| URL: | https://cjoint.net/?3krtn0jmod17qrzvqd83 |
| Full analysis: | https://app.any.run/tasks/5f31d445-683c-47ca-a4b7-89841af9bcb2 |
| Verdict: | Malicious activity |
| Threats: | Quasar is a very popular RAT in the world thanks to its code being available in open-source. This malware can be used to control the victim’s computer remotely. |
| Analysis date: | March 05, 2024, 19:11:36 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MD5: | 0C935999BE4868EE53E05FB0436EE322 |
| SHA1: | 2DAC4D89ECD2ADF8307D9342A7EB4CFCEF85AC44 |
| SHA256: | A36320647E3C9497A11C6085DBF346B1A4F7ADC4239770426885CCDEDF85CA83 |
| SSDEEP: | 3:N8SXySOXRLV/NC:2Sm4 |
MALICIOUS
Drops/Copies Quasar RAT executable
- iexplore.exe (PID: 3664)
- iexplore.exe (PID: 2160)
- firefox.exe (PID: 2648)
Changes the autorun value in the registry
- firefox.exe (PID: 2648)
- csrsss.exe (PID: 2208)
QUASAR has been detected (YARA)
- csrsss.exe (PID: 2208)
QUASAR has been detected (SURICATA)
- csrsss.exe (PID: 2208)
Drops the executable file immediately after the start
- firefox.exe (PID: 2648)
SUSPICIOUS
Reads the Internet Settings
- firefox.exe (PID: 2648)
- csrsss.exe (PID: 2208)
Executable content was dropped or overwritten
- firefox.exe (PID: 2648)
Cleans NTFS data stream (Zone Identifier)
- firefox.exe (PID: 2648)
Checks for external IP
- firefox.exe (PID: 2648)
- csrsss.exe (PID: 2208)
Connects to unusual port
- csrsss.exe (PID: 2208)
Starts itself from another location
- firefox.exe (PID: 2648)
INFO
Checks supported languages
- wmpnscfg.exe (PID: 1384)
- firefox.exe (PID: 2648)
- csrsss.exe (PID: 2208)
Application launched itself
- iexplore.exe (PID: 2160)
Executable content was dropped or overwritten
- iexplore.exe (PID: 3664)
- iexplore.exe (PID: 2160)
Drops the executable file immediately after the start
- iexplore.exe (PID: 3664)
- iexplore.exe (PID: 2160)
Reads the computer name
- wmpnscfg.exe (PID: 1384)
- firefox.exe (PID: 2648)
- csrsss.exe (PID: 2208)
Modifies the phishing filter of IE
- iexplore.exe (PID: 2160)
Reads Environment values
- firefox.exe (PID: 2648)
- csrsss.exe (PID: 2208)
The process uses the downloaded file
- iexplore.exe (PID: 2160)
- firefox.exe (PID: 2648)
Creates files or folders in the user directory
- firefox.exe (PID: 2648)
- csrsss.exe (PID: 2208)
Reads the machine GUID from the registry
- csrsss.exe (PID: 2208)
- firefox.exe (PID: 2648)
Manual execution by a user
- cmd.exe (PID: 2900)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Quasar
(PID) Process(2208) csrsss.exe
Version1.3.0.0
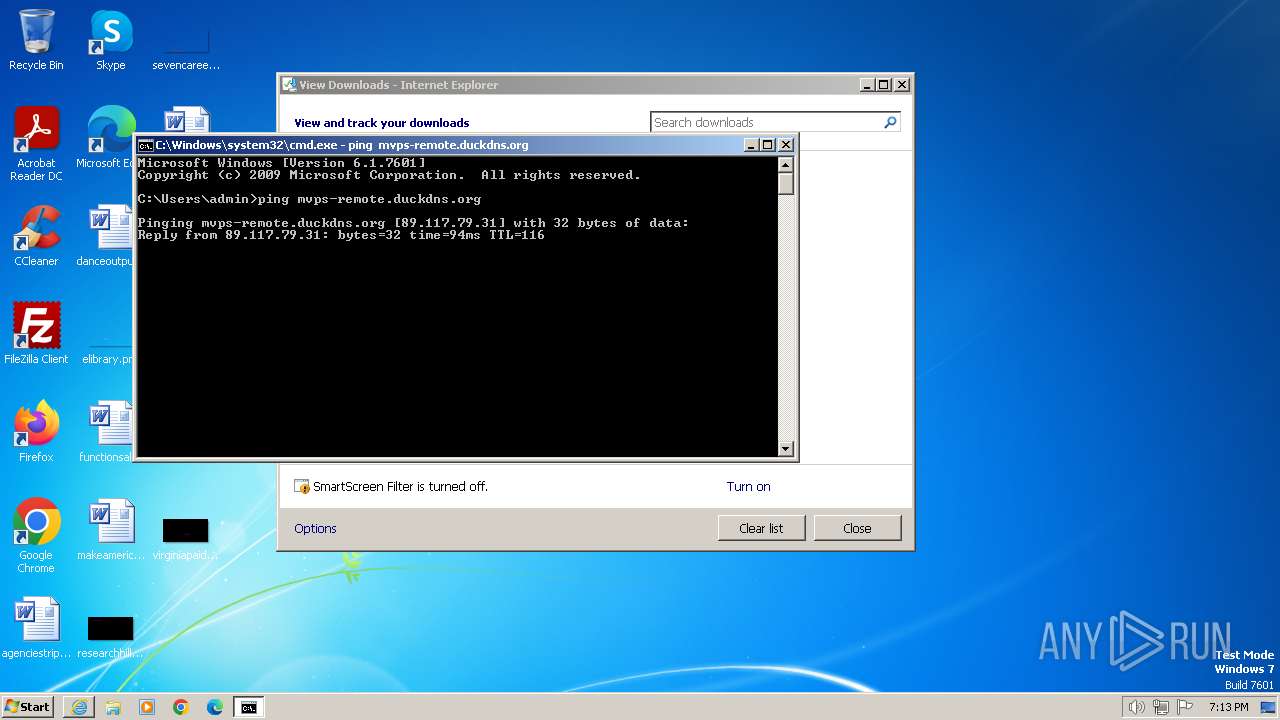
C2 (2)mvps-remote.duckdns.org:7
Sub_Dirupdatess
Install_Namecsrsss.exe
MutexQSR_MUTEX_75FzcMZvy1nRcxtL1M
Startupcsrsss
TagNEW 2025
LogDirLogs
Signature
Certificate
Total processes
45
Monitored processes
7
Malicious processes
4
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1308 | ping mvps-remote.duckdns.org | C:\Windows\System32\PING.EXE | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: TCP/IP Ping Command Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1384 | "C:\Program Files\Windows Media Player\wmpnscfg.exe" | C:\Program Files\Windows Media Player\wmpnscfg.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Media Player Network Sharing Service Configuration Application Exit code: 0 Version: 12.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2160 | "C:\Program Files\Internet Explorer\iexplore.exe" "https://cjoint.net/?3krtn0jmod17qrzvqd83" | C:\Program Files\Internet Explorer\iexplore.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 2208 | "C:\Users\admin\AppData\Roaming\updatess\csrsss.exe" | C:\Users\admin\AppData\Roaming\updatess\csrsss.exe | firefox.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Version: 1.3.0.0 Modules
Quasar(PID) Process(2208) csrsss.exe Version1.3.0.0 C2 (2)mvps-remote.duckdns.org:7 Sub_Dirupdatess Install_Namecsrsss.exe MutexQSR_MUTEX_75FzcMZvy1nRcxtL1M Startupcsrsss TagNEW 2025 LogDirLogs Signature Certificate | |||||||||||||||
| 2648 | "C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\B6QGX7LP\firefox.exe" | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\B6QGX7LP\firefox.exe | iexplore.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Version: 1.3.0.0 Modules
| |||||||||||||||
| 2900 | "C:\Windows\system32\cmd.exe" | C:\Windows\System32\cmd.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 3664 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:2160 CREDAT:267521 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
Total events
25 804
Read events
25 674
Write events
102
Delete events
28
Modification events
| (PID) Process: | (2160) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPDaysSinceLastAutoMigration |
Value: 1 | |||
| (PID) Process: | (2160) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchLowDateTime |
Value: | |||
| (PID) Process: | (2160) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchHighDateTime |
Value: 31092528 | |||
| (PID) Process: | (2160) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateLowDateTime |
Value: 146279666 | |||
| (PID) Process: | (2160) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 31092529 | |||
| (PID) Process: | (2160) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (2160) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (2160) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (2160) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (2160) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
Executable files
4
Suspicious files
19
Text files
13
Unknown types
6
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3664 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\0911256CEC942F326366AB96DD55218C | der | |
MD5:799FE59EEE7161F022BA72C056EE70B0 | SHA256:88E2E53D3CF75439E81F7866FD62917A0A4C735C4BA6F622DF41383BD3E6C09C | |||
| 3664 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\0DA515F703BB9B49479E8697ADB0B955_96EEC010953ED454BBCDFA69FC071E7C | binary | |
MD5:FF52A53A30643D37C47916314D1DE457 | SHA256:84F8ACD296C3C64894CD263F51B951D31D95E213DE0355FC60B3B222AFA034E0 | |||
| 3664 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\B2FAF7692FD9FFBD64EDE317E42334BA_D7393C8F62BDE4D4CB606228BC7A711E | der | |
MD5:735C7674E62AAE7E72A6EB609F330987 | SHA256:2E6759B73933DC5E1759434377066819E363FD082550D0B6F764EBED62DD4E73 | |||
| 3664 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\4B3D1CD03E2BE9D4F9CDDE390F5EFE31_90C327705AC5B6308D44D78AC1977195 | binary | |
MD5:0F338917B856F85500CE11AF272B05E5 | SHA256:29DC1F69209D80FCB07D1EF6E65EC321F67236183BD48D86BA42F6AA7C9989E4 | |||
| 3664 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\4B3D1CD03E2BE9D4F9CDDE390F5EFE31_90C327705AC5B6308D44D78AC1977195 | binary | |
MD5:5FCB8AB13BADD7818E5700BDEB3EF856 | SHA256:B6D609D7C41F700A998A1C61B9BEB92A31B59F1BE1D321D78EA9EF154B2C3EC1 | |||
| 3664 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\0DA515F703BB9B49479E8697ADB0B955_96EEC010953ED454BBCDFA69FC071E7C | der | |
MD5:619EA4A597A613172C310891E7F5F8D8 | SHA256:CDFA57AE66811963A8C151E204705A9FCE2F06AAE4FCB52AB74E087F2F70BBE4 | |||
| 2160 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Internet Explorer\Recovery\Active\{3474A7B3-DB24-11EE-AE0A-12A9866C77DE}.dat | binary | |
MD5:A3961A1707C057C9CE2ACC2BFEC30BAD | SHA256:83B5568C52D2E7852FE59D1CFBDC224FDBD2875AB779FD6CFADA6D0F8B695C73 | |||
| 3664 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\07CEF2F654E3ED6050FFC9B6EB844250_3431D4C539FB2CFCB781821E9902850D | der | |
MD5:C99EA45B55DB0DD4852EB69EED0D77C6 | SHA256:797DA85C1ECD23A17C3246741426C6F1D6EA2A661B8C41CADC969C3A5AF12193 | |||
| 3664 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\B6QGX7LP\firefox.exe.uednp5o.partial | executable | |
MD5:09CACB6BA159224E5FC3EFAEC6F05C7B | SHA256:4FE12C11ED6C872D655C05BB2A61E6605193DBCFC865AF6A4D33DEF4D3FD22FE | |||
| 3664 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\MFAQUS6V\firefox[1].exe | executable | |
MD5:0194C2EF1B7640783BF6963F6B0B49D2 | SHA256:F7E927082CF23020C29C68326281B37FFD0D42F4772B60CCA0AC4AD3901D913E | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
18
TCP/UDP connections
31
DNS requests
18
Threats
11
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3664 | iexplore.exe | GET | 304 | 23.48.23.34:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?d362edf7b65e9a48 | unknown | — | — | unknown |
3664 | iexplore.exe | GET | 200 | 104.18.38.233:80 | http://ocsp.comodoca.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBRTtU9uFqgVGHhJwXZyWCNXmVR5ngQUoBEKIz6W8Qfs4q8p74Klf9AwpLQCEDlyRDr5IrdR19NsEN0xNZU%3D | unknown | binary | 1.42 Kb | unknown |
3664 | iexplore.exe | GET | 200 | 172.64.149.23:80 | http://ocsp.usertrust.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTNMNJMNDqCqx8FcBWK16EHdimS6QQUU3m%2FWqorSs9UgOHYm8Cd8rIDZssCEH1bUSa0droR23QWC7xTDac%3D | unknown | binary | 2.18 Kb | unknown |
3664 | iexplore.exe | GET | 200 | 172.64.149.23:80 | http://ocsp.sectigo.com/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBRDC9IOTxN6GmyRjyTl2n4yTUczyAQUjYxexFStiuF36Zv5mwXhuAGNYeECEQCswwDztTW5%2BiafvAydgYq%2F | unknown | binary | 472 b | unknown |
3664 | iexplore.exe | GET | 200 | 104.18.20.226:80 | http://ocsp.globalsign.com/alphasslcasha256g4/ME0wSzBJMEcwRTAJBgUrDgMCGgUABBSPdwLcDiHQXlVfp8h37hrpMerTggQUT8usqMLvq92Db2u%2Fzpg9XFgldhUCDE957Ej9f2yuuh%2F1lQ%3D%3D | unknown | binary | 1.40 Kb | unknown |
3664 | iexplore.exe | GET | 200 | 104.18.20.226:80 | http://ocsp.globalsign.com/rootr1/MFEwTzBNMEswSTAJBgUrDgMCGgUABBS3V7W2nAf4FiMTjpDJKg6%2BMgGqMQQUYHtmGkUNl8qJUC99BM00qP%2F8%2FUsCEH1NQqkrQx1%2BZFPnwZqNWHc%3D | unknown | binary | 1.41 Kb | unknown |
2208 | csrsss.exe | GET | 200 | 208.95.112.1:80 | http://ip-api.com/json/ | unknown | binary | 292 b | unknown |
1080 | svchost.exe | GET | 200 | 23.48.23.21:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab?fc91d912a85a08d5 | unknown | compressed | 67.5 Kb | unknown |
1080 | svchost.exe | GET | 304 | 23.48.23.21:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?6776476d79efed94 | unknown | compressed | 67.5 Kb | unknown |
2160 | iexplore.exe | GET | 304 | 23.48.23.21:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?18014fff35250a83 | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
3664 | iexplore.exe | 5.39.224.140:443 | cjoint.net | DSTORAGE s.a.s. | FR | unknown |
3664 | iexplore.exe | 23.48.23.7:80 | ctldl.windowsupdate.com | Akamai International B.V. | DE | unknown |
3664 | iexplore.exe | 23.48.23.34:80 | ctldl.windowsupdate.com | Akamai International B.V. | DE | unknown |
3664 | iexplore.exe | 104.18.38.233:80 | ocsp.comodoca.com | CLOUDFLARENET | — | shared |
3664 | iexplore.exe | 172.64.149.23:80 | ocsp.comodoca.com | CLOUDFLARENET | US | unknown |
3664 | iexplore.exe | 5.39.224.2:443 | a-2.1fichier.com | DSTORAGE s.a.s. | FR | unknown |
3664 | iexplore.exe | 104.18.20.226:80 | ocsp.globalsign.com | CLOUDFLARENET | — | shared |
DNS requests
Domain | IP | Reputation |
|---|---|---|
cjoint.net |
| unknown |
ctldl.windowsupdate.com |
| whitelisted |
ocsp.comodoca.com |
| whitelisted |
ocsp.usertrust.com |
| whitelisted |
ocsp.sectigo.com |
| whitelisted |
a-2.1fichier.com |
| unknown |
ocsp.globalsign.com |
| whitelisted |
ip-api.com |
| shared |
mvps-remote.duckdns.org |
| malicious |
iecvlist.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2648 | firefox.exe | Potential Corporate Privacy Violation | AV POLICY Internal Host Retrieving External IP Address (ip-api. com) |
2648 | firefox.exe | Device Retrieving External IP Address Detected | ET POLICY External IP Lookup ip-api.com |
2648 | firefox.exe | A Network Trojan was detected | ET MALWARE Common RAT Connectivity Check Observed |
2208 | csrsss.exe | Potential Corporate Privacy Violation | AV POLICY Internal Host Retrieving External IP Address (ip-api. com) |
2208 | csrsss.exe | A Network Trojan was detected | ET MALWARE Common RAT Connectivity Check Observed |
2208 | csrsss.exe | Device Retrieving External IP Address Detected | ET POLICY External IP Lookup ip-api.com |
1080 | svchost.exe | Potentially Bad Traffic | ET INFO DYNAMIC_DNS Query to a *.duckdns .org Domain |
1080 | svchost.exe | Misc activity | ET INFO DYNAMIC_DNS Query to *.duckdns. Domain |
2208 | csrsss.exe | Malware Command and Control Activity Detected | REMOTE [ANY.RUN] QuasarRAT Successful Connection (TCP) |
1080 | svchost.exe | Potentially Bad Traffic | ET INFO DYNAMIC_DNS Query to a *.duckdns .org Domain |