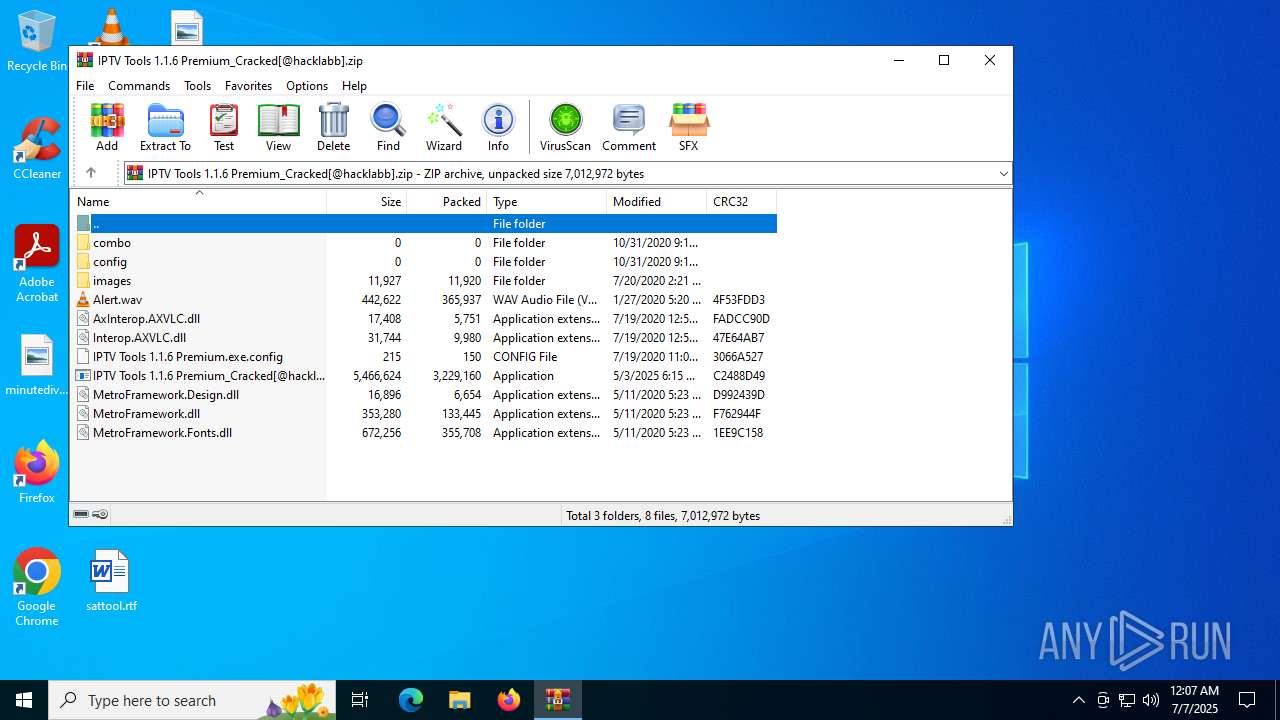
| File name: | IPTV Tools 1.1.6 Premium_Cracked[@hacklabb].zip |
| Full analysis: | https://app.any.run/tasks/3dc079f2-8bed-467a-93dc-86acee05cbc1 |
| Verdict: | Malicious activity |
| Threats: | Amadey is a formidable Windows infostealer threat, characterized by its persistence mechanisms, modular design, and ability to execute various malicious tasks. |
| Analysis date: | July 07, 2025, 00:07:08 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v1.0 to extract, compression method=store |
| MD5: | 6F7409CE070C062CD17C4D4121D3951B |
| SHA1: | 9D9A7ED2F249642DB0BC82DAECC6547E321C524A |
| SHA256: | A54D1C9DC0D2C7080A99B90530D0C2C1117E9A7A03F7C71644F04BF6ABD2324D |
| SSDEEP: | 98304:i6SvFtvpZXiXXHYeF81hj+cPi/fG+jcnid2AKVb2hHapSXVtzPOX4JzvXedLEX4P:wjH |
MALICIOUS
TINYNUKE has been found (auto)
- IPTV Tools 1.1.6 Premium_Cracked[@hacklabb].exe (PID: 6652)
- bvxbvbvf.exe (PID: 6636)
Runs injected code in another process
- bvxbvbvf.exe (PID: 6636)
- svchost.exe (PID: 5560)
Application was injected by another process
- explorer.exe (PID: 4772)
Changes the autorun value in the registry
- bvxbvbvf.exe (PID: 6636)
- systaxpcosx.exe (PID: 2120)
- audiodg.exe (PID: 4084)
- explorer.exe (PID: 4772)
- msiexec.exe (PID: 5876)
AMADEY has been found (auto)
- Launcher.exe (PID: 1100)
- sysxchostbvv.exe (PID: 3872)
REDLINE mutex has been found
- svchost.exe (PID: 5560)
- explorer.exe (PID: 4772)
- audiodg.exe (PID: 4084)
- msiexec.exe (PID: 5876)
AMADEY mutex has been found
- sysxchostbvv.exe (PID: 3872)
- Gxtuum.exe (PID: 5352)
Actions looks like stealing of personal data
- yutuytt.exe (PID: 3720)
Registers / Runs the DLL via REGSVR32.EXE
- vbdvbccw.tmp (PID: 1480)
DIAMOTRIX has been detected (SURICATA)
- svchost.exe (PID: 2200)
SVCSTEALER has been detected (YARA)
- yutuytt.exe (PID: 3720)
DIAMOTRIX mutex has been found
- regsvr32.exe (PID: 7100)
AMADEY has been detected (YARA)
- Gxtuum.exe (PID: 5352)
SUSPICIOUS
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 5480)
- IPTV Tools 1.1.6 Premium_Cracked[@hacklabb].exe (PID: 6652)
- vbdvbccw.tmp (PID: 1660)
- sysxchostbvv.exe (PID: 3872)
- yutuytt.exe (PID: 3720)
- Gxtuum.exe (PID: 5352)
Executable content was dropped or overwritten
- IPTV Tools 1.1.6 Premium_Cracked[@hacklabb].exe (PID: 6652)
- Launcher.exe (PID: 1100)
- vbdvbccw.exe (PID: 1964)
- systaxpcosx.exe (PID: 2120)
- bvxbvbvf.exe (PID: 6636)
- vbdvbccw.tmp (PID: 1660)
- vbdvbccw.exe (PID: 3864)
- sysxchostbvv.exe (PID: 3872)
- vbdvbccw.tmp (PID: 1480)
Reads the date of Windows installation
- IPTV Tools 1.1.6 Premium_Cracked[@hacklabb].exe (PID: 6652)
Process drops legitimate windows executable
- Launcher.exe (PID: 1100)
- systaxpcosx.exe (PID: 2120)
- vbdvbccw.tmp (PID: 1660)
- vbdvbccw.tmp (PID: 1480)
Reads the Windows owner or organization settings
- vbdvbccw.tmp (PID: 1660)
- vbdvbccw.tmp (PID: 1480)
Starts itself from another location
- sysxchostbvv.exe (PID: 3872)
Starts POWERSHELL.EXE for commands execution
- regsvr32.exe (PID: 7100)
Executes application which crashes
- IptvRChecker.exe (PID: 6700)
Contacting a server suspected of hosting an CnC
- svchost.exe (PID: 2200)
There is functionality for taking screenshot (YARA)
- yutuytt.exe (PID: 3720)
- svchost.exe (PID: 5560)
- Gxtuum.exe (PID: 5352)
The process bypasses the loading of PowerShell profile settings
- regsvr32.exe (PID: 7100)
Found regular expressions for crypto-addresses (YARA)
- svchost.exe (PID: 5560)
The process hide an interactive prompt from the user
- regsvr32.exe (PID: 7100)
The process executes via Task Scheduler
- regsvr32.exe (PID: 2536)
- regsvr32.exe (PID: 5548)
- regsvr32.exe (PID: 6892)
- regsvr32.exe (PID: 1468)
There is functionality for enable RDP (YARA)
- Gxtuum.exe (PID: 5352)
INFO
Executable content was dropped or overwritten
- WinRAR.exe (PID: 5480)
The sample compiled with english language support
- WinRAR.exe (PID: 5480)
- IPTV Tools 1.1.6 Premium_Cracked[@hacklabb].exe (PID: 6652)
- Launcher.exe (PID: 1100)
- systaxpcosx.exe (PID: 2120)
- vbdvbccw.tmp (PID: 1660)
- vbdvbccw.tmp (PID: 1480)
Creates files or folders in the user directory
- IPTV Tools 1.1.6 Premium_Cracked[@hacklabb].exe (PID: 6652)
- Launcher.exe (PID: 1100)
- systaxpcosx.exe (PID: 2120)
- vbdvbccw.tmp (PID: 1480)
- Gxtuum.exe (PID: 5352)
- WerFault.exe (PID: 6808)
Reads the computer name
- IPTV Tools 1.1.6 Premium_Cracked[@hacklabb].exe (PID: 6652)
- gfgfrxr.exe (PID: 3800)
- yutuytt.exe (PID: 3720)
- vbdvbccw.tmp (PID: 1660)
- IptvRChecker.exe (PID: 6700)
- vbdvbccw.tmp (PID: 1480)
- sysxchostbvv.exe (PID: 3872)
- Gxtuum.exe (PID: 5352)
Checks supported languages
- IPTV Tools 1.1.6 Premium_Cracked[@hacklabb].exe (PID: 6652)
- gfgfrxr.exe (PID: 3800)
- bvxbvbvf.exe (PID: 6636)
- yutuytt.exe (PID: 3720)
- vbdvbccw.exe (PID: 1964)
- Launcher.exe (PID: 1100)
- IptvRChecker.exe (PID: 6700)
- systaxpcosx.exe (PID: 2120)
- vbdvbccw.tmp (PID: 1660)
- sysxchostbvv.exe (PID: 3872)
- vbdvbccw.exe (PID: 3864)
- vbdvbccw.tmp (PID: 1480)
- Gxtuum.exe (PID: 5352)
Reads the machine GUID from the registry
- bvxbvbvf.exe (PID: 6636)
- IptvRChecker.exe (PID: 6700)
Process checks computer location settings
- IPTV Tools 1.1.6 Premium_Cracked[@hacklabb].exe (PID: 6652)
- vbdvbccw.tmp (PID: 1660)
- sysxchostbvv.exe (PID: 3872)
Creates files in the program directory
- bvxbvbvf.exe (PID: 6636)
- yutuytt.exe (PID: 3720)
Launching a file from a Registry key
- bvxbvbvf.exe (PID: 6636)
- systaxpcosx.exe (PID: 2120)
- audiodg.exe (PID: 4084)
- msiexec.exe (PID: 5876)
- explorer.exe (PID: 4772)
Create files in a temporary directory
- vbdvbccw.exe (PID: 1964)
- Launcher.exe (PID: 1100)
- vbdvbccw.tmp (PID: 1660)
- vbdvbccw.exe (PID: 3864)
- sysxchostbvv.exe (PID: 3872)
- yutuytt.exe (PID: 3720)
- vbdvbccw.tmp (PID: 1480)
Checks proxy server information
- explorer.exe (PID: 4772)
- yutuytt.exe (PID: 3720)
- Gxtuum.exe (PID: 5352)
- WerFault.exe (PID: 6808)
- slui.exe (PID: 7160)
Reads the software policy settings
- WerFault.exe (PID: 6808)
- slui.exe (PID: 7160)
Checks if a key exists in the options dictionary (POWERSHELL)
- powershell.exe (PID: 3876)
- powershell.exe (PID: 3112)
Application based on Rust
- regsvr32.exe (PID: 7100)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Amadey
(PID) Process(5352) Gxtuum.exe
C2185.81.68.147
Strings (127)GET
SOFTWARE\Microsoft\Windows NT\CurrentVersion
00000419
av:
?scr=1
+++
Panda Security
wb
SYSTEM\CurrentControlSet\Control\UnitedVideo\CONTROL\VIDEO\
:::
------
2025
SYSTEM\ControlSet001\Services\BasicDisplay\Video
WinDefender
shutdown -s -t 0
ComputerName
00000423
ProductName
%USERPROFILE%
d1
lv:
Main
Doctor Web
<d>
abcdefghijklmnopqrstuvwxyz0123456789-_
random
0123456789
exe
S-%lu-
#
" && timeout 1 && del
\0000
2019
kernel32.dll
/quiet
=
ESET
Powershell.exe
AVAST Software
rundll32.exe
shell32.dll
vs:
&&
<c>
\
os:
e1
VideoID
Content-Disposition: form-data; name="data"; filename="
id:
------
rundll32
pc:
SOFTWARE\Microsoft\Windows\CurrentVersion\Run
Keyboard Layout\Preload
185.81.68.147
Content-Type: application/x-www-form-urlencoded
ProgramData\
dll
http://
%-lu
-%lu
og:
Comodo
GetNativeSystemInfo
0000043f
/k
bi:
|
Sophos
sd:
Content-Type: multipart/form-data; boundary=----
Kaspersky Lab
SYSTEM\CurrentControlSet\Control\ComputerName\ComputerName
.jpg
Gxtuum.exe
"
Content-Type: application/octet-stream
-unicode-
dm:
SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\Shell Folders
ar:
"taskkill /f /im "
\App
Programs
ps1
SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\User Shell Folders
-executionpolicy remotesigned -File "
Bitdefender
185.81.68.148
r=
/Plugins/
2016
Norton
5.10
00000422
msi
Avira
360TotalSecurity
2022
https://
AVG
&unit=
st=s
zip
rb
e3
" && ren
e2
Rem
"
cmd
&& Exit"
/7vhfjke3/index.php
ee29ea508b
/8Fvu5jh4DbS/index.php
DefaultSettings.XResolution
CurrentBuild
Startup
--
cmd /C RMDIR /s/q
cred.dll
clip.dll
un:
POST
DefaultSettings.YResolution
SOFTWARE\Microsoft\Windows\CurrentVersion\RunOnce
cred.dll|clip.dll|
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 10 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | None |
| ZipModifyDate: | 2020:10:31 02:15:50 |
| ZipCRC: | 0x00000000 |
| ZipCompressedSize: | - |
| ZipUncompressedSize: | - |
| ZipFileName: | config/ |
Total processes
176
Monitored processes
31
Malicious processes
16
Suspicious processes
3
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 984 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1100 | "C:\Users\admin\AppData\Roaming\Launcher.exe" | C:\Users\admin\AppData\Roaming\Launcher.exe | IPTV Tools 1.1.6 Premium_Cracked[@hacklabb].exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 1468 | "C:\WINDOWS\system32\regsvr32.EXE" /s /i:INSTALL "C:\Users\admin\AppData\Roaming\Microsoft\SystemCertificates\8TextInputServices.pfx" | C:\Windows\System32\regsvr32.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft(C) Register Server Exit code: 4 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1480 | "C:\Users\admin\AppData\Local\Temp\is-2HAL8.tmp\vbdvbccw.tmp" /SL5="$702BE,696294,301056,C:\Users\admin\AppData\Roaming\vbdvbccw.exe" /VERYSILENT | C:\Users\admin\AppData\Local\Temp\is-2HAL8.tmp\vbdvbccw.tmp | vbdvbccw.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Description: Setup/Uninstall Exit code: 0 Version: 51.1052.0.0 Modules
| |||||||||||||||
| 1660 | "C:\Users\admin\AppData\Local\Temp\is-JOHH1.tmp\vbdvbccw.tmp" /SL5="$D0326,696294,301056,C:\Users\admin\AppData\Roaming\vbdvbccw.exe" | C:\Users\admin\AppData\Local\Temp\is-JOHH1.tmp\vbdvbccw.tmp | vbdvbccw.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Description: Setup/Uninstall Exit code: 1 Version: 51.1052.0.0 Modules
| |||||||||||||||
| 1964 | "C:\Users\admin\AppData\Roaming\vbdvbccw.exe" | C:\Users\admin\AppData\Roaming\vbdvbccw.exe | IPTV Tools 1.1.6 Premium_Cracked[@hacklabb].exe | ||||||||||||
User: admin Company: Integrity Level: MEDIUM Description: Attribute Utility Setup Exit code: 1 Version: Modules
| |||||||||||||||
| 2120 | "C:\Users\admin\AppData\Roaming\systaxpcosx.exe" | C:\Users\admin\AppData\Roaming\systaxpcosx.exe | Launcher.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: System Exit code: 0 Version: 2.0.0.1 Modules
| |||||||||||||||
| 2200 | C:\WINDOWS\system32\svchost.exe -k NetworkService -p -s Dnscache | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2536 | "C:\WINDOWS\system32\regsvr32.EXE" /s /i:INSTALL "C:\Users\admin\AppData\Roaming\Microsoft\SystemCertificates\8TextInputServices.pfx" | C:\Windows\System32\regsvr32.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft(C) Register Server Exit code: 4 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3112 | "powershell" -Command "if (Get-ScheduledTask | Where-Object { $_.Actions.Execute -eq 'regsvr32' -and $_.Actions.Arguments -eq '/s /i:INSTALL \"%APPDATA%\Microsoft\SystemCertificates\8TextInputServices.pfx\"' }) { exit 0 } else { exit 1 }" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | regsvr32.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
23 792
Read events
23 390
Write events
397
Delete events
5
Modification events
| (PID) Process: | (4772) explorer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\SessionInfo\1\ApplicationViewManagement\W32:0000000000050318 |
| Operation: | write | Name: | VirtualDesktop |
Value: 10000000303044563096AFED4A643448A750FA41CFC7F708 | |||
| (PID) Process: | (4772) explorer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\Shell\Bags\1\Desktop |
| Operation: | write | Name: | IconLayouts |
Value: 0000000000000000000000000000000003000100010001000F000000000000002C000000000000003A003A007B00360034003500460046003000340030002D0035003000380031002D0031003000310042002D0039004600300038002D003000300041004100300030003200460039003500340045007D003E002000200000001000000000000000430043006C00650061006E00650072002E006C006E006B003E0020007C0000001500000000000000410064006F006200650020004100630072006F006200610074002E006C006E006B003E0020007C00000016000000000000006D0069006E007500740065006400690076006900730069006F006E002E006A00700067003E002000200000000F00000000000000460069007200650066006F0078002E006C006E006B003E0020007C000000150000000000000047006F006F0067006C00650020004300680072006F006D0065002E006C006E006B003E0020007C000000180000000000000056004C00430020006D006500640069006100200070006C0061007900650072002E006C006E006B003E0020007C00000016000000000000004D006900630072006F0073006F0066007400200045006400670065002E006C006E006B003E0020007C0000001A00000000000000650078007400650072006E0061006C0073007400610074006900730074006900630073002E006A00700067003E002000200000001300000000000000660069006E0061006C006C0079006200610063006B002E007200740066003E002000200000001900000000000000700068006F006E00650073007000750062006C00690063006100740069006F006E002E0070006E0067003E002000200000000F0000000000000073006100740074006F006F006C002E007200740066003E002000200000001700000000000000730074006F007200690065007300660075006E006300740069006F006E002E0070006E0067003E002000200000000D00000000000000790074007200750065002E007200740066003E0020002000000033000000000000004900500054005600200054006F006F006C007300200031002E0031002E00360020005000720065006D00690075006D005F0043007200610063006B00650064005B0040006800610063006B006C006100620062005D002E007A00690070003E00200020000000010000000000000002000100000000000000000001000000000000000200010000000000000000001100000006000000010000000F00000000000000000000000000000000000000803F0000004008000000803F000040400900000000000000404003000000803F000080400A000000803F0000A0400B0000000040000000000C00000000400000803F0D00000000000000803F01000000000000000040020000000000000080400400000000000000A04005000000803F0000000006000000803F0000803F070000000040000000400E00 | |||
| (PID) Process: | (4772) explorer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\Shell\Bags\1\Desktop |
| Operation: | write | Name: | IconNameVersion |
Value: 1 | |||
| (PID) Process: | (4772) explorer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\OneDrive\Accounts |
| Operation: | write | Name: | LastUpdate |
Value: B10F6B6800000000 | |||
| (PID) Process: | (5480) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (5480) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (5480) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (5480) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (5480) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (5480) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\IPTV Tools 1.1.6 Premium_Cracked[@hacklabb].zip | |||
Executable files
25
Suspicious files
14
Text files
16
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4772 | explorer.exe | C:\Users\admin\AppData\Local\Microsoft\PenWorkspace\DiscoverCacheData.dat | binary | |
MD5:E49C56350AEDF784BFE00E444B879672 | SHA256:A8BD235303668981563DFB5AAE338CB802817C4060E2C199B7C84901D57B7E1E | |||
| 5480 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa5480.14760\MetroFramework.dll | executable | |
MD5:34EA7F7D66563F724318E322FF08F4DB | SHA256:C2C12D31B4844E29DE31594FC9632A372A553631DE0A0A04C8AF91668E37CF49 | |||
| 5480 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa5480.14760\IPTV Tools 1.1.6 Premium_Cracked[@hacklabb].exe | executable | |
MD5:56638FC759924EFA6068FEEBAAFE0918 | SHA256:536CC2842D4121B16B585F11DB2A0641F85EC8033CBE77F480D12EF3A54F40DC | |||
| 5480 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa5480.14760\AxInterop.AXVLC.dll | executable | |
MD5:12695F884550E0D29493B69D6F54F3DC | SHA256:4BB3582746683A09C49BC462AE5AA879E12AD4E78AA9324EFDB1F9260D99B476 | |||
| 6652 | IPTV Tools 1.1.6 Premium_Cracked[@hacklabb].exe | C:\Users\admin\AppData\Roaming\vbdvbccw.exe | executable | |
MD5:5235983724705B359C8248A6D84C416D | SHA256:198F737D5A64D2A44FAE287C50929D208E2D4CEE9A77C1605E56F7D04799ED42 | |||
| 6652 | IPTV Tools 1.1.6 Premium_Cracked[@hacklabb].exe | C:\Users\admin\AppData\Roaming\Launcher.exe | executable | |
MD5:87D1949CEFFBA9F68FA73E2A1EF768DA | SHA256:B239DA042DBB23C0EDAA6F1CDB53C95F80417969D6F6CAFF3926901F4275DAF7 | |||
| 6652 | IPTV Tools 1.1.6 Premium_Cracked[@hacklabb].exe | C:\Users\admin\AppData\Roaming\gfgfrxr.exe | executable | |
MD5:52B1EAA4E45665A7BC3EF22EED6CC099 | SHA256:C4E57BA5280096EC6C499A8E03B28428352D9270CDB889D745DBA2418F3FAF19 | |||
| 5480 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa5480.14760\IPTV Tools 1.1.6 Premium.exe.config | xml | |
MD5:81269737FFD0833E696BB479D14D0578 | SHA256:9D430AB95568B65CE6C8E8E4C58E73C6D595DD07ACDC87921F09979B1394063E | |||
| 5480 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa5480.14760\images\pause.png | image | |
MD5:A97A4FD94583E624FD7E17D74F98905F | SHA256:80EB2C6FFE735302A4E9062984B8F82DAFA904B2B8EAC5D735E82B7F8AAA4D93 | |||
| 5480 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa5480.14760\images\play.png | image | |
MD5:706A7F496F0225ED5FE2C2CB4923132E | SHA256:EA9D4CE8BB78E3C616C1406A340023C3D0F528E66BD65B8F3637EC6019AC6A31 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
10
TCP/UDP connections
64
DNS requests
27
Threats
4
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1268 | svchost.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 23.216.77.6:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
6808 | WerFault.exe | GET | 200 | 23.216.77.6:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
6808 | WerFault.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
2552 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
6256 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
6256 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
2940 | svchost.exe | GET | 200 | 23.209.209.135:80 | http://x1.c.lencr.org/ | unknown | — | — | whitelisted |
3908 | backgroundTaskHost.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEA77flR%2B3w%2FxBpruV2lte6A%3D | unknown | — | — | whitelisted |
1356 | svchost.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
5944 | MoUsoCoreWorker.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1268 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
2228 | RUXIMICS.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4772 | explorer.exe | 185.81.68.147:80 | — | Chang Way Technologies Co. Limited | RU | malicious |
4772 | explorer.exe | 92.255.57.100:80 | — | Chang Way Technologies Co. Limited | HK | unknown |
3720 | yutuytt.exe | 92.255.57.100:80 | — | Chang Way Technologies Co. Limited | HK | unknown |
1268 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1268 | svchost.exe | 23.216.77.6:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
watson.events.data.microsoft.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
nexusrules.officeapps.live.com |
| whitelisted |
diamotrix.world |
| malicious |
client.wns.windows.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2200 | svchost.exe | Domain Observed Used for C2 Detected | ET MALWARE Diamotrix Clipper Domain (diamotrix .world) in DNS Lookup |
2200 | svchost.exe | Domain Observed Used for C2 Detected | ET MALWARE Diamotrix Clipper Domain (diamotrix .world) in DNS Lookup |
2200 | svchost.exe | Domain Observed Used for C2 Detected | ET MALWARE Diamotrix Clipper Domain (diamotrix .world) in DNS Lookup |
2200 | svchost.exe | Domain Observed Used for C2 Detected | ET MALWARE Diamotrix Clipper Domain (diamotrix .world) in DNS Lookup |