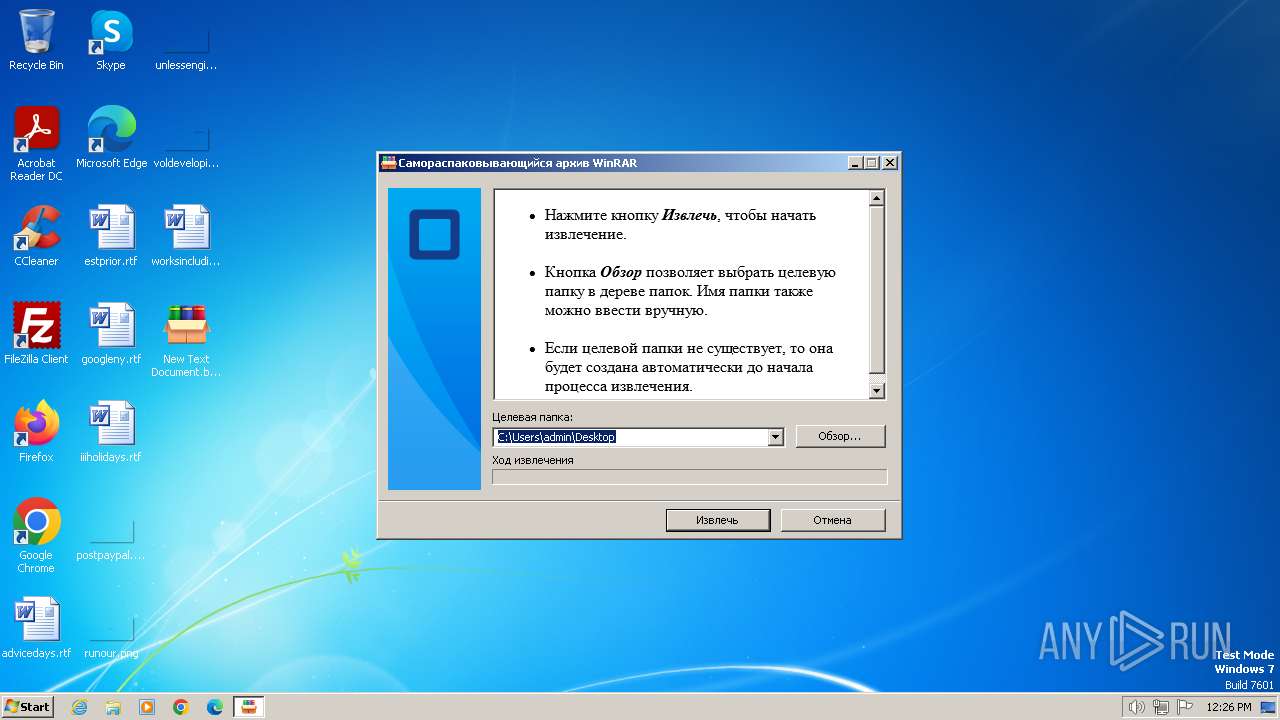
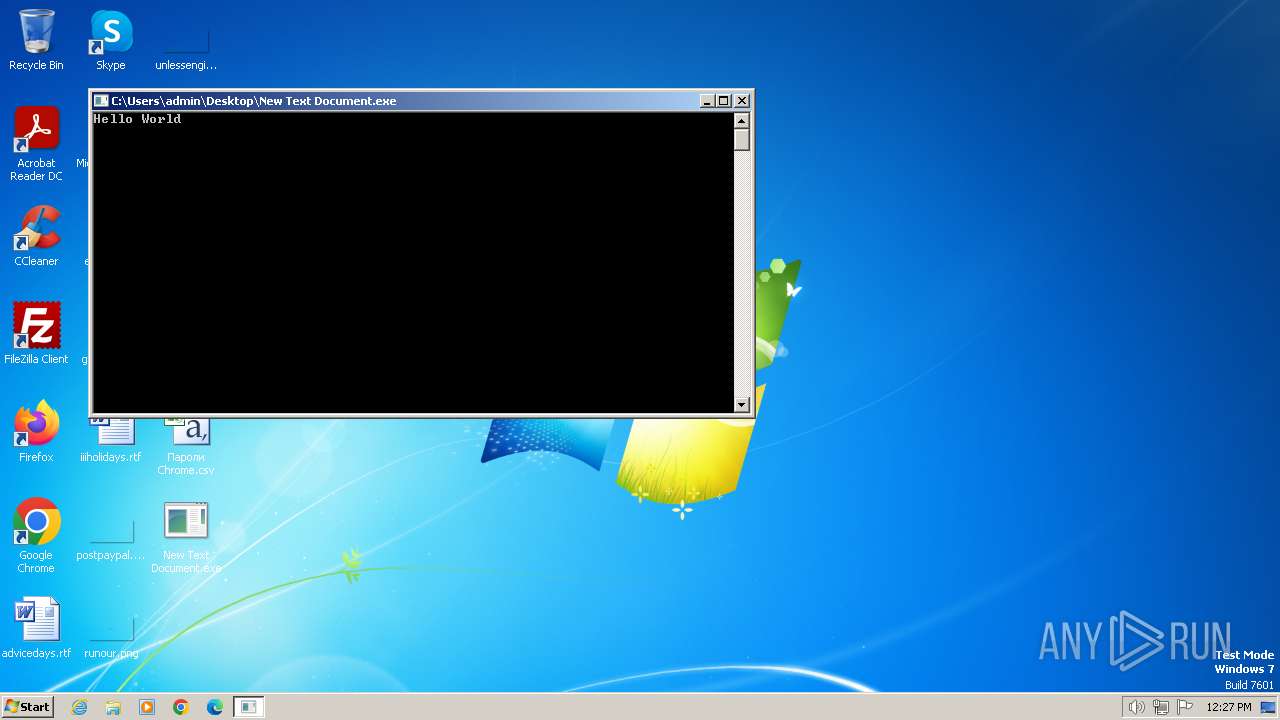
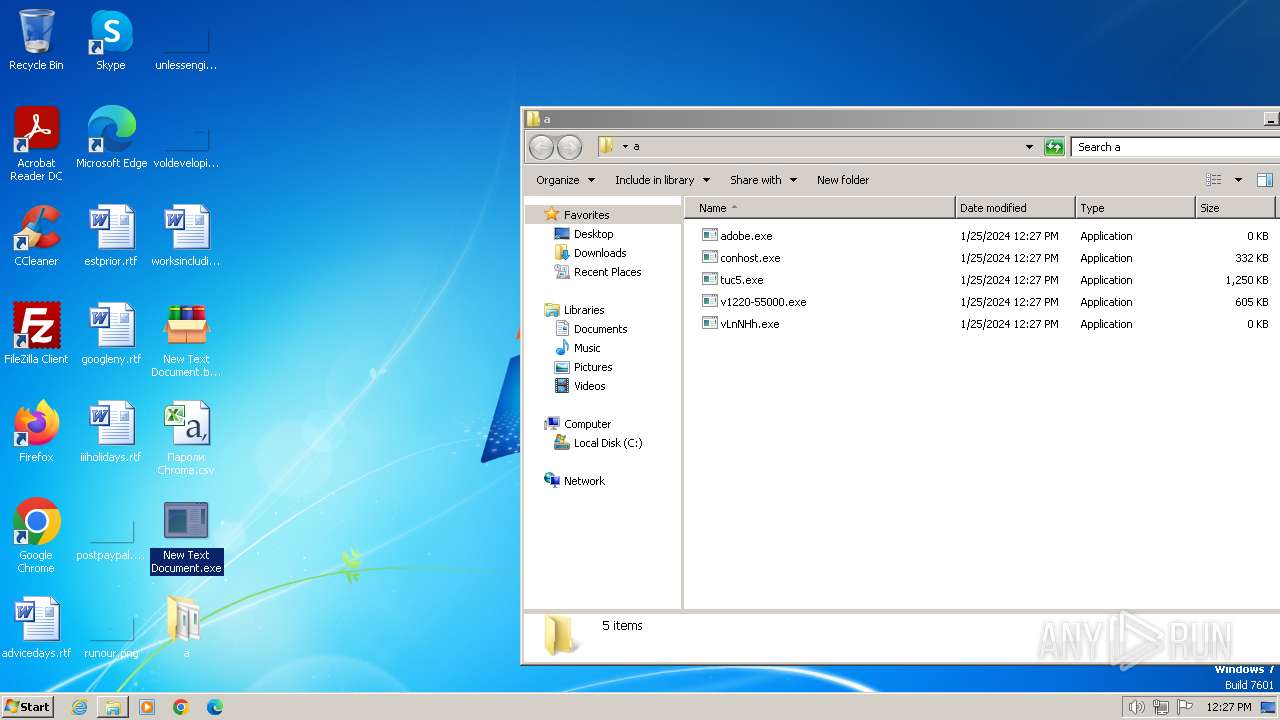
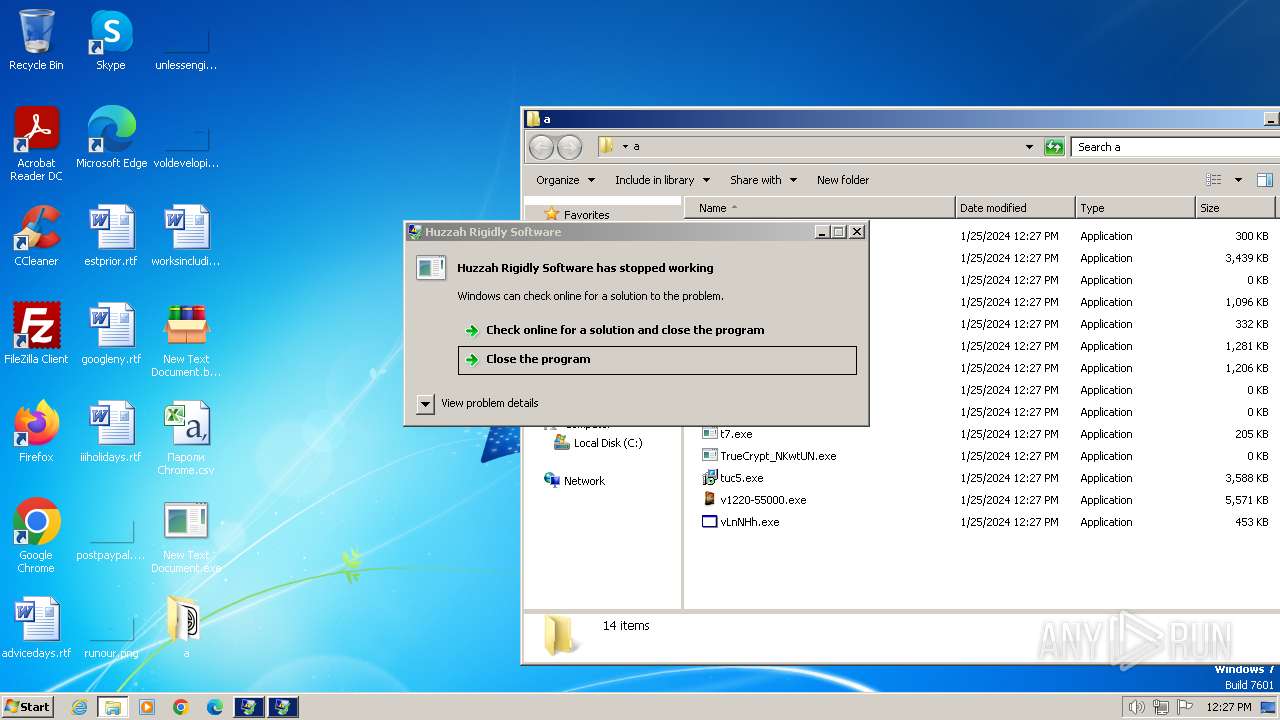
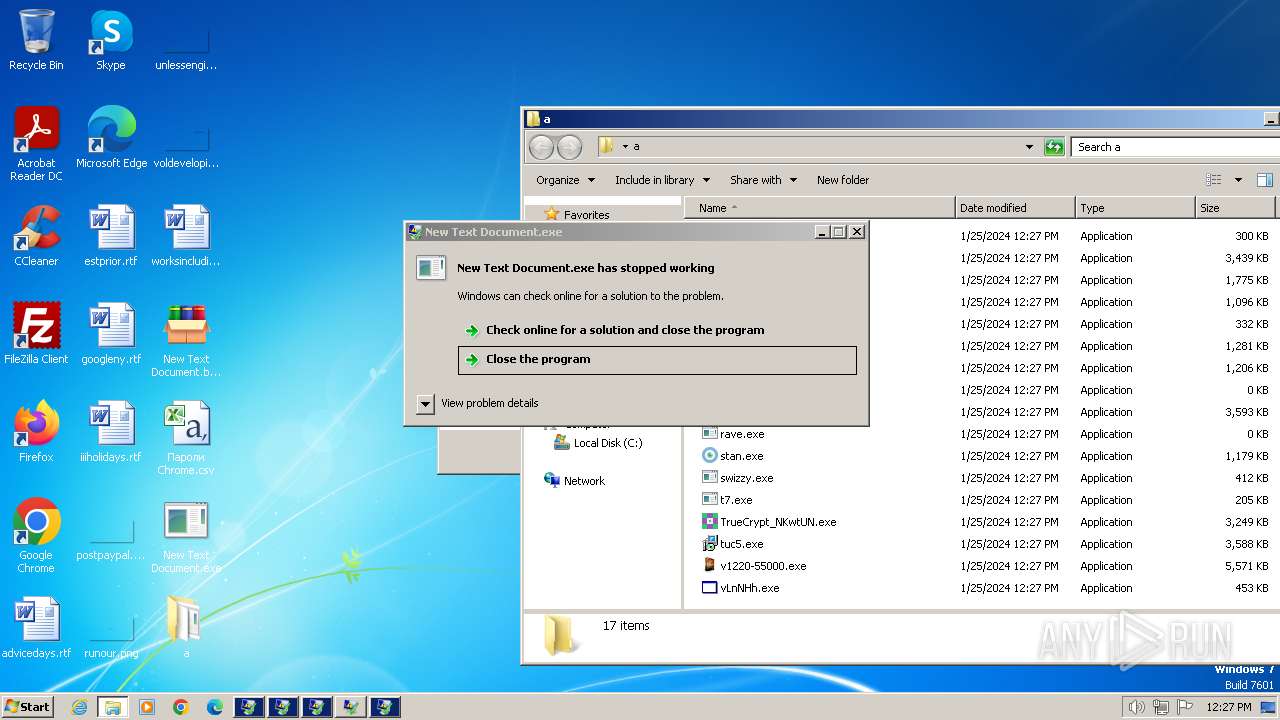
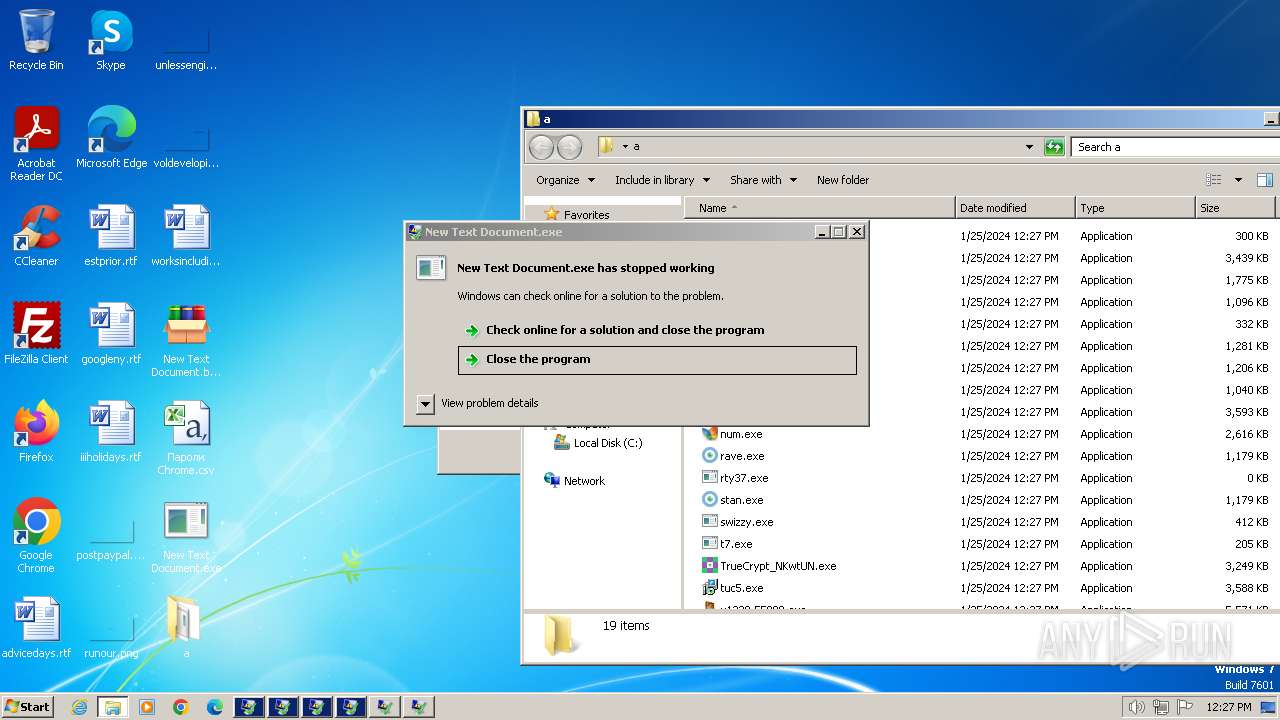
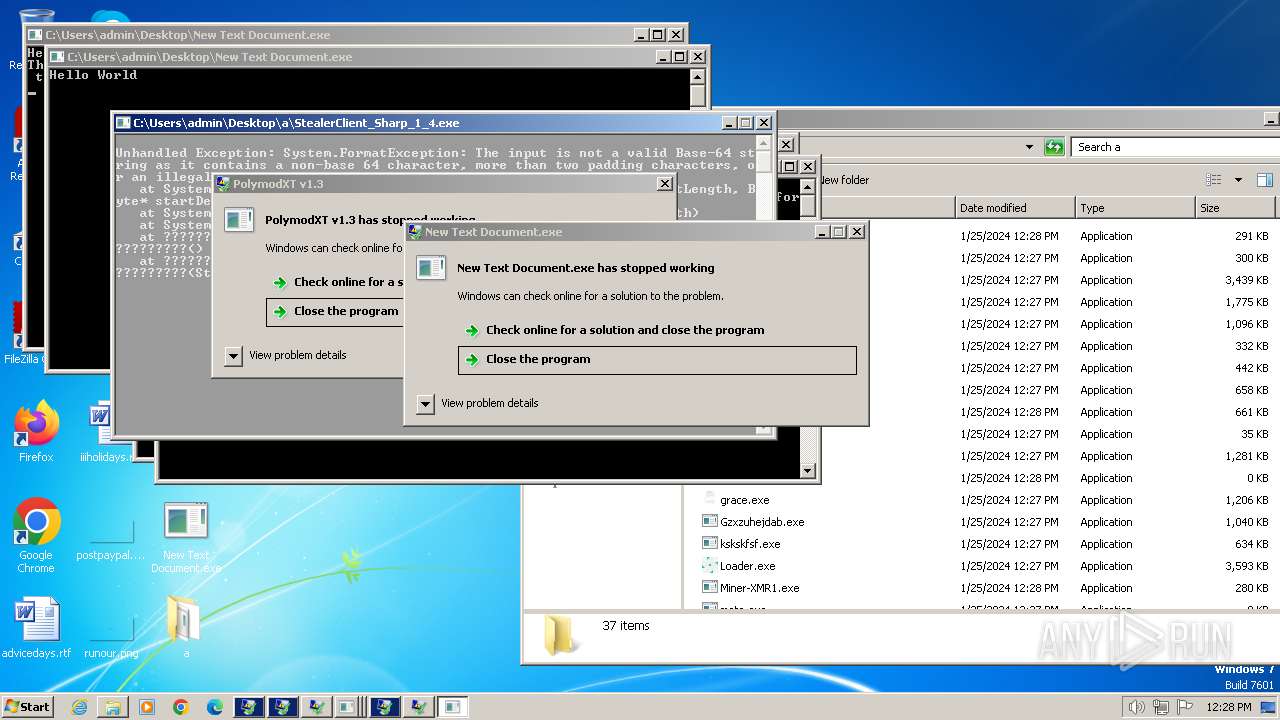
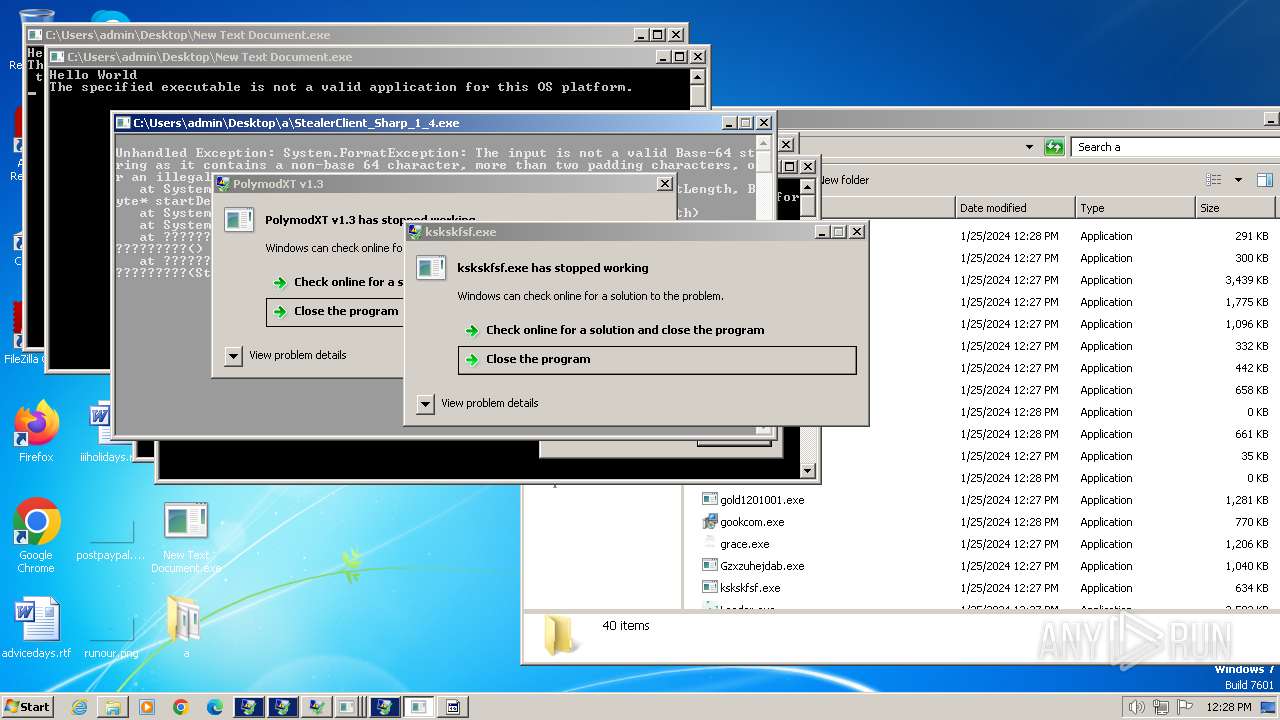
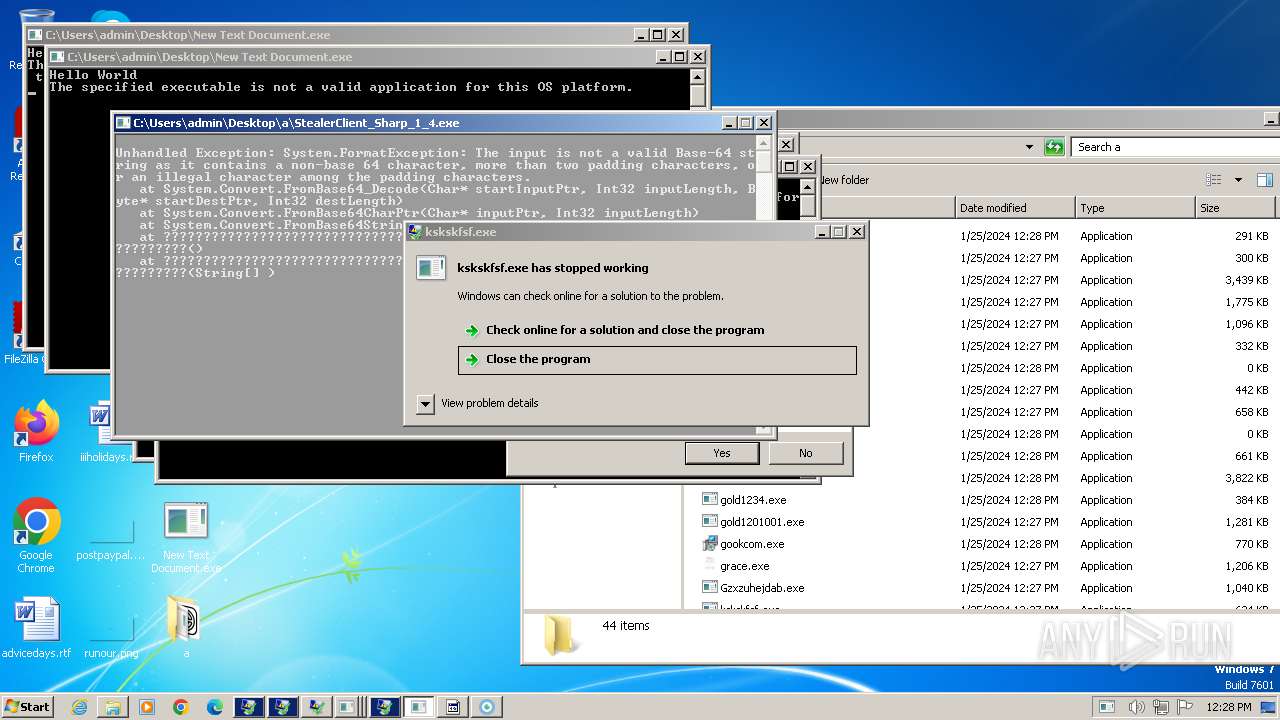
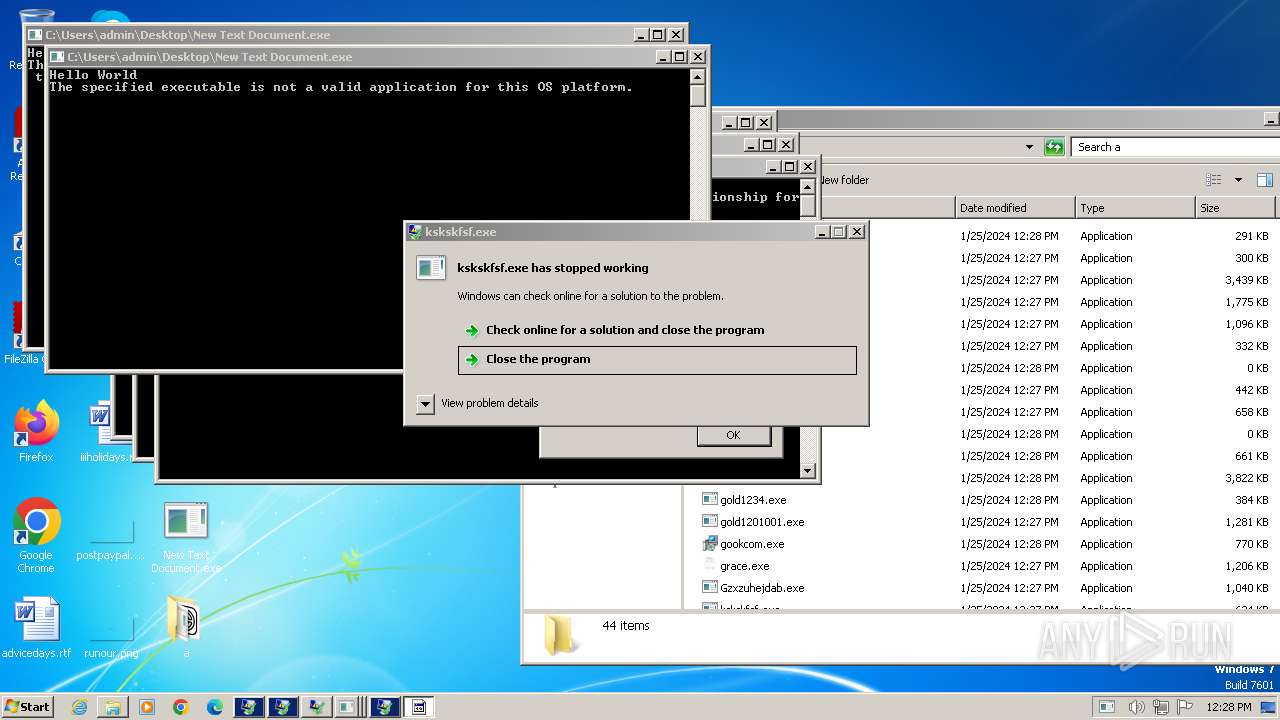
| File name: | New Text Document.bin.exe |
| Full analysis: | https://app.any.run/tasks/ab5d523b-c67d-4377-9f47-0c0839579415 |
| Verdict: | Malicious activity |
| Threats: | Agent Tesla is spyware that collects information about the actions of its victims by recording keystrokes and user interactions. It is falsely marketed as a legitimate software on the dedicated website where this malware is sold. |
| Analysis date: | January 25, 2024, 12:26:20 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | 0B0D247AA1F24C2F5867B3BF29F69450 |
| SHA1: | 48DE9F34226FD7F637E2379365BE035AF5C0DF1A |
| SHA256: | A6E7292E734C3A15CFA654BBA8DEA72A2F55F1C24CF6BBDC2FD7E63887E9315A |
| SSDEEP: | 12288:dcgCzNHJj96xfKJStJkRm3bYXob0AnmFMcaGQxkZVVVVVVVVVAtVVVUvqGV:UQKgLIQmFuGQxklvqO |
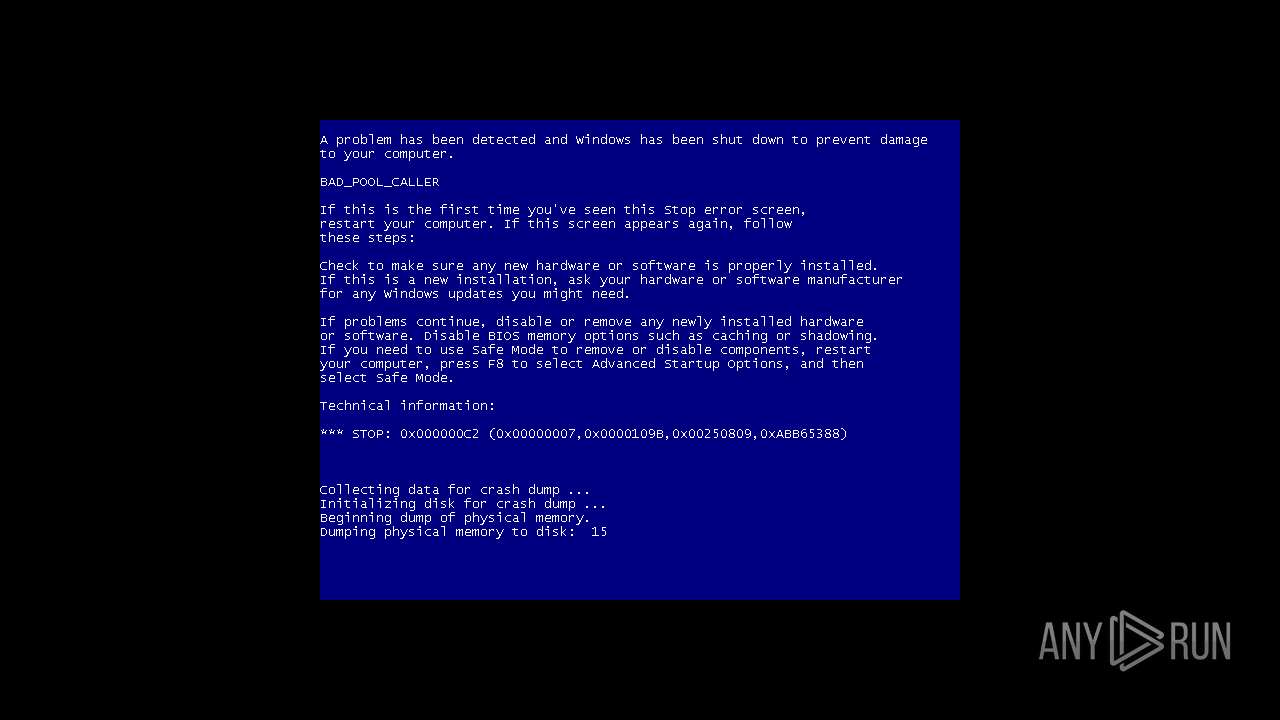
MALICIOUS
Drops the executable file immediately after the start
- New Text Document.bin.exe (PID: 2396)
- New Text Document.exe (PID: 1404)
- New Text Document.exe (PID: 2968)
- New Text Document.exe (PID: 2672)
- New Text Document.exe (PID: 2372)
- tuc5.exe (PID: 3612)
- tuc5.exe (PID: 3896)
- tuc5.tmp (PID: 3828)
- adobe.exe (PID: 3688)
- adobe.exe (PID: 3964)
- adobe.tmp (PID: 1876)
- xdrencodelib.exe (PID: 120)
- RegSvcs.exe (PID: 3768)
- num.exe (PID: 128)
- vLnNHh.exe (PID: 3560)
- rave.exe (PID: 2336)
- stan.exe (PID: 896)
- New Text Document.exe (PID: 2960)
- New Text Document.exe (PID: 3704)
- Awwnbpxqsf.exe (PID: 2948)
- New Text Document.exe (PID: 3412)
- New Text Document.exe (PID: 908)
- New Text Document.exe (PID: 2740)
- New Text Document.exe (PID: 1924)
- RegAsm.exe (PID: 1652)
- dd.exe (PID: 3752)
- first.exe (PID: 5376)
- Dctooux.exe (PID: 2336)
- New Text Document.exe (PID: 3808)
- New Text Document.exe (PID: 2908)
- New Text Document.exe (PID: 2604)
- univ.exe (PID: 3504)
- client.exe (PID: 3416)
- InstallSetup2.exe (PID: 4556)
- dvchost.exe (PID: 3452)
- bin.exe (PID: 2196)
- amer.exe (PID: 4120)
- MartDrum.exe (PID: 8028)
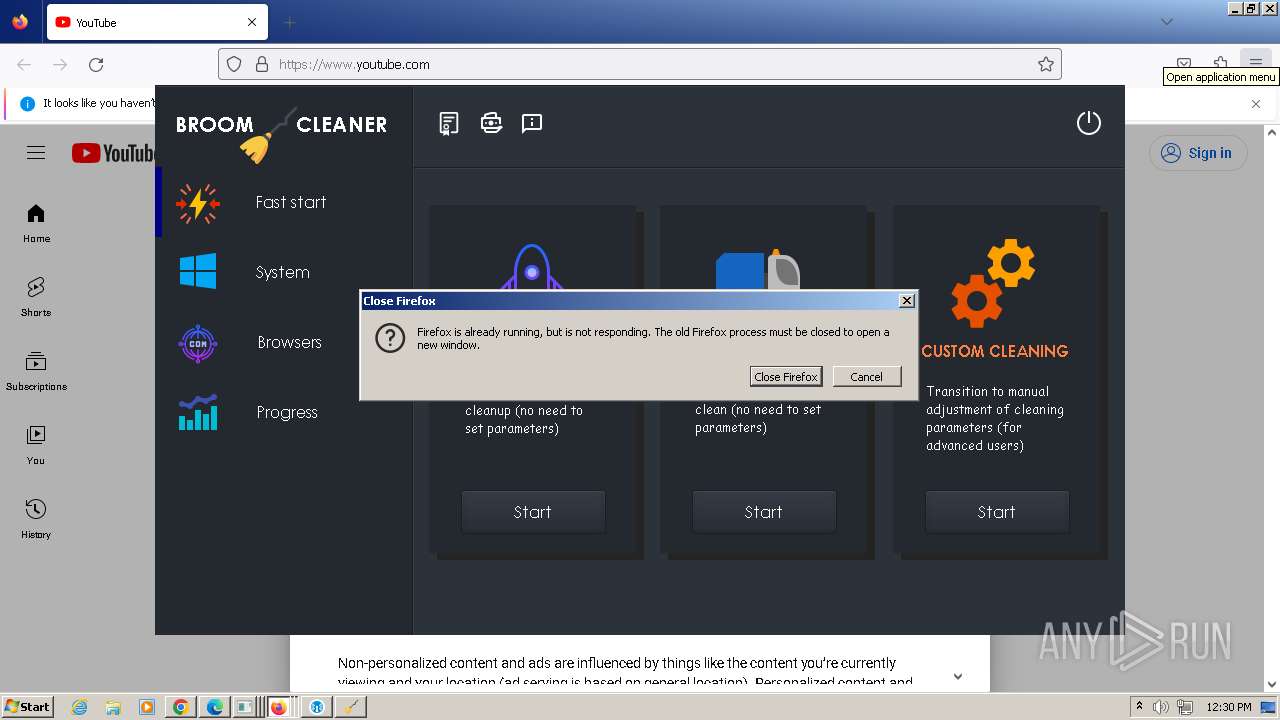
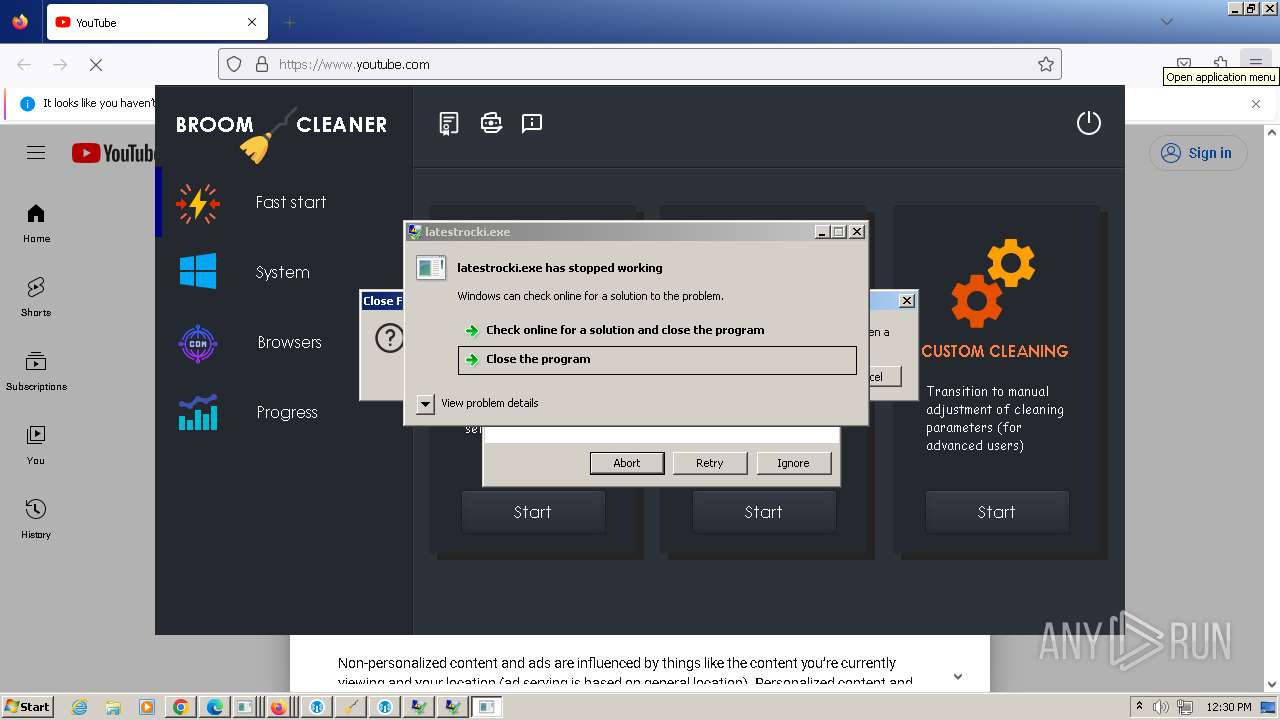
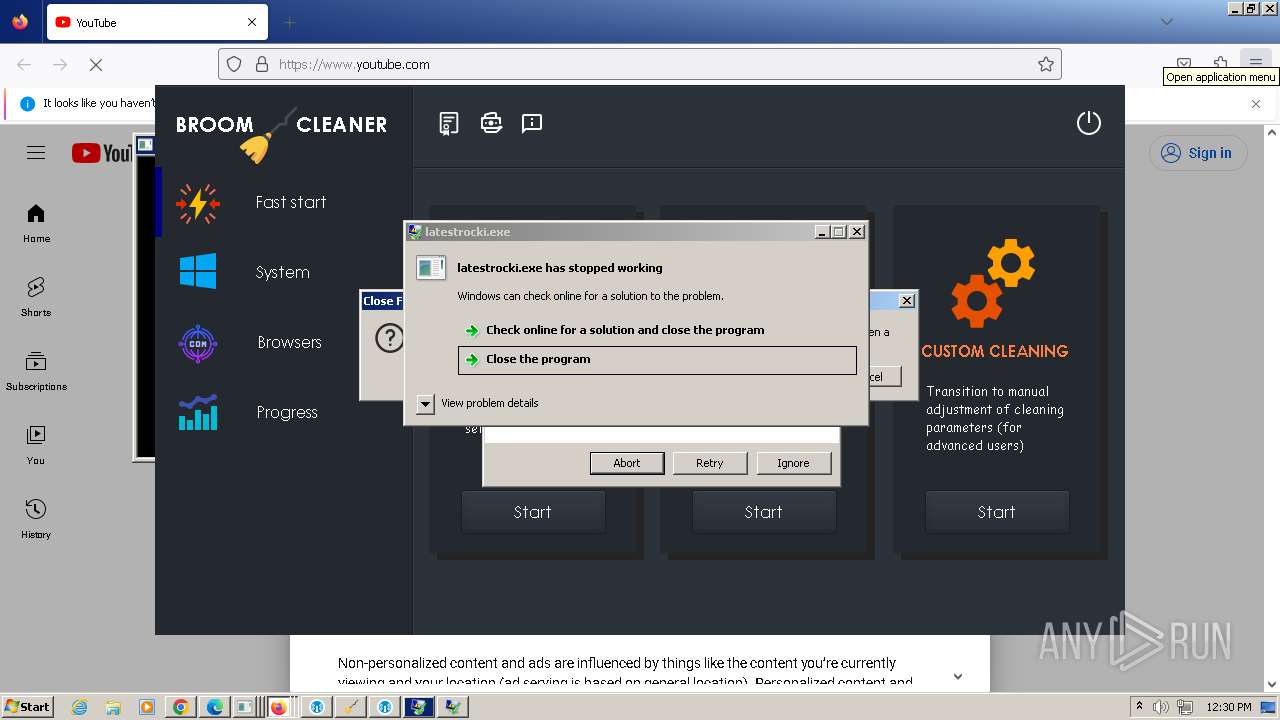
- latestrocki.exe (PID: 6764)
- GorgeousMovement.exe (PID: 6784)
- explorhe.exe (PID: 4048)
- Client-built.exe (PID: 3760)
- cmd.exe (PID: 6496)
- Fighting.pif (PID: 3712)
- cmd.exe (PID: 3516)
- costa.exe (PID: 3200)
- store.exe (PID: 1920)
HAUSBOMBER has been detected (YARA)
- New Text Document.exe (PID: 2672)
- New Text Document.exe (PID: 1404)
- New Text Document.exe (PID: 3704)
- New Text Document.exe (PID: 2960)
Starts NET.EXE for service management
- tuc5.tmp (PID: 3828)
- net.exe (PID: 3936)
Connects to the CnC server
- 2024.exe (PID: 3384)
- rave.exe (PID: 2336)
- stan.exe (PID: 896)
- RegAsm.exe (PID: 2784)
- RegAsm.exe (PID: 5108)
- Dctooux.exe (PID: 2336)
- rundll32.exe (PID: 2356)
- rundll32.exe (PID: 3188)
- syncUpd.exe (PID: 2572)
- nsd2D75.tmp (PID: 4200)
- explorhe.exe (PID: 4048)
- 2024.exe (PID: 6148)
REDLINE has been detected (SURICATA)
- 2024.exe (PID: 3384)
- RegAsm.exe (PID: 1652)
- flesh.exe (PID: 764)
- RegAsm.exe (PID: 2784)
- leg221.exe (PID: 1504)
- RegAsm.exe (PID: 4884)
- RegAsm.exe (PID: 5108)
- 2024.exe (PID: 6148)
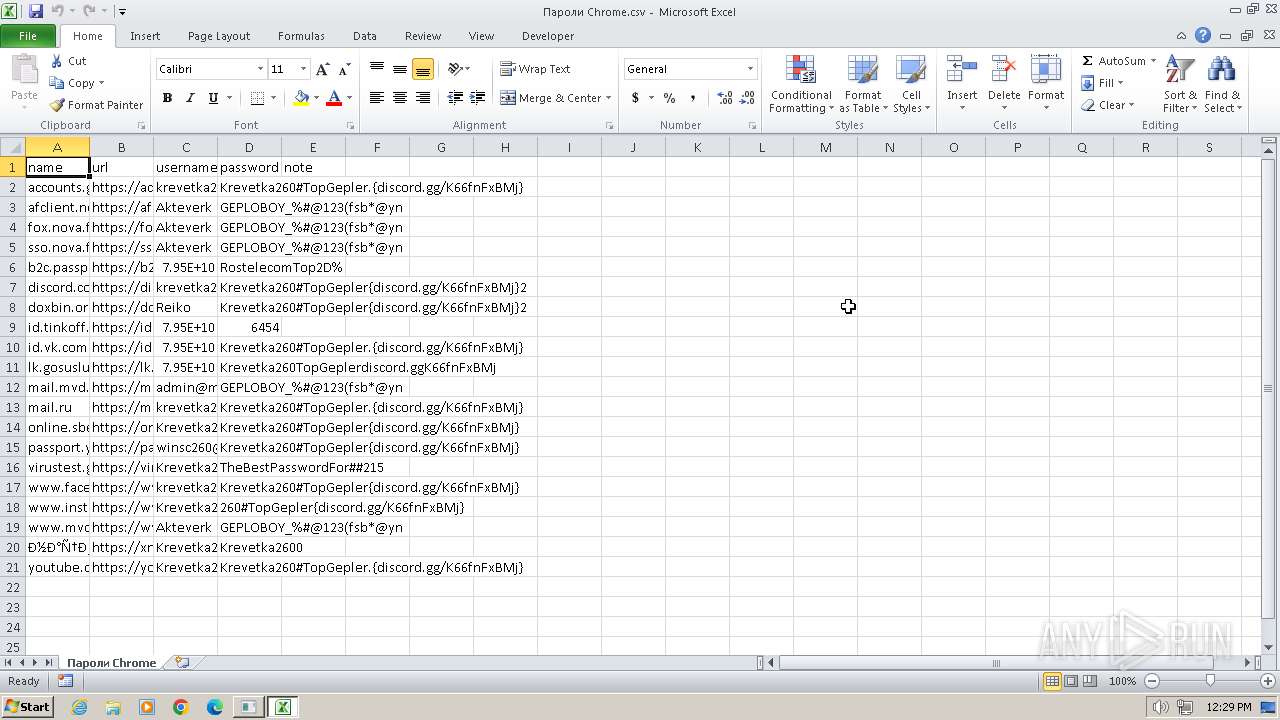
Steals credentials from Web Browsers
- RegSvcs.exe (PID: 3768)
- RegAsm.exe (PID: 1652)
- conhost.exe (PID: 2776)
- 2024.exe (PID: 3384)
- rave.exe (PID: 2336)
- stan.exe (PID: 896)
- flesh.exe (PID: 764)
- leg221.exe (PID: 1504)
- RegAsm.exe (PID: 4884)
- dd.exe (PID: 3564)
- oSIrag.exe (PID: 4016)
- rundll32.exe (PID: 2356)
- Accommodations.pif (PID: 3668)
Actions looks like stealing of personal data
- RegSvcs.exe (PID: 3768)
- 2024.exe (PID: 3384)
- RegAsm.exe (PID: 1652)
- conhost.exe (PID: 2776)
- flesh.exe (PID: 764)
- leg221.exe (PID: 1504)
- RegAsm.exe (PID: 2784)
- RegAsm.exe (PID: 4884)
- dd.exe (PID: 3564)
- rave.exe (PID: 2336)
- oSIrag.exe (PID: 4016)
- stan.exe (PID: 896)
- rundll32.exe (PID: 2356)
- Accommodations.pif (PID: 3668)
- jsc.exe (PID: 6716)
Changes the autorun value in the registry
- vLnNHh.exe (PID: 3560)
- buildcosta.exe (PID: 5128)
- explorhe.exe (PID: 4048)
- Client.exe (PID: 1852)
Uses Task Scheduler to autorun other applications
- stan.exe (PID: 896)
RISEPRO has been detected (SURICATA)
- rave.exe (PID: 2336)
- stan.exe (PID: 896)
- RageMP131.exe (PID: 2316)
- vimu.exe (PID: 5380)
- next.exe (PID: 600)
Steals credentials
- rave.exe (PID: 2336)
- stan.exe (PID: 896)
AGENTTESLA has been detected (YARA)
- RegSvcs.exe (PID: 3768)
- conhost.exe (PID: 2776)
Run PowerShell with an invisible window
- powershell.exe (PID: 2572)
RISEPRO has been detected (YARA)
- rave.exe (PID: 2336)
ASYNCRAT has been detected (YARA)
- t7.exe (PID: 2036)
Bypass execution policy to execute commands
- powershell.exe (PID: 3528)
- powershell.exe (PID: 3404)
AMADEY has been detected (SURICATA)
- Dctooux.exe (PID: 2336)
- rundll32.exe (PID: 2356)
- rundll32.exe (PID: 3188)
- explorhe.exe (PID: 4048)
Unusual connection from system programs
- rundll32.exe (PID: 2356)
- rundll32.exe (PID: 3188)
- rundll32.exe (PID: 3776)
KELIHOS has been detected (SURICATA)
- New Text Document.exe (PID: 2604)
GCLEANER has been detected (SURICATA)
- inte.exe (PID: 3428)
- inte.exe (PID: 5356)
- inte.exe (PID: 5704)
Starts CMD.EXE for self-deleting
- inte.exe (PID: 3428)
- inte.exe (PID: 5356)
- inte.exe (PID: 5704)
STEALC has been detected (SURICATA)
- syncUpd.exe (PID: 2572)
- nsd2D75.tmp (PID: 4200)
Raccoon mutex has been detected
- 2.3.1.1.exe (PID: 4528)
Antivirus name has been found in the command line (generic signature)
- findstr.exe (PID: 6372)
- findstr.exe (PID: 6236)
- findstr.exe (PID: 7344)
- findstr.exe (PID: 3912)
Lumma mutex has been detected
- store.exe (PID: 1920)
ASYNCRAT has been detected (SURICATA)
- jsc.exe (PID: 6716)
ASYNCRAT has been detected (MUTEX)
- jsc.exe (PID: 6716)
SUSPICIOUS
Executable content was dropped or overwritten
- New Text Document.bin.exe (PID: 2396)
- New Text Document.exe (PID: 2968)
- New Text Document.exe (PID: 2672)
- New Text Document.exe (PID: 2372)
- New Text Document.exe (PID: 1404)
- tuc5.exe (PID: 3896)
- tuc5.tmp (PID: 3828)
- tuc5.exe (PID: 3612)
- adobe.exe (PID: 3688)
- adobe.exe (PID: 3964)
- adobe.tmp (PID: 1876)
- xdrencodelib.exe (PID: 120)
- RegSvcs.exe (PID: 3768)
- num.exe (PID: 128)
- vLnNHh.exe (PID: 3560)
- rave.exe (PID: 2336)
- stan.exe (PID: 896)
- New Text Document.exe (PID: 2960)
- New Text Document.exe (PID: 3704)
- Awwnbpxqsf.exe (PID: 2948)
- New Text Document.exe (PID: 3412)
- New Text Document.exe (PID: 908)
- New Text Document.exe (PID: 2740)
- New Text Document.exe (PID: 1924)
- RegAsm.exe (PID: 1652)
- dd.exe (PID: 3752)
- first.exe (PID: 5376)
- Dctooux.exe (PID: 2336)
- New Text Document.exe (PID: 3808)
- New Text Document.exe (PID: 2908)
- New Text Document.exe (PID: 2604)
- client.exe (PID: 3416)
- InstallSetup2.exe (PID: 4556)
- dvchost.exe (PID: 3452)
- bin.exe (PID: 2196)
- amer.exe (PID: 4120)
- MartDrum.exe (PID: 8028)
- GorgeousMovement.exe (PID: 6784)
- latestrocki.exe (PID: 6764)
- clip.exe (PID: 2204)
- explorhe.exe (PID: 4048)
- Client-built.exe (PID: 3760)
- cmd.exe (PID: 6496)
- costa.exe (PID: 3200)
- Fighting.pif (PID: 3712)
- cmd.exe (PID: 3516)
- store.exe (PID: 1920)
Reads Internet Explorer settings
- New Text Document.bin.exe (PID: 2396)
Reads Microsoft Outlook installation path
- New Text Document.bin.exe (PID: 2396)
Reads the Internet Settings
- New Text Document.bin.exe (PID: 2396)
- New Text Document.exe (PID: 2672)
- New Text Document.exe (PID: 1404)
- New Text Document.exe (PID: 2372)
- New Text Document.exe (PID: 2968)
- conhost.exe (PID: 2776)
- RegSvcs.exe (PID: 3768)
- num.exe (PID: 128)
- cmd.exe (PID: 2528)
- New Text Document.exe (PID: 3704)
- New Text Document.exe (PID: 2960)
- New Text Document.exe (PID: 2740)
- New Text Document.exe (PID: 1924)
- New Text Document.exe (PID: 3412)
- New Text Document.exe (PID: 908)
- rave.exe (PID: 2336)
- RegAsm.exe (PID: 880)
- stan.exe (PID: 896)
- RegAsm.exe (PID: 1652)
- gookcom.exe (PID: 3872)
- 23.exe (PID: 3044)
- dd.exe (PID: 3752)
- Z7UbUl6TpTWrg8iMRm6f.exe (PID: 2940)
- Z7UbUl6TpTWrg8iMRm6f.exe (PID: 4424)
- dd.exe (PID: 3564)
- first.exe (PID: 5376)
- svcservice.exe (PID: 3944)
- sipnotify.exe (PID: 2100)
- runonce.exe (PID: 2164)
- first.exe (PID: 2348)
- powershell.exe (PID: 3404)
- powershell.exe (PID: 3528)
- Dctooux.exe (PID: 2336)
- New Text Document.exe (PID: 3808)
- oSIrag.exe (PID: 2080)
- oSIrag.exe (PID: 4016)
- New Text Document.exe (PID: 2908)
- rundll32.exe (PID: 2356)
- New Text Document.exe (PID: 2604)
- rundll32.exe (PID: 3188)
- univ.exe (PID: 3504)
- inte.exe (PID: 3428)
- go.exe (PID: 3580)
- buildcosta.exe (PID: 5128)
- inte.exe (PID: 5356)
- InstallSetup2.exe (PID: 4556)
- dvchost.exe (PID: 3452)
- inte.exe (PID: 5704)
- cmd.exe (PID: 2600)
- syncUpd.exe (PID: 2572)
- amer.exe (PID: 4120)
- explorhe.exe (PID: 4048)
- nsd2D75.tmp (PID: 4200)
- 2.3.1.1.exe (PID: 4528)
- MartDrum.exe (PID: 8028)
- latestrocki.exe (PID: 6764)
- GorgeousMovement.exe (PID: 6784)
- clip.exe (PID: 2204)
- rundll32.exe (PID: 3776)
- costa.exe (PID: 3200)
- Accommodations.pif (PID: 3668)
Reads settings of System Certificates
- New Text Document.exe (PID: 2672)
- New Text Document.exe (PID: 2372)
- New Text Document.exe (PID: 1404)
- New Text Document.exe (PID: 2968)
- RegSvcs.exe (PID: 3768)
- conhost.exe (PID: 2776)
- rave.exe (PID: 2336)
- New Text Document.exe (PID: 3704)
- New Text Document.exe (PID: 2960)
- New Text Document.exe (PID: 2740)
- New Text Document.exe (PID: 1924)
- New Text Document.exe (PID: 3412)
- New Text Document.exe (PID: 908)
- stan.exe (PID: 896)
- RegAsm.exe (PID: 880)
- RageMP131.exe (PID: 2316)
- sipnotify.exe (PID: 2100)
- oSIrag.exe (PID: 4016)
- New Text Document.exe (PID: 3808)
- New Text Document.exe (PID: 2908)
- New Text Document.exe (PID: 2604)
- vimu.exe (PID: 5380)
- next.exe (PID: 600)
- jsc.exe (PID: 6716)
The process creates files with name similar to system file names
- New Text Document.exe (PID: 2968)
- New Text Document.exe (PID: 3808)
- bin.exe (PID: 2196)
- clip.exe (PID: 2204)
Application launched itself
- conhost.exe (PID: 2508)
- Awwnbpxqsf.exe (PID: 2948)
- dd.exe (PID: 3752)
- WerFault.exe (PID: 2188)
- oSIrag.exe (PID: 2080)
- cmd.exe (PID: 6636)
- cmd.exe (PID: 2652)
- cmd.exe (PID: 6632)
- cmd.exe (PID: 7352)
Connects to the server without a host name
- New Text Document.exe (PID: 2968)
- New Text Document.exe (PID: 2372)
- New Text Document.exe (PID: 2672)
- New Text Document.exe (PID: 1404)
- New Text Document.exe (PID: 2960)
- New Text Document.exe (PID: 3704)
- New Text Document.exe (PID: 908)
- New Text Document.exe (PID: 1924)
- stan.exe (PID: 896)
- rave.exe (PID: 2336)
- Dctooux.exe (PID: 2336)
- rundll32.exe (PID: 2356)
- rundll32.exe (PID: 3188)
- New Text Document.exe (PID: 2908)
- New Text Document.exe (PID: 2604)
- New Text Document.exe (PID: 3808)
- inte.exe (PID: 3428)
- New Text Document.exe (PID: 2740)
- syncUpd.exe (PID: 2572)
- explorhe.exe (PID: 4048)
- rundll32.exe (PID: 3776)
Process requests binary or script from the Internet
- New Text Document.exe (PID: 2968)
- New Text Document.exe (PID: 2672)
- New Text Document.exe (PID: 2372)
- New Text Document.exe (PID: 1404)
- New Text Document.exe (PID: 2960)
- New Text Document.exe (PID: 3704)
- New Text Document.exe (PID: 908)
- New Text Document.exe (PID: 1924)
- stan.exe (PID: 896)
- rave.exe (PID: 2336)
- Dctooux.exe (PID: 2336)
- New Text Document.exe (PID: 2908)
- New Text Document.exe (PID: 2604)
- New Text Document.exe (PID: 3808)
- explorhe.exe (PID: 4048)
- univ.exe (PID: 3504)
Reads the Windows owner or organization settings
- tuc5.tmp (PID: 3828)
- adobe.tmp (PID: 1876)
Process drops legitimate windows executable
- tuc5.tmp (PID: 3828)
- adobe.tmp (PID: 1876)
- RegSvcs.exe (PID: 3768)
- univ.exe (PID: 3504)
- clip.exe (PID: 2204)
- Fighting.pif (PID: 3712)
The process drops C-runtime libraries
- tuc5.tmp (PID: 3828)
- adobe.tmp (PID: 1876)
Searches for installed software
- adobe.tmp (PID: 1876)
- RegAsm.exe (PID: 1652)
- 2024.exe (PID: 3384)
- rave.exe (PID: 2336)
- stan.exe (PID: 896)
- flesh.exe (PID: 764)
- leg221.exe (PID: 1504)
- RegAsm.exe (PID: 5108)
- RegAsm.exe (PID: 4884)
- Accommodations.pif (PID: 3668)
Connects to unusual port
- 2024.exe (PID: 3384)
- t7.exe (PID: 2036)
- RegAsm.exe (PID: 1652)
- rave.exe (PID: 2336)
- stan.exe (PID: 896)
- pixellslsss.exe (PID: 2848)
- flesh.exe (PID: 764)
- RegAsm.exe (PID: 2784)
- powershell.exe (PID: 2572)
- pixelcloudnew2.exe (PID: 4040)
- leg221.exe (PID: 1504)
- RegAsm.exe (PID: 4884)
- RegAsm.exe (PID: 5108)
- aspnet_compiler.exe (PID: 5620)
- RageMP131.exe (PID: 2316)
- chromeupdate.exe (PID: 3556)
- vimu.exe (PID: 5380)
- next.exe (PID: 600)
- New Text Document.exe (PID: 2604)
- New Text Document.exe (PID: 2908)
- New Text Document.exe (PID: 3808)
- Client.exe (PID: 1852)
- dialer.exe (PID: 6368)
- jsc.exe (PID: 6716)
- 2024.exe (PID: 6148)
Accesses Microsoft Outlook profiles
- RegSvcs.exe (PID: 3768)
- conhost.exe (PID: 2776)
- rave.exe (PID: 2336)
- stan.exe (PID: 896)
- dd.exe (PID: 3564)
- rundll32.exe (PID: 2356)
- oSIrag.exe (PID: 4016)
- Accommodations.pif (PID: 3668)
Reads browser cookies
- RegAsm.exe (PID: 1652)
- 2024.exe (PID: 3384)
- rave.exe (PID: 2336)
- flesh.exe (PID: 764)
Drops 7-zip archiver for unpacking
- num.exe (PID: 128)
- dvchost.exe (PID: 3452)
Starts CMD.EXE for commands execution
- num.exe (PID: 128)
- inte.exe (PID: 3428)
- client.exe (PID: 3416)
- inte.exe (PID: 5356)
- dvchost.exe (PID: 3452)
- inte.exe (PID: 5704)
- BroomSetup.exe (PID: 5488)
- cmd.exe (PID: 6636)
- MartDrum.exe (PID: 8028)
- cmd.exe (PID: 2652)
- GorgeousMovement.exe (PID: 6784)
- mimi.exe (PID: 6672)
- cmd.exe (PID: 6632)
- cmd.exe (PID: 7352)
Executing commands from a ".bat" file
- num.exe (PID: 128)
- client.exe (PID: 3416)
- dvchost.exe (PID: 3452)
- BroomSetup.exe (PID: 5488)
Connects to SMTP port
- RegSvcs.exe (PID: 3768)
- conhost.exe (PID: 2776)
- oSIrag.exe (PID: 4016)
Uses ATTRIB.EXE to modify file attributes
- cmd.exe (PID: 2528)
- cmd.exe (PID: 2600)
Checks for external IP
- rave.exe (PID: 2336)
- stan.exe (PID: 896)
- first.exe (PID: 5376)
- RageMP131.exe (PID: 2316)
- first.exe (PID: 2348)
- vimu.exe (PID: 5380)
- next.exe (PID: 600)
Starts a Microsoft application from unusual location
- setup_wm.exe (PID: 920)
- jsc.exe (PID: 6716)
Base64-obfuscated command line is found
- gookcom.exe (PID: 3872)
Potential TCP-based PowerShell reverse shell connection
- gookcom.exe (PID: 3872)
Starts POWERSHELL.EXE for commands execution
- gookcom.exe (PID: 3872)
- rundll32.exe (PID: 2356)
- cmd.exe (PID: 8056)
Suspicious use of symmetric encryption in PowerShell
- gookcom.exe (PID: 3872)
Starts itself from another location
- 23.exe (PID: 3044)
- amer.exe (PID: 4120)
- clip.exe (PID: 2204)
- Client-built.exe (PID: 3760)
Windows Defender mutex has been found
- timeSync.exe (PID: 4524)
- syncUpd.exe (PID: 2572)
- nsd2D75.tmp (PID: 4200)
The Powershell connects to the Internet
- powershell.exe (PID: 2572)
Unusual connection from system programs
- powershell.exe (PID: 2572)
The process executes via Task Scheduler
- ctfmon.exe (PID: 2072)
- sipnotify.exe (PID: 2100)
- oSIrag.exe (PID: 2080)
- buildcosta.exe (PID: 3156)
- explorhe.exe (PID: 4220)
- buildcosta.exe (PID: 4680)
Probably UAC bypass using CMSTP.exe (Connection Manager service profile)
- first.exe (PID: 2348)
Using PowerShell to operate with local accounts
- powershell.exe (PID: 3528)
- powershell.exe (PID: 3404)
Opens a file (MACROS)
- EXCEL.EXE (PID: 3928)
Reads data from a file (MACROS)
- EXCEL.EXE (PID: 3928)
Uses RUNDLL32.EXE to load library
- Dctooux.exe (PID: 2336)
- explorhe.exe (PID: 4048)
- powershell.exe (PID: 4220)
Loads DLL from Mozilla Firefox
- rundll32.exe (PID: 2356)
Uses NETSH.EXE to obtain data on the network
- rundll32.exe (PID: 2356)
Uses TASKKILL.EXE to kill process
- cmd.exe (PID: 2584)
- cmd.exe (PID: 6064)
- cmd.exe (PID: 4212)
Uses TIMEOUT.EXE to delay execution
- cmd.exe (PID: 4808)
The executable file from the user directory is run by the CMD process
- chromeupdate.exe (PID: 3556)
- Fighting.pif (PID: 3712)
- Accommodations.pif (PID: 3668)
Starts application with an unusual extension
- InstallSetup2.exe (PID: 4556)
- cmd.exe (PID: 7020)
- cmd.exe (PID: 6632)
- cmd.exe (PID: 7352)
Malware-specific behavior (creating "System.dll" in Temp)
- bin.exe (PID: 2196)
Get information on the list of running processes
- cmd.exe (PID: 6632)
- cmd.exe (PID: 7352)
Using 'findstr.exe' to search for text patterns in files and output
- cmd.exe (PID: 6632)
- cmd.exe (PID: 7352)
The process checks if it is being run in the virtual environment
- dialer.exe (PID: 6368)
Drops a file with a rarely used extension (PIF)
- cmd.exe (PID: 6496)
- Fighting.pif (PID: 3712)
- cmd.exe (PID: 3516)
Runs PING.EXE to delay simulation
- cmd.exe (PID: 6632)
- cmd.exe (PID: 7352)
INFO
Reads the computer name
- New Text Document.bin.exe (PID: 2396)
- New Text Document.exe (PID: 2672)
- New Text Document.exe (PID: 1404)
- New Text Document.exe (PID: 2372)
- New Text Document.exe (PID: 2968)
- conhost.exe (PID: 2508)
- conhost.exe (PID: 2776)
- tuc5.tmp (PID: 3624)
- tuc5.tmp (PID: 3828)
- gold1201001.exe (PID: 3864)
- Awwnbpxqsf.exe (PID: 2948)
- adobe.tmp (PID: 4028)
- 2024.exe (PID: 3384)
- adobe.tmp (PID: 1876)
- t7.exe (PID: 2036)
- alex.exe (PID: 2104)
- xdrencodelib.exe (PID: 120)
- RegSvcs.exe (PID: 3768)
- stan.exe (PID: 896)
- swizzy.exe (PID: 2304)
- RegAsm.exe (PID: 1652)
- rave.exe (PID: 2336)
- Gzxzuhejdab.exe (PID: 1848)
- num.exe (PID: 128)
- vLnNHh.exe (PID: 3560)
- New Text Document.exe (PID: 2960)
- New Text Document.exe (PID: 3704)
- New Text Document.exe (PID: 2740)
- New Text Document.exe (PID: 1924)
- dd.exe (PID: 3752)
- New Text Document.exe (PID: 3412)
- pixellslsss.exe (PID: 2848)
- New Text Document.exe (PID: 908)
- RegAsm.exe (PID: 880)
- crypted_d786fd3e.exe (PID: 1196)
- StealerClient_Sharp_1_4.exe (PID: 2492)
- flesh.exe (PID: 764)
- 23.exe (PID: 3044)
- gookcom.exe (PID: 3872)
- qemu-ga.exe (PID: 1636)
- setup_wm.exe (PID: 920)
- gold1234.exe (PID: 3428)
- Zjqkz.exe (PID: 884)
- RegAsm.exe (PID: 2784)
- pixelcloudnew2.exe (PID: 4040)
- leg221.exe (PID: 1504)
- Z7UbUl6TpTWrg8iMRm6f.exe (PID: 2940)
- dd.exe (PID: 3564)
- crypted.exe (PID: 4480)
- Z7UbUl6TpTWrg8iMRm6f.exe (PID: 4424)
- rdx1122.exe (PID: 4968)
- RegAsm.exe (PID: 5108)
- RegAsm.exe (PID: 4884)
- first.exe (PID: 5376)
- aspnet_compiler.exe (PID: 5620)
- aspnet_compiler.exe (PID: 5756)
- aspnet_compiler.exe (PID: 5952)
- aspnet_compiler.exe (PID: 6092)
- aspnet_compiler.exe (PID: 2928)
- aspnet_compiler.exe (PID: 5996)
- aspnet_compiler.exe (PID: 6028)
- timeSync.exe (PID: 4524)
- 288c47bbc1871b439df19ff4df68f0766.exe (PID: 584)
- svcservice.exe (PID: 3944)
- IMEKLMG.EXE (PID: 2276)
- IMEKLMG.EXE (PID: 2284)
- RageMP131.exe (PID: 2316)
- first.exe (PID: 2348)
- oSIrag.exe (PID: 2080)
- OYZKbZu.exe (PID: 2304)
- qemu-ga.exe (PID: 2364)
- wmpnscfg.exe (PID: 2920)
- wmpnscfg.exe (PID: 2964)
- Dctooux.exe (PID: 2336)
- oSIrag.exe (PID: 4016)
- New Text Document.exe (PID: 3808)
- New Text Document.exe (PID: 2908)
- New Text Document.exe (PID: 2604)
- nika.exe (PID: 3072)
- Windows.exe (PID: 3256)
- client.exe (PID: 3416)
- inte.exe (PID: 3428)
- go.exe (PID: 3580)
- univ.exe (PID: 3504)
- vimu.exe (PID: 5380)
- buildcosta.exe (PID: 5128)
- inte.exe (PID: 5356)
- bin.exe (PID: 2196)
- BroomSetup.exe (PID: 5488)
- chromeupdate.exe (PID: 3556)
- InstallSetup2.exe (PID: 4556)
- dvchost.exe (PID: 3452)
- inte.exe (PID: 5704)
- syncUpd.exe (PID: 2572)
- InstallSetup8.exe (PID: 3164)
- nsd2D75.tmp (PID: 4200)
- amer.exe (PID: 4120)
- explorhe.exe (PID: 4048)
- 2.3.1.1.exe (PID: 4528)
- next.exe (PID: 600)
- MartDrum.exe (PID: 8028)
- latestrocki.exe (PID: 6764)
- InstallSetup7.exe (PID: 5716)
- 31839b57a4f11171d6abc8bbc4451ee4.exe (PID: 5624)
- GorgeousMovement.exe (PID: 6784)
- Client-built.exe (PID: 3760)
- cayV0Deo9jSt417.exe (PID: 6384)
- Client.exe (PID: 1852)
- costa.exe (PID: 3200)
- e0cbefcb1af40c7d4aff4aca26621a98.exe (PID: 5356)
- Fighting.pif (PID: 3712)
- Accommodations.pif (PID: 3668)
- store.exe (PID: 1920)
- explorhe.exe (PID: 4220)
- alex.exe (PID: 3296)
- 2024.exe (PID: 6148)
- jsc.exe (PID: 6716)
Checks proxy server information
- New Text Document.bin.exe (PID: 2396)
- rave.exe (PID: 2336)
- stan.exe (PID: 896)
- Dctooux.exe (PID: 2336)
- rundll32.exe (PID: 2356)
- rundll32.exe (PID: 3188)
- inte.exe (PID: 3428)
- univ.exe (PID: 3504)
- buildcosta.exe (PID: 5128)
- inte.exe (PID: 5356)
- inte.exe (PID: 5704)
- InstallSetup2.exe (PID: 4556)
- syncUpd.exe (PID: 2572)
- explorhe.exe (PID: 4048)
- 2.3.1.1.exe (PID: 4528)
- nsd2D75.tmp (PID: 4200)
- rundll32.exe (PID: 3776)
- Accommodations.pif (PID: 3668)
Checks supported languages
- New Text Document.bin.exe (PID: 2396)
- New Text Document.exe (PID: 2672)
- New Text Document.exe (PID: 1404)
- New Text Document.exe (PID: 2968)
- New Text Document.exe (PID: 2372)
- conhost.exe (PID: 2508)
- conhost.exe (PID: 2776)
- v1220-55000.exe (PID: 3436)
- vLnNHh.exe (PID: 3560)
- tuc5.exe (PID: 3612)
- tuc5.tmp (PID: 3624)
- tuc5.exe (PID: 3896)
- tuc5.tmp (PID: 3828)
- gold1201001.exe (PID: 3864)
- adobe.exe (PID: 3688)
- Awwnbpxqsf.exe (PID: 2948)
- grace.exe (PID: 4052)
- adobe.tmp (PID: 4028)
- 2024.exe (PID: 3384)
- xdrencodelib.exe (PID: 120)
- adobe.exe (PID: 3964)
- adobe.tmp (PID: 1876)
- t7.exe (PID: 2036)
- xdrencodelib.exe (PID: 1492)
- alex.exe (PID: 2104)
- RegSvcs.exe (PID: 3768)
- stan.exe (PID: 896)
- swizzy.exe (PID: 2304)
- RegAsm.exe (PID: 1652)
- rave.exe (PID: 2336)
- num.exe (PID: 128)
- Gzxzuhejdab.exe (PID: 1848)
- mode.com (PID: 2508)
- New Text Document.exe (PID: 3704)
- New Text Document.exe (PID: 2960)
- New Text Document.exe (PID: 2740)
- New Text Document.exe (PID: 1924)
- dd.exe (PID: 3752)
- New Text Document.exe (PID: 3412)
- New Text Document.exe (PID: 908)
- pixellslsss.exe (PID: 2848)
- crypted_d786fd3e.exe (PID: 1196)
- kskskfsf.exe (PID: 1992)
- RegAsm.exe (PID: 880)
- StealerClient_Sharp_1_4.exe (PID: 2492)
- StealerClient_Cpp_1_3.exe (PID: 900)
- StealerClient_Cpp_1_4.exe (PID: 2536)
- StealerClient_Cpp.exe (PID: 3444)
- flesh.exe (PID: 764)
- 23.exe (PID: 3044)
- StealerClient_Cpp_1_3_1.exe (PID: 2824)
- gookcom.exe (PID: 3872)
- qemu-ga.exe (PID: 1636)
- setup_wm.exe (PID: 920)
- Zjqkz.exe (PID: 884)
- RegAsm.exe (PID: 2784)
- gold1234.exe (PID: 3428)
- pixelcloudnew2.exe (PID: 4040)
- Z7UbUl6TpTWrg8iMRm6f.exe (PID: 2940)
- dd.exe (PID: 3564)
- leg221.exe (PID: 1504)
- Z7UbUl6TpTWrg8iMRm6f.exe (PID: 4424)
- crypted.exe (PID: 4480)
- rdx1122.exe (PID: 4968)
- RegAsm.exe (PID: 4884)
- RegAsm.exe (PID: 5108)
- aspnet_compiler.exe (PID: 5620)
- aspnet_compiler.exe (PID: 5756)
- aspnet_compiler.exe (PID: 5996)
- aspnet_compiler.exe (PID: 5952)
- aspnet_compiler.exe (PID: 6028)
- first.exe (PID: 5376)
- aspnet_compiler.exe (PID: 2928)
- 288c47bbc1871b439df19ff4df68f0766.exe (PID: 584)
- aspnet_compiler.exe (PID: 6092)
- svcservice.exe (PID: 3944)
- crypteddaisy.exe (PID: 1288)
- 5777786423.exe (PID: 6136)
- timeSync.exe (PID: 4524)
- oSIrag.exe (PID: 2080)
- IMEKLMG.EXE (PID: 2276)
- IMEKLMG.EXE (PID: 2284)
- RageMP131.exe (PID: 2316)
- Dctooux.exe (PID: 2336)
- OYZKbZu.exe (PID: 2304)
- qemu-ga.exe (PID: 2364)
- first.exe (PID: 2348)
- wmpnscfg.exe (PID: 2920)
- wmpnscfg.exe (PID: 2964)
- oSIrag.exe (PID: 4016)
- New Text Document.exe (PID: 3808)
- New Text Document.exe (PID: 2908)
- New Text Document.exe (PID: 2604)
- networ.exe (PID: 3080)
- nika.exe (PID: 3072)
- Windows.exe (PID: 3256)
- dvchost.exe (PID: 3452)
- inte.exe (PID: 3428)
- univ.exe (PID: 3504)
- client.exe (PID: 3416)
- go.exe (PID: 3580)
- inte.exe (PID: 5356)
- vimu.exe (PID: 5380)
- buildcosta.exe (PID: 5128)
- 9.exe (PID: 2752)
- bin.exe (PID: 2196)
- InstallSetup2.exe (PID: 4556)
- BroomSetup.exe (PID: 5488)
- chromeupdate.exe (PID: 3556)
- inte.exe (PID: 5704)
- mode.com (PID: 3884)
- nsd2D75.tmp (PID: 4200)
- InstallSetup8.exe (PID: 3164)
- syncUpd.exe (PID: 2572)
- amer.exe (PID: 4120)
- explorhe.exe (PID: 4048)
- buildcosta.exe (PID: 3156)
- next.exe (PID: 600)
- 2.3.1.1.exe (PID: 4528)
- chcp.com (PID: 7088)
- MartDrum.exe (PID: 8028)
- latestrocki.exe (PID: 6764)
- GorgeousMovement.exe (PID: 6784)
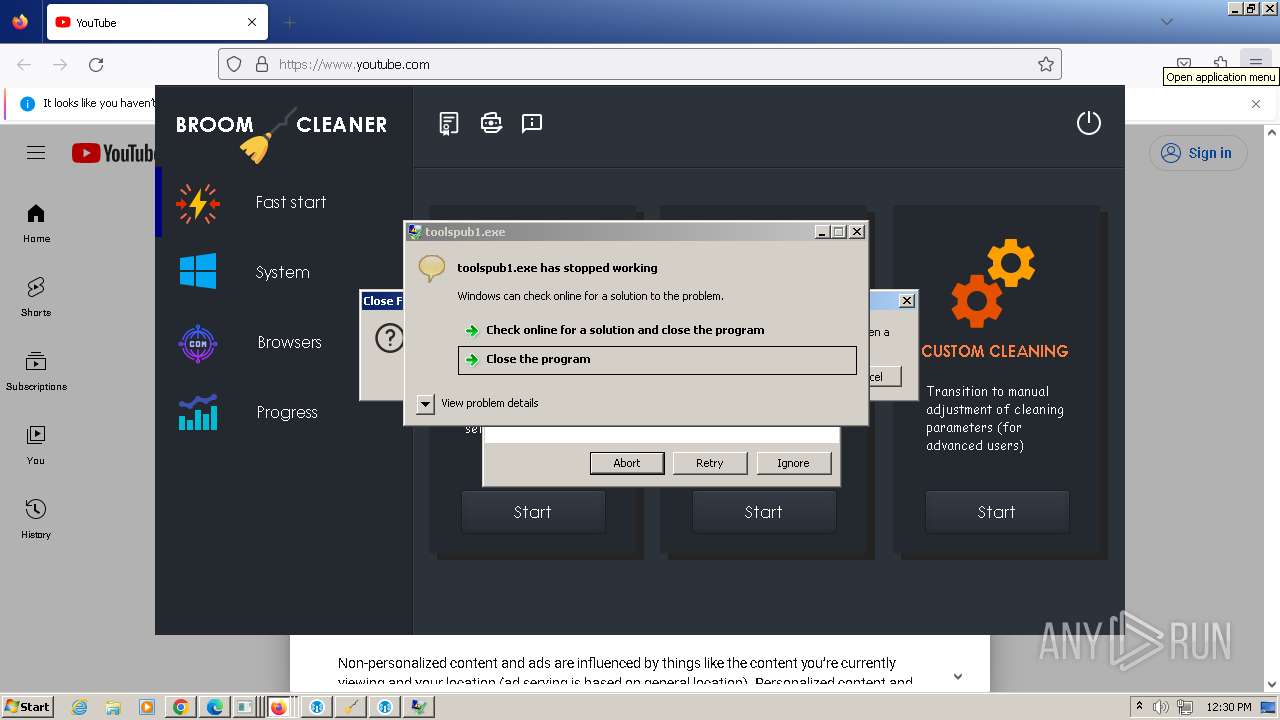
- toolspub1.exe (PID: 5196)
- InstallSetup7.exe (PID: 5716)
- Client-built.exe (PID: 3760)
- cayV0Deo9jSt417.exe (PID: 6384)
- 31839b57a4f11171d6abc8bbc4451ee4.exe (PID: 5624)
- brg.exe (PID: 6208)
- mimi.exe (PID: 6672)
- Client.exe (PID: 1852)
- taskhost.exe (PID: 3912)
- costa.exe (PID: 3200)
- Fighting.pif (PID: 3712)
- Accommodations.pif (PID: 3668)
- explorhe.exe (PID: 4220)
- store.exe (PID: 1920)
- buildcosta.exe (PID: 4680)
- kskskfsf.exe (PID: 2160)
- e0cbefcb1af40c7d4aff4aca26621a98.exe (PID: 5356)
- jsc.exe (PID: 6716)
- MSBuild.exe (PID: 3420)
- 2024.exe (PID: 6148)
- alex.exe (PID: 3296)
Reads the machine GUID from the registry
- New Text Document.bin.exe (PID: 2396)
- New Text Document.exe (PID: 2672)
- New Text Document.exe (PID: 2372)
- New Text Document.exe (PID: 2968)
- New Text Document.exe (PID: 1404)
- conhost.exe (PID: 2776)
- gold1201001.exe (PID: 3864)
- Awwnbpxqsf.exe (PID: 2948)
- 2024.exe (PID: 3384)
- t7.exe (PID: 2036)
- alex.exe (PID: 2104)
- RegSvcs.exe (PID: 3768)
- RegAsm.exe (PID: 1652)
- Gzxzuhejdab.exe (PID: 1848)
- rave.exe (PID: 2336)
- New Text Document.exe (PID: 3704)
- New Text Document.exe (PID: 2960)
- stan.exe (PID: 896)
- New Text Document.exe (PID: 2740)
- New Text Document.exe (PID: 1924)
- dd.exe (PID: 3752)
- New Text Document.exe (PID: 908)
- pixellslsss.exe (PID: 2848)
- New Text Document.exe (PID: 3412)
- RegAsm.exe (PID: 880)
- flesh.exe (PID: 764)
- gookcom.exe (PID: 3872)
- Zjqkz.exe (PID: 884)
- pixelcloudnew2.exe (PID: 4040)
- RegAsm.exe (PID: 2784)
- dd.exe (PID: 3564)
- leg221.exe (PID: 1504)
- RegAsm.exe (PID: 4884)
- RegAsm.exe (PID: 5108)
- aspnet_compiler.exe (PID: 5620)
- first.exe (PID: 5376)
- aspnet_compiler.exe (PID: 5756)
- first.exe (PID: 2348)
- RageMP131.exe (PID: 2316)
- oSIrag.exe (PID: 2080)
- Dctooux.exe (PID: 2336)
- New Text Document.exe (PID: 3808)
- oSIrag.exe (PID: 4016)
- New Text Document.exe (PID: 2908)
- New Text Document.exe (PID: 2604)
- client.exe (PID: 3416)
- inte.exe (PID: 3428)
- Windows.exe (PID: 3256)
- univ.exe (PID: 3504)
- inte.exe (PID: 5356)
- buildcosta.exe (PID: 5128)
- chromeupdate.exe (PID: 3556)
- InstallSetup2.exe (PID: 4556)
- inte.exe (PID: 5704)
- 2.3.1.1.exe (PID: 4528)
- explorhe.exe (PID: 4048)
- nsd2D75.tmp (PID: 4200)
- vimu.exe (PID: 5380)
- next.exe (PID: 600)
- 31839b57a4f11171d6abc8bbc4451ee4.exe (PID: 5624)
- Client-built.exe (PID: 3760)
- cayV0Deo9jSt417.exe (PID: 6384)
- Client.exe (PID: 1852)
- costa.exe (PID: 3200)
- e0cbefcb1af40c7d4aff4aca26621a98.exe (PID: 5356)
- store.exe (PID: 1920)
- Accommodations.pif (PID: 3668)
- 2024.exe (PID: 6148)
- jsc.exe (PID: 6716)
- alex.exe (PID: 3296)
Manual execution by a user
- New Text Document.exe (PID: 2672)
- New Text Document.exe (PID: 1404)
- New Text Document.exe (PID: 2372)
- New Text Document.exe (PID: 2968)
- New Text Document.exe (PID: 3704)
- New Text Document.exe (PID: 2960)
- New Text Document.exe (PID: 2740)
- New Text Document.exe (PID: 1924)
- New Text Document.exe (PID: 3412)
- New Text Document.exe (PID: 908)
- runonce.exe (PID: 2164)
- IMEKLMG.EXE (PID: 2276)
- IMEKLMG.EXE (PID: 2284)
- OYZKbZu.exe (PID: 2304)
- RageMP131.exe (PID: 2316)
- Dctooux.exe (PID: 2336)
- first.exe (PID: 2348)
- qemu-ga.exe (PID: 2364)
- wmpnscfg.exe (PID: 2920)
- wmpnscfg.exe (PID: 2964)
- EXCEL.EXE (PID: 3928)
- New Text Document.exe (PID: 3808)
- New Text Document.exe (PID: 2908)
- New Text Document.exe (PID: 2604)
- cmd.exe (PID: 8060)
- jsc.exe (PID: 6716)
Reads Environment values
- New Text Document.exe (PID: 2672)
- New Text Document.exe (PID: 1404)
- New Text Document.exe (PID: 2372)
- New Text Document.exe (PID: 2968)
- conhost.exe (PID: 2776)
- t7.exe (PID: 2036)
- RegSvcs.exe (PID: 3768)
- RegAsm.exe (PID: 1652)
- 2024.exe (PID: 3384)
- New Text Document.exe (PID: 3704)
- New Text Document.exe (PID: 2960)
- New Text Document.exe (PID: 2740)
- New Text Document.exe (PID: 1924)
- New Text Document.exe (PID: 3412)
- New Text Document.exe (PID: 908)
- rave.exe (PID: 2336)
- RegAsm.exe (PID: 880)
- stan.exe (PID: 896)
- flesh.exe (PID: 764)
- leg221.exe (PID: 1504)
- dd.exe (PID: 3564)
- RegAsm.exe (PID: 2784)
- RegAsm.exe (PID: 5108)
- first.exe (PID: 5376)
- RegAsm.exe (PID: 4884)
- first.exe (PID: 2348)
- oSIrag.exe (PID: 4016)
- New Text Document.exe (PID: 3808)
- New Text Document.exe (PID: 2908)
- New Text Document.exe (PID: 2604)
- client.exe (PID: 3416)
- Windows.exe (PID: 3256)
- chromeupdate.exe (PID: 3556)
- Client-built.exe (PID: 3760)
- Client.exe (PID: 1852)
- jsc.exe (PID: 6716)
Create files in a temporary directory
- New Text Document.exe (PID: 2968)
- tuc5.exe (PID: 3612)
- tuc5.exe (PID: 3896)
- tuc5.tmp (PID: 3828)
- adobe.exe (PID: 3688)
- grace.exe (PID: 4052)
- adobe.exe (PID: 3964)
- adobe.tmp (PID: 1876)
- stan.exe (PID: 896)
- num.exe (PID: 128)
- vLnNHh.exe (PID: 3560)
- rave.exe (PID: 2336)
- RegAsm.exe (PID: 1652)
- dd.exe (PID: 3752)
- first.exe (PID: 5376)
- WerFault.exe (PID: 2196)
- RageMP131.exe (PID: 2316)
- Dctooux.exe (PID: 2336)
- oSIrag.exe (PID: 2080)
- dvchost.exe (PID: 3452)
- client.exe (PID: 3416)
- bin.exe (PID: 2196)
- InstallSetup2.exe (PID: 4556)
- amer.exe (PID: 4120)
- explorhe.exe (PID: 4048)
- vimu.exe (PID: 5380)
- next.exe (PID: 600)
- MartDrum.exe (PID: 8028)
- latestrocki.exe (PID: 6764)
- GorgeousMovement.exe (PID: 6784)
- costa.exe (PID: 3200)
- Fighting.pif (PID: 3712)
- store.exe (PID: 1920)
- univ.exe (PID: 3504)
Creates files or folders in the user directory
- tuc5.tmp (PID: 3828)
- adobe.tmp (PID: 1876)
- t7.exe (PID: 2036)
- RegSvcs.exe (PID: 3768)
- rave.exe (PID: 2336)
- Awwnbpxqsf.exe (PID: 2948)
- 23.exe (PID: 3044)
- stan.exe (PID: 896)
- dd.exe (PID: 3752)
- Dctooux.exe (PID: 2336)
- univ.exe (PID: 3504)
- inte.exe (PID: 3428)
- client.exe (PID: 3416)
- inte.exe (PID: 5356)
- InstallSetup2.exe (PID: 4556)
- bin.exe (PID: 2196)
- inte.exe (PID: 5704)
- explorhe.exe (PID: 4048)
- BroomSetup.exe (PID: 5488)
- clip.exe (PID: 2204)
- Client-built.exe (PID: 3760)
- Fighting.pif (PID: 3712)
- Accommodations.pif (PID: 3668)
Reads mouse settings
- grace.exe (PID: 4052)
- Z7UbUl6TpTWrg8iMRm6f.exe (PID: 2940)
- Z7UbUl6TpTWrg8iMRm6f.exe (PID: 4424)
- networ.exe (PID: 3080)
- go.exe (PID: 3580)
- Accommodations.pif (PID: 3668)
- Fighting.pif (PID: 3712)
Creates files in the program directory
- xdrencodelib.exe (PID: 120)
- stan.exe (PID: 896)
Reads product name
- RegAsm.exe (PID: 1652)
- 2024.exe (PID: 3384)
- rave.exe (PID: 2336)
- stan.exe (PID: 896)
- flesh.exe (PID: 764)
- leg221.exe (PID: 1504)
- RegAsm.exe (PID: 2784)
- RegAsm.exe (PID: 5108)
- RegAsm.exe (PID: 4884)
Reads CPU info
- rave.exe (PID: 2336)
- stan.exe (PID: 896)
Application launched itself
- chrome.exe (PID: 4268)
- chrome.exe (PID: 4280)
- msedge.exe (PID: 4256)
- msedge.exe (PID: 4192)
- msedge.exe (PID: 4136)
- msedge.exe (PID: 4228)
- msedge.exe (PID: 4112)
- chrome.exe (PID: 4292)
- msedge.exe (PID: 4732)
- msedge.exe (PID: 4772)
- msedge.exe (PID: 4156)
- msedge.exe (PID: 4892)
- msedge.exe (PID: 5020)
- msedge.exe (PID: 5072)
- msedge.exe (PID: 5152)
- firefox.exe (PID: 4312)
- firefox.exe (PID: 4648)
- chrome.exe (PID: 5296)
- firefox.exe (PID: 4488)
- chrome.exe (PID: 5408)
- firefox.exe (PID: 5596)
- firefox.exe (PID: 5796)
- chrome.exe (PID: 5484)
- msedge.exe (PID: 3532)
- msedge.exe (PID: 3668)
- msedge.exe (PID: 3528)
- chrome.exe (PID: 2080)
- msedge.exe (PID: 3924)
- firefox.exe (PID: 2324)
- chrome.exe (PID: 3876)
- firefox.exe (PID: 2592)
- msedge.exe (PID: 3640)
- msedge.exe (PID: 3672)
- chrome.exe (PID: 1840)
- firefox.exe (PID: 2380)
- firefox.exe (PID: 2496)
- firefox.exe (PID: 2892)
- firefox.exe (PID: 2448)
Reads the time zone
- runonce.exe (PID: 2164)
Process checks whether UAC notifications are on
- IMEKLMG.EXE (PID: 2276)
- IMEKLMG.EXE (PID: 2284)
Reads security settings of Internet Explorer
- sipnotify.exe (PID: 2100)
Checks transactions between databases Windows and Oracle
- cmstp.exe (PID: 2720)
Drops the executable file immediately after the start
- clip.exe (PID: 2204)
- firefox.exe (PID: 2496)
Executable content was dropped or overwritten
- firefox.exe (PID: 2496)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
AgentTesla
(PID) Process(3768) RegSvcs.exe
Protocolsmtp
Hostmymobileorder.com
Port587
Usernamegrace@mymobileorder.com
PasswordGrace@2023@121
(PID) Process(2776) conhost.exe
Protocolsmtp
Hostmail.officeemailbackup.com
Port587
Usernamesud@officeemailbackup.com
PassworddS,DR,%Ij@uc
AsyncRat
(PID) Process(2036) t7.exe
C2 (1)212.118.52.86
Ports (1)4449
BotnetDefault
VersionVenom RAT + HVNC + Stealer + Grabber v6.0.3
Options
AutoRunfalse
Mutexcwntqnxqwxlfgvwc
InstallFolder%AppData%
BSoDfalse
AntiVMfalse
Certificates
Cert1MIICOTCCAaKgAwIBAgIVAPyfwFFMs6hxoSr1U5gHJmBruaj1MA0GCSqGSIb3DQEBDQUAMGoxGDAWBgNVBAMMD1Zlbm9tUkFUIFNlcnZlcjETMBEGA1UECwwKcXdxZGFuY2h1bjEfMB0GA1UECgwWVmVub21SQVQgQnkgcXdxZGFuY2h1bjELMAkGA1UEBwwCU0gxCzAJBgNVBAYTAkNOMB4XDTIyMDgxNDA5NDEwOVoXDTMzMDUyMzA5NDEwOVowEzERMA8GA1UEAwwIVmVub21SQVQwgZ8wDQYJKoZIhvcN...
Server_SignatureEsahSMpzK5s4VgapwMpLD654HoAv4SdAcVUO/C+DpXdBUyqHC3U0d+h4PhEpSvIRG4VHigcAqrOfNQmtPyAgcOYWRkbdFMrG+381jknRSa2yswXGCJvBjoQDNuZP5XDtr/0dA32CUN8zT/XmBZLnys8xnef2/2TO5MXadYGNqPo=
Keys
AES6588fc4a442b2d5f3a8016b3a95eb825cd0c30770273ee413910085fe77b68a5
SaltVenomRATByVenom
TRiD
| .exe | | | Win32 Executable (generic) (52.9) |
|---|---|---|
| .exe | | | Generic Win/DOS Executable (23.5) |
| .exe | | | DOS Executable Generic (23.5) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2023:10:03 09:51:19+02:00 |
| ImageFileCharacteristics: | Executable, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 14.33 |
| CodeSize: | 214528 |
| InitializedDataSize: | 119296 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x21d50 |
| OSVersion: | 5.1 |
| ImageVersion: | - |
| SubsystemVersion: | 5.1 |
| Subsystem: | Windows GUI |
Total processes
559
Monitored processes
382
Malicious processes
82
Suspicious processes
16
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 120 | "C:\Users\admin\AppData\Local\XDR Encode LIB\xdrencodelib.exe" -i | C:\Users\admin\AppData\Local\XDR Encode LIB\xdrencodelib.exe | tuc5.tmp | ||||||||||||
User: admin Integrity Level: HIGH Description: ExpressCenter Exit code: 0 Version: 1, 20, 0, 1 Modules
| |||||||||||||||
| 128 | "C:\Users\admin\Desktop\a\num.exe" | C:\Users\admin\Desktop\a\num.exe | New Text Document.exe | ||||||||||||
User: admin Company: MAGIX Computer Products Intl. Co. Integrity Level: MEDIUM Description: VEGAS Pro Exit code: 0 Version: 14.0.0.211 Modules
| |||||||||||||||
| 584 | "C:\Users\admin\Desktop\a\288c47bbc1871b439df19ff4df68f0766.exe" | C:\Users\admin\Desktop\a\288c47bbc1871b439df19ff4df68f0766.exe | — | New Text Document.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 600 | "C:\Users\admin\Desktop\a\next.exe" | C:\Users\admin\Desktop\a\next.exe | New Text Document.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 680 | C:\Users\admin\Desktop\a\Awwnbpxqsf.exe | C:\Users\admin\Desktop\a\Awwnbpxqsf.exe | — | Awwnbpxqsf.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 4294967295 Version: 1.0.0.0 Modules
| |||||||||||||||
| 764 | "C:\Users\admin\Desktop\a\flesh.exe" | C:\Users\admin\Desktop\a\flesh.exe | New Text Document.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 880 | "C:\Windows\Microsoft.NET\Framework\v4.0.30319\RegAsm.exe" | C:\Windows\Microsoft.NET\Framework\v4.0.30319\RegAsm.exe | crypted_d786fd3e.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft .NET Assembly Registration Utility Exit code: 0 Version: 4.8.3761.0 built by: NET48REL1 Modules
| |||||||||||||||
| 884 | "C:\Users\admin\Desktop\a\Zjqkz.exe" | C:\Users\admin\Desktop\a\Zjqkz.exe | — | New Text Document.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 896 | "C:\Users\admin\Desktop\a\stan.exe" | C:\Users\admin\Desktop\a\stan.exe | New Text Document.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 900 | "C:\Users\admin\Desktop\a\StealerClient_Cpp_1_3.exe" | C:\Users\admin\Desktop\a\StealerClient_Cpp_1_3.exe | — | New Text Document.exe | |||||||||||
User: admin Company: Oracle Integrity Level: MEDIUM Description: VirtualBox ExtPack Helper Exit code: 0 Version: 7.0.10.8379 Modules
| |||||||||||||||
Total events
207 984
Read events
206 456
Write events
1 487
Delete events
41
Modification events
| (PID) Process: | (2396) New Text Document.bin.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (2396) New Text Document.bin.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (2396) New Text Document.bin.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (2396) New Text Document.bin.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (2396) New Text Document.bin.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (2396) New Text Document.bin.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (2672) New Text Document.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2372) New Text Document.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2968) New Text Document.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (1404) New Text Document.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
Executable files
193
Suspicious files
995
Text files
227
Unknown types
7
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2672 | New Text Document.exe | C:\Users\admin\Desktop\a\vLnNHh.exe | executable | |
MD5:38EA9A029DFF6005919E4F195B275A69 | SHA256:A7D2010888096F3A0AD884B423EBE9432C13A9ED8C1AA81DE541E9FD0838192F | |||
| 2968 | New Text Document.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\77EC63BDA74BD0D0E0426DC8F8008506 | compressed | |
MD5:AC05D27423A85ADC1622C714F2CB6184 | SHA256:C6456E12E5E53287A547AF4103E0397CB9697E466CF75844312DC296D43D144D | |||
| 3828 | tuc5.tmp | C:\Users\admin\AppData\Local\Temp\is-0PECF.tmp\_isetup\_RegDLL.tmp | executable | |
MD5:0EE914C6F0BB93996C75941E1AD629C6 | SHA256:4DC09BAC0613590F1FAC8771D18AF5BE25A1E1CB8FDBF4031AA364F3057E74A2 | |||
| 2396 | New Text Document.bin.exe | C:\Users\admin\Desktop\Пароли Chrome.csv | binary | |
MD5:64F50AFB35DD16EE46F187015CEE84CE | SHA256:C2D389870DE77426A31A8C478E0FDDCBBEA7A3733B453806317914E6F946EA91 | |||
| 2968 | New Text Document.exe | C:\Users\admin\Desktop\a\conhost.exe | executable | |
MD5:36CE48E31D675698D3DE4FD0C982610F | SHA256:070B9D022843AC420D8BDFCB8F91D5D5DACE6DDC452CFF9E0D3F85D564030D31 | |||
| 2968 | New Text Document.exe | C:\Users\admin\AppData\Local\Temp\Cab587A.tmp | compressed | |
MD5:AC05D27423A85ADC1622C714F2CB6184 | SHA256:C6456E12E5E53287A547AF4103E0397CB9697E466CF75844312DC296D43D144D | |||
| 1404 | New Text Document.exe | C:\Users\admin\Desktop\a\tuc5.exe | executable | |
MD5:5E6D8C73D07FA0303D7E6DDA244C0189 | SHA256:BCE43A791F179892491AF55D87ABF9CB56DA17C1BC81AF2FC68B5E903A2CBB29 | |||
| 2372 | New Text Document.exe | C:\Users\admin\Desktop\a\grace.exe | executable | |
MD5:2EB93DAECF86D6E3748F12009553E71E | SHA256:78AADD377E0F48690C32AEB0F5482A3EF4F1E4EA3675B442C46AB7298BEF68D1 | |||
| 2968 | New Text Document.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\77EC63BDA74BD0D0E0426DC8F8008506 | binary | |
MD5:5D32C74B6C6E12433E1CBE041370B635 | SHA256:19B877E15403A0BEB5E44D79082A680AD31CD11694678BA0FA866124358DFDA7 | |||
| 2396 | New Text Document.bin.exe | C:\Users\admin\Desktop\New Text Document.exe | executable | |
MD5:A239A27C2169AF388D4F5BE6B52F272C | SHA256:98E895F711226A32BFAB152E224279D859799243845C46E550C2D32153C619FC | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
168
TCP/UDP connections
457
DNS requests
331
Threats
633
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
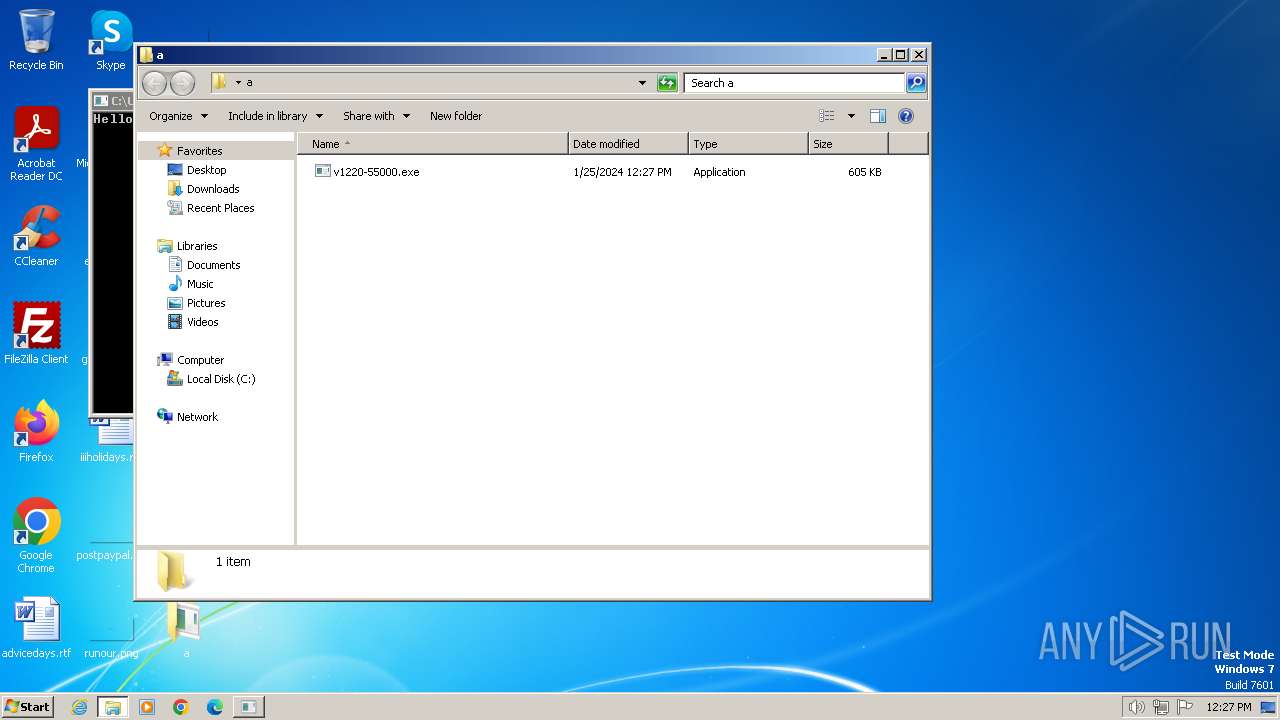
2672 | New Text Document.exe | GET | 200 | 64.31.22.34:80 | http://ftsolutions.com.pk/v1220-55000.exe | unknown | executable | 5.44 Mb | unknown |
2372 | New Text Document.exe | GET | 200 | 104.21.80.24:80 | http://silco.ayazprak.com/order/tuc5.exe | unknown | executable | 3.50 Mb | unknown |
2968 | New Text Document.exe | GET | 200 | 107.175.243.133:80 | http://107.175.243.133/4030/conhost.exe | unknown | executable | 331 Kb | unknown |
2968 | New Text Document.exe | GET | 200 | 93.184.221.240:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab?e5ea96a1612133ed | unknown | compressed | 65.2 Kb | unknown |
2968 | New Text Document.exe | GET | 200 | 109.107.182.3:80 | http://109.107.182.3/lego/gold1201001.exe | unknown | executable | 1.25 Mb | unknown |
2672 | New Text Document.exe | GET | 200 | 78.138.46.125:80 | http://78.138.46.125/grace.exe | unknown | executable | 1.18 Mb | unknown |
1404 | New Text Document.exe | GET | 200 | 109.107.182.3:80 | http://109.107.182.3/lego/alex.exe | unknown | executable | 1.73 Mb | unknown |
2672 | New Text Document.exe | GET | 200 | 109.107.182.3:80 | http://109.107.182.3/lego/Loader.exe | unknown | executable | 3.51 Mb | unknown |
2372 | New Text Document.exe | GET | 200 | 109.107.182.3:80 | http://109.107.182.3/lego/TrueCrypt_NKwtUN.exe | unknown | executable | 3.17 Mb | unknown |
1404 | New Text Document.exe | GET | 200 | 109.107.182.3:80 | http://109.107.182.3/lego/swizzy.exe | unknown | executable | 411 Kb | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
2672 | New Text Document.exe | 151.101.2.49:443 | urlhaus.abuse.ch | FASTLY | US | unknown |
2672 | New Text Document.exe | 64.31.22.34:80 | ftsolutions.com.pk | LIMESTONENETWORKS | US | unknown |
1404 | New Text Document.exe | 151.101.2.49:443 | urlhaus.abuse.ch | FASTLY | US | unknown |
2372 | New Text Document.exe | 151.101.2.49:443 | urlhaus.abuse.ch | FASTLY | US | unknown |
2372 | New Text Document.exe | 104.21.80.24:80 | silco.ayazprak.com | CLOUDFLARENET | — | unknown |
2968 | New Text Document.exe | 151.101.2.49:443 | urlhaus.abuse.ch | FASTLY | US | unknown |
2968 | New Text Document.exe | 107.175.243.133:80 | — | AS-COLOCROSSING | US | unknown |
1404 | New Text Document.exe | 104.21.15.216:80 | ok.spartabig.com | CLOUDFLARENET | — | unknown |
2968 | New Text Document.exe | 144.76.136.153:443 | transfer.sh | Hetzner Online GmbH | DE | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
urlhaus.abuse.ch |
| whitelisted |
ftsolutions.com.pk |
| unknown |
silco.ayazprak.com |
| unknown |
ok.spartabig.com |
| unknown |
transfer.sh |
| whitelisted |
ctldl.windowsupdate.com |
| whitelisted |
api.ipify.org |
| shared |
github.com |
| shared |
raw.githubusercontent.com |
| shared |
ji.alie3ksgbb.com |
| unknown |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2672 | New Text Document.exe | Potential Corporate Privacy Violation | AV POLICY HTTP request for .exe file with no User-Agent |
2672 | New Text Document.exe | Potential Corporate Privacy Violation | ET POLICY PE EXE or DLL Windows file download HTTP |
2672 | New Text Document.exe | Potentially Bad Traffic | ET INFO Executable Retrieved With Minimal HTTP Headers - Potential Second Stage Download |
2372 | New Text Document.exe | Potential Corporate Privacy Violation | AV POLICY HTTP request for .exe file with no User-Agent |
2372 | New Text Document.exe | Potentially Bad Traffic | ET MALWARE Terse alphanumeric executable downloader high likelihood of being hostile |
2372 | New Text Document.exe | Potential Corporate Privacy Violation | ET POLICY PE EXE or DLL Windows file download HTTP |
2372 | New Text Document.exe | Potentially Bad Traffic | ET INFO Executable Retrieved With Minimal HTTP Headers - Potential Second Stage Download |
2372 | New Text Document.exe | Misc activity | ET INFO EXE - Served Attached HTTP |
1404 | New Text Document.exe | Potential Corporate Privacy Violation | AV POLICY HTTP request for .exe file with no User-Agent |
1404 | New Text Document.exe | Potential Corporate Privacy Violation | ET POLICY PE EXE or DLL Windows file download HTTP |
13 ETPRO signatures available at the full report
Process | Message |
|---|---|
rave.exe | NtDebugWriter |
rave.exe | Facepalm |
stan.exe | NtDebugWriter |
stan.exe | Facepalm |