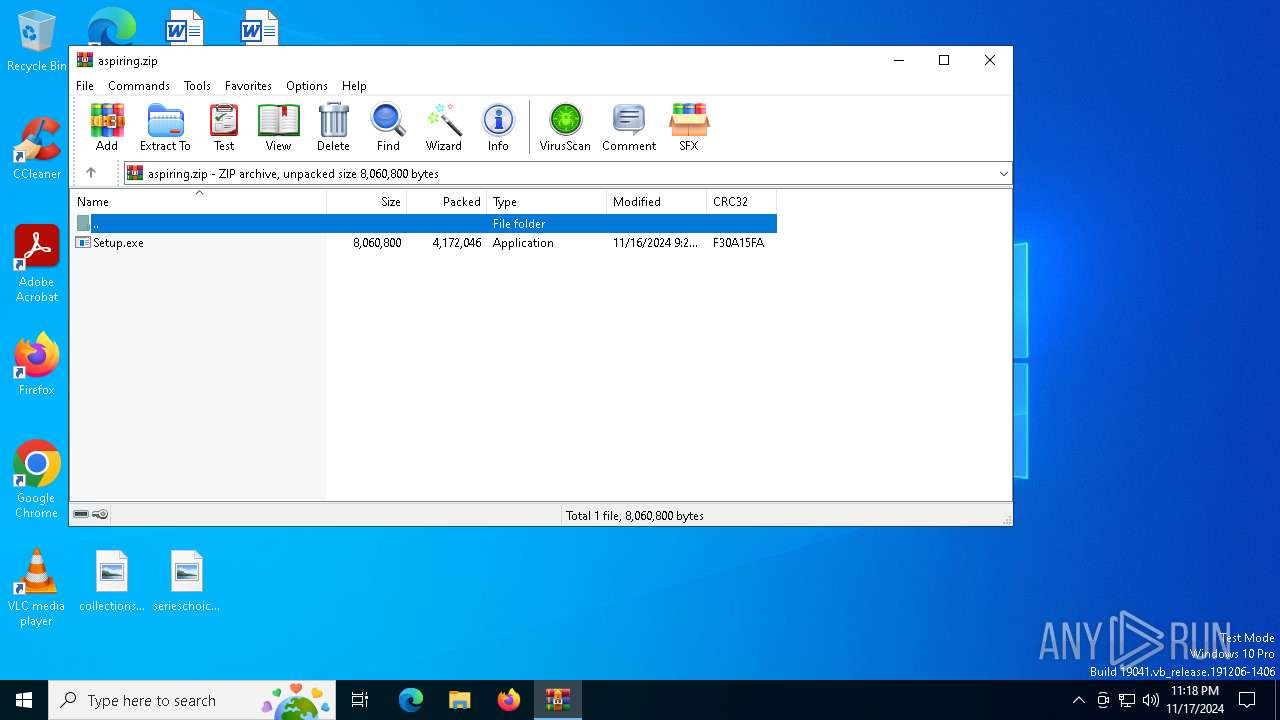
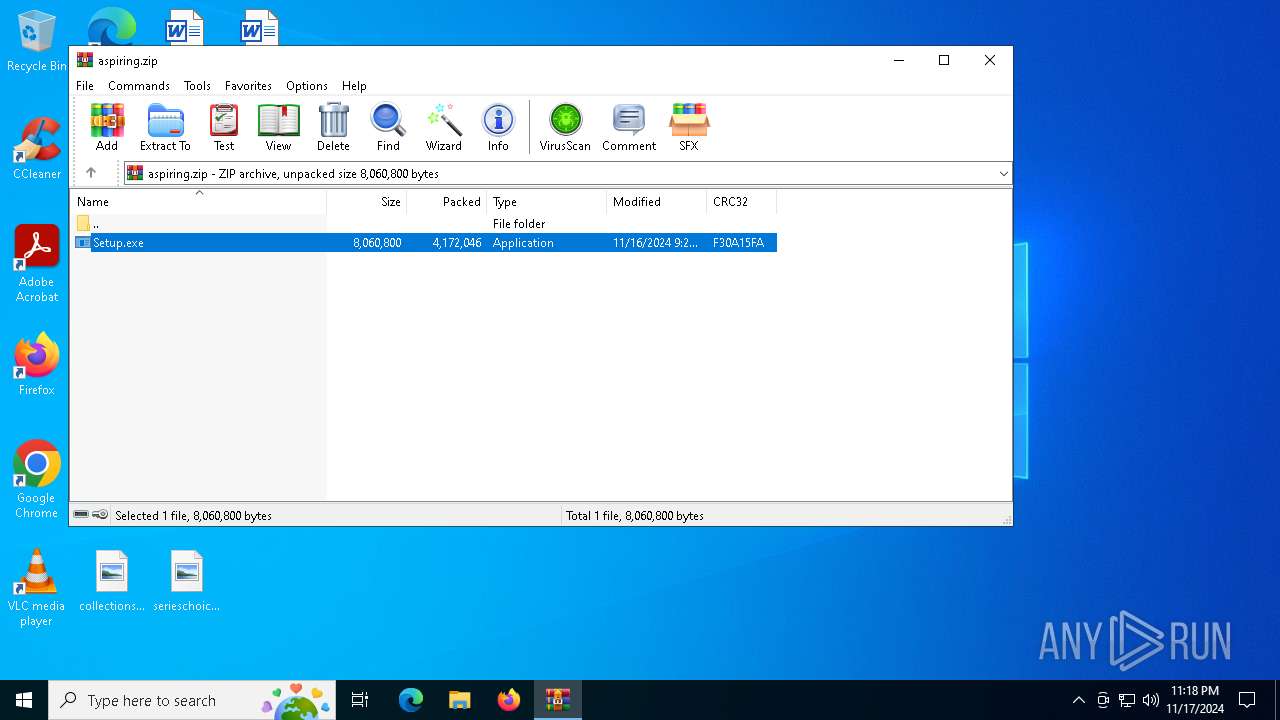
| File name: | aspiring.zip |
| Full analysis: | https://app.any.run/tasks/f57d3533-36d9-4796-bc1b-6079dcd48cc9 |
| Verdict: | Malicious activity |
| Threats: | Lumma is an information stealer, developed using the C programming language. It is offered for sale as a malware-as-a-service, with several plans available. It usually targets cryptocurrency wallets, login credentials, and other sensitive information on a compromised system. The malicious software regularly gets updates that improve and expand its functionality, making it a serious stealer threat. |
| Analysis date: | November 17, 2024, 23:18:03 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=deflate |
| MD5: | B379100E44DAFF6A75FE058337BA12E4 |
| SHA1: | B82486360369B32BA2390FA8008F77D86A1328AE |
| SHA256: | A3BA5C85886C045EACDE6C12C3B4263A4F62D6D98C7EE5A58AC4E85F5F21AFEC |
| SSDEEP: | 98304:pNhk7zCYP0mJrkJs9HMqqGcAv3ByiIt/ak84QGiPEvhydq8ZYJcKnf7VBguJlQJi:J2zXk |
MALICIOUS
Generic archive extractor
- WinRAR.exe (PID: 5328)
Executing a file with an untrusted certificate
- Setup.exe (PID: 3848)
- Setup.exe (PID: 4312)
Steals credentials from Web Browsers
- msiexec.exe (PID: 2928)
LUMMA has been detected (YARA)
- msiexec.exe (PID: 2928)
Actions looks like stealing of personal data
- msiexec.exe (PID: 2928)
SUSPICIOUS
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 5328)
Starts application with an unusual extension
- msiexec.exe (PID: 2928)
Drops a file with a rarely used extension (PIF)
- msiexec.exe (PID: 2928)
Starts the AutoIt3 executable file
- msiexec.exe (PID: 2928)
The process executes via Task Scheduler
- Setup.exe (PID: 4312)
INFO
The process uses the downloaded file
- WinRAR.exe (PID: 5328)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 5328)
- msiexec.exe (PID: 2928)
Checks supported languages
- Setup.exe (PID: 3848)
Reads the computer name
- Setup.exe (PID: 3848)
Create files in a temporary directory
- choice.exe (PID: 1440)
- Setup.exe (PID: 3848)
- Setup.exe (PID: 4312)
Creates files or folders in the user directory
- msiexec.exe (PID: 2928)
Reads the software policy settings
- msiexec.exe (PID: 2928)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2024:11:16 01:29:32 |
| ZipCRC: | 0xf30a15fa |
| ZipCompressedSize: | 4172046 |
| ZipUncompressedSize: | 8060800 |
| ZipFileName: | Setup.exe |
Total processes
144
Monitored processes
10
Malicious processes
5
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1440 | C:\WINDOWS\SysWOW64\choice.exe | C:\Windows\SysWOW64\choice.exe | — | Setup.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Offers the user a choice Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2172 | C:\WINDOWS\system32\svchost.exe -k NetworkService -p -s Dnscache | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2364 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | choice.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2928 | C:\WINDOWS\SysWOW64\msiexec.exe | C:\Windows\SysWOW64\msiexec.exe | choice.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows® installer Exit code: 0 Version: 5.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3848 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa5328.30280\Setup.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa5328.30280\Setup.exe | — | WinRAR.exe | |||||||||||
User: admin Company: RimArts Inc. Integrity Level: MEDIUM Description: RimArts Setup applicatioin Exit code: 1 Version: 1, 3, 0, 4 Modules
| |||||||||||||||
| 3952 | C:\WINDOWS\SysWOW64\choice.exe | C:\Windows\SysWOW64\choice.exe | — | Setup.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Offers the user a choice Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4080 | "C:\Users\admin\AppData\Roaming\H74IRG.pif" "C:\Users\admin\AppData\Roaming\7918VA.tiff" | C:\Users\admin\AppData\Roaming\H74IRG.pif | — | msiexec.exe | |||||||||||
User: admin Company: AutoIt Team Integrity Level: MEDIUM Description: AutoIt v3 Script (Beta) Exit code: 0 Version: 3, 3, 15, 1 Modules
| |||||||||||||||
| 4312 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa5328.30280\Setup.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa5328.30280\Setup.exe | — | svchost.exe | |||||||||||
User: admin Company: RimArts Inc. Integrity Level: MEDIUM Description: RimArts Setup applicatioin Exit code: 1 Version: 1, 3, 0, 4 Modules
| |||||||||||||||
| 5036 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | choice.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5328 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\Desktop\aspiring.zip | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
Total events
2 235
Read events
2 229
Write events
6
Delete events
0
Modification events
| (PID) Process: | (5328) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\GoogleChromeEnterpriseBundle64.zip | |||
| (PID) Process: | (5328) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\aspiring.zip | |||
| (PID) Process: | (5328) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (5328) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (5328) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (5328) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
Executable files
2
Suspicious files
3
Text files
2
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1440 | choice.exe | C:\Users\admin\AppData\Local\Temp\jdrenybciww | — | |
MD5:— | SHA256:— | |||
| 2928 | msiexec.exe | C:\Users\admin\AppData\Roaming\7918VA.tiff | — | |
MD5:— | SHA256:— | |||
| 5328 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa5328.30280\Setup.exe | executable | |
MD5:0BF89E05C575D4BCDCDADB17C7517C29 | SHA256:8CE1CDE3BD1FA2945AF8E03459775A87DBA7275C17401AB19E525B3238609F6B | |||
| 3848 | Setup.exe | C:\Users\admin\AppData\Local\Temp\7b04eded | binary | |
MD5:7C6FA120C383ED159C9C88631C32BD26 | SHA256:36F643A44EFD078D41071E92721DE4FEFF29DB21DAAAFBF5924C9D577BF778E0 | |||
| 3848 | Setup.exe | C:\Users\admin\AppData\Local\Temp\7ad41dae | image | |
MD5:4615267061BD631365026A16EE70CCA1 | SHA256:95E75DD101A71FE9F06C6D3104532907728812A0F9F7C5349CD9FDA0C148FB9E | |||
| 1440 | choice.exe | C:\Windows\Tasks\ROG Live Service.job | binary | |
MD5:B23578C53A5B9A0E24203297D555DA3B | SHA256:867DB381DC0BC41E45FFBE851FB77EF28FAE73BCF581B32C310DFD59E23E7916 | |||
| 4312 | Setup.exe | C:\Users\admin\AppData\Local\Temp\b85b0126 | binary | |
MD5:7C6FA120C383ED159C9C88631C32BD26 | SHA256:36F643A44EFD078D41071E92721DE4FEFF29DB21DAAAFBF5924C9D577BF778E0 | |||
| 4312 | Setup.exe | C:\Users\admin\AppData\Local\Temp\b8306c4f | image | |
MD5:4615267061BD631365026A16EE70CCA1 | SHA256:95E75DD101A71FE9F06C6D3104532907728812A0F9F7C5349CD9FDA0C148FB9E | |||
| 2928 | msiexec.exe | C:\Users\admin\AppData\Roaming\H74IRG.pif | executable | |
MD5:3F58A517F1F4796225137E7659AD2ADB | SHA256:1DA298CAB4D537B0B7B5DABF09BFF6A212B9E45731E0CC772F99026005FB9E48 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
7
TCP/UDP connections
44
DNS requests
23
Threats
2
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
6944 | svchost.exe | GET | 200 | 23.53.40.176:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
4360 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
4004 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
6212 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
4464 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
4464 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
6944 | svchost.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
6944 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1588 | RUXIMICS.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5488 | MoUsoCoreWorker.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4360 | SearchApp.exe | 104.126.37.123:443 | www.bing.com | Akamai International B.V. | DE | whitelisted |
4360 | SearchApp.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4004 | svchost.exe | 20.190.159.64:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4004 | svchost.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
4360 | SearchApp.exe | 104.126.37.145:443 | th.bing.com | Akamai International B.V. | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
google.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
login.live.com |
| whitelisted |
th.bing.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
sliperyedhby.icu |
| unknown |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2172 | svchost.exe | Potentially Bad Traffic | ET INFO DNS Query for Suspicious .icu Domain |
2928 | msiexec.exe | Potentially Bad Traffic | ET INFO Suspicious Domain (*.icu) in TLS SNI |