| File name: | hack tool for minecraft.exe |
| Full analysis: | https://app.any.run/tasks/632c031f-4bb1-4d51-9932-5961e722c862 |
| Verdict: | Malicious activity |
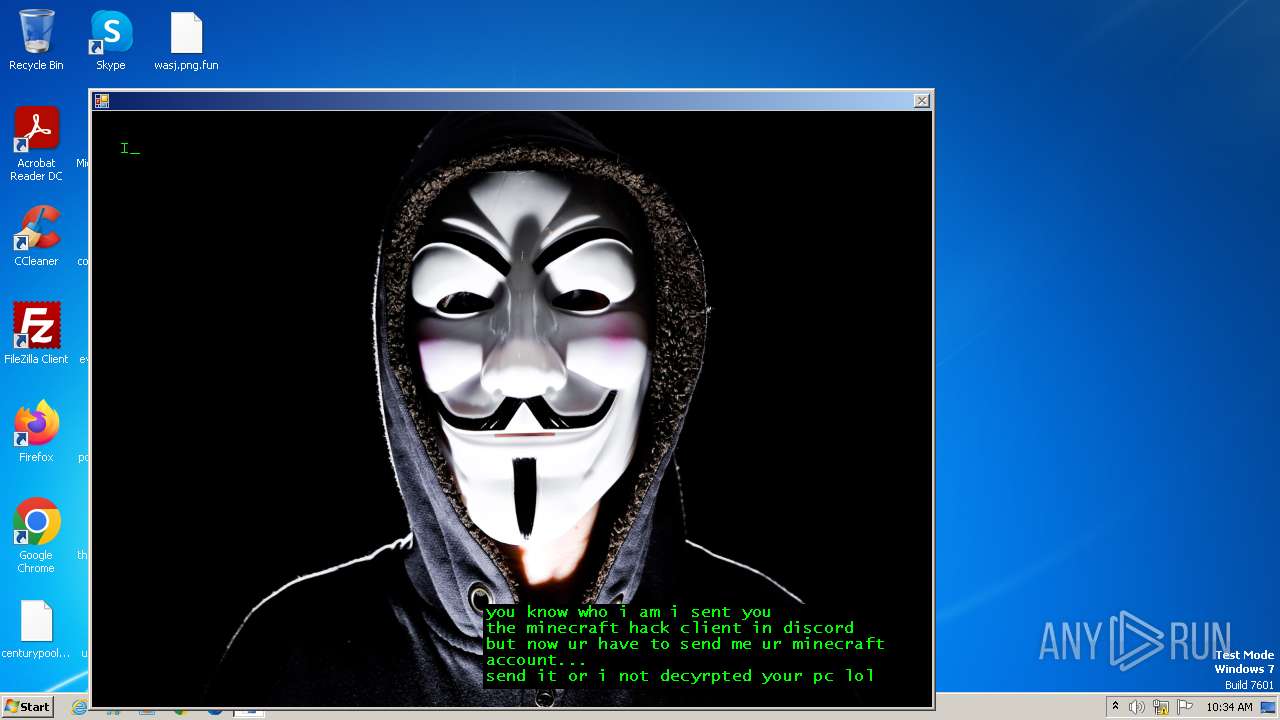
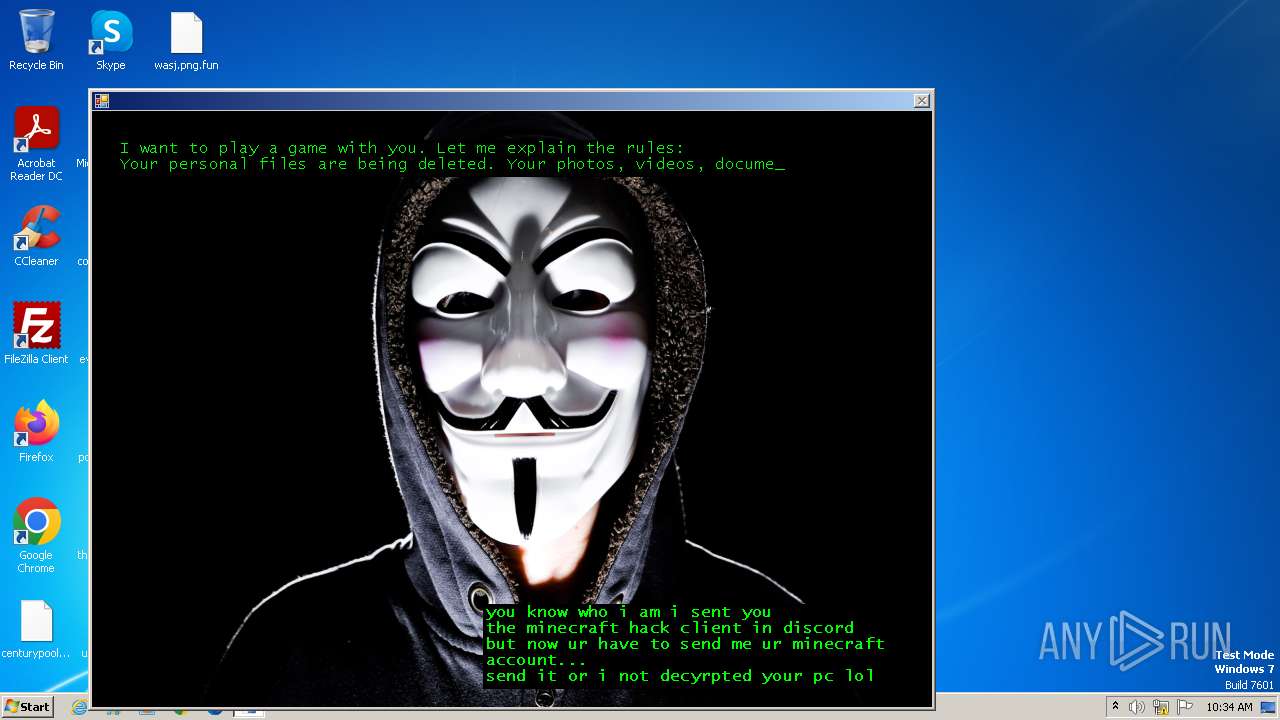
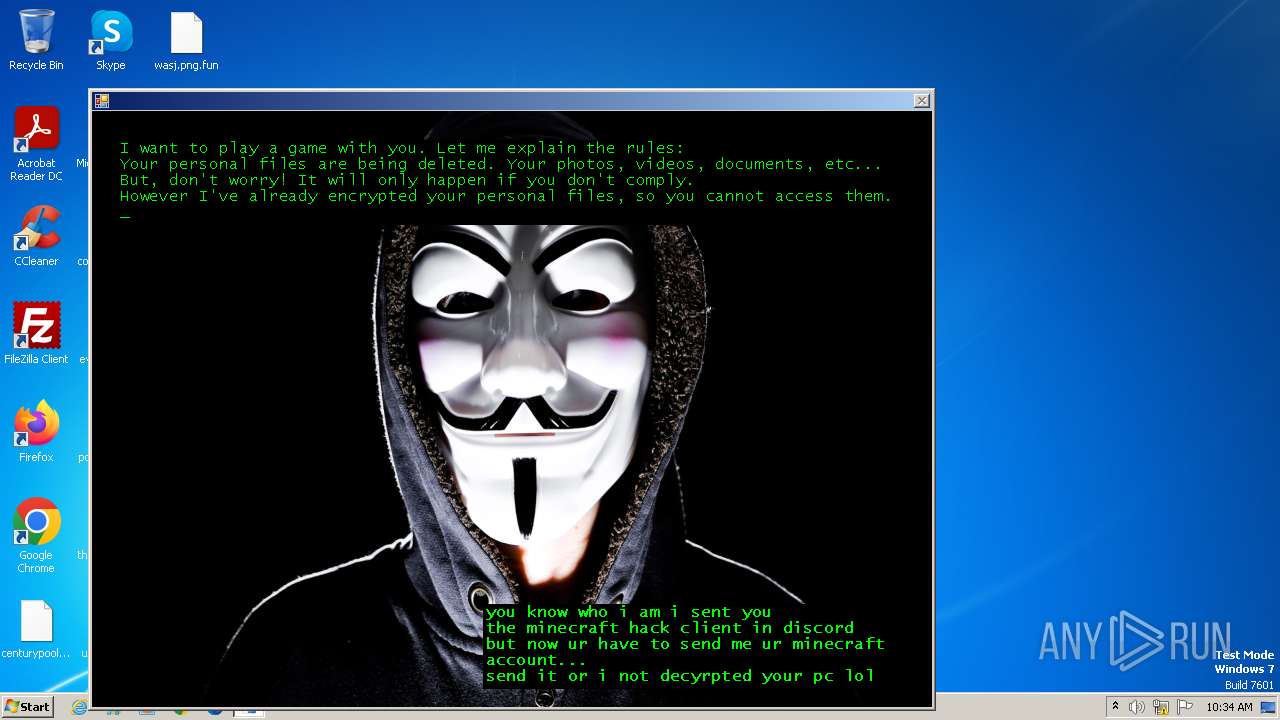
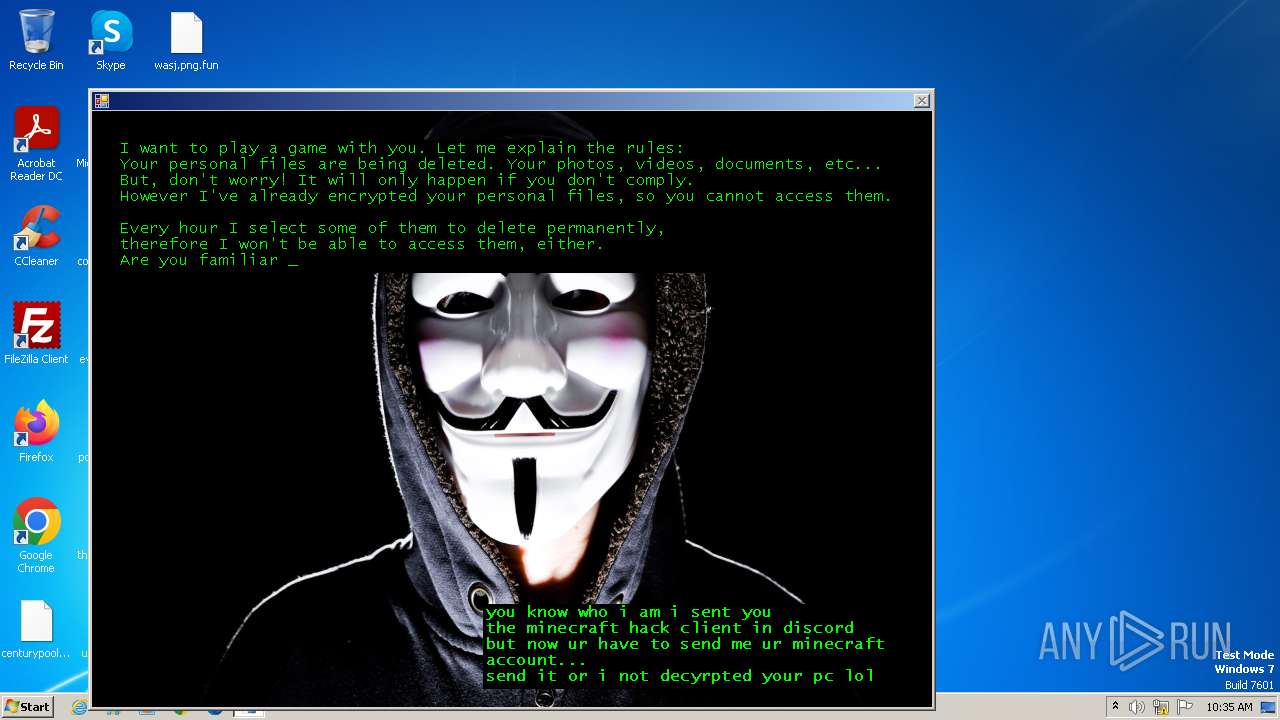
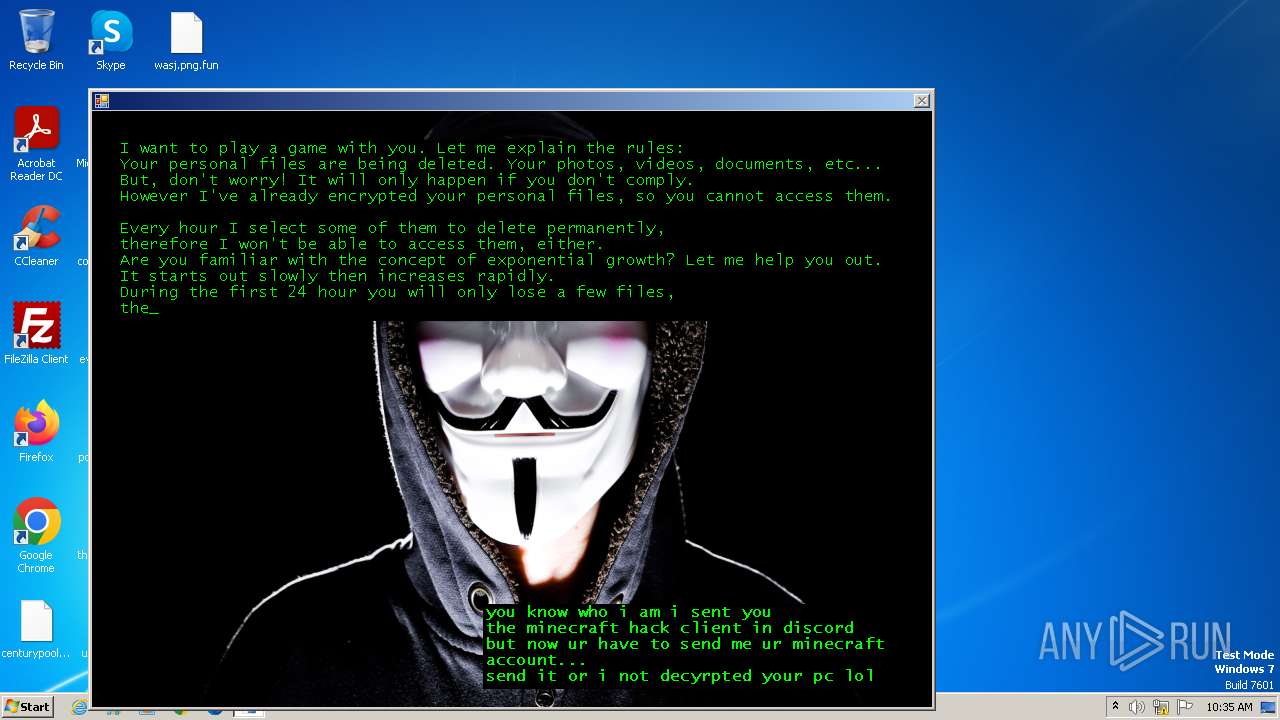
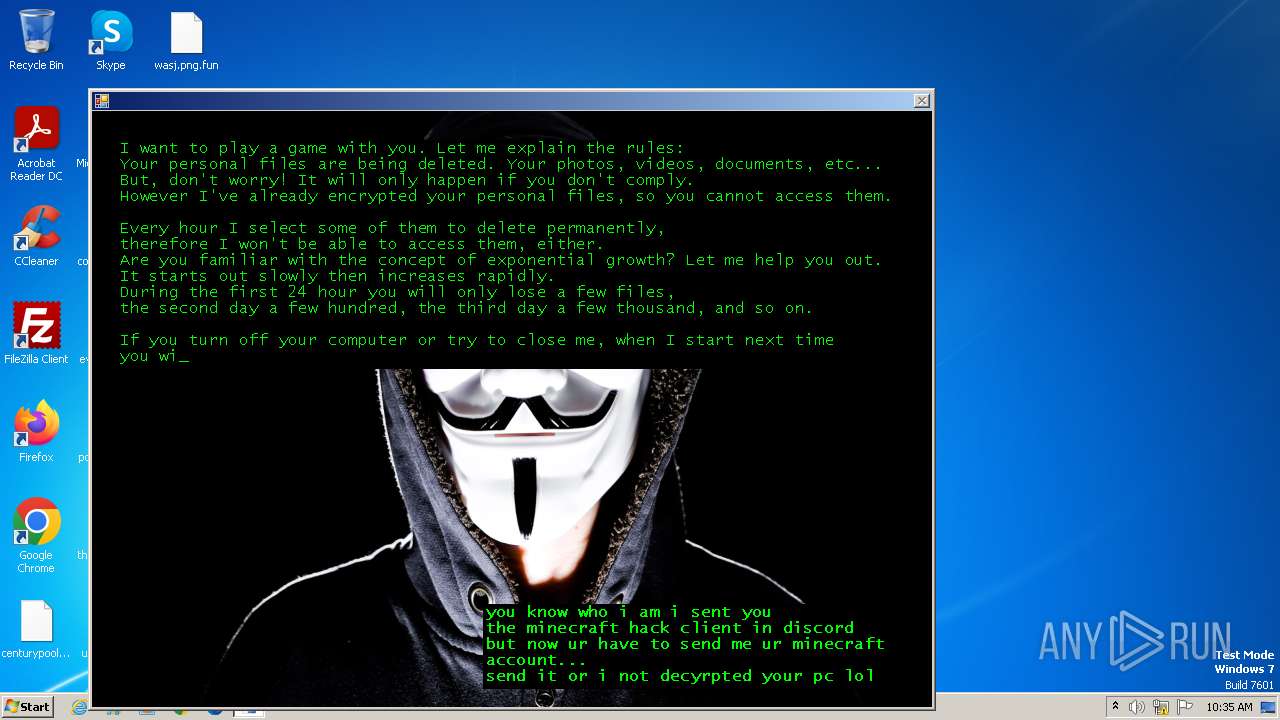
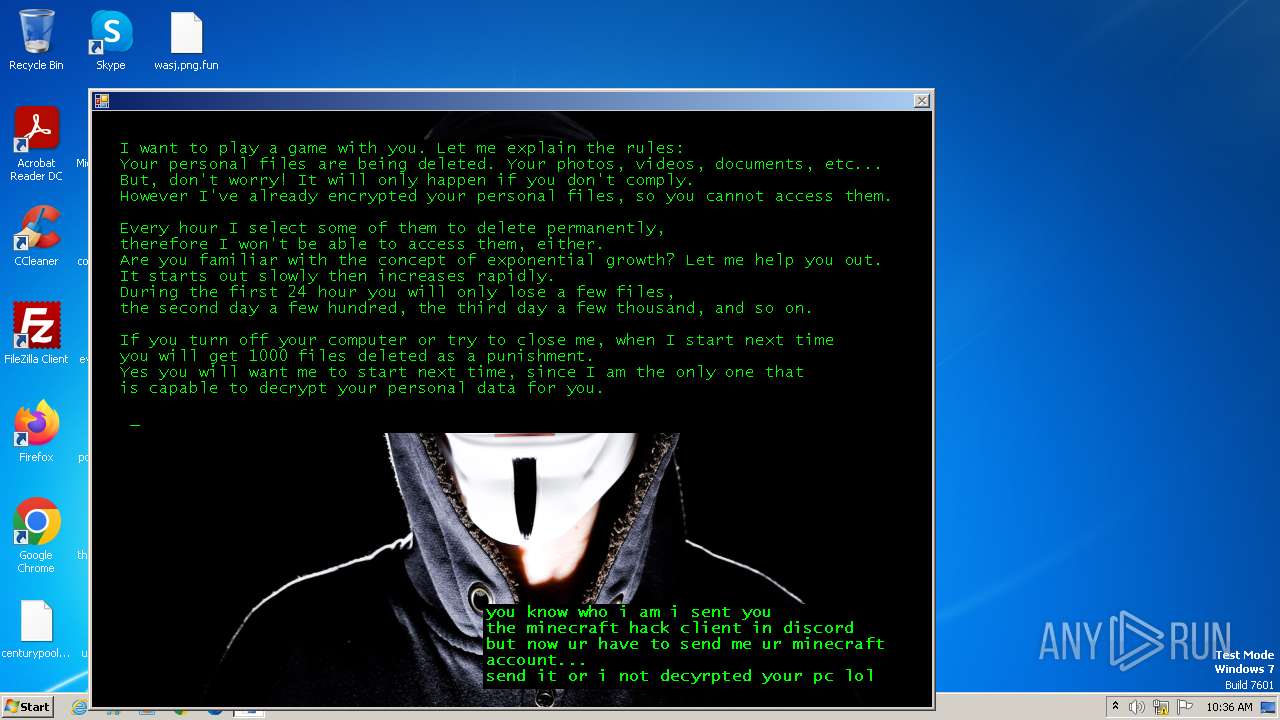
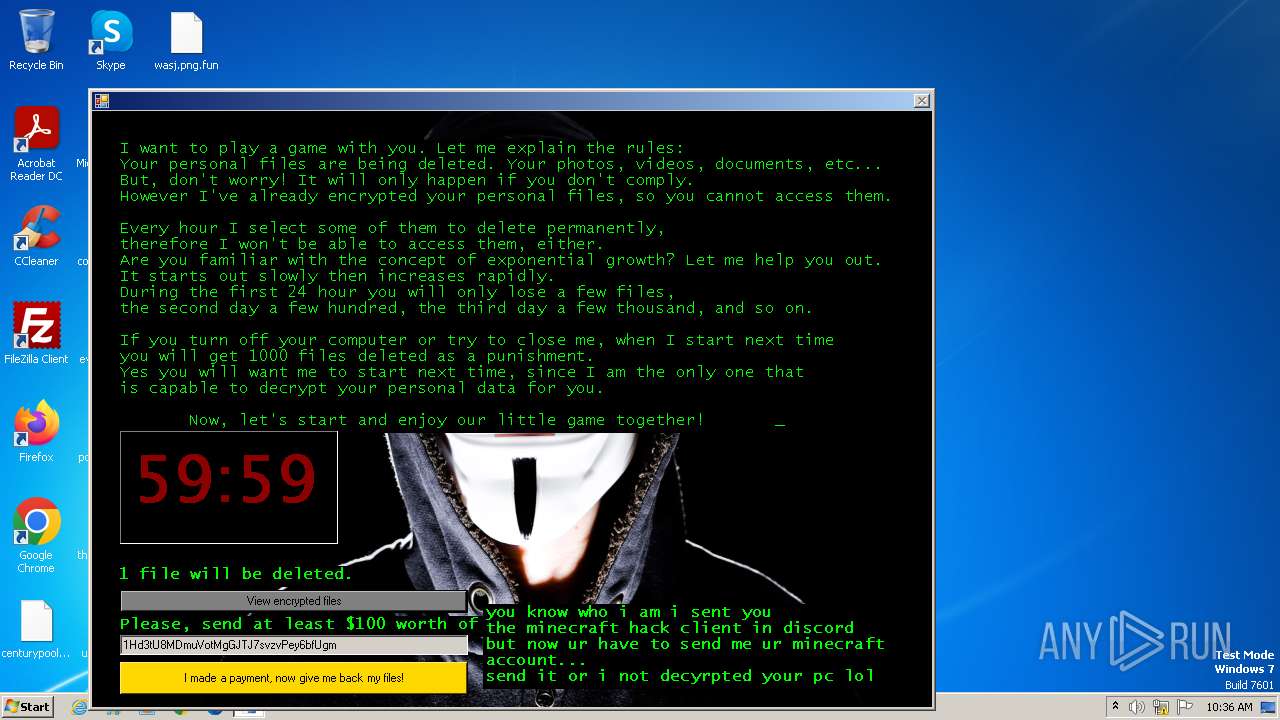
| Threats: | The Jigsaw ransomware, initially detected in 2016, encrypts files on compromised systems and requires a ransom payment in Bitcoin. If the ransom is not paid, the malware starts deleting files, increasing the pressure on victims to comply. Its source code is publicly accessible, allowing various threat actors to customize and repurpose the malware for different objectives. |
| Analysis date: | December 10, 2023, 10:33:11 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386 Mono/.Net assembly, for MS Windows |
| MD5: | 1FF8649E8F8D0652D583B9A648161D3F |
| SHA1: | 3441FF983221742ED460F8310E49203B5DC59A15 |
| SHA256: | 9F3C538A1118F82D49A993967C520BE4C7F14AD994EB17C4D778E5D7F32241A7 |
| SSDEEP: | 12288:2w1pOfl/oUzs8vwfzNquSgkE9tSF/aXx6:3po/oUNwfpqVrktOc6 |
MALICIOUS
Drops the executable file immediately after the start
- hack tool for minecraft.exe (PID: 1556)
Modifies files in the Chrome extension folder
- drpbx.exe (PID: 2620)
Steals credentials from Web Browsers
- drpbx.exe (PID: 2620)
Actions looks like stealing of personal data
- drpbx.exe (PID: 2620)
SUSPICIOUS
Reads the Internet Settings
- hack tool for minecraft.exe (PID: 1556)
Starts itself from another location
- hack tool for minecraft.exe (PID: 1556)
INFO
Checks supported languages
- hack tool for minecraft.exe (PID: 1556)
- drpbx.exe (PID: 2620)
Reads the computer name
- hack tool for minecraft.exe (PID: 1556)
Reads the machine GUID from the registry
- hack tool for minecraft.exe (PID: 1556)
- drpbx.exe (PID: 2620)
Creates files or folders in the user directory
- hack tool for minecraft.exe (PID: 1556)
- drpbx.exe (PID: 2620)
Creates files in the program directory
- drpbx.exe (PID: 2620)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Generic CIL Executable (.NET, Mono, etc.) (63.1) |
|---|---|---|
| .exe | | | Win64 Executable (generic) (23.8) |
| .dll | | | Win32 Dynamic Link Library (generic) (5.6) |
| .exe | | | Win32 Executable (generic) (3.8) |
| .exe | | | Generic Win/DOS Executable (1.7) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2022:10:26 00:50:34+02:00 |
| ImageFileCharacteristics: | Executable, Large address aware |
| PEType: | PE32 |
| LinkerVersion: | 48 |
| CodeSize: | 428544 |
| InitializedDataSize: | 2560 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x6a97e |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 37.0.2.5583 |
| ProductVersionNumber: | 37.0.2.5583 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
| Comments: | - |
| CompanyName: | - |
| FileDescription: | Firefox |
| FileVersion: | 37.0.2.5583 |
| InternalName: | JigsawRansomware.exe |
| LegalCopyright: | Copyright 1999-2012 Firefox and Mozzilla developers. All rights reserved. |
| LegalTrademarks: | - |
| OriginalFileName: | JigsawRansomware.exe |
| ProductName: | Firefox |
| ProductVersion: | 37.0.2.5583 |
| AssemblyVersion: | 37.0.2.5583 |
Total processes
40
Monitored processes
2
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1556 | "C:\Users\admin\Desktop\hack tool for minecraft.exe" | C:\Users\admin\Desktop\hack tool for minecraft.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: Firefox Exit code: 0 Version: 37.0.2.5583 Modules
| |||||||||||||||
| 2620 | "C:\Users\admin\AppData\Local\Drpbx\drpbx.exe" C:\Users\admin\Desktop\hack?tool?for?minecraft.exe | C:\Users\admin\AppData\Local\Drpbx\drpbx.exe | hack tool for minecraft.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Description: Firefox Exit code: 0 Version: 37.0.2.5583 Modules
| |||||||||||||||
Total events
60 608
Read events
60 600
Write events
8
Delete events
0
Modification events
| (PID) Process: | (1556) hack tool for minecraft.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (1556) hack tool for minecraft.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (1556) hack tool for minecraft.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (1556) hack tool for minecraft.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
Executable files
2
Suspicious files
938
Text files
5
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2620 | drpbx.exe | C:\MSOCache\All Users\{90140000-0015-0411-0000-0000000FF1CE}-C\branding.xml.fun | binary | |
MD5:9CE60AE5D902C725E5F2FA69BDEF31F4 | SHA256:508FE948F27833BC173744AFE1E894624CC199962667BED8B1BDB1D767522835 | |||
| 2620 | drpbx.exe | C:\MSOCache\All Users\{90140000-0015-0407-0000-0000000FF1CE}-C\AccessMUI.xml.fun | binary | |
MD5:AB579E792F7FA3290B54EF871C01A74D | SHA256:853239C7DCF00B123F7AECDA700FC78ED139B8F0DAE5136C0F537D68E516F8F5 | |||
| 2620 | drpbx.exe | C:\MSOCache\All Users\{90140000-0015-0407-0000-0000000FF1CE}-C\branding.xml.fun | binary | |
MD5:EF000E1A1EFCFE8A912643A14539E620 | SHA256:2C69C389931513B53EA16E90EB2A9CC520A05E0D9A735698670C0DAB5CA1FAE9 | |||
| 2620 | drpbx.exe | C:\MSOCache\All Users\{90140000-0015-040C-0000-0000000FF1CE}-C\AccessMUI.xml.fun | binary | |
MD5:A0F9CC5AB721241DCE18151AF1072BD7 | SHA256:15CA21FE60EBE43D4D3CC867246B10A622E6CD39D765200E909A057516BFB227 | |||
| 1556 | hack tool for minecraft.exe | C:\Users\admin\AppData\Local\Drpbx\drpbx.exe | executable | |
MD5:1FF8649E8F8D0652D583B9A648161D3F | SHA256:9F3C538A1118F82D49A993967C520BE4C7F14AD994EB17C4D778E5D7F32241A7 | |||
| 2620 | drpbx.exe | C:\MSOCache\All Users\{90140000-0015-040C-0000-0000000FF1CE}-C\Setup.xml.fun | binary | |
MD5:947CE8C6C3B65B0A23F758417767B8E7 | SHA256:D1235C6EA86F5C35D7CAA8F2054B7A7A9F031309BB05DA31E5A74FD6F7159D43 | |||
| 2620 | drpbx.exe | C:\MSOCache\All Users\{90140000-0015-0410-0000-0000000FF1CE}-C\AccessMUI.xml.fun | binary | |
MD5:AC219F9BB0B2463BABE301C5CF26E337 | SHA256:0A07391DE5E2F383D85C786BCECCBD980064202801201A46DDF757CD537A1182 | |||
| 2620 | drpbx.exe | C:\MSOCache\All Users\{90140000-0015-0410-0000-0000000FF1CE}-C\Setup.xml.fun | binary | |
MD5:1003A80B99EB3F9661F6F8D11E68D2C8 | SHA256:FCAD2459807B675F3C0F7DB7C5C020F06F50EF19113E5697962B67578D7A5F4D | |||
| 2620 | drpbx.exe | C:\MSOCache\All Users\{90140000-0015-0411-0000-0000000FF1CE}-C\AccessMUI.xml.fun | binary | |
MD5:A039C14D02B16E6B45EDF4AF2FF3E822 | SHA256:AA0EDB903170CB8174FD6C70AC0F9ECD96DC8F2313BC88E95B0E5D6F3FC923DB | |||
| 2620 | drpbx.exe | C:\MSOCache\All Users\{90140000-0015-0411-0000-0000000FF1CE}-C\Setup.xml.fun | binary | |
MD5:5B45E96AB1F1B4355DA52AAEFF609C48 | SHA256:48FBF2AA6C73E576034B9F91148748D4EA680CBDFF4167169218DBC4154EC189 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
4
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2588 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |