| File name: | a7018ff4aaaaebda06615da54ab7d3dcfe06ffda501254eb9654aa27152629bb.exe |
| Full analysis: | https://app.any.run/tasks/0e0646d0-4fc4-4656-a751-3133d84e3faf |
| Verdict: | Malicious activity |
| Threats: | Ransomware is a type of malicious software that locks users out of their system or data using different methods to force them to pay a ransom. Most often, such programs encrypt files on an infected machine and demand a fee to be paid in exchange for the decryption key. Additionally, such programs can be used to steal sensitive information from the compromised computer and even conduct DDoS attacks against affected organizations to pressure them into paying. |
| Analysis date: | January 15, 2022, 01:41:52 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386 Mono/.Net assembly, for MS Windows |
| MD5: | 22367699E131A9D98F842A1003FD193A |
| SHA1: | C275084D65F845B4D957C05B874FADE071193468 |
| SHA256: | A7018FF4AAAAEBDA06615DA54AB7D3DCFE06FFDA501254EB9654AA27152629BB |
| SSDEEP: | 12288:aMA8K777777777777oPAIBeqRJ620hP9EWyuJsP9ZUNF:aEK777777777777o3BeqRJiUjuJF |
MALICIOUS
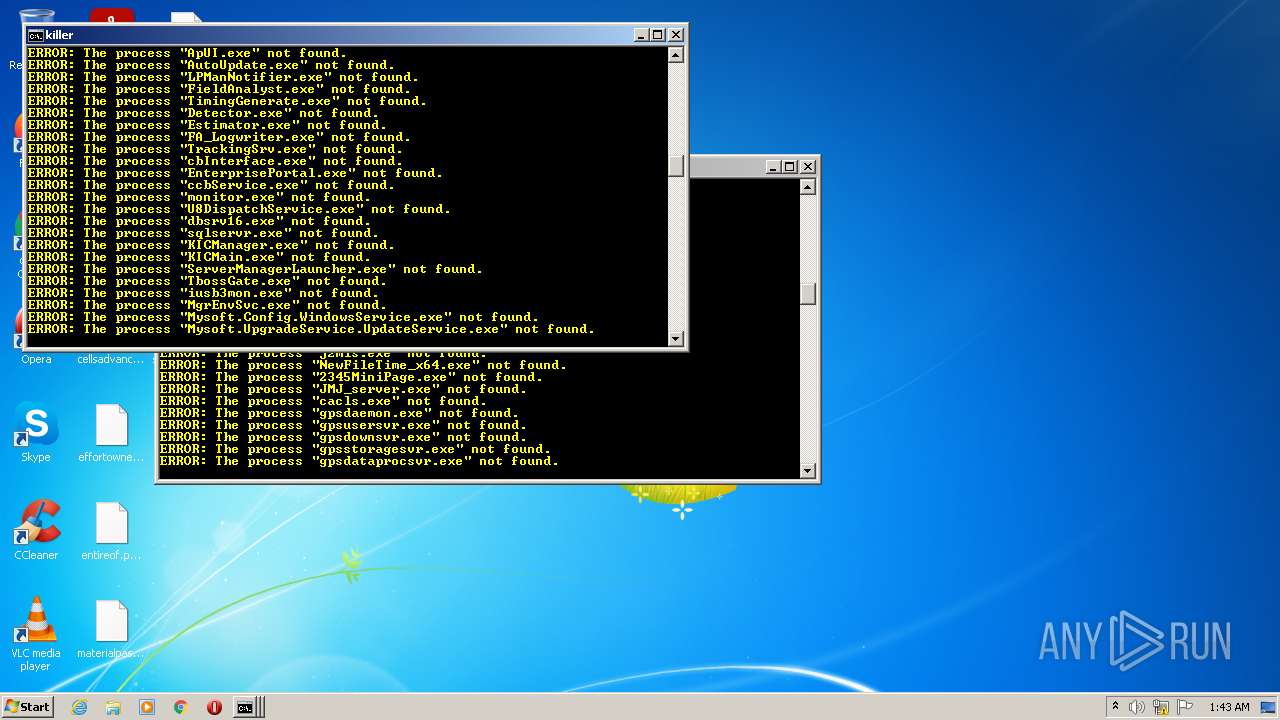
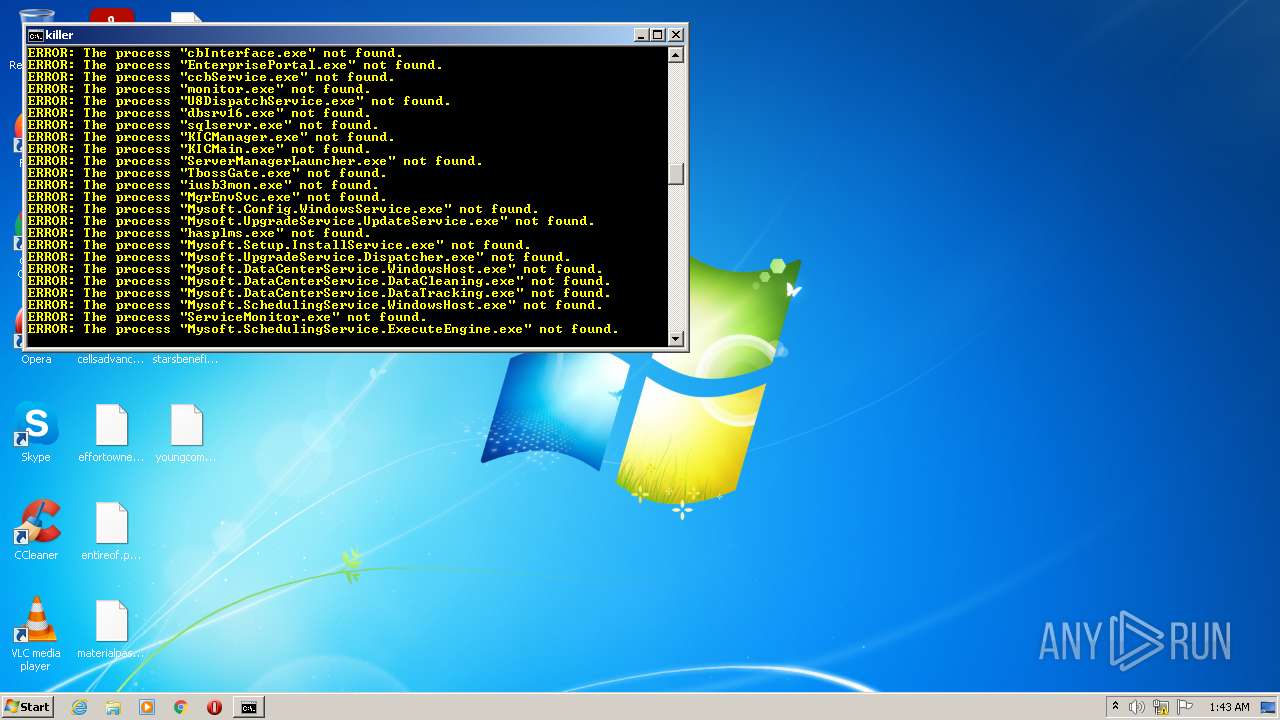
Starts NET.EXE for service management
- cmd.exe (PID: 2520)
- cmd.exe (PID: 3680)
- cmd.exe (PID: 2332)
- cmd.exe (PID: 3780)
- cmd.exe (PID: 1288)
- cmd.exe (PID: 392)
- cmd.exe (PID: 3008)
- cmd.exe (PID: 1256)
- cmd.exe (PID: 2392)
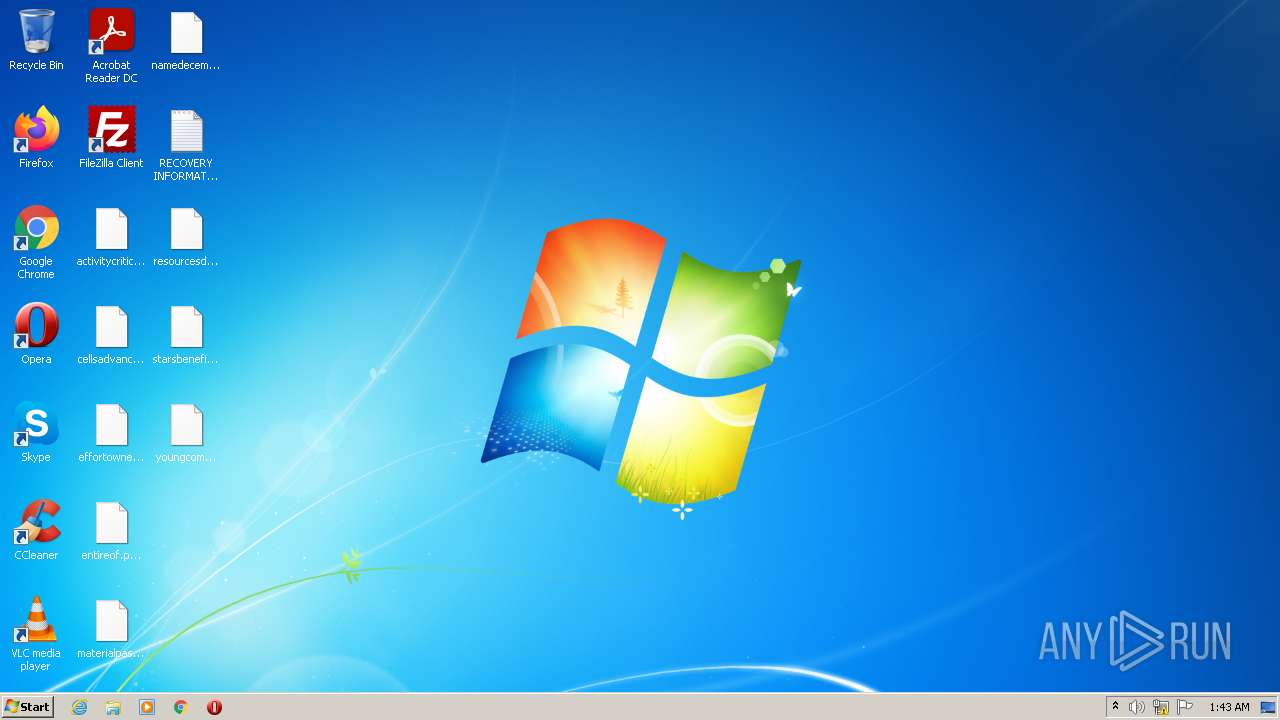
Renames files like Ransomware
- a7018ff4aaaaebda06615da54ab7d3dcfe06ffda501254eb9654aa27152629bb.exe (PID: 3928)
SUSPICIOUS
Reads the computer name
- a7018ff4aaaaebda06615da54ab7d3dcfe06ffda501254eb9654aa27152629bb.exe (PID: 3148)
- a7018ff4aaaaebda06615da54ab7d3dcfe06ffda501254eb9654aa27152629bb.exe (PID: 3928)
Checks supported languages
- a7018ff4aaaaebda06615da54ab7d3dcfe06ffda501254eb9654aa27152629bb.exe (PID: 3148)
- cmd.exe (PID: 3352)
- a7018ff4aaaaebda06615da54ab7d3dcfe06ffda501254eb9654aa27152629bb.exe (PID: 3928)
- cmd.exe (PID: 2520)
- cmd.exe (PID: 2340)
- cmd.exe (PID: 2332)
- cmd.exe (PID: 1068)
- cmd.exe (PID: 3680)
- cmd.exe (PID: 956)
- cmd.exe (PID: 2392)
- cmd.exe (PID: 1544)
- cmd.exe (PID: 3180)
- cmd.exe (PID: 2752)
- cmd.exe (PID: 3732)
- cmd.exe (PID: 3008)
- cmd.exe (PID: 1408)
- cmd.exe (PID: 1288)
- cmd.exe (PID: 1256)
- cmd.exe (PID: 3780)
- cmd.exe (PID: 2908)
- cmd.exe (PID: 1748)
- cmd.exe (PID: 1372)
- cmd.exe (PID: 392)
- cmd.exe (PID: 1636)
- cmd.exe (PID: 3464)
Changes tracing settings of the file or console
- a7018ff4aaaaebda06615da54ab7d3dcfe06ffda501254eb9654aa27152629bb.exe (PID: 3148)
Application launched itself
- a7018ff4aaaaebda06615da54ab7d3dcfe06ffda501254eb9654aa27152629bb.exe (PID: 3148)
- cmd.exe (PID: 3352)
Reads Environment values
- a7018ff4aaaaebda06615da54ab7d3dcfe06ffda501254eb9654aa27152629bb.exe (PID: 3148)
Starts CMD.EXE for commands execution
- a7018ff4aaaaebda06615da54ab7d3dcfe06ffda501254eb9654aa27152629bb.exe (PID: 3148)
- cmd.exe (PID: 3352)
Starts SC.EXE for service management
- cmd.exe (PID: 2340)
- cmd.exe (PID: 2332)
- cmd.exe (PID: 956)
- cmd.exe (PID: 3732)
- cmd.exe (PID: 3008)
- cmd.exe (PID: 1408)
- cmd.exe (PID: 2752)
- cmd.exe (PID: 1256)
- cmd.exe (PID: 2520)
- cmd.exe (PID: 2392)
- cmd.exe (PID: 1544)
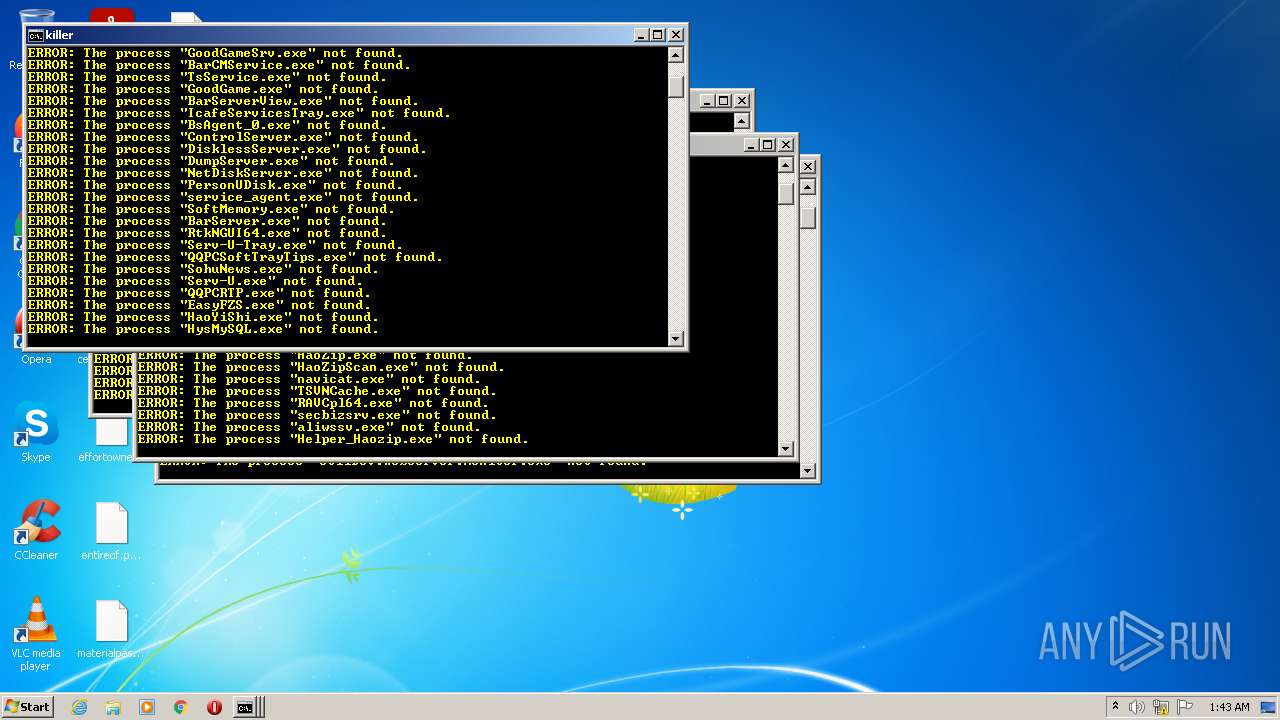
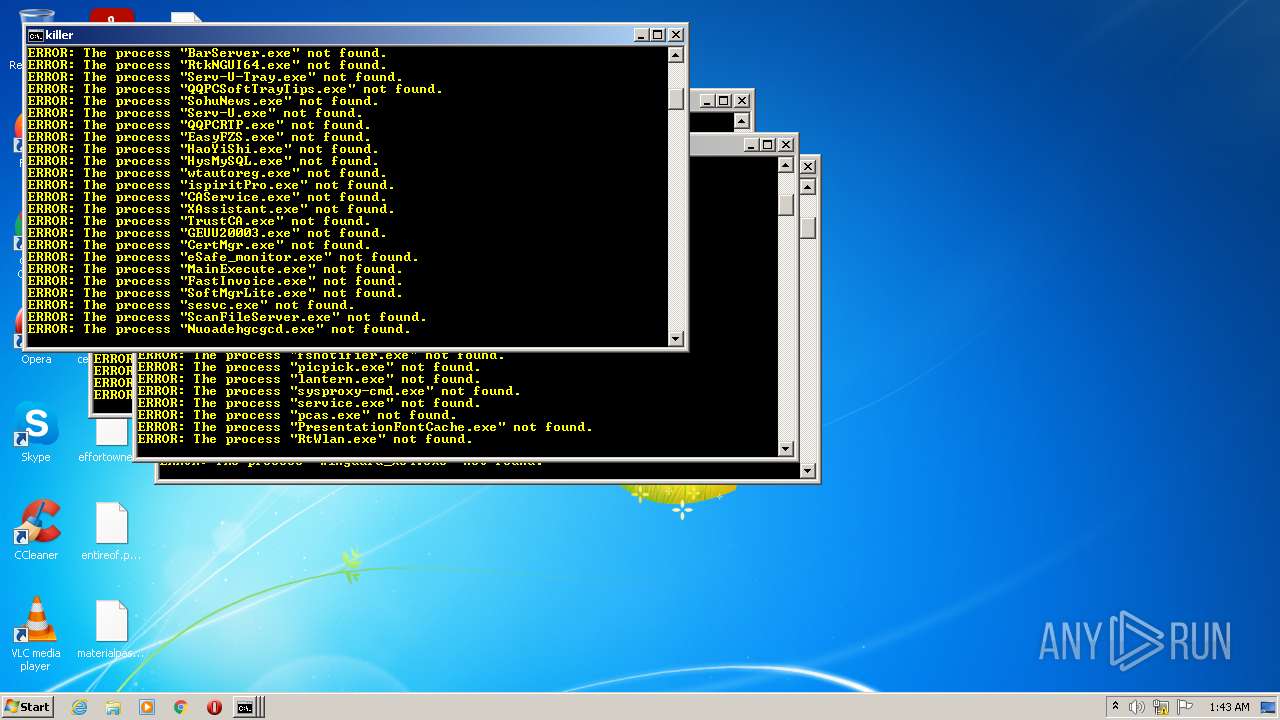
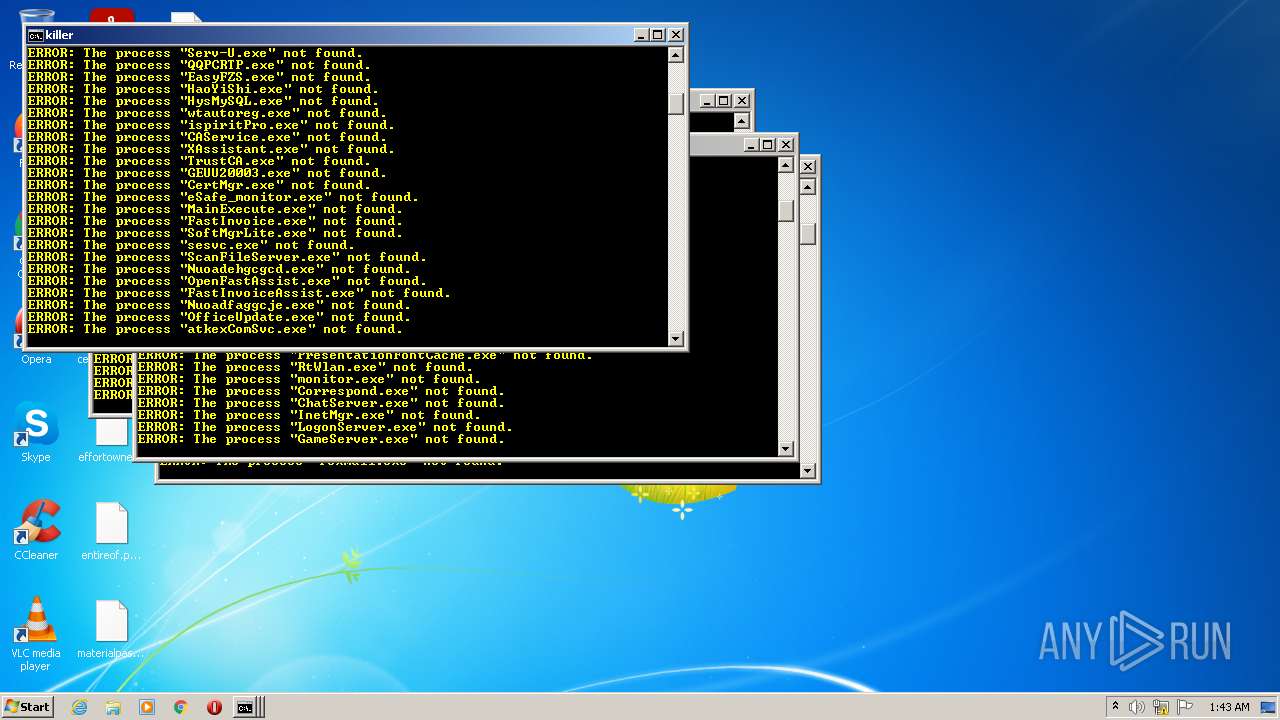
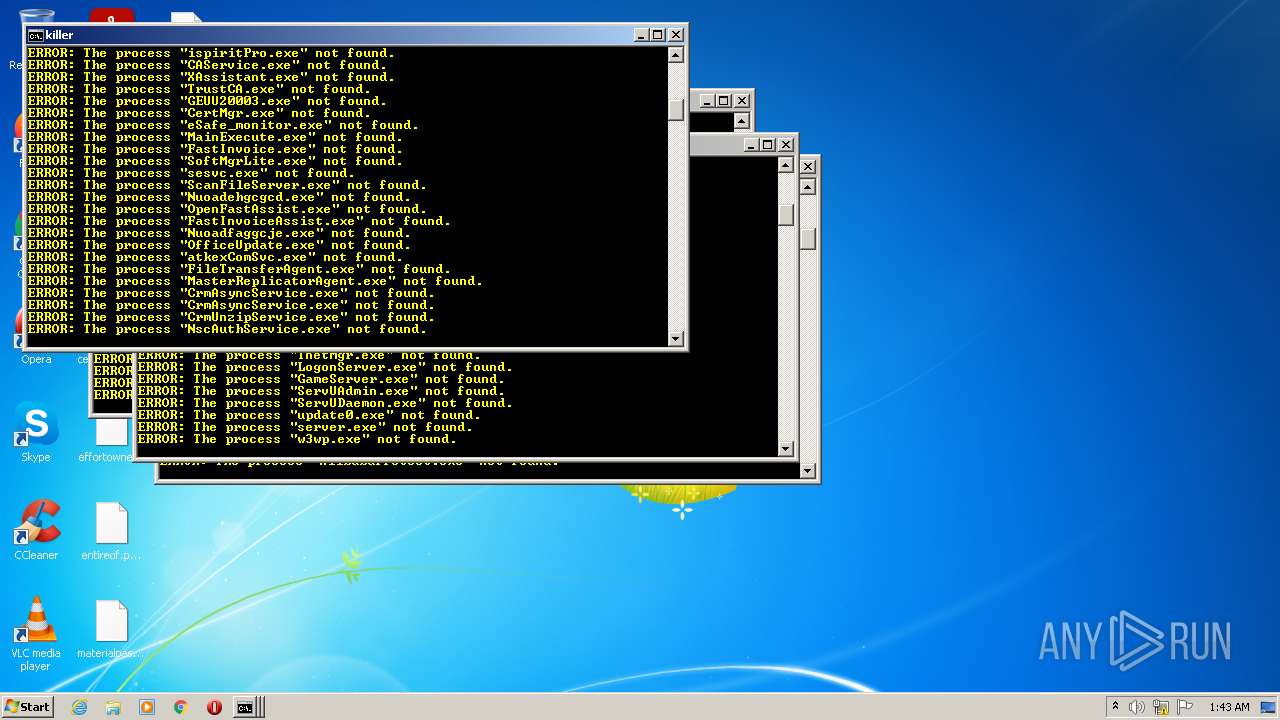
Uses TASKKILL.EXE to kill process
- cmd.exe (PID: 1068)
- cmd.exe (PID: 2392)
- cmd.exe (PID: 1544)
- cmd.exe (PID: 3180)
- cmd.exe (PID: 1256)
- cmd.exe (PID: 2908)
- cmd.exe (PID: 1748)
- cmd.exe (PID: 1372)
- cmd.exe (PID: 1636)
- cmd.exe (PID: 3464)
- cmd.exe (PID: 3680)
Uses TASKKILL.EXE to kill Browsers
- cmd.exe (PID: 1372)
Drops a file with a compile date too recent
- a7018ff4aaaaebda06615da54ab7d3dcfe06ffda501254eb9654aa27152629bb.exe (PID: 3928)
Creates files like Ransomware instruction
- a7018ff4aaaaebda06615da54ab7d3dcfe06ffda501254eb9654aa27152629bb.exe (PID: 3928)
Creates files in the program directory
- a7018ff4aaaaebda06615da54ab7d3dcfe06ffda501254eb9654aa27152629bb.exe (PID: 3928)
INFO
Checks supported languages
- net.exe (PID: 3112)
- net1.exe (PID: 2688)
- sc.exe (PID: 700)
- sc.exe (PID: 3100)
- net.exe (PID: 1368)
- sc.exe (PID: 1116)
- net1.exe (PID: 3988)
- sc.exe (PID: 2992)
- net.exe (PID: 2616)
- sc.exe (PID: 1384)
- taskkill.exe (PID: 2216)
- net.exe (PID: 2316)
- sc.exe (PID: 3604)
- sc.exe (PID: 496)
- net1.exe (PID: 3204)
- net.exe (PID: 3116)
- net.exe (PID: 3860)
- net.exe (PID: 3428)
- net1.exe (PID: 2800)
- sc.exe (PID: 3896)
- sc.exe (PID: 2808)
- sc.exe (PID: 2276)
- sc.exe (PID: 3488)
- net1.exe (PID: 2492)
- net1.exe (PID: 2496)
- net1.exe (PID: 3712)
- sc.exe (PID: 2440)
- net.exe (PID: 4092)
- net.exe (PID: 2532)
- net1.exe (PID: 672)
- net.exe (PID: 3876)
- net1.exe (PID: 1144)
- net.exe (PID: 2516)
- sc.exe (PID: 3852)
- net.exe (PID: 2952)
- net1.exe (PID: 3760)
- net1.exe (PID: 3976)
- sc.exe (PID: 4036)
- net1.exe (PID: 3708)
- sc.exe (PID: 2152)
- net.exe (PID: 1096)
- sc.exe (PID: 3176)
- net.exe (PID: 3400)
- sc.exe (PID: 2428)
- sc.exe (PID: 3704)
- net1.exe (PID: 576)
- net1.exe (PID: 2508)
- sc.exe (PID: 2436)
- taskkill.exe (PID: 2604)
- net.exe (PID: 2100)
- net.exe (PID: 2496)
- sc.exe (PID: 1876)
- net1.exe (PID: 2092)
- net.exe (PID: 832)
- net1.exe (PID: 2856)
- sc.exe (PID: 3716)
- net1.exe (PID: 3880)
- taskkill.exe (PID: 2212)
- sc.exe (PID: 2740)
- taskkill.exe (PID: 1660)
- net.exe (PID: 1000)
- sc.exe (PID: 2848)
- net.exe (PID: 3500)
- sc.exe (PID: 1236)
- sc.exe (PID: 3068)
- net1.exe (PID: 3272)
- sc.exe (PID: 1304)
- sc.exe (PID: 3060)
- sc.exe (PID: 3988)
- net.exe (PID: 3468)
- taskkill.exe (PID: 2316)
- net1.exe (PID: 1296)
- sc.exe (PID: 1520)
- sc.exe (PID: 3552)
- taskkill.exe (PID: 2968)
- sc.exe (PID: 3280)
- net.exe (PID: 1412)
- net.exe (PID: 356)
- net1.exe (PID: 3520)
- net.exe (PID: 672)
- sc.exe (PID: 1760)
- taskkill.exe (PID: 3276)
- net1.exe (PID: 2424)
- sc.exe (PID: 2820)
- sc.exe (PID: 3304)
- sc.exe (PID: 2972)
- net.exe (PID: 652)
- sc.exe (PID: 3864)
- sc.exe (PID: 2684)
- taskkill.exe (PID: 1088)
- net1.exe (PID: 3876)
- net1.exe (PID: 572)
- sc.exe (PID: 2932)
- taskkill.exe (PID: 3924)
- sc.exe (PID: 3232)
- net.exe (PID: 3852)
- net1.exe (PID: 3580)
- sc.exe (PID: 188)
- net.exe (PID: 2872)
- net1.exe (PID: 3860)
- sc.exe (PID: 2856)
- sc.exe (PID: 2184)
- net.exe (PID: 3020)
- sc.exe (PID: 2812)
- net.exe (PID: 3588)
- net.exe (PID: 2052)
- sc.exe (PID: 2528)
- net1.exe (PID: 3324)
- sc.exe (PID: 2244)
- net1.exe (PID: 3584)
- net1.exe (PID: 2424)
- net.exe (PID: 2200)
- sc.exe (PID: 804)
- net1.exe (PID: 3908)
- sc.exe (PID: 576)
- net.exe (PID: 2324)
- net1.exe (PID: 2532)
- sc.exe (PID: 188)
- sc.exe (PID: 3892)
- net1.exe (PID: 4092)
- sc.exe (PID: 1324)
- net.exe (PID: 3480)
- net1.exe (PID: 3068)
- sc.exe (PID: 2764)
- net.exe (PID: 2156)
- sc.exe (PID: 2292)
- sc.exe (PID: 636)
- net.exe (PID: 3172)
- net1.exe (PID: 3804)
- sc.exe (PID: 2580)
- sc.exe (PID: 3788)
- sc.exe (PID: 3380)
- sc.exe (PID: 2860)
- net1.exe (PID: 3100)
- net.exe (PID: 1512)
- net.exe (PID: 1564)
- sc.exe (PID: 1436)
- net.exe (PID: 1996)
- net1.exe (PID: 3116)
- net.exe (PID: 3644)
- sc.exe (PID: 2400)
- sc.exe (PID: 3972)
- net1.exe (PID: 3552)
- net.exe (PID: 2248)
- sc.exe (PID: 2436)
- sc.exe (PID: 3956)
- sc.exe (PID: 2456)
- net1.exe (PID: 532)
- sc.exe (PID: 1220)
- net1.exe (PID: 2200)
- net1.exe (PID: 2872)
- net.exe (PID: 3340)
- net.exe (PID: 1968)
- sc.exe (PID: 2888)
- net.exe (PID: 3588)
- net1.exe (PID: 2024)
- net.exe (PID: 4004)
- sc.exe (PID: 1236)
- taskkill.exe (PID: 2648)
- sc.exe (PID: 3432)
- sc.exe (PID: 3352)
- sc.exe (PID: 2440)
- net1.exe (PID: 2280)
- sc.exe (PID: 3584)
- net1.exe (PID: 2800)
- taskkill.exe (PID: 3116)
- net1.exe (PID: 700)
- sc.exe (PID: 1872)
- sc.exe (PID: 804)
- sc.exe (PID: 868)
- net.exe (PID: 3640)
- sc.exe (PID: 1936)
- sc.exe (PID: 1124)
- sc.exe (PID: 4048)
- net.exe (PID: 1608)
- sc.exe (PID: 2376)
- sc.exe (PID: 3728)
- net1.exe (PID: 1996)
- sc.exe (PID: 1524)
- net1.exe (PID: 2480)
- net.exe (PID: 1784)
- net1.exe (PID: 4020)
- net1.exe (PID: 2076)
- sc.exe (PID: 2524)
- net1.exe (PID: 2284)
- sc.exe (PID: 3916)
- net.exe (PID: 1992)
- sc.exe (PID: 1728)
- net.exe (PID: 3908)
- sc.exe (PID: 3244)
- net.exe (PID: 4092)
- sc.exe (PID: 3020)
- net1.exe (PID: 2676)
- net1.exe (PID: 1948)
- net.exe (PID: 576)
- sc.exe (PID: 2216)
- taskkill.exe (PID: 2100)
- sc.exe (PID: 3936)
- sc.exe (PID: 1872)
- sc.exe (PID: 628)
- net.exe (PID: 3712)
- net.exe (PID: 3532)
- sc.exe (PID: 4048)
- sc.exe (PID: 2024)
- net1.exe (PID: 3540)
- net1.exe (PID: 2720)
- sc.exe (PID: 3060)
- net.exe (PID: 2092)
- net.exe (PID: 3500)
- sc.exe (PID: 2284)
- net.exe (PID: 2504)
- net.exe (PID: 2384)
- net1.exe (PID: 3568)
- net.exe (PID: 2400)
- net1.exe (PID: 744)
- sc.exe (PID: 2440)
- net1.exe (PID: 3488)
- sc.exe (PID: 3036)
- net1.exe (PID: 2892)
- sc.exe (PID: 2340)
- sc.exe (PID: 2972)
- net.exe (PID: 2856)
- net1.exe (PID: 1292)
- net.exe (PID: 2528)
- sc.exe (PID: 2616)
- net1.exe (PID: 628)
- sc.exe (PID: 3164)
- sc.exe (PID: 3580)
- sc.exe (PID: 4048)
- net.exe (PID: 3876)
- sc.exe (PID: 2756)
- net.exe (PID: 3848)
- net1.exe (PID: 2792)
- net.exe (PID: 3000)
- sc.exe (PID: 1228)
- net1.exe (PID: 580)
- net1.exe (PID: 4052)
- net.exe (PID: 3020)
- sc.exe (PID: 3904)
- net1.exe (PID: 2388)
- sc.exe (PID: 3488)
- sc.exe (PID: 3044)
- net.exe (PID: 2572)
- sc.exe (PID: 868)
- net.exe (PID: 3480)
- net1.exe (PID: 636)
- net1.exe (PID: 3996)
- net.exe (PID: 2856)
- net.exe (PID: 3588)
- sc.exe (PID: 3892)
- sc.exe (PID: 2860)
- sc.exe (PID: 3212)
- net1.exe (PID: 2156)
- sc.exe (PID: 3552)
- net1.exe (PID: 2712)
- net1.exe (PID: 3460)
- net.exe (PID: 3788)
- net.exe (PID: 3500)
- sc.exe (PID: 3316)
- sc.exe (PID: 2664)
- net1.exe (PID: 1512)
- sc.exe (PID: 2788)
- sc.exe (PID: 3968)
- net.exe (PID: 1740)
- net.exe (PID: 3852)
- sc.exe (PID: 1728)
- sc.exe (PID: 2096)
- net1.exe (PID: 1760)
- sc.exe (PID: 3708)
- net1.exe (PID: 3332)
- sc.exe (PID: 1968)
- net.exe (PID: 1852)
- net.exe (PID: 3540)
- sc.exe (PID: 2280)
- net.exe (PID: 3564)
- sc.exe (PID: 3728)
- net1.exe (PID: 1564)
- net1.exe (PID: 2236)
- net1.exe (PID: 3804)
- sc.exe (PID: 1296)
- sc.exe (PID: 4092)
- net.exe (PID: 3908)
- net.exe (PID: 3520)
- net.exe (PID: 736)
- net1.exe (PID: 3716)
- sc.exe (PID: 4040)
- sc.exe (PID: 3016)
- net1.exe (PID: 3788)
- sc.exe (PID: 2388)
- sc.exe (PID: 4048)
- net.exe (PID: 3804)
- sc.exe (PID: 2736)
- net1.exe (PID: 1412)
- net1.exe (PID: 1176)
- sc.exe (PID: 744)
- net.exe (PID: 1384)
- net1.exe (PID: 3900)
- net1.exe (PID: 2852)
- net.exe (PID: 564)
- net1.exe (PID: 3284)
- net.exe (PID: 3000)
- sc.exe (PID: 3712)
- sc.exe (PID: 3816)
- sc.exe (PID: 2476)
- sc.exe (PID: 3832)
- sc.exe (PID: 1404)
- net.exe (PID: 3860)
- net.exe (PID: 1176)
- sc.exe (PID: 848)
- net.exe (PID: 1612)
- sc.exe (PID: 4092)
- taskkill.exe (PID: 1520)
- net1.exe (PID: 1220)
- sc.exe (PID: 3532)
- net1.exe (PID: 1436)
- taskkill.exe (PID: 1984)
- net1.exe (PID: 576)
- sc.exe (PID: 532)
- sc.exe (PID: 2156)
- net.exe (PID: 3792)
- sc.exe (PID: 2912)
- net1.exe (PID: 2972)
- net1.exe (PID: 2252)
- net.exe (PID: 672)
- sc.exe (PID: 2512)
- sc.exe (PID: 2952)
- net.exe (PID: 1368)
- sc.exe (PID: 3848)
- net1.exe (PID: 3640)
- sc.exe (PID: 3492)
- sc.exe (PID: 1296)
- sc.exe (PID: 2200)
- net.exe (PID: 2960)
- net1.exe (PID: 1324)
- net1.exe (PID: 3008)
- sc.exe (PID: 3644)
- taskkill.exe (PID: 3908)
- sc.exe (PID: 2464)
- net.exe (PID: 3000)
- sc.exe (PID: 3616)
- sc.exe (PID: 4028)
- net.exe (PID: 2436)
- taskkill.exe (PID: 3716)
- taskkill.exe (PID: 2684)
- sc.exe (PID: 2128)
- net.exe (PID: 2932)
- net.exe (PID: 3900)
- net1.exe (PID: 3748)
- net1.exe (PID: 1164)
- net1.exe (PID: 1660)
- sc.exe (PID: 2800)
- sc.exe (PID: 1412)
- sc.exe (PID: 1852)
- net1.exe (PID: 3324)
- sc.exe (PID: 3592)
- net.exe (PID: 2492)
- sc.exe (PID: 636)
- sc.exe (PID: 3480)
- sc.exe (PID: 3704)
- taskkill.exe (PID: 4028)
- net1.exe (PID: 3284)
- sc.exe (PID: 712)
- net.exe (PID: 804)
- net.exe (PID: 1596)
- sc.exe (PID: 1168)
- net.exe (PID: 272)
- sc.exe (PID: 3692)
- net1.exe (PID: 1400)
- taskkill.exe (PID: 1968)
- sc.exe (PID: 1444)
- net1.exe (PID: 652)
- sc.exe (PID: 2380)
- sc.exe (PID: 2464)
- sc.exe (PID: 3044)
- net1.exe (PID: 2472)
- net.exe (PID: 3212)
- net.exe (PID: 1296)
- net1.exe (PID: 600)
- sc.exe (PID: 3268)
- sc.exe (PID: 3316)
- sc.exe (PID: 1424)
- net.exe (PID: 3532)
- net.exe (PID: 2616)
- sc.exe (PID: 1996)
- taskkill.exe (PID: 2184)
- net1.exe (PID: 568)
- taskkill.exe (PID: 3568)
- taskkill.exe (PID: 3128)
- sc.exe (PID: 532)
- sc.exe (PID: 3492)
- sc.exe (PID: 2092)
- net1.exe (PID: 2544)
- net1.exe (PID: 1368)
- net.exe (PID: 3792)
- sc.exe (PID: 832)
- net.exe (PID: 2376)
- sc.exe (PID: 2292)
- net1.exe (PID: 2640)
- sc.exe (PID: 3832)
- sc.exe (PID: 3704)
- sc.exe (PID: 2104)
- sc.exe (PID: 3972)
- sc.exe (PID: 3500)
- sc.exe (PID: 3732)
- sc.exe (PID: 3892)
- net1.exe (PID: 3440)
- net.exe (PID: 2496)
- net.exe (PID: 2092)
- sc.exe (PID: 2368)
- net1.exe (PID: 3832)
- net1.exe (PID: 3372)
- net.exe (PID: 3988)
- sc.exe (PID: 636)
- taskkill.exe (PID: 832)
- sc.exe (PID: 4012)
- net.exe (PID: 3804)
- sc.exe (PID: 3124)
- sc.exe (PID: 2180)
- net1.exe (PID: 1740)
- sc.exe (PID: 2252)
- net1.exe (PID: 2276)
- sc.exe (PID: 3232)
- net1.exe (PID: 568)
- sc.exe (PID: 1116)
- net.exe (PID: 2880)
- sc.exe (PID: 2332)
- net.exe (PID: 3108)
- net.exe (PID: 3096)
- sc.exe (PID: 3720)
- net1.exe (PID: 2280)
- net.exe (PID: 3004)
- sc.exe (PID: 3456)
- net1.exe (PID: 2960)
- sc.exe (PID: 2476)
- net.exe (PID: 1044)
- sc.exe (PID: 1876)
- net1.exe (PID: 2084)
- sc.exe (PID: 2092)
- net.exe (PID: 2932)
- net1.exe (PID: 3108)
- net.exe (PID: 3480)
- sc.exe (PID: 1164)
- net.exe (PID: 2440)
- net1.exe (PID: 2508)
- sc.exe (PID: 2252)
- sc.exe (PID: 3156)
- net1.exe (PID: 3440)
- sc.exe (PID: 3360)
- sc.exe (PID: 2236)
- net1.exe (PID: 1996)
- sc.exe (PID: 1384)
- net.exe (PID: 1936)
- net.exe (PID: 3728)
- net1.exe (PID: 3640)
- net1.exe (PID: 1632)
- net1.exe (PID: 712)
- sc.exe (PID: 3912)
- net.exe (PID: 2232)
- sc.exe (PID: 2968)
- net.exe (PID: 2528)
- net.exe (PID: 3372)
- net.exe (PID: 1660)
- sc.exe (PID: 2540)
- net1.exe (PID: 2496)
- sc.exe (PID: 2480)
- taskkill.exe (PID: 2816)
- sc.exe (PID: 4076)
- net.exe (PID: 1236)
- sc.exe (PID: 1304)
- net.exe (PID: 3916)
- sc.exe (PID: 2920)
- net1.exe (PID: 2288)
- net1.exe (PID: 1872)
- sc.exe (PID: 2696)
- sc.exe (PID: 2056)
- sc.exe (PID: 3004)
- net.exe (PID: 2288)
- net.exe (PID: 2464)
- net1.exe (PID: 2232)
- net.exe (PID: 520)
- taskkill.exe (PID: 2276)
- net1.exe (PID: 3732)
- taskkill.exe (PID: 1704)
- net1.exe (PID: 2532)
- net1.exe (PID: 968)
- sc.exe (PID: 3204)
- net1.exe (PID: 1728)
- sc.exe (PID: 1992)
- taskkill.exe (PID: 3096)
- taskkill.exe (PID: 2424)
- sc.exe (PID: 568)
- sc.exe (PID: 2912)
- net.exe (PID: 3372)
- net1.exe (PID: 3908)
- sc.exe (PID: 996)
- sc.exe (PID: 2104)
- sc.exe (PID: 3856)
- net.exe (PID: 4048)
- net1.exe (PID: 2216)
- net1.exe (PID: 3968)
- net1.exe (PID: 3816)
- net.exe (PID: 496)
- net.exe (PID: 3536)
- net.exe (PID: 3896)
- net.exe (PID: 1272)
- sc.exe (PID: 3900)
- net1.exe (PID: 436)
- sc.exe (PID: 2696)
- net1.exe (PID: 3932)
- net1.exe (PID: 3232)
- sc.exe (PID: 1096)
- sc.exe (PID: 3212)
- net.exe (PID: 3268)
- taskkill.exe (PID: 2472)
- sc.exe (PID: 2380)
- net.exe (PID: 2388)
- net1.exe (PID: 2216)
- sc.exe (PID: 1688)
- net.exe (PID: 848)
- net.exe (PID: 120)
- sc.exe (PID: 652)
- net1.exe (PID: 3880)
- sc.exe (PID: 3372)
- net.exe (PID: 3276)
- taskkill.exe (PID: 3020)
- sc.exe (PID: 2284)
- net1.exe (PID: 2632)
- net.exe (PID: 492)
- net.exe (PID: 3716)
- taskkill.exe (PID: 3712)
- sc.exe (PID: 2172)
- taskkill.exe (PID: 4028)
- net.exe (PID: 2712)
- net1.exe (PID: 2532)
- net.exe (PID: 3736)
- net1.exe (PID: 2916)
- net1.exe (PID: 2696)
- sc.exe (PID: 3268)
- taskkill.exe (PID: 4092)
- sc.exe (PID: 1164)
- sc.exe (PID: 3196)
- sc.exe (PID: 1524)
- sc.exe (PID: 3640)
- net1.exe (PID: 2684)
- net1.exe (PID: 1024)
- net1.exe (PID: 848)
- net1.exe (PID: 2640)
- sc.exe (PID: 568)
- net.exe (PID: 3064)
- net.exe (PID: 3044)
- net.exe (PID: 3732)
- net1.exe (PID: 3268)
- sc.exe (PID: 4076)
- net1.exe (PID: 3060)
- net1.exe (PID: 3304)
- net1.exe (PID: 2236)
- sc.exe (PID: 1588)
- net.exe (PID: 1228)
- net.exe (PID: 3740)
- sc.exe (PID: 3956)
- net.exe (PID: 3204)
- sc.exe (PID: 3536)
- sc.exe (PID: 1600)
- net.exe (PID: 1828)
- net.exe (PID: 2568)
- sc.exe (PID: 3428)
- sc.exe (PID: 3616)
- net1.exe (PID: 1632)
- sc.exe (PID: 2252)
- net1.exe (PID: 1512)
- net1.exe (PID: 804)
- taskkill.exe (PID: 4004)
- net.exe (PID: 3124)
- net.exe (PID: 1220)
- sc.exe (PID: 3036)
- taskkill.exe (PID: 1992)
- net.exe (PID: 1876)
- net1.exe (PID: 4084)
- net1.exe (PID: 2812)
- net.exe (PID: 4048)
- net.exe (PID: 1272)
- net1.exe (PID: 3264)
- net.exe (PID: 2088)
- net1.exe (PID: 2280)
- sc.exe (PID: 2616)
- net.exe (PID: 1000)
- sc.exe (PID: 2376)
- sc.exe (PID: 4088)
- net1.exe (PID: 3592)
- sc.exe (PID: 2440)
- taskkill.exe (PID: 3064)
- net1.exe (PID: 1588)
- net.exe (PID: 688)
- net.exe (PID: 3976)
- sc.exe (PID: 1176)
- net.exe (PID: 2216)
- net1.exe (PID: 2516)
- taskkill.exe (PID: 1936)
- net.exe (PID: 652)
- net1.exe (PID: 600)
- taskkill.exe (PID: 2312)
- net1.exe (PID: 2992)
- net1.exe (PID: 2736)
- sc.exe (PID: 2632)
- net1.exe (PID: 3592)
- net.exe (PID: 2712)
- net.exe (PID: 3876)
- sc.exe (PID: 2756)
- net.exe (PID: 3968)
- net.exe (PID: 3112)
- taskkill.exe (PID: 2144)
- sc.exe (PID: 880)
- net1.exe (PID: 2512)
- net.exe (PID: 2520)
- taskkill.exe (PID: 1024)
- taskkill.exe (PID: 3760)
- net.exe (PID: 3164)
- net1.exe (PID: 2968)
- net.exe (PID: 4072)
- net1.exe (PID: 2832)
- net1.exe (PID: 3860)
- net1.exe (PID: 2504)
- taskkill.exe (PID: 3848)
- taskkill.exe (PID: 576)
- net1.exe (PID: 3704)
- net.exe (PID: 1740)
- net.exe (PID: 1384)
- net1.exe (PID: 4076)
- net.exe (PID: 4052)
- net1.exe (PID: 1444)
- taskkill.exe (PID: 2400)
- net.exe (PID: 3068)
- net.exe (PID: 2260)
- net1.exe (PID: 2544)
- net1.exe (PID: 492)
- net1.exe (PID: 1808)
- net.exe (PID: 3468)
- net.exe (PID: 2284)
- net1.exe (PID: 3752)
- net1.exe (PID: 4028)
- taskkill.exe (PID: 2380)
- taskkill.exe (PID: 1996)
- taskkill.exe (PID: 3752)
- net.exe (PID: 876)
- taskkill.exe (PID: 3160)
- taskkill.exe (PID: 4068)
- net.exe (PID: 2112)
- net1.exe (PID: 4060)
- net.exe (PID: 3248)
- net1.exe (PID: 3368)
- taskkill.exe (PID: 2648)
- taskkill.exe (PID: 3380)
- net.exe (PID: 3912)
- taskkill.exe (PID: 3400)
- taskkill.exe (PID: 3228)
- taskkill.exe (PID: 1244)
- net1.exe (PID: 1000)
- taskkill.exe (PID: 2156)
- taskkill.exe (PID: 868)
- net1.exe (PID: 3892)
- net.exe (PID: 3880)
- net.exe (PID: 3788)
- net1.exe (PID: 3304)
- net.exe (PID: 2092)
- net.exe (PID: 628)
- net1.exe (PID: 3712)
- net1.exe (PID: 2476)
- net.exe (PID: 1324)
- net1.exe (PID: 1524)
- net.exe (PID: 2812)
- net.exe (PID: 2572)
- net1.exe (PID: 3644)
- taskkill.exe (PID: 1696)
- net1.exe (PID: 3832)
- net.exe (PID: 3244)
- net1.exe (PID: 1876)
- taskkill.exe (PID: 2216)
- taskkill.exe (PID: 1404)
- net.exe (PID: 2072)
- net.exe (PID: 2688)
- net1.exe (PID: 2676)
- net1.exe (PID: 3352)
- net1.exe (PID: 3736)
- net.exe (PID: 2164)
- net.exe (PID: 2632)
- net1.exe (PID: 3220)
- net1.exe (PID: 3816)
- taskkill.exe (PID: 3568)
- net1.exe (PID: 2172)
- net.exe (PID: 736)
- taskkill.exe (PID: 2744)
- net1.exe (PID: 1296)
- net.exe (PID: 2336)
- net.exe (PID: 3992)
- net1.exe (PID: 1124)
- net.exe (PID: 3540)
- net1.exe (PID: 2512)
- net.exe (PID: 2916)
- net.exe (PID: 4072)
- net.exe (PID: 2916)
- net1.exe (PID: 2436)
- net.exe (PID: 3380)
- net1.exe (PID: 996)
- net1.exe (PID: 1148)
- net1.exe (PID: 2092)
- taskkill.exe (PID: 2428)
- net1.exe (PID: 3996)
- net.exe (PID: 652)
- sc.exe (PID: 3852)
- net.exe (PID: 1272)
- net1.exe (PID: 3336)
- taskkill.exe (PID: 3480)
- sc.exe (PID: 3352)
- taskkill.exe (PID: 2820)
- net.exe (PID: 496)
- taskkill.exe (PID: 3864)
- net1.exe (PID: 2336)
- taskkill.exe (PID: 832)
- taskkill.exe (PID: 3532)
- sc.exe (PID: 1424)
- taskkill.exe (PID: 2756)
- taskkill.exe (PID: 1996)
- taskkill.exe (PID: 3280)
- taskkill.exe (PID: 4040)
- net.exe (PID: 1644)
- taskkill.exe (PID: 3908)
- net1.exe (PID: 1096)
- taskkill.exe (PID: 3644)
- taskkill.exe (PID: 1228)
- net1.exe (PID: 3468)
- taskkill.exe (PID: 3536)
- net.exe (PID: 3924)
- taskkill.exe (PID: 2972)
- taskkill.exe (PID: 3368)
- sc.exe (PID: 2520)
- taskkill.exe (PID: 3008)
- taskkill.exe (PID: 2912)
- sc.exe (PID: 3748)
- taskkill.exe (PID: 1740)
- sc.exe (PID: 2460)
- taskkill.exe (PID: 572)
- taskkill.exe (PID: 576)
- taskkill.exe (PID: 2380)
- taskkill.exe (PID: 2852)
- taskkill.exe (PID: 3004)
- sc.exe (PID: 1292)
- taskkill.exe (PID: 2316)
- taskkill.exe (PID: 3688)
- taskkill.exe (PID: 1228)
- taskkill.exe (PID: 2112)
- taskkill.exe (PID: 3336)
- taskkill.exe (PID: 188)
- taskkill.exe (PID: 3760)
- taskkill.exe (PID: 2252)
- taskkill.exe (PID: 1368)
- taskkill.exe (PID: 1332)
- taskkill.exe (PID: 3636)
- taskkill.exe (PID: 3892)
- taskkill.exe (PID: 2300)
- taskkill.exe (PID: 3924)
- taskkill.exe (PID: 2752)
- taskkill.exe (PID: 3368)
- taskkill.exe (PID: 1876)
- taskkill.exe (PID: 760)
- taskkill.exe (PID: 628)
- taskkill.exe (PID: 1300)
- taskkill.exe (PID: 876)
- taskkill.exe (PID: 3028)
- taskkill.exe (PID: 1412)
- taskkill.exe (PID: 3100)
- taskkill.exe (PID: 436)
- net.exe (PID: 2572)
- net1.exe (PID: 2264)
- taskkill.exe (PID: 652)
- taskkill.exe (PID: 3936)
- taskkill.exe (PID: 676)
- taskkill.exe (PID: 3576)
- taskkill.exe (PID: 3020)
- taskkill.exe (PID: 3848)
- net.exe (PID: 744)
- net.exe (PID: 1548)
- taskkill.exe (PID: 1324)
- net1.exe (PID: 3976)
- net1.exe (PID: 3272)
- taskkill.exe (PID: 2532)
- taskkill.exe (PID: 3276)
- taskkill.exe (PID: 2928)
- taskkill.exe (PID: 1828)
- net1.exe (PID: 3424)
- net.exe (PID: 3028)
- net1.exe (PID: 3816)
- net1.exe (PID: 2572)
- net.exe (PID: 2144)
- net.exe (PID: 1004)
- net1.exe (PID: 2892)
- net.exe (PID: 1548)
- taskkill.exe (PID: 2384)
- taskkill.exe (PID: 3020)
- taskkill.exe (PID: 2080)
- net1.exe (PID: 2540)
- net.exe (PID: 3644)
- taskkill.exe (PID: 2616)
- taskkill.exe (PID: 2580)
- taskkill.exe (PID: 1876)
- taskkill.exe (PID: 1660)
- taskkill.exe (PID: 4052)
- net.exe (PID: 2268)
- net1.exe (PID: 1708)
- net1.exe (PID: 4004)
- net.exe (PID: 3272)
- net.exe (PID: 3028)
- net1.exe (PID: 2724)
- net1.exe (PID: 3956)
- taskkill.exe (PID: 3972)
- taskkill.exe (PID: 3468)
- taskkill.exe (PID: 3556)
- taskkill.exe (PID: 564)
- taskkill.exe (PID: 2888)
- taskkill.exe (PID: 2928)
- net.exe (PID: 3400)
- taskkill.exe (PID: 3020)
- taskkill.exe (PID: 2284)
- taskkill.exe (PID: 3160)
- taskkill.exe (PID: 2248)
- taskkill.exe (PID: 2764)
- taskkill.exe (PID: 3644)
- taskkill.exe (PID: 2264)
- taskkill.exe (PID: 1948)
- taskkill.exe (PID: 2604)
- taskkill.exe (PID: 3468)
- taskkill.exe (PID: 1124)
- taskkill.exe (PID: 1148)
- taskkill.exe (PID: 2852)
- taskkill.exe (PID: 2960)
- taskkill.exe (PID: 1412)
- taskkill.exe (PID: 2212)
- taskkill.exe (PID: 3792)
- taskkill.exe (PID: 392)
- taskkill.exe (PID: 1596)
- taskkill.exe (PID: 3652)
- taskkill.exe (PID: 1116)
- taskkill.exe (PID: 776)
- taskkill.exe (PID: 3028)
- taskkill.exe (PID: 3540)
- taskkill.exe (PID: 3100)
- taskkill.exe (PID: 3536)
- taskkill.exe (PID: 2532)
- taskkill.exe (PID: 2336)
- taskkill.exe (PID: 532)
- taskkill.exe (PID: 2520)
- taskkill.exe (PID: 3804)
- taskkill.exe (PID: 2544)
- taskkill.exe (PID: 3032)
- taskkill.exe (PID: 3336)
- taskkill.exe (PID: 1864)
- taskkill.exe (PID: 3272)
- taskkill.exe (PID: 2216)
- taskkill.exe (PID: 580)
- taskkill.exe (PID: 2516)
- taskkill.exe (PID: 3980)
- taskkill.exe (PID: 1644)
- taskkill.exe (PID: 2880)
- taskkill.exe (PID: 3732)
- taskkill.exe (PID: 1996)
- taskkill.exe (PID: 3360)
- taskkill.exe (PID: 2580)
- taskkill.exe (PID: 2148)
- taskkill.exe (PID: 2088)
- taskkill.exe (PID: 3904)
- taskkill.exe (PID: 2704)
- taskkill.exe (PID: 3872)
- taskkill.exe (PID: 2848)
- taskkill.exe (PID: 3804)
- taskkill.exe (PID: 1412)
- taskkill.exe (PID: 1696)
- taskkill.exe (PID: 2696)
- taskkill.exe (PID: 3432)
- taskkill.exe (PID: 2440)
- taskkill.exe (PID: 1728)
- taskkill.exe (PID: 120)
- taskkill.exe (PID: 1304)
Reads the computer name
- sc.exe (PID: 700)
- net1.exe (PID: 2688)
- sc.exe (PID: 3100)
- sc.exe (PID: 1116)
- net1.exe (PID: 3988)
- sc.exe (PID: 2992)
- sc.exe (PID: 1384)
- sc.exe (PID: 3604)
- net1.exe (PID: 3204)
- taskkill.exe (PID: 2216)
- sc.exe (PID: 496)
- net1.exe (PID: 2800)
- sc.exe (PID: 3896)
- sc.exe (PID: 2276)
- net1.exe (PID: 2492)
- net1.exe (PID: 3712)
- net1.exe (PID: 2496)
- sc.exe (PID: 2440)
- sc.exe (PID: 3488)
- net1.exe (PID: 672)
- sc.exe (PID: 2808)
- net1.exe (PID: 3708)
- sc.exe (PID: 2152)
- sc.exe (PID: 3852)
- net1.exe (PID: 1144)
- net1.exe (PID: 3760)
- net1.exe (PID: 3976)
- sc.exe (PID: 4036)
- sc.exe (PID: 3704)
- sc.exe (PID: 3176)
- sc.exe (PID: 2428)
- net1.exe (PID: 576)
- net1.exe (PID: 2508)
- sc.exe (PID: 2436)
- sc.exe (PID: 1876)
- taskkill.exe (PID: 2604)
- net1.exe (PID: 2092)
- net1.exe (PID: 3880)
- sc.exe (PID: 3716)
- sc.exe (PID: 2740)
- taskkill.exe (PID: 2212)
- taskkill.exe (PID: 1660)
- net1.exe (PID: 2856)
- sc.exe (PID: 3988)
- sc.exe (PID: 1236)
- sc.exe (PID: 3068)
- net1.exe (PID: 3272)
- sc.exe (PID: 1304)
- sc.exe (PID: 2848)
- sc.exe (PID: 3552)
- net1.exe (PID: 1296)
- sc.exe (PID: 1520)
- sc.exe (PID: 3060)
- net1.exe (PID: 2424)
- sc.exe (PID: 3280)
- net1.exe (PID: 3520)
- sc.exe (PID: 1760)
- sc.exe (PID: 2820)
- sc.exe (PID: 2972)
- sc.exe (PID: 3304)
- taskkill.exe (PID: 2316)
- sc.exe (PID: 3864)
- sc.exe (PID: 2684)
- net1.exe (PID: 3876)
- net1.exe (PID: 572)
- taskkill.exe (PID: 2968)
- sc.exe (PID: 2932)
- sc.exe (PID: 188)
- net1.exe (PID: 3580)
- taskkill.exe (PID: 3924)
- net1.exe (PID: 3860)
- sc.exe (PID: 3232)
- sc.exe (PID: 2184)
- taskkill.exe (PID: 3276)
- sc.exe (PID: 2856)
- taskkill.exe (PID: 1088)
- sc.exe (PID: 2812)
- sc.exe (PID: 804)
- net1.exe (PID: 3324)
- sc.exe (PID: 2528)
- sc.exe (PID: 2244)
- net1.exe (PID: 3584)
- net1.exe (PID: 2424)
- net1.exe (PID: 3908)
- net1.exe (PID: 2532)
- sc.exe (PID: 576)
- sc.exe (PID: 188)
- net1.exe (PID: 4092)
- sc.exe (PID: 3892)
- sc.exe (PID: 1324)
- net1.exe (PID: 3068)
- sc.exe (PID: 3788)
- sc.exe (PID: 2764)
- sc.exe (PID: 2292)
- sc.exe (PID: 636)
- net1.exe (PID: 3804)
- sc.exe (PID: 2580)
- sc.exe (PID: 2860)
- sc.exe (PID: 3380)
- net1.exe (PID: 3552)
- sc.exe (PID: 1436)
- net1.exe (PID: 3100)
- sc.exe (PID: 2400)
- sc.exe (PID: 3972)
- net1.exe (PID: 3116)
- sc.exe (PID: 2436)
- sc.exe (PID: 2456)
- sc.exe (PID: 1220)
- sc.exe (PID: 3956)
- net1.exe (PID: 2200)
- net1.exe (PID: 532)
- sc.exe (PID: 3432)
- sc.exe (PID: 2888)
- net1.exe (PID: 2872)
- net1.exe (PID: 2024)
- sc.exe (PID: 1236)
- sc.exe (PID: 3352)
- net1.exe (PID: 2280)
- sc.exe (PID: 2440)
- sc.exe (PID: 868)
- sc.exe (PID: 3584)
- taskkill.exe (PID: 2648)
- net1.exe (PID: 2800)
- net1.exe (PID: 700)
- sc.exe (PID: 804)
- sc.exe (PID: 1872)
- sc.exe (PID: 1124)
- taskkill.exe (PID: 3116)
- sc.exe (PID: 2376)
- net1.exe (PID: 1996)
- sc.exe (PID: 1524)
- sc.exe (PID: 1936)
- sc.exe (PID: 4048)
- sc.exe (PID: 3728)
- net1.exe (PID: 4020)
- net1.exe (PID: 2076)
- sc.exe (PID: 2524)
- net1.exe (PID: 2284)
- sc.exe (PID: 1728)
- net1.exe (PID: 2480)
- sc.exe (PID: 2216)
- net1.exe (PID: 1948)
- sc.exe (PID: 3916)
- sc.exe (PID: 3244)
- sc.exe (PID: 3020)
- net1.exe (PID: 2676)
- net1.exe (PID: 3540)
- sc.exe (PID: 1872)
- sc.exe (PID: 3936)
- sc.exe (PID: 4048)
- sc.exe (PID: 2024)
- sc.exe (PID: 3060)
- sc.exe (PID: 2284)
- sc.exe (PID: 628)
- net1.exe (PID: 3568)
- net1.exe (PID: 2720)
- net1.exe (PID: 744)
- sc.exe (PID: 2440)
- sc.exe (PID: 3036)
- net1.exe (PID: 2892)
- taskkill.exe (PID: 2100)
- sc.exe (PID: 2340)
- sc.exe (PID: 3164)
- sc.exe (PID: 2972)
- net1.exe (PID: 3488)
- net1.exe (PID: 1292)
- sc.exe (PID: 2616)
- net1.exe (PID: 628)
- sc.exe (PID: 2756)
- sc.exe (PID: 4048)
- sc.exe (PID: 3580)
- sc.exe (PID: 1228)
- net1.exe (PID: 580)
- net1.exe (PID: 4052)
- sc.exe (PID: 3044)
- net1.exe (PID: 2388)
- sc.exe (PID: 3488)
- sc.exe (PID: 3904)
- net1.exe (PID: 2792)
- sc.exe (PID: 868)
- net1.exe (PID: 636)
- net1.exe (PID: 2712)
- sc.exe (PID: 3892)
- sc.exe (PID: 3212)
- net1.exe (PID: 2156)
- sc.exe (PID: 3552)
- sc.exe (PID: 2860)
- sc.exe (PID: 3316)
- sc.exe (PID: 2664)
- net1.exe (PID: 1512)
- net1.exe (PID: 3996)
- sc.exe (PID: 2788)
- sc.exe (PID: 3968)
- net1.exe (PID: 3460)
- sc.exe (PID: 1968)
- sc.exe (PID: 3708)
- net1.exe (PID: 3332)
- sc.exe (PID: 1728)
- sc.exe (PID: 2096)
- net1.exe (PID: 1564)
- net1.exe (PID: 1760)
- net1.exe (PID: 2236)
- net1.exe (PID: 3804)
- sc.exe (PID: 1296)
- sc.exe (PID: 2280)
- sc.exe (PID: 3016)
- net1.exe (PID: 3788)
- sc.exe (PID: 3728)
- net1.exe (PID: 3716)
- sc.exe (PID: 4040)
- sc.exe (PID: 4092)
- net1.exe (PID: 1176)
- sc.exe (PID: 744)
- sc.exe (PID: 2388)
- sc.exe (PID: 4048)
- sc.exe (PID: 2736)
- net1.exe (PID: 1412)
- sc.exe (PID: 2476)
- net1.exe (PID: 3284)
- net1.exe (PID: 3900)
- net1.exe (PID: 2852)
- sc.exe (PID: 3712)
- sc.exe (PID: 3816)
- net1.exe (PID: 1220)
- sc.exe (PID: 1404)
- sc.exe (PID: 3832)
- sc.exe (PID: 848)
- sc.exe (PID: 4092)
- sc.exe (PID: 3532)
- taskkill.exe (PID: 1520)
- sc.exe (PID: 2156)
- sc.exe (PID: 532)
- sc.exe (PID: 2912)
- net1.exe (PID: 2972)
- net1.exe (PID: 1436)
- net1.exe (PID: 576)
- net1.exe (PID: 2252)
- sc.exe (PID: 2512)
- taskkill.exe (PID: 1984)
- sc.exe (PID: 2952)
- sc.exe (PID: 3848)
- net1.exe (PID: 3640)
- sc.exe (PID: 1296)
- sc.exe (PID: 2200)
- sc.exe (PID: 3492)
- net1.exe (PID: 3008)
- sc.exe (PID: 3644)
- sc.exe (PID: 2464)
- sc.exe (PID: 3616)
- sc.exe (PID: 4028)
- net1.exe (PID: 1324)
- taskkill.exe (PID: 3908)
- sc.exe (PID: 2128)
- net1.exe (PID: 3748)
- net1.exe (PID: 1164)
- net1.exe (PID: 1660)
- sc.exe (PID: 2800)
- sc.exe (PID: 1412)
- sc.exe (PID: 1852)
- taskkill.exe (PID: 3716)
- taskkill.exe (PID: 2684)
- sc.exe (PID: 636)
- sc.exe (PID: 3592)
- sc.exe (PID: 3704)
- net1.exe (PID: 3324)
- sc.exe (PID: 3480)
- net1.exe (PID: 1400)
- net1.exe (PID: 3284)
- sc.exe (PID: 3692)
- sc.exe (PID: 712)
- sc.exe (PID: 1444)
- net1.exe (PID: 2472)
- sc.exe (PID: 2380)
- sc.exe (PID: 2464)
- sc.exe (PID: 1168)
- sc.exe (PID: 3044)
- taskkill.exe (PID: 4028)
- taskkill.exe (PID: 1968)
- net1.exe (PID: 652)
- sc.exe (PID: 1996)
- net1.exe (PID: 600)
- sc.exe (PID: 3268)
- sc.exe (PID: 1424)
- sc.exe (PID: 3316)
- net1.exe (PID: 1368)
- sc.exe (PID: 2092)
- net1.exe (PID: 568)
- sc.exe (PID: 3492)
- taskkill.exe (PID: 2184)
- net1.exe (PID: 2544)
- sc.exe (PID: 2292)
- sc.exe (PID: 832)
- sc.exe (PID: 2104)
- sc.exe (PID: 532)
- sc.exe (PID: 3832)
- sc.exe (PID: 3704)
- taskkill.exe (PID: 3128)
- taskkill.exe (PID: 3568)
- sc.exe (PID: 3732)
- sc.exe (PID: 3892)
- sc.exe (PID: 3500)
- net1.exe (PID: 3440)
- sc.exe (PID: 2368)
- net1.exe (PID: 3832)
- net1.exe (PID: 2640)
- net1.exe (PID: 3372)
- sc.exe (PID: 3972)
- sc.exe (PID: 636)
- net1.exe (PID: 2276)
- sc.exe (PID: 4012)
- sc.exe (PID: 3124)
- sc.exe (PID: 2180)
- net1.exe (PID: 1740)
- sc.exe (PID: 2252)
- net1.exe (PID: 568)
- net1.exe (PID: 2280)
- sc.exe (PID: 3232)
- sc.exe (PID: 1116)
- taskkill.exe (PID: 832)
- sc.exe (PID: 3720)
- sc.exe (PID: 3456)
- sc.exe (PID: 2092)
- sc.exe (PID: 2476)
- sc.exe (PID: 2332)
- sc.exe (PID: 1876)
- net1.exe (PID: 2084)
- net1.exe (PID: 2960)
- sc.exe (PID: 3156)
- net1.exe (PID: 3440)
- sc.exe (PID: 3360)
- net1.exe (PID: 3108)
- net1.exe (PID: 2508)
- sc.exe (PID: 2252)
- sc.exe (PID: 2236)
- net1.exe (PID: 1996)
- sc.exe (PID: 1384)
- net1.exe (PID: 3640)
- sc.exe (PID: 1164)
- net1.exe (PID: 712)
- sc.exe (PID: 3912)
- sc.exe (PID: 2968)
- sc.exe (PID: 2540)
- net1.exe (PID: 2496)
- net1.exe (PID: 1632)
- sc.exe (PID: 4076)
- sc.exe (PID: 2480)
- taskkill.exe (PID: 2816)
- sc.exe (PID: 2920)
- net1.exe (PID: 2232)
- net1.exe (PID: 2288)
- net1.exe (PID: 1872)
- sc.exe (PID: 2696)
- sc.exe (PID: 1304)
- sc.exe (PID: 2056)
- net1.exe (PID: 2532)
- sc.exe (PID: 3004)
- taskkill.exe (PID: 2276)
- net1.exe (PID: 3732)
- net1.exe (PID: 968)
- sc.exe (PID: 3204)
- net1.exe (PID: 1728)
- sc.exe (PID: 1992)
- sc.exe (PID: 996)
- sc.exe (PID: 2912)
- taskkill.exe (PID: 1704)
- net1.exe (PID: 3908)
- net1.exe (PID: 2216)
- taskkill.exe (PID: 3096)
- sc.exe (PID: 2104)
- taskkill.exe (PID: 2424)
- net1.exe (PID: 3968)
- sc.exe (PID: 3856)
- net1.exe (PID: 3816)
- sc.exe (PID: 568)
- sc.exe (PID: 2696)
- net1.exe (PID: 3932)
- sc.exe (PID: 1096)
- sc.exe (PID: 3212)
- net1.exe (PID: 436)
- sc.exe (PID: 3900)
- sc.exe (PID: 2380)
- sc.exe (PID: 1688)
- net1.exe (PID: 3232)
- taskkill.exe (PID: 2472)
- net1.exe (PID: 2216)
- net1.exe (PID: 3880)
- sc.exe (PID: 3372)
- sc.exe (PID: 2284)
- net1.exe (PID: 2632)
- sc.exe (PID: 652)
- sc.exe (PID: 3268)
- sc.exe (PID: 2172)
- taskkill.exe (PID: 3020)
- net1.exe (PID: 2916)
- net1.exe (PID: 2696)
- net1.exe (PID: 1024)
- sc.exe (PID: 1164)
- taskkill.exe (PID: 3712)
- taskkill.exe (PID: 4028)
- sc.exe (PID: 1524)
- net1.exe (PID: 2532)
- sc.exe (PID: 3640)
- net1.exe (PID: 2684)
- net1.exe (PID: 3268)
- net1.exe (PID: 848)
- sc.exe (PID: 4076)
- net1.exe (PID: 2640)
- sc.exe (PID: 568)
- sc.exe (PID: 3196)
- taskkill.exe (PID: 4092)
- sc.exe (PID: 3536)
- net1.exe (PID: 3304)
- net1.exe (PID: 2236)
- net1.exe (PID: 3060)
- sc.exe (PID: 1588)
- sc.exe (PID: 1600)
- sc.exe (PID: 3956)
- sc.exe (PID: 3428)
- taskkill.exe (PID: 4004)
- sc.exe (PID: 3616)
- net1.exe (PID: 1632)
- net1.exe (PID: 1512)
- net1.exe (PID: 804)
- sc.exe (PID: 2252)
- sc.exe (PID: 3036)
- net1.exe (PID: 3264)
- sc.exe (PID: 2616)
- sc.exe (PID: 2376)
- net1.exe (PID: 2280)
- net1.exe (PID: 2812)
- net1.exe (PID: 4084)
- net1.exe (PID: 3592)
- net1.exe (PID: 2516)
- taskkill.exe (PID: 1992)
- sc.exe (PID: 2440)
- taskkill.exe (PID: 1936)
- sc.exe (PID: 4088)
- net1.exe (PID: 1588)
- taskkill.exe (PID: 3064)
- sc.exe (PID: 1176)
- net1.exe (PID: 600)
- net1.exe (PID: 2992)
- net1.exe (PID: 2736)
- sc.exe (PID: 2632)
- taskkill.exe (PID: 2312)
- sc.exe (PID: 880)
- taskkill.exe (PID: 2144)
- sc.exe (PID: 2756)
- net1.exe (PID: 2512)
- net1.exe (PID: 3592)
- net1.exe (PID: 3860)
- net1.exe (PID: 2504)
- taskkill.exe (PID: 1024)
- net1.exe (PID: 2968)
- net1.exe (PID: 2832)
- net1.exe (PID: 3704)
- taskkill.exe (PID: 2400)
- taskkill.exe (PID: 3848)
- net1.exe (PID: 1444)
- taskkill.exe (PID: 3760)
- taskkill.exe (PID: 576)
- net1.exe (PID: 3752)
- net1.exe (PID: 4028)
- net1.exe (PID: 2544)
- taskkill.exe (PID: 2380)
- net1.exe (PID: 4076)
- net1.exe (PID: 1808)
- taskkill.exe (PID: 3160)
- taskkill.exe (PID: 1996)
- net1.exe (PID: 3368)
- taskkill.exe (PID: 3752)
- net1.exe (PID: 492)
- net1.exe (PID: 4060)
- taskkill.exe (PID: 4068)
- taskkill.exe (PID: 3400)
- taskkill.exe (PID: 3380)
- taskkill.exe (PID: 2156)
- taskkill.exe (PID: 868)
- net1.exe (PID: 1000)
- taskkill.exe (PID: 2648)
- taskkill.exe (PID: 1244)
- net1.exe (PID: 1524)
- net1.exe (PID: 3304)
- taskkill.exe (PID: 3228)
- net1.exe (PID: 2476)
- net1.exe (PID: 3892)
- net1.exe (PID: 3644)
- net1.exe (PID: 3832)
- net1.exe (PID: 3712)
- net1.exe (PID: 1876)
- taskkill.exe (PID: 2216)
- taskkill.exe (PID: 1404)
- net1.exe (PID: 2676)
- net1.exe (PID: 3352)
- net1.exe (PID: 3736)
- taskkill.exe (PID: 1696)
- net1.exe (PID: 3220)
- net1.exe (PID: 3816)
- net1.exe (PID: 2172)
- taskkill.exe (PID: 2744)
- net1.exe (PID: 1296)
- net1.exe (PID: 1124)
- net1.exe (PID: 2512)
- taskkill.exe (PID: 3568)
- net1.exe (PID: 3996)
- net1.exe (PID: 2436)
- net1.exe (PID: 996)
- net1.exe (PID: 2092)
- taskkill.exe (PID: 2428)
- net1.exe (PID: 2336)
- taskkill.exe (PID: 3864)
- net1.exe (PID: 3336)
- taskkill.exe (PID: 832)
- taskkill.exe (PID: 3480)
- sc.exe (PID: 3852)
- net1.exe (PID: 1148)
- taskkill.exe (PID: 2820)
- taskkill.exe (PID: 3532)
- sc.exe (PID: 1424)
- taskkill.exe (PID: 2756)
- taskkill.exe (PID: 1996)
- sc.exe (PID: 3352)
- taskkill.exe (PID: 4040)
- net1.exe (PID: 1096)
- taskkill.exe (PID: 2972)
- taskkill.exe (PID: 3644)
- taskkill.exe (PID: 3280)
- net1.exe (PID: 3468)
- taskkill.exe (PID: 3536)
- taskkill.exe (PID: 3908)
- taskkill.exe (PID: 1740)
- sc.exe (PID: 2460)
- taskkill.exe (PID: 3368)
- taskkill.exe (PID: 3008)
- taskkill.exe (PID: 1228)
- sc.exe (PID: 3748)
- taskkill.exe (PID: 2912)
- taskkill.exe (PID: 3688)
- taskkill.exe (PID: 2380)
- sc.exe (PID: 2520)
- sc.exe (PID: 1292)
- taskkill.exe (PID: 2316)
- taskkill.exe (PID: 572)
- taskkill.exe (PID: 576)
- taskkill.exe (PID: 2252)
- taskkill.exe (PID: 1228)
- taskkill.exe (PID: 3336)
- taskkill.exe (PID: 2112)
- taskkill.exe (PID: 2852)
- taskkill.exe (PID: 3004)
- taskkill.exe (PID: 3760)
- taskkill.exe (PID: 1368)
- taskkill.exe (PID: 3368)
- taskkill.exe (PID: 1332)
- taskkill.exe (PID: 3892)
- taskkill.exe (PID: 3636)
- taskkill.exe (PID: 2300)
- taskkill.exe (PID: 188)
- taskkill.exe (PID: 3924)
- taskkill.exe (PID: 2752)
- taskkill.exe (PID: 1412)
- taskkill.exe (PID: 3100)
- taskkill.exe (PID: 760)
- taskkill.exe (PID: 628)
- taskkill.exe (PID: 1876)
- taskkill.exe (PID: 1300)
- taskkill.exe (PID: 876)
- taskkill.exe (PID: 3028)
- taskkill.exe (PID: 436)
- taskkill.exe (PID: 652)
- taskkill.exe (PID: 3576)
- taskkill.exe (PID: 3020)
- taskkill.exe (PID: 3936)
- taskkill.exe (PID: 2532)
- taskkill.exe (PID: 676)
- net1.exe (PID: 2264)
- net1.exe (PID: 3976)
- taskkill.exe (PID: 1828)
- taskkill.exe (PID: 1324)
- net1.exe (PID: 3424)
- taskkill.exe (PID: 3276)
- taskkill.exe (PID: 2928)
- taskkill.exe (PID: 3848)
- net1.exe (PID: 2892)
- net1.exe (PID: 3816)
- taskkill.exe (PID: 3020)
- taskkill.exe (PID: 2384)
- net1.exe (PID: 2540)
- net1.exe (PID: 3272)
- net1.exe (PID: 2572)
- taskkill.exe (PID: 2080)
- taskkill.exe (PID: 2616)
- taskkill.exe (PID: 4052)
- taskkill.exe (PID: 1876)
- taskkill.exe (PID: 1660)
- taskkill.exe (PID: 2580)
- net1.exe (PID: 4004)
- net1.exe (PID: 1708)
- net1.exe (PID: 2724)
- taskkill.exe (PID: 2928)
- taskkill.exe (PID: 3556)
- taskkill.exe (PID: 564)
- taskkill.exe (PID: 3468)
- taskkill.exe (PID: 2888)
- net1.exe (PID: 3956)
- taskkill.exe (PID: 3972)
- taskkill.exe (PID: 3020)
- taskkill.exe (PID: 2764)
- taskkill.exe (PID: 2248)
- taskkill.exe (PID: 2284)
- taskkill.exe (PID: 2264)
- taskkill.exe (PID: 3644)
- taskkill.exe (PID: 1948)
- taskkill.exe (PID: 3160)
- taskkill.exe (PID: 1412)
- taskkill.exe (PID: 3468)
- taskkill.exe (PID: 2212)
- taskkill.exe (PID: 2604)
- taskkill.exe (PID: 1124)
- taskkill.exe (PID: 2852)
- taskkill.exe (PID: 2960)
- taskkill.exe (PID: 3540)
- taskkill.exe (PID: 392)
- taskkill.exe (PID: 3792)
- taskkill.exe (PID: 1596)
- taskkill.exe (PID: 3100)
- taskkill.exe (PID: 1148)
- taskkill.exe (PID: 776)
- taskkill.exe (PID: 3028)
- taskkill.exe (PID: 3652)
- taskkill.exe (PID: 532)
- taskkill.exe (PID: 2336)
- taskkill.exe (PID: 3804)
- taskkill.exe (PID: 2544)
- taskkill.exe (PID: 3536)
- taskkill.exe (PID: 2532)
- taskkill.exe (PID: 1116)
- taskkill.exe (PID: 2520)
- taskkill.exe (PID: 3980)
- taskkill.exe (PID: 3032)
- taskkill.exe (PID: 3336)
- taskkill.exe (PID: 2216)
- taskkill.exe (PID: 1644)
- taskkill.exe (PID: 580)
- taskkill.exe (PID: 2516)
- taskkill.exe (PID: 3272)
- taskkill.exe (PID: 2148)
- taskkill.exe (PID: 3732)
- taskkill.exe (PID: 2880)
- taskkill.exe (PID: 3360)
- taskkill.exe (PID: 3904)
- taskkill.exe (PID: 1996)
- taskkill.exe (PID: 2580)
- taskkill.exe (PID: 1864)
- taskkill.exe (PID: 2088)
- taskkill.exe (PID: 1412)
- taskkill.exe (PID: 1696)
- taskkill.exe (PID: 2704)
- taskkill.exe (PID: 2848)
- taskkill.exe (PID: 3872)
- taskkill.exe (PID: 3804)
- taskkill.exe (PID: 2696)
- taskkill.exe (PID: 3432)
- taskkill.exe (PID: 2440)
- taskkill.exe (PID: 1728)
- taskkill.exe (PID: 120)
- taskkill.exe (PID: 1304)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Generic CIL Executable (.NET, Mono, etc.) (82.9) |
|---|---|---|
| .dll | | | Win32 Dynamic Link Library (generic) (7.4) |
| .exe | | | Win32 Executable (generic) (5.1) |
| .exe | | | Generic Win/DOS Executable (2.2) |
| .exe | | | DOS Executable Generic (2.2) |
EXIF
EXE
| AssemblyVersion: | 1.0.0.0 |
|---|---|
| ProductVersion: | 1.0.0.0 |
| ProductName: | ram machine |
| OriginalFileName: | InternalCrossContextDelega.exe |
| LegalTrademarks: | - |
| LegalCopyright: | Copyright © 2015 |
| InternalName: | InternalCrossContextDelega.exe |
| FileVersion: | 1.0.0.0 |
| FileDescription: | ram machine |
| CompanyName: | - |
| Comments: | - |
| CharacterSet: | Unicode |
| LanguageCode: | Neutral |
| FileSubtype: | - |
| ObjectFileType: | Executable application |
| FileOS: | Win32 |
| FileFlags: | (none) |
| FileFlagsMask: | 0x003f |
| ProductVersionNumber: | 1.0.0.0 |
| FileVersionNumber: | 1.0.0.0 |
| Subsystem: | Windows GUI |
| SubsystemVersion: | 4 |
| ImageVersion: | - |
| OSVersion: | 4 |
| EntryPoint: | 0x6b9ee |
| UninitializedDataSize: | - |
| InitializedDataSize: | 6656 |
| CodeSize: | 432640 |
| LinkerVersion: | 48 |
| PEType: | PE32 |
| TimeStamp: | 2022:01:13 17:48:48+01:00 |
| MachineType: | Intel 386 or later, and compatibles |
Summary
| Architecture: | IMAGE_FILE_MACHINE_I386 |
|---|---|
| Subsystem: | IMAGE_SUBSYSTEM_WINDOWS_GUI |
| Compilation Date: | 13-Jan-2022 16:48:48 |
| Comments: | - |
| CompanyName: | - |
| FileDescription: | ram machine |
| FileVersion: | 1.0.0.0 |
| InternalName: | InternalCrossContextDelega.exe |
| LegalCopyright: | Copyright © 2015 |
| LegalTrademarks: | - |
| OriginalFilename: | InternalCrossContextDelega.exe |
| ProductName: | ram machine |
| ProductVersion: | 1.0.0.0 |
| Assembly Version: | 1.0.0.0 |
DOS Header
| Magic number: | MZ |
|---|---|
| Bytes on last page of file: | 0x0090 |
| Pages in file: | 0x0003 |
| Relocations: | 0x0000 |
| Size of header: | 0x0004 |
| Min extra paragraphs: | 0x0000 |
| Max extra paragraphs: | 0xFFFF |
| Initial SS value: | 0x0000 |
| Initial SP value: | 0x00B8 |
| Checksum: | 0x0000 |
| Initial IP value: | 0x0000 |
| Initial CS value: | 0x0000 |
| Overlay number: | 0x0000 |
| OEM identifier: | 0x0000 |
| OEM information: | 0x0000 |
| Address of NE header: | 0x00000080 |
PE Headers
| Signature: | PE |
|---|---|
| Machine: | IMAGE_FILE_MACHINE_I386 |
| Number of sections: | 3 |
| Time date stamp: | 13-Jan-2022 16:48:48 |
| Pointer to Symbol Table: | 0x00000000 |
| Number of symbols: | 0 |
| Size of Optional Header: | 0x00E0 |
| Characteristics: |
|
Sections
Name | Virtual Address | Virtual Size | Raw Size | Charateristics | Entropy |
|---|---|---|---|---|---|
.text | 0x00002000 | 0x000699F4 | 0x00069A00 | IMAGE_SCN_CNT_CODE, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ | 7.61301 |
.rsrc | 0x0006C000 | 0x00001748 | 0x00001800 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 5.22255 |
.reloc | 0x0006E000 | 0x0000000C | 0x00000200 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_DISCARDABLE, IMAGE_SCN_MEM_READ | 0.10191 |
Resources
Title | Entropy | Size | Codepage | Language | Type |
|---|---|---|---|---|---|
1 | 5.00112 | 490 | Latin 1 / Western European | UNKNOWN | RT_MANIFEST |
Imports
mscoree.dll |
Total processes
982
Monitored processes
924
Malicious processes
25
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 120 | net stop TPlusStdAppService1220 | C:\Windows\system32\net.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Net Command Exit code: 2 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 120 | taskkill /IM ControlServer.exe /F | C:\Windows\system32\taskkill.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Terminates Processes Exit code: 128 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 188 | sc delete "ZTE USBIP Client" | C:\Windows\system32\sc.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: A tool to aid in developing services for WindowsNT Exit code: 1060 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 188 | sc delete RtcQms | C:\Windows\system32\sc.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: A tool to aid in developing services for WindowsNT Exit code: 1060 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 188 | taskkill /IM SecureCRTPortable.exe /F | C:\Windows\system32\taskkill.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Terminates Processes Exit code: 128 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 272 | net stop MSExchangeFrontEndTransport | C:\Windows\system32\net.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Net Command Exit code: 2 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 356 | net stop HaoZipSvc | C:\Windows\system32\net.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Net Command Exit code: 2 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 392 | cmd /c "color a & @net stop UIODetect & @net stop VMwareHostd & @net stop TeamViewer8 & @net stop VMUSBArbService & @net stop VMAuthdService & @net stop wanxiao-monitor & @net stop WebAttendServer & @net stop mysqltransport & @net stop VMnetDHCP & @net stop "VMware NAT Service" & @net stop Tomcat8 & @net stop TeamViewer & @net stop QPCore & @net stop CASLicenceServer & @net stop CASWebServer & @net stop AutoUpdateService & @net stop "Alibaba Security Aegis Detect Service" & @net stop "Alibaba Security Aegis Update Service" & @net stop "AliyunService" & @net stop CASXMLService & @net stop AGSService & @net stop RapService & @net stop DDNSService & @net stop iNethinkSQLBackupSvc & @net stop CASVirtualDiskService & @net stop CASMsgSrv & @net stop "OracleOraDb10g_homeliSQL*Plus" & @net stop OracleDBConsoleilas & @net stop MySQL & @net stop TPlusStdAppService1220 & @net stop TPlusStdTaskService1220 & @net stop TPlusStdUpgradeService1220 & @net stop K3MobileServiceManage & @net stop "FileZilla Server" & @net stop DDVRulesProcessor & @net stop ImtsEventSvr & @net stop AutoUpdatePatchService & @net stop OMAILREPORT & @net stop "Dell Hardware Support" & @net stop SupportAssistAgent & @net stop K3MMainSuspendService & @net stop KpService & @net stop ceng_web_svc_d & @net stop KugouService & @net stop pcas & @net stop U8SendMailAdmin & @net stop "Bonjour Service" & @net stop "Apple Mobile Device Service" & @net stop "ABBYY.Licensing.FineReader.Professional.12.0"" | C:\Windows\system32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 2 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 392 | taskkill /IM edr_agent.exe /F | C:\Windows\system32\taskkill.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Terminates Processes Exit code: 128 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 436 | C:\Windows\system32\net1 stop OracleDBConsoleilas | C:\Windows\system32\net1.exe | — | net.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Net Command Exit code: 2 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
Total events
14 443
Read events
14 423
Write events
20
Delete events
0
Modification events
| (PID) Process: | (3148) a7018ff4aaaaebda06615da54ab7d3dcfe06ffda501254eb9654aa27152629bb.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\RASAPI32 |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (3148) a7018ff4aaaaebda06615da54ab7d3dcfe06ffda501254eb9654aa27152629bb.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\RASAPI32 |
| Operation: | write | Name: | EnableConsoleTracing |
Value: 0 | |||
| (PID) Process: | (3148) a7018ff4aaaaebda06615da54ab7d3dcfe06ffda501254eb9654aa27152629bb.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\RASAPI32 |
| Operation: | write | Name: | FileTracingMask |
Value: | |||
| (PID) Process: | (3148) a7018ff4aaaaebda06615da54ab7d3dcfe06ffda501254eb9654aa27152629bb.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\RASAPI32 |
| Operation: | write | Name: | ConsoleTracingMask |
Value: | |||
| (PID) Process: | (3148) a7018ff4aaaaebda06615da54ab7d3dcfe06ffda501254eb9654aa27152629bb.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\RASAPI32 |
| Operation: | write | Name: | MaxFileSize |
Value: 1048576 | |||
| (PID) Process: | (3148) a7018ff4aaaaebda06615da54ab7d3dcfe06ffda501254eb9654aa27152629bb.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\RASAPI32 |
| Operation: | write | Name: | FileDirectory |
Value: %windir%\tracing | |||
| (PID) Process: | (3148) a7018ff4aaaaebda06615da54ab7d3dcfe06ffda501254eb9654aa27152629bb.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\RASMANCS |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (3148) a7018ff4aaaaebda06615da54ab7d3dcfe06ffda501254eb9654aa27152629bb.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\RASMANCS |
| Operation: | write | Name: | EnableConsoleTracing |
Value: 0 | |||
| (PID) Process: | (3148) a7018ff4aaaaebda06615da54ab7d3dcfe06ffda501254eb9654aa27152629bb.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\RASMANCS |
| Operation: | write | Name: | FileTracingMask |
Value: | |||
| (PID) Process: | (3148) a7018ff4aaaaebda06615da54ab7d3dcfe06ffda501254eb9654aa27152629bb.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\RASMANCS |
| Operation: | write | Name: | ConsoleTracingMask |
Value: | |||
Executable files
0
Suspicious files
136
Text files
59
Unknown types
6
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3928 | a7018ff4aaaaebda06615da54ab7d3dcfe06ffda501254eb9654aa27152629bb.exe | C:\Users\admin\.oracle_jre_usage\90737d32e3abaa4.timestamp.mallox | binary | |
MD5:— | SHA256:— | |||
| 3928 | a7018ff4aaaaebda06615da54ab7d3dcfe06ffda501254eb9654aa27152629bb.exe | C:\Users\admin\Contacts\admin.contact | binary | |
MD5:— | SHA256:— | |||
| 3928 | a7018ff4aaaaebda06615da54ab7d3dcfe06ffda501254eb9654aa27152629bb.exe | C:\Users\admin\Desktop\effortowner.png | binary | |
MD5:— | SHA256:— | |||
| 3928 | a7018ff4aaaaebda06615da54ab7d3dcfe06ffda501254eb9654aa27152629bb.exe | C:\Users\admin\Desktop\resourcesdev.rtf | binary | |
MD5:— | SHA256:— | |||
| 3928 | a7018ff4aaaaebda06615da54ab7d3dcfe06ffda501254eb9654aa27152629bb.exe | C:\Users\admin\Desktop\RECOVERY INFORMATION.txt | text | |
MD5:— | SHA256:— | |||
| 3928 | a7018ff4aaaaebda06615da54ab7d3dcfe06ffda501254eb9654aa27152629bb.exe | C:\Users\admin\Desktop\namedecember.jpg | binary | |
MD5:— | SHA256:— | |||
| 3928 | a7018ff4aaaaebda06615da54ab7d3dcfe06ffda501254eb9654aa27152629bb.exe | C:\Users\admin\Desktop\materialpass.rtf | binary | |
MD5:— | SHA256:— | |||
| 3928 | a7018ff4aaaaebda06615da54ab7d3dcfe06ffda501254eb9654aa27152629bb.exe | C:\Users\admin\Desktop\effortowner.png.mallox | binary | |
MD5:— | SHA256:— | |||
| 3928 | a7018ff4aaaaebda06615da54ab7d3dcfe06ffda501254eb9654aa27152629bb.exe | C:\Users\admin\Contacts\admin.contact.mallox | binary | |
MD5:— | SHA256:— | |||
| 3928 | a7018ff4aaaaebda06615da54ab7d3dcfe06ffda501254eb9654aa27152629bb.exe | C:\Users\admin\Desktop\starsbenefits.png | binary | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
1
TCP/UDP connections
16
DNS requests
0
Threats
2
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3148 | a7018ff4aaaaebda06615da54ab7d3dcfe06ffda501254eb9654aa27152629bb.exe | GET | 200 | 91.243.44.32:80 | http://91.243.44.32/F.bat | RU | text | 40.3 Kb | malicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3148 | a7018ff4aaaaebda06615da54ab7d3dcfe06ffda501254eb9654aa27152629bb.exe | 91.243.44.32:80 | — | Foxcloud Llp | RU | malicious |
— | — | 192.168.100.2:139 | — | — | — | whitelisted |
— | — | 192.168.100.2:445 | — | — | — | whitelisted |
— | — | 192.168.100.2:135 | — | — | — | whitelisted |
DNS requests
Threats
2 ETPRO signatures available at the full report