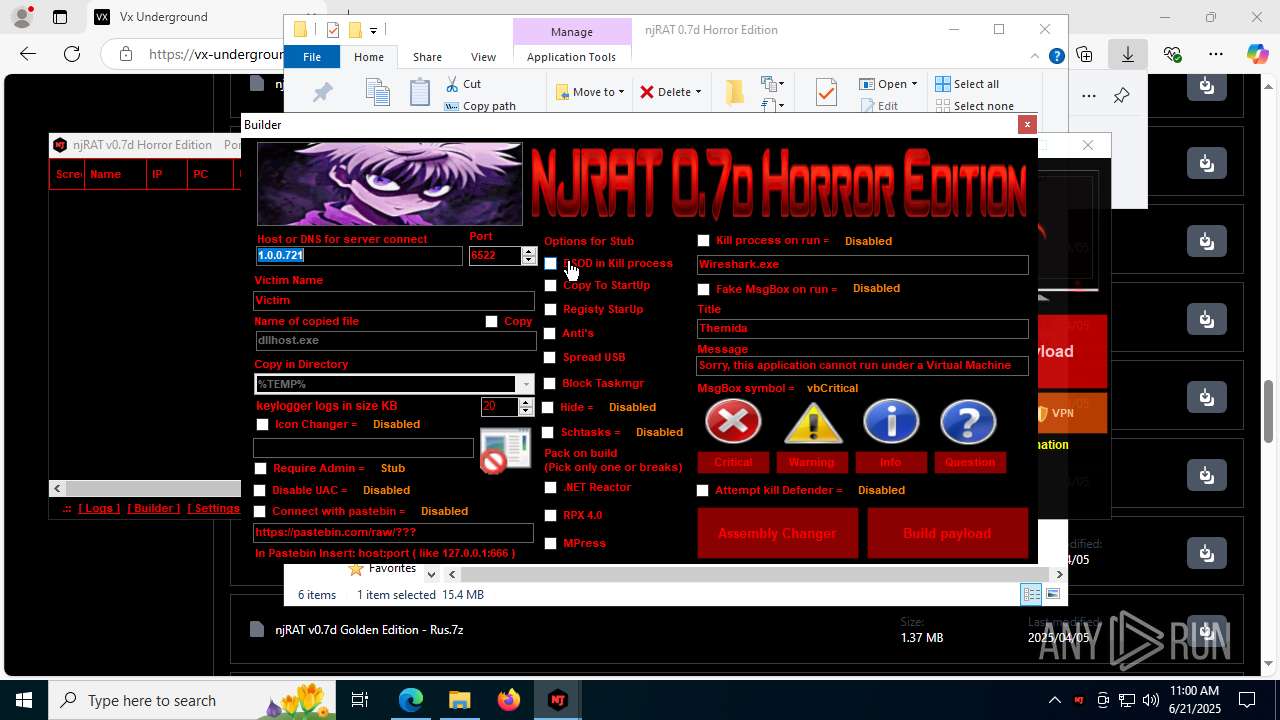
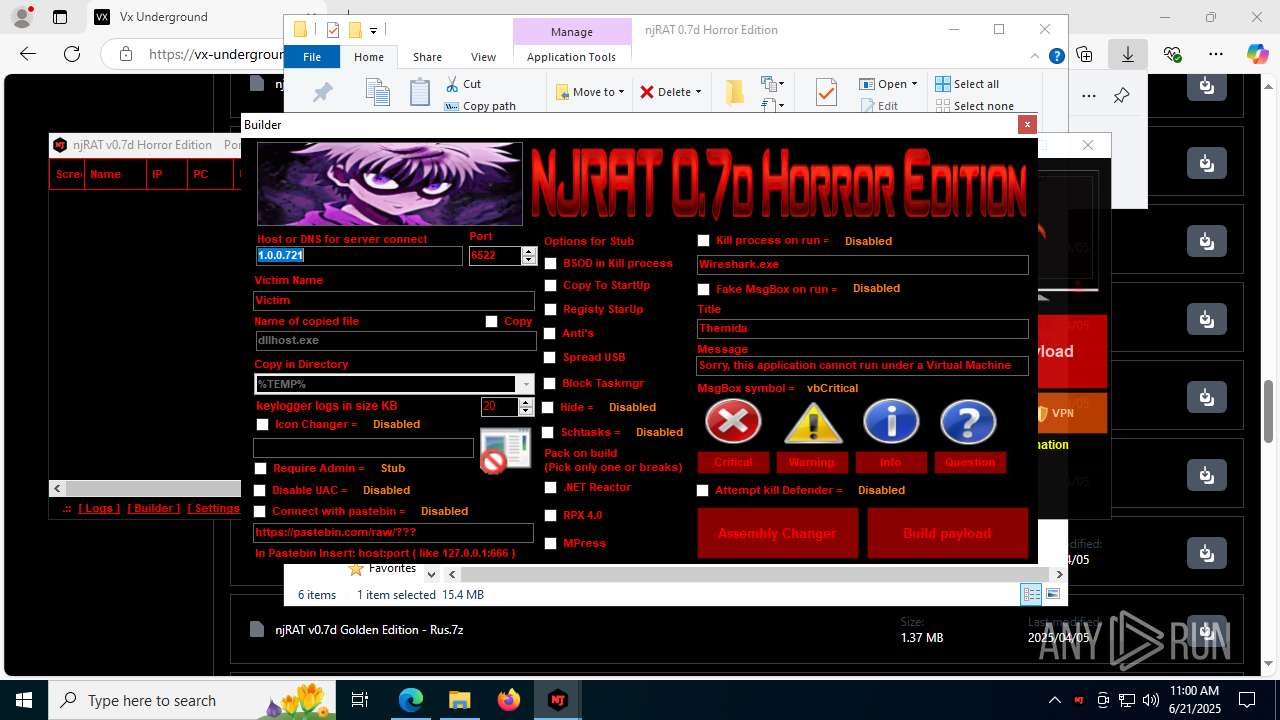
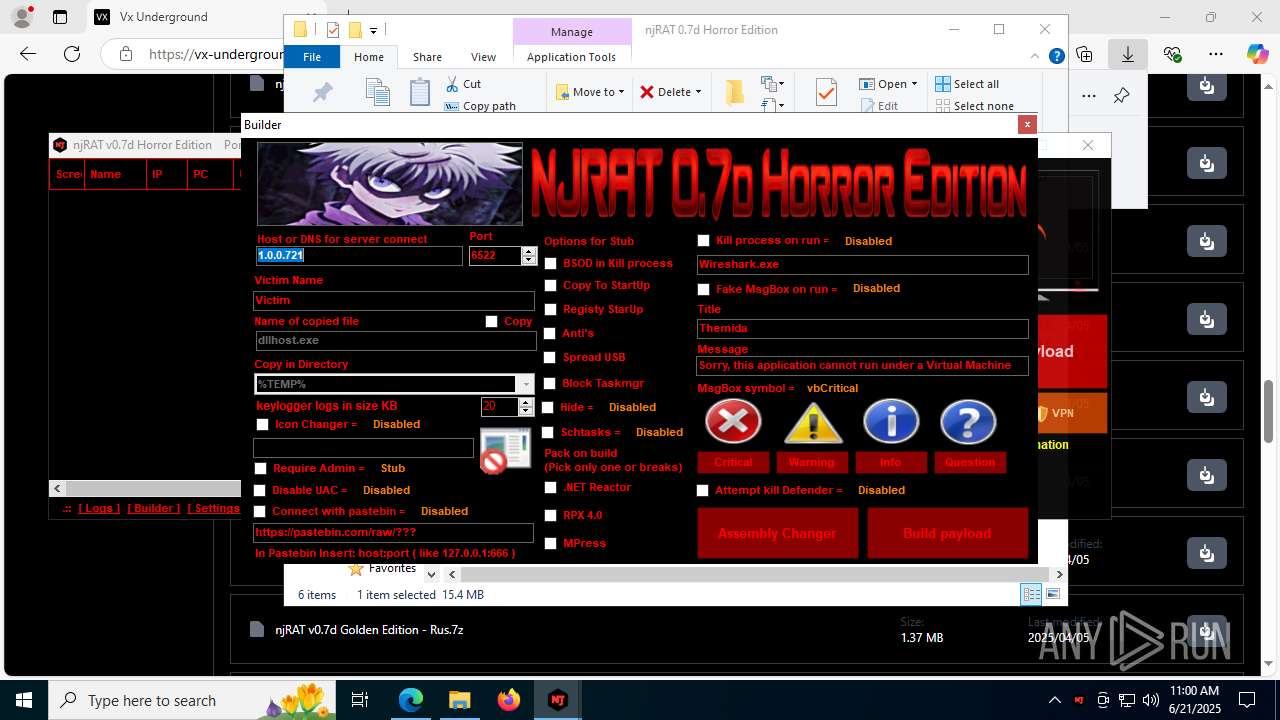
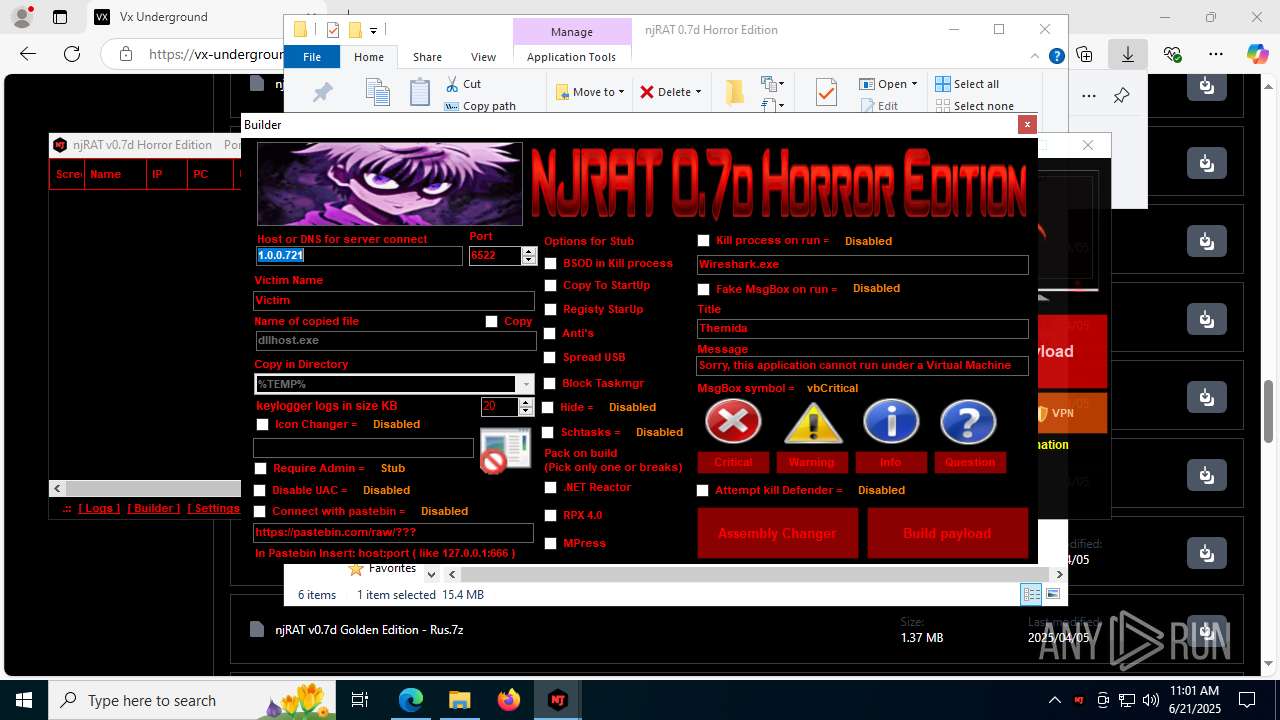
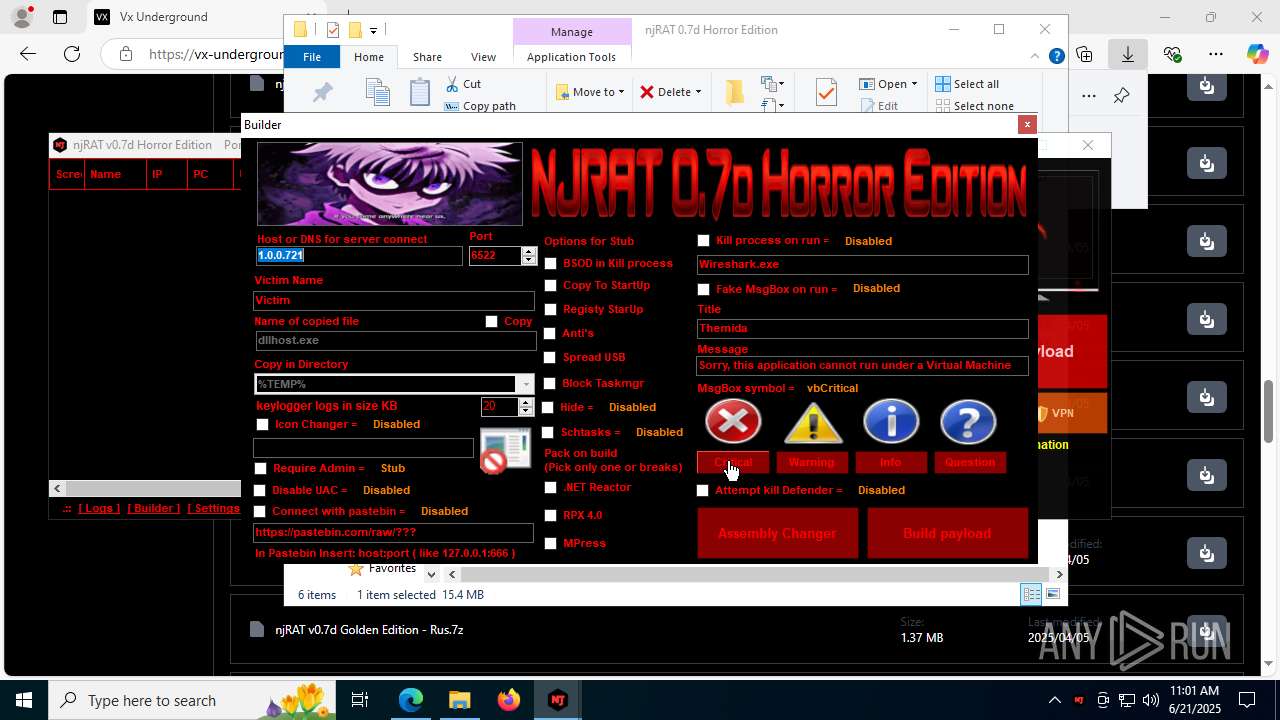
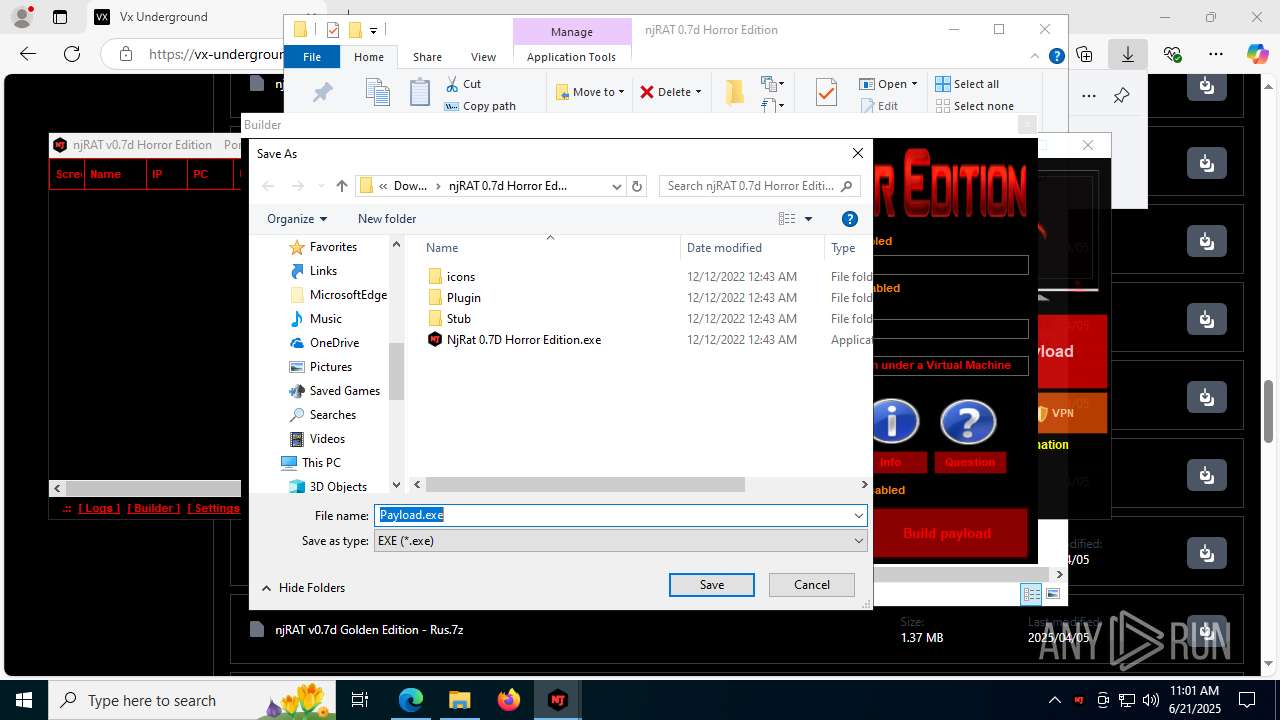
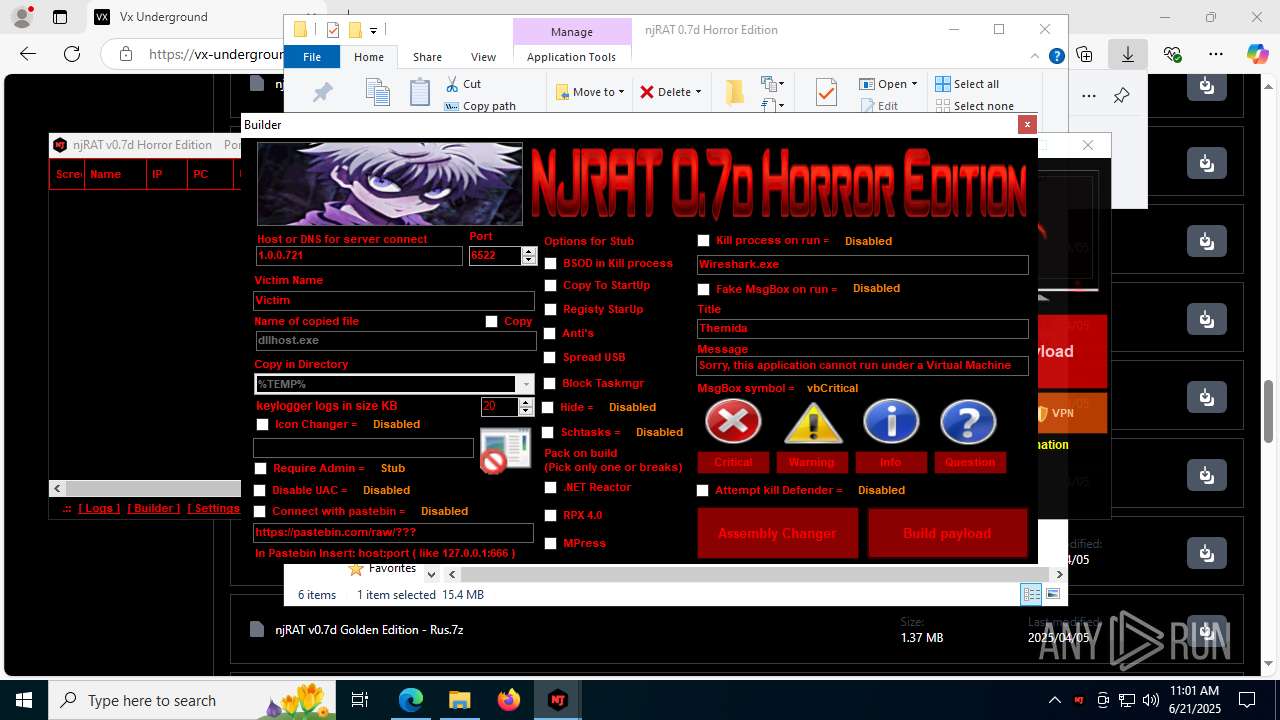
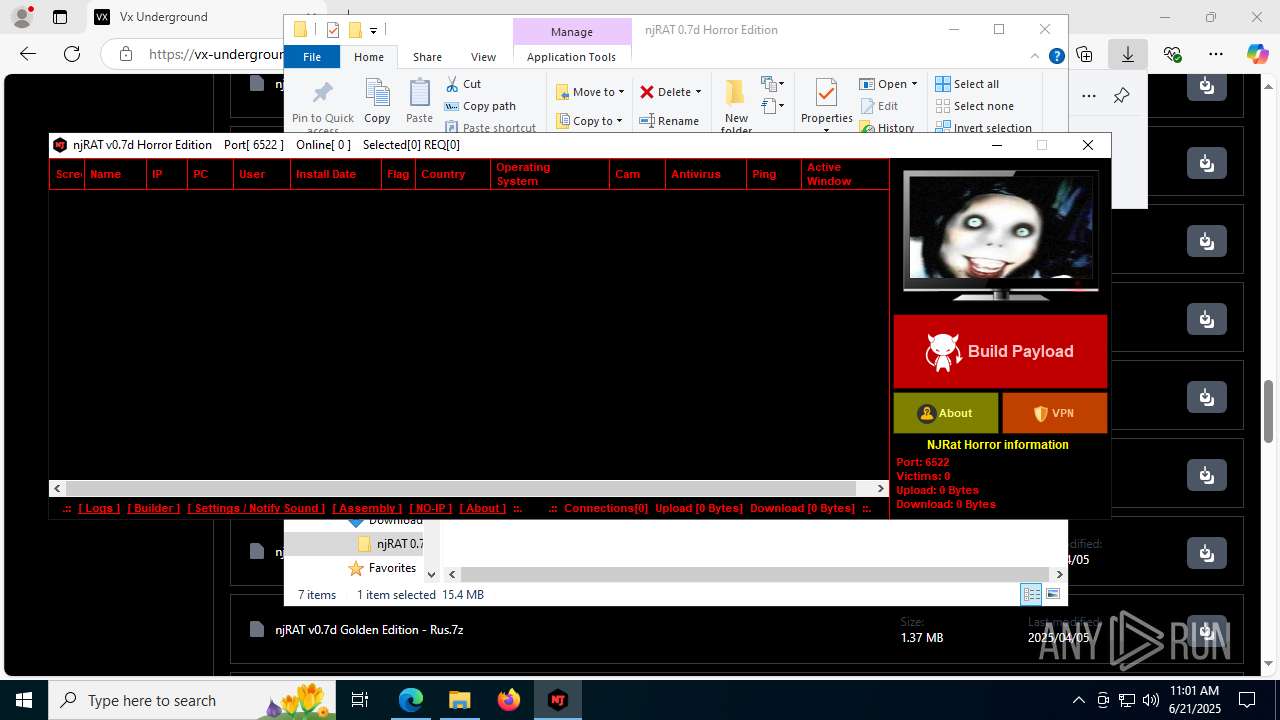
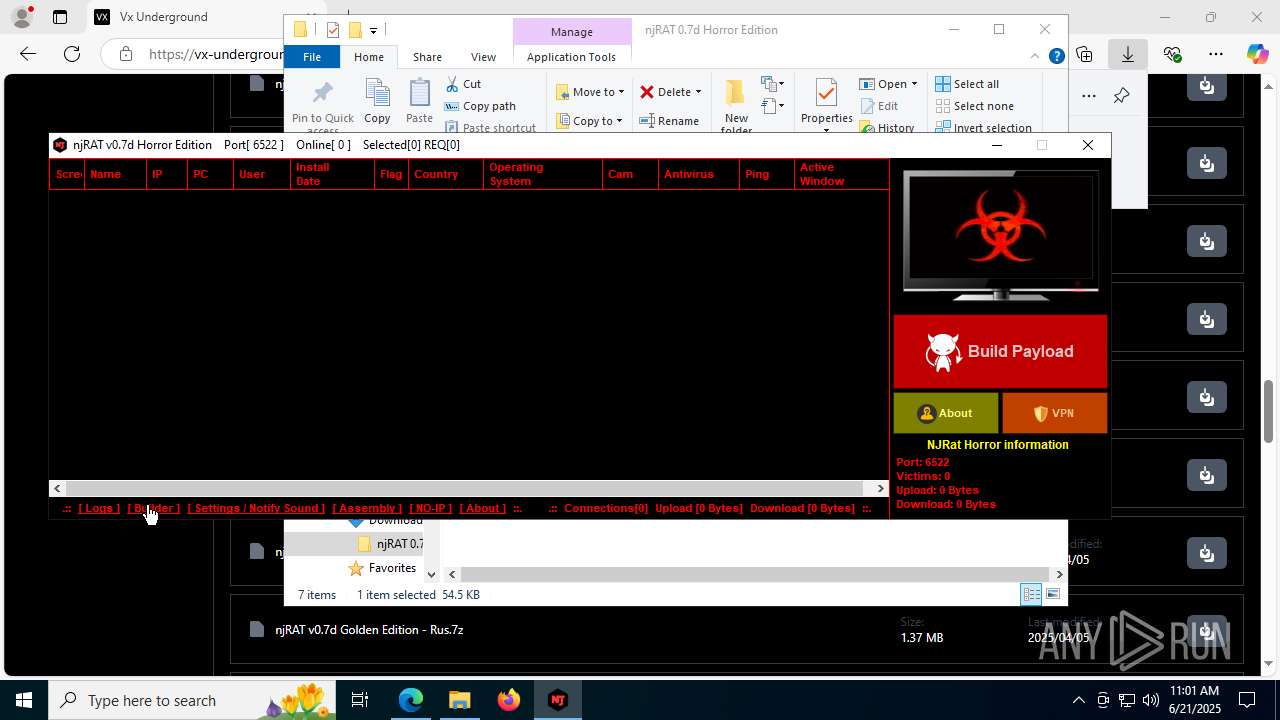
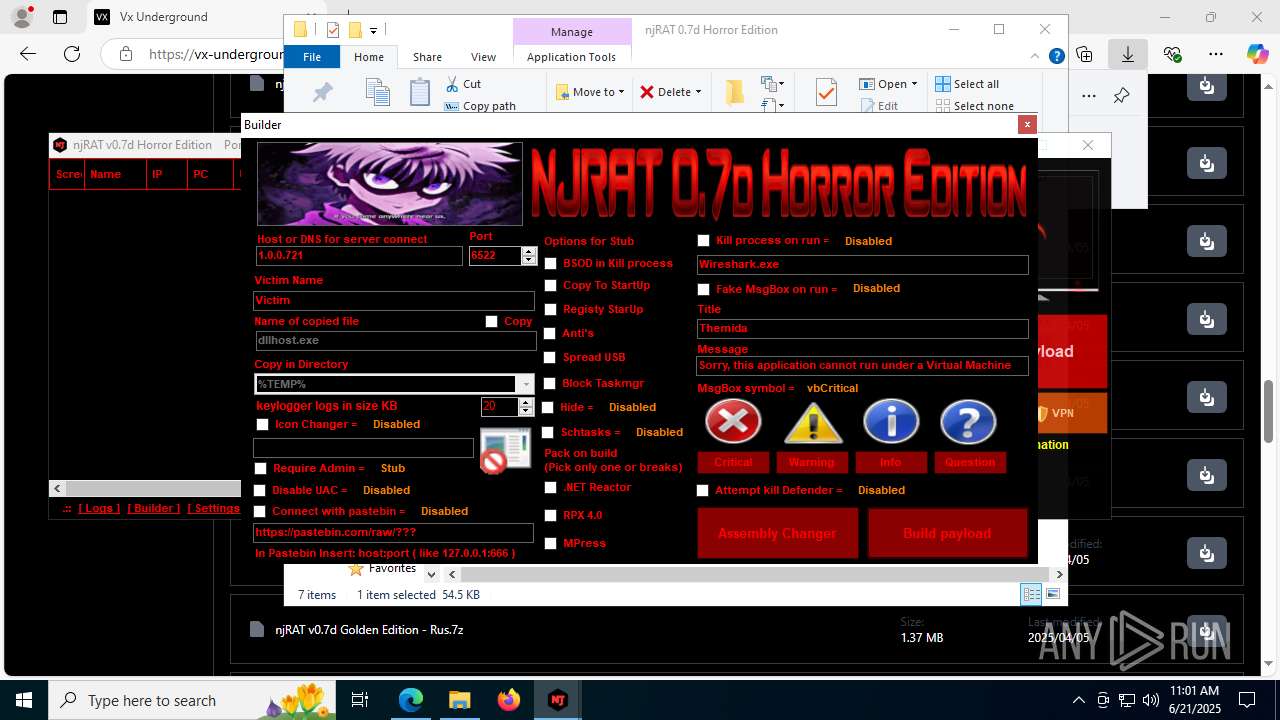
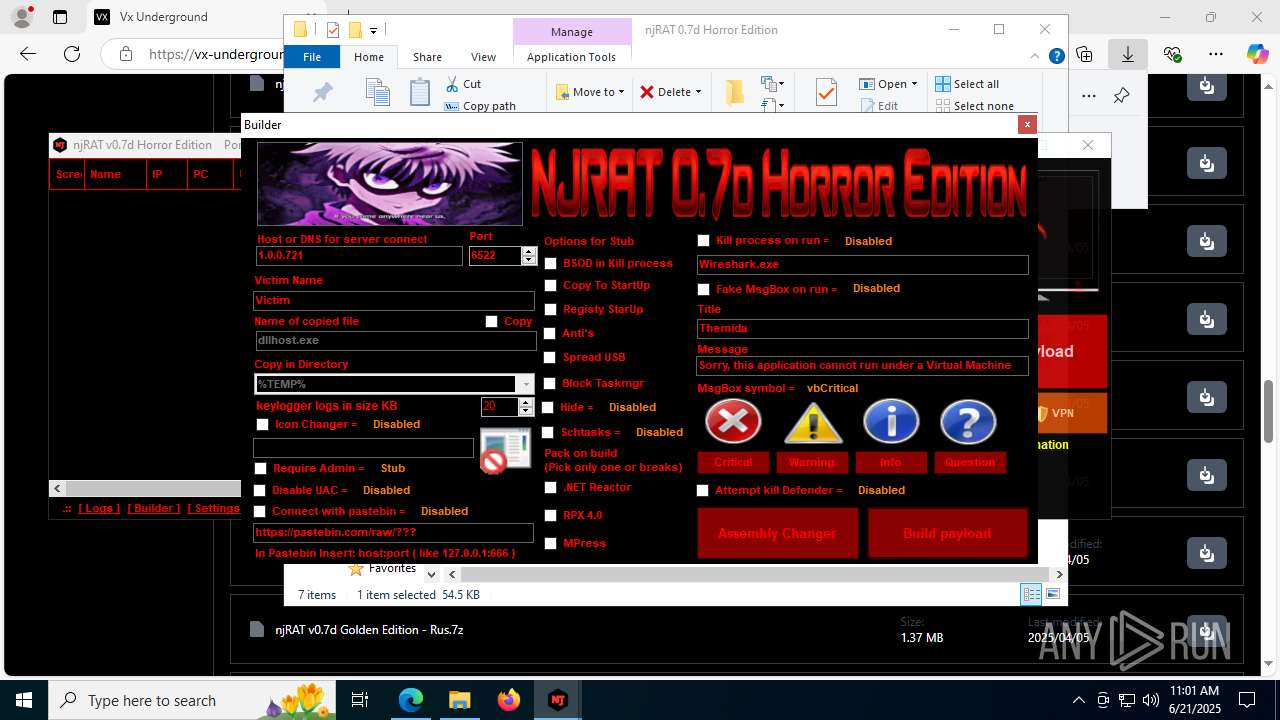
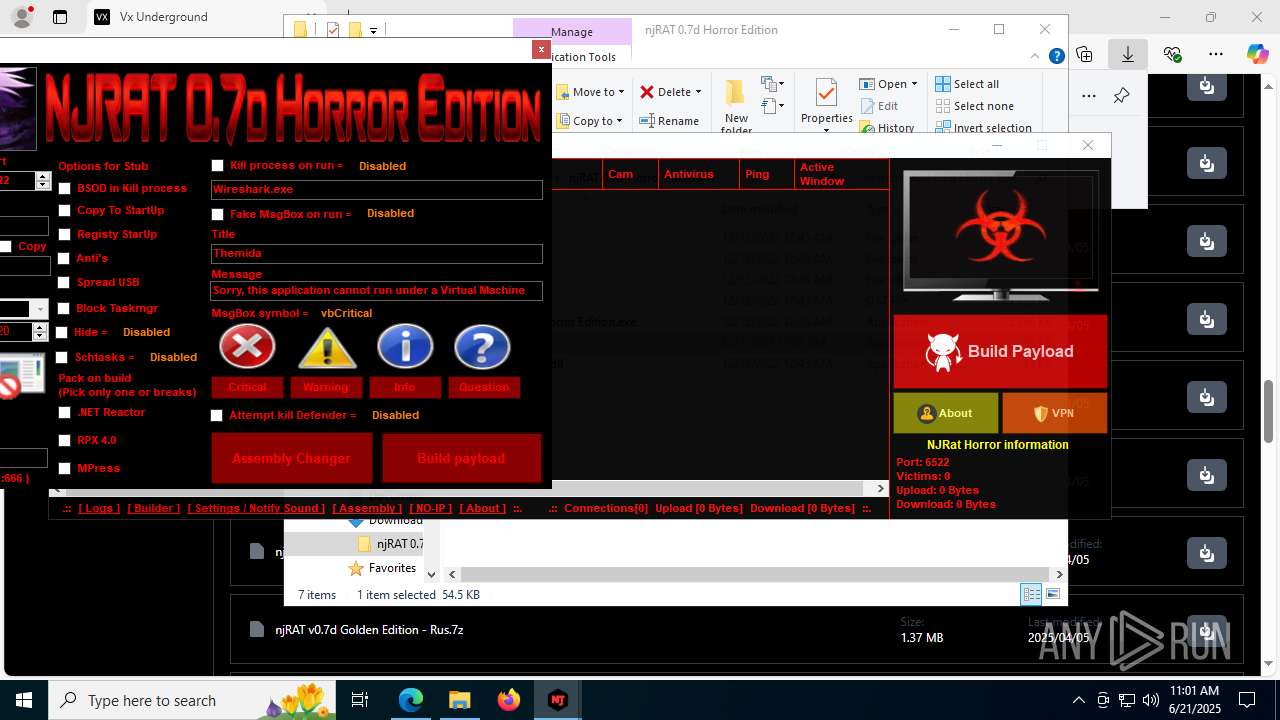
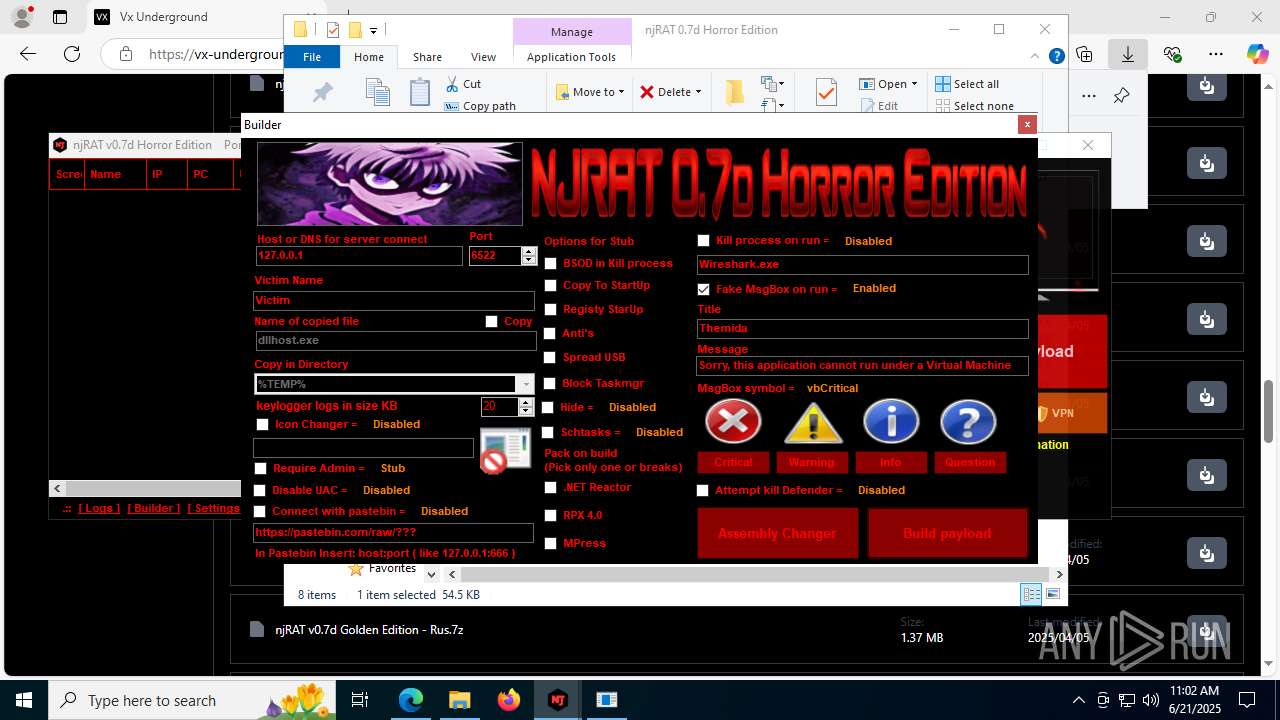
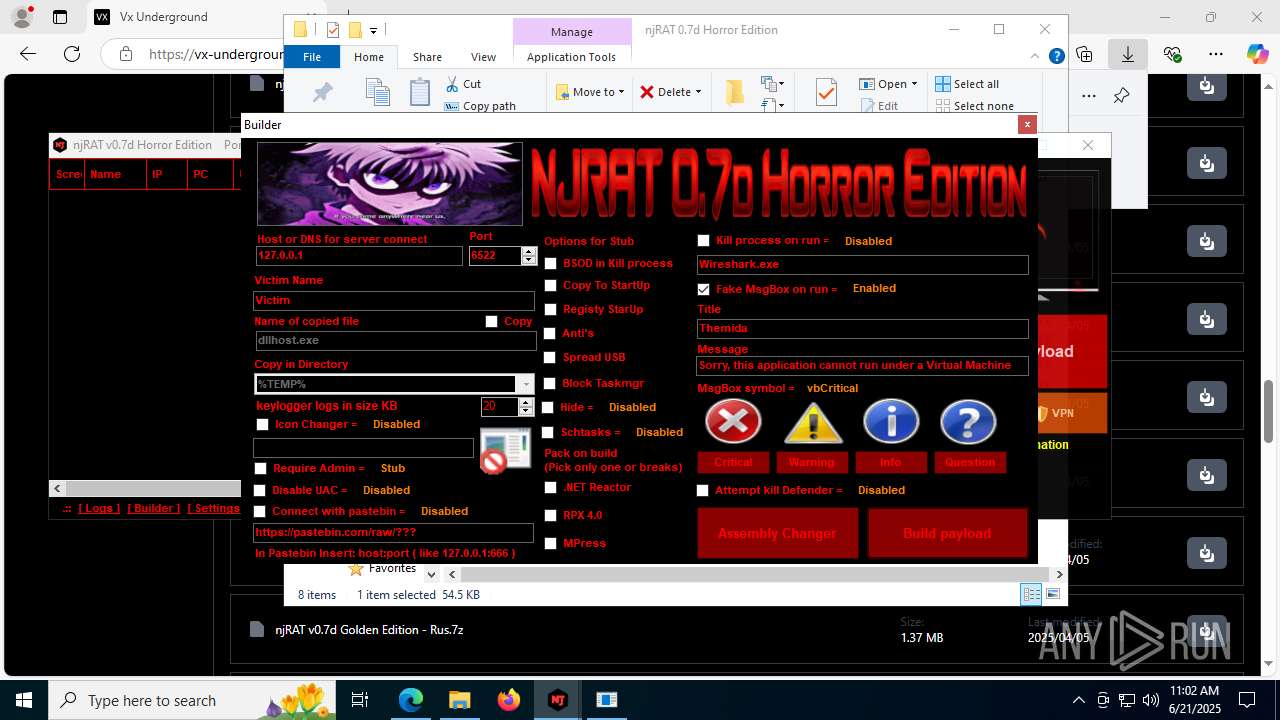
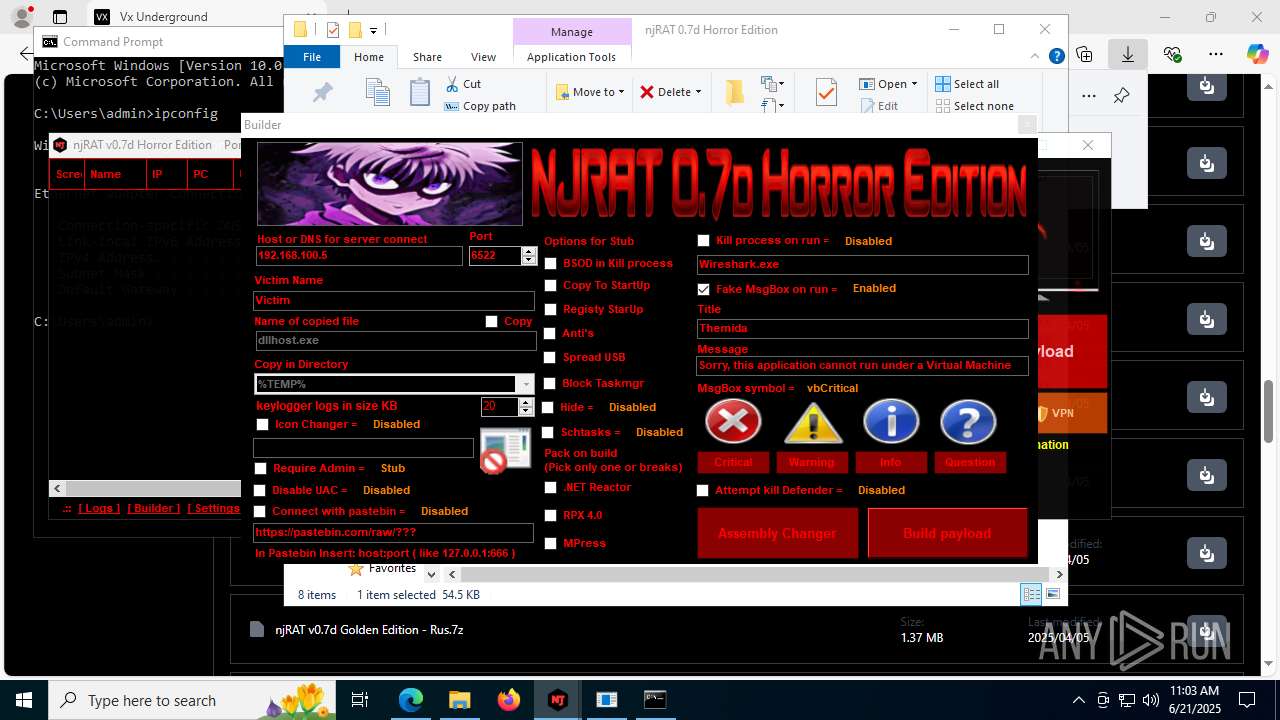
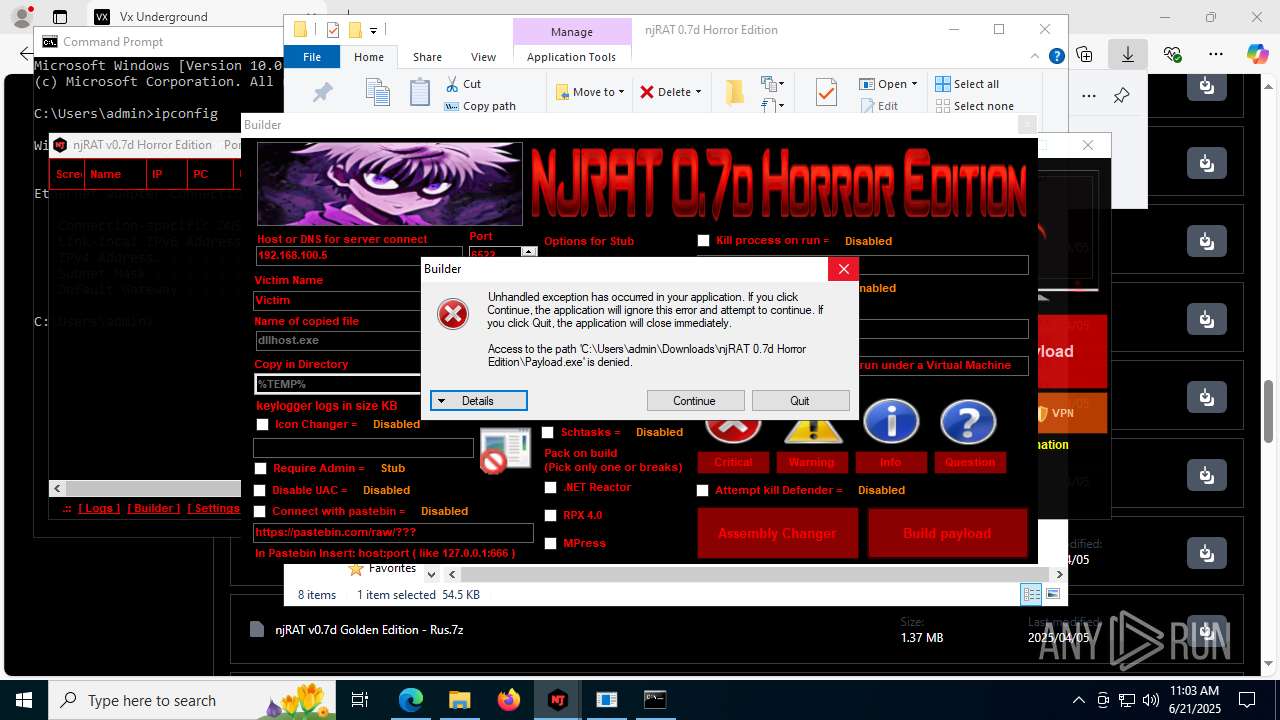
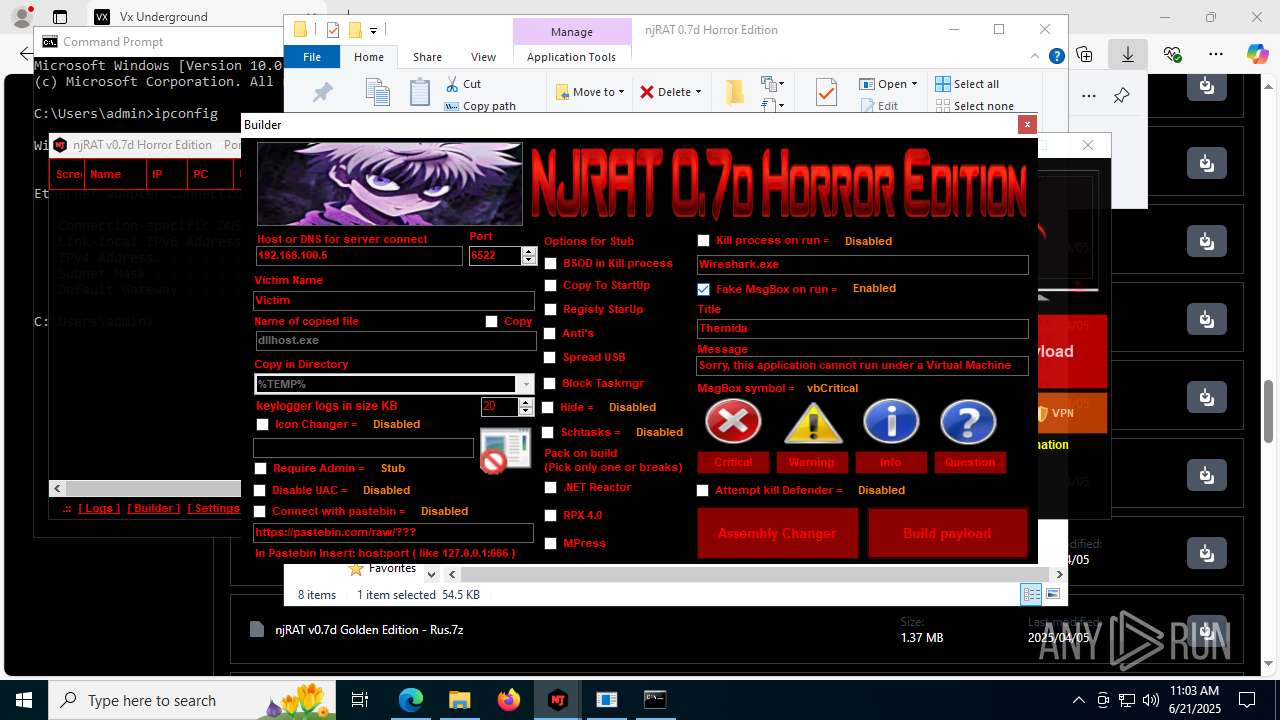
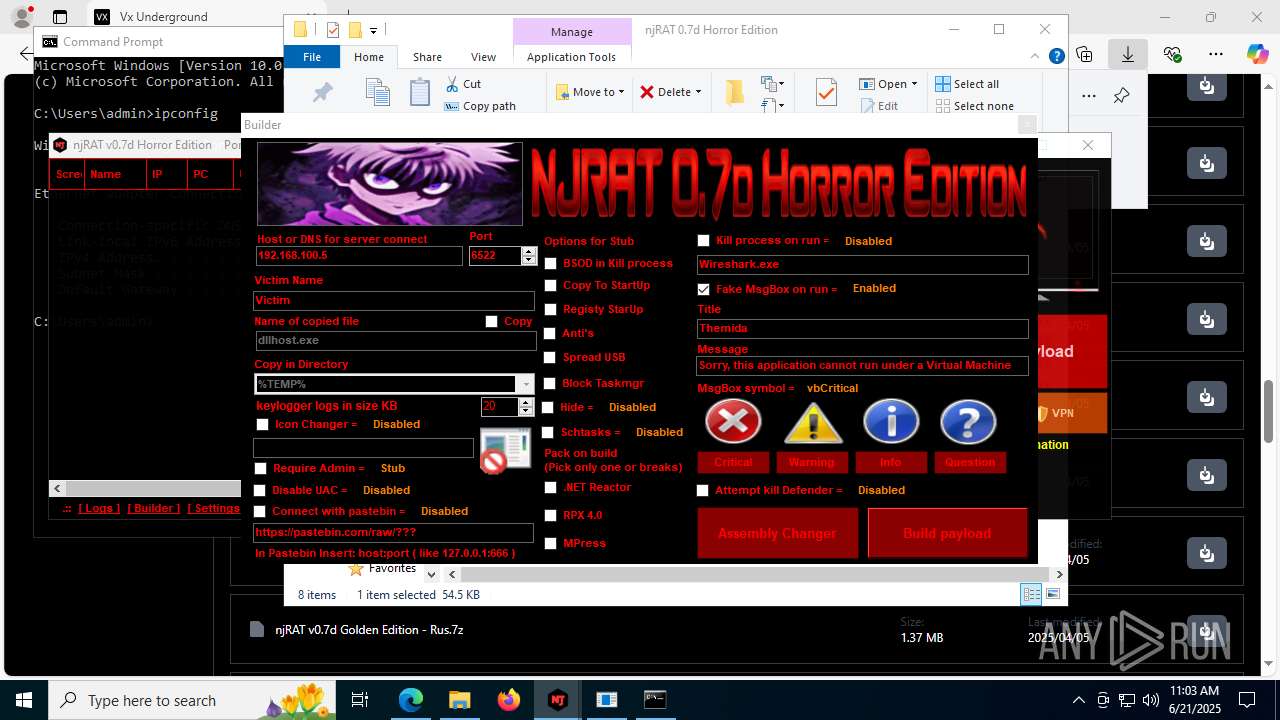
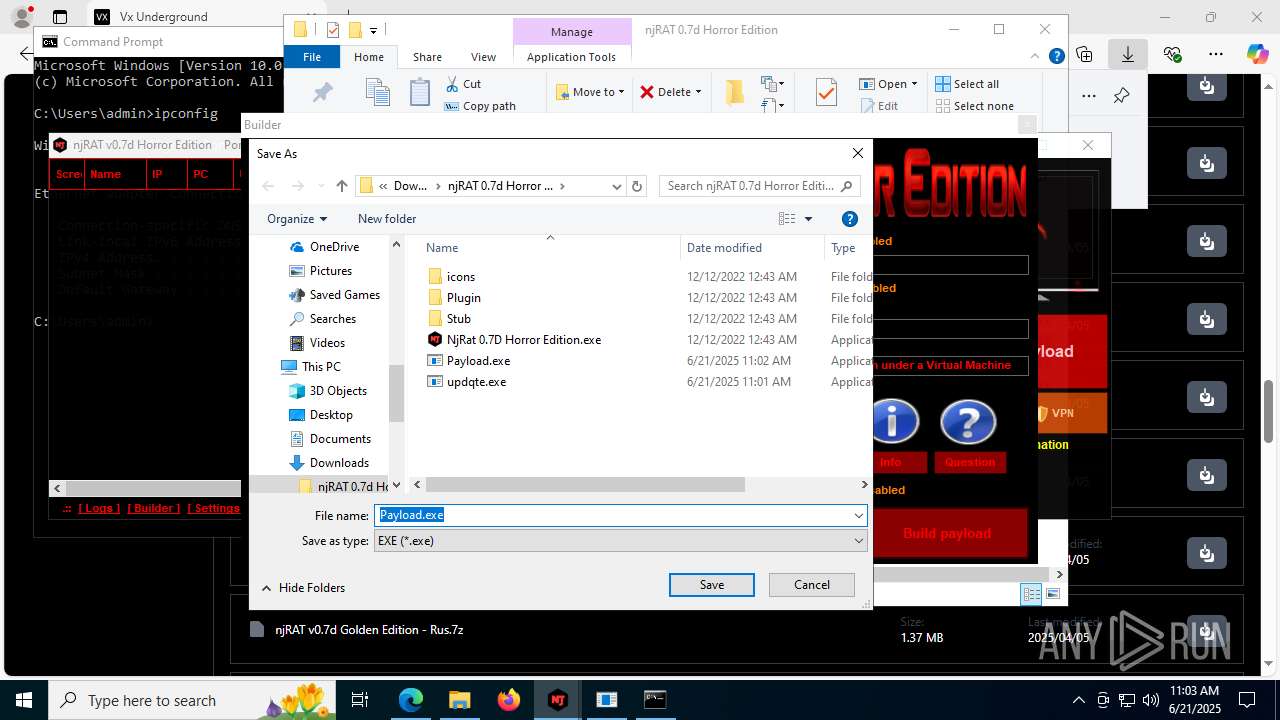
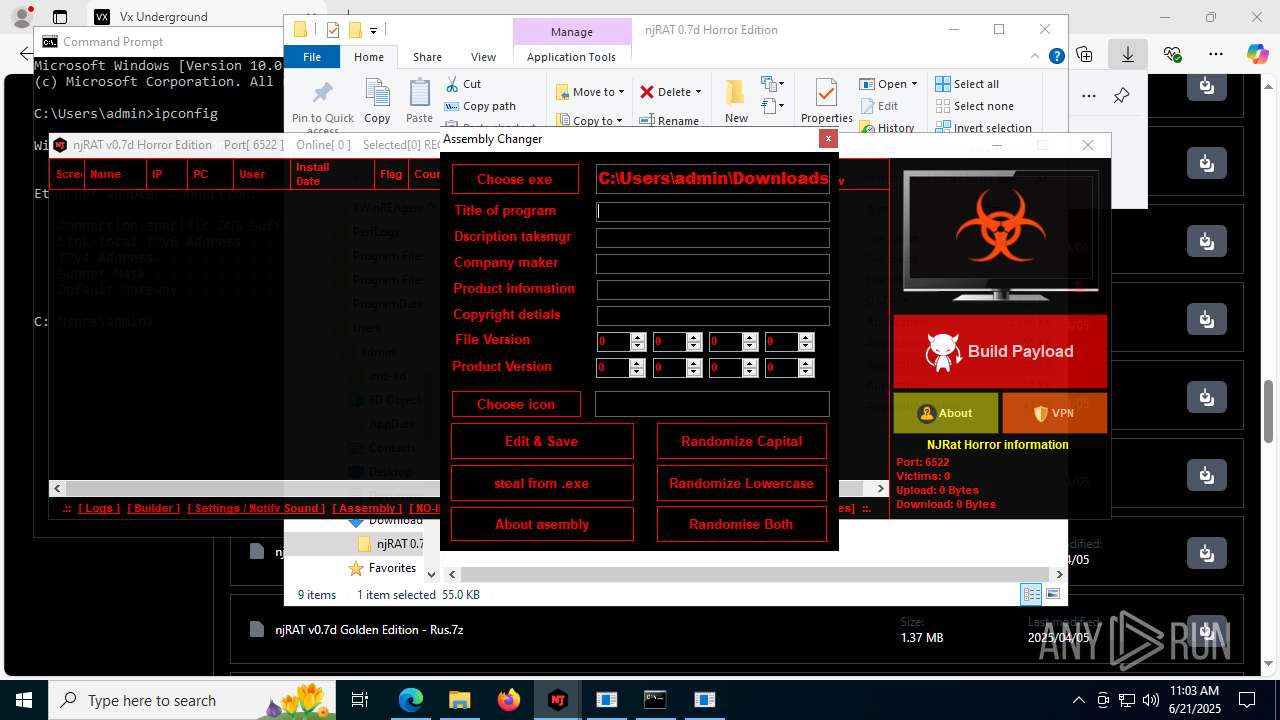
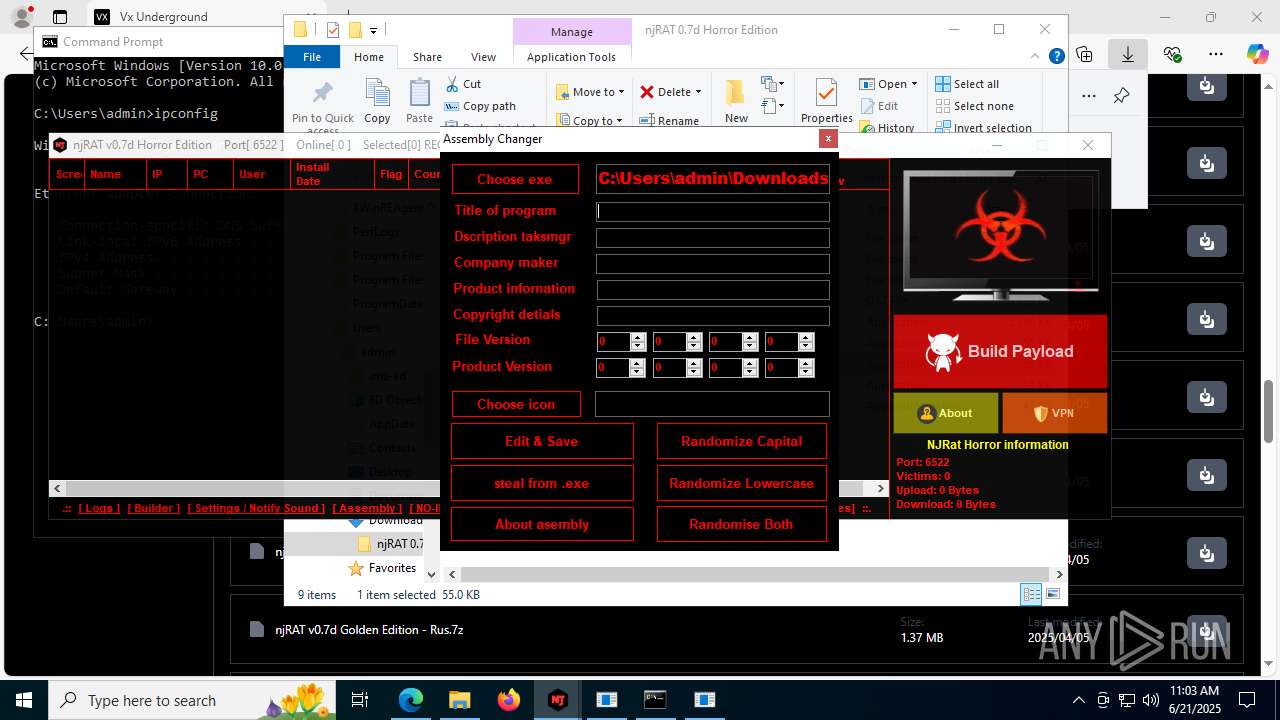
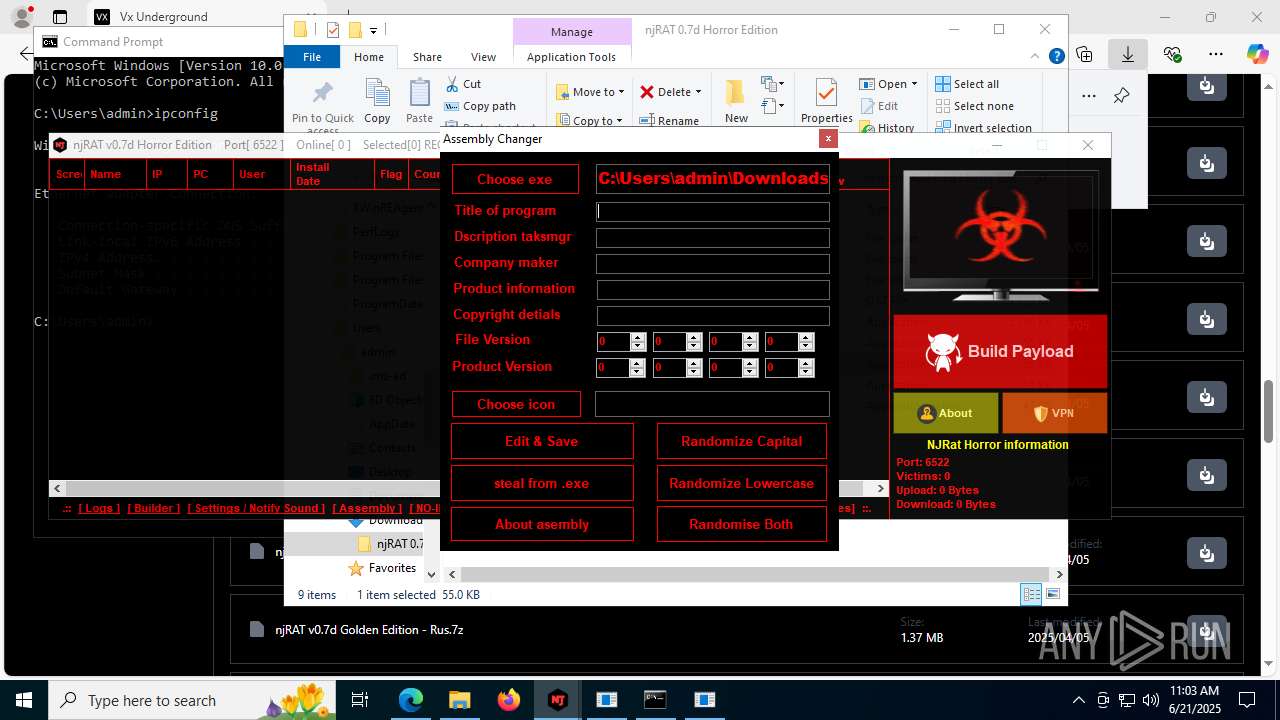
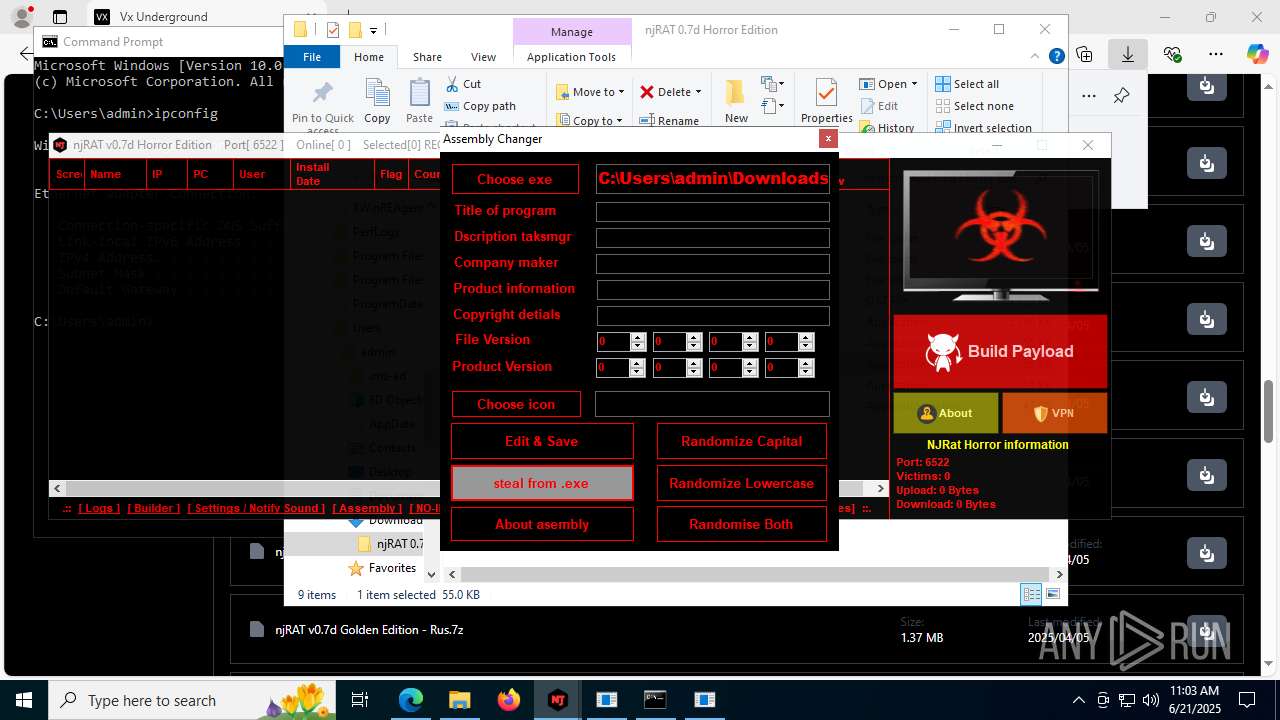
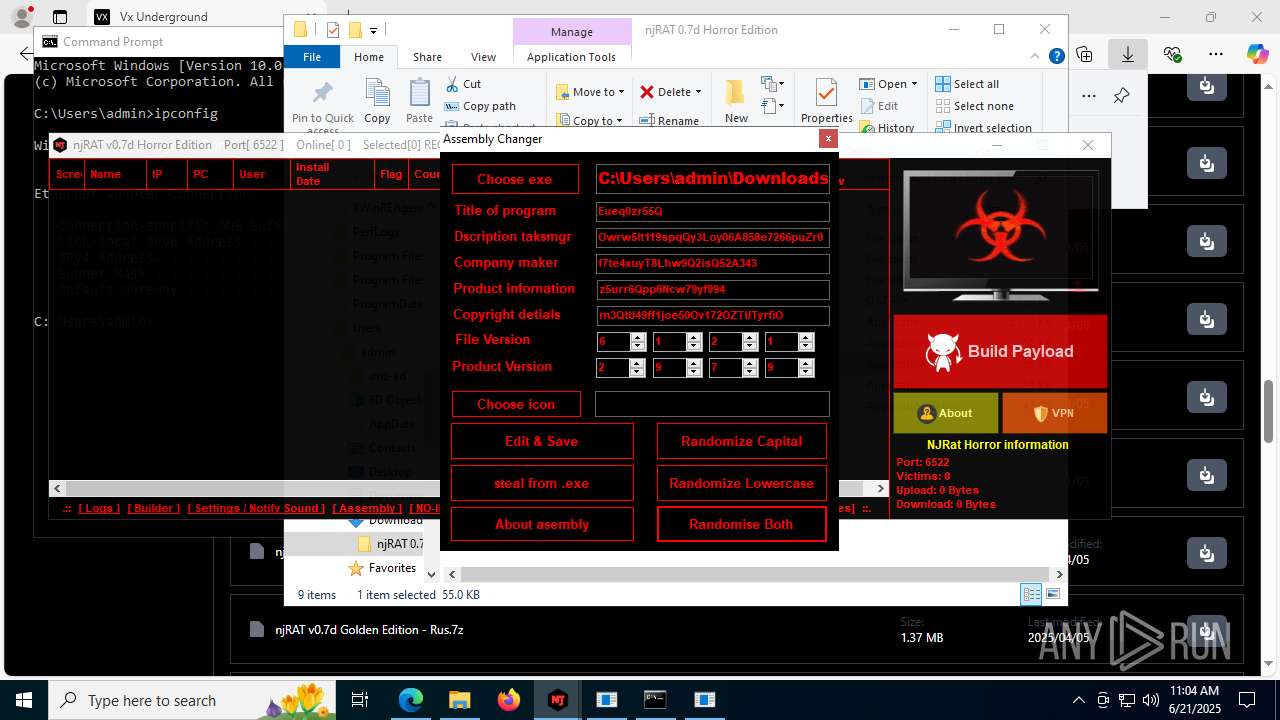
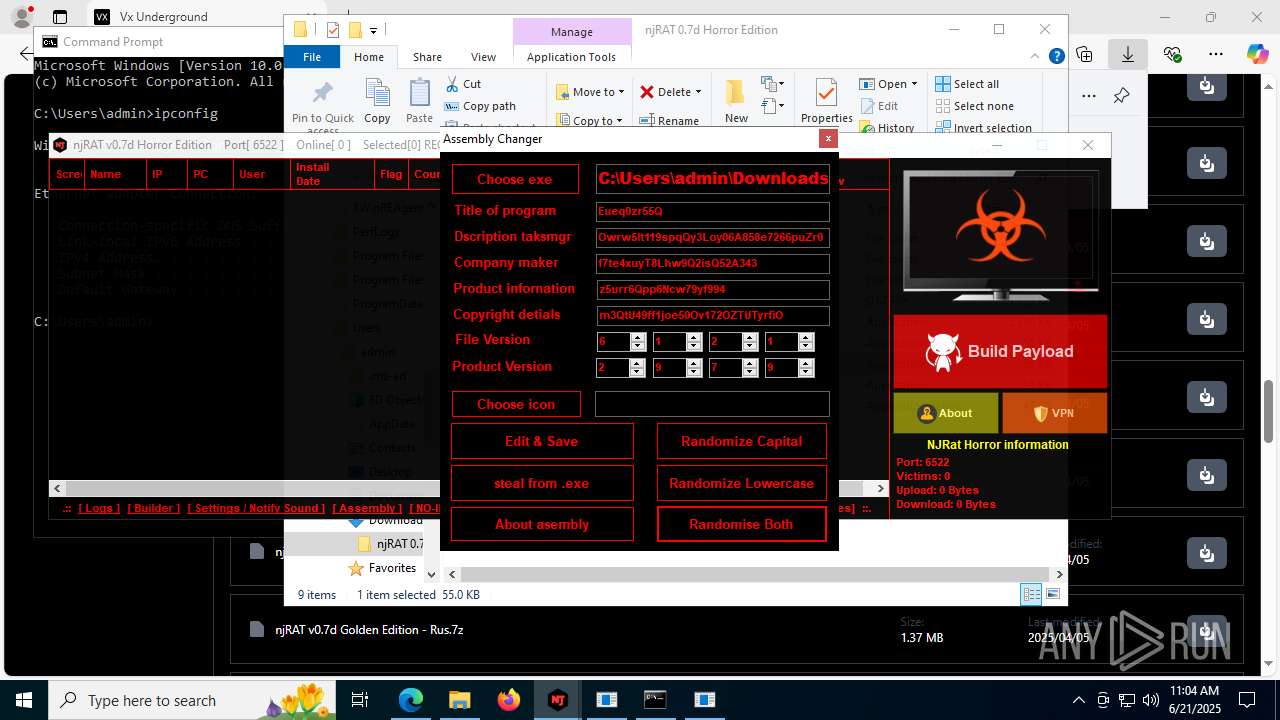
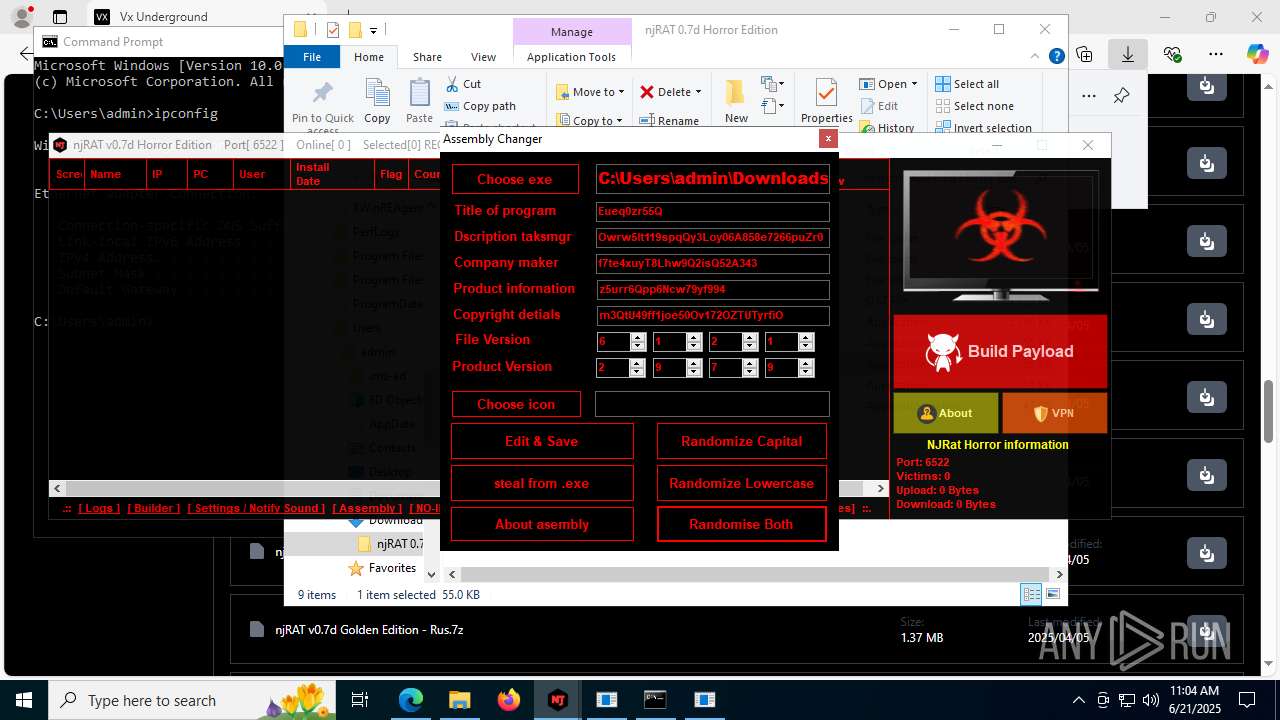
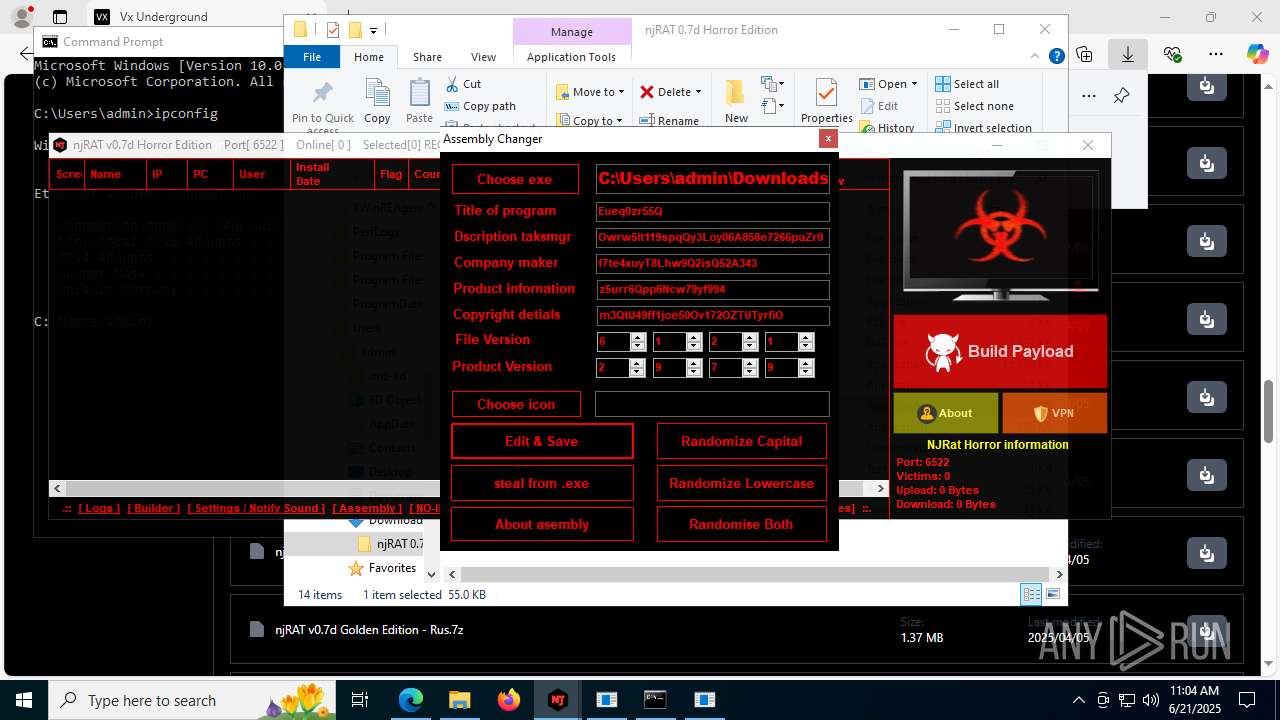
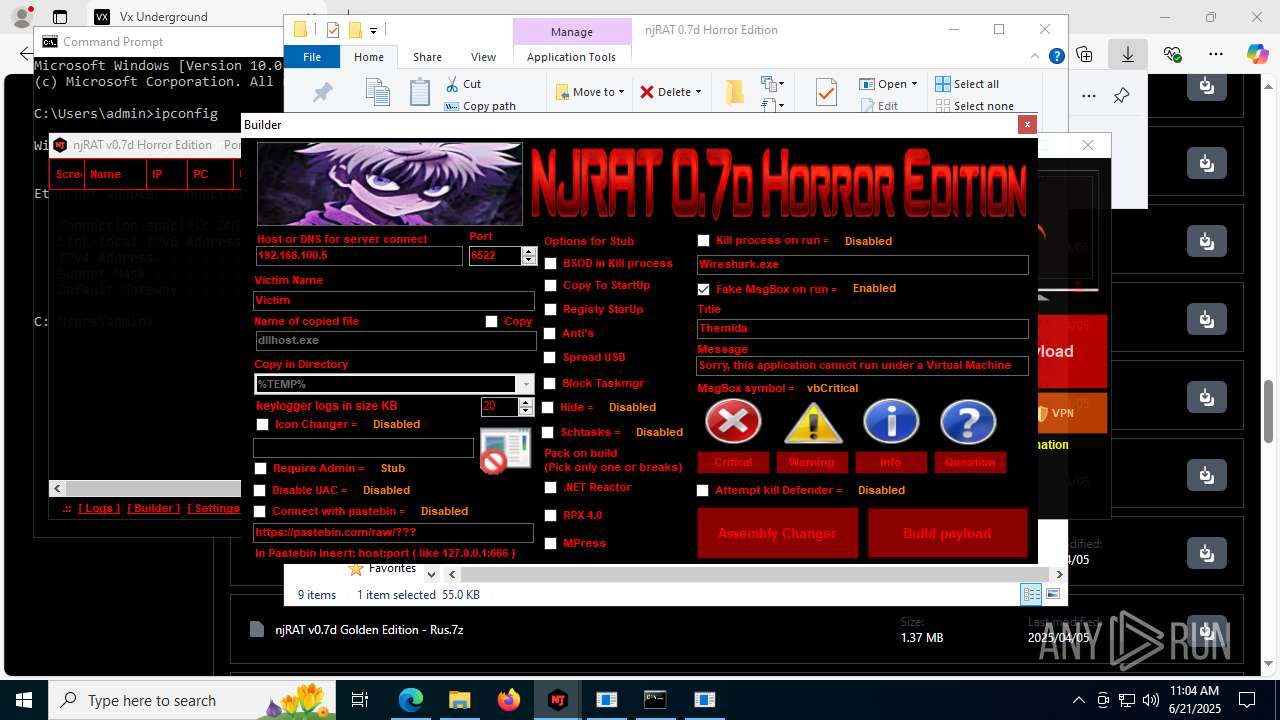
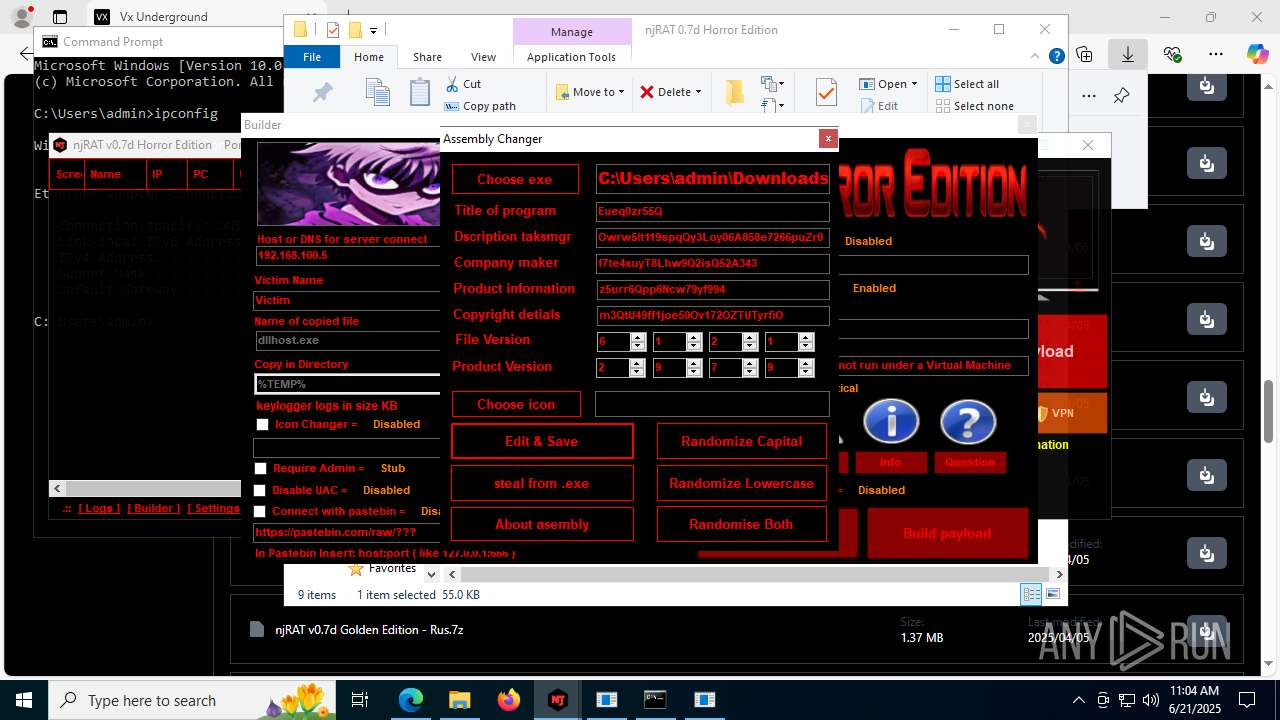
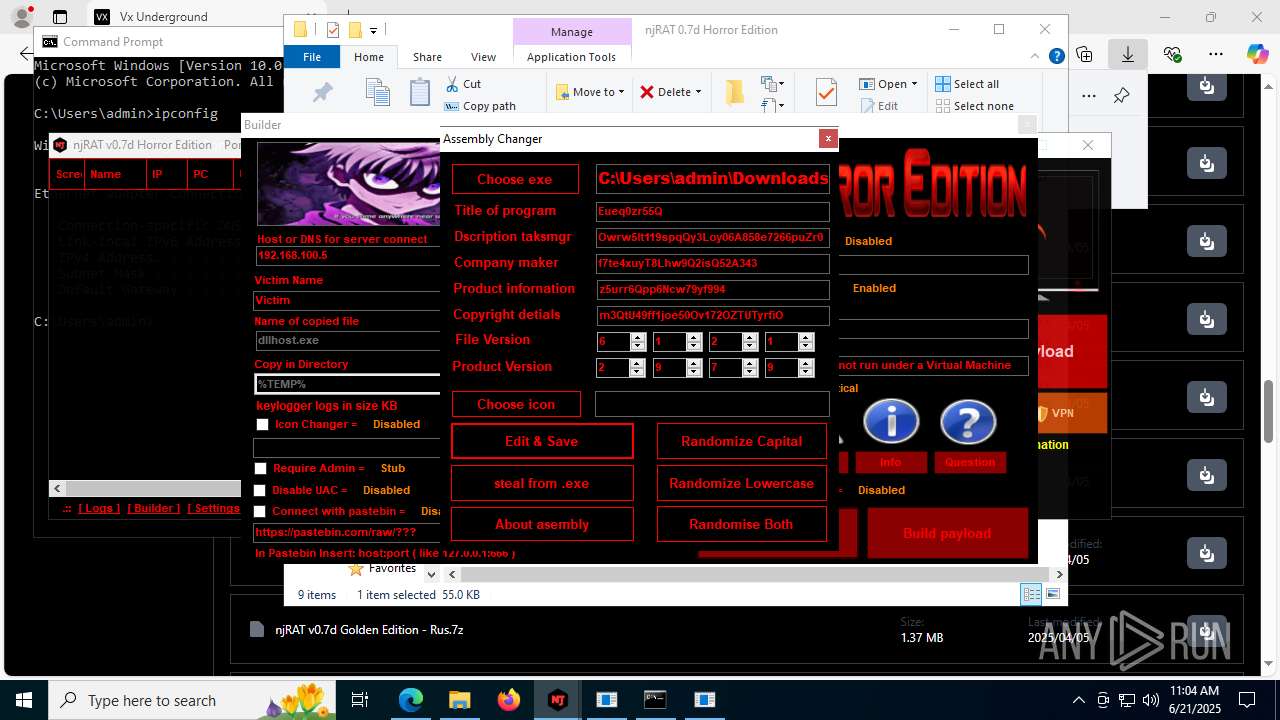
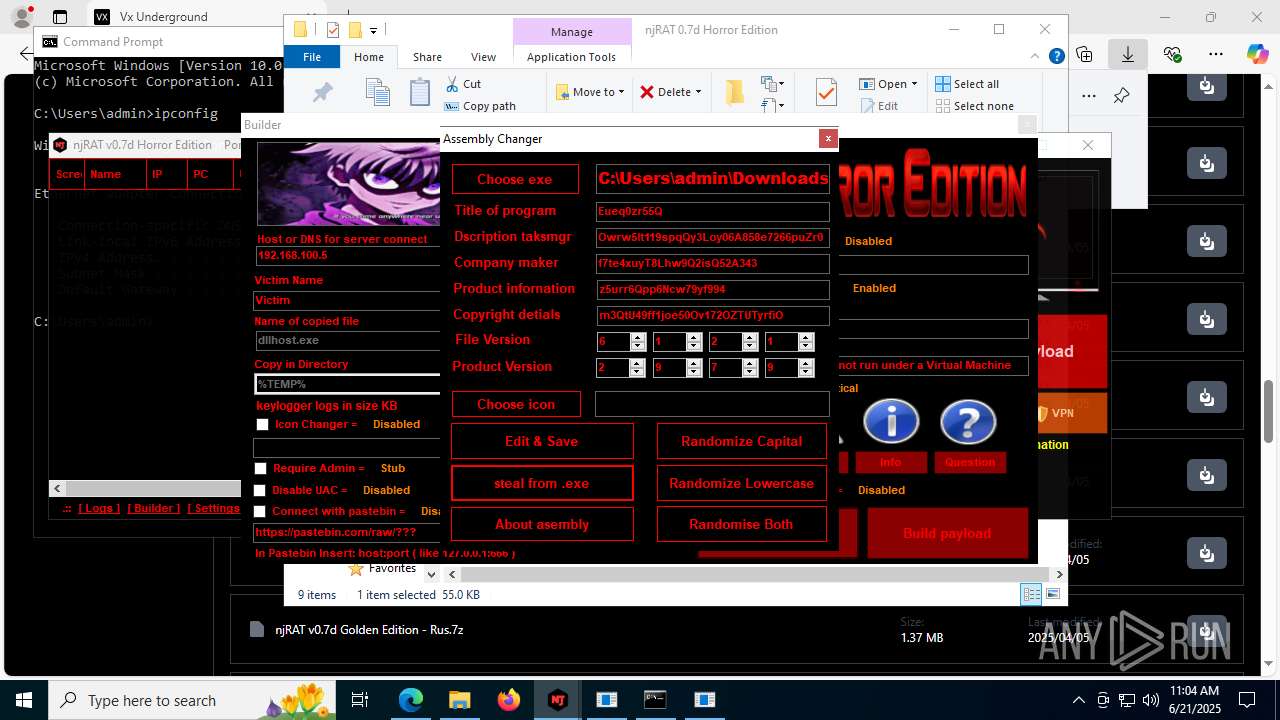
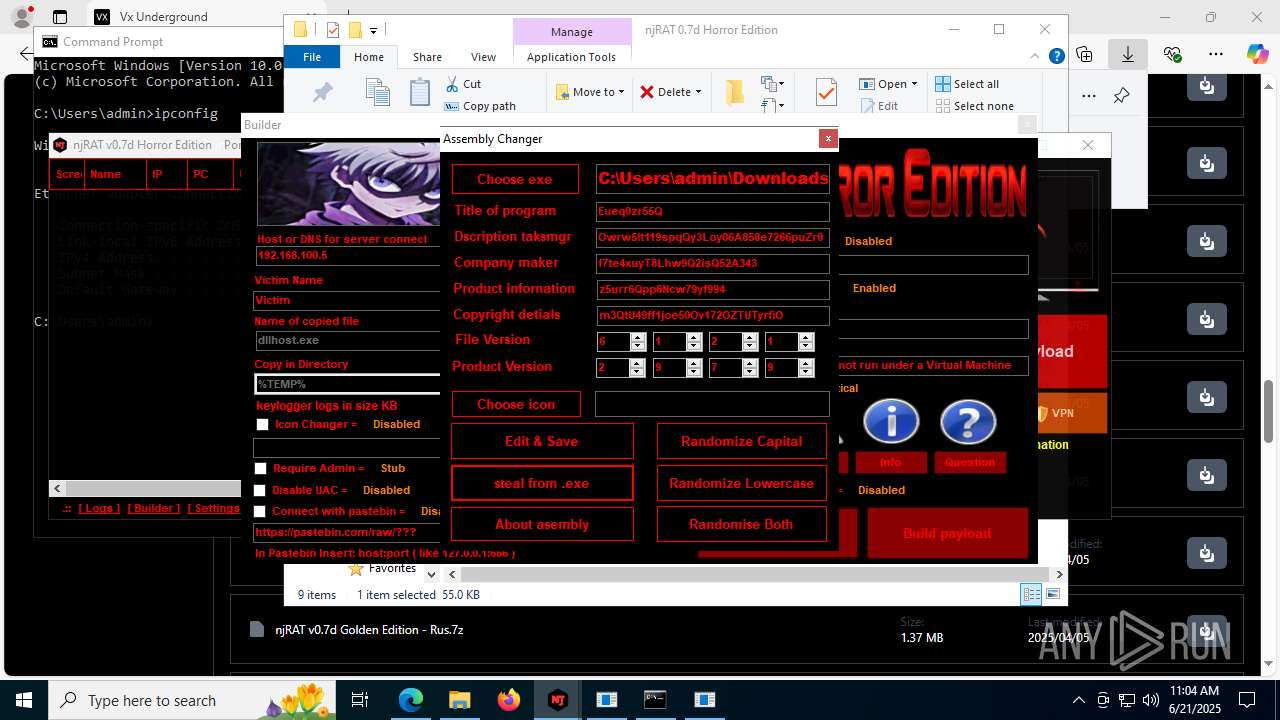
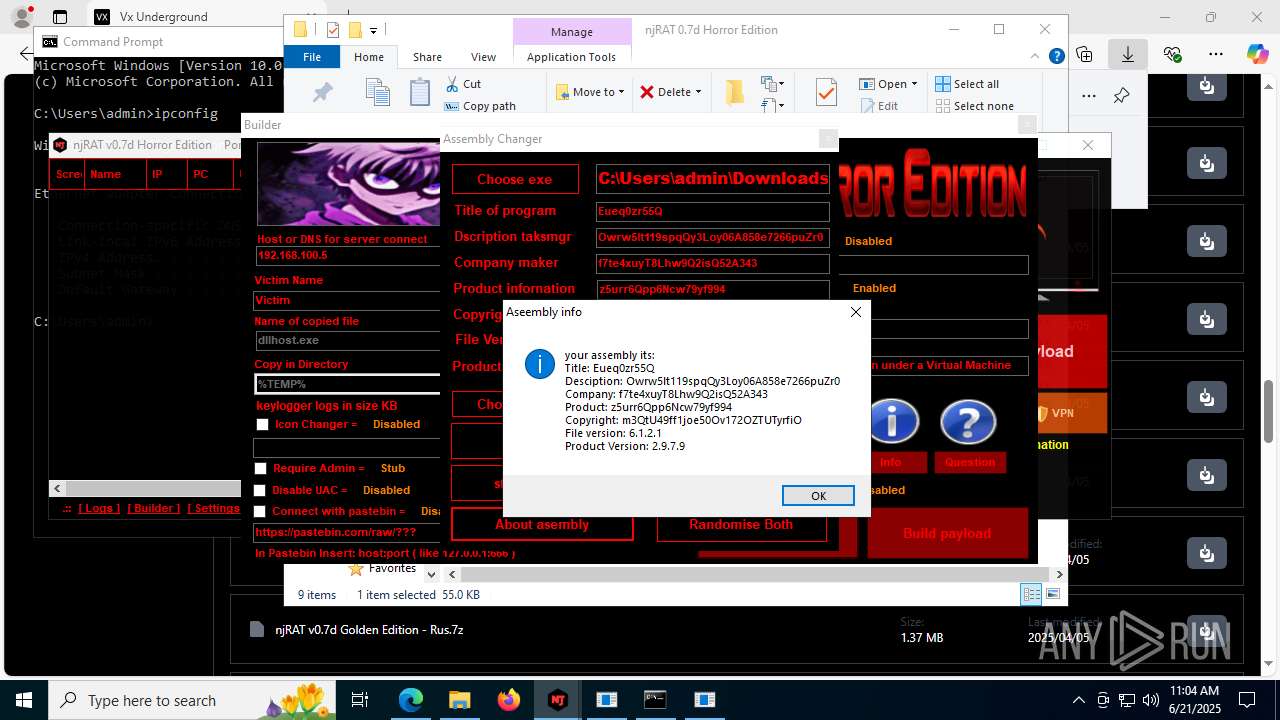
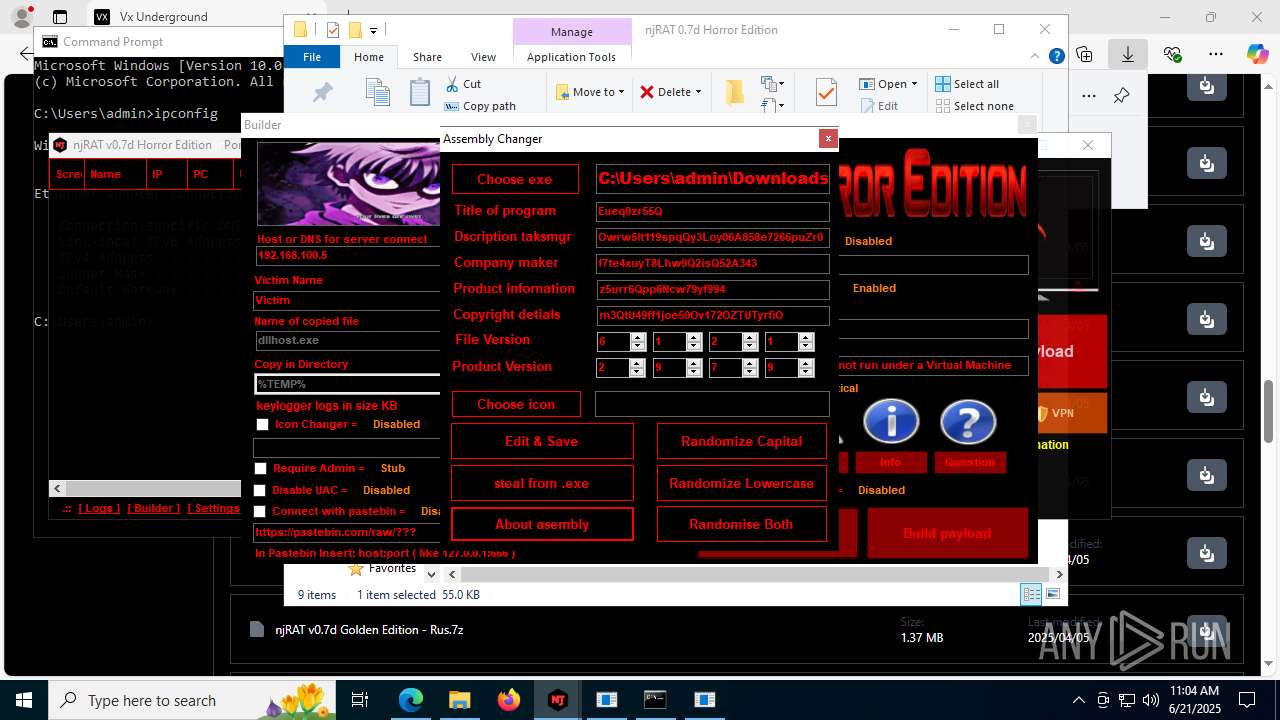
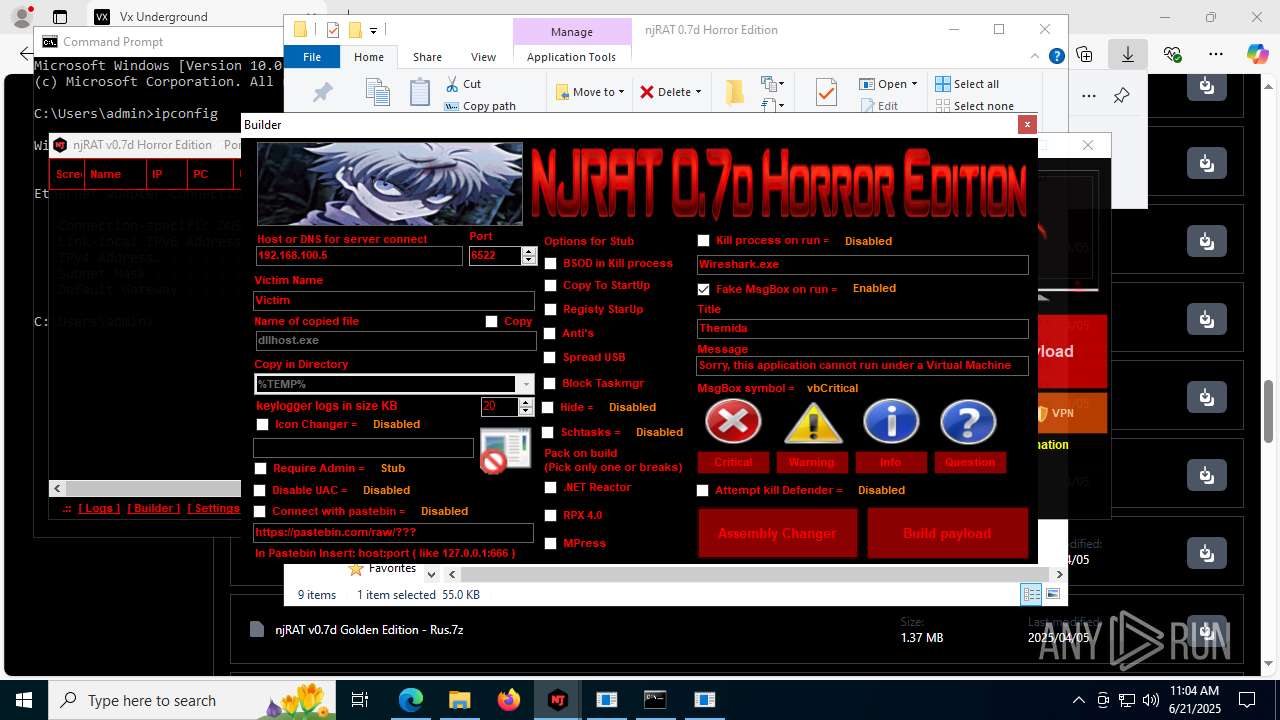
| URL: | https://vx-underground.org/Builders/NjRat |
| Full analysis: | https://app.any.run/tasks/208414e2-b8e2-4151-a84f-c7b3422fd0fb |
| Verdict: | Malicious activity |
| Threats: | njRAT is a remote access trojan. It is one of the most widely accessible RATs on the market that features an abundance of educational information. Interested attackers can even find tutorials on YouTube. This allows it to become one of the most popular RATs in the world. |
| Analysis date: | June 21, 2025, 10:59:36 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MD5: | 45D0B9189C5A691F7C06B1D7F954FA5B |
| SHA1: | A90D34FD82FCEAFB27CB8AAF64BB4F4D654EF852 |
| SHA256: | A573A97A1C36D3CE94DAC97F1A095C12B11BBAD7807920031684E9E01BD74709 |
| SSDEEP: | 3:N83mWAn:23mWA |
MALICIOUS
NJRAT has been detected (YARA)
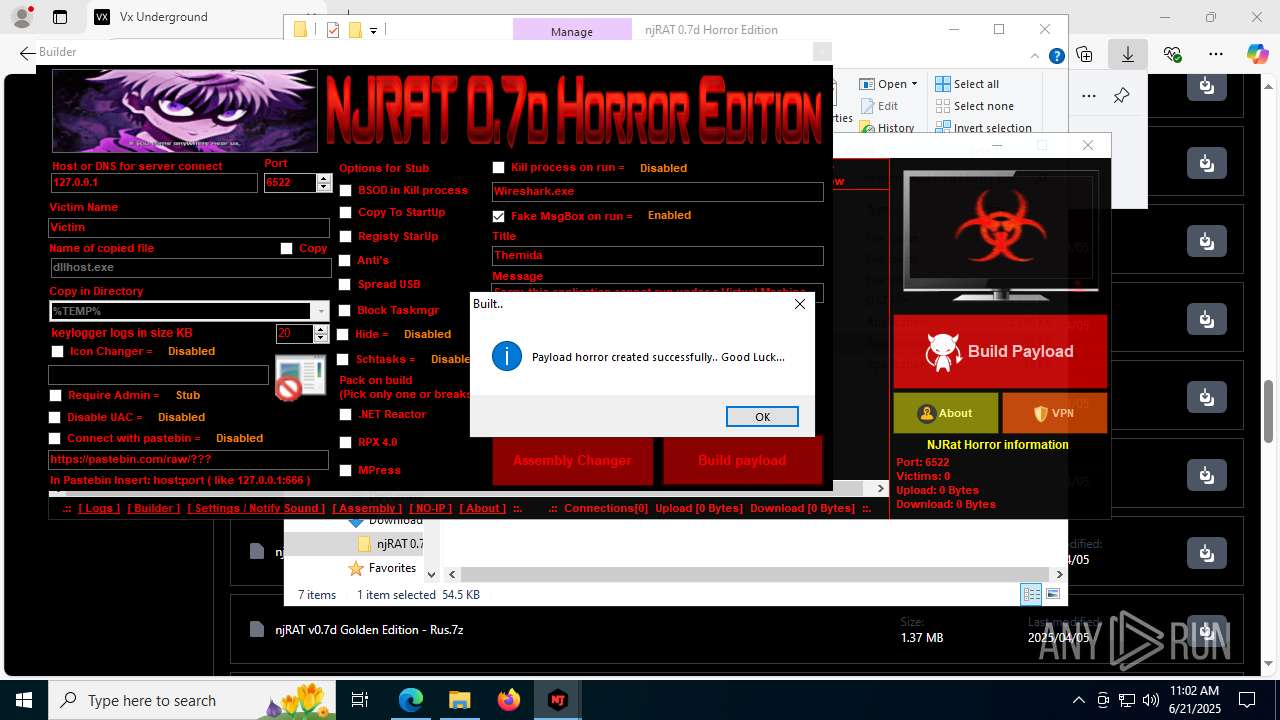
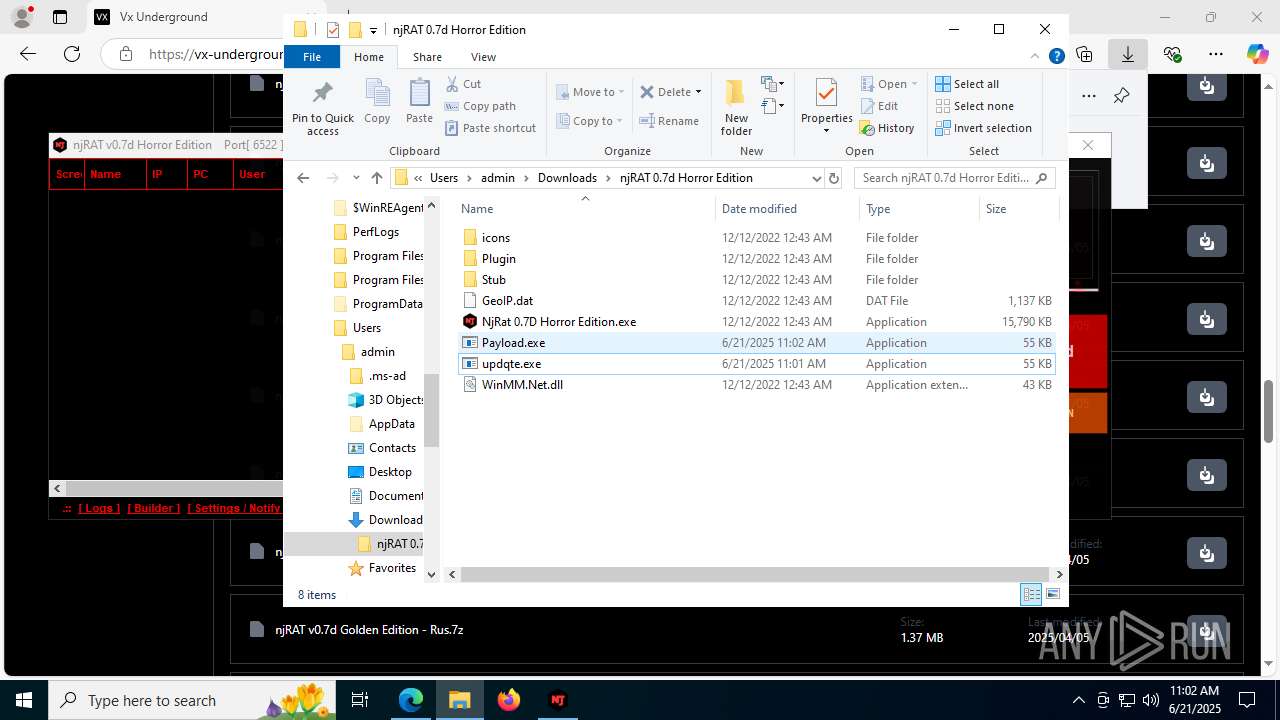
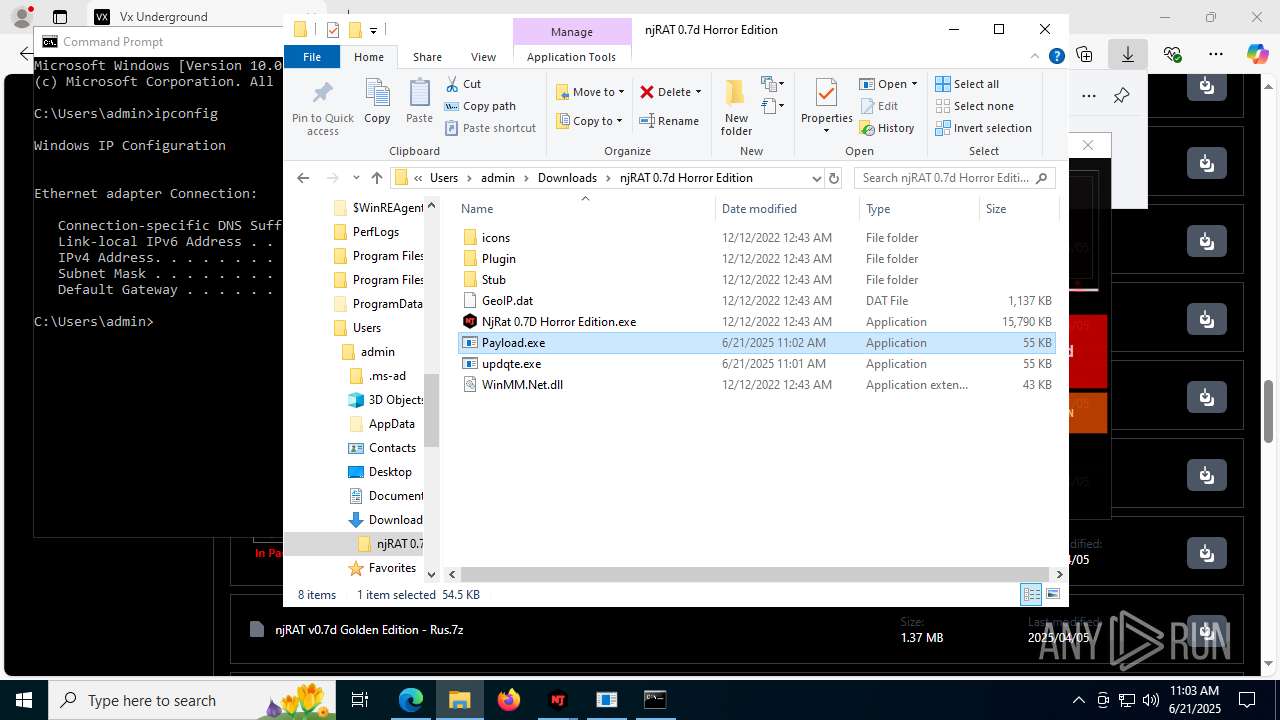
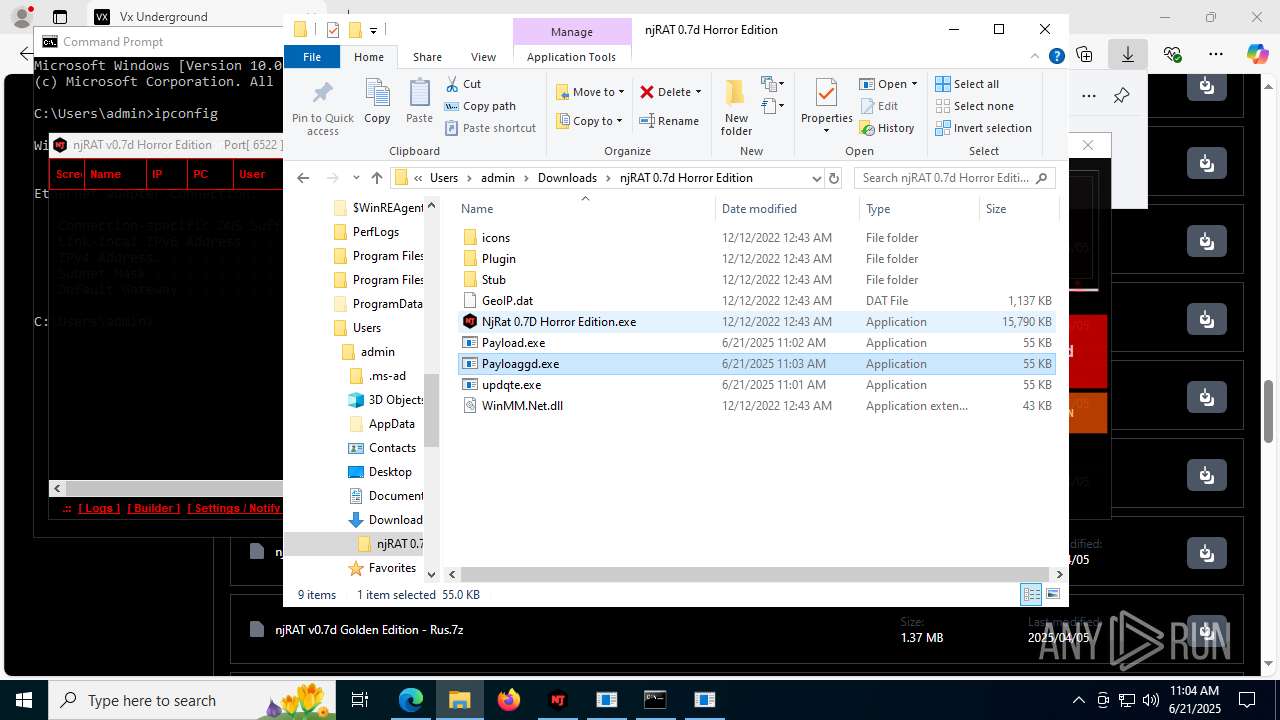
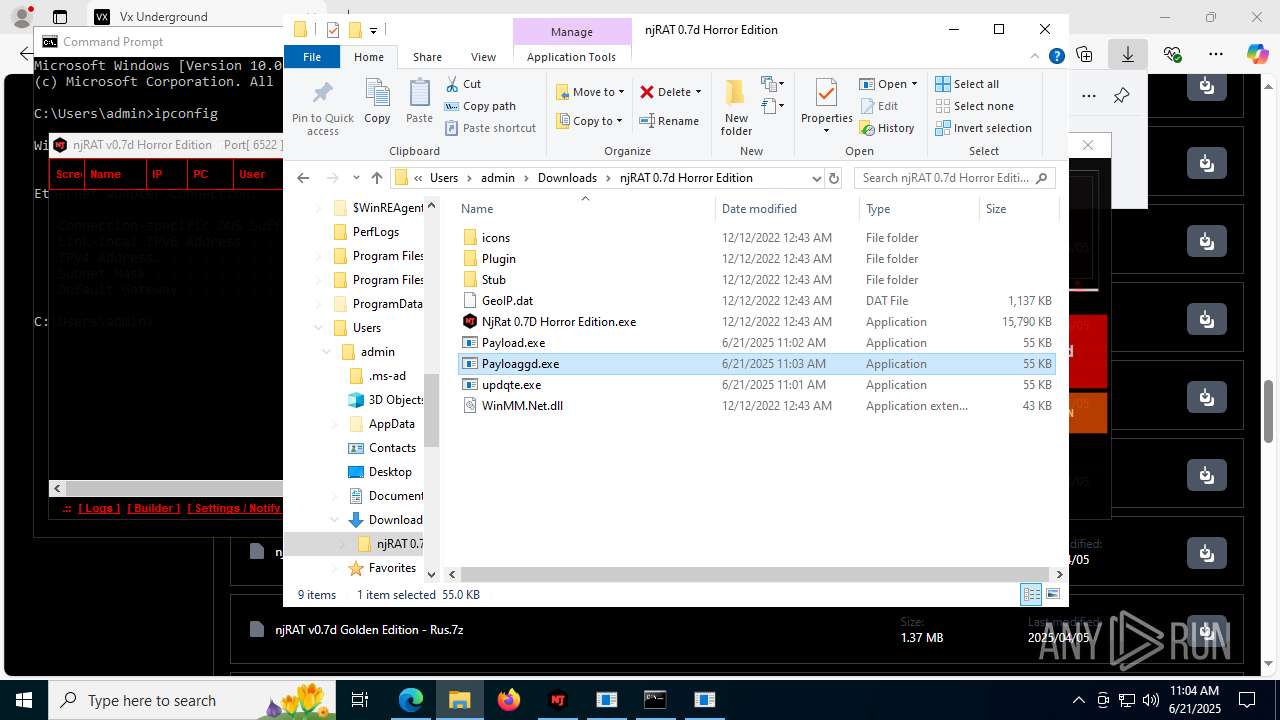
- updqte.exe (PID: 2124)
- Payload.exe (PID: 4844)
- Payloaggd.exe (PID: 4760)
NjRAT is detected
- updqte.exe (PID: 2124)
SUSPICIOUS
Reads Internet Explorer settings
- NjRat 0.7D Horror Edition.exe (PID: 8120)
Reads security settings of Internet Explorer
- NjRat 0.7D Horror Edition.exe (PID: 8120)
Reads the date of Windows installation
- NjRat 0.7D Horror Edition.exe (PID: 8120)
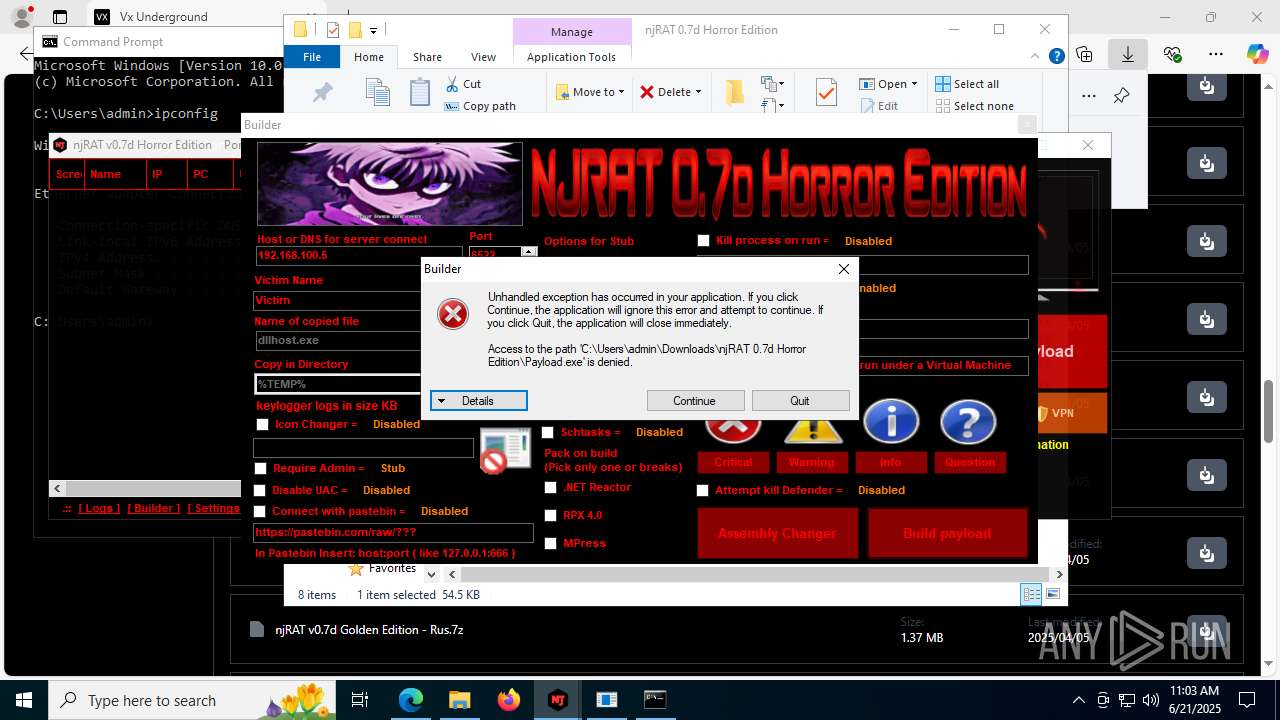
Executable content was dropped or overwritten
- ilasm.exe (PID: 8144)
- NjRat 0.7D Horror Edition.exe (PID: 8120)
- ilasm.exe (PID: 2728)
- ilasm.exe (PID: 2324)
- vbc.exe (PID: 5600)
There is functionality for taking screenshot (YARA)
- updqte.exe (PID: 2124)
- Payloaggd.exe (PID: 4760)
- Payload.exe (PID: 4844)
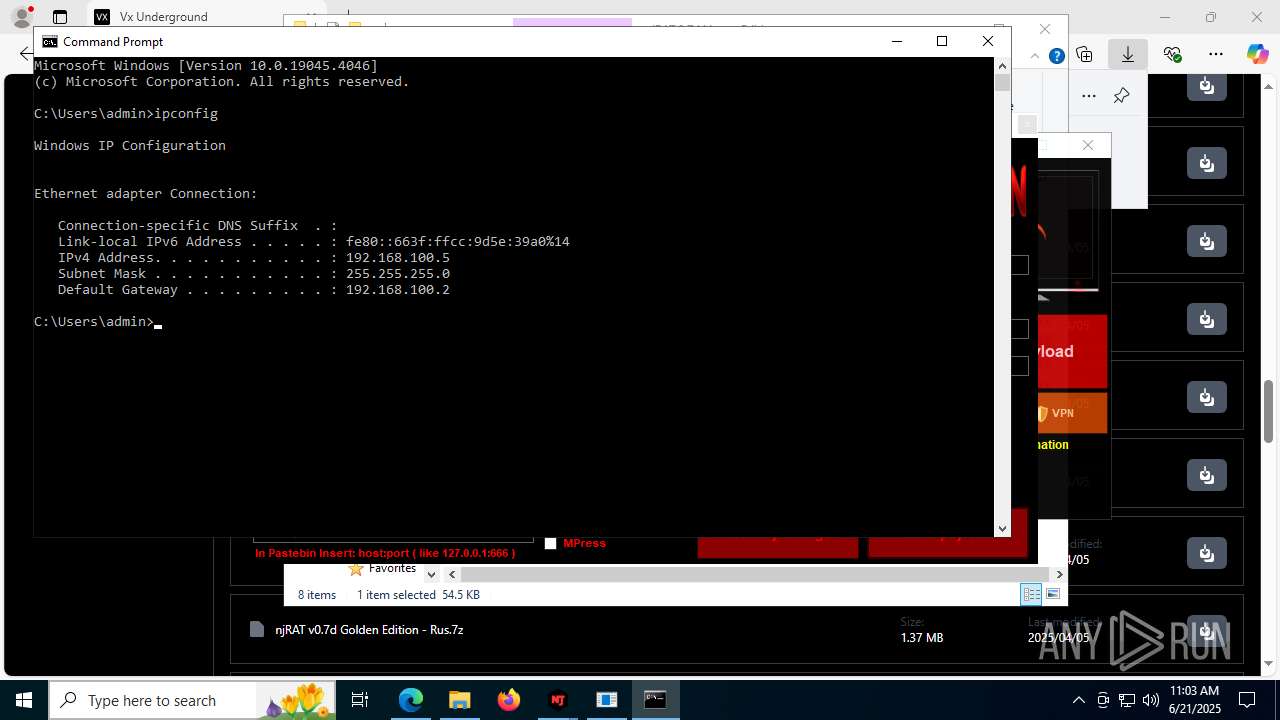
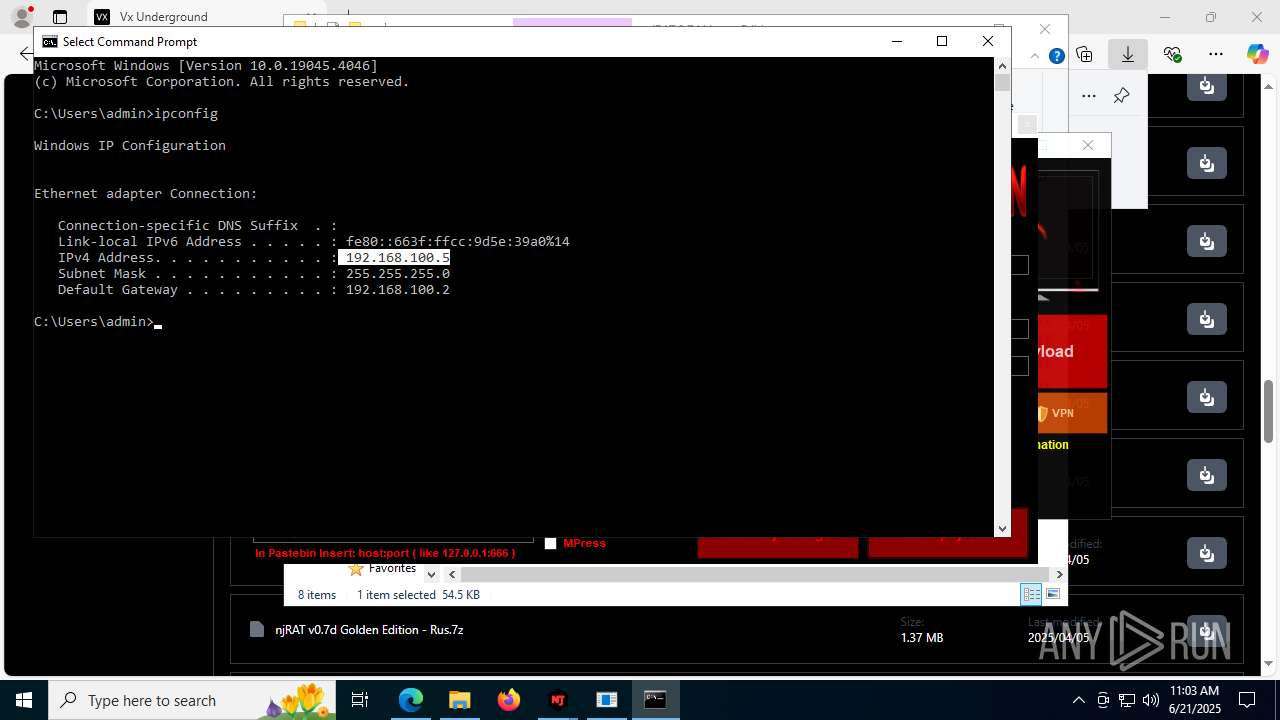
Process uses IPCONFIG to get network configuration information
- cmd.exe (PID: 2524)
Block-list domains
- NjRat 0.7D Horror Edition.exe (PID: 8120)
INFO
Application launched itself
- msedge.exe (PID: 3780)
Reads the computer name
- identity_helper.exe (PID: 7704)
- NjRat 0.7D Horror Edition.exe (PID: 8120)
- updqte.exe (PID: 2124)
- Payload.exe (PID: 4844)
- Payloaggd.exe (PID: 4760)
- res.exe (PID: 3860)
- res.exe (PID: 8160)
- Payloaggd.exe (PID: 3976)
- res.exe (PID: 5628)
Checks supported languages
- identity_helper.exe (PID: 7704)
- NjRat 0.7D Horror Edition.exe (PID: 8120)
- ilasm.exe (PID: 8144)
- updqte.exe (PID: 2124)
- Payload.exe (PID: 4844)
- ilasm.exe (PID: 2728)
- ilasm.exe (PID: 2324)
- Payloaggd.exe (PID: 4760)
- vbc.exe (PID: 5600)
- cvtres.exe (PID: 8168)
- res.exe (PID: 5628)
- Payloaggd.exe (PID: 3976)
- res.exe (PID: 3860)
- res.exe (PID: 8160)
Reads Environment values
- identity_helper.exe (PID: 7704)
- NjRat 0.7D Horror Edition.exe (PID: 8120)
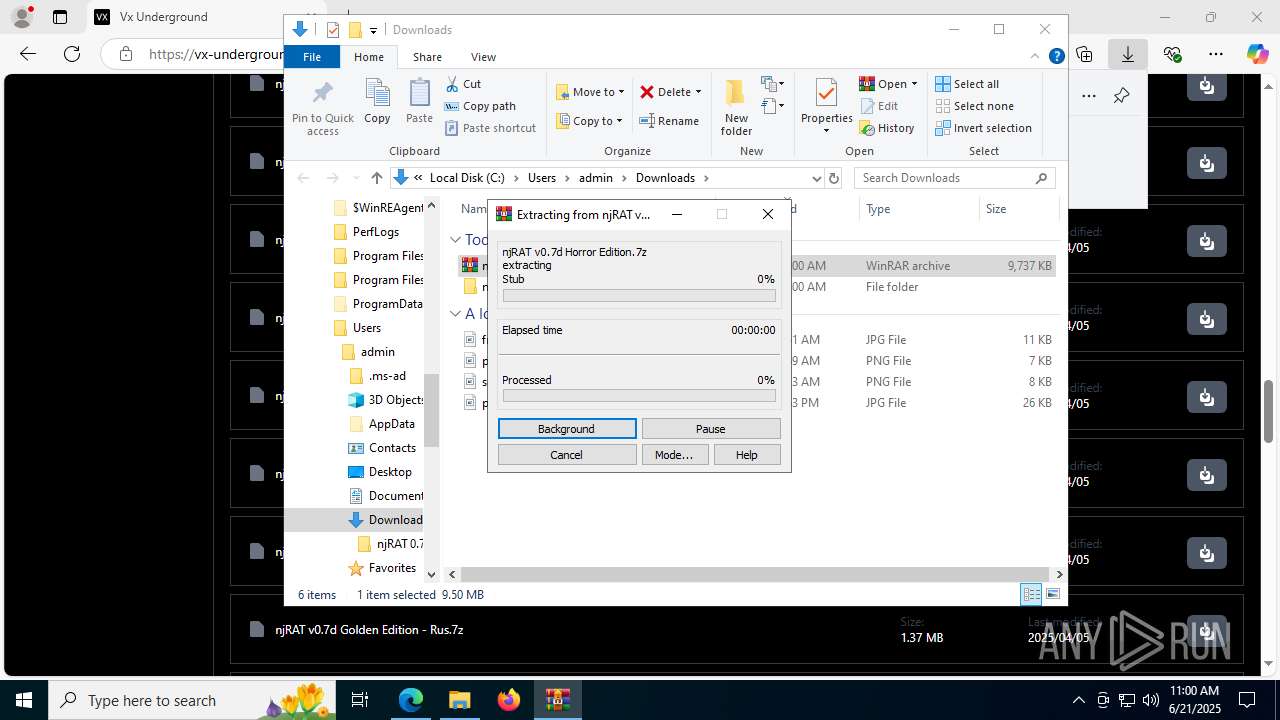
Manual execution by a user
- WinRAR.exe (PID: 7192)
- NjRat 0.7D Horror Edition.exe (PID: 8120)
- updqte.exe (PID: 2124)
- Payload.exe (PID: 4844)
- Payloaggd.exe (PID: 4760)
- cmd.exe (PID: 2524)
- Payloaggd.exe (PID: 3976)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 7192)
Reads the machine GUID from the registry
- NjRat 0.7D Horror Edition.exe (PID: 8120)
- updqte.exe (PID: 2124)
- cvtres.exe (PID: 8168)
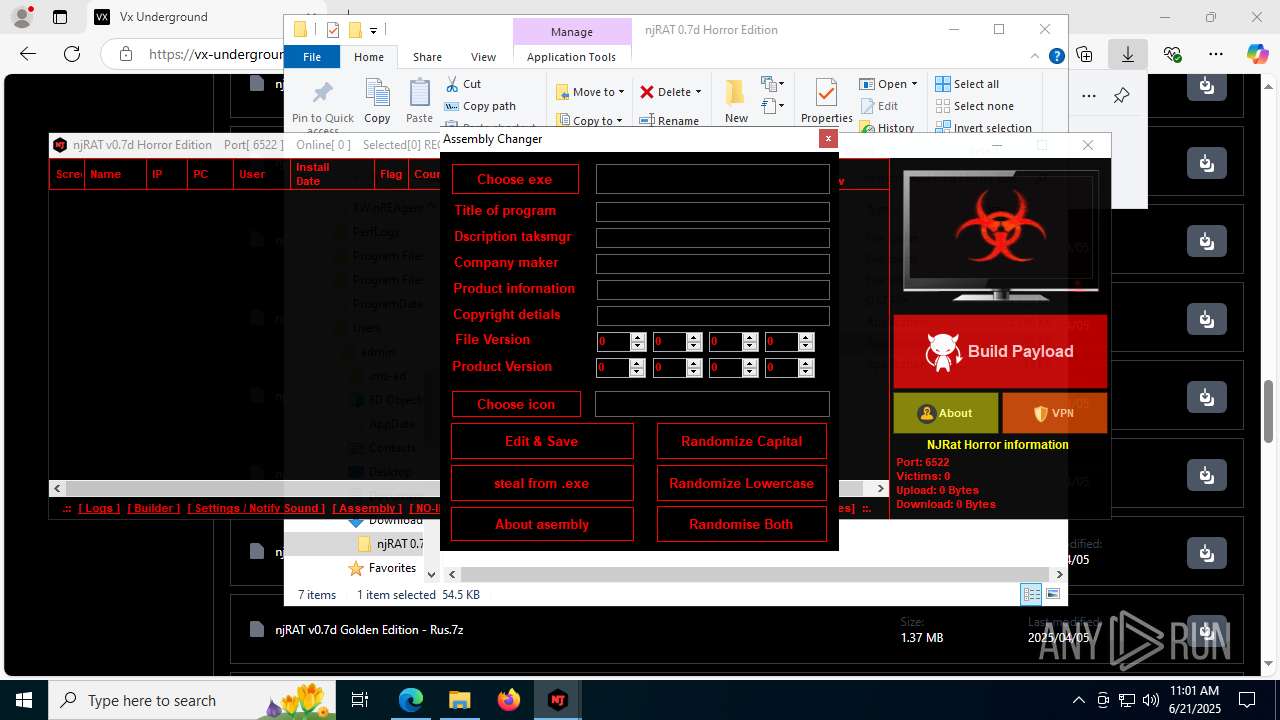
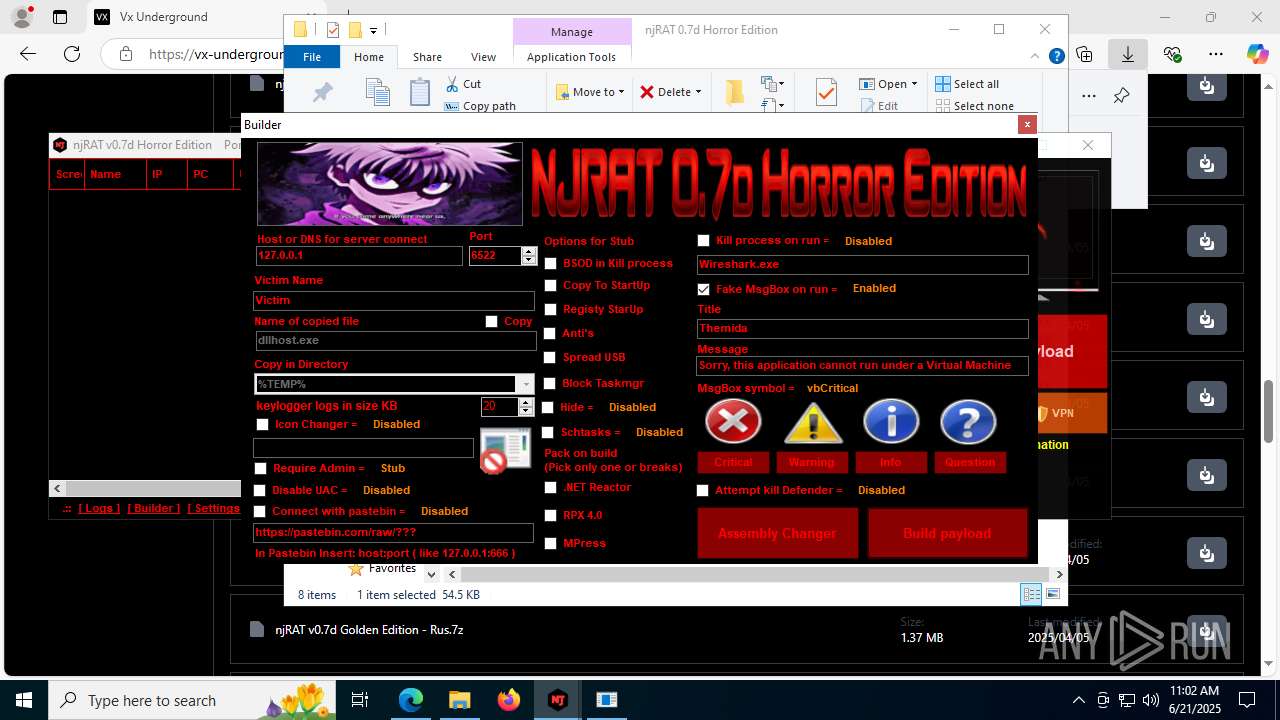
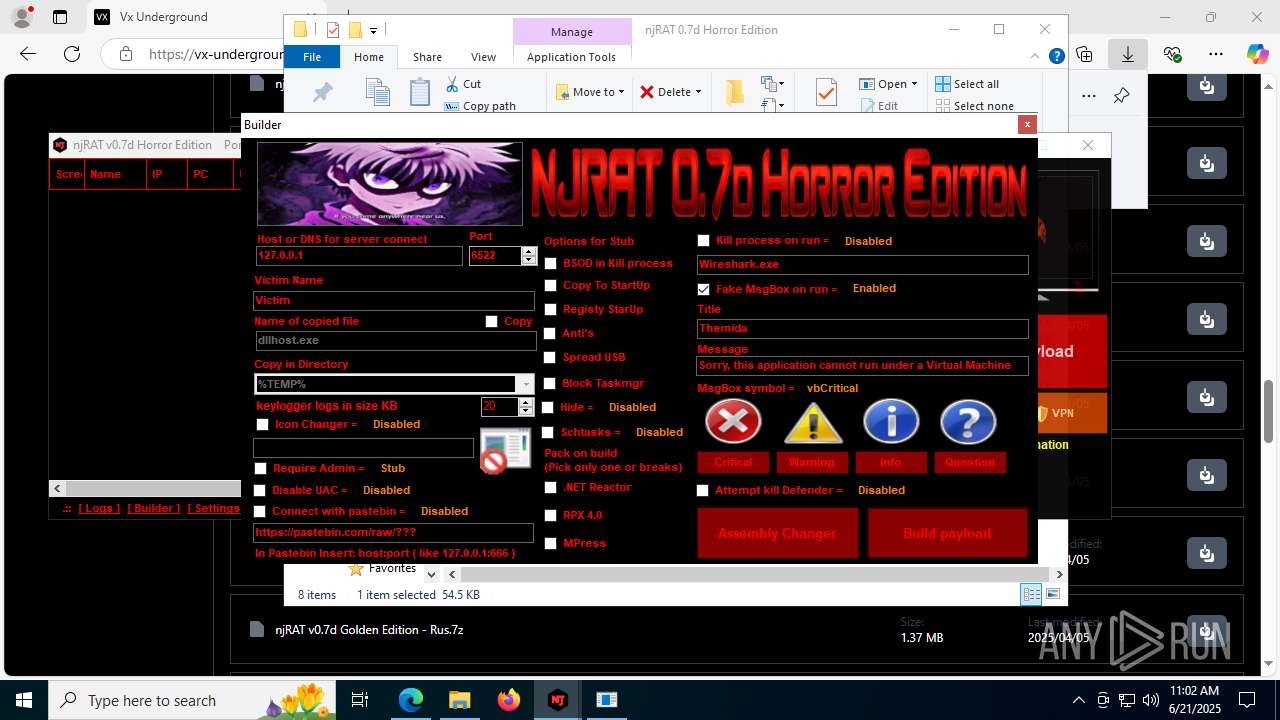
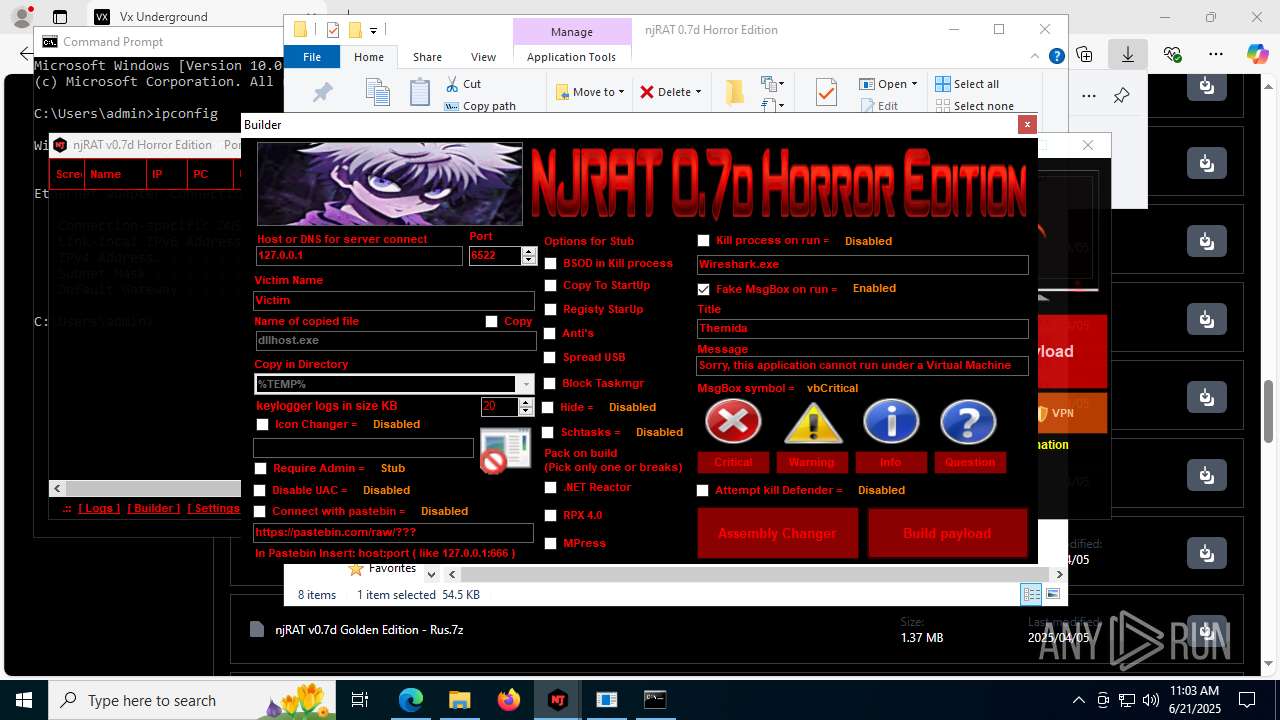
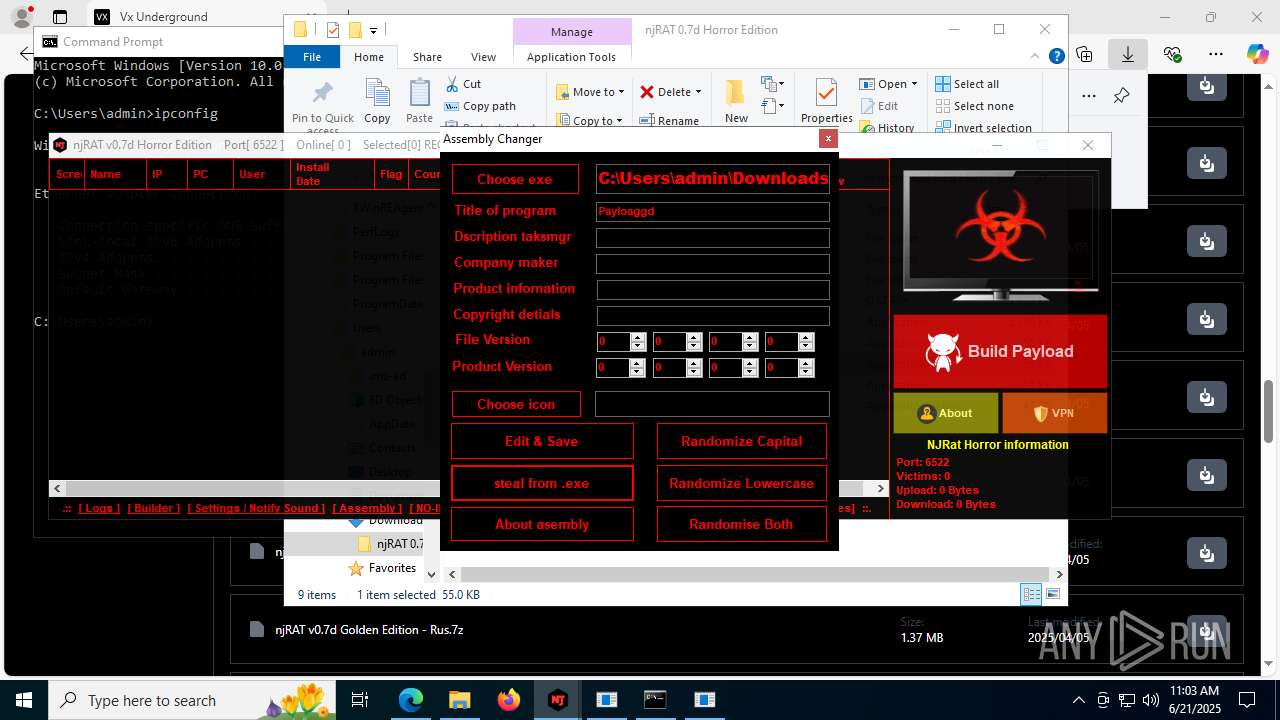
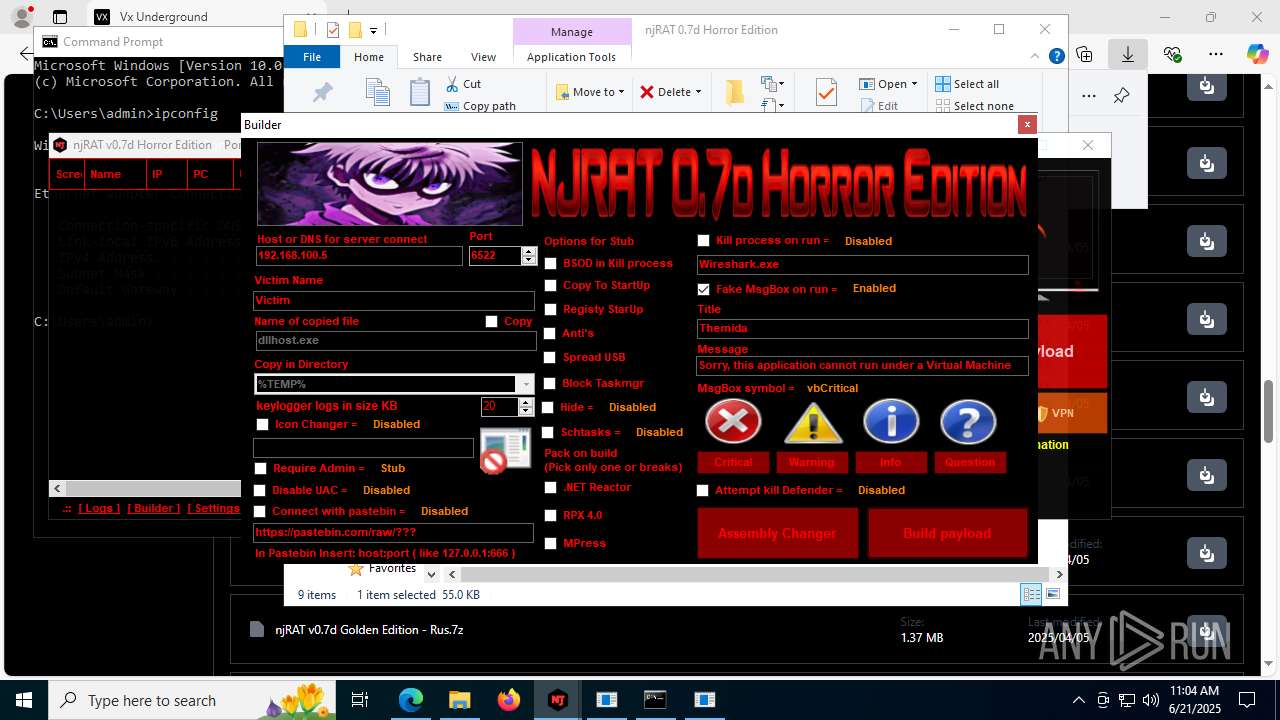
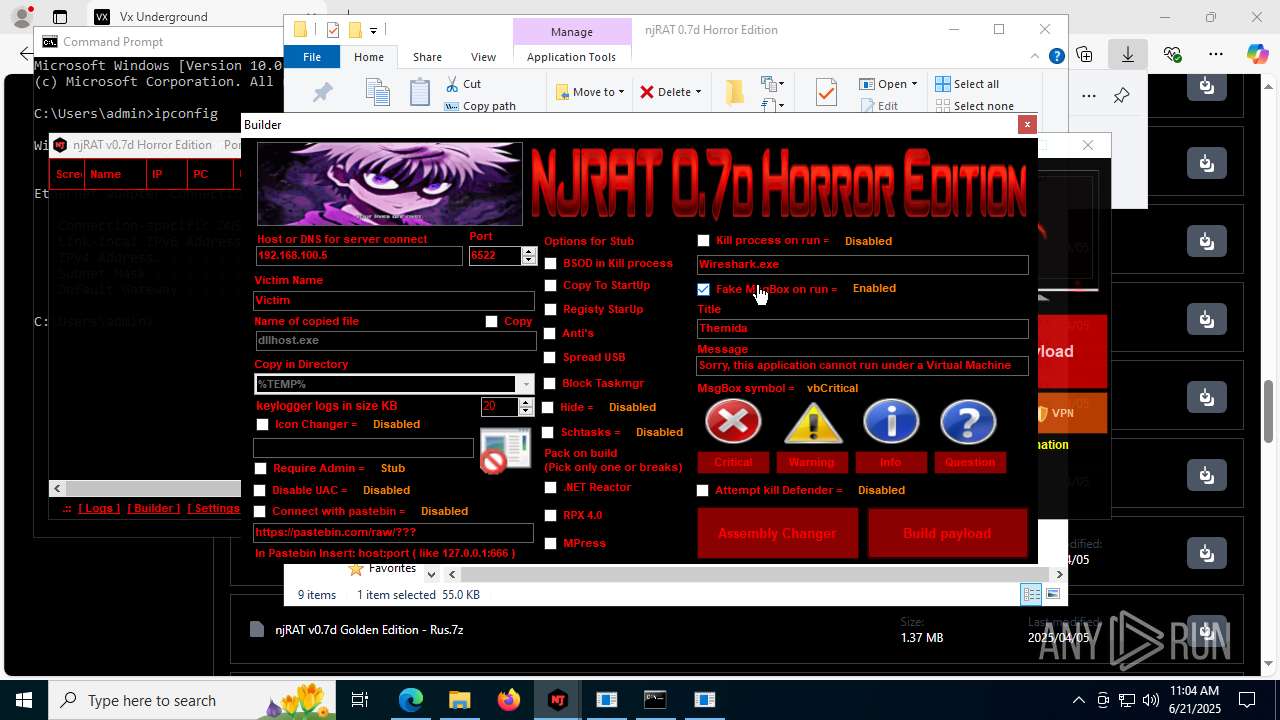
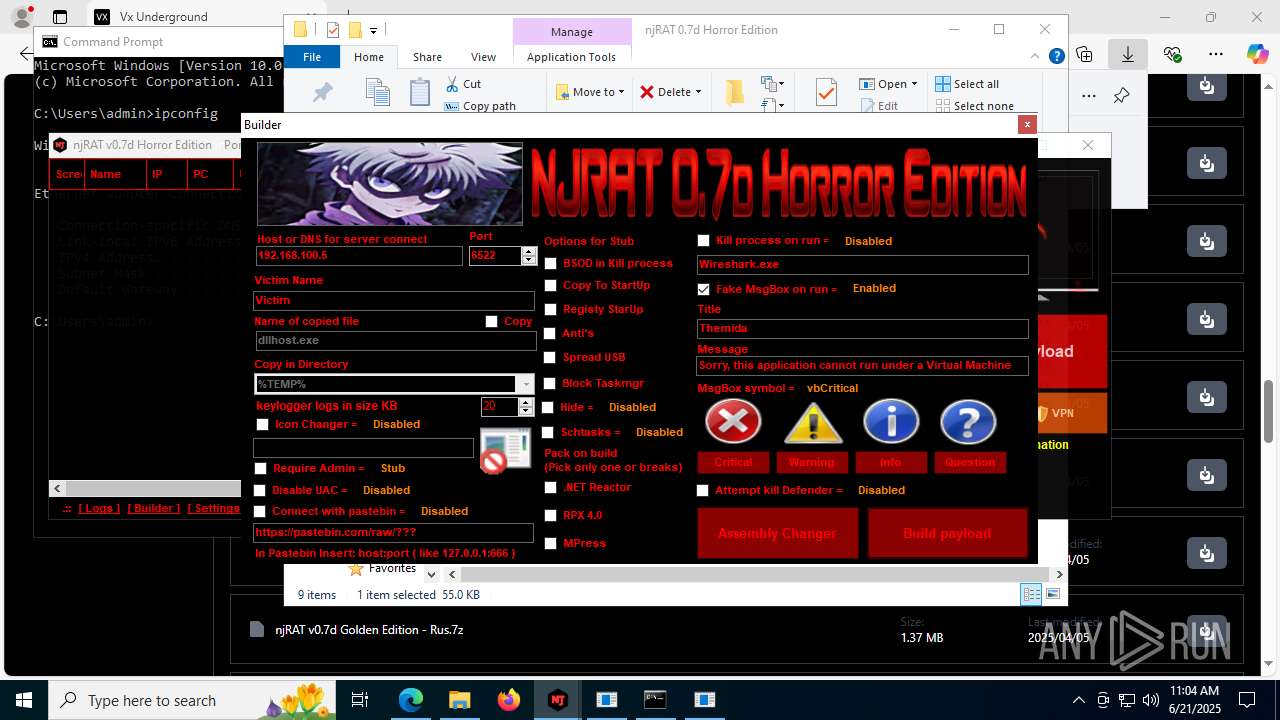
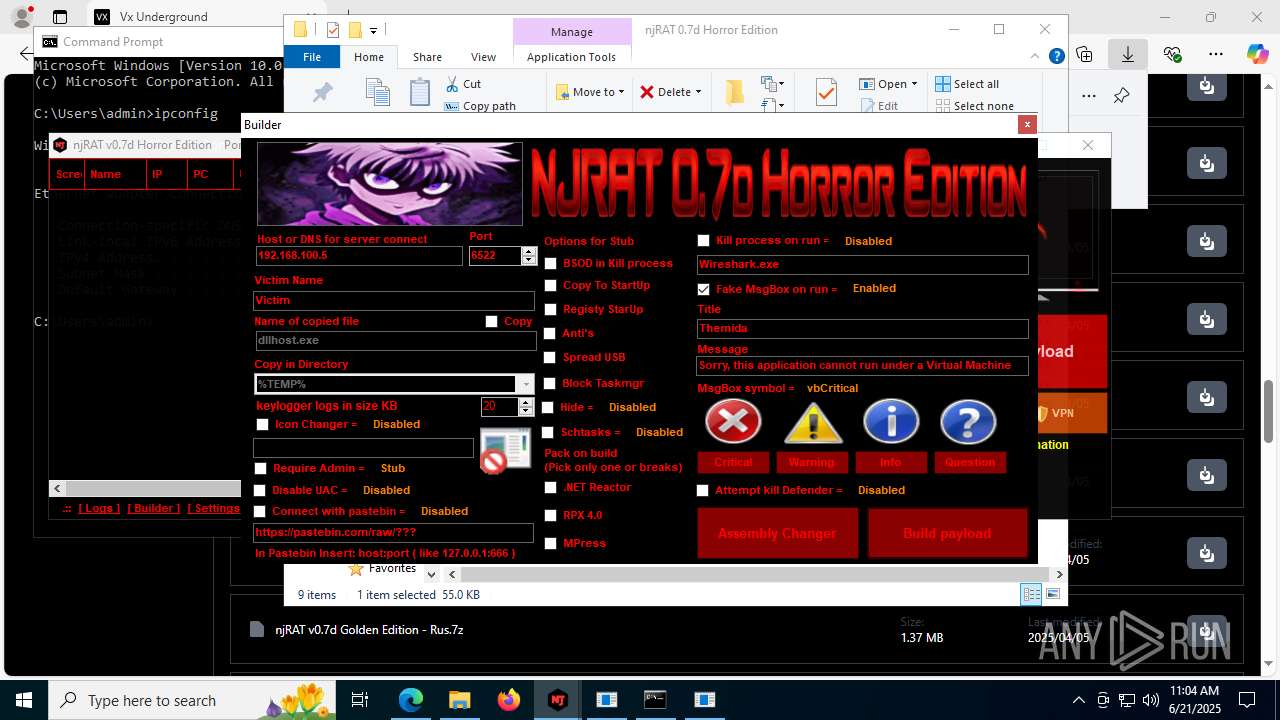
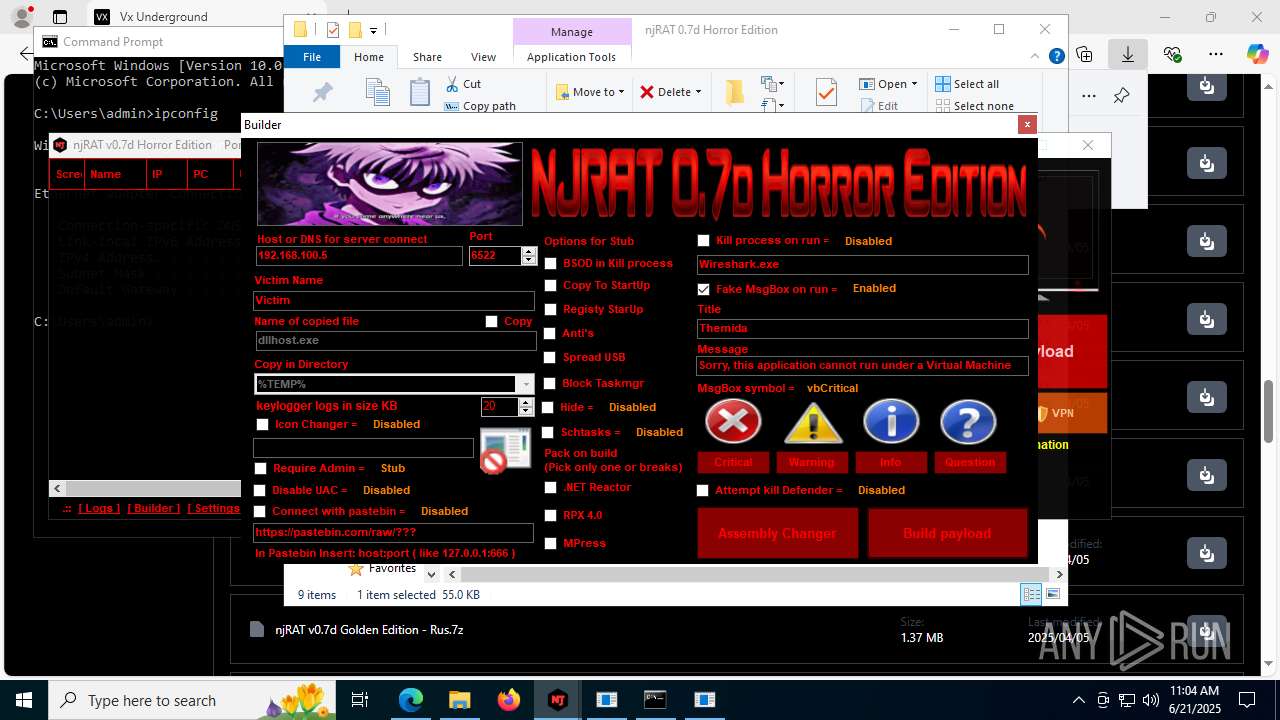
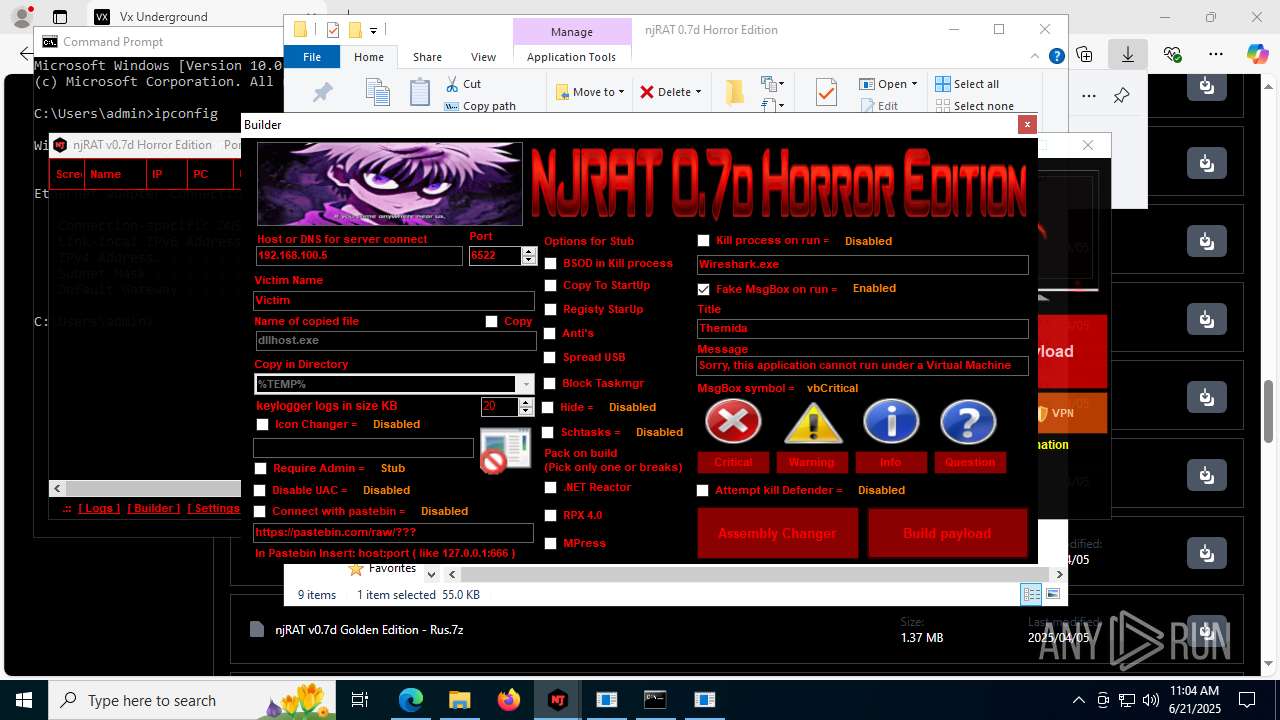
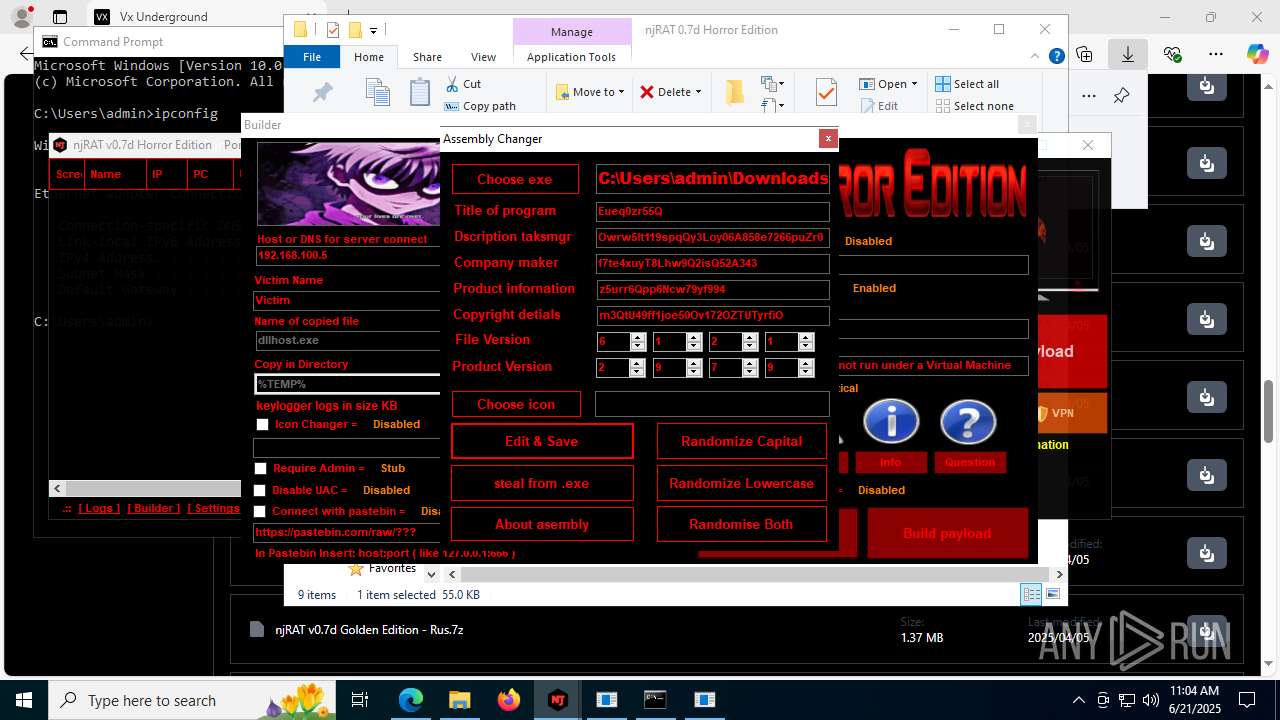
.NET Reactor protector has been detected
- NjRat 0.7D Horror Edition.exe (PID: 8120)
Compiled with Borland Delphi (YARA)
- NjRat 0.7D Horror Edition.exe (PID: 8120)
Mpress packer has been detected
- NjRat 0.7D Horror Edition.exe (PID: 8120)
Process checks computer location settings
- NjRat 0.7D Horror Edition.exe (PID: 8120)
Create files in a temporary directory
- NjRat 0.7D Horror Edition.exe (PID: 8120)
- vbc.exe (PID: 5600)
- cvtres.exe (PID: 8168)
Checks proxy server information
- slui.exe (PID: 7904)
- NjRat 0.7D Horror Edition.exe (PID: 8120)
Reads the software policy settings
- slui.exe (PID: 7904)
Disables trace logs
- NjRat 0.7D Horror Edition.exe (PID: 8120)
The sample compiled with english language support
- NjRat 0.7D Horror Edition.exe (PID: 8120)
RESOURCEHACKER mutex has been found
- res.exe (PID: 5628)
- res.exe (PID: 3860)
- res.exe (PID: 8160)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
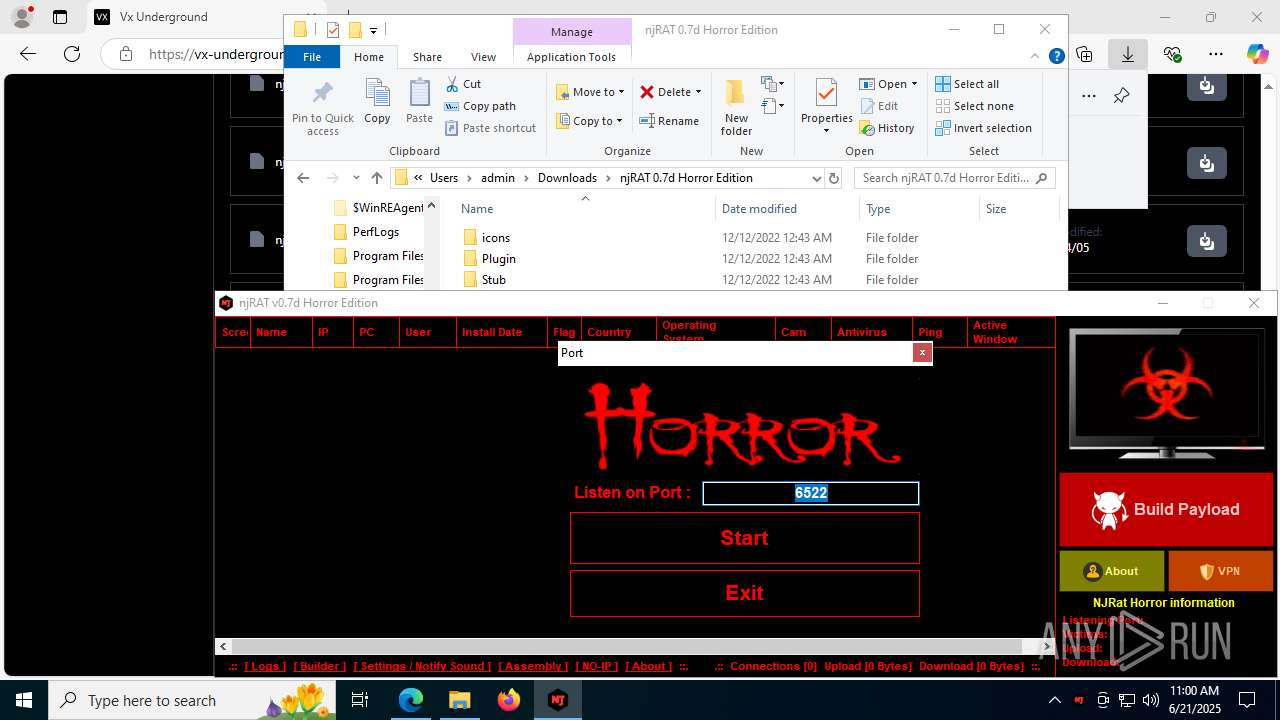
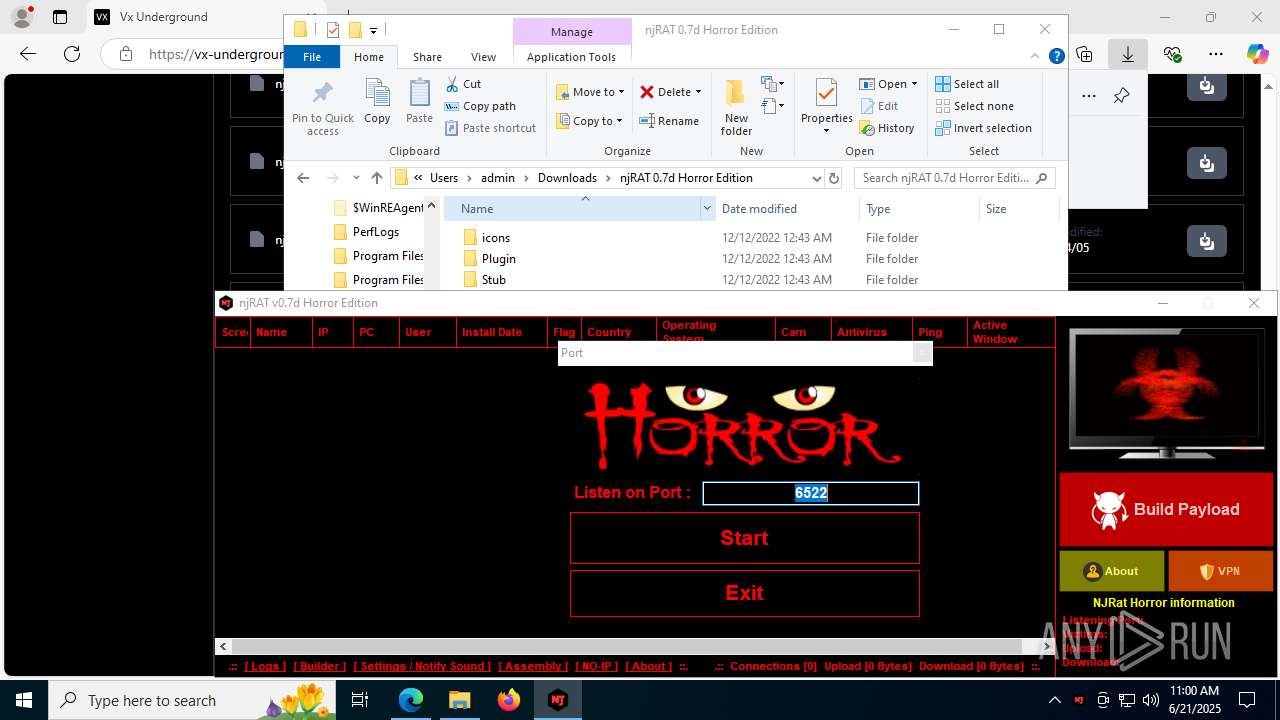
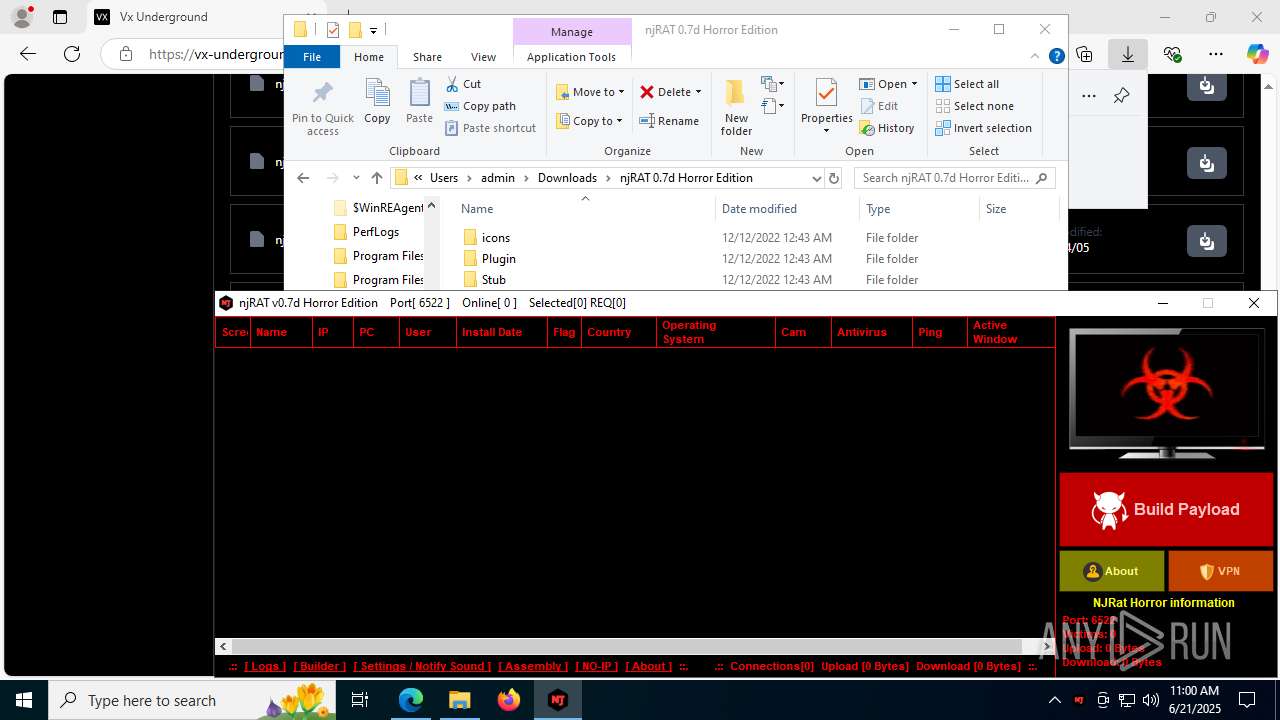
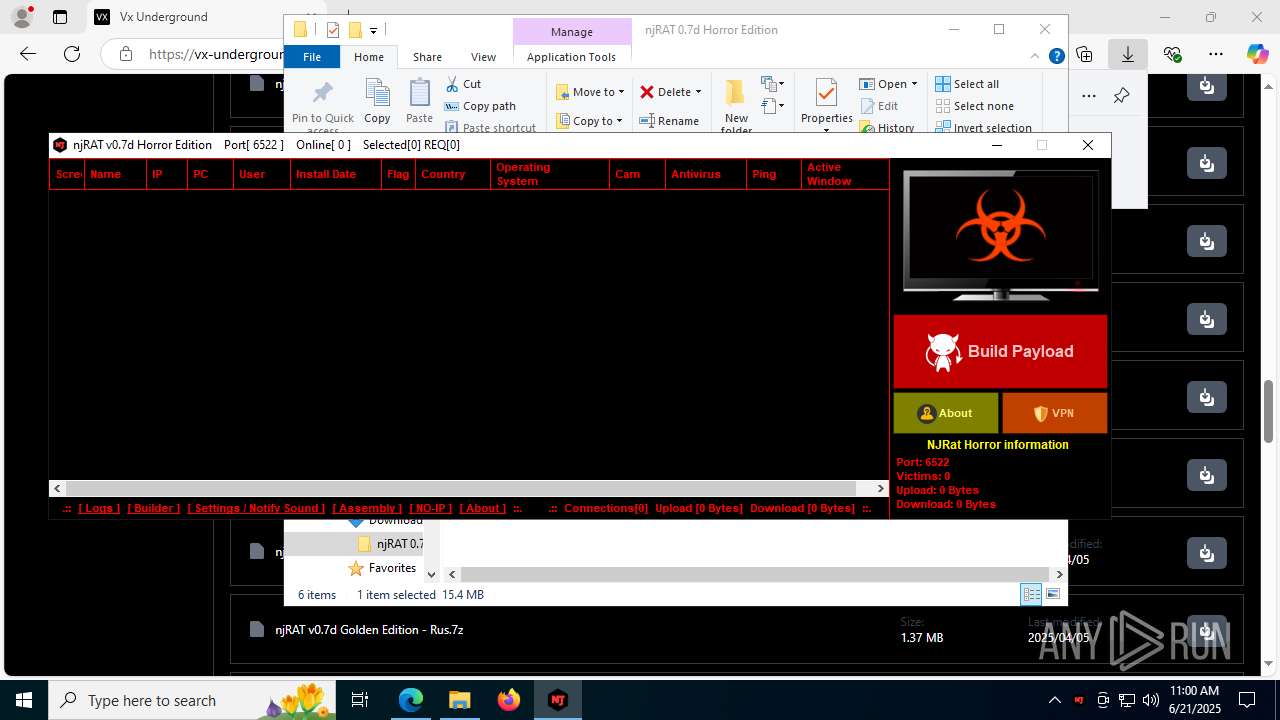
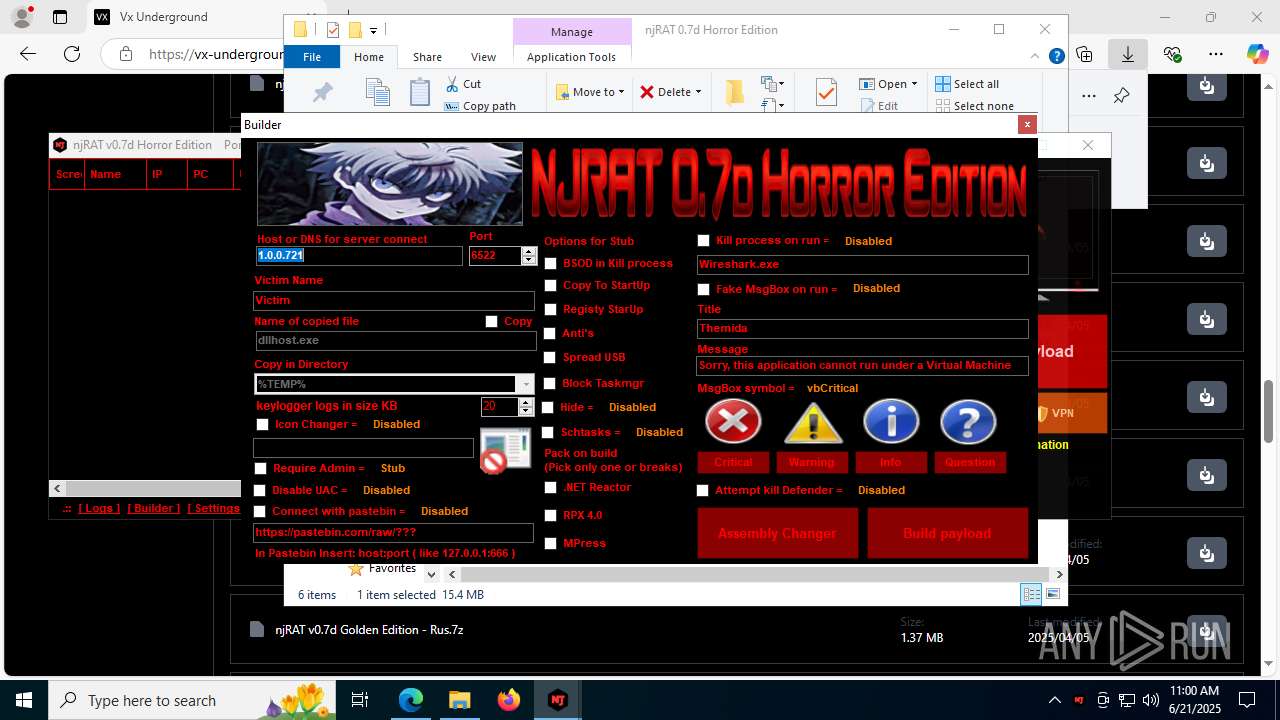
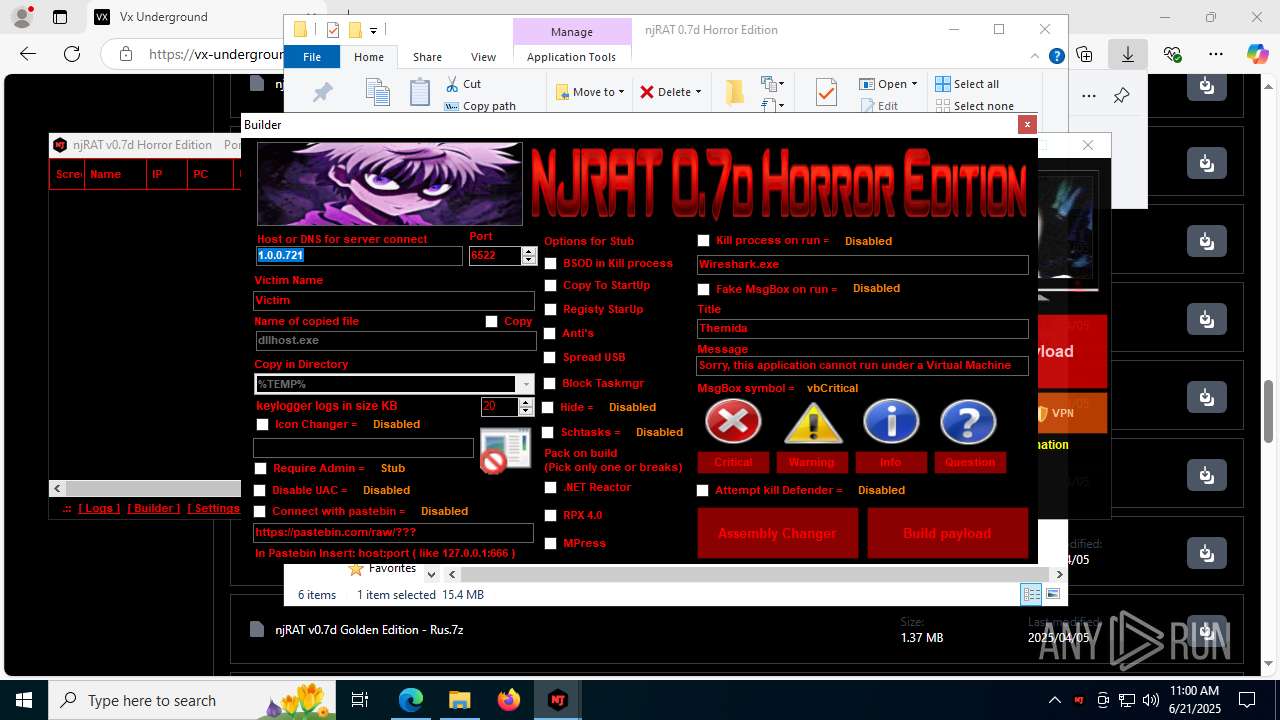
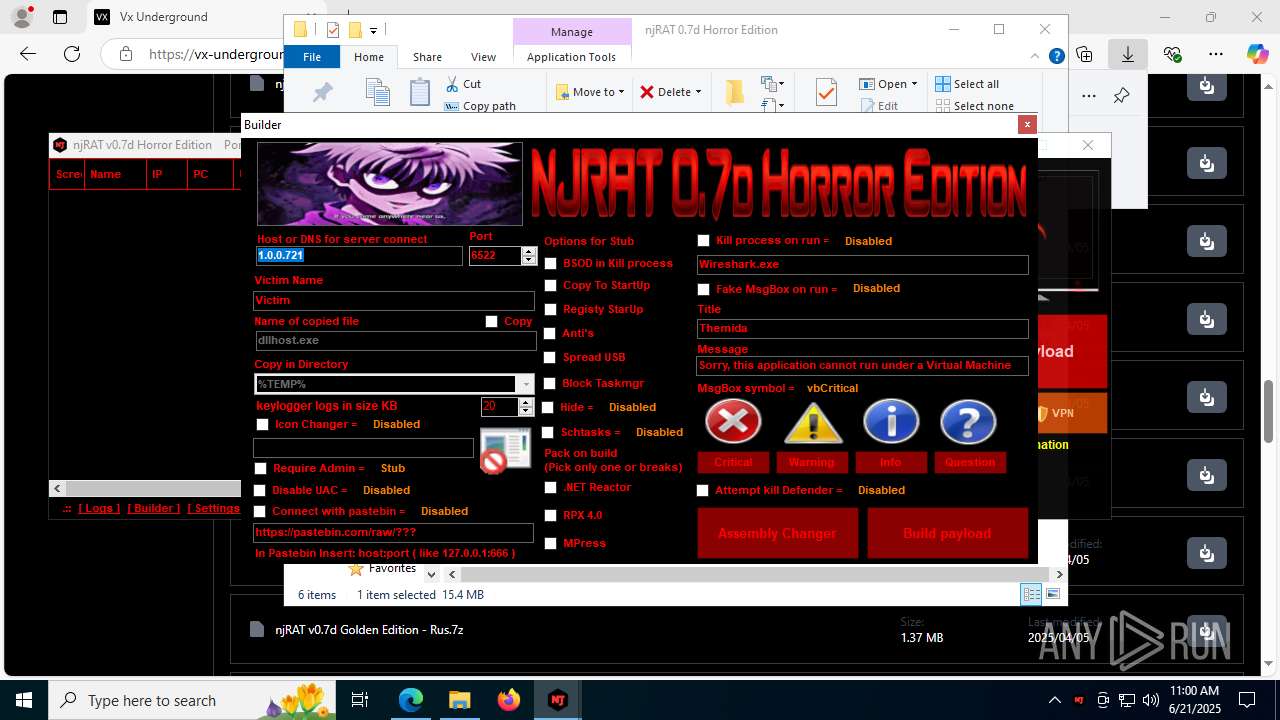
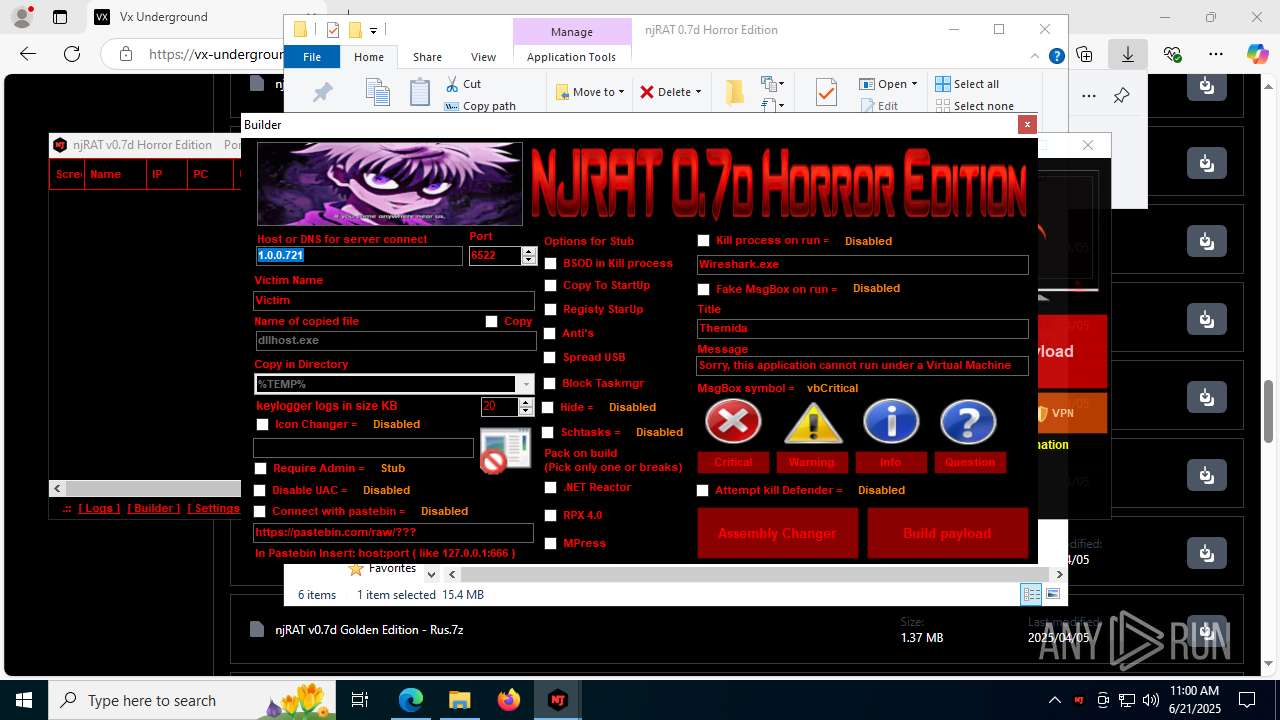
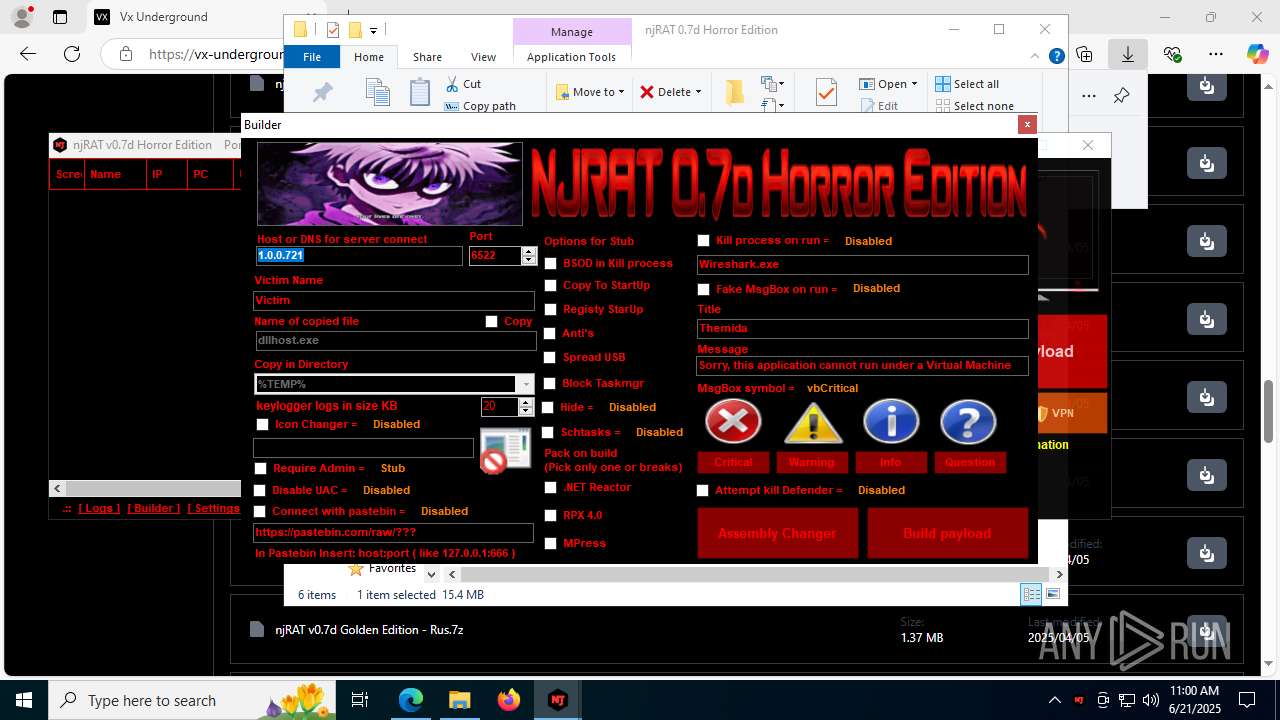
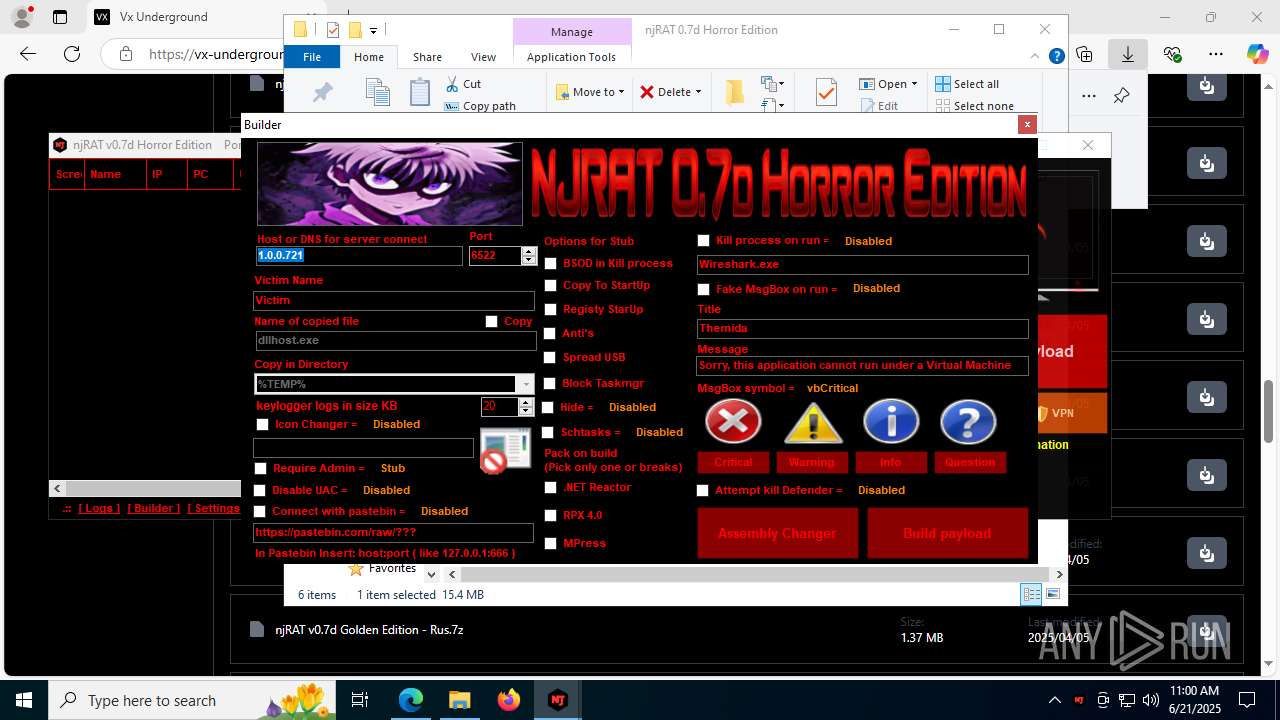
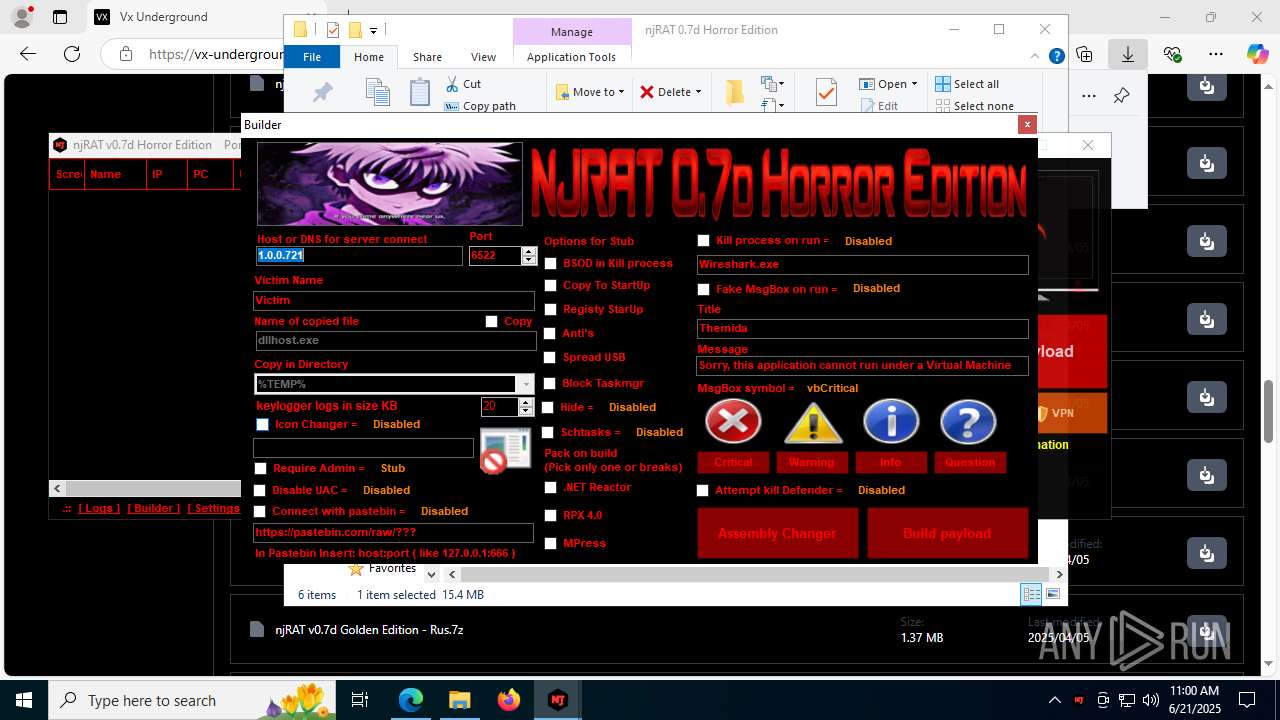
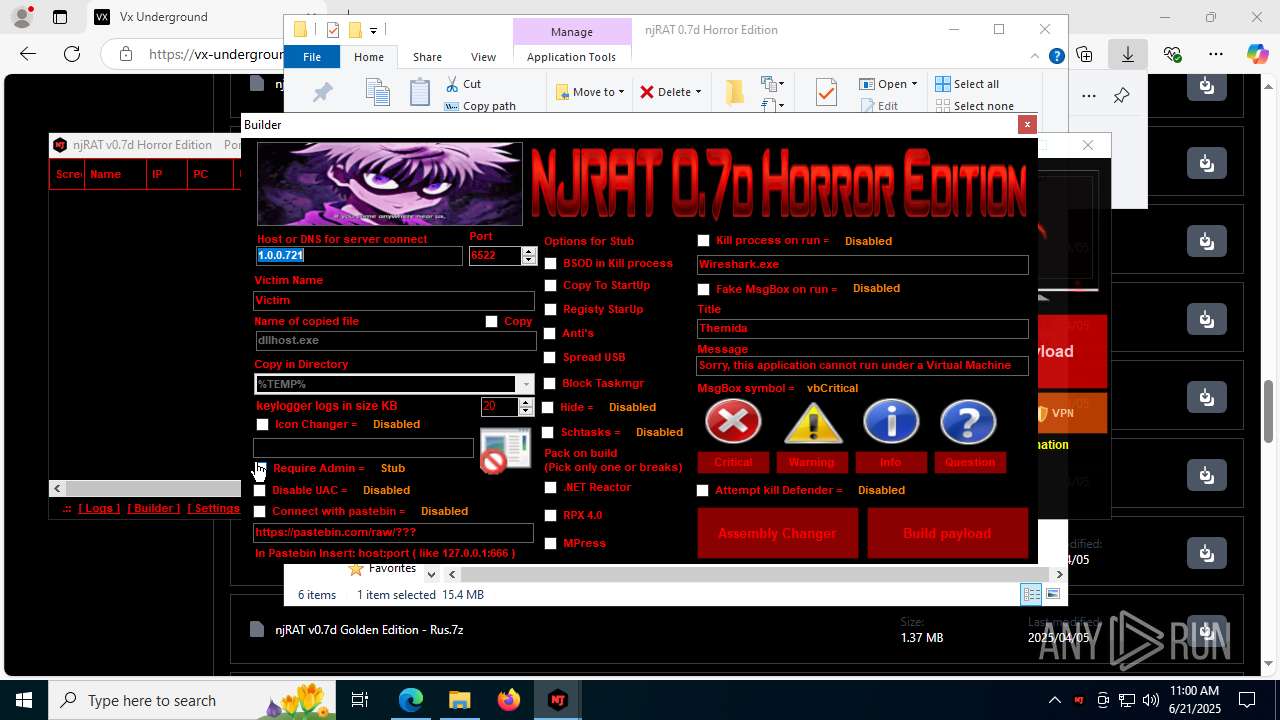
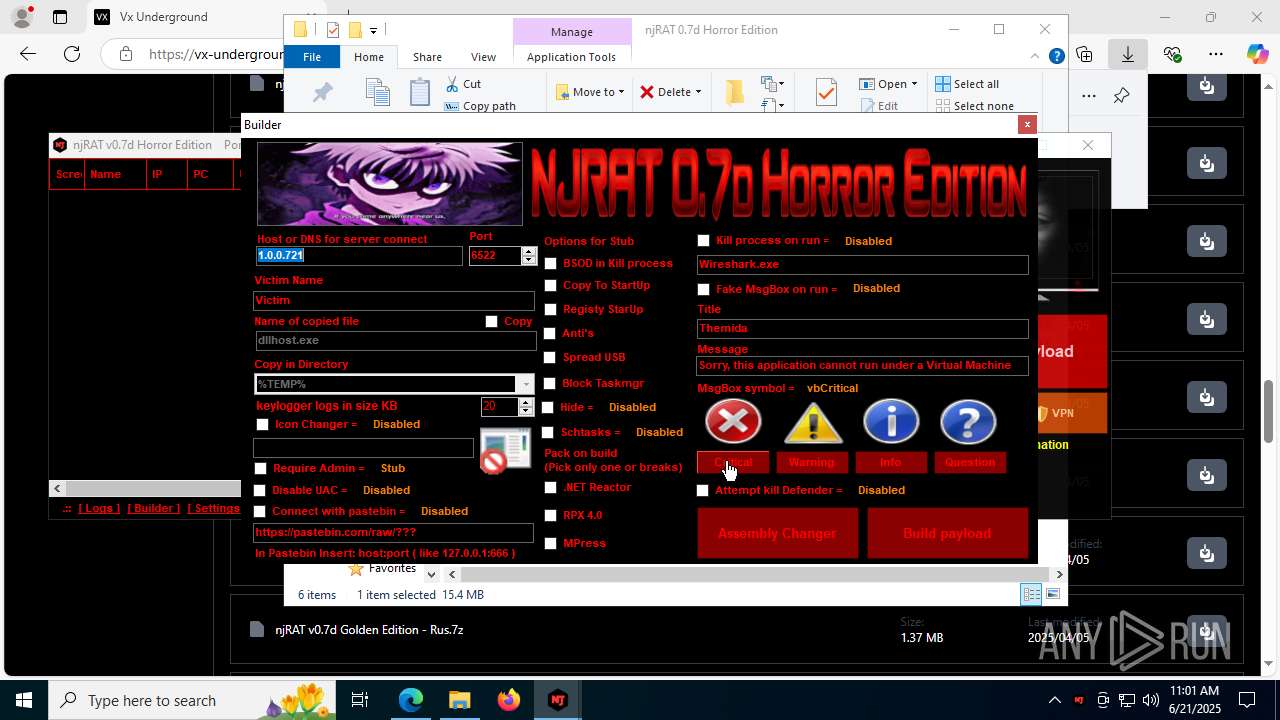
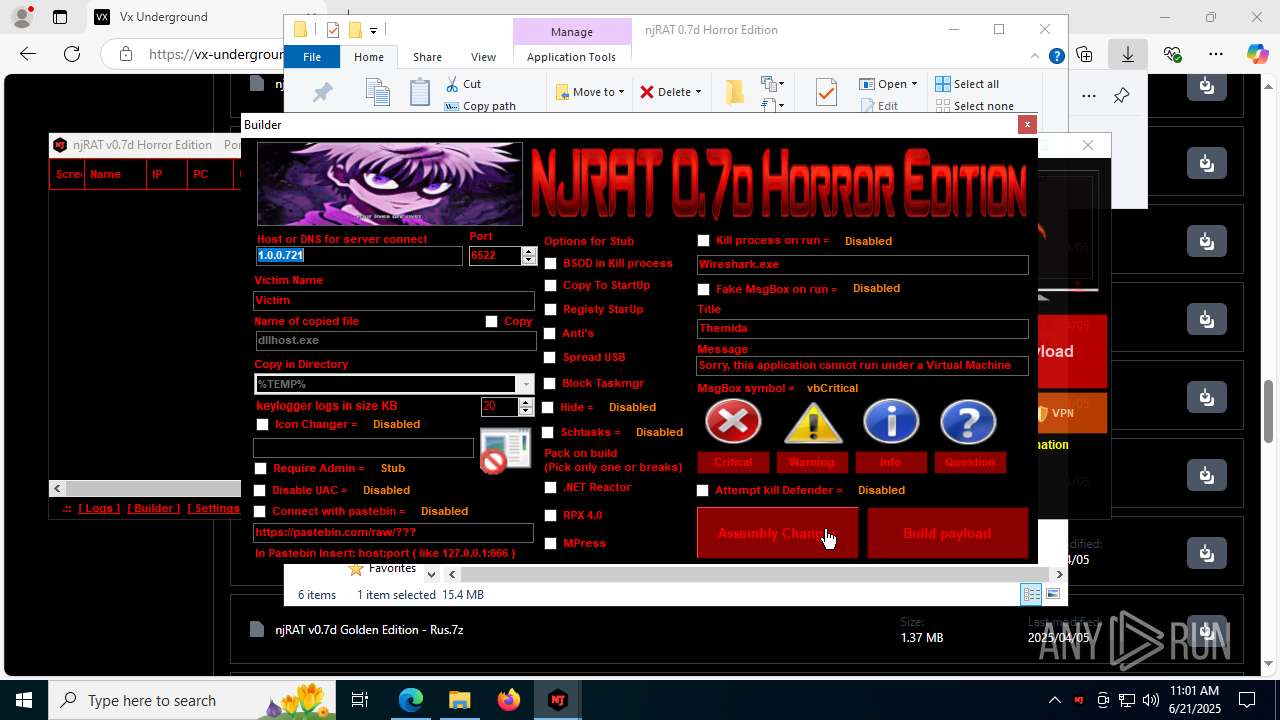
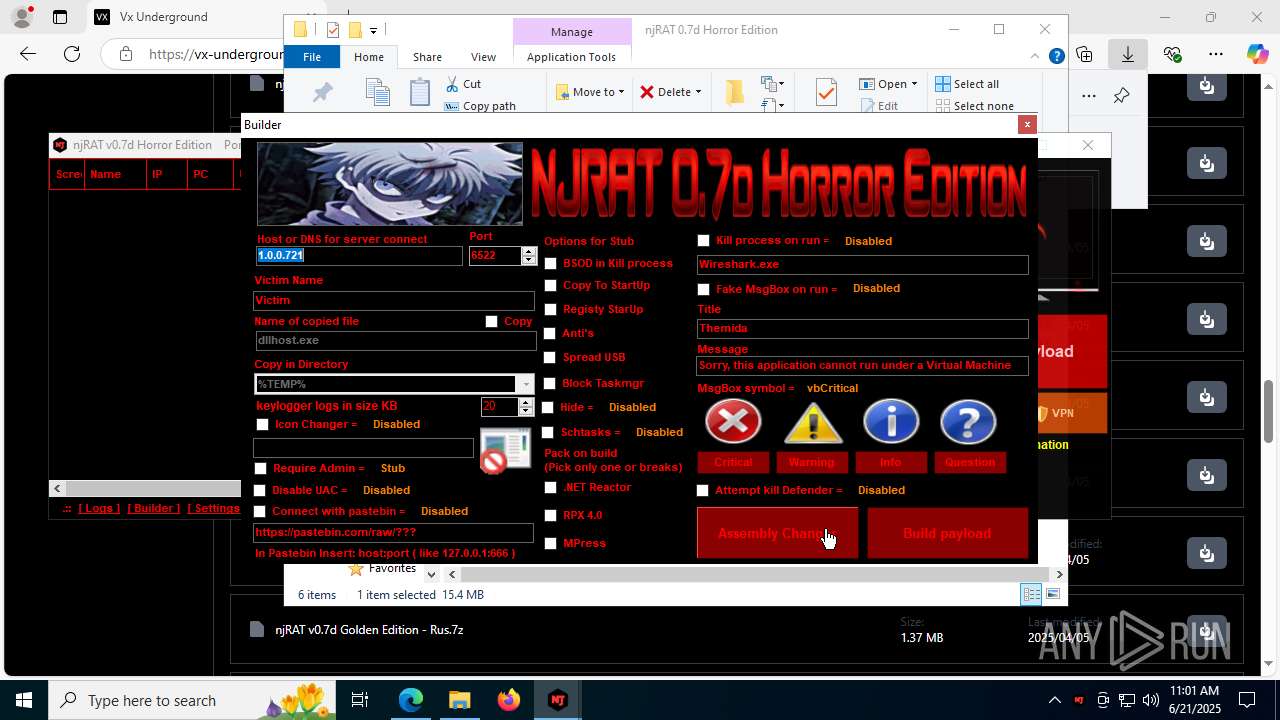
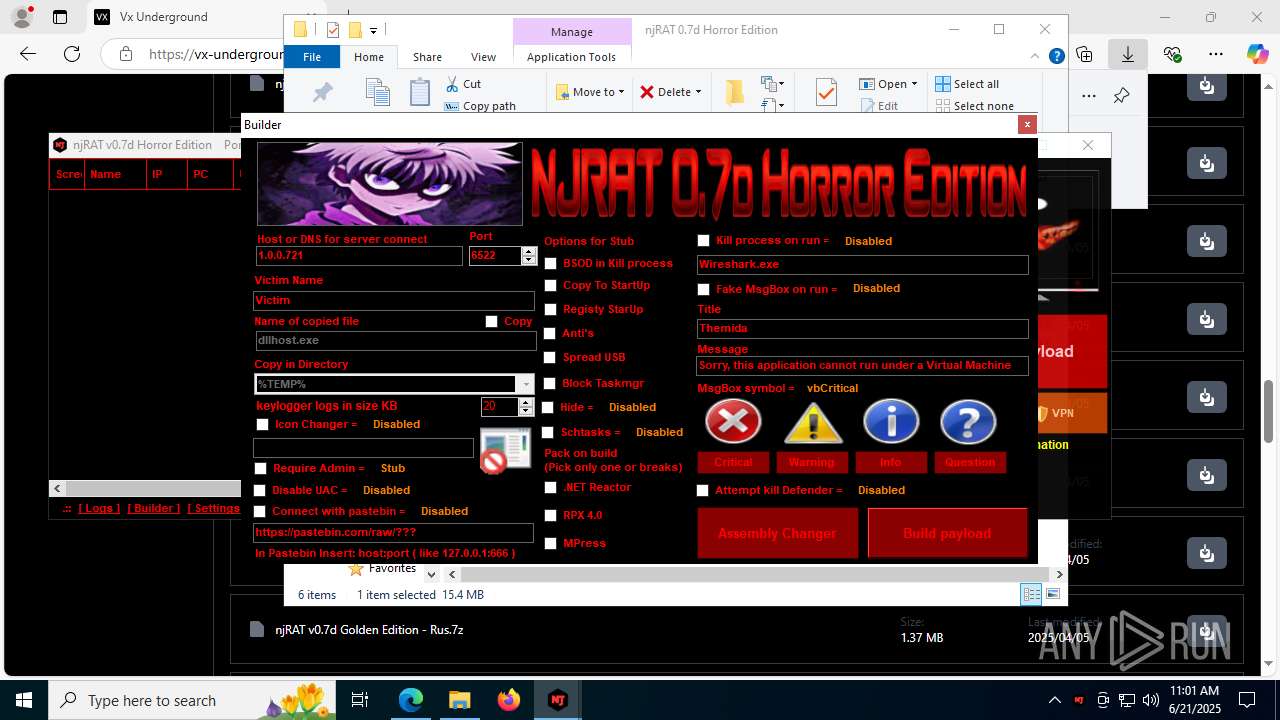
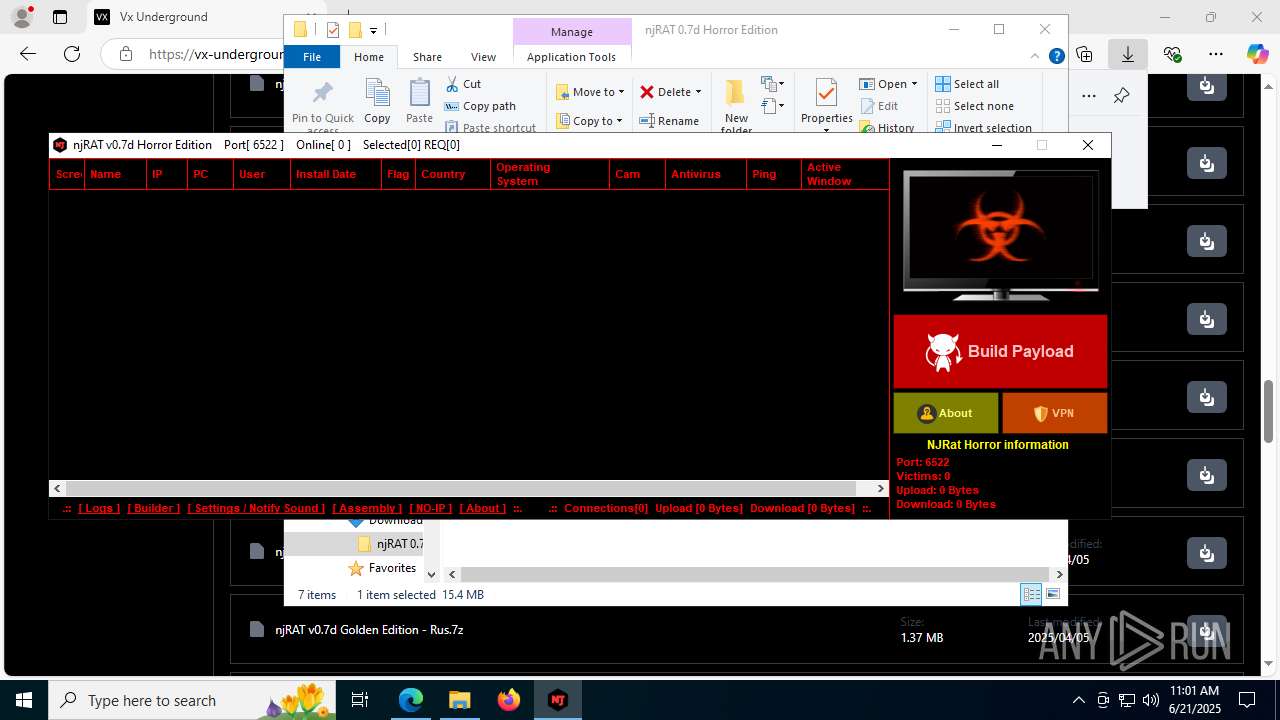
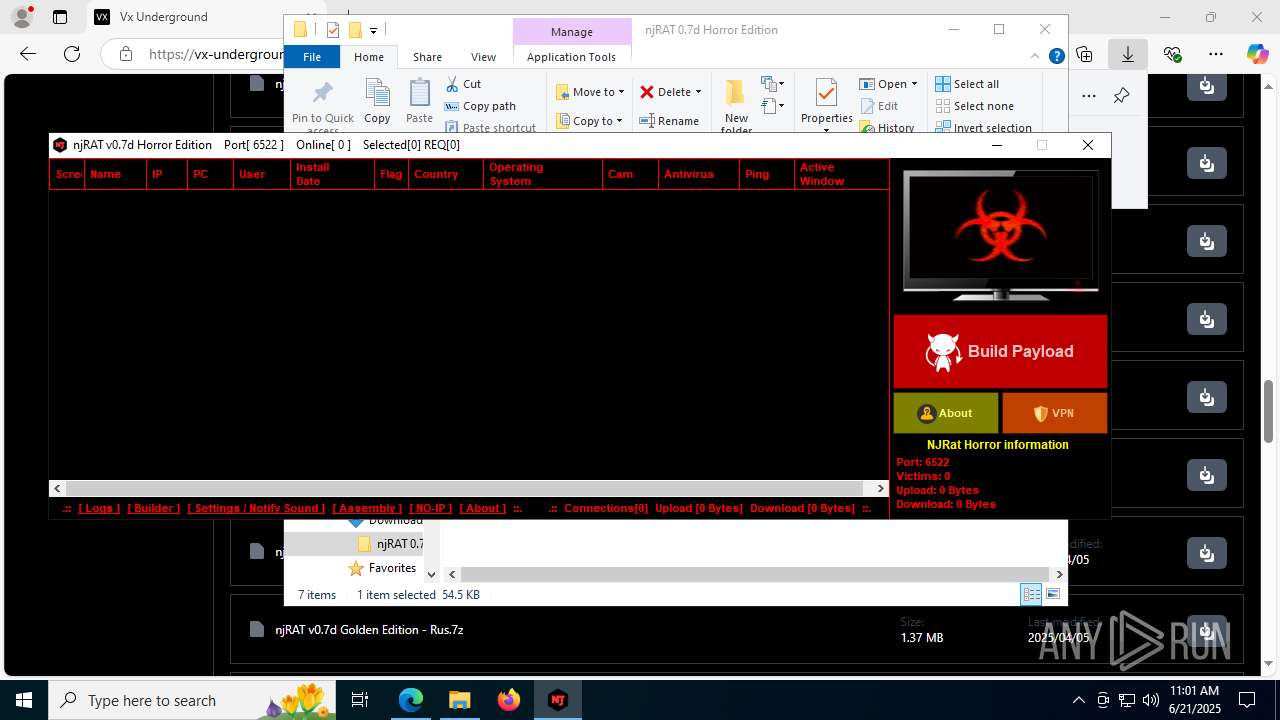
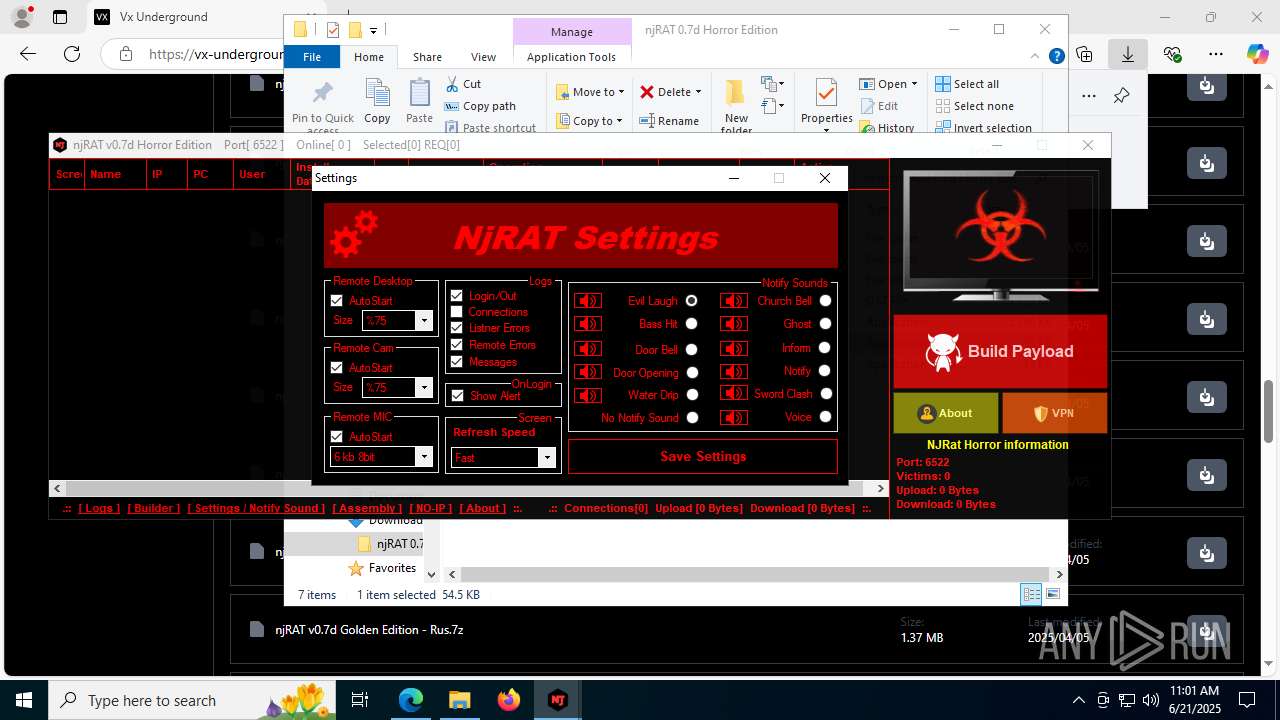
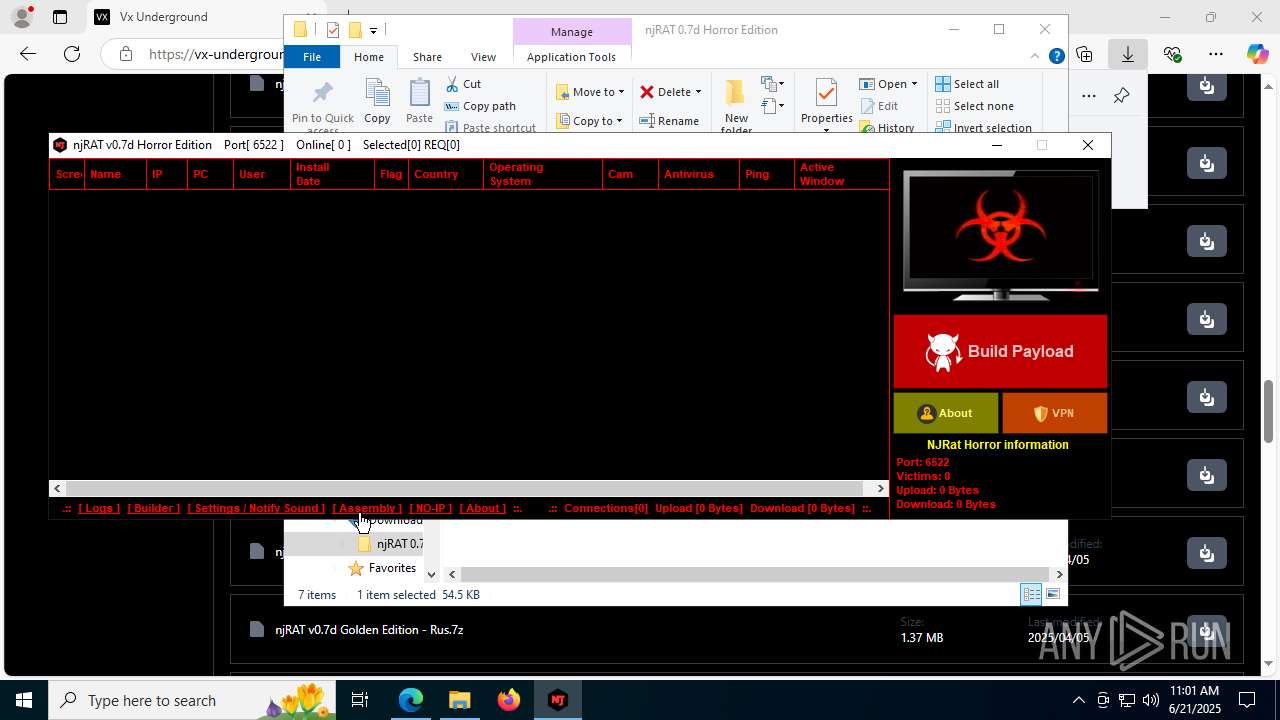
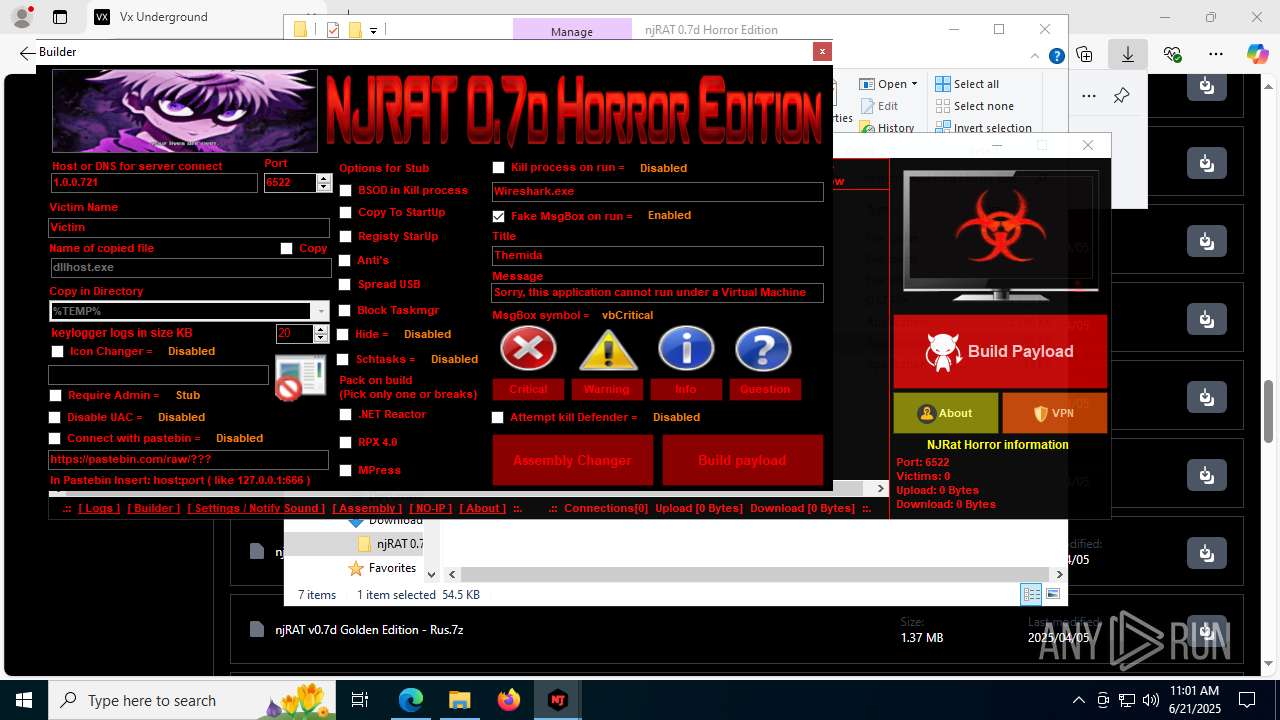
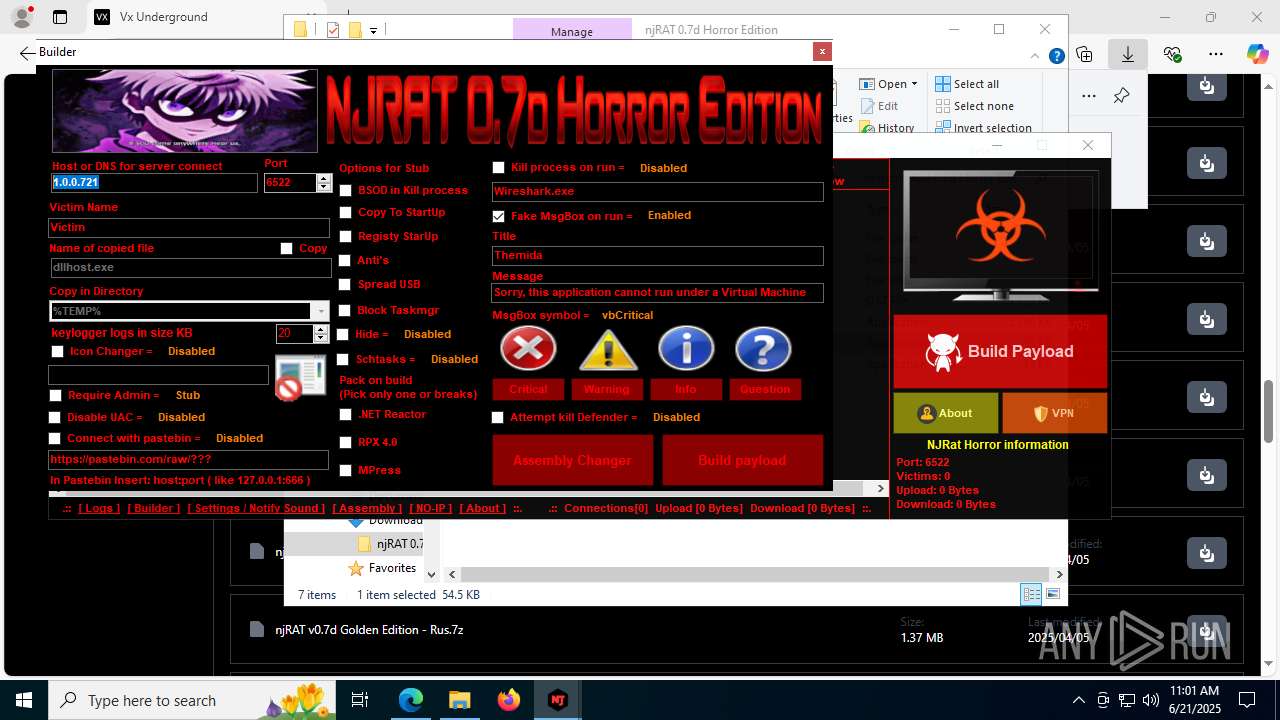
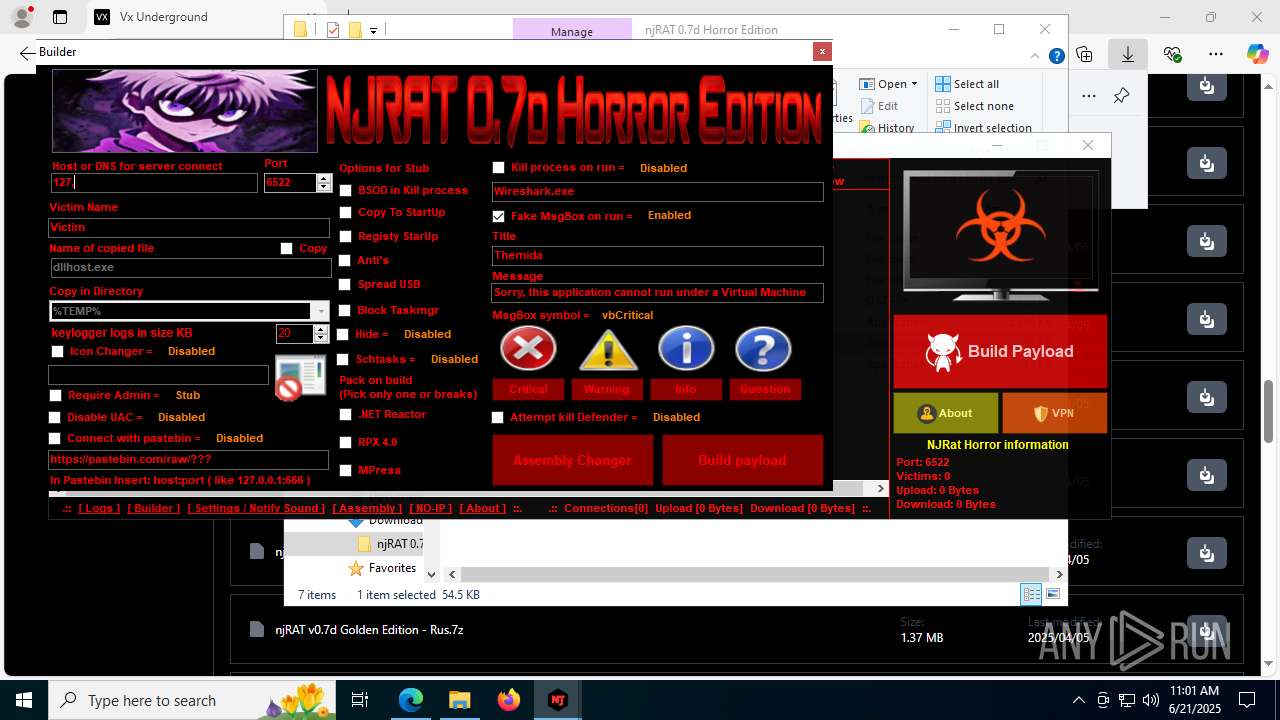
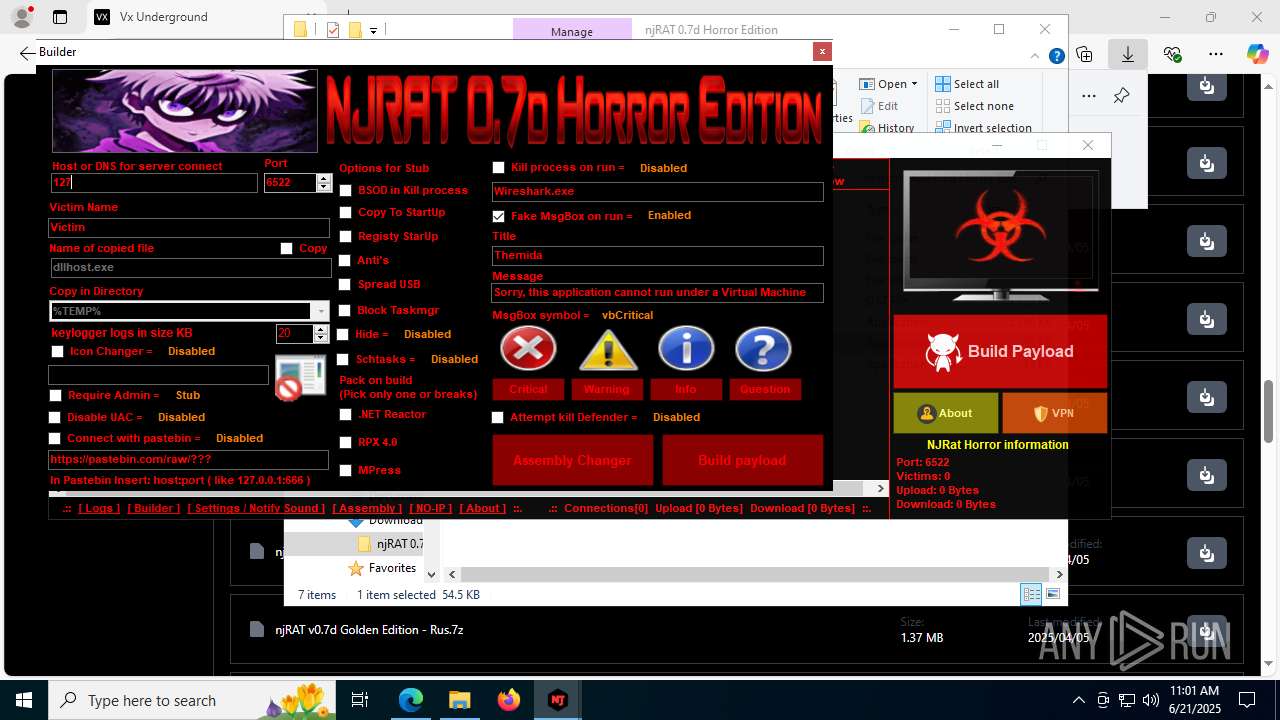
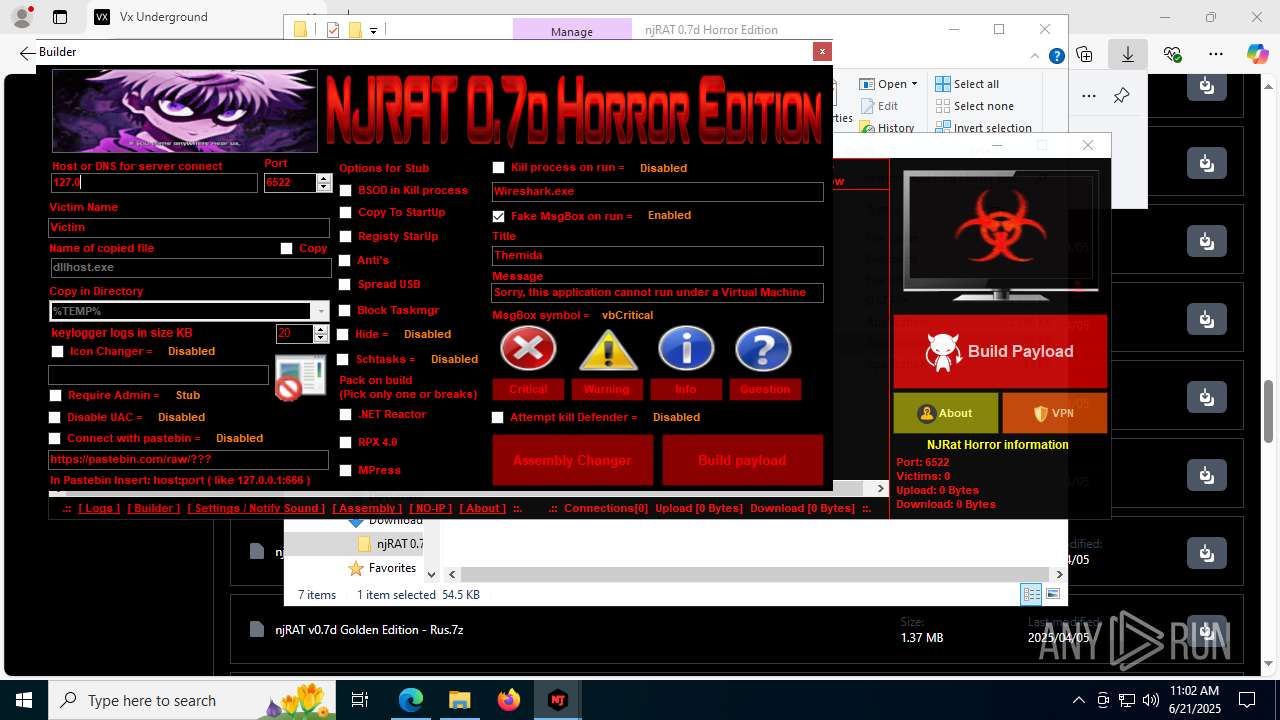
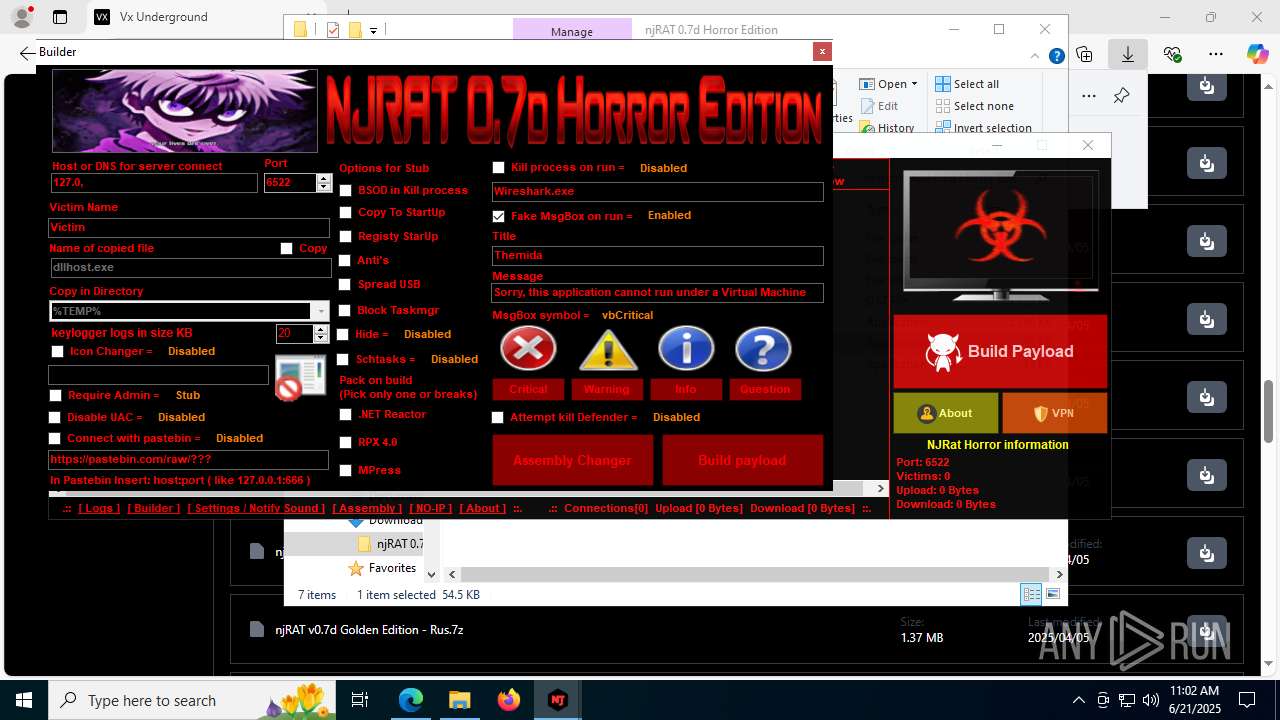
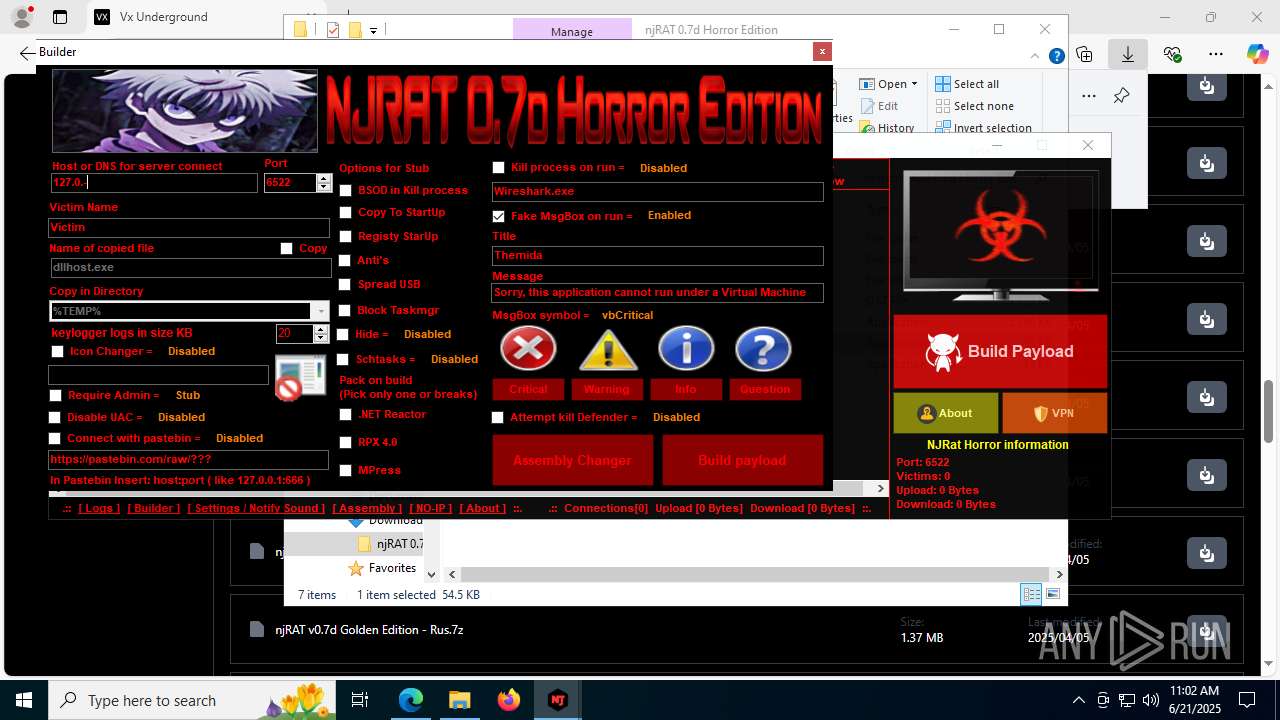
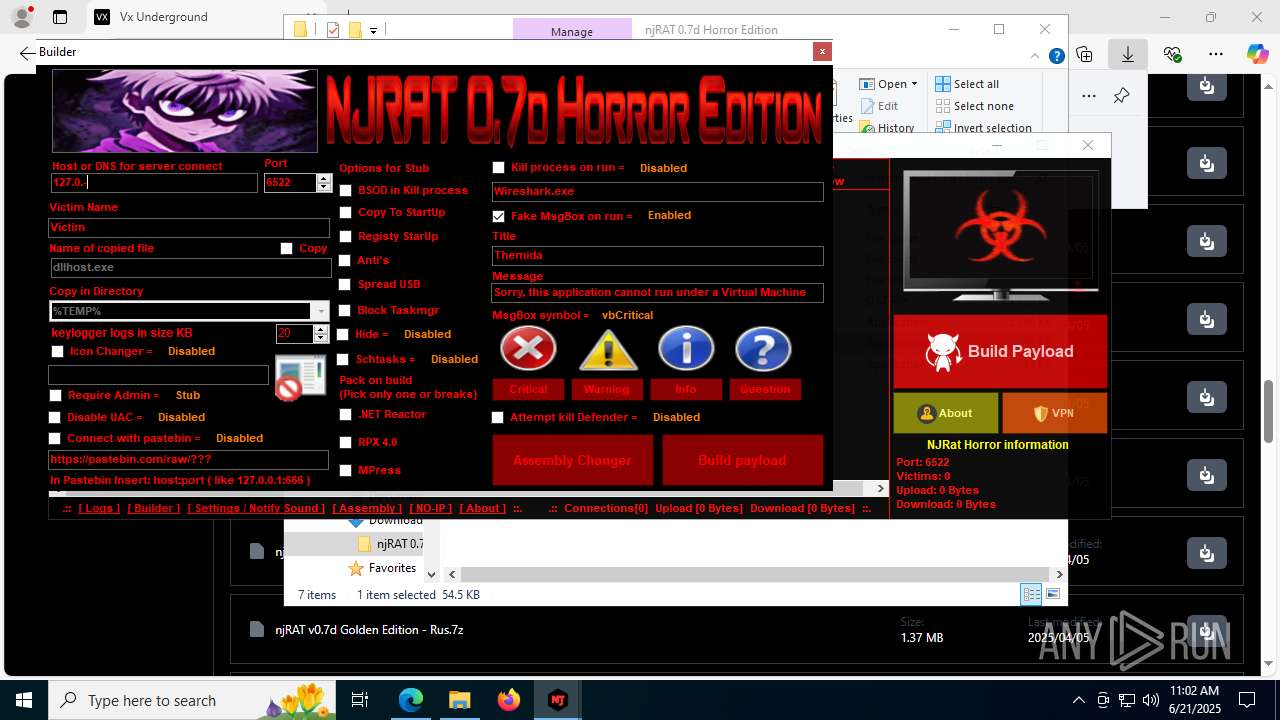
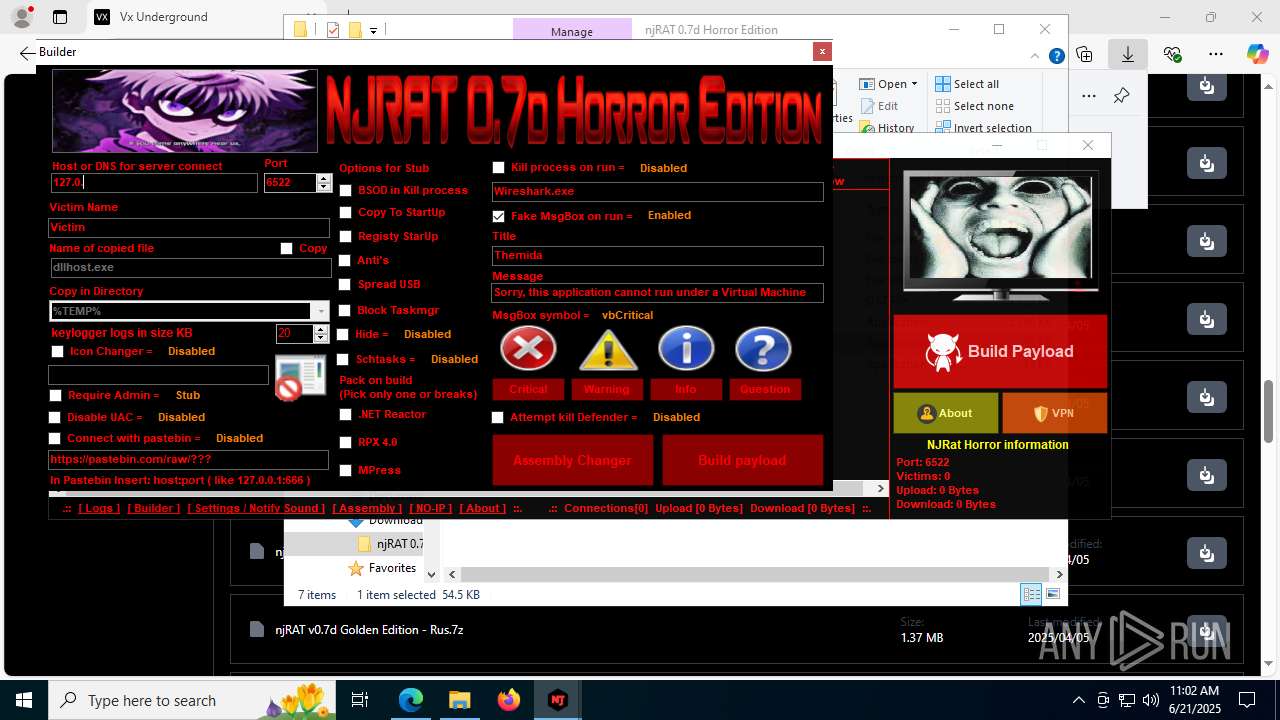
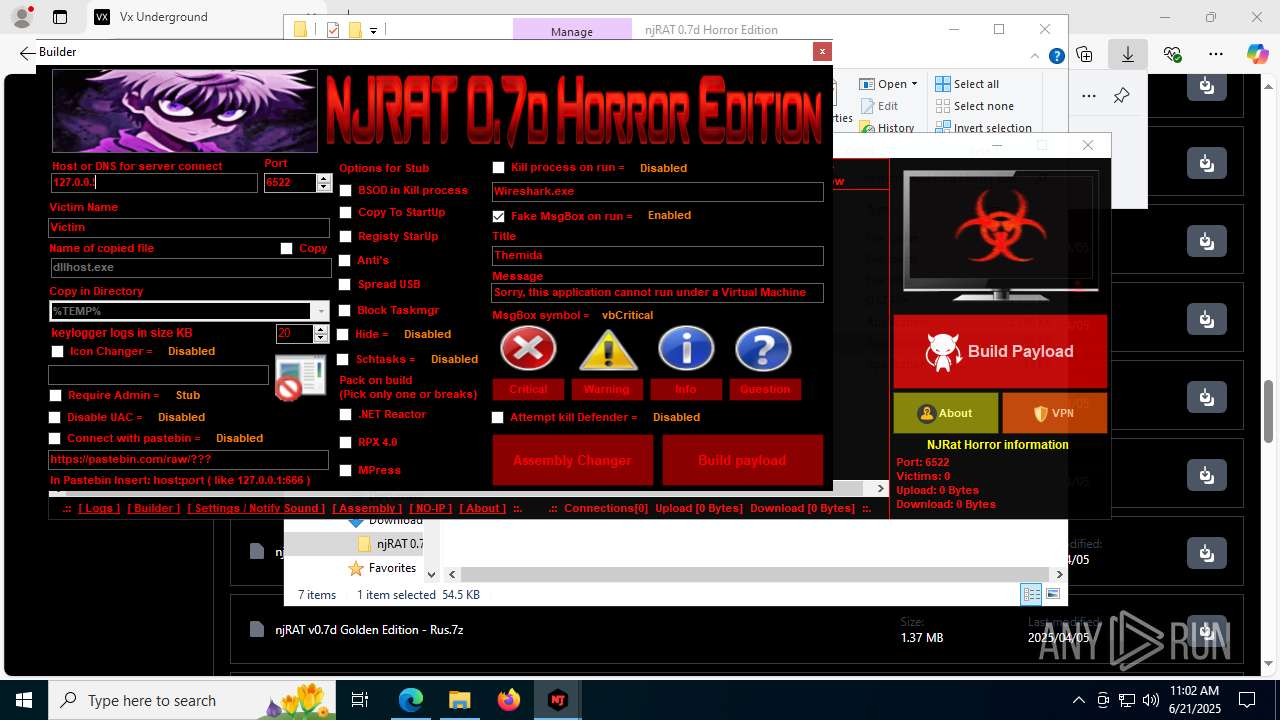
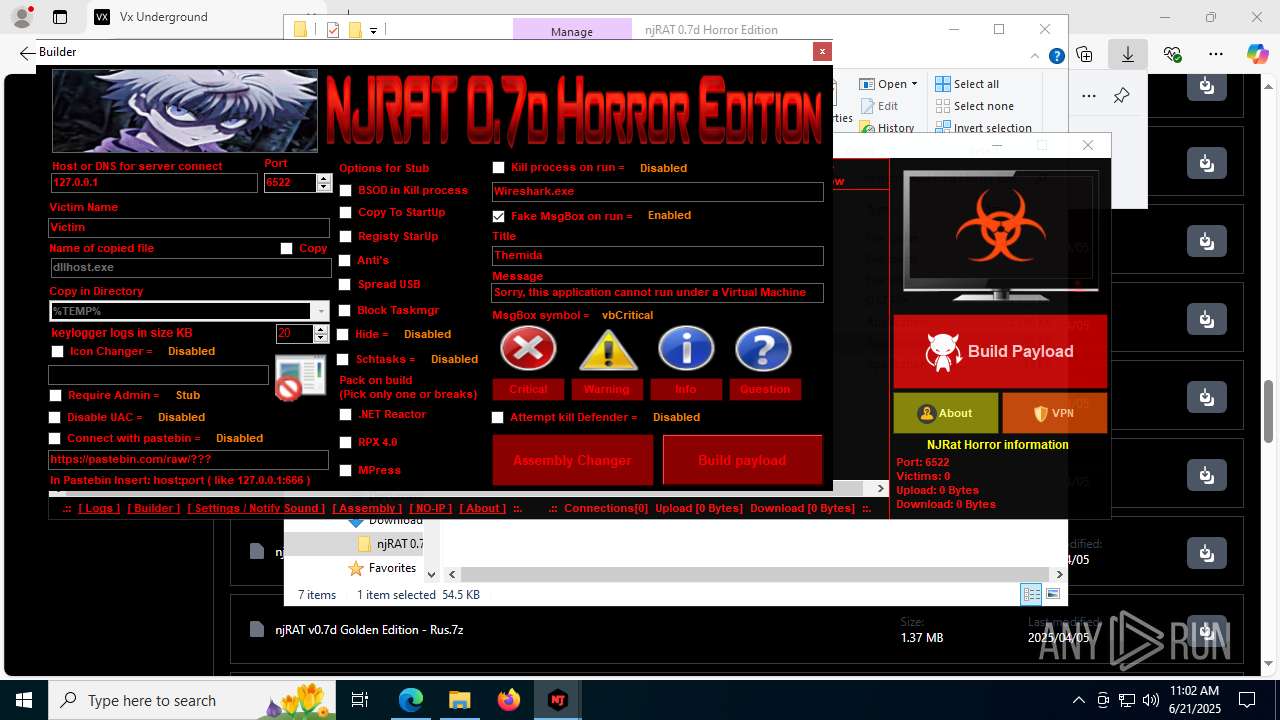
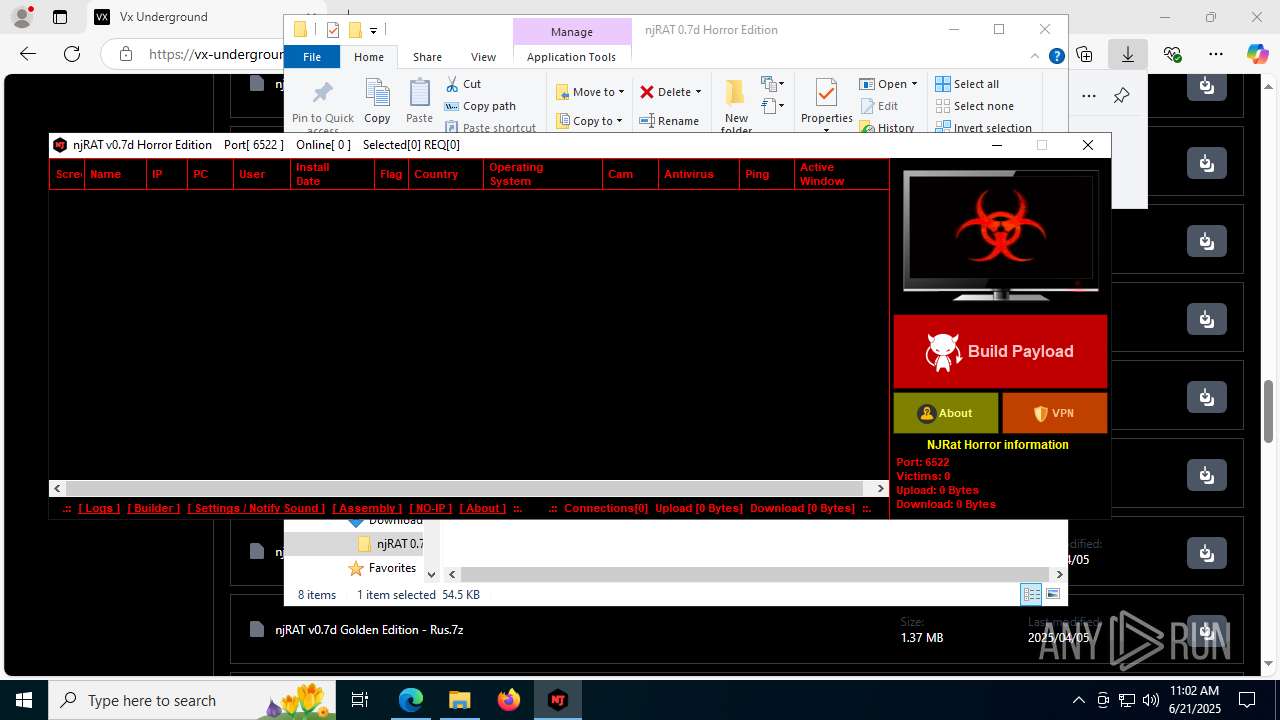
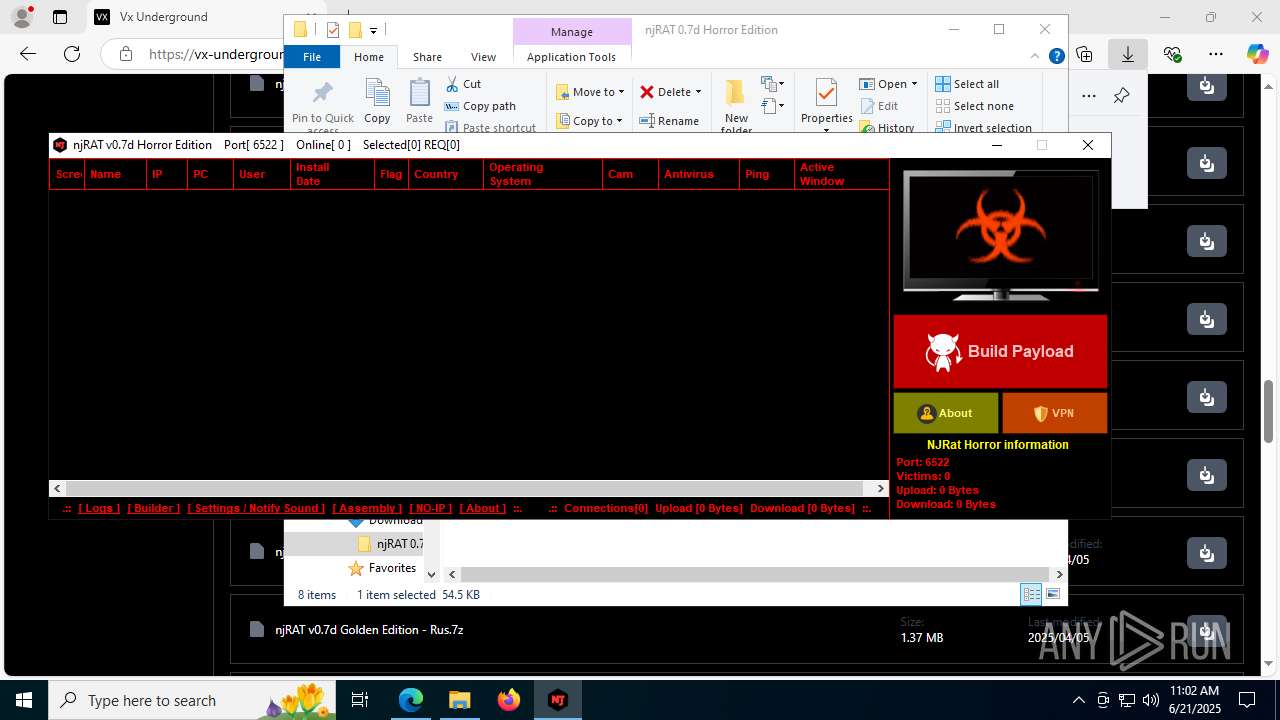
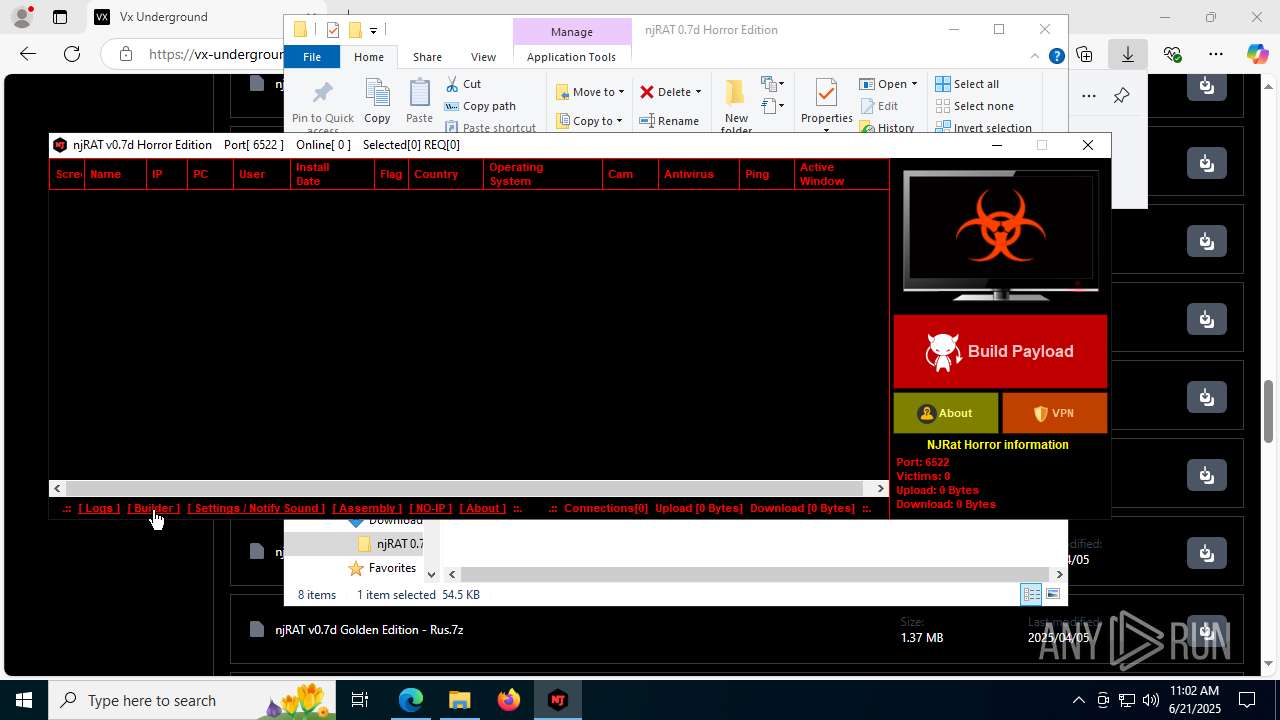
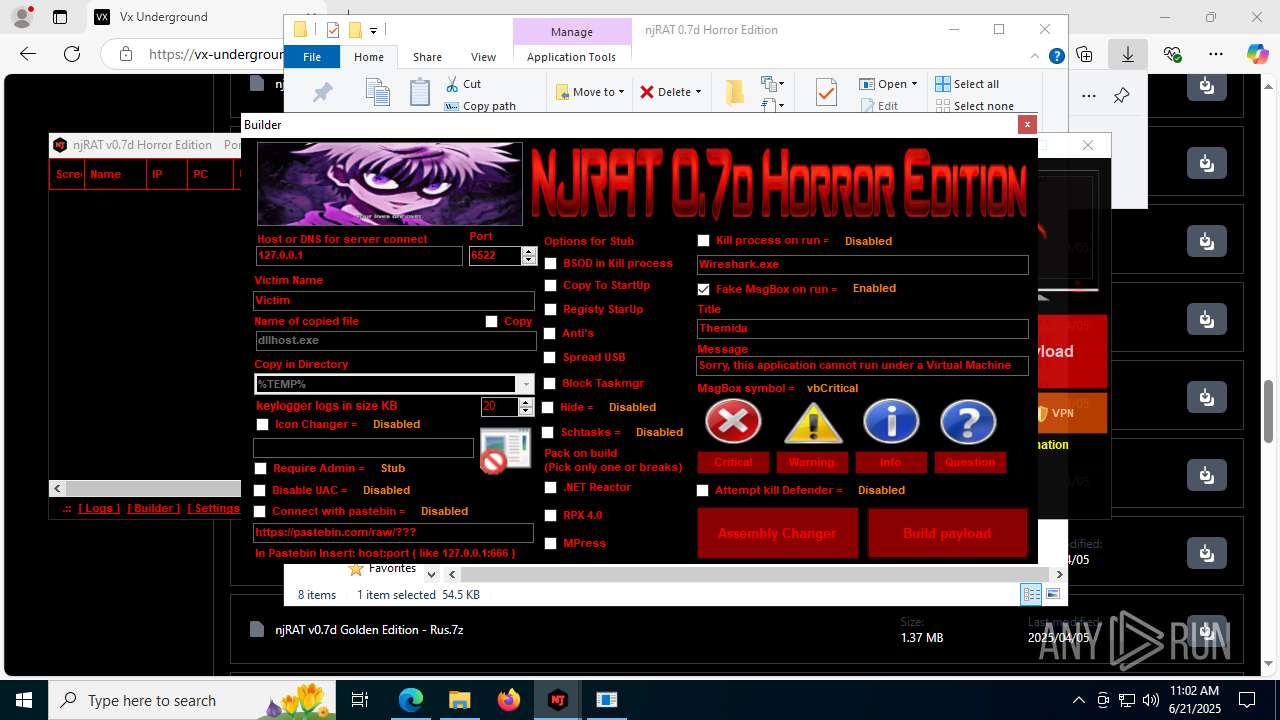
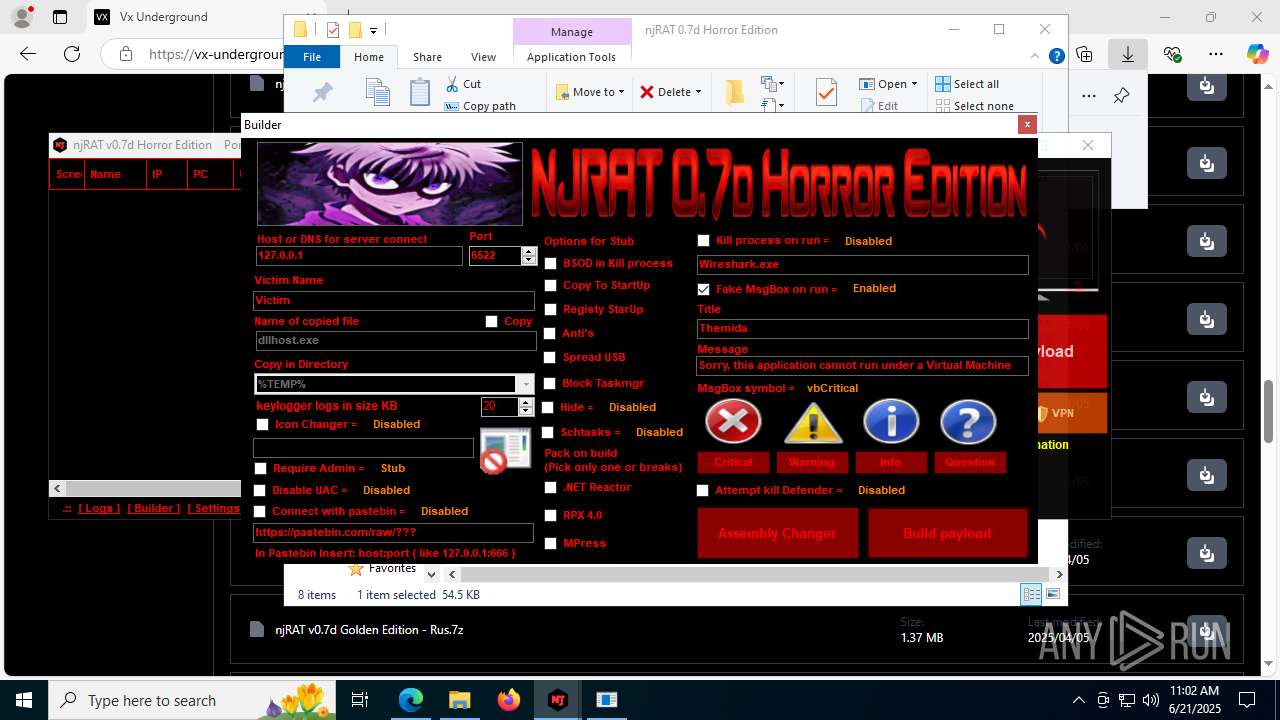
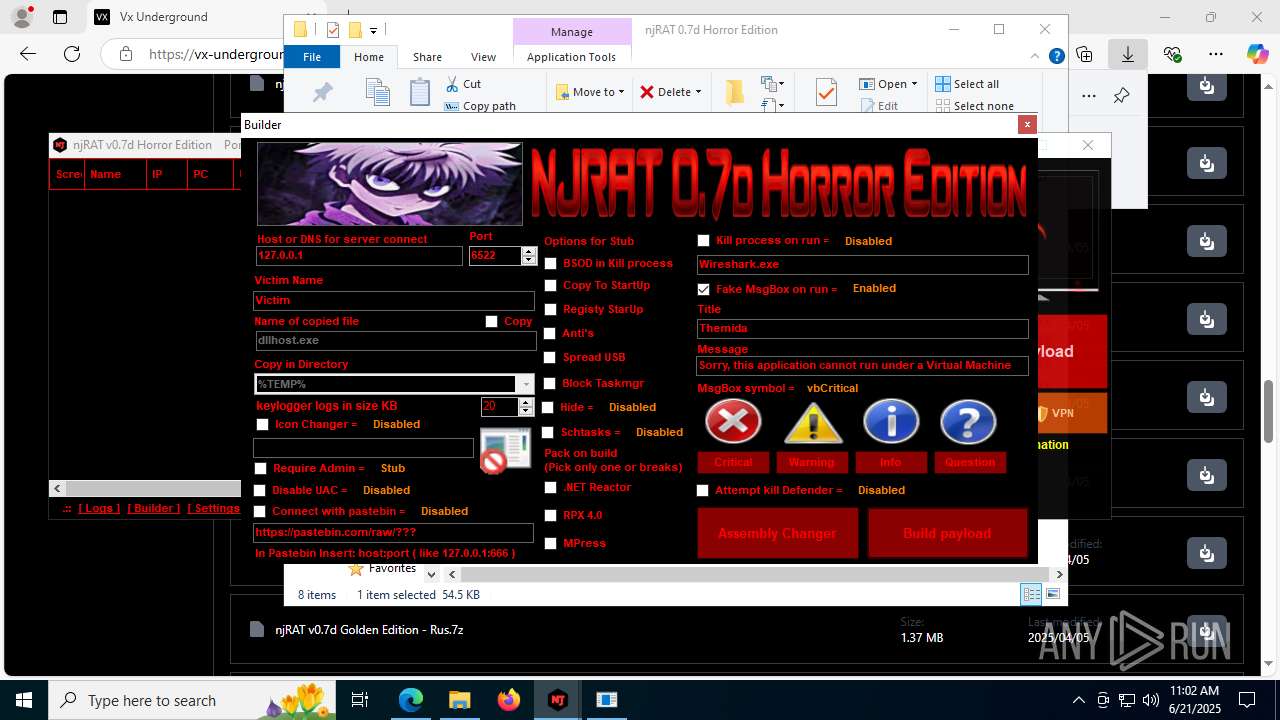
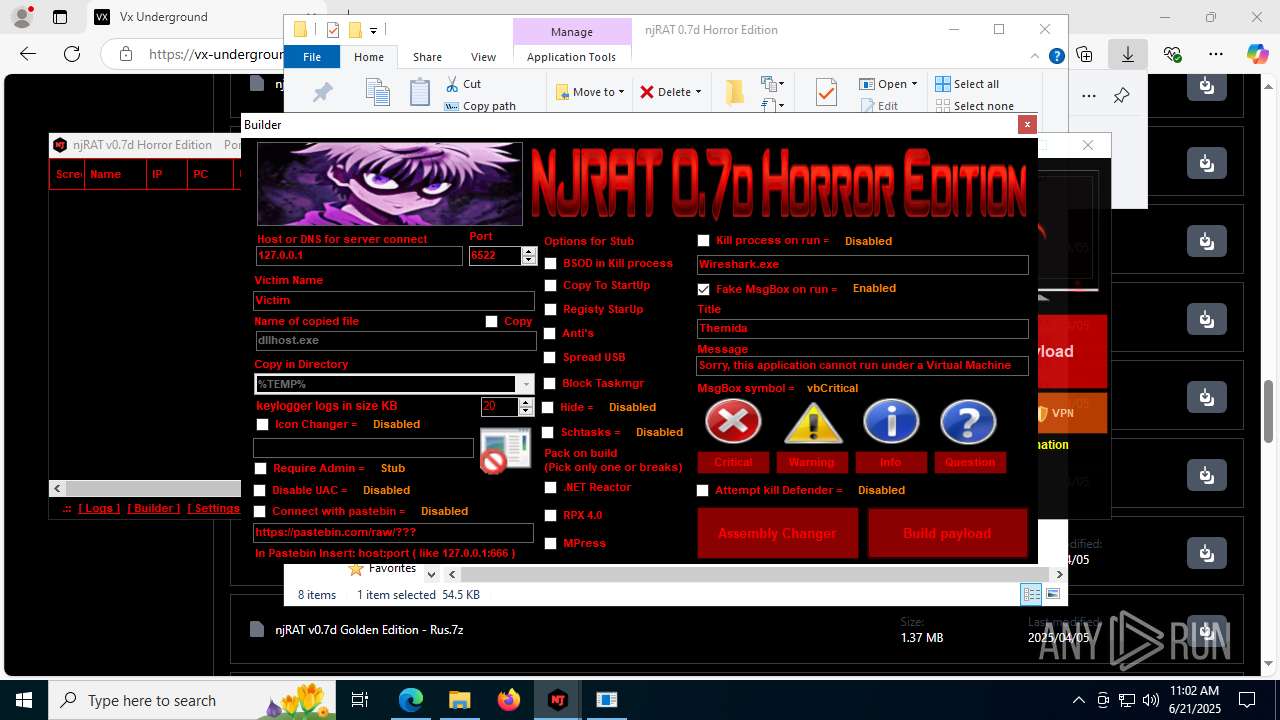
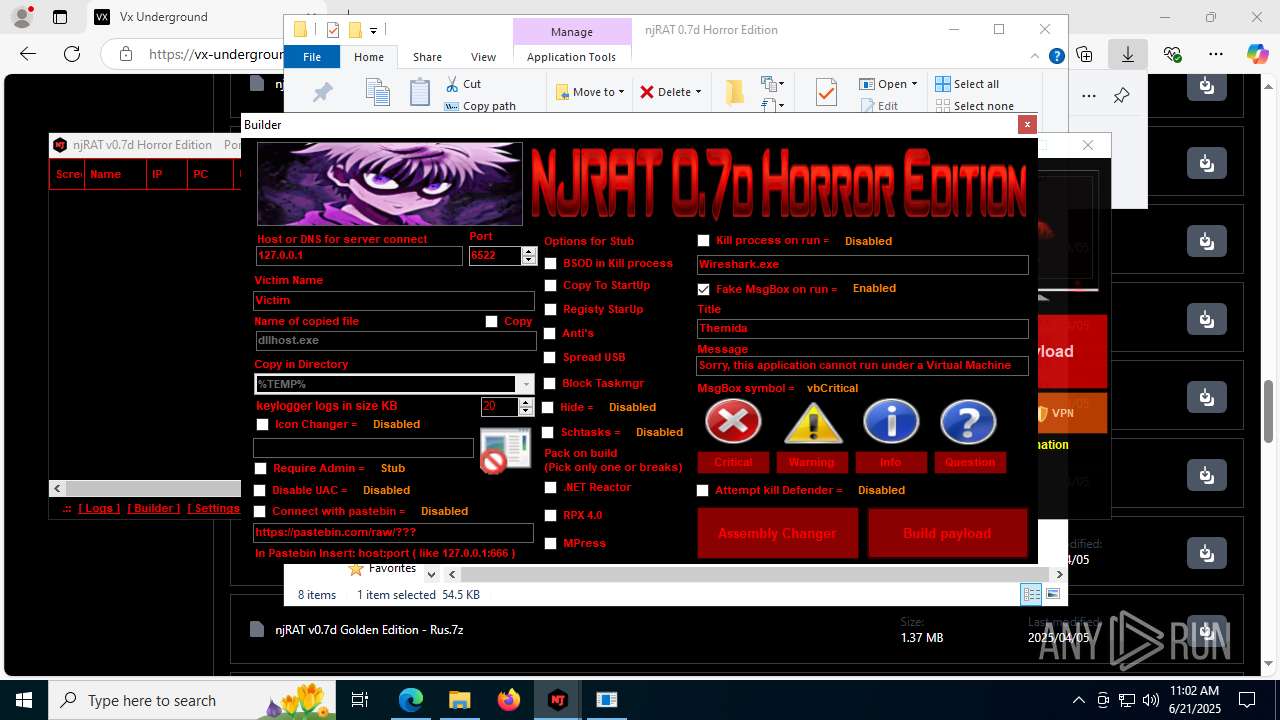
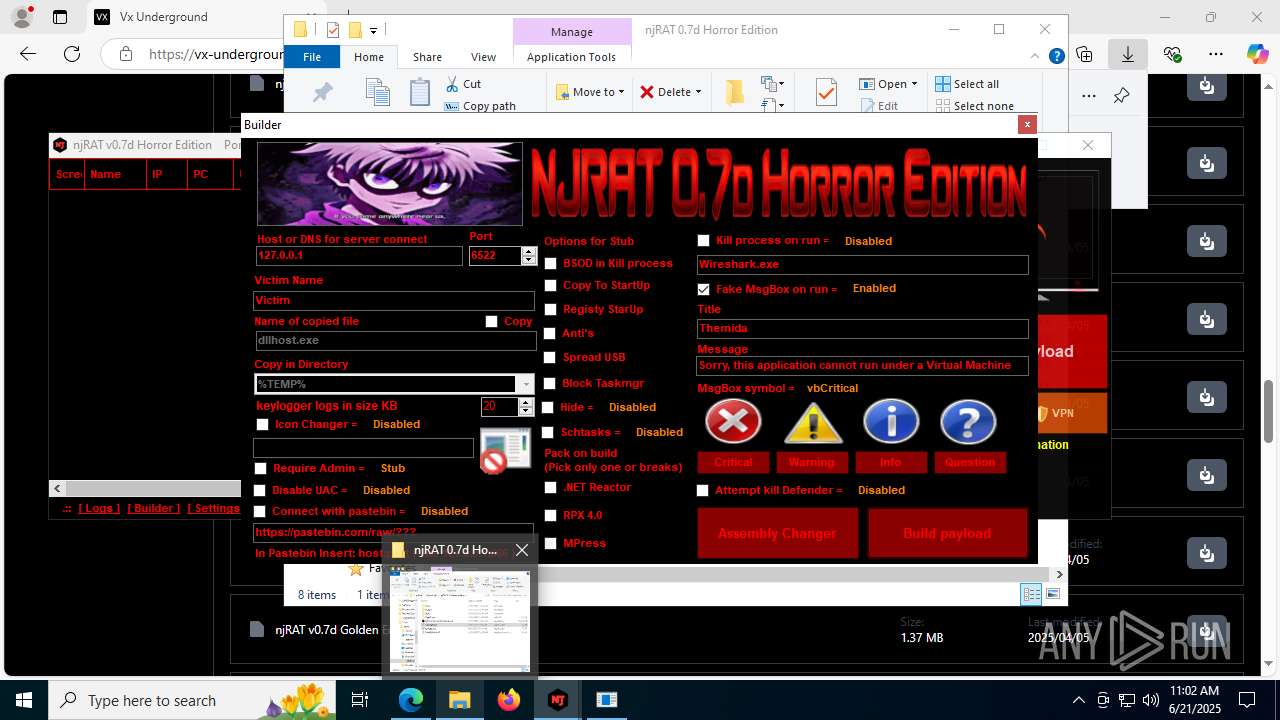
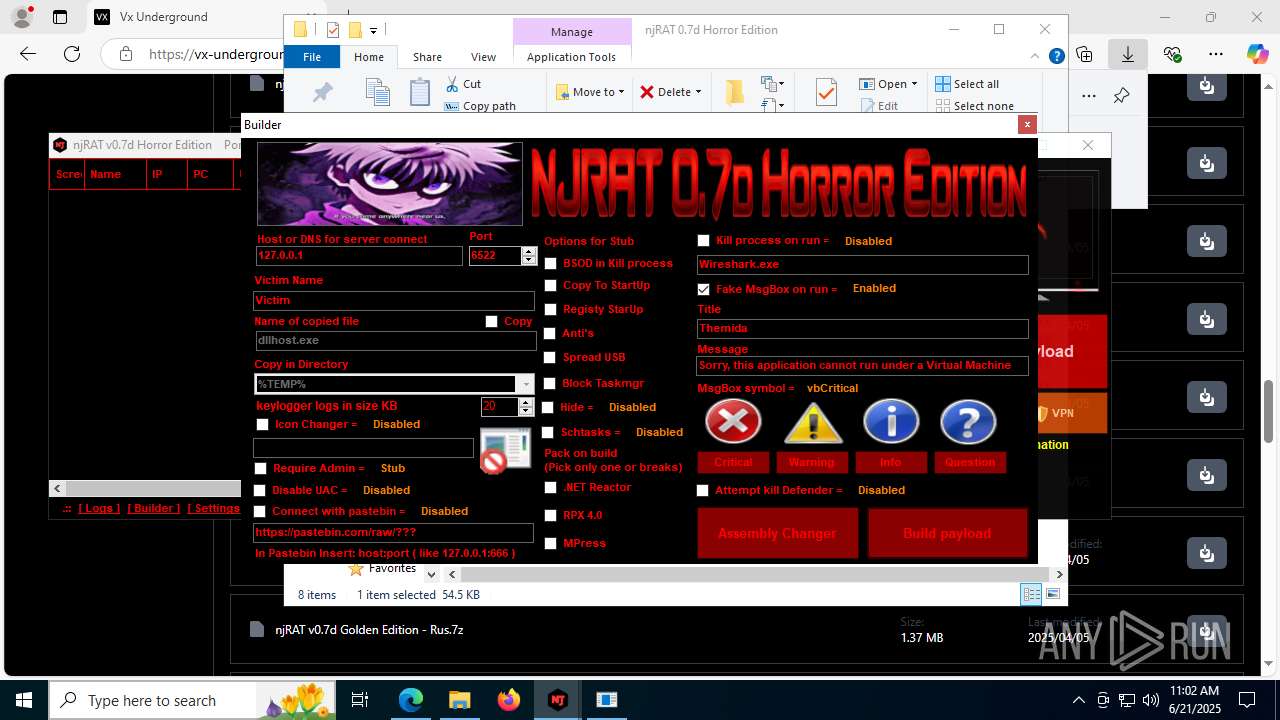
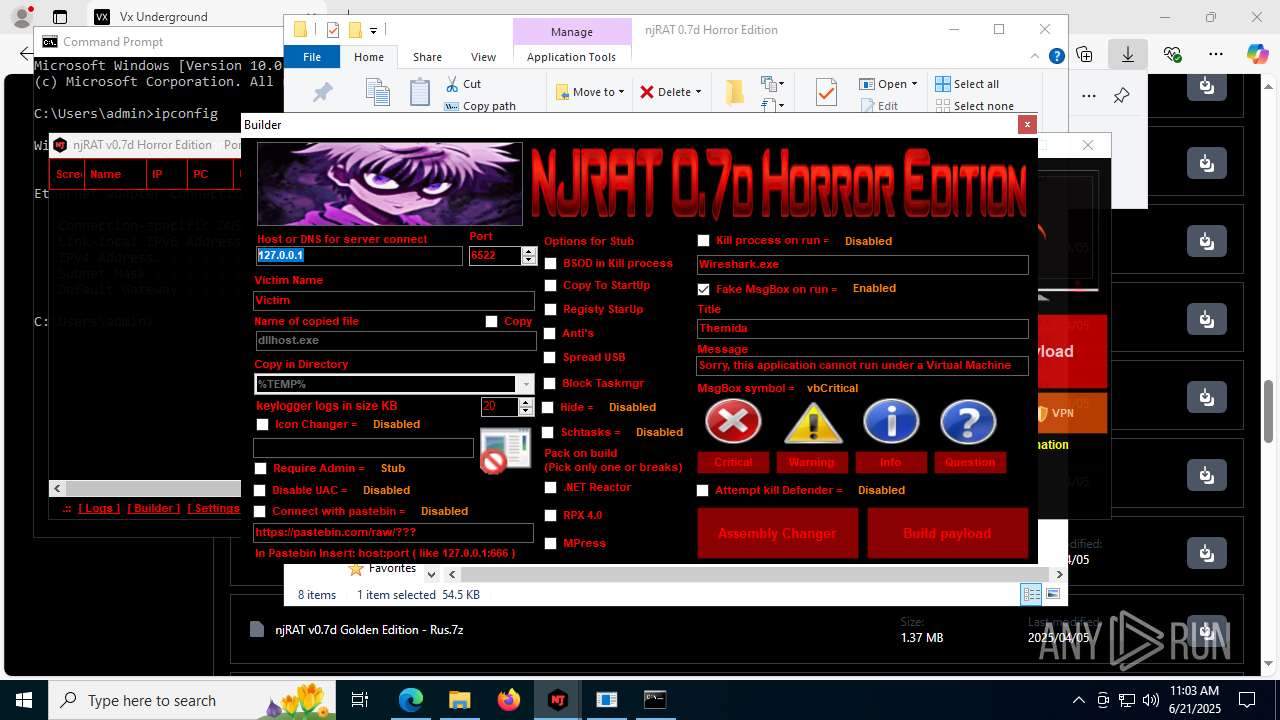
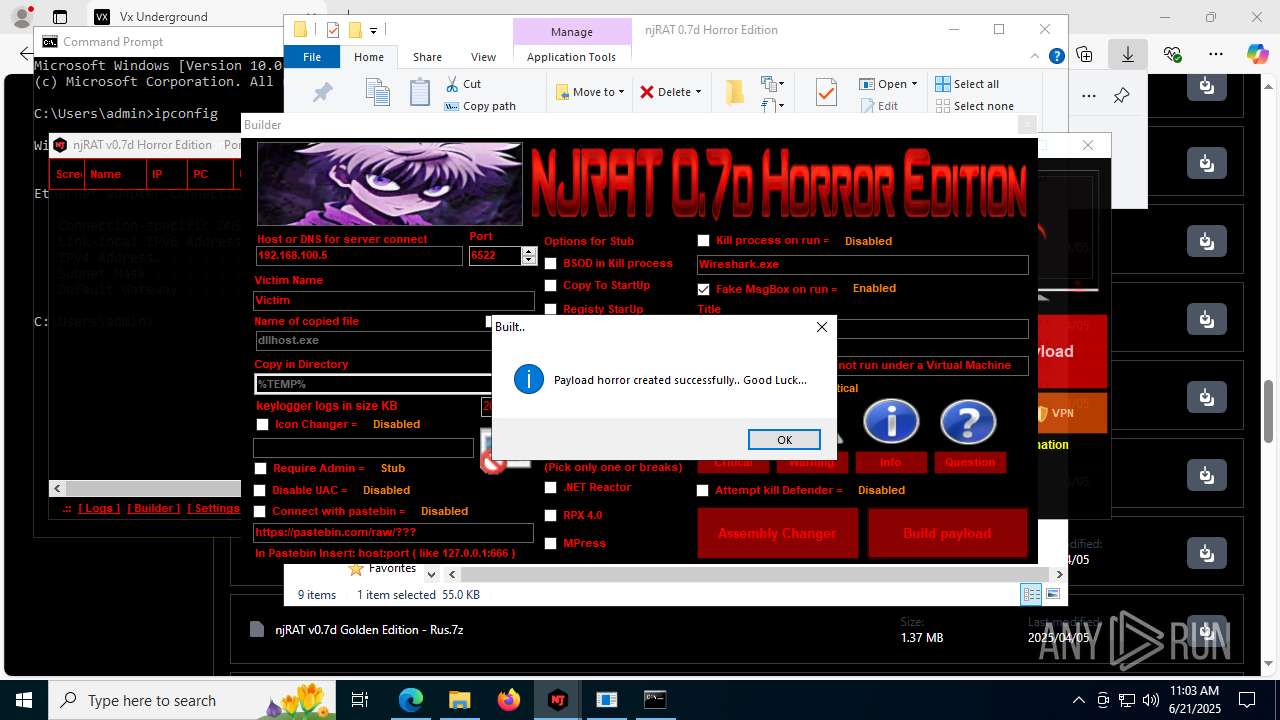
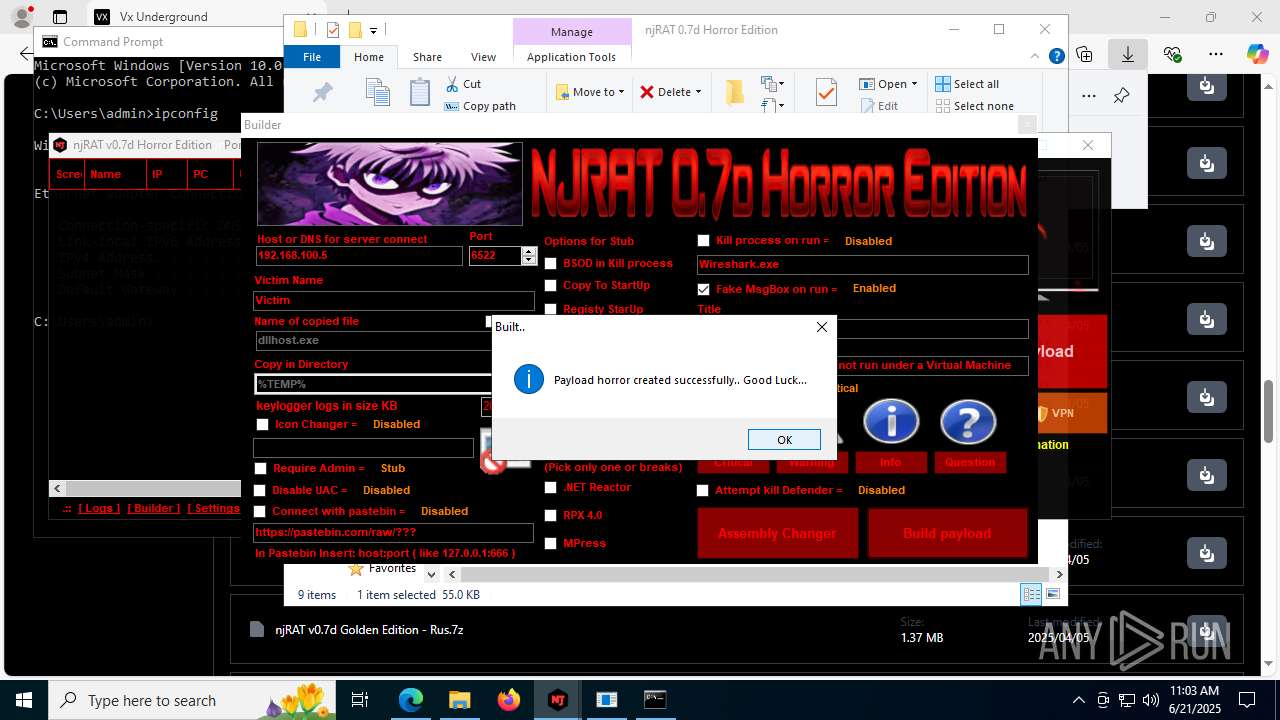
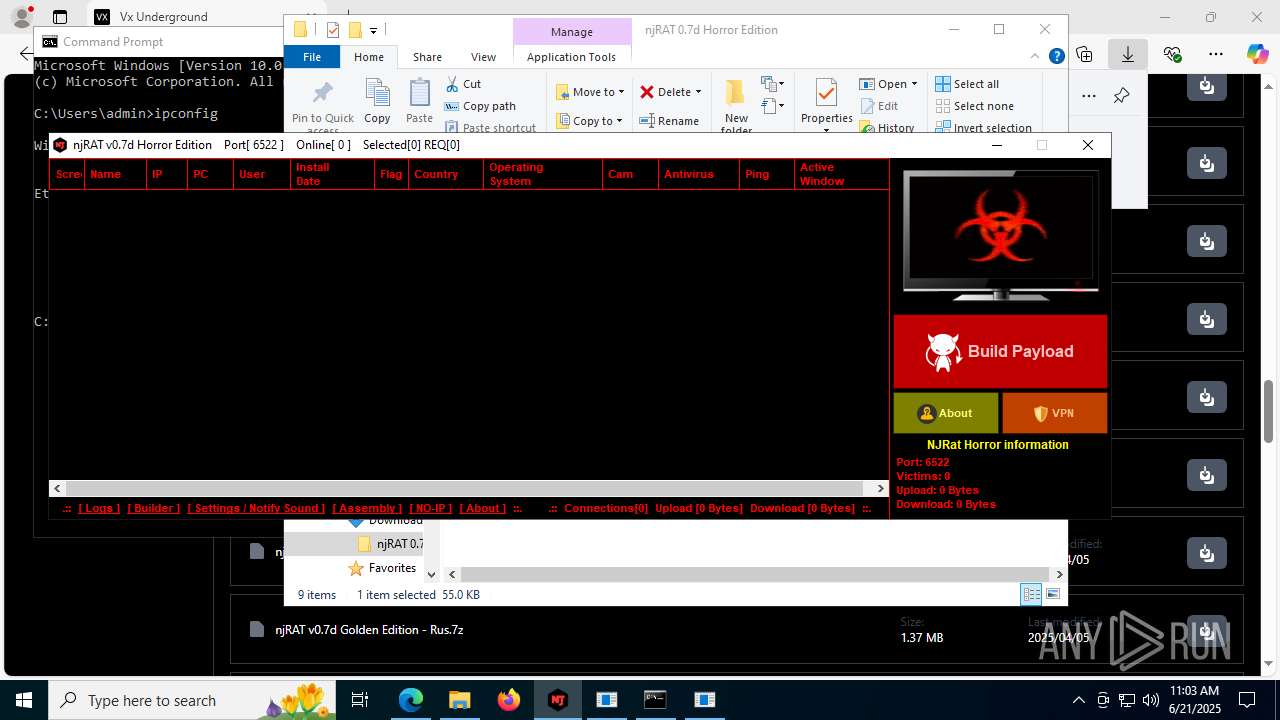
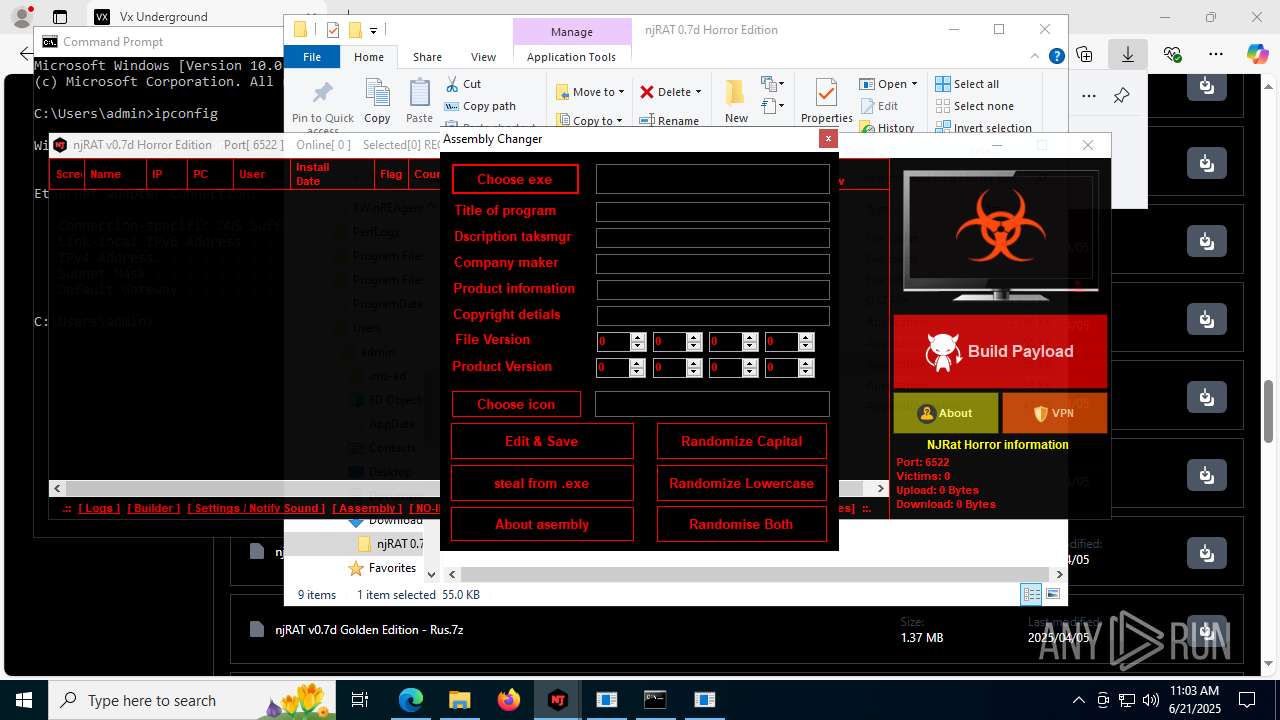
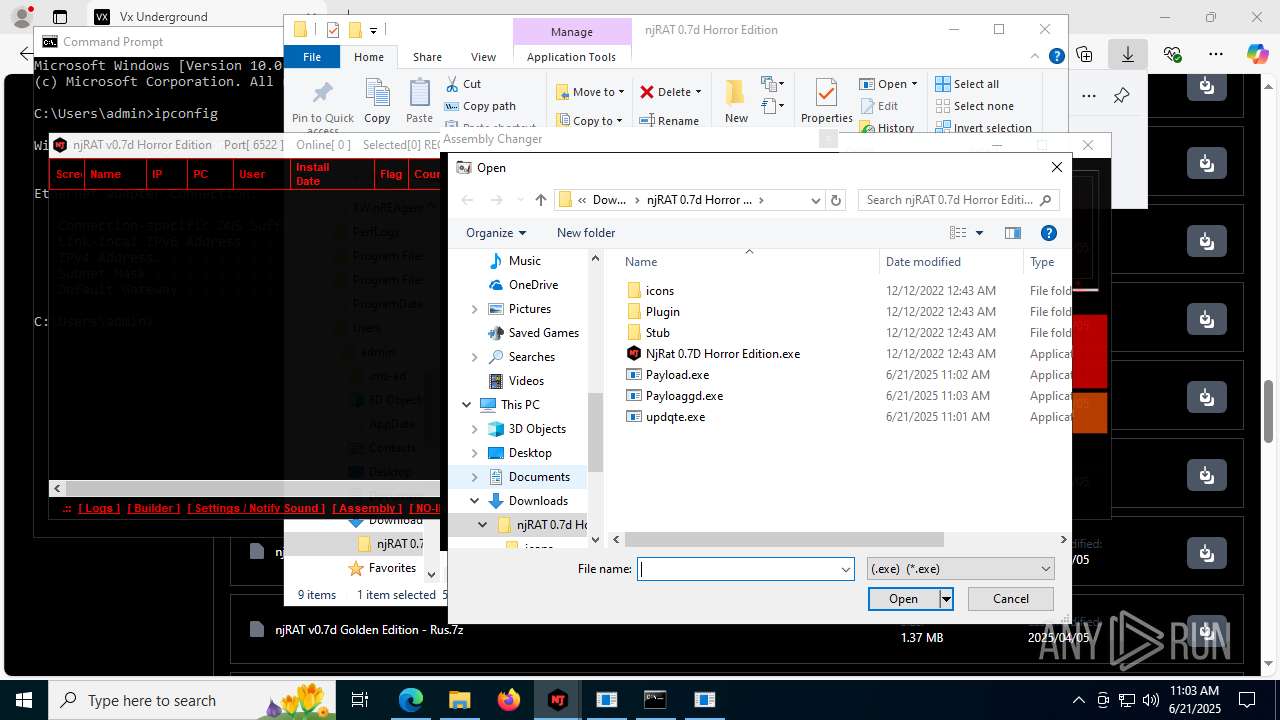
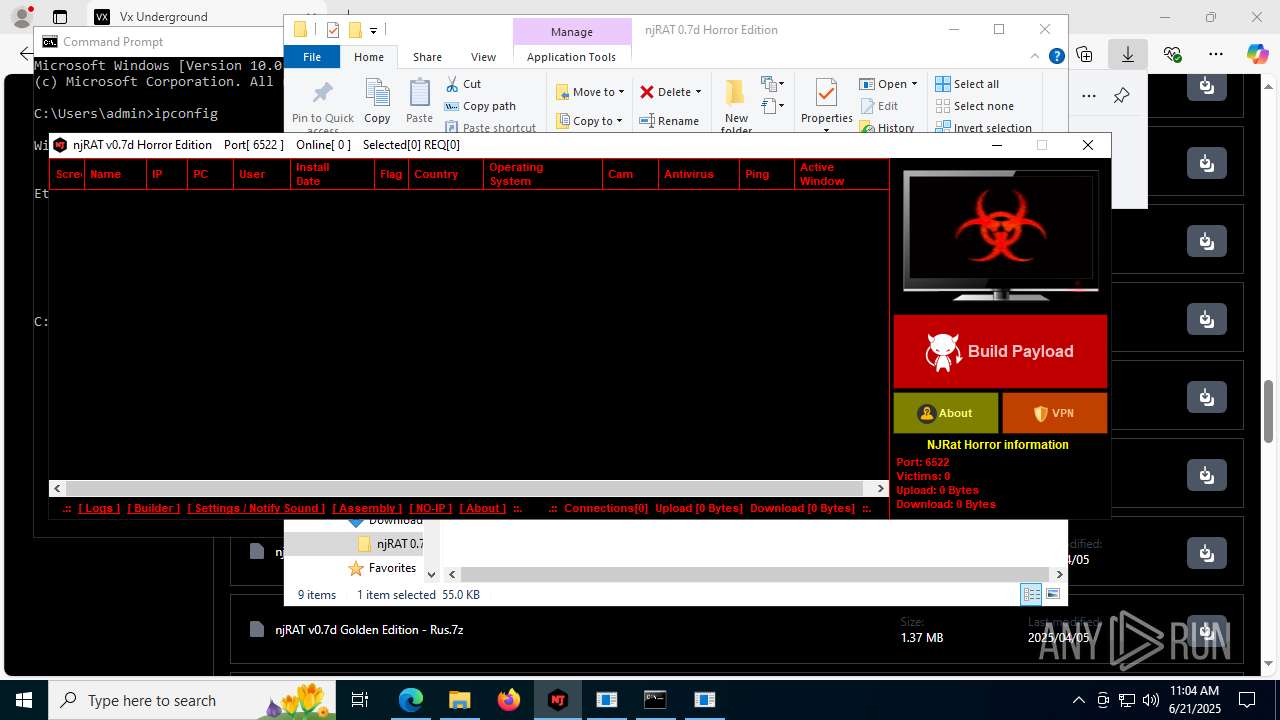
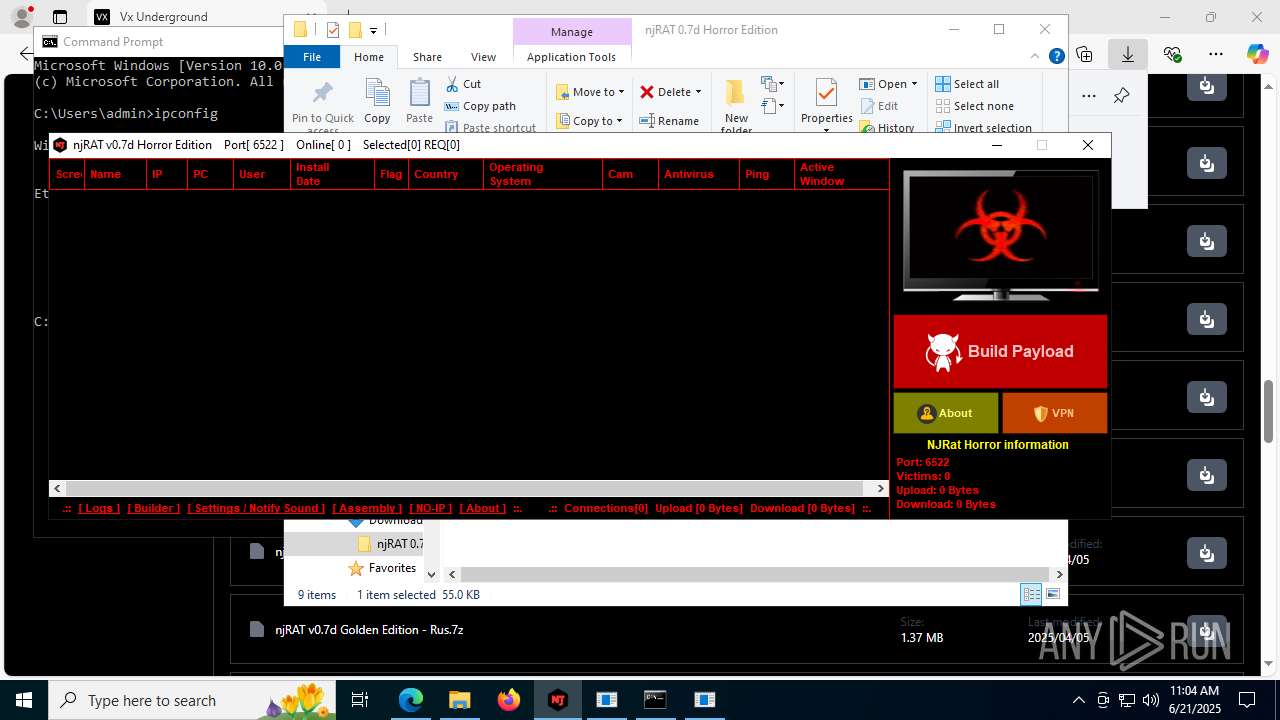
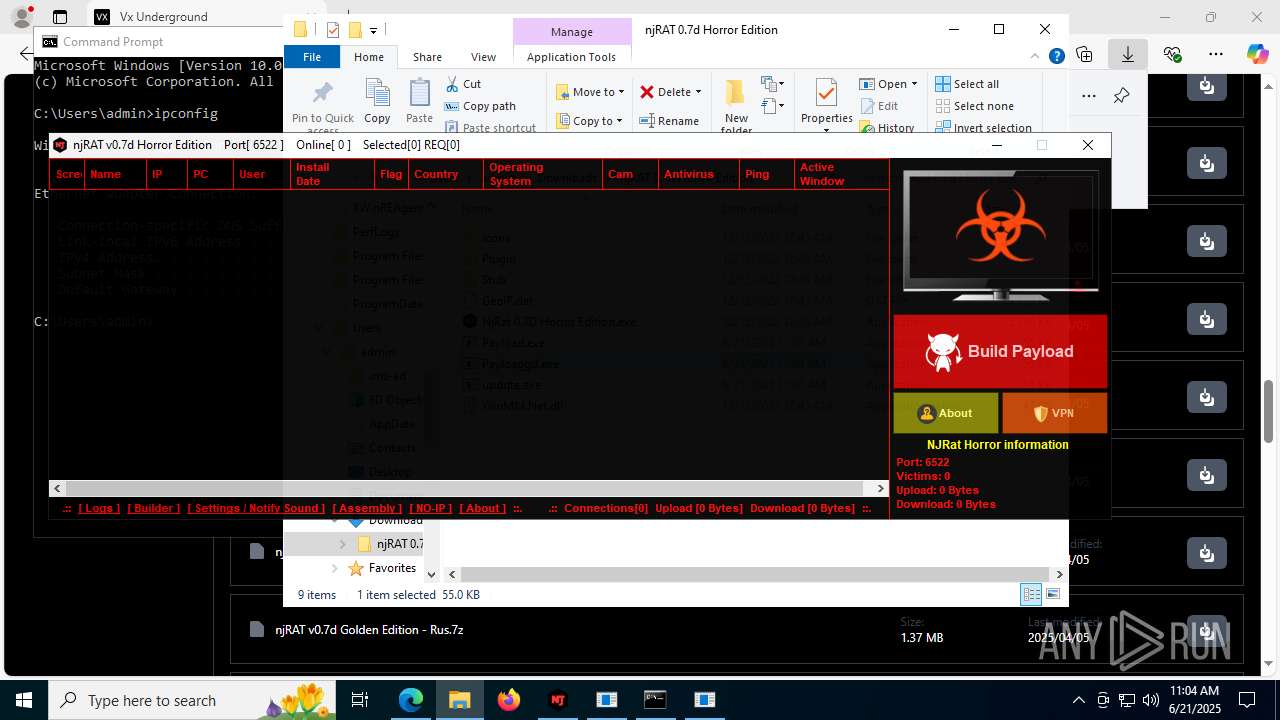
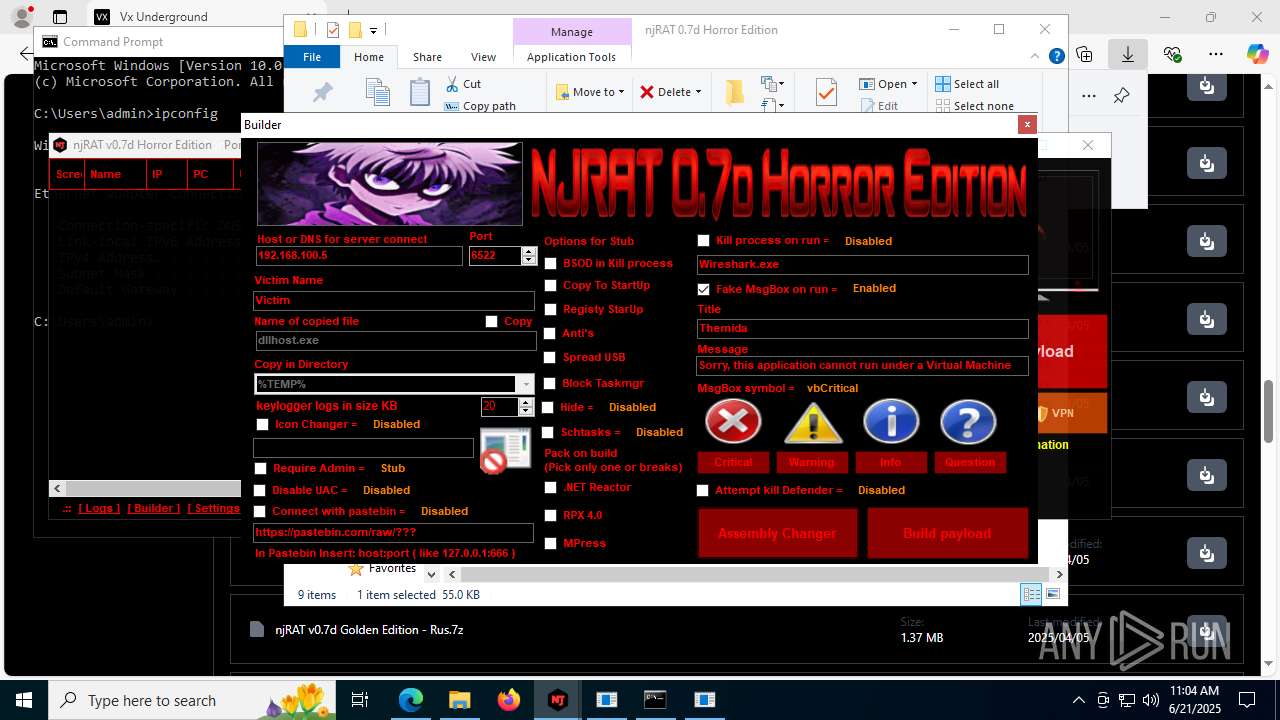
NjRat
(PID) Process(2124) updqte.exe
C21.0.0.721
Ports6522
BotnetVictim
Options
Auto-run registry keySoftware\Microsoft\Windows\CurrentVersion\Run\99f38bbe0af13fde32226e71d4a6ac11
SplitterY262SUCZ4UJJ
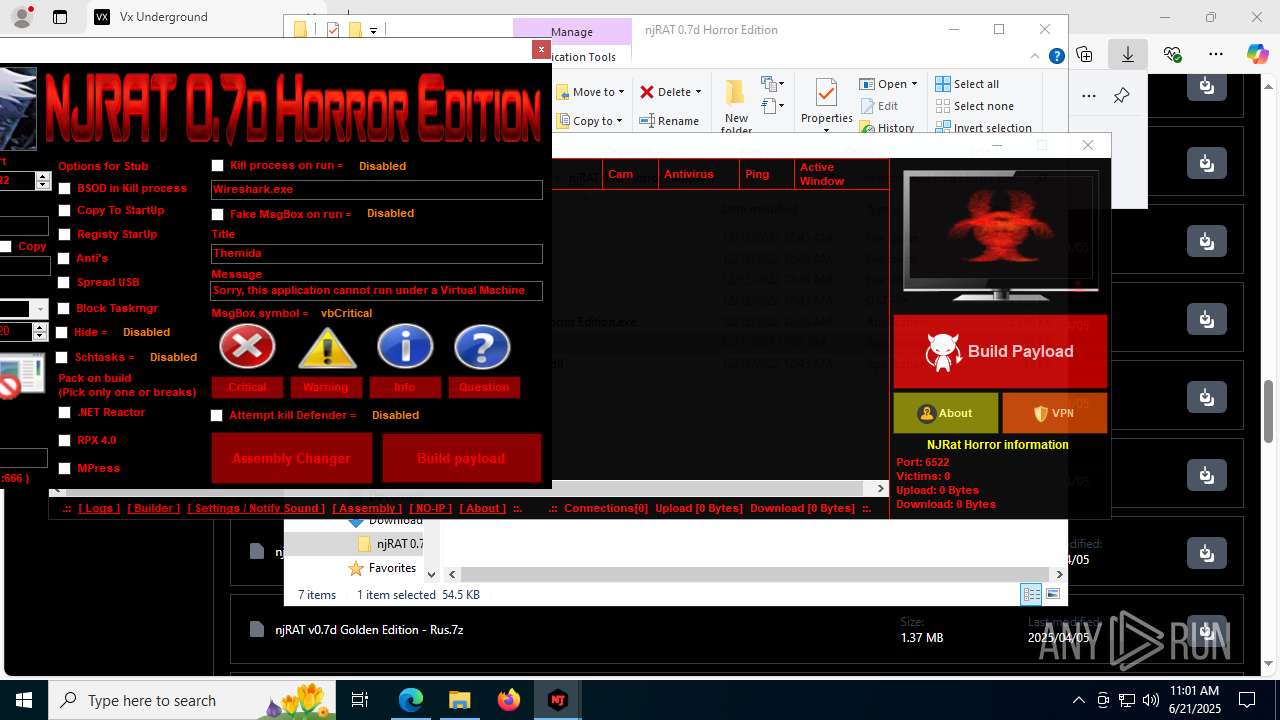
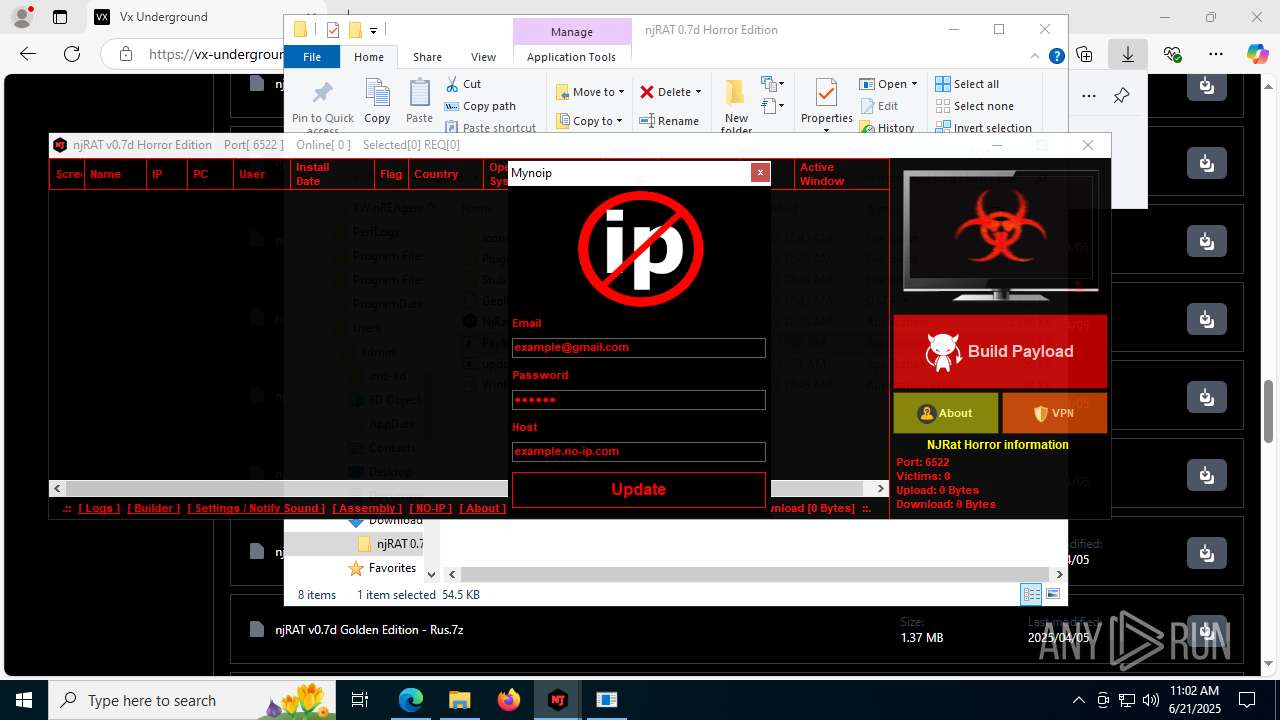
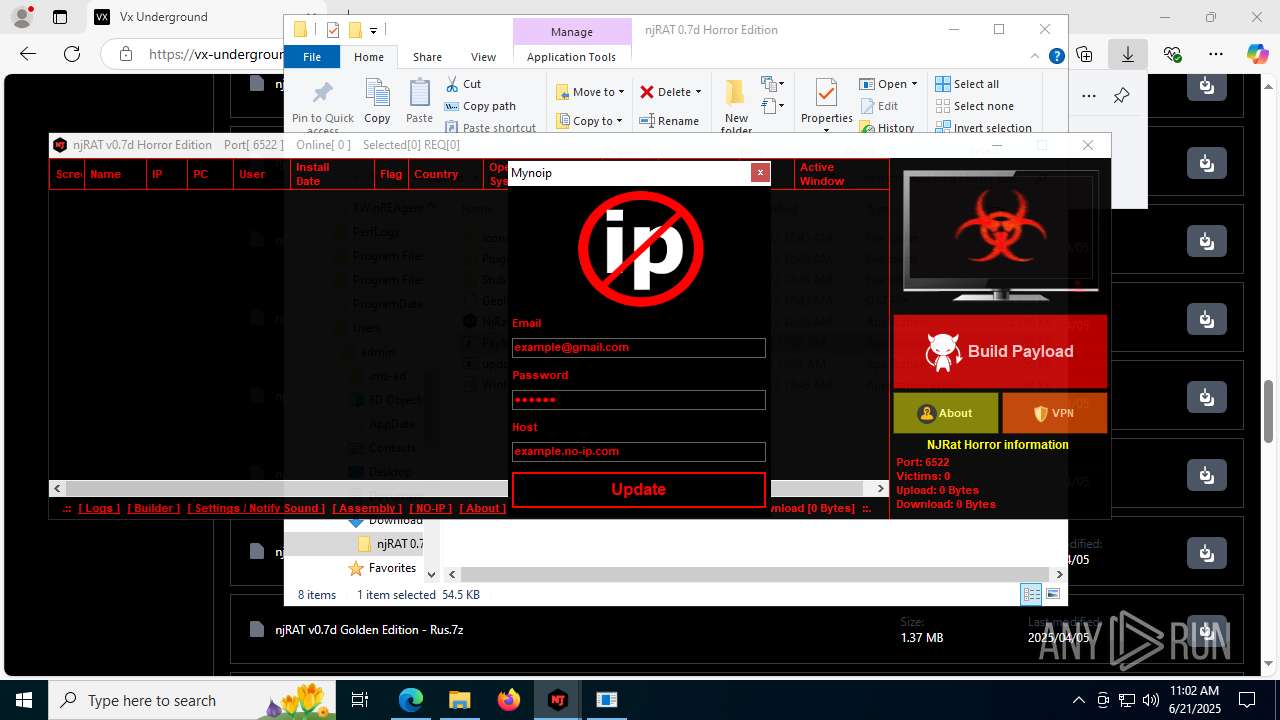
Version<- NjRAT 0.7d Horror Edition ->
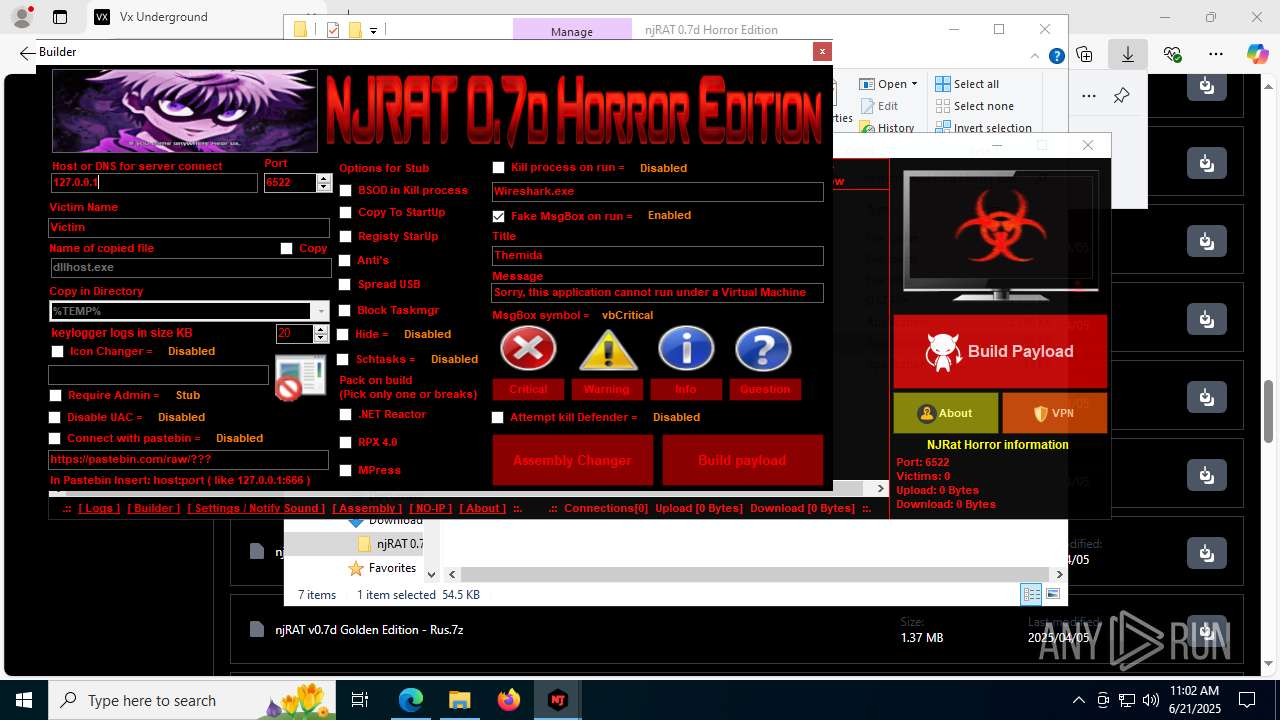
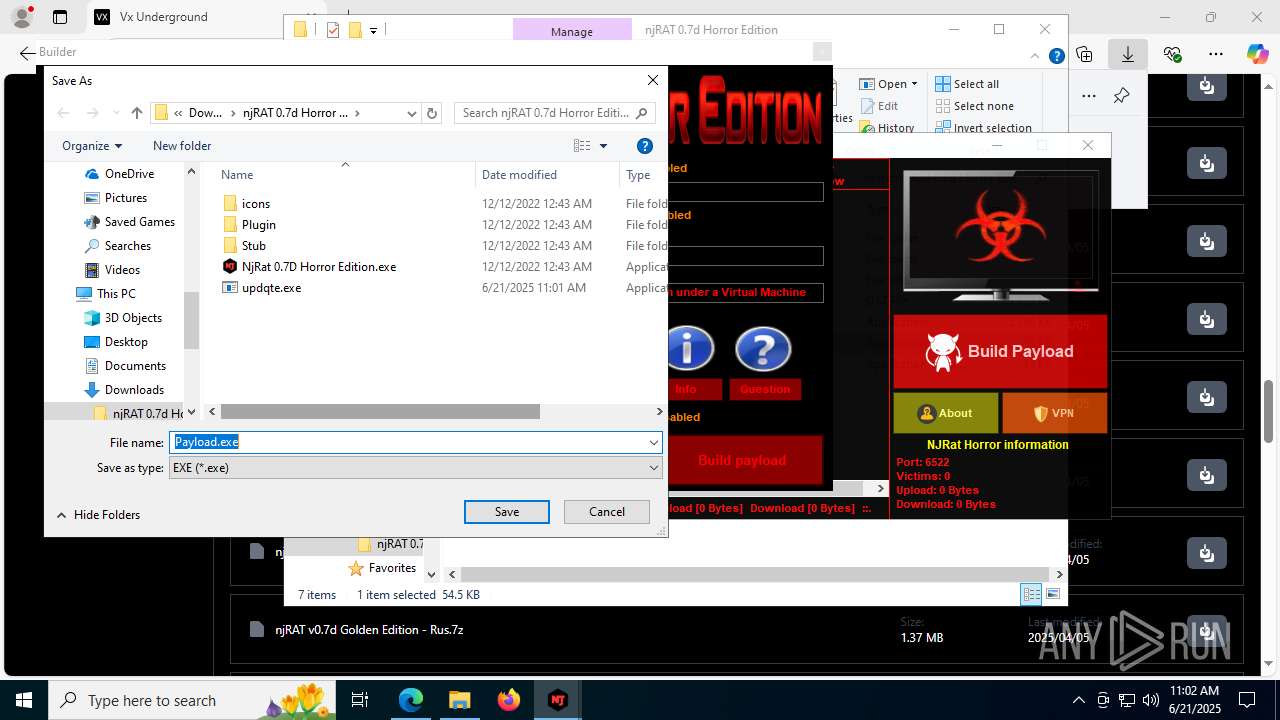
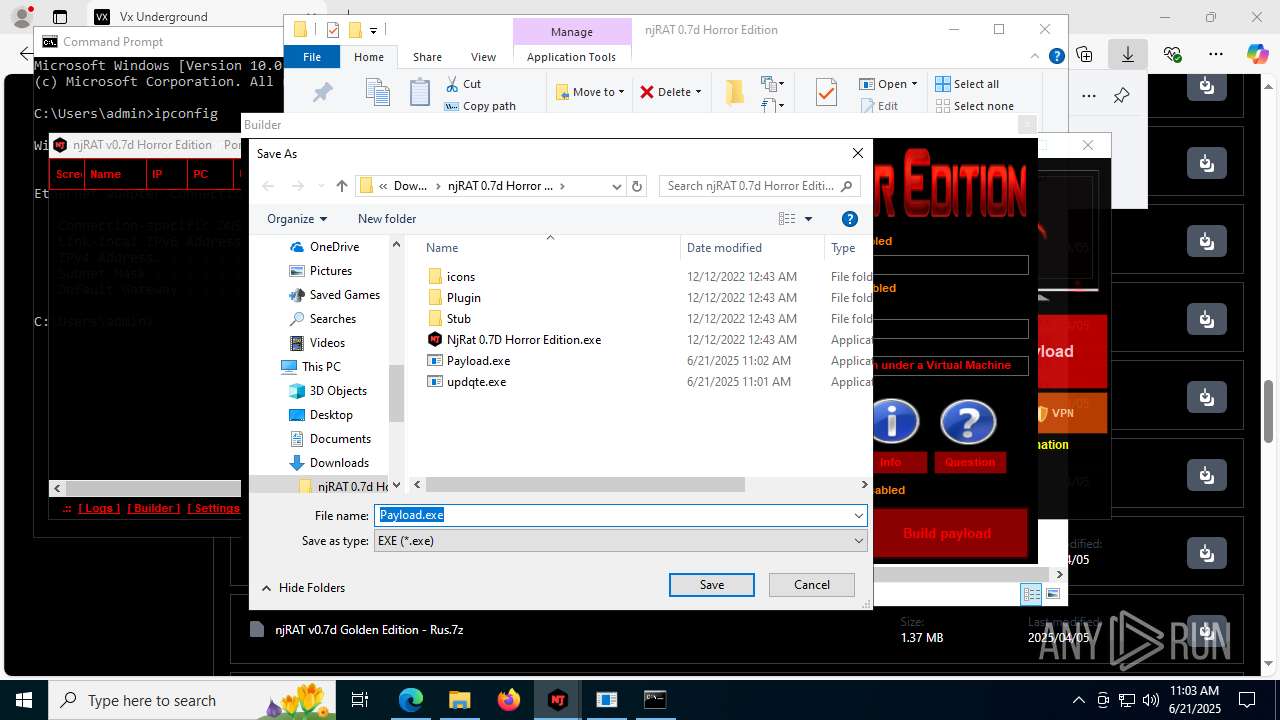
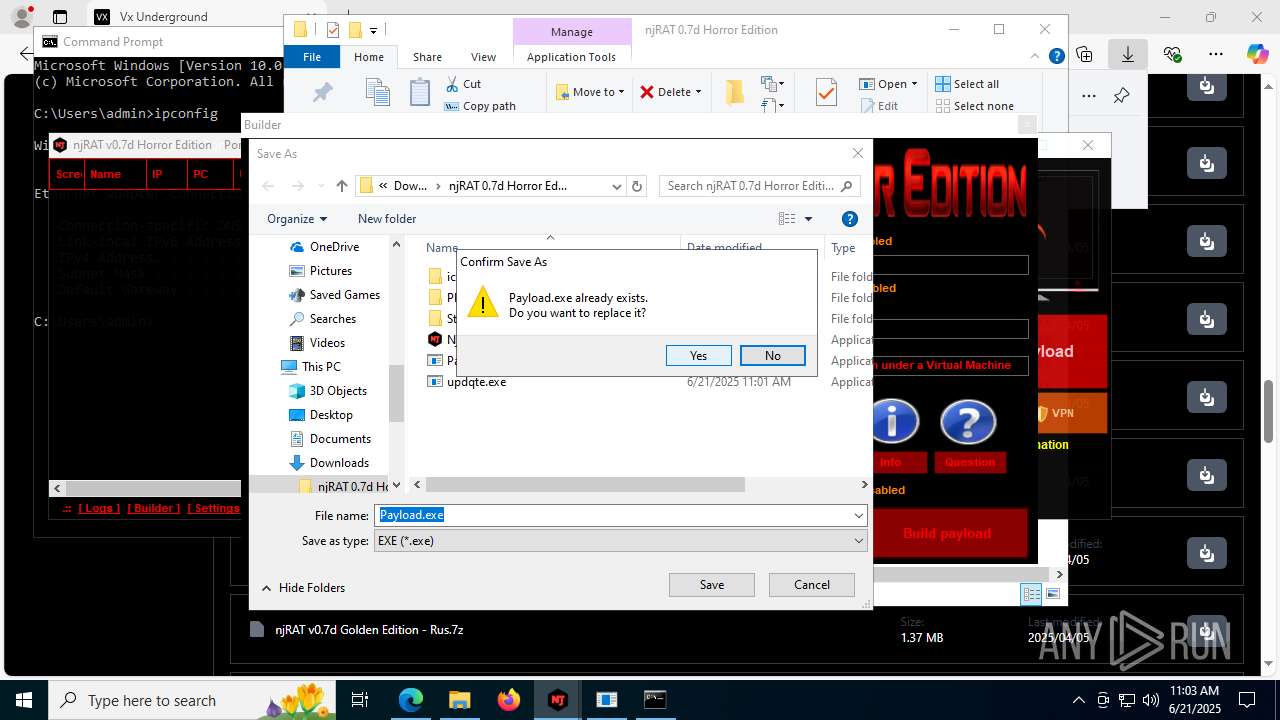
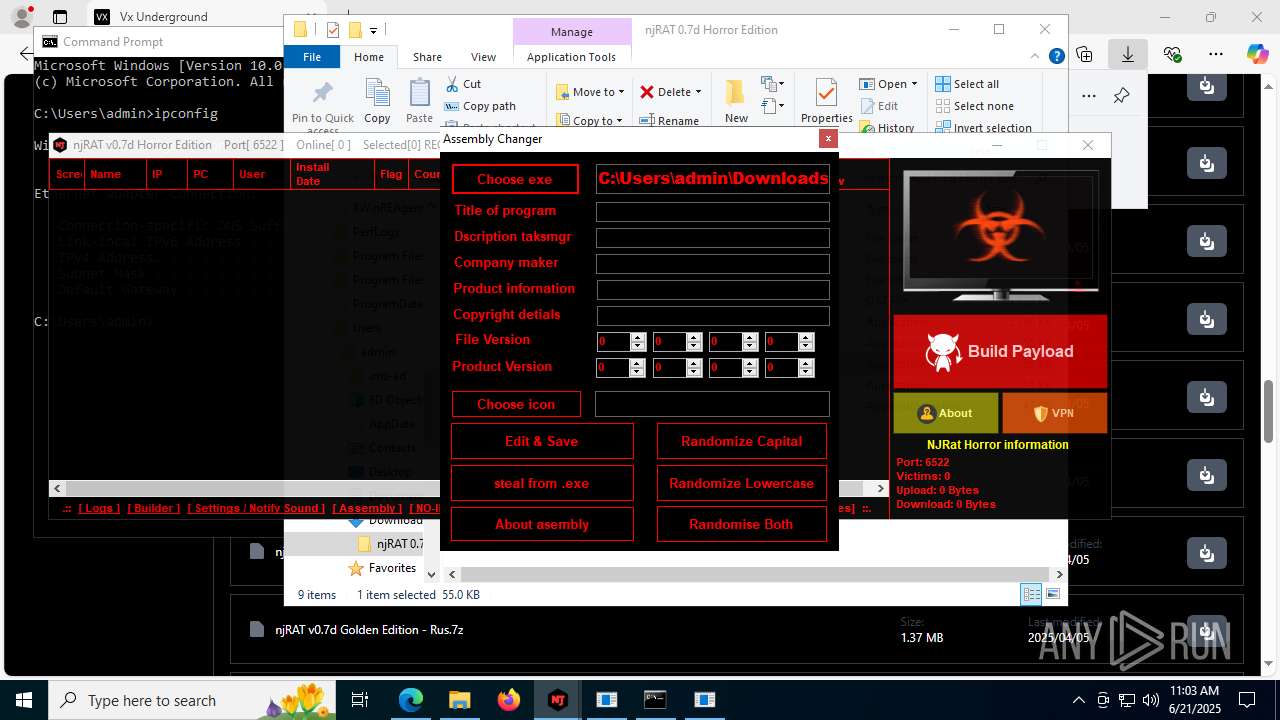
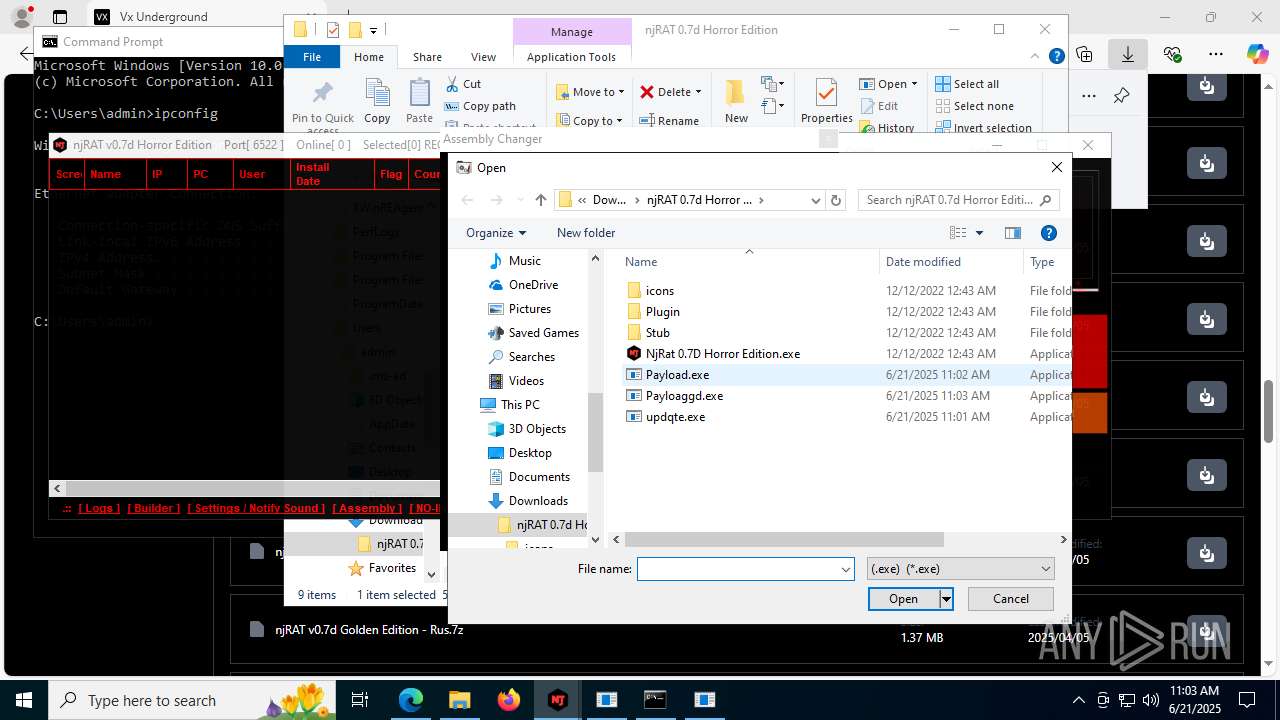
(PID) Process(4844) Payload.exe
C2127.0.0.1
Ports6522
BotnetVictim
Options
Auto-run registry keySoftware\Microsoft\Windows\CurrentVersion\Run\b6f83ebf0bce1d5c2e2e278edaabc64b
SplitterY262SUCZ4UJJ
Version<- NjRAT 0.7d Horror Edition ->
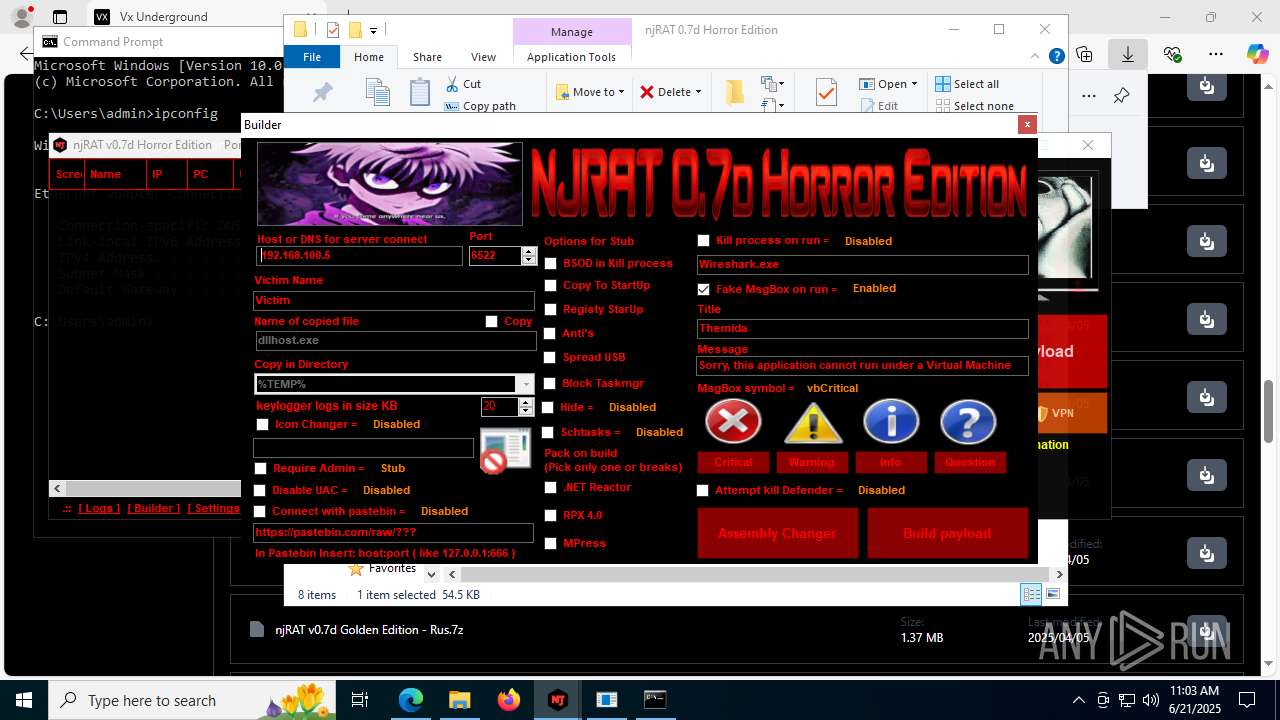
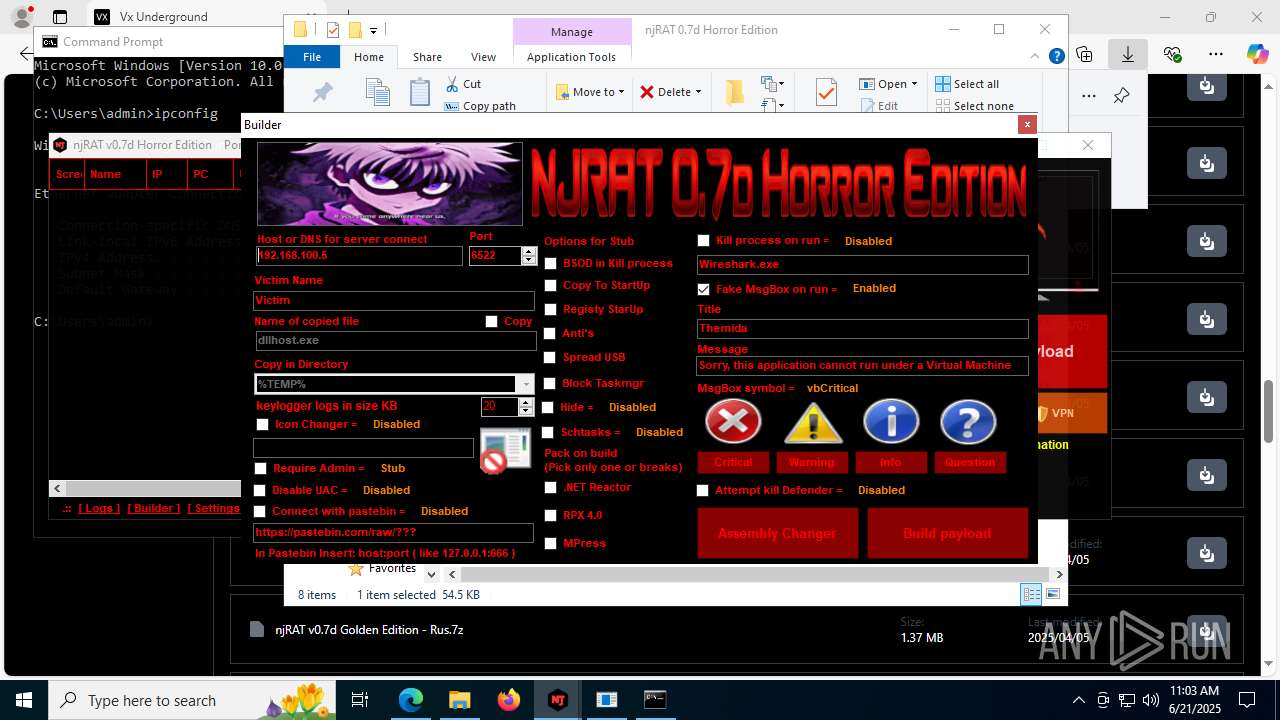
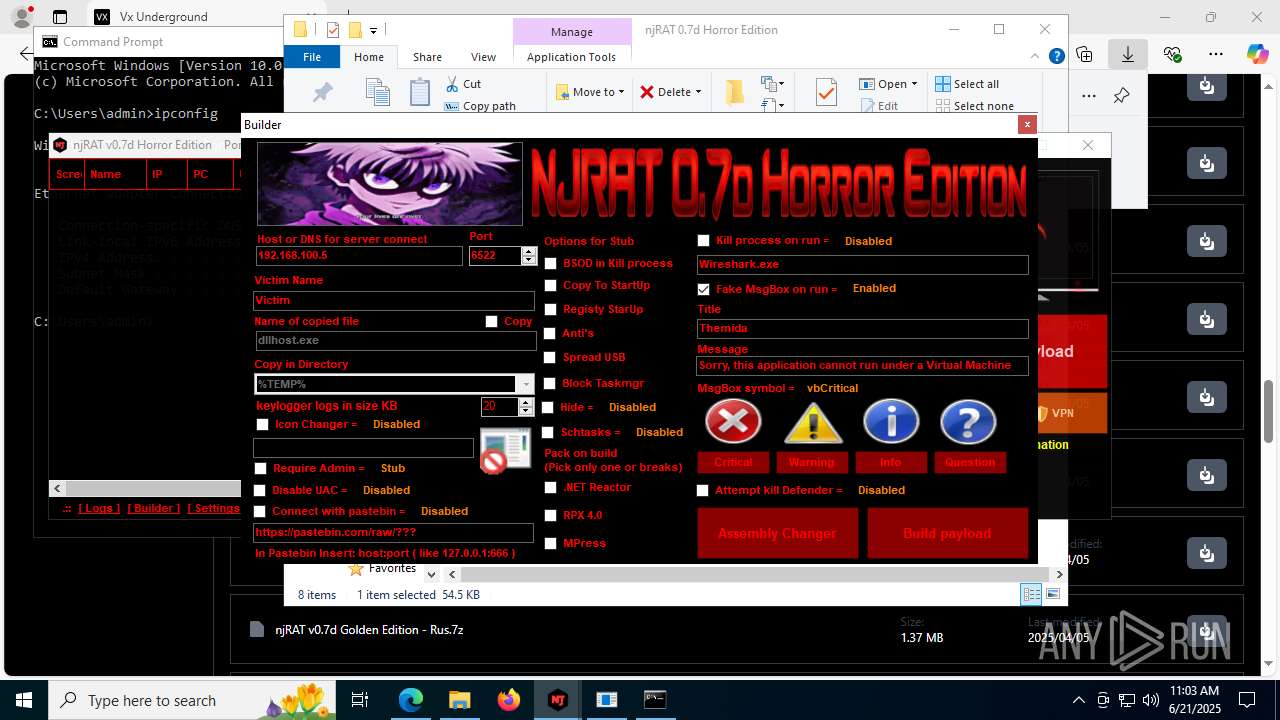
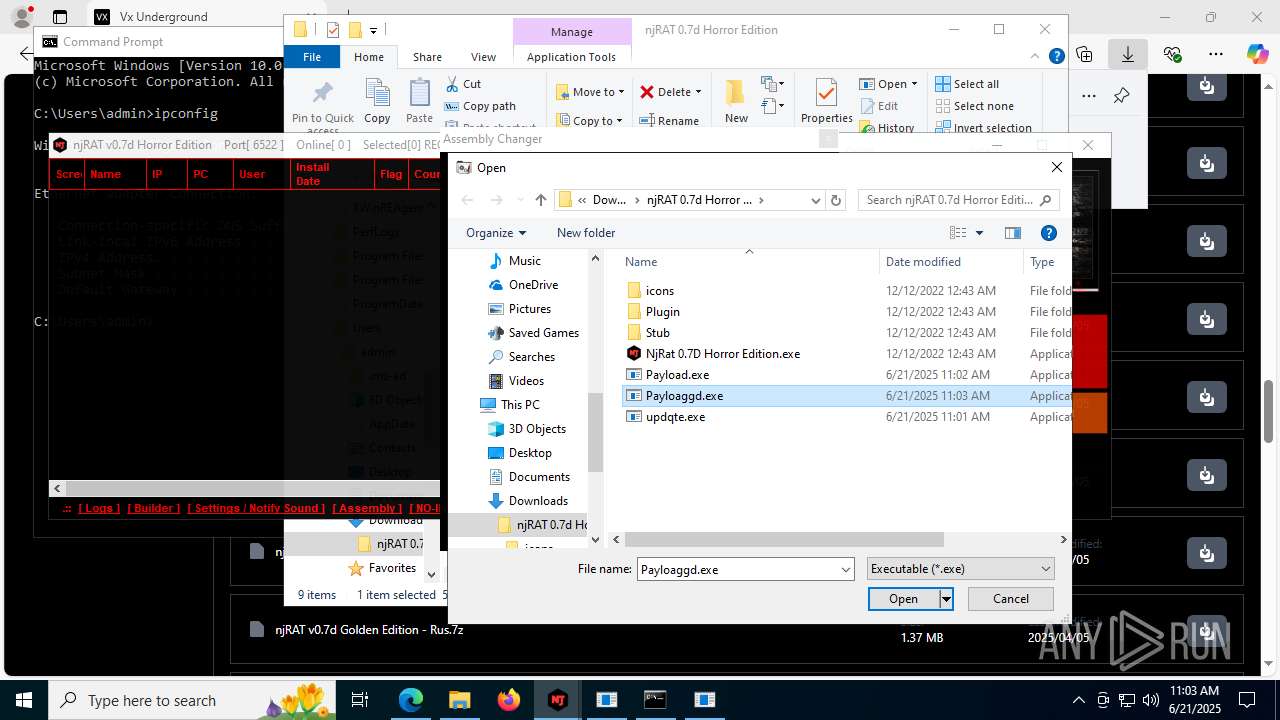
(PID) Process(4760) Payloaggd.exe
C2192.168.100.5
Ports6522
BotnetVictim
Options
Auto-run registry keySoftware\Microsoft\Windows\CurrentVersion\Run\0524d78e7b17e966d95a3532d27a1dd8
SplitterY262SUCZ4UJJ
Version<- NjRAT 0.7d Horror Edition ->
Total processes
210
Monitored processes
62
Malicious processes
4
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 188 | C:\WINDOWS\System32\rundll32.exe C:\WINDOWS\System32\shell32.dll,SHCreateLocalServerRunDll {9aa46009-3ce0-458a-a354-715610a075e6} -Embedding | C:\Windows\System32\rundll32.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 592 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 620 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=renderer --string-annotations --video-capture-use-gpu-memory-buffer --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=5 --always-read-main-dll --field-trial-handle=3676,i,8310268599763254050,17294941735269626930,262144 --variations-seed-version --mojo-platform-channel-handle=3704 /prefetch:1 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 133.0.3065.92 Modules
| |||||||||||||||
| 888 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=asset_store.mojom.AssetStoreService --lang=en-US --service-sandbox-type=asset_store_service --disable-quic --string-annotations --always-read-main-dll --field-trial-handle=7420,i,8310268599763254050,17294941735269626930,262144 --variations-seed-version --mojo-platform-channel-handle=1420 /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 133.0.3065.92 Modules
| |||||||||||||||
| 1056 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | ilasm.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
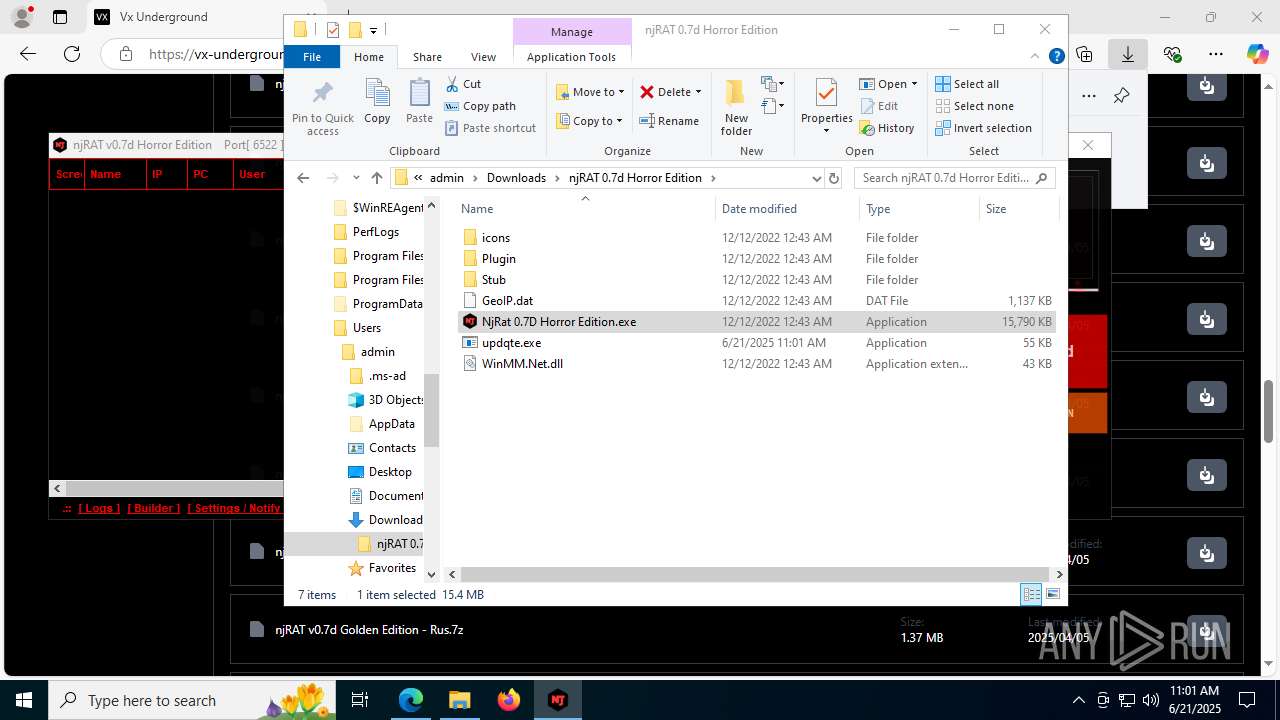
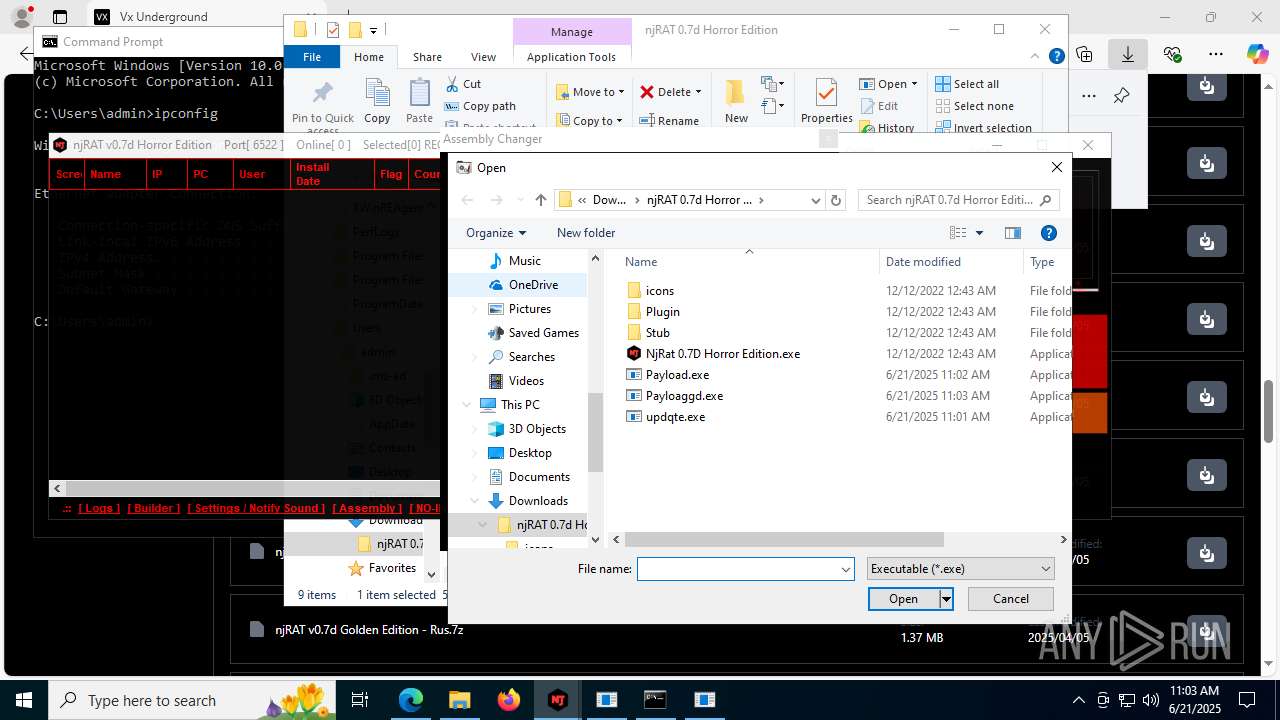
| 2124 | "C:\Users\admin\Downloads\njRAT 0.7d Horror Edition\updqte.exe" | C:\Users\admin\Downloads\njRAT 0.7d Horror Edition\updqte.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Modules
NjRat(PID) Process(2124) updqte.exe C21.0.0.721 Ports6522 BotnetVictim Options Auto-run registry keySoftware\Microsoft\Windows\CurrentVersion\Run\99f38bbe0af13fde32226e71d4a6ac11 SplitterY262SUCZ4UJJ Version<- NjRAT 0.7d Horror Edition -> | |||||||||||||||
| 2200 | C:\WINDOWS\system32\svchost.exe -k NetworkService -p -s Dnscache | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2324 | "C:\WINDOWS\Microsoft.NET\Framework\v2.0.50727\ilasm.exe" /alignment=512 /QUIET "C:\Users\admin\AppData\Local\Temp\stub.il" /output:"C:\Users\admin\Downloads\njRAT 0.7d Horror Edition\Payloaggd.exe" | C:\Windows\Microsoft.NET\Framework\v2.0.50727\ilasm.exe | NjRat 0.7D Horror Edition.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft .NET Framework IL assembler Exit code: 0 Version: 2.0.50727.9149 (WinRelRS6.050727-9100) Modules
| |||||||||||||||
| 2388 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=renderer --string-annotations --extension-process --renderer-sub-type=extension --video-capture-use-gpu-memory-buffer --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=7 --always-read-main-dll --field-trial-handle=4232,i,8310268599763254050,17294941735269626930,262144 --variations-seed-version --mojo-platform-channel-handle=4304 /prefetch:2 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 133.0.3065.92 Modules
| |||||||||||||||
| 2428 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | ilasm.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
21 545
Read events
21 249
Write events
287
Delete events
9
Modification events
| (PID) Process: | (3780) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (3780) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (3780) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\ThirdParty |
| Operation: | write | Name: | StatusCodes |
Value: | |||
| (PID) Process: | (3780) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\ThirdParty |
| Operation: | write | Name: | StatusCodes |
Value: 01000000 | |||
| (PID) Process: | (3780) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (3780) msedge.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\EdgeUpdate\ClientStateMedium\{56EB18F8-B008-4CBD-B6D2-8C97FE7E9062}\LastWasDefault |
| Operation: | write | Name: | S-1-5-21-1693682860-607145093-2874071422-1001 |
Value: 033DD028A9962F00 | |||
| (PID) Process: | (3780) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\WindowProperties\263014 |
| Operation: | write | Name: | WindowTabManagerFileMappingId |
Value: {0F311C8F-4972-4CD5-921F-9B62177E89E6} | |||
| (PID) Process: | (3780) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\StabilityMetrics |
| Operation: | write | Name: | user_experience_metrics.stability.exited_cleanly |
Value: 0 | |||
| (PID) Process: | (3780) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\WindowProperties\263014 |
| Operation: | write | Name: | WindowTabManagerFileMappingId |
Value: {5D0372FE-EB4C-4729-9EA2-150714FC172D} | |||
| (PID) Process: | (3780) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\WindowProperties\263014 |
| Operation: | write | Name: | WindowTabManagerFileMappingId |
Value: {A6AF2588-00C4-48A6-BC81-1A38DFBF17A1} | |||
Executable files
38
Suspicious files
156
Text files
101
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3780 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\ClientCertificates\LOG.old~RF176532.TMP | — | |
MD5:— | SHA256:— | |||
| 3780 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\ClientCertificates\LOG.old | — | |
MD5:— | SHA256:— | |||
| 3780 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old~RF176542.TMP | — | |
MD5:— | SHA256:— | |||
| 3780 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\parcel_tracking_db\LOG.old~RF176542.TMP | — | |
MD5:— | SHA256:— | |||
| 3780 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 3780 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\parcel_tracking_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 3780 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\PersistentOriginTrials\LOG.old~RF176542.TMP | — | |
MD5:— | SHA256:— | |||
| 3780 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\PersistentOriginTrials\LOG.old | — | |
MD5:— | SHA256:— | |||
| 3780 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\EdgePushStorageWithConnectTokenAndKey\LOG.old~RF176570.TMP | — | |
MD5:— | SHA256:— | |||
| 3780 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\EdgePushStorageWithConnectTokenAndKey\LOG.old | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
33
TCP/UDP connections
97
DNS requests
83
Threats
4
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
6228 | msedge.exe | GET | 200 | 150.171.27.11:80 | http://edge.microsoft.com/browsernetworktime/time/1/current?cup2key=2:iundHAj6Nlifo0yULyguP8ejEh8z5FVbdaTE4UxAi6k&cup2hreq=e3b0c44298fc1c149afbf4c8996fb92427ae41e4649b934ca495991b7852b855 | unknown | — | — | whitelisted |
5012 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 23.53.40.176:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
7656 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
7656 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
3872 | svchost.exe | HEAD | 200 | 199.232.214.172:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/bf8090eb-6e5c-4c51-9250-5bf9b46cf160?P1=1751066862&P2=404&P3=2&P4=acrB1mbtusgvT9vkDlUBNptvTjQCxcOb8IY6ej%2bk9lufAl4xHHJGRQ9prr07tLF%2bND7xTMTimR%2f5rxrN5Zj5WQ%3d%3d | unknown | — | — | whitelisted |
3872 | svchost.exe | GET | 206 | 199.232.214.172:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/bf8090eb-6e5c-4c51-9250-5bf9b46cf160?P1=1751066862&P2=404&P3=2&P4=acrB1mbtusgvT9vkDlUBNptvTjQCxcOb8IY6ej%2bk9lufAl4xHHJGRQ9prr07tLF%2bND7xTMTimR%2f5rxrN5Zj5WQ%3d%3d | unknown | — | — | whitelisted |
3872 | svchost.exe | GET | 206 | 199.232.214.172:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/bf8090eb-6e5c-4c51-9250-5bf9b46cf160?P1=1751066862&P2=404&P3=2&P4=acrB1mbtusgvT9vkDlUBNptvTjQCxcOb8IY6ej%2bk9lufAl4xHHJGRQ9prr07tLF%2bND7xTMTimR%2f5rxrN5Zj5WQ%3d%3d | unknown | — | — | whitelisted |
3872 | svchost.exe | HEAD | 200 | 199.232.214.172:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/4c4fdee0-d69c-42b7-bf5c-3ec046e9dfc9?P1=1751066864&P2=404&P3=2&P4=RoCo7GwMG2OAFnEwXZWkO125hL%2fjrXwAKCHGRm5ibWp2V1fZeuu4pORuAzTRYAP4GenSG%2bqvKZhRS2MxZOJ9ww%3d%3d | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
1268 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
5944 | MoUsoCoreWorker.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6368 | RUXIMICS.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
6228 | msedge.exe | 104.18.7.192:443 | vx-underground.org | CLOUDFLARENET | — | shared |
6228 | msedge.exe | 13.107.42.16:443 | config.edge.skype.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
6228 | msedge.exe | 92.123.104.31:443 | www.bing.com | Akamai International B.V. | DE | whitelisted |
6228 | msedge.exe | 150.171.27.11:80 | edge.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
6228 | msedge.exe | 104.18.95.41:443 | challenges.cloudflare.com | CLOUDFLARENET | — | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
edge.microsoft.com |
| whitelisted |
config.edge.skype.com |
| whitelisted |
vx-underground.org |
| malicious |
copilot.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
challenges.cloudflare.com |
| whitelisted |
update.googleapis.com |
| whitelisted |
edgeassetservice.azureedge.net |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
6228 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] Cloudflare turnstile CAPTCHA challenge |
6228 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] Cloudflare turnstile CAPTCHA challenge |
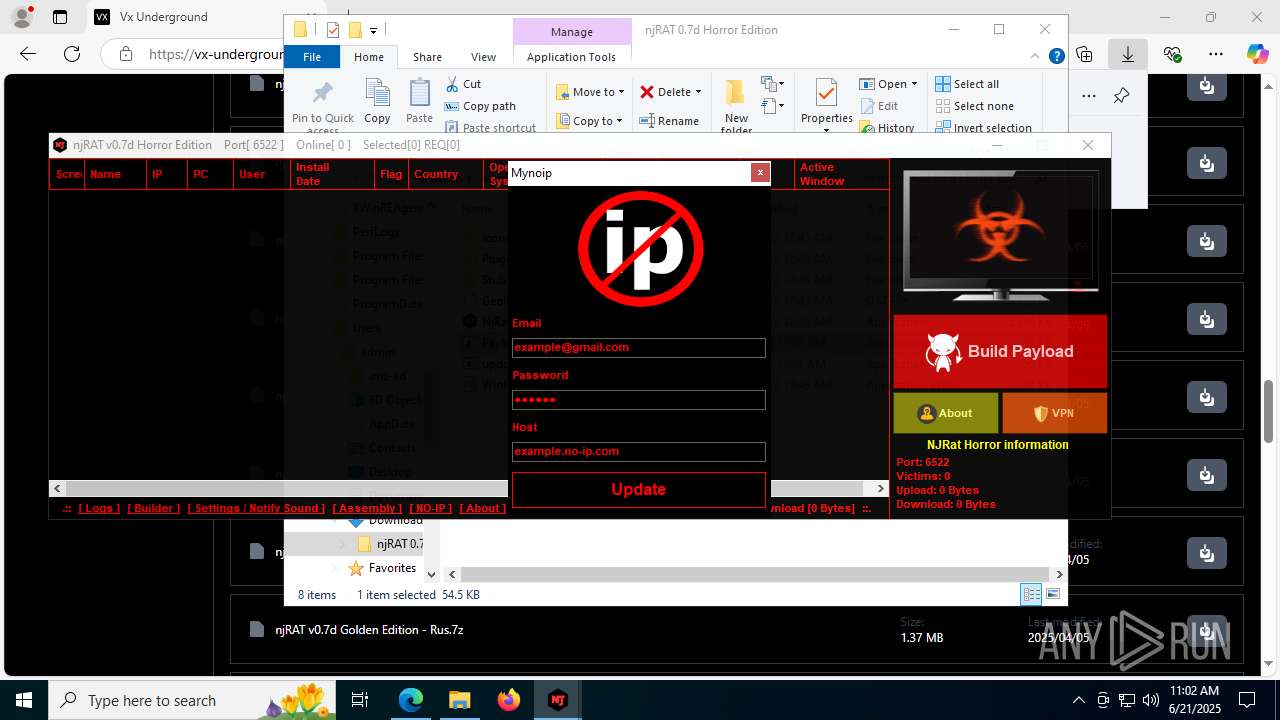
2200 | svchost.exe | Potentially Bad Traffic | ET DYN_DNS DYNAMIC_DNS Query to a Suspicious no-ip Domain |
8120 | NjRat 0.7D Horror Edition.exe | Potentially Bad Traffic | ET DYN_DNS DYNAMIC_DNS HTTP Request to a no-ip Domain |