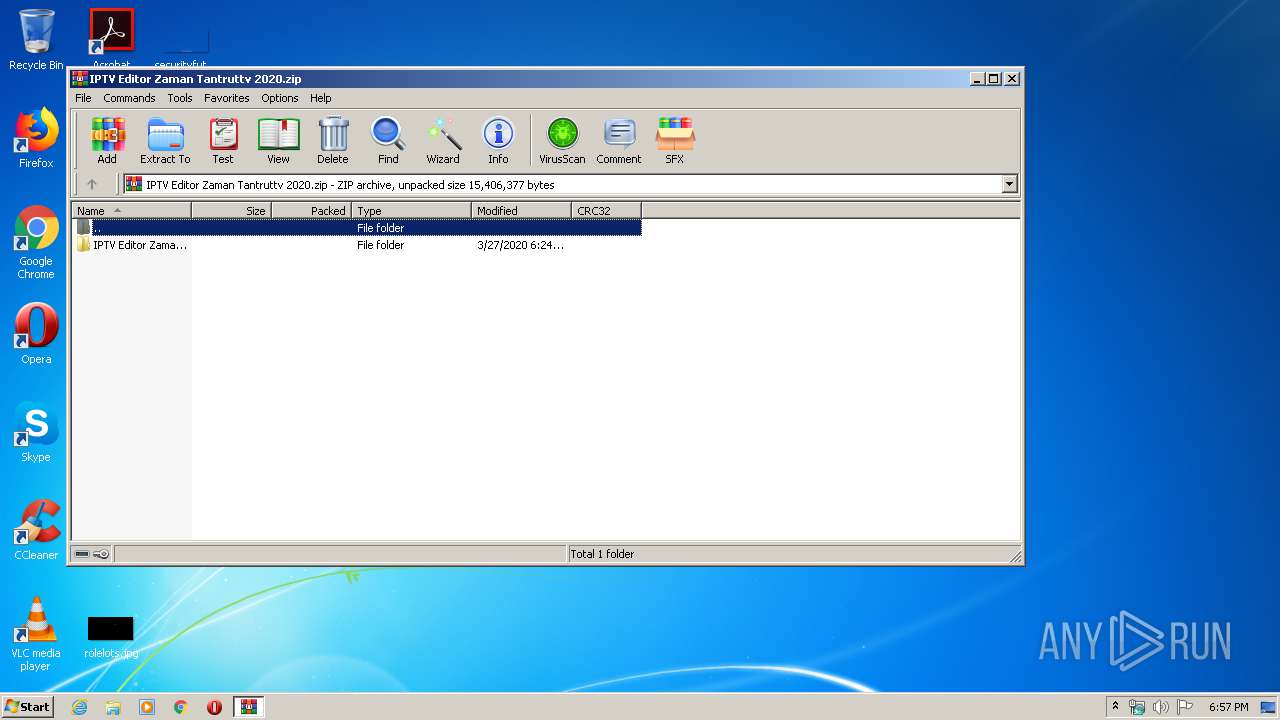
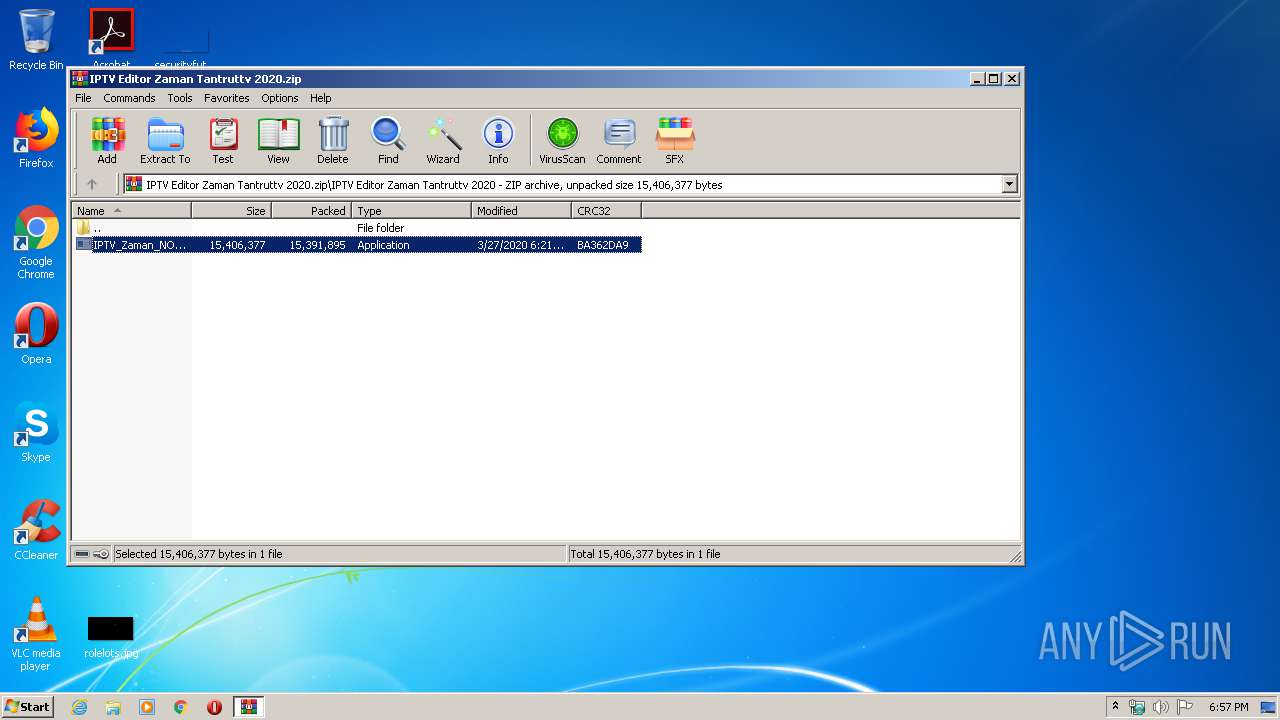
| File name: | IPTV Editor Zaman Tantruttv 2020.zip |
| Full analysis: | https://app.any.run/tasks/9542612a-2c8b-4fc0-824e-6154e9cee5be |
| Verdict: | Malicious activity |
| Threats: | Crypto mining malware is a resource-intensive threat that infiltrates computers with the purpose of mining cryptocurrencies. This type of threat can be deployed either on an infected machine or a compromised website. In both cases the miner will utilize the computing power of the device and its network bandwidth. |
| Analysis date: | March 27, 2020, 18:56:45 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract |
| MD5: | B797406E62D7AE9622DA43AC74F3FC11 |
| SHA1: | 37E5915C0E26E4E310E1E750E62D1D8B8F981341 |
| SHA256: | 9F3512E389ABF88043BAFA695766AD4CD9971FBB85DF275C72164061ACB1725C |
| SSDEEP: | 393216:qOY9fa6WwGNrVroBTWR5j26JC6089B2uPFdnEU7qJ:M9+XZroBTgROypfnEUGJ |
MALICIOUS
Application was dropped or rewritten from another process
- IPTV_Zaman_NOW.exe (PID: 3080)
- IPTV_Zaman_NOW.exe (PID: 1724)
- IPTV_Zaman_NOW.exe (PID: 2792)
- IPTV_Zaman_NOW.exe (PID: 3932)
- CL_Debug_Log.txt (PID: 2432)
- Svchost.exe (PID: 3220)
- Helper.exe (PID: 1500)
- Helper.exe (PID: 1516)
- svchost.com (PID: 1744)
- svchost.com (PID: 280)
- Helper.exe (PID: 3428)
- Helper.exe (PID: 1920)
- Helper.exe (PID: 3972)
- tor.exe (PID: 3768)
- svchost.com (PID: 3352)
- svchost.com (PID: 3040)
- Helper.exe (PID: 3460)
- Helper.exe (PID: 2920)
- Helper.exe (PID: 2428)
- svchost.com (PID: 3272)
- svchost.com (PID: 2884)
- Helper.exe (PID: 2548)
- Helper.exe (PID: 1684)
- Helper.exe (PID: 1940)
- Helper.exe (PID: 3136)
- svchost.com (PID: 2752)
- svchost.com (PID: 3884)
- Helper.exe (PID: 3916)
- Helper.exe (PID: 3424)
Changes the autorun value in the registry
- WScript.exe (PID: 660)
Writes to a start menu file
- WScript.exe (PID: 660)
Uses Task Scheduler to run other applications
- cmd.exe (PID: 3556)
Loads dropped or rewritten executable
- IPTV_Zaman_NOW.exe (PID: 2792)
- tor.exe (PID: 3768)
Loads the Task Scheduler COM API
- schtasks.exe (PID: 2540)
Connects to CnC server
- attrib.exe (PID: 3892)
Looks like application has launched a miner
- Helper.exe (PID: 1920)
Modifies files in Chrome extension folder
- chrome.exe (PID: 3052)
MINER was detected
- attrib.exe (PID: 3892)
Changes settings of System certificates
- IPTV_Zaman_NOW.exe (PID: 2792)
SUSPICIOUS
Executes scripts
- IPTV_Zaman_NOW.exe (PID: 1724)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 3284)
- IPTV_Zaman_NOW.exe (PID: 1724)
- IPTV_Zaman_NOW.exe (PID: 3932)
- Svchost.exe (PID: 3220)
- CL_Debug_Log.txt (PID: 2432)
- IPTV_Zaman_NOW.exe (PID: 2792)
- Helper.exe (PID: 1500)
- Helper.exe (PID: 3972)
- Helper.exe (PID: 1920)
Creates files in the user directory
- IPTV_Zaman_NOW.exe (PID: 1724)
- WScript.exe (PID: 660)
- Svchost.exe (PID: 3220)
- vlc.exe (PID: 2312)
Creates executable files which already exist in Windows
- IPTV_Zaman_NOW.exe (PID: 1724)
Creates files in the Windows directory
- IPTV_Zaman_NOW.exe (PID: 3932)
Reads Internet Cache Settings
- WScript.exe (PID: 660)
- chrome.exe (PID: 3052)
- IPTV_Zaman_NOW.exe (PID: 2792)
Modifies the open verb of a shell class
- IPTV_Zaman_NOW.exe (PID: 3932)
Starts application with an unusual extension
- Svchost.exe (PID: 3220)
- Helper.exe (PID: 1516)
- Helper.exe (PID: 1500)
- Helper.exe (PID: 1920)
- Helper.exe (PID: 2428)
- Helper.exe (PID: 3460)
- Helper.exe (PID: 1940)
- Helper.exe (PID: 3136)
Executed via Task Scheduler
- Helper.exe (PID: 1516)
- Helper.exe (PID: 1500)
- Helper.exe (PID: 3460)
- Helper.exe (PID: 2428)
- Helper.exe (PID: 3136)
- Helper.exe (PID: 1940)
Starts CMD.EXE for commands execution
- Svchost.exe (PID: 3220)
Checks for external IP
- WScript.exe (PID: 660)
Starts itself from another location
- Helper.exe (PID: 1516)
- Helper.exe (PID: 1500)
- Helper.exe (PID: 3460)
- Helper.exe (PID: 2428)
- Helper.exe (PID: 1940)
- Helper.exe (PID: 3136)
Reads Environment values
- IPTV_Zaman_NOW.exe (PID: 2792)
Application launched itself
- Helper.exe (PID: 1920)
- chrome.exe (PID: 3052)
Reads the cookies of Google Chrome
- chrome.exe (PID: 3140)
Uses ATTRIB.EXE to modify file attributes
- Helper.exe (PID: 1920)
Reads internet explorer settings
- IPTV_Zaman_NOW.exe (PID: 2792)
Adds / modifies Windows certificates
- IPTV_Zaman_NOW.exe (PID: 2792)
INFO
Reads the hosts file
- chrome.exe (PID: 3140)
- chrome.exe (PID: 3052)
Manual execution by user
- svchost.com (PID: 3040)
Reads settings of System Certificates
- chrome.exe (PID: 3140)
- IPTV_Zaman_NOW.exe (PID: 2792)
Dropped object may contain Bitcoin addresses
- tor.exe (PID: 3768)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | None |
| ZipModifyDate: | 2020:03:27 19:24:16 |
| ZipCRC: | 0x00000000 |
| ZipCompressedSize: | - |
| ZipUncompressedSize: | - |
| ZipFileName: | IPTV Editor Zaman Tantruttv 2020/ |
Total processes
116
Monitored processes
70
Malicious processes
18
Suspicious processes
4
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 280 | "C:\Windows\svchost.com" "C:\Users\admin\AppData\Local\Temp\3582-490\Helper.exe" -SystemCheck | C:\Windows\svchost.com | — | Helper.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 528 | "C:\PROGRA~1\Google\Chrome\APPLIC~1\chrome.exe" --type=utility --field-trial-handle=980,350635825690401994,6632272437260086580,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --service-request-channel-token=13572955635994695765 --mojo-platform-channel-handle=2924 --ignored=" --type=renderer " /prefetch:8 | C:\PROGRA~1\Google\Chrome\APPLIC~1\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 572 | "C:\PROGRA~1\Google\Chrome\APPLIC~1\chrome.exe" --type=renderer --field-trial-handle=980,350635825690401994,6632272437260086580,131072 --enable-features=PasswordImport --disable-gpu-compositing --lang=en-US --extension-process --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=10208943683839588720 --renderer-client-id=28 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=4892 /prefetch:1 | C:\PROGRA~1\Google\Chrome\APPLIC~1\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 660 | "C:\Windows\System32\WScript.exe" "C:\Users\admin\AppData\Roaming\Svchost.js" | C:\Windows\System32\WScript.exe | IPTV_Zaman_NOW.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft ® Windows Based Script Host Exit code: 0 Version: 5.8.7600.16385 Modules
| |||||||||||||||
| 852 | "C:\PROGRA~1\Google\Chrome\APPLIC~1\chrome.exe" --type=utility --field-trial-handle=980,350635825690401994,6632272437260086580,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --service-request-channel-token=330936590752769550 --mojo-platform-channel-handle=3764 --ignored=" --type=renderer " /prefetch:8 | C:\PROGRA~1\Google\Chrome\APPLIC~1\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 1024 | "C:\PROGRA~1\Google\Chrome\APPLIC~1\chrome.exe" --type=utility --field-trial-handle=980,350635825690401994,6632272437260086580,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --service-request-channel-token=10517998790332361995 --mojo-platform-channel-handle=4588 --ignored=" --type=renderer " /prefetch:8 | C:\PROGRA~1\Google\Chrome\APPLIC~1\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 1156 | "C:\PROGRA~1\Google\Chrome\APPLIC~1\chrome.exe" --type=utility --field-trial-handle=980,350635825690401994,6632272437260086580,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --service-request-channel-token=17667901783833409361 --mojo-platform-channel-handle=4508 --ignored=" --type=renderer " /prefetch:8 | C:\PROGRA~1\Google\Chrome\APPLIC~1\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 1348 | "C:\PROGRA~1\Google\Chrome\APPLIC~1\chrome.exe" --type=utility --field-trial-handle=980,350635825690401994,6632272437260086580,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --service-request-channel-token=2597586867368871759 --mojo-platform-channel-handle=4832 --ignored=" --type=renderer " /prefetch:8 | C:\PROGRA~1\Google\Chrome\APPLIC~1\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 1392 | "C:\PROGRA~1\Google\Chrome\APPLIC~1\chrome.exe" --type=utility --field-trial-handle=980,350635825690401994,6632272437260086580,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --service-request-channel-token=17459562068456163968 --mojo-platform-channel-handle=3632 --ignored=" --type=renderer " /prefetch:8 | C:\PROGRA~1\Google\Chrome\APPLIC~1\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 1444 | "C:\PROGRA~1\Google\Chrome\APPLIC~1\chrome.exe" --type=utility --field-trial-handle=980,350635825690401994,6632272437260086580,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --service-request-channel-token=2443516270010675808 --mojo-platform-channel-handle=3584 --ignored=" --type=renderer " /prefetch:8 | C:\PROGRA~1\Google\Chrome\APPLIC~1\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
Total events
6 342
Read events
4 976
Write events
1 361
Delete events
5
Modification events
| (PID) Process: | (3284) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (3284) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (3284) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\12B\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3284) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\IPTV Editor Zaman Tantruttv 2020.zip | |||
| (PID) Process: | (3284) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3284) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3284) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (3284) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (3284) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (3284) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
Executable files
67
Suspicious files
50
Text files
342
Unknown types
8
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1724 | IPTV_Zaman_NOW.exe | C:\Users\admin\AppData\Local\Temp\nsiA765.tmp | — | |
MD5:— | SHA256:— | |||
| 3220 | Svchost.exe | C:\Users\admin\AppData\Local\Temp\autB0DA.tmp | — | |
MD5:— | SHA256:— | |||
| 3220 | Svchost.exe | C:\Users\admin\AppData\Local\Temp\asacpiex.dll | — | |
MD5:— | SHA256:— | |||
| 1724 | IPTV_Zaman_NOW.exe | C:\Users\admin\AppData\Roaming\Svchost.js | text | |
MD5:4DC8D7FF45200E9EE04EAE201F2E15FC | SHA256:CF1B5ED9C45E6FA14B6A27BCA9B5220912C683FD5373FF829AC4B191A716DD3E | |||
| 3932 | IPTV_Zaman_NOW.exe | C:\MSOCache\All Users\{90140000-003D-0000-0000-0000000FF1CE}-C\setup.exe | executable | |
MD5:566ED4F62FDC96F175AFEDD811FA0370 | SHA256:E17CD94C08FC0E001A49F43A0801CEA4625FB9AEE211B6DFEBEBEC446C21F460 | |||
| 3284 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3284.26509\IPTV Editor Zaman Tantruttv 2020\IPTV_Zaman_NOW.exe | executable | |
MD5:0D9E44521B0135384280B8551341B1A8 | SHA256:2C4E3395AE9B95B8EF906BC05530ED283C7AF00F4D54CD6D7E00735759F0EF49 | |||
| 3932 | IPTV_Zaman_NOW.exe | C:\MSOCache\All Users\{90140000-006E-0407-0000-0000000FF1CE}-C\dwtrig20.exe | executable | |
MD5:CF6C595D3E5E9667667AF096762FD9C4 | SHA256:593E60CC30AE0789448547195AF77F550387F6648D45847EA244DD0DD7ABF03D | |||
| 660 | WScript.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\Svchost.js | text | |
MD5:4DC8D7FF45200E9EE04EAE201F2E15FC | SHA256:CF1B5ED9C45E6FA14B6A27BCA9B5220912C683FD5373FF829AC4B191A716DD3E | |||
| 3220 | Svchost.exe | C:\Users\admin\AppData\Local\Temp\CR_Debug_Log.txt | — | |
MD5:— | SHA256:— | |||
| 1724 | IPTV_Zaman_NOW.exe | C:\Users\admin\AppData\Roaming\Svchost.exe | executable | |
MD5:9A2BAA5017D31548BA8BA8AE75E7B46E | SHA256:04F2B26AB1E4BD3F0B44739ED422D1128791E9FA57075868FB5620C5A80E80BF | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
99
TCP/UDP connections
140
DNS requests
45
Threats
30
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
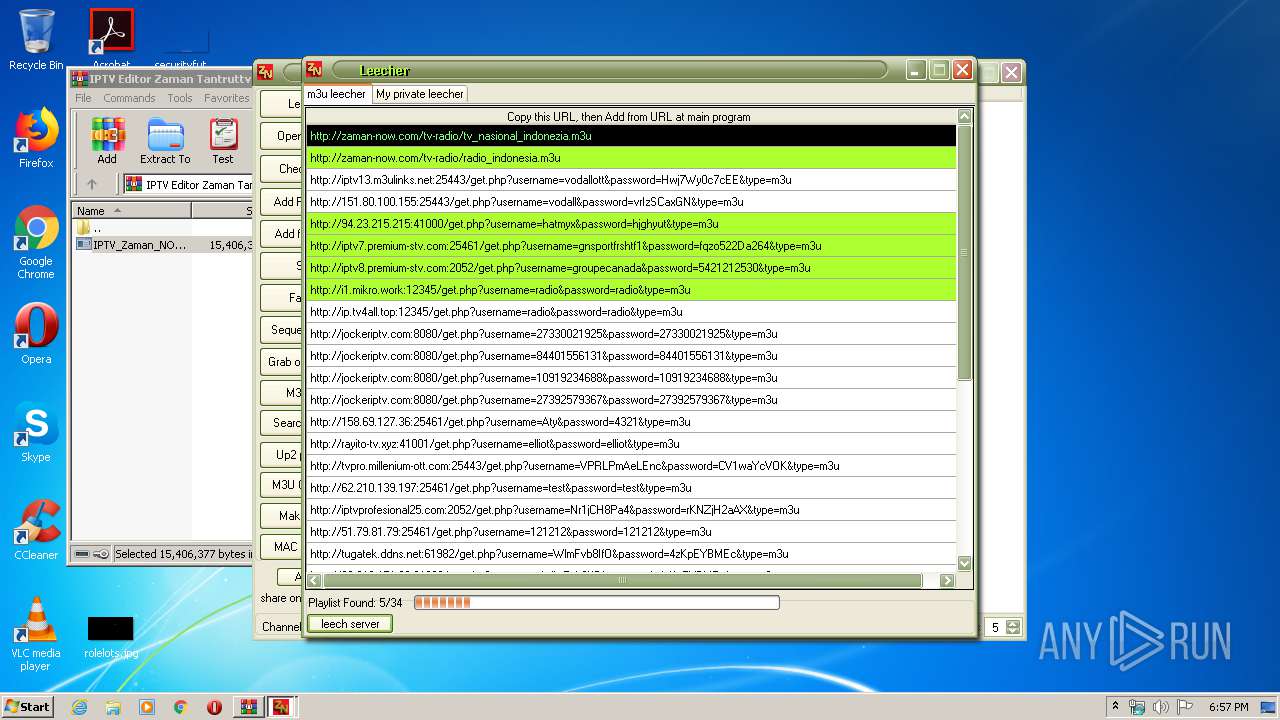
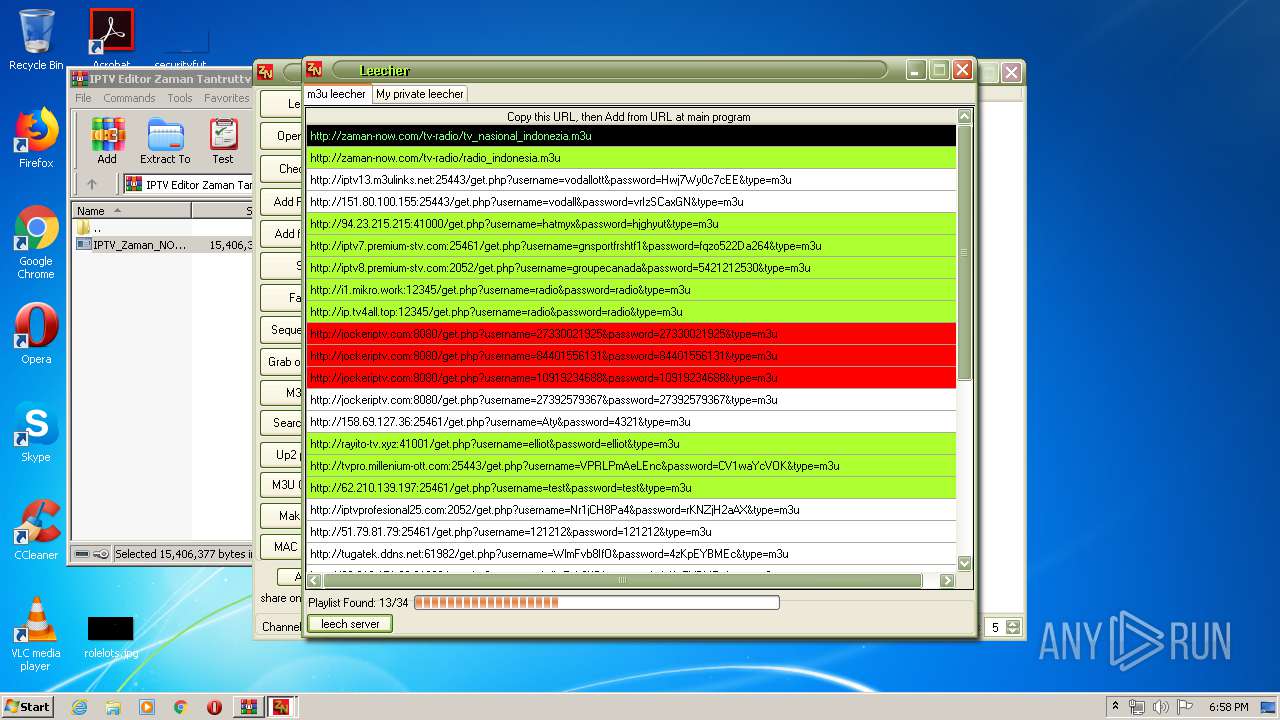
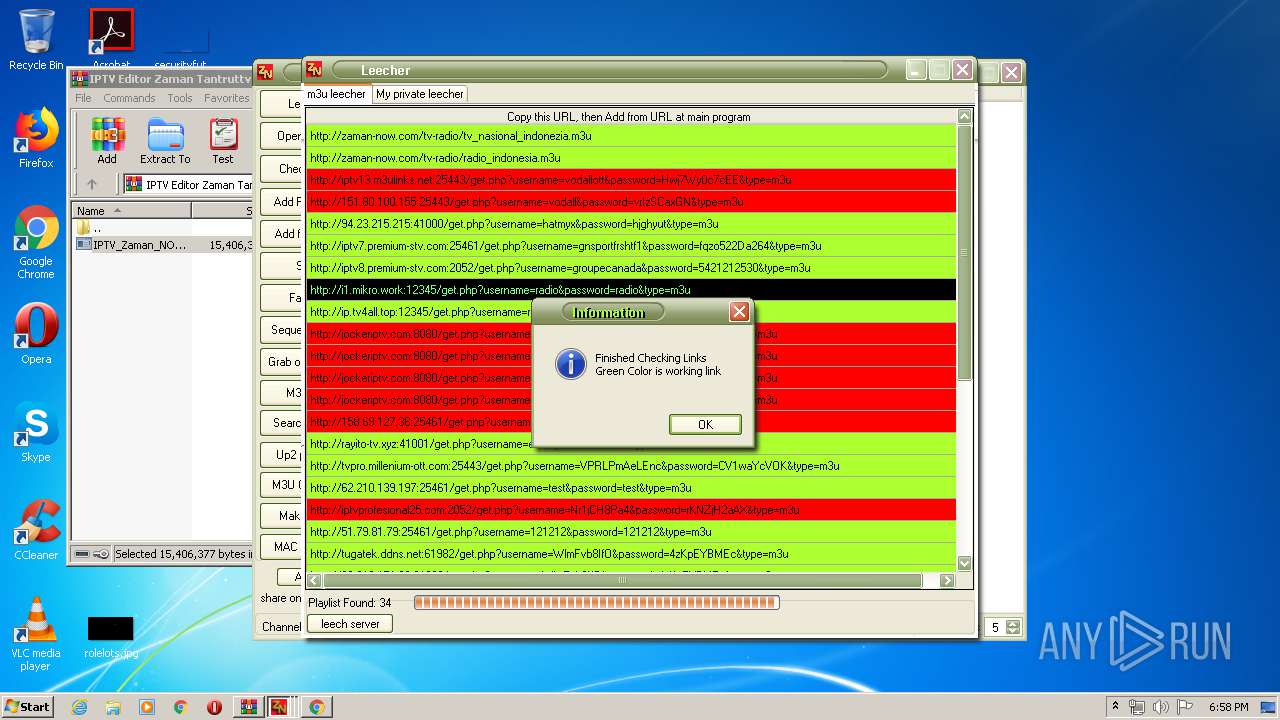
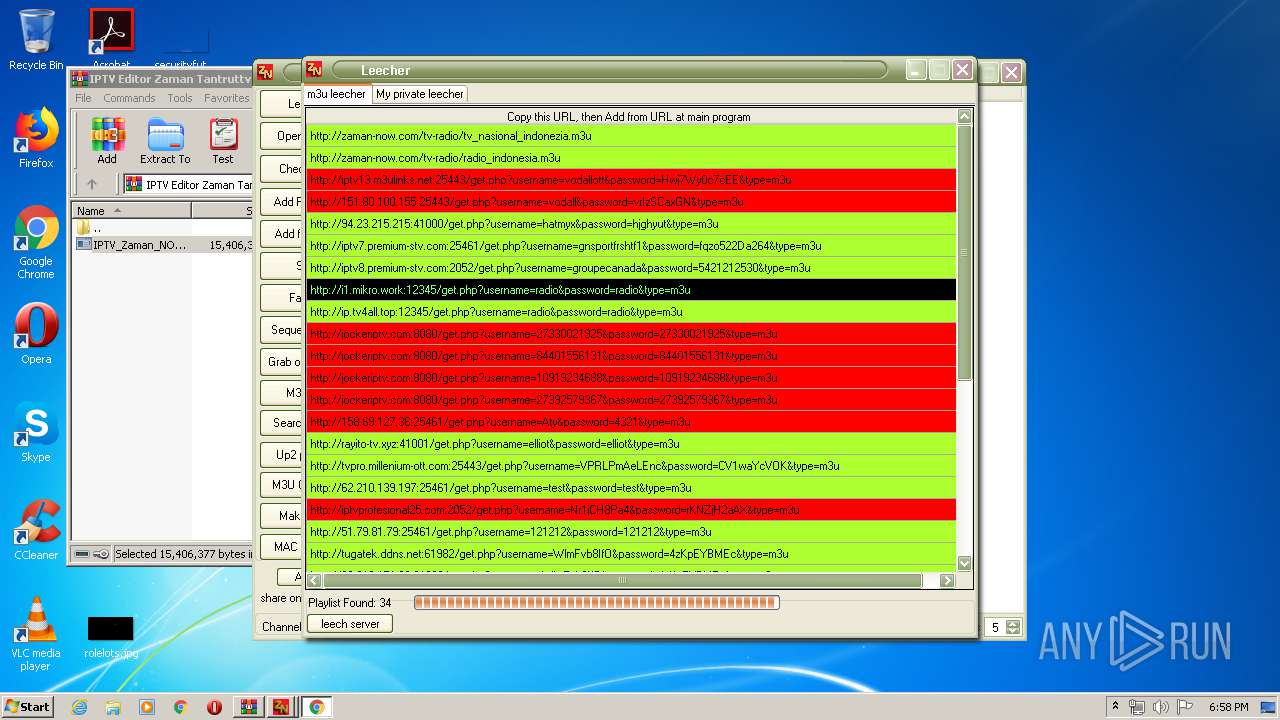
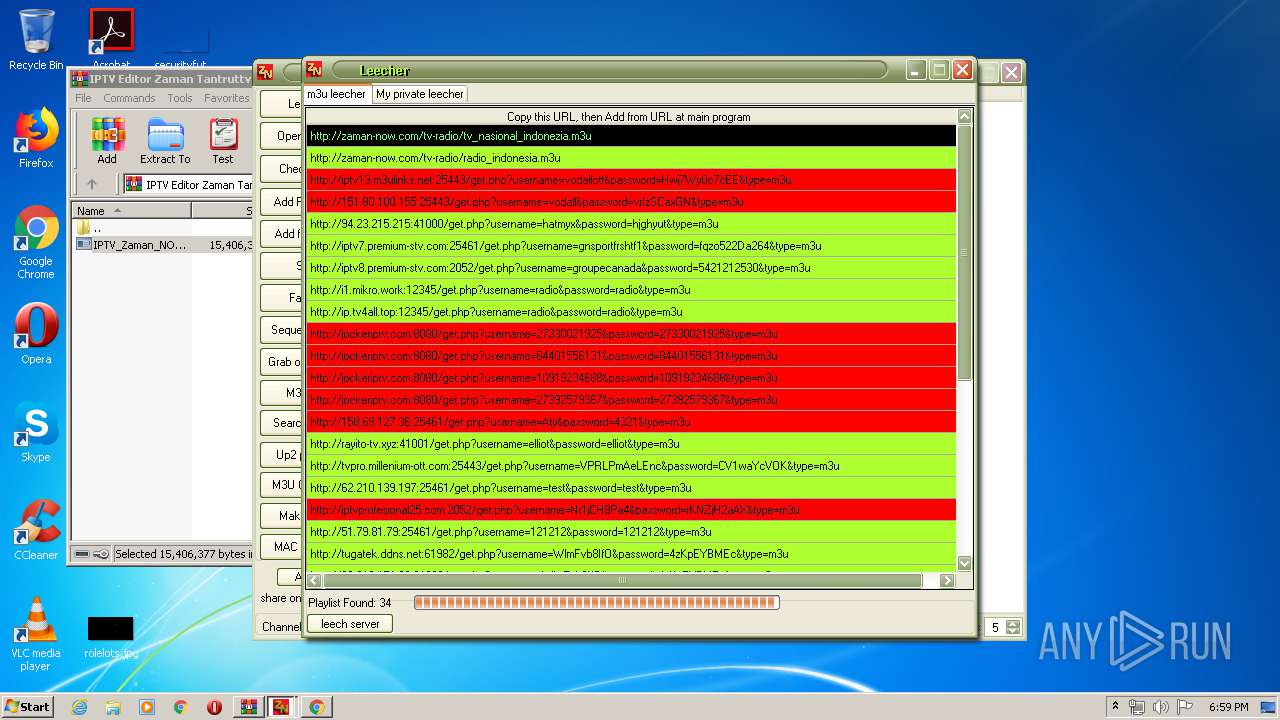
2792 | IPTV_Zaman_NOW.exe | GET | 302 | 103.29.214.171:80 | http://zaman-now.com/tv-radio/tv_nasional%EF%BB%BF_indonezia.m3u/ | ID | — | — | suspicious |
2792 | IPTV_Zaman_NOW.exe | GET | — | 144.76.71.228:12345 | http://ip.tv4all.top:12345/get.php?username=radio&password=radio&type=m3u | DE | — | — | suspicious |
2792 | IPTV_Zaman_NOW.exe | GET | — | 103.29.214.171:80 | http://zaman-now.com/tv-radio/tv_nasional%EF%BB%BF_indonezia7.m3u | ID | — | — | suspicious |
2792 | IPTV_Zaman_NOW.exe | GET | — | 63.250.32.224:8080 | http://jockeriptv.com:8080/get.php?username=84401556131&password=84401556131&type=m3u | US | — | — | unknown |
2792 | IPTV_Zaman_NOW.exe | GET | — | 63.250.32.224:8080 | http://jockeriptv.com:8080/get.php?username=10919234688&password=10919234688&type=m3u | US | — | — | unknown |
2792 | IPTV_Zaman_NOW.exe | GET | — | 63.250.32.224:8080 | http://jockeriptv.com:8080/get.php?username=27330021925&password=27330021925&type=m3u | US | — | — | unknown |
2792 | IPTV_Zaman_NOW.exe | GET | — | 63.250.32.224:8080 | http://jockeriptv.com:8080/get.php?username=84401556131&password=84401556131&type=m3u | US | — | — | unknown |
2792 | IPTV_Zaman_NOW.exe | GET | — | 63.250.32.224:8080 | http://jockeriptv.com:8080/get.php?username=27330021925&password=27330021925&type=m3u | US | — | — | unknown |
2792 | IPTV_Zaman_NOW.exe | GET | — | 63.250.32.224:8080 | http://jockeriptv.com:8080/get.php?username=10919234688&password=10919234688&type=m3u | US | — | — | unknown |
2792 | IPTV_Zaman_NOW.exe | GET | — | 63.250.32.224:8080 | http://jockeriptv.com:8080/get.php?username=27330021925&password=27330021925&type=m3u | US | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
660 | WScript.exe | 208.95.112.1:80 | ip-api.com | IBURST | — | malicious |
660 | WScript.exe | 81.61.77.92:8000 | — | Vodafone Ono, S.A. | ES | malicious |
2792 | IPTV_Zaman_NOW.exe | 103.29.214.171:80 | ez-tracker.net | Sentra Niaga Solusindo, PT. | ID | unknown |
2792 | IPTV_Zaman_NOW.exe | 151.80.100.155:25443 | iptv13.m3ulinks.net | OVH SAS | FR | unknown |
2792 | IPTV_Zaman_NOW.exe | 94.23.215.215:41000 | — | OVH SAS | FR | unknown |
2792 | IPTV_Zaman_NOW.exe | 185.23.215.146:25461 | iptv7.premium-stv.com | Global Layer B.V. | NL | unknown |
2792 | IPTV_Zaman_NOW.exe | 51.159.21.231:2052 | iptv8.premium-stv.com | — | GB | unknown |
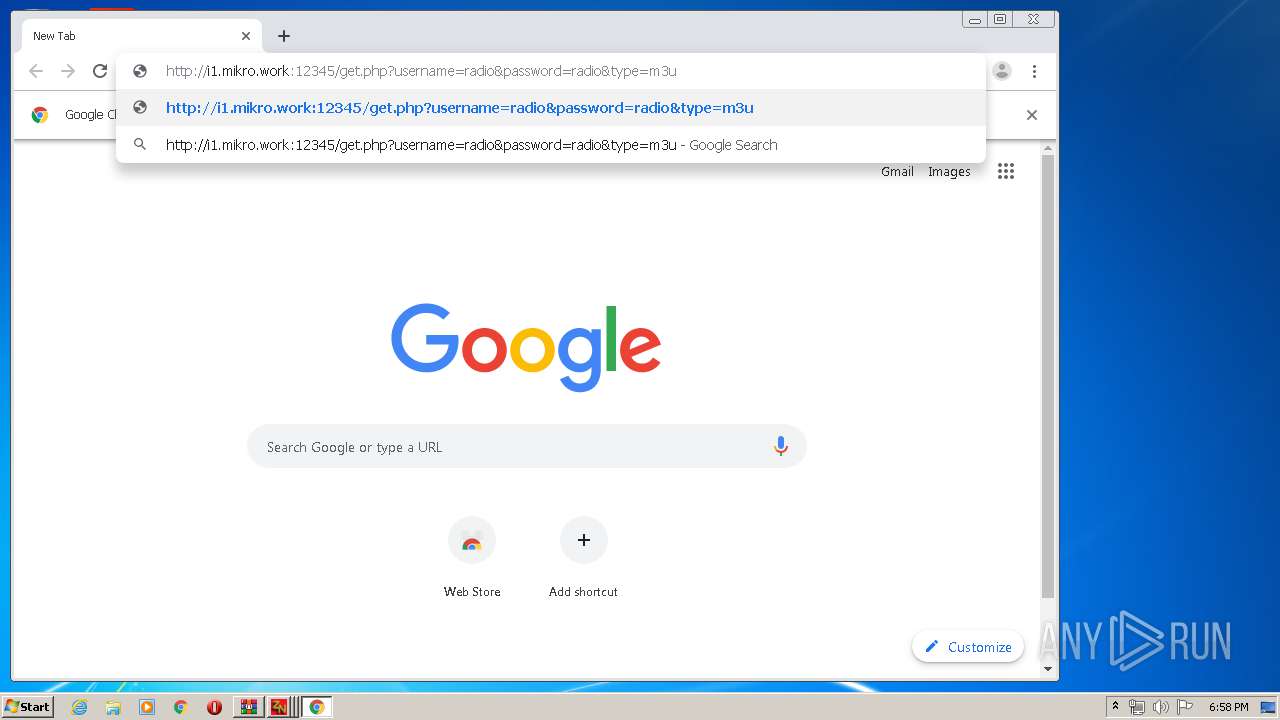
2792 | IPTV_Zaman_NOW.exe | 144.76.71.228:12345 | i1.mikro.work | Hetzner Online GmbH | DE | suspicious |
2792 | IPTV_Zaman_NOW.exe | 63.250.32.224:8080 | jockeriptv.com | Frontline Data Services, Inc | US | unknown |
— | — | 63.250.32.224:8080 | jockeriptv.com | Frontline Data Services, Inc | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
ip-api.com |
| malicious |
ez-tracker.net |
| suspicious |
zaman-now.com |
| unknown |
iptv13.m3ulinks.net |
| unknown |
iptv7.premium-stv.com |
| unknown |
iptv8.premium-stv.com |
| unknown |
i1.mikro.work |
| suspicious |
ip.tv4all.top |
| suspicious |
jockeriptv.com |
| unknown |
rayito-tv.xyz |
| unknown |
Threats
PID | Process | Class | Message |
|---|---|---|---|
660 | WScript.exe | Potential Corporate Privacy Violation | ET POLICY External IP Lookup ip-api.com |
660 | WScript.exe | Potential Corporate Privacy Violation | AV POLICY Internal Host Retrieving External IP Address (ip-api. com) |
1052 | svchost.exe | Potentially Bad Traffic | ET INFO Observed DNS Query to .work TLD |
2792 | IPTV_Zaman_NOW.exe | Potentially Bad Traffic | ET INFO HTTP Request to Suspicious *.work Domain |
1052 | svchost.exe | Potentially Bad Traffic | ET DNS Query to a *.top domain - Likely Hostile |
2792 | IPTV_Zaman_NOW.exe | Potentially Bad Traffic | ET INFO HTTP Request to a *.top domain |
2792 | IPTV_Zaman_NOW.exe | Potentially Bad Traffic | AV INFO HTTP Request to a *.xyz domain |
3768 | tor.exe | Misc Attack | ET TOR Known Tor Relay/Router (Not Exit) Node Traffic group 229 |
1052 | svchost.exe | Potentially Bad Traffic | ET POLICY DNS Query to DynDNS Domain *.ddns .net |
3768 | tor.exe | Potential Corporate Privacy Violation | POLICY [PTsecurity] TOR SSL connection |
Process | Message |
|---|---|
vlc.exe | core libvlc: one instance mode ENABLED
|
vlc.exe | core libvlc: Running vlc with the default interface. Use 'cvlc' to use vlc without interface.
|
vlc.exe | core playlist: stopping playback
|
vlc.exe | ts demux: MPEG-4 descriptor not found for pid 0x100 type 0xf
|
vlc.exe | packetizer_mpeg4audio packetizer: AAC channels: 2 samplerate: 22050
|