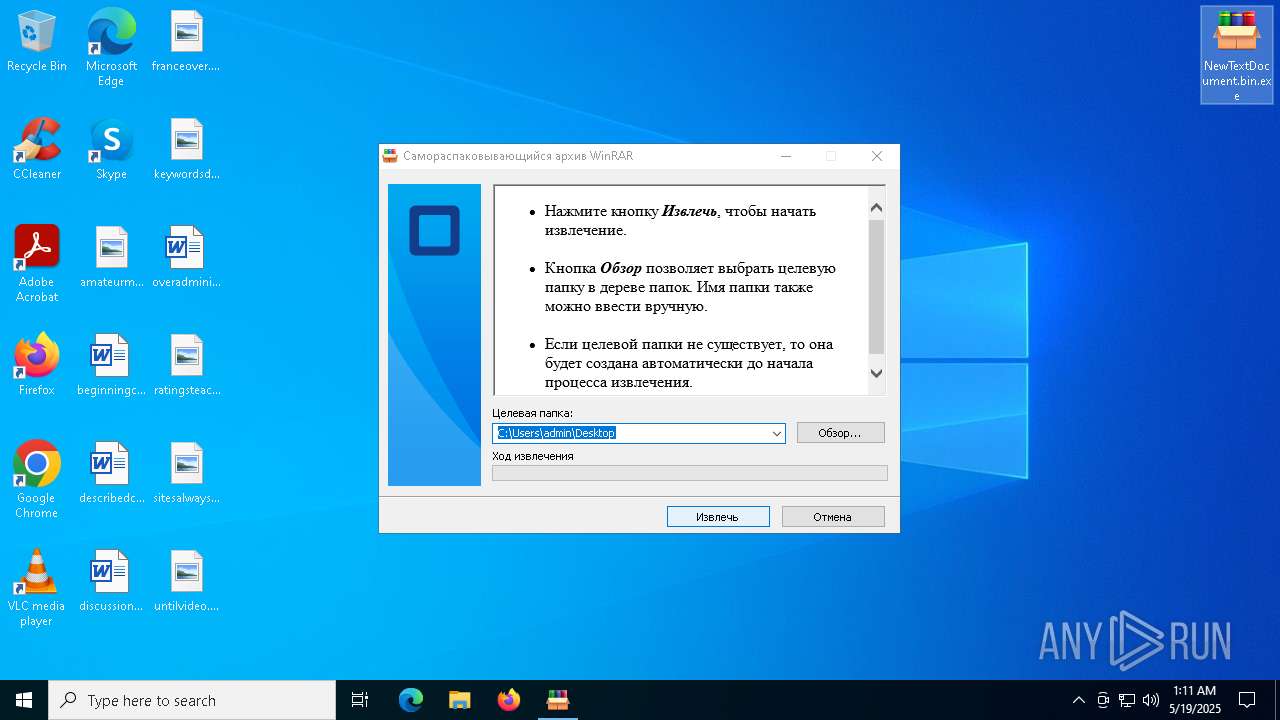
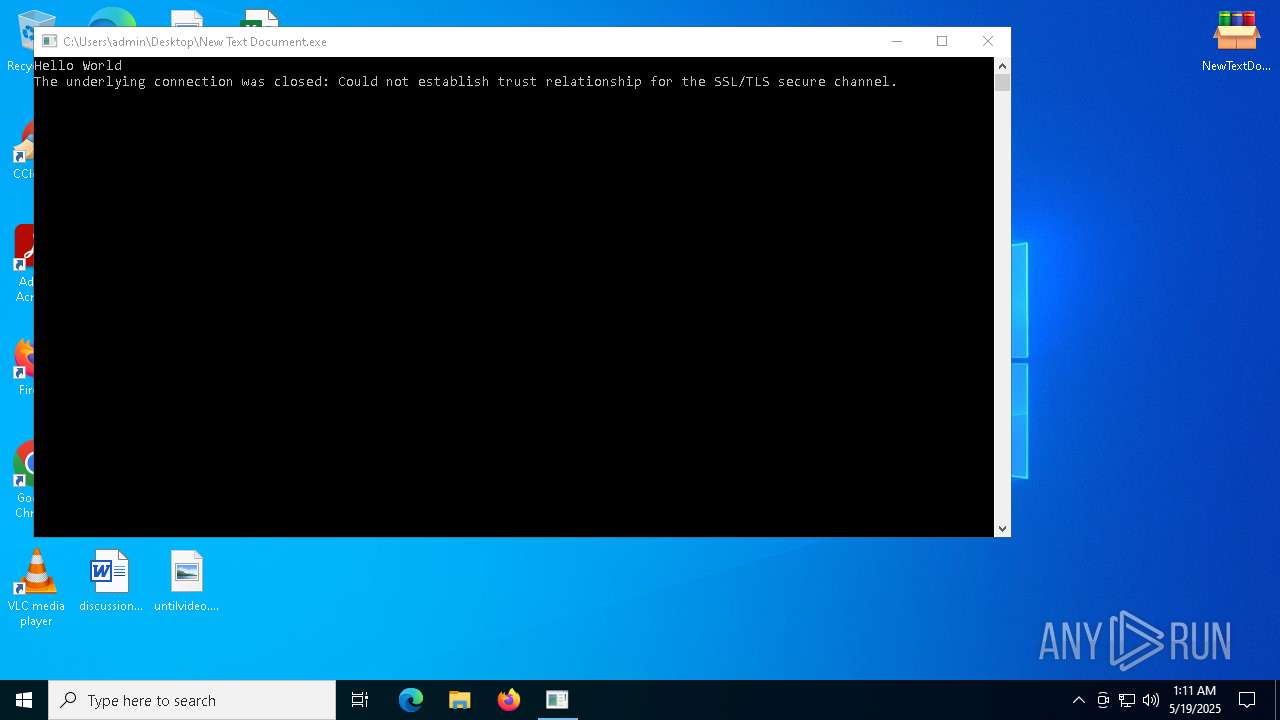
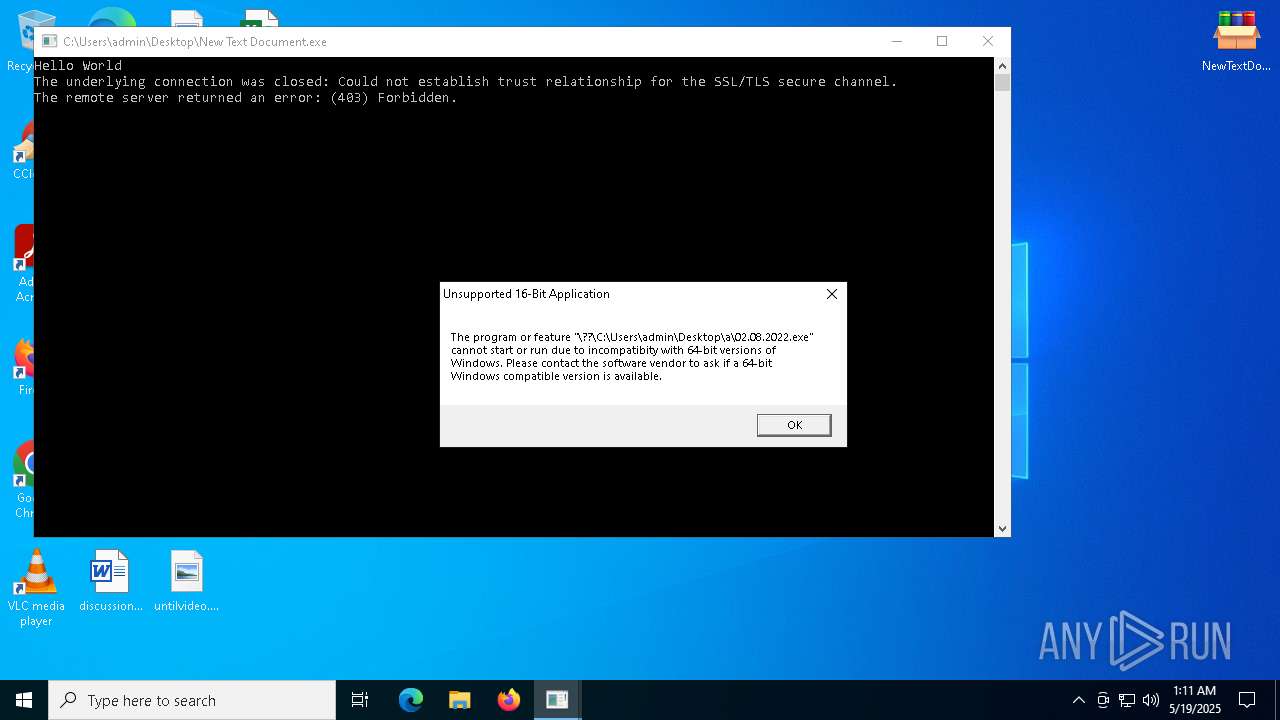
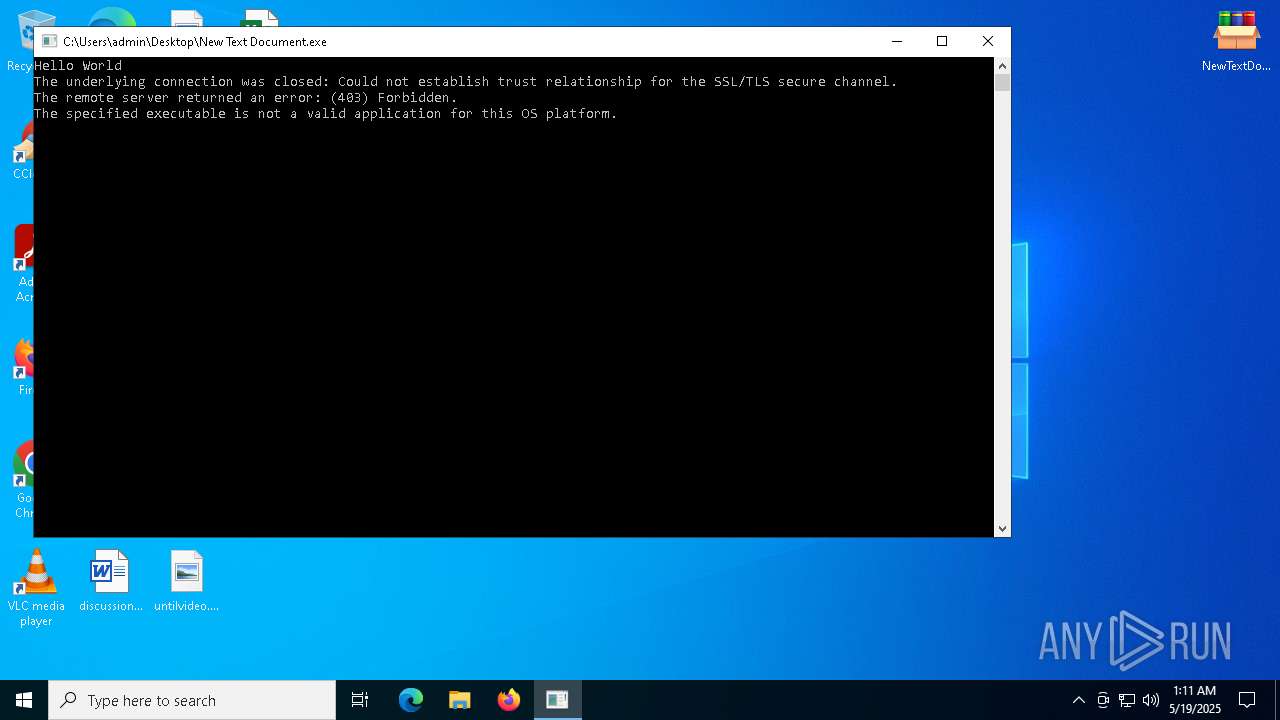
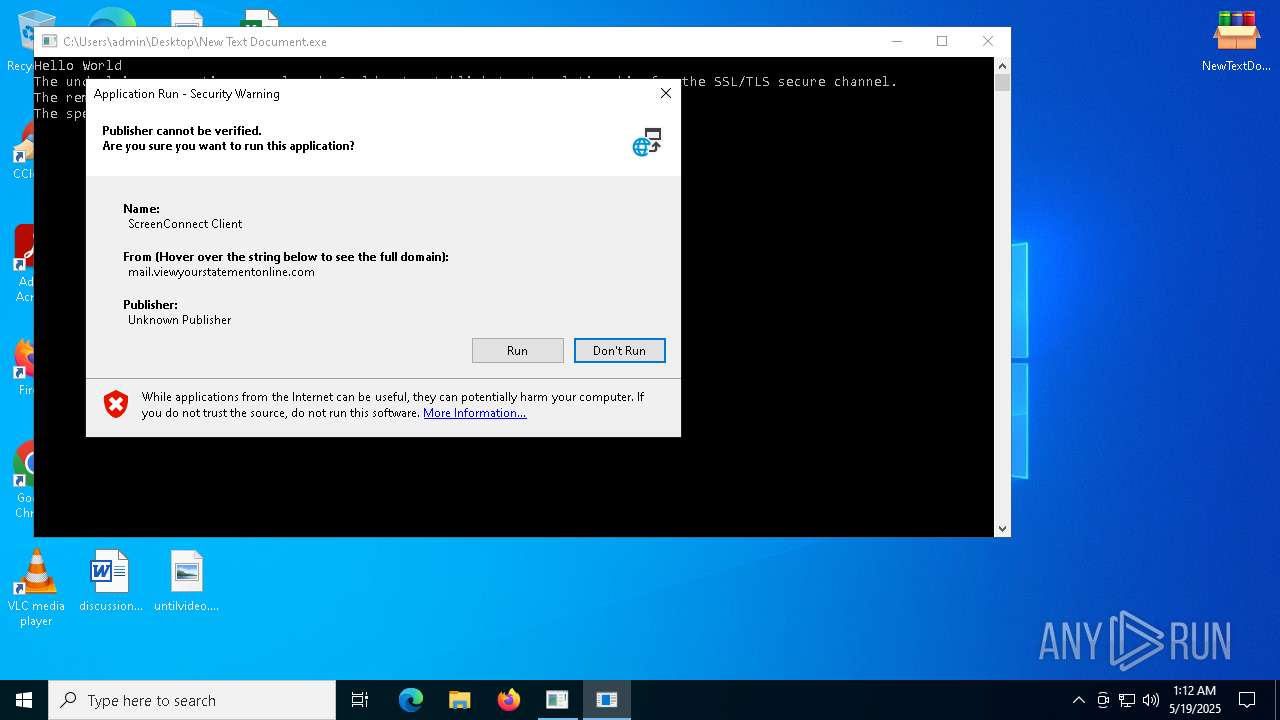
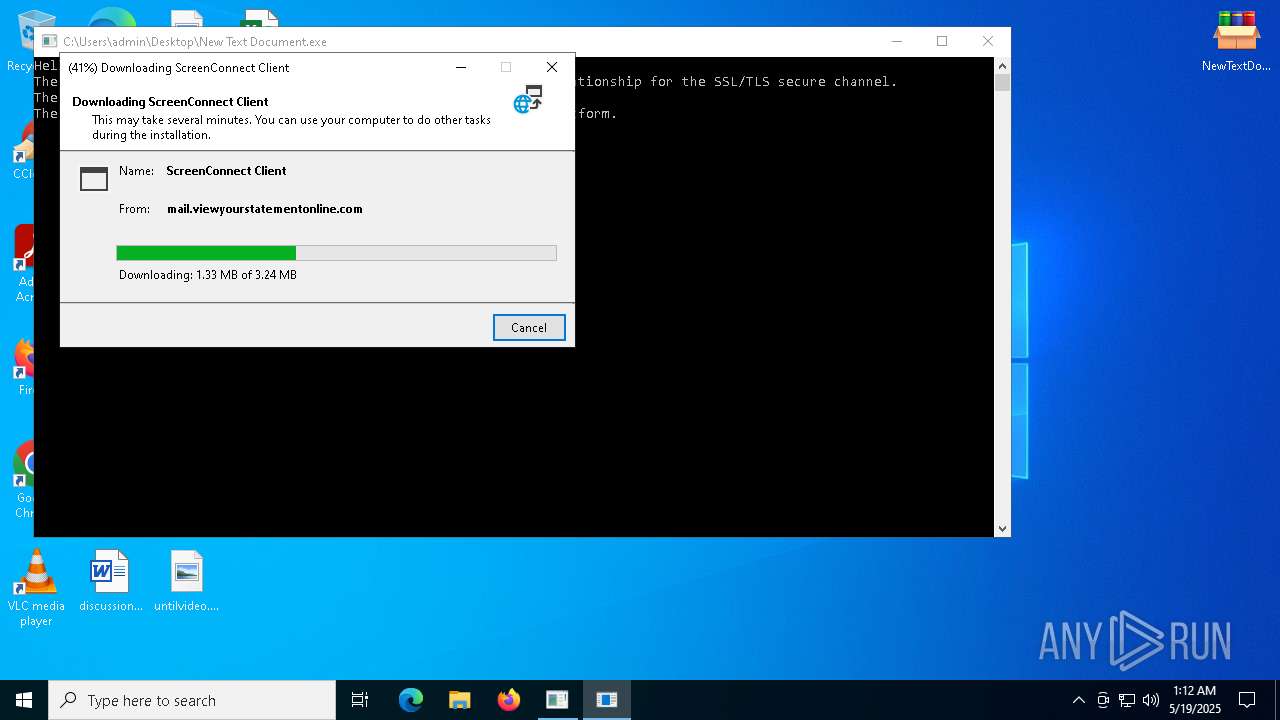
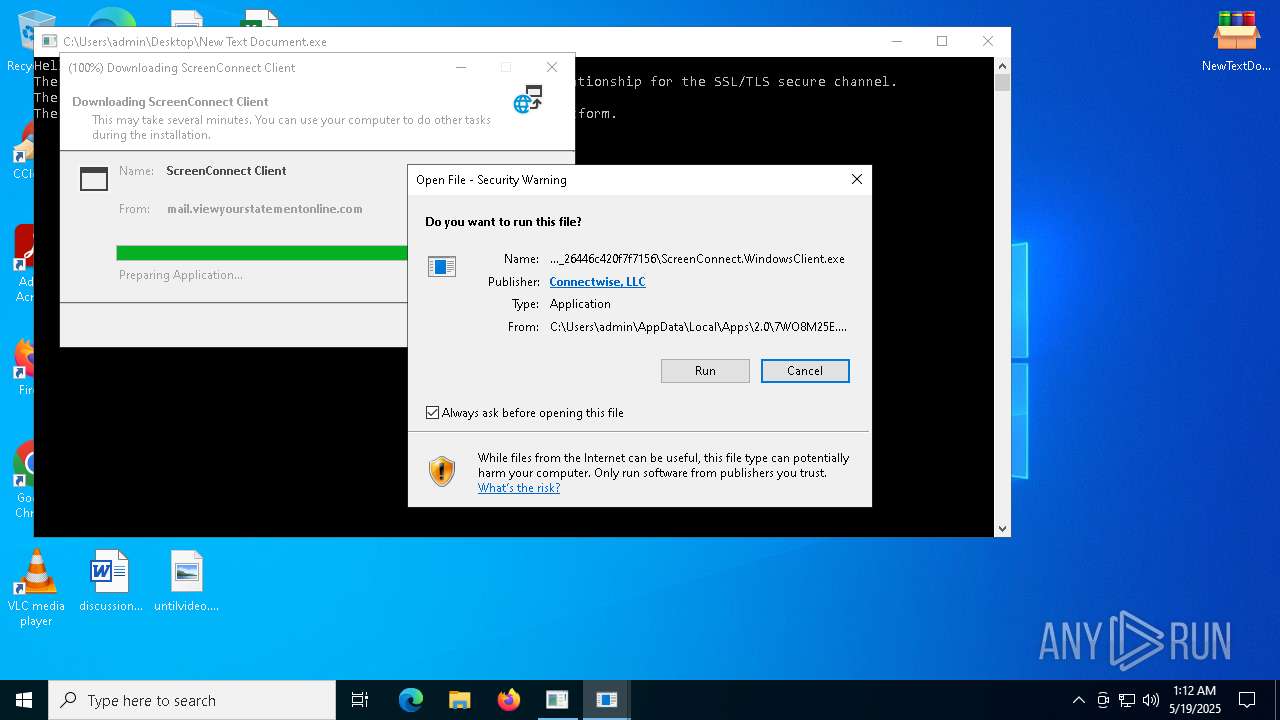
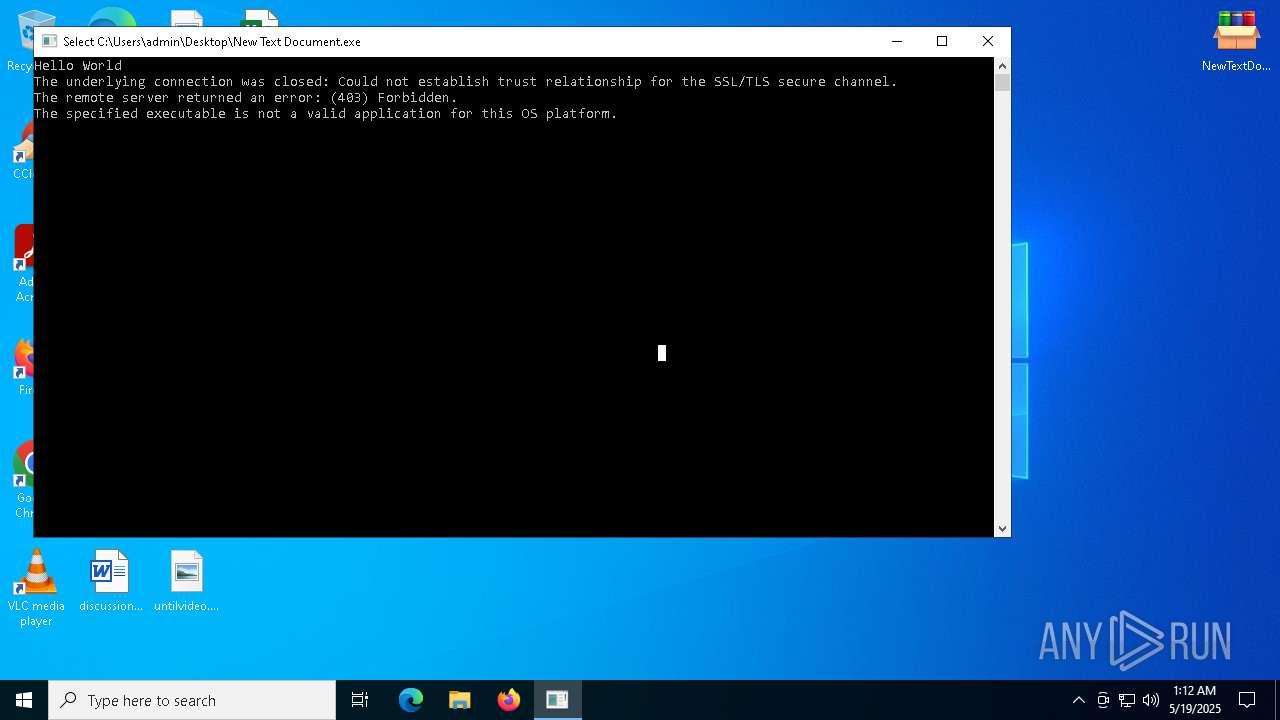
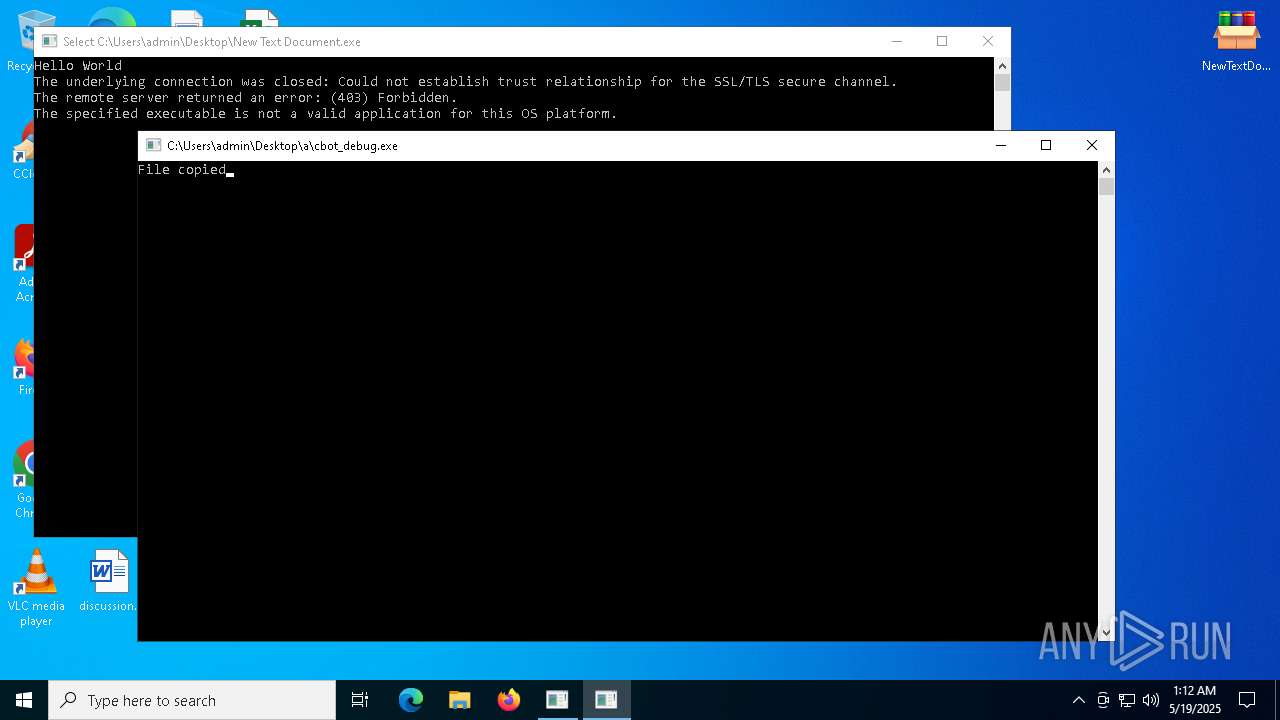
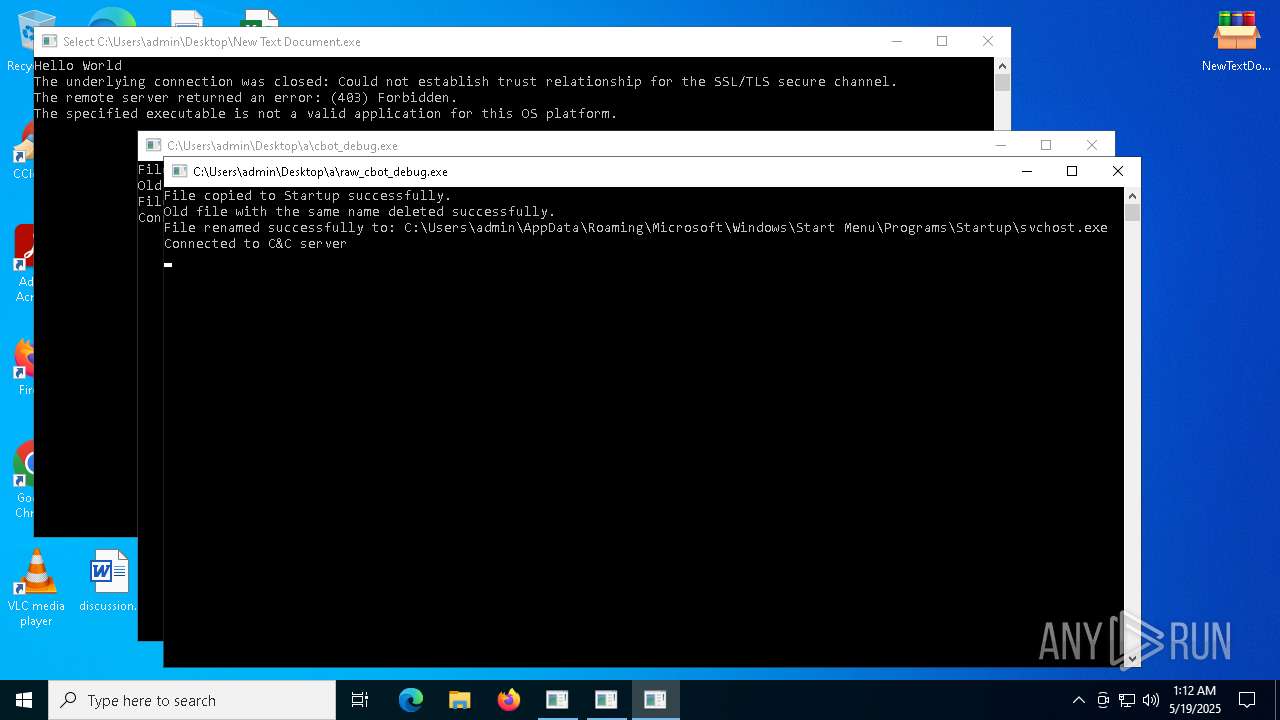
| File name: | NewTextDocument.bin.exe |
| Full analysis: | https://app.any.run/tasks/c2dfbc7f-f129-49ed-97eb-6c99b8788310 |
| Verdict: | Malicious activity |
| Threats: | AsyncRAT is a RAT that can monitor and remotely control infected systems. This malware was introduced on Github as a legitimate open-source remote administration software, but hackers use it for its many powerful malicious functions. |
| Analysis date: | May 19, 2025, 01:11:09 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, 6 sections |
| MD5: | 0B0D247AA1F24C2F5867B3BF29F69450 |
| SHA1: | 48DE9F34226FD7F637E2379365BE035AF5C0DF1A |
| SHA256: | A6E7292E734C3A15CFA654BBA8DEA72A2F55F1C24CF6BBDC2FD7E63887E9315A |
| SSDEEP: | 12288:dcgCzNHJj96xfKJStJkRm3bYXob0AnmFMcaGQxkZVVVVVVVVVAtVVVUvqGV:UQKgLIQmFuGQxklvqO |
MALICIOUS
GENERIC has been found (auto)
- NewTextDocument.bin.exe (PID: 7496)
Known privilege escalation attack
- dllhost.exe (PID: 5552)
Adds process to the Windows Defender exclusion list
- WinTemp-v4.exe (PID: 7172)
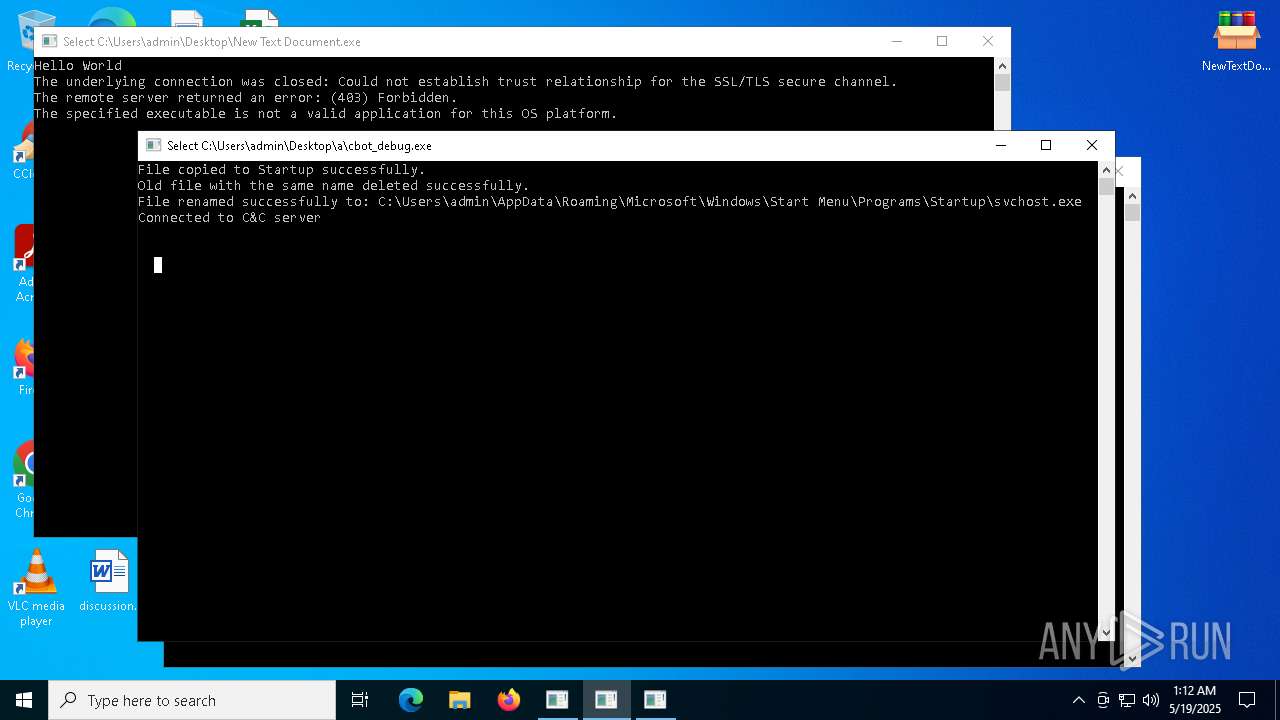
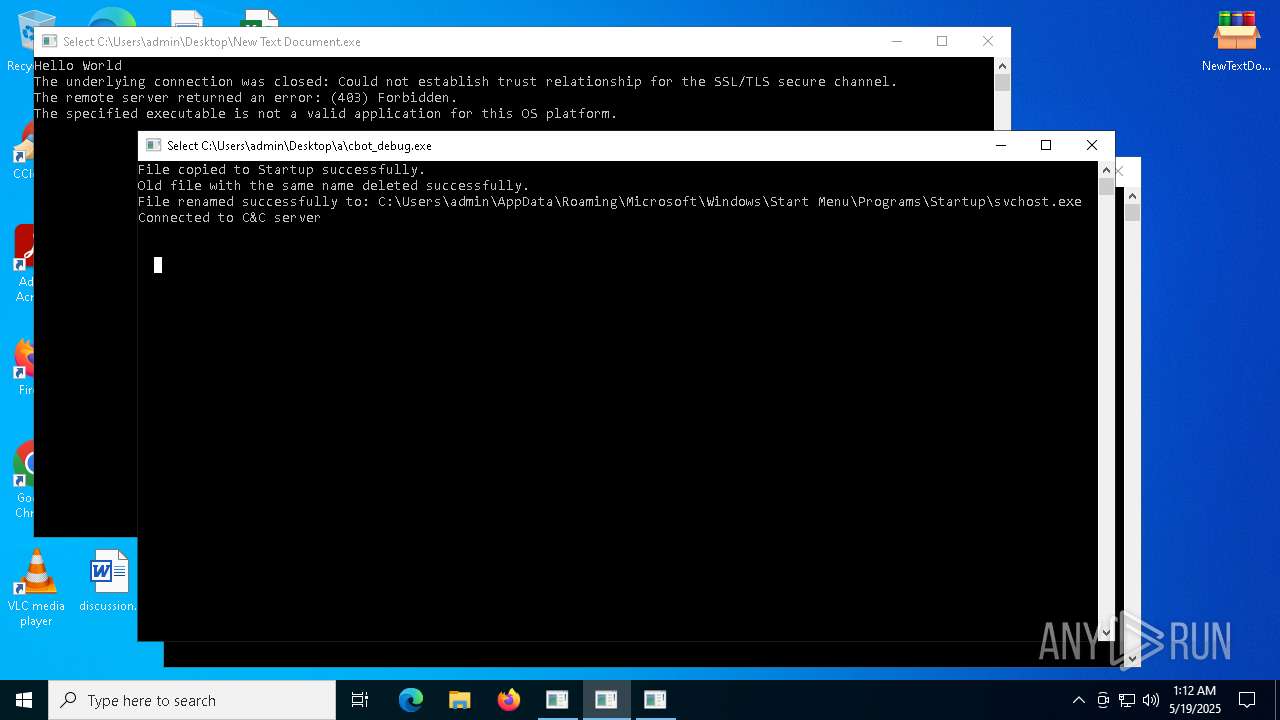
Create files in the Startup directory
- ckjg.exe (PID: 5064)
- cbot_debug.exe (PID: 6244)
- cbot.exe (PID: 1328)
- raw_cbot.exe (PID: 2984)
- raw_cbot_debug.exe (PID: 5400)
Changes Windows Defender settings
- WinTemp-v4.exe (PID: 7172)
HAUSBOMBER has been detected (YARA)
- New Text Document.exe (PID: 7488)
GHOSTSOCKS has been found (auto)
- New Text Document.exe (PID: 7488)
SCREENCONNECT has been detected (SURICATA)
- ScreenConnect.WindowsClient.exe (PID: 7992)
Changes the autorun value in the registry
- Quodlibet.exe (PID: 7956)
- WinTemp-v4.exe (PID: 7172)
ASYNCRAT has been detected (SURICATA)
- ckjg.exe (PID: 5064)
Uses Task Scheduler to autorun other applications
- WinTemp-v4.exe (PID: 7172)
Starts REAGENTC.EXE to disable the Windows Recovery Environment
- ReAgentc.exe (PID: 4164)
Connects to the CnC server
- cmd.exe (PID: 7432)
- svchost.exe (PID: 2196)
MINER has been detected (SURICATA)
- cmd.exe (PID: 7432)
Executing a file with an untrusted certificate
- Supawn.exe (PID: 5360)
- Nationalbankdirektrernes.exe (PID: 7936)
- CompoundsTrim.exe (PID: 4012)
- 123123213.exe (PID: 8180)
- inferno.exe (PID: 3176)
LUMMA has been detected (SURICATA)
- svchost.exe (PID: 2196)
- MSBuild.exe (PID: 8028)
SUSPICIOUS
Reads Microsoft Outlook installation path
- NewTextDocument.bin.exe (PID: 7496)
- NewTextDocument.bin.exe (PID: 7388)
Reads Internet Explorer settings
- NewTextDocument.bin.exe (PID: 7496)
- NewTextDocument.bin.exe (PID: 7388)
- dfsvc.exe (PID: 6872)
There is functionality for taking screenshot (YARA)
- NewTextDocument.bin.exe (PID: 7496)
Reads security settings of Internet Explorer
- NewTextDocument.bin.exe (PID: 7496)
- NewTextDocument.bin.exe (PID: 7388)
- New Text Document.exe (PID: 7488)
- dfsvc.exe (PID: 6872)
Executable content was dropped or overwritten
- NewTextDocument.bin.exe (PID: 7388)
- New Text Document.exe (PID: 7488)
- dfsvc.exe (PID: 6872)
- oxDU0MW.exe (PID: 1180)
- cbot.exe (PID: 1328)
- cbot_debug.exe (PID: 6244)
- raw_cbot.exe (PID: 2984)
- Quodlibet.exe (PID: 7956)
- WinTemp-v4.exe (PID: 7172)
- New Text Document.exe (PID: 7764)
- New Text Document.exe (PID: 6192)
- New Text Document.exe (PID: 7980)
- Slasher.exe (PID: 7996)
- raw_cbot_debug.exe (PID: 5400)
- Supawn.exe (PID: 5360)
- New Text Document.exe (PID: 6048)
- Nationalbankdirektrernes.exe (PID: 7936)
- New Text Document.exe (PID: 7144)
- New Text Document.exe (PID: 7868)
Reads the date of Windows installation
- New Text Document.exe (PID: 7488)
- dfsvc.exe (PID: 6872)
Connects to unusual port
- New Text Document.exe (PID: 7488)
- cbot.exe (PID: 1328)
- cbot_debug.exe (PID: 6244)
- raw_cbot_debug.exe (PID: 5400)
- raw_cbot.exe (PID: 2984)
- ckjg.exe (PID: 5064)
- ScreenConnect.WindowsClient.exe (PID: 7992)
- Quodlibet.exe (PID: 7956)
- WinTemp-v4.exe (PID: 7172)
- cmd.exe (PID: 7432)
Adds/modifies Windows certificates
- work_approval_pdf3.Client.exe (PID: 5116)
- dfsvc.exe (PID: 6872)
Process requests binary or script from the Internet
- New Text Document.exe (PID: 7488)
- New Text Document.exe (PID: 7144)
- New Text Document.exe (PID: 7868)
- New Text Document.exe (PID: 7980)
- New Text Document.exe (PID: 6192)
- New Text Document.exe (PID: 3156)
Potential Corporate Privacy Violation
- New Text Document.exe (PID: 7488)
- cmd.exe (PID: 7432)
- New Text Document.exe (PID: 6192)
- New Text Document.exe (PID: 7868)
- New Text Document.exe (PID: 3156)
- New Text Document.exe (PID: 7980)
- ScreenConnect.WindowsClient.exe (PID: 7992)
- New Text Document.exe (PID: 7144)
Connects to the server without a host name
- New Text Document.exe (PID: 7488)
- New Text Document.exe (PID: 6192)
- New Text Document.exe (PID: 7868)
- New Text Document.exe (PID: 7144)
- New Text Document.exe (PID: 7980)
- New Text Document.exe (PID: 3156)
Script adds exclusion process to Windows Defender
- WinTemp-v4.exe (PID: 7172)
Executes application which crashes
- TiWorker.exe (PID: 1020)
- kjoxca.exe (PID: 7516)
- alphamm.exe (PID: 5072)
The process creates files with name similar to system file names
- dfsvc.exe (PID: 6872)
Starts POWERSHELL.EXE for commands execution
- WinTemp-v4.exe (PID: 7172)
Process drops legitimate windows executable
- New Text Document.exe (PID: 7488)
- cbot.exe (PID: 1328)
- cbot_debug.exe (PID: 6244)
- raw_cbot.exe (PID: 2984)
- raw_cbot_debug.exe (PID: 5400)
Starts a Microsoft application from unusual location
- cbot_debug.exe (PID: 6244)
- cbot.exe (PID: 1328)
- raw_cbot_debug.exe (PID: 5400)
- raw_cbot.exe (PID: 2984)
- inferno.exe (PID: 3176)
- 123123213.exe (PID: 8180)
Script adds exclusion path to Windows Defender
- WinTemp-v4.exe (PID: 7172)
Contacting a server suspected of hosting an CnC
- ckjg.exe (PID: 5064)
- svchost.exe (PID: 2196)
- MSBuild.exe (PID: 8028)
Uses WMIC.EXE to obtain computer system information
- ckjg.exe (PID: 5064)
Accesses domain name via WMI (SCRIPT)
- WMIC.exe (PID: 6828)
Starts CMD.EXE for commands execution
- WinTemp-v4.exe (PID: 7172)
- CompoundsTrim.exe (PID: 4012)
Checks for external IP
- WinTemp-v4.exe (PID: 7172)
- svchost.exe (PID: 2196)
Takes ownership (TAKEOWN.EXE)
- cmd.exe (PID: 4228)
Uses ICACLS.EXE to modify access control lists
- cmd.exe (PID: 7464)
- cmd.exe (PID: 7932)
Hides command output
- cmd.exe (PID: 5324)
Uses powercfg.exe to modify the power settings
- WinTemp-v4.exe (PID: 7172)
Malware-specific behavior (creating "System.dll" in Temp)
- Supawn.exe (PID: 5360)
- Nationalbankdirektrernes.exe (PID: 7936)
Executing commands from a ".bat" file
- CompoundsTrim.exe (PID: 4012)
INFO
Checks supported languages
- NewTextDocument.bin.exe (PID: 7496)
- NewTextDocument.bin.exe (PID: 7388)
- New Text Document.exe (PID: 7488)
- work_approval_pdf3.Client.exe (PID: 5116)
- dfsvc.exe (PID: 6872)
- ckjg.exe (PID: 5064)
- TiWorker.exe (PID: 1020)
- WinTemp-v4.exe (PID: 7172)
- Quodlibet.exe (PID: 7956)
- oxDU0MW.exe (PID: 1180)
- ScreenConnect.WindowsClient.exe (PID: 7992)
- widsmob_denoise_win.exe (PID: 7780)
- cbot.exe (PID: 1328)
- cbot_debug.exe (PID: 6244)
- raw_cbot.exe (PID: 2984)
- raw_cbot_debug.exe (PID: 5400)
Manual execution by a user
- NewTextDocument.bin.exe (PID: 7388)
- New Text Document.exe (PID: 7488)
- NewTextDocument.bin.exe (PID: 2320)
- New Text Document.exe (PID: 7868)
- New Text Document.exe (PID: 3156)
- NewTextDocument.bin.exe (PID: 7740)
- New Text Document.exe (PID: 6192)
- New Text Document.exe (PID: 7764)
- New Text Document.exe (PID: 7980)
- New Text Document.exe (PID: 5720)
- New Text Document.exe (PID: 7144)
- New Text Document.exe (PID: 6048)
- New Text Document.exe (PID: 7292)
Checks proxy server information
- NewTextDocument.bin.exe (PID: 7496)
- NewTextDocument.bin.exe (PID: 7388)
- New Text Document.exe (PID: 7488)
- dfsvc.exe (PID: 6872)
- ScreenConnect.WindowsClient.exe (PID: 7992)
Reads the computer name
- NewTextDocument.bin.exe (PID: 7496)
- New Text Document.exe (PID: 7488)
- NewTextDocument.bin.exe (PID: 7388)
- work_approval_pdf3.Client.exe (PID: 5116)
- dfsvc.exe (PID: 6872)
- ckjg.exe (PID: 5064)
- oxDU0MW.exe (PID: 1180)
- ScreenConnect.WindowsClient.exe (PID: 7992)
Reads the machine GUID from the registry
- New Text Document.exe (PID: 7488)
- work_approval_pdf3.Client.exe (PID: 5116)
- dfsvc.exe (PID: 6872)
- oxDU0MW.exe (PID: 1180)
- ckjg.exe (PID: 5064)
- ScreenConnect.WindowsClient.exe (PID: 7992)
- cbot.exe (PID: 1328)
- cbot_debug.exe (PID: 6244)
- raw_cbot.exe (PID: 2984)
- raw_cbot_debug.exe (PID: 5400)
Reads Environment values
- New Text Document.exe (PID: 7488)
- dfsvc.exe (PID: 6872)
- ckjg.exe (PID: 5064)
- ScreenConnect.WindowsClient.exe (PID: 7992)
Disables trace logs
- New Text Document.exe (PID: 7488)
- dfsvc.exe (PID: 6872)
- ScreenConnect.WindowsClient.exe (PID: 7992)
Reads the software policy settings
- New Text Document.exe (PID: 7488)
- dfsvc.exe (PID: 6872)
- ckjg.exe (PID: 5064)
- slui.exe (PID: 7632)
Process checks computer location settings
- New Text Document.exe (PID: 7488)
- dfsvc.exe (PID: 6872)
Creates files or folders in the user directory
- dfsvc.exe (PID: 6872)
- ckjg.exe (PID: 5064)
- WerFault.exe (PID: 7936)
- ScreenConnect.WindowsClient.exe (PID: 7992)
- cbot.exe (PID: 1328)
- cbot_debug.exe (PID: 6244)
- raw_cbot.exe (PID: 2984)
- raw_cbot_debug.exe (PID: 5400)
- Quodlibet.exe (PID: 7956)
- WinTemp-v4.exe (PID: 7172)
Process checks whether UAC notifications are on
- dfsvc.exe (PID: 6872)
Create files in a temporary directory
- dfsvc.exe (PID: 6872)
- TiWorker.exe (PID: 1020)
- oxDU0MW.exe (PID: 1180)
- Quodlibet.exe (PID: 7956)
The sample compiled with english language support
- New Text Document.exe (PID: 7488)
- cbot.exe (PID: 1328)
- cbot_debug.exe (PID: 6244)
- raw_cbot.exe (PID: 2984)
- Quodlibet.exe (PID: 7956)
- New Text Document.exe (PID: 7144)
- New Text Document.exe (PID: 7868)
- New Text Document.exe (PID: 3156)
- New Text Document.exe (PID: 7980)
- raw_cbot_debug.exe (PID: 5400)
Reads mouse settings
- TiWorker.exe (PID: 1020)
Checks transactions between databases Windows and Oracle
- oxDU0MW.exe (PID: 1180)
Reads security settings of Internet Explorer
- dllhost.exe (PID: 5552)
- WMIC.exe (PID: 6828)
Checks if a key exists in the options dictionary (POWERSHELL)
- powershell.exe (PID: 7212)
- powershell.exe (PID: 1132)
- powershell.exe (PID: 7516)
Script raised an exception (POWERSHELL)
- powershell.exe (PID: 7212)
- powershell.exe (PID: 1132)
- powershell.exe (PID: 7516)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable (generic) (52.9) |
|---|---|---|
| .exe | | | Generic Win/DOS Executable (23.5) |
| .exe | | | DOS Executable Generic (23.5) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2023:10:03 07:51:19+00:00 |
| ImageFileCharacteristics: | Executable, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 14.33 |
| CodeSize: | 214528 |
| InitializedDataSize: | 119296 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x21d50 |
| OSVersion: | 5.1 |
| ImageVersion: | - |
| SubsystemVersion: | 5.1 |
| Subsystem: | Windows GUI |
Total processes
250
Monitored processes
112
Malicious processes
25
Suspicious processes
5
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 728 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | New Text Document.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1020 | "C:\Users\admin\Desktop\a\TiWorker.exe" | C:\Users\admin\Desktop\a\TiWorker.exe | New Text Document.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221225477 Modules
| |||||||||||||||
| 1096 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | New Text Document.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1132 | powershell -Command "Add-MpPreference -ExclusionProcess 'cmd.exe'; Add-MpPreference -ExclusionPath 'C:\'" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | WinTemp-v4.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1180 | "C:\Users\admin\Desktop\a\oxDU0MW.exe" | C:\Users\admin\Desktop\a\oxDU0MW.exe | New Text Document.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 1180 | C:\WINDOWS\SysWOW64\WerFault.exe -u -p 5072 -s 640 | C:\Windows\SysWOW64\WerFault.exe | — | alphamm.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Problem Reporting Exit code: 0 Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1196 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | New Text Document.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1328 | "C:\Users\admin\Desktop\a\cbot.exe" | C:\Users\admin\Desktop\a\cbot.exe | New Text Document.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Host Process for Windows Services Version: 1.2.0.0 Modules
| |||||||||||||||
| 1560 | "C:\Users\admin\Desktop\a\RedFireEXTERNAL.exe" | C:\Users\admin\Desktop\a\RedFireEXTERNAL.exe | — | New Text Document.exe | |||||||||||
User: admin Company: Esx Cheats Integrity Level: MEDIUM Description: Esx Cheats Exit code: 3221226540 Version: 31.31.31.31 Modules
| |||||||||||||||
| 1672 | "C:\Users\admin\Desktop\a\alphamm.exe" | C:\Windows\SysWOW64\svchost.exe | — | alphamm.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) | |||||||||||||||
Total events
72 325
Read events
71 311
Write events
924
Delete events
90
Modification events
| (PID) Process: | (7496) NewTextDocument.bin.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (7496) NewTextDocument.bin.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (7496) NewTextDocument.bin.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (7496) NewTextDocument.bin.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Internet Explorer\LowRegistry |
| Operation: | delete value | Name: | AddToFavoritesInitialSelection |
Value: | |||
| (PID) Process: | (7496) NewTextDocument.bin.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Internet Explorer\LowRegistry |
| Operation: | delete value | Name: | AddToFeedsInitialSelection |
Value: | |||
| (PID) Process: | (7388) NewTextDocument.bin.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (7388) NewTextDocument.bin.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (7388) NewTextDocument.bin.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (7388) NewTextDocument.bin.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Internet Explorer\LowRegistry |
| Operation: | delete value | Name: | AddToFavoritesInitialSelection |
Value: | |||
| (PID) Process: | (7388) NewTextDocument.bin.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Internet Explorer\LowRegistry |
| Operation: | delete value | Name: | AddToFeedsInitialSelection |
Value: | |||
Executable files
64
Suspicious files
62
Text files
70
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1020 | TiWorker.exe | C:\Users\admin\AppData\Local\Temp\demonetising | binary | |
MD5:24466CEAA754885D3AE569EF821E7103 | SHA256:B24A39DB91A037063D1EA2D79E3170C7A5290AB14C2221C1C7B34F6682854589 | |||
| 7488 | New Text Document.exe | C:\Users\admin\Desktop\a\ckjg.exe | executable | |
MD5:962D2A0880C5325328930B66BB4E2CF1 | SHA256:08037DE4A729634FA818DDF03DDD27C28C89F42158AF5EDE71CF0AE2D78FA198 | |||
| 1180 | oxDU0MW.exe | C:\Users\admin\AppData\Local\Temp\WinTemp-v4.exe | executable | |
MD5:681A95FEBF7ED62BA6B2F121CB59814F | SHA256:236DE5AA0CFF922623BF5863B69587354BC81BAC6384FEA29843C7B3F14D1D98 | |||
| 1020 | TiWorker.exe | C:\Users\admin\AppData\Local\Temp\aut6C15.tmp | binary | |
MD5:24466CEAA754885D3AE569EF821E7103 | SHA256:B24A39DB91A037063D1EA2D79E3170C7A5290AB14C2221C1C7B34F6682854589 | |||
| 7388 | NewTextDocument.bin.exe | C:\Users\admin\Desktop\Пароли Chrome.csv | csv | |
MD5:64F50AFB35DD16EE46F187015CEE84CE | SHA256:C2D389870DE77426A31A8C478E0FDDCBBEA7A3733B453806317914E6F946EA91 | |||
| 7388 | NewTextDocument.bin.exe | C:\Users\admin\Desktop\New Text Document.exe | executable | |
MD5:A239A27C2169AF388D4F5BE6B52F272C | SHA256:98E895F711226A32BFAB152E224279D859799243845C46E550C2D32153C619FC | |||
| 6872 | dfsvc.exe | C:\Users\admin\AppData\Local\Temp\Deployment\8BPJNMX9.BZM\EZPK3CBW.HXW\ScreenConnect.ClientService.exe | executable | |
MD5:752D5CDDA2A1D93D27E38F98A5D23FC2 | SHA256:F048400C23ADD8C75ABE189393D33C873C02C74EEAF43D47B950C8D643763B35 | |||
| 6872 | dfsvc.exe | C:\Users\admin\AppData\Local\Temp\Deployment\8BPJNMX9.BZM\EZPK3CBW.HXW\ScreenConnect.WindowsBackstageShell.exe | executable | |
MD5:AB9A2C07B3B1222F5ADA4CB7C1FD144E | SHA256:1404090DB3128DE503BA4D991A960C7C1BC3B910A62D06ECF7E7081A2FCF11B9 | |||
| 6872 | dfsvc.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\C8E534EE129F27D55460CE17FD628216_1130D9B25898B0DB0D4F04DC5B93F141 | binary | |
MD5:308308A22123BDFE4C862E0FBEAF0DAA | SHA256:3A7A08106979C3A4A0C0D4B886AE4B1120C1923F5685A034DDE95A9A08819DCF | |||
| 7488 | New Text Document.exe | C:\Users\admin\Desktop\a\oxDU0MW.exe | executable | |
MD5:4EDFA1364A6E703A3DE2F73DA22841C3 | SHA256:27E23AB71F60E78FB0705F42134EDC4F0E6B99B9F0C82A8238D59DBCDE2C7D14 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
27
TCP/UDP connections
117
DNS requests
34
Threats
79
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5496 | MoUsoCoreWorker.exe | GET | 200 | 23.216.77.6:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 23.216.77.6:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
6800 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
6800 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
7488 | New Text Document.exe | GET | 200 | 106.75.78.139:33333 | http://106.75.78.139:33333/02.08.2022.exe | unknown | — | — | malicious |
7488 | New Text Document.exe | GET | 200 | 193.46.217.4:80 | http://gettsveriff.com/bgj3/ckjg.exe | unknown | — | — | malicious |
6872 | dfsvc.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTfIs%2BLjDtGwQ09XEB1Yeq%2BtX%2BBgQQU7NfjgtJxXWRM3y5nP%2Be6mK4cD08CEAitQLJg0pxMn17Nqb2Trtk%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | 23.216.77.6:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
— | — | 23.216.77.6:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
5496 | MoUsoCoreWorker.exe | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
— | — | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
3216 | svchost.exe | 172.211.123.248:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
6544 | svchost.exe | 40.126.31.130:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6544 | svchost.exe | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
urlhaus.abuse.ch |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
7488 | New Text Document.exe | Potentially Bad Traffic | ET INFO Executable Download from dotted-quad Host |
7488 | New Text Document.exe | Misc activity | ET INFO Observed ZeroSSL SSL/TLS Certificate |
6872 | dfsvc.exe | Misc activity | ET INFO Observed ZeroSSL SSL/TLS Certificate |
7488 | New Text Document.exe | Potential Corporate Privacy Violation | ET INFO PE EXE or DLL Windows file download HTTP |
7488 | New Text Document.exe | Potentially Bad Traffic | ET INFO Executable Retrieved With Minimal HTTP Headers - Potential Second Stage Download |
7488 | New Text Document.exe | Potentially Bad Traffic | ET INFO Executable Download from dotted-quad Host |
7488 | New Text Document.exe | Potential Corporate Privacy Violation | ET INFO PE EXE or DLL Windows file download HTTP |
7488 | New Text Document.exe | Potentially Bad Traffic | ET INFO Executable Retrieved With Minimal HTTP Headers - Potential Second Stage Download |
7488 | New Text Document.exe | Potentially Bad Traffic | ET HUNTING SUSPICIOUS Dotted Quad Host MZ Response |
7488 | New Text Document.exe | Potentially Bad Traffic | ET INFO Executable Download from dotted-quad Host |