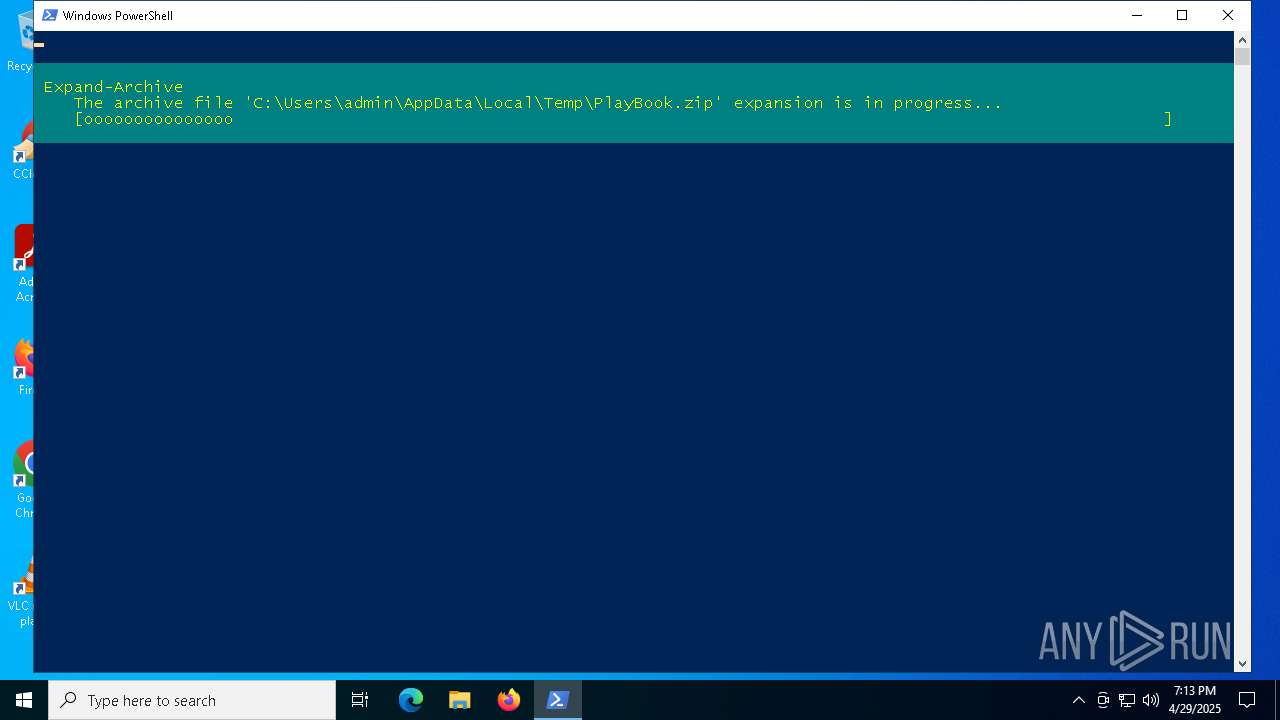
| File name: | turd.ps1 |
| Full analysis: | https://app.any.run/tasks/9f7eb7f1-c559-4f84-8028-94fca4b47a44 |
| Verdict: | Malicious activity |
| Threats: | HijackLoader is a modular malware acting as a vehicle for distributing different types of malicious software on compromised systems. It gained prominence during the summer of 2023 and has since been used in multiple attacks against organizations from various sectors, including hospitality businesses. |
| Analysis date: | April 29, 2025, 19:13:19 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | text/plain |
| File info: | ASCII text, with no line terminators |
| MD5: | 0F1320618915EFB3EF41F86531026E8B |
| SHA1: | A42D2AD0C7FAB25B605F75256EDB7A10B7F562B0 |
| SHA256: | A217C8B8CBFA39721F57EDF61DA87C24F5C9F34EC005986F2247A6385D669E71 |
| SSDEEP: | 6:q3Lh8JSRMRyLhv2lddtYen9cddtYeFIWQusdYsdoEb:yG0MRYh+lddtZcddthIpJdYsdoEb |
MALICIOUS
Bypass execution policy to execute commands
- powershell.exe (PID: 1020)
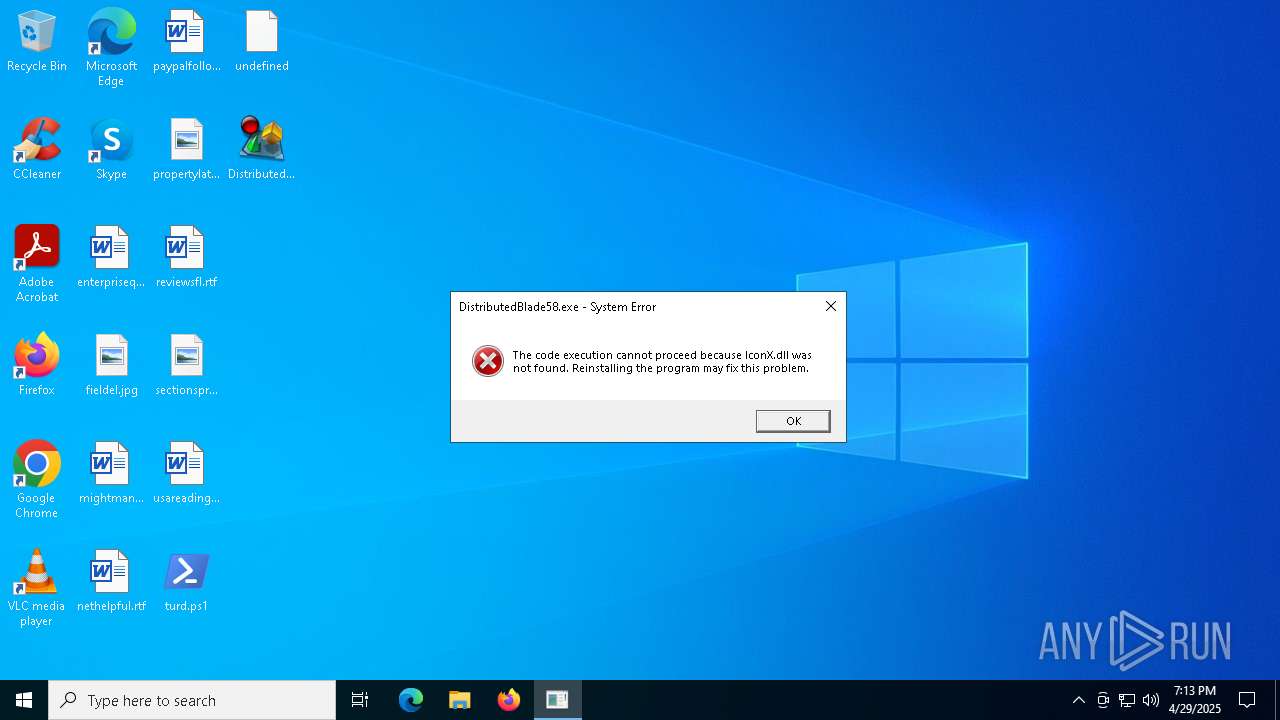
Executing a file with an untrusted certificate
- DistributedBlade58.exe (PID: 4220)
- DistributedBlade58.exe (PID: 5364)
- DistributedBlade58.exe (PID: 5024)
HIJACKLOADER has been detected (YARA)
- DistributedBlade58.exe (PID: 5024)
SUSPICIOUS
Executable content was dropped or overwritten
- powershell.exe (PID: 1020)
- DistributedBlade58.exe (PID: 5024)
- DistributedBlade58.exe (PID: 4220)
Gets file extension (POWERSHELL)
- powershell.exe (PID: 1020)
There is functionality for taking screenshot (YARA)
- DistributedBlade58.exe (PID: 5024)
- DistributedBlade58.exe (PID: 5364)
Possibly patching Antimalware Scan Interface function (YARA)
- MSLauncher.exe (PID: 2236)
Starts itself from another location
- DistributedBlade58.exe (PID: 4220)
INFO
Checks if a key exists in the options dictionary (POWERSHELL)
- powershell.exe (PID: 1020)
Disables trace logs
- powershell.exe (PID: 1020)
Creates files or folders in the user directory
- DistributedBlade58.exe (PID: 5024)
Checks whether the specified file exists (POWERSHELL)
- powershell.exe (PID: 1020)
Checks proxy server information
- powershell.exe (PID: 1020)
- slui.exe (PID: 6656)
The executable file from the user directory is run by the Powershell process
- DistributedBlade58.exe (PID: 4220)
Checks supported languages
- DistributedBlade58.exe (PID: 4220)
- 360Tray.exe (PID: 4736)
- MSLauncher.exe (PID: 2236)
- DistributedBlade58.exe (PID: 5024)
Reads the computer name
- DistributedBlade58.exe (PID: 4220)
- DistributedBlade58.exe (PID: 5024)
- MSLauncher.exe (PID: 2236)
- 360Tray.exe (PID: 4736)
The sample compiled with chinese language support
- DistributedBlade58.exe (PID: 5024)
Manual execution by a user
- OpenWith.exe (PID: 6512)
- DistributedBlade58.exe (PID: 5364)
- OpenWith.exe (PID: 5756)
Reads Microsoft Office registry keys
- OpenWith.exe (PID: 6512)
- OpenWith.exe (PID: 5756)
Create files in a temporary directory
- DistributedBlade58.exe (PID: 5024)
- 360Tray.exe (PID: 4736)
Reads the machine GUID from the registry
- MSLauncher.exe (PID: 2236)
Reads the software policy settings
- slui.exe (PID: 6656)
Creates files in the program directory
- DistributedBlade58.exe (PID: 4220)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
131
Monitored processes
10
Malicious processes
3
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1020 | "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" -ep bypass C:\Users\admin\Desktop\turd.ps1 | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2236 | C:\Users\admin\AppData\Local\Temp\MSLauncher.exe | C:\Users\admin\AppData\Local\Temp\MSLauncher.exe | DistributedBlade58.exe | ||||||||||||
User: admin Company: Blizzard Entertainment Integrity Level: MEDIUM Description: Battle.net Launcher Version: 2.34.0.14907 Modules
| |||||||||||||||
| 4220 | "C:\Users\admin\AppData\Local\Temp\Package\DistributedBlade58.exe" | C:\Users\admin\AppData\Local\Temp\Package\DistributedBlade58.exe | powershell.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 4736 | "C:\Users\admin\AppData\Roaming\PoFirefox\360Tray.exe" "C:\Users\admin\AppData\Roaming\PoFirefox\360Tray.exe" /onui | C:\Users\admin\AppData\Roaming\PoFirefox\360Tray.exe | — | DistributedBlade58.exe | |||||||||||
User: admin Company: 360.cn Integrity Level: MEDIUM Description: 360安全卫士 安全防护中心模块 Exit code: 0 Version: 12, 0, 0, 1761 Modules
| |||||||||||||||
| 5024 | C:\ProgramData\PoFirefox\DistributedBlade58.exe | C:\ProgramData\PoFirefox\DistributedBlade58.exe | DistributedBlade58.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 5364 | "C:\Users\admin\Desktop\DistributedBlade58.exe" | C:\Users\admin\Desktop\DistributedBlade58.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Modules
| |||||||||||||||
| 5640 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
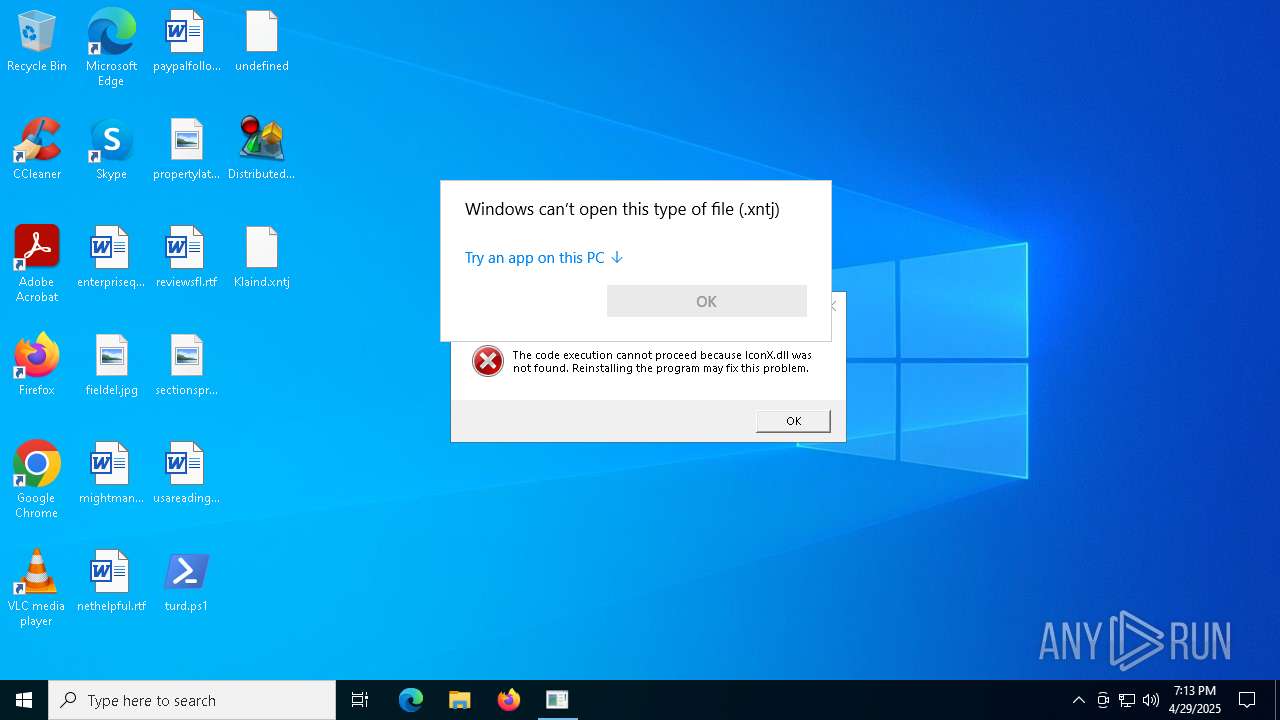
| 5756 | "C:\WINDOWS\System32\OpenWith.exe" C:\Users\admin\Desktop\Maik.xt | C:\Windows\System32\OpenWith.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Pick an app Exit code: 2147943623 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6512 | "C:\WINDOWS\System32\OpenWith.exe" C:\Users\admin\Desktop\Klaind.xntj | C:\Windows\System32\OpenWith.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Pick an app Exit code: 2147943623 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6656 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
10 620
Read events
10 620
Write events
0
Delete events
0
Modification events
Executable files
10
Suspicious files
13
Text files
2
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
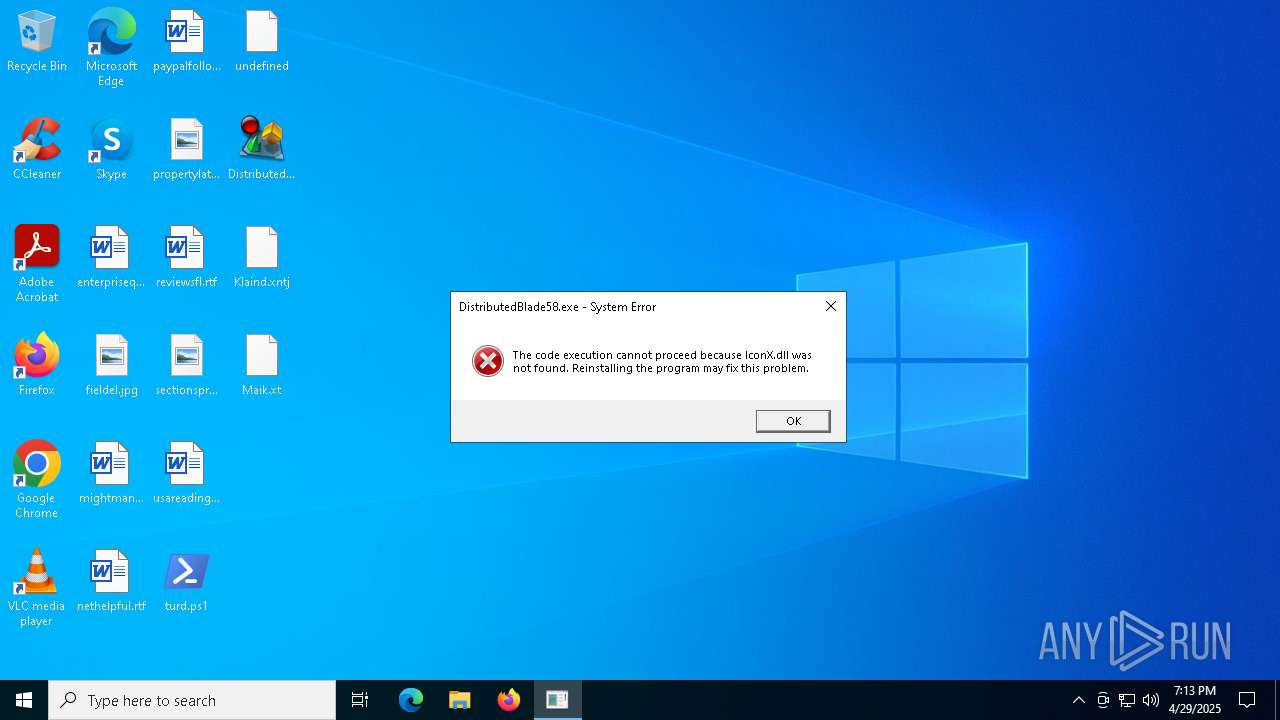
| 4220 | DistributedBlade58.exe | C:\ProgramData\PoFirefox\IconX.dll | executable | |
MD5:D2DBDD831DDCE917D58571E0FD70A742 | SHA256:0F4AF1600462AA57259FD9D935E2DBB5CA22336CF6515F4A390B04CD5DA7955F | |||
| 1020 | powershell.exe | C:\Users\admin\AppData\Local\Temp\Package\dx0.dll | executable | |
MD5:693DFBB9B324E80B70660927CA1DEA69 | SHA256:7C28D90E3484B566EE00ADAB4679A3D1C51F86F01560035D86C8F7788AC05234 | |||
| 1020 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\590aee7bdd69b59b.customDestinations-ms | binary | |
MD5:8F4EB37E818AADFFCABC8F4EF0FD9631 | SHA256:CF6CD466B633B70379338AE9E44308E517E99B068B7B72CE38B60E3C89868A05 | |||
| 1020 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\4BX9SW7XXL6W9TM3JGWK.temp | binary | |
MD5:8F4EB37E818AADFFCABC8F4EF0FD9631 | SHA256:CF6CD466B633B70379338AE9E44308E517E99B068B7B72CE38B60E3C89868A05 | |||
| 5024 | DistributedBlade58.exe | C:\Users\admin\AppData\Local\Temp\EFA13E4.tmp | — | |
MD5:— | SHA256:— | |||
| 1020 | powershell.exe | C:\Users\admin\AppData\Local\Temp\Package\DirectGUI.dll | executable | |
MD5:DBB97D5BA941838BB34FF9F98BD47B6C | SHA256:D121A42FC56B92CD0B8AEDE3C0A268BEC534293F87DA0C774CF78CA557D3E1AD | |||
| 1020 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_wn45vsen.m0h.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 1020 | powershell.exe | C:\Users\admin\AppData\Local\Temp\Package\IconX.dll | executable | |
MD5:D2DBDD831DDCE917D58571E0FD70A742 | SHA256:0F4AF1600462AA57259FD9D935E2DBB5CA22336CF6515F4A390B04CD5DA7955F | |||
| 1020 | powershell.exe | C:\Users\admin\AppData\Local\Temp\Package\Maik.xt | binary | |
MD5:ACE46038DC3BF9FB1E177950555CF701 | SHA256:B7570587305E05D79B85FF769A9FD46723B68E0C7ECA2DD87AF4AC1BC6B0C6D3 | |||
| 1020 | powershell.exe | C:\Users\admin\AppData\Local\Temp\Package\DistributedBlade58.exe | executable | |
MD5:9E90C7BA64A66D9AB4703AF006540193 | SHA256:A519304C3BBA23EAE2045A85E01AAE44E6556B2F787966654B7209DB13CFA0C4 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
25
TCP/UDP connections
42
DNS requests
14
Threats
2
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 301 | 188.114.96.3:443 | https://shorter.me/T7mMy | unknown | — | — | unknown |
— | — | GET | 304 | 20.109.210.53:443 | https://slscr.update.microsoft.com/SLS/%7B522D76A4-93E1-47F8-B8CE-07C937AD1A1E%7D/x64/10.0.19045.4046/0?CH=686&L=en-US&P=&PT=0x30&WUA=10.0.19041.3996&MK=DELL&MD=DELL | unknown | — | — | unknown |
3300 | SIHClient.exe | GET | 200 | 2.19.11.120:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
3300 | SIHClient.exe | GET | 200 | 88.221.169.152:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20Update%20Signing%20CA%202.1.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 20.109.210.53:443 | https://slscr.update.microsoft.com/SLS/%7B522D76A4-93E1-47F8-B8CE-07C937AD1A1E%7D/x64/10.0.19045.4046/0?CH=686&L=en-US&P=&PT=0x30&WUA=10.0.19041.3996&MK=DELL&MD=DELL | unknown | — | — | unknown |
3300 | SIHClient.exe | GET | 200 | 2.19.11.120:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut_2010-06-23.crl | unknown | — | — | whitelisted |
3300 | SIHClient.exe | GET | 200 | 2.19.11.120:80 | http://crl.microsoft.com/pki/crl/products/MicTimStaPCA_2010-07-01.crl | unknown | — | — | whitelisted |
3300 | SIHClient.exe | GET | 200 | 88.221.169.152:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Signing%20CA%202.1.crl | unknown | — | — | whitelisted |
3300 | SIHClient.exe | GET | 200 | 88.221.169.152:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Signing%20CA%202.2.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 20.242.39.171:443 | https://fe3cr.delivery.mp.microsoft.com/clientwebservice/ping | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
3216 | svchost.exe | 172.211.123.250:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
1020 | powershell.exe | 188.114.97.3:443 | shorter.me | CLOUDFLARENET | NL | malicious |
1020 | powershell.exe | 188.114.96.3:443 | shorter.me | CLOUDFLARENET | NL | unknown |
3300 | SIHClient.exe | 172.202.163.200:443 | slscr.update.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | GB | whitelisted |
3300 | SIHClient.exe | 2.19.11.120:80 | crl.microsoft.com | Elisa Oyj | NL | whitelisted |
3300 | SIHClient.exe | 88.221.169.152:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
3300 | SIHClient.exe | 13.85.23.206:443 | fe3cr.delivery.mp.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
shorter.me |
| malicious |
marinescoatsnow.click |
| unknown |
slscr.update.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
activation-v2.sls.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
— | — | Not Suspicious Traffic | ET INFO Windows Powershell User-Agent Usage |
— | — | Not Suspicious Traffic | ET INFO Windows Powershell User-Agent Usage |