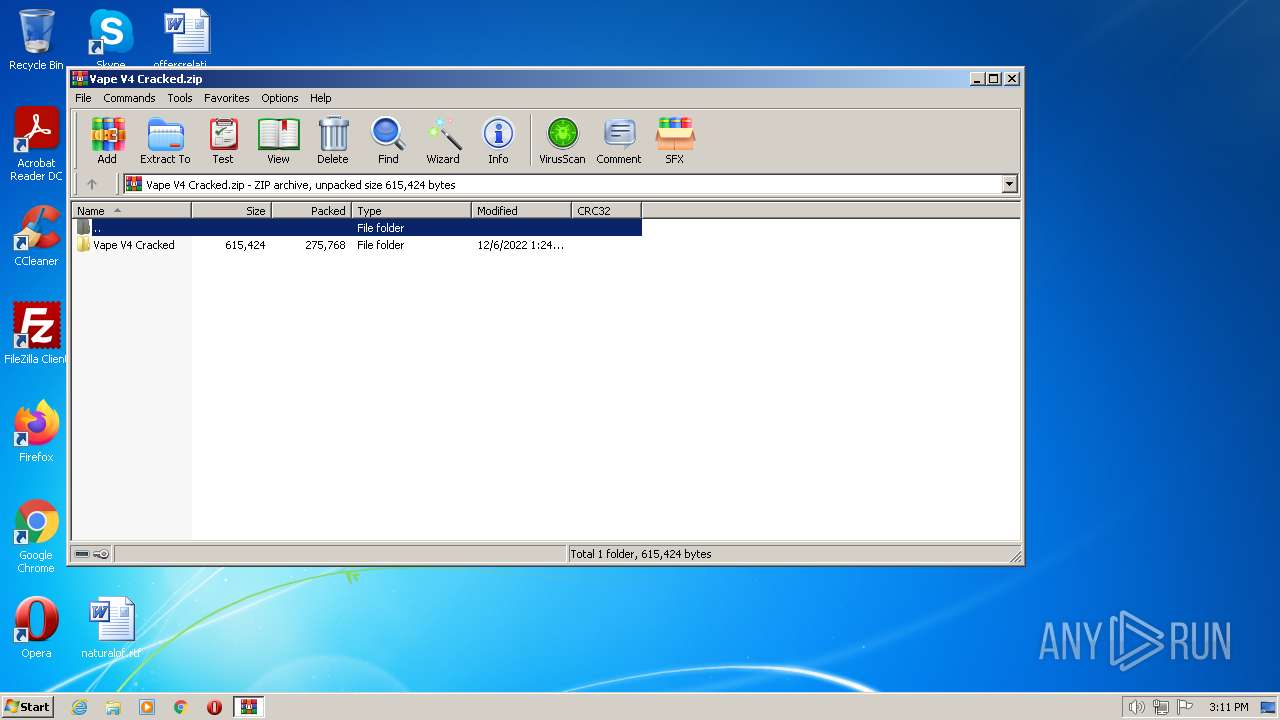
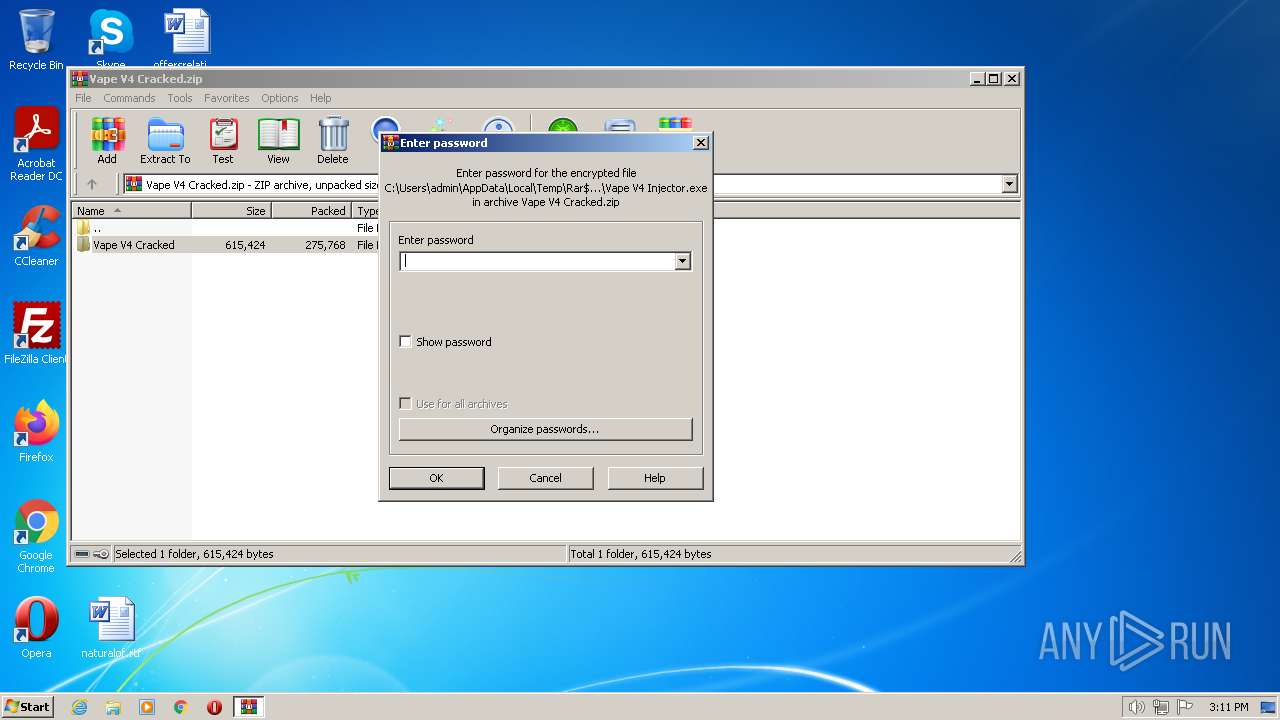
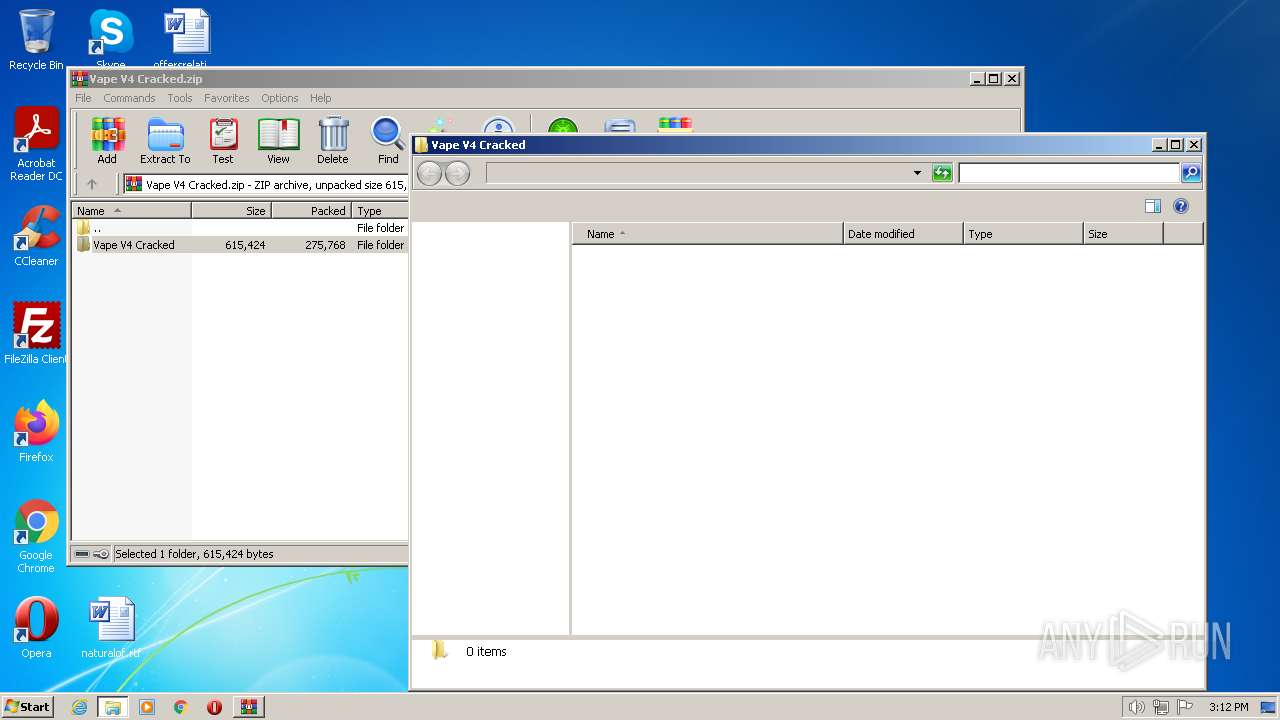
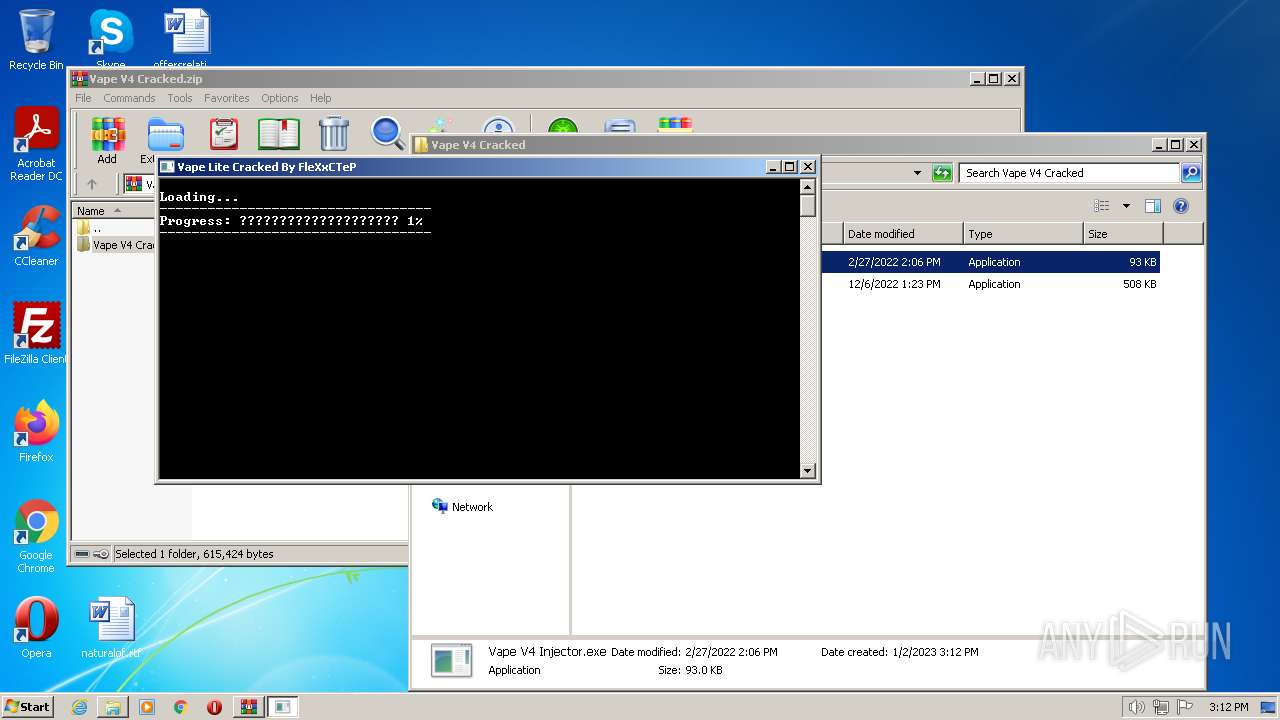
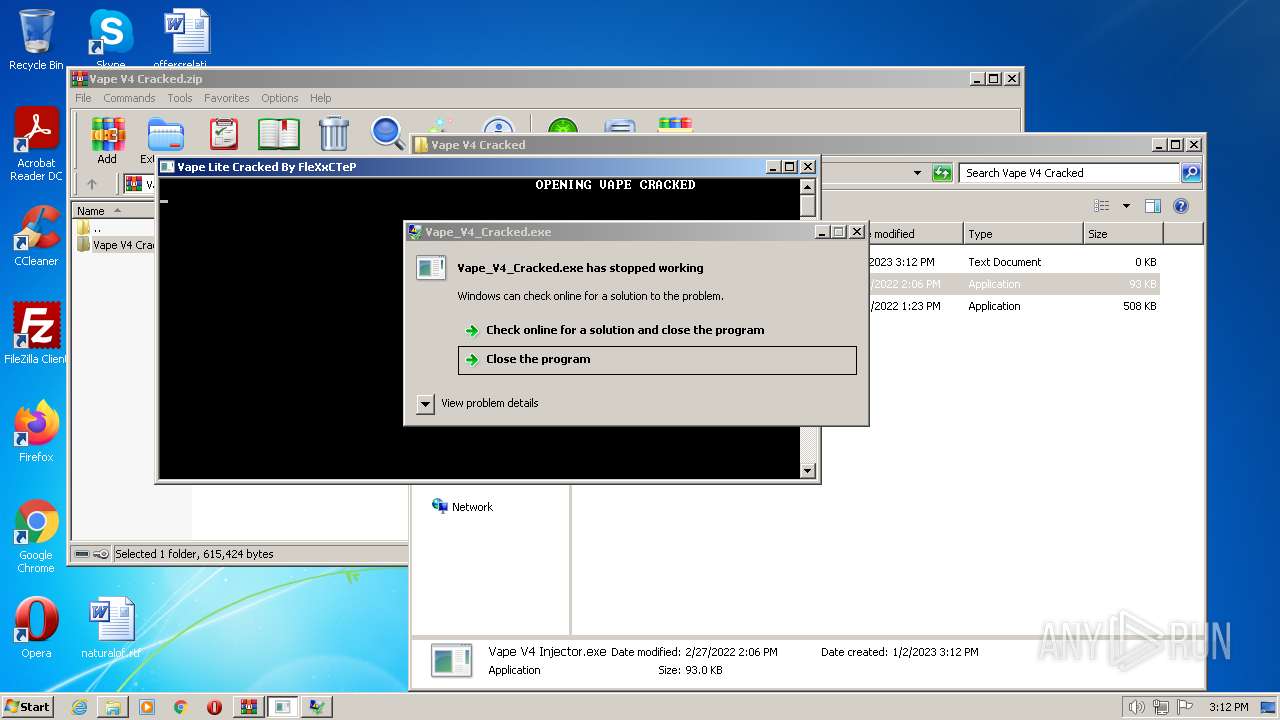
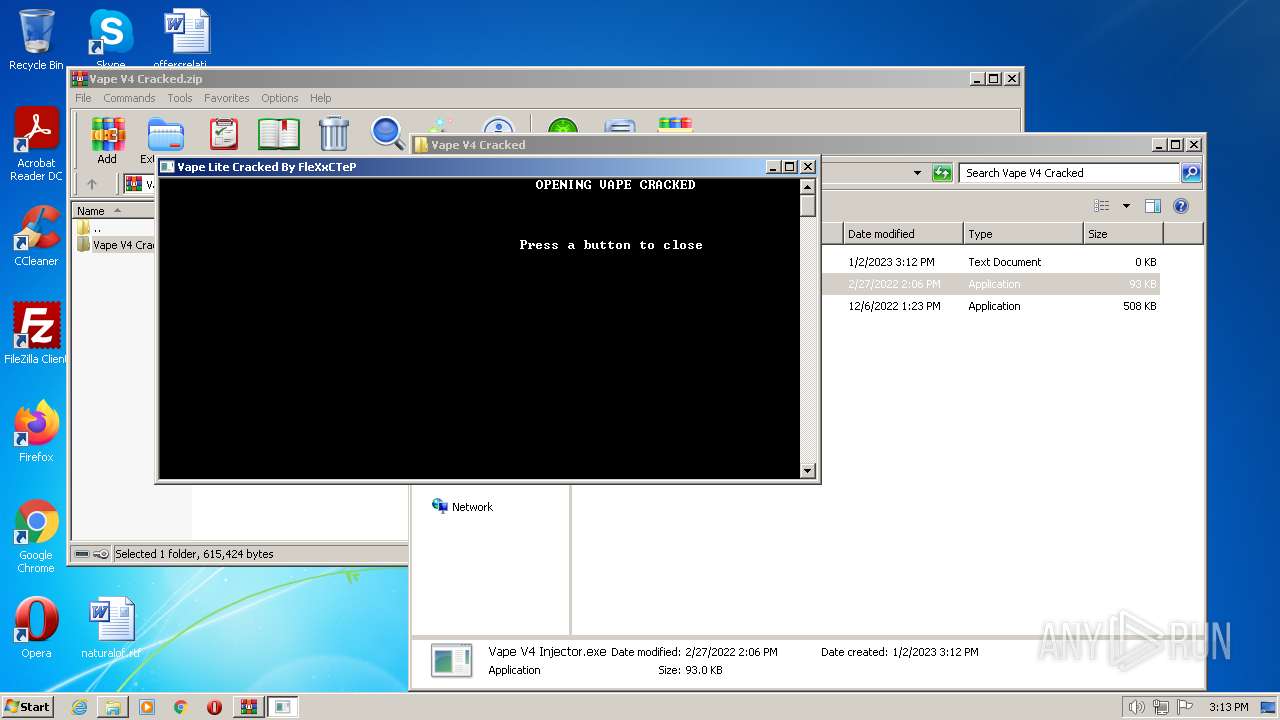
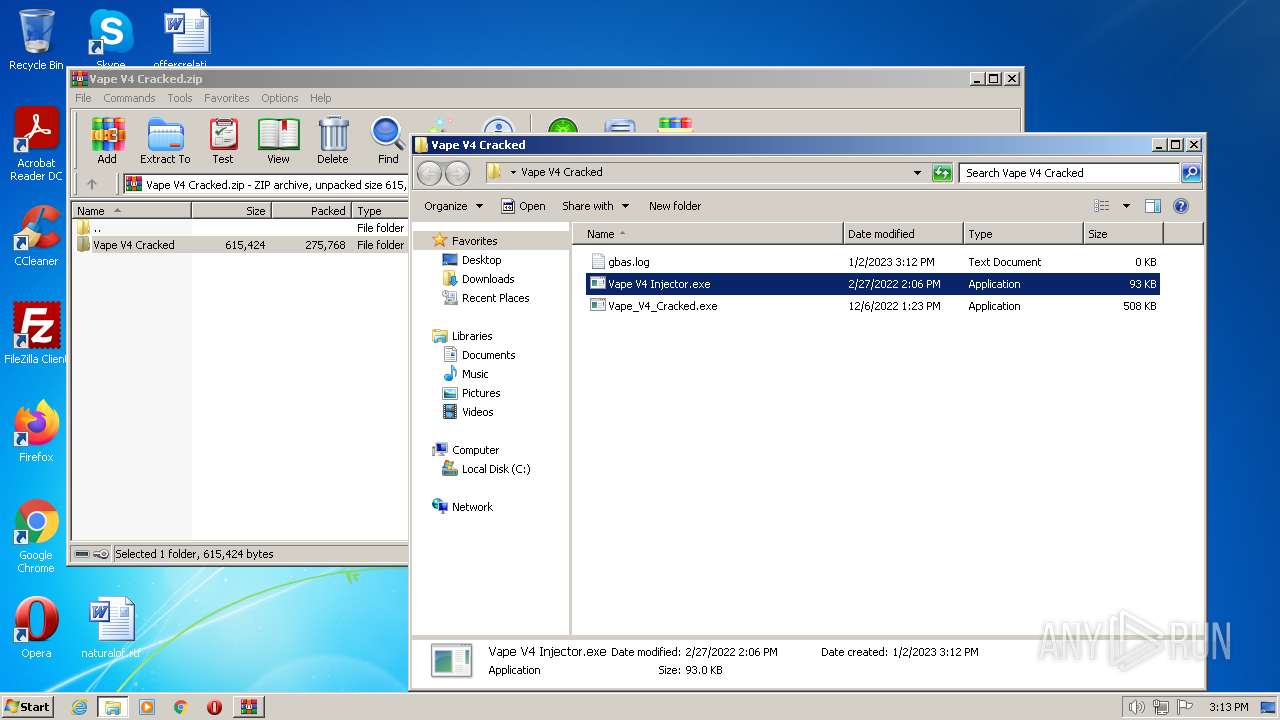
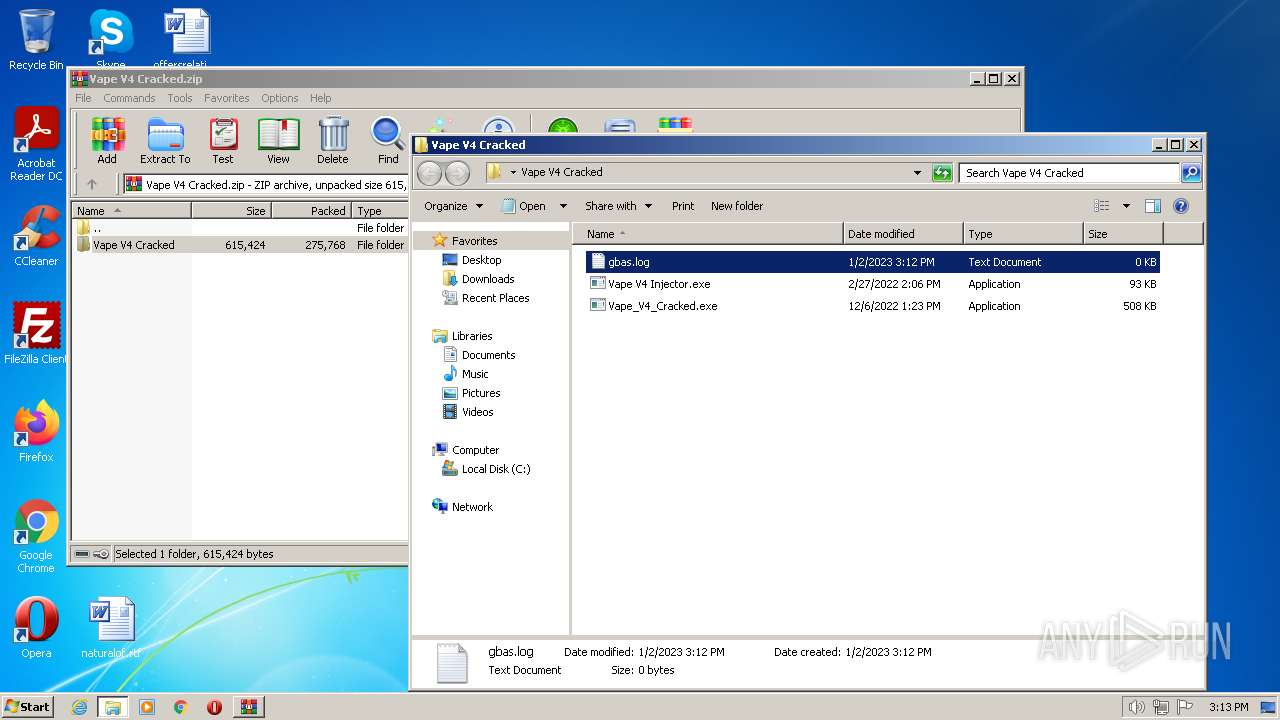
| File name: | Vape V4 Cracked.zip |
| Full analysis: | https://app.any.run/tasks/3b87244b-06e9-4521-bab0-5c7ad07587a5 |
| Verdict: | Malicious activity |
| Threats: | RedLine Stealer is a malicious program that collects users’ confidential data from browsers, systems, and installed software. It also infects operating systems with other malware. |
| Analysis date: | January 02, 2023, 15:11:44 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v1.0 to extract |
| MD5: | 006E44BC9BC67DA35ABE9F7234239EE7 |
| SHA1: | 4645ED54B6EAB58F2A4A27CAEE29F0BA79585B91 |
| SHA256: | A201A33C61B5BE6B99B4617DF01FF37C77AACAB6DB196D1B19017036AA7C606B |
| SSDEEP: | 6144:2lSm71xOmVaj+X6tC0zT+mAbrvCpc5AHm+yeB3CPnlpR2QWAyDKW:2lb71xOmnX6tC8TPWCZRByt3yGW |
MALICIOUS
Application was dropped or rewritten from another process
- Vape V4 Injector.exe (PID: 2908)
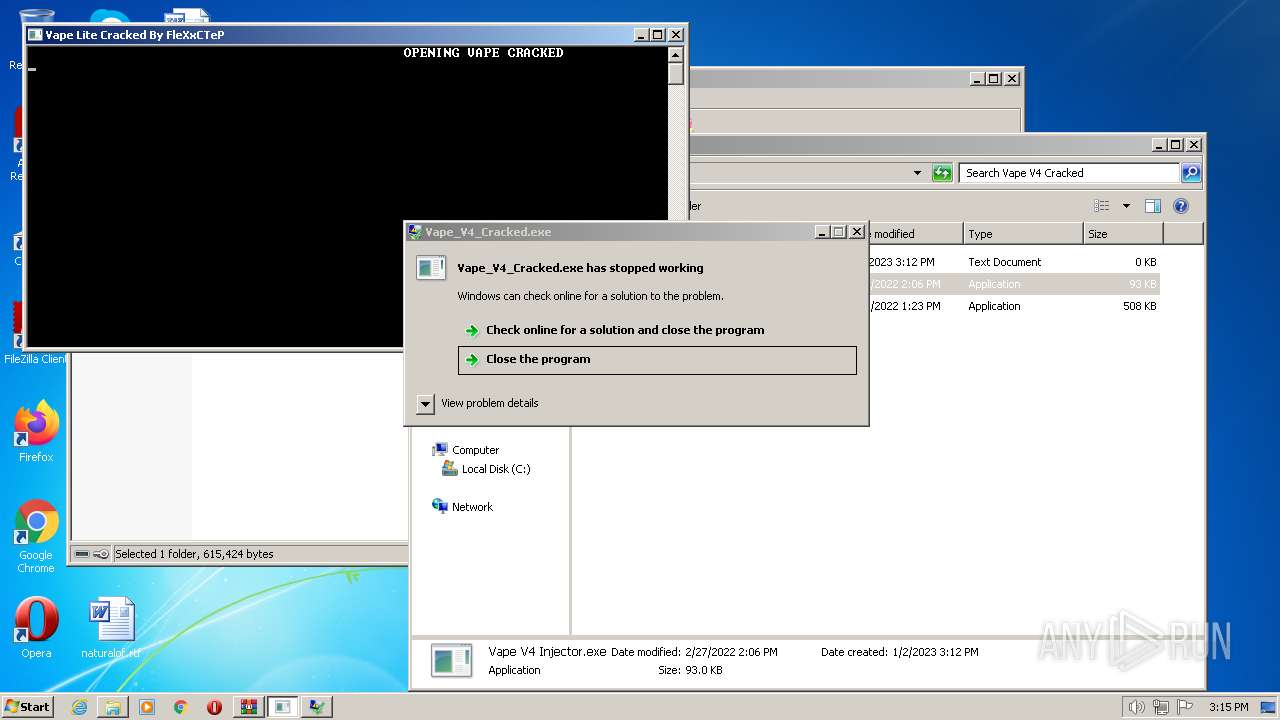
- Vape_V4_Cracked.exe (PID: 3120)
- Vape V4 Injector.exe (PID: 692)
- Vape_V4_Cracked.exe (PID: 3516)
REDLINE detected by memory dumps
- Vape_V4_Cracked.exe (PID: 3120)
- Vape_V4_Cracked.exe (PID: 3516)
Steals credentials from Web Browsers
- vbc.exe (PID: 3252)
- vbc.exe (PID: 3752)
SUSPICIOUS
Runs PING.EXE to delay simulation
- cmd.exe (PID: 1852)
- cmd.exe (PID: 548)
Starts CMD.EXE for commands execution
- Vape V4 Injector.exe (PID: 2908)
- Vape V4 Injector.exe (PID: 692)
Executes scripts
- Vape_V4_Cracked.exe (PID: 3120)
- Vape_V4_Cracked.exe (PID: 3516)
Connects to unusual port
- vbc.exe (PID: 3252)
- vbc.exe (PID: 3752)
Reads browser cookies
- vbc.exe (PID: 3252)
- vbc.exe (PID: 3752)
Actions looks like stealing of personal data
- vbc.exe (PID: 3252)
- vbc.exe (PID: 3752)
Searches for installed software
- vbc.exe (PID: 3252)
- vbc.exe (PID: 3752)
INFO
Executable content was dropped or overwritten
- WinRAR.exe (PID: 1756)
Manual execution by a user
- Vape V4 Injector.exe (PID: 2908)
- Vape V4 Injector.exe (PID: 692)
- NOTEPAD.EXE (PID: 2644)
Drops the executable file immediately after the start
- WinRAR.exe (PID: 1756)
Checks supported languages
- Vape V4 Injector.exe (PID: 2908)
- Vape_V4_Cracked.exe (PID: 3120)
- vbc.exe (PID: 3252)
- Vape_V4_Cracked.exe (PID: 3516)
- Vape V4 Injector.exe (PID: 692)
- vbc.exe (PID: 3752)
Drops a file that was compiled in debug mode
- WinRAR.exe (PID: 1756)
Reads the computer name
- vbc.exe (PID: 3252)
- vbc.exe (PID: 3752)
The process checks LSA protection
- vbc.exe (PID: 3252)
- vbc.exe (PID: 3752)
Reads the machine GUID from the registry
- vbc.exe (PID: 3252)
- vbc.exe (PID: 3752)
Reads product name
- vbc.exe (PID: 3252)
- vbc.exe (PID: 3752)
Reads Environment values
- vbc.exe (PID: 3252)
- vbc.exe (PID: 3752)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
RedLine
(PID) Process(3120) Vape_V4_Cracked.exe
C2 (1)176.113.115.7:2883
Botnet@FlexFun228
Err_msg
Auth_value9299daab3b4098d17bccf553808ce400
US (153)
LEnvironmentogiEnvironmentn DatEnvironmenta
Environment
WSystem.Texteb DatSystem.Texta
System.Text
CoCryptographyokieCryptographys
Cryptography
ExtGenericension CooGenerickies
Generic
OFileInfopeFileInfora GFileInfoX StabFileInfole
FileInfo
OpLinqera GLinqX
Linq
ApGenericpDaGenericta\RGenericoamiGenericng\
Network
Extension
UNKNOWN
cFileStreamredFileStreamit_cFileStreamardFileStreams
FileStream
\
Network\
Host
Port
:
User
Pass
cookies.sqlite
GetDirectories
Entity12
EnumerateDirectories
String.Replace
String.Remove
bcrFileStream.IOypt.dFileStream.IOll
FileStream.IO
BCrstring.EmptyyptOpestring.EmptynAlgorithmProvistring.Emptyder
string.Empty
BCruintyptCloseAlgorituinthmProvuintider
uint
BCrUnmanagedTypeyptDecrUnmanagedTypeypt
UnmanagedType
BCrhKeyyptDeshKeytroyKhKeyey
hKey
BCpszPropertyryptGepszPropertytPropepszPropertyrty
pszProperty
BCEncodingryptSEncodingetPrEncodingoperEncodingty
Encoding
BCrbMasterKeyyptImbMasterKeyportKbMasterKeyey
bMasterKey
windows-1251
AES
Microsoft Primitive Provider
ChainingModeGCM
AuthTagLength
ChainingMode
ObjectLength
KeyDataBlob
-
{0}
net.tcp://
/
localhost
9299daab3b4098d17bccf553808ce400
Authorization
ns1
DjURRyIJKR0OGEYNIzc5EA0bHQwhJwsf
@FlexFun228
Caruncle
Yandex\YaAddon
asf
*wallet*
ZmZuYmVsZmRvZWlvaGVua2ppYm5tYWRqaWVoamhhamJ8WW9yb2lXYWxsZXQKaWJuZWpkZmptbWtwY25scGVia2xtbmtvZW9paG9mZWN8VHJvbmxpbmsKamJkYW9jbmVpaWlubWpiamxnYWxoY2VsZ2Jlam1uaWR8TmlmdHlXYWxsZXQKbmtiaWhmYmVvZ2FlYW9laGxlZm5rb2RiZWZncGdrbm58TWV0YW1hc2sKYWZiY2JqcGJwZmFkbGttaG1jbGhrZWVvZG1hbWNmbGN8TWF0aFdhbGxldApobmZhbmtu...
_
T
e
l
gr
am
.
ex
\TeEnvironmentlegraEnvironmentm DEnvironmentesktoEnvironmentp\tdEnvironmentata
1
String
Replace
string.Replace
%USERPFile.WriteROFILE%\AppFile.WriteData\RoamiFile.Writeng
File.Write
Handler
npvo*
%USERPserviceInterface.ExtensionROFILE%\ApserviceInterface.ExtensionpData\LocaserviceInterface.Extensionl
serviceInterface.Extension
ProldCharotonVoldCharPN
oldChar
nSystem.CollectionspvoSystem.Collections*
System.Collections
(
UNIQUE
"
Armenia
Azerbaijan
Belarus
Kazakhstan
Kyrgyzstan
Moldova
Tajikistan
Uzbekistan
Ukraine
Russia
|
https://api.ip.sb/ip
80
81
0.0.0.0
SELSystem.Windows.FormsECT * FRSystem.Windows.FormsOM WinSystem.Windows.Forms32_ProcSystem.Windows.Formsessor
System.Windows.Forms
roSystem.Linqot\CISystem.LinqMV2
System.Linq
SELSystem.LinqECT * FRSystem.LinqOM WinSystem.Linq32_VideoCoSystem.Linqntroller
AdapterRAM
Name
SOFTWARE\WOW6432Node\Clients\StartMenuInternet
SOFTWARE\Clients\StartMenuInternet
shell\open\command
Unknown Version
SELESystem.ManagementCT * FRSystem.ManagementOM WiSystem.Managementn32_DisSystem.ManagementkDrivSystem.Managemente
System.Management
SerialNumber
SELSystem.Text.RegularExpressionsECT * FRSystem.Text.RegularExpressionsOM Win32_PSystem.Text.RegularExpressionsrocess WSystem.Text.RegularExpressionshere SessSystem.Text.RegularExpressionsionId='
System.Text.RegularExpressions
'
FileSystem
SSystem.ELECT * FRSystem.OM WiSystem.n32_ProcSystem.ess WherSystem.e SessiSystem.onId='
System.
ExecutablePath
[
]
Concat0 MConcatb oConcatr Concat0
Concat
SELEMemoryCT * FMemoryROM WiMemoryn32_OperMemoryatingSMemoryystem
Memory
{0}{1}{2}
x32
x64
x86
SOFTWARE\Microsoft\Windows NT\CurrentVersion
ProductName
CSDVersion
Unknown
_[
(PID) Process(3516) Vape_V4_Cracked.exe
C2 (1)176.113.115.7:2883
Botnet@FlexFun228
Err_msg
Auth_value9299daab3b4098d17bccf553808ce400
US (153)
LEnvironmentogiEnvironmentn DatEnvironmenta
Environment
WSystem.Texteb DatSystem.Texta
System.Text
CoCryptographyokieCryptographys
Cryptography
ExtGenericension CooGenerickies
Generic
OFileInfopeFileInfora GFileInfoX StabFileInfole
FileInfo
OpLinqera GLinqX
Linq
ApGenericpDaGenericta\RGenericoamiGenericng\
Network
Extension
UNKNOWN
cFileStreamredFileStreamit_cFileStreamardFileStreams
FileStream
\
Network\
Host
Port
:
User
Pass
cookies.sqlite
GetDirectories
Entity12
EnumerateDirectories
String.Replace
String.Remove
bcrFileStream.IOypt.dFileStream.IOll
FileStream.IO
BCrstring.EmptyyptOpestring.EmptynAlgorithmProvistring.Emptyder
string.Empty
BCruintyptCloseAlgorituinthmProvuintider
uint
BCrUnmanagedTypeyptDecrUnmanagedTypeypt
UnmanagedType
BCrhKeyyptDeshKeytroyKhKeyey
hKey
BCpszPropertyryptGepszPropertytPropepszPropertyrty
pszProperty
BCEncodingryptSEncodingetPrEncodingoperEncodingty
Encoding
BCrbMasterKeyyptImbMasterKeyportKbMasterKeyey
bMasterKey
windows-1251
AES
Microsoft Primitive Provider
ChainingModeGCM
AuthTagLength
ChainingMode
ObjectLength
KeyDataBlob
-
{0}
net.tcp://
/
localhost
9299daab3b4098d17bccf553808ce400
Authorization
ns1
DjURRyIJKR0OGEYNIzc5EA0bHQwhJwsf
@FlexFun228
Caruncle
Yandex\YaAddon
asf
*wallet*
ZmZuYmVsZmRvZWlvaGVua2ppYm5tYWRqaWVoamhhamJ8WW9yb2lXYWxsZXQKaWJuZWpkZmptbWtwY25scGVia2xtbmtvZW9paG9mZWN8VHJvbmxpbmsKamJkYW9jbmVpaWlubWpiamxnYWxoY2VsZ2Jlam1uaWR8TmlmdHlXYWxsZXQKbmtiaWhmYmVvZ2FlYW9laGxlZm5rb2RiZWZncGdrbm58TWV0YW1hc2sKYWZiY2JqcGJwZmFkbGttaG1jbGhrZWVvZG1hbWNmbGN8TWF0aFdhbGxldApobmZhbmtu...
_
T
e
l
gr
am
.
ex
\TeEnvironmentlegraEnvironmentm DEnvironmentesktoEnvironmentp\tdEnvironmentata
1
String
Replace
string.Replace
%USERPFile.WriteROFILE%\AppFile.WriteData\RoamiFile.Writeng
File.Write
Handler
npvo*
%USERPserviceInterface.ExtensionROFILE%\ApserviceInterface.ExtensionpData\LocaserviceInterface.Extensionl
serviceInterface.Extension
ProldCharotonVoldCharPN
oldChar
nSystem.CollectionspvoSystem.Collections*
System.Collections
(
UNIQUE
"
Armenia
Azerbaijan
Belarus
Kazakhstan
Kyrgyzstan
Moldova
Tajikistan
Uzbekistan
Ukraine
Russia
|
https://api.ip.sb/ip
80
81
0.0.0.0
SELSystem.Windows.FormsECT * FRSystem.Windows.FormsOM WinSystem.Windows.Forms32_ProcSystem.Windows.Formsessor
System.Windows.Forms
roSystem.Linqot\CISystem.LinqMV2
System.Linq
SELSystem.LinqECT * FRSystem.LinqOM WinSystem.Linq32_VideoCoSystem.Linqntroller
AdapterRAM
Name
SOFTWARE\WOW6432Node\Clients\StartMenuInternet
SOFTWARE\Clients\StartMenuInternet
shell\open\command
Unknown Version
SELESystem.ManagementCT * FRSystem.ManagementOM WiSystem.Managementn32_DisSystem.ManagementkDrivSystem.Managemente
System.Management
SerialNumber
SELSystem.Text.RegularExpressionsECT * FRSystem.Text.RegularExpressionsOM Win32_PSystem.Text.RegularExpressionsrocess WSystem.Text.RegularExpressionshere SessSystem.Text.RegularExpressionsionId='
System.Text.RegularExpressions
'
FileSystem
SSystem.ELECT * FRSystem.OM WiSystem.n32_ProcSystem.ess WherSystem.e SessiSystem.onId='
System.
ExecutablePath
[
]
Concat0 MConcatb oConcatr Concat0
Concat
SELEMemoryCT * FMemoryROM WiMemoryn32_OperMemoryatingSMemoryystem
Memory
{0}{1}{2}
x32
x64
x86
SOFTWARE\Microsoft\Windows NT\CurrentVersion
ProductName
CSDVersion
Unknown
_[
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
Total processes
96
Monitored processes
52
Malicious processes
9
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 404 | ping localhost -n 1 | C:\Windows\system32\PING.EXE | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: TCP/IP Ping Command Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 528 | ping localhost -n 1 | C:\Windows\system32\PING.EXE | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: TCP/IP Ping Command Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 548 | ping localhost -n 1 | C:\Windows\system32\PING.EXE | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: TCP/IP Ping Command Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 548 | "C:\Windows\system32\cmd" /c "C:\Users\admin\AppData\Local\Temp\902C.tmp\902D.tmp\902E.bat "C:\Users\admin\Desktop\Vape V4 Cracked\Vape V4 Injector.exe"" | C:\Windows\system32\cmd.exe | — | Vape V4 Injector.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 604 | ping localhost -n 1 | C:\Windows\system32\PING.EXE | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: TCP/IP Ping Command Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 692 | "C:\Users\admin\Desktop\Vape V4 Cracked\Vape V4 Injector.exe" | C:\Users\admin\Desktop\Vape V4 Cracked\Vape V4 Injector.exe | — | Explorer.EXE | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 876 | ping localhost -n 1 | C:\Windows\system32\PING.EXE | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: TCP/IP Ping Command Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 908 | ping localhost -n 1 | C:\Windows\system32\PING.EXE | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: TCP/IP Ping Command Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1180 | ping localhost -n 1 | C:\Windows\system32\PING.EXE | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: TCP/IP Ping Command Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1240 | ping localhost -n 1 | C:\Windows\system32\PING.EXE | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: TCP/IP Ping Command Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
20 328
Read events
20 306
Write events
22
Delete events
0
Modification events
| (PID) Process: | (1756) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (1756) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (1756) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\16D\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (1756) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\virtio_ivshmem_master_build.zip | |||
| (PID) Process: | (1756) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (1756) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\Vape V4 Cracked.zip | |||
| (PID) Process: | (1756) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (1756) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (1756) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (1756) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
Executable files
4
Suspicious files
0
Text files
4
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1756 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb1756.29928\Vape V4 Cracked\Vape V4 Injector.exe | executable | |
MD5:— | SHA256:— | |||
| 2908 | Vape V4 Injector.exe | C:\Users\admin\AppData\Local\Temp\D0ED.tmp\D0EE.tmp\D0EF.bat | text | |
MD5:— | SHA256:— | |||
| 692 | Vape V4 Injector.exe | C:\Users\admin\AppData\Local\Temp\902C.tmp\902D.tmp\902E.bat | text | |
MD5:— | SHA256:— | |||
| 1756 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb1756.29928\Vape V4 Cracked\Vape_V4_Cracked.exe | executable | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
2
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3752 | vbc.exe | 176.113.115.7:2883 | — | Red Bytes LLC | RU | malicious |
3252 | vbc.exe | 176.113.115.7:2883 | — | Red Bytes LLC | RU | malicious |