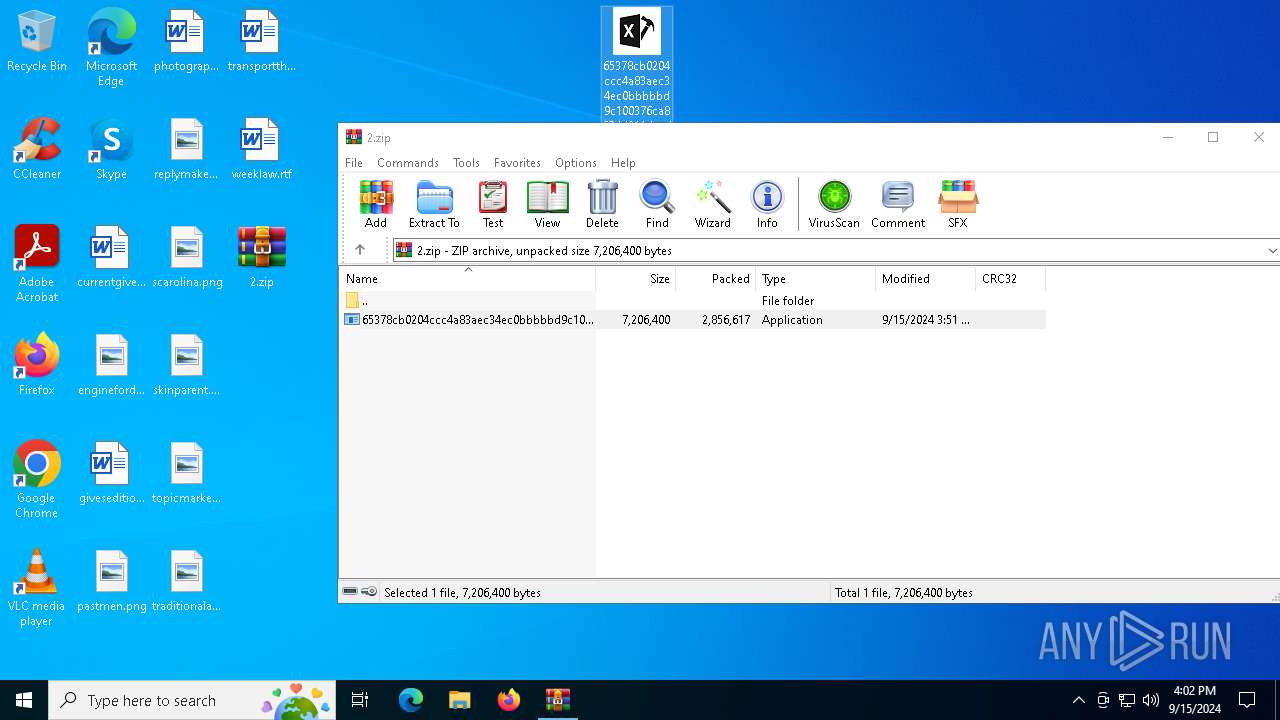
| File name: | 2.zip |
| Full analysis: | https://app.any.run/tasks/753caaad-fb7e-495b-9ec3-fa5bf9701aa4 |
| Verdict: | Malicious activity |
| Threats: | Lumma is an information stealer, developed using the C programming language. It is offered for sale as a malware-as-a-service, with several plans available. It usually targets cryptocurrency wallets, login credentials, and other sensitive information on a compromised system. The malicious software regularly gets updates that improve and expand its functionality, making it a serious stealer threat. |
| Analysis date: | September 15, 2024, 16:01:40 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
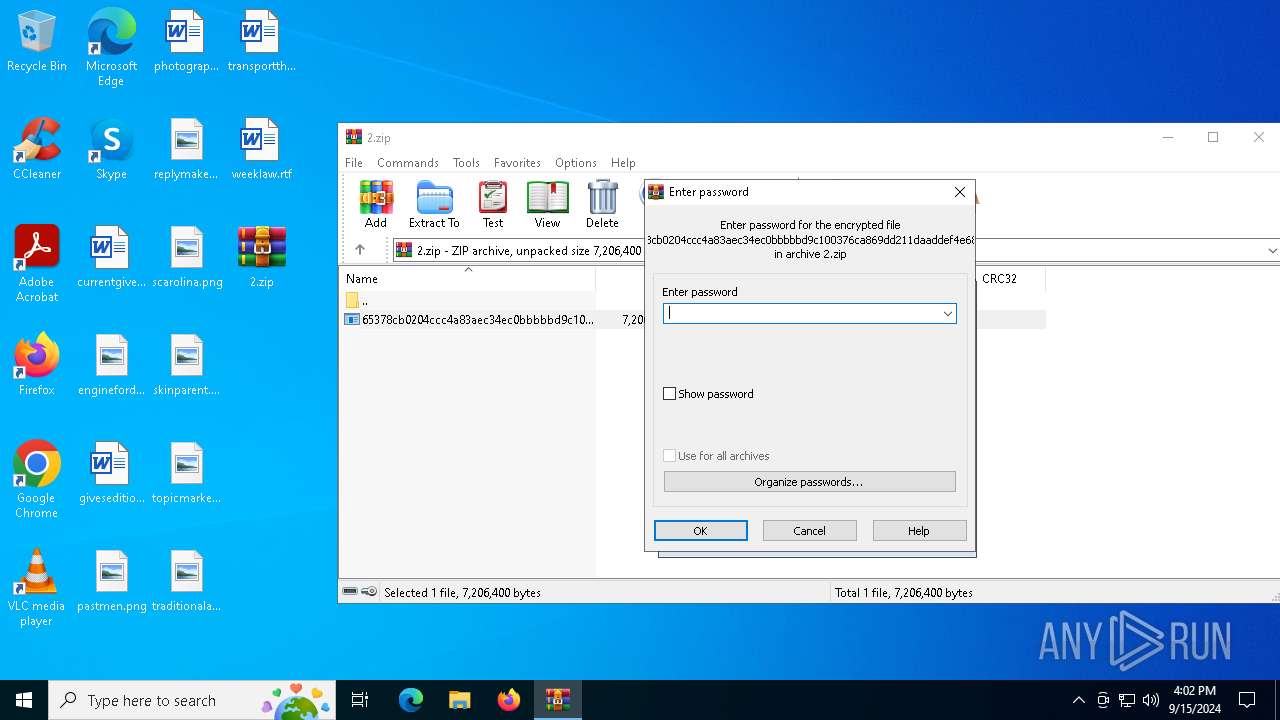
| File info: | Zip archive data, at least v5.1 to extract, compression method=AES Encrypted |
| MD5: | E79ED8C77862685356316587E5F2BCC3 |
| SHA1: | 0E0A77221E73EE8B235FA59713B7BF91D10D72A4 |
| SHA256: | A891223BA150A45F0907D86E8C809CEB73D103BB48CB1E700D54F78CB308CF40 |
| SSDEEP: | 98304:v4eBrNwbLrUB7/phIcwST9UWLBrHq3qjmjWSRIZ1jhj6HdinTGN7tBjUo8IOSTKu:TWk5i |
MALICIOUS
LUMMA has been detected (SURICATA)
- BitLockerToGo.exe (PID: 6488)
Stealers network behavior
- BitLockerToGo.exe (PID: 6488)
Actions looks like stealing of personal data
- BitLockerToGo.exe (PID: 6488)
StealC has been detected
- RegAsm.exe (PID: 5220)
SUSPICIOUS
Windows Defender mutex has been found
- RegAsm.exe (PID: 5220)
Executes application which crashes
- c5d5a4fd2200126f32170a7fd214850c244eed7c7279c5773e41c45049202526.exe (PID: 5760)
INFO
Manual execution by a user
- 65378cb0204ccc4a83aec34ec0bbbbbd9c100376ca869dd211daaddef4e68bf4.exe (PID: 3032)
- WinRAR.exe (PID: 6740)
- c5d5a4fd2200126f32170a7fd214850c244eed7c7279c5773e41c45049202526.exe (PID: 5760)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 2180)
- WinRAR.exe (PID: 6740)
The process uses the downloaded file
- WinRAR.exe (PID: 2180)
- WinRAR.exe (PID: 6740)
Checks supported languages
- BitLockerToGo.exe (PID: 6488)
- 65378cb0204ccc4a83aec34ec0bbbbbd9c100376ca869dd211daaddef4e68bf4.exe (PID: 3032)
- RegAsm.exe (PID: 5220)
- c5d5a4fd2200126f32170a7fd214850c244eed7c7279c5773e41c45049202526.exe (PID: 5760)
Reads the computer name
- BitLockerToGo.exe (PID: 6488)
- c5d5a4fd2200126f32170a7fd214850c244eed7c7279c5773e41c45049202526.exe (PID: 5760)
- RegAsm.exe (PID: 5220)
Reads the software policy settings
- BitLockerToGo.exe (PID: 6488)
- slui.exe (PID: 4060)
- slui.exe (PID: 3716)
- WerFault.exe (PID: 6304)
Checks proxy server information
- slui.exe (PID: 3716)
- WerFault.exe (PID: 6304)
Reads the machine GUID from the registry
- c5d5a4fd2200126f32170a7fd214850c244eed7c7279c5773e41c45049202526.exe (PID: 5760)
Creates files or folders in the user directory
- WerFault.exe (PID: 6304)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 51 |
|---|---|
| ZipBitFlag: | 0x0003 |
| ZipCompression: | Unknown (99) |
| ZipModifyDate: | 2024:09:15 15:51:24 |
| ZipCRC: | 0x0c7ee6df |
| ZipCompressedSize: | 2856617 |
| ZipUncompressedSize: | 7206400 |
| ZipFileName: | 65378cb0204ccc4a83aec34ec0bbbbbd9c100376ca869dd211daaddef4e68bf4.exe |
Total processes
149
Monitored processes
13
Malicious processes
3
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2112 | "C:\Windows\Microsoft.NET\Framework\v4.0.30319\RegAsm.exe" | C:\Windows\Microsoft.NET\Framework\v4.0.30319\RegAsm.exe | — | c5d5a4fd2200126f32170a7fd214850c244eed7c7279c5773e41c45049202526.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft .NET Assembly Registration Utility Exit code: 0 Version: 4.8.9037.0 built by: NET481REL1 Modules
| |||||||||||||||
| 2180 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\Desktop\2.zip | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
| 2588 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | c5d5a4fd2200126f32170a7fd214850c244eed7c7279c5773e41c45049202526.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
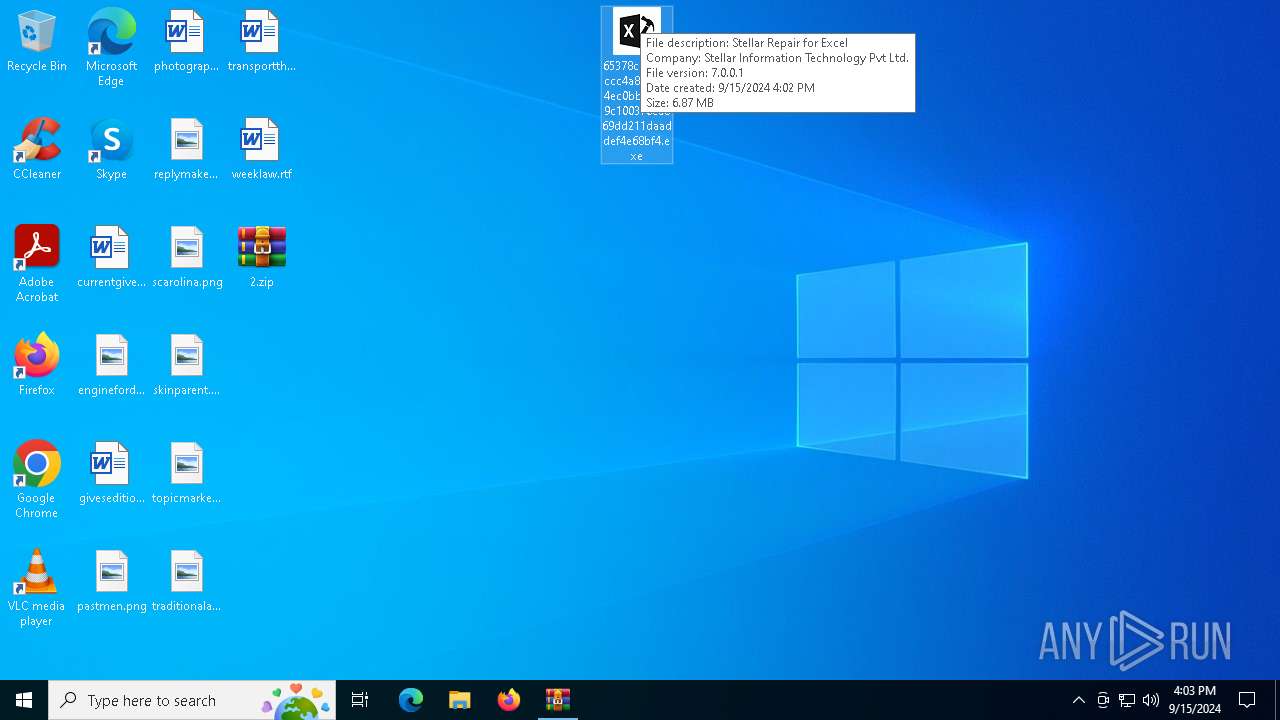
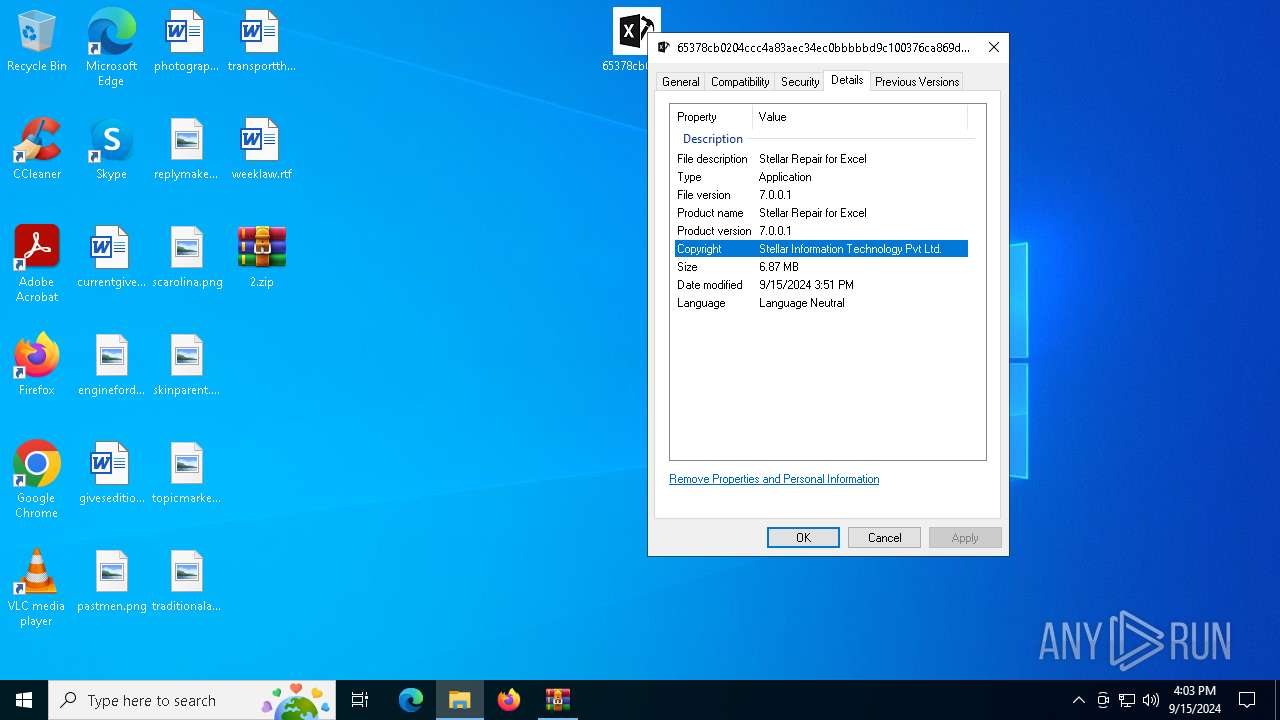
| 3032 | "C:\Users\admin\Desktop\65378cb0204ccc4a83aec34ec0bbbbbd9c100376ca869dd211daaddef4e68bf4.exe" | C:\Users\admin\Desktop\65378cb0204ccc4a83aec34ec0bbbbbd9c100376ca869dd211daaddef4e68bf4.exe | — | explorer.exe | |||||||||||
User: admin Company: Stellar Information Technology Pvt Ltd. Integrity Level: MEDIUM Description: Stellar Repair for Excel Exit code: 666 Version: 7.0.0.1 Modules
| |||||||||||||||
| 3716 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4060 | "C:\WINDOWS\System32\SLUI.exe" RuleId=3482d82e-ca2c-4e1f-8864-da0267b484b2;Action=AutoActivate;AppId=55c92734-d682-4d71-983e-d6ec3f16059f;SkuId=4de7cb65-cdf1-4de9-8ae8-e3cce27b9f2c;NotificationInterval=1440;Trigger=TimerEvent | C:\Windows\System32\slui.exe | SppExtComObj.Exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Activation Client Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4772 | C:\WINDOWS\system32\SppExtComObj.exe -Embedding | C:\Windows\System32\SppExtComObj.Exe | — | svchost.exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: KMS Connection Broker Exit code: 0 Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5220 | "C:\Windows\Microsoft.NET\Framework\v4.0.30319\RegAsm.exe" | C:\Windows\Microsoft.NET\Framework\v4.0.30319\RegAsm.exe | c5d5a4fd2200126f32170a7fd214850c244eed7c7279c5773e41c45049202526.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft .NET Assembly Registration Utility Exit code: 0 Version: 4.8.9037.0 built by: NET481REL1 Modules
| |||||||||||||||
| 5760 | "C:\Users\admin\Desktop\c5d5a4fd2200126f32170a7fd214850c244eed7c7279c5773e41c45049202526.exe" | C:\Users\admin\Desktop\c5d5a4fd2200126f32170a7fd214850c244eed7c7279c5773e41c45049202526.exe | explorer.exe | ||||||||||||
User: admin Company: deacidifies infinitively succeeded Integrity Level: MEDIUM Description: soundlessly inhalant encase Exit code: 3762504530 Version: 1.0.0.0 Modules
| |||||||||||||||
| 6304 | C:\WINDOWS\SysWOW64\WerFault.exe -u -p 5760 -s 904 | C:\Windows\SysWOW64\WerFault.exe | c5d5a4fd2200126f32170a7fd214850c244eed7c7279c5773e41c45049202526.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Problem Reporting Exit code: 0 Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
8 235
Read events
8 210
Write events
25
Delete events
0
Modification events
| (PID) Process: | (2180) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\GoogleChromeEnterpriseBundle64.zip | |||
| (PID) Process: | (2180) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\2.zip | |||
| (PID) Process: | (2180) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (2180) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (2180) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (2180) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (2180) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface |
| Operation: | write | Name: | ShowPassword |
Value: 0 | |||
| (PID) Process: | (6740) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\GoogleChromeEnterpriseBundle64.zip | |||
| (PID) Process: | (6740) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\2.zip | |||
| (PID) Process: | (6740) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\1.zip | |||
Executable files
2
Suspicious files
4
Text files
2
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6304 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\ReportArchive\AppCrash_UV4U1SWGRXHHBAB0_7c5342bf4d1b246c536ed278c53f3d22e8c041d6_8f90f906_e0cf3bc8-6da0-41f8-84c6-f92e7b0993ca\Report.wer | — | |
MD5:— | SHA256:— | |||
| 6304 | WerFault.exe | C:\Users\admin\AppData\Local\CrashDumps\c5d5a4fd2200126f32170a7fd214850c244eed7c7279c5773e41c45049202526.exe.5760.dmp | — | |
MD5:— | SHA256:— | |||
| 2180 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb2180.45962\65378cb0204ccc4a83aec34ec0bbbbbd9c100376ca869dd211daaddef4e68bf4.exe | executable | |
MD5:D5B15F04C8781F14220D88DB6AFF30C7 | SHA256:65378CB0204CCC4A83AEC34EC0BBBBBD9C100376CA869DD211DAADDEF4E68BF4 | |||
| 6304 | WerFault.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\37C951188967C8EB88D99893D9D191FE | binary | |
MD5:FB64A9EBEDF48D3895381D5B7D80743D | SHA256:EA21D495930AD76F267A33A0F593DBF0C7EA75E457FCAE49A29DAAD8BD920F42 | |||
| 6304 | WerFault.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\21253908F3CB05D51B1C2DA8B681A785 | binary | |
MD5:1982881E8A34A875CFD94C5EC39DFD35 | SHA256:EE4A8F019C842B142BBF116F6BC417D9EEABE645904736AA60D391B80FD7428E | |||
| 6304 | WerFault.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\21253908F3CB05D51B1C2DA8B681A785 | der | |
MD5:1B7FD5177461034E4086724C5845E927 | SHA256:065AF18C229898A1C2A8D989911ADCD9B1E2AB14B1953EBF8EAF34AE37EA1627 | |||
| 6304 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\Temp\WER327E.tmp.dmp | dmp | |
MD5:8D5ECAC4ED61DAE397F11186CDC85AD5 | SHA256:6E9628E8F1F5ED0DA7650ACC1FEEA9C9B978B9C4C77E35618392A1469BC7DD13 | |||
| 6304 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\Temp\WER334A.tmp.WERInternalMetadata.xml | xml | |
MD5:8CEFCA6464B929CD2E112D5727A9188C | SHA256:F7631363898B0A1C0D9E7F7C979219567B2A44A8576219AEEB2CBE17B842F005 | |||
| 6304 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\Temp\WER338A.tmp.xml | xml | |
MD5:204FE0B31B40F81EB647B7747D6839B5 | SHA256:1D11E679194B4BEB0FAB140F5DACCFBD5675043601438BCC2A18864454937F1E | |||
| 6740 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb6740.14162\c5d5a4fd2200126f32170a7fd214850c244eed7c7279c5773e41c45049202526.exe | executable | |
MD5:D0388E4EFE1978E6485FC5292F84CA81 | SHA256:C5D5A4FD2200126F32170A7FD214850C244EED7C7279C5773E41C45049202526 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
6
TCP/UDP connections
50
DNS requests
24
Threats
1
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1356 | svchost.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
2108 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
1064 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
1064 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
6304 | WerFault.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
2768 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1356 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6020 | RUXIMICS.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
2120 | MoUsoCoreWorker.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1356 | svchost.exe | 23.35.229.160:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
3260 | svchost.exe | 40.113.110.67:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
2108 | svchost.exe | 40.126.32.140:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
2108 | svchost.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
1064 | SIHClient.exe | 52.165.165.26:443 | slscr.update.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
planntyitemiw.shop |
| malicious |
activation-v2.sls.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
6488 | BitLockerToGo.exe | A Network Trojan was detected | STEALER [ANY.RUN] Lumma Stealer TLS Connection |