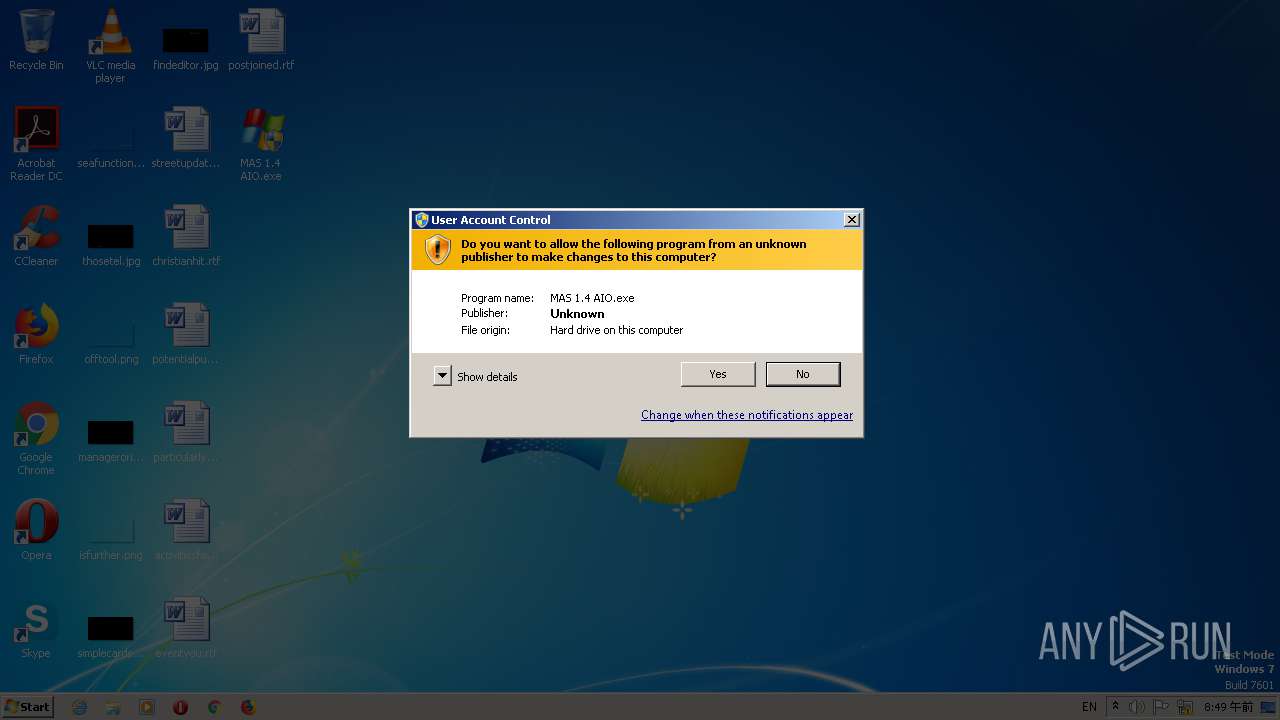
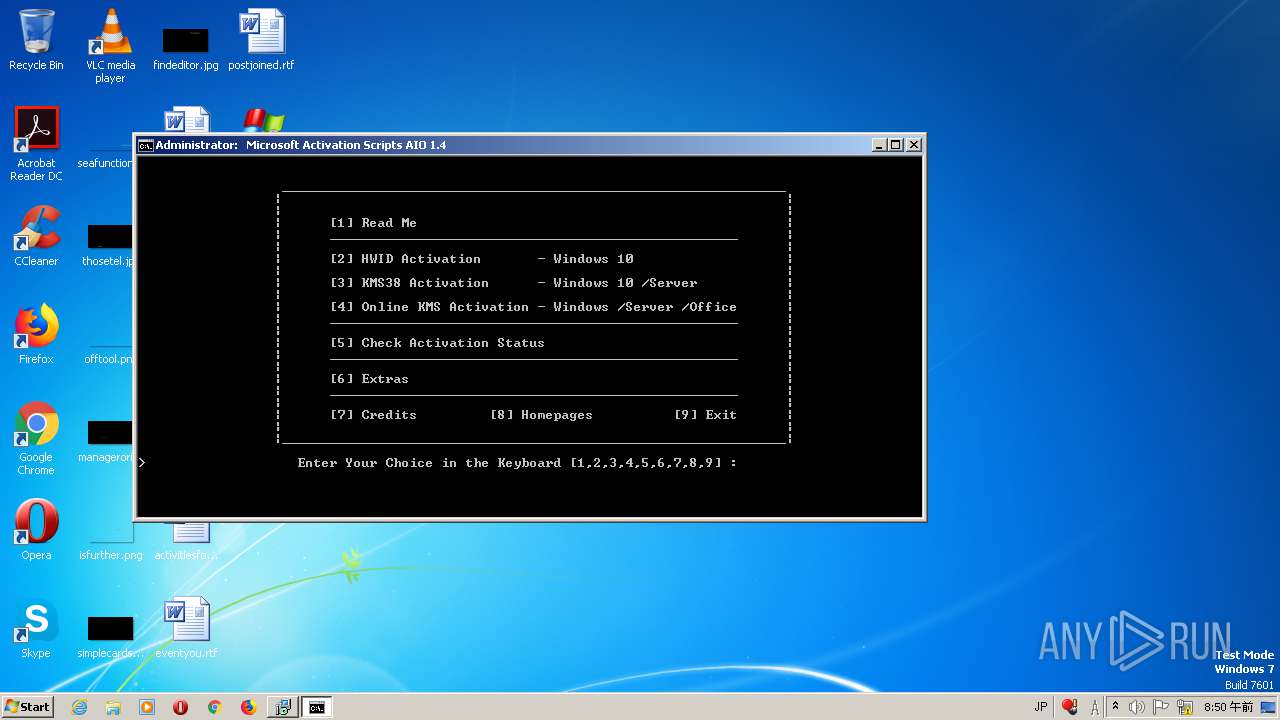
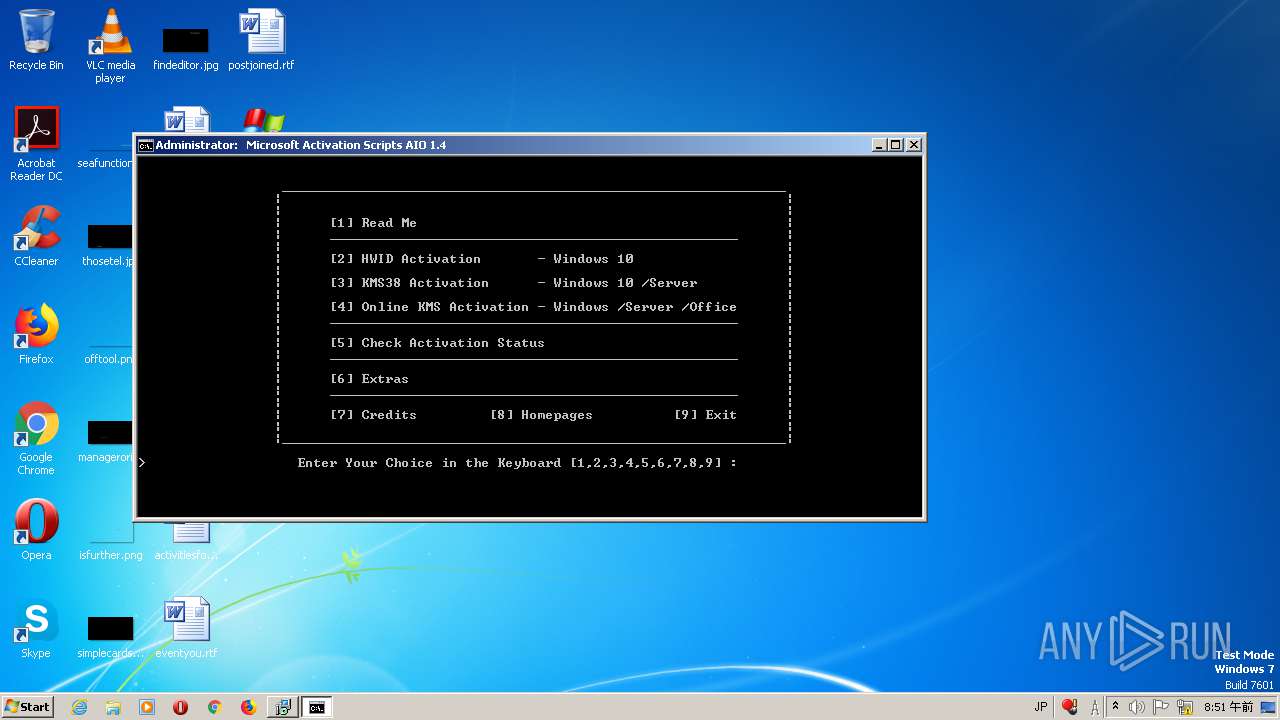
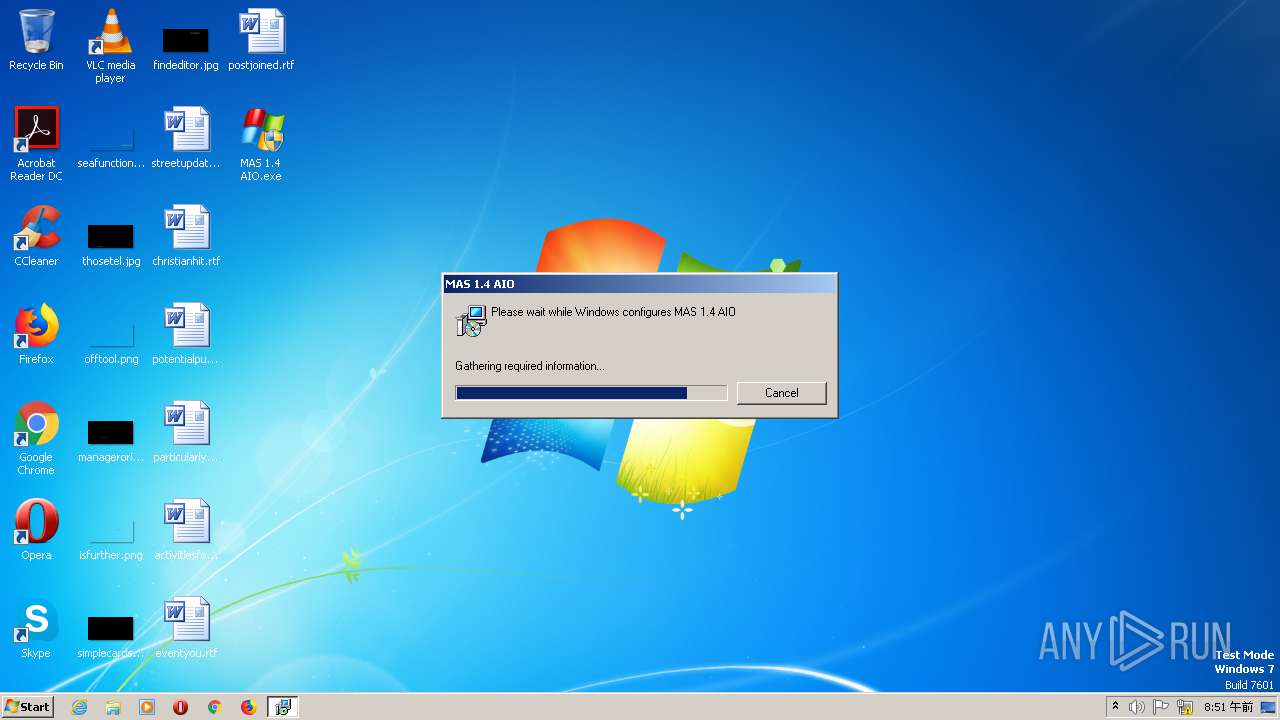
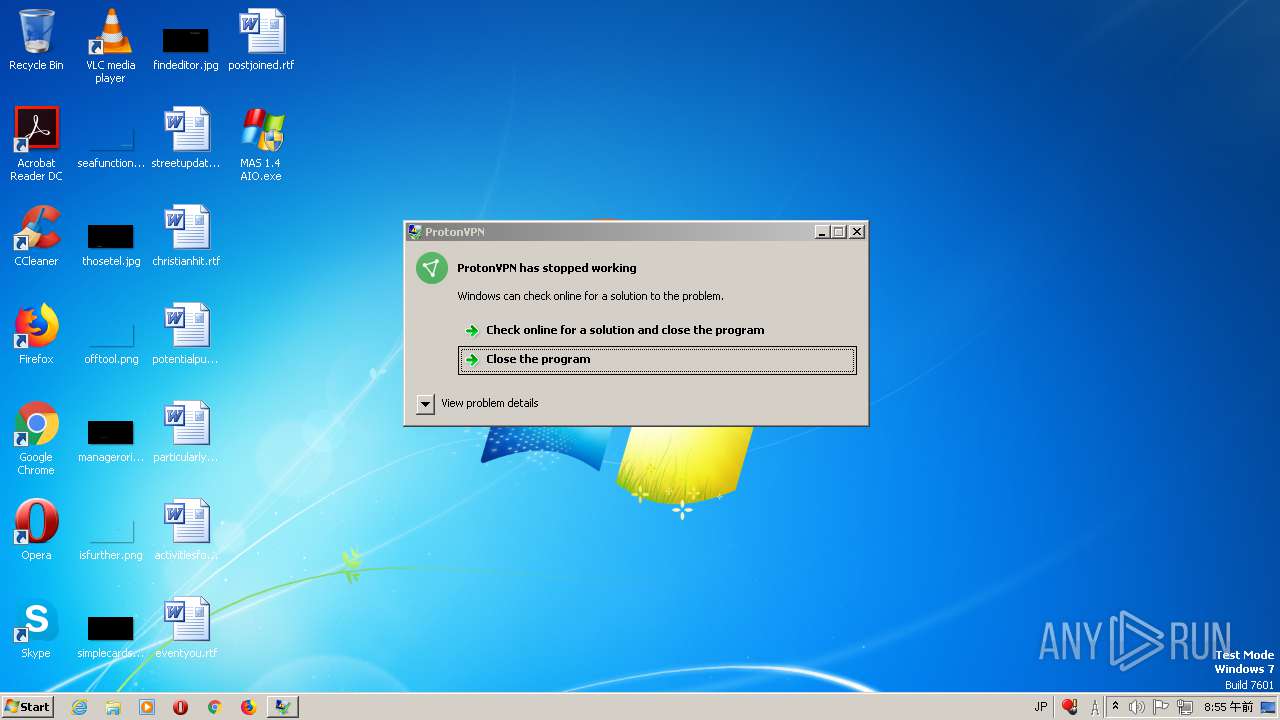
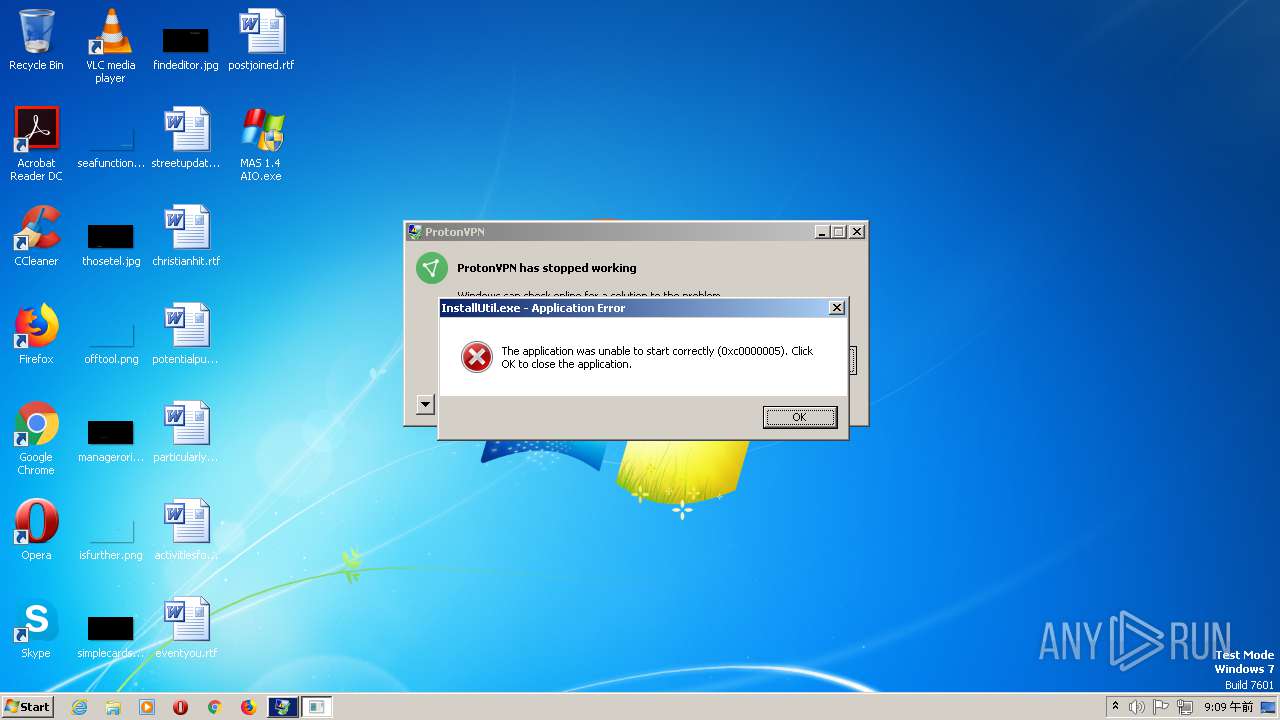
| File name: | MAS 1.4 AIO.exe |
| Full analysis: | https://app.any.run/tasks/bd99a366-2abb-4cc7-8f94-30e5f41d29a8 |
| Verdict: | Malicious activity |
| Threats: | AsyncRAT is a RAT that can monitor and remotely control infected systems. This malware was introduced on Github as a legitimate open-source remote administration software, but hackers use it for its many powerful malicious functions. |
| Analysis date: | May 16, 2021, 23:49:14 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | 36E498231CAB6BC349EDE50715E69072 |
| SHA1: | D30F62BB81130C68F6F679191E23E361C32E128A |
| SHA256: | A7AA1265A8549AC7EF9A5A62AB22874B5288A2A75A068344AE16F7FF2E2D0C80 |
| SSDEEP: | 196608:hDjxHkKaiXGxfTCv0ddbazw0ZEegjzyRP7yvNuanigdz2:hl8cGMv4dbow0CeiyZYNuGiA2 |
MALICIOUS
Application was dropped or rewritten from another process
- RegAsm.exe (PID: 848)
SUSPICIOUS
Executable content was dropped or overwritten
- MAS 1.4 AIO.exe (PID: 1508)
- MSI16AE.tmp (PID: 2300)
Drops a file that was compiled in debug mode
- MAS 1.4 AIO.exe (PID: 1508)
- MSI16AE.tmp (PID: 2300)
Starts Microsoft Installer
- MAS 1.4 AIO.exe (PID: 1508)
Starts CMD.EXE for commands execution
- MSI5F51.tmp (PID: 2908)
INFO
Loads dropped or rewritten executable
- MsiExec.exe (PID: 2864)
- MsiExec.exe (PID: 1368)
Application was dropped or rewritten from another process
- MSI16AE.tmp (PID: 2300)
- MSI5F51.tmp (PID: 2908)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 EXE PECompact compressed (generic) (20.7) |
|---|---|---|
| .exe | | | Win64 Executable (generic) (13.7) |
| .dll | | | Win32 Dynamic Link Library (generic) (3.2) |
| .exe | | | Win32 Executable (generic) (2.2) |
EXIF
EXE
| ProductVersion: | 1.0.0 |
|---|---|
| ProductName: | MAS 1.4 AIO |
| OriginalFileName: | MAS 1.4 AIO.exe |
| LegalCopyright: | Copyright (C) 2021 IGI |
| InternalName: | MAS 1.4 AIO |
| FileVersion: | 1.0.0 |
| FileDescription: | MAS 1.4 AIO Installer |
| CompanyName: | IGI |
| CharacterSet: | Unicode |
| LanguageCode: | English (U.S.) |
| FileSubtype: | - |
| ObjectFileType: | Dynamic link library |
| FileOS: | Win32 |
| FileFlags: | Debug |
| FileFlagsMask: | 0x003f |
| ProductVersionNumber: | 1.0.0.0 |
| FileVersionNumber: | 1.0.0.0 |
| Subsystem: | Windows GUI |
| SubsystemVersion: | 6 |
| ImageVersion: | - |
| OSVersion: | 6 |
| EntryPoint: | 0x122d48 |
| UninitializedDataSize: | - |
| InitializedDataSize: | 770560 |
| CodeSize: | 1534976 |
| LinkerVersion: | 14.28 |
| PEType: | PE32 |
| TimeStamp: | 2021:03:23 09:59:59+01:00 |
| MachineType: | Intel 386 or later, and compatibles |
Summary
| Architecture: | IMAGE_FILE_MACHINE_I386 |
|---|---|
| Subsystem: | IMAGE_SUBSYSTEM_WINDOWS_GUI |
| Compilation Date: | 23-Mar-2021 08:59:59 |
| Detected languages: |
|
| Debug artifacts: |
|
| CompanyName: | IGI |
| FileDescription: | MAS 1.4 AIO Installer |
| FileVersion: | 1.0.0 |
| InternalName: | MAS 1.4 AIO |
| LegalCopyright: | Copyright (C) 2021 IGI |
| OriginalFileName: | MAS 1.4 AIO.exe |
| ProductName: | MAS 1.4 AIO |
| ProductVersion: | 1.0.0 |
DOS Header
| Magic number: | MZ |
|---|---|
| Bytes on last page of file: | 0x0090 |
| Pages in file: | 0x0003 |
| Relocations: | 0x0000 |
| Size of header: | 0x0004 |
| Min extra paragraphs: | 0x0000 |
| Max extra paragraphs: | 0xFFFF |
| Initial SS value: | 0x0000 |
| Initial SP value: | 0x00B8 |
| Checksum: | 0x0000 |
| Initial IP value: | 0x0000 |
| Initial CS value: | 0x0000 |
| Overlay number: | 0x0000 |
| OEM identifier: | 0x0000 |
| OEM information: | 0x0000 |
| Address of NE header: | 0x00000110 |
PE Headers
| Signature: | PE |
|---|---|
| Machine: | IMAGE_FILE_MACHINE_I386 |
| Number of sections: | 5 |
| Time date stamp: | 23-Mar-2021 08:59:59 |
| Pointer to Symbol Table: | 0x00000000 |
| Number of symbols: | 0 |
| Size of Optional Header: | 0x00E0 |
| Characteristics: |
|
Sections
Name | Virtual Address | Virtual Size | Raw Size | Charateristics | Entropy |
|---|---|---|---|---|---|
.text | 0x00001000 | 0x00176A3F | 0x00176C00 | IMAGE_SCN_CNT_CODE, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ | 6.44959 |
.rdata | 0x00178000 | 0x0005DC38 | 0x0005DE00 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 4.58321 |
.data | 0x001D6000 | 0x00006E40 | 0x00005400 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 2.06148 |
.rsrc | 0x001DD000 | 0x0003FAA6 | 0x0003FC00 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 5.35523 |
.reloc | 0x0021D000 | 0x00019318 | 0x00019400 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_DISCARDABLE, IMAGE_SCN_MEM_READ | 6.56754 |
Resources
Title | Entropy | Size | Codepage | Language | Type |
|---|---|---|---|---|---|
1 | 5.21546 | 1898 | Latin 1 / Western European | English - United States | RT_MANIFEST |
2 | 4.16964 | 67624 | UNKNOWN | English - United States | RT_ICON |
3 | 4.52869 | 38056 | UNKNOWN | English - United States | RT_ICON |
4 | 4.5751 | 21640 | UNKNOWN | English - United States | RT_ICON |
5 | 4.53043 | 16936 | UNKNOWN | English - United States | RT_ICON |
6 | 4.84234 | 9640 | UNKNOWN | English - United States | RT_ICON |
7 | 4.96796 | 4264 | UNKNOWN | English - United States | RT_ICON |
8 | 5.26658 | 2440 | UNKNOWN | English - United States | RT_ICON |
9 | 3.37783 | 1116 | Latin 1 / Western European | English - United States | RT_STRING |
10 | 3.34881 | 836 | Latin 1 / Western European | English - United States | RT_STRING |
Imports
KERNEL32.dll |
msi.dll (delay-loaded) |
Total processes
75
Monitored processes
8
Malicious processes
0
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 848 | C:\Users\admin\AppData\Local\Temp\RegAsm.exe | C:\Users\admin\AppData\Local\Temp\RegAsm.exe | — | MSI16AE.tmp | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft .NET Assembly Registration Utility Exit code: 0 Version: 4.7.3062.0 built by: NET472REL1 Modules
| |||||||||||||||
| 1368 | C:\Windows\syswow64\MsiExec.exe -Embedding CFDDC031E95F529F2E2949E15327DB85 | C:\Windows\syswow64\MsiExec.exe | — | msiexec.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows® installer Exit code: 0 Version: 5.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1508 | "C:\Users\admin\Desktop\MAS 1.4 AIO.exe" | C:\Users\admin\Desktop\MAS 1.4 AIO.exe | explorer.exe | ||||||||||||
User: admin Company: IGI Integrity Level: HIGH Description: MAS 1.4 AIO Installer Exit code: 0 Version: 1.0.0 Modules
| |||||||||||||||
| 2144 | "C:\Users\admin\Desktop\MAS 1.4 AIO.exe" | C:\Users\admin\Desktop\MAS 1.4 AIO.exe | — | explorer.exe | |||||||||||
User: admin Company: IGI Integrity Level: MEDIUM Description: MAS 1.4 AIO Installer Exit code: 3221226540 Version: 1.0.0 Modules
| |||||||||||||||
| 2252 | "C:\Windows\system32\msiexec.exe" /i "C:\Users\admin\AppData\Local\Temp\MAS 1.4 AIO.msi" AI_SETUPEXEPATH="C:\Users\admin\Desktop\MAS 1.4 AIO.exe" SETUPEXEDIR=C:\Users\admin\Desktop\ EXE_CMD_LINE="/exenoupdates /forcecleanup /wintime 1621208747 " | C:\Windows\SysWOW64\msiexec.exe | — | MAS 1.4 AIO.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows® installer Exit code: 0 Version: 5.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2300 | "C:\Windows\Installer\MSI16AE.tmp" | C:\Windows\Installer\MSI16AE.tmp | msiexec.exe | ||||||||||||
User: admin Company: VOICEMOD Integrity Level: HIGH Description: Voicemod Activator Exit code: 0 Version: 9.43.3.9 Modules
| |||||||||||||||
| 2864 | C:\Windows\syswow64\MsiExec.exe -Embedding A7D0B7DF24A4C72E71C41576ADAB5720 C | C:\Windows\syswow64\MsiExec.exe | — | msiexec.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows® installer Exit code: 0 Version: 5.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2908 | "C:\Windows\Installer\MSI5F51.tmp" | C:\Windows\Installer\MSI5F51.tmp | — | msiexec.exe | |||||||||||
User: admin Company: Islam Adel Integrity Level: HIGH Description: Created by BAT2EXE.net Exit code: 0 Version: 2.0 Modules
| |||||||||||||||
Total events
725
Read events
715
Write events
10
Delete events
0
Modification events
| (PID) Process: | (1508) MAS 1.4 AIO.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\IMEJP\10.0\MSIME\AutoCharWidth |
| Operation: | write | Name: | LearnData |
Value: A2,040,050,060,070,080,090,160,170, | |||
| (PID) Process: | (2908) MSI5F51.tmp | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (2908) MSI5F51.tmp | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (2908) MSI5F51.tmp | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (2908) MSI5F51.tmp | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
Executable files
4
Suspicious files
1
Text files
13
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1508 | MAS 1.4 AIO.exe | C:\Users\admin\AppData\Local\Temp\MAS 1.4 AIO.msi | — | |
MD5:— | SHA256:— | |||
| 1508 | MAS 1.4 AIO.exe | C:\Users\admin\AppData\Local\Temp\MSIBA68.tmp | — | |
MD5:— | SHA256:— | |||
| 1508 | MAS 1.4 AIO.exe | C:\Users\admin\AppData\Local\Temp\MSIBBE1.tmp | — | |
MD5:— | SHA256:— | |||
| 1508 | MAS 1.4 AIO.exe | C:\Users\admin\AppData\Local\Temp\holder0.aiph | gmc | |
MD5:2E492A798E23AE8D91FE7A93E4405D3A | SHA256:EC776CDABEAA5E510DC5FC16CEC0147B48F0ADBF69A88BB89EFED8D926BD2423 | |||
| 1508 | MAS 1.4 AIO.exe | C:\Users\admin\AppData\Local\Temp\AI_EXTUI_BIN_1508\completi | image | |
MD5:45B0E074F96A859ADAE198187AB9FA11 | SHA256:050282E679AC80F6A357FFF92F1E7A95D30A06B35247E25CBFD2DD8CEEE1A412 | |||
| 1508 | MAS 1.4 AIO.exe | C:\Users\admin\AppData\Local\Temp\AI_EXTUI_BIN_1508\repairic | image | |
MD5:D234CA0358B21BDCFC5E3F9B2E7C7A22 | SHA256:99D490C2BDEF5115F306A595964663540370141F65A25C5052352155F2603F68 | |||
| 1508 | MAS 1.4 AIO.exe | C:\Users\admin\AppData\Local\Temp\AI_EXTUI_BIN_1508\insticon | image | |
MD5:66C842AF0B4FC1C918F531D2E1087B82 | SHA256:48278165490487EE414BE65E20501B19A65EDAF1B6F473EB7D8C55023175EC88 | |||
| 1508 | MAS 1.4 AIO.exe | C:\Users\admin\AppData\Local\Temp\AI_EXTUI_BIN_1508\info | image | |
MD5:554FF4C199562515D758C9ABFF5C2943 | SHA256:9AE4A96BF2A349667E844ACC1E2AC4F89361A6182268438F4D063DF3A6FC47BC | |||
| 1508 | MAS 1.4 AIO.exe | C:\Users\admin\AppData\Local\Temp\MSIBB82.tmp | executable | |
MD5:71B541254864BD52F85E932E2040CBE8 | SHA256:B29AB4744FF6C8C9C440E878ABF6F76255C538E71564E6A6279513B543BE0538 | |||
| 1508 | MAS 1.4 AIO.exe | C:\Users\admin\AppData\Local\Temp\AI_EXTUI_BIN_1508\dialog | image | |
MD5:553DF955CB4B2E7BE5CEF99CB8EC9254 | SHA256:F1FCB09DF932AEF09B24EEA796286CEAEDCBCECCD4D8F4536345163C4D3D9FF7 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
9
TCP/UDP connections
19
DNS requests
8
Threats
15
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 172.67.167.212:80 | http://utorrent-servers.xyz/1337/A.txt | US | text | 83 b | suspicious |
— | — | GET | 200 | 172.67.167.212:80 | http://utorrent-servers.xyz/1337/B.txt | US | text | 83 b | suspicious |
— | — | GET | 200 | 172.67.167.212:80 | http://utorrent-servers.xyz/1337/C.txt | US | text | 83 b | suspicious |
— | — | GET | 200 | 172.67.167.212:80 | http://utorrent-servers.xyz/1337/E.txt | US | text | 83 b | suspicious |
— | — | GET | 200 | 172.67.167.212:80 | http://utorrent-servers.xyz/1337/D.txt | US | text | 83 b | suspicious |
— | — | POST | 200 | 193.142.146.202:47945 | http://193.142.146.202:47945// | unknown | text | 150 b | malicious |
— | — | POST | 200 | 193.142.146.202:47945 | http://193.142.146.202:47945// | unknown | text | 4.59 Kb | malicious |
— | — | POST | 200 | 193.142.146.202:47945 | http://193.142.146.202:47945// | unknown | text | 261 b | malicious |
— | — | GET | 200 | 2.17.120.90:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab?0018b79e43bc2ea0 | unknown | compressed | 58.4 Kb | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 172.67.167.212:80 | utorrent-servers.xyz | — | US | suspicious |
— | — | 162.159.133.233:443 | cdn.discordapp.com | Cloudflare Inc | — | shared |
— | — | 104.23.99.190:443 | pastebin.com | Cloudflare Inc | US | malicious |
— | — | 193.142.146.202:8808 | — | — | — | malicious |
— | — | 193.142.146.202:47945 | — | — | — | malicious |
— | — | 104.26.12.31:443 | api.ip.sb | Cloudflare Inc | US | suspicious |
— | — | 2.17.120.90:80 | ctldl.windowsupdate.com | Akamai International B.V. | — | suspicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
utorrent-servers.xyz |
| suspicious |
cdn.discordapp.com |
| shared |
pastebin.com |
| malicious |
ctldl.windowsupdate.com |
| whitelisted |
api.ip.sb |
| whitelisted |
teredo.ipv6.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
— | — | Potentially Bad Traffic | ET INFO Request to .XYZ Domain with Minimal Headers |
— | — | Potentially Bad Traffic | AV INFO HTTP Request to a *.xyz domain |
— | — | Potentially Bad Traffic | AV INFO HTTP Request to a *.xyz domain |
— | — | Potentially Bad Traffic | AV INFO HTTP Request to a *.xyz domain |
— | — | Potentially Bad Traffic | AV INFO HTTP Request to a *.xyz domain |
— | — | Potentially Bad Traffic | AV INFO HTTP Request to a *.xyz domain |
— | — | A Network Trojan was detected | ET TROJAN Observed Malicious SSL Cert (AsyncRAT Server) |
— | — | A Network Trojan was detected | AV TROJAN RedLine Stealer Config Download |
— | — | Generic Protocol Command Decode | SURICATA HTTP unable to match response to request |
6 ETPRO signatures available at the full report