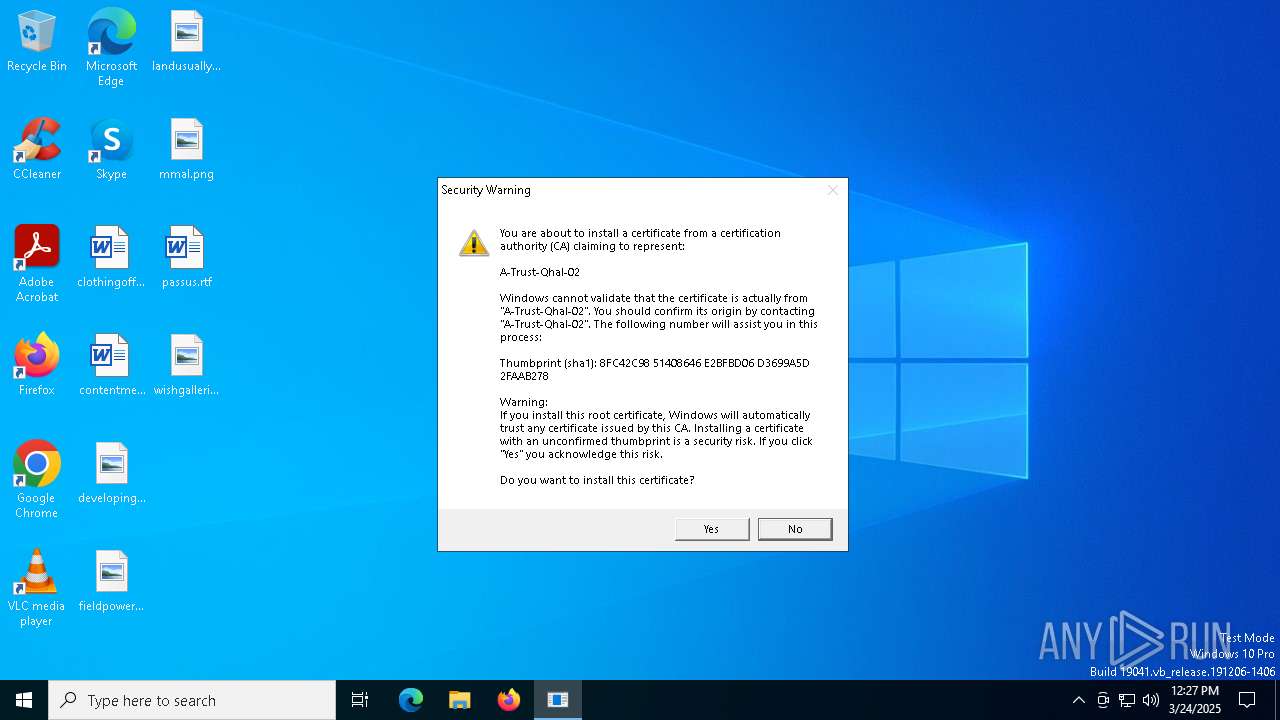
| File name: | as00r1vaa1.exe |
| Full analysis: | https://app.any.run/tasks/6e958185-f1bc-42a6-8f0f-8e2864f80762 |
| Verdict: | Malicious activity |
| Threats: | Danabot is an advanced banking Trojan malware that was designed to steal financial information from victims. Out of the Trojans in the wild, this is one of the most advanced thanks to the modular design and a complex delivery method. |
| Analysis date: | March 24, 2025, 12:27:05 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32+ executable (GUI) x86-64, for MS Windows, 11 sections |
| MD5: | B2CF02902E8F85BCCB58E927B720B140 |
| SHA1: | 6F118B3AA839D9CE86F102C087CFA8D8E84B2A8C |
| SHA256: | A090257138F134A407EE62702FBE237AB14379F119C9C21686863C940F507BEE |
| SSDEEP: | 98304:SZQ4Q2yBGymRTsgSiXitD9XCsNhUdX+SRrXJsKu2cxEu088j1tfHQ10TSBVKa5Yj:1ImKvV |
MALICIOUS
DANABOT has been detected (SURICATA)
- as00r1vaa1.exe (PID: 7148)
DANABOT has been detected (YARA)
- as00r1vaa1.exe (PID: 7148)
Actions looks like stealing of personal data
- as00r1vaa1.exe (PID: 7148)
- msedge.exe (PID: 2236)
Suspicious browser debugging (Possible cookie theft)
- as00r1vaa1.exe (PID: 7148)
Steals credentials from Web Browsers
- as00r1vaa1.exe (PID: 7148)
SUSPICIOUS
Starts CMD.EXE for commands execution
- as00r1vaa1.exe (PID: 7148)
Uses WMIC.EXE to obtain physical disk drive information
- cmd.exe (PID: 3884)
Reads the date of Windows installation
- as00r1vaa1.exe (PID: 7148)
There is functionality for taking screenshot (YARA)
- as00r1vaa1.exe (PID: 7148)
There is functionality for communication over UDP network (YARA)
- as00r1vaa1.exe (PID: 7148)
Contacting a server suspected of hosting an CnC
- as00r1vaa1.exe (PID: 7148)
Searches for installed software
- as00r1vaa1.exe (PID: 7148)
Loads DLL from Mozilla Firefox
- as00r1vaa1.exe (PID: 7148)
The process verifies whether the antivirus software is installed
- as00r1vaa1.exe (PID: 7148)
Application launched itself
- msedge.exe (PID: 2236)
- chrome.exe (PID: 7152)
Reads Mozilla Firefox installation path
- as00r1vaa1.exe (PID: 7148)
INFO
Checks supported languages
- as00r1vaa1.exe (PID: 7148)
Reads the computer name
- as00r1vaa1.exe (PID: 7148)
Reads Windows Product ID
- as00r1vaa1.exe (PID: 7148)
Reads Environment values
- as00r1vaa1.exe (PID: 7148)
Reads security settings of Internet Explorer
- WMIC.exe (PID: 2908)
Reads CPU info
- as00r1vaa1.exe (PID: 7148)
Reads product name
- as00r1vaa1.exe (PID: 7148)
Reads the machine GUID from the registry
- as00r1vaa1.exe (PID: 7148)
Create files in a temporary directory
- as00r1vaa1.exe (PID: 7148)
Creates files or folders in the user directory
- msedge.exe (PID: 2236)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Generic Win/DOS Executable (49.6) |
|---|---|---|
| .exe | | | DOS Executable Generic (49.5) |
| .vxd | | | VXD Driver (0.7) |
EXIF
EXE
| MachineType: | AMD AMD64 |
|---|---|
| TimeStamp: | 2025:01:18 08:32:05+00:00 |
| ImageFileCharacteristics: | Executable, Large address aware |
| PEType: | PE32+ |
| LinkerVersion: | 8 |
| CodeSize: | 5310976 |
| InitializedDataSize: | 401920 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x50aa50 |
| OSVersion: | 5.2 |
| ImageVersion: | 5.2 |
| SubsystemVersion: | 5.2 |
| Subsystem: | Windows GUI |
Total processes
145
Monitored processes
13
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1912 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=network.mojom.NetworkService --lang=en-US --service-sandbox-type=none --use-angle=swiftshader-webgl --use-gl=angle --headless --mojo-platform-channel-handle=1768 --field-trial-handle=1420,i,4852063130272787469,16479028162429935851,262144 --disable-features=PaintHolding --variations-seed-version /prefetch:3 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 2236 | --restore-last-session --remote-debugging-port=9225 --remote-allow-origins=* --headless "--user-data-dir=C:\Users\admin\AppData\Local\Microsoft\Edge\User Data" --profile-directory="Default" | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | as00r1vaa1.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 2908 | wmic diskdrive where "DeviceID=\'c:\'" get SerialNumber /value | C:\Windows\System32\wbem\WMIC.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: WMI Commandline Utility Exit code: 2147749911 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3332 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3884 | cmd.exe /C wmic diskdrive where "DeviceID=\'c:\'" get SerialNumber /value | C:\Windows\System32\cmd.exe | — | as00r1vaa1.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 2147749911 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4220 | "C:\WINDOWS\System32\SLUI.exe" RuleId=3482d82e-ca2c-4e1f-8864-da0267b484b2;Action=AutoActivate;AppId=55c92734-d682-4d71-983e-d6ec3f16059f;SkuId=4de7cb65-cdf1-4de9-8ae8-e3cce27b9f2c;NotificationInterval=1440;Trigger=TimerEvent | C:\Windows\System32\slui.exe | — | SppExtComObj.Exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Activation Client Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4756 | C:\WINDOWS\system32\SppExtComObj.exe -Embedding | C:\Windows\System32\SppExtComObj.Exe | — | svchost.exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: KMS Connection Broker Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6148 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=gpu-process --headless --use-angle=swiftshader-webgl --headless --gpu-preferences=WAAAAAAAAADgAAAMAAAAAAAAAAAAAAAAAABgAAAAAAA4AAAAAAAAAAAAAAAEAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAGAAAAAAAAAAYAAAAAAAAAAgAAAAAAAAACAAAAAAAAAAIAAAAAAAAAA== --use-gl=angle --mojo-platform-channel-handle=1440 --field-trial-handle=1420,i,4852063130272787469,16479028162429935851,262144 --disable-features=PaintHolding --variations-seed-version /prefetch:2 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 6264 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=network.mojom.NetworkService --lang=en-US --service-sandbox-type=none --use-angle=swiftshader-webgl --use-gl=angle --headless --mojo-platform-channel-handle=1704 --field-trial-handle=1440,i,6963347080060861717,6235995699746134409,262144 --disable-features=PaintHolding --variations-seed-version /prefetch:3 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 122.0.6261.70 Modules
| |||||||||||||||
| 6456 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=crashpad-handler "--user-data-dir=C:\Users\admin\AppData\Local\Google\Chrome\User Data" /prefetch:4 --monitor-self-annotation=ptype=crashpad-handler "--database=C:\Users\admin\AppData\Local\Google\Chrome\User Data\Crashpad" --url=https://clients2.google.com/cr/report --annotation=channel= --annotation=plat=Win64 --annotation=prod=Chrome --annotation=ver=122.0.6261.70 --initial-client-data=0x224,0x228,0x22c,0x200,0x230,0x7ffc88ccdc40,0x7ffc88ccdc4c,0x7ffc88ccdc58 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 122.0.6261.70 Modules
| |||||||||||||||
Total events
29 007
Read events
28 991
Write events
16
Delete events
0
Modification events
| (PID) Process: | (7148) as00r1vaa1.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\as00r1vaa1_RASAPI32 |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (7148) as00r1vaa1.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\as00r1vaa1_RASAPI32 |
| Operation: | write | Name: | EnableAutoFileTracing |
Value: 0 | |||
| (PID) Process: | (7148) as00r1vaa1.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\as00r1vaa1_RASAPI32 |
| Operation: | write | Name: | EnableConsoleTracing |
Value: 0 | |||
| (PID) Process: | (7148) as00r1vaa1.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\as00r1vaa1_RASAPI32 |
| Operation: | write | Name: | FileTracingMask |
Value: | |||
| (PID) Process: | (7148) as00r1vaa1.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\as00r1vaa1_RASAPI32 |
| Operation: | write | Name: | ConsoleTracingMask |
Value: | |||
| (PID) Process: | (7148) as00r1vaa1.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\as00r1vaa1_RASAPI32 |
| Operation: | write | Name: | MaxFileSize |
Value: 1048576 | |||
| (PID) Process: | (7148) as00r1vaa1.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\as00r1vaa1_RASAPI32 |
| Operation: | write | Name: | FileDirectory |
Value: %windir%\tracing | |||
| (PID) Process: | (7148) as00r1vaa1.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (7148) as00r1vaa1.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (7148) as00r1vaa1.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
Executable files
0
Suspicious files
22
Text files
31
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2236 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\PersistentOriginTrials\LOG.old~RF112373.TMP | — | |
MD5:— | SHA256:— | |||
| 2236 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\PersistentOriginTrials\LOG.old | — | |
MD5:— | SHA256:— | |||
| 7148 | as00r1vaa1.exe | C:\Users\admin\AppData\Local\Temp\Iduhtauhueu | binary | |
MD5:1E1F96F03DCB32CBEDE6A33AF67A44A7 | SHA256:B6DCEC10039FBA99019A6DE818D433847EFAD62FAE59851E328EC42396DFD9CB | |||
| 7148 | as00r1vaa1.exe | C:\Users\admin\AppData\Local\Temp\Fpsruh | binary | |
MD5:1E1F96F03DCB32CBEDE6A33AF67A44A7 | SHA256:B6DCEC10039FBA99019A6DE818D433847EFAD62FAE59851E328EC42396DFD9CB | |||
| 7148 | as00r1vaa1.exe | C:\Users\admin\AppData\Local\Temp\Uthwetdwiu | binary | |
MD5:29A644B1F0D96166A05602FE27B3F4AD | SHA256:BF96902FEB97E990A471492F78EE8386BCF430D66BDAEFDEAFBF912C8CF7CE46 | |||
| 7148 | as00r1vaa1.exe | C:\Users\admin\AppData\Local\Temp\Ieedyhwrtdt | sqlite | |
MD5:F6C33AC5E1032A0873BE7BFC65169287 | SHA256:D97895CEDED32E33D57BDCACCDBE144E58AA87AF4D2F8855D630286CE30A8D83 | |||
| 7148 | as00r1vaa1.exe | C:\Users\admin\AppData\Local\Temp\Eypaeqpfsheuyrp | binary | |
MD5:1E1F96F03DCB32CBEDE6A33AF67A44A7 | SHA256:B6DCEC10039FBA99019A6DE818D433847EFAD62FAE59851E328EC42396DFD9CB | |||
| 7148 | as00r1vaa1.exe | C:\Users\admin\AppData\Local\Temp\Eaiiuuyi | binary | |
MD5:1E1F96F03DCB32CBEDE6A33AF67A44A7 | SHA256:B6DCEC10039FBA99019A6DE818D433847EFAD62FAE59851E328EC42396DFD9CB | |||
| 7148 | as00r1vaa1.exe | C:\Users\admin\AppData\Local\Temp\Upesqharfh | binary | |
MD5:F6C33AC5E1032A0873BE7BFC65169287 | SHA256:D97895CEDED32E33D57BDCACCDBE144E58AA87AF4D2F8855D630286CE30A8D83 | |||
| 7148 | as00r1vaa1.exe | C:\Users\admin\AppData\Local\Temp\Efposeyt | binary | |
MD5:95FFD778940E6DF4846B0B12C8DD5821 | SHA256:21A2DEBD389DB456465DFEFFDB15F0AF3FBC46F007CBA67513A13EB10D14E94F | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
5
TCP/UDP connections
24
DNS requests
13
Threats
2
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 23.48.23.162:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
668 | backgroundTaskHost.exe | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
6640 | SIHClient.exe | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
6640 | SIHClient.exe | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 51.104.136.2:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 23.48.23.162:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
2104 | svchost.exe | 51.104.136.2:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
7148 | as00r1vaa1.exe | 194.32.76.77:443 | — | MVPS LTD | FR | malicious |
3216 | svchost.exe | 40.113.103.199:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6544 | svchost.exe | 20.190.160.128:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6544 | svchost.exe | 184.30.131.245:80 | ocsp.digicert.com | AKAMAI-AS | US | whitelisted |
2112 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
668 | backgroundTaskHost.exe | 20.74.47.205:443 | arc.msn.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
arc.msn.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
7148 | as00r1vaa1.exe | Malware Command and Control Activity Detected | STEALER [ANY.RUN] Danabot TCP Packet |
7148 | as00r1vaa1.exe | Malware Command and Control Activity Detected | STEALER [ANY.RUN] Danabot TCP Packet |