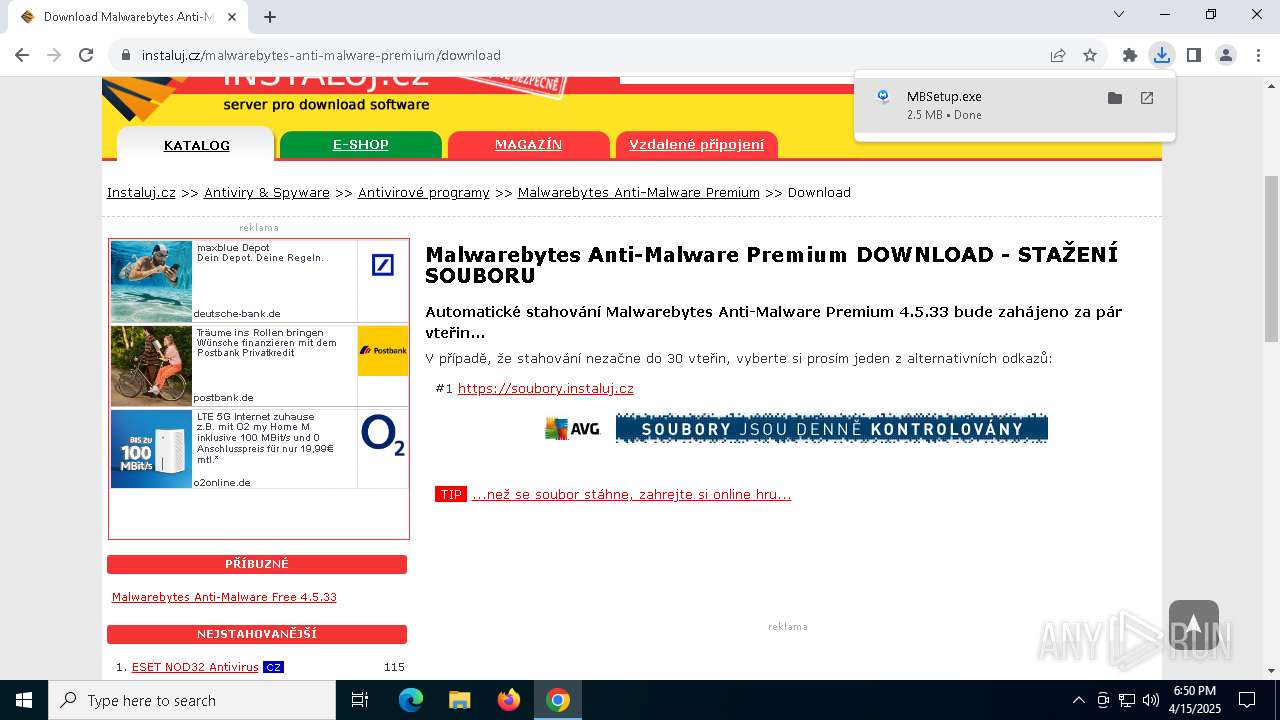
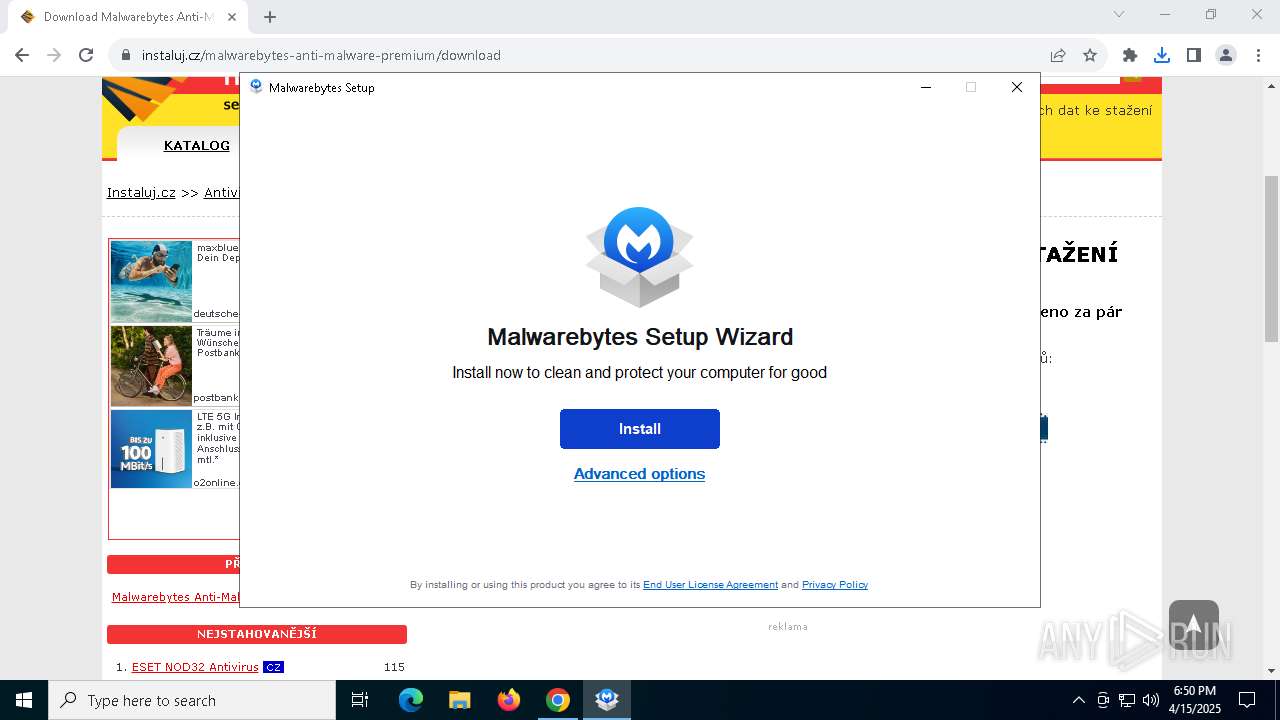
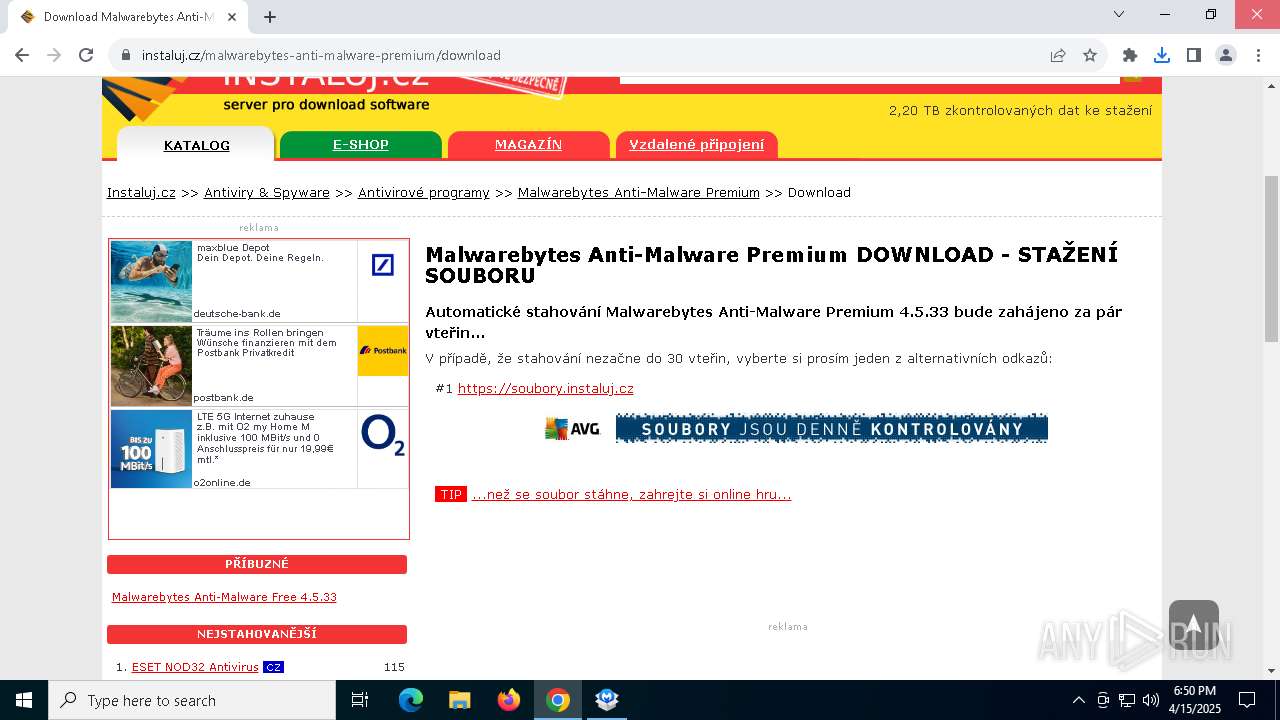
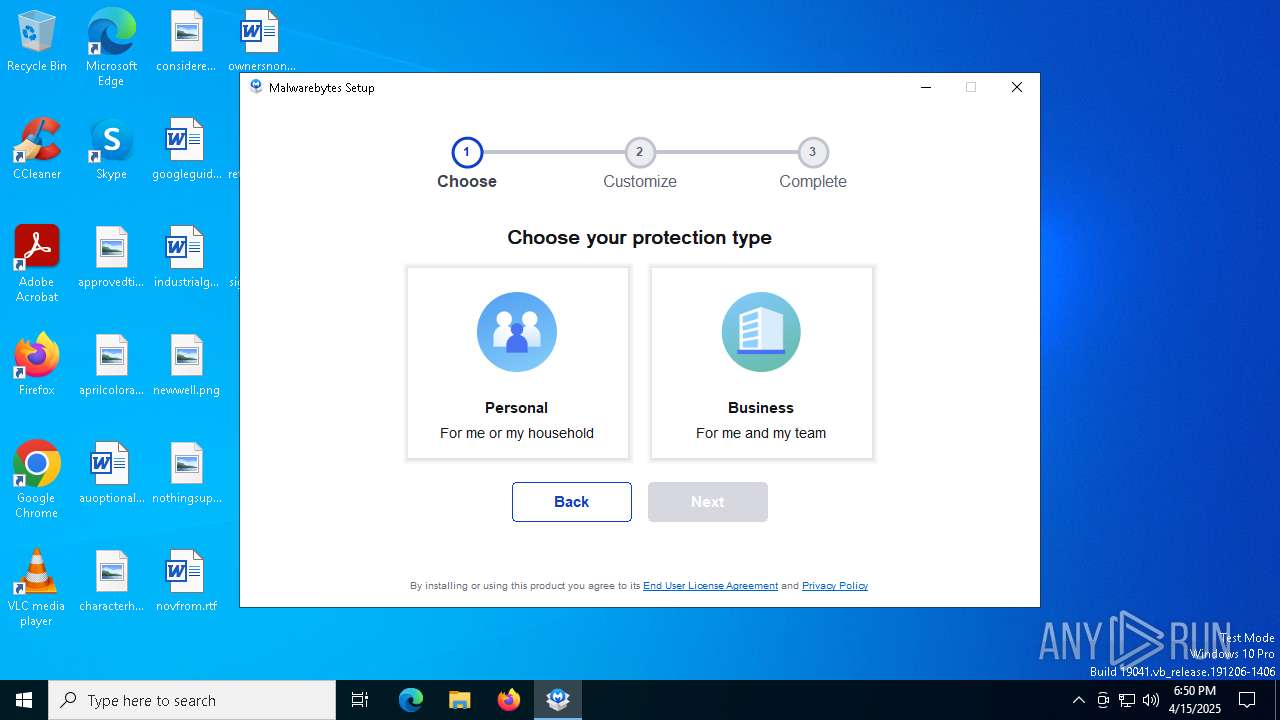
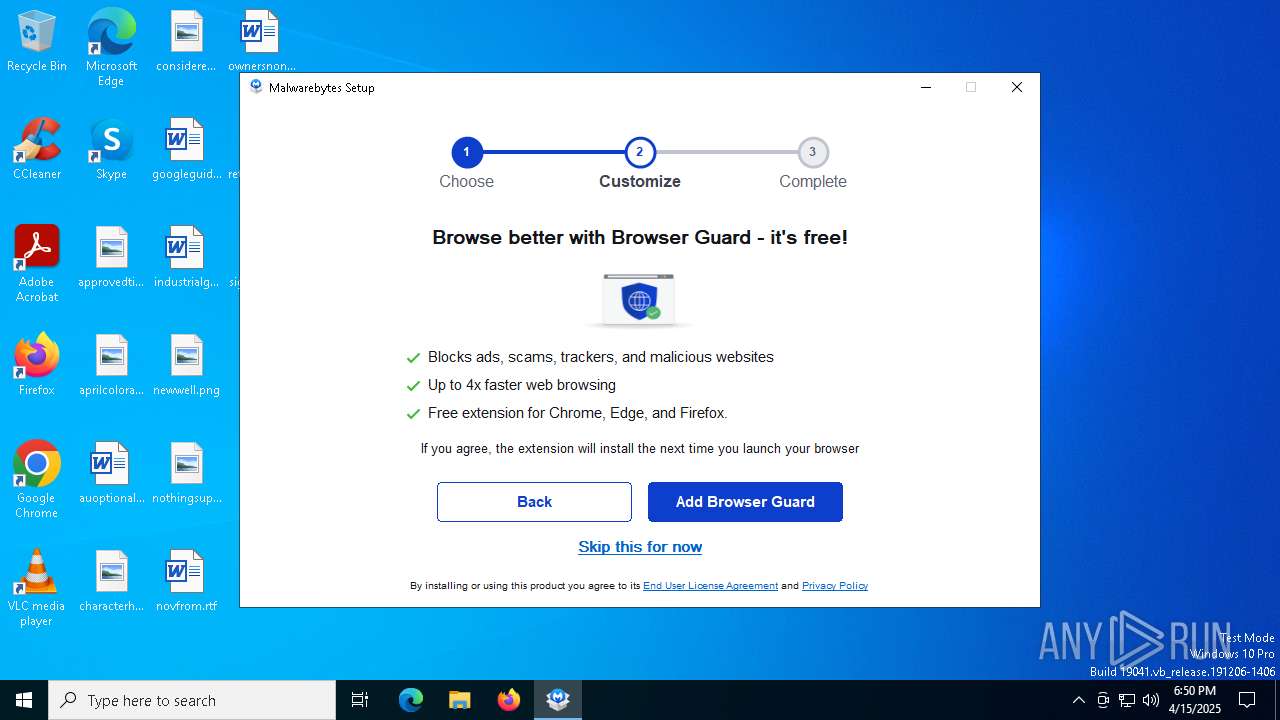
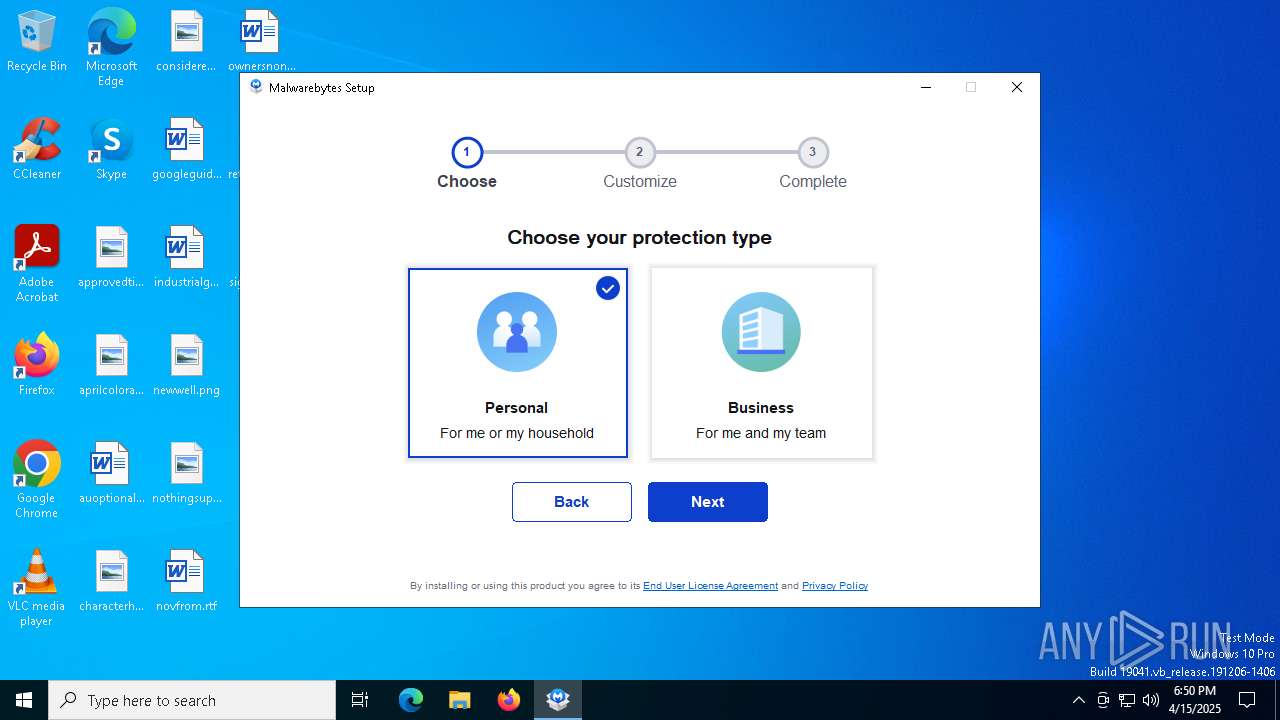
| URL: | https://www.instaluj.cz/malwarebytes-anti-malware-premium |
| Full analysis: | https://app.any.run/tasks/3e2062b1-5f56-4ab1-9ab2-f953c90b3ce4 |
| Verdict: | Malicious activity |
| Threats: | Agent Tesla is spyware that collects information about the actions of its victims by recording keystrokes and user interactions. It is falsely marketed as a legitimate software on the dedicated website where this malware is sold. |
| Analysis date: | April 15, 2025, 18:50:08 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MD5: | 6567F0C0BD9786C94E8D0719851F3795 |
| SHA1: | 166D467B89EC46410B17F1E12933CC52B0EE4FEC |
| SHA256: | 9F5EF26F613A47C0F1EB37555A9D02AB0BD02BD84703BF0AE8DB79801F1A5A88 |
| SSDEEP: | 3:N8DSLNRvzCTWIn:2OLDvuKIn |
MALICIOUS
Actions looks like stealing of personal data
- MBAMService.exe (PID: 7524)
Antivirus name has been found in the command line (generic signature)
- mbam.exe (PID: 6960)
Steals credentials from Web Browsers
- MBAMService.exe (PID: 7524)
AGENTTESLA is detected
- MBAMService.exe (PID: 7524)
SUSPICIOUS
Reads the BIOS version
- MBSetup.exe (PID: 2240)
- MBAMService.exe (PID: 7524)
- mbupdatrV5.exe (PID: 4380)
Creates files in the driver directory
- MBSetup.exe (PID: 2240)
- MBAMInstallerService.exe (PID: 7916)
- MBAMService.exe (PID: 1088)
- MBAMService.exe (PID: 7524)
Executable content was dropped or overwritten
- MBSetup.exe (PID: 2240)
- MBAMInstallerService.exe (PID: 7916)
- MBAMService.exe (PID: 1088)
- MBAMService.exe (PID: 7524)
The process verifies whether the antivirus software is installed
- MBSetup.exe (PID: 2240)
- MBAMInstallerService.exe (PID: 7916)
- MBAMService.exe (PID: 1088)
- MBAMService.exe (PID: 7524)
- MBAMWsc.exe (PID: 5744)
- mbamtray.exe (PID: 684)
- mbam.exe (PID: 6960)
- mbupdatrV5.exe (PID: 4380)
- MBAMWsc.exe (PID: 7048)
Searches for installed software
- MBSetup.exe (PID: 2240)
- MBAMInstallerService.exe (PID: 7916)
- MBAMService.exe (PID: 7524)
Executes as Windows Service
- MBAMInstallerService.exe (PID: 7916)
- MBAMService.exe (PID: 7524)
Process drops legitimate windows executable
- MBAMInstallerService.exe (PID: 7916)
- MBAMService.exe (PID: 7524)
Drops 7-zip archiver for unpacking
- MBAMInstallerService.exe (PID: 7916)
Drops a system driver (possible attempt to evade defenses)
- MBAMInstallerService.exe (PID: 7916)
- MBAMService.exe (PID: 1088)
- MBAMService.exe (PID: 7524)
The process drops C-runtime libraries
- MBAMInstallerService.exe (PID: 7916)
Adds/modifies Windows certificates
- MBAMInstallerService.exe (PID: 7916)
- MBAMService.exe (PID: 7524)
Changes Internet Explorer settings (feature browser emulation)
- MBAMInstallerService.exe (PID: 7916)
Creates or modifies Windows services
- MBAMService.exe (PID: 1088)
- MBAMService.exe (PID: 7524)
Reads security settings of Internet Explorer
- MBAMService.exe (PID: 7524)
- ig.exe (PID: 4812)
- mbamtray.exe (PID: 684)
- mbam.exe (PID: 6960)
Creates/Modifies COM task schedule object
- MBAMService.exe (PID: 7524)
Creates file in the systems drive root
- mbam.exe (PID: 6960)
Detected use of alternative data streams (AltDS)
- mbam.exe (PID: 6960)
Read startup parameters
- MBAMService.exe (PID: 7524)
Starts application from unusual location
- MBAMService.exe (PID: 7524)
Reads the date of Windows installation
- mbam.exe (PID: 6960)
There is functionality for taking screenshot (YARA)
- mbamtray.exe (PID: 684)
INFO
The sample compiled with english language support
- chrome.exe (PID: 1760)
- MBSetup.exe (PID: 2240)
- MBAMInstallerService.exe (PID: 7916)
- MBAMService.exe (PID: 1088)
- MBAMService.exe (PID: 7524)
Application launched itself
- chrome.exe (PID: 1760)
Create files in a temporary directory
- MBSetup.exe (PID: 2240)
- mbam.exe (PID: 6960)
Checks supported languages
- MBSetup.exe (PID: 2240)
- MBAMInstallerService.exe (PID: 7916)
- MBAMService.exe (PID: 1088)
- MBAMService.exe (PID: 7524)
- ig.exe (PID: 4812)
- mbamtray.exe (PID: 684)
- MBAMWsc.exe (PID: 5744)
- MBAMWsc.exe (PID: 7048)
- mbupdatrV5.exe (PID: 4380)
- mbam.exe (PID: 6960)
Reads the machine GUID from the registry
- MBSetup.exe (PID: 2240)
- MBAMInstallerService.exe (PID: 7916)
- MBAMService.exe (PID: 7524)
- mbupdatrV5.exe (PID: 4380)
Creates files in the program directory
- MBSetup.exe (PID: 2240)
- MBAMInstallerService.exe (PID: 7916)
- MBAMService.exe (PID: 7524)
- mbupdatrV5.exe (PID: 4380)
Executable content was dropped or overwritten
- chrome.exe (PID: 1760)
Reads the computer name
- MBSetup.exe (PID: 2240)
- MBAMInstallerService.exe (PID: 7916)
- MBAMService.exe (PID: 1088)
- MBAMService.exe (PID: 7524)
- mbamtray.exe (PID: 684)
- MBAMWsc.exe (PID: 5744)
- mbupdatrV5.exe (PID: 4380)
Checks proxy server information
- MBSetup.exe (PID: 2240)
- slui.exe (PID: 7884)
- mbamtray.exe (PID: 684)
- mbam.exe (PID: 6960)
Reads the software policy settings
- MBSetup.exe (PID: 2240)
- MBAMInstallerService.exe (PID: 7916)
- slui.exe (PID: 7792)
- slui.exe (PID: 7884)
- MBAMService.exe (PID: 7524)
The sample compiled with spanish language support
- MBAMInstallerService.exe (PID: 7916)
Reads CPU info
- MBAMService.exe (PID: 7524)
Reads the time zone
- MBAMService.exe (PID: 7524)
Reads Environment values
- MBAMService.exe (PID: 7524)
CONNECTWISE has been detected
- MBAMService.exe (PID: 7524)
Creates files or folders in the user directory
- mbamtray.exe (PID: 684)
- mbam.exe (PID: 6960)
Manual execution by a user
- mbam.exe (PID: 6960)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
180
Monitored processes
43
Malicious processes
10
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 684 | "C:\Program Files\Malwarebytes\Anti-Malware\mbamtray.exe" | C:\Program Files\Malwarebytes\Anti-Malware\mbamtray.exe | MBAMService.exe | ||||||||||||
User: admin Company: Malwarebytes Integrity Level: MEDIUM Description: Malwarebytes Tray Application Version: 4.0.0.1750 Modules
| |||||||||||||||
| 1088 | "C:\Program Files\Malwarebytes\Anti-Malware\MBAMService.exe" /Service /Protected | C:\Program Files\Malwarebytes\Anti-Malware\MBAMService.exe | MBAMInstallerService.exe | ||||||||||||
User: SYSTEM Company: Malwarebytes Integrity Level: SYSTEM Description: Malwarebytes Service Exit code: 0 Version: 3.2.0.1314 Modules
| |||||||||||||||
| 1760 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --disk-cache-dir=null --disk-cache-size=1 --media-cache-size=1 --disable-gpu-shader-disk-cache --disable-background-networking --disable-features=OptimizationGuideModelDownloading,OptimizationHintsFetching,OptimizationTargetPrediction,OptimizationHints "https://www.instaluj.cz/malwarebytes-anti-malware-premium" | C:\Program Files\Google\Chrome\Application\chrome.exe | explorer.exe | ||||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 122.0.6261.70 Modules
| |||||||||||||||
| 2240 | "C:\Users\admin\Downloads\MBSetup.exe" | C:\Users\admin\Downloads\MBSetup.exe | chrome.exe | ||||||||||||
User: admin Company: Malwarebytes Integrity Level: HIGH Description: Malwarebytes Setup Exit code: 0 Version: 4.5.34.347 Modules
| |||||||||||||||
| 2320 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=crashpad-handler "--user-data-dir=C:\Users\admin\AppData\Local\Google\Chrome\User Data" /prefetch:4 --monitor-self-annotation=ptype=crashpad-handler "--database=C:\Users\admin\AppData\Local\Google\Chrome\User Data\Crashpad" --url=https://clients2.google.com/cr/report --annotation=channel= --annotation=plat=Win64 --annotation=prod=Chrome --annotation=ver=122.0.6261.70 --initial-client-data=0x228,0x22c,0x230,0x204,0x234,0x7ffc8830dc40,0x7ffc8830dc4c,0x7ffc8830dc58 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 122.0.6261.70 Modules
| |||||||||||||||
| 2384 | ig.exe reseed | C:\Program Files\Malwarebytes\Anti-Malware\ig.exe | — | MBAMService.exe | |||||||||||
User: admin Company: MalwareBytes Integrity Level: LOW Description: Malware Scanner Exit code: 16711680 Version: 1.0.4.8 Modules
| |||||||||||||||
| 2392 | "C:\Users\admin\Downloads\MBSetup.exe" | C:\Users\admin\Downloads\MBSetup.exe | — | chrome.exe | |||||||||||
User: admin Company: Malwarebytes Integrity Level: MEDIUM Description: Malwarebytes Setup Exit code: 3221226540 Version: 4.5.34.347 Modules
| |||||||||||||||
| 3096 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --no-appcompat-clear --disable-gpu-compositing --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=14 --mojo-platform-channel-handle=5288 --field-trial-handle=1916,i,12222001880830628917,10693002999977549082,262144 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction --variations-seed-version /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 122.0.6261.70 Modules
| |||||||||||||||
| 4380 | "C:\PROGRAMDATA\MALWAREBYTES\MBAMSERVICE\updatrpkg\mbupdatrV5.exe" "C:\PROGRAM FILES\MALWAREBYTES\ANTI-MALWARE" "C:\PROGRAMDATA\MALWAREBYTES\MBAMSERVICE\config\UpdateControllerConfig.json" "C:\PROGRAMDATA\MALWAREBYTES\MBAMSERVICE" "C:\PROGRAMDATA\MALWAREBYTES\MBAMSERVICE\dbclsupdate\staging" /db:dbupdate /su:no | C:\ProgramData\Malwarebytes\MBAMService\updatrpkg\mbupdatrV5.exe | — | MBAMService.exe | |||||||||||
User: SYSTEM Company: Malwarebytes Integrity Level: SYSTEM Description: Malwarebytes Component Updater Exit code: 0 Version: 3.1.0.510 Modules
| |||||||||||||||
| 4812 | ig.exe secure | C:\Users\admin\AppData\LocalLow\IGDump\sec\ig.exe | — | MBAMService.exe | |||||||||||
User: admin Company: MalwareBytes Integrity Level: LOW Description: Malware Scanner Exit code: 3235811341 Version: 1.0.4.8 Modules
| |||||||||||||||
Total events
305 106
Read events
304 155
Write events
913
Delete events
38
Modification events
| (PID) Process: | (1760) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (1760) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (1760) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (1760) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\StabilityMetrics |
| Operation: | write | Name: | user_experience_metrics.stability.exited_cleanly |
Value: 0 | |||
| (PID) Process: | (1760) chrome.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Google\Update\ClientStateMedium\{8A69D345-D564-463C-AFF1-A69D9E530F96} |
| Operation: | write | Name: | usagestats |
Value: 0 | |||
| (PID) Process: | (7944) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Shell Extensions\Cached |
| Operation: | write | Name: | {2781761E-28E0-4109-99FE-B9D127C57AFE} {56FFCC30-D398-11D0-B2AE-00A0C908FA49} 0xFFFF |
Value: 010000000000000026975D4237AEDB01 | |||
| (PID) Process: | (2240) MBSetup.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Malwarebytes |
| Operation: | write | Name: | id |
Value: e736bf3e799440b4b983e93b2d181dbc | |||
| (PID) Process: | (2240) MBSetup.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Malwarebytes |
| Operation: | write | Name: | id |
Value: e736bf3e799440b4b983e93b2d181dbc | |||
| (PID) Process: | (2240) MBSetup.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\mbamtestkey |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (1760) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\StabilityMetrics |
| Operation: | write | Name: | user_experience_metrics.stability.exited_cleanly |
Value: 1 | |||
Executable files
336
Suspicious files
570
Text files
1 134
Unknown types
6
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1760 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\parcel_tracking_db\LOG.old~RF10c323.TMP | — | |
MD5:— | SHA256:— | |||
| 1760 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\coupon_db\LOG.old~RF10c323.TMP | — | |
MD5:— | SHA256:— | |||
| 1760 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\discounts_db\LOG.old~RF10c323.TMP | — | |
MD5:— | SHA256:— | |||
| 1760 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\coupon_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 1760 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\parcel_tracking_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 1760 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\discounts_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 1760 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\commerce_subscription_db\LOG.old~RF10c323.TMP | — | |
MD5:— | SHA256:— | |||
| 1760 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\PersistentOriginTrials\LOG.old~RF10c332.TMP | — | |
MD5:— | SHA256:— | |||
| 1760 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\commerce_subscription_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 1760 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\chrome_cart_db\LOG.old~RF10c323.TMP | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
24
TCP/UDP connections
183
DNS requests
152
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 23.48.23.173:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | GET | 200 | 23.48.23.173:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
7524 | MBAMService.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTfIs%2BLjDtGwQ09XEB1Yeq%2BtX%2BBgQQU7NfjgtJxXWRM3y5nP%2Be6mK4cD08CEAitQLJg0pxMn17Nqb2Trtk%3D | unknown | — | — | whitelisted |
7524 | MBAMService.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSRXerF0eFeSWRripTgTkcJWMm7iQQUaDfg67Y7%2BF8Rhvv%2BYXsIiGX0TkICEAYsPEaBY%2BtRPgLpmSJnQ9Y%3D | unknown | — | — | whitelisted |
7524 | MBAMService.exe | GET | 200 | 172.64.149.23:80 | http://ocsp.comodoca.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBRTtU9uFqgVGHhJwXZyWCNXmVR5ngQUoBEKIz6W8Qfs4q8p74Klf9AwpLQCEDlyRDr5IrdR19NsEN0xNZU%3D | unknown | — | — | whitelisted |
7524 | MBAMService.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTfIs%2BLjDtGwQ09XEB1Yeq%2BtX%2BBgQQU7NfjgtJxXWRM3y5nP%2Be6mK4cD08CEAc2N7ckVHzYR6z9KGYqXls%3D | unknown | — | — | whitelisted |
7524 | MBAMService.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTjzY2p9Pa8oibmj%2BNSMWsz63kmWgQUuhbZbU2FL3MpdpovdYxqII%2BeyG8CEAuuZrxaun%2BVh8b56QTjMwQ%3D | unknown | — | — | whitelisted |
7524 | MBAMService.exe | GET | 200 | 172.64.149.23:80 | http://ocsp.usertrust.com/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBTNMNJMNDqCqx8FcBWK16EHdimS6QQUU3m%2FWqorSs9UgOHYm8Cd8rIDZssCEQCeArDpSs6yEJyh6YNr4MLb | unknown | — | — | whitelisted |
7524 | MBAMService.exe | GET | 200 | 104.18.38.233:80 | http://ocsp.sectigo.com/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBQRz3ETyLz2DaZTxGOH%2BA%2BjK7MkGAQUJGWTmAgB6E7U1kzqZFXhwPr7z7MCEQCmV%2Fd4sxrlI9ZnExcY0W6y | unknown | — | — | whitelisted |
7524 | MBAMService.exe | GET | 200 | 184.24.77.7:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut_2010-06-23.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 4.231.128.59:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
2104 | svchost.exe | 4.231.128.59:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 23.48.23.173:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
5496 | MoUsoCoreWorker.exe | 23.48.23.173:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1760 | chrome.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
7248 | chrome.exe | 185.59.208.192:443 | www.instaluj.cz | VSHosting s.r.o. | CZ | whitelisted |
7248 | chrome.exe | 108.177.14.84:443 | accounts.google.com | GOOGLE | US | whitelisted |
3216 | svchost.exe | 172.211.123.248:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.instaluj.cz |
| whitelisted |
accounts.google.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
www.googletagmanager.com |
| whitelisted |
www.google.com |
| whitelisted |
pagead2.googlesyndication.com |
| whitelisted |
fundingchoicesmessages.google.com |
| whitelisted |
www.facebook.com |
| whitelisted |