| File name: | Computer32.exe |
| Full analysis: | https://app.any.run/tasks/5536c787-6dc1-407e-9441-8cb7bb0533f7 |
| Verdict: | Malicious activity |
| Threats: | Lumma is an information stealer, developed using the C programming language. It is offered for sale as a malware-as-a-service, with several plans available. It usually targets cryptocurrency wallets, login credentials, and other sensitive information on a compromised system. The malicious software regularly gets updates that improve and expand its functionality, making it a serious stealer threat. |
| Analysis date: | June 01, 2025, 11:02:13 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32+ executable (console) x86-64, for MS Windows, 7 sections |
| MD5: | 6B1E15C1AF201DF2185CF0BA9B927832 |
| SHA1: | A89002C4555A28FE761A84783BE8D91C4E498152 |
| SHA256: | A9DA31D5C92E14751C3A976B654CCBB24091CBC0242BD17352251A30CDFCDD61 |
| SSDEEP: | 98304:k/0CeAb/ncfRkzKVfq7AnYRO4Y6ZhkDQet54netUjZUj0vB+kzK/7ueSnKHdFG1n:bvfkfxXwE1MUr881mwU/kiG7k5+G |
MALICIOUS
LUMMA has been detected (SURICATA)
- svchost.exe (PID: 2196)
Stealers network behavior
- svchost.exe (PID: 2196)
SUSPICIOUS
The process drops C-runtime libraries
- Computer32.exe (PID: 7232)
- Computer32.exe (PID: 5864)
- Computer32.exe (PID: 3132)
- Computer32.exe (PID: 7848)
- Computer32.exe (PID: 6644)
Process drops legitimate windows executable
- Computer32.exe (PID: 7232)
- Computer32.exe (PID: 5864)
- Computer32.exe (PID: 3132)
- Computer32.exe (PID: 7848)
- Computer32.exe (PID: 6644)
Executable content was dropped or overwritten
- Computer32.exe (PID: 7232)
- Computer32.exe (PID: 5864)
- Computer32.exe (PID: 3132)
- Computer32.exe (PID: 7848)
- Computer32.exe (PID: 6644)
Process drops python dynamic module
- Computer32.exe (PID: 7232)
- Computer32.exe (PID: 5864)
- Computer32.exe (PID: 3132)
- Computer32.exe (PID: 7848)
- Computer32.exe (PID: 6644)
Application launched itself
- Computer32.exe (PID: 7232)
- Computer32.exe (PID: 5864)
- Computer32.exe (PID: 3132)
- Computer32.exe (PID: 7848)
- Computer32.exe (PID: 6644)
Loads Python modules
- Computer32.exe (PID: 7288)
- Computer32.exe (PID: 4200)
- Computer32.exe (PID: 6660)
- Computer32.exe (PID: 2420)
- Computer32.exe (PID: 4700)
Contacting a server suspected of hosting an CnC
- svchost.exe (PID: 2196)
INFO
Reads the computer name
- Computer32.exe (PID: 7232)
- Computer32.exe (PID: 7288)
- Computer32.exe (PID: 5864)
- Computer32.exe (PID: 3132)
- Computer32.exe (PID: 4200)
- Computer32.exe (PID: 6660)
- Computer32.exe (PID: 7848)
- Computer32.exe (PID: 2420)
- Computer32.exe (PID: 6644)
- Computer32.exe (PID: 4700)
Checks supported languages
- Computer32.exe (PID: 7232)
- Computer32.exe (PID: 7288)
- Computer32.exe (PID: 5864)
- Computer32.exe (PID: 4200)
- Computer32.exe (PID: 3132)
- Computer32.exe (PID: 6660)
- Computer32.exe (PID: 7848)
- Computer32.exe (PID: 2420)
- Computer32.exe (PID: 6644)
- Computer32.exe (PID: 4700)
The sample compiled with english language support
- Computer32.exe (PID: 7232)
- Computer32.exe (PID: 5864)
- Computer32.exe (PID: 3132)
- Computer32.exe (PID: 7848)
- Computer32.exe (PID: 6644)
Create files in a temporary directory
- Computer32.exe (PID: 7232)
- Computer32.exe (PID: 5864)
- Computer32.exe (PID: 3132)
- Computer32.exe (PID: 7848)
- Computer32.exe (PID: 6644)
Checks proxy server information
- Computer32.exe (PID: 7288)
- Computer32.exe (PID: 4200)
- Computer32.exe (PID: 6660)
- Computer32.exe (PID: 2420)
- Computer32.exe (PID: 4700)
- slui.exe (PID: 3032)
Attempting to use instant messaging service
- svchost.exe (PID: 2196)
- Computer32.exe (PID: 4200)
Manual execution by a user
- Computer32.exe (PID: 5864)
- Computer32.exe (PID: 3132)
- firefox.exe (PID: 6960)
- Computer32.exe (PID: 7848)
- Computer32.exe (PID: 6644)
Application launched itself
- firefox.exe (PID: 5404)
- firefox.exe (PID: 6960)
Reads the software policy settings
- slui.exe (PID: 3032)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win64 Executable (generic) (87.3) |
|---|---|---|
| .exe | | | Generic Win/DOS Executable (6.3) |
| .exe | | | DOS Executable Generic (6.3) |
EXIF
EXE
| MachineType: | AMD AMD64 |
|---|---|
| TimeStamp: | 2025:06:01 10:46:28+00:00 |
| ImageFileCharacteristics: | Executable, Large address aware |
| PEType: | PE32+ |
| LinkerVersion: | 14.43 |
| CodeSize: | 178688 |
| InitializedDataSize: | 153600 |
| UninitializedDataSize: | - |
| EntryPoint: | 0xc380 |
| OSVersion: | 6 |
| ImageVersion: | - |
| SubsystemVersion: | 6 |
| Subsystem: | Windows command line |
Total processes
144
Monitored processes
28
Malicious processes
6
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 132 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel=4688 -parentBuildID 20240213221259 -sandboxingKind 0 -prefsHandle 4840 -prefMapHandle 4844 -prefsLen 36588 -prefMapSize 244583 -win32kLockedDown -appDir "C:\Program Files\Mozilla Firefox\browser" - {257dd991-5b39-4ca2-a2cf-353235d3309b} 5404 "\\.\pipe\gecko-crash-server-pipe.5404" 11b6107b710 utility | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Exit code: 1 Version: 123.0 Modules
| |||||||||||||||
| 1052 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel=4244 -childID 2 -isForBrowser -prefsHandle 4236 -prefMapHandle 4232 -prefsLen 36588 -prefMapSize 244583 -jsInitHandle 1420 -jsInitLen 235124 -parentBuildID 20240213221259 -win32kLockedDown -appDir "C:\Program Files\Mozilla Firefox\browser" - {cdd07492-c991-4390-89c5-0b0b0a3e9cbe} 5404 "\\.\pipe\gecko-crash-server-pipe.5404" 11b5e6e1690 tab | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Exit code: 0 Version: 123.0 Modules
| |||||||||||||||
| 1452 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel=5280 -childID 4 -isForBrowser -prefsHandle 5272 -prefMapHandle 5268 -prefsLen 31243 -prefMapSize 244583 -jsInitHandle 1420 -jsInitLen 235124 -parentBuildID 20240213221259 -win32kLockedDown -appDir "C:\Program Files\Mozilla Firefox\browser" - {3c0b8aa0-a519-4495-b283-f4d7bcfb2fc3} 5404 "\\.\pipe\gecko-crash-server-pipe.5404" 11b5d579310 tab | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Exit code: 0 Version: 123.0 Modules
| |||||||||||||||
| 2196 | C:\WINDOWS\system32\svchost.exe -k NetworkService -p -s Dnscache | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2240 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel=5400 -childID 5 -isForBrowser -prefsHandle 5392 -prefMapHandle 5164 -prefsLen 31243 -prefMapSize 244583 -jsInitHandle 1420 -jsInitLen 235124 -parentBuildID 20240213221259 -win32kLockedDown -appDir "C:\Program Files\Mozilla Firefox\browser" - {0fbcbd39-693f-4c49-97d5-5c24a77bb7b3} 5404 "\\.\pipe\gecko-crash-server-pipe.5404" 11b5d579850 tab | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Exit code: 0 Version: 123.0 Modules
| |||||||||||||||
| 2420 | "C:\Users\admin\Desktop\Computer32.exe" | C:\Users\admin\Desktop\Computer32.exe | Computer32.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 3032 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3132 | "C:\Users\admin\Desktop\Computer32.exe" | C:\Users\admin\Desktop\Computer32.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 4200 | "C:\Users\admin\Desktop\Computer32.exe" | C:\Users\admin\Desktop\Computer32.exe | Computer32.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 4208 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | Computer32.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
21 546
Read events
21 507
Write events
38
Delete events
1
Modification events
| (PID) Process: | (5404) firefox.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Mozilla\Firefox\DllPrefetchExperiment |
| Operation: | write | Name: | C:\Program Files\Mozilla Firefox\firefox.exe |
Value: 0 | |||
| (PID) Process: | (5404) firefox.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\BagMRU |
| Operation: | write | Name: | NodeSlots |
Value: 02020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202 | |||
| (PID) Process: | (5404) firefox.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\BagMRU |
| Operation: | write | Name: | MRUListEx |
Value: 04000000030000000E00000000000000100000000F0000000C0000000D0000000B000000050000000A000000090000000800000001000000070000000600000002000000FFFFFFFF | |||
| (PID) Process: | (5404) firefox.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\BagMRU\4 |
| Operation: | write | Name: | MRUListEx |
Value: 010000000000000004000000050000000200000003000000FFFFFFFF | |||
| (PID) Process: | (5404) firefox.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\Bags\34\Shell |
| Operation: | write | Name: | SniffedFolderType |
Value: Generic | |||
| (PID) Process: | (5404) firefox.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer |
| Operation: | write | Name: | GlobalAssocChangedCounter |
Value: 114 | |||
| (PID) Process: | (5404) firefox.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\Modules\NavPane |
| Operation: | write | Name: | ExpandedState |
Value: 12000000160014001F80CB859F6720028040B29B5540CC05AAB60000010000004D0000001C00000031535053A66A63283D95D211B5D600C04FD918D0000000002D00000031535053357EC777E31B5043A48C7563D727776D1100000002000000000B000000FFFF00000000000000000000160014001F60983FFBB4EAC18D42A78AD1F5659CBA930000010000004D0000001C00000031535053A66A63283D95D211B5D600C04FD918D0000000002D00000031535053357EC777E31B5043A48C7563D727776D1100000002000000000B000000FFFF00000000000000000000160014001F7840F05F6481501B109F0800AA002F954E0000010000004D0000001C00000031535053A66A63283D95D211B5D600C04FD918D0000000002D00000031535053357EC777E31B5043A48C7563D727776D1100000002000000000B000000000000000000000000000000160014001F706806EE260AA0D7449371BEB064C986830000010000004D0000001C00000031535053A66A63283D95D211B5D600C04FD918D0000000002D00000031535053357EC777E31B5043A48C7563D727776D1100000002000000000B000000FFFF00000000000000000000160014001F580D1A2CF021BE504388B07367FC96EF3C0000010000004D0000001C00000031535053A66A63283D95D211B5D600C04FD918D0000000002D00000031535053357EC777E31B5043A48C7563D727776D1100000002000000000B000000000000000000000000000000160014001F5425481E03947BC34DB131E946B44C8DD50000010000004D0000001C00000031535053A66A63283D95D211B5D600C04FD918D0000000002D00000031535053357EC777E31B5043A48C7563D727776D1100000002000000000B000000000000000000000000000000160014001F50E04FD020EA3A6910A2D808002B30309D0000010000004D0000001C00000031535053A66A63283D95D211B5D600C04FD918D0000000002D00000031535053357EC777E31B5043A48C7563D727776D1100000002000000000B000000FFFF000000000000000000003C003A001F44471A0359723FA74489C55595FE6B30EE260001002600EFBE1000000034E9025AA9B7D80155EC262BAAB7D8018F3827B5B0B7D80114000000010000004D0000001C00000031535053A66A63283D95D211B5D600C04FD918D0000000002D00000031535053357EC777E31B5043A48C7563D727776D1100000002000000000B000000FFFF000000000000000000003C003A001F42665C8D01334507439B53224DE2ED1FE6260001002600EFBE11000000A1C1E0E0AF27D301F77F6305B0B7D8019F22F307B0B7D80114000000010000004D0000001C00000031535053A66A63283D95D211B5D600C04FD918D0000000002D00000031535053357EC777E31B5043A48C7563D727776D1100000002000000000B000000000000000000000000000000940092003200000080004658D1892000474F4F474C457E312E5A49500000760009000400EFBE4658D1894658D1892E000000F55D05000000090000000000000000000000000000001F47700047006F006F0067006C0065004300680072006F006D00650045006E0074006500720070007200690073006500420075006E0064006C006500360034002E007A006900700000001C000000010000004D0000001C00000031535053A66A63283D95D211B5D600C04FD918D0000000002D00000031535053357EC777E31B5043A48C7563D727776D1100000002000000000B0000000000000000000000000000005C005A00320099030000F2588C582000657874312E7A69700000420009000400EFBEF2588C58F2588C582E000000A70D00000000160000000000000000000000000000003A91F90065007800740031002E007A0069007000000018000000010000004D0000001C00000031535053A66A63283D95D211B5D600C04FD918D0000000002D00000031535053357EC777E31B5043A48C7563D727776D1100000002000000000B00000000000000000000000000000050004E00310000000000F258CE5810006578743100003A0009000400EFBEF258CE58F258CE582E000000DE0200000000170000000000000000000000000000001CB7E9006500780074003100000014000000010000004D0000001C00000031535053A66A63283D95D211B5D600C04FD918D0000000002D00000031535053357EC777E31B5043A48C7563D727776D1100000002000000000B000000FFFF000000000000000000006E006C0032001EEC0500F258826620005052454645527E312E5A49500000500009000400EFBEF2588266F25882662E00000028D4000000001900000000000000000000000000000005A1250050007200650066006500720065006E006300650073002E007A006900700000001C000000010000004D0000001C00000031535053A66A63283D95D211B5D600C04FD918D0000000002D00000031535053357EC777E31B5043A48C7563D727776D1100000002000000000B0000000000000000000000000000005800560032007E0D0000F258866620006578742E7A697000400009000400EFBEF2588666F25886662E0000002AD4000000001E0000000000000000000000000000005498DF006500780074002E007A0069007000000016000000010000004D0000001C00000031535053A66A63283D95D211B5D600C04FD918D0000000002D00000031535053357EC777E31B5043A48C7563D727776D1100000002000000000B00000000000000000000000000000062006000310000000000F2588D6610005052454645527E310000480009000400EFBEF2588D66F2588F662E0000002E2F0100000017000000000000000000000000000000CF57130150007200650066006500720065006E00630065007300000018000000010000004D0000001C00000031535053A66A63283D95D211B5D600C04FD918D0000000002D00000031535053357EC777E31B5043A48C7563D727776D1100000002000000000B0000000000000000000000000000004C004A00310000000000F2589066100065787400380009000400EFBEF2589066F25890662E000000E88D0100000007000000000000000000000000000000DE8B4100650078007400000012000000010000004D0000001C00000031535053A66A63283D95D211B5D600C04FD918D0000000002D00000031535053357EC777E31B5043A48C7563D727776D1100000002000000000B000000000000000000000000000000780076003200C1862C03F258957920004F4D4E495F327E312E5A495000005A0009000400EFBEF258E578F25895792E0000007C600500000039000000000000000000000000000000DE6FED006F006D006E0069005F00320033005F00310030005F0032003000320034005F002E007A006900700000001C000000010000004D0000001C00000031535053A66A63283D95D211B5D600C04FD918D0000000002D00000031535053357EC777E31B5043A48C7563D727776D1100000002000000000B00000000000000000000000000000070006E0032007E0D0000F2587B7920004348524F4D497E312E5A49500000520009000400EFBEF2587B79F2587B792E000000C260050000001800000000000000000000000000000028F586006300680072006F006D00690075006D005F006500780074002E007A006900700000001C000000010000004D0000001C00000031535053A66A63283D95D211B5D600C04FD918D0000000002D00000031535053357EC777E31B5043A48C7563D727776D1100000002000000000B000000000000000000000000000000 | |||
| (PID) Process: | (5404) firefox.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\ComDlg32\OpenSavePidlMRU\exe |
| Operation: | write | Name: | 2 |
Value: 14001F50E04FD020EA3A6910A2D808002B30309D14002E803ACCBFB42CDB4C42B0297FE99A87C6416A0032002F07DE00C15A4B582000434F4D5055547E312E45584500004E0009000400EFBEC15A4B58C15A4B582E000000E25D050000000D0000000000000000000000000000003B0C770043006F006D0070007500740065007200330032002E0065007800650000001C000000 | |||
| (PID) Process: | (5404) firefox.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\ComDlg32\OpenSavePidlMRU\exe |
| Operation: | write | Name: | MRUListEx |
Value: 020000000100000000000000FFFFFFFF | |||
| (PID) Process: | (5404) firefox.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\ComDlg32\OpenSavePidlMRU\* |
| Operation: | write | Name: | 8 |
Value: 14001F50E04FD020EA3A6910A2D808002B30309D14002E803ACCBFB42CDB4C42B0297FE99A87C6416A0032002F07DE00C15A4B582000434F4D5055547E312E45584500004E0009000400EFBEC15A4B58C15A4B582E000000E25D050000000D0000000000000000000000000000003B0C770043006F006D0070007500740065007200330032002E0065007800650000001C000000 | |||
Executable files
345
Suspicious files
177
Text files
100
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 7232 | Computer32.exe | C:\Users\admin\AppData\Local\Temp\_MEI72322\_cffi_backend.cp313-win_amd64.pyd | executable | |
MD5:5CBA92E7C00D09A55F5CBADC8D16CD26 | SHA256:0E3D149B91FC7DC3367AB94620A5E13AF6E419F423B31D4800C381468CB8AD85 | |||
| 7232 | Computer32.exe | C:\Users\admin\AppData\Local\Temp\_MEI72322\VCRUNTIME140_1.dll | executable | |
MD5:C0C0B4C611561F94798B62EB43097722 | SHA256:497A280550443E3E9F89E428E51CB795139CA8944D5DEDD54A7083C00E7164E5 | |||
| 7232 | Computer32.exe | C:\Users\admin\AppData\Local\Temp\_MEI72322\_asyncio.pyd | executable | |
MD5:56F958EEBBC62305B4BF690D61C78E28 | SHA256:50631361EF074BE42D788818AF91D0301D22FA24A970F41F496D8272B92CFE31 | |||
| 7232 | Computer32.exe | C:\Users\admin\AppData\Local\Temp\_MEI72322\_hashlib.pyd | executable | |
MD5:3E540EF568215561590DF215801B0F59 | SHA256:0ED7A6ED080499BC6C29D7113485A8A61BDBA93087B010FCA67D9B8289CBE6FA | |||
| 7232 | Computer32.exe | C:\Users\admin\AppData\Local\Temp\_MEI72322\VCRUNTIME140.dll | executable | |
MD5:32DA96115C9D783A0769312C0482A62D | SHA256:8B10C53241726B0ACC9F513157E67FCB01C166FEC69E5E38CA6AADA8F9A3619F | |||
| 7232 | Computer32.exe | C:\Users\admin\AppData\Local\Temp\_MEI72322\_overlapped.pyd | executable | |
MD5:363409FBACB1867F2CE45E3C6922DDB4 | SHA256:F154AC9D5CA0646D18F6197C0406F7541B6E0752B2D82A330036C1E39D3A49E7 | |||
| 7232 | Computer32.exe | C:\Users\admin\AppData\Local\Temp\_MEI72322\_queue.pyd | executable | |
MD5:CC0F4A77CCFE39EFC8019FA8B74C06D0 | SHA256:DEE7D19A9FCAB0DF043DC56F2CDC32F1A2A968AB229679B38B378C61CA0CBA53 | |||
| 7232 | Computer32.exe | C:\Users\admin\AppData\Local\Temp\_MEI72322\_lzma.pyd | executable | |
MD5:D63E2E743EA103626D33B3C1D882F419 | SHA256:7C2D2030D5D246739C5D85F087FCF404BC36E1815E69A8AC7C9541267734FC28 | |||
| 7232 | Computer32.exe | C:\Users\admin\AppData\Local\Temp\_MEI72322\_multiprocessing.pyd | executable | |
MD5:807DD90BE59EA971DAC06F3AAB4F2A7E | SHA256:B20DD6F5FAB31476D3D8D7F40CB5AB098117FA5612168C0FF4044945B6156D47 | |||
| 7232 | Computer32.exe | C:\Users\admin\AppData\Local\Temp\_MEI72322\api-ms-win-core-debug-l1-1-0.dll | executable | |
MD5:7DC2026ABEDAA10841EAE4129EF1A9AE | SHA256:E83D5E5EB772070999F34A214EBFFCF0A6068EBC1C4B4F1991188448F323808D | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
101
TCP/UDP connections
83
DNS requests
96
Threats
16
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 184.25.206.92:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 2.16.168.114:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 151.101.67.19:443 | https://contile.services.mozilla.com/v1/tiles | unknown | binary | 5.05 Kb | whitelisted |
5404 | firefox.exe | GET | 200 | 34.107.221.82:80 | http://detectportal.firefox.com/canonical.html | unknown | — | — | whitelisted |
— | — | POST | 200 | 151.101.67.19:443 | https://spocs.getpocket.com/spocs | unknown | binary | 18.5 Kb | whitelisted |
— | — | GET | 200 | 34.160.144.191:443 | https://content-signature-2.cdn.mozilla.net/chains/remote-settings.content-signature.mozilla.org-2024-03-20-10-07-03.chain | unknown | text | 5.23 Kb | whitelisted |
— | — | GET | 101 | 34.107.243.93:443 | https://push.services.mozilla.com/ | unknown | — | — | unknown |
— | — | GET | 200 | 142.250.185.138:443 | https://safebrowsing.googleapis.com/v4/threatListUpdates:fetch?$ct=application/x-protobuf&key=AIzaSyC7jsptDS3am4tPx4r3nxis7IMjBc5Dovo&$httpMethod=POST&$req=ChUKE25hdmNsaWVudC1hdXRvLWZmb3gaJwgFEAEaGwoNCAUQBhgBIgMwMDEwARD31RUaAhgJ1ShmESICIAIoARonCAEQARobCg0IARAGGAEiAzAwMTABEJz_DRoCGAnWZvpiIgIgAigBGicIAxABGhsKDQgDEAYYASIDMDAxMAEQpPYNGgIYCRiY-6YiAiACKAEaJwgHEAEaGwoNCAcQBhgBIgMwMDEwARDLxQ4aAhgJeFtrxyICIAIoARolCAkQARoZCg0ICRAGGAEiAzAwMTABECMaAhgJi9M7nSICIAIoAQ== | unknown | binary | 6.43 Mb | whitelisted |
— | — | GET | 200 | 34.149.100.209:443 | https://firefox.settings.services.mozilla.com/v1/buckets/main/collections/ms-language-packs/records/cfr-v1-en-US | unknown | binary | 330 b | whitelisted |
— | — | GET | 200 | 151.101.195.19:443 | https://ads-img.mozilla.org/v1/images?image_data=Cj0KO2h0dHBzOi8vYW1wLWFzc2V0LjQ1dHUxYzAuY29tL2Fzc2V0cy8xMDA5LzE1MjEyMjgwODcxNzYuanBnEiAV36GGy4uG4Kc3hcPXsQNe08loM62OgGAgcMju8zD3jQ | unknown | image | 9.76 Kb | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 2.16.168.114:80 | crl.microsoft.com | Akamai International B.V. | RU | whitelisted |
— | — | 184.25.206.92:80 | www.microsoft.com | AKAMAI-AS | US | whitelisted |
7288 | Computer32.exe | 162.159.138.232:443 | discord.com | CLOUDFLARENET | — | whitelisted |
4200 | Computer32.exe | 162.159.138.232:443 | discord.com | CLOUDFLARENET | — | whitelisted |
5404 | firefox.exe | 34.107.221.82:80 | detectportal.firefox.com | GOOGLE | US | whitelisted |
5404 | firefox.exe | 34.36.137.203:443 | contile.services.mozilla.com | GOOGLE-CLOUD-PLATFORM | US | whitelisted |
5404 | firefox.exe | 34.160.144.191:443 | content-signature-2.cdn.mozilla.net | GOOGLE | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
discord.com |
| whitelisted |
detectportal.firefox.com |
| whitelisted |
prod.detectportal.prod.cloudops.mozgcp.net |
| whitelisted |
contile.services.mozilla.com |
| whitelisted |
spocs.getpocket.com |
| whitelisted |
mc.prod.ads.prod.webservices.mozgcp.net |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2196 | svchost.exe | Misc activity | ET INFO Observed Discord Domain in DNS Lookup (discord .com) |
7288 | Computer32.exe | Misc activity | ET INFO Observed Discord Domain (discord .com in TLS SNI) |
7288 | Computer32.exe | Misc activity | ET INFO Observed Discord Service Domain (discord .com) in TLS SNI |
2196 | svchost.exe | Misc activity | ET INFO Discord Chat Service Domain in DNS Lookup (discord .com) |
4200 | Computer32.exe | Misc activity | ET INFO Observed Discord Domain (discord .com in TLS SNI) |
4200 | Computer32.exe | Misc activity | ET INFO Observed Discord Service Domain (discord .com) in TLS SNI |
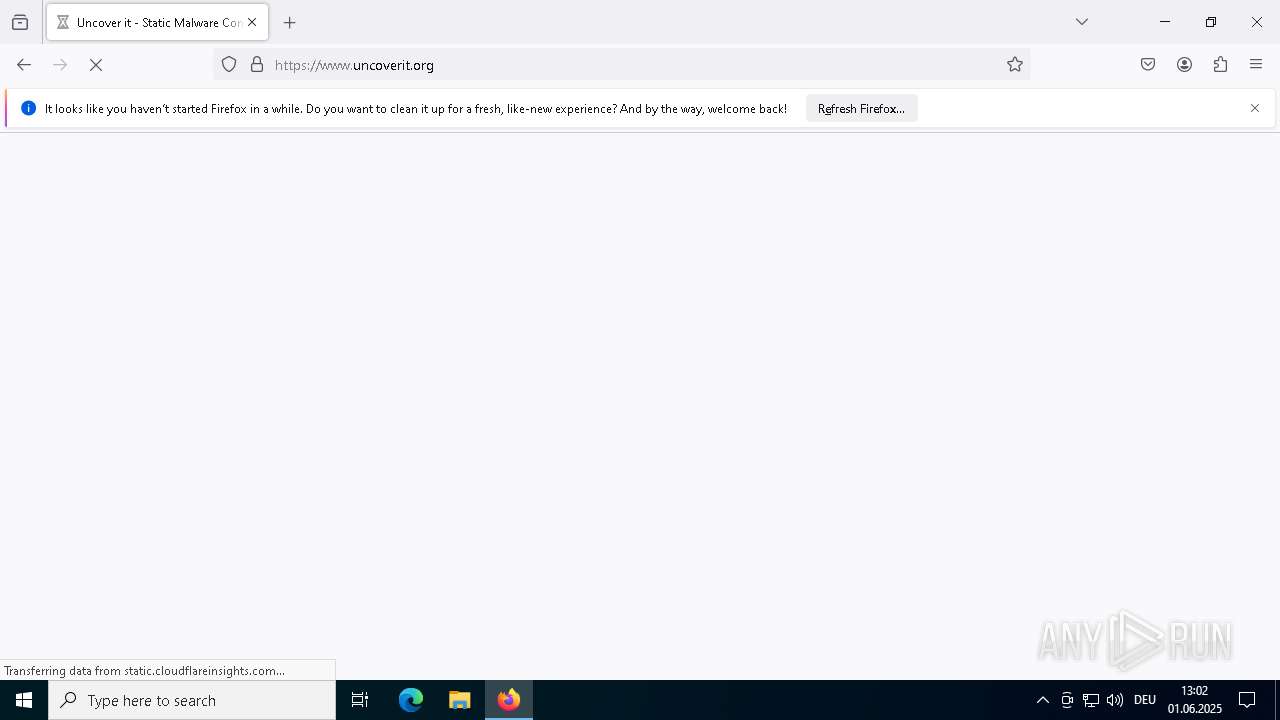
2196 | svchost.exe | Domain Observed Used for C2 Detected | STEALER [ANY.RUN] Suspected Lumma domain by CrossDomain (uncoverit .org) |
2196 | svchost.exe | Domain Observed Used for C2 Detected | STEALER [ANY.RUN] Suspected Lumma domain by CrossDomain (uncoverit .org) |
2196 | svchost.exe | Domain Observed Used for C2 Detected | STEALER [ANY.RUN] Suspected Lumma domain by CrossDomain (uncoverit .org) |
— | — | Misc activity | ET INFO Generic HTTP EXE Upload Outbound |