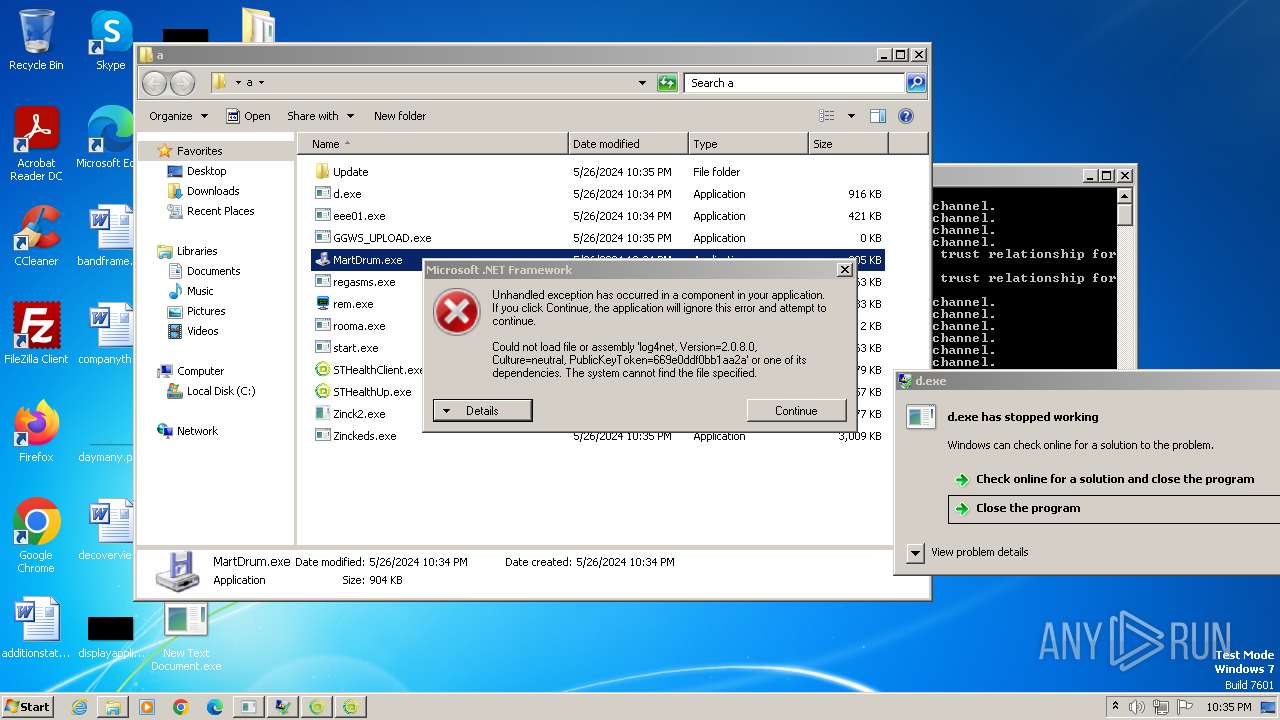
| File name: | New Text Document.bin.exe |
| Full analysis: | https://app.any.run/tasks/551991bb-d2fd-4ab8-ab75-816a36ce5e7c |
| Verdict: | Malicious activity |
| Threats: | AsyncRAT is a RAT that can monitor and remotely control infected systems. This malware was introduced on Github as a legitimate open-source remote administration software, but hackers use it for its many powerful malicious functions. |
| Analysis date: | May 26, 2024, 21:34:34 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | 0B0D247AA1F24C2F5867B3BF29F69450 |
| SHA1: | 48DE9F34226FD7F637E2379365BE035AF5C0DF1A |
| SHA256: | A6E7292E734C3A15CFA654BBA8DEA72A2F55F1C24CF6BBDC2FD7E63887E9315A |
| SSDEEP: | 12288:dcgCzNHJj96xfKJStJkRm3bYXob0AnmFMcaGQxkZVVVVVVVVVAtVVVUvqGV:UQKgLIQmFuGQxklvqO |
MALICIOUS
Drops the executable file immediately after the start
- New Text Document.bin.exe (PID: 3968)
- New Text Document.exe (PID: 2108)
- MartDrum.exe (PID: 2092)
- cmd.exe (PID: 2020)
- rem.exe (PID: 2472)
- Fighting.pif (PID: 2460)
- start.exe (PID: 2364)
- Zinck2.exe (PID: 2632)
- MartDrum.exe (PID: 1116)
- cmd.exe (PID: 2448)
- STHealthClient.exe (PID: 3912)
Known privilege escalation attack
- dllhost.exe (PID: 312)
Antivirus name has been found in the command line (generic signature)
- findstr.exe (PID: 2368)
- findstr.exe (PID: 1820)
- findstr.exe (PID: 2328)
- findstr.exe (PID: 1900)
REMCOS has been detected
- rem.exe (PID: 2472)
- svcs.exe (PID: 2456)
- svcs.exe (PID: 2456)
Changes the autorun value in the registry
- rem.exe (PID: 2472)
- svcs.exe (PID: 2456)
- start.exe (PID: 2364)
- Zinck2.exe (PID: 2632)
Create files in the Startup directory
- cmd.exe (PID: 1612)
ASYNCRAT has been detected (MUTEX)
- start.exe (PID: 2364)
- regasms.exe (PID: 2324)
- svchos.exe (PID: 2696)
- jsc.exe (PID: 3856)
REMCOS has been detected (SURICATA)
- svcs.exe (PID: 2456)
Uses Task Scheduler to run other applications
- Zinck2.exe (PID: 2632)
Uses Task Scheduler to autorun other applications
- Zinck2.exe (PID: 2632)
Actions looks like stealing of personal data
- regasms.exe (PID: 2324)
- svchos.exe (PID: 2696)
- jsc.exe (PID: 3856)
ASYNCRAT has been detected (SURICATA)
- regasms.exe (PID: 2324)
- svchos.exe (PID: 2696)
DCRAT has been detected (YARA)
- New Text Document.exe (PID: 2108)
RISEPRO has been detected (SURICATA)
- Zinck2.exe (PID: 2632)
- IEUpdater2663.exe (PID: 2088)
- Zinck2.exe (PID: 3496)
Changes the Windows auto-update feature
- IEUpdater2663.exe (PID: 2088)
- IEUpdater2663.exe (PID: 580)
REMCOS has been detected (YARA)
- svcs.exe (PID: 2456)
ASYNCRAT has been detected (YARA)
- regasms.exe (PID: 2324)
- jsc.exe (PID: 3856)
REDLINE has been detected (YARA)
- d.exe (PID: 1660)
HAUSBOMBER has been detected (YARA)
- New Text Document.exe (PID: 2108)
SUSPICIOUS
Reads the Internet Settings
- New Text Document.bin.exe (PID: 3968)
- New Text Document.exe (PID: 2108)
- MartDrum.exe (PID: 2092)
- rem.exe (PID: 2472)
- Zinck2.exe (PID: 2632)
- STHealthClient.exe (PID: 3912)
- Zinck2.exe (PID: 3496)
- MartDrum.exe (PID: 1116)
- go.exe (PID: 2724)
Reads security settings of Internet Explorer
- New Text Document.bin.exe (PID: 3968)
- New Text Document.exe (PID: 2108)
- MartDrum.exe (PID: 2092)
- rem.exe (PID: 2472)
- Zinck2.exe (PID: 2632)
- MartDrum.exe (PID: 1116)
- Zinck2.exe (PID: 3496)
Reads Microsoft Outlook installation path
- New Text Document.bin.exe (PID: 3968)
Reads Internet Explorer settings
- New Text Document.bin.exe (PID: 3968)
Executable content was dropped or overwritten
- New Text Document.bin.exe (PID: 3968)
- New Text Document.exe (PID: 2108)
- cmd.exe (PID: 2020)
- MartDrum.exe (PID: 2092)
- rem.exe (PID: 2472)
- Fighting.pif (PID: 2460)
- start.exe (PID: 2364)
- Zinck2.exe (PID: 2632)
- MartDrum.exe (PID: 1116)
- cmd.exe (PID: 2448)
- STHealthClient.exe (PID: 3912)
Reads settings of System Certificates
- New Text Document.exe (PID: 2108)
- regasms.exe (PID: 2324)
- Zinck2.exe (PID: 2632)
- svchos.exe (PID: 2696)
- Zinck2.exe (PID: 3496)
- jsc.exe (PID: 3856)
Potential Corporate Privacy Violation
- New Text Document.exe (PID: 2108)
Connects to the server without a host name
- New Text Document.exe (PID: 2108)
Process requests binary or script from the Internet
- New Text Document.exe (PID: 2108)
- STHealthClient.exe (PID: 3912)
Starts CMD.EXE for commands execution
- cmd.exe (PID: 1640)
- cmd.exe (PID: 1824)
- MartDrum.exe (PID: 2092)
- start.exe (PID: 2364)
- MartDrum.exe (PID: 1116)
- cmd.exe (PID: 1212)
- cmd.exe (PID: 2080)
Application launched itself
- cmd.exe (PID: 1824)
- cmd.exe (PID: 1640)
- cmd.exe (PID: 1212)
- cmd.exe (PID: 2080)
Get information on the list of running processes
- cmd.exe (PID: 1640)
- cmd.exe (PID: 2080)
Using 'findstr.exe' to search for text patterns in files and output
- cmd.exe (PID: 1640)
- cmd.exe (PID: 2080)
Suspicious file concatenation
- cmd.exe (PID: 2624)
- cmd.exe (PID: 2020)
- cmd.exe (PID: 2448)
- cmd.exe (PID: 2472)
The executable file from the user directory is run by the CMD process
- Fighting.pif (PID: 2460)
- svchos.exe (PID: 2696)
- Fighting.pif (PID: 1344)
Starts application with an unusual extension
- cmd.exe (PID: 1640)
- cmd.exe (PID: 2080)
Writes files like Keylogger logs
- rem.exe (PID: 2472)
Starts itself from another location
- rem.exe (PID: 2472)
- Zinck2.exe (PID: 2632)
- Zinck2.exe (PID: 3496)
Drops a file with a rarely used extension (PIF)
- Fighting.pif (PID: 2460)
- cmd.exe (PID: 2448)
Runs PING.EXE to delay simulation
- cmd.exe (PID: 1640)
- cmd.exe (PID: 2080)
Creates file in the systems drive root
- ntvdm.exe (PID: 1576)
Contacting a server suspected of hosting an CnC
- svcs.exe (PID: 2456)
- regasms.exe (PID: 2324)
- Zinck2.exe (PID: 2632)
- IEUpdater2663.exe (PID: 2088)
- svchos.exe (PID: 2696)
- Zinck2.exe (PID: 3496)
Executing commands from a ".bat" file
- start.exe (PID: 2364)
Uses TIMEOUT.EXE to delay execution
- cmd.exe (PID: 2680)
Connects to unusual port
- svcs.exe (PID: 2456)
- Zinck2.exe (PID: 2632)
- regasms.exe (PID: 2324)
- IEUpdater2663.exe (PID: 2088)
- svchos.exe (PID: 2696)
- Zinck2.exe (PID: 3496)
- IEUpdater2663.exe (PID: 580)
- jsc.exe (PID: 3856)
- New Text Document.exe (PID: 2108)
Adds/modifies Windows certificates
- Zinck2.exe (PID: 2632)
- Zinck2.exe (PID: 3496)
Device Retrieving External IP Address Detected
- Zinck2.exe (PID: 2632)
- Zinck2.exe (PID: 3496)
Checks for external IP
- Zinck2.exe (PID: 2632)
- Zinck2.exe (PID: 3496)
Process drops legitimate windows executable
- Fighting.pif (PID: 2460)
Starts a Microsoft application from unusual location
- jsc.exe (PID: 3856)
INFO
Reads the computer name
- New Text Document.bin.exe (PID: 3968)
- New Text Document.exe (PID: 2108)
- eee01.exe (PID: 2024)
- wmpnscfg.exe (PID: 588)
- start.exe (PID: 2364)
- MartDrum.exe (PID: 2092)
- rem.exe (PID: 2472)
- svcs.exe (PID: 2456)
- Fighting.pif (PID: 2460)
- regasms.exe (PID: 2324)
- Zinck2.exe (PID: 2632)
- svchos.exe (PID: 2696)
- IEUpdater2663.exe (PID: 2088)
- STHealthUp.exe (PID: 3028)
- Zinck2.exe (PID: 3496)
- STHealthClient.exe (PID: 3912)
- MartDrum.exe (PID: 1116)
- Fighting.pif (PID: 1344)
- jsc.exe (PID: 3856)
- IEUpdater2663.exe (PID: 580)
- GGWS_UPLOAD.exe (PID: 952)
- MyCheckBack.exe (PID: 2940)
- go.exe (PID: 2724)
Checks supported languages
- New Text Document.bin.exe (PID: 3968)
- New Text Document.exe (PID: 2108)
- eee01.exe (PID: 2024)
- eee01.exe (PID: 1652)
- MartDrum.exe (PID: 2092)
- wmpnscfg.exe (PID: 588)
- d.exe (PID: 1660)
- start.exe (PID: 2364)
- Fighting.pif (PID: 2460)
- rem.exe (PID: 2472)
- svcs.exe (PID: 2456)
- regasms.exe (PID: 2324)
- Zinck2.exe (PID: 2632)
- Zinckeds.exe (PID: 2712)
- svchos.exe (PID: 2696)
- STHealthUp.exe (PID: 3028)
- IEUpdater2663.exe (PID: 2088)
- Zinck2.exe (PID: 3496)
- STHealthClient.exe (PID: 3912)
- MartDrum.exe (PID: 1116)
- IEUpdater2663.exe (PID: 580)
- Fighting.pif (PID: 1344)
- jsc.exe (PID: 3856)
- GGWS_UPLOAD.exe (PID: 952)
- MyCheckBack.exe (PID: 2940)
- go.exe (PID: 2724)
- crypted.exe (PID: 4092)
- aaaaaaaa.exe (PID: 3288)
Checks proxy server information
- New Text Document.bin.exe (PID: 3968)
Reads the machine GUID from the registry
- New Text Document.bin.exe (PID: 3968)
- New Text Document.exe (PID: 2108)
- eee01.exe (PID: 2024)
- svcs.exe (PID: 2456)
- start.exe (PID: 2364)
- regasms.exe (PID: 2324)
- Zinck2.exe (PID: 2632)
- STHealthUp.exe (PID: 3028)
- svchos.exe (PID: 2696)
- STHealthClient.exe (PID: 3912)
- Zinck2.exe (PID: 3496)
- jsc.exe (PID: 3856)
- GGWS_UPLOAD.exe (PID: 952)
- MyCheckBack.exe (PID: 2940)
Manual execution by a user
- New Text Document.exe (PID: 2108)
- wmpnscfg.exe (PID: 588)
- cmd.exe (PID: 1612)
- Zinck2.exe (PID: 3496)
- jsc.exe (PID: 3856)
- MartDrum.exe (PID: 1116)
Reads Environment values
- New Text Document.exe (PID: 2108)
- rem.exe (PID: 2472)
- svcs.exe (PID: 2456)
- regasms.exe (PID: 2324)
- svchos.exe (PID: 2696)
- STHealthClient.exe (PID: 3912)
- jsc.exe (PID: 3856)
Disables trace logs
- New Text Document.exe (PID: 2108)
- STHealthClient.exe (PID: 3912)
Reads the software policy settings
- New Text Document.exe (PID: 2108)
- regasms.exe (PID: 2324)
- Zinck2.exe (PID: 2632)
- svchos.exe (PID: 2696)
- Zinck2.exe (PID: 3496)
- jsc.exe (PID: 3856)
Checks transactions between databases Windows and Oracle
- eee01.exe (PID: 2024)
Reads security settings of Internet Explorer
- dllhost.exe (PID: 312)
Create files in a temporary directory
- MartDrum.exe (PID: 2092)
- New Text Document.exe (PID: 2108)
- start.exe (PID: 2364)
- Zinck2.exe (PID: 2632)
- IEUpdater2663.exe (PID: 2088)
- Fighting.pif (PID: 2460)
- Zinck2.exe (PID: 3496)
- MartDrum.exe (PID: 1116)
- IEUpdater2663.exe (PID: 580)
- svchos.exe (PID: 2696)
Reads mouse settings
- Fighting.pif (PID: 2460)
- Fighting.pif (PID: 1344)
- go.exe (PID: 2724)
Reads product name
- rem.exe (PID: 2472)
- svcs.exe (PID: 2456)
Creates files or folders in the user directory
- rem.exe (PID: 2472)
- Fighting.pif (PID: 2460)
- start.exe (PID: 2364)
- Zinck2.exe (PID: 2632)
Creates files in the program directory
- svcs.exe (PID: 2456)
- Zinck2.exe (PID: 2632)
Application launched itself
- msedge.exe (PID: 2540)
- msedge.exe (PID: 904)
- msedge.exe (PID: 2732)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Remcos
(PID) Process(2456) svcs.exe
C2 (1)leetboy.dynuddns.net:1998
BotnetRemote
Options
Connect_interval1
Install_flagTrue
Install_HKCU\RunTrue
Install_HKLM\RunTrue
Install_HKLM\Explorer\Run1
Install_HKLM\Winlogon\Shell100000
Setup_path%APPDATA%
Copy_filesvcs.exe
Startup_valueFalse
Hide_fileFalse
Mutex_nameRmc-3XK1S0
Keylog_flag1
Keylog_path%LOCALAPPDATA%
Keylog_filelogs.dat
Keylog_cryptTrue
Hide_keylogTrue
Screenshot_flagFalse
Screenshot_time5
Take_ScreenshotFalse
Screenshot_path%APPDATA%
Screenshot_fileScreenshots
Screenshot_cryptFalse
Mouse_optionFalse
Delete_fileFalse
Audio_record_time5
Audio_path%ProgramFiles%
Audio_dirMicRecords
Connect_delay0
Copy_dirmicrosofts
Keylog_dirlogsa
AsyncRat
(PID) Process(2324) regasms.exe
C2 (1)leetboy.dynuddns.net
Ports (1)1338
Version| Edit 3LOSH RAT
Options
AutoRunfalse
MutexAsyncMutex_6h2caasdas2133sOkPnk
InstallFolder%AppData%
Certificates
Cert1MIIE8jCCAtqgAwIBAgIQAPeWQ4YJ3MvReCGwLzn7rTANBgkqhkiG9w0BAQ0FADAaMRgwFgYDVQQDDA9Bc3luY1JBVCBTZXJ2ZXIwIBcNMjIwNDI1MDA0MTA5WhgPOTk5OTEyMzEyMzU5NTlaMBoxGDAWBgNVBAMMD0FzeW5jUkFUIFNlcnZlcjCCAiIwDQYJKoZIhvcNAQEBBQADggIPADCCAgoCggIBAKT9nYYTjYTZhY+g1tekZ8/F29gsEIDgf/8odvCbCmYKGGZZi2yND9NjtBXEMANM9PAXCyMapGva...
Server_SignaturehUCRKfWx9nGw5XGDblhiEIV3zURXPlpK8TiLmoZKV0mDdyxvPAOGKUqG22Ik3uOcZPytxZuF8v7OhIdgm9avNAph/boSR3vkxtiYrZU4J3JbwUkXTHRyWbqP/bDwR00KR4ySkAOcmpTrCPs5+VBNC4EAreSw/GILZhGD0YAa9d2LdzXNKUWMYMGTwN5rwD9Z9aDqcGlGIZgxIqCj4TcLpbFfuvC462FuWkhFjIo3IwHp0aaZFn6dWelpdBnfBlVn5bCTK/QiYqpSl+ZgBh1NQa2Yz7aYRFpLh+9Gx1UHosxd...
Keys
AESdc2604de1da7229b18926116abb0c0b1f81e84cda389e89ffad7cdbaaf4a2a48
Saltbfeb1e56fbcd973bb219022430a57843003d5644d21e62b9d4f180e7e6c33941
(PID) Process(3856) jsc.exe
C2 (1)leetman.dynuddns.com
Ports (1)1337
Version| Edit 3LOSH RAT
Options
AutoRunfalse
MutexAsyncMutex_6SI8asdasd2casOkPnk
InstallFolder%AppData%
Certificates
Cert1MIIE8jCCAtqgAwIBAgIQAPeWQ4YJ3MvReCGwLzn7rTANBgkqhkiG9w0BAQ0FADAaMRgwFgYDVQQDDA9Bc3luY1JBVCBTZXJ2ZXIwIBcNMjIwNDI1MDA0MTA5WhgPOTk5OTEyMzEyMzU5NTlaMBoxGDAWBgNVBAMMD0FzeW5jUkFUIFNlcnZlcjCCAiIwDQYJKoZIhvcNAQEBBQADggIPADCCAgoCggIBAKT9nYYTjYTZhY+g1tekZ8/F29gsEIDgf/8odvCbCmYKGGZZi2yND9NjtBXEMANM9PAXCyMapGva...
Server_SignatureIbuNhUBHIZ1xEnw2W+T0ktoQBPdl2eN+bFbGaSHnaXQWdBpXBtFcIPy9Kvo76G+Bqot+Mhbmdi45iMXnMd/XtW6hGIYpm1b65Yu9aW89anhCDFxtvTtQRtStn+mEI4HyLyQ/jEWSFx3J4uWsqaYt6M+nvgmrQd92SvWtxYC4AJ39P922sacmFLSsAsiSPJzJL4w3h+xlDMy6z6hQ9AASDqgU6h3bTNcR5v4xdNZyL0zg8dZzseqPd7WHqbIUXp2jf0UV01UrQWDnisTbZw52CbUDPjUOBD1GaOSf220w3MsM...
Keys
AES0ddff9ba1c73ebea6f3d16e8d8ccf4ed931b5562a16813d6bd25abaa5389e284
Saltbfeb1e56fbcd973bb219022430a57843003d5644d21e62b9d4f180e7e6c33941
TRiD
| .exe | | | Win32 Executable (generic) (52.9) |
|---|---|---|
| .exe | | | Generic Win/DOS Executable (23.5) |
| .exe | | | DOS Executable Generic (23.5) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2023:10:03 07:51:19+00:00 |
| ImageFileCharacteristics: | Executable, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 14.33 |
| CodeSize: | 214528 |
| InitializedDataSize: | 119296 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x21d50 |
| OSVersion: | 5.1 |
| ImageVersion: | - |
| SubsystemVersion: | 5.1 |
| Subsystem: | Windows GUI |
Total processes
144
Monitored processes
81
Malicious processes
21
Suspicious processes
4
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 304 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=renderer --disable-gpu-compositing --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=11 --mojo-platform-channel-handle=2208 --field-trial-handle=1380,i,14511711206539546345,13737973573951145760,131072 /prefetch:1 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Version: 109.0.1518.115 Modules
| |||||||||||||||
| 312 | C:\Windows\system32\DllHost.exe /Processid:{3E5FC7F9-9A51-4367-9063-A120244FBEC7} | C:\Windows\System32\dllhost.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: COM Surrogate Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 560 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=renderer --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=5 --mojo-platform-channel-handle=2156 --field-trial-handle=1380,i,14511711206539546345,13737973573951145760,131072 /prefetch:1 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Version: 109.0.1518.115 Modules
| |||||||||||||||
| 580 | "C:\ProgramData\IEUpdater2663\IEUpdater2663.exe" | C:\ProgramData\IEUpdater2663\IEUpdater2663.exe | Zinck2.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 588 | "C:\Program Files\Windows Media Player\wmpnscfg.exe" | C:\Program Files\Windows Media Player\wmpnscfg.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Media Player Network Sharing Service Configuration Application Exit code: 0 Version: 12.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 904 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --single-argument https://www.youtube.com/account | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | go.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
| 952 | "C:\Users\admin\Desktop\a\GGWS_UPLOAD.exe" | C:\Users\admin\Desktop\a\GGWS_UPLOAD.exe | — | New Text Document.exe | |||||||||||
User: admin Company: Microsoft Integrity Level: MEDIUM Description: GGWS_UPLOAD Version: 1.0.0.0 Modules
| |||||||||||||||
| 960 | ping -n 5 localhost | C:\Windows\System32\PING.EXE | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: TCP/IP Ping Command Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 992 | ping -n 5 localhost | C:\Windows\System32\PING.EXE | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: TCP/IP Ping Command Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1116 | "C:\Users\admin\Desktop\a\MartDrum.exe" | C:\Users\admin\Desktop\a\MartDrum.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
Total events
39 227
Read events
38 838
Write events
299
Delete events
90
Modification events
| (PID) Process: | (3968) New Text Document.bin.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (3968) New Text Document.bin.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (3968) New Text Document.bin.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (3968) New Text Document.bin.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (3968) New Text Document.bin.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (3968) New Text Document.bin.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (3968) New Text Document.bin.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (3968) New Text Document.bin.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\LowRegistry |
| Operation: | delete value | Name: | AddToFavoritesInitialSelection |
Value: | |||
| (PID) Process: | (3968) New Text Document.bin.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\LowRegistry |
| Operation: | delete value | Name: | AddToFeedsInitialSelection |
Value: | |||
| (PID) Process: | (2108) New Text Document.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\New Text Document_RASAPI32 |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
Executable files
22
Suspicious files
93
Text files
42
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2108 | New Text Document.exe | C:\Users\admin\Desktop\a\d.exe | executable | |
MD5:8E38E8ECD481EB08CEAA4AE363251311 | SHA256:036FB259B53E5DB9DBE7039BD4A2C5E2118B3242E38E9C0CC697E4E4C44B9F40 | |||
| 2092 | MartDrum.exe | C:\Users\admin\AppData\Local\Temp\7ZipSfx.000\Grocery | binary | |
MD5:7A10D8C21D509285032CCC39BE8CA70A | SHA256:7A4F7C61B90F5E0C6467EEF51446CBCCAF8E410117F4EC2DAD6B400CDC3BE9EE | |||
| 2092 | MartDrum.exe | C:\Users\admin\AppData\Local\Temp\7ZipSfx.000\Tunisia | text | |
MD5:89D7B6FAB91C718D1EB98295746B0E0E | SHA256:F593D273036A2DB89A963774319942D27D7DE6718033988297B5220E4566037B | |||
| 3968 | New Text Document.bin.exe | C:\Users\admin\Desktop\New Text Document.exe | executable | |
MD5:A239A27C2169AF388D4F5BE6B52F272C | SHA256:98E895F711226A32BFAB152E224279D859799243845C46E550C2D32153C619FC | |||
| 3968 | New Text Document.bin.exe | C:\Users\admin\Desktop\Пароли Chrome.csv | csv | |
MD5:64F50AFB35DD16EE46F187015CEE84CE | SHA256:C2D389870DE77426A31A8C478E0FDDCBBEA7A3733B453806317914E6F946EA91 | |||
| 2108 | New Text Document.exe | C:\Users\admin\AppData\Local\Temp\Cab59DA.tmp | compressed | |
MD5:29F65BA8E88C063813CC50A4EA544E93 | SHA256:1ED81FA8DFB6999A9FEDC6E779138FFD99568992E22D300ACD181A6D2C8DE184 | |||
| 2108 | New Text Document.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\77EC63BDA74BD0D0E0426DC8F8008506 | binary | |
MD5:FEF99FFD49B46C88F794DC724AF74C27 | SHA256:FEDF936168EDD39709D23C9A2E0B31768ABA755CE2B946D04E3B9A1B4A20DBF3 | |||
| 2108 | New Text Document.exe | C:\Users\admin\Desktop\a\start.exe | executable | |
MD5:C1ADE258F05C512E98EBC4D9D1165F8A | SHA256:447EAE52AB1979405497866C72DF7EC0703085AD6946AB0127F612B1518F8759 | |||
| 2108 | New Text Document.exe | C:\Users\admin\AppData\Local\Temp\Tar59DB.tmp | binary | |
MD5:435A9AC180383F9FA094131B173A2F7B | SHA256:67DC37ED50B8E63272B49A254A6039EE225974F1D767BB83EB1FD80E759A7C34 | |||
| 2020 | cmd.exe | C:\Users\admin\AppData\Local\Temp\7ZipSfx.000\1937\Fighting.pif | executable | |
MD5:848164D084384C49937F99D5B894253E | SHA256:F58D3A4B2F3F7F10815C24586FAE91964EEED830369E7E0701B43895B0CEFBD3 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
13
TCP/UDP connections
129
DNS requests
58
Threats
160
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 94.156.66.179:80 | http://94.156.66.179/start.exe | unknown | — | — | unknown |
2108 | New Text Document.exe | GET | 200 | 94.232.45.38:80 | http://94.232.45.38/eee01/eee01.exe | unknown | — | — | unknown |
2108 | New Text Document.exe | GET | 200 | 23.50.131.200:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab?12e27d4abf843930 | unknown | — | — | unknown |
2108 | New Text Document.exe | GET | 200 | 94.156.66.179:80 | http://94.156.66.179/rem.exe | unknown | — | — | unknown |
2108 | New Text Document.exe | GET | 200 | 47.104.173.216:8081 | http://47.104.173.216:8081/STHealthUp.exe | unknown | — | — | unknown |
2108 | New Text Document.exe | GET | 200 | 47.104.173.216:8081 | http://47.104.173.216:8081/GGWS_UPLOAD.exe | unknown | — | — | unknown |
2108 | New Text Document.exe | GET | 200 | 47.104.173.216:8081 | http://47.104.173.216:8081/STHealthClient.exe | unknown | — | — | unknown |
3912 | STHealthClient.exe | GET | 200 | 47.104.173.216:8081 | http://47.104.173.216:8081/STHealthUpdate.exe | unknown | — | — | unknown |
3912 | STHealthClient.exe | GET | 200 | 47.104.173.216:8081 | http://47.104.173.216:8081/server.txt | unknown | — | — | unknown |
2108 | New Text Document.exe | GET | 200 | 114.132.120.166:8080 | http://114.132.120.166:8080/beacon.exe | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 224.0.0.252:5355 | — | — | — | unknown |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1088 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
2108 | New Text Document.exe | 151.101.194.49:443 | urlhaus.abuse.ch | FASTLY | US | unknown |
2108 | New Text Document.exe | 94.232.45.38:80 | — | Belcloud LTD | RU | unknown |
2108 | New Text Document.exe | 109.70.148.130:443 | atou.mg | Hydra Communications Ltd | GB | unknown |
2108 | New Text Document.exe | 207.180.242.32:443 | appz.dieera.com | Contabo GmbH | DE | unknown |
2108 | New Text Document.exe | 172.67.197.239:443 | postaipay.top | CLOUDFLARENET | US | unknown |
2108 | New Text Document.exe | 94.156.66.179:80 | — | Terasyst Ltd | BG | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
urlhaus.abuse.ch |
| whitelisted |
atou.mg |
| unknown |
appz.dieera.com |
| unknown |
postaipay.top |
| unknown |
areekat-aldeera.com |
| unknown |
www.vga.areekat-aldeera.com |
| unknown |
ctldl.windowsupdate.com |
| whitelisted |
vga.areekat-aldeera.com |
| unknown |
leetboy.dynuddns.net |
| malicious |
ILEBAjQfqsOIasLkjMdYuEw.ILEBAjQfqsOIasLkjMdYuEw |
| unknown |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2108 | New Text Document.exe | Potentially Bad Traffic | ET INFO Executable Download from dotted-quad Host |
2108 | New Text Document.exe | Potential Corporate Privacy Violation | ET POLICY PE EXE or DLL Windows file download HTTP |
2108 | New Text Document.exe | Potentially Bad Traffic | ET INFO Executable Retrieved With Minimal HTTP Headers - Potential Second Stage Download |
2108 | New Text Document.exe | Potentially Bad Traffic | ET HUNTING SUSPICIOUS Dotted Quad Host MZ Response |
2108 | New Text Document.exe | Misc activity | ET INFO EXE IsDebuggerPresent (Used in Malware Anti-Debugging) |
1088 | svchost.exe | Potentially Bad Traffic | ET DNS Query to a *.top domain - Likely Hostile |
2108 | New Text Document.exe | Potentially Bad Traffic | ET INFO Executable Download from dotted-quad Host |
2108 | New Text Document.exe | Potential Corporate Privacy Violation | ET POLICY PE EXE or DLL Windows file download HTTP |
2108 | New Text Document.exe | Potentially Bad Traffic | ET INFO Executable Retrieved With Minimal HTTP Headers - Potential Second Stage Download |
2108 | New Text Document.exe | Potentially Bad Traffic | ET HUNTING SUSPICIOUS Dotted Quad Host MZ Response |
2 ETPRO signatures available at the full report
Process | Message |
|---|---|
Zinck2.exe | ret 345 fdhg r |
Zinck2.exe | tr 656 56 65 8658 658hfty |
Zinck2.exe | er er y try rtsdh |
Zinck2.exe | h6rt hrd54 |
Zinck2.exe | ret 345 fdhg r |
Zinck2.exe | er er y try rtsdh |
Zinck2.exe | tr 656 56 65 8658 658hfty |
Zinck2.exe | h6rt hrd54 |