| File name: | (大å¦æ ¡é¨çæ¸ çº¯ç¾å¥³è¢«ç·åç©å¼ä¸ä½ï¼ç²å«©èä¸æ¹¿ååçãç«ç¶æ¯ä¸ªç½èï¼å®æ´è§é¢_MP4).exe |
| Full analysis: | https://app.any.run/tasks/1c70431b-7543-44aa-aff2-6723d368f315 |
| Verdict: | Malicious activity |
| Threats: | Gh0st RAT is a malware with advanced trojan functionality that enables attackers to establish full control over the victim’s system. The spying capabilities of Gh0st RAT made it a go-to tool for numerous criminal groups in high-profile attacks against government and corporate organizations. The most common vector of attack involving this malware begins with spam and phishing emails. |
| Analysis date: | March 15, 2025, 03:08:53 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, 4 sections |
| MD5: | 0BC35438A436C6CC1E69C43F8A276E08 |
| SHA1: | ACAAA2F39A5DEB7E9B78A9E28F9702E1D355D9E3 |
| SHA256: | A4D6D4C90D5E120323A4686C8A521D83123016F6952D6AF78FAC0A45822777FB |
| SSDEEP: | 12288:y+U5fL2PX55B2VbWGhyZKdJyzGFCwA/qT4:y+U5fKPX55B2VbWGhx6GFCxqT |
MALICIOUS
GH0ST has been detected (SURICATA)
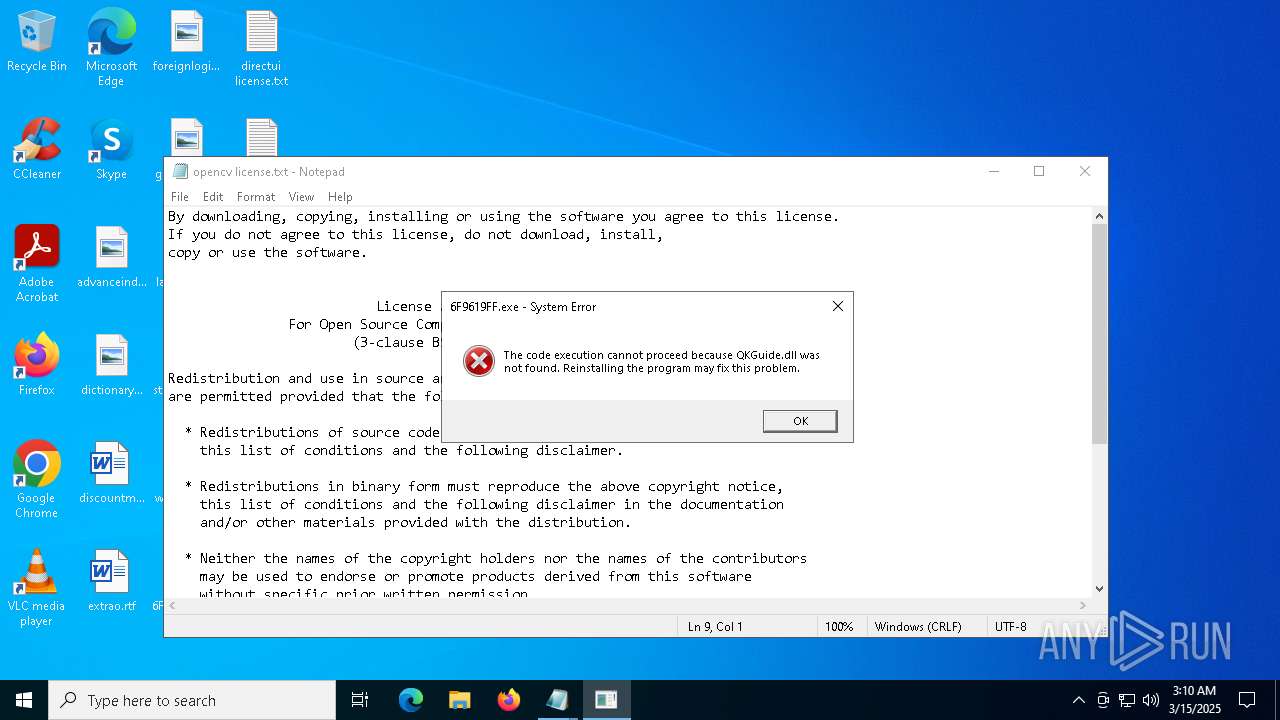
- 6F9619FF.exe (PID: 6248)
SUSPICIOUS
Executable content was dropped or overwritten
- 1c70431b-7543-44aa-aff2-6723d368f315.exe (PID: 6724)
Process drops legitimate windows executable
- 1c70431b-7543-44aa-aff2-6723d368f315.exe (PID: 6724)
The process drops C-runtime libraries
- 1c70431b-7543-44aa-aff2-6723d368f315.exe (PID: 6724)
Reads security settings of Internet Explorer
- 1c70431b-7543-44aa-aff2-6723d368f315.exe (PID: 6724)
Likely accesses (executes) a file from the Public directory
- 6F9619FF.exe (PID: 3240)
- 6F9619FF.exe (PID: 6248)
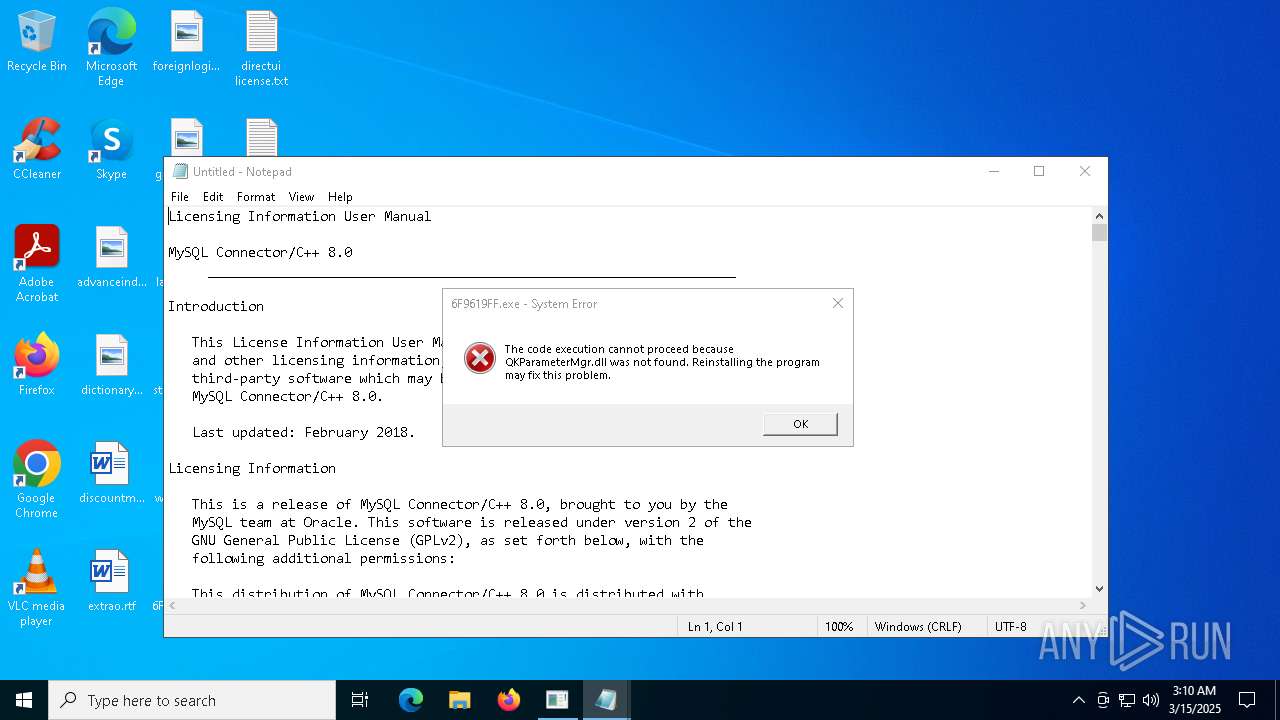
Executes application which crashes
- 1c70431b-7543-44aa-aff2-6723d368f315.exe (PID: 6724)
Contacting a server suspected of hosting an CnC
- 6F9619FF.exe (PID: 6248)
Connects to unusual port
- 6F9619FF.exe (PID: 6248)
INFO
Reads the computer name
- 1c70431b-7543-44aa-aff2-6723d368f315.exe (PID: 6724)
- 6F9619FF.exe (PID: 6248)
The sample compiled with chinese language support
- 1c70431b-7543-44aa-aff2-6723d368f315.exe (PID: 6724)
Reads security settings of Internet Explorer
- BackgroundTransferHost.exe (PID: 1348)
- BackgroundTransferHost.exe (PID: 1328)
- BackgroundTransferHost.exe (PID: 6372)
- BackgroundTransferHost.exe (PID: 6080)
- BackgroundTransferHost.exe (PID: 5552)
- notepad.exe (PID: 3124)
- notepad.exe (PID: 1600)
- notepad.exe (PID: 5864)
- notepad.exe (PID: 6044)
- notepad.exe (PID: 4572)
- notepad.exe (PID: 5512)
Checks proxy server information
- BackgroundTransferHost.exe (PID: 1328)
Checks supported languages
- 1c70431b-7543-44aa-aff2-6723d368f315.exe (PID: 6724)
- 6F9619FF.exe (PID: 6248)
Reads the software policy settings
- BackgroundTransferHost.exe (PID: 1328)
- slui.exe (PID: 6972)
Creates files or folders in the user directory
- BackgroundTransferHost.exe (PID: 1328)
- WerFault.exe (PID: 6584)
- WerFault.exe (PID: 2240)
The sample compiled with english language support
- 1c70431b-7543-44aa-aff2-6723d368f315.exe (PID: 6724)
Process checks computer location settings
- 1c70431b-7543-44aa-aff2-6723d368f315.exe (PID: 6724)
Reads the machine GUID from the registry
- 6F9619FF.exe (PID: 6248)
Manual execution by a user
- notepad.exe (PID: 1600)
- 6F9619FF.exe (PID: 1616)
- 6F9619FF.exe (PID: 1012)
- notepad.exe (PID: 3124)
- notepad.exe (PID: 5512)
- OpenWith.exe (PID: 2140)
- notepad.exe (PID: 5864)
- notepad.exe (PID: 4572)
- notepad.exe (PID: 6044)
Reads CPU info
- 6F9619FF.exe (PID: 6248)
Reads Microsoft Office registry keys
- OpenWith.exe (PID: 2140)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable MS Visual C++ (generic) (35.8) |
|---|---|---|
| .exe | | | Win64 Executable (generic) (31.7) |
| .scr | | | Windows screen saver (15) |
| .dll | | | Win32 Dynamic Link Library (generic) (7.5) |
| .exe | | | Win32 Executable (generic) (5.1) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2025:03:12 12:48:07+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 6 |
| CodeSize: | 286720 |
| InitializedDataSize: | 81920 |
| UninitializedDataSize: | - |
| EntryPoint: | 0xebd4 |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 1.0.16.4 |
| ProductVersionNumber: | 1.0.16.4 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Chinese (Simplified) |
| CharacterSet: | ASCII |
| Comments: | 此安装程序由 Inno Setup 构建。 |
| CompanyName: | www.moage.com |
| FileDescription: | 平板刷机王 |
| FileVersion: | 1.0.16.4 |
| LegalCopyright: | 版权所有 © 2012 www.moage.com |
| ProductName: | 平板刷机王 |
| ProductVersion: | 1.0.16.4 |
Total processes
161
Monitored processes
22
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1012 | "C:\Users\admin\Desktop\6F9619FF.exe" | C:\Users\admin\Desktop\6F9619FF.exe | explorer.exe | ||||||||||||
User: admin Company: 巧课教育科技(深圳)有限公司 Integrity Level: HIGH Description: 巧课客户端 Version: 2.0.0.0 Modules
| |||||||||||||||
| 1328 | "BackgroundTransferHost.exe" -ServerName:BackgroundTransferHost.1 | C:\Windows\System32\BackgroundTransferHost.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Download/Upload Host Exit code: 1 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1348 | "BackgroundTransferHost.exe" -ServerName:BackgroundTransferHost.1 | C:\Windows\System32\BackgroundTransferHost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Download/Upload Host Exit code: 1 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1600 | "C:\WINDOWS\system32\NOTEPAD.EXE" "C:\Users\admin\Desktop\mysql connector.txt" | C:\Windows\System32\notepad.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1616 | "C:\Users\admin\Desktop\6F9619FF.exe" | C:\Users\admin\Desktop\6F9619FF.exe | — | explorer.exe | |||||||||||
User: admin Company: 巧课教育科技(深圳)有限公司 Integrity Level: MEDIUM Description: 巧课客户端 Exit code: 3221226540 Version: 2.0.0.0 Modules
| |||||||||||||||
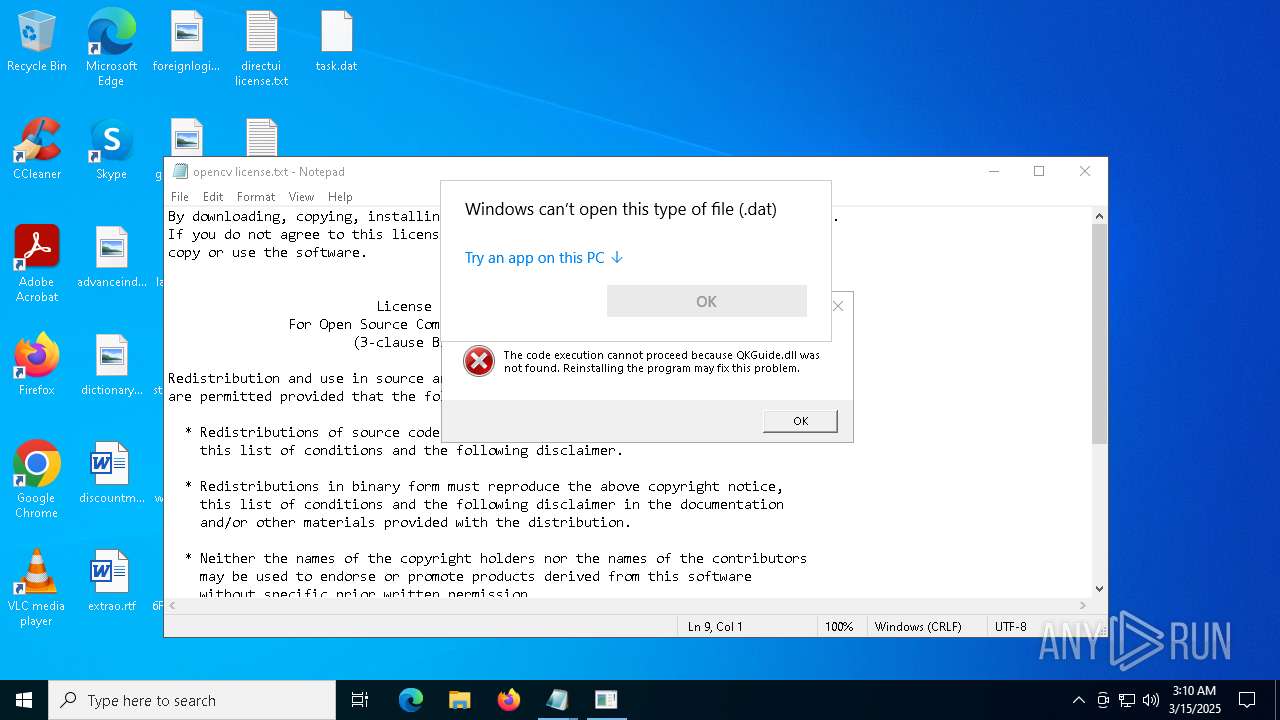
| 2140 | "C:\WINDOWS\System32\OpenWith.exe" C:\Users\admin\Desktop\task.dat | C:\Windows\System32\OpenWith.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Pick an app Exit code: 2147943623 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2240 | C:\WINDOWS\SysWOW64\WerFault.exe -u -p 6724 -s 1412 | C:\Windows\SysWOW64\WerFault.exe | — | 1c70431b-7543-44aa-aff2-6723d368f315.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Problem Reporting Exit code: 0 Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3124 | "C:\WINDOWS\system32\NOTEPAD.EXE" "C:\Users\admin\Desktop\directui license.txt" | C:\Windows\System32\notepad.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3240 | "C:\Users\Public\00C04FC964FF\6F9619FF.exe" | C:\Users\Public\00C04FC964FF\6F9619FF.exe | — | 1c70431b-7543-44aa-aff2-6723d368f315.exe | |||||||||||
User: admin Company: 巧课教育科技(深圳)有限公司 Integrity Level: MEDIUM Description: 巧课客户端 Exit code: 3221226540 Version: 2.0.0.0 Modules
| |||||||||||||||
| 4572 | "C:\WINDOWS\system32\NOTEPAD.EXE" "C:\Users\admin\Desktop\opencv license.txt" | C:\Windows\System32\notepad.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
7 843
Read events
7 828
Write events
15
Delete events
0
Modification events
| (PID) Process: | (1348) BackgroundTransferHost.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\CurrentVersion\AppContainer\Storage\microsoft.windows.contentdeliverymanager_cw5n1h2txyewy\Internet Settings\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (1348) BackgroundTransferHost.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\CurrentVersion\AppContainer\Storage\microsoft.windows.contentdeliverymanager_cw5n1h2txyewy\Internet Settings\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (1348) BackgroundTransferHost.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\CurrentVersion\AppContainer\Storage\microsoft.windows.contentdeliverymanager_cw5n1h2txyewy\Internet Settings\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (1328) BackgroundTransferHost.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\CurrentVersion\AppContainer\Storage\microsoft.windows.contentdeliverymanager_cw5n1h2txyewy\Internet Settings\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (1328) BackgroundTransferHost.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\CurrentVersion\AppContainer\Storage\microsoft.windows.contentdeliverymanager_cw5n1h2txyewy\Internet Settings\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (1328) BackgroundTransferHost.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\CurrentVersion\AppContainer\Storage\microsoft.windows.contentdeliverymanager_cw5n1h2txyewy\Internet Settings\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (6080) BackgroundTransferHost.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\CurrentVersion\AppContainer\Storage\microsoft.windows.contentdeliverymanager_cw5n1h2txyewy\Internet Settings\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (6080) BackgroundTransferHost.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\CurrentVersion\AppContainer\Storage\microsoft.windows.contentdeliverymanager_cw5n1h2txyewy\Internet Settings\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (6080) BackgroundTransferHost.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\CurrentVersion\AppContainer\Storage\microsoft.windows.contentdeliverymanager_cw5n1h2txyewy\Internet Settings\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (5552) BackgroundTransferHost.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\CurrentVersion\AppContainer\Storage\microsoft.windows.contentdeliverymanager_cw5n1h2txyewy\Internet Settings\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
Executable files
45
Suspicious files
13
Text files
11
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1328 | BackgroundTransferHost.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.ContentDeliveryManager_cw5n1h2txyewy\AC\BackgroundTransferApi\81596368-018e-4a12-9d32-aee3cec7ce7f.down_data | — | |
MD5:— | SHA256:— | |||
| 6724 | 1c70431b-7543-44aa-aff2-6723d368f315.exe | C:\Users\Public\ykhhdg.dat | — | |
MD5:— | SHA256:— | |||
| 1328 | BackgroundTransferHost.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.ContentDeliveryManager_cw5n1h2txyewy\AC\Microsoft\CryptnetUrlCache\MetaData\26C212D9399727259664BDFCA073966E_F9F7D6A7ECE73106D2A8C63168CDA10D | binary | |
MD5:B215F2A815D78927A5C3FE4ED61B0491 | SHA256:BD0A7453E7B6803784393EA71F0360F5168E9A82B22D6617B4F55C4AAA9F79FC | |||
| 1328 | BackgroundTransferHost.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.ContentDeliveryManager_cw5n1h2txyewy\AC\BackgroundTransferApi\81596368-018e-4a12-9d32-aee3cec7ce7f.2921230a-37b0-48d8-85cb-4b2c01290738.down_meta | binary | |
MD5:E4A98C4D72F4A55EF8CCC48634C3B035 | SHA256:C36A04DF27953BC085C3942AAD854B6F4749090608428C017640BB4438FA2FEC | |||
| 1328 | BackgroundTransferHost.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.ContentDeliveryManager_cw5n1h2txyewy\AC\BackgroundTransferApi\c7fe2742-8df1-4f6d-956d-d4a44557506c.2921230a-37b0-48d8-85cb-4b2c01290738.down_meta | binary | |
MD5:E4A98C4D72F4A55EF8CCC48634C3B035 | SHA256:C36A04DF27953BC085C3942AAD854B6F4749090608428C017640BB4438FA2FEC | |||
| 1328 | BackgroundTransferHost.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.ContentDeliveryManager_cw5n1h2txyewy\AC\BackgroundTransferApi\c7fe2742-8df1-4f6d-956d-d4a44557506c.up_meta_secure | binary | |
MD5:9C87BB28799054DF7242D562C5BB600C | SHA256:3B272A2B1297E40CACF6289DF82A21D5706ED679CD8F7811127D6CEDE198D8C8 | |||
| 6724 | 1c70431b-7543-44aa-aff2-6723d368f315.exe | C:\Users\Public\00C04FC964FF\api-ms-win-core-file-l2-1-0.dll | executable | |
MD5:3F224766FE9B090333FDB43D5A22F9EA | SHA256:AE5E73416EB64BC18249ACE99F6847024ECEEA7CE9C343696C84196460F3A357 | |||
| 6724 | 1c70431b-7543-44aa-aff2-6723d368f315.exe | C:\Users\Public\00C04FC964FF\api-ms-win-core-localization-l1-2-0.dll | executable | |
MD5:23BD405A6CFD1E38C74C5150EEC28D0A | SHA256:A7FA48DE6C06666B80184AFEE7E544C258E0FB11399AB3FE47D4E74667779F41 | |||
| 6724 | 1c70431b-7543-44aa-aff2-6723d368f315.exe | C:\Users\Public\00C04FC964FF\6F9619FF.exe | executable | |
MD5:B575CFEFD5C7B14F4743EF2AD74B2736 | SHA256:A38708DA0DB2003A1D14ED1E9D45A9ECB30A6294D472692F804FFB0CEA70334B | |||
| 6724 | 1c70431b-7543-44aa-aff2-6723d368f315.exe | C:\Users\Public\00C04FC964FF\api-ms-win-core-processthreads-l1-1-1.dll | executable | |
MD5:95C5B49AF7F2C7D3CD0BC14B1E9EFACB | SHA256:FF9B51AFF7FBEC8D7FE5CC478B12492A59B38B068DC2B518324173BB3179A0E1 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
7
TCP/UDP connections
30
DNS requests
21
Threats
1
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
6724 | 1c70431b-7543-44aa-aff2-6723d368f315.exe | GET | 200 | 27.124.34.85:80 | http://download.linuxroot.site/download/2825.dat | unknown | — | — | unknown |
— | — | GET | 200 | 23.216.77.18:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
1324 | backgroundTaskHost.exe | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
1328 | BackgroundTransferHost.exe | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
5988 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
5988 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2104 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 23.216.77.18:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
6724 | 1c70431b-7543-44aa-aff2-6723d368f315.exe | 27.124.34.85:80 | download.linuxroot.site | BGPNET Global ASN | SG | unknown |
3216 | svchost.exe | 40.113.103.199:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6544 | svchost.exe | 20.190.160.131:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6544 | svchost.exe | 184.30.131.245:80 | ocsp.digicert.com | AKAMAI-AS | US | whitelisted |
2112 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
download.linuxroot.site |
| unknown |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
arc.msn.com |
| whitelisted |
www.bing.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
6248 | 6F9619FF.exe | Malware Command and Control Activity Detected | REMOTE [ANY.RUN] Gh0stRAT TCP Packet |