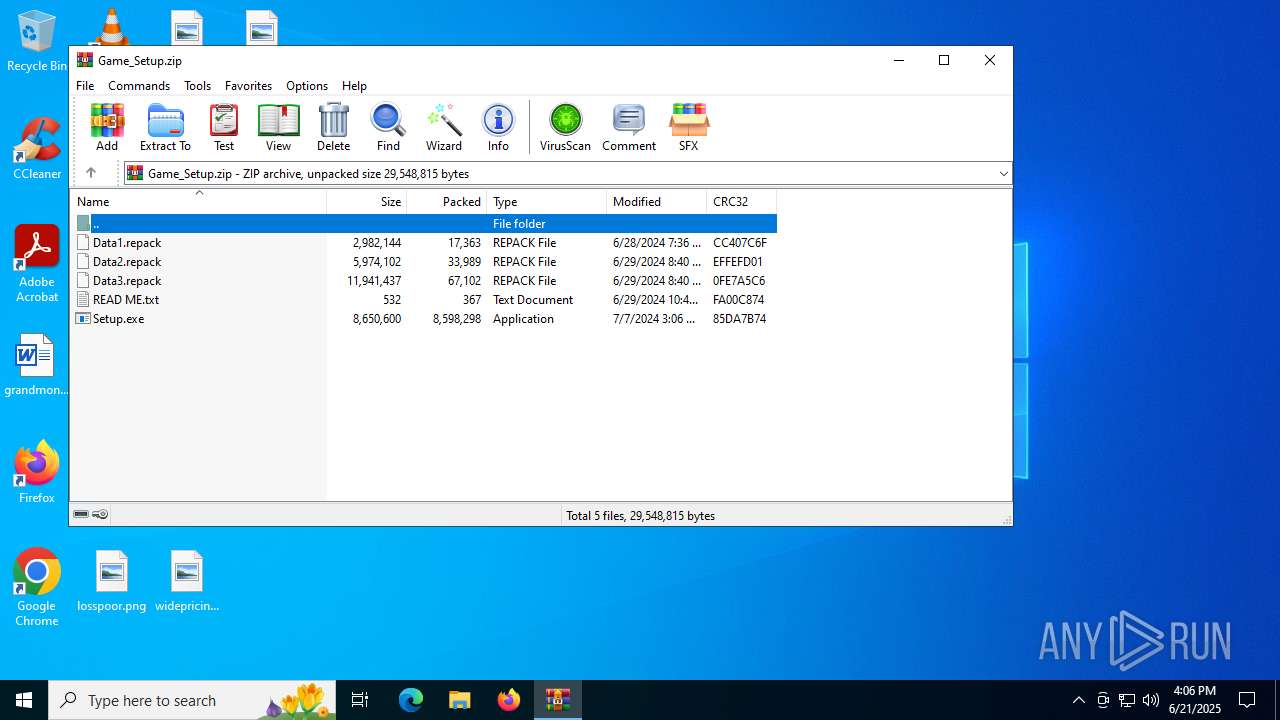
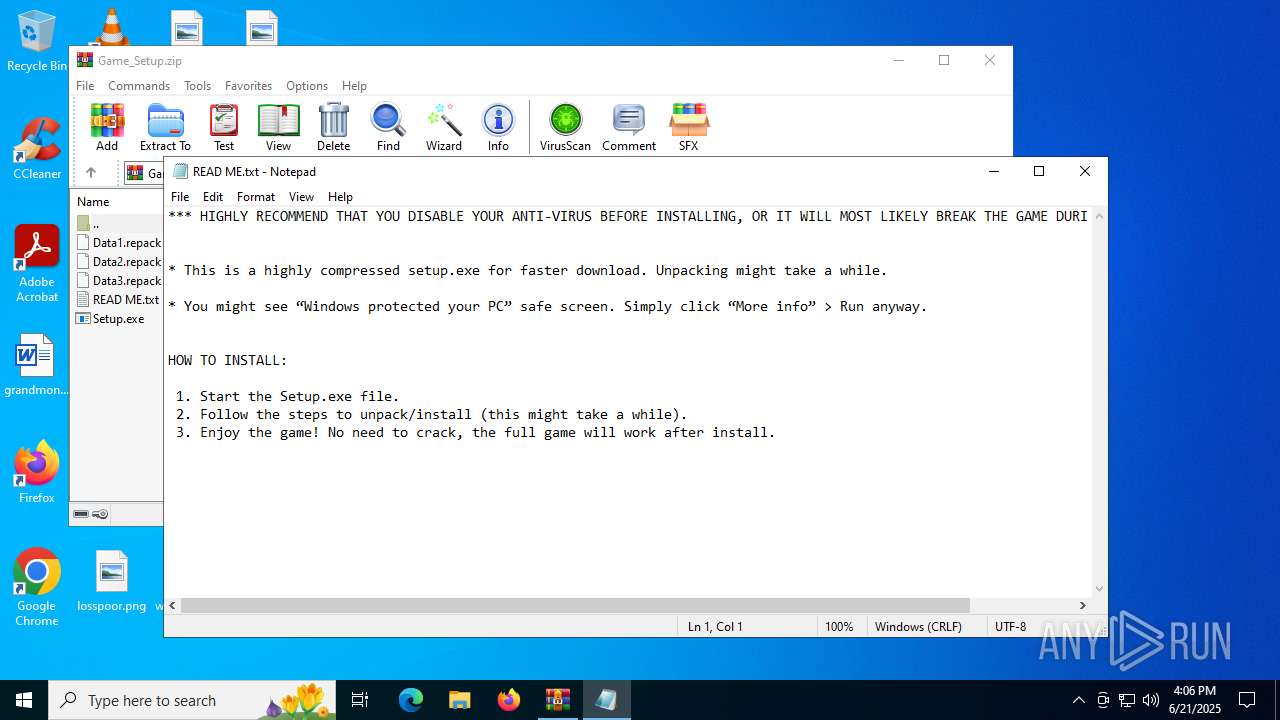
| File name: | Game_Setup.zip |
| Full analysis: | https://app.any.run/tasks/7c2b42a3-885d-467b-80d6-919a1fd919cf |
| Verdict: | Malicious activity |
| Threats: | Amadey is a formidable Windows infostealer threat, characterized by its persistence mechanisms, modular design, and ability to execute various malicious tasks. |
| Analysis date: | June 21, 2025, 16:05:50 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=deflate |
| MD5: | 95A6838ADE68096DDC7969F54F4FDDC7 |
| SHA1: | 3A3D8B521224595D5AB60307263393C80ABAEBFB |
| SHA256: | A03B1F38FD828330FFA3FDD97E54F063F6E735A6C15A4B906B09FB1B1AF707F2 |
| SSDEEP: | 98304:Jx7JVqdi6TmmHD3xNyX6duuadHEfFA0mdVlqDkywx2ESaptrYgHh9lc0shKVgGtm:szXuYZPRGjJERl |
MALICIOUS
Generic archive extractor
- WinRAR.exe (PID: 5644)
Changes Windows Defender settings
- Setup.exe (PID: 6384)
- install.exe (PID: 3852)
Adds extension to the Windows Defender exclusion list
- Setup.exe (PID: 6384)
- install.exe (PID: 3852)
Uninstalls Malicious Software Removal Tool (MRT)
- cmd.exe (PID: 4960)
- cmd.exe (PID: 4664)
Vulnerable driver has been detected
- install.exe (PID: 3852)
XORed URL has been found (YARA)
- explorer.exe (PID: 7124)
MINER has been detected (SURICATA)
- svchost.exe (PID: 2200)
XMRIG has been detected (YARA)
- explorer.exe (PID: 7124)
SUSPICIOUS
Starts POWERSHELL.EXE for commands execution
- Setup.exe (PID: 4648)
- Setup.exe (PID: 6384)
- install.exe (PID: 3852)
Starts process via Powershell
- powershell.exe (PID: 4552)
Reads the BIOS version
- Setup.exe (PID: 4648)
- Setup.exe (PID: 6384)
- install.exe (PID: 3852)
Script adds exclusion path to Windows Defender
- Setup.exe (PID: 6384)
- install.exe (PID: 3852)
Script adds exclusion extension to Windows Defender
- Setup.exe (PID: 6384)
- install.exe (PID: 3852)
Manipulates environment variables
- powershell.exe (PID: 5008)
- powershell.exe (PID: 3504)
Stops a currently running service
- sc.exe (PID: 6004)
- sc.exe (PID: 1488)
- sc.exe (PID: 6404)
- sc.exe (PID: 4764)
- sc.exe (PID: 3876)
- sc.exe (PID: 6512)
- sc.exe (PID: 416)
- sc.exe (PID: 2356)
- sc.exe (PID: 1336)
- sc.exe (PID: 6368)
- sc.exe (PID: 856)
Process uninstalls Windows update
- wusa.exe (PID: 5348)
- wusa.exe (PID: 5896)
Creates a new Windows service
- sc.exe (PID: 6836)
Starts SC.EXE for service management
- Setup.exe (PID: 6384)
- install.exe (PID: 3852)
Modifies hosts file to alter network resolution
- Setup.exe (PID: 6384)
- install.exe (PID: 3852)
Executable content was dropped or overwritten
- Setup.exe (PID: 6384)
- install.exe (PID: 3852)
Uses powercfg.exe to modify the power settings
- Setup.exe (PID: 6384)
- install.exe (PID: 3852)
Windows service management via SC.EXE
- sc.exe (PID: 5708)
- sc.exe (PID: 3948)
Executes as Windows Service
- install.exe (PID: 3852)
Starts CMD.EXE for commands execution
- Setup.exe (PID: 6384)
- install.exe (PID: 3852)
Potential Corporate Privacy Violation
- svchost.exe (PID: 2200)
Connects to unusual port
- explorer.exe (PID: 7124)
Drops a system driver (possible attempt to evade defenses)
- install.exe (PID: 3852)
INFO
Checks supported languages
- Setup.exe (PID: 4648)
- Setup.exe (PID: 6384)
- install.exe (PID: 3852)
Manual execution by a user
- Setup.exe (PID: 4648)
- notepad.exe (PID: 4824)
Reads security settings of Internet Explorer
- notepad.exe (PID: 4824)
Process checks whether UAC notifications are on
- Setup.exe (PID: 6384)
- install.exe (PID: 3852)
Themida protector has been detected
- Setup.exe (PID: 6384)
Checks if a key exists in the options dictionary (POWERSHELL)
- powershell.exe (PID: 5008)
- powershell.exe (PID: 3504)
Script raised an exception (POWERSHELL)
- powershell.exe (PID: 5008)
- powershell.exe (PID: 3504)
Creates files in the program directory
- Setup.exe (PID: 6384)
The sample compiled with english language support
- Setup.exe (PID: 6384)
Reads the software policy settings
- slui.exe (PID: 7100)
UPX packer has been detected
- explorer.exe (PID: 7124)
Checks proxy server information
- slui.exe (PID: 7100)
The sample compiled with japanese language support
- install.exe (PID: 3852)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2024:06:28 14:36:30 |
| ZipCRC: | 0xcc407c6f |
| ZipCompressedSize: | 17363 |
| ZipUncompressedSize: | 2982144 |
| ZipFileName: | Data1.repack |
Total processes
197
Monitored processes
66
Malicious processes
6
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 416 | C:\WINDOWS\system32\sc.exe stop dosvc | C:\Windows\System32\sc.exe | — | install.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Service Control Manager Configuration Tool Exit code: 1062 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 684 | C:\WINDOWS\system32\powercfg.exe /x -standby-timeout-dc 0 | C:\Windows\System32\powercfg.exe | — | Setup.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Power Settings Command-Line Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 856 | C:\WINDOWS\system32\sc.exe stop bits | C:\Windows\System32\sc.exe | — | install.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Service Control Manager Configuration Tool Exit code: 1062 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 984 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | sc.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1336 | C:\WINDOWS\system32\sc.exe stop WaaSMedicSvc | C:\Windows\System32\sc.exe | — | install.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Service Control Manager Configuration Tool Exit code: 1062 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1488 | C:\WINDOWS\system32\sc.exe stop dosvc | C:\Windows\System32\sc.exe | — | Setup.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Service Control Manager Configuration Tool Exit code: 1062 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2120 | C:\WINDOWS\system32\powercfg.exe /x -hibernate-timeout-ac 0 | C:\Windows\System32\powercfg.exe | — | install.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Power Settings Command-Line Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2200 | C:\WINDOWS\system32\svchost.exe -k NetworkService -p -s Dnscache | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2320 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powercfg.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2356 | C:\WINDOWS\system32\sc.exe stop UsoSvc | C:\Windows\System32\sc.exe | — | install.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Service Control Manager Configuration Tool Exit code: 1061 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
24 771
Read events
24 759
Write events
12
Delete events
0
Modification events
| (PID) Process: | (5644) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (5644) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (5644) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (5644) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\Game_Setup.zip | |||
| (PID) Process: | (5644) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (5644) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (5644) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (5644) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (5644) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList |
| Operation: | write | Name: | ArcSort |
Value: 32 | |||
| (PID) Process: | (5644) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList |
| Operation: | write | Name: | ArcSort |
Value: 0 | |||
Executable files
2
Suspicious files
2
Text files
9
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4552 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_ynlvpubr.lns.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 5008 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_4fqfsvqj.cup.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 5008 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_cbqmmejn.kih.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 6384 | Setup.exe | C:\ProgramData\LocalUpdateUpdate\install.exe | executable | |
MD5:42DF176B4530E5B5434D66AE95B992A9 | SHA256:94CAFF833F3196A7ADB6C25D96442F9316BF3B4044B8B1F95EE50C5CABC67EF3 | |||
| 4552 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_wwrahxsq.h20.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 3504 | powershell.exe | C:\Windows\Temp\__PSScriptPolicyTest_ddvepqeo.3qx.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 3504 | powershell.exe | C:\Windows\System32\config\systemprofile\AppData\Local\Microsoft\Windows\PowerShell\StartupProfileData-NonInteractive | binary | |
MD5:51D9D9E1E51140C5232D79510394A3A0 | SHA256:7DA347A38A26BA84A5882C86B971B6F5E8D74D395566489C0B98BB1500166313 | |||
| 3504 | powershell.exe | C:\Windows\Temp\__PSScriptPolicyTest_btajwxms.ndp.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 3504 | powershell.exe | C:\Windows\Temp\__PSScriptPolicyTest_om2ix3vs.4th.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 3852 | install.exe | C:\Windows\Temp\vozzhmumpjds.sys | executable | |
MD5:0C0195C48B6B8582FA6F6373032118DA | SHA256:11BD2C9F9E2397C9A16E0990E4ED2CF0679498FE0FD418A3DFDAC60B5C160EE5 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
9
TCP/UDP connections
27
DNS requests
9
Threats
4
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1268 | svchost.exe | GET | 200 | 23.55.104.172:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5944 | MoUsoCoreWorker.exe | GET | 200 | 23.55.104.172:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
3572 | RUXIMICS.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
5944 | MoUsoCoreWorker.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | POST | 200 | 172.67.157.64:443 | https://23865.fr/api/endpoint.php | unknown | binary | 17 b | malicious |
— | — | POST | 500 | 20.83.72.98:443 | https://activation-v2.sls.microsoft.com/SLActivateProduct/SLActivateProduct.asmx?configextension=Retail | unknown | xml | 512 b | whitelisted |
— | — | POST | 500 | 20.83.72.98:443 | https://activation-v2.sls.microsoft.com/SLActivateProduct/SLActivateProduct.asmx?configextension=Retail | unknown | xml | 512 b | whitelisted |
— | — | POST | 200 | 172.67.157.64:443 | https://23865.fr/api/endpoint.php | unknown | binary | 2 b | malicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
5944 | MoUsoCoreWorker.exe | 40.127.240.158:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
3572 | RUXIMICS.exe | 40.127.240.158:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
1268 | svchost.exe | 40.127.240.158:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1268 | svchost.exe | 23.55.104.172:80 | crl.microsoft.com | Akamai International B.V. | US | whitelisted |
5944 | MoUsoCoreWorker.exe | 23.55.104.172:80 | crl.microsoft.com | Akamai International B.V. | US | whitelisted |
1268 | svchost.exe | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
3572 | RUXIMICS.exe | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
5944 | MoUsoCoreWorker.exe | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
activation-v2.sls.microsoft.com |
| whitelisted |
xmr-eu1.nanopool.org |
| whitelisted |
23865.fr |
| malicious |
self.events.data.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2200 | svchost.exe | Potential Corporate Privacy Violation | ET INFO Observed DNS Query to Coin Mining Domain (nanopool .org) |
— | — | Misc activity | SUSPICIOUS [ANY.RUN] Sent Host Name in HTTP POST Body |
— | — | A Network Trojan was detected | ET MALWARE Win32/Amadey Host Fingerprint Exfil (POST) M3 |
— | — | A Network Trojan was detected | ET MALWARE Win32/Amadey Host Fingerprint Exfil (POST) M3 |