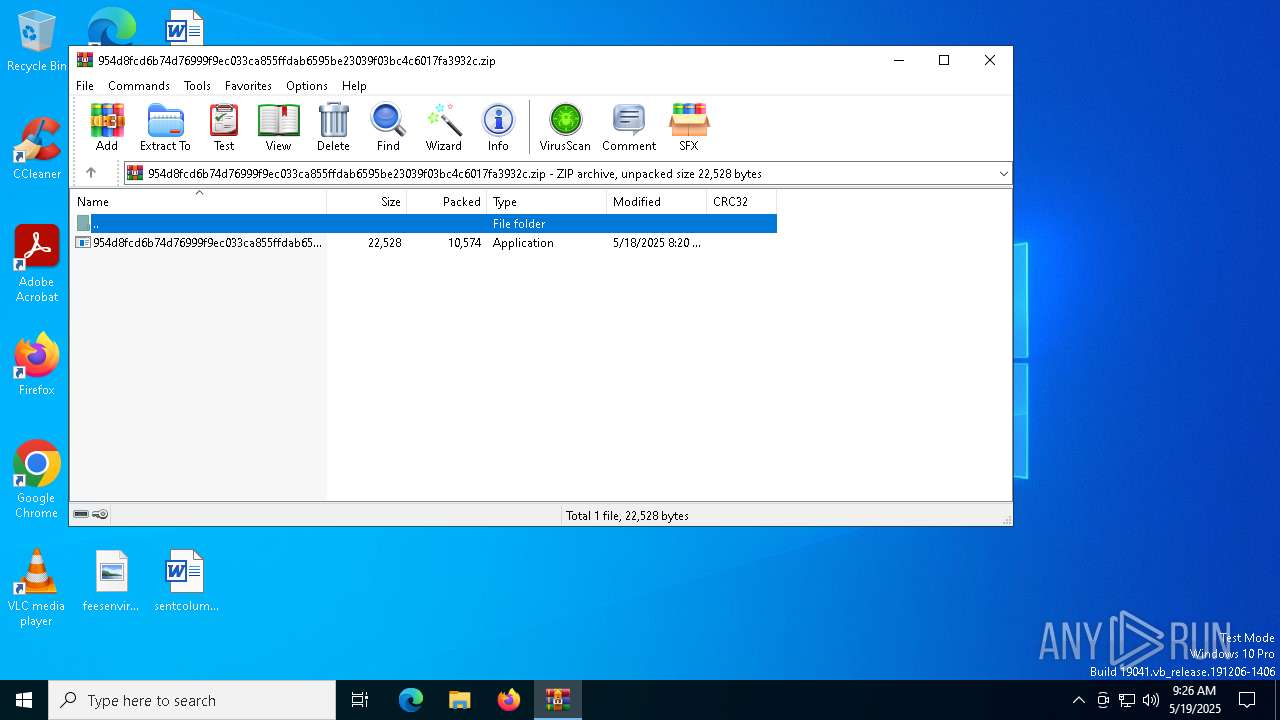
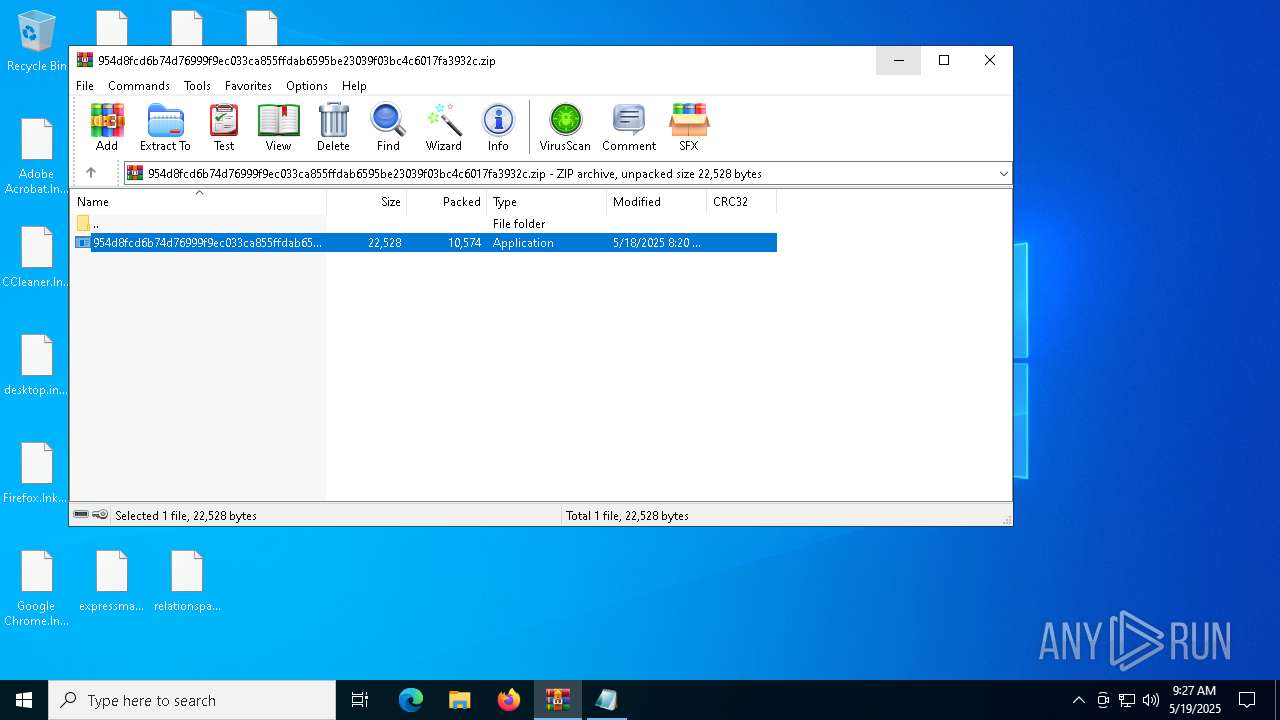
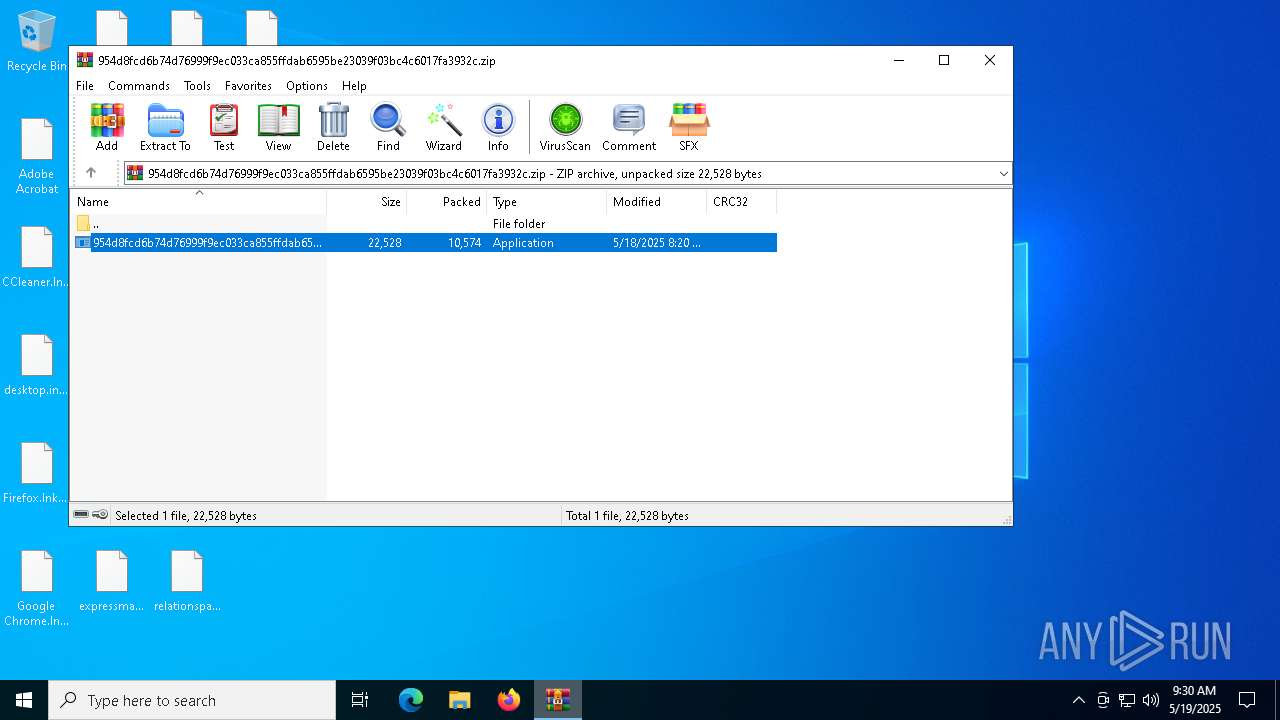
| File name: | 954d8fcd6b74d76999f9ec033ca855ffdab6595be23039f03bc4c6017fa3932c.zip |
| Full analysis: | https://app.any.run/tasks/b400e2c4-57c3-4cad-bf92-4cb9b290927c |
| Verdict: | Malicious activity |
| Threats: | Chaos ransomware is a malware family known for its destructive capabilities and diverse variants. It first appeared in 2021 as a ransomware builder and later acted as a wiper. Unlike most ransomware strains that encrypt data to extort payment, early Chaos variants permanently corrupted files, while later versions adopted more conventional encryption techniques. |
| Analysis date: | May 19, 2025, 09:26:19 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
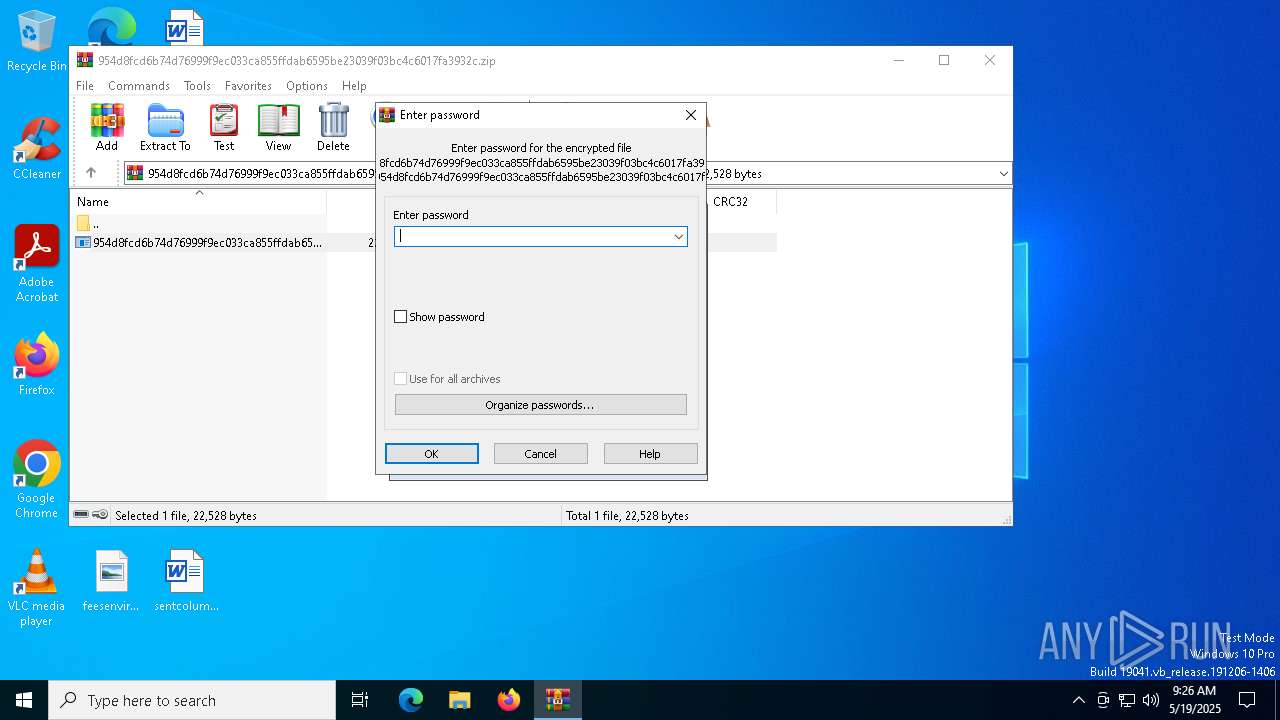
| File info: | Zip archive data, at least v5.1 to extract, compression method=AES Encrypted |
| MD5: | A05CE871E3EC26C8A78C275AA92E0D6D |
| SHA1: | C695ECDE0924471E64BE6402F70EDCAD484E8AA6 |
| SHA256: | A0D3403E803BEB821C9CD39708DD2ED870206220AAD137C08A4C57EAB2B54DFE |
| SSDEEP: | 384:c1S6ynthDlepMDy5hKC9p0lqg48KTQqRrveh:ck68jZZC9pI48KTZjeh |
MALICIOUS
Generic archive extractor
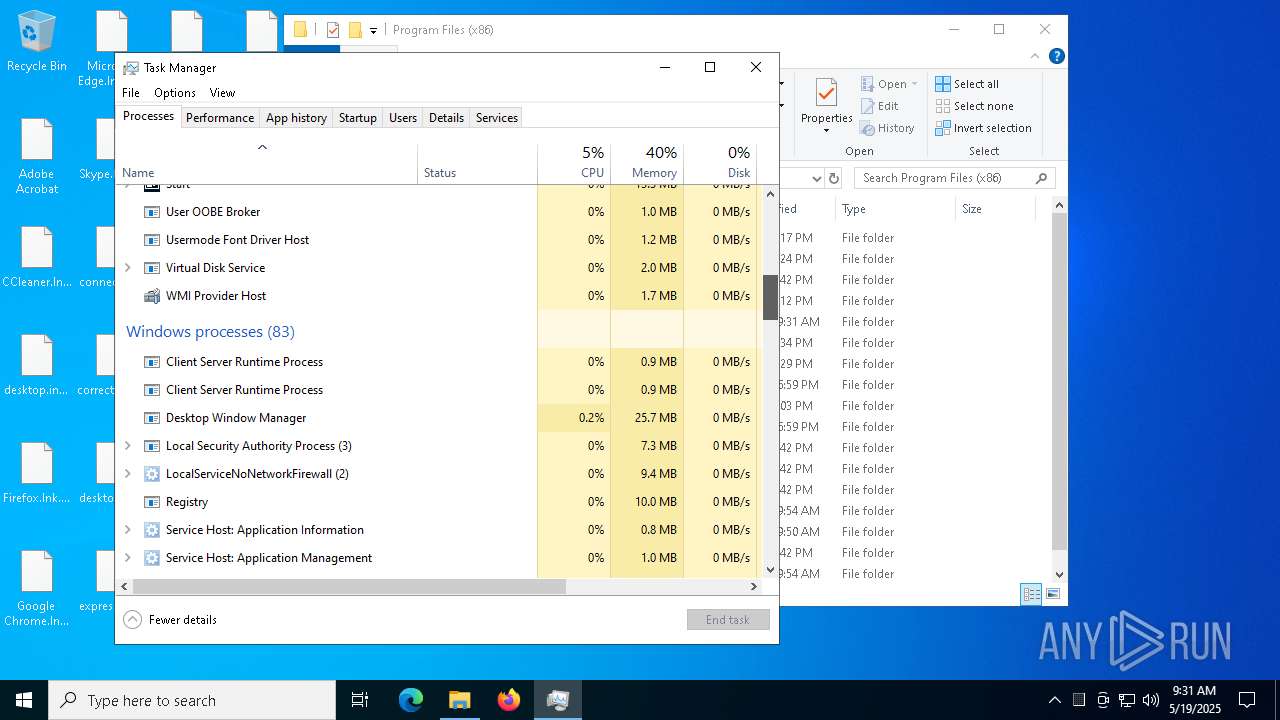
- WinRAR.exe (PID: 6480)
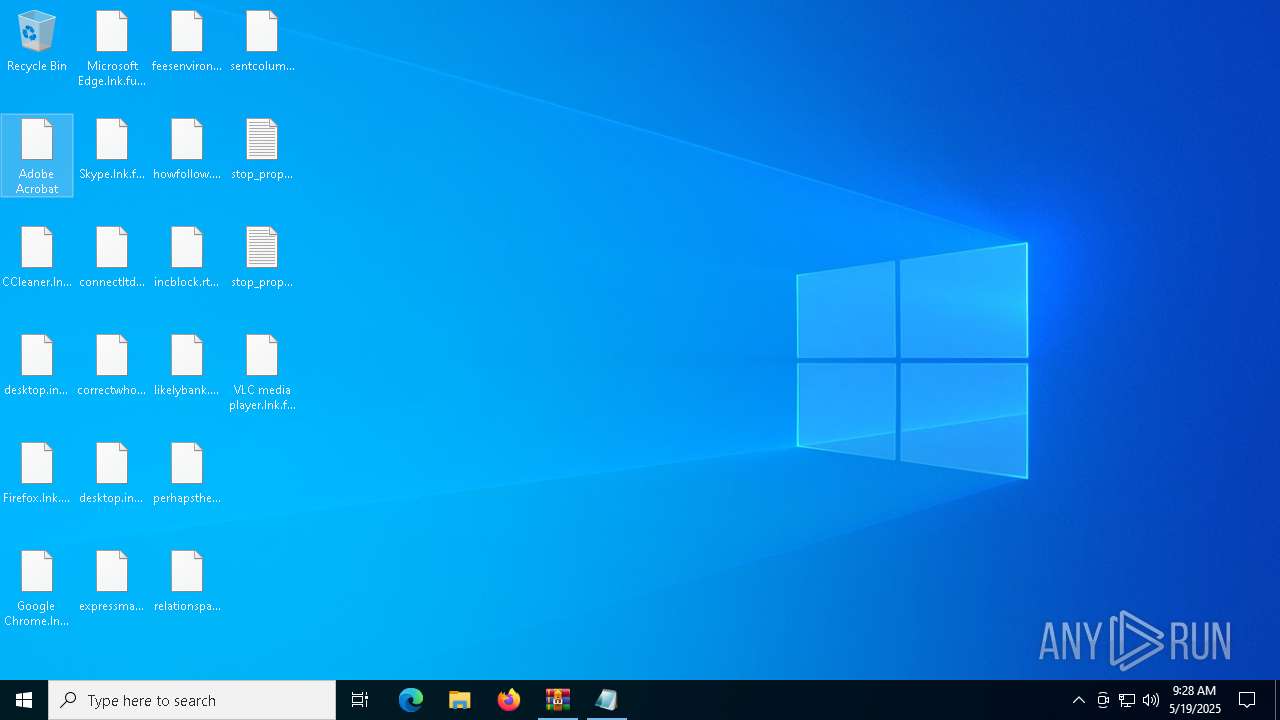
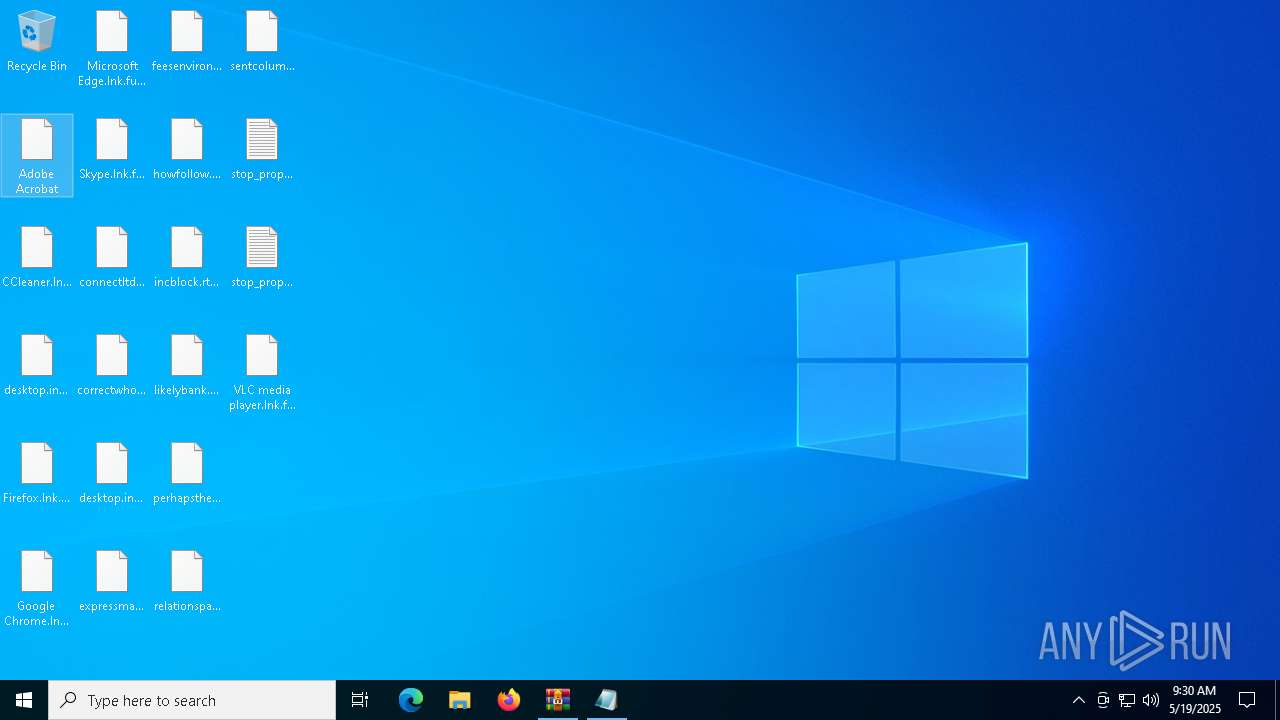
Create files in the Startup directory
- svchost.exe (PID: 5380)
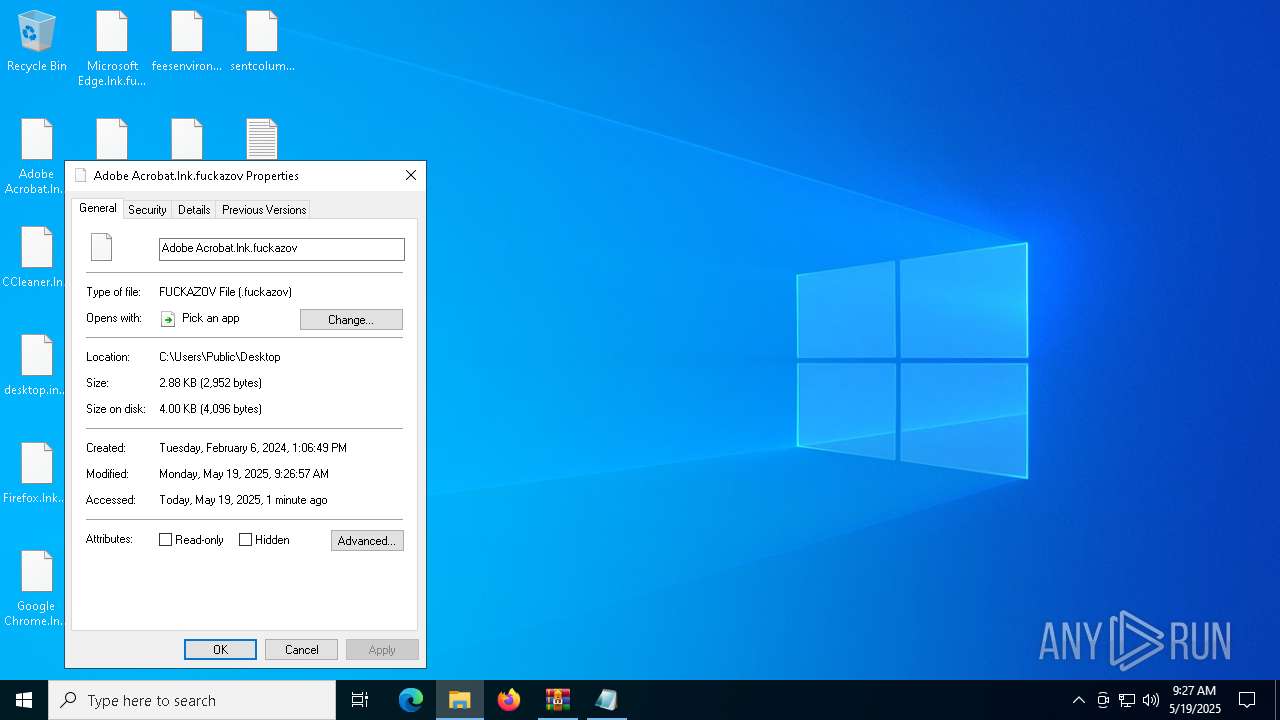
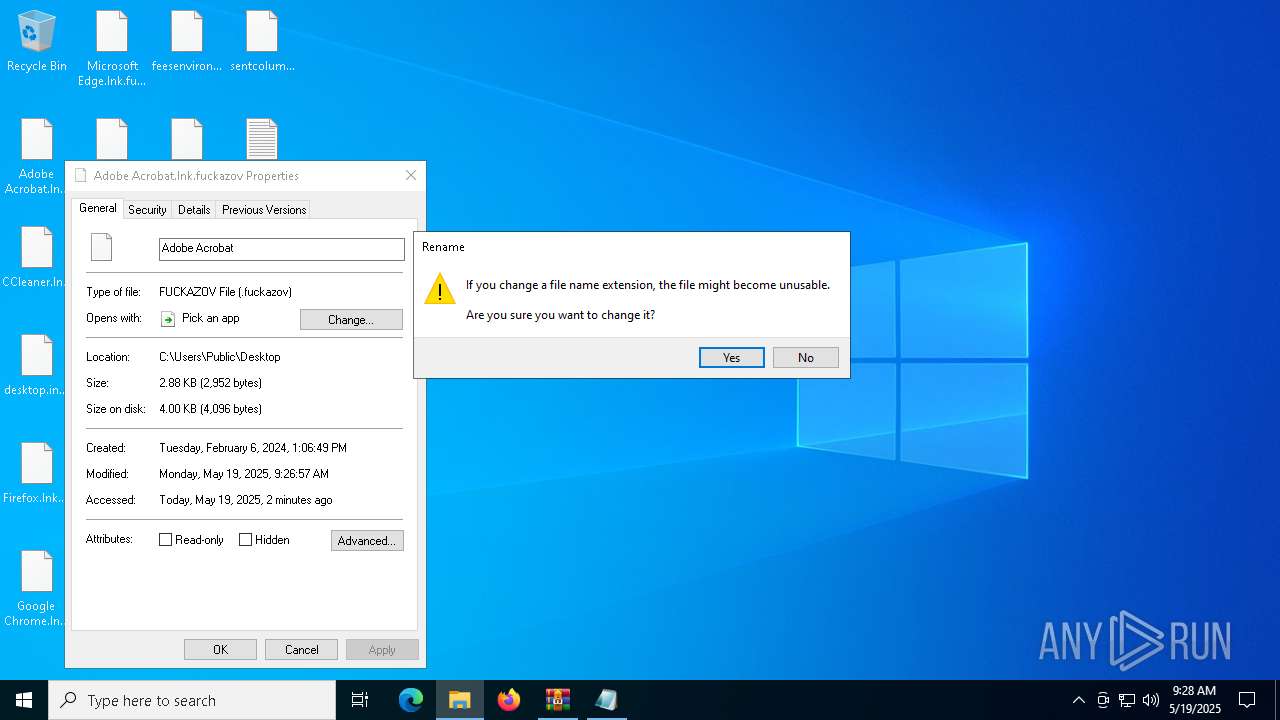
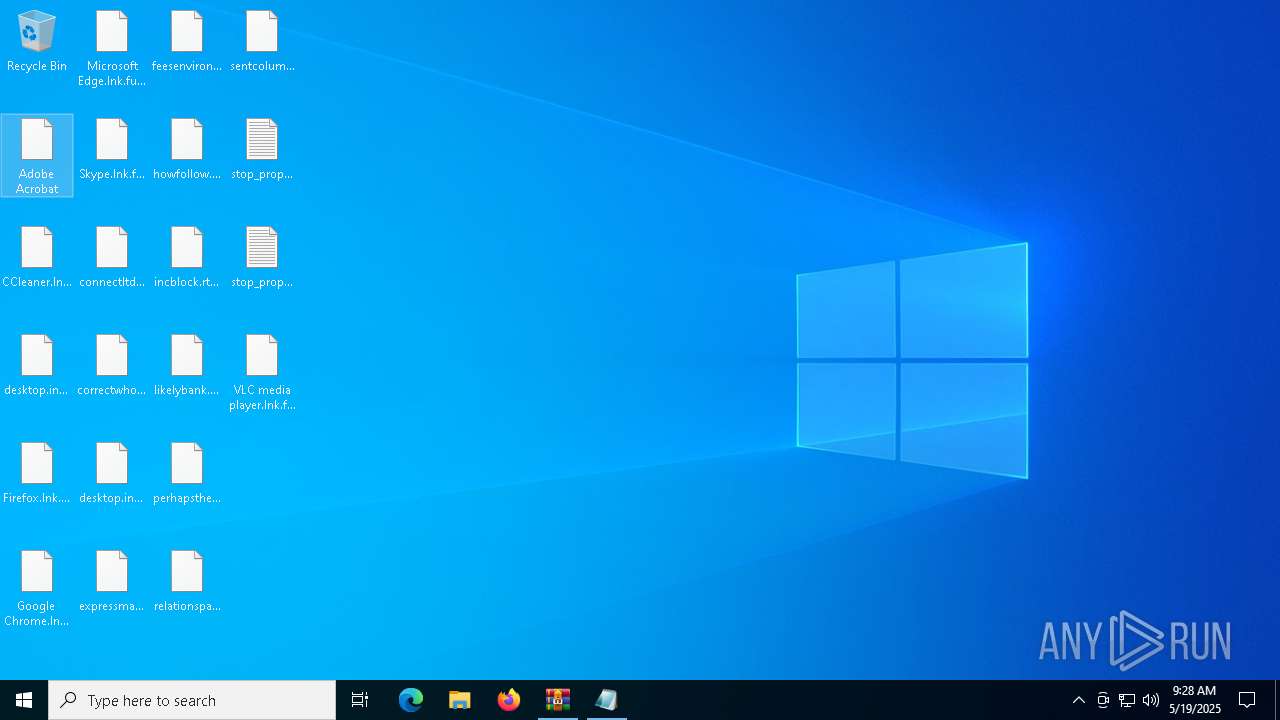
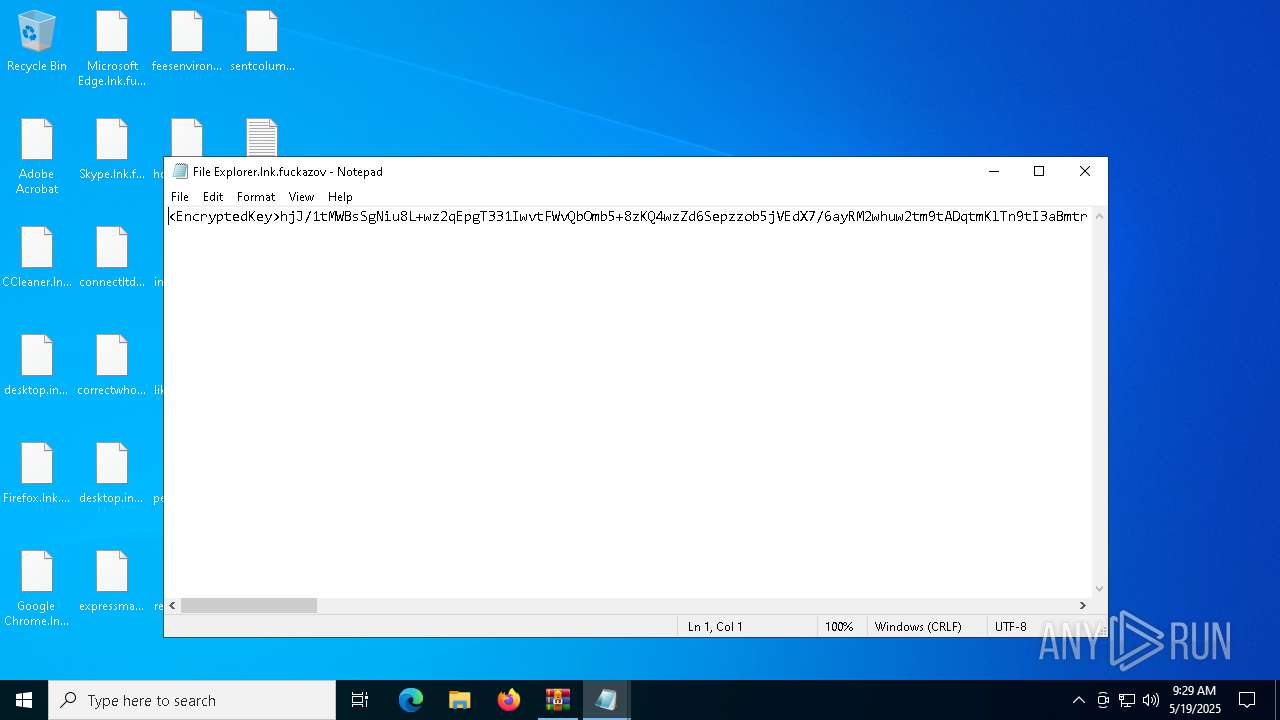
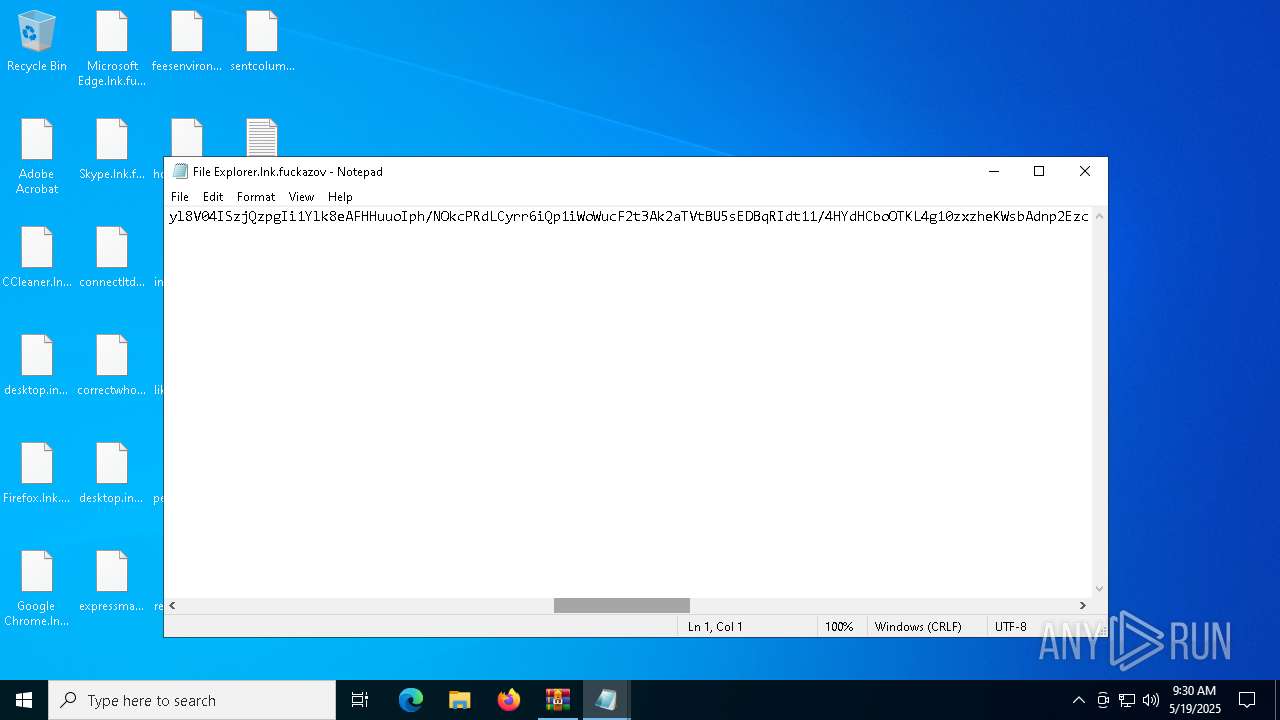
Renames files like ransomware
- svchost.exe (PID: 5380)
RANSOMWARE has been detected
- svchost.exe (PID: 5380)
CHAOS has been detected (YARA)
- svchost.exe (PID: 5380)
Deletes shadow copies
- cmd.exe (PID: 3676)
- cmd.exe (PID: 6068)
Using BCDEDIT.EXE to modify recovery options
- cmd.exe (PID: 4776)
SUSPICIOUS
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 6480)
- 954d8fcd6b74d76999f9ec033ca855ffdab6595be23039f03bc4c6017fa3932c.exe (PID: 4776)
- svchost.exe (PID: 5380)
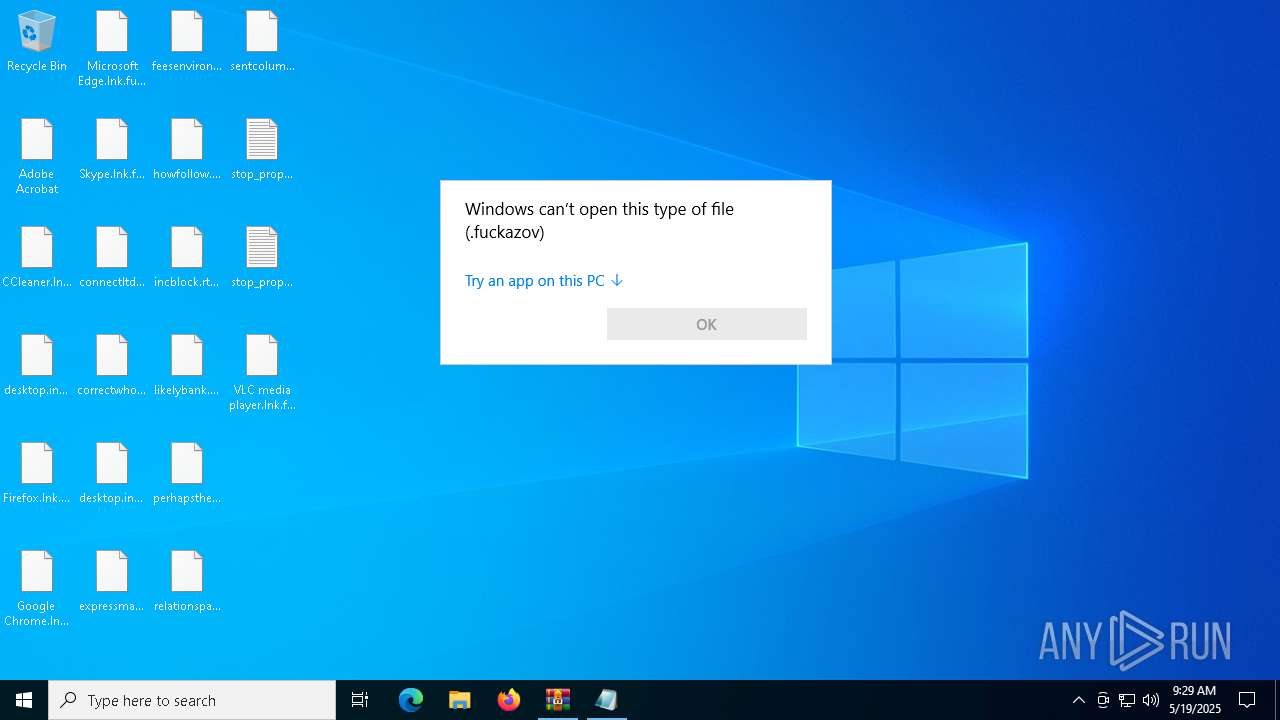
The process creates files with name similar to system file names
- 954d8fcd6b74d76999f9ec033ca855ffdab6595be23039f03bc4c6017fa3932c.exe (PID: 4776)
Executable content was dropped or overwritten
- 954d8fcd6b74d76999f9ec033ca855ffdab6595be23039f03bc4c6017fa3932c.exe (PID: 4776)
Reads the date of Windows installation
- 954d8fcd6b74d76999f9ec033ca855ffdab6595be23039f03bc4c6017fa3932c.exe (PID: 4776)
- svchost.exe (PID: 5380)
Starts itself from another location
- 954d8fcd6b74d76999f9ec033ca855ffdab6595be23039f03bc4c6017fa3932c.exe (PID: 4776)
Write to the desktop.ini file (may be used to cloak folders)
- svchost.exe (PID: 5380)
Found regular expressions for crypto-addresses (YARA)
- svchost.exe (PID: 5380)
Starts CMD.EXE for commands execution
- svchost.exe (PID: 5380)
Executes as Windows Service
- VSSVC.exe (PID: 4560)
- wbengine.exe (PID: 5344)
- vds.exe (PID: 2616)
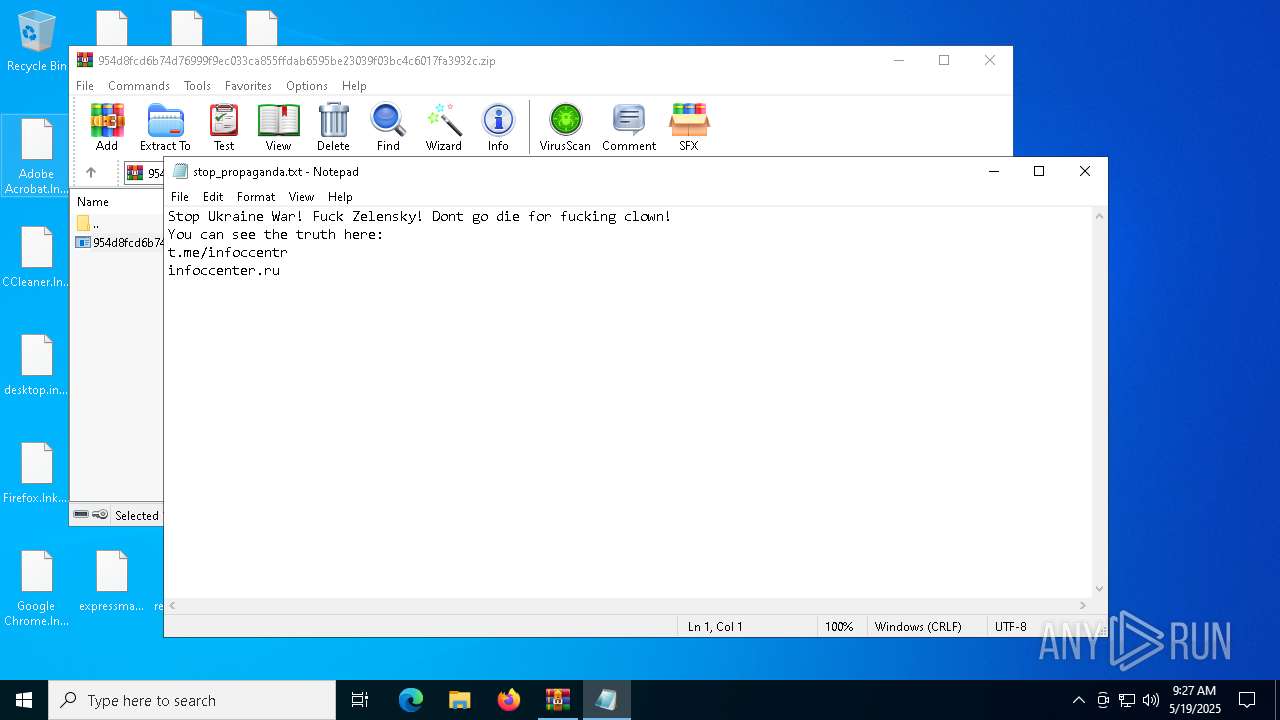
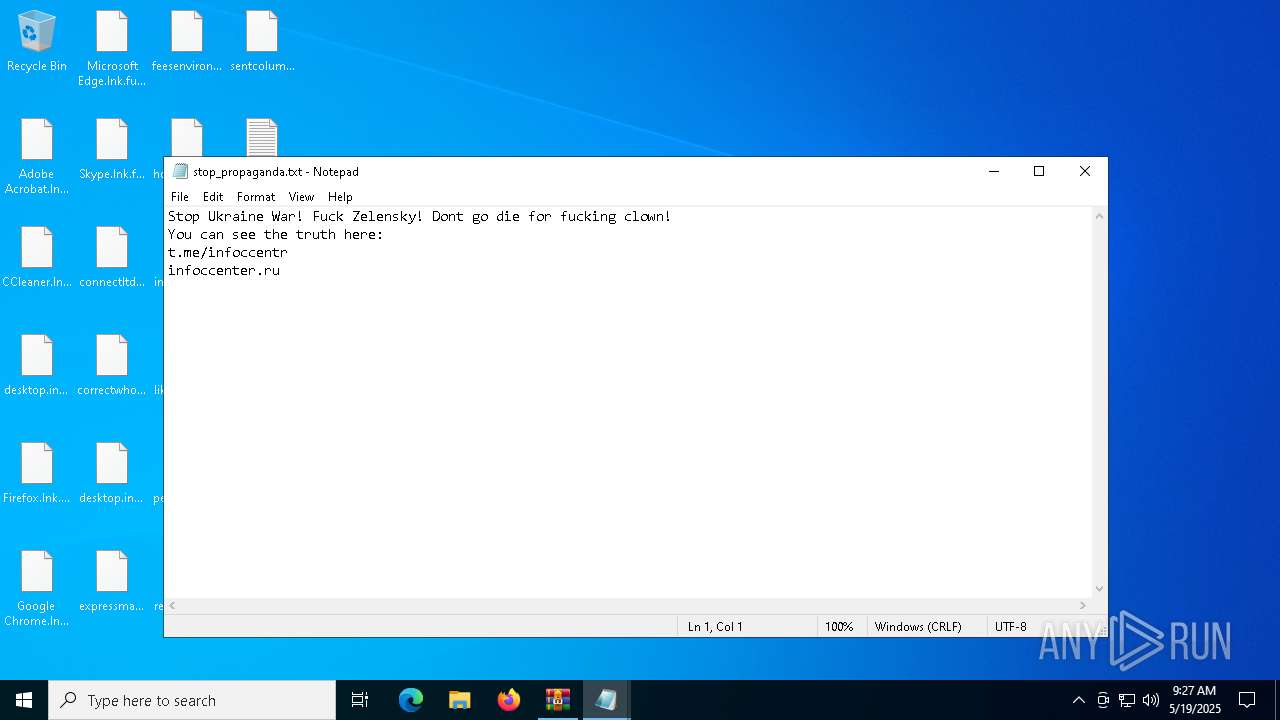
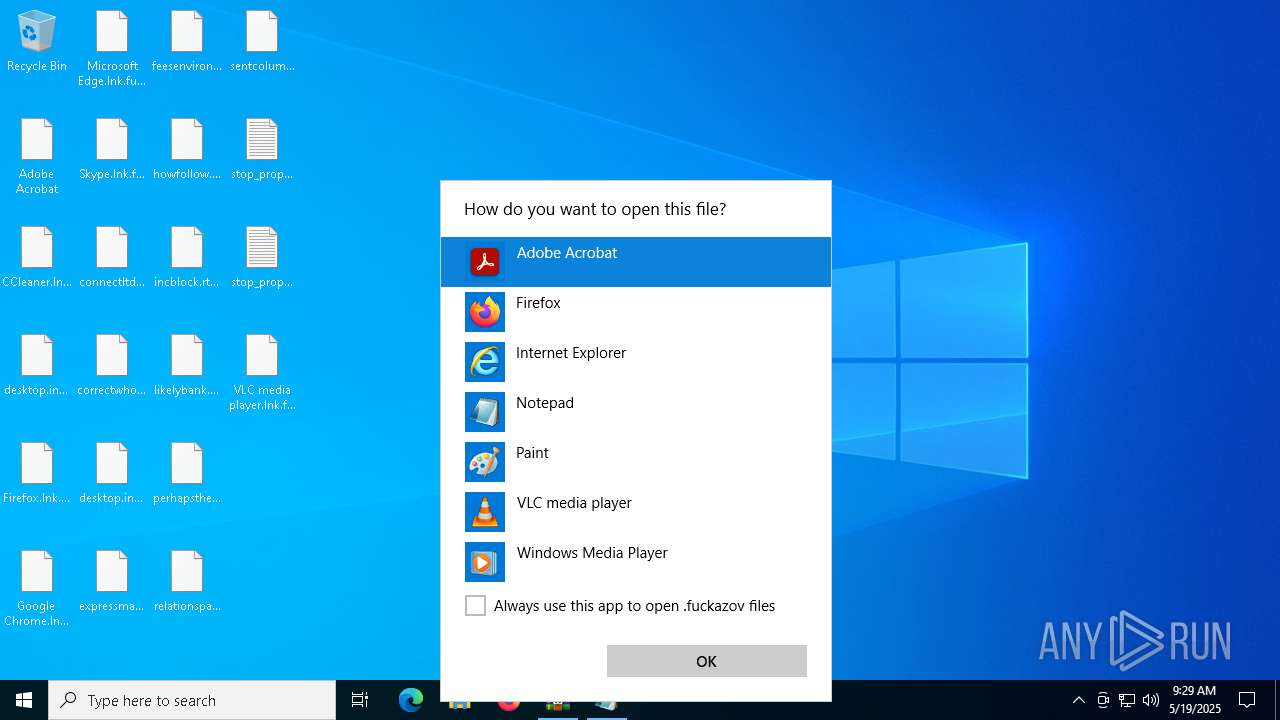
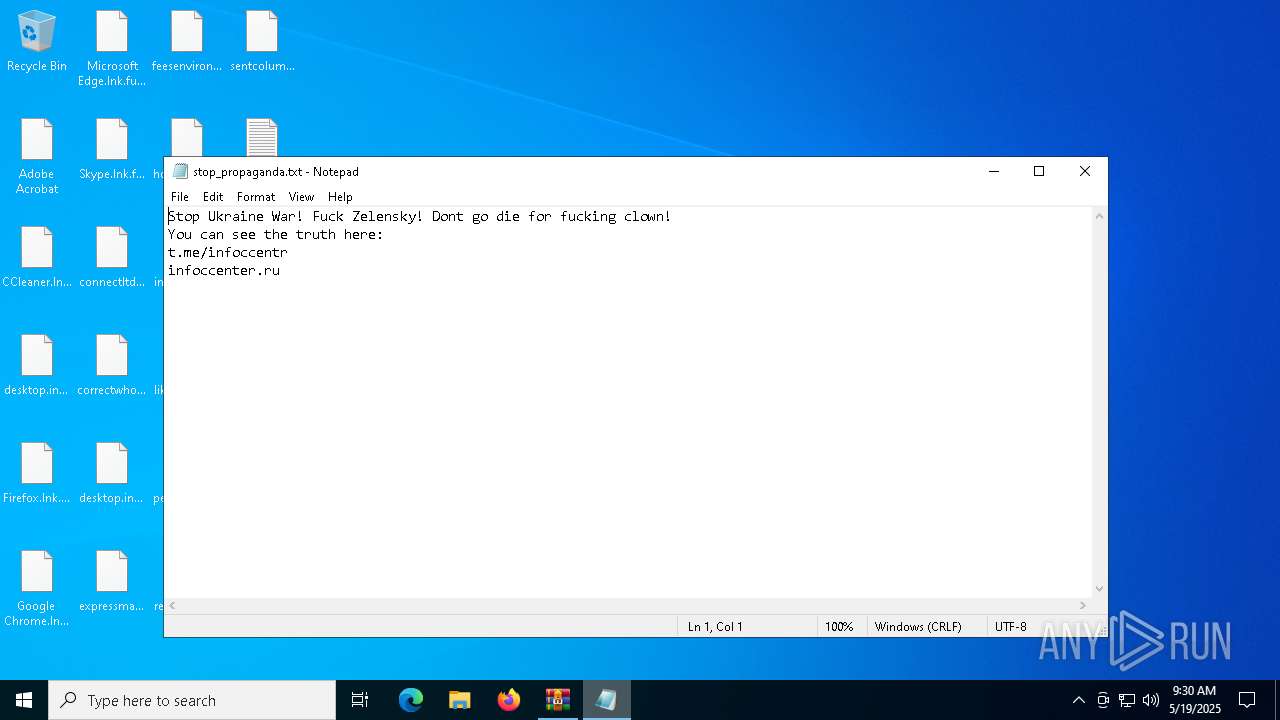
Start notepad (likely ransomware note)
- svchost.exe (PID: 5380)
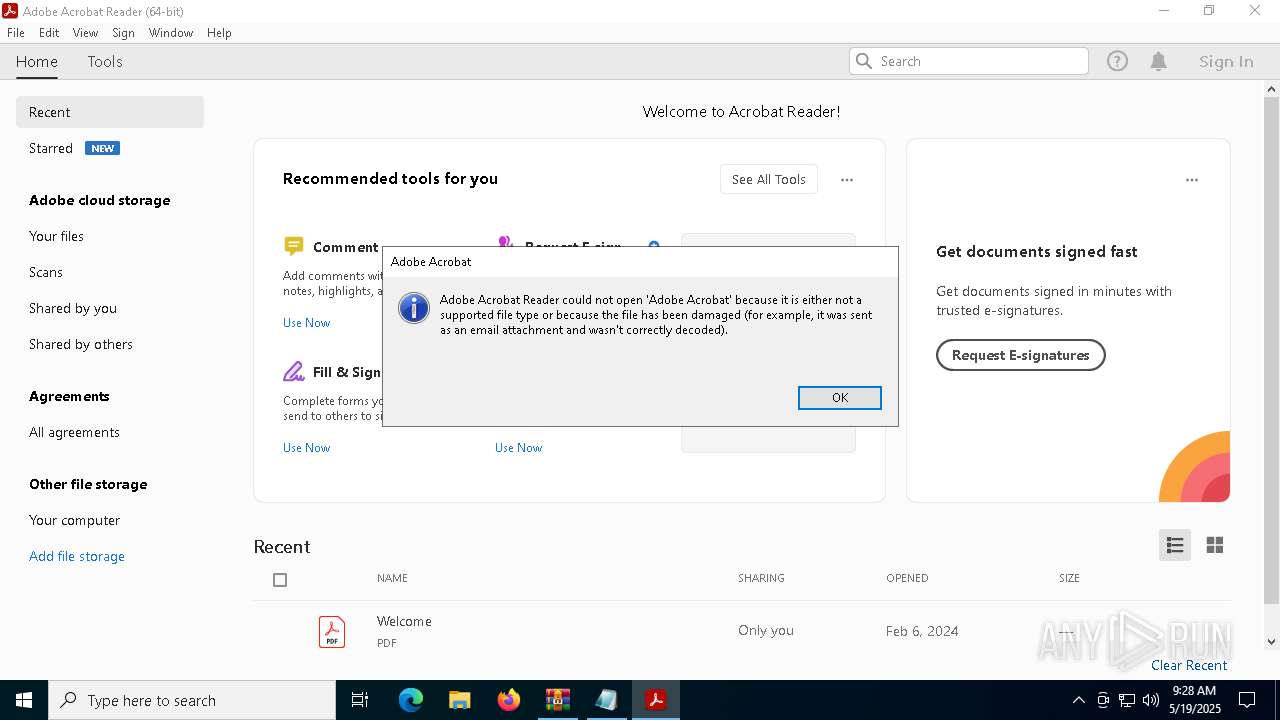
Likely accesses (executes) a file from the Public directory
- notepad.exe (PID: 744)
- Acrobat.exe (PID: 6980)
- Acrobat.exe (PID: 1760)
INFO
Executable content was dropped or overwritten
- WinRAR.exe (PID: 6480)
Checks supported languages
- 954d8fcd6b74d76999f9ec033ca855ffdab6595be23039f03bc4c6017fa3932c.exe (PID: 4776)
- svchost.exe (PID: 5380)
Creates files or folders in the user directory
- 954d8fcd6b74d76999f9ec033ca855ffdab6595be23039f03bc4c6017fa3932c.exe (PID: 4776)
- svchost.exe (PID: 5380)
Reads the computer name
- 954d8fcd6b74d76999f9ec033ca855ffdab6595be23039f03bc4c6017fa3932c.exe (PID: 4776)
- svchost.exe (PID: 5380)
Process checks computer location settings
- 954d8fcd6b74d76999f9ec033ca855ffdab6595be23039f03bc4c6017fa3932c.exe (PID: 4776)
- svchost.exe (PID: 5380)
Reads the machine GUID from the registry
- svchost.exe (PID: 5380)
Reads security settings of Internet Explorer
- WMIC.exe (PID: 5772)
- notepad.exe (PID: 1388)
- notepad.exe (PID: 1116)
- notepad.exe (PID: 744)
- dllhost.exe (PID: 5624)
- OpenWith.exe (PID: 4284)
Reads Microsoft Office registry keys
- svchost.exe (PID: 5380)
- OpenWith.exe (PID: 5956)
- OpenWith.exe (PID: 4112)
- OpenWith.exe (PID: 4284)
Manual execution by a user
- notepad.exe (PID: 1116)
- GoogleUpdate.exe (PID: 6268)
- Taskmgr.exe (PID: 2432)
- Taskmgr.exe (PID: 5048)
- notepad.exe (PID: 744)
Application launched itself
- Acrobat.exe (PID: 1760)
- AcroCEF.exe (PID: 6540)
Checks proxy server information
- slui.exe (PID: 2772)
Reads the software policy settings
- slui.exe (PID: 2772)
- slui.exe (PID: 6640)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 51 |
|---|---|
| ZipBitFlag: | 0x0003 |
| ZipCompression: | Unknown (99) |
| ZipModifyDate: | 2025:05:18 20:20:42 |
| ZipCRC: | 0x9fe3fe0d |
| ZipCompressedSize: | 10574 |
| ZipUncompressedSize: | 22528 |
| ZipFileName: | 954d8fcd6b74d76999f9ec033ca855ffdab6595be23039f03bc4c6017fa3932c.exe |
Total processes
179
Monitored processes
46
Malicious processes
5
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 240 | "C:\Program Files\Adobe\Acrobat DC\Acrobat\acrocef_1\AcroCEF.exe" --type=renderer --log-severity=disable --user-agent-product="ReaderServices/23.1.20093 Chrome/105.0.0.0" --first-renderer-process --log-file="C:\Program Files\Adobe\Acrobat DC\Acrobat\acrocef_1\debug.log" --touch-events=enabled --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=5 --mojo-platform-channel-handle=2324 --field-trial-handle=1596,i,14595853487436397744,6398009922681687235,131072 --disable-features=BackForwardCache,CalculateNativeWinOcclusion,WinUseBrowserSpellChecker /prefetch:1 | C:\Program Files\Adobe\Acrobat DC\Acrobat\acrocef_1\AcroCEF.exe | — | AcroCEF.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: LOW Description: Adobe AcroCEF Exit code: 0 Version: 23.1.20093.0 Modules
| |||||||||||||||
| 348 | C:\WINDOWS\system32\OpenWith.exe -Embedding | C:\Windows\System32\OpenWith.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Pick an app Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 456 | "C:\Program Files\Adobe\Acrobat DC\Acrobat\acrocef_1\AcroCEF.exe" --type=renderer --log-severity=disable --user-agent-product="ReaderServices/23.1.20093 Chrome/105.0.0.0" --log-file="C:\Program Files\Adobe\Acrobat DC\Acrobat\acrocef_1\debug.log" --touch-events=enabled --disable-gpu-compositing --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=8 --mojo-platform-channel-handle=2860 --field-trial-handle=1596,i,14595853487436397744,6398009922681687235,131072 --disable-features=BackForwardCache,CalculateNativeWinOcclusion,WinUseBrowserSpellChecker /prefetch:1 | C:\Program Files\Adobe\Acrobat DC\Acrobat\acrocef_1\AcroCEF.exe | — | AcroCEF.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: LOW Description: Adobe AcroCEF Exit code: 0 Version: 23.1.20093.0 Modules
| |||||||||||||||
| 744 | "C:\WINDOWS\system32\NOTEPAD.EXE" C:\Users\Public\Desktop\stop_propaganda.txt | C:\Windows\System32\notepad.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1096 | "C:\Program Files\Adobe\Acrobat DC\Acrobat\acrocef_1\AcroCEF.exe" --type=gpu-process --log-severity=disable --user-agent-product="ReaderServices/23.1.20093 Chrome/105.0.0.0" --lang=en-US --gpu-preferences=UAAAAAAAAADgACAYAAAAAAAAAAAAAAAAAABgAAAAAAAwAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAEgAAAAAAAAASAAAAAAAAAAYAAAAAgAAABAAAAAAAAAAGAAAAAAAAAAQAAAAAAAAAAAAAAAOAAAAEAAAAAAAAAABAAAADgAAAAgAAAAAAAAACAAAAAAAAAA= --use-gl=angle --use-angle=swiftshader-webgl --log-file="C:\Program Files\Adobe\Acrobat DC\Acrobat\acrocef_1\debug.log" --mojo-platform-channel-handle=2660 --field-trial-handle=1596,i,14595853487436397744,6398009922681687235,131072 --disable-features=BackForwardCache,CalculateNativeWinOcclusion,WinUseBrowserSpellChecker /prefetch:2 | C:\Program Files\Adobe\Acrobat DC\Acrobat\acrocef_1\AcroCEF.exe | — | AcroCEF.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: LOW Description: Adobe AcroCEF Exit code: 0 Version: 23.1.20093.0 Modules
| |||||||||||||||
| 1116 | "C:\WINDOWS\system32\NOTEPAD.EXE" C:\Users\admin\Desktop\stop_propaganda.txt | C:\Windows\System32\notepad.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1348 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1388 | "C:\WINDOWS\system32\NOTEPAD.EXE" C:\Users\admin\AppData\Roaming\stop_propaganda.txt | C:\Windows\System32\notepad.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Notepad Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1760 | "C:\Program Files\Adobe\Acrobat DC\Acrobat\Acrobat.exe" "C:\Users\Public\Desktop\Adobe Acrobat" | C:\Program Files\Adobe\Acrobat DC\Acrobat\Acrobat.exe | — | OpenWith.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: MEDIUM Description: Adobe Acrobat Exit code: 1 Version: 23.1.20093.0 Modules
| |||||||||||||||
| 2268 | vssadmin delete shadows /all /quiet | C:\Windows\System32\vssadmin.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Command Line Interface for Microsoft® Volume Shadow Copy Service Exit code: 2 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
31 089
Read events
30 846
Write events
210
Delete events
33
Modification events
| (PID) Process: | (6480) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (6480) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (6480) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (6480) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\954d8fcd6b74d76999f9ec033ca855ffdab6595be23039f03bc4c6017fa3932c.zip | |||
| (PID) Process: | (6480) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (6480) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (6480) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (6480) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (6480) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface |
| Operation: | write | Name: | ShowPassword |
Value: 0 | |||
| (PID) Process: | (7156) bcdedit.exe | Key: | HKEY_LOCAL_MACHINE\BCD00000000\Objects\{9dea862c-5cdd-4e70-acc1-f32b344d4795}\Elements\11000001 |
| Operation: | delete key | Name: | (default) |
Value: | |||
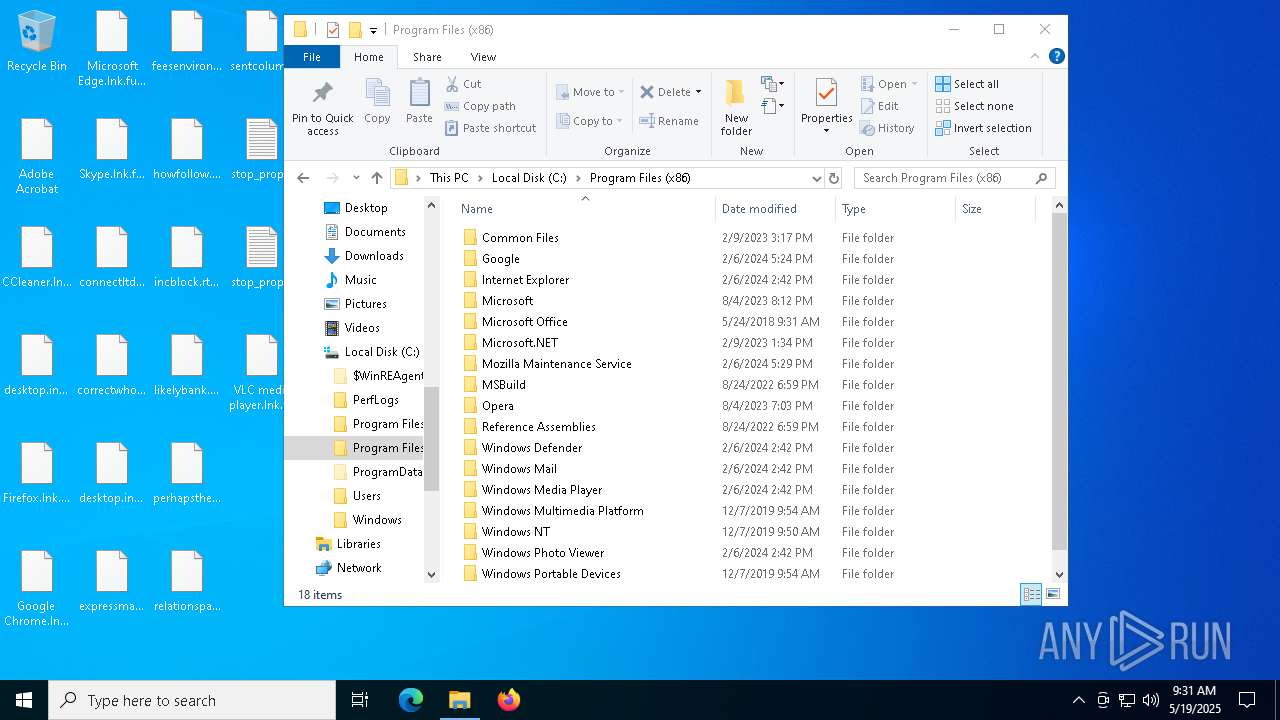
Executable files
2
Suspicious files
92
Text files
630
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6480 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXb6480.9921\954d8fcd6b74d76999f9ec033ca855ffdab6595be23039f03bc4c6017fa3932c.exe | executable | |
MD5:A4AC3F1674F24C6E596BF71FC47BD275 | SHA256:954D8FCD6B74D76999F9EC033CA855FFDAB6595BE23039F03BC4C6017FA3932C | |||
| 5380 | svchost.exe | C:\Users\admin\Desktop\expressmax.rtf | text | |
MD5:9E876FE9380C1ED55EFC7FA05EB8808B | SHA256:28B95C20D8CC738738CF5A85DA3F9CC4AD6C939CD00CA7EE5FC770E9C55C6BF0 | |||
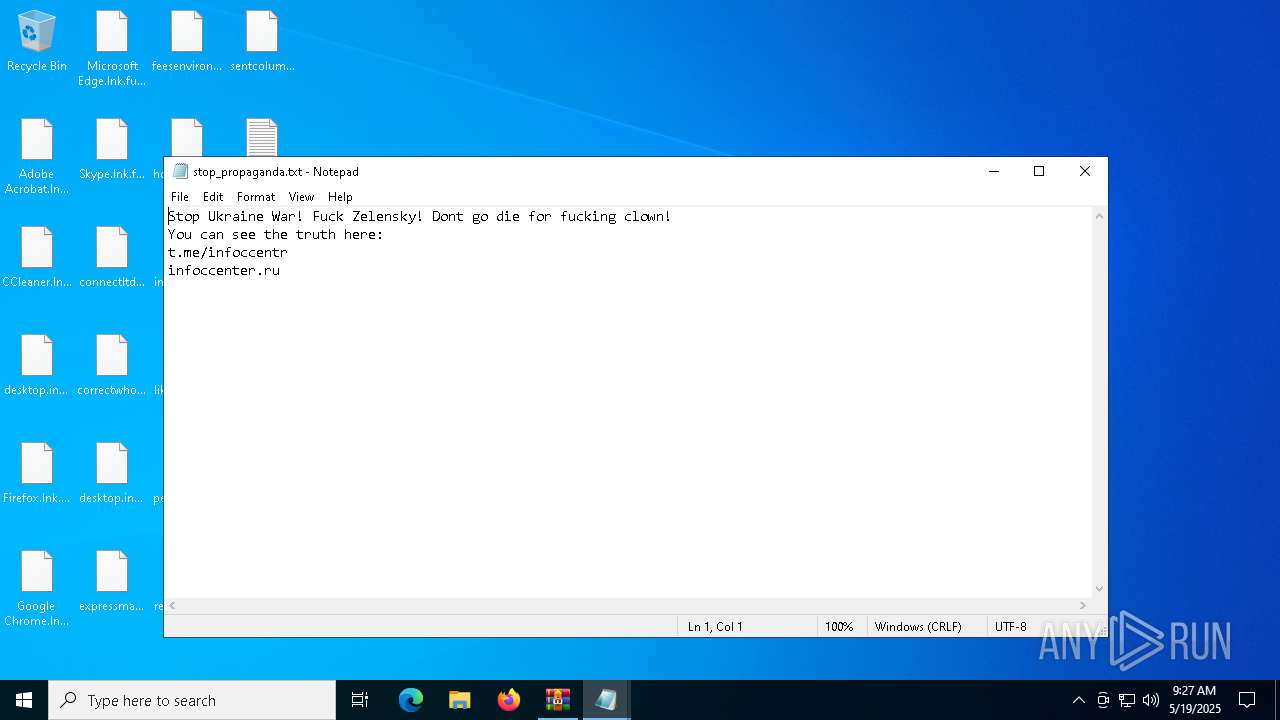
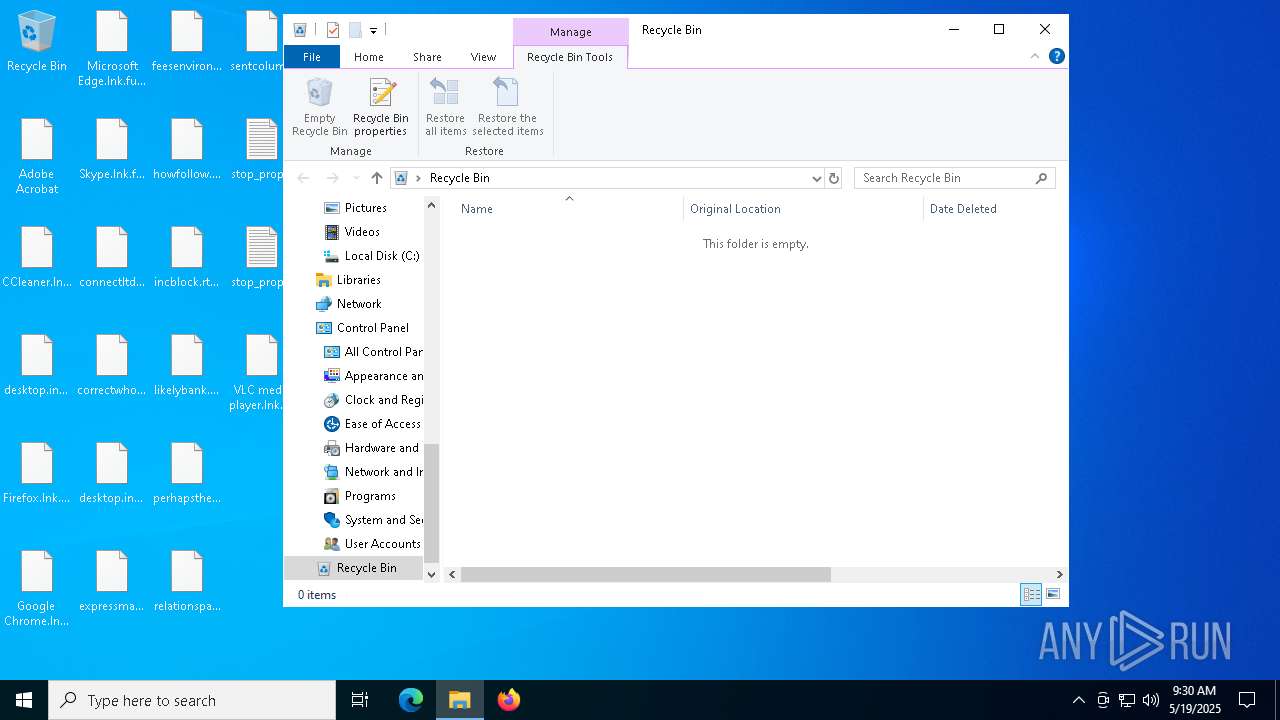
| 5380 | svchost.exe | C:\Users\admin\Desktop\stop_propaganda.txt | text | |
MD5:4E70E7628592C28E0A1B796E5FF7CBB6 | SHA256:49CCDD40EBFE0B3DA0CA1D2C034B7E2EECAAFFE273F0FB14CF4AF50AF09170F7 | |||
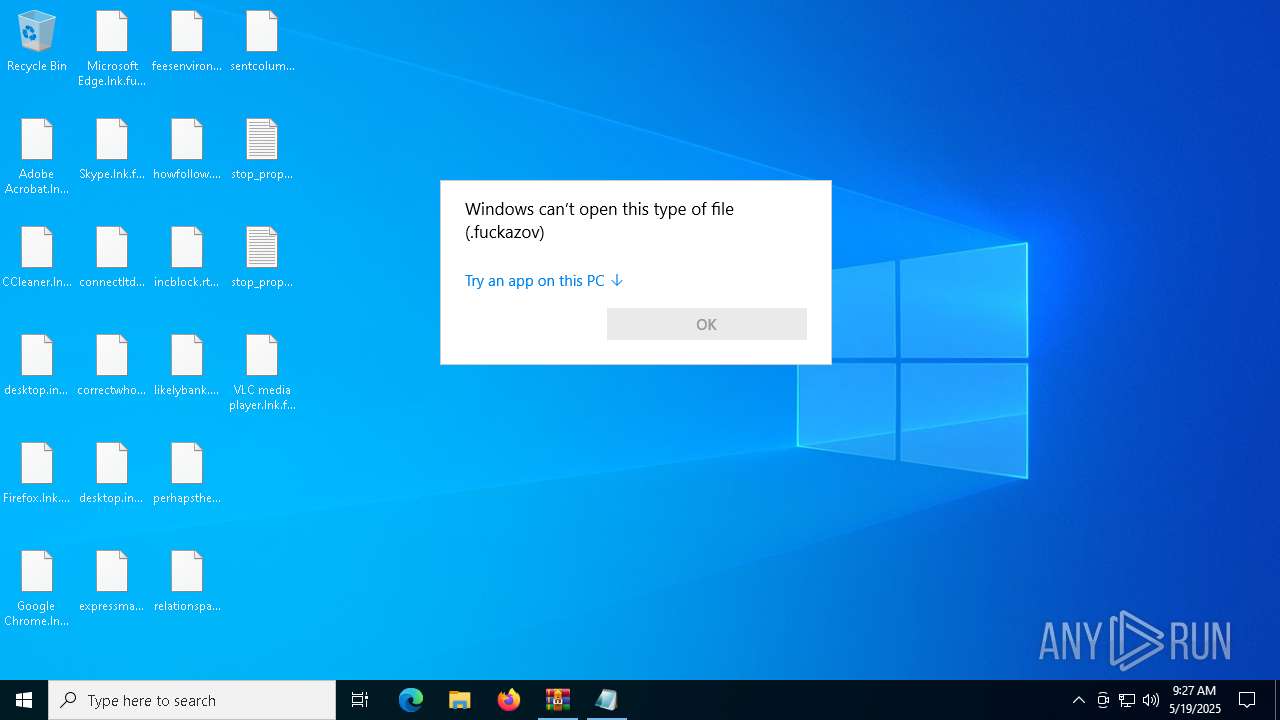
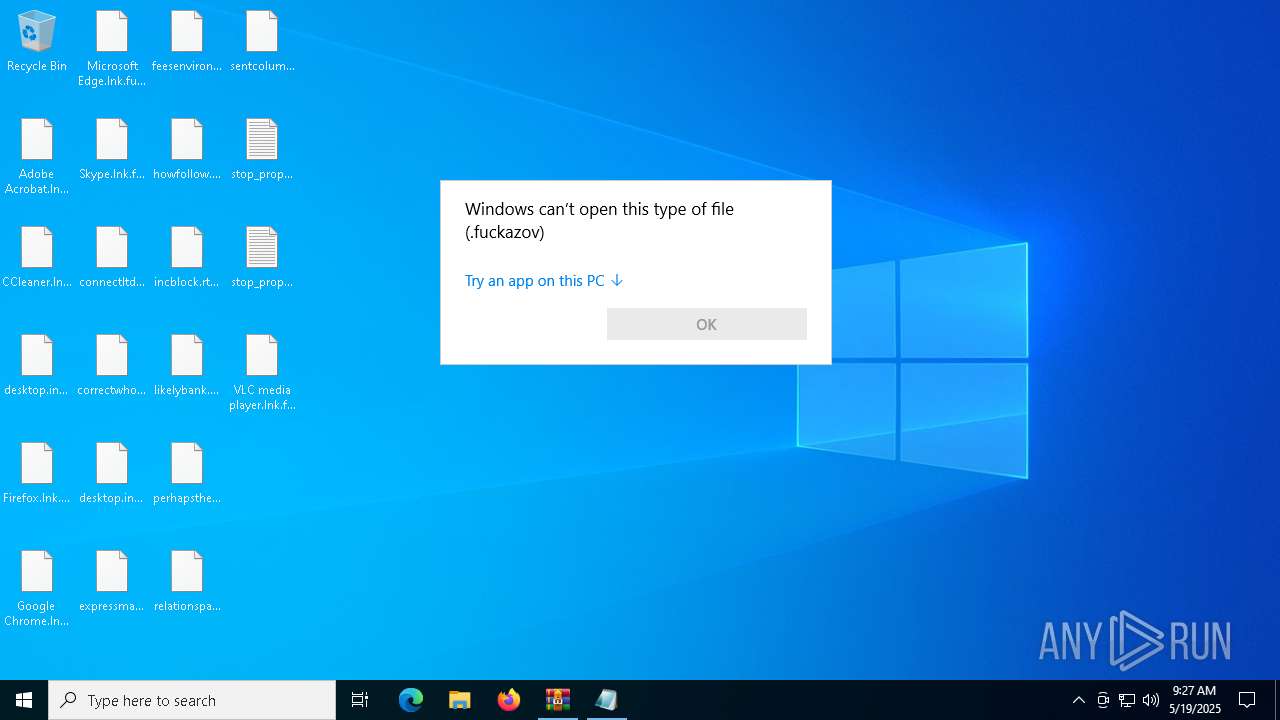
| 5380 | svchost.exe | C:\Users\admin\Desktop\correctwhole.png.fuckazov | text | |
MD5:91BEBC9FAA03001FC4FC68726F219FFB | SHA256:96AB727B62559ED6C37CF347B0A608568B0B631DBEE803638CC87591ED94CD52 | |||
| 5380 | svchost.exe | C:\Users\admin\Desktop\expressmax.rtf.fuckazov | text | |
MD5:9E876FE9380C1ED55EFC7FA05EB8808B | SHA256:28B95C20D8CC738738CF5A85DA3F9CC4AD6C939CD00CA7EE5FC770E9C55C6BF0 | |||
| 5380 | svchost.exe | C:\Users\admin\Desktop\desktop.ini | text | |
MD5:FE9814ADDFA07D7AF4E4CD4073472402 | SHA256:FE1572D92B36070524B5A4C0D089864D3DD51AE7BD3E52015A3BBEE312846AAB | |||
| 5380 | svchost.exe | C:\Users\admin\Desktop\correctwhole.png | text | |
MD5:91BEBC9FAA03001FC4FC68726F219FFB | SHA256:96AB727B62559ED6C37CF347B0A608568B0B631DBEE803638CC87591ED94CD52 | |||
| 5380 | svchost.exe | C:\Users\admin\Desktop\desktop.ini.fuckazov | text | |
MD5:FE9814ADDFA07D7AF4E4CD4073472402 | SHA256:FE1572D92B36070524B5A4C0D089864D3DD51AE7BD3E52015A3BBEE312846AAB | |||
| 5380 | svchost.exe | C:\Users\admin\Desktop\connectltd.rtf | text | |
MD5:EA26DAD9839A7FFEEE9DABCCD38ECC00 | SHA256:C6A72783F9F8913398BE862A66C478C0F006440BE0C7AF05A8B9921F42DD453D | |||
| 5380 | svchost.exe | C:\Users\admin\Desktop\connectltd.rtf.fuckazov | text | |
MD5:EA26DAD9839A7FFEEE9DABCCD38ECC00 | SHA256:C6A72783F9F8913398BE862A66C478C0F006440BE0C7AF05A8B9921F42DD453D | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
51
DNS requests
18
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 20.73.194.208:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
2104 | svchost.exe | 20.73.194.208:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | 20.73.194.208:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
2112 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
3216 | svchost.exe | 172.211.123.249:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
6544 | svchost.exe | 20.190.160.131:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
2104 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1228 | SIHClient.exe | 20.109.210.53:443 | slscr.update.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
206.23.85.13.in-addr.arpa |
| unknown |
4.8.2.0.0.0.0.0.0.0.0.0.0.0.0.0.2.0.0.0.2.0.c.0.0.3.0.1.3.0.6.2.ip6.arpa |
| unknown |
activation-v2.sls.microsoft.com |
| whitelisted |
nexusrules.officeapps.live.com |
| whitelisted |