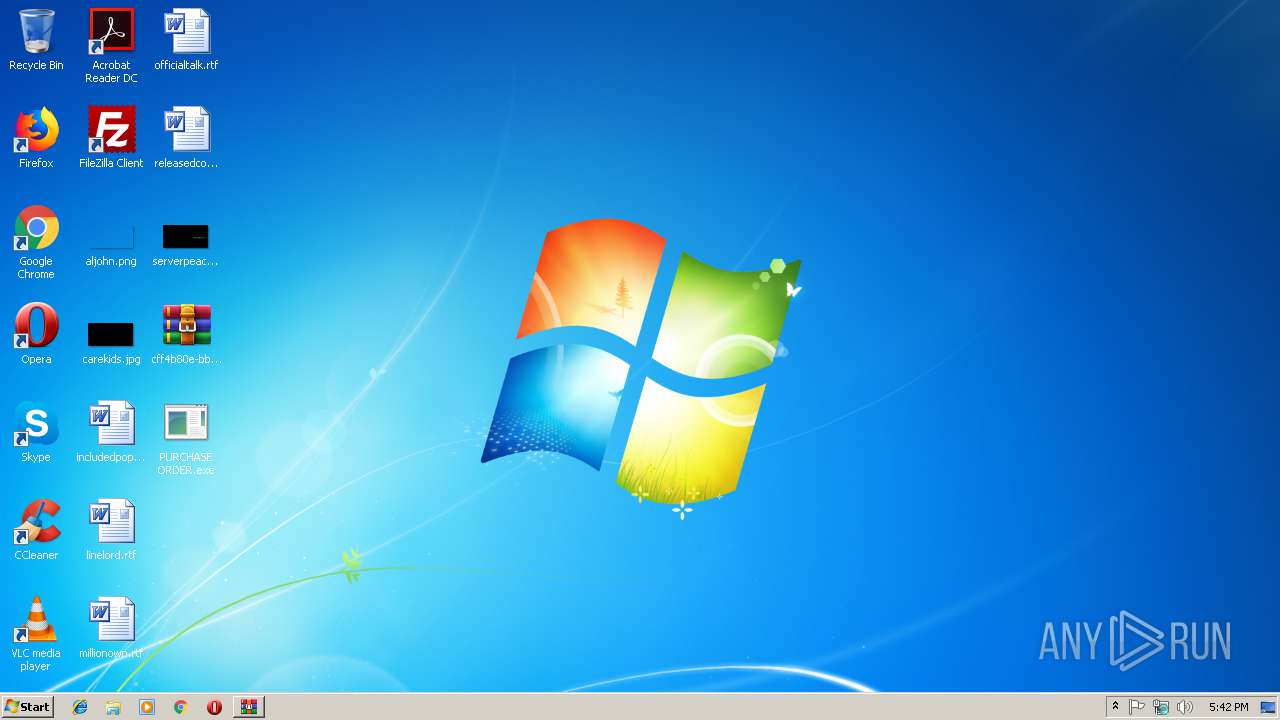
| download: | PURCHASE%20ORDER.lzh |
| Full analysis: | https://app.any.run/tasks/de23bfe7-1278-498e-8444-d1acf834516d |
| Verdict: | Malicious activity |
| Threats: | FormBook is a data stealer that is being distributed as a MaaS. FormBook differs from a lot of competing malware by its extreme ease of use that allows even the unexperienced threat actors to use FormBook virus. |
| Analysis date: | January 22, 2019, 17:41:21 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v5 |
| MD5: | CB81DD9A8C895E34DA57F1591C4C7477 |
| SHA1: | 8B41800F27BD3501EA56C5556CDBE73A1DFDC632 |
| SHA256: | A66BCFED1504E5657689999D59C9CE59EEE692554C66D8BB42F39CB21FAC42EE |
| SSDEEP: | 6144:YKIsAH6OSCLXBXfJ+aHu5MVYbmkuIMKPxd9dBLEZpk9oaQTSYeBp/kBaV6Kgz00i:YSAH6OPLBfJ1Hu5MVYaGMKJdOZp1T6/Z |
MALICIOUS
Application was dropped or rewritten from another process
- PURCHASE ORDER.exe (PID: 2996)
- app.exe (PID: 3264)
- app.exe (PID: 3148)
- configrxopljmx.exe (PID: 2808)
- app.exe (PID: 1156)
Writes to a start menu file
- cmd.exe (PID: 4068)
- cmd.exe (PID: 1592)
Changes the autorun value in the registry
- dwm.exe (PID: 3800)
- app.exe (PID: 3148)
FORMBOOK was detected
- explorer.exe (PID: 2028)
Connects to CnC server
- explorer.exe (PID: 2028)
Formbook was detected
- dwm.exe (PID: 3800)
- Firefox.exe (PID: 3324)
Actions looks like stealing of personal data
- dwm.exe (PID: 3800)
Stealing of credential data
- dwm.exe (PID: 3800)
SUSPICIOUS
Executable content was dropped or overwritten
- explorer.exe (PID: 2028)
- WinRAR.exe (PID: 3044)
- cmd.exe (PID: 4068)
- DllHost.exe (PID: 3672)
- dwm.exe (PID: 3800)
- cmd.exe (PID: 1592)
Starts CMD.EXE for commands execution
- PURCHASE ORDER.exe (PID: 2996)
- dwm.exe (PID: 3800)
- configrxopljmx.exe (PID: 2808)
Creates files in the user directory
- explorer.exe (PID: 2028)
- cmd.exe (PID: 4068)
- dwm.exe (PID: 3800)
- cmd.exe (PID: 1592)
Application launched itself
- app.exe (PID: 3148)
Reads Internet Cache Settings
- explorer.exe (PID: 2028)
Loads DLL from Mozilla Firefox
- dwm.exe (PID: 3800)
Creates files in the program directory
- DllHost.exe (PID: 3672)
INFO
Dropped object may contain Bitcoin addresses
- WinRAR.exe (PID: 3044)
- cmd.exe (PID: 4068)
- explorer.exe (PID: 2028)
- cmd.exe (PID: 1592)
- DllHost.exe (PID: 3672)
Creates files in the user directory
- Firefox.exe (PID: 3324)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v5.0) (61.5) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (38.4) |
Total processes
52
Monitored processes
15
Malicious processes
4
Suspicious processes
3
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1156 | "C:\Users\admin\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\app.exe" | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\app.exe | — | cmd.exe | |||||||||||
User: admin Company: Pinnacle West Capital Corp Integrity Level: MEDIUM Description: Application Server Command Line Admin Too Exit code: 0 Version: 12.6.22.2 Modules
| |||||||||||||||
| 1204 | "C:\Windows\System32\cmd.exe" /c, "C:\Users\admin\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\app.exe" | C:\Windows\System32\cmd.exe | — | configrxopljmx.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 1592 | "C:\Windows\System32\cmd.exe" /c copy "C:\Program Files\Txnjhcxyh\configrxopljmx.exe" "C:\Users\admin\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\app.exe" | C:\Windows\System32\cmd.exe | configrxopljmx.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 2028 | C:\Windows\Explorer.EXE | C:\Windows\explorer.exe | — | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2496 | "C:\Windows\System32\cmd.exe" /c, "C:\Users\admin\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\app.exe" | C:\Windows\System32\cmd.exe | — | PURCHASE ORDER.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 2576 | /c del "C:\Users\admin\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\app.exe" | C:\Windows\System32\cmd.exe | — | dwm.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 2808 | "C:\Program Files\Txnjhcxyh\configrxopljmx.exe" | C:\Program Files\Txnjhcxyh\configrxopljmx.exe | — | explorer.exe | |||||||||||
User: admin Company: Pinnacle West Capital Corp Integrity Level: MEDIUM Description: Application Server Command Line Admin Too Exit code: 0 Version: 12.6.22.2 Modules
| |||||||||||||||
| 2996 | "C:\Users\admin\Desktop\PURCHASE ORDER.exe" | C:\Users\admin\Desktop\PURCHASE ORDER.exe | — | explorer.exe | |||||||||||
User: admin Company: Pinnacle West Capital Corp Integrity Level: MEDIUM Description: Application Server Command Line Admin Too Exit code: 0 Version: 12.6.22.2 Modules
| |||||||||||||||
| 3044 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\Desktop\cff4b80e-bbb3-40c5-8cfc-6e469cedb3f5.rar" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
| 3148 | "C:\Users\admin\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\app.exe" | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\app.exe | cmd.exe | ||||||||||||
User: admin Company: Pinnacle West Capital Corp Integrity Level: MEDIUM Description: Application Server Command Line Admin Too Exit code: 0 Version: 12.6.22.2 Modules
| |||||||||||||||
Total events
5 254
Read events
5 203
Write events
49
Delete events
2
Modification events
| (PID) Process: | (3044) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (3044) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (3044) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\5F\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3044) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\cff4b80e-bbb3-40c5-8cfc-6e469cedb3f5.rar | |||
| (PID) Process: | (3044) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3044) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3044) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (3044) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (2028) explorer.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\FileExts\.rar\OpenWithList |
| Operation: | write | Name: | a |
Value: WinRAR.exe | |||
| (PID) Process: | (2028) explorer.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\FileExts\.rar\OpenWithList |
| Operation: | write | Name: | MRUList |
Value: a | |||
Executable files
7
Suspicious files
74
Text files
1
Unknown types
4
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2028 | explorer.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\History\History.IE5\MSHist012019012220190123\index.dat | dat | |
MD5:— | SHA256:— | |||
| 2028 | explorer.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\AutomaticDestinations\290532160612e071.automaticDestinations-ms | automaticdestinations-ms | |
MD5:— | SHA256:— | |||
| 2028 | explorer.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\cff4b80e-bbb3-40c5-8cfc-6e469cedb3f5.rar.lnk | lnk | |
MD5:— | SHA256:— | |||
| 3800 | dwm.exe | C:\Users\admin\AppData\Roaming\L13QQC3E\L13logrc.ini | binary | |
MD5:— | SHA256:— | |||
| 2028 | explorer.exe | C:\Users\admin\Desktop\PURCHASE ORDER.exe | executable | |
MD5:— | SHA256:— | |||
| 3044 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3044.42166\PURCHASE ORDER.exe | executable | |
MD5:— | SHA256:— | |||
| 4068 | cmd.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\app.exe | executable | |
MD5:— | SHA256:— | |||
| 3800 | dwm.exe | C:\Users\admin\AppData\Roaming\L13QQC3E\L13logim.jpeg | image | |
MD5:— | SHA256:— | |||
| 3324 | Firefox.exe | C:\Users\admin\AppData\Roaming\L13QQC3E\L13logrf.ini | binary | |
MD5:— | SHA256:— | |||
| 3800 | dwm.exe | C:\Users\admin\AppData\Roaming\L13QQC3E\L13logrv.ini | binary | |
MD5:BA3B6BC807D4F76794C4B81B09BB9BA5 | SHA256:6EEBF968962745B2E9DE2CA969AF7C424916D4E3FE3CC0BB9B3D414ABFCE9507 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
17
TCP/UDP connections
17
DNS requests
8
Threats
32
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2028 | explorer.exe | GET | — | 184.168.221.48:80 | http://www.trevorfetter.info/cu/?1b=QEXX3Vha/LFA1W4yfgnrhRSY4dHBT/5KY6lE5xBMLcQYuMtG6KyE1myNqYqa0uTFxpxNUg==&PV=bl1TDBMX&sql=1 | US | — | — | malicious |
2028 | explorer.exe | GET | — | 81.88.57.68:80 | http://www.my-financement.com/cu/?1b=p1um2x2awrdWxDuogR27tR6dMGPoltvHu5fZl/LgUKClkw2Js/1lx21OywqyzRUexysFeA==&PV=bl1TDBMX&sql=1 | IT | — | — | malicious |
2028 | explorer.exe | GET | 404 | 74.63.242.18:80 | http://www.invictnet.com/cu/?1b=4x9hiDMMBqRJOeV4nD4RuIc6oO02DiqRDcs3ioPu2jDwMxi4iYjZlJ7Fw8A5fh/yLXjigw==&PV=bl1TDBMX | US | html | 320 b | malicious |
2028 | explorer.exe | POST | — | 81.88.57.68:80 | http://www.my-financement.com/cu/ | IT | — | — | malicious |
2028 | explorer.exe | POST | — | 81.88.57.68:80 | http://www.my-financement.com/cu/ | IT | — | — | malicious |
2028 | explorer.exe | POST | — | 81.88.57.68:80 | http://www.my-financement.com/cu/ | IT | — | — | malicious |
2028 | explorer.exe | POST | — | 42.51.10.228:80 | http://www.xiaopangdashang.com/cu/ | CN | — | — | malicious |
2028 | explorer.exe | GET | — | 42.51.10.228:80 | http://www.xiaopangdashang.com/cu/?1b=pwOjNDcdZ/fLCpHqPGy78a52QHRvh++WZCSaKKihGh3UKww8afvtL6v3BtLe8uK/1vSGEg==&PV=bl1TDBMX&sql=1 | CN | — | — | malicious |
2028 | explorer.exe | GET | 200 | 192.64.115.82:80 | http://www.dronlac.com/cu/?1b=twhE5n0oBcR/6a+q28Yit8sxGnt5zk5TgyzWOrLjD4+9Qa3pu1EcFkU3uKAVihAkR52K3w==&PV=bl1TDBMX&sql=1 | US | binary | 323 Kb | malicious |
2028 | explorer.exe | POST | — | 42.51.10.228:80 | http://www.xiaopangdashang.com/cu/ | CN | — | — | malicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2028 | explorer.exe | 74.63.242.18:80 | www.invictnet.com | Limestone Networks, Inc. | US | suspicious |
2028 | explorer.exe | 184.168.221.48:80 | www.trevorfetter.info | GoDaddy.com, LLC | US | malicious |
2028 | explorer.exe | 81.88.57.68:80 | www.my-financement.com | Register.it SpA | IT | malicious |
2028 | explorer.exe | 42.51.10.228:80 | www.xiaopangdashang.com | Henan Telcom Union Technology Co., LTD | CN | malicious |
2028 | explorer.exe | 192.64.115.82:80 | www.dronlac.com | Namecheap, Inc. | US | malicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.videomusikmp3.review |
| unknown |
www.dirsphoabloi.biz |
| unknown |
www.girlsinsocial.com |
| unknown |
www.invictnet.com |
| malicious |
www.trevorfetter.info |
| malicious |
www.my-financement.com |
| malicious |
www.xiaopangdashang.com |
| malicious |
www.dronlac.com |
| malicious |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2028 | explorer.exe | A Network Trojan was detected | SC TROJAN_DOWNLOADER Suspicious HTTP-GET request with body and minimal header |
2028 | explorer.exe | A Network Trojan was detected | MALWARE [PTsecurity] FormBook CnC Checkin (GET) |
2028 | explorer.exe | A Network Trojan was detected | SC TROJAN_DOWNLOADER Suspicious HTTP-GET request with body and minimal header |
2028 | explorer.exe | A Network Trojan was detected | MALWARE [PTsecurity] FormBook CnC Checkin (GET) |
2028 | explorer.exe | A Network Trojan was detected | MALWARE [PTsecurity] FormBook CnC Checkin (POST) |
2028 | explorer.exe | A Network Trojan was detected | MALWARE [PTsecurity] TrojanSpy:FormBook CnC Checkin (POST) |
2028 | explorer.exe | A Network Trojan was detected | MALWARE [PTsecurity] TrojanSpy:FormBook CnC Checkin (POST) |
2028 | explorer.exe | A Network Trojan was detected | SC TROJAN_DOWNLOADER Suspicious HTTP-GET request with body and minimal header |
2028 | explorer.exe | A Network Trojan was detected | MALWARE [PTsecurity] FormBook CnC Checkin (GET) |
2028 | explorer.exe | A Network Trojan was detected | MALWARE [PTsecurity] TrojanSpy:FormBook CnC Checkin (POST) |
13 ETPRO signatures available at the full report