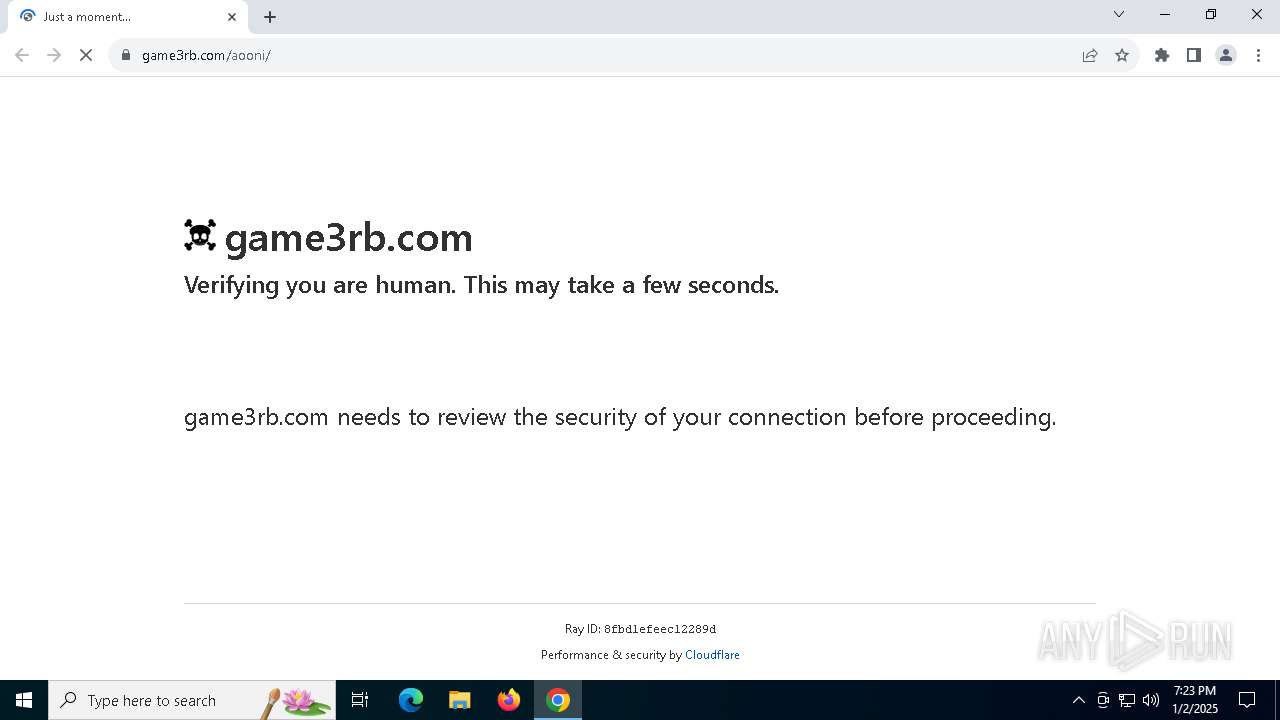
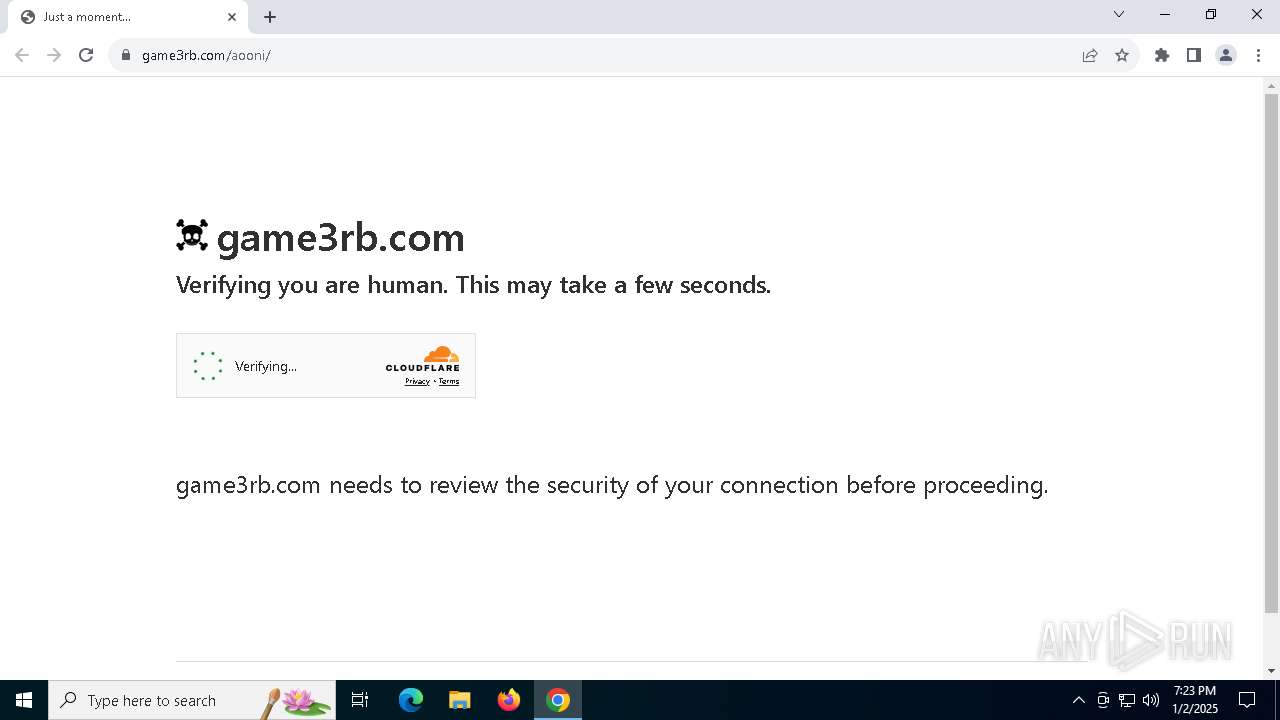
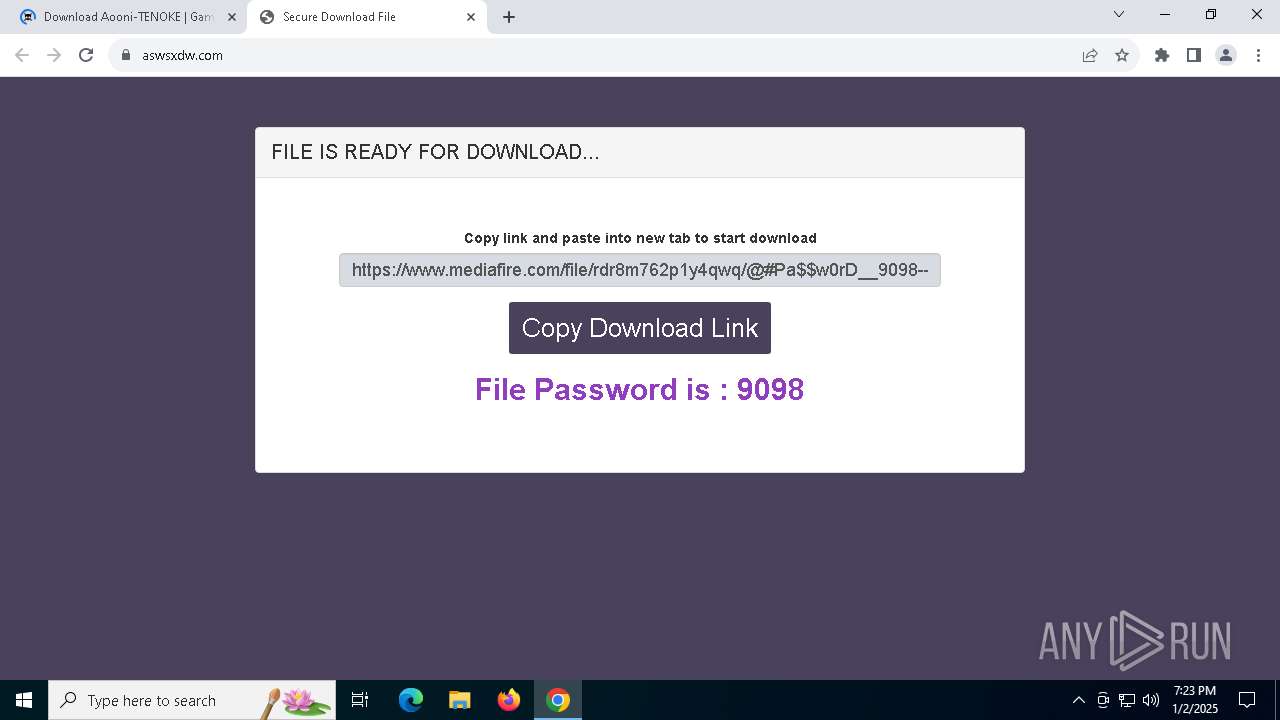
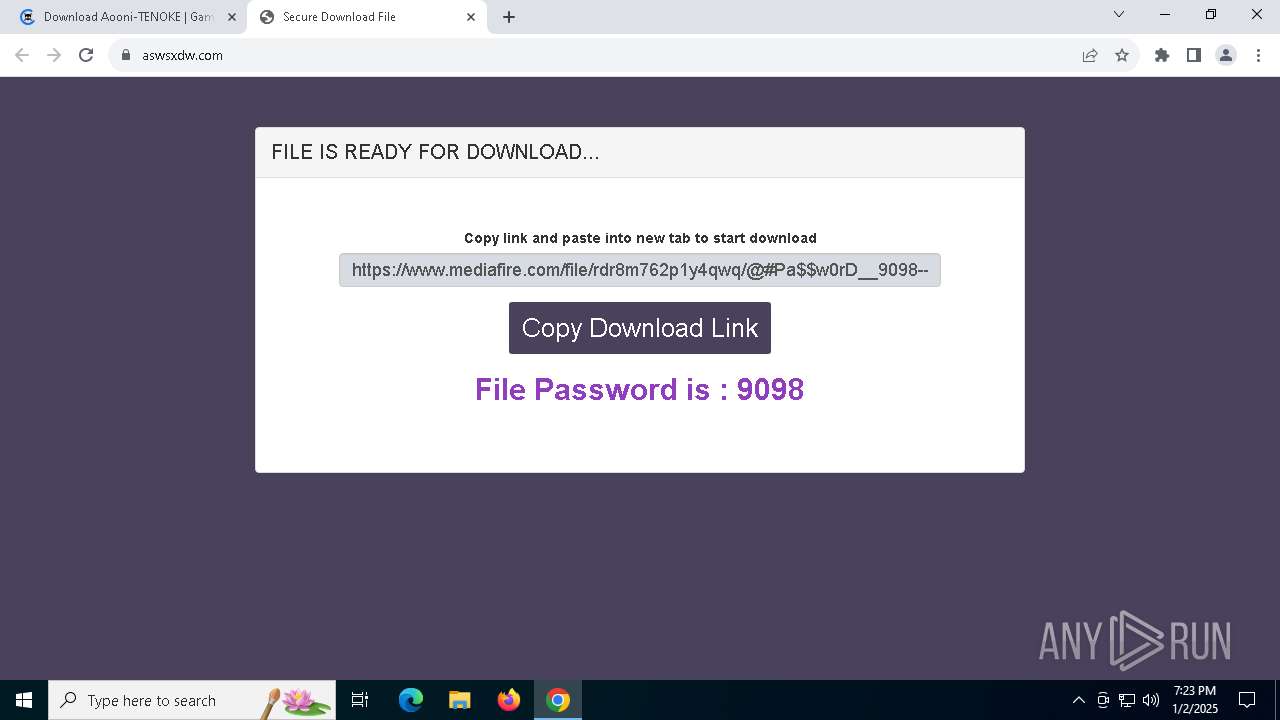
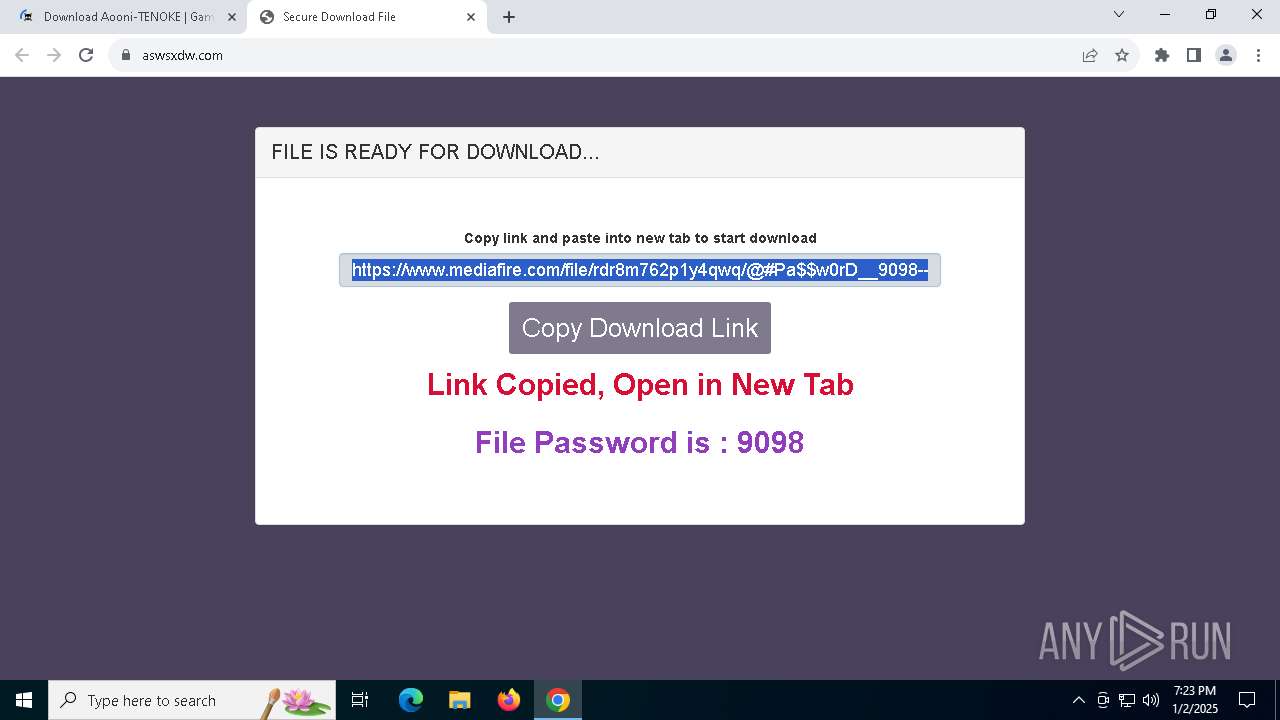
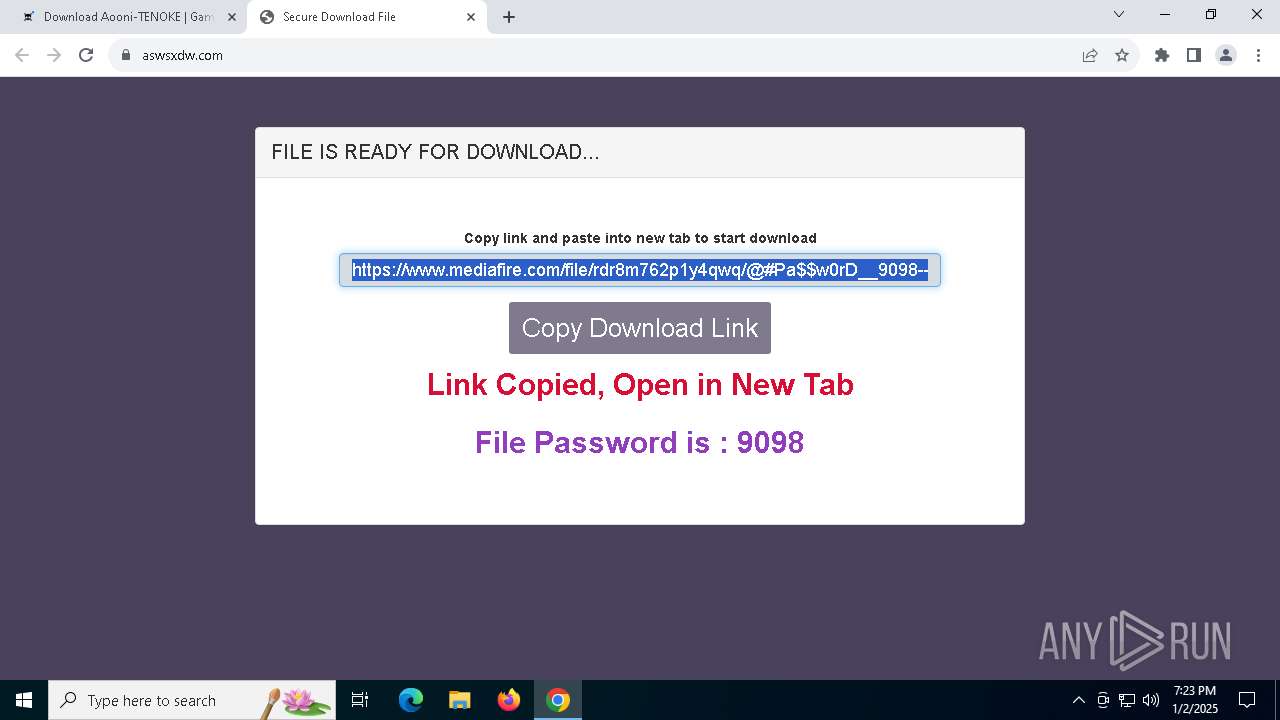
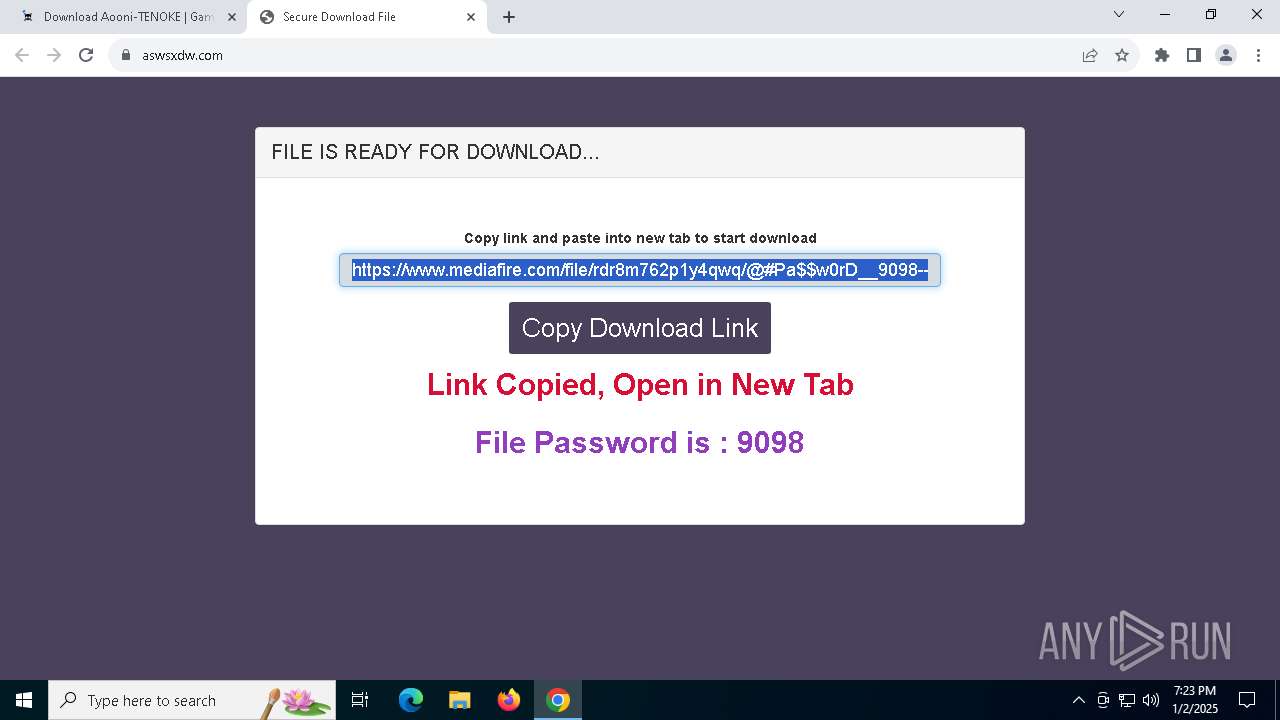
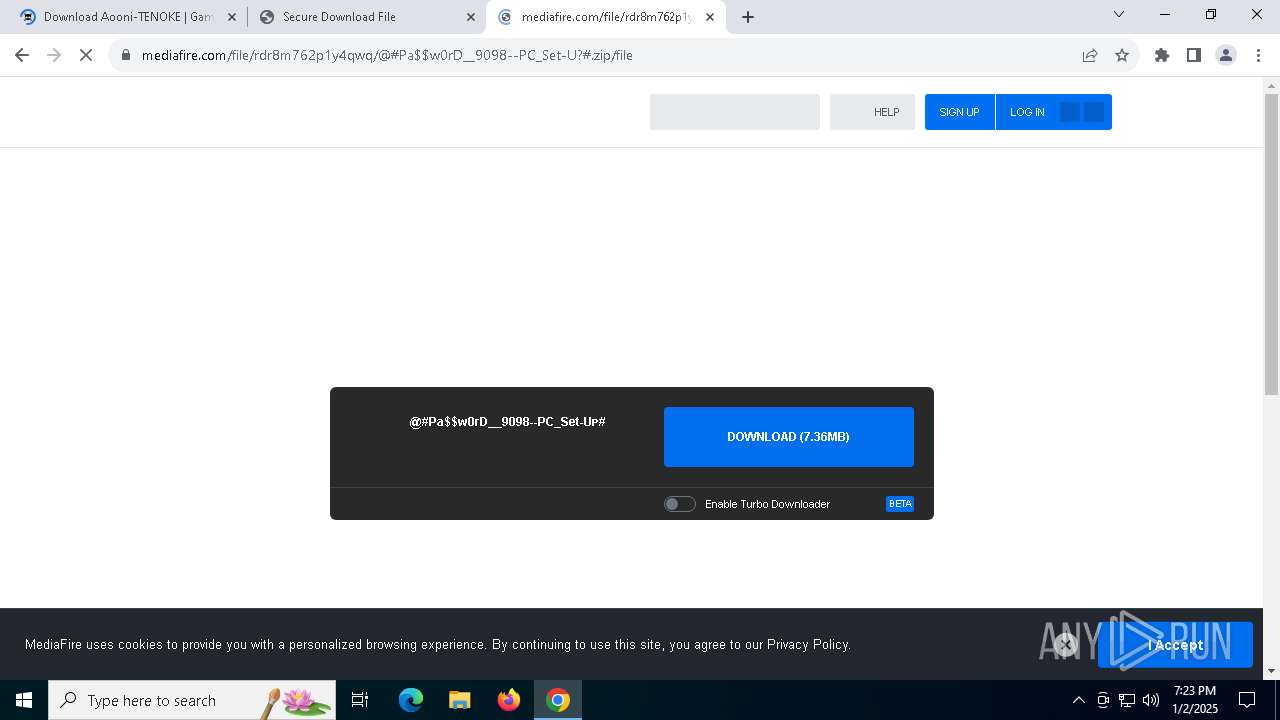
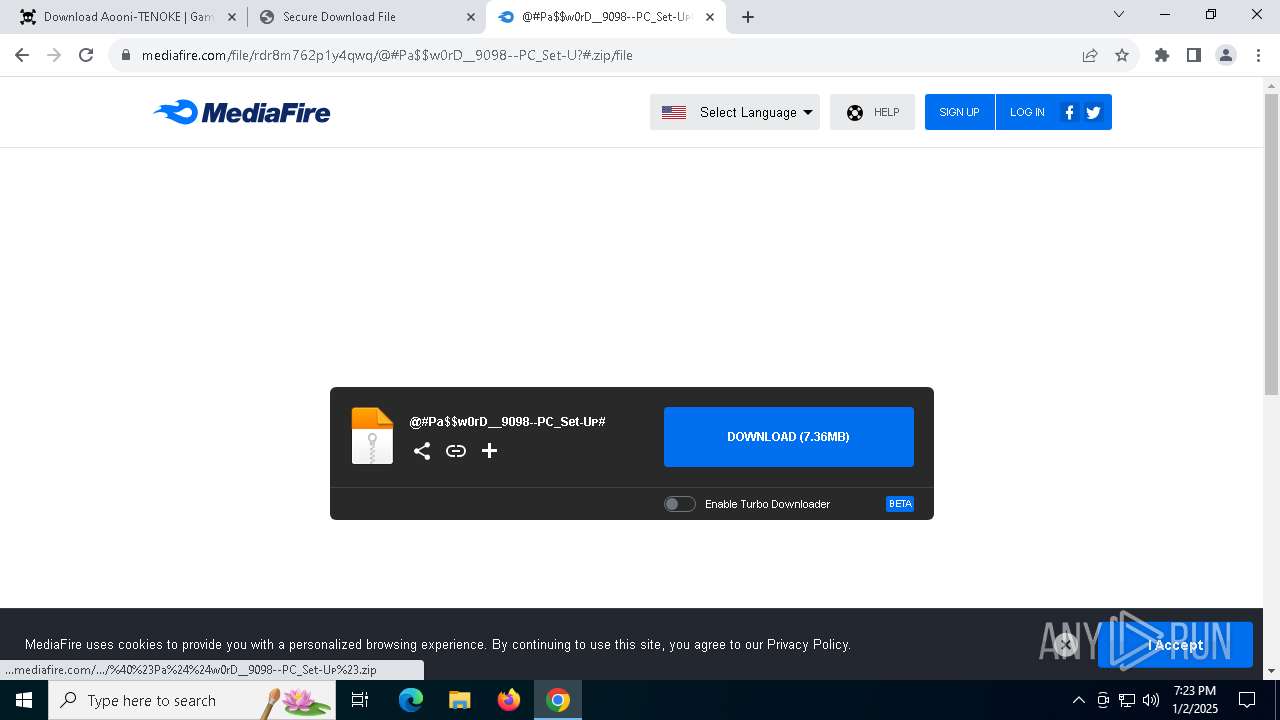
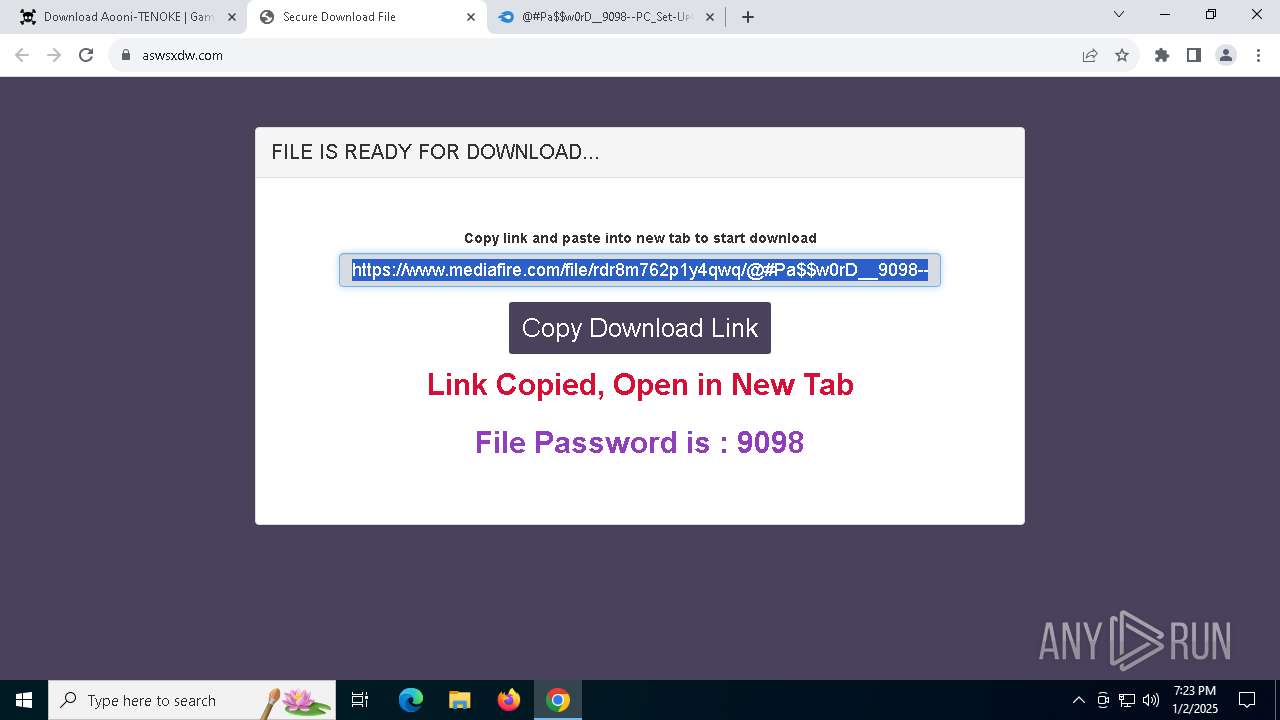
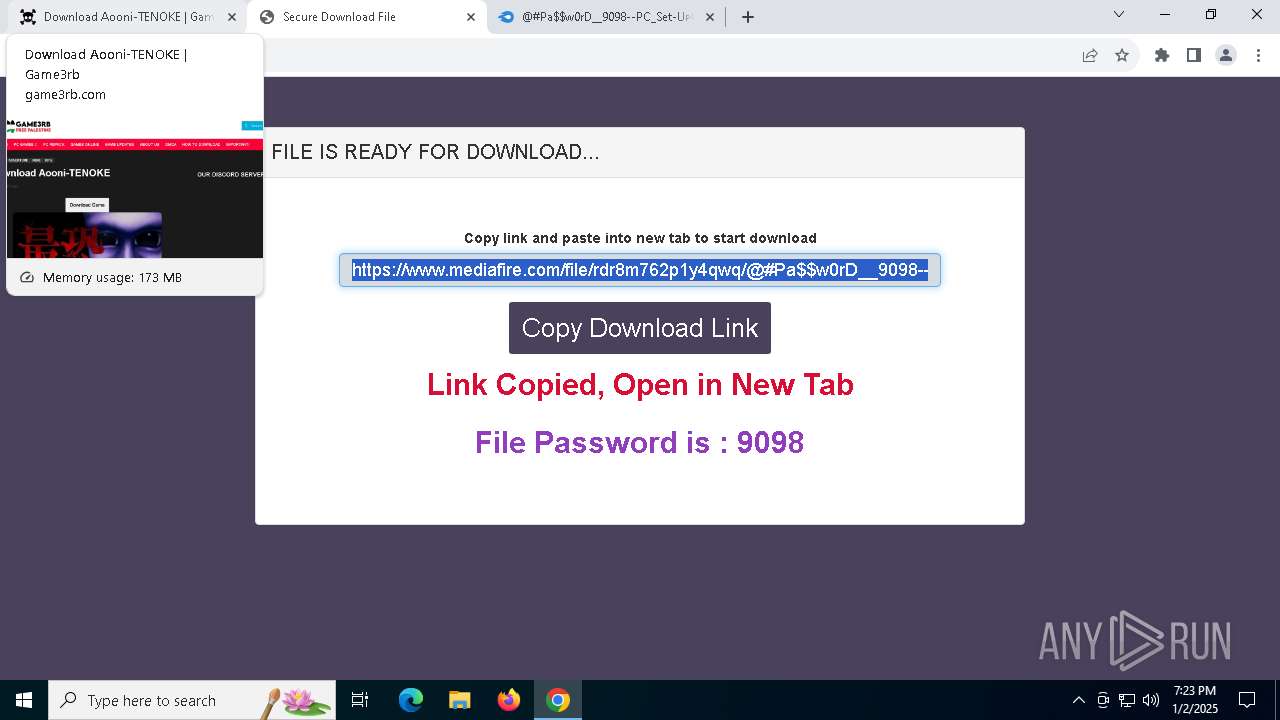
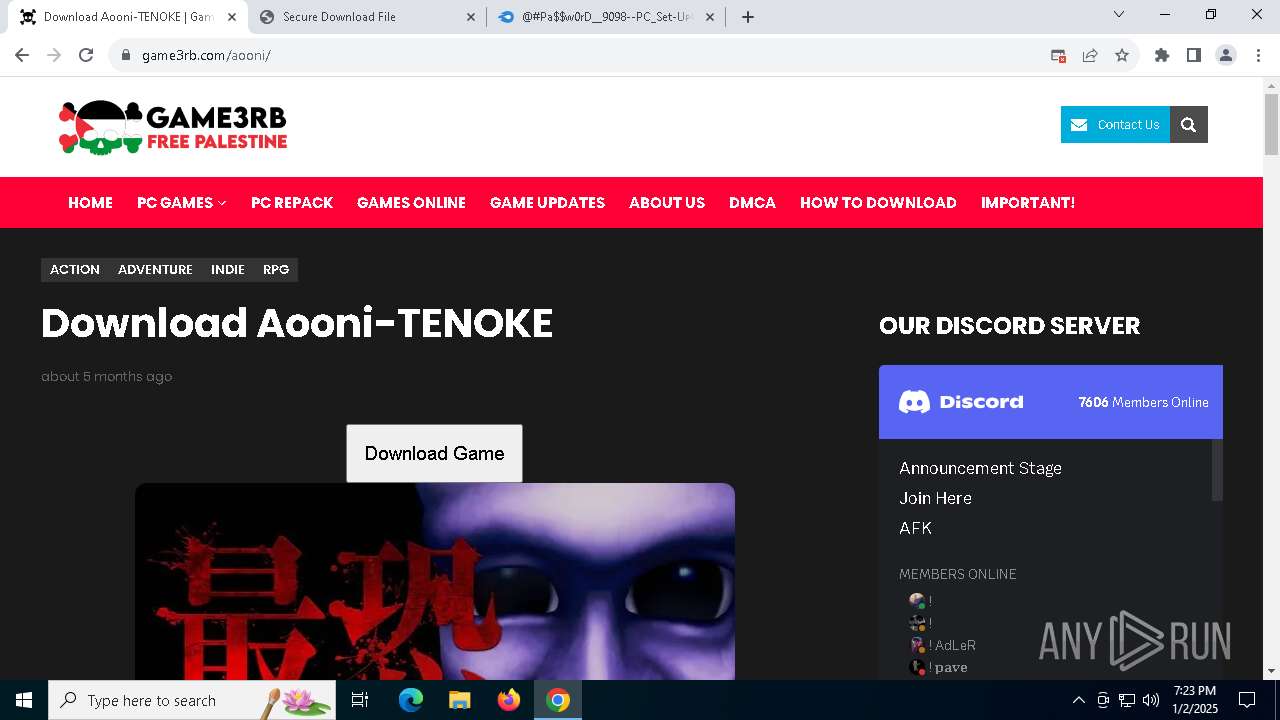
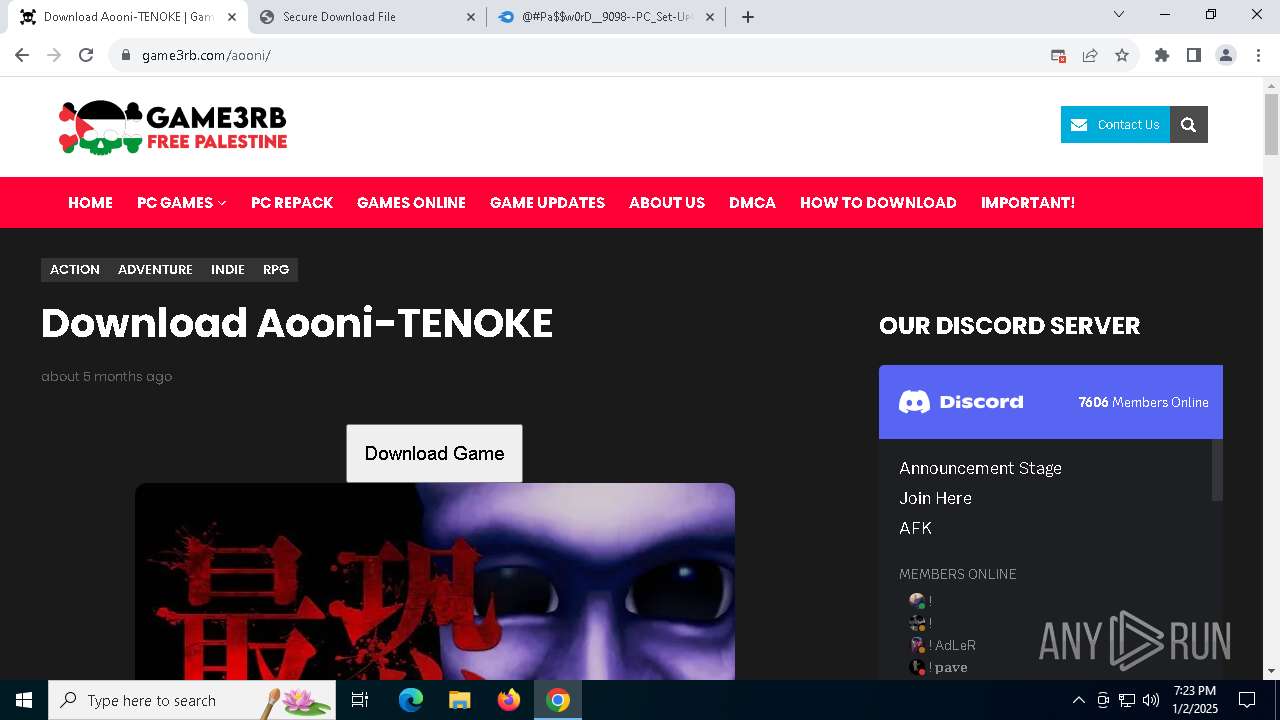
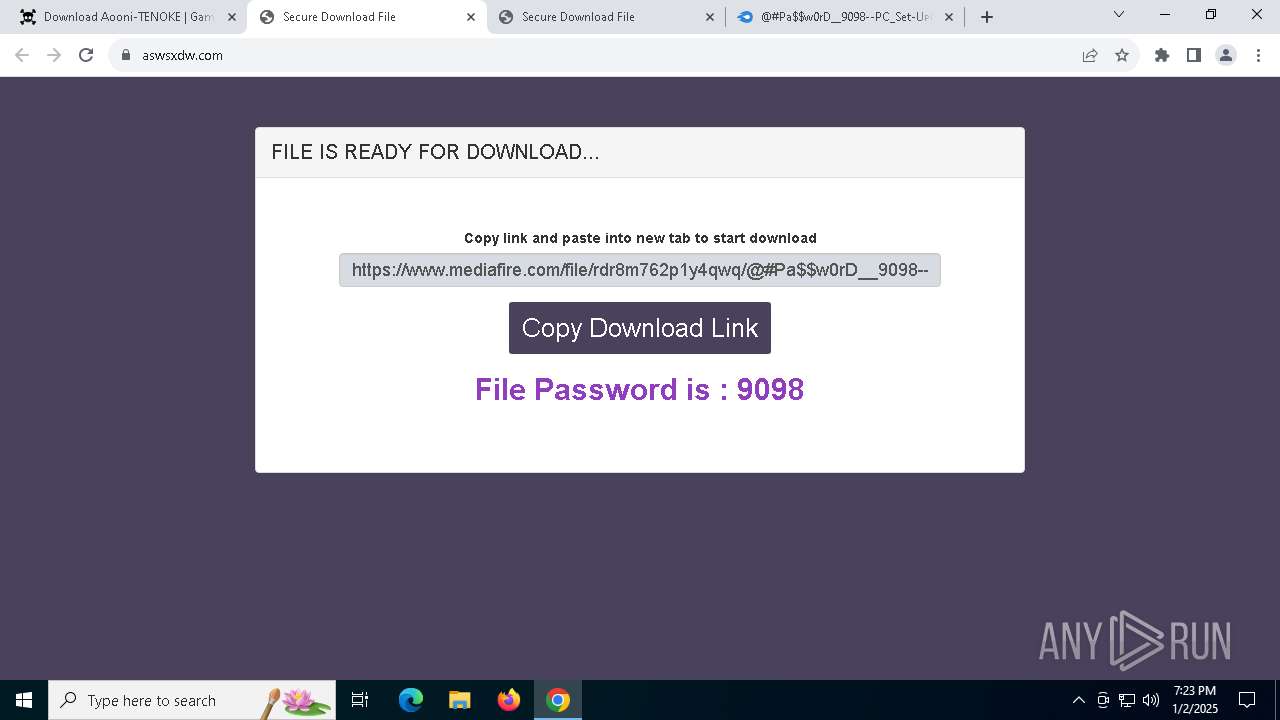
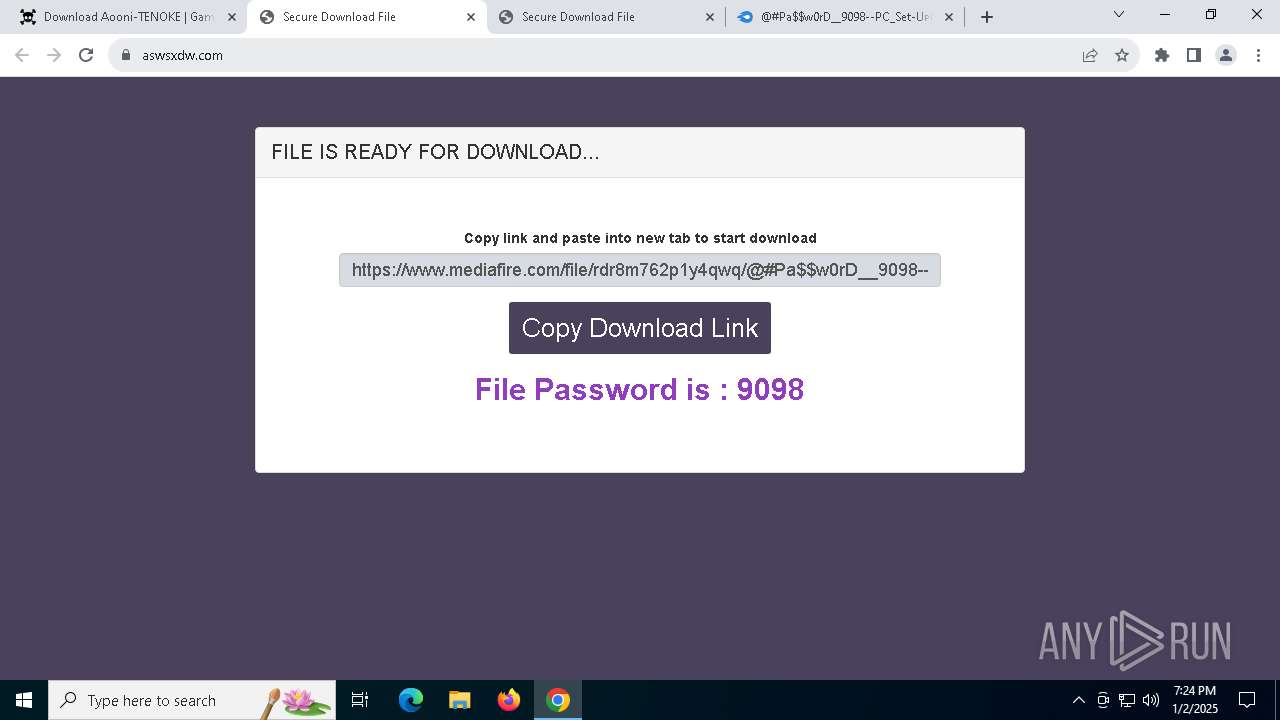
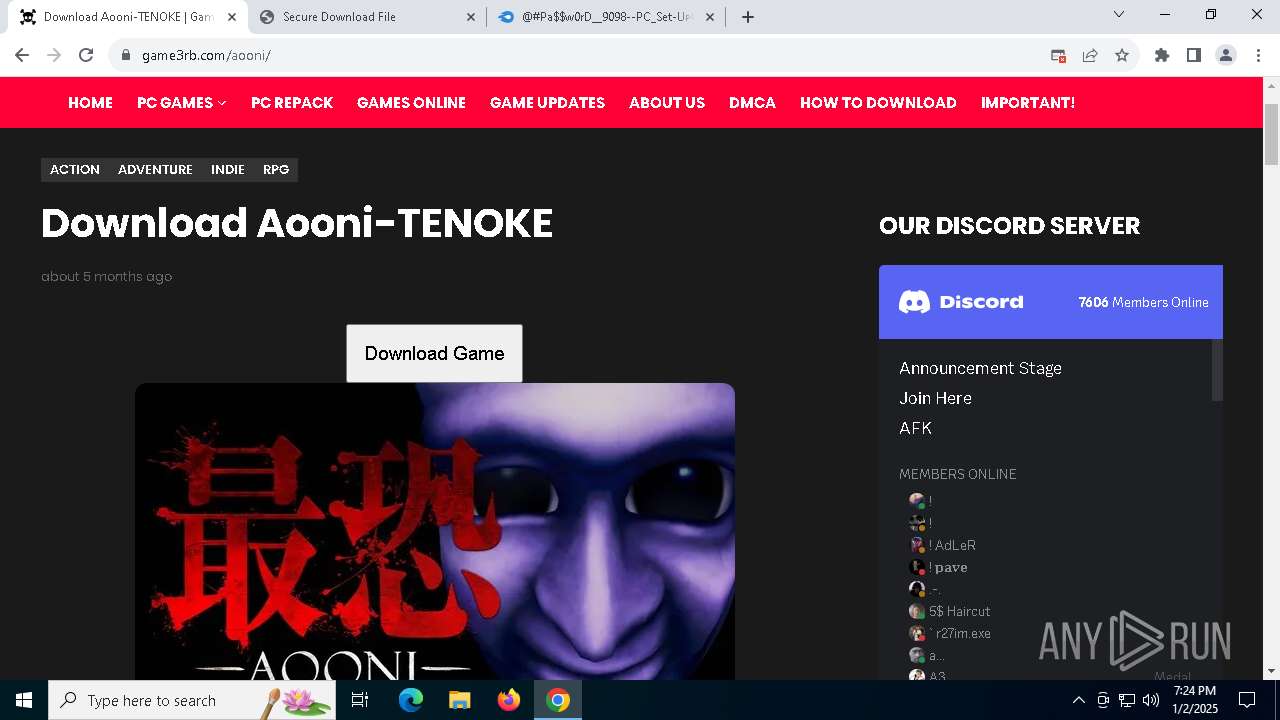
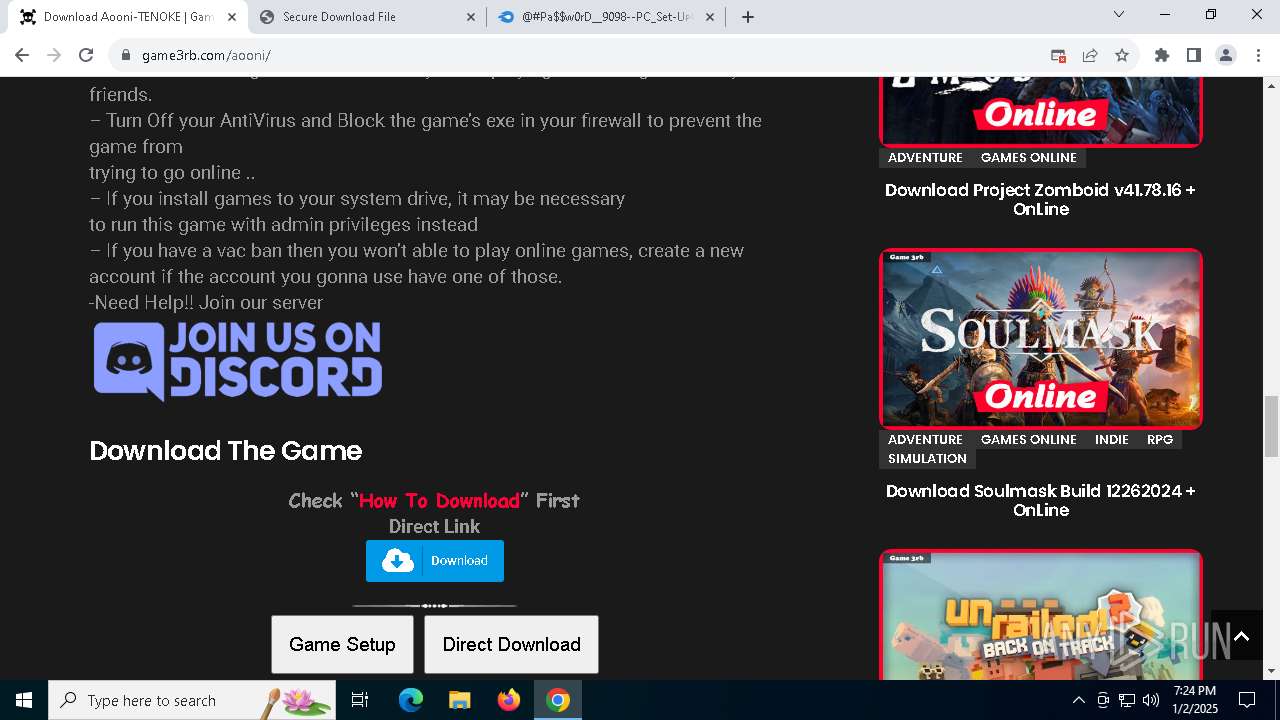
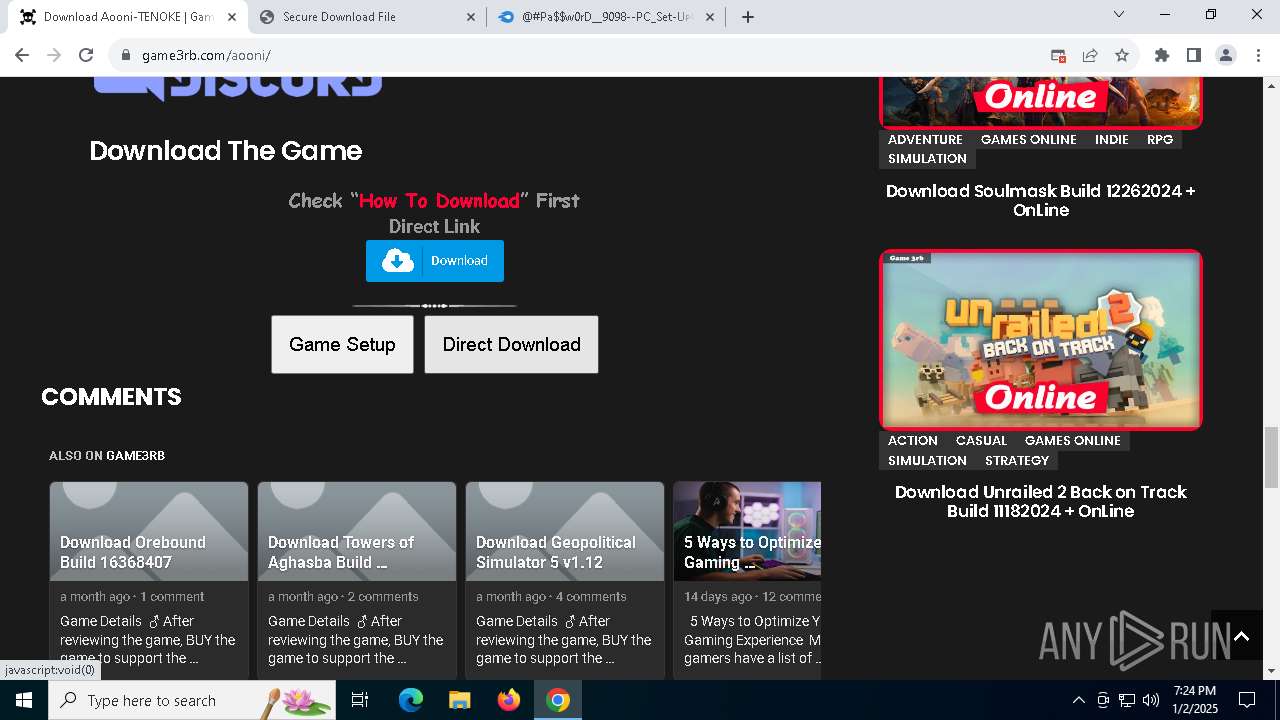
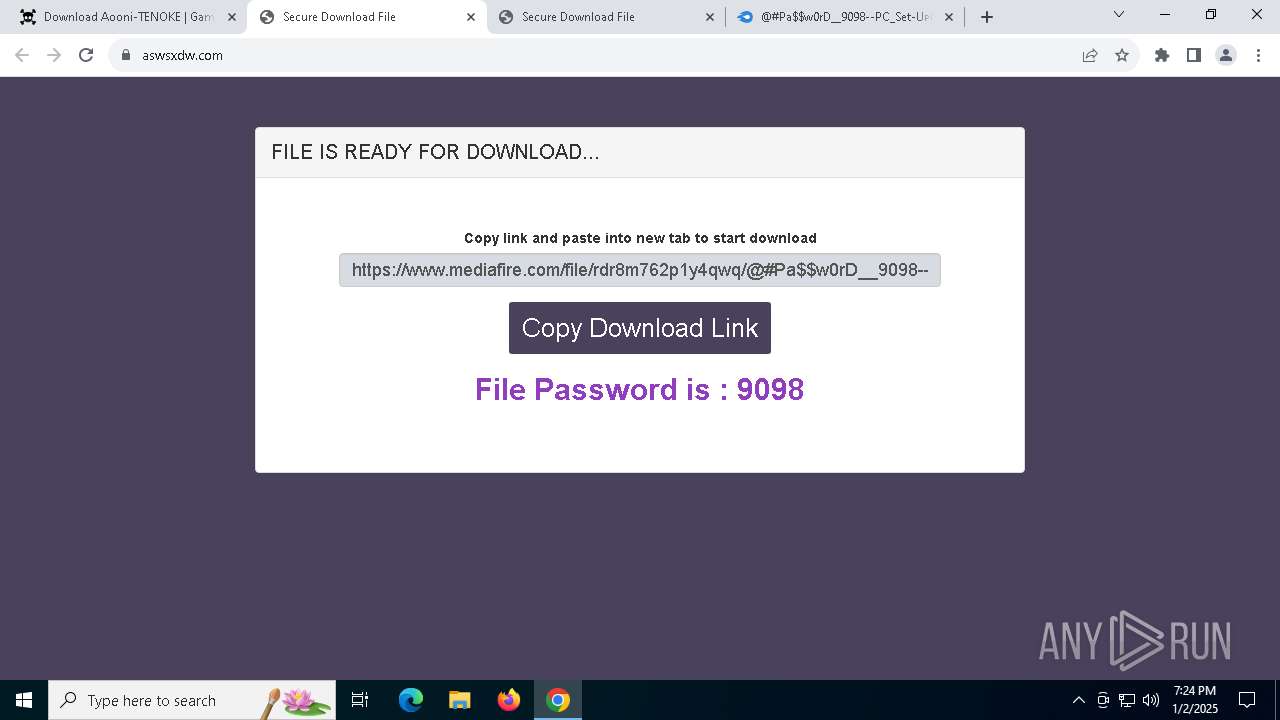
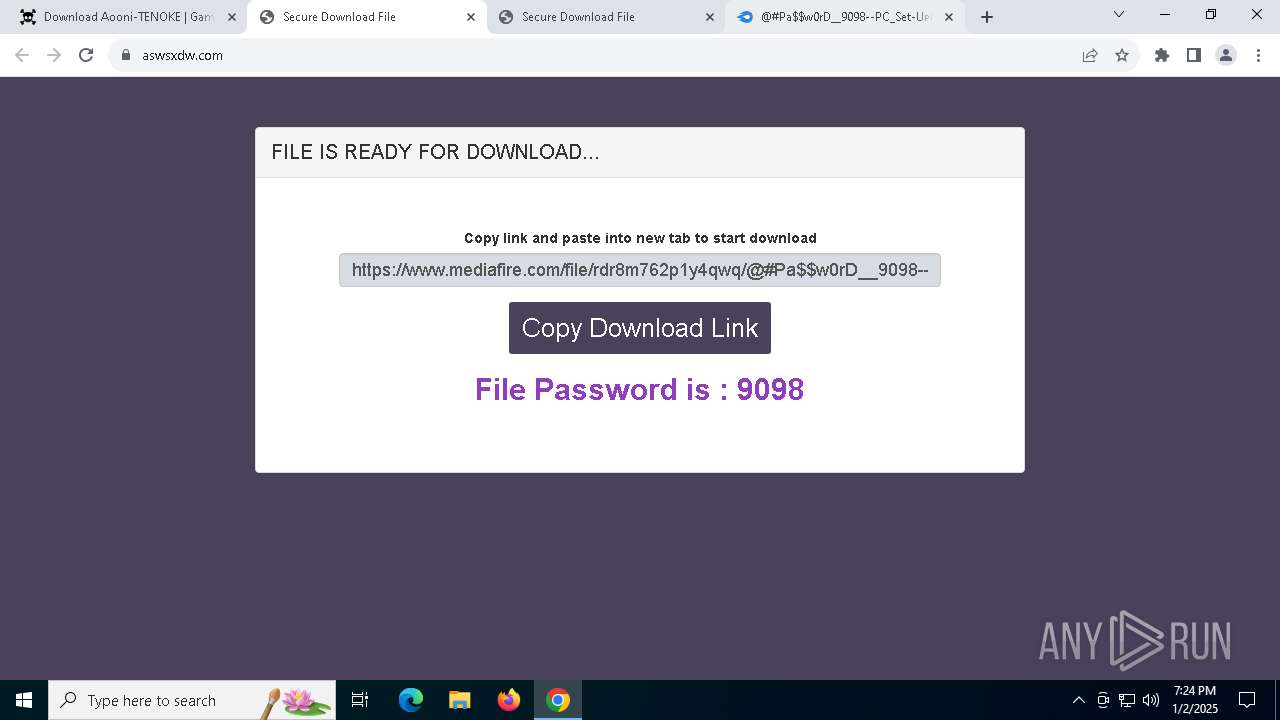
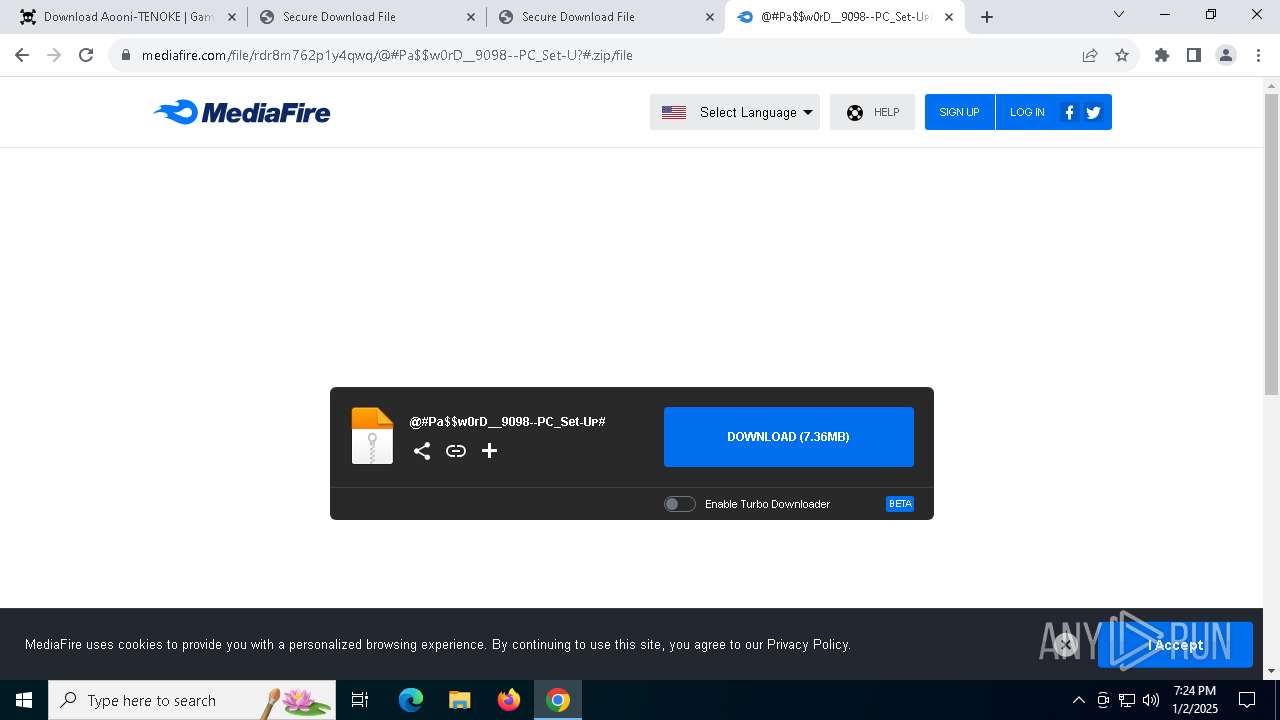
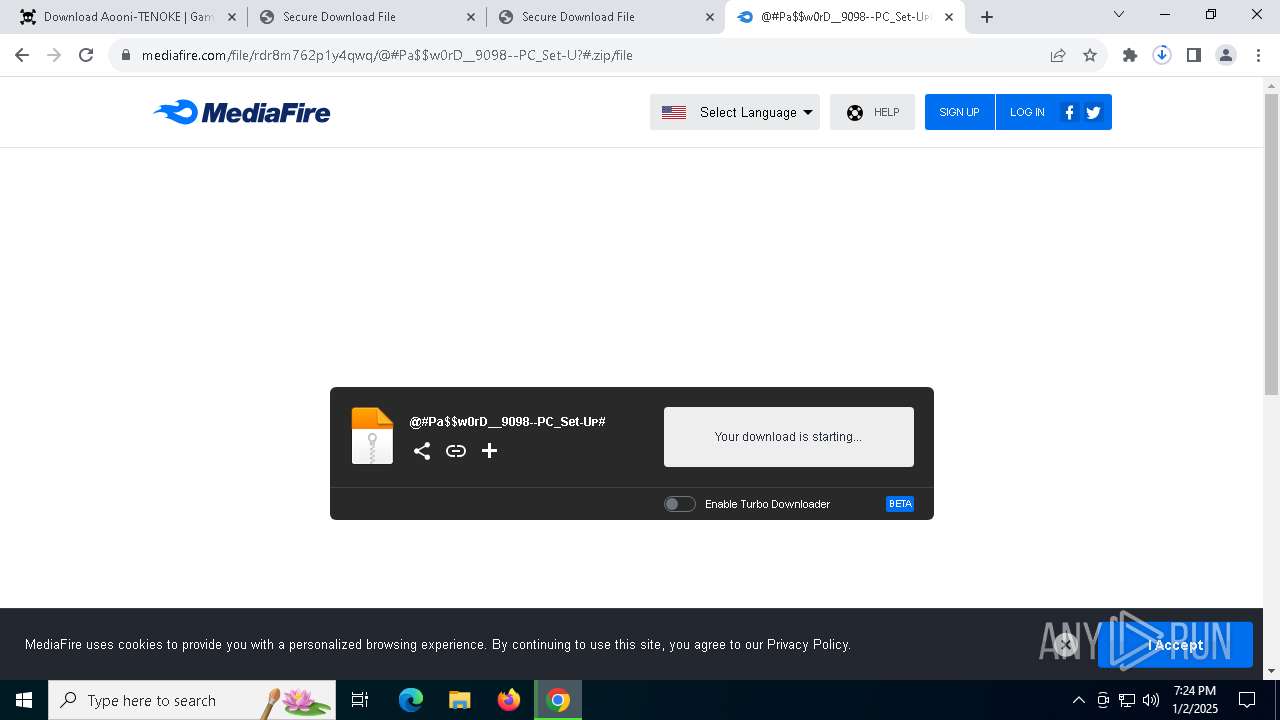
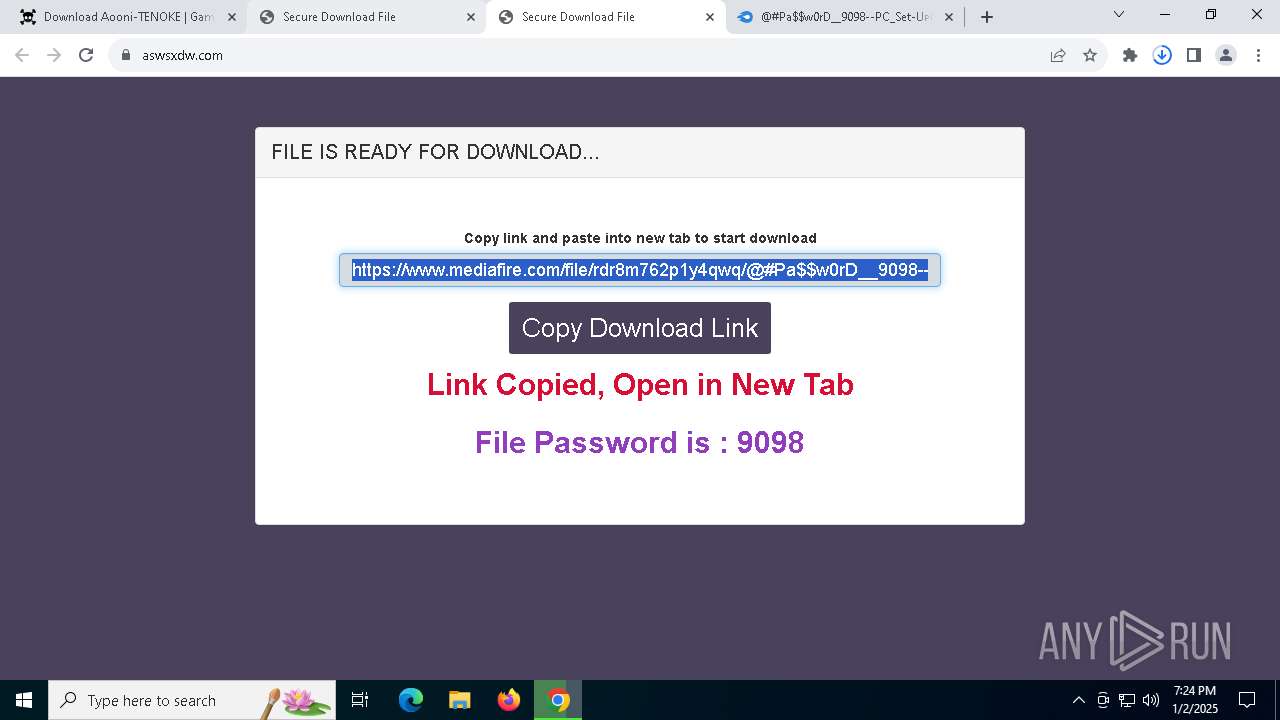
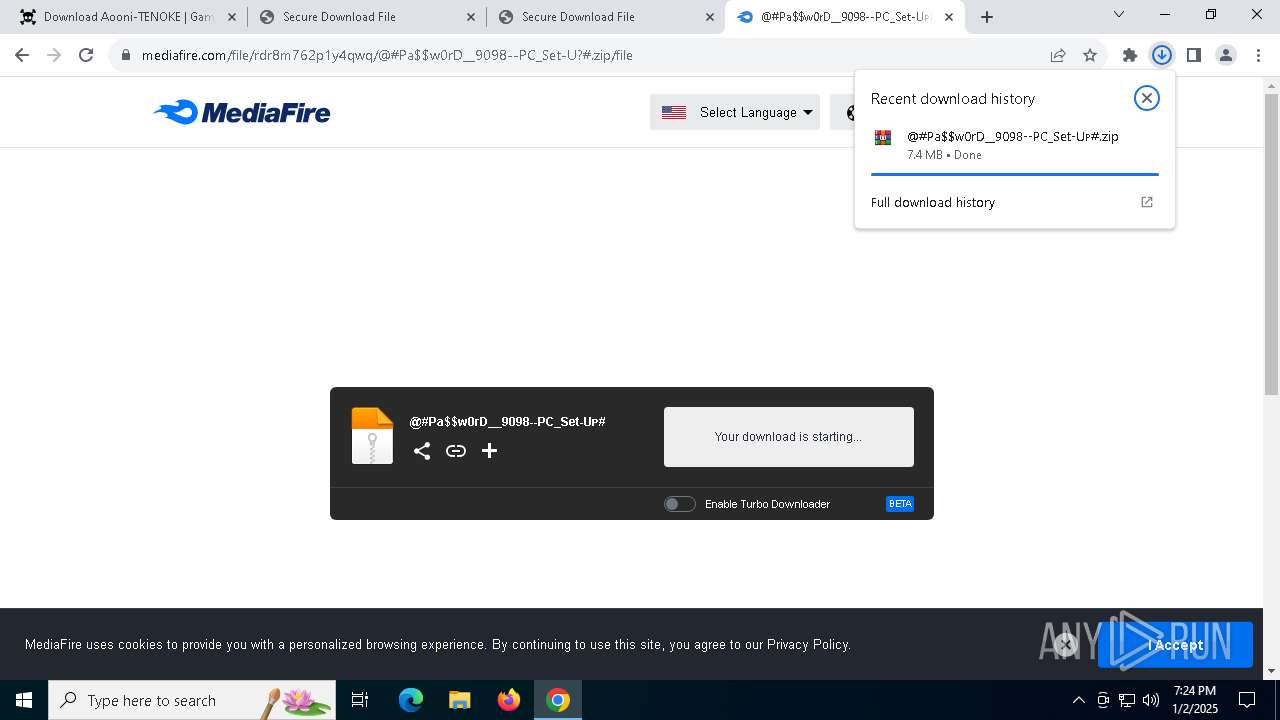
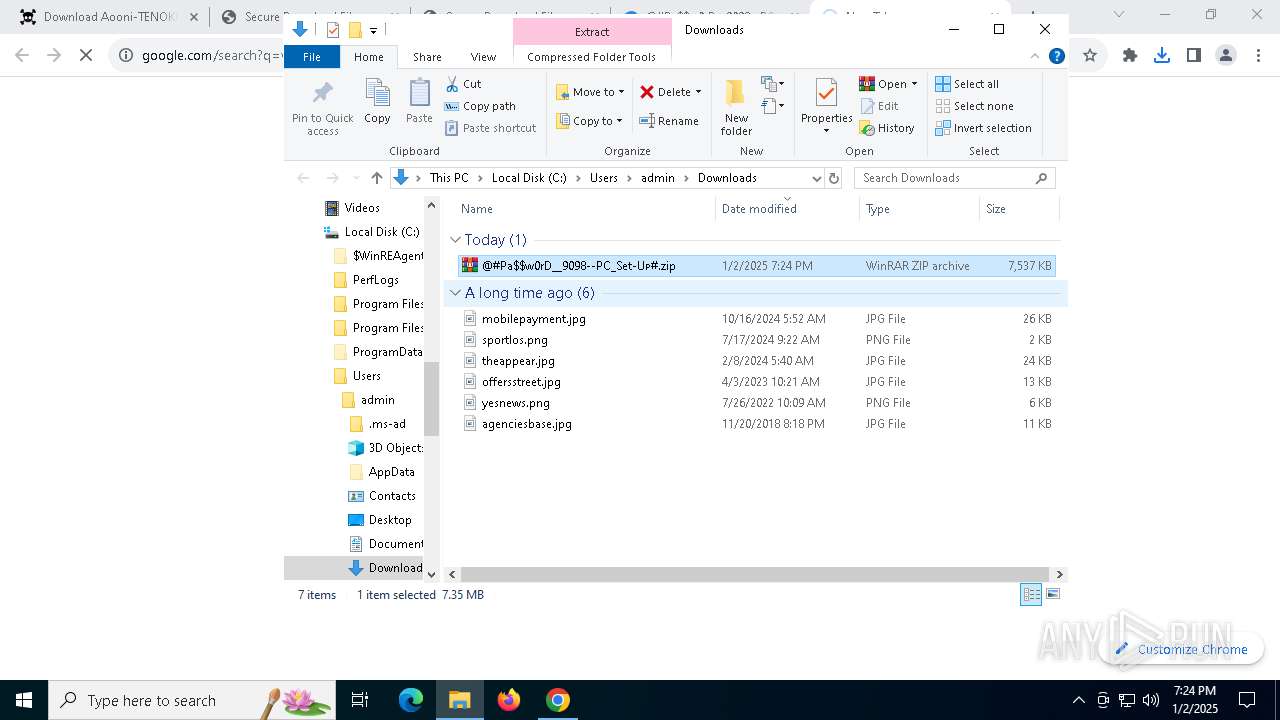
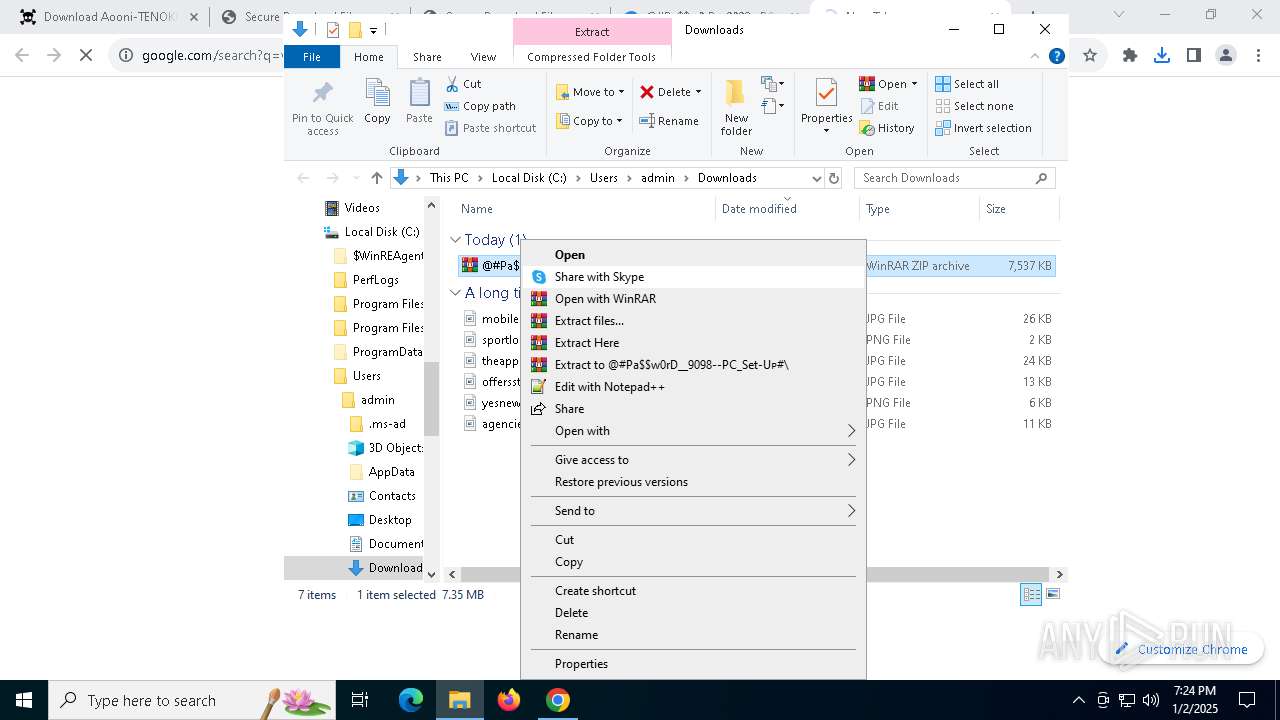
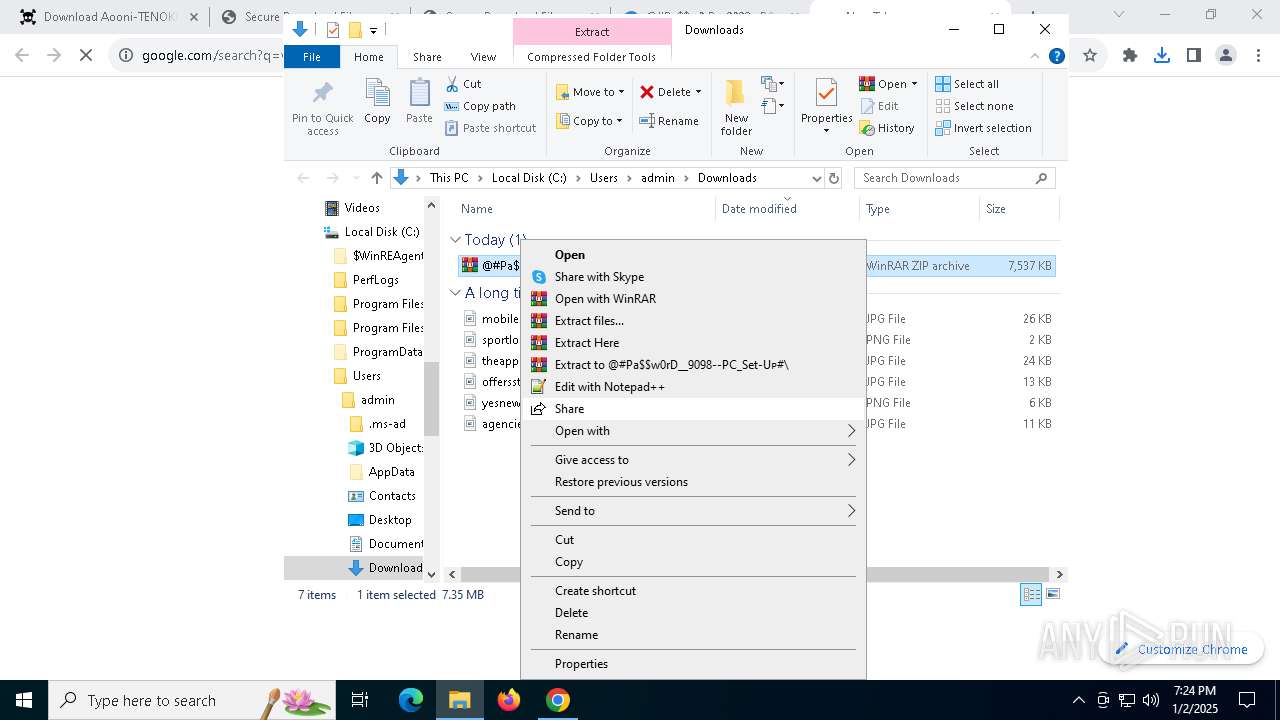
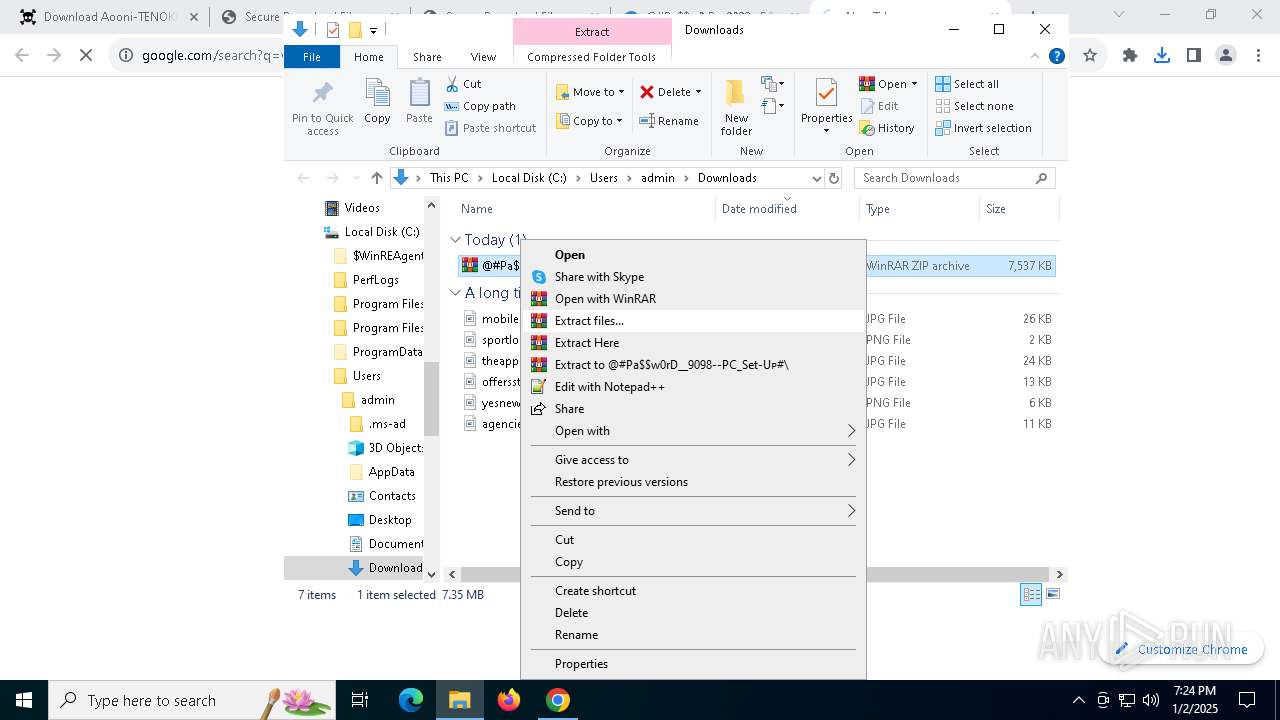
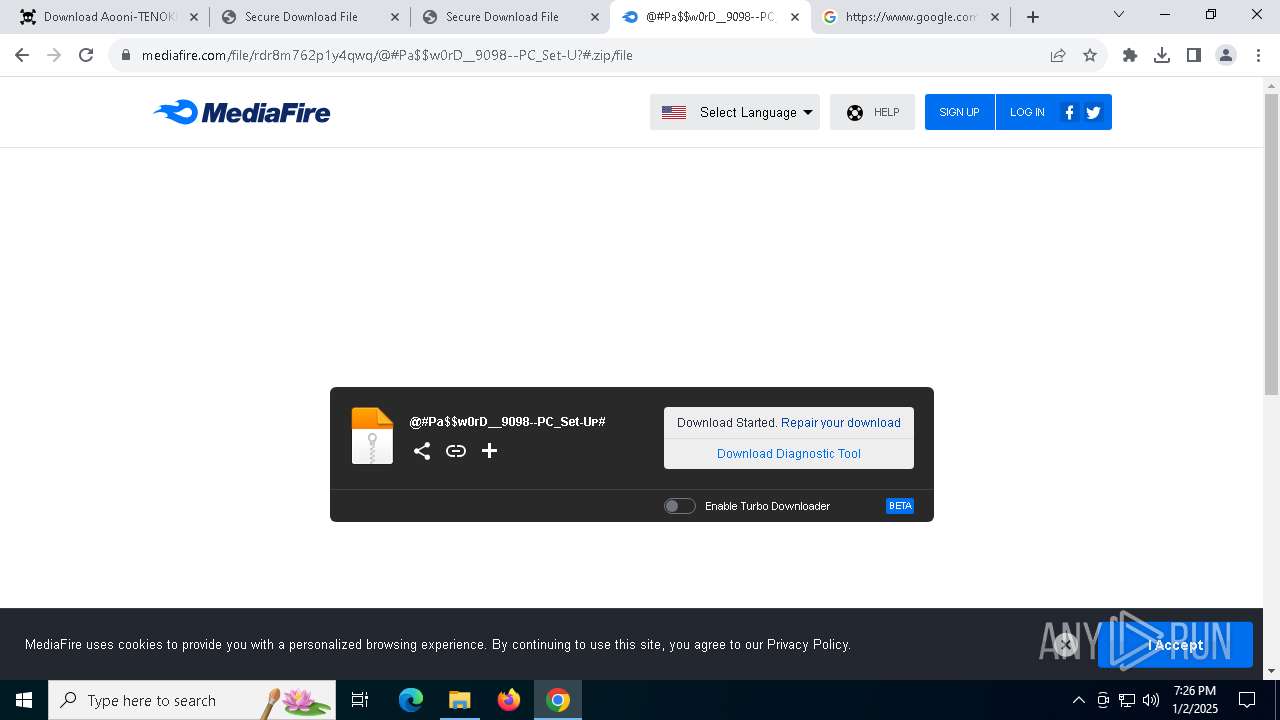
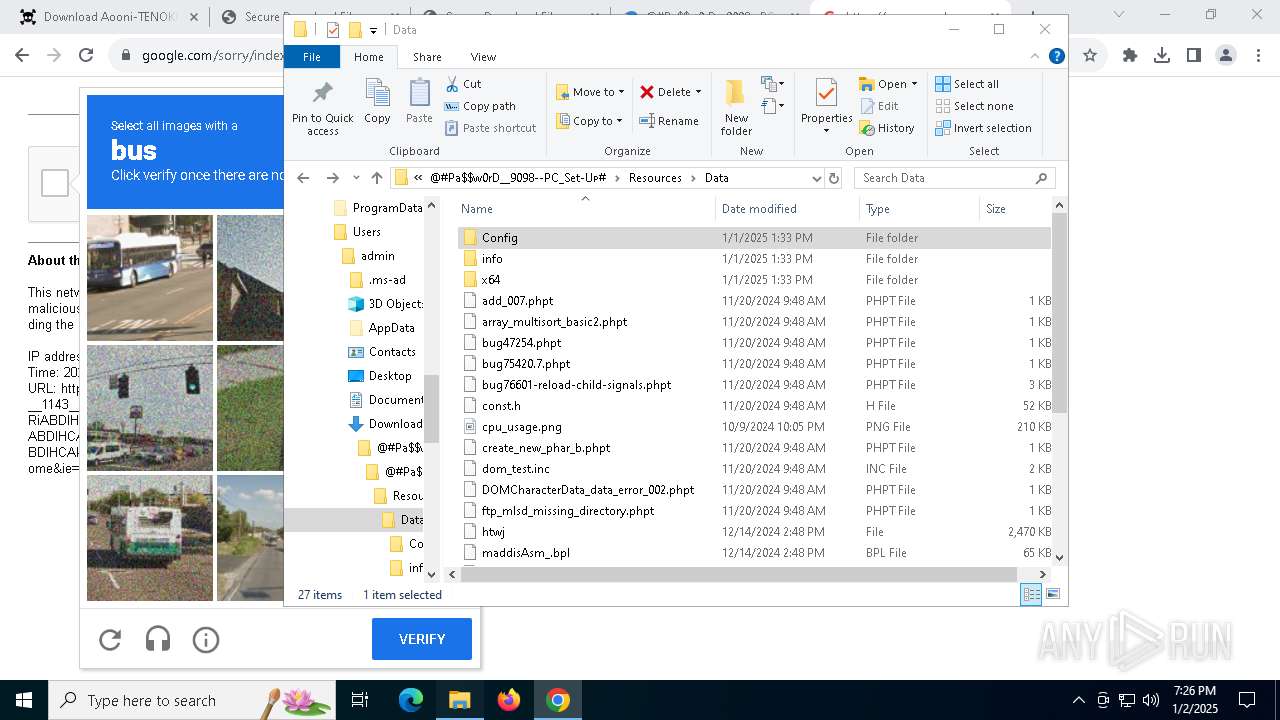
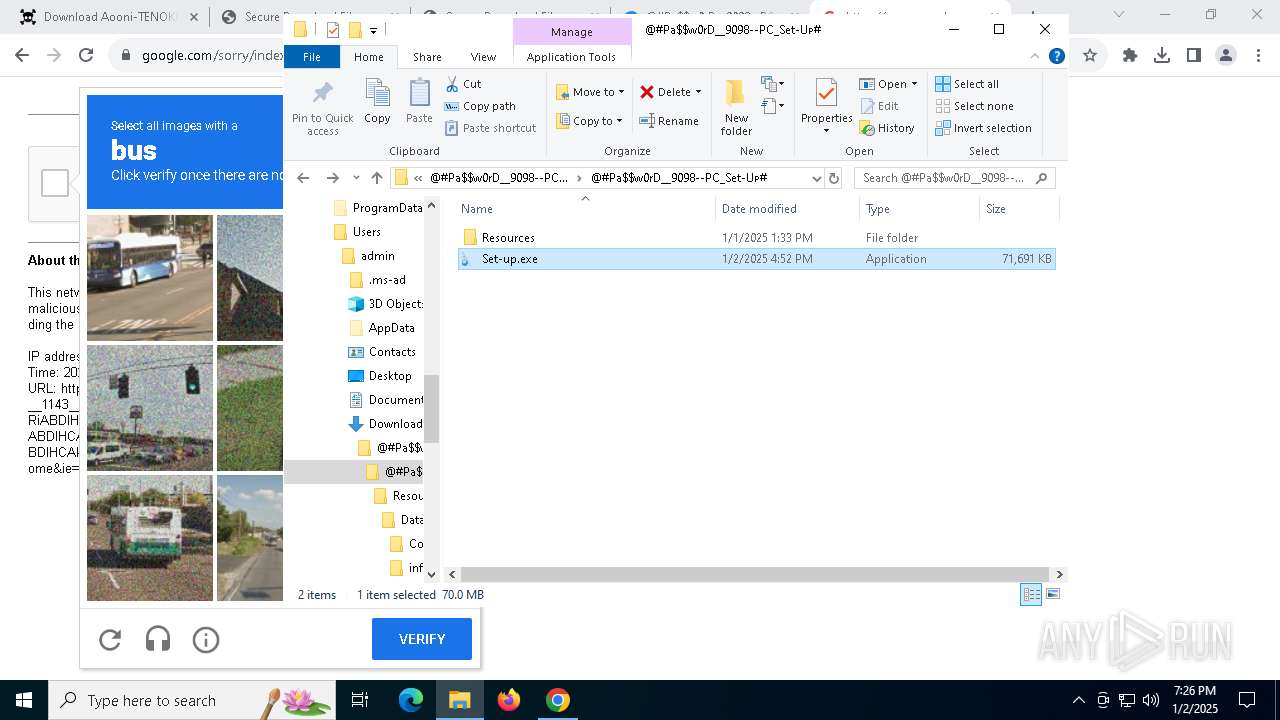
| URL: | https://game3rb.com/aooni/ |
| Full analysis: | https://app.any.run/tasks/ea0291b1-e593-4e50-a40b-ed62144b8567 |
| Verdict: | Malicious activity |
| Threats: | Lumma is an information stealer, developed using the C programming language. It is offered for sale as a malware-as-a-service, with several plans available. It usually targets cryptocurrency wallets, login credentials, and other sensitive information on a compromised system. The malicious software regularly gets updates that improve and expand its functionality, making it a serious stealer threat. |
| Analysis date: | January 02, 2025, 19:22:52 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MD5: | CA8E1952DE4B8DB74937D36E4F1EBDBC |
| SHA1: | 4E15942AEAF429834AFE2EB51B95C6BF8C8EC2CB |
| SHA256: | A9BA7F79761DE328401BF60919B703A3279A968E02C1F3C9E4AEC3558E7593D1 |
| SSDEEP: | 3:N8lIyGEtLn:2mEtL |
MALICIOUS
PHISHING has been detected (SURICATA)
- chrome.exe (PID: 6408)
Executing a file with an untrusted certificate
- Set-up.exe (PID: 6736)
- 0E0D8GQX7X5WQ5FLZ3.exe (PID: 5936)
- 0E0D8GQX7X5WQ5FLZ3.exe (PID: 3364)
- Set-up.exe (PID: 4724)
Bypass execution policy to execute commands
- powershell.exe (PID: 3912)
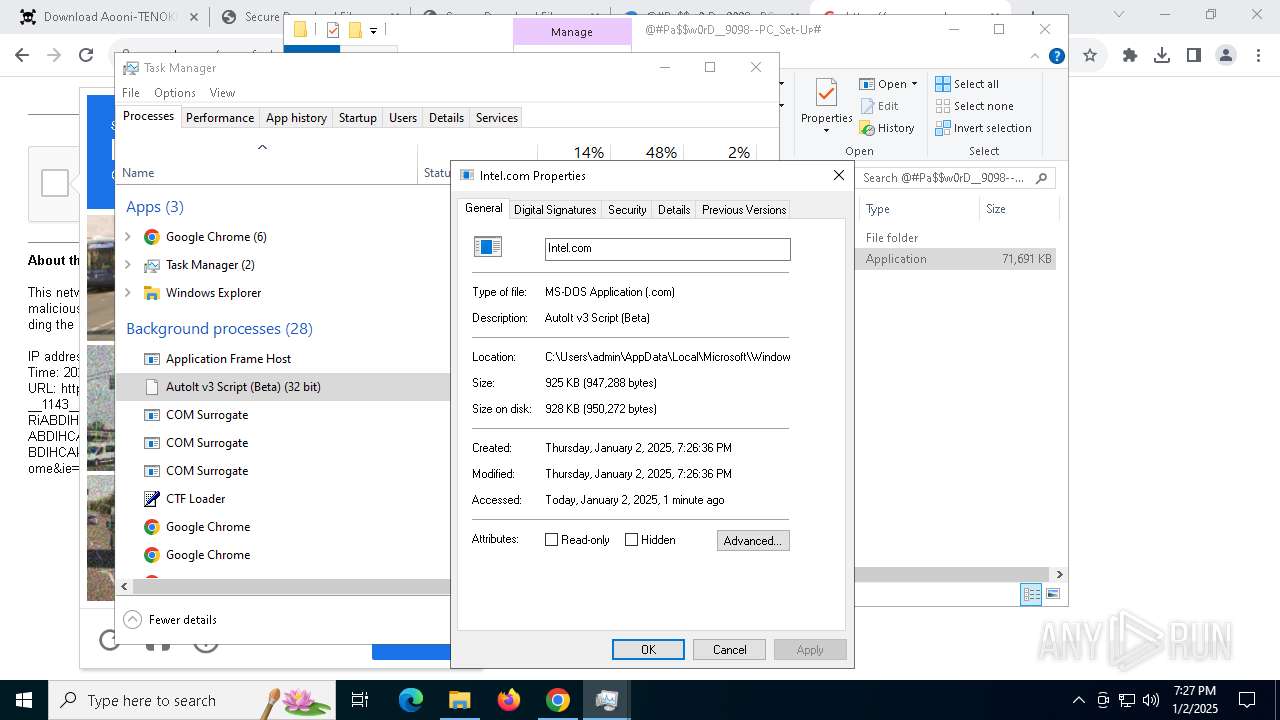
AutoIt loader has been detected (YARA)
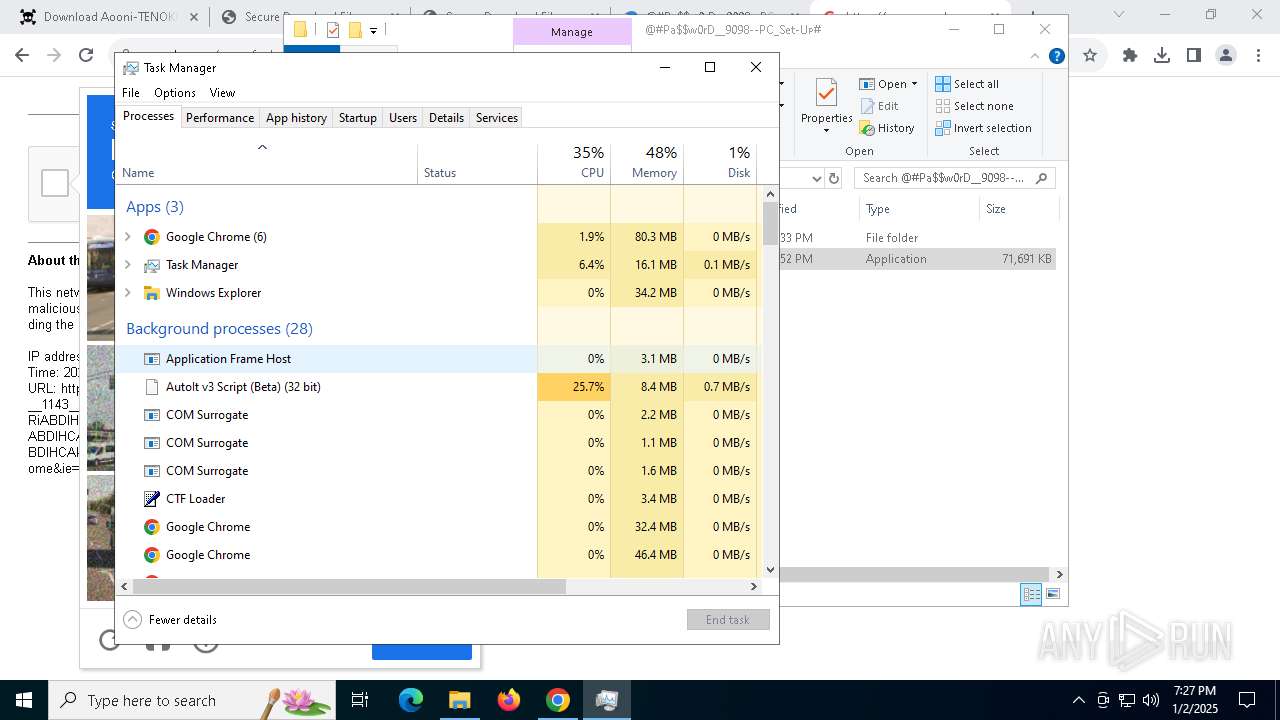
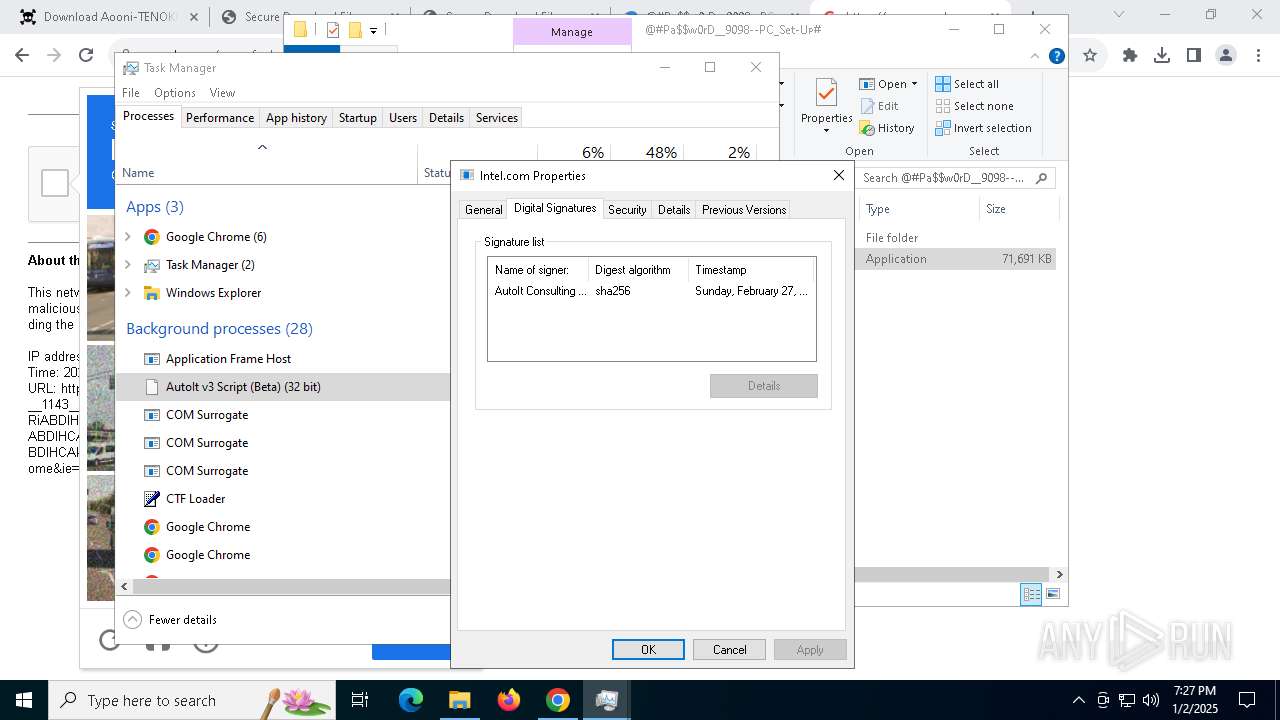
- Intel.com (PID: 1224)
LUMMA mutex has been found
- Intel.com (PID: 1224)
Actions looks like stealing of personal data
- Intel.com (PID: 1224)
Steals credentials from Web Browsers
- Intel.com (PID: 1224)
Changes powershell execution policy (Bypass)
- Intel.com (PID: 1224)
Antivirus name has been found in the command line (generic signature)
- cmd.exe (PID: 2712)
- tasklist.exe (PID: 5980)
- find.exe (PID: 6268)
- find.exe (PID: 68)
- tasklist.exe (PID: 5004)
- cmd.exe (PID: 6948)
- find.exe (PID: 1668)
- cmd.exe (PID: 1228)
- tasklist.exe (PID: 5992)
- tasklist.exe (PID: 2392)
- find.exe (PID: 4392)
- cmd.exe (PID: 7036)
- tasklist.exe (PID: 876)
- cmd.exe (PID: 2744)
- find.exe (PID: 5304)
SUSPICIOUS
Process drops legitimate windows executable
- WinRAR.exe (PID: 1144)
Starts CMD.EXE for commands execution
- Set-up.exe (PID: 6736)
- cmd.exe (PID: 4540)
- Set-up.exe (PID: 4724)
- cmd.exe (PID: 3864)
- 0E0D8GQX7X5WQ5FLZ3.tmp (PID: 3532)
Get information on the list of running processes
- cmd.exe (PID: 4540)
- cmd.exe (PID: 3864)
- 0E0D8GQX7X5WQ5FLZ3.tmp (PID: 3532)
- cmd.exe (PID: 2712)
- cmd.exe (PID: 1920)
- cmd.exe (PID: 1228)
- cmd.exe (PID: 6948)
- cmd.exe (PID: 7036)
- cmd.exe (PID: 2744)
Application launched itself
- cmd.exe (PID: 4540)
- cmd.exe (PID: 3864)
The process creates files with name similar to system file names
- WinRAR.exe (PID: 1144)
Reads security settings of Internet Explorer
- Set-up.exe (PID: 6736)
- 0E0D8GQX7X5WQ5FLZ3.tmp (PID: 6680)
- 0E0D8GQX7X5WQ5FLZ3.tmp (PID: 3532)
Executing commands from ".cmd" file
- Set-up.exe (PID: 6736)
- Set-up.exe (PID: 4724)
Using 'findstr.exe' to search for text patterns in files and output
- cmd.exe (PID: 4540)
- cmd.exe (PID: 3864)
The executable file from the user directory is run by the CMD process
- Intel.com (PID: 1224)
- Intel.com (PID: 6724)
Possibly malicious use of IEX has been detected
- Intel.com (PID: 1224)
Manipulates environment variables
- powershell.exe (PID: 3912)
Found IP address in command line
- powershell.exe (PID: 3912)
Starts POWERSHELL.EXE for commands execution
- Intel.com (PID: 1224)
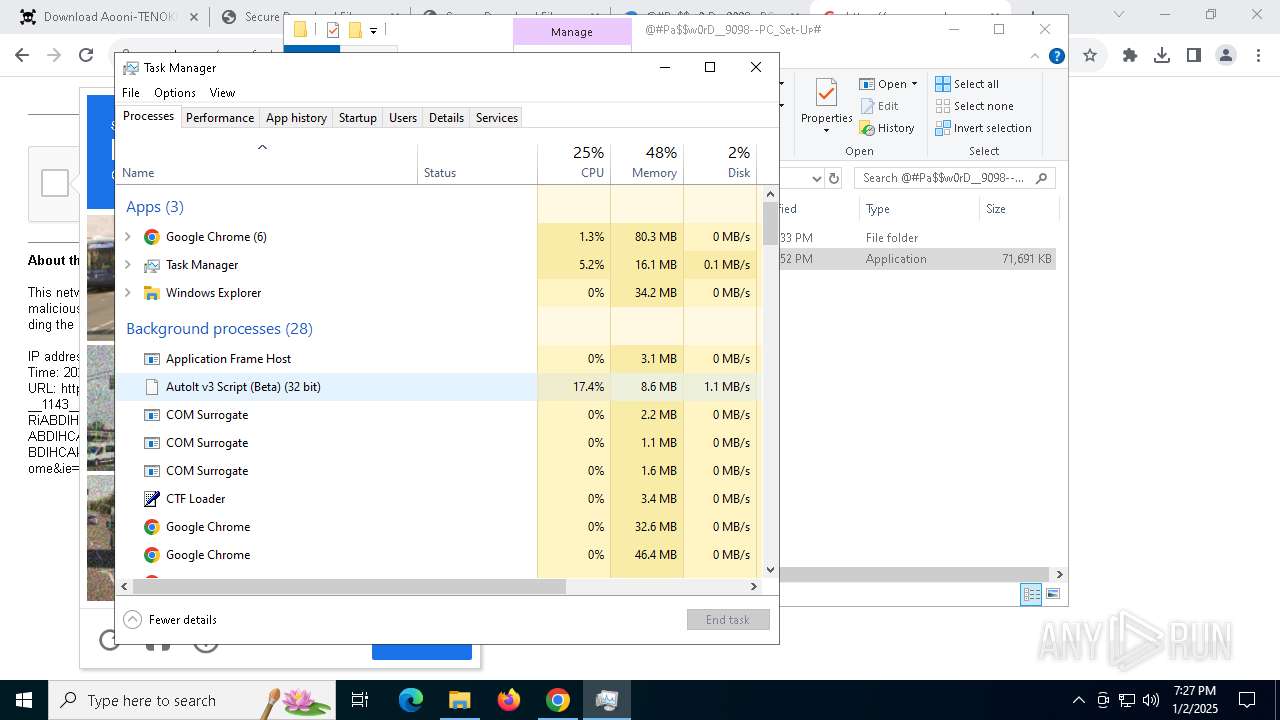
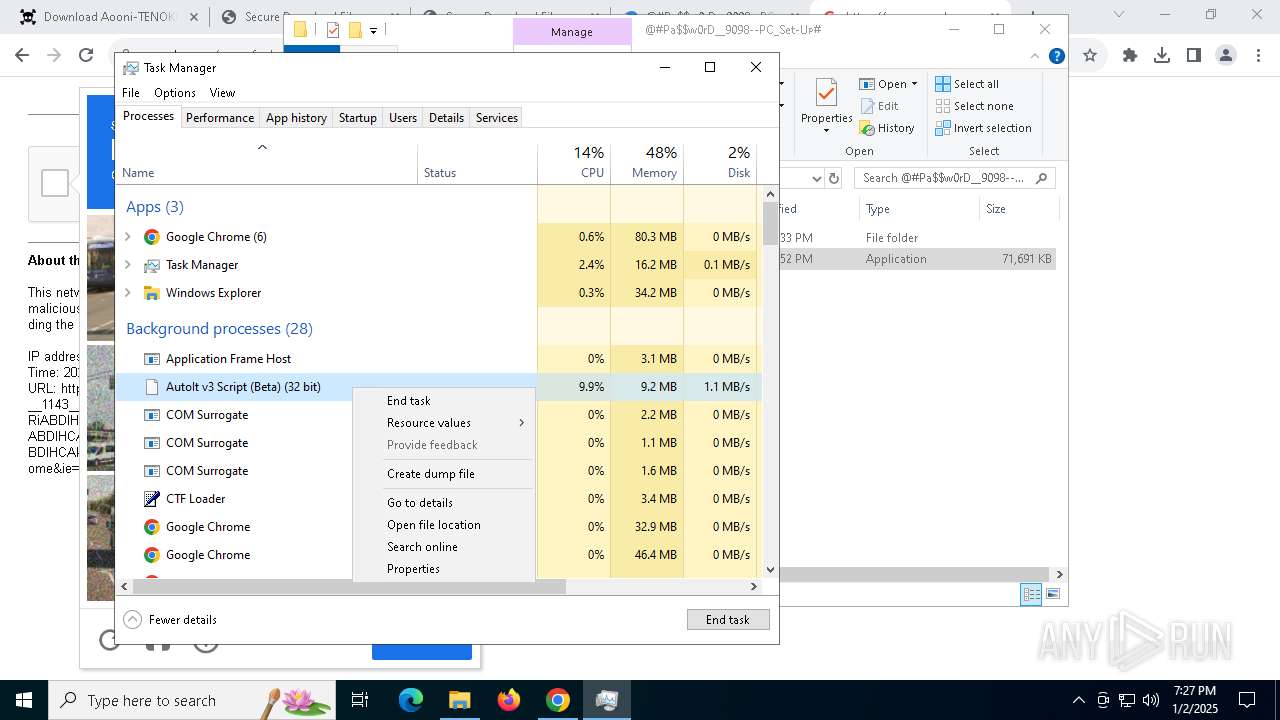
Starts the AutoIt3 executable file
- cmd.exe (PID: 4540)
- cmd.exe (PID: 3864)
Starts application with an unusual extension
- cmd.exe (PID: 4540)
- cmd.exe (PID: 3864)
Executable content was dropped or overwritten
- Intel.com (PID: 1224)
- 0E0D8GQX7X5WQ5FLZ3.tmp (PID: 6680)
- 0E0D8GQX7X5WQ5FLZ3.exe (PID: 5936)
- 0E0D8GQX7X5WQ5FLZ3.exe (PID: 3364)
- 0E0D8GQX7X5WQ5FLZ3.tmp (PID: 3532)
Gets or sets the security protocol (POWERSHELL)
- powershell.exe (PID: 3912)
Downloads file from URI via Powershell
- powershell.exe (PID: 3912)
Reads the Windows owner or organization settings
- 0E0D8GQX7X5WQ5FLZ3.tmp (PID: 6680)
- 0E0D8GQX7X5WQ5FLZ3.tmp (PID: 3532)
Uses TIMEOUT.EXE to delay execution
- 0E0D8GQX7X5WQ5FLZ3.tmp (PID: 3532)
INFO
Application launched itself
- chrome.exe (PID: 4128)
The process uses the downloaded file
- chrome.exe (PID: 2212)
- WinRAR.exe (PID: 4020)
- WinRAR.exe (PID: 1144)
- Set-up.exe (PID: 4724)
Manual execution by a user
- notepad++.exe (PID: 2380)
- WinRAR.exe (PID: 4020)
- WinRAR.exe (PID: 1144)
- notepad.exe (PID: 712)
- notepad.exe (PID: 4228)
- Set-up.exe (PID: 6736)
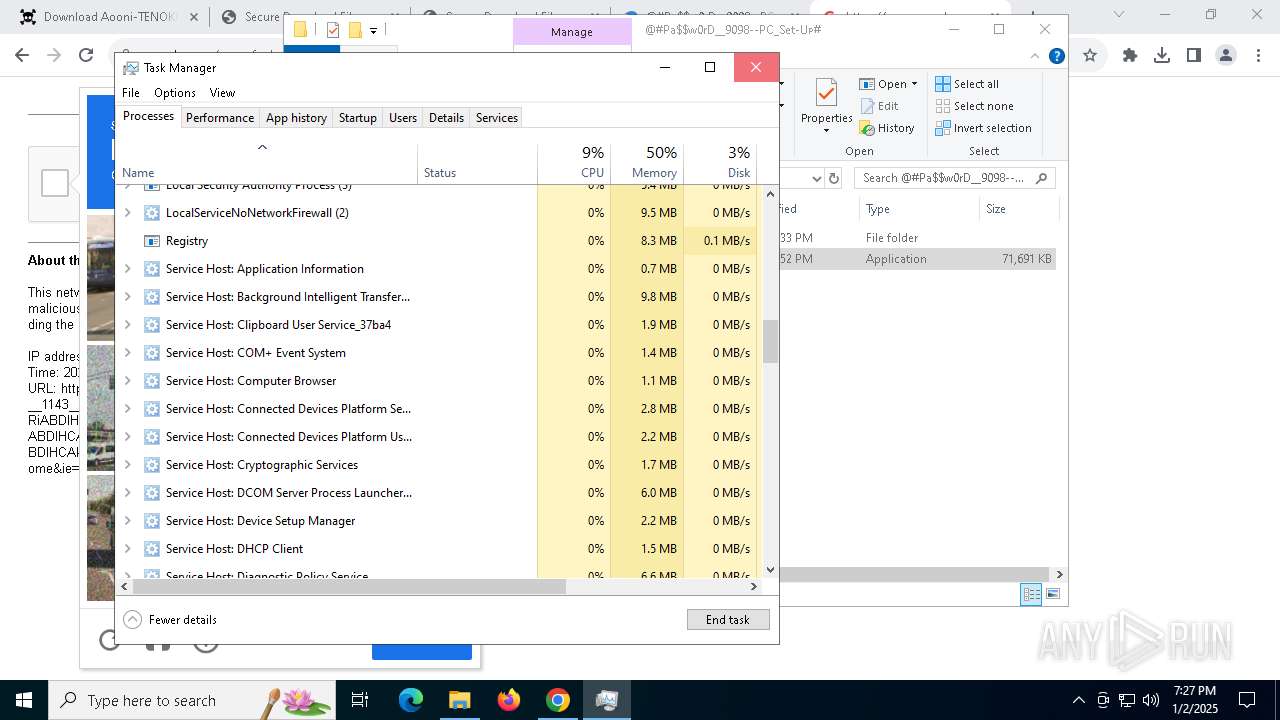
- Taskmgr.exe (PID: 2456)
- Taskmgr.exe (PID: 1348)
- Set-up.exe (PID: 4724)
Sends debugging messages
- notepad++.exe (PID: 2380)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 1144)
Creates a new folder
- cmd.exe (PID: 624)
- cmd.exe (PID: 6736)
The sample compiled with english language support
- WinRAR.exe (PID: 1144)
Reads security settings of Internet Explorer
- notepad.exe (PID: 712)
- powershell.exe (PID: 3912)
Creates files or folders in the user directory
- Set-up.exe (PID: 6736)
- extrac32.exe (PID: 5872)
- 0E0D8GQX7X5WQ5FLZ3.tmp (PID: 3532)
- Set-up.exe (PID: 4724)
- extrac32.exe (PID: 2776)
Reads the software policy settings
- Intel.com (PID: 1224)
- powershell.exe (PID: 3912)
Checks supported languages
- extrac32.exe (PID: 5872)
- Intel.com (PID: 1224)
- 0E0D8GQX7X5WQ5FLZ3.exe (PID: 5936)
- 0E0D8GQX7X5WQ5FLZ3.tmp (PID: 6680)
- 0E0D8GQX7X5WQ5FLZ3.exe (PID: 3364)
- Set-up.exe (PID: 4724)
- 0E0D8GQX7X5WQ5FLZ3.tmp (PID: 3532)
- extrac32.exe (PID: 2776)
Create files in a temporary directory
- powershell.exe (PID: 3912)
- Intel.com (PID: 1224)
- 0E0D8GQX7X5WQ5FLZ3.tmp (PID: 6680)
- 0E0D8GQX7X5WQ5FLZ3.exe (PID: 5936)
- 0E0D8GQX7X5WQ5FLZ3.exe (PID: 3364)
Reads the computer name
- 0E0D8GQX7X5WQ5FLZ3.tmp (PID: 6680)
- extrac32.exe (PID: 2776)
- Intel.com (PID: 6724)
Process checks computer location settings
- 0E0D8GQX7X5WQ5FLZ3.tmp (PID: 6680)
- Set-up.exe (PID: 4724)
- 0E0D8GQX7X5WQ5FLZ3.tmp (PID: 3532)
Script raised an exception (POWERSHELL)
- powershell.exe (PID: 3912)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
237
Monitored processes
104
Malicious processes
11
Suspicious processes
4
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 68 | find /I "sophoshealth.exe" | C:\Windows\System32\find.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Find String (grep) Utility Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 432 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --no-appcompat-clear --disable-gpu-compositing --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=27 --mojo-platform-channel-handle=6532 --field-trial-handle=1932,i,5127470520626221837,2837375941829141030,262144 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction --variations-seed-version /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Version: 122.0.6261.70 Modules
| |||||||||||||||
| 448 | cmd /c copy /b ..\Transfer + ..\Matthew + ..\Cases + ..\Puzzle + ..\Perceived + ..\Discs O | C:\Windows\SysWOW64\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 624 | cmd /c md 797812 | C:\Windows\SysWOW64\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 624 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 640 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=gpu-process --disable-gpu-sandbox --use-gl=disabled --gpu-vendor-id=5140 --gpu-device-id=140 --gpu-sub-system-id=0 --gpu-revision=0 --gpu-driver-version=10.0.19041.3636 --no-appcompat-clear --gpu-preferences=WAAAAAAAAADoABAMAAAAAAAAAAAAAAAAAABgAAAAAAA4AAAAAAAAAAAAAABEAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAGAAAAAAAAAAYAAAAAAAAAAgAAAAAAAAACAAAAAAAAAAIAAAAAAAAAA== --mojo-platform-channel-handle=5348 --field-trial-handle=1932,i,5127470520626221837,2837375941829141030,262144 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction --variations-seed-version /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 122.0.6261.70 Modules
| |||||||||||||||
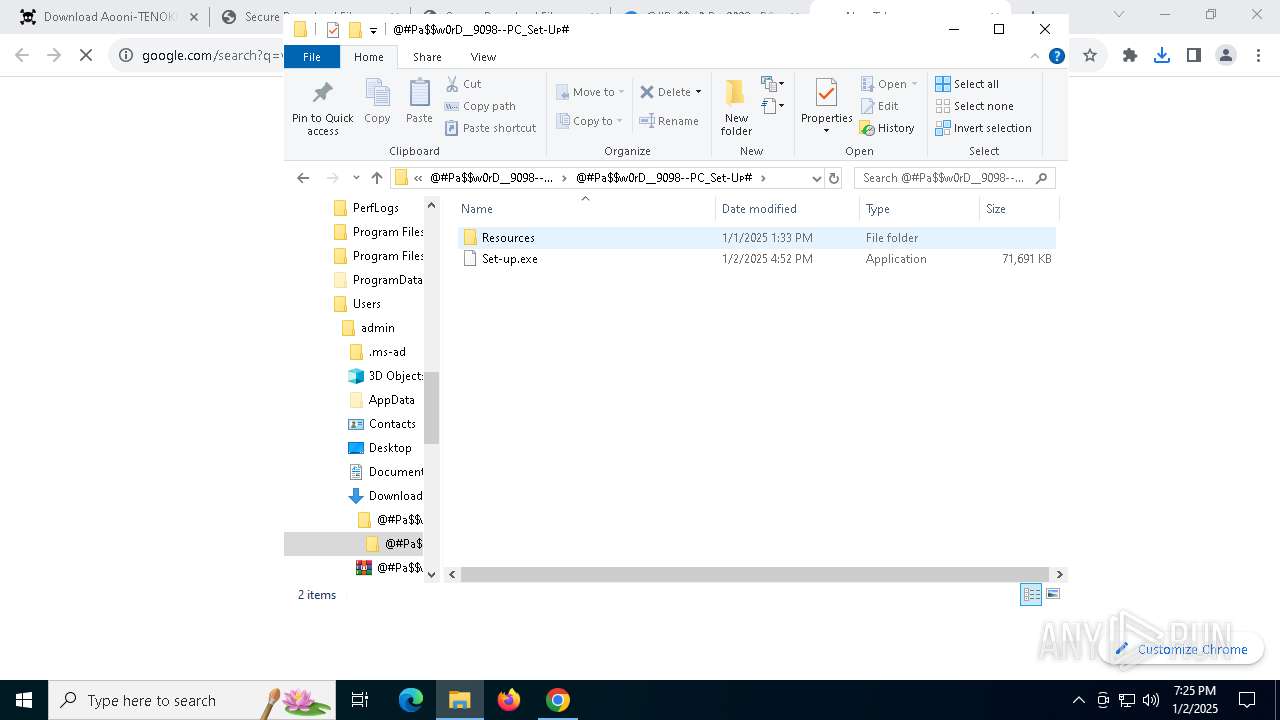
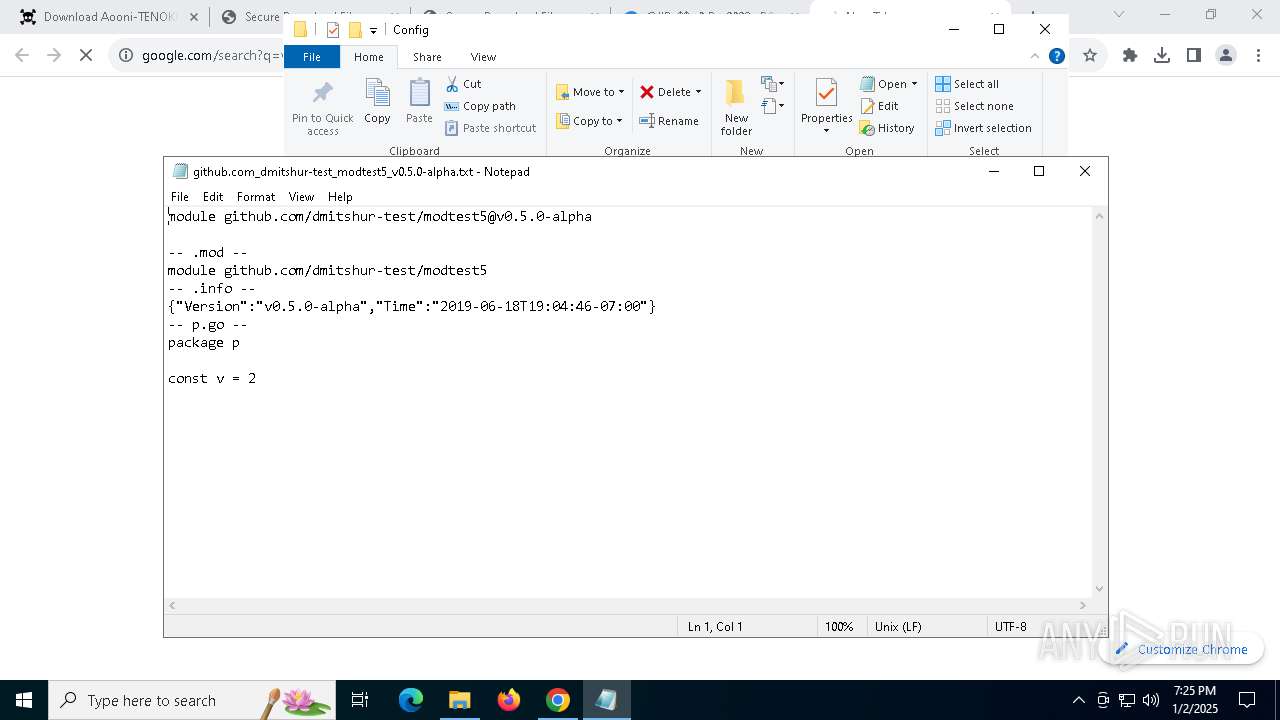
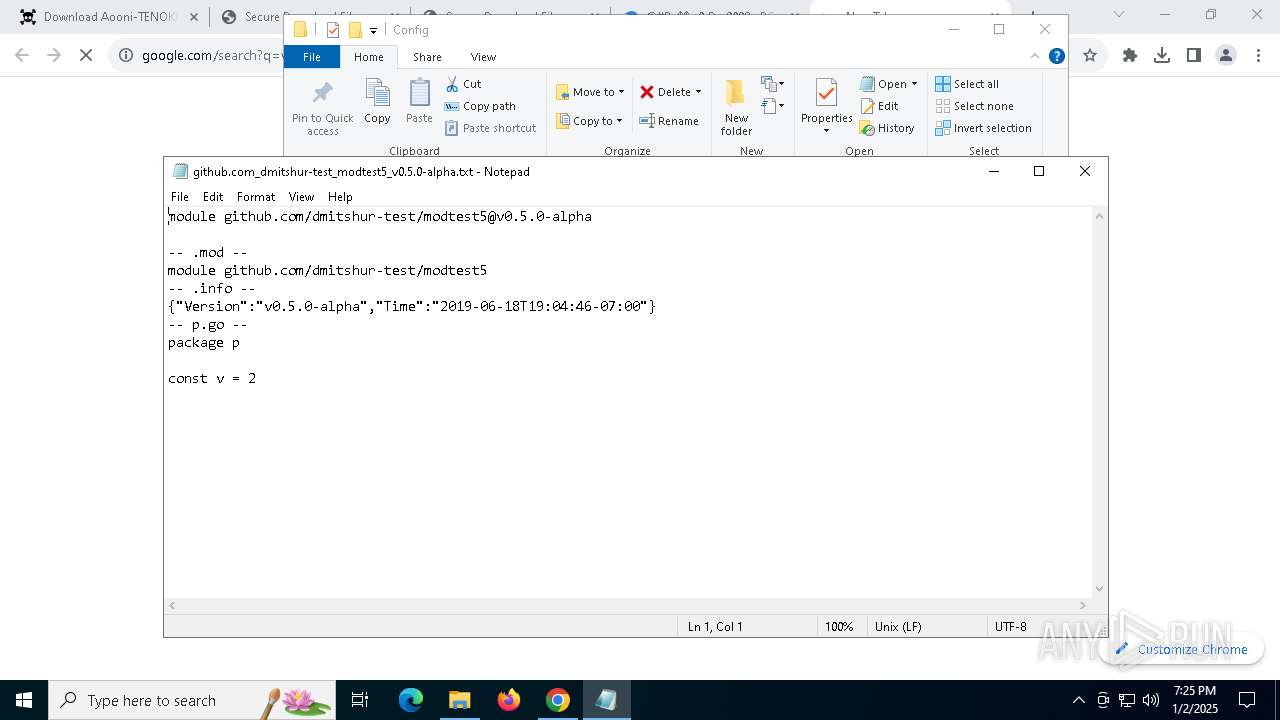
| 712 | "C:\WINDOWS\system32\NOTEPAD.EXE" C:\Users\admin\Downloads\@#Pa$w0rD__9098--PC_Set-Uᴘ#\@#Pa$w0rD__9098--PC_Set-Uᴘ#\Resources\Data\Config\github.com_dmitshur-test_modtest5_v0.5.0-alpha.txt | C:\Windows\System32\notepad.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 876 | tasklist /FI "IMAGENAME eq avastui.exe" /FO CSV /NH | C:\Windows\System32\tasklist.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Lists the current running tasks Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 936 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=chrome.mojom.ProcessorMetrics --lang=en-US --service-sandbox-type=none --disable-quic --no-appcompat-clear --mojo-platform-channel-handle=4968 --field-trial-handle=1932,i,5127470520626221837,2837375941829141030,262144 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction --variations-seed-version /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 122.0.6261.70 Modules
| |||||||||||||||
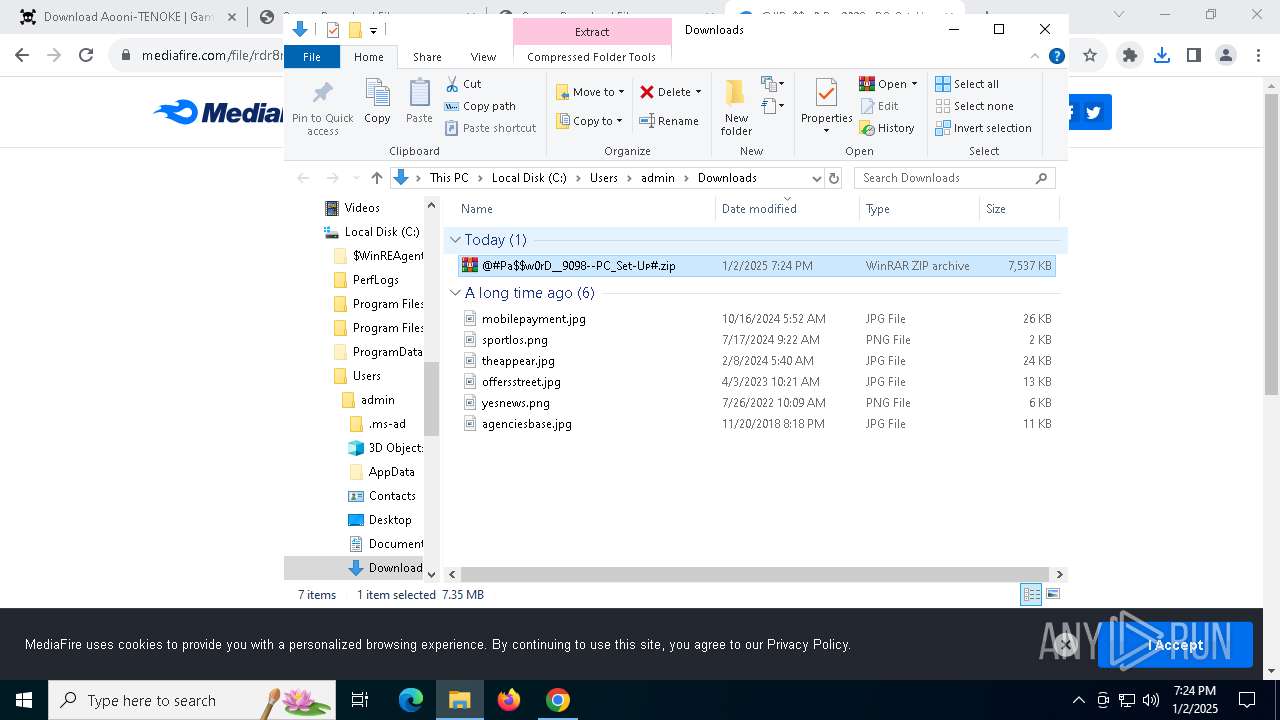
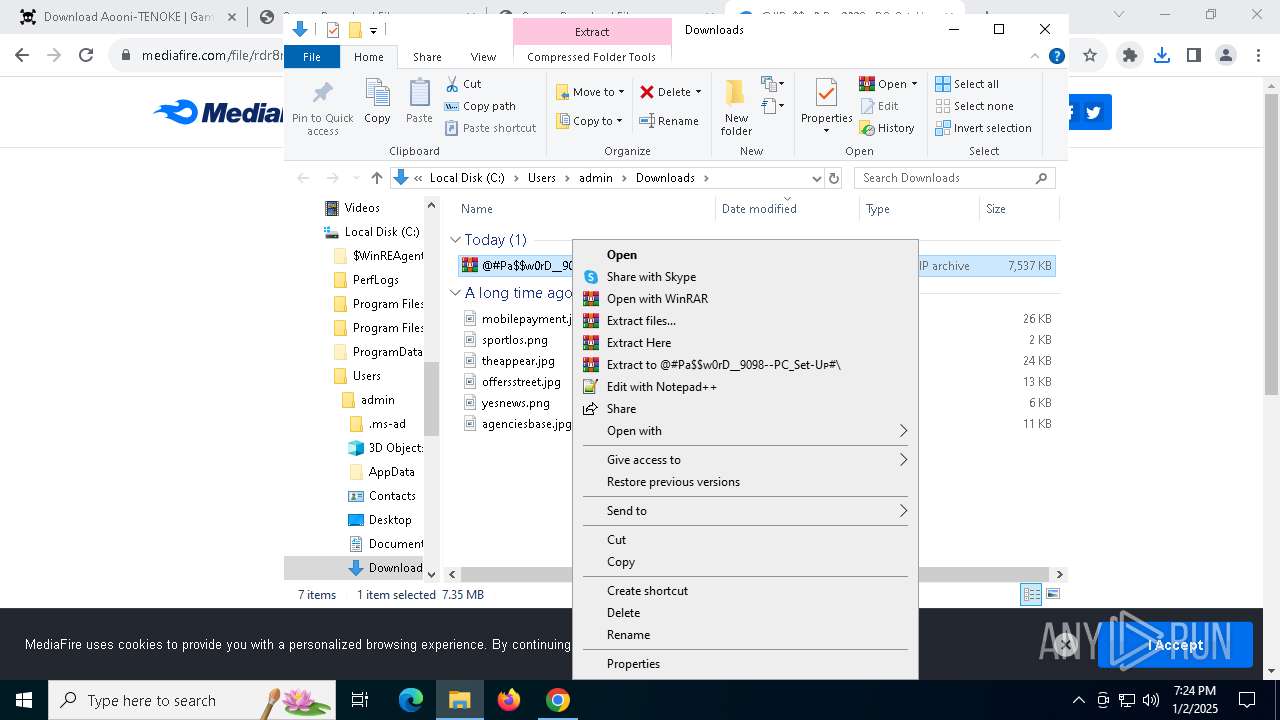
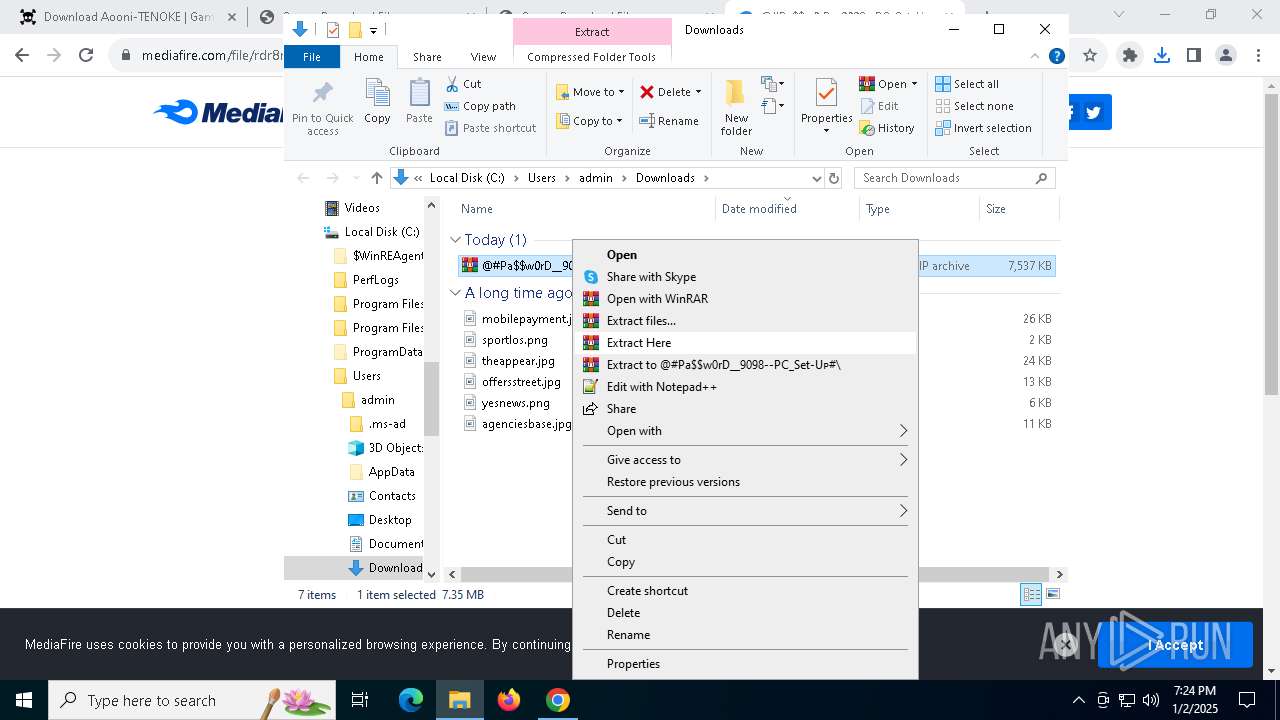
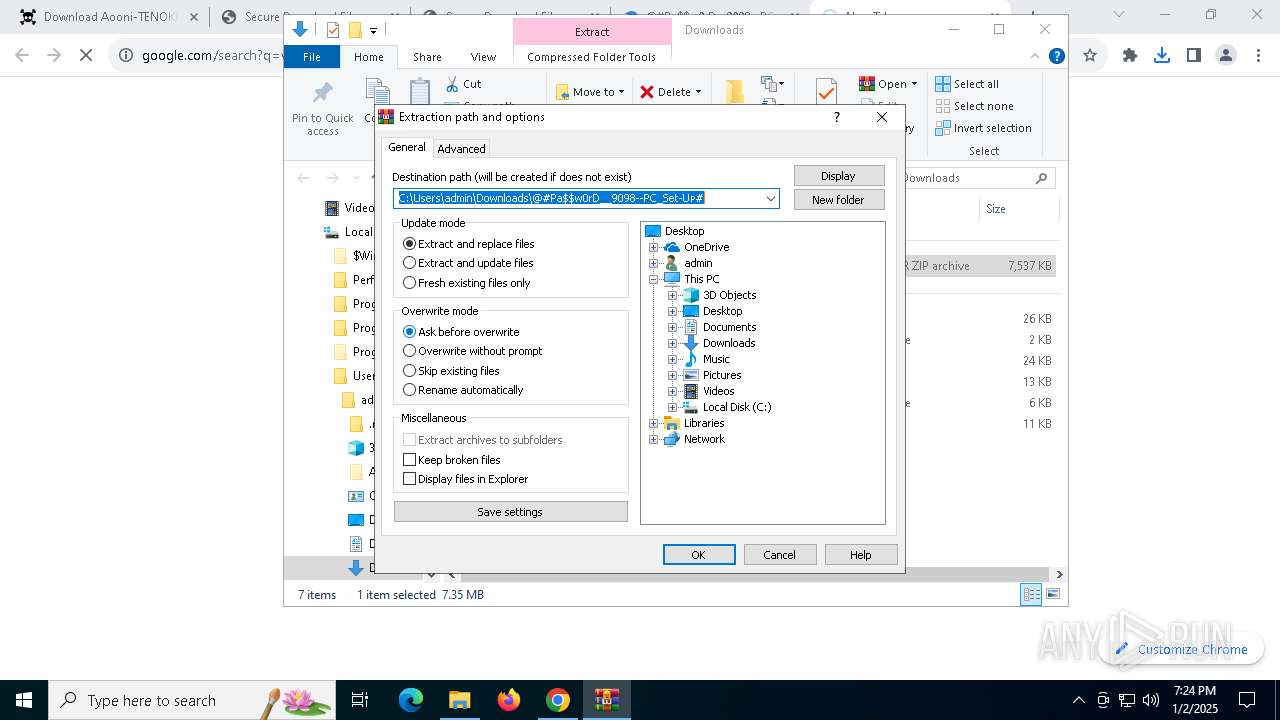
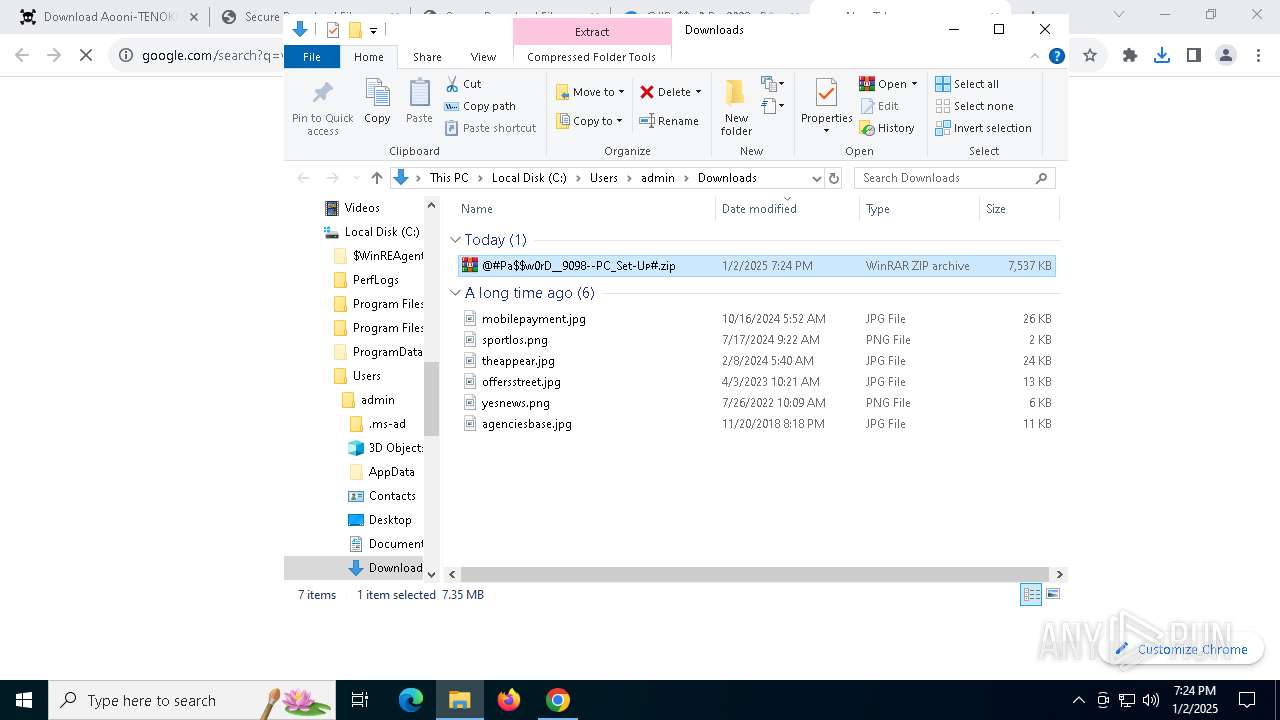
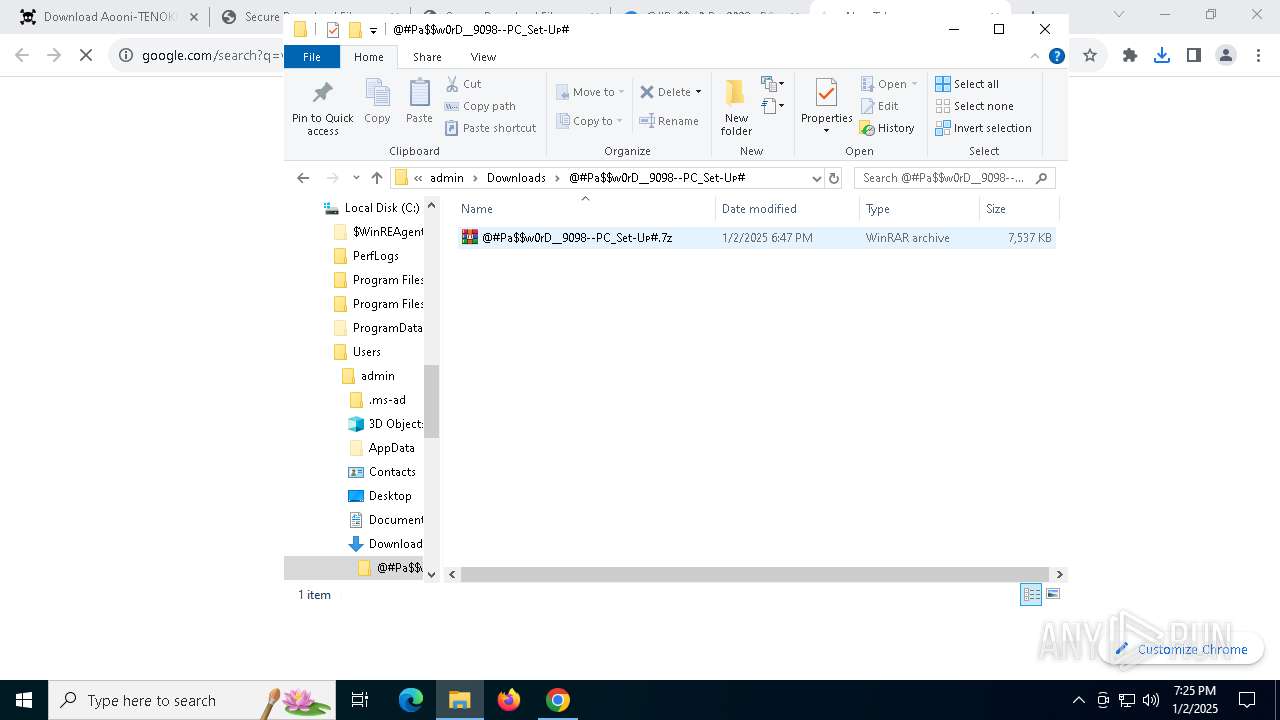
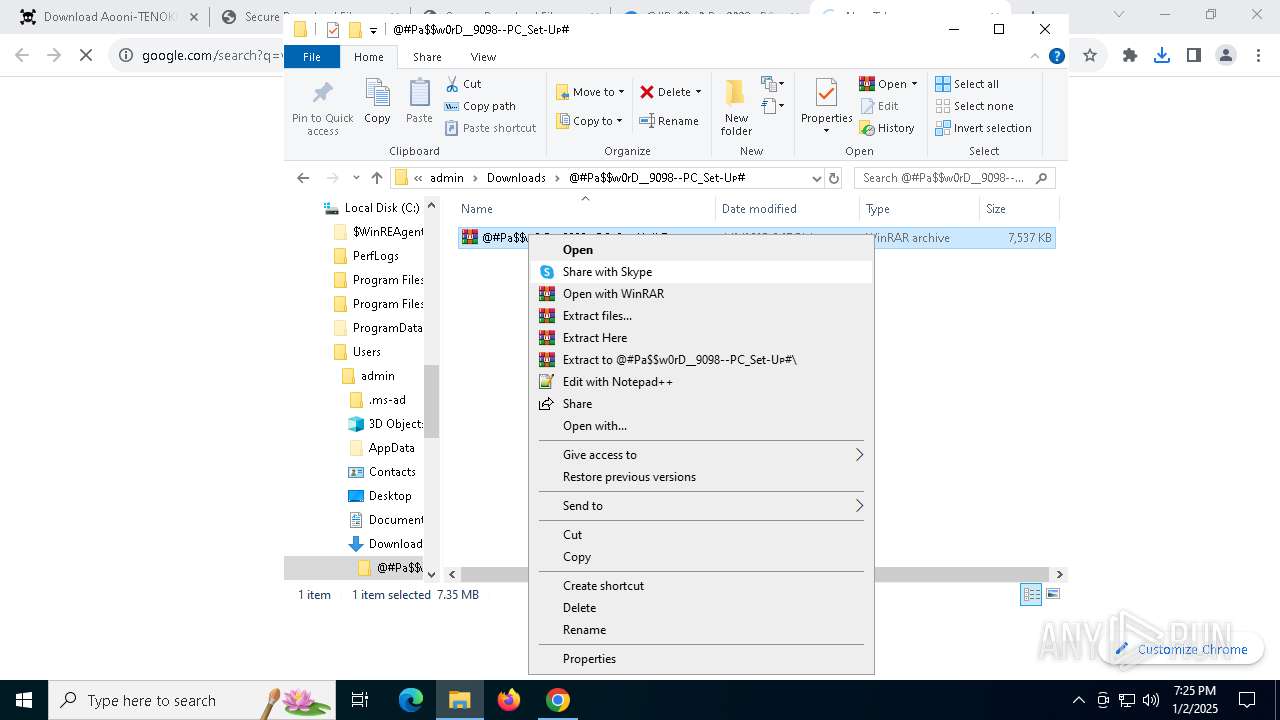
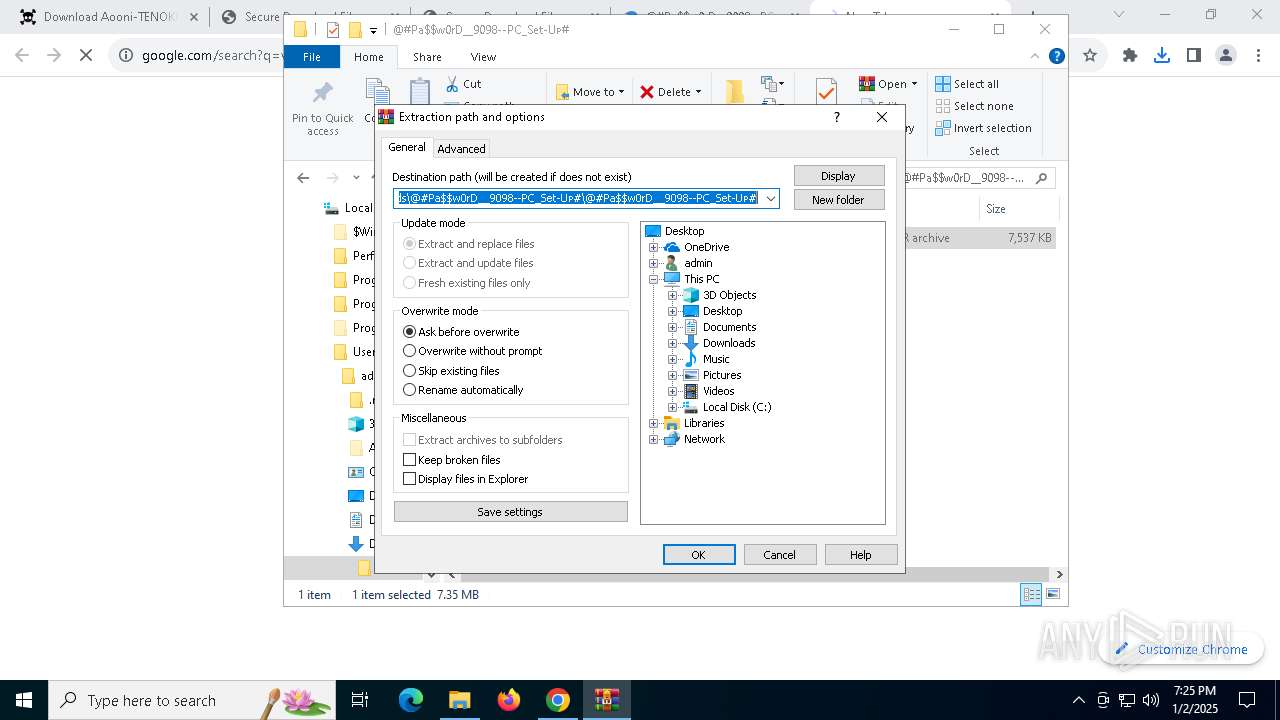
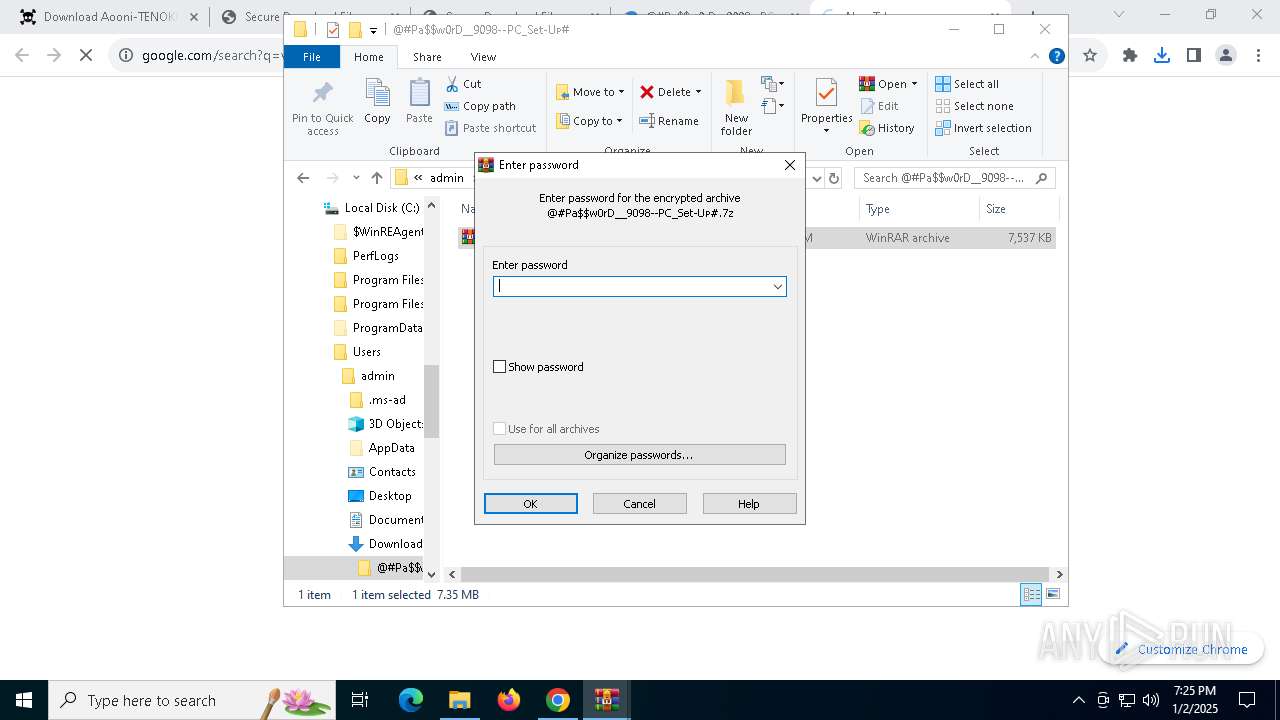
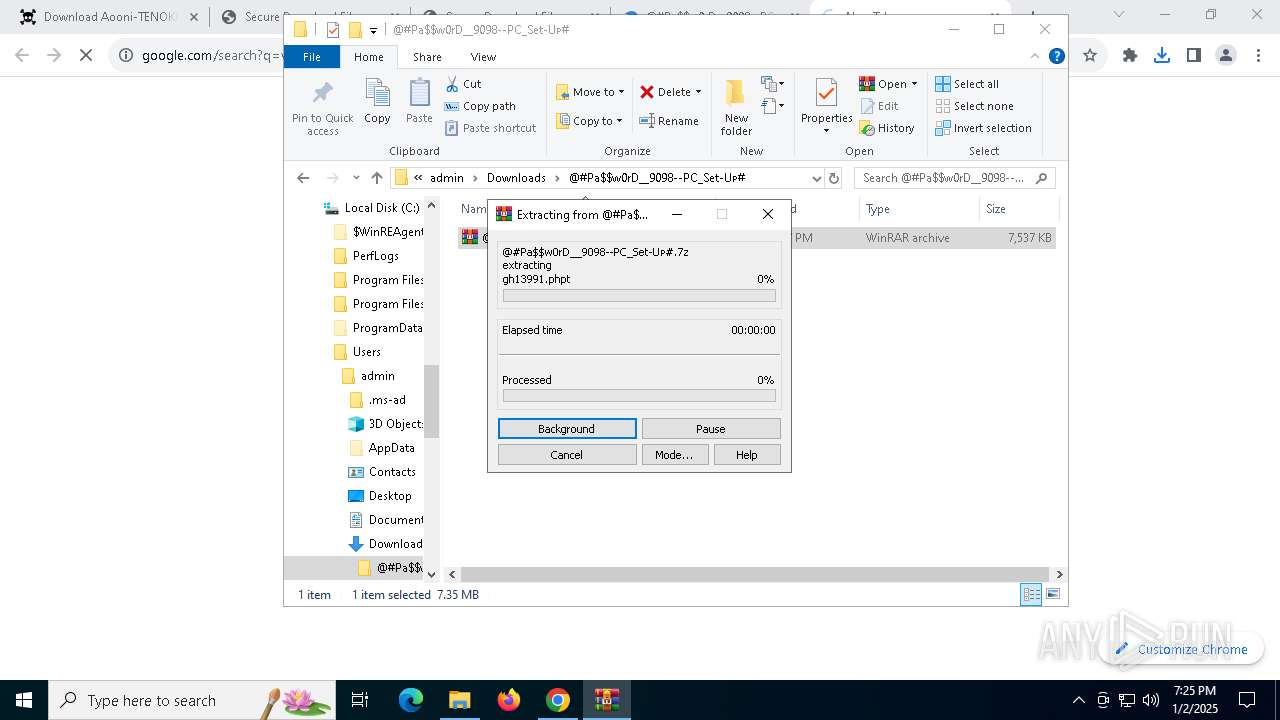
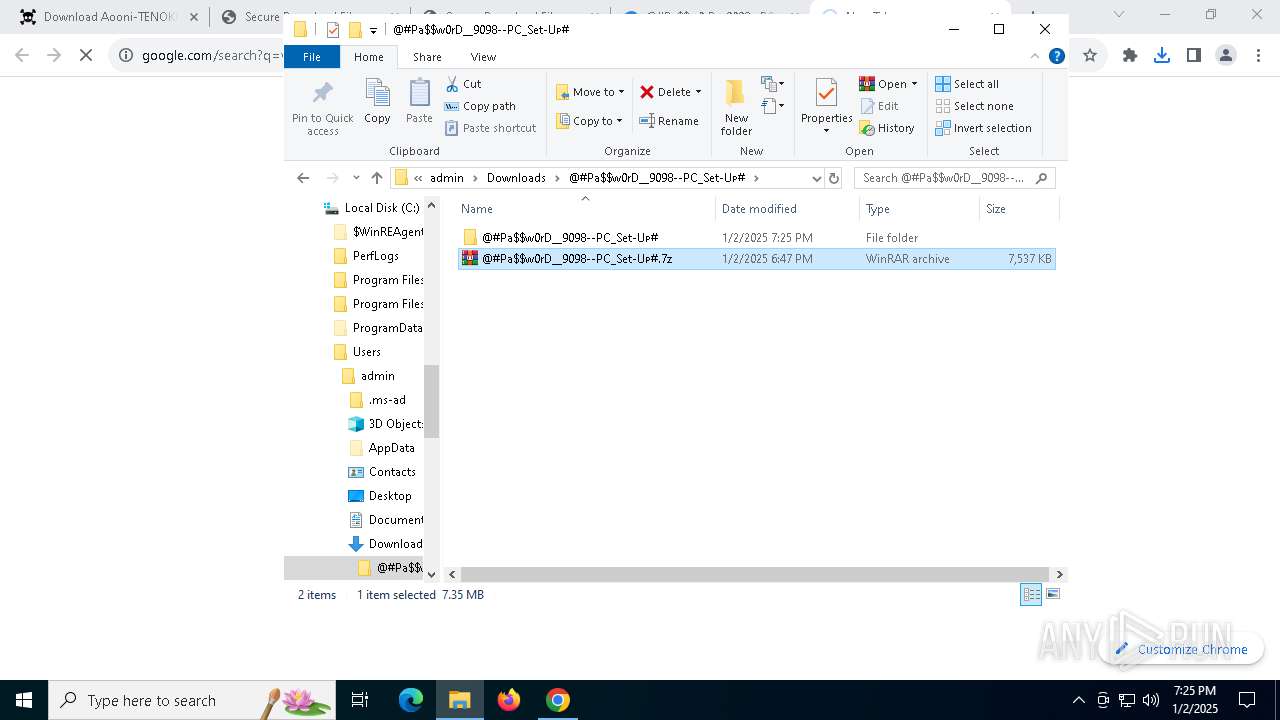
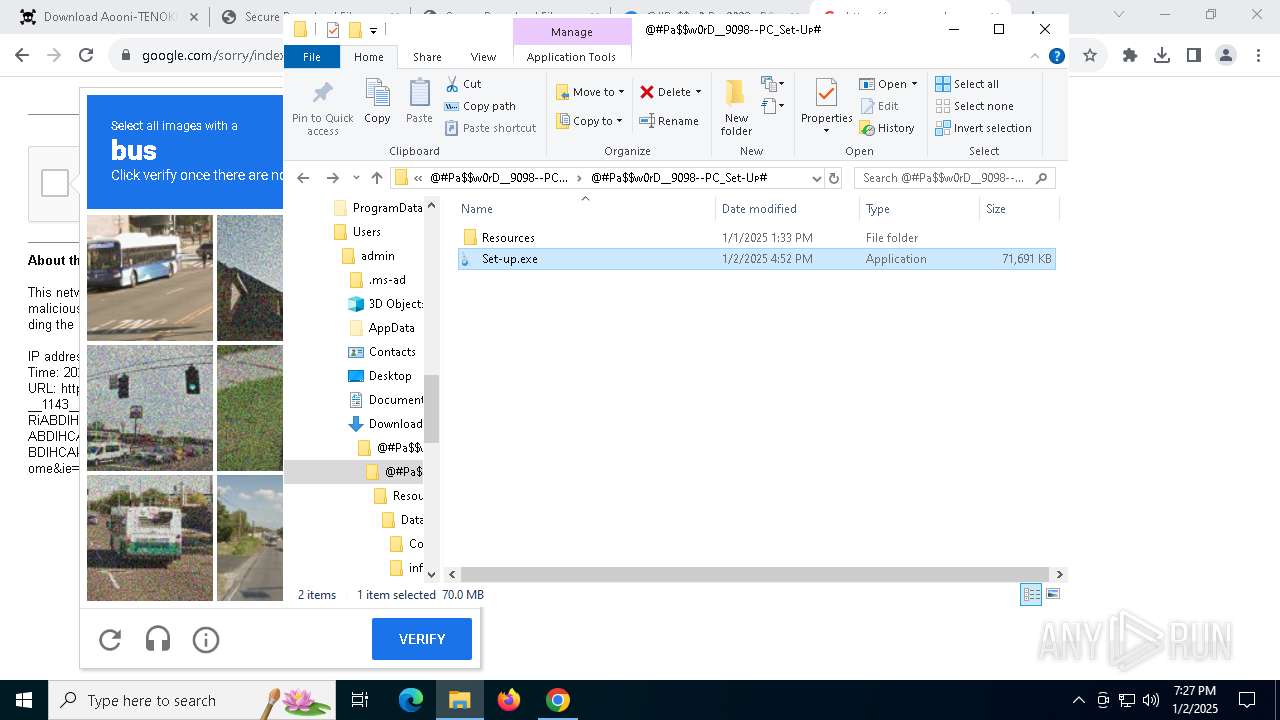
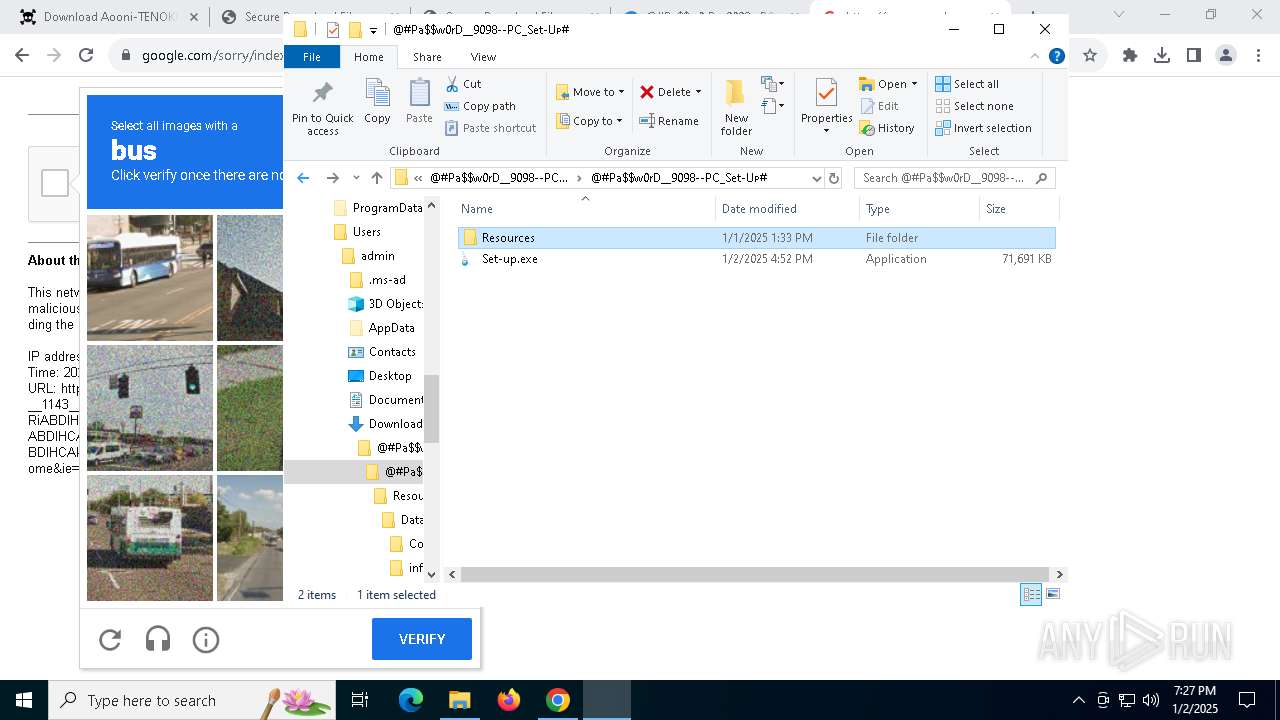
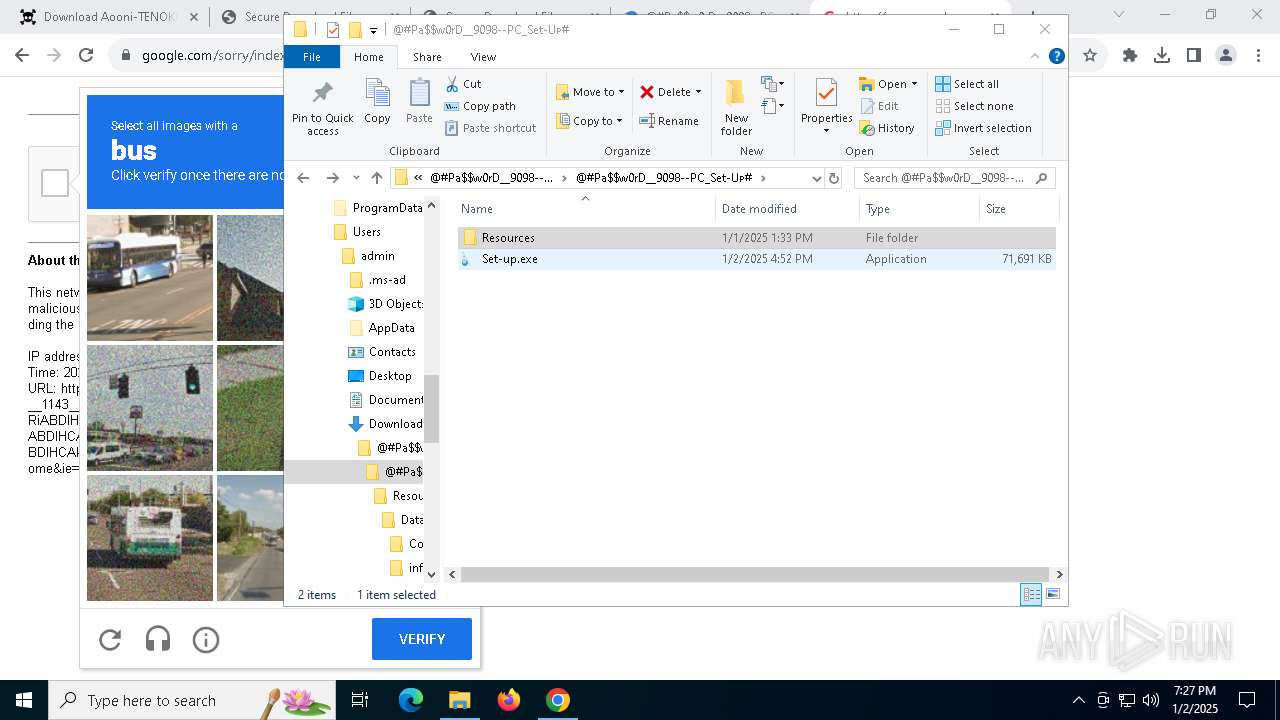
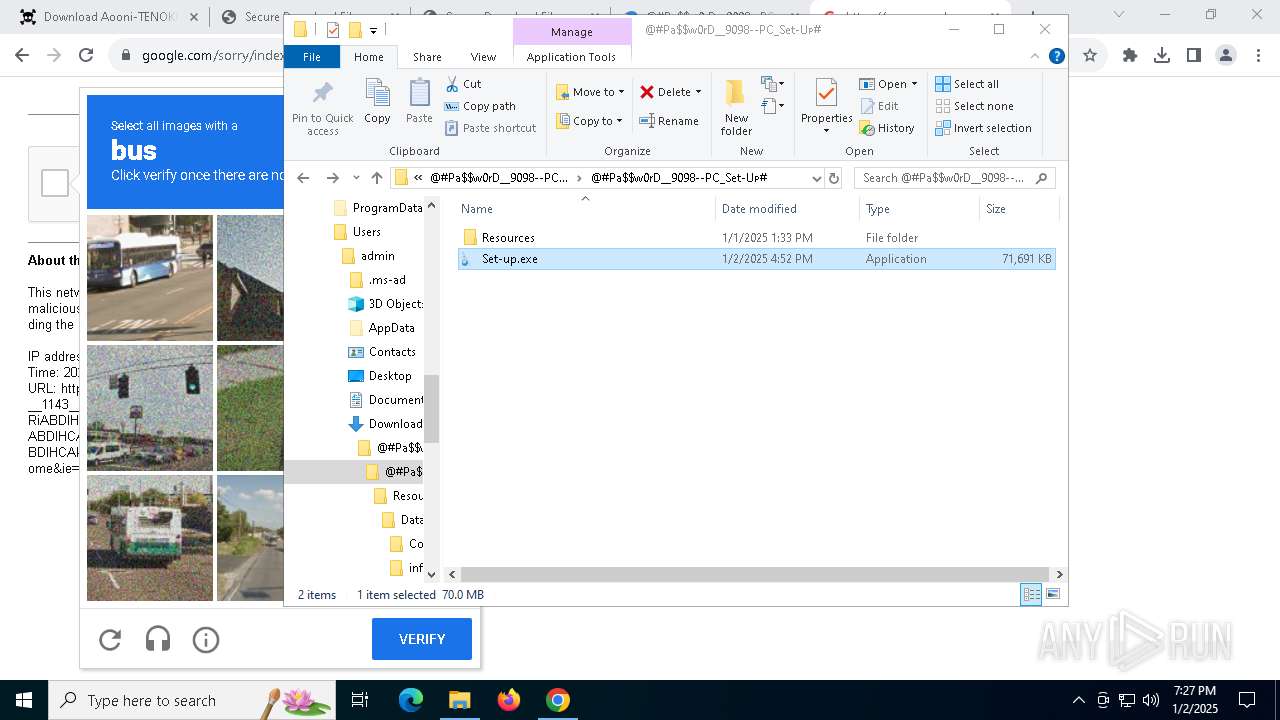
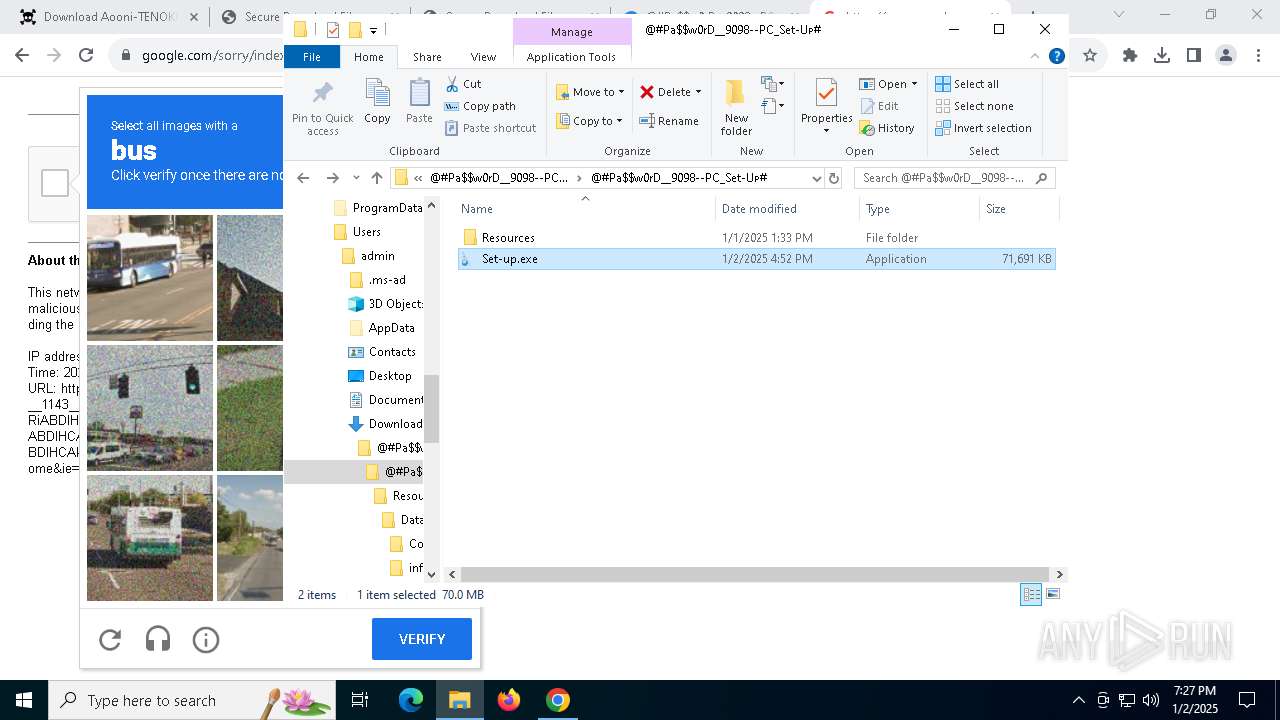
| 1144 | "C:\Program Files\WinRAR\WinRAR.exe" x -iext -ow -ver -- "C:\Users\admin\Downloads\@#Pa$w0rD__9098--PC_Set-Uᴘ#\@#Pa$w0rD__9098--PC_Set-Uᴘ#.7z" "?\" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
Total events
23 621
Read events
23 520
Write events
51
Delete events
50
Modification events
| (PID) Process: | (4128) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (4128) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (4128) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (4128) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\StabilityMetrics |
| Operation: | write | Name: | user_experience_metrics.stability.exited_cleanly |
Value: 0 | |||
| (PID) Process: | (4128) chrome.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Google\Update\ClientStateMedium\{8A69D345-D564-463C-AFF1-A69D9E530F96} |
| Operation: | write | Name: | usagestats |
Value: 0 | |||
| (PID) Process: | (4128) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Spelling\Dictionaries |
| Operation: | delete value | Name: | en-US |
Value: | |||
| (PID) Process: | (4128) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Spelling\Dictionaries |
| Operation: | delete value | Name: | en |
Value: | |||
| (PID) Process: | (4128) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Spelling\Dictionaries |
| Operation: | delete value | Name: | _Global_ |
Value: | |||
| (PID) Process: | (2212) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Shell Extensions\Cached |
| Operation: | write | Name: | {2781761E-28E0-4109-99FE-B9D127C57AFE} {56FFCC30-D398-11D0-B2AE-00A0C908FA49} 0xFFFF |
Value: 0100000000000000169DCBEE4B5DDB01 | |||
| (PID) Process: | (4128) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Common\Rlz\Events\C |
| Operation: | write | Name: | C1I |
Value: 1 | |||
Executable files
23
Suspicious files
439
Text files
103
Unknown types
10
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4128 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\commerce_subscription_db\LOG.old~RF135dd3.TMP | — | |
MD5:— | SHA256:— | |||
| 4128 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\commerce_subscription_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 4128 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\discounts_db\LOG.old~RF135dd3.TMP | — | |
MD5:— | SHA256:— | |||
| 4128 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\chrome_cart_db\LOG.old~RF135de2.TMP | — | |
MD5:— | SHA256:— | |||
| 4128 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\chrome_cart_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 4128 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\discounts_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 4128 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\PersistentOriginTrials\LOG.old~RF135df2.TMP | — | |
MD5:— | SHA256:— | |||
| 4128 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\PersistentOriginTrials\LOG.old | — | |
MD5:— | SHA256:— | |||
| 4128 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\parcel_tracking_db\LOG.old~RF135df2.TMP | — | |
MD5:— | SHA256:— | |||
| 4128 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\coupon_db\LOG.old~RF135df2.TMP | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
40
TCP/UDP connections
178
DNS requests
326
Threats
55
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2632 | svchost.exe | GET | 200 | 2.18.244.211:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
2092 | svchost.exe | GET | 206 | 142.251.36.14:80 | http://dl.google.com/release2/chrome_component/ads7ltfl2gw6hxwgakn3sxrkoijq_9.53.0/gcmjkmgdlgnkkcocmoeiminaijmmjnii_9.53.0_all_iky7dhj3jd5su3axccoshyd4xm.crx3 | unknown | — | — | whitelisted |
2092 | svchost.exe | GET | 206 | 142.251.36.14:80 | http://dl.google.com/release2/chrome_component/ads7ltfl2gw6hxwgakn3sxrkoijq_9.53.0/gcmjkmgdlgnkkcocmoeiminaijmmjnii_9.53.0_all_iky7dhj3jd5su3axccoshyd4xm.crx3 | unknown | — | — | whitelisted |
2092 | svchost.exe | GET | 206 | 142.251.36.14:80 | http://dl.google.com/release2/chrome_component/ads7ltfl2gw6hxwgakn3sxrkoijq_9.53.0/gcmjkmgdlgnkkcocmoeiminaijmmjnii_9.53.0_all_iky7dhj3jd5su3axccoshyd4xm.crx3 | unknown | — | — | whitelisted |
2092 | svchost.exe | HEAD | 403 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/AMpg5-cnrANo_2018.8.8.0/2018.8.8.0_win64_win_third_party_module_list.crx3 | unknown | — | — | whitelisted |
2092 | svchost.exe | GET | 206 | 142.251.36.14:80 | http://dl.google.com/release2/chrome_component/ads7ltfl2gw6hxwgakn3sxrkoijq_9.53.0/gcmjkmgdlgnkkcocmoeiminaijmmjnii_9.53.0_all_iky7dhj3jd5su3axccoshyd4xm.crx3 | unknown | — | — | whitelisted |
2092 | svchost.exe | HEAD | 302 | 142.251.36.46:80 | http://redirector.gvt1.com/edgedl/release2/chrome_component/AMpg5-cnrANo_2018.8.8.0/2018.8.8.0_win64_win_third_party_module_list.crx3 | unknown | — | — | whitelisted |
2092 | svchost.exe | GET | 206 | 142.251.36.14:80 | http://dl.google.com/release2/chrome_component/ads7ltfl2gw6hxwgakn3sxrkoijq_9.53.0/gcmjkmgdlgnkkcocmoeiminaijmmjnii_9.53.0_all_iky7dhj3jd5su3axccoshyd4xm.crx3 | unknown | — | — | whitelisted |
2092 | svchost.exe | GET | 302 | 142.251.36.46:80 | http://redirector.gvt1.com/edgedl/release2/chrome_component/AMpg5-cnrANo_2018.8.8.0/2018.8.8.0_win64_win_third_party_module_list.crx3 | unknown | — | — | whitelisted |
2092 | svchost.exe | GET | 302 | 142.251.36.46:80 | http://redirector.gvt1.com/edgedl/release2/chrome_component/AMpg5-cnrANo_2018.8.8.0/2018.8.8.0_win64_win_third_party_module_list.crx3 | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | unknown |
2632 | svchost.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4160 | RUXIMICS.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | 2.18.244.211:80 | crl.microsoft.com | Akamai International B.V. | FR | whitelisted |
2632 | svchost.exe | 2.18.244.211:80 | crl.microsoft.com | Akamai International B.V. | FR | whitelisted |
4160 | RUXIMICS.exe | 2.18.244.211:80 | crl.microsoft.com | Akamai International B.V. | FR | whitelisted |
4712 | MoUsoCoreWorker.exe | 173.223.117.131:80 | www.microsoft.com | AKAMAI-AS | US | whitelisted |
4160 | RUXIMICS.exe | 173.223.117.131:80 | www.microsoft.com | AKAMAI-AS | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| unknown |
www.microsoft.com |
| whitelisted |
game3rb.com |
| whitelisted |
accounts.google.com |
| whitelisted |
a.nel.cloudflare.com |
| whitelisted |
challenges.cloudflare.com |
| whitelisted |
www.google.com |
| whitelisted |
fonts.googleapis.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
6408 | chrome.exe | Not Suspicious Traffic | INFO [ANY.RUN] Cloudflare Network Error Logging (NEL) |
6408 | chrome.exe | Not Suspicious Traffic | INFO [ANY.RUN] Cloudflare Network Error Logging (NEL) |
6408 | chrome.exe | Not Suspicious Traffic | INFO [ANY.RUN] Cloudflare Network Error Logging (NEL) |
6408 | chrome.exe | Not Suspicious Traffic | INFO [ANY.RUN] Cloudflare turnstile CAPTCHA challenge |
6408 | chrome.exe | Not Suspicious Traffic | INFO [ANY.RUN] Cloudflare turnstile CAPTCHA challenge |
6408 | chrome.exe | Not Suspicious Traffic | INFO [ANY.RUN] Cloudflare turnstile CAPTCHA challenge |
6408 | chrome.exe | Not Suspicious Traffic | INFO [ANY.RUN] Cloudflare content delivery network (cdnjs .cloudflare .com) |
6408 | chrome.exe | Not Suspicious Traffic | INFO [ANY.RUN] Cloudflare content delivery network (cdnjs .cloudflare .com) |
6408 | chrome.exe | Not Suspicious Traffic | INFO [ANY.RUN] BootstrapCDN (maxcdn .bootstrapcdn .com) |
6408 | chrome.exe | Not Suspicious Traffic | INFO [ANY.RUN] BootstrapCDN (maxcdn .bootstrapcdn .com) |
Process | Message |
|---|---|
notepad++.exe | VerifyLibrary: C:\Program Files\Notepad++\SciLexer.dll
|
notepad++.exe | VerifyLibrary: certificate revocation checking is disabled
|
notepad++.exe | ED255D9151912E40DF048A56288E969A8D0DAFA3
|
notepad++.exe | VerifyLibrary: certificate revocation checking is disabled
|
notepad++.exe | VerifyLibrary: C:\Program Files\Notepad++\updater\gup.exe
|
notepad++.exe | VerifyLibrary: error while getting certificate informations
|