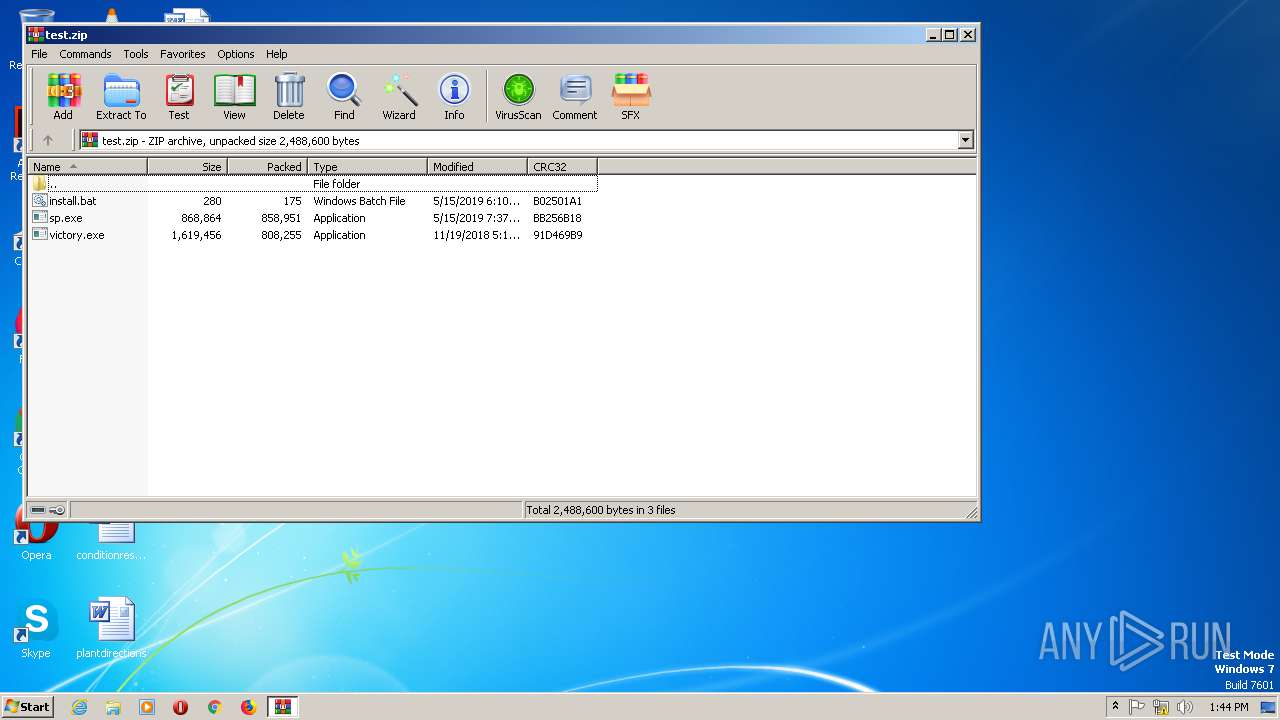
| File name: | test.zip |
| Full analysis: | https://app.any.run/tasks/5101b95a-1df3-4202-98d1-e4ce3a166a60 |
| Verdict: | Malicious activity |
| Threats: | Amadey is a formidable Windows infostealer threat, characterized by its persistence mechanisms, modular design, and ability to execute various malicious tasks. |
| Analysis date: | May 15, 2019, 13:43:19 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 64 bit) |
| Tags: | |
| Indicators: | |
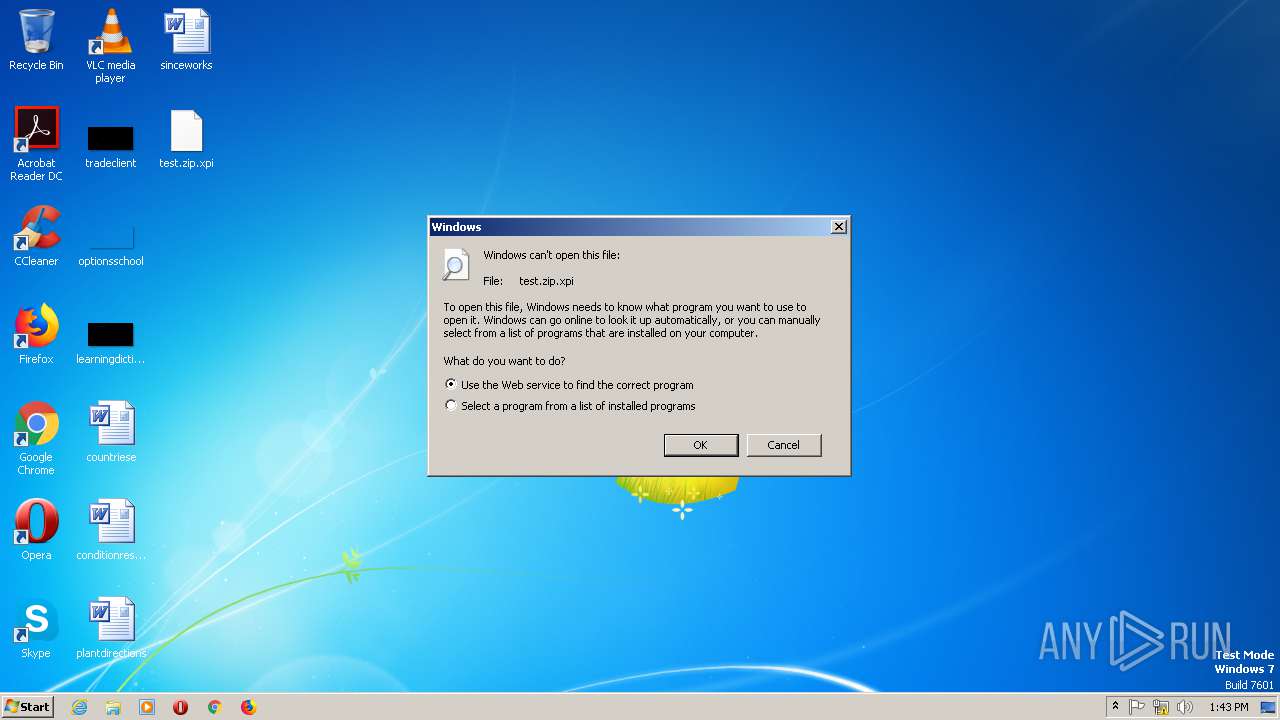
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract |
| MD5: | 815C4000399CF67F1E3852069D60326E |
| SHA1: | ECE83A7252C85A4B815C4CFEA0D4D56C4D360FC2 |
| SHA256: | A5BB49D4641F77DF65A1E729C4D60FF48BB1ED40BE2D89D7B13A951FECEAB25B |
| SSDEEP: | 24576:OaW62JtV33oW/nP0cuBPpYiuU0akl+CDysdPmdoi1uICBhGG+W47gzoZ:xWZtVKBhHuUVkACJPmdRCTVt47VZ |
MALICIOUS
Changes the autorun value in the registry
- reg.exe (PID: 2476)
Application was dropped or rewritten from another process
- victory.exe (PID: 1652)
- sp.exe (PID: 940)
- victory.exe (PID: 3020)
Connects to CnC server
- victory.exe (PID: 3020)
AMADEY was detected
- victory.exe (PID: 3020)
SUSPICIOUS
Application launched itself
- victory.exe (PID: 1652)
Uses REG.EXE to modify Windows registry
- cmd.exe (PID: 2440)
Reads the machine GUID from the registry
- WinRAR.exe (PID: 2412)
Executable content was dropped or overwritten
- cmd.exe (PID: 2440)
- WinRAR.exe (PID: 2412)
INFO
No info indicators.
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .xpi | | | Mozilla Firefox browser extension (66.6) |
|---|---|---|
| .zip | | | ZIP compressed archive (33.3) |
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2019:05:15 08:10:04 |
| ZipCRC: | 0xb02501a1 |
| ZipCompressedSize: | 175 |
| ZipUncompressedSize: | 280 |
| ZipFileName: | install.bat |
Total processes
44
Monitored processes
8
Malicious processes
3
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 940 | "C:\Users\admin\Desktop\sp.exe" | C:\Users\admin\Desktop\sp.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 1652 | C:\Users\Public\Documents\victory.exe | C:\Users\Public\Documents\victory.exe | — | cmd.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 2412 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\Desktop\test.zip" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
| 2440 | C:\Windows\system32\cmd.exe /c ""C:\Users\admin\Desktop\install.bat" " | C:\Windows\system32\cmd.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 1 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 2476 | reg add "HKCU\Software\Microsoft\Windows\CurrentVersion\Run" /v svchost /t REG_SZ /d "C:\Users\Public\Documents\victory.exe" /f | C:\Windows\system32\reg.exe | cmd.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Registry Console Tool Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3020 | "C:\Users\Public\Documents\victory.exe" | C:\Users\Public\Documents\victory.exe | victory.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 3024 | "C:\Windows\system32\rundll32.exe" C:\Windows\system32\shell32.dll,OpenAs_RunDLL C:\Users\admin\Desktop\test.zip.xpi | C:\Windows\system32\rundll32.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3044 | "C:\Windows\System32\NOTEPAD.EXE" C:\Users\admin\Desktop\install.bat | C:\Windows\System32\NOTEPAD.EXE | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
402
Read events
380
Write events
22
Delete events
0
Modification events
| (PID) Process: | (2412) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (2412) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (2412) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\65\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2412) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\test.zip | |||
| (PID) Process: | (2412) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (2412) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (2412) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (2412) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (2412) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\65\52C64B7E |
| Operation: | write | Name: | @C:\Windows\System32\acppage.dll,-6002 |
Value: Windows Batch File | |||
| (PID) Process: | (2412) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\MainWin |
| Operation: | write | Name: | Placement |
Value: 2C0000000000000001000000FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF1600000016000000D60300000B020000 | |||
Executable files
3
Suspicious files
0
Text files
1
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1652 | victory.exe | C:\Users\admin\AppData\Local\Temp\Liebert.bmp | — | |
MD5:— | SHA256:— | |||
| 2412 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2412.35747\sp.exe | executable | |
MD5:— | SHA256:— | |||
| 2412 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2412.35747\install.bat | text | |
MD5:— | SHA256:— | |||
| 2440 | cmd.exe | C:\Users\Public\Documents\victory.exe | executable | |
MD5:— | SHA256:— | |||
| 2412 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2412.35747\victory.exe | executable | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
5
TCP/UDP connections
15
DNS requests
2
Threats
15
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3020 | victory.exe | POST | 200 | 104.243.41.186:80 | http://charley-online.com/back/2019/index.php | US | text | 6 b | malicious |
3020 | victory.exe | POST | 200 | 104.243.41.186:80 | http://charley-online.com/back/2019/index.php | US | text | 6 b | malicious |
3020 | victory.exe | POST | 200 | 104.243.41.186:80 | http://charley-online.com/back/2019/index.php | US | text | 6 b | malicious |
3020 | victory.exe | POST | 200 | 104.243.41.186:80 | http://charley-online.com/back/2019/index.php | US | text | 6 b | malicious |
3020 | victory.exe | POST | 200 | 104.243.41.186:80 | http://charley-online.com/back/2019/index.php | US | text | 6 b | malicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3020 | victory.exe | 104.243.41.186:80 | charley-online.com | Choopa, LLC | US | suspicious |
940 | sp.exe | 5.252.198.93:7337 | — | — | — | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
charley-online.com |
| malicious |
dns.msftncsi.com |
| shared |
Threats
PID | Process | Class | Message |
|---|---|---|---|
3020 | victory.exe | A Network Trojan was detected | MALWARE [PTsecurity] Trojan.Win32.Amadey |
3020 | victory.exe | A Network Trojan was detected | MALWARE [PTsecurity] Trojan.Win32.Amadey |
3020 | victory.exe | A Network Trojan was detected | MALWARE [PTsecurity] Trojan.Win32.Amadey |
3020 | victory.exe | A Network Trojan was detected | MALWARE [PTsecurity] Trojan.Win32.Amadey |
3020 | victory.exe | A Network Trojan was detected | MALWARE [PTsecurity] Trojan.Win32.Amadey |
3020 | victory.exe | A Network Trojan was detected | MALWARE [PTsecurity] Trojan.Win32.Amadey |
3020 | victory.exe | A Network Trojan was detected | MALWARE [PTsecurity] Trojan.Win32.Amadey |
3020 | victory.exe | A Network Trojan was detected | MALWARE [PTsecurity] Trojan.Win32.Amadey |
3020 | victory.exe | A Network Trojan was detected | MALWARE [PTsecurity] Trojan.Win32.Amadey |
3020 | victory.exe | A Network Trojan was detected | MALWARE [PTsecurity] Trojan.Win32.Amadey |
5 ETPRO signatures available at the full report