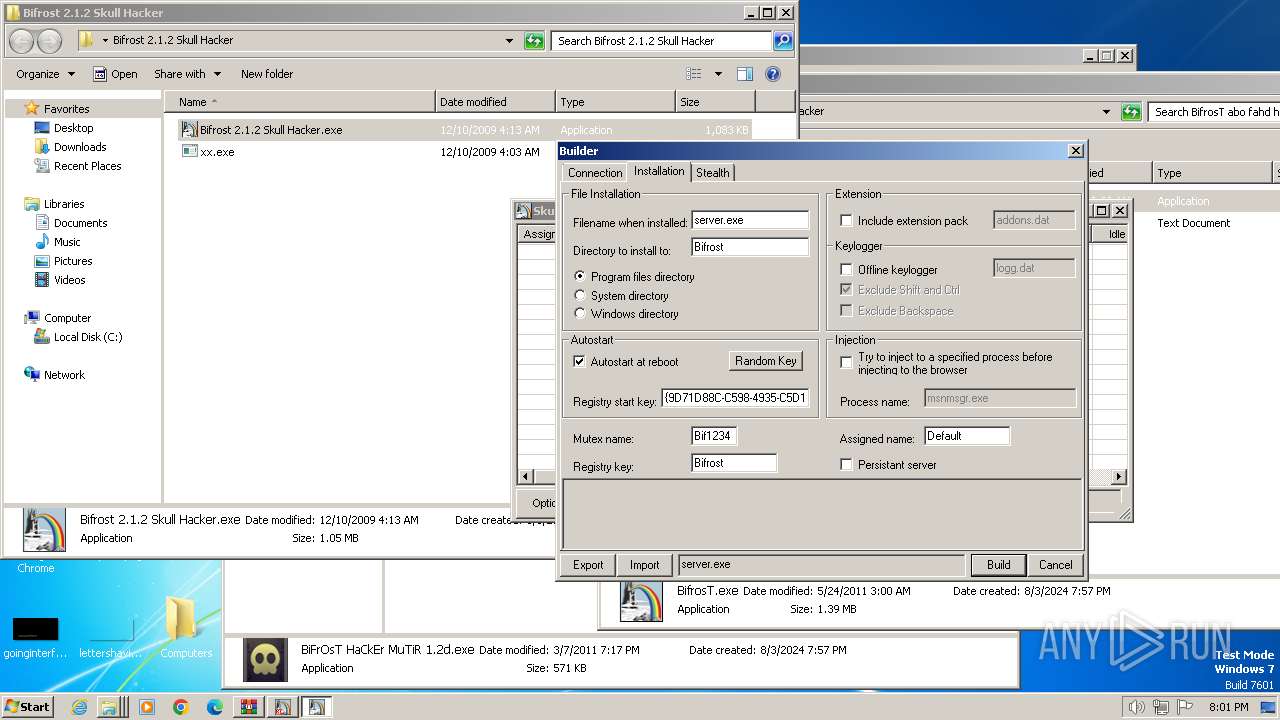
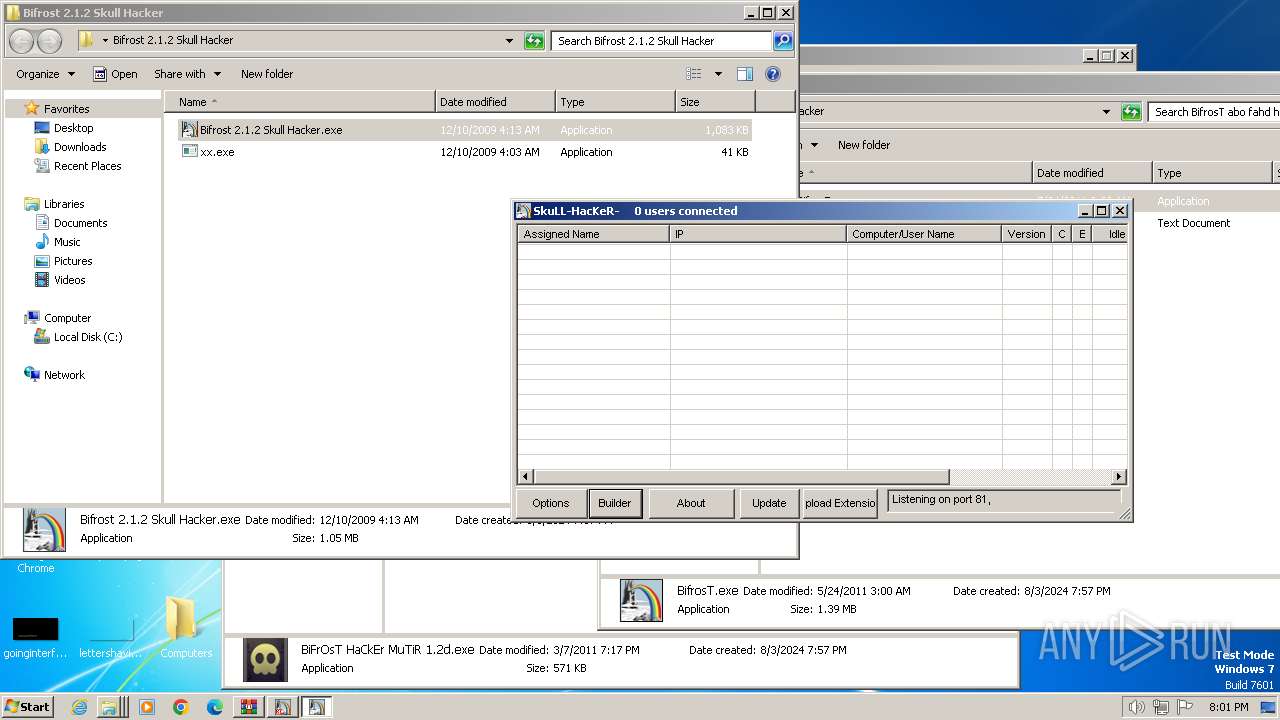
| File name: | Bif Archive.7z |
| Full analysis: | https://app.any.run/tasks/7e3926b1-22d5-4993-a126-e002cccec83c |
| Verdict: | Malicious activity |
| Threats: | A keylogger is a type of spyware that infects a system and has the ability to record every keystroke made on the device. This lets attackers collect personal information of victims, which may include their online banking credentials, as well as personal conversations. The most widespread vector of attack leading to a keylogger infection begins with a phishing email or link. Keylogging is also often present in remote access trojans as part of an extended set of malicious tools. |
| Analysis date: | August 03, 2024, 18:57:18 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-7z-compressed |
| File info: | 7-zip archive data, version 0.4 |
| MD5: | 5FEC5AC45E3A45B5C4E710B6EE3D87B8 |
| SHA1: | 18ECDABE47E7B63D02EDAE2F99627C523D6C4581 |
| SHA256: | A9F9B44D847B89500C7DA54CBFDBAD946792E3ED162DBF3A8355D308CA82D2CB |
| SSDEEP: | 98304:cequWYBaoffc7jOGT3vnXyBe4YYFpxq9J8RZAi9hR3V4uj9REeRamNtyn8IWbu0P:f478Qkj21B2eN5Hk4vqWsl/ |
MALICIOUS
Drops the executable file immediately after the start
- WinRAR.exe (PID: 1488)
- Bifrost By SpY--HackeR..exe (PID: 3184)
- Bifrost hamoody 1.2.1.exe (PID: 2376)
- server.exe (PID: 292)
- Borland.exe (PID: 2220)
- bifrost Nasser hacker2.exe (PID: 3652)
- Bifrost Nasser hacker.exe (PID: 3176)
- Bifrost Arabic 1.2.1.exe (PID: 3028)
- Bifrost 2.1.2 Skull Hacker.exe (PID: 740)
Changes the autorun value in the registry
- server.exe (PID: 292)
- msedge.exe (PID: 3220)
- explorer.exe (PID: 1296)
Runs injected code in another process
- server.exe (PID: 292)
- 43.exe (PID: 3004)
- one.exe (PID: 3320)
Application was injected by another process
- explorer.exe (PID: 1296)
SUSPICIOUS
Writes files like Keylogger logs
- explorer.exe (PID: 1296)
- Bifrost By SpY--HackeR..exe (PID: 3184)
- bifrost Nasser hacker2.exe (PID: 3652)
- Bifrost Arabic 1.2.1.exe (PID: 3028)
- Bifrost 2.1.2 Skull Hacker.exe (PID: 740)
Executable content was dropped or overwritten
- Bifrost By SpY--HackeR..exe (PID: 3184)
- server.exe (PID: 292)
- Borland.exe (PID: 2220)
- Bifrost hamoody 1.2.1.exe (PID: 2376)
- Bifrost Nasser hacker.exe (PID: 3176)
- bifrost Nasser hacker2.exe (PID: 3652)
- explorer.exe (PID: 1296)
- Bifrost Arabic 1.2.1.exe (PID: 3028)
- Bifrost 2.1.2 Skull Hacker.exe (PID: 740)
Starts CMD.EXE for commands execution
- Bifrost By SpY--HackeR..exe (PID: 3184)
The executable file from the user directory is run by the CMD process
- 0.exe (PID: 2704)
- 1.EXE (PID: 4080)
Reads the Internet Settings
- Bifrost hamoody 1.2.1.exe (PID: 2376)
- bifrost Nasser hacker2.exe (PID: 3652)
- Bifrost Nasser hacker.exe (PID: 3176)
- Bifrost Arabic 1.2.1.exe (PID: 3028)
Reads security settings of Internet Explorer
- Bifrost hamoody 1.2.1.exe (PID: 2376)
- Bifrost Nasser hacker.exe (PID: 3176)
- bifrost Nasser hacker2.exe (PID: 3652)
- Bifrost Arabic 1.2.1.exe (PID: 3028)
Creates file in the systems drive root
- msedge.exe (PID: 3220)
- Borland.exe (PID: 2220)
Application launched itself
- 43.exe (PID: 1460)
- one.exe (PID: 1944)
The process creates files with name similar to system file names
- explorer.exe (PID: 1296)
INFO
Executable content was dropped or overwritten
- WinRAR.exe (PID: 1488)
Reads security settings of Internet Explorer
- explorer.exe (PID: 1296)
Reads the Internet Settings
- explorer.exe (PID: 1296)
Reads the computer name
- wmpnscfg.exe (PID: 2552)
- Bifrost By SpY--HackeR..exe (PID: 3184)
- Bifrost hamoody 1.2.1.exe (PID: 2376)
- server.exe (PID: 292)
- 1.EXE (PID: 4080)
- Copy of bifrost 1.2.1 hamoody10 .exe (PID: 1076)
- msedge.exe (PID: 3220)
- Bifrost Nasser hacker.exe (PID: 3176)
- Borland.exe (PID: 2220)
- bifrost Nasser hacker2.exe (PID: 3652)
- 43.exe (PID: 1460)
- Bifrost Palestine 1.2.1.exe (PID: 1180)
- Bifrost 1.2.1 zmm@Hotmail.com.exe (PID: 2880)
- Bifrost Nasser Hacker.exe (PID: 3996)
- BiFrOsT HaCkEr MuTiR 1.2d.exe (PID: 2004)
- Bifrost Arabic 1.2.1.exe (PID: 3028)
- Bifrostv1.3 black-hacker.exe (PID: 3496)
- BifrosT.exe (PID: 3292)
- Bifrost 2.1.2 Skull Hacker.exe (PID: 740)
- Bifrost Dr.cratos.exe (PID: 3632)
- Bifrost 2.1.2 Skull Hacker.exe (PID: 936)
- BiFrOsT HaCkEr MuTiR 1.2d.exe (PID: 3484)
- Bifrost Dr.cratos.exe (PID: 2420)
Dropped object may contain TOR URL's
- WinRAR.exe (PID: 1488)
- Bifrost Arabic 1.2.1.exe (PID: 3028)
Manual execution by a user
- wmpnscfg.exe (PID: 2552)
- Bifrost By SpY--HackeR..exe (PID: 3184)
- Bifrost hamoody 1.2.1.exe (PID: 2376)
- iexplore.exe (PID: 2752)
- Bifrost Nasser hacker.exe (PID: 3176)
- iexplore.exe (PID: 2540)
- Bifrost Palestine 1.2.1.exe (PID: 1180)
- Bifrost 1.2.1 zmm@Hotmail.com.exe (PID: 2880)
- Bifrost Arabic 1.2.1.exe (PID: 3028)
- iexplore.exe (PID: 1580)
- BiFrOsT HaCkEr MuTiR 1.2d.exe (PID: 2004)
- iexplore.exe (PID: 3592)
- BiFrOsT.شامخ رغم الألم.EXE (PID: 3440)
- Bifrostv1.3 black-hacker.exe (PID: 3496)
- BiFrOsT HaCkEr MuTiR 1.2d.exe (PID: 3484)
- BifrosT.exe (PID: 3292)
- Bifrost 2.1.2 Skull Hacker.exe (PID: 740)
- RCBF_Builder_EVA.exe (PID: 2268)
- Bifrost 2.1.2 Skull Hacker.exe (PID: 936)
Checks supported languages
- wmpnscfg.exe (PID: 2552)
- Bifrost By SpY--HackeR..exe (PID: 3184)
- 0.exe (PID: 2704)
- 1.EXE (PID: 4080)
- Bifrost hamoody 1.2.1.exe (PID: 2376)
- server.exe (PID: 292)
- msedge.exe (PID: 3220)
- Copy of bifrost 1.2.1 hamoody10 .exe (PID: 1076)
- Bifrost Nasser hacker.exe (PID: 3176)
- Borland.exe (PID: 2220)
- 43.exe (PID: 1460)
- Bifrost Nasser Hacker.exe (PID: 3996)
- 43.exe (PID: 3004)
- bifrost Nasser hacker2.exe (PID: 3652)
- Bifrost Palestine 1.2.1.exe (PID: 1180)
- Bifrost 1.2.1 zmm@Hotmail.com.exe (PID: 2880)
- Bifrost Arabic 1.2.1.exe (PID: 3028)
- BiFrOsT HaCkEr MuTiR 1.2d.exe (PID: 2004)
- Bifrost 1.2.1.ExE (PID: 2712)
- one.exe (PID: 1944)
- one.exe (PID: 3320)
- BiFrOsT.شامخ رغم الألم.EXE (PID: 3440)
- Bifrostv1.3 black-hacker.exe (PID: 3496)
- BiFrOsT HaCkEr MuTiR 1.2d.exe (PID: 3484)
- BifrosT.exe (PID: 3292)
- Bifrost 2.1.2 Skull Hacker.exe (PID: 740)
- RCBF_Builder_EVA.exe (PID: 2268)
- Bifrost 2.1.2 Skull Hacker.exe (PID: 936)
- Bifrost Dr.cratos.exe (PID: 3632)
- xx.exe (PID: 4000)
- Bifrost Dr.cratos.exe (PID: 2420)
- xx.exe (PID: 3176)
Drops the executable file immediately after the start
- explorer.exe (PID: 1296)
Create files in a temporary directory
- Bifrost By SpY--HackeR..exe (PID: 3184)
- Bifrost hamoody 1.2.1.exe (PID: 2376)
- Bifrost Nasser hacker.exe (PID: 3176)
- bifrost Nasser hacker2.exe (PID: 3652)
- Bifrost Arabic 1.2.1.exe (PID: 3028)
- Bifrost 2.1.2 Skull Hacker.exe (PID: 740)
Reads the machine GUID from the registry
- Bifrost By SpY--HackeR..exe (PID: 3184)
- 1.EXE (PID: 4080)
- 43.exe (PID: 1460)
- Bifrost Palestine 1.2.1.exe (PID: 1180)
- Bifrost 1.2.1 zmm@Hotmail.com.exe (PID: 2880)
- Bifrost Nasser Hacker.exe (PID: 3996)
- BiFrOsT HaCkEr MuTiR 1.2d.exe (PID: 2004)
- BiFrOsT HaCkEr MuTiR 1.2d.exe (PID: 3484)
- Bifrost Dr.cratos.exe (PID: 3632)
Creates files or folders in the user directory
- explorer.exe (PID: 1296)
- one.exe (PID: 3320)
Application launched itself
- iexplore.exe (PID: 1580)
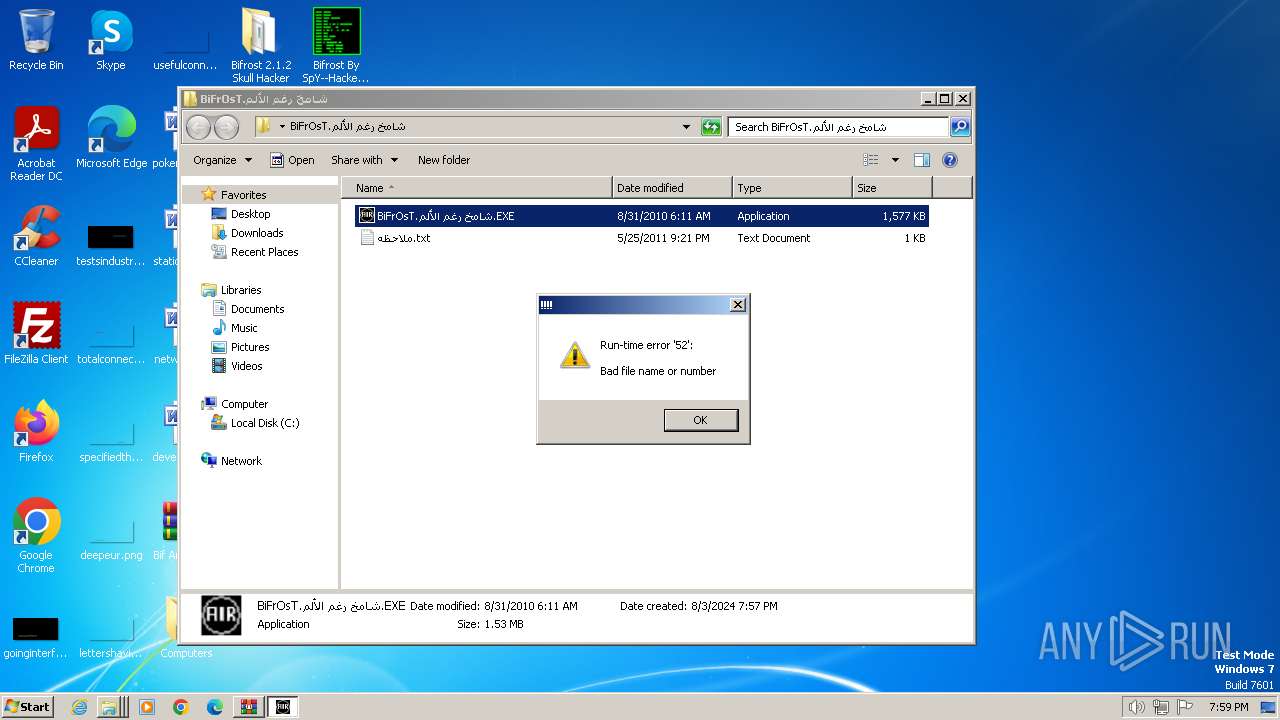
Failed to create an executable file in Windows directory
- explorer.exe (PID: 1296)
Aspack has been detected
- Bifrost 1.2.1.ExE (PID: 2712)
UPX packer has been detected
- Bifrost 1.2.1.ExE (PID: 2712)
- Bifrostv1.3 black-hacker.exe (PID: 3496)
Themida protector has been detected
- Bifrostv1.3 black-hacker.exe (PID: 3496)
Reads mouse settings
- Bifrost 2.1.2 Skull Hacker.exe (PID: 740)
- Bifrost 2.1.2 Skull Hacker.exe (PID: 936)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .7z | | | 7-Zip compressed archive (v0.4) (57.1) |
|---|---|---|
| .7z | | | 7-Zip compressed archive (gen) (42.8) |
Total processes
105
Monitored processes
41
Malicious processes
8
Suspicious processes
5
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
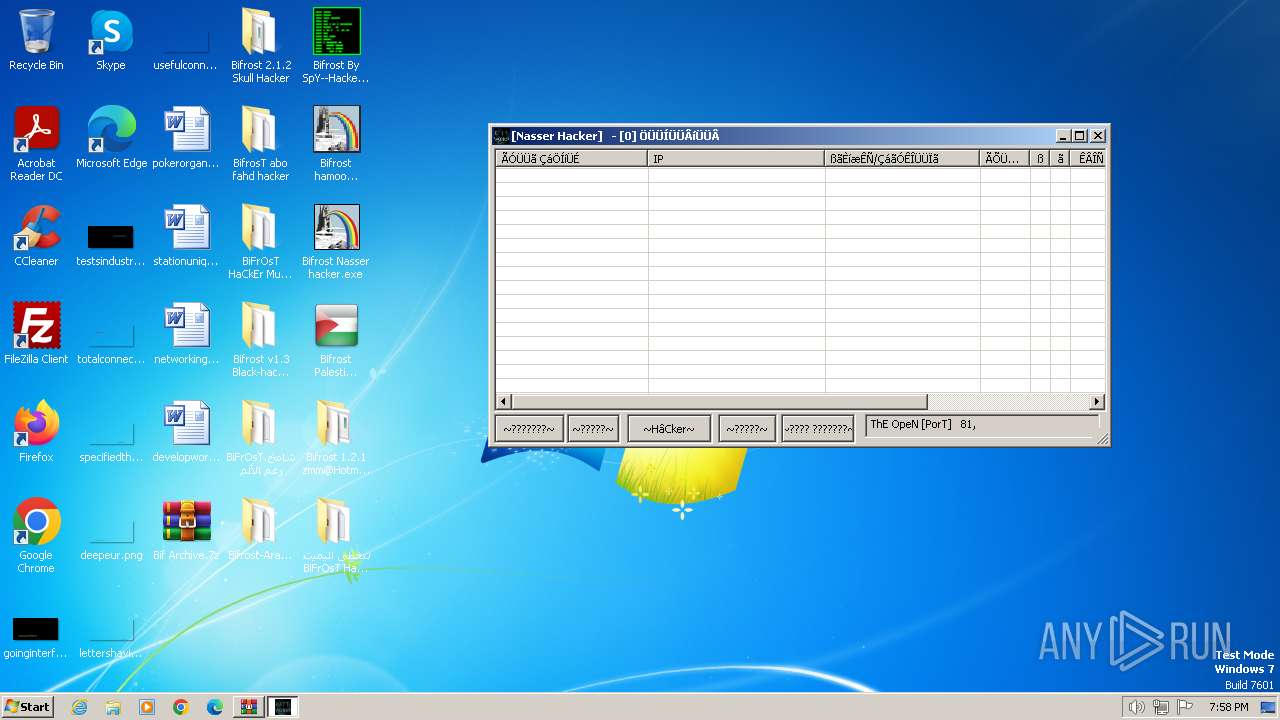
| 292 | "C:\Users\admin\AppData\Local\Temp\server.exe" | C:\Users\admin\AppData\Local\Temp\server.exe | Bifrost hamoody 1.2.1.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 740 | "C:\Users\admin\Desktop\Bifrost 2.1.2 Skull Hacker\Bifrost 2.1.2 Skull Hacker.exe" | C:\Users\admin\Desktop\Bifrost 2.1.2 Skull Hacker\Bifrost 2.1.2 Skull Hacker.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Version: 3, 3, 0, 0 Modules
| |||||||||||||||
| 828 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:1580 CREDAT:144385 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | — | iexplore.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 936 | "C:\Users\admin\Desktop\Bifrost 2.1.2 Skull Hacker\Bifrost 2.1.2 Skull Hacker.exe" | C:\Users\admin\Desktop\Bifrost 2.1.2 Skull Hacker\Bifrost 2.1.2 Skull Hacker.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Version: 3, 3, 0, 0 Modules
| |||||||||||||||
| 1076 | "C:\Users\admin\AppData\Local\Temp\Copy of bifrost 1.2.1 hamoody10 .exe" | C:\Users\admin\AppData\Local\Temp\Copy of bifrost 1.2.1 hamoody10 .exe | — | Bifrost hamoody 1.2.1.exe | |||||||||||
User: admin Company: http://as7apcool.com/vb Integrity Level: HIGH Description: by hamoody Exit code: 20 Version: 1, 2, 1, 0 Modules
| |||||||||||||||
| 1180 | "C:\Users\admin\Desktop\Bifrost Palestine 1.2.1.exe" | C:\Users\admin\Desktop\Bifrost Palestine 1.2.1.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Description: Palestine Exit code: 20 Version: 1, 2, 1, 0 Modules
| |||||||||||||||
| 1296 | C:\Windows\Explorer.EXE | C:\Windows\explorer.exe | — | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1460 | "C:\Users\admin\AppData\Local\Temp\43.exe" | C:\Users\admin\AppData\Local\Temp\43.exe | — | Bifrost Nasser hacker.exe | |||||||||||
User: admin Company: السيّد العلوي Integrity Level: HIGH Description: السيّد العلوي Exit code: 0 Version: 444.666.0888 Modules
| |||||||||||||||
| 1488 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\Desktop\Bif Archive.7z" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
| 1580 | "C:\Program Files\Internet Explorer\iexplore.exe" C:\Users\admin\Desktop\Bifrost 1.2.1 zmm@Hotmail.com\TNT_ON السيف عزام.gif | C:\Program Files\Internet Explorer\iexplore.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 1 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
Total events
66 136
Read events
65 141
Write events
965
Delete events
30
Modification events
| (PID) Process: | (1296) explorer.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Action Center\Checks\{C8E6F269-B90A-4053-A3BE-499AFCEC98C4}.check.0 |
| Operation: | write | Name: | CheckSetting |
Value: 01000000D08C9DDF0115D1118C7A00C04FC297EB010000000A82066E518DA4419A50D76DC5E2963D000000000200000000001066000000010000200000002F4B8503CBA20BE874A605D8003FE178F679DF0393BE79FDF5A191095CB99EA6000000000E800000000200002000000097BB53AD5629330F8B331C9969AA328010E5AF1943A7804E083BF62BAB77DB2C30000000702012A038927C94533A95931A11B98C2E6BBCFD79690C71494AFDA88C21B9EDA09238F3422D174AFAE7DF0BBDE88A4640000000243D90FF960F2B7749D69C803AE3D6732B49B5050250A56074D2AA3FBCC4C33C48675967F0E8BCDF236516AE4FC768D0F9716B7EB73C093D7E4D59C5C3C26B35 | |||
| (PID) Process: | (1488) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (1488) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (1488) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (1488) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\phacker.zip | |||
| (PID) Process: | (1488) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (1488) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\curl-8.5.0_1-win32-mingw.zip | |||
| (PID) Process: | (1488) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\Bif Archive.7z | |||
| (PID) Process: | (1296) explorer.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\FileExts\.7z\OpenWithList |
| Operation: | write | Name: | a |
Value: WinRAR.exe | |||
| (PID) Process: | (1296) explorer.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\FileExts\.7z\OpenWithList |
| Operation: | write | Name: | MRUList |
Value: a | |||
Executable files
36
Suspicious files
16
Text files
9
Unknown types
3
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1488 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa1488.27603\Bifrost 1.2.1 zmm@Hotmail.com\TNT_ON السيف عزام.gif | image | |
MD5:09EAB44C5717713EC8DD01A4D621018F | SHA256:0FB97874DB6980D9192E80003C7E5CE4730B600619A0344B35797D2935E7A8B0 | |||
| 1296 | explorer.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\AutomaticDestinations\290532160612e071.automaticDestinations-ms | binary | |
MD5:7BB5249C94A535CABBED5A2194EFAB46 | SHA256:75CD2314C88E9D233A64C267DACE660626E302284B2647390E76B8C86D6251F9 | |||
| 1488 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa1488.27603\تتخطى اليميت BiFrOsT HaCkEr MuTiR 1.2dX\ملاحظه.txt | text | |
MD5:220608329962C35DD89AA92B9C12FEEF | SHA256:B0F49EE90AB5E8CECDBDFB46331ECD9A2E31D06D6F71A4C2238038CAC16E464A | |||
| 1488 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa1488.27603\BiFrOsT HaCkEr MuTiR 1.2d\About.txt | text | |
MD5:3F961C8EA480DDBBEA2F0125591EADC2 | SHA256:8252F1EF6B7DD152886B43008C45BCBA67BA2F5B3CEE99D677009602ED311689 | |||
| 1488 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa1488.27603\Bifrost 2.1.2 Skull Hacker\Bifrost 2.1.2 Skull Hacker.exe | executable | |
MD5:498572C51FEA8019D228D4E4E8DB9D1E | SHA256:7CA4923FC92CBD0731D426A94321E889AA1C395D1CFC5980A2CC39C3724A2678 | |||
| 1488 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa1488.27603\BifrosT abo fahd hacker\ملاحظه.txt | text | |
MD5:49A0190345030BD3989C969E3D0B1FA3 | SHA256:B988C88C694B02E30FA15736352A540D1FC665604686C231C7900FB5D1CAC3E5 | |||
| 1488 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa1488.27603\BiFrOsT.شامخ رغم الألم\ملاحظه.txt | text | |
MD5:692B2D14C34102CBB9863B98FF65DC8D | SHA256:A194B8BB432645CB6E5D9DFEF8490EB0DA448E9925C50E4D6BF7D6F14C47A022 | |||
| 1488 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa1488.27603\Bifrost 1.2.1 zmm@Hotmail.com\server.exe | executable | |
MD5:3CA47E2C1C05F0AF250C51B150B9796D | SHA256:65B5C64B922124ACBCF92E24F2E10A44122FDDFDA57FBE97180C913903A42382 | |||
| 1296 | explorer.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\Bif Archive.7z.lnk | binary | |
MD5:DC71BDD894C9B93048D878BD58B04BA7 | SHA256:908889BB30B50136E6ED4C47C91C1C0EBCB551C53E5895FD876D4DC8BF06D90D | |||
| 1296 | explorer.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\AutomaticDestinations\1b4dd67f29cb1962.automaticDestinations-ms | binary | |
MD5:1D3A3A31B95F6075D913F01604D2C02D | SHA256:7B8807E14DEF8E119C2F7F492FE3B93827A94B210BCAED73736E4ED6A34214F9 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
5
TCP/UDP connections
16
DNS requests
12
Threats
3
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1372 | svchost.exe | GET | 304 | 23.50.131.196:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?33775f6043c93e33 | unknown | — | — | whitelisted |
1372 | svchost.exe | GET | 200 | 23.48.23.164:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
1372 | svchost.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
1060 | svchost.exe | GET | 304 | 199.232.214.172:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?8f69642324cc87bd | unknown | — | — | whitelisted |
1580 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 224.0.0.252:5355 | — | — | — | whitelisted |
— | — | 239.255.255.250:3702 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1372 | svchost.exe | 51.124.78.146:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
1060 | svchost.exe | 224.0.0.252:5355 | — | — | — | whitelisted |
1372 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
1372 | svchost.exe | 23.50.131.196:80 | ctldl.windowsupdate.com | Akamai International B.V. | DE | unknown |
1372 | svchost.exe | 23.48.23.164:80 | crl.microsoft.com | Akamai International B.V. | DE | unknown |
1372 | svchost.exe | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
ctldl.windowsupdate.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
zx3500.no-ip.biz |
| unknown |
nassersalem6.no-ip.org |
| malicious |
al7rbi.no-ip.info |
| unknown |
iecvlist.microsoft.com |
| whitelisted |
r20swj13mr.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1060 | svchost.exe | Misc activity | ET INFO DYNAMIC_DNS Query to a Suspicious no-ip Domain |
1060 | svchost.exe | Misc activity | ET INFO DYNAMIC_DNS Query to a Suspicious no-ip Domain |
1060 | svchost.exe | Misc activity | ET INFO DYNAMIC_DNS Query to a Suspicious no-ip Domain |
Process | Message |
|---|---|
Bifrostv1.3 black-hacker.exe |
%s------------------------------------------------
--- Themida Professional ---
--- (c)2007 Oreans Technologies ---
------------------------------------------------
|