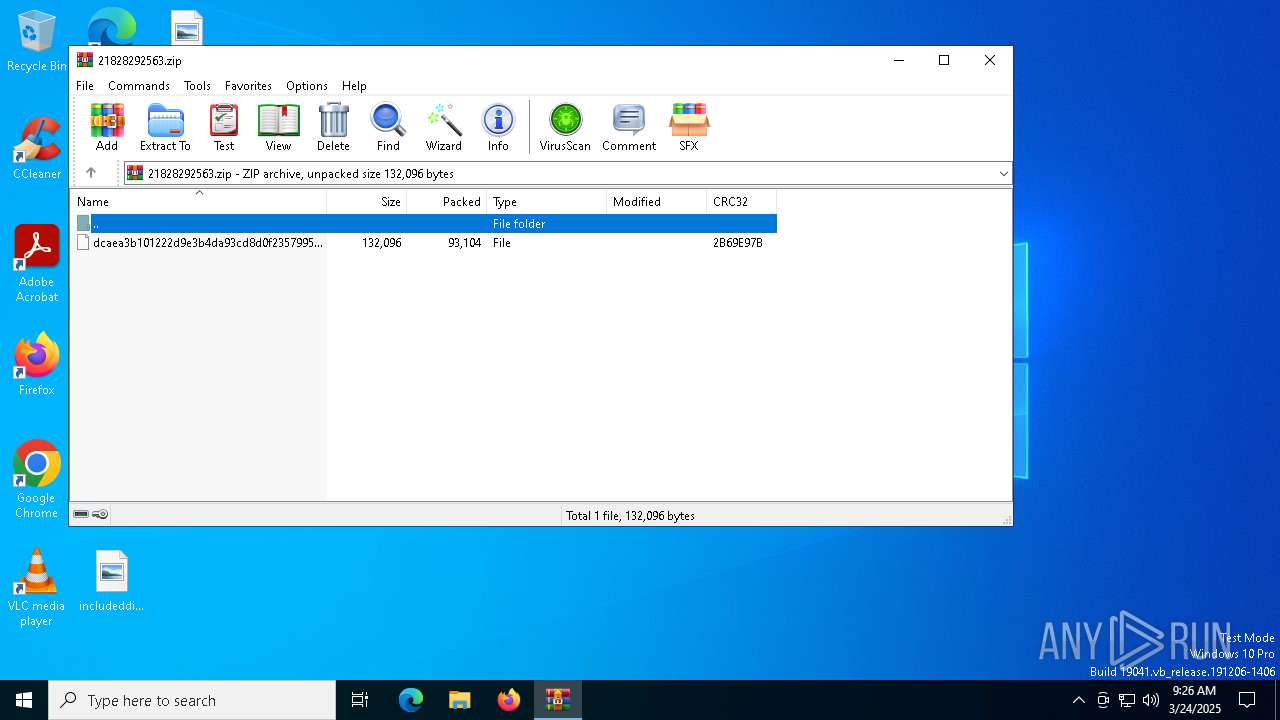
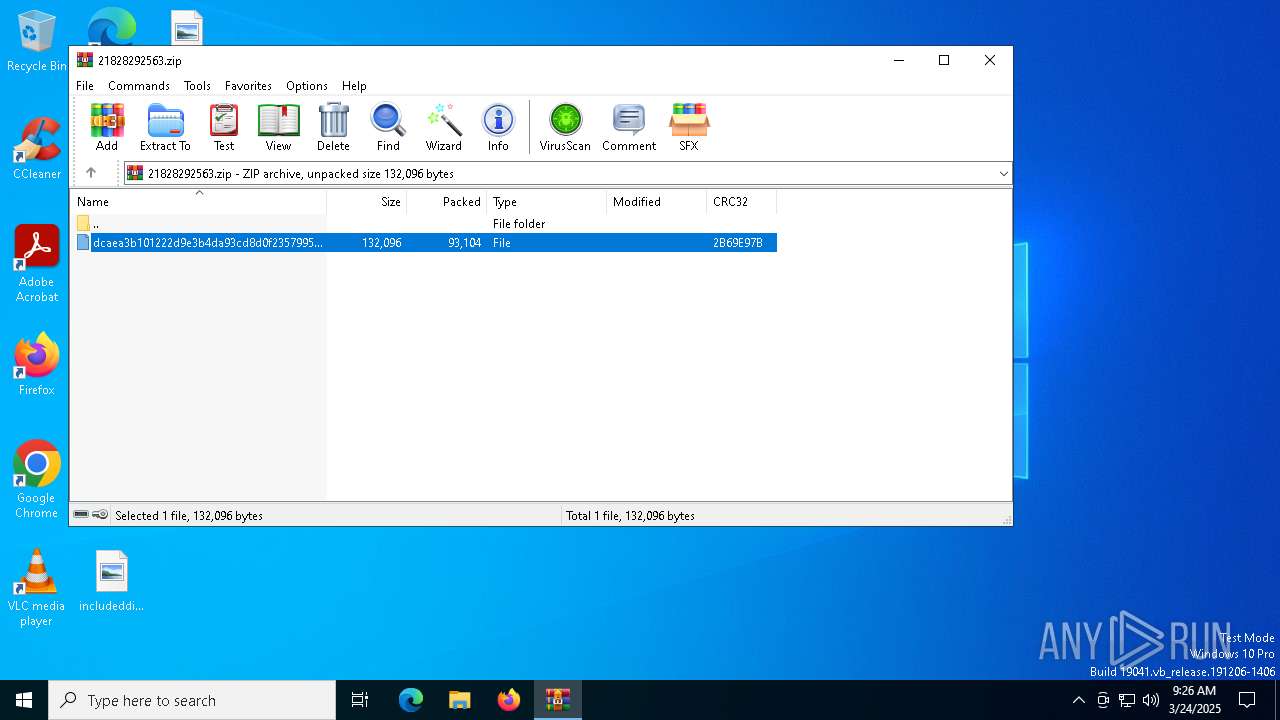
| File name: | 21828292563.zip |
| Full analysis: | https://app.any.run/tasks/7a5bcd08-ce81-4b1e-89f2-aec3b16e9a6f |
| Verdict: | Malicious activity |
| Threats: | AsyncRAT is a RAT that can monitor and remotely control infected systems. This malware was introduced on Github as a legitimate open-source remote administration software, but hackers use it for its many powerful malicious functions. |
| Analysis date: | March 24, 2025, 09:26:24 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=deflate |
| MD5: | C26EA9957EA8209D4D0A401D687C5D00 |
| SHA1: | D6D4A3C2C3911072AB2DEE4A783A468CA4B39BF1 |
| SHA256: | A5F50C0BFB7E25B284D3CE5CE24222BAE44D12515D71093D60757DBCEA2686DF |
| SSDEEP: | 3072:msFZyPZ4W+dN+Qu4JqfT54WcyMRDOeF57:dZA4dN+Q1qfT5hc57 |
MALICIOUS
BORAT mutex has been found
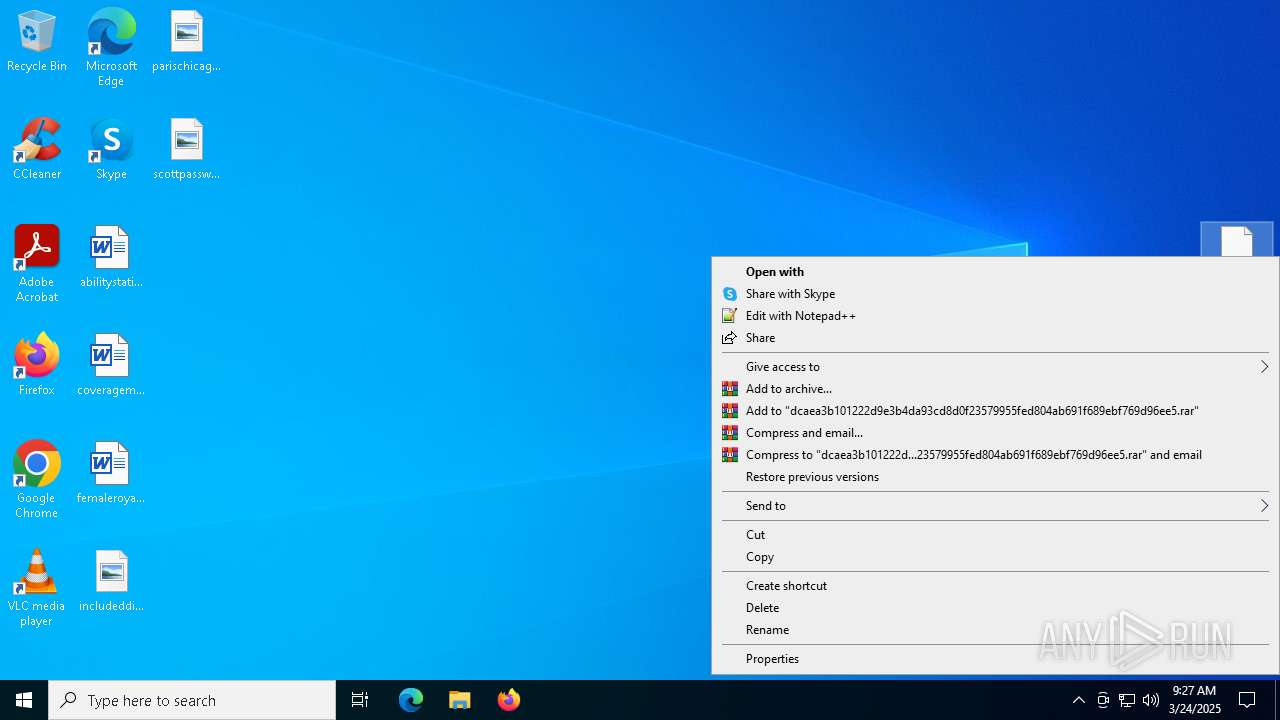
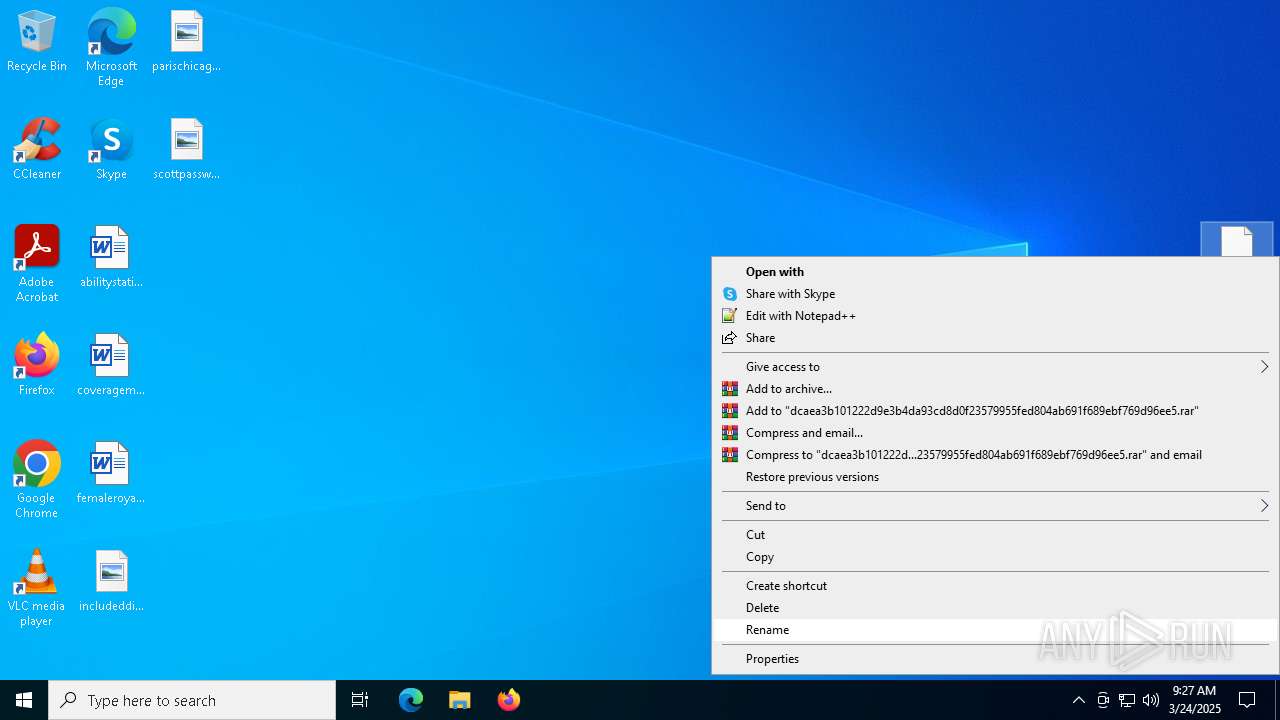
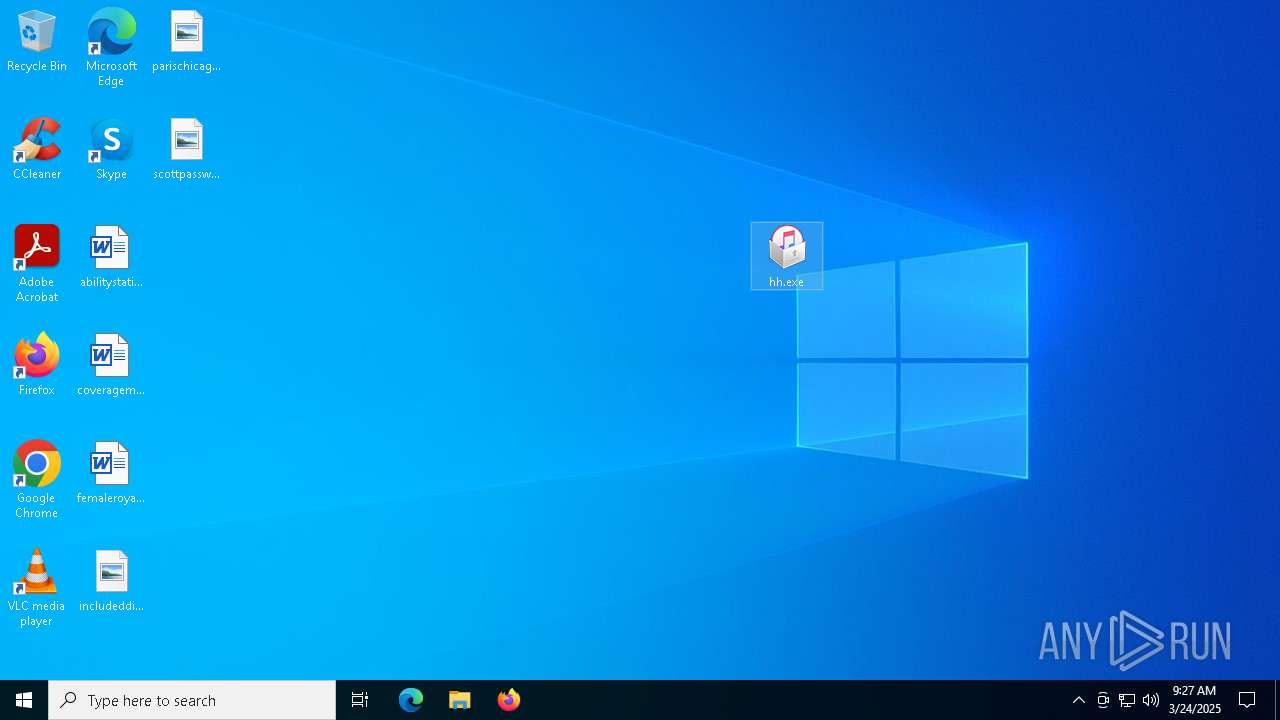
- hh.exe (PID: 7052)
ASYNCRAT has been detected (YARA)
- hh.exe (PID: 7052)
SUSPICIOUS
No suspicious indicators.INFO
Manual execution by a user
- hh.exe (PID: 7052)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 7620)
Reads the computer name
- hh.exe (PID: 7052)
Checks supported languages
- hh.exe (PID: 7052)
Reads the machine GUID from the registry
- hh.exe (PID: 7052)
Reads the software policy settings
- slui.exe (PID: 5728)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
AsyncRat
(PID) Process(7052) hh.exe
C2 (1)127.0.0.1
Ports (2)8848
8080
Version0x0x1
Options
AutoRunfalse
MutexBoratRatMutex_Sa8XOfH1BudX
InstallFolder%AppData%
Certificates
Cert1MIICQTCCAaqgAwIBAgIVAPFjWXX9EizVOccA+56tkmH/lllDMA0GCSqGSIb3DQEBDQUAMHIxHDAaBgNVBAMME21pY3Jvc29mdCBhbnRpdmlydXMxFTATBgNVBAsMDFNhOFhPZkgxQnVkWDEhMB8GA1UECgwYQm9yYXRSYXQgQnkgU2E4WE9mSDFCdWRYMQswCQYDVQQHDAJTSDELMAkGA1UEBhMCQ04wHhcNMjQwNTI5MTg1MzQzWhcNMzUwMzA4MTg1MzQzWjATMREwDwYDVQQDDAhCb3JhdFJhdDCBnzAN...
Server_SignatureW9L/HBh9kcdICyUl0q1tQYiwWwAYkDxtk+gPRhU03aZx2TQY37npRDtElfmBEAaMZOB9e+Q/Ce8B7O8zMAkxBKlu3T+zS6YrK3zVo2kicrJNjgTtbq8BbghzVzFW/a28rWQNY5z0/2SHSGz9HVveUtsHEVfYqi1IctI1MOuJEQ8=
Keys
AESbcd675038a002375e1af31351108c1179938d7dce78820b24a54b7c0259deeee
SaltBor@tRAT584
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
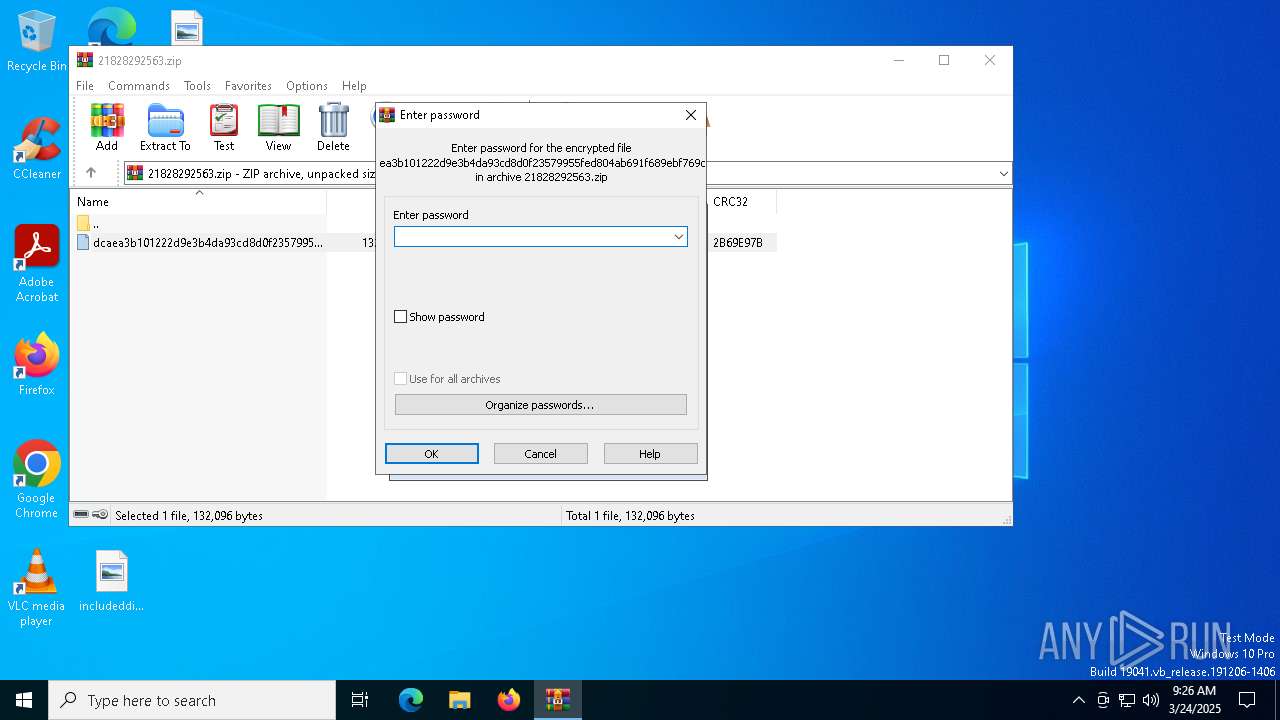
| ZipBitFlag: | 0x0009 |
| ZipCompression: | Deflated |
| ZipModifyDate: | 1980:00:00 00:00:00 |
| ZipCRC: | 0x2b69e97b |
| ZipCompressedSize: | 93104 |
| ZipUncompressedSize: | 132096 |
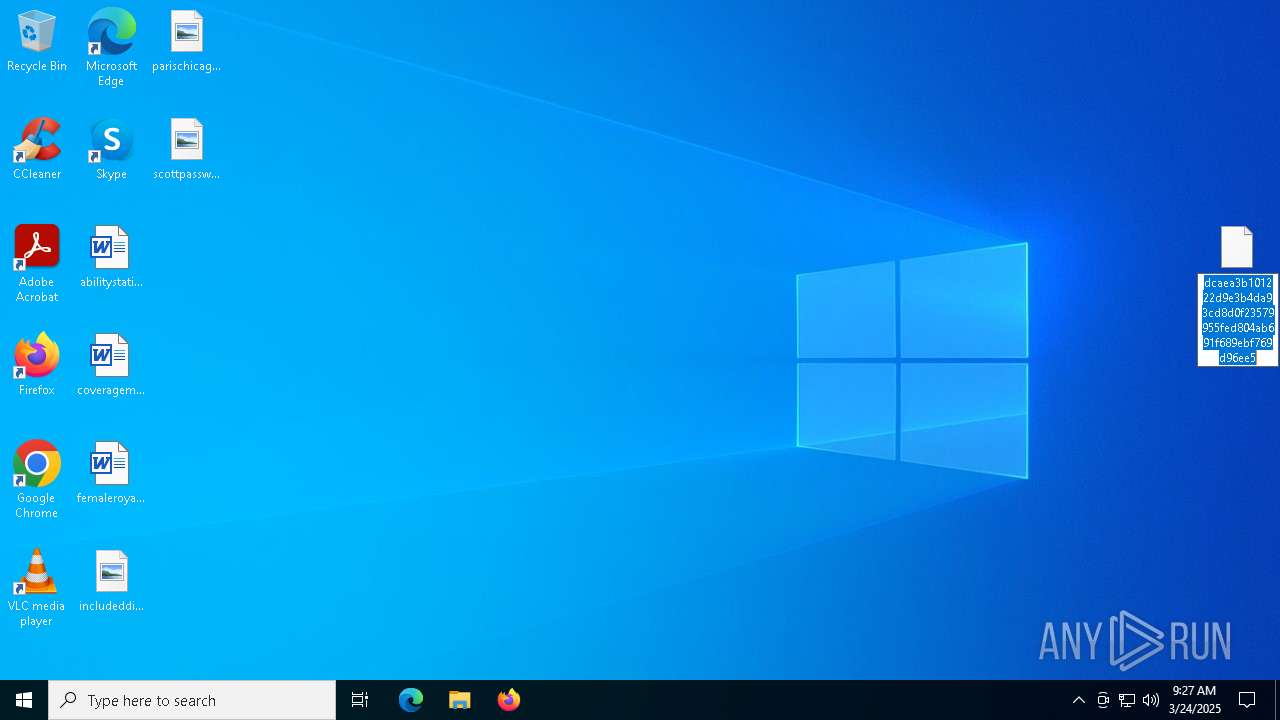
| ZipFileName: | dcaea3b101222d9e3b4da93cd8d0f23579955fed804ab691f689ebf769d96ee5 |
Total processes
142
Monitored processes
3
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 5728 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7052 | "C:\Users\admin\Desktop\hh.exe" | C:\Users\admin\Desktop\hh.exe | explorer.exe | ||||||||||||
User: admin Company: Apple Inc. Integrity Level: MEDIUM Description: iTunes Installer Version: 12.13.6.1 Modules
AsyncRat(PID) Process(7052) hh.exe C2 (1)127.0.0.1 Ports (2)8848 8080 Version0x0x1 Options AutoRunfalse MutexBoratRatMutex_Sa8XOfH1BudX InstallFolder%AppData% Certificates Cert1MIICQTCCAaqgAwIBAgIVAPFjWXX9EizVOccA+56tkmH/lllDMA0GCSqGSIb3DQEBDQUAMHIxHDAaBgNVBAMME21pY3Jvc29mdCBhbnRpdmlydXMxFTATBgNVBAsMDFNhOFhPZkgxQnVkWDEhMB8GA1UECgwYQm9yYXRSYXQgQnkgU2E4WE9mSDFCdWRYMQswCQYDVQQHDAJTSDELMAkGA1UEBhMCQ04wHhcNMjQwNTI5MTg1MzQzWhcNMzUwMzA4MTg1MzQzWjATMREwDwYDVQQDDAhCb3JhdFJhdDCBnzAN... Server_SignatureW9L/HBh9kcdICyUl0q1tQYiwWwAYkDxtk+gPRhU03aZx2TQY37npRDtElfmBEAaMZOB9e+Q/Ce8B7O8zMAkxBKlu3T+zS6YrK3zVo2kicrJNjgTtbq8BbghzVzFW/a28rWQNY5z0/2SHSGz9HVveUtsHEVfYqi1IctI1MOuJEQ8= Keys AESbcd675038a002375e1af31351108c1179938d7dce78820b24a54b7c0259deeee SaltBor@tRAT584 | |||||||||||||||
| 7620 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\AppData\Local\Temp\21828292563.zip | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
Total events
2 475
Read events
2 456
Write events
19
Delete events
0
Modification events
| (PID) Process: | (7620) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (7620) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (7620) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (7620) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\21828292563.zip | |||
| (PID) Process: | (7620) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (7620) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (7620) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (7620) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (7620) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface |
| Operation: | write | Name: | ShowPassword |
Value: 0 | |||
| (PID) Process: | (7620) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\ArcColumnWidths |
| Operation: | write | Name: | name |
Value: 256 | |||
Executable files
1
Suspicious files
0
Text files
0
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 7620 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb7620.20871\dcaea3b101222d9e3b4da93cd8d0f23579955fed804ab691f689ebf769d96ee5 | executable | |
MD5:B604A2F9E3BD2B86552E2810BFB3CC53 | SHA256:02A09FFDC6F7A95E957A68FD72DDC27A63AD0BC6D6BEBD316E8DB7F64D22FF36 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
5
TCP/UDP connections
24
DNS requests
16
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
6544 | svchost.exe | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | GET | 200 | 23.48.23.143:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
7380 | SIHClient.exe | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
7380 | SIHClient.exe | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
7780 | backgroundTaskHost.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
5496 | MoUsoCoreWorker.exe | 23.48.23.143:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2104 | svchost.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6700 | RUXIMICS.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
2112 | svchost.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
3216 | svchost.exe | 40.115.3.253:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6544 | svchost.exe | 20.190.160.20:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6544 | svchost.exe | 184.30.131.245:80 | ocsp.digicert.com | AKAMAI-AS | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
crl.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
arc.msn.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |