| File name: | demo-sample.msg |
| Full analysis: | https://app.any.run/tasks/feaddc60-480c-46d9-a547-3816b07e0243 |
| Verdict: | Malicious activity |
| Threats: | LokiBot was developed in 2015 to steal information from a variety of applications. Despite the age, this malware is still rather popular among cybercriminals. |
| Analysis date: | June 01, 2025, 22:09:34 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.ms-outlook |
| File info: | CDFV2 Microsoft Outlook Message |
| MD5: | A67B03F57933663D0779115B74A4B2E3 |
| SHA1: | 5C4D663A15E428F1367A42406D5C7B78524B48F9 |
| SHA256: | A6189266C815831C91E79464638DA6249C3D27D6EE06C524434A99FE9F7BB689 |
| SSDEEP: | 24576:MafQNcq5V8m16Yru0Oec7UYPJROYDU5m8XUBt4wZlGYCq1wSpdJkkN4+:MafQWq5V8m16Yru0OecAYPJROY+m8kBL |
MALICIOUS
Lokibot is detected
- cvtres.exe (PID: 7516)
LOKIBOT mutex has been found
- cvtres.exe (PID: 7516)
Steals credentials from Web Browsers
- cvtres.exe (PID: 7516)
Actions looks like stealing of personal data
- cvtres.exe (PID: 7516)
LOKIBOT has been detected (YARA)
- cvtres.exe (PID: 7516)
XORed URL has been found (YARA)
- cvtres.exe (PID: 7516)
Scans artifacts that could help determine the target
- cvtres.exe (PID: 7516)
SUSPICIOUS
Process drops legitimate windows executable
- cvtres.exe (PID: 7516)
Reads security settings of Internet Explorer
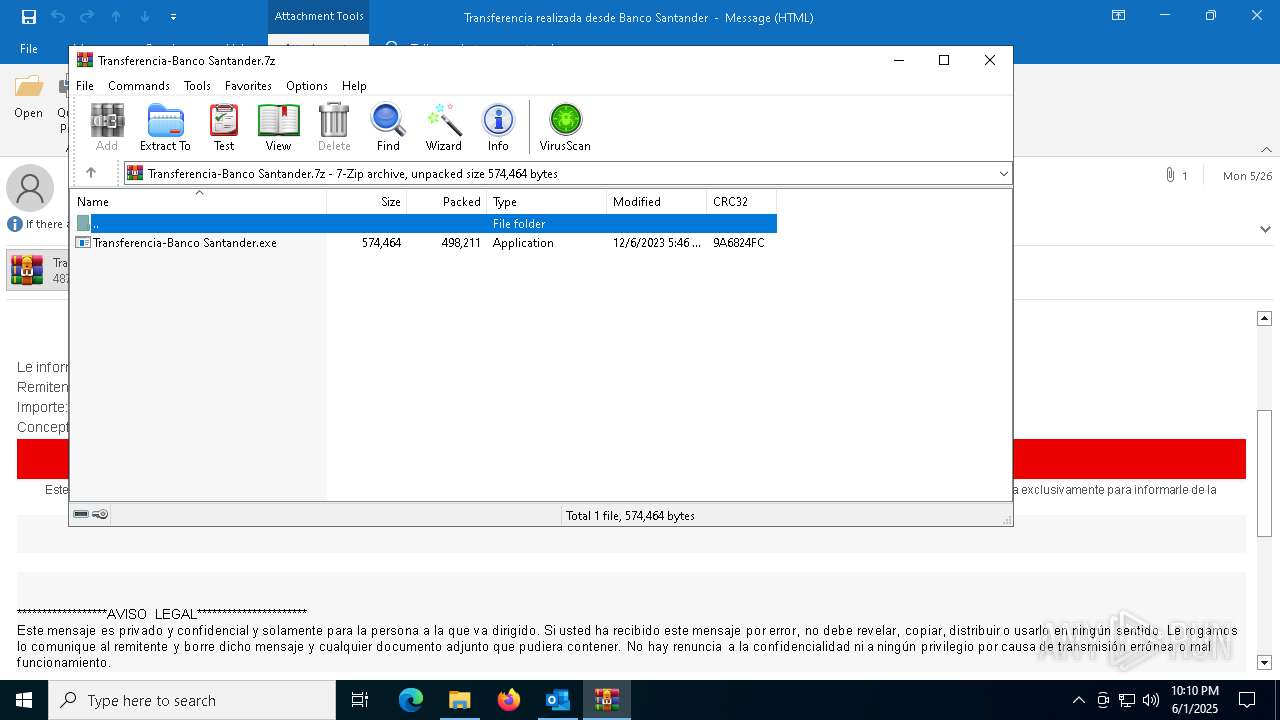
- WinRAR.exe (PID: 7976)
- cvtres.exe (PID: 7516)
Executable content was dropped or overwritten
- cvtres.exe (PID: 7516)
INFO
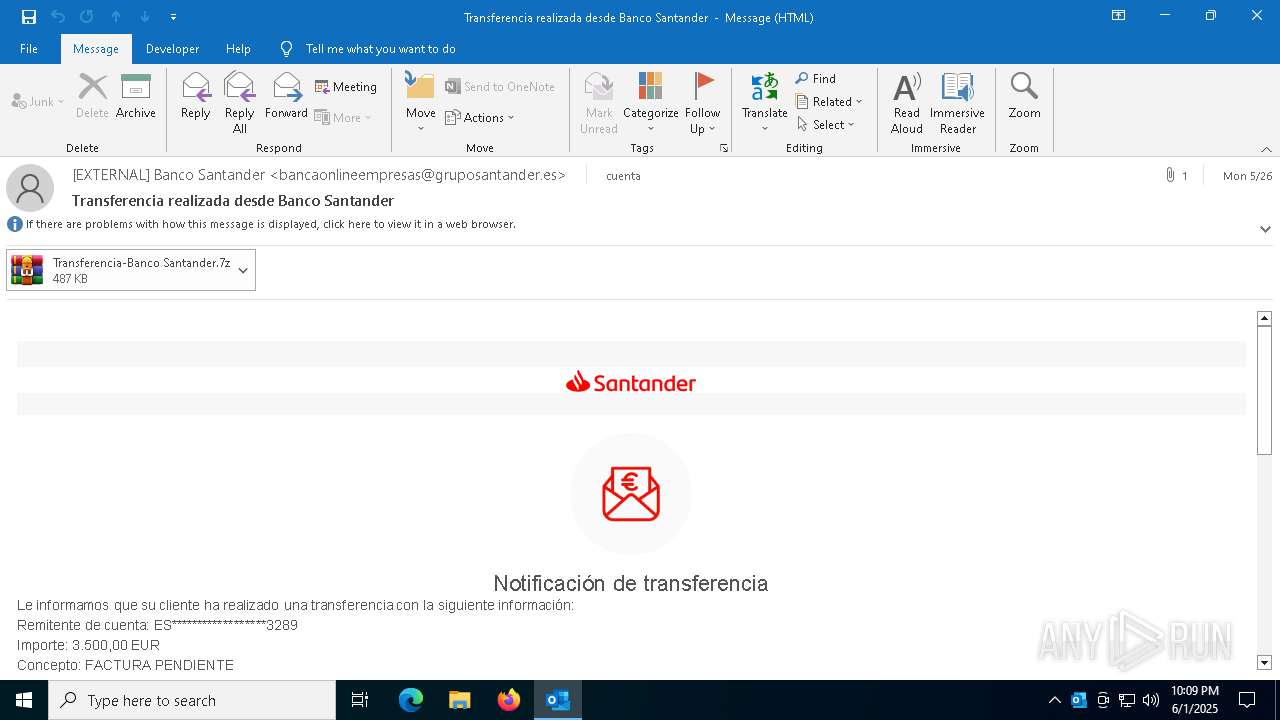
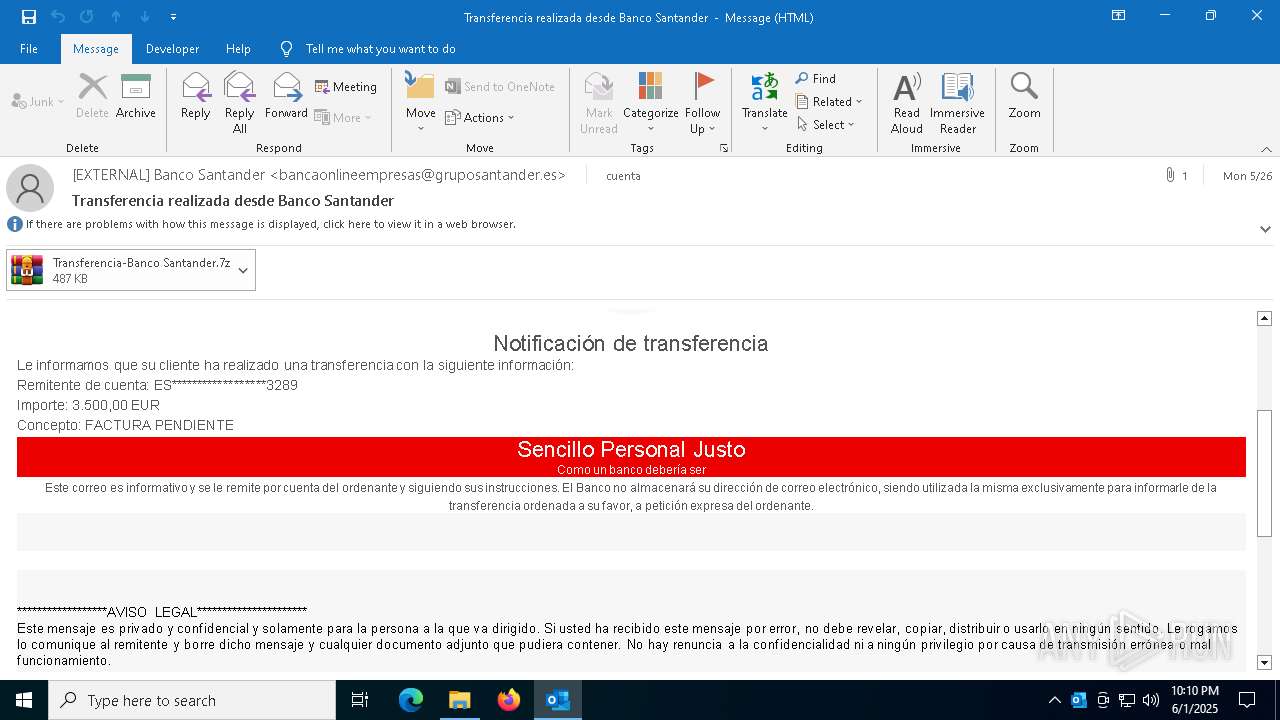
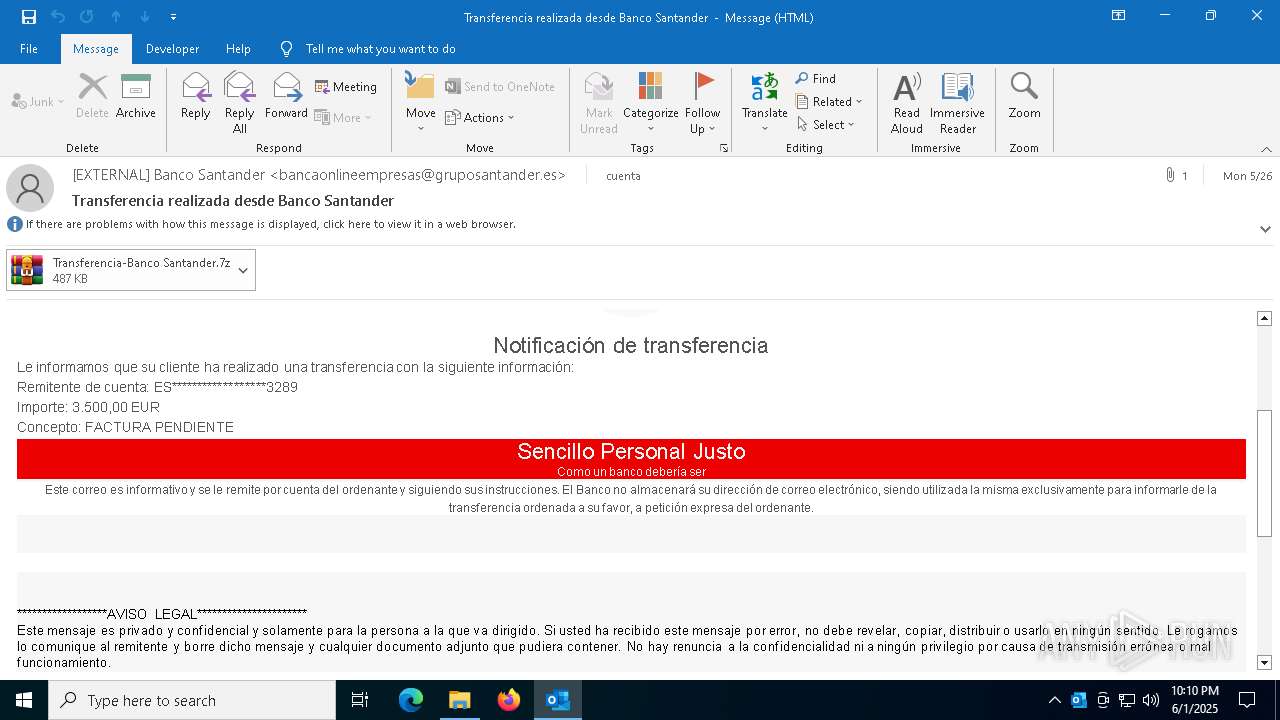
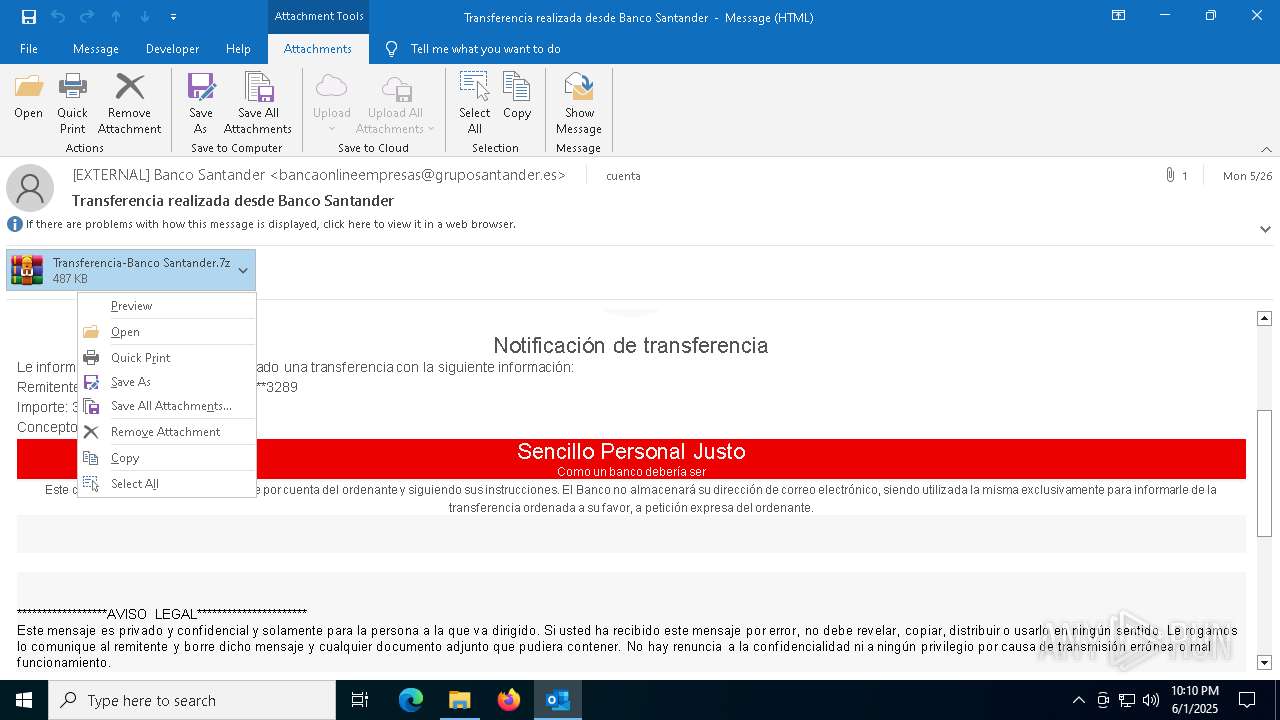
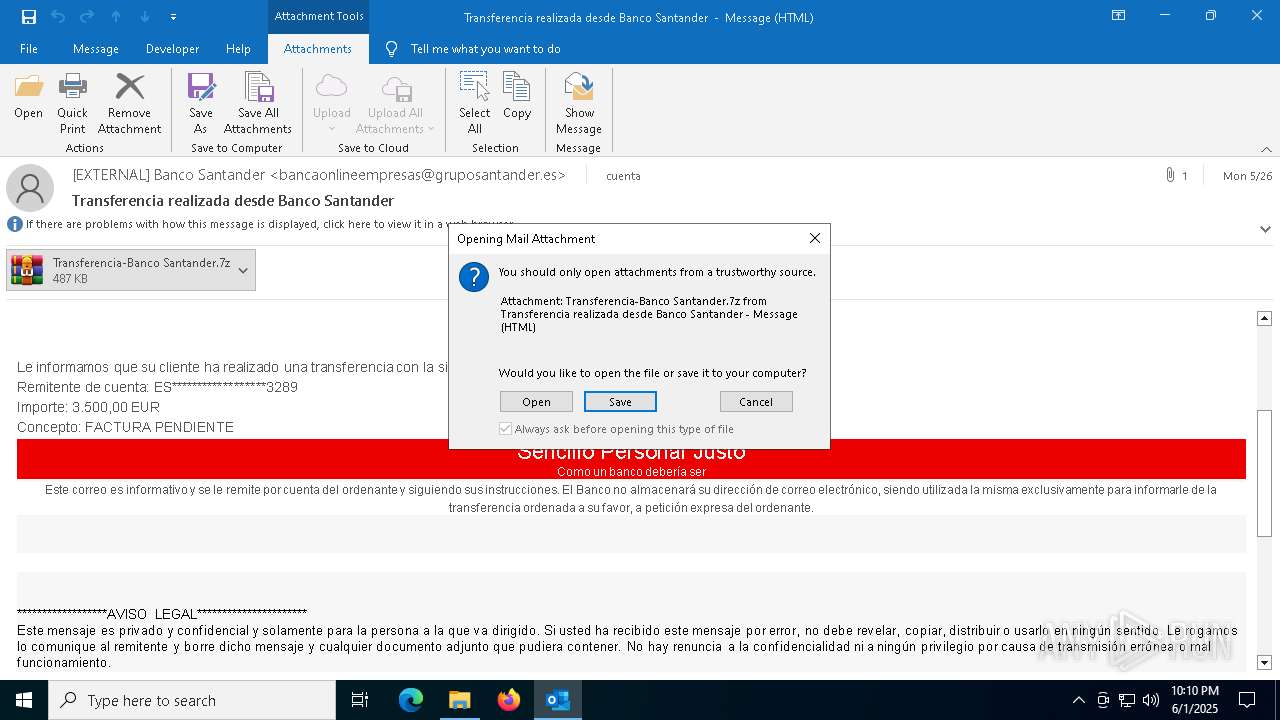
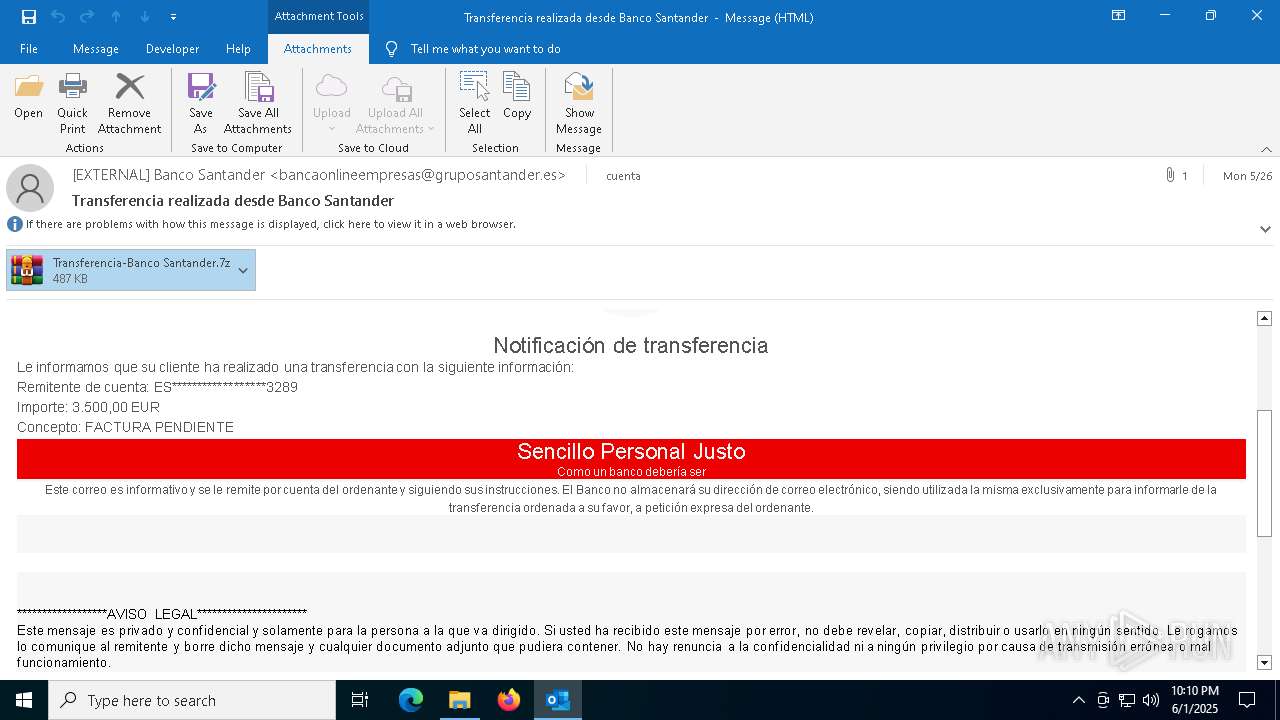
Email with attachments
- OUTLOOK.EXE (PID: 1164)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 7976)
Checks supported languages
- cvtres.exe (PID: 7516)
- Transferencia-Banco Santander.exe (PID: 6564)
Reads the computer name
- Transferencia-Banco Santander.exe (PID: 6564)
- cvtres.exe (PID: 7516)
Reads the machine GUID from the registry
- Transferencia-Banco Santander.exe (PID: 6564)
- cvtres.exe (PID: 7516)
Manual execution by a user
- mspaint.exe (PID: 7260)
The sample compiled with english language support
- cvtres.exe (PID: 7516)
Reads the software policy settings
- slui.exe (PID: 1188)
- slui.exe (PID: 2552)
Checks proxy server information
- slui.exe (PID: 2552)
Reads Microsoft Office registry keys
- cvtres.exe (PID: 7516)
Creates files or folders in the user directory
- cvtres.exe (PID: 7516)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .msg | | | Outlook Message (58.9) |
|---|---|---|
| .oft | | | Outlook Form Template (34.4) |
Total processes
143
Monitored processes
10
Malicious processes
4
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1164 | "C:\Program Files\Microsoft Office\Root\Office16\OUTLOOK.EXE" /f C:\Users\admin\AppData\Local\Temp\demo-sample.msg | C:\Program Files\Microsoft Office\root\Office16\OUTLOOK.EXE | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Outlook Version: 16.0.16026.20146 Modules
| |||||||||||||||
| 1188 | "C:\WINDOWS\System32\SLUI.exe" RuleId=3482d82e-ca2c-4e1f-8864-da0267b484b2;Action=AutoActivate;AppId=55c92734-d682-4d71-983e-d6ec3f16059f;SkuId=4de7cb65-cdf1-4de9-8ae8-e3cce27b9f2c;NotificationInterval=1440;Trigger=TimerEvent | C:\Windows\System32\slui.exe | SppExtComObj.Exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Activation Client Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2552 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5400 | C:\WINDOWS\system32\SppExtComObj.exe -Embedding | C:\Windows\System32\SppExtComObj.Exe | — | svchost.exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: KMS Connection Broker Exit code: 0 Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6384 | "C:\Program Files\Microsoft Office\root\VFS\ProgramFilesCommonX64\Microsoft Shared\OFFICE16\ai.exe" "61FAEAEC-C512-45EB-B466-E7E68FF507D2" "9256687B-97F4-41CB-A138-9602E52CC27F" "1164" | C:\Program Files\Microsoft Office\root\VFS\ProgramFilesCommonX64\Microsoft Shared\OFFICE16\ai.exe | — | OUTLOOK.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Artificial Intelligence (AI) Host for the Microsoft® Windows® Operating System and Platform x64. Version: 0.12.2.0 Modules
| |||||||||||||||
| 6564 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa7976.14849\Transferencia-Banco Santander.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa7976.14849\Transferencia-Banco Santander.exe | — | WinRAR.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: MKiJ887777 Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 7260 | "C:\WINDOWS\system32\mspaint.exe" "C:\Users\admin\Downloads\leavecomplete.png" | C:\Windows\System32\mspaint.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Paint Exit code: 0 Version: 10.0.19041.3758 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7296 | C:\WINDOWS\System32\rundll32.exe C:\WINDOWS\System32\shell32.dll,SHCreateLocalServerRunDll {9aa46009-3ce0-458a-a354-715610a075e6} -Embedding | C:\Windows\System32\rundll32.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7516 | "C:\Windows\Microsoft.NET\Framework\v4.0.30319\cvtres.exe" | C:\Windows\Microsoft.NET\Framework\v4.0.30319\cvtres.exe | Transferencia-Banco Santander.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft® Resource File To COFF Object Conversion Utility Version: 14.32.31326.0 Modules
| |||||||||||||||
| 7976 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\Content.Outlook\GDW51GGD\Transferencia-Banco Santander.7z" | C:\Program Files\WinRAR\WinRAR.exe | OUTLOOK.EXE | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
Total events
16 135
Read events
14 873
Write events
1 112
Delete events
150
Modification events
| (PID) Process: | (1164) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\Common\ClientTelemetry\Sampling |
| Operation: | write | Name: | 6 |
Value: 01941A000000001000B24E9A3E06000000000000000600000000000000 | |||
| (PID) Process: | (1164) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\Common\CrashPersistence\OUTLOOK\1164 |
| Operation: | write | Name: | 0 |
Value: 0B0E10B95FD719C5BA544083B1D14F369D7923230046869BB3FE9DE8F4ED016A04102400449A7D64B29D01008500A907556E6B6E6F776EC906022222CA0DC2190000C91003783634C5118C09D2120B6F00750074006C006F006F006B002E00650078006500C51620C517808004C91808323231322D44656300 | |||
| (PID) Process: | (1164) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Outlook\Diagnostics |
| Operation: | delete value | Name: | BootCommand |
Value: | |||
| (PID) Process: | (1164) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Outlook\Diagnostics\BootDiagnosticsData |
| Operation: | write | Name: | SessionId |
Value: 19D75FB9-BAC5-4054-83B1-D14F369D7923 | |||
| (PID) Process: | (1164) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Outlook\Diagnostics |
| Operation: | delete value | Name: | BootFailureCount |
Value: | |||
| (PID) Process: | (1164) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Outlook\Profiles\Outlook\0a0d020000000000c000000000000046 |
| Operation: | write | Name: | 00030429 |
Value: 09000000 | |||
| (PID) Process: | (1164) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Outlook\Diagnostics\BootDiagnosticsData |
| Operation: | write | Name: | ProfileBeingOpened |
Value: Outlook | |||
| (PID) Process: | (1164) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Outlook\Profiles\Outlook\0a0d020000000000c000000000000046 |
| Operation: | write | Name: | 00030397 |
Value: 60000000 | |||
| (PID) Process: | (1164) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\Experiment\outlook |
| Operation: | write | Name: | BuildNumber |
Value: 16.0.16026 | |||
| (PID) Process: | (1164) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\ExperimentConfigs\Ecs\outlook |
| Operation: | write | Name: | Expires |
Value: int64_t|0 | |||
Executable files
2
Suspicious files
10
Text files
8
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1164 | OUTLOOK.EXE | C:\Users\admin\Documents\Outlook Files\Outlook1.pst | — | |
MD5:— | SHA256:— | |||
| 1164 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\TokenBroker\Cache\089d66ba04a8cec4bdc5267f42f39cf84278bb67.tbres | binary | |
MD5:C9DFCC6D7AA1E799009AD7211A2BCBF0 | SHA256:1A58F0AB9137D131FD8098947273A219722E6253B7E7B14FA413DC55AEDE9D03 | |||
| 1164 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\TokenBroker\Cache\56a61aeb75d8f5be186c26607f4bb213abe7c5ec.tbres | binary | |
MD5:FEDADA88AF9A336002C54B82F3942090 | SHA256:77524B0A82A94033FE9B4290CC359C31411457BE67C2C4205CF5CCA011AB0D48 | |||
| 1164 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Office\16.0\AddInClassifierCache\OfficeSharedEntitiesUpdated.bin | text | |
MD5:132AAEEE896CA30FF234A376D60BA158 | SHA256:C2F79D0307CC657406C73E241C4AB06CFAA708578B9C0BE609737B8EC9F7BDF0 | |||
| 1164 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\Content.Outlook\GDW51GGD\Transferencia-Banco Santander.7z | compressed | |
MD5:1A19E68F34BD318980D39B2CF0CD9918 | SHA256:DC5B31FCBB13B0FEA350BC82F98B74C9E9F7031720B9D6D0254B521607920C3B | |||
| 1164 | OUTLOOK.EXE | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\E2C6CBAF0AF08CF203BA74BF0D0AB6D5_6372E0472AFF76BB926C97818BC773B9 | binary | |
MD5:81266F284EC56BA00847118B903C6B4F | SHA256:B7D7AE372861376D19F3A7CF2E23622E1921AE5140B295B6F32A550C78DC0725 | |||
| 1164 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Outlook\RoamCache\Stream_TableViewPreviewPrefs_2_B499A185902BC349B9637C7F52325437.dat | xml | |
MD5:0E092DB99AEE99FDFF9B5B222C732CFD | SHA256:D1614AD99ADED9F6F5C1BE7FE7FFA5124BD04A526580DA3818EA8A954E852AA6 | |||
| 1164 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\Content.MSO\357DE9B0.dat | image | |
MD5:6F44F45C9077DC98816F4B88255005B3 | SHA256:ED340E5CB087125C72A498A4F603D57B6591D37D638F7A4ABFBC86E98270C883 | |||
| 1164 | OUTLOOK.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Templates\~$rmalEmail.dotm | binary | |
MD5:10A58A3B3AD8B0C3458684B0A8D55C74 | SHA256:8260099B2A424A65F42C4B588F94A2ED7365383F123AB0C7FD4F438B32BDB809 | |||
| 1164 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\Content.Outlook\GDW51GGD\Transferencia-Banco Santander (002).7z:Zone.Identifier | text | |
MD5:FBCCF14D504B7B2DBCB5A5BDA75BD93B | SHA256:EACD09517CE90D34BA562171D15AC40D302F0E691B439F91BE1B6406E25F5913 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
7
TCP/UDP connections
30
DNS requests
26
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
7964 | svchost.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | GET | 200 | 23.48.23.138:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
7892 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
1164 | OUTLOOK.EXE | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEA77flR%2B3w%2FxBpruV2lte6A%3D | unknown | — | — | whitelisted |
7892 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
5056 | RUXIMICS.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5496 | MoUsoCoreWorker.exe | 23.48.23.138:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
5496 | MoUsoCoreWorker.exe | 23.35.229.160:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
7964 | svchost.exe | 23.35.229.160:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
1164 | OUTLOOK.EXE | 52.123.128.14:443 | ecs.office.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
7964 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1164 | OUTLOOK.EXE | 23.48.23.30:443 | omex.cdn.office.net | Akamai International B.V. | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
ecs.office.com |
| whitelisted |
omex.cdn.office.net |
| whitelisted |
messaging.lifecycle.office.com |
| whitelisted |
self.events.data.microsoft.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
login.live.com |
| whitelisted |