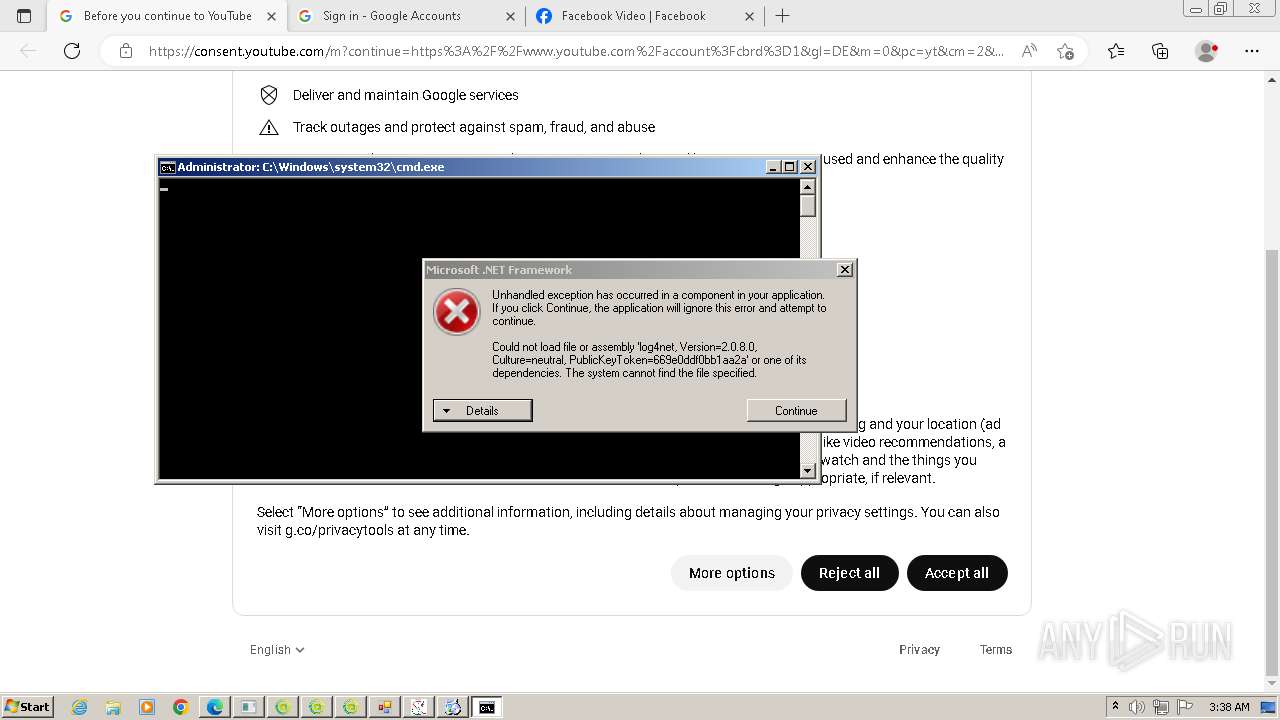
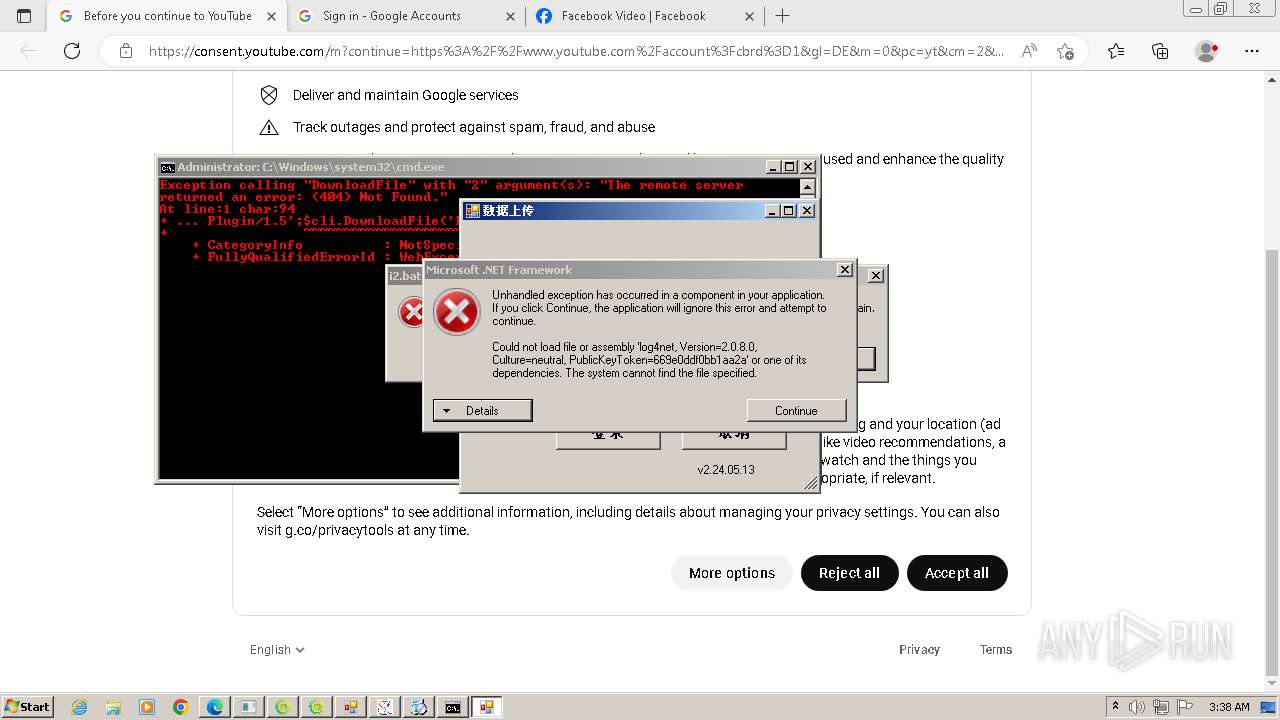
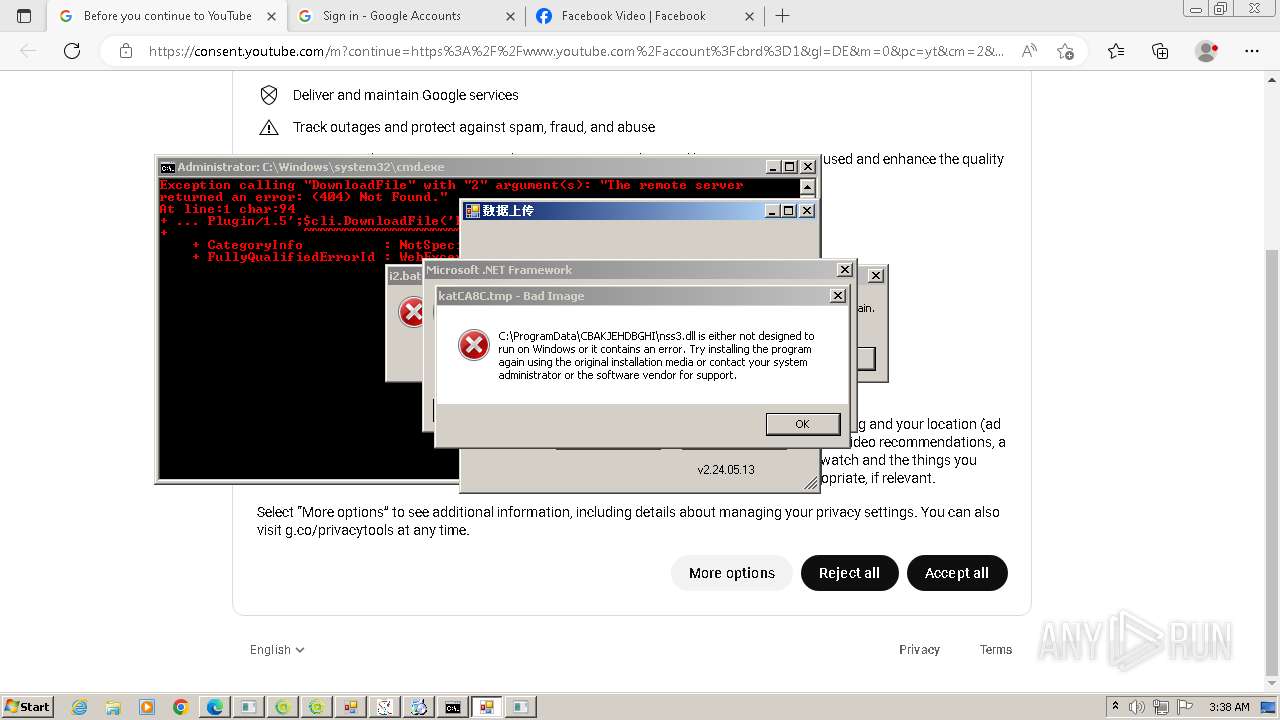
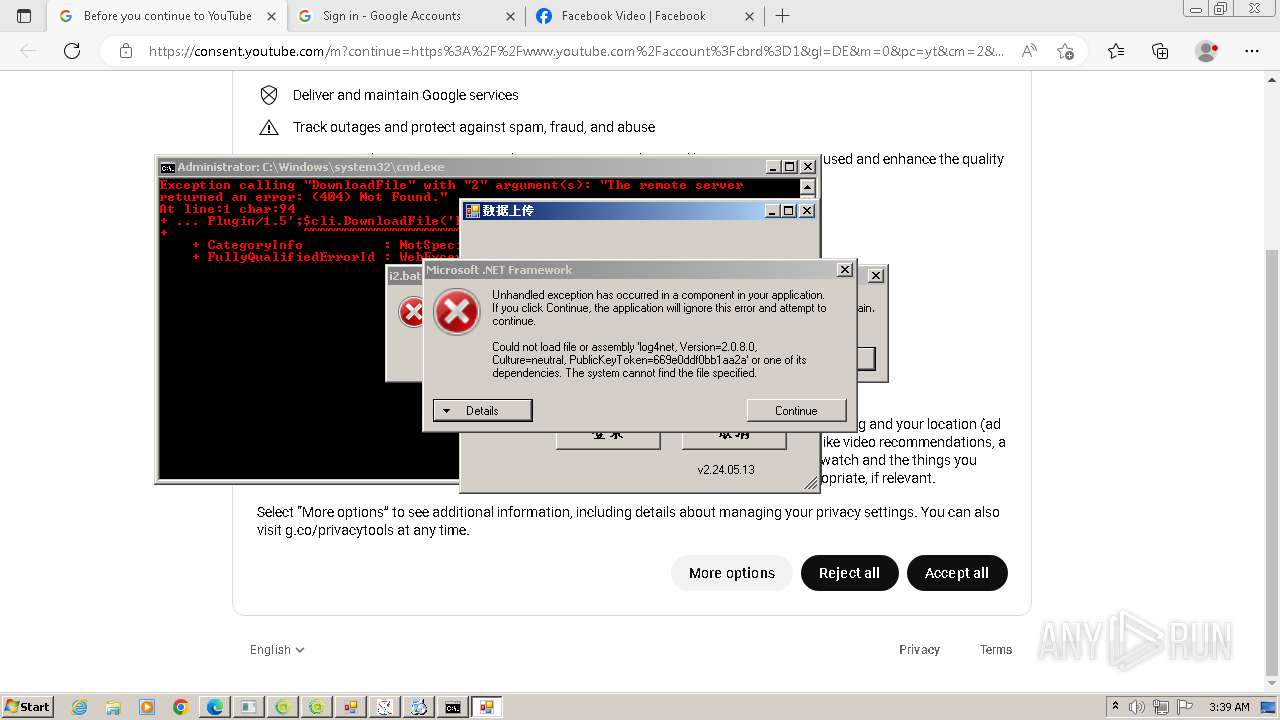
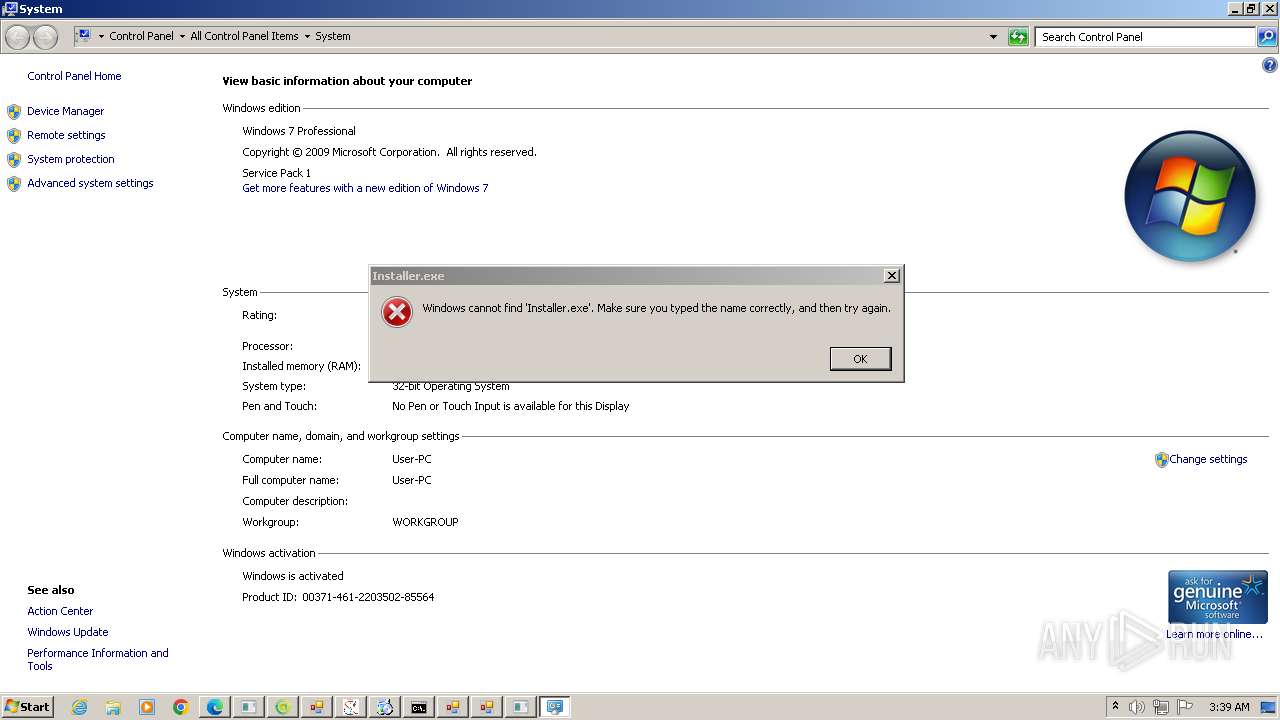
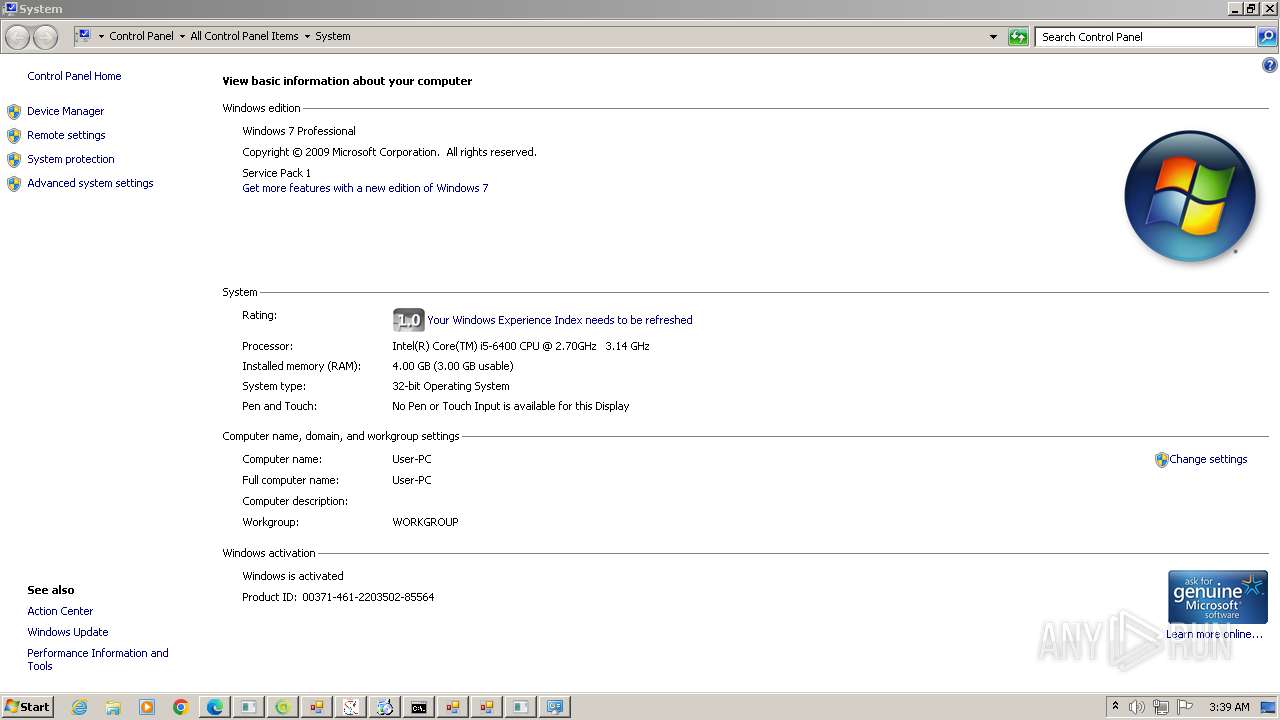
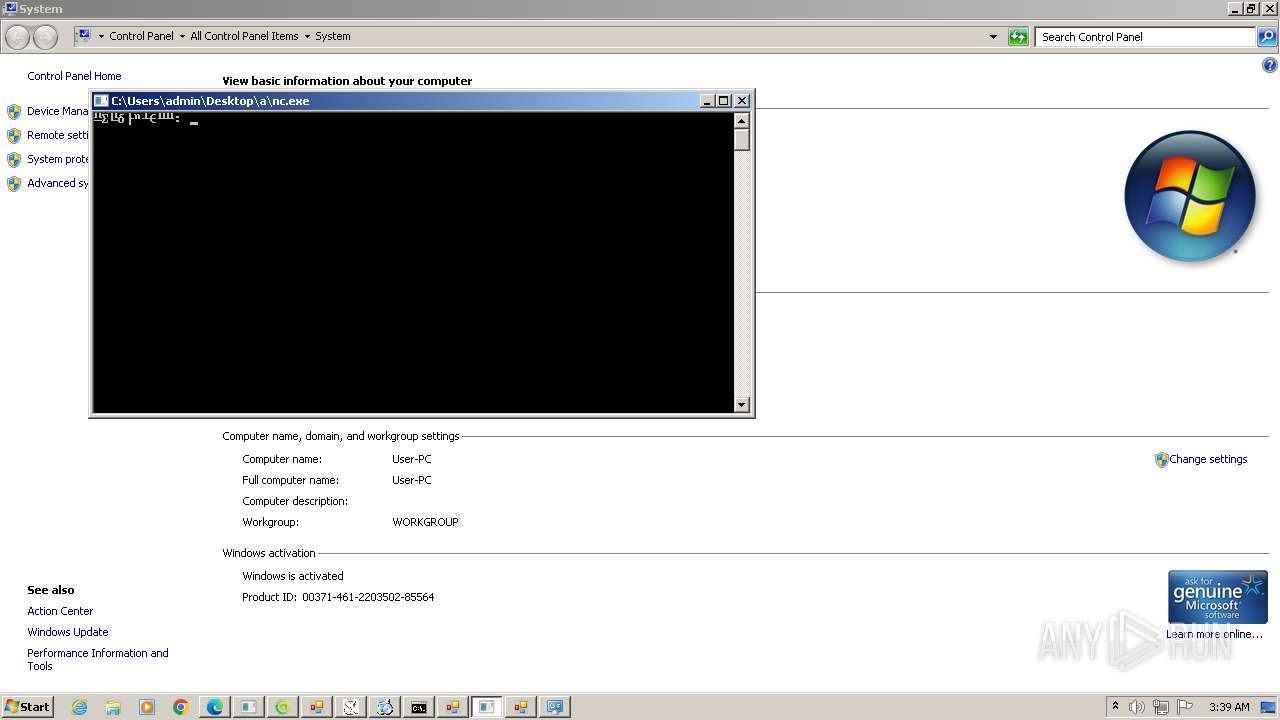
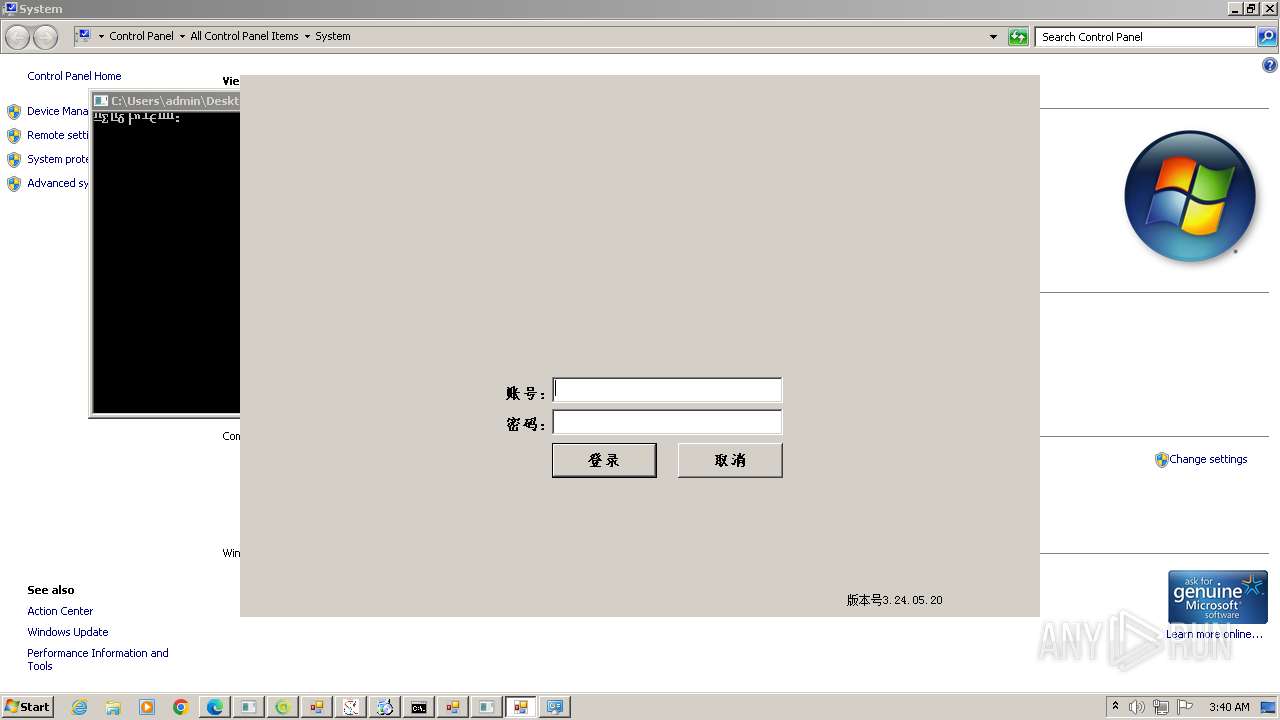
| File name: | New Text Document.bin.exe |
| Full analysis: | https://app.any.run/tasks/75ed53aa-a3fc-4c47-aafe-39877eb1e7c8 |
| Verdict: | Malicious activity |
| Threats: | Adware is a form of malware that targets users with unwanted advertisements, often disrupting their browsing experience. It typically infiltrates systems through software bundling, malicious websites, or deceptive downloads. Once installed, it may track user activity, collect sensitive data, and display intrusive ads, including pop-ups or banners. Some advanced adware variants can bypass security measures and establish persistence on devices, making removal challenging. Additionally, adware can create vulnerabilities that other malware can exploit, posing a significant risk to user privacy and system security. |
| Analysis date: | May 26, 2024, 02:35:47 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | 0B0D247AA1F24C2F5867B3BF29F69450 |
| SHA1: | 48DE9F34226FD7F637E2379365BE035AF5C0DF1A |
| SHA256: | A6E7292E734C3A15CFA654BBA8DEA72A2F55F1C24CF6BBDC2FD7E63887E9315A |
| SSDEEP: | 12288:dcgCzNHJj96xfKJStJkRm3bYXob0AnmFMcaGQxkZVVVVVVVVVAtVVVUvqGV:UQKgLIQmFuGQxklvqO |
MALICIOUS
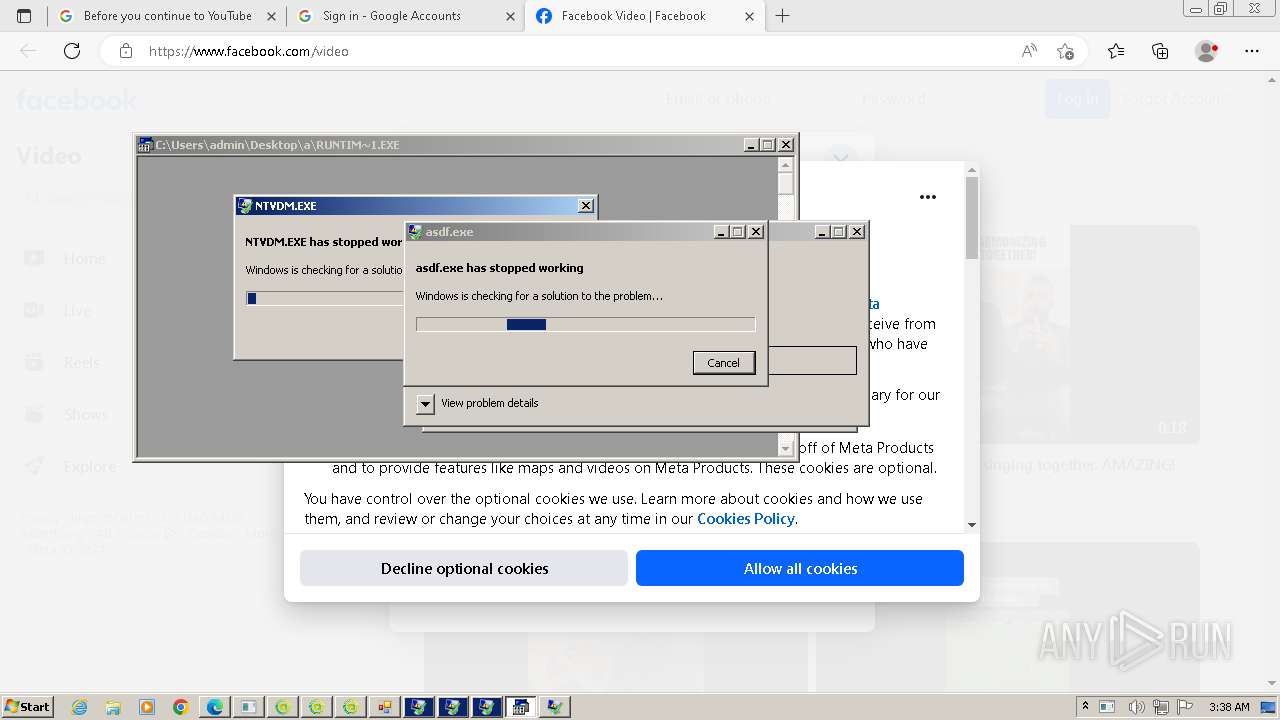
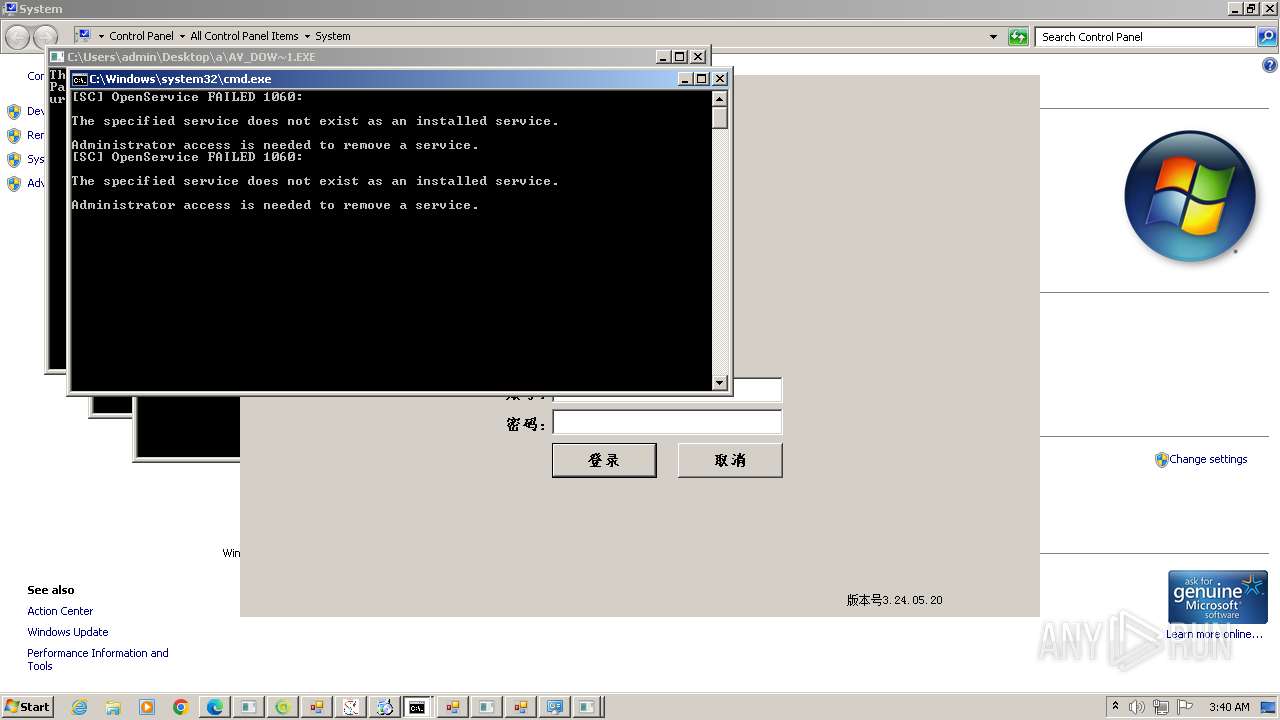
Drops the executable file immediately after the start
- New Text Document.bin.exe (PID: 3976)
- STHealthClient.exe (PID: 1620)
- New Text Document.exe (PID: 2032)
- rtx.exe (PID: 3392)
- Bypass3_Pure_Mode.exe (PID: 2484)
- csrss.exe (PID: 1280)
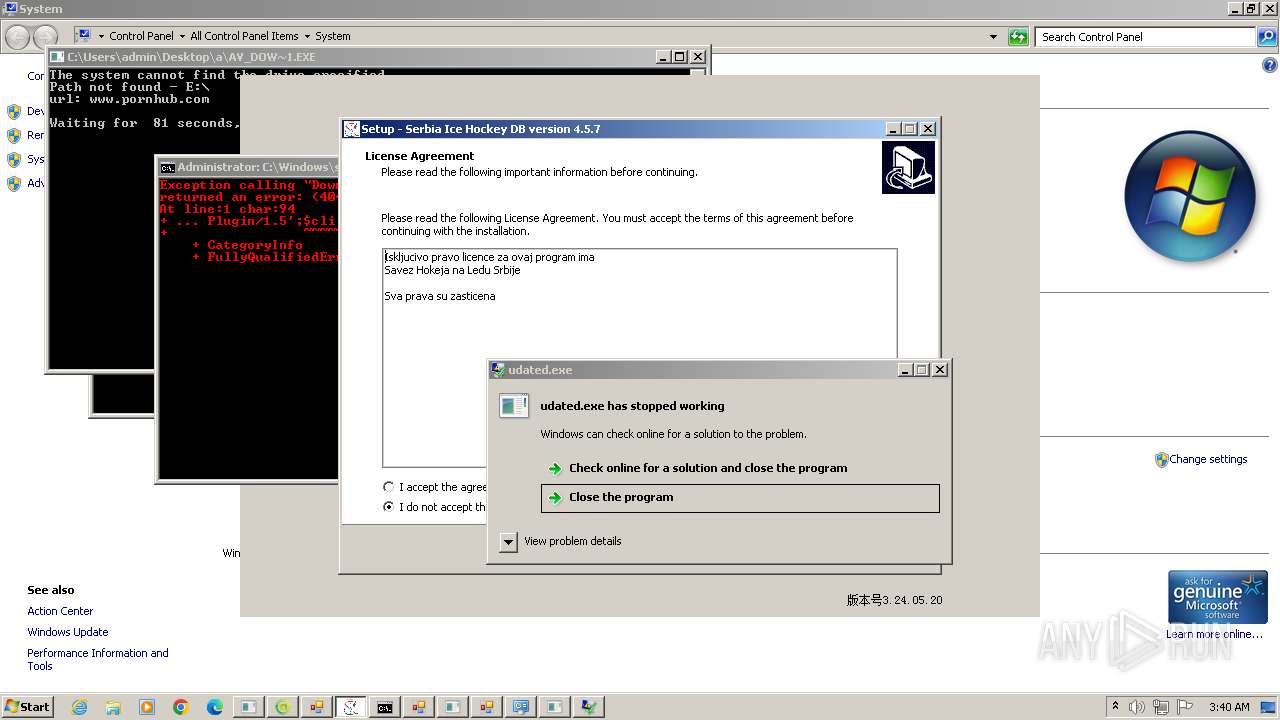
- SrbijaSetupHokej.exe (PID: 2940)
- sharonzx.exe (PID: 2616)
- XClient.exe (PID: 2832)
- SrbijaSetupHokej.exe (PID: 1128)
- ChromeSetup.exe (PID: 2072)
- sharonzx.exe (PID: 4040)
- GoogleUpdate.exe (PID: 2992)
- GoogleUpdateSetup.exe (PID: 2304)
- crt.exe (PID: 4160)
- svchost.exe (PID: 1880)
- crt.exe (PID: 4840)
- crt.tmp (PID: 4880)
- cdplayer.exe (PID: 5116)
- sdf34ert3etgrthrthfghfghjfgh.exe (PID: 5620)
- conhost.exe (PID: 5352)
- vpn-1002.exe (PID: 4512)
- o2i3jroi23joj23ikrjokij3oroi.exe (PID: 6000)
- tdrpload.exe (PID: 4608)
- katCA8C.tmp (PID: 5684)
- 472111564.exe (PID: 6056)
- Pirate_24S.exe (PID: 4388)
- cmd.exe (PID: 5452)
- 222.exe (PID: 4984)
- 888.exe (PID: 5648)
- 109.0.5414.120_chrome_installer.exe (PID: 5952)
- Discord.exe (PID: 4640)
- yar.exe (PID: 4924)
- install.exe (PID: 3756)
- e_win.exe (PID: 4240)
- setup_1715277229.6072824.exe (PID: 4952)
- pojgysef.exe (PID: 4388)
- work.exe (PID: 5760)
- setup.exe (PID: 4380)
DCRAT has been detected (YARA)
- New Text Document.exe (PID: 2032)
HAUSBOMBER has been detected (YARA)
- New Text Document.exe (PID: 2032)
REDLINE has been detected (YARA)
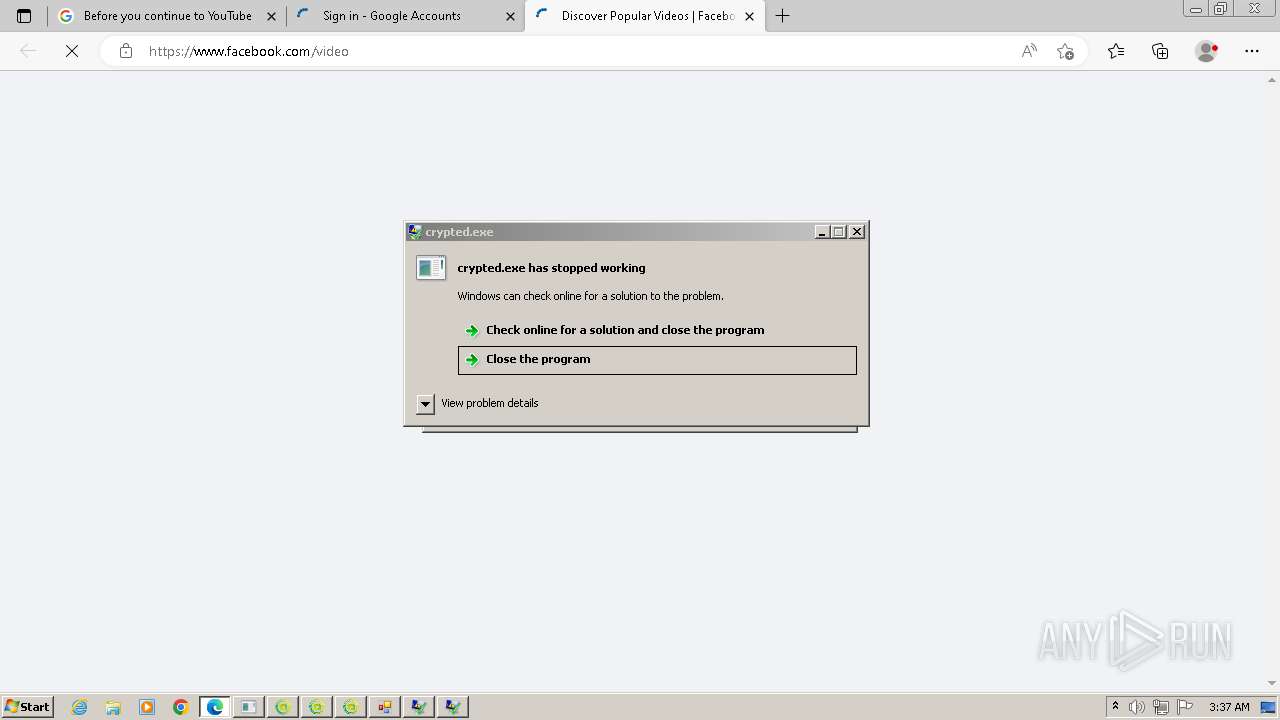
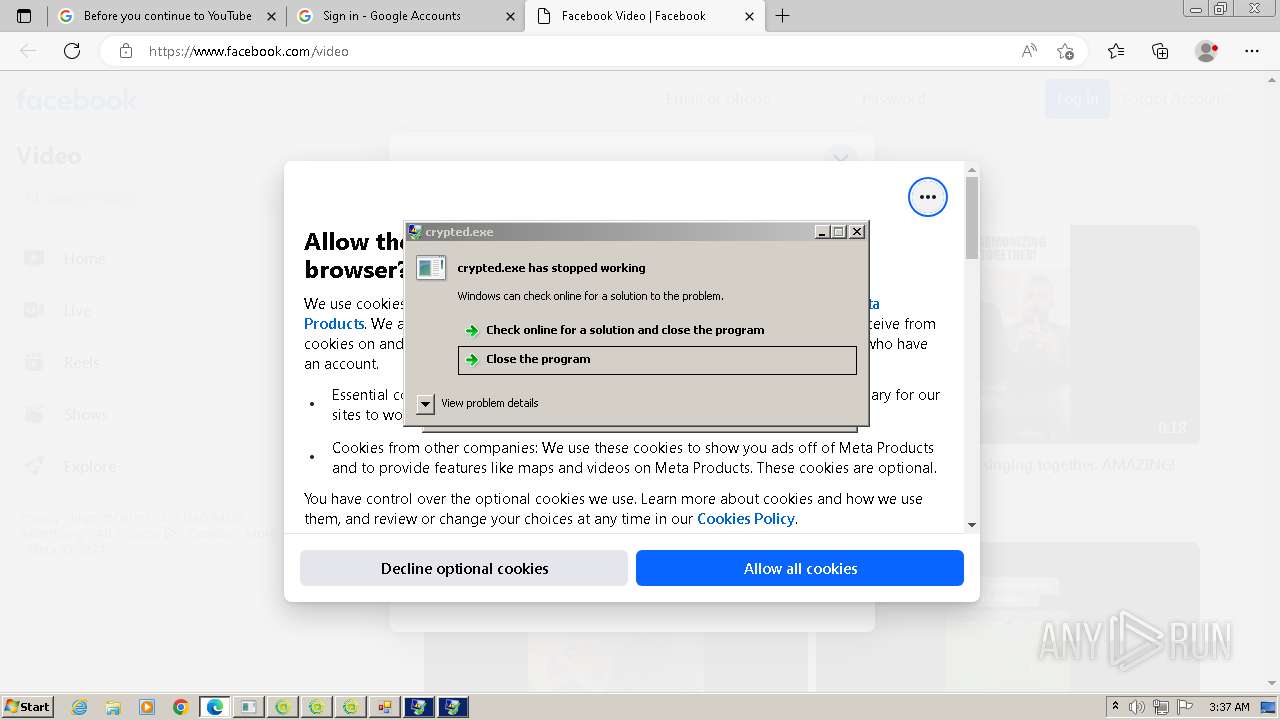
- crypted.exe (PID: 1980)
Actions looks like stealing of personal data
- RegSvcs.exe (PID: 3008)
- RegSvcs.exe (PID: 824)
- RegSvcs.exe (PID: 2368)
- sharonzx.exe (PID: 4040)
- RegSvcs.exe (PID: 1604)
- RegSvcs.exe (PID: 3640)
- netbtugc.exe (PID: 3412)
- gHIvTf22qvmZjum.exe (PID: 5868)
- katD46F.tmp (PID: 4552)
- Discord.exe (PID: 4640)
- New Text Document.exe (PID: 2032)
- katCA8C.tmp (PID: 5684)
- taskhostw.exe (PID: 5816)
- MSBuild.exe (PID: 4248)
Steals credentials from Web Browsers
- RegSvcs.exe (PID: 3008)
- RegSvcs.exe (PID: 824)
- RegSvcs.exe (PID: 2368)
- sharonzx.exe (PID: 4040)
- RegSvcs.exe (PID: 1604)
- RegSvcs.exe (PID: 3640)
- katCA8C.tmp (PID: 5684)
- gHIvTf22qvmZjum.exe (PID: 5868)
- MSBuild.exe (PID: 4248)
Changes the autorun value in the registry
- rtx.exe (PID: 3392)
- tdrpload.exe (PID: 4608)
- 472111564.exe (PID: 6056)
- Discord.exe (PID: 4640)
- yar.exe (PID: 4924)
- setup.exe (PID: 4380)
AGENTTESLA has been detected (YARA)
- RegSvcs.exe (PID: 824)
- RegSvcs.exe (PID: 2368)
- RegSvcs.exe (PID: 3640)
- gHIvTf22qvmZjum.exe (PID: 5868)
AGENTTESLA has been detected (SURICATA)
- RegSvcs.exe (PID: 2368)
- gHIvTf22qvmZjum.exe (PID: 5868)
Connects to the CnC server
- RegSvcs.exe (PID: 2368)
- sharonzx.exe (PID: 4040)
- sysblardsv.exe (PID: 5060)
- New Text Document.exe (PID: 2032)
- gHIvTf22qvmZjum.exe (PID: 5868)
- syslmgrsvc.exe (PID: 3268)
- MSBuild.exe (PID: 4248)
- cdplayer.exe (PID: 5224)
Create files in the Startup directory
- XClient.exe (PID: 2832)
- svchost.exe (PID: 1880)
- Discord.exe (PID: 4640)
FORMBOOK has been detected (YARA)
- rooma.exe (PID: 1116)
- netbtugc.exe (PID: 3412)
Uses Task Scheduler to run other applications
- sharonzx.exe (PID: 2616)
- Discord.exe (PID: 4640)
- yar.exe (PID: 4924)
XWORM has been detected (YARA)
- XClient.exe (PID: 2832)
- csrss.exe (PID: 1280)
- svchost.exe (PID: 1880)
- Discord.exe (PID: 4640)
Lokibot is detected
- sharonzx.exe (PID: 4040)
- sharonzx.exe (PID: 4040)
LOKIBOT has been detected (SURICATA)
- sharonzx.exe (PID: 4040)
LOKIBOT has been detected (YARA)
- sharonzx.exe (PID: 4040)
ASYNCRAT has been detected (YARA)
- vax.exe (PID: 2320)
- my.exe (PID: 4480)
Steals credentials
- netbtugc.exe (PID: 3412)
- katCA8C.tmp (PID: 5684)
Starts CMD.EXE for self-deleting
- inte.exe (PID: 6028)
- katCA8C.tmp (PID: 5684)
- univ.exe (PID: 6084)
- univ.exe (PID: 2828)
FORMBOOK has been detected (SURICATA)
- New Text Document.exe (PID: 2032)
Changes appearance of the Explorer extensions
- sysblardsv.exe (PID: 5060)
- syslmgrsvc.exe (PID: 3268)
Changes Security Center notification settings
- sysblardsv.exe (PID: 5060)
- syslmgrsvc.exe (PID: 3268)
Changes the Windows auto-update feature
- sysblardsv.exe (PID: 5060)
- syslmgrsvc.exe (PID: 3268)
Creates a writable file in the system directory
- cmd.exe (PID: 5452)
PHORPIEX has been detected (SURICATA)
- syslmgrsvc.exe (PID: 3268)
GCLEANER has been detected (SURICATA)
- univ.exe (PID: 6084)
- univ.exe (PID: 2828)
Deletes shadow copies
- cmd.exe (PID: 5160)
- cmd.exe (PID: 5676)
- cmd.exe (PID: 5384)
Renames files like ransomware
- e_win.exe (PID: 4240)
UAC/LUA settings modification
- reg.exe (PID: 4204)
Starts CertUtil for downloading files
- cmd.exe (PID: 4228)
Uses Task Scheduler to autorun other applications
- cmd.exe (PID: 4228)
METASTEALER has been detected (SURICATA)
- MSBuild.exe (PID: 4248)
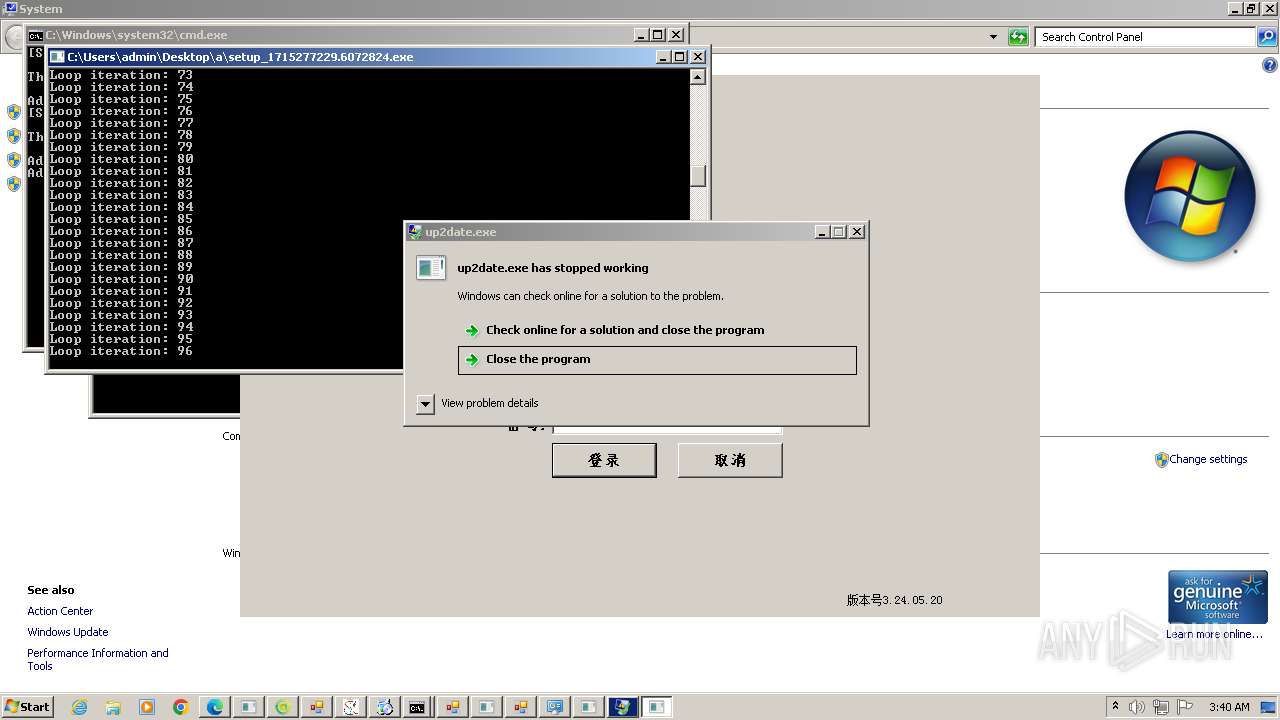
LUMMA has been detected (YARA)
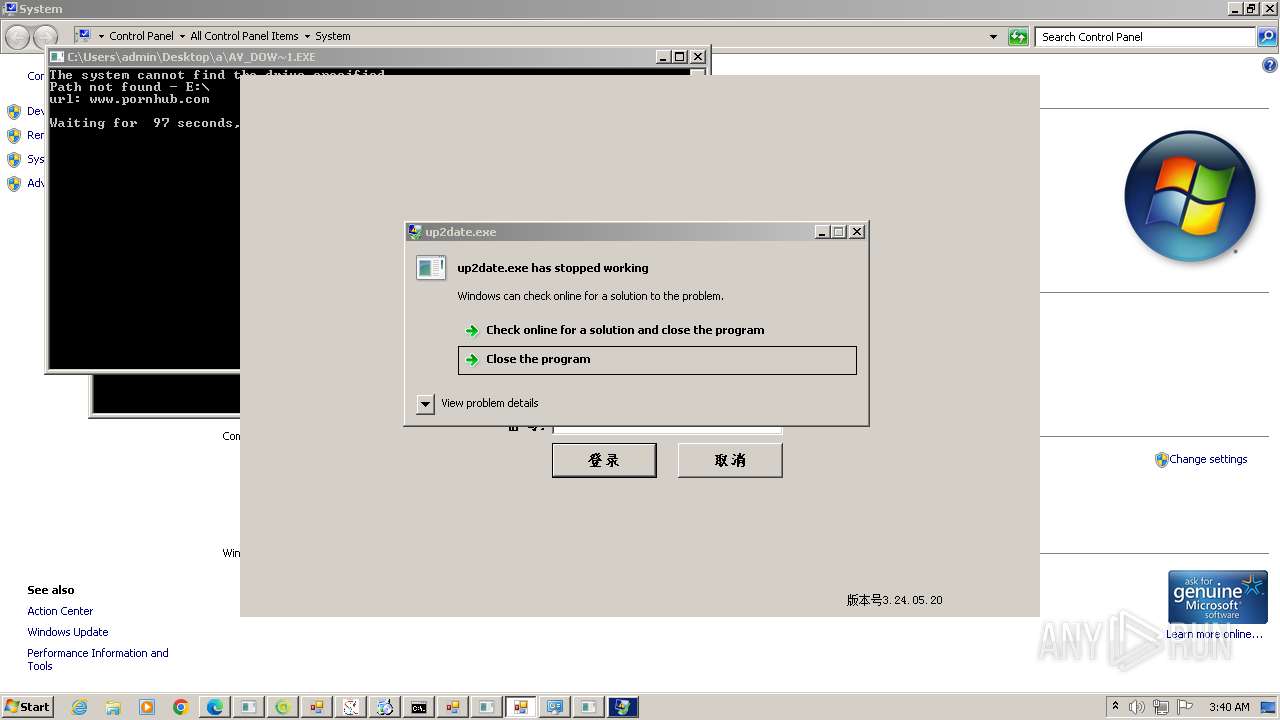
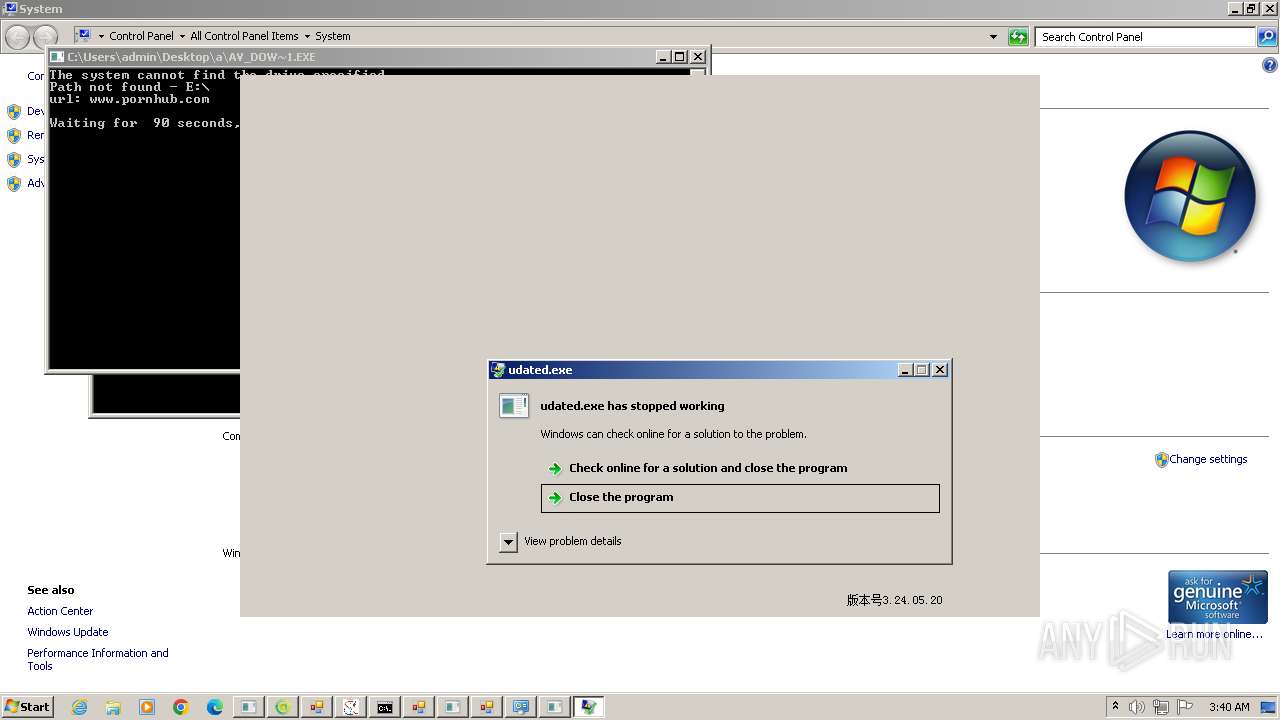
- up2date.exe (PID: 4256)
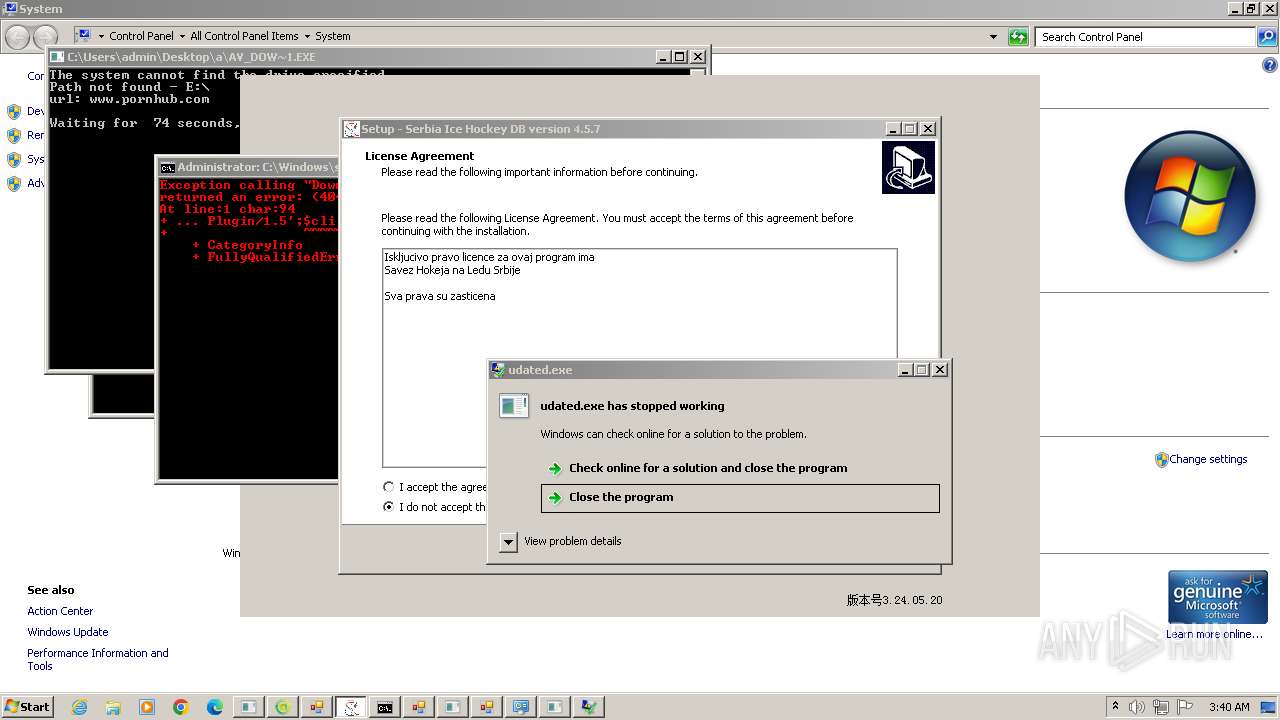
- udated.exe (PID: 5144)
Known privilege escalation attack
- dllhost.exe (PID: 8184)
SOCKS5SYSTEMZ has been detected (SURICATA)
- cdplayer.exe (PID: 5224)
SUSPICIOUS
Executable content was dropped or overwritten
- New Text Document.bin.exe (PID: 3976)
- New Text Document.exe (PID: 2032)
- STHealthClient.exe (PID: 1620)
- rtx.exe (PID: 3392)
- Bypass3_Pure_Mode.exe (PID: 2484)
- csrss.exe (PID: 1280)
- XClient.exe (PID: 2832)
- SrbijaSetupHokej.exe (PID: 2940)
- sharonzx.exe (PID: 2616)
- SrbijaSetupHokej.exe (PID: 1128)
- ChromeSetup.exe (PID: 2072)
- sharonzx.exe (PID: 4040)
- GoogleUpdateSetup.exe (PID: 2304)
- GoogleUpdate.exe (PID: 2992)
- netbtugc.exe (PID: 3412)
- crt.exe (PID: 4160)
- svchost.exe (PID: 1880)
- crt.exe (PID: 4840)
- crt.tmp (PID: 4880)
- cdplayer.exe (PID: 5116)
- sdf34ert3etgrthrthfghfghjfgh.exe (PID: 5620)
- conhost.exe (PID: 5352)
- vpn-1002.exe (PID: 4512)
- o2i3jroi23joj23ikrjokij3oroi.exe (PID: 6000)
- tdrpload.exe (PID: 4608)
- katCA8C.tmp (PID: 5684)
- 472111564.exe (PID: 6056)
- cmd.exe (PID: 5452)
- Pirate_24S.exe (PID: 4388)
- 222.exe (PID: 4984)
- 888.exe (PID: 5648)
- 109.0.5414.120_chrome_installer.exe (PID: 5952)
- Discord.exe (PID: 4640)
- yar.exe (PID: 4924)
- install.exe (PID: 3756)
- setup_1715277229.6072824.exe (PID: 4952)
- pojgysef.exe (PID: 4388)
- work.exe (PID: 5760)
- setup.exe (PID: 4380)
Potential Corporate Privacy Violation
- New Text Document.exe (PID: 2032)
- rtx.exe (PID: 3392)
- certutil.exe (PID: 5092)
Reads security settings of Internet Explorer
- New Text Document.bin.exe (PID: 3976)
- New Text Document.exe (PID: 2032)
- Bypass3_Pure_Mode.exe (PID: 2484)
- sharonzx.exe (PID: 2616)
- katCA8C.tmp (PID: 5684)
- conhost.exe (PID: 5352)
- inte.exe (PID: 6028)
- vpn-1002.exe (PID: 4512)
- sysblardsv.exe (PID: 5060)
- katD46F.tmp (PID: 4552)
- Pirate_24S.exe (PID: 4388)
- 222.exe (PID: 4984)
- syslmgrsvc.exe (PID: 3268)
- univ.exe (PID: 6084)
- 888.exe (PID: 5648)
- univ.exe (PID: 2828)
- Discord.exe (PID: 4640)
- e_win.exe (PID: 4240)
- yar.exe (PID: 4924)
- f.exe (PID: 2328)
- install.exe (PID: 3756)
- GameService.exe (PID: 5364)
- GameService.exe (PID: 5700)
- GameService.exe (PID: 4284)
- GameService.exe (PID: 5760)
- GameService.exe (PID: 4712)
- GameService.exe (PID: 4204)
- GameService.exe (PID: 5120)
- GameService.exe (PID: 5812)
- pojgysef.exe (PID: 4388)
- work.exe (PID: 5760)
- cdplayer.exe (PID: 5224)
Reads Internet Explorer settings
- New Text Document.bin.exe (PID: 3976)
Reads the Internet Settings
- New Text Document.bin.exe (PID: 3976)
- New Text Document.exe (PID: 2032)
- STHealthClient.exe (PID: 1620)
- go.exe (PID: 2368)
- RegSvcs.exe (PID: 3008)
- RegSvcs.exe (PID: 3992)
- Bypass3_Pure_Mode.exe (PID: 2484)
- RegSvcs.exe (PID: 2368)
- XClient.exe (PID: 2832)
- csrss.exe (PID: 1280)
- sharonzx.exe (PID: 4040)
- sharonzx.exe (PID: 2616)
- GoogleUpdate.exe (PID: 2424)
- RegSvcs.exe (PID: 1604)
- svchost.exe (PID: 1880)
- netbtugc.exe (PID: 3412)
- katCA8C.tmp (PID: 5684)
- conhost.exe (PID: 5352)
- inte.exe (PID: 6028)
- vpn-1002.exe (PID: 4512)
- cmd.exe (PID: 5856)
- powershell.exe (PID: 4568)
- cmd.exe (PID: 4584)
- powershell.exe (PID: 5184)
- gHIvTf22qvmZjum.exe (PID: 5868)
- sysblardsv.exe (PID: 5060)
- cmd.exe (PID: 992)
- katD46F.tmp (PID: 4552)
- wscript.exe (PID: 5448)
- Pirate_24S.exe (PID: 4388)
- regedt32.exe (PID: 4936)
- syslmgrsvc.exe (PID: 3268)
- 222.exe (PID: 4984)
- cmd.exe (PID: 4816)
- regedt32.exe (PID: 5968)
- univ.exe (PID: 6084)
- 888.exe (PID: 5648)
- cmd.exe (PID: 5040)
- univ.exe (PID: 2828)
- Discord.exe (PID: 4640)
- yar.exe (PID: 4924)
- f.exe (PID: 2328)
- e_win.exe (PID: 4240)
- mshta.exe (PID: 5664)
- install.exe (PID: 3756)
- GameService.exe (PID: 5364)
- certutil.exe (PID: 5092)
- GameService.exe (PID: 5700)
- GameService.exe (PID: 4284)
- GameService.exe (PID: 5760)
- GameService.exe (PID: 4712)
- certutil.exe (PID: 6016)
- GameService.exe (PID: 4204)
- GameService.exe (PID: 5120)
- MSBuild.exe (PID: 4248)
- GameService.exe (PID: 5812)
- pojgysef.exe (PID: 4388)
- work.exe (PID: 5760)
- GoogleUpdate.exe (PID: 4592)
- eee01.exe (PID: 8392)
- cdplayer.exe (PID: 5224)
- eee01.exe (PID: 4712)
Reads Microsoft Outlook installation path
- New Text Document.bin.exe (PID: 3976)
Reads settings of System Certificates
- New Text Document.exe (PID: 2032)
- RegSvcs.exe (PID: 824)
- GoogleUpdate.exe (PID: 2424)
- RegSvcs.exe (PID: 1604)
- katCA8C.tmp (PID: 5684)
- vpn-1002.exe (PID: 4512)
- RegSvcs.exe (PID: 3640)
- katD46F.tmp (PID: 4552)
- Discord.exe (PID: 4640)
- MSBuild.exe (PID: 4248)
- GoogleUpdate.exe (PID: 4592)
Process requests binary or script from the Internet
- New Text Document.exe (PID: 2032)
- STHealthClient.exe (PID: 1620)
Connects to unusual port
- New Text Document.exe (PID: 2032)
- RegSvcs.exe (PID: 3008)
- example.exe (PID: 2392)
- RegSvcs.exe (PID: 2368)
- rtx.exe (PID: 3392)
- csrss.exe (PID: 1280)
- XClient.exe (PID: 2832)
- vax.exe (PID: 2320)
- svchost.exe (PID: 1880)
- gHIvTf22qvmZjum.exe (PID: 5868)
- sysblardsv.exe (PID: 5060)
- syslmgrsvc.exe (PID: 3268)
- Discord.exe (PID: 4640)
- yar.exe (PID: 4924)
- certutil.exe (PID: 5092)
- MSBuild.exe (PID: 4248)
- cdplayer.exe (PID: 5224)
Connects to the server without a host name
- New Text Document.exe (PID: 2032)
- inte.exe (PID: 6028)
- sysblardsv.exe (PID: 5060)
- syslmgrsvc.exe (PID: 3268)
- univ.exe (PID: 6084)
- univ.exe (PID: 2828)
Accesses Microsoft Outlook profiles
- RegSvcs.exe (PID: 3008)
- RegSvcs.exe (PID: 824)
- RegSvcs.exe (PID: 2368)
- sharonzx.exe (PID: 4040)
- RegSvcs.exe (PID: 1604)
- RegSvcs.exe (PID: 3640)
- gHIvTf22qvmZjum.exe (PID: 5868)
Connects to FTP
- RegSvcs.exe (PID: 3008)
- RegSvcs.exe (PID: 2368)
- gHIvTf22qvmZjum.exe (PID: 5868)
- rtx.exe (PID: 3392)
Creates file in the systems drive root
- ntvdm.exe (PID: 936)
The process checks if it is being run in the virtual environment
- New Text Document.exe (PID: 2032)
Connects to SMTP port
- RegSvcs.exe (PID: 824)
- RegSvcs.exe (PID: 3640)
- rtx.exe (PID: 3392)
Application launched itself
- rtx.exe (PID: 1240)
- sharonzx.exe (PID: 2616)
- gHIvTf22qvmZjum.exe (PID: 368)
- setup.exe (PID: 4380)
- GameService.exe (PID: 5364)
- GameService.exe (PID: 5700)
- GameService.exe (PID: 4284)
- GameService.exe (PID: 4712)
- GameService.exe (PID: 5760)
- GameService.exe (PID: 4204)
- GameService.exe (PID: 5120)
- GameService.exe (PID: 5812)
- setup.exe (PID: 5604)
- GoogleUpdate.exe (PID: 3848)
The process creates files with name similar to system file names
- rtx.exe (PID: 3392)
- New Text Document.exe (PID: 2032)
- XClient.exe (PID: 2832)
- csrss.exe (PID: 1280)
- svchost.exe (PID: 1880)
Starts a Microsoft application from unusual location
- sharonzx.exe (PID: 2616)
- sharonzx.exe (PID: 4040)
Process drops legitimate windows executable
- New Text Document.exe (PID: 2032)
- sharonzx.exe (PID: 2616)
- sharonzx.exe (PID: 4040)
- crt.tmp (PID: 4880)
- Pirate_24S.exe (PID: 4388)
- cmd.exe (PID: 5452)
Device Retrieving External IP Address Detected
- XClient.exe (PID: 2832)
- csrss.exe (PID: 1280)
Checks for external IP
- XClient.exe (PID: 2832)
- csrss.exe (PID: 1280)
- RegSvcs.exe (PID: 1604)
- svchost.exe (PID: 1880)
Reads Mozilla Firefox installation path
- sharonzx.exe (PID: 4040)
Loads DLL from Mozilla Firefox
- sharonzx.exe (PID: 4040)
- netbtugc.exe (PID: 3412)
Reads the Windows owner or organization settings
- SrbijaSetupHokej.tmp (PID: 1072)
- crt.tmp (PID: 4880)
Contacting a server suspected of hosting an CnC
- sharonzx.exe (PID: 4040)
- New Text Document.exe (PID: 2032)
- cdplayer.exe (PID: 5224)
Disables SEHOP
- GoogleUpdate.exe (PID: 2992)
Creates/Modifies COM task schedule object
- GoogleUpdate.exe (PID: 580)
Executes as Windows Service
- GoogleUpdate.exe (PID: 3848)
Process drops SQLite DLL files
- netbtugc.exe (PID: 3412)
The process drops C-runtime libraries
- crt.tmp (PID: 4880)
Starts application with an unusual extension
- sdf34ert3etgrthrthfghfghjfgh.exe (PID: 5620)
- o2i3jroi23joj23ikrjokij3oroi.exe (PID: 6000)
Checks Windows Trust Settings
- katCA8C.tmp (PID: 5684)
- vpn-1002.exe (PID: 4512)
- katD46F.tmp (PID: 4552)
Drops 7-zip archiver for unpacking
- conhost.exe (PID: 5352)
- 222.exe (PID: 4984)
- 888.exe (PID: 5648)
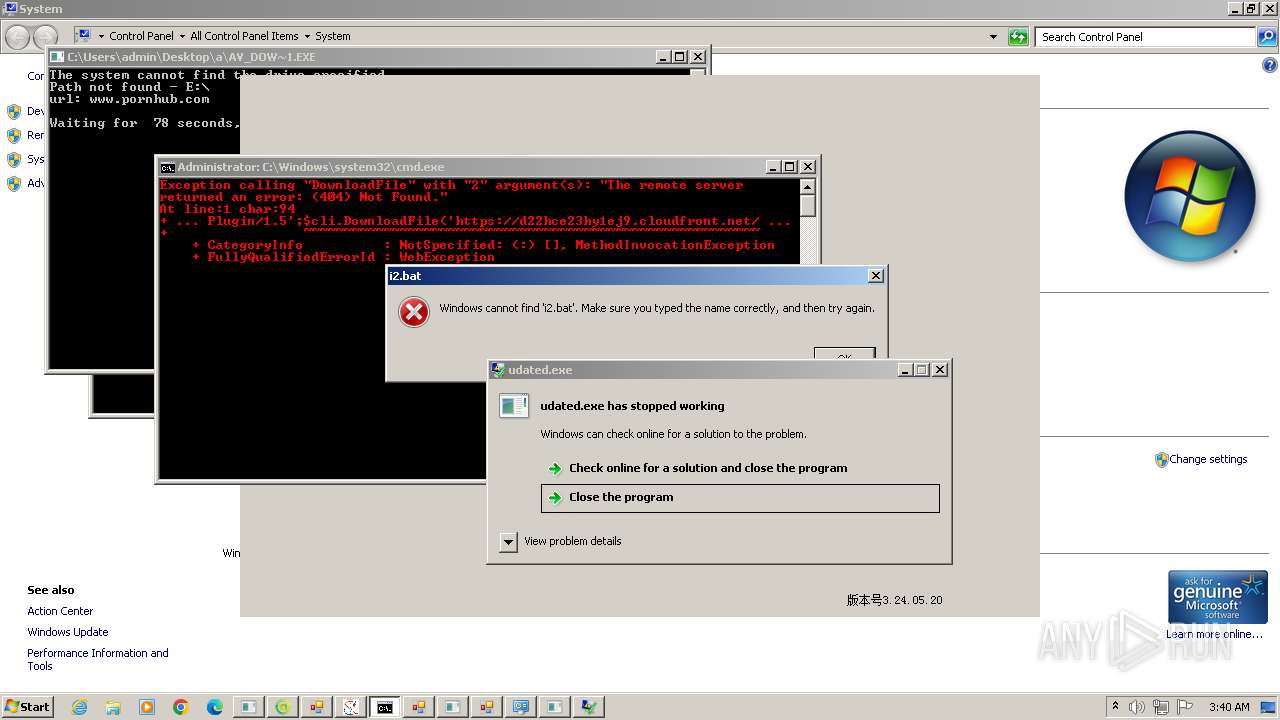
Executing commands from a ".bat" file
- conhost.exe (PID: 5352)
- vpn-1002.exe (PID: 4512)
- 222.exe (PID: 4984)
- 888.exe (PID: 5648)
- av_downloader.exe (PID: 4576)
- install.exe (PID: 3756)
- av_downloader.exe (PID: 5612)
- pojgysef.exe (PID: 4388)
Uses ATTRIB.EXE to modify file attributes
- cmd.exe (PID: 5856)
- cmd.exe (PID: 4816)
- cmd.exe (PID: 5040)
- cmd.exe (PID: 4228)
Starts CMD.EXE for commands execution
- conhost.exe (PID: 5352)
- vpn-1002.exe (PID: 4512)
- inte.exe (PID: 6028)
- katCA8C.tmp (PID: 5684)
- wscript.exe (PID: 5448)
- 222.exe (PID: 4984)
- 888.exe (PID: 5648)
- univ.exe (PID: 6084)
- univ.exe (PID: 2828)
- f.exe (PID: 2328)
- e_win.exe (PID: 4240)
- av_downloader.exe (PID: 5612)
- av_downloader.exe (PID: 4576)
- install.exe (PID: 3756)
- pojgysef.exe (PID: 4388)
Uses TASKKILL.EXE to kill process
- cmd.exe (PID: 4580)
- cmd.exe (PID: 6076)
- cmd.exe (PID: 1044)
Searches for installed software
- katCA8C.tmp (PID: 5684)
- katD46F.tmp (PID: 4552)
- MSBuild.exe (PID: 4248)
- setup.exe (PID: 4380)
Starts itself from another location
- tdrpload.exe (PID: 4608)
- 472111564.exe (PID: 6056)
- syslmgrsvc.exe (PID: 3268)
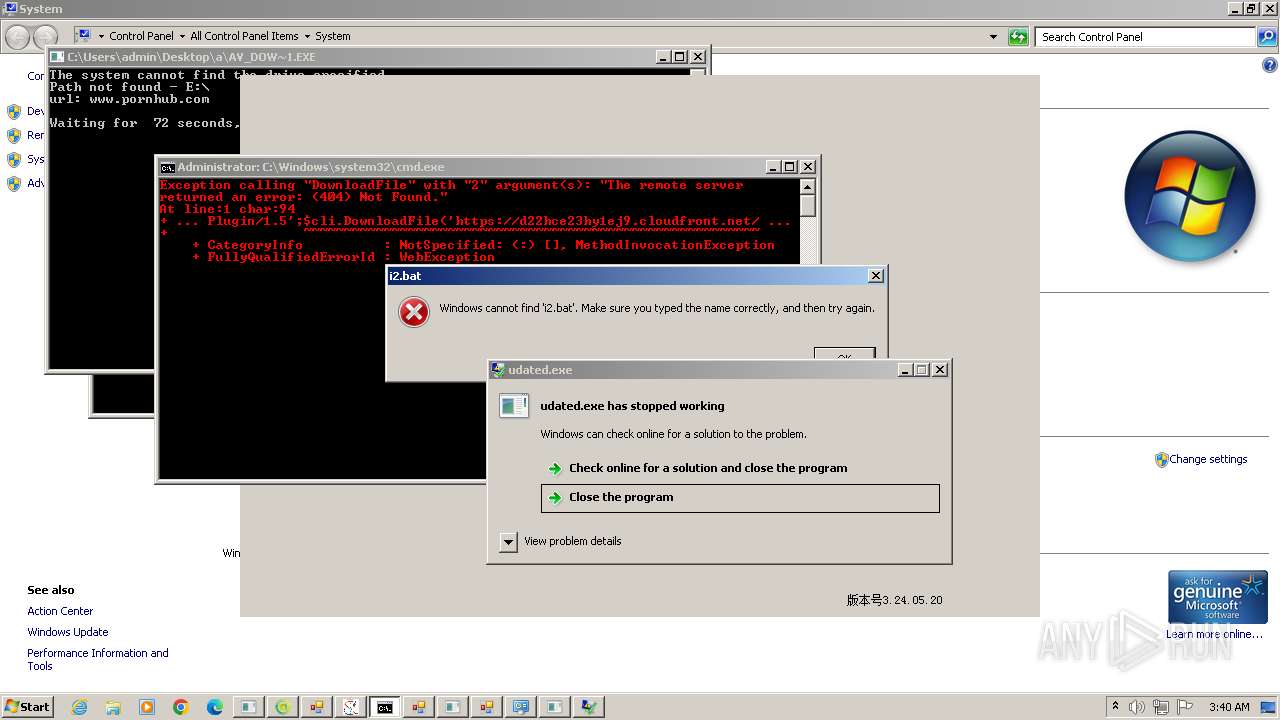
Probably download files using WebClient
- cmd.exe (PID: 4584)
Starts POWERSHELL.EXE for commands execution
- cmd.exe (PID: 4584)
The Powershell connects to the Internet
- powershell.exe (PID: 4568)
- powershell.exe (PID: 5184)
Unusual connection from system programs
- powershell.exe (PID: 4568)
- powershell.exe (PID: 5184)
Uses TIMEOUT.EXE to delay execution
- cmd.exe (PID: 4112)
- cmd.exe (PID: 4228)
The process executes VB scripts
- Pirate_24S.exe (PID: 4388)
Executing commands from ".cmd" file
- wscript.exe (PID: 5448)
- install.exe (PID: 3756)
Takes ownership (TAKEOWN.EXE)
- cmd.exe (PID: 5452)
Runs shell command (SCRIPT)
- wscript.exe (PID: 5448)
- mshta.exe (PID: 5664)
Uses ICACLS.EXE to modify access control lists
- cmd.exe (PID: 5452)
Uses REG/REGEDIT.EXE to modify registry
- regedt32.exe (PID: 4936)
- regedt32.exe (PID: 5968)
- cmd.exe (PID: 4228)
Runs PING.EXE to delay simulation
- cmd.exe (PID: 5452)
Creates files like ransomware instruction
- e_win.exe (PID: 4240)
The process executes via Task Scheduler
- taskhostw.exe (PID: 5816)
- yar.exe (PID: 1944)
Starts SC.EXE for service management
- cmd.exe (PID: 4140)
- cmd.exe (PID: 2912)
- cmd.exe (PID: 4948)
The executable file from the user directory is run by the CMD process
- work.exe (PID: 5760)
Reads the date of Windows installation
- setup.exe (PID: 5604)
Creates a software uninstall entry
- setup.exe (PID: 4380)
Reads browser cookies
- MSBuild.exe (PID: 4248)
Connects to SSH
- rtx.exe (PID: 3392)
INFO
Checks supported languages
- New Text Document.bin.exe (PID: 3976)
- New Text Document.exe (PID: 2032)
- STHealthUp.exe (PID: 308)
- STHealthClient.exe (PID: 1620)
- wmpnscfg.exe (PID: 2304)
- GGWS_UPLOAD.exe (PID: 1844)
- go.exe (PID: 2368)
- aaaaaaaa.exe (PID: 2472)
- crypted.exe (PID: 1980)
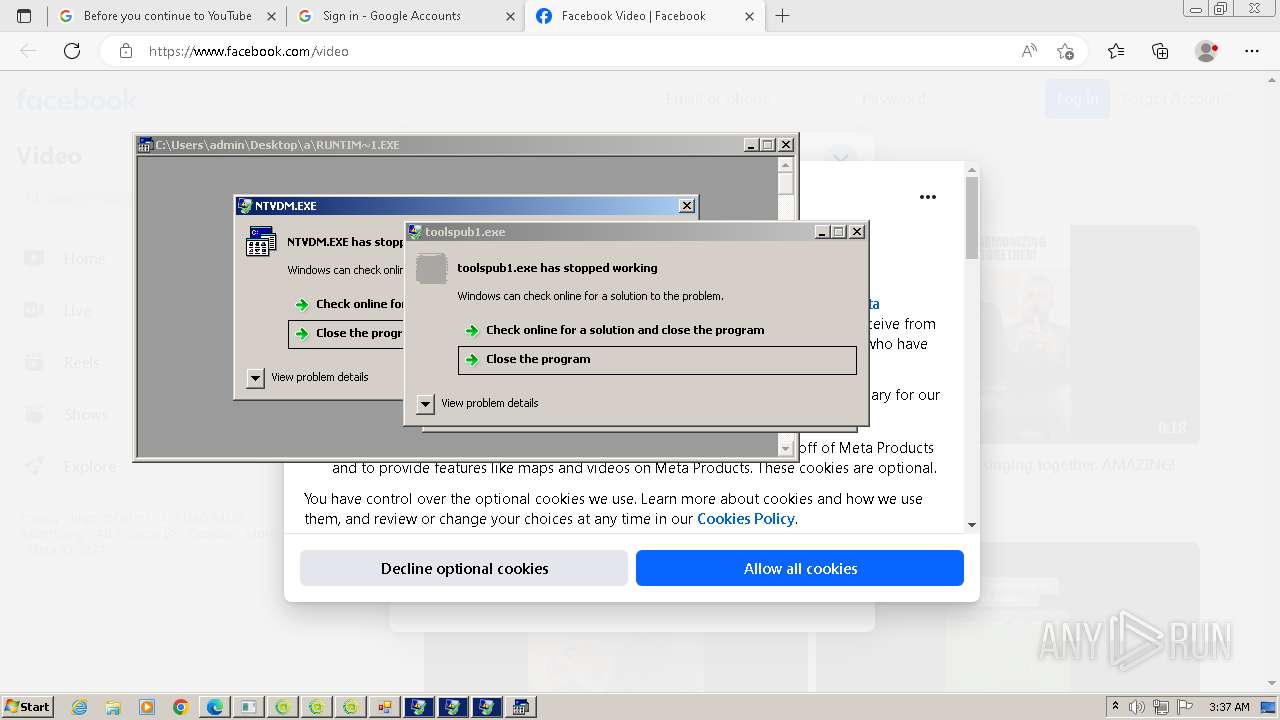
- toolspub1.exe (PID: 3220)
- MyCheckBack.exe (PID: 2240)
- wxijgyp.exe (PID: 2944)
- RegSvcs.exe (PID: 3008)
- zwuivg.exe (PID: 2480)
- rtx.exe (PID: 1240)
- example.exe (PID: 2392)
- backdoor.exe (PID: 2644)
- asdf.exe (PID: 2600)
- rtx.exe (PID: 3392)
- RegSvcs.exe (PID: 824)
- wsiopohwqsd.exe (PID: 1120)
- RegSvcs.exe (PID: 3992)
- QEwecfyhj.exe (PID: 3024)
- tsaplQyj.exe (PID: 1556)
- RegSvcs.exe (PID: 3432)
- RegSvcs.exe (PID: 2368)
- sharonzx.exe (PID: 2616)
- Bypass3_Pure_Mode.exe (PID: 2484)
- XClient.exe (PID: 2832)
- csrss.exe (PID: 1280)
- rooma.exe (PID: 1116)
- SrbijaSetupHokej.exe (PID: 2940)
- sharonzx.exe (PID: 4040)
- SrbijaSetupHokej.exe (PID: 1128)
- SrbijaSetupHokej.tmp (PID: 3184)
- SrbijaSetupHokej.tmp (PID: 1072)
- ChromeSetup.exe (PID: 2072)
- GoogleUpdate.exe (PID: 1284)
- GoogleUpdateSetup.exe (PID: 2304)
- GoogleUpdate.exe (PID: 2696)
- GoogleUpdate.exe (PID: 580)
- GoogleUpdate.exe (PID: 2992)
- GoogleUpdate.exe (PID: 2424)
- GoogleUpdate.exe (PID: 948)
- GoogleUpdate.exe (PID: 3848)
- gywervcyuj.exe (PID: 2972)
- RegSvcs.exe (PID: 1604)
- xxxz.exe (PID: 2912)
- vax.exe (PID: 2320)
- ngown.exe (PID: 1804)
- RegSvcs.exe (PID: 3640)
- gHIvTf22qvmZjum.exe (PID: 368)
- crt.exe (PID: 4160)
- crt.exe (PID: 4840)
- crt.tmp (PID: 4880)
- crt.tmp (PID: 4168)
- conhost.exe (PID: 5352)
- cdplayer.exe (PID: 5224)
- sdf34ert3etgrthrthfghfghjfgh.exe (PID: 5620)
- katCA8C.tmp (PID: 5684)
- cdplayer.exe (PID: 5116)
- o2i3jroi23joj23ikrjokij3oroi.exe (PID: 6000)
- inte.exe (PID: 6028)
- vpn-1002.exe (PID: 4512)
- mode.com (PID: 5884)
- katD46F.tmp (PID: 4552)
- tdrpload.exe (PID: 4608)
- sysblardsv.exe (PID: 5060)
- svchost.exe (PID: 1880)
- gHIvTf22qvmZjum.exe (PID: 5868)
- 472111564.exe (PID: 6056)
- 222.exe (PID: 4984)
- syslmgrsvc.exe (PID: 3268)
- Pirate_24S.exe (PID: 4388)
- nc.exe (PID: 5556)
- pub11.exe (PID: 5020)
- mode.com (PID: 1136)
- 1733825023.exe (PID: 5788)
- 888.exe (PID: 5648)
- univ.exe (PID: 6084)
- nine.exe (PID: 3116)
- mode.com (PID: 1488)
- 109.0.5414.120_chrome_installer.exe (PID: 5952)
- univ.exe (PID: 2828)
- Discord.exe (PID: 4640)
- setup.exe (PID: 4380)
- setup.exe (PID: 4860)
- my.exe (PID: 4480)
- yar.exe (PID: 4924)
- e_win.exe (PID: 4240)
- f.exe (PID: 2328)
- taskhostw.exe (PID: 5816)
- install.exe (PID: 3756)
- yar.exe (PID: 1944)
- av_downloader.exe (PID: 4576)
- update.exe (PID: 4936)
- update_3.exe (PID: 736)
- av_downloader.exe (PID: 5612)
- GameService.exe (PID: 5364)
- up2date.exe (PID: 4256)
- GameService.exe (PID: 5768)
- GameService.exe (PID: 5700)
- GameService.exe (PID: 4284)
- GameService.exe (PID: 3904)
- GameService.exe (PID: 5944)
- GameService.exe (PID: 5960)
- GameService.exe (PID: 5760)
- setup_1715277229.6072824.exe (PID: 4952)
- GameService.exe (PID: 4712)
- GameService.exe (PID: 5712)
- GameService.exe (PID: 4204)
- GameService.exe (PID: 2984)
- MSBuild.exe (PID: 4248)
- GameService.exe (PID: 5704)
- GameService.exe (PID: 5120)
- GameService.exe (PID: 4604)
- GameService.exe (PID: 5812)
- GameService.exe (PID: 4488)
- GameService.exe (PID: 2976)
- GameService.exe (PID: 4996)
- pojgysef.exe (PID: 4388)
- work.exe (PID: 5760)
- pgsthse.exe (PID: 2328)
- udated.exe (PID: 5144)
- setup.exe (PID: 5604)
- eee01.exe (PID: 4712)
- GoogleCrashHandler.exe (PID: 4204)
- GoogleUpdate.exe (PID: 4592)
- setup.exe (PID: 2820)
- GoogleUpdateOnDemand.exe (PID: 2912)
- GoogleUpdate.exe (PID: 5420)
- eee01.exe (PID: 8392)
Checks proxy server information
- New Text Document.bin.exe (PID: 3976)
- netbtugc.exe (PID: 3412)
- katCA8C.tmp (PID: 5684)
- inte.exe (PID: 6028)
- vpn-1002.exe (PID: 4512)
- sysblardsv.exe (PID: 5060)
- katD46F.tmp (PID: 4552)
- syslmgrsvc.exe (PID: 3268)
- univ.exe (PID: 6084)
- univ.exe (PID: 2828)
- certutil.exe (PID: 5092)
- cdplayer.exe (PID: 5224)
Reads the computer name
- New Text Document.bin.exe (PID: 3976)
- New Text Document.exe (PID: 2032)
- STHealthUp.exe (PID: 308)
- STHealthClient.exe (PID: 1620)
- wmpnscfg.exe (PID: 2304)
- GGWS_UPLOAD.exe (PID: 1844)
- MyCheckBack.exe (PID: 2240)
- go.exe (PID: 2368)
- RegSvcs.exe (PID: 3008)
- RegSvcs.exe (PID: 824)
- rtx.exe (PID: 3392)
- RegSvcs.exe (PID: 3992)
- RegSvcs.exe (PID: 2368)
- RegSvcs.exe (PID: 3432)
- sharonzx.exe (PID: 2616)
- Bypass3_Pure_Mode.exe (PID: 2484)
- csrss.exe (PID: 1280)
- XClient.exe (PID: 2832)
- sharonzx.exe (PID: 4040)
- SrbijaSetupHokej.tmp (PID: 3184)
- GoogleUpdate.exe (PID: 1284)
- SrbijaSetupHokej.tmp (PID: 1072)
- GoogleUpdate.exe (PID: 2992)
- GoogleUpdate.exe (PID: 2696)
- GoogleUpdate.exe (PID: 580)
- GoogleUpdate.exe (PID: 2424)
- GoogleUpdate.exe (PID: 948)
- GoogleUpdate.exe (PID: 3848)
- vax.exe (PID: 2320)
- RegSvcs.exe (PID: 1604)
- RegSvcs.exe (PID: 3640)
- gHIvTf22qvmZjum.exe (PID: 368)
- svchost.exe (PID: 1880)
- crt.tmp (PID: 4168)
- crt.tmp (PID: 4880)
- katCA8C.tmp (PID: 5684)
- cdplayer.exe (PID: 5116)
- conhost.exe (PID: 5352)
- inte.exe (PID: 6028)
- vpn-1002.exe (PID: 4512)
- katD46F.tmp (PID: 4552)
- gHIvTf22qvmZjum.exe (PID: 5868)
- sysblardsv.exe (PID: 5060)
- Pirate_24S.exe (PID: 4388)
- syslmgrsvc.exe (PID: 3268)
- 222.exe (PID: 4984)
- pub11.exe (PID: 5020)
- univ.exe (PID: 6084)
- 888.exe (PID: 5648)
- 109.0.5414.120_chrome_installer.exe (PID: 5952)
- Discord.exe (PID: 4640)
- setup.exe (PID: 4380)
- my.exe (PID: 4480)
- yar.exe (PID: 4924)
- univ.exe (PID: 2828)
- e_win.exe (PID: 4240)
- f.exe (PID: 2328)
- yar.exe (PID: 1944)
- taskhostw.exe (PID: 5816)
- install.exe (PID: 3756)
- GameService.exe (PID: 5364)
- GameService.exe (PID: 5700)
- GameService.exe (PID: 3904)
- GameService.exe (PID: 5768)
- GameService.exe (PID: 4284)
- GameService.exe (PID: 5960)
- GameService.exe (PID: 5944)
- GameService.exe (PID: 5760)
- GameService.exe (PID: 5712)
- GameService.exe (PID: 2984)
- GameService.exe (PID: 4712)
- GameService.exe (PID: 4204)
- setup_1715277229.6072824.exe (PID: 4952)
- MSBuild.exe (PID: 4248)
- GameService.exe (PID: 5704)
- GameService.exe (PID: 4604)
- GameService.exe (PID: 5120)
- GameService.exe (PID: 4488)
- GameService.exe (PID: 5812)
- GameService.exe (PID: 4996)
- GameService.exe (PID: 2976)
- pojgysef.exe (PID: 4388)
- work.exe (PID: 5760)
- setup.exe (PID: 5604)
- GoogleCrashHandler.exe (PID: 4204)
- GoogleUpdate.exe (PID: 4592)
- GoogleUpdate.exe (PID: 5420)
- eee01.exe (PID: 4712)
- cdplayer.exe (PID: 5224)
Manual execution by a user
- wmpnscfg.exe (PID: 2304)
- New Text Document.exe (PID: 2032)
Reads the machine GUID from the registry
- New Text Document.bin.exe (PID: 3976)
- New Text Document.exe (PID: 2032)
- STHealthUp.exe (PID: 308)
- STHealthClient.exe (PID: 1620)
- GGWS_UPLOAD.exe (PID: 1844)
- MyCheckBack.exe (PID: 2240)
- RegSvcs.exe (PID: 3008)
- RegSvcs.exe (PID: 824)
- rtx.exe (PID: 3392)
- RegSvcs.exe (PID: 3992)
- RegSvcs.exe (PID: 3432)
- RegSvcs.exe (PID: 2368)
- sharonzx.exe (PID: 2616)
- Bypass3_Pure_Mode.exe (PID: 2484)
- csrss.exe (PID: 1280)
- XClient.exe (PID: 2832)
- sharonzx.exe (PID: 4040)
- GoogleUpdate.exe (PID: 1284)
- GoogleUpdate.exe (PID: 2992)
- GoogleUpdate.exe (PID: 948)
- GoogleUpdate.exe (PID: 3848)
- GoogleUpdate.exe (PID: 2424)
- vax.exe (PID: 2320)
- RegSvcs.exe (PID: 1604)
- RegSvcs.exe (PID: 3640)
- gHIvTf22qvmZjum.exe (PID: 368)
- svchost.exe (PID: 1880)
- katCA8C.tmp (PID: 5684)
- inte.exe (PID: 6028)
- vpn-1002.exe (PID: 4512)
- sysblardsv.exe (PID: 5060)
- gHIvTf22qvmZjum.exe (PID: 5868)
- katD46F.tmp (PID: 4552)
- syslmgrsvc.exe (PID: 3268)
- pub11.exe (PID: 5020)
- univ.exe (PID: 6084)
- Discord.exe (PID: 4640)
- yar.exe (PID: 4924)
- my.exe (PID: 4480)
- univ.exe (PID: 2828)
- f.exe (PID: 2328)
- e_win.exe (PID: 4240)
- taskhostw.exe (PID: 5816)
- yar.exe (PID: 1944)
- MSBuild.exe (PID: 4248)
- setup.exe (PID: 4380)
- setup.exe (PID: 5604)
- GoogleUpdate.exe (PID: 5420)
- GoogleUpdate.exe (PID: 4592)
- eee01.exe (PID: 4712)
- cdplayer.exe (PID: 5224)
Disables trace logs
- New Text Document.exe (PID: 2032)
- STHealthClient.exe (PID: 1620)
- RegSvcs.exe (PID: 3008)
- RegSvcs.exe (PID: 3992)
- RegSvcs.exe (PID: 2368)
- XClient.exe (PID: 2832)
- csrss.exe (PID: 1280)
- RegSvcs.exe (PID: 1604)
- svchost.exe (PID: 1880)
- powershell.exe (PID: 4568)
- powershell.exe (PID: 5184)
- gHIvTf22qvmZjum.exe (PID: 5868)
- Discord.exe (PID: 4640)
- MSBuild.exe (PID: 4248)
Reads Environment values
- New Text Document.exe (PID: 2032)
- STHealthClient.exe (PID: 1620)
- RegSvcs.exe (PID: 3008)
- RegSvcs.exe (PID: 824)
- RegSvcs.exe (PID: 3992)
- RegSvcs.exe (PID: 2368)
- RegSvcs.exe (PID: 3432)
- XClient.exe (PID: 2832)
- csrss.exe (PID: 1280)
- vax.exe (PID: 2320)
- RegSvcs.exe (PID: 1604)
- RegSvcs.exe (PID: 3640)
- svchost.exe (PID: 1880)
- katCA8C.tmp (PID: 5684)
- gHIvTf22qvmZjum.exe (PID: 5868)
- katD46F.tmp (PID: 4552)
- Discord.exe (PID: 4640)
- MSBuild.exe (PID: 4248)
Reads the software policy settings
- New Text Document.exe (PID: 2032)
- RegSvcs.exe (PID: 824)
- GoogleUpdate.exe (PID: 2424)
- GoogleUpdate.exe (PID: 3848)
- RegSvcs.exe (PID: 1604)
- RegSvcs.exe (PID: 3640)
- katCA8C.tmp (PID: 5684)
- vpn-1002.exe (PID: 4512)
- katD46F.tmp (PID: 4552)
- Discord.exe (PID: 4640)
- MSBuild.exe (PID: 4248)
- GoogleUpdate.exe (PID: 4592)
Application launched itself
- msedge.exe (PID: 2256)
- msedge.exe (PID: 824)
- msedge.exe (PID: 736)
- chrome.exe (PID: 5012)
Reads mouse settings
- go.exe (PID: 2368)
- wxijgyp.exe (PID: 2944)
- zwuivg.exe (PID: 2480)
- wsiopohwqsd.exe (PID: 1120)
- QEwecfyhj.exe (PID: 3024)
- tsaplQyj.exe (PID: 1556)
- gywervcyuj.exe (PID: 2972)
- ngown.exe (PID: 1804)
Create files in a temporary directory
- wxijgyp.exe (PID: 2944)
- New Text Document.exe (PID: 2032)
- zwuivg.exe (PID: 2480)
- rtx.exe (PID: 3392)
- wsiopohwqsd.exe (PID: 1120)
- QEwecfyhj.exe (PID: 3024)
- tsaplQyj.exe (PID: 1556)
- SrbijaSetupHokej.exe (PID: 2940)
- sharonzx.exe (PID: 2616)
- SrbijaSetupHokej.exe (PID: 1128)
- ChromeSetup.exe (PID: 2072)
- gywervcyuj.exe (PID: 2972)
- ngown.exe (PID: 1804)
- netbtugc.exe (PID: 3412)
- crt.exe (PID: 4160)
- crt.exe (PID: 4840)
- crt.tmp (PID: 4880)
- conhost.exe (PID: 5352)
- vpn-1002.exe (PID: 4512)
- sysblardsv.exe (PID: 5060)
- 222.exe (PID: 4984)
- Pirate_24S.exe (PID: 4388)
- syslmgrsvc.exe (PID: 3268)
- 888.exe (PID: 5648)
- av_downloader.exe (PID: 4576)
- av_downloader.exe (PID: 5612)
- install.exe (PID: 3756)
- pojgysef.exe (PID: 4388)
- work.exe (PID: 5760)
Creates files in the program directory
- rtx.exe (PID: 3392)
- GoogleUpdateSetup.exe (PID: 2304)
- GoogleUpdate.exe (PID: 2992)
- GoogleUpdate.exe (PID: 2696)
- GoogleUpdate.exe (PID: 580)
- GoogleUpdate.exe (PID: 2424)
- GoogleUpdate.exe (PID: 948)
- GoogleUpdate.exe (PID: 3848)
- cdplayer.exe (PID: 5116)
- katCA8C.tmp (PID: 5684)
- katD46F.tmp (PID: 4552)
- 109.0.5414.120_chrome_installer.exe (PID: 5952)
- cdplayer.exe (PID: 5224)
- setup.exe (PID: 4380)
- setup.exe (PID: 5604)
- GoogleUpdate.exe (PID: 4592)
Creates files or folders in the user directory
- XClient.exe (PID: 2832)
- csrss.exe (PID: 1280)
- sharonzx.exe (PID: 2616)
- sharonzx.exe (PID: 4040)
- vax.exe (PID: 2320)
- netbtugc.exe (PID: 3412)
- svchost.exe (PID: 1880)
- crt.tmp (PID: 4880)
- katCA8C.tmp (PID: 5684)
- vpn-1002.exe (PID: 4512)
- inte.exe (PID: 6028)
- sysblardsv.exe (PID: 5060)
- katD46F.tmp (PID: 4552)
- syslmgrsvc.exe (PID: 3268)
- univ.exe (PID: 6084)
- univ.exe (PID: 2828)
- Discord.exe (PID: 4640)
- yar.exe (PID: 4924)
- e_win.exe (PID: 4240)
- certutil.exe (PID: 5092)
- setup_1715277229.6072824.exe (PID: 4952)
Reads security settings of Internet Explorer
- netbtugc.exe (PID: 3412)
- regedt32.exe (PID: 4936)
- regedt32.exe (PID: 5968)
- certutil.exe (PID: 5092)
- dllhost.exe (PID: 8184)
Drops the executable file immediately after the start
- netbtugc.exe (PID: 3412)
Creates a software uninstall entry
- crt.tmp (PID: 4880)
Reads product name
- katCA8C.tmp (PID: 5684)
- katD46F.tmp (PID: 4552)
- MSBuild.exe (PID: 4248)
Reads CPU info
- katCA8C.tmp (PID: 5684)
- katD46F.tmp (PID: 4552)
Script raised an exception (POWERSHELL)
- powershell.exe (PID: 5184)
Dropped object may contain TOR URL's
- New Text Document.exe (PID: 2032)
Reads Internet Explorer settings
- mshta.exe (PID: 5664)
Checks transactions between databases Windows and Oracle
- eee01.exe (PID: 4712)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
AgentTesla
(PID) Process(824) RegSvcs.exe
Protocolsmtp
Hostmail.worlorderbillions.top
Port587
Usernamenwammuoocha@worlorderbillions.top
PasswordvqpF.#;cCodu
(PID) Process(3640) RegSvcs.exe
Protocolsmtp
Hostmail.worlorderbillions.top
Port587
Usernameniggabown22jan2024@worlorderbillions.top
Password3^?r?mtxk(kt
Formbook
(PID) Process(1116) rooma.exe
C2www.3xfootball.com/fo8o/
Strings (160)wZ22jDxn8hwtYnnk/w==
q7/IljAuWKUjP9LzhVY6WZAW9xV7Lg==
anq78FxRDdKIkSoWlEQ4UEY=
eoSThluq4iN+Rc41zntRhYHb6g==
O7h30riqRAahR9T5HRI7p/6UE1viZkY=
aRcJ4yR+JIlEsDUz7RliR0c=
P2kk3YkFysLZ/xr8j/NT
j7IAjFzbh8BedRjGafGC
90ZjYDDmDegov0HX93hL+BrlCg==
VsB/tN7GW0IFCVxBK3vSdgciaRw=
H2irRWi3sEVnQwpn
mhcjIf6APjHV6w==
HAYqkhKqQwlU/+84
jtQLwFdZ6cHaVA==
AcSWbce98Gsa3H82yeOI6PU=
P/hl4kjf5lO9sx8CPgVLtN0=
FyorLjEqBPkYxd/H21pCdCXeTRU=
2mA3Vksr7QqmQYRh
zN7V+QxiOiJucVyPV4tnoEEC8Q==
vOXO5TwZqh4J
aBo2kIefHxtRX9tg+blTqCBUoaSmUA==
ym9QCdS0FskyRQW1K8aS
QHqoCUeH3RU=
+UJdoYhH0dD7h9tu
Gc2LVVpZN7Z5TpULwg8=
4civn4lQpEI=
joSQgk4Zulvmr5FllmCK
OBlNjAjPL0wWVzbYOvk5KRX20vA=
GHL66NFKaYDm0cPfSOTb
jgQX31OVhboCZNs=
iHkmyaL+z9Qv6pxULDjbdg==
uQwC+RvpT7YO1adGimLC
pMIXi/72muqkB92h5rtgXF8K1wWh
LPlp6EDzMKb54YJ+PsJG
74LKKYDwOswIEZH8
32HxZtOweLPzgYOtapw=
jbsLo3quFldiNGxZd/pl4Q==
MBujXUAtHYKkJhltfDsCIA==
+9Zoakef2z7Z4HWZ3vQOWwgitgY=
E3ZGa1Mxh8TVks2o6Jq+2AcLwwY=
LpD8ktMaPtn+36mfdJE=
PA9jrCXW5/545XgBZQ==
9IdSnrZ6FejIUA==
zmTz3LjDiW9gHw==
RjQA3SM/LSY/Vm+AzFk9XRqEHgI=
cA2gKXAjjUvKHQ==
H1UWMp77XV0Vfzckjz5d6JEInA==
zMTMqYuyvylNTKeyWdAV5G8=
R8FUU7VPz5oOWA==
NqVC3s+EEmnc3ZB3qmGgisk=
hWkeFU0k8euvtAzROivfAFADzQ==
ZLMTNMbPaM6Mll+gaI5SqsEl
/5M+8u4pdcT0o1M=
klXyGLgc/igvqqUE/agIQcuKH6nW
sbpIMePNoeasuAlnNmE=
w9h15yT/GUabbUYOxle5kro+olk=
5jPmD22F+yGZXaG4STUWJ/LEr+xF
32UZpKuV1T7ISCfS
XBqwal9KQYlJn30jirmREQzvp+02
d6noklWTPPb0jA==
J59j4FW+S9Dq9KOQuLAY2wE9nq61
+vj5urFvIEJOnr4mZNdu
tHYXzDTgsf6ddg==
xpRPfdi+yRdY/2c=
XGuo+LeH4w966ZOpW5DbeGUIbw425TnS+g==
netbtugc.exe
verclsid.exe
chkdsk.exe
mshta.exe
sdiagnhost.exe
taskkill.exe
msdt.exe
winver.exe
rundll32.exe
ReAgentc.exe
Utilman.exe
msiexec.exe
kernel32.dll
advapi32.dll
ws2_32.dll
USERNAME
LOCALAPPDATA
USERPROFILE
APPDATA
TEMP
COMPUTERNAME
ProgramFiles
/c copy "
\Run
\Policies
\Explorer
\Registry\User
\Registry\Machine
\SOFTWARE\Microsoft\Windows\CurrentVersion
Office\15.0\Outlook\Profiles\Outlook\
\SOFTWARE\Mozilla\Mozilla
\Mozilla
Username:
Password:
formSubmitURL
usernameField
encryptedUsername
encryptedPassword
\logins.json
\Mail\
\Foxmail
\Storage\
\Accounts\Account.rec0
\Data\AccCfg\Accounts.tdat
\Google\Chrome\User Data\Default\Login Data
SeShutdownPrivilege
\BaseNamedObjects
POST
HTTP/1.1
Host:
Connection: close
Content-Length:
Cache-Control:
Origin: http://
Content-Type: application/x-www-form-urlencoded
Accept:
Referer: http://
Accept-Language:
Accept-Encoding:
Set-ExecutionPolicy RemoteSigned -Scope CurrentUser
-noexit "& ""
PowerShell.exe
\Opera Software\Opera Stable
kernel32.dll
user32.dll
wininet.dll
rg.ini
Recovery
profiles.ini
guid
Connection: close
pass
token
email
login
signin
account
persistent
GET
GET
PUT
POST
OPTIONS
User-Agent:
API-
MS-W
_301 Moved
_302 Found
InternetOpenA
InternetConnectA
HttpOpenRequestA
HttpSendRequestA
InternetReadFile
InternetCloseHandle
(PID) Process(3412) netbtugc.exe
C2www.3xfootball.com/fo8o/
Strings (160)wZ22jDxn8hwtYnnk/w==
q7/IljAuWKUjP9LzhVY6WZAW9xV7Lg==
anq78FxRDdKIkSoWlEQ4UEY=
eoSThluq4iN+Rc41zntRhYHb6g==
O7h30riqRAahR9T5HRI7p/6UE1viZkY=
aRcJ4yR+JIlEsDUz7RliR0c=
P2kk3YkFysLZ/xr8j/NT
j7IAjFzbh8BedRjGafGC
90ZjYDDmDegov0HX93hL+BrlCg==
VsB/tN7GW0IFCVxBK3vSdgciaRw=
H2irRWi3sEVnQwpn
mhcjIf6APjHV6w==
HAYqkhKqQwlU/+84
jtQLwFdZ6cHaVA==
AcSWbce98Gsa3H82yeOI6PU=
P/hl4kjf5lO9sx8CPgVLtN0=
FyorLjEqBPkYxd/H21pCdCXeTRU=
2mA3Vksr7QqmQYRh
zN7V+QxiOiJucVyPV4tnoEEC8Q==
vOXO5TwZqh4J
aBo2kIefHxtRX9tg+blTqCBUoaSmUA==
ym9QCdS0FskyRQW1K8aS
QHqoCUeH3RU=
+UJdoYhH0dD7h9tu
Gc2LVVpZN7Z5TpULwg8=
4civn4lQpEI=
joSQgk4Zulvmr5FllmCK
OBlNjAjPL0wWVzbYOvk5KRX20vA=
GHL66NFKaYDm0cPfSOTb
jgQX31OVhboCZNs=
iHkmyaL+z9Qv6pxULDjbdg==
uQwC+RvpT7YO1adGimLC
pMIXi/72muqkB92h5rtgXF8K1wWh
LPlp6EDzMKb54YJ+PsJG
74LKKYDwOswIEZH8
32HxZtOweLPzgYOtapw=
jbsLo3quFldiNGxZd/pl4Q==
MBujXUAtHYKkJhltfDsCIA==
+9Zoakef2z7Z4HWZ3vQOWwgitgY=
E3ZGa1Mxh8TVks2o6Jq+2AcLwwY=
LpD8ktMaPtn+36mfdJE=
PA9jrCXW5/545XgBZQ==
9IdSnrZ6FejIUA==
zmTz3LjDiW9gHw==
RjQA3SM/LSY/Vm+AzFk9XRqEHgI=
cA2gKXAjjUvKHQ==
H1UWMp77XV0Vfzckjz5d6JEInA==
zMTMqYuyvylNTKeyWdAV5G8=
R8FUU7VPz5oOWA==
NqVC3s+EEmnc3ZB3qmGgisk=
hWkeFU0k8euvtAzROivfAFADzQ==
ZLMTNMbPaM6Mll+gaI5SqsEl
/5M+8u4pdcT0o1M=
klXyGLgc/igvqqUE/agIQcuKH6nW
sbpIMePNoeasuAlnNmE=
w9h15yT/GUabbUYOxle5kro+olk=
5jPmD22F+yGZXaG4STUWJ/LEr+xF
32UZpKuV1T7ISCfS
XBqwal9KQYlJn30jirmREQzvp+02
d6noklWTPPb0jA==
J59j4FW+S9Dq9KOQuLAY2wE9nq61
+vj5urFvIEJOnr4mZNdu
tHYXzDTgsf6ddg==
xpRPfdi+yRdY/2c=
XGuo+LeH4w966ZOpW5DbeGUIbw425TnS+g==
netbtugc.exe
verclsid.exe
chkdsk.exe
mshta.exe
sdiagnhost.exe
taskkill.exe
msdt.exe
winver.exe
rundll32.exe
ReAgentc.exe
Utilman.exe
msiexec.exe
kernel32.dll
advapi32.dll
ws2_32.dll
USERNAME
LOCALAPPDATA
USERPROFILE
APPDATA
TEMP
COMPUTERNAME
ProgramFiles
/c copy "
\Run
\Policies
\Explorer
\Registry\User
\Registry\Machine
\SOFTWARE\Microsoft\Windows\CurrentVersion
Office\15.0\Outlook\Profiles\Outlook\
\SOFTWARE\Mozilla\Mozilla
\Mozilla
Username:
Password:
formSubmitURL
usernameField
encryptedUsername
encryptedPassword
\logins.json
\Mail\
\Foxmail
\Storage\
\Accounts\Account.rec0
\Data\AccCfg\Accounts.tdat
\Google\Chrome\User Data\Default\Login Data
SeShutdownPrivilege
\BaseNamedObjects
POST
HTTP/1.1
Host:
Connection: close
Content-Length:
Cache-Control:
Origin: http://
Content-Type: application/x-www-form-urlencoded
Accept:
Referer: http://
Accept-Language:
Accept-Encoding:
Set-ExecutionPolicy RemoteSigned -Scope CurrentUser
-noexit "& ""
PowerShell.exe
\Opera Software\Opera Stable
kernel32.dll
user32.dll
wininet.dll
rg.ini
Recovery
profiles.ini
guid
Connection: close
pass
token
email
login
signin
account
persistent
GET
GET
PUT
POST
OPTIONS
User-Agent:
API-
MS-W
_301 Moved
_302 Found
InternetOpenA
InternetConnectA
HttpOpenRequestA
HttpSendRequestA
InternetReadFile
InternetCloseHandle
XWorm
(PID) Process(2832) XClient.exe
C245.141.27.41:7000
Keys
AES<123456789>
Options
Splitter<Xwormmm>
Sleep time3
USB drop nameXWorm V5.4
Mutex9ZF9ZsOZGh1T1r1n
(PID) Process(1280) csrss.exe
C245.141.26.119:1996
Keys
AES<123456789>
Options
Splitter<Xwormmm>
Sleep time3
USB drop nameXWorm V5.4
MutexwHK5NlknpAL3Lk1X
(PID) Process(1880) svchost.exe
C285.203.4.146:7000
Keys
AES<123456789>
Options
Splitter<Xwormmm>
Sleep time3
USB drop nameXWorm V5.4
MutexeItTbYBfBYihwkyW
(PID) Process(4640) Discord.exe
C2https://pastebin.com/raw/Xuc6dzua:<123456789>
Keys
AES<Xwormmm>
Options
Splitter3
Sleep timeXWorm V5.6
USB drop nameUSB.exe
MutexbEeZ4MhyYSkjMJ8j
AsyncRat
(PID) Process(2320) vax.exe
C2 (1)185.196.10.81
Ports (1)4449
VersionVenom RAT + HVNC + Stealer + Grabber v6.0.3
Options
AutoRunfalse
Mutexwrteyuiooo
InstallFolder%AppData%
Certificates
Cert1MIICOTCCAaKgAwIBAgIVAPyfwFFMs6hxoSr1U5gHJmBruaj1MA0GCSqGSIb3DQEBDQUAMGoxGDAWBgNVBAMMD1Zlbm9tUkFUIFNlcnZlcjETMBEGA1UECwwKcXdxZGFuY2h1bjEfMB0GA1UECgwWVmVub21SQVQgQnkgcXdxZGFuY2h1bjELMAkGA1UEBwwCU0gxCzAJBgNVBAYTAkNOMB4XDTIyMDgxNDA5NDEwOVoXDTMzMDUyMzA5NDEwOVowEzERMA8GA1UEAwwIVmVub21SQVQwgZ8wDQYJKoZIhvcN...
Server_SignatureMEd1CD8iTeY7YWWzU44VHmQiwZS0TqUpDmIWlmo0xiZD7K2igThi817GSA28/UBclqmoHVBHFzuue93FAc4ZcQ+RC7CaTRV+xP4PHhapIzCKMPZJgQ8rIFeJ52qZki6XkIMdZaql0Abkf4xbxuBvtAfARl3Hzx63Jf0zc0OexIs=
Keys
AES3c5e0e0cefb94aaa704b50bdbf5dd46c7955034f9d83305435430b78f745d551
SaltVenomRATByVenom
(PID) Process(4480) my.exe
C2 (1)127.0.0.1
Ports (1)8848
Version1.0.7
Options
AutoRunfalse
MutexDcRatMutex_qwqdanchun
InstallFolder%AppData%
Certificates
Cert1MIICLTCCAZagAwIBAgIVALkjCXUqNpWpON/3oq3YOq49NK8LMA0GCSqGSIb3DQEBDQUAMGExEjAQBgNVBAMMCU15IFNlcnZlcjETMBEGA1UECwwKcXdxZGFuY2h1bjEcMBoGA1UECgwTRGNSYXQgQnkgcXdxZGFuY2h1bjELMAkGA1UEBwwCU0gxCzAJBgNVBAYTAkNOMB4XDTIzMDgwMTEyMDQyN1oXDTM0MDUxMDEyMDQyN1owEDEOMAwGA1UEAwwFRGNSYXQwgZ8wDQYJKoZIhvcNAQEBBQADgY0AMIGJ...
Server_Signaturebe5s8dxLLMy6Li3DursjAj/o3Xw068NUtbdZExXKlm/UTk8VHfvX3W0yBc7qcXqyfVrxQ0L0MBzBLuZgFz86cmleQJkUh2ldYAStNJcXGNa3Rm30LOg+WDqpfRN70uGrxpqpCVftgFy7iS+Z6vIC267l2q6lQ5wx/dWuaQQP7Kg=
Keys
AESb86153efa26d23c860c6babd692d71879bf261887b5584950d9ec2ce05d7321b
SaltDcRatByqwqdanchun
Lumma
(PID) Process(4256) up2date.exe
C2 (8)plaintediousidowsko.shop
acceptabledcooeprs.shop
miniaturefinerninewjs.shop
sweetsquarediaslw.shop
zippyfinickysofwps.shop
boredimperissvieos.shop
holicisticscrarws.shop
obsceneclassyjuwks.shop
(PID) Process(5144) udated.exe
C2 (8)plaintediousidowsko.shop
acceptabledcooeprs.shop
miniaturefinerninewjs.shop
sweetsquarediaslw.shop
zippyfinickysofwps.shop
boredimperissvieos.shop
holicisticscrarws.shop
obsceneclassyjuwks.shop
TRiD
| .exe | | | Win32 Executable (generic) (52.9) |
|---|---|---|
| .exe | | | Generic Win/DOS Executable (23.5) |
| .exe | | | DOS Executable Generic (23.5) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2023:10:03 07:51:19+00:00 |
| ImageFileCharacteristics: | Executable, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 14.33 |
| CodeSize: | 214528 |
| InitializedDataSize: | 119296 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x21d50 |
| OSVersion: | 5.1 |
| ImageVersion: | - |
| SubsystemVersion: | 5.1 |
| Subsystem: | Windows GUI |
Total processes
388
Monitored processes
264
Malicious processes
81
Suspicious processes
14
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 188 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=crashpad-handler "--user-data-dir=C:\Users\admin\AppData\Local\Microsoft\Edge\User Data" /prefetch:7 --monitor-self-annotation=ptype=crashpad-handler "--database=C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Crashpad" "--metrics-dir=C:\Users\admin\AppData\Local\Microsoft\Edge\User Data" --annotation=IsOfficialBuild=1 --annotation=channel= --annotation=chromium-version=109.0.5414.149 "--annotation=exe=C:\Program Files\Microsoft\Edge\Application\msedge.exe" --annotation=plat=Win32 "--annotation=prod=Microsoft Edge" --annotation=ver=109.0.1518.115 --initial-client-data=0xc4,0xc8,0xcc,0x98,0xd4,0x6779f598,0x6779f5a8,0x6779f5b4 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
| 308 | "C:\Users\admin\Desktop\a\STHealthUp.exe" | C:\Users\admin\Desktop\a\STHealthUp.exe | — | New Text Document.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: STHealthUp Version: 1.0.0.0 Modules
| |||||||||||||||
| 324 | takeown /f C:\Windows\SysWOW64\slwga.dll | C:\Windows\System32\takeown.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Takes ownership of a file Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 368 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=chrome.mojom.UtilWin --lang=en-US --service-sandbox-type=none --mojo-platform-channel-handle=4220 --field-trial-handle=1328,i,12447548874499528148,8797926776172985615,131072 /prefetch:8 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
| 368 | "C:\Users\admin\Desktop\a\gHIvTf22qvmZjum.exe" | C:\Users\admin\Desktop\a\gHIvTf22qvmZjum.exe | — | New Text Document.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: Presentacion Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 580 | "C:\Program Files\Google\Update\GoogleUpdate.exe" /regserver | C:\Program Files\Google\Update\GoogleUpdate.exe | — | GoogleUpdate.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: HIGH Description: Google Installer Exit code: 0 Version: 1.3.33.23 Modules
| |||||||||||||||
| 736 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --single-argument https://www.facebook.com/video | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | go.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
| 736 | "C:\Users\admin\Desktop\a\update_3.exe" | C:\Users\admin\Desktop\a\update_3.exe | New Text Document.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 764 | takeown /f C:\Windows\System32\sppsvc.exe | C:\Windows\System32\takeown.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Takes ownership of a file Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 824 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --single-argument https://accounts.google.com/ | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | go.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
Total events
188 648
Read events
184 101
Write events
4 308
Delete events
239
Modification events
| (PID) Process: | (3976) New Text Document.bin.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (3976) New Text Document.bin.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (3976) New Text Document.bin.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (3976) New Text Document.bin.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (3976) New Text Document.bin.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (3976) New Text Document.bin.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (3976) New Text Document.bin.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (3976) New Text Document.bin.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\LowRegistry |
| Operation: | delete value | Name: | AddToFavoritesInitialSelection |
Value: | |||
| (PID) Process: | (3976) New Text Document.bin.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\LowRegistry |
| Operation: | delete value | Name: | AddToFeedsInitialSelection |
Value: | |||
| (PID) Process: | (2032) New Text Document.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\New Text Document_RASAPI32 |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
Executable files
393
Suspicious files
478
Text files
251
Unknown types
6
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 824 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Crashpad\settings.dat | — | |
MD5:— | SHA256:— | |||
| 860 | msedge.exe | — | ||
MD5:— | SHA256:— | |||
| 2256 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old~RF115bc9.TMP | — | |
MD5:— | SHA256:— | |||
| 2256 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 824 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Variations | binary | |
MD5:961E3604F228B0D10541EBF921500C86 | SHA256:F7B24F2EB3D5EB0550527490395D2F61C3D2FE74BB9CB345197DAD81B58B5FED | |||
| 3976 | New Text Document.bin.exe | C:\Users\admin\Desktop\New Text Document.exe | executable | |
MD5:A239A27C2169AF388D4F5BE6B52F272C | SHA256:98E895F711226A32BFAB152E224279D859799243845C46E550C2D32153C619FC | |||
| 1620 | STHealthClient.exe | C:\Users\admin\Desktop\a\Update\server.txt | text | |
MD5:D3C9A1D8DD718E64BAD0FB5660E29827 | SHA256:F7266A7DD1E376547CFBD1AA3880E61F6C9F0BE6D7E65CEF4D980F282C565196 | |||
| 2256 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\EdgePushStorageWithConnectTokenAndKey\LOG.old~RF115bf8.TMP | — | |
MD5:— | SHA256:— | |||
| 2032 | New Text Document.exe | C:\Users\admin\Desktop\a\aaaaaaaa.exe | executable | |
MD5:3DE3B5B66DF61DE3BE752238D11317E3 | SHA256:9B9438E01B7841DAD1CDA34AAE49F7BC60E09F88AB4E6F639B838E72BECF20AB | |||
| 3976 | New Text Document.bin.exe | C:\Users\admin\Desktop\Пароли Chrome.csv | csv | |
MD5:64F50AFB35DD16EE46F187015CEE84CE | SHA256:C2D389870DE77426A31A8C478E0FDDCBBEA7A3733B453806317914E6F946EA91 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
902
TCP/UDP connections
7 793
DNS requests
2 015
Threats
819
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2032 | New Text Document.exe | GET | 200 | 47.104.173.216:8081 | http://47.104.173.216:8081/STHealthClient.exe | unknown | — | — | unknown |
2032 | New Text Document.exe | GET | 200 | 47.104.173.216:8081 | http://47.104.173.216:8081/STHealthUp.exe | unknown | — | — | unknown |
2032 | New Text Document.exe | GET | 200 | 141.8.192.6:80 | http://a0984086.xsph.ru/a.exe | unknown | — | — | unknown |
2032 | New Text Document.exe | GET | 200 | 47.104.173.216:8081 | http://47.104.173.216:8081/GGWS_UPLOAD.exe | unknown | — | — | unknown |
1620 | STHealthClient.exe | GET | 200 | 47.104.173.216:8081 | http://47.104.173.216:8081/server.txt | unknown | — | — | unknown |
1620 | STHealthClient.exe | GET | 200 | 47.104.173.216:8081 | http://47.104.173.216:8081/STHealthUpdate.exe | unknown | — | — | unknown |
2032 | New Text Document.exe | GET | 200 | 47.104.173.216:8081 | http://47.104.173.216:8081/MyCheckBack.exe | unknown | — | — | unknown |
2032 | New Text Document.exe | GET | 200 | 114.132.120.166:8080 | http://114.132.120.166:8080/beacon.exe | unknown | — | — | unknown |
2032 | New Text Document.exe | GET | 200 | 147.45.47.102:57893 | http://147.45.47.102:57893/cost/go.exe | unknown | — | — | unknown |
2032 | New Text Document.exe | GET | 200 | 185.172.128.82:80 | http://185.172.128.82/server/15/AppGate2103v15.exe | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 224.0.0.252:5355 | — | — | — | unknown |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1088 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
2032 | New Text Document.exe | 151.101.130.49:443 | urlhaus.abuse.ch | FASTLY | US | unknown |
2032 | New Text Document.exe | 141.8.192.6:80 | a0984086.xsph.ru | Sprinthost.ru LLC | RU | unknown |
2032 | New Text Document.exe | 47.104.173.216:8081 | — | Hangzhou Alibaba Advertising Co.,Ltd. | CN | unknown |
1620 | STHealthClient.exe | 47.104.173.216:8081 | — | Hangzhou Alibaba Advertising Co.,Ltd. | CN | unknown |
2032 | New Text Document.exe | 114.132.120.166:8080 | — | Shenzhen Tencent Computer Systems Company Limited | CN | unknown |
2032 | New Text Document.exe | 147.45.47.102:57893 | — | OOO FREEnet Group | RU | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
urlhaus.abuse.ch |
| whitelisted |
a0984086.xsph.ru |
| unknown |
transfer.adttemp.com.br |
| unknown |
config.edge.skype.com |
| whitelisted |
www.youtube.com |
| whitelisted |
edge.microsoft.com |
| whitelisted |
accounts.google.com |
| shared |
www.facebook.com |
| whitelisted |
consent.youtube.com |
| whitelisted |
www.bing.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1088 | svchost.exe | Misc activity | ET INFO Observed DNS Query to xsph .ru Domain |
2032 | New Text Document.exe | A Network Trojan was detected | ET MALWARE Single char EXE direct download likely trojan (multiple families) |
2032 | New Text Document.exe | Potentially Bad Traffic | ET MALWARE Terse alphanumeric executable downloader high likelihood of being hostile |
2032 | New Text Document.exe | Potential Corporate Privacy Violation | ET POLICY PE EXE or DLL Windows file download HTTP |
2032 | New Text Document.exe | Potentially Bad Traffic | ET INFO Executable Retrieved With Minimal HTTP Headers - Potential Second Stage Download |
— | — | Potentially Bad Traffic | ET INFO Executable Download from dotted-quad Host |
— | — | Potential Corporate Privacy Violation | ET POLICY PE EXE or DLL Windows file download HTTP |
— | — | Potentially Bad Traffic | ET INFO Executable Retrieved With Minimal HTTP Headers - Potential Second Stage Download |
— | — | Potentially Bad Traffic | ET HUNTING SUSPICIOUS Dotted Quad Host MZ Response |
— | — | Potentially Bad Traffic | ET INFO Executable Download from dotted-quad Host |
138 ETPRO signatures available at the full report