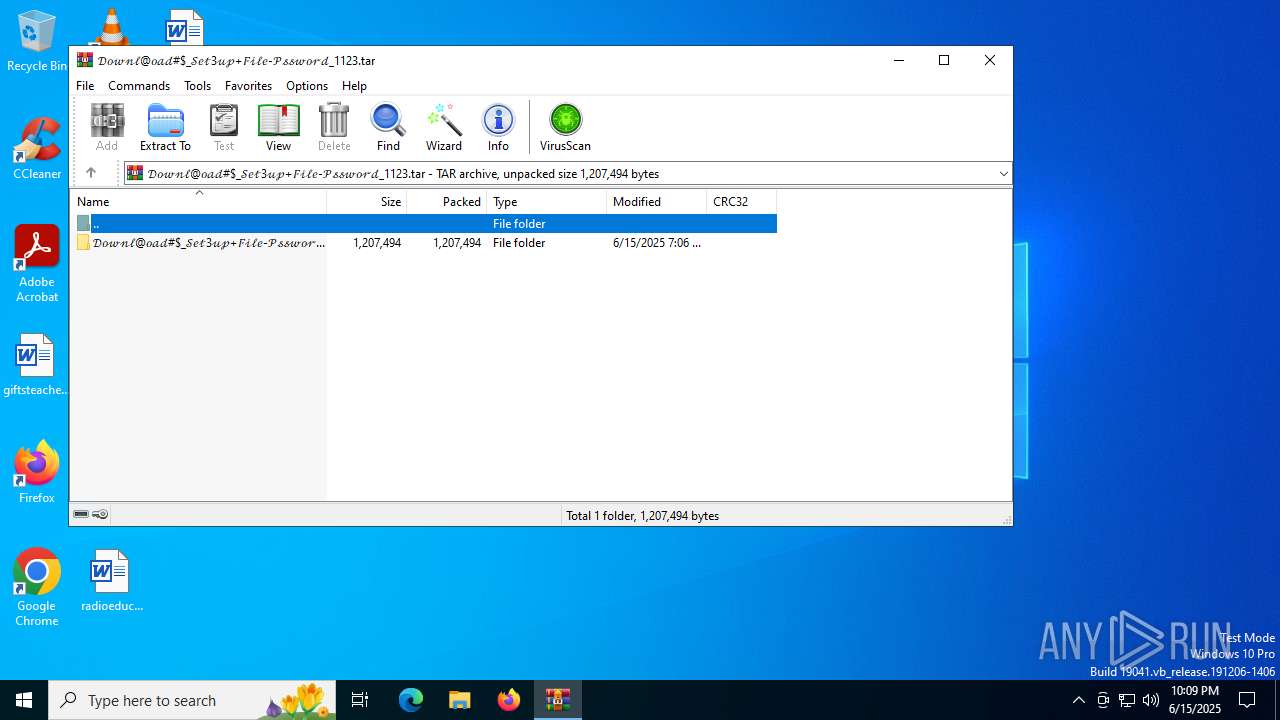
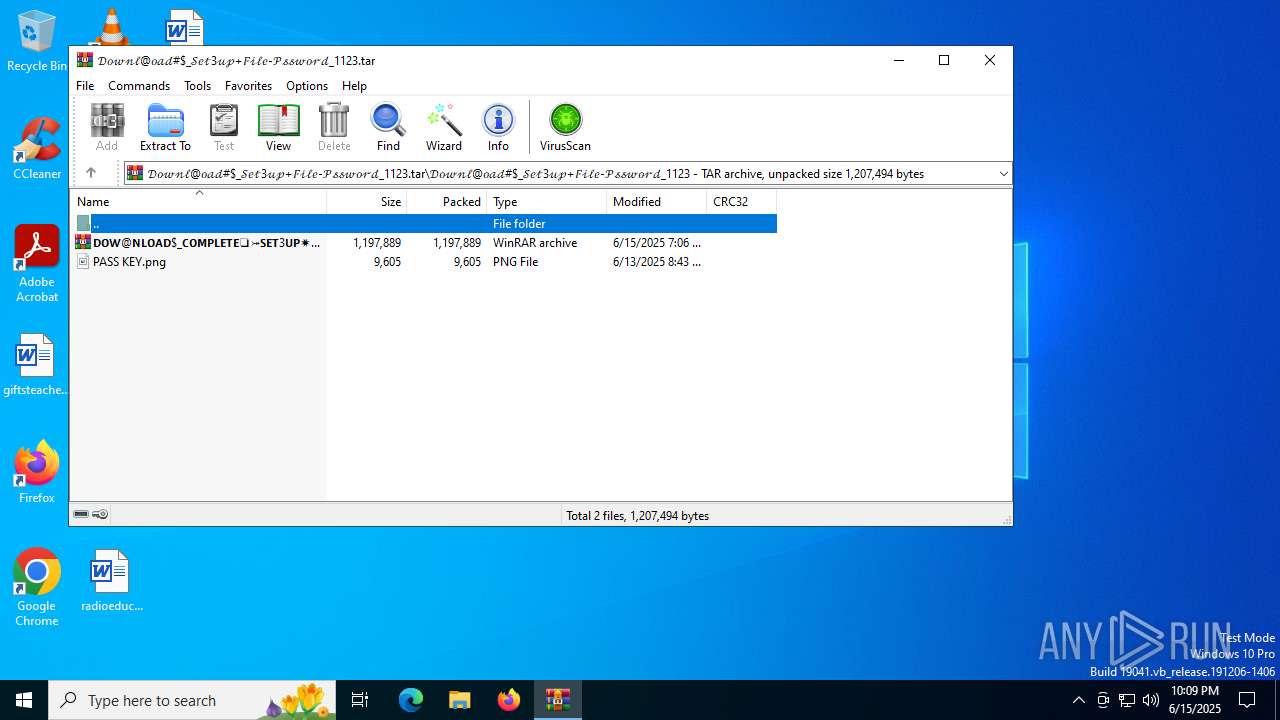
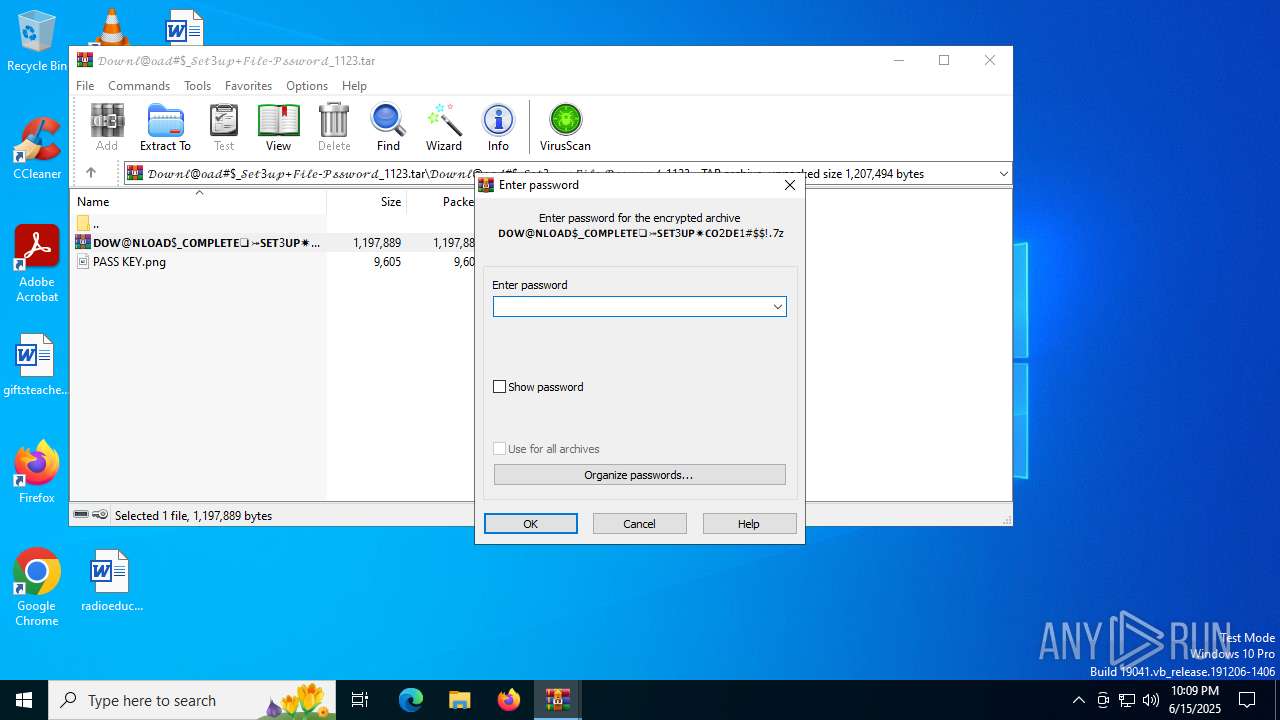
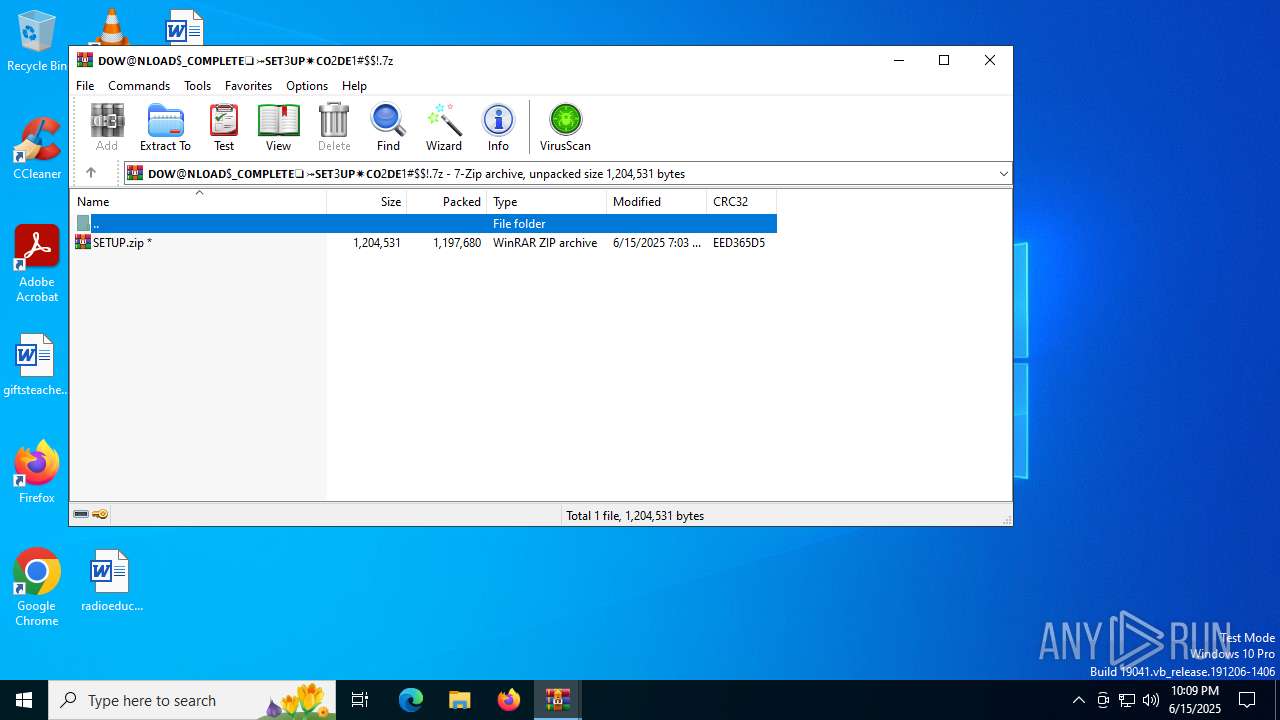
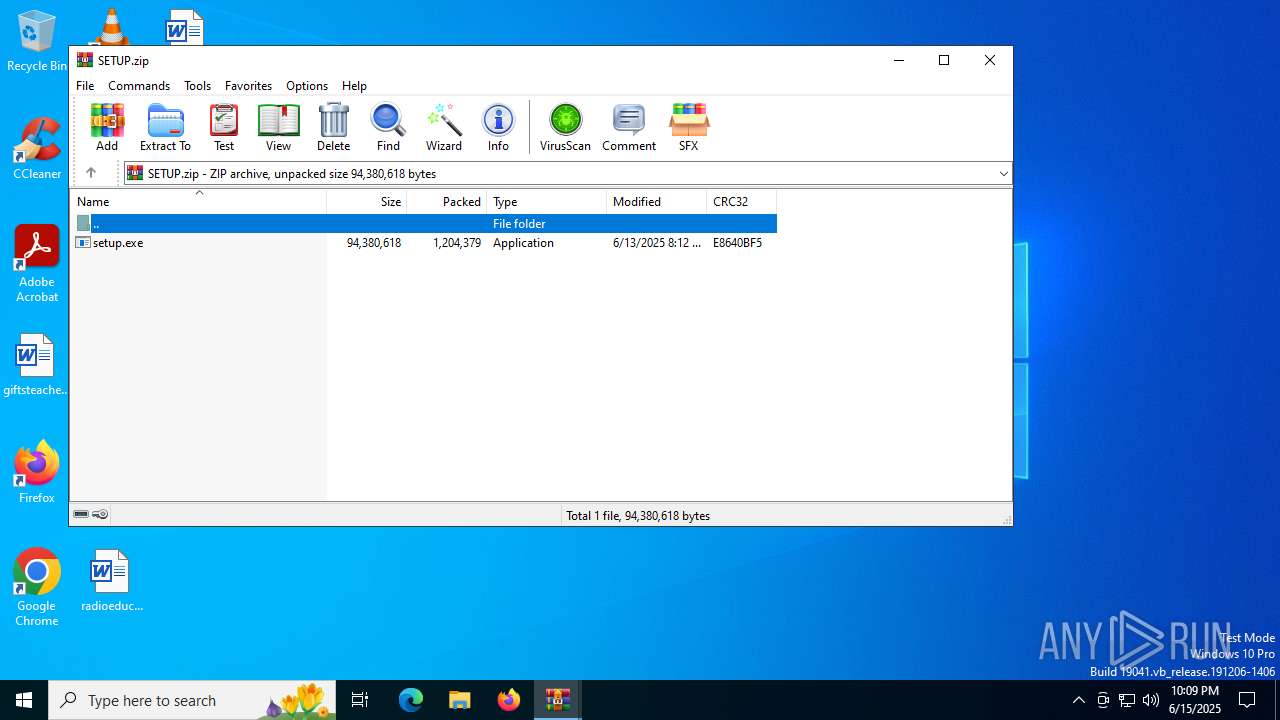
| File name: | 𝒟𝑜𝓌𝓃𝓁@𝑜𝒶𝒹#$_𝒮𝑒𝓉3𝓊𝓅+𝐹𝒾𝓁𝑒-𝒫𝓈𝓈𝓌𝑜𝓇𝒹_1123.tar |
| Full analysis: | https://app.any.run/tasks/51e7c96d-786c-4048-aa38-5ba75a06aecc |
| Verdict: | Malicious activity |
| Threats: | Lumma is an information stealer, developed using the C programming language. It is offered for sale as a malware-as-a-service, with several plans available. It usually targets cryptocurrency wallets, login credentials, and other sensitive information on a compromised system. The malicious software regularly gets updates that improve and expand its functionality, making it a serious stealer threat. |
| Analysis date: | June 15, 2025, 22:09:37 |
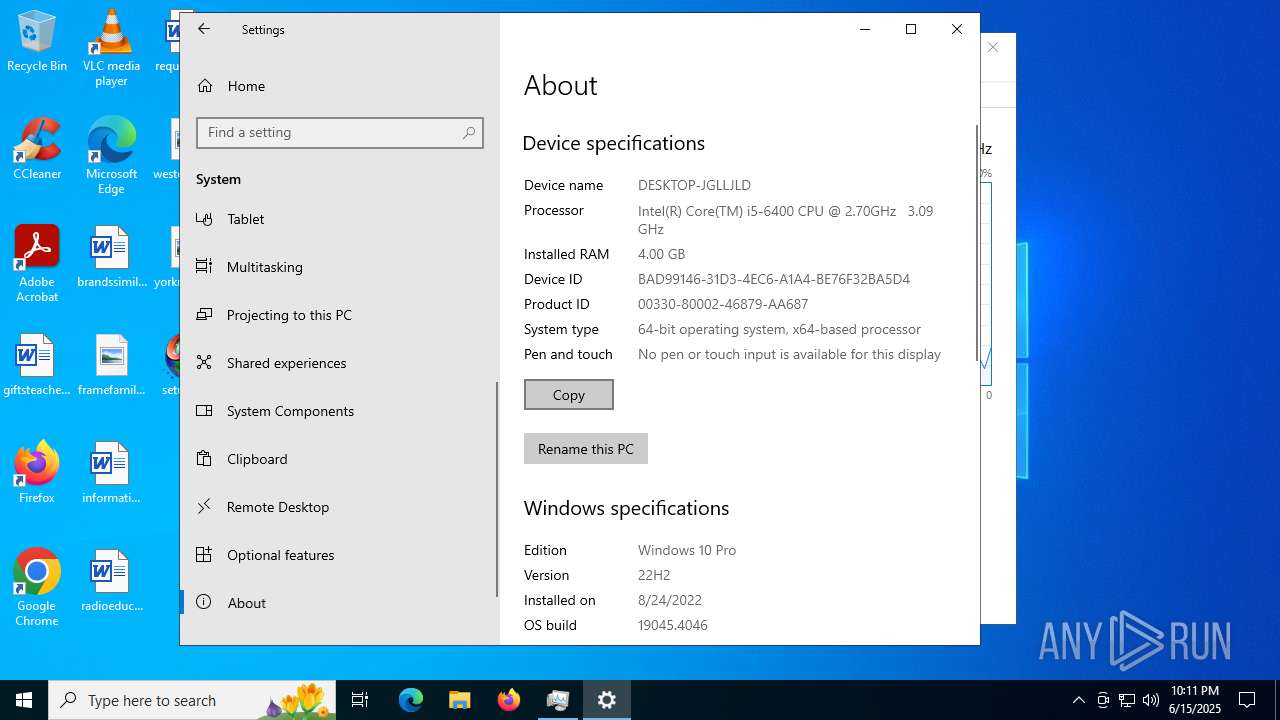
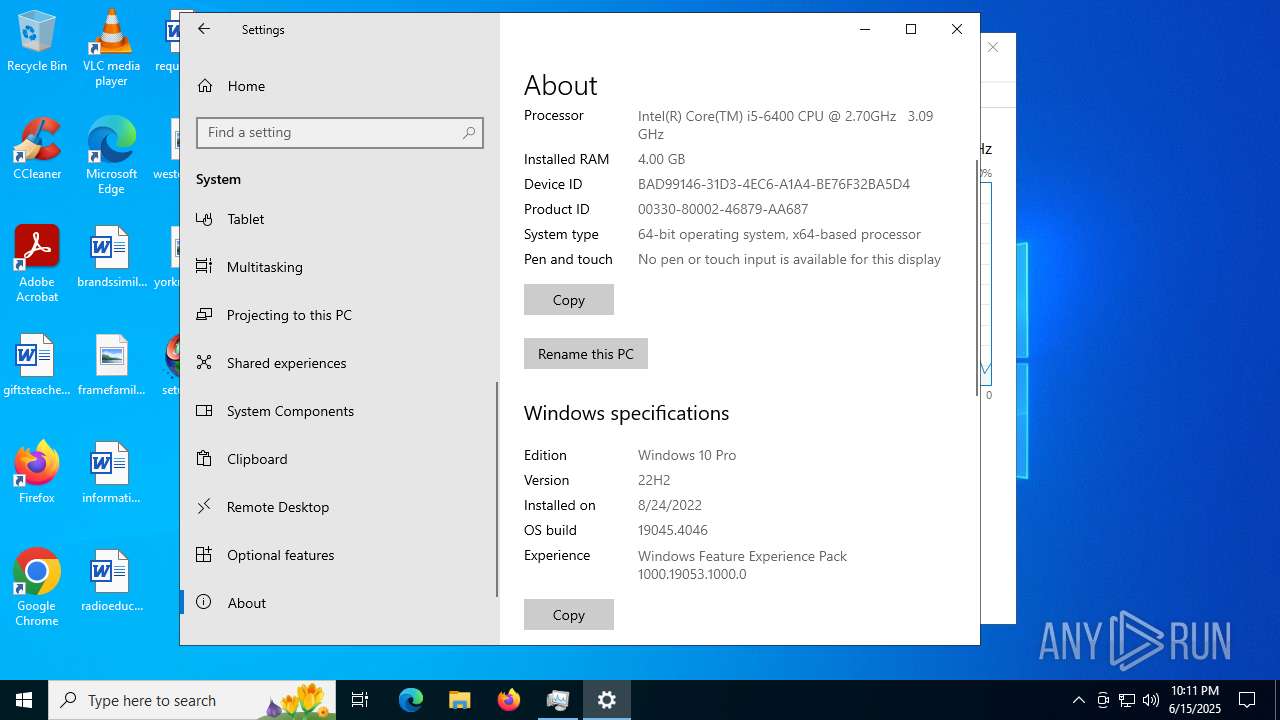
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-tar |
| File info: | POSIX tar archive (GNU) |
| MD5: | 389EF8E3731241DB0F2088564BAC9ECD |
| SHA1: | 73588BF1EAB137C84164E59D0D251D4F5B023AAF |
| SHA256: | A4429FCF47807BAA3A3682782E64B757FDF356A3D8E13570053D07F69D4F70F4 |
| SSDEEP: | 49152:QzDwdsYbpZlVPRSESXr4fe5pfJyqDRiAgP+gL/VzZK1PjdF1aX65iTM5N7/Ak611:QzDKDHPiraoHyIi1PPL/Vt0sX65V5N7Q |
MALICIOUS
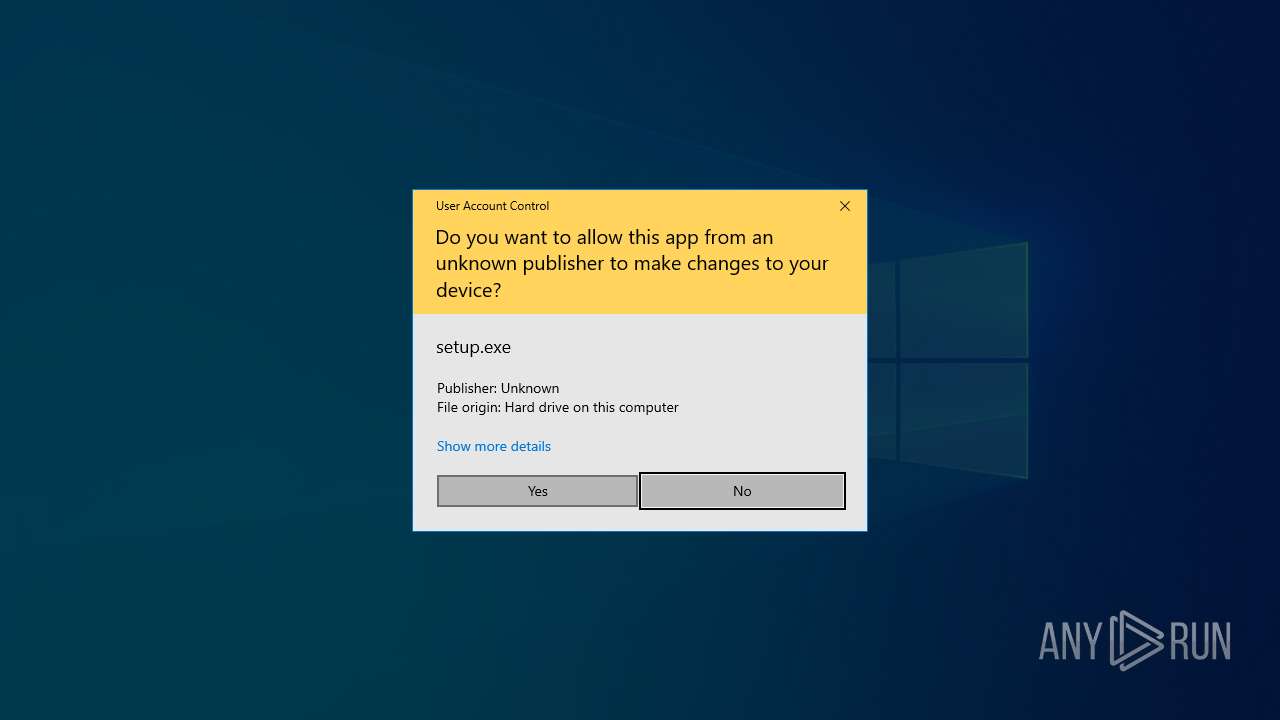
Executing a file with an untrusted certificate
- setup.exe (PID: 3908)
- setup.exe (PID: 1268)
AutoIt loader has been detected (YARA)
- Word.com (PID: 2288)
- Word.com (PID: 5116)
Connects to the CnC server
- svchost.exe (PID: 2200)
LUMMA has been detected (SURICATA)
- svchost.exe (PID: 2200)
- Word.com (PID: 2288)
- Word.com (PID: 5116)
SUSPICIOUS
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 3948)
- WinRAR.exe (PID: 2528)
- setup.exe (PID: 3908)
Application launched itself
- WinRAR.exe (PID: 2528)
- WinRAR.exe (PID: 3948)
Starts CMD.EXE for commands execution
- setup.exe (PID: 3908)
- setup.exe (PID: 1268)
Executing commands from a ".bat" file
- setup.exe (PID: 3908)
- setup.exe (PID: 1268)
Get information on the list of running processes
- cmd.exe (PID: 1816)
- cmd.exe (PID: 3608)
Using 'findstr.exe' to search for text patterns in files and output
- cmd.exe (PID: 1816)
- cmd.exe (PID: 3608)
The executable file from the user directory is run by the CMD process
- Word.com (PID: 2288)
- Word.com (PID: 5116)
Starts application with an unusual extension
- cmd.exe (PID: 1816)
- cmd.exe (PID: 3608)
Starts the AutoIt3 executable file
- cmd.exe (PID: 1816)
- cmd.exe (PID: 3608)
There is functionality for taking screenshot (YARA)
- setup.exe (PID: 3908)
- Word.com (PID: 2288)
- setup.exe (PID: 1268)
- Word.com (PID: 5116)
Contacting a server suspected of hosting an CnC
- svchost.exe (PID: 2200)
- Word.com (PID: 2288)
- Word.com (PID: 5116)
INFO
Checks supported languages
- setup.exe (PID: 3908)
- extrac32.exe (PID: 6256)
- Word.com (PID: 2288)
Reads the computer name
- setup.exe (PID: 3908)
- extrac32.exe (PID: 6256)
- Word.com (PID: 2288)
Manual execution by a user
- setup.exe (PID: 3908)
- Taskmgr.exe (PID: 4216)
- Taskmgr.exe (PID: 4084)
- msinfo32.exe (PID: 4172)
- setup.exe (PID: 1268)
Create files in a temporary directory
- setup.exe (PID: 3908)
- extrac32.exe (PID: 6256)
Process checks computer location settings
- setup.exe (PID: 3908)
Reads mouse settings
- Word.com (PID: 2288)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .tar | | | TAR - Tape ARchive (100) |
|---|
Total processes
174
Monitored processes
31
Malicious processes
7
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 316 | findstr /I "opssvc wrsa" | C:\Windows\SysWOW64\findstr.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Find String (QGREP) Utility Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 640 | findstr /I "opssvc wrsa" | C:\Windows\SysWOW64\findstr.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Find String (QGREP) Utility Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 984 | findstr "bdservicehost SophosHealth AvastUI AVGUI nsWscSvc ekrn" | C:\Windows\SysWOW64\findstr.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Find String (QGREP) Utility Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1036 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1100 | tasklist | C:\Windows\SysWOW64\tasklist.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Lists the current running tasks Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1128 | tasklist | C:\Windows\SysWOW64\tasklist.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Lists the current running tasks Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1268 | "C:\Users\admin\Desktop\setup.exe" | C:\Users\admin\Desktop\setup.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 1644 | tasklist | C:\Windows\SysWOW64\tasklist.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Lists the current running tasks Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1816 | "C:\WINDOWS\system32\cmd.exe" /c copy About.xll About.xll.bat & About.xll.bat | C:\Windows\SysWOW64\cmd.exe | — | setup.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 1 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2200 | C:\WINDOWS\system32\svchost.exe -k NetworkService -p -s Dnscache | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
9 749
Read events
9 692
Write events
56
Delete events
1
Modification events
| (PID) Process: | (2528) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (2528) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (2528) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (2528) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Downloads\𝒟𝑜𝓌𝓃𝓁@𝑜𝒶𝒹#$_𝒮𝑒𝓉3𝓊𝓅+𝐹𝒾𝓁𝑒-𝒫𝓈𝓈𝓌𝑜𝓇𝒹_1123.tar | |||
| (PID) Process: | (2528) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (2528) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (2528) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (2528) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (3948) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface |
| Operation: | write | Name: | ShowPassword |
Value: 0 | |||
| (PID) Process: | (3948) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
Executable files
0
Suspicious files
22
Text files
4
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3800 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3800.20782\setup.exe | — | |
MD5:— | SHA256:— | |||
| 3948 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DIb3948.20497\SETUP.zip | compressed | |
MD5:80721A621DB4E82DC50074EA2FB9B800 | SHA256:A8ADEC359F6D5C7BC417E71C76948431F8193D03703D106D5541D1633C66D367 | |||
| 3908 | setup.exe | C:\Users\admin\AppData\Local\Temp\Cow.xll | compressed | |
MD5:D7AD543584A702753965100A657BA587 | SHA256:CE70BF53234E2B579CFA8BCCC4CF5BFD4A509277AE6BE7D3A7D14DDF339AB7BD | |||
| 2528 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DIa2528.19973\𝗗𝗢𝗪@𝗡𝗟𝗢𝗔𝗗$_𝗖𝗢𝗠𝗣𝗟𝗘𝗧𝗘❏⤖𝗦𝗘𝗧3𝗨𝗣✷𝗖𝗢2𝗗𝗘1#$!.7z | compressed | |
MD5:C4CCD79A36B1D5A27D05D166C65BEA23 | SHA256:9F555B89B92DCB7315CEE2C97E3BA23D30B829EE0B372C53FEE65B5310166375 | |||
| 3908 | setup.exe | C:\Users\admin\AppData\Local\Temp\Bring.xll | binary | |
MD5:47502726850949B29D12E072E50F5E0B | SHA256:C5069EC294EEBF2CC6C9DA4C7A415C11EB40308FB81FE4A6974A6815CAB5E46F | |||
| 3908 | setup.exe | C:\Users\admin\AppData\Local\Temp\Intake.xll | binary | |
MD5:E2CC1C93247109BDC56FB87D889B618E | SHA256:0282CE1298F4D605846121A2978BA58334BBE6C4CDCEC210C70DA2DE756D36C0 | |||
| 3908 | setup.exe | C:\Users\admin\AppData\Local\Temp\Landscape.xll | binary | |
MD5:A3BABF7605F0D6B799033536ADBC10CD | SHA256:886D88B7E30AF30D60FA25CAD416DB8A0227112088687D051F2928D914D80657 | |||
| 3908 | setup.exe | C:\Users\admin\AppData\Local\Temp\Horrible.xll | binary | |
MD5:00C196F0187EA4D609DA4FEC975D548B | SHA256:DBABB467B26AACD8BC23BFF3797495B3EACBB3F9306748B015C8282AC0C7EC6F | |||
| 3908 | setup.exe | C:\Users\admin\AppData\Local\Temp\Dense.xll | binary | |
MD5:97C6F6CA6C88CCE88503143776E7F09B | SHA256:BDDB48B3A4B91D40D37302008ACEC7DCB6976495A3BA106C11A56B0F31E24B4A | |||
| 6256 | extrac32.exe | C:\Users\admin\AppData\Local\Temp\Conducting | binary | |
MD5:EF3DD5786E6821C03DC67C3168516E79 | SHA256:38843D5B2FDF9A3092BFAB56E15E5D7F1506AC8636B3BC35DA880D48595F607E | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
10
TCP/UDP connections
47
DNS requests
27
Threats
9
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3576 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 184.24.77.7:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5708 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
5708 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
2940 | svchost.exe | GET | 200 | 23.209.209.135:80 | http://x1.c.lencr.org/ | unknown | — | — | whitelisted |
5328 | SearchApp.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
5040 | SystemSettings.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
5328 | SearchApp.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
5040 | SystemSettings.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1268 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5944 | MoUsoCoreWorker.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6356 | RUXIMICS.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2336 | svchost.exe | 172.211.123.250:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
3576 | svchost.exe | 20.190.160.5:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
3576 | svchost.exe | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
1268 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1268 | svchost.exe | 184.24.77.7:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
nexusrules.officeapps.live.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2200 | svchost.exe | Potentially Bad Traffic | ET DNS Query to a *.top domain - Likely Hostile |
2200 | svchost.exe | Domain Observed Used for C2 Detected | ET MALWARE Win32/Lumma Stealer Related CnC Domain in DNS Lookup (battlefled .top) |
2288 | Word.com | Misc Attack | ET DROP Spamhaus DROP Listed Traffic Inbound group 42 |
2288 | Word.com | Domain Observed Used for C2 Detected | ET MALWARE Observed Win32/Lumma Stealer Related Domain (battlefled .top) in TLS SNI |
2288 | Word.com | Domain Observed Used for C2 Detected | ET MALWARE Observed Win32/Lumma Stealer Related Domain (battlefled .top) in TLS SNI |
2288 | Word.com | Domain Observed Used for C2 Detected | ET MALWARE Observed Win32/Lumma Stealer Related Domain (battlefled .top) in TLS SNI |
5116 | Word.com | Domain Observed Used for C2 Detected | ET MALWARE Observed Win32/Lumma Stealer Related Domain (battlefled .top) in TLS SNI |
5116 | Word.com | Domain Observed Used for C2 Detected | ET MALWARE Observed Win32/Lumma Stealer Related Domain (battlefled .top) in TLS SNI |
5116 | Word.com | Domain Observed Used for C2 Detected | ET MALWARE Observed Win32/Lumma Stealer Related Domain (battlefled .top) in TLS SNI |