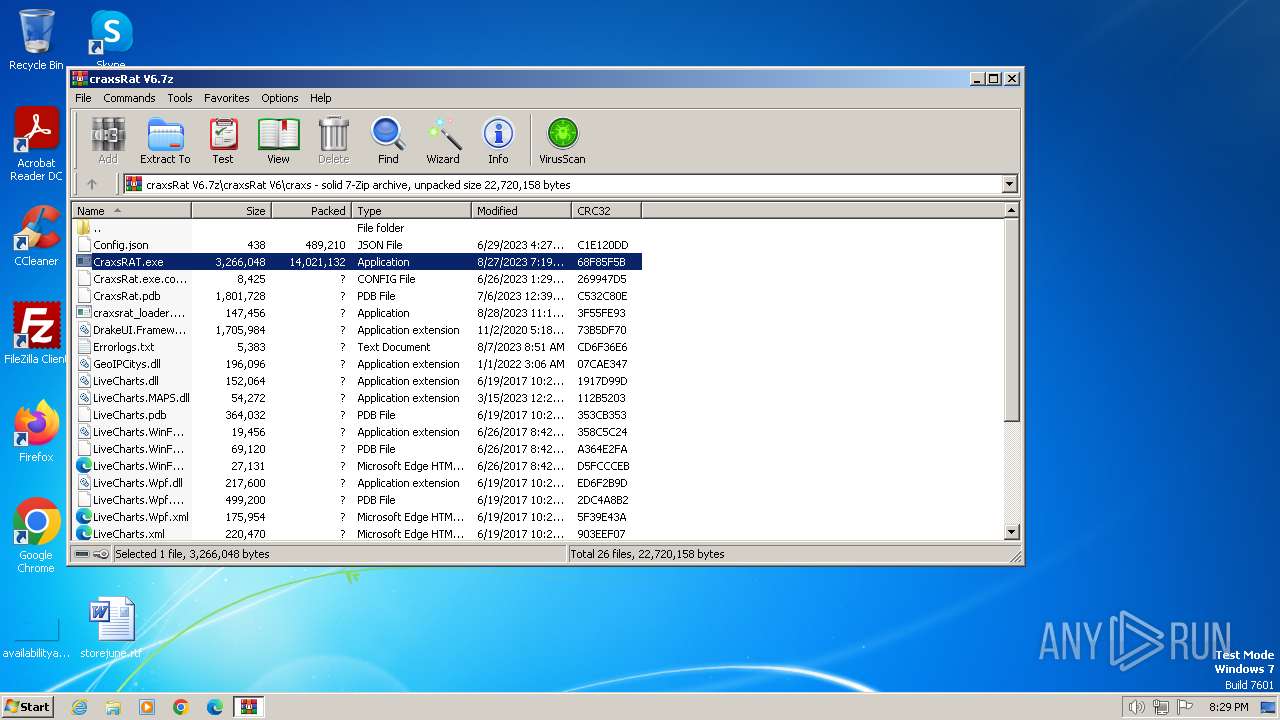
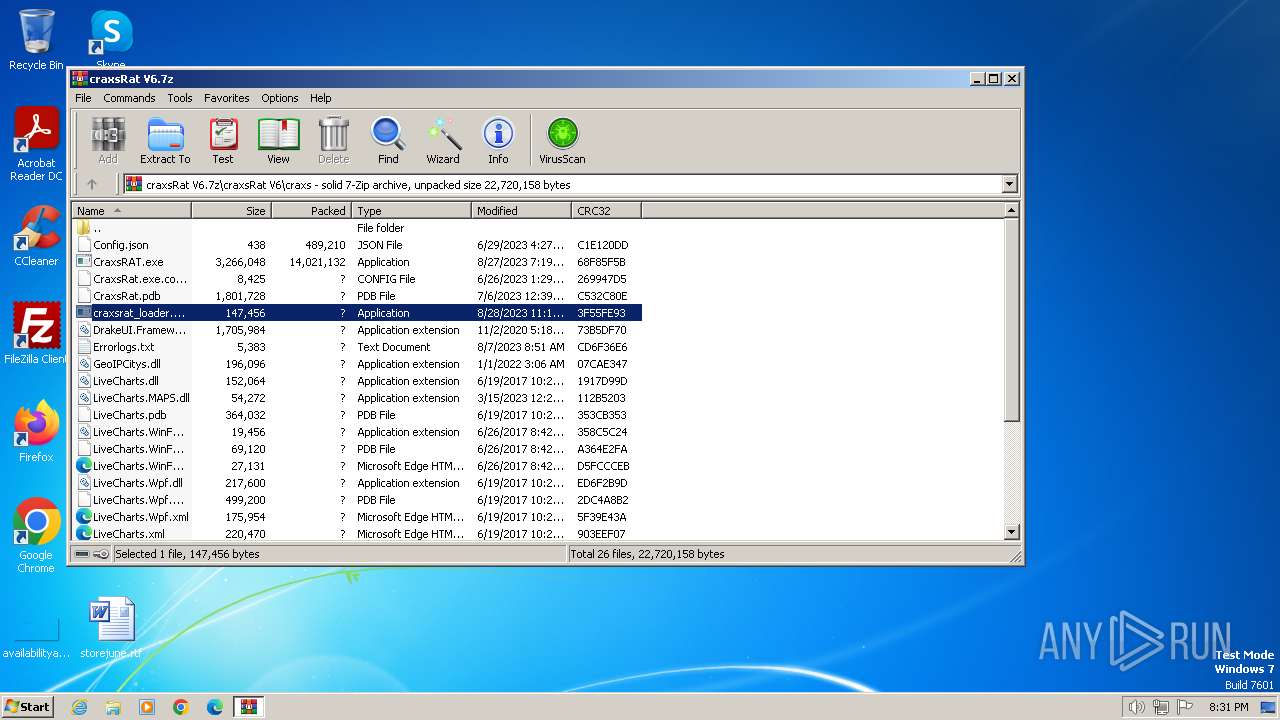
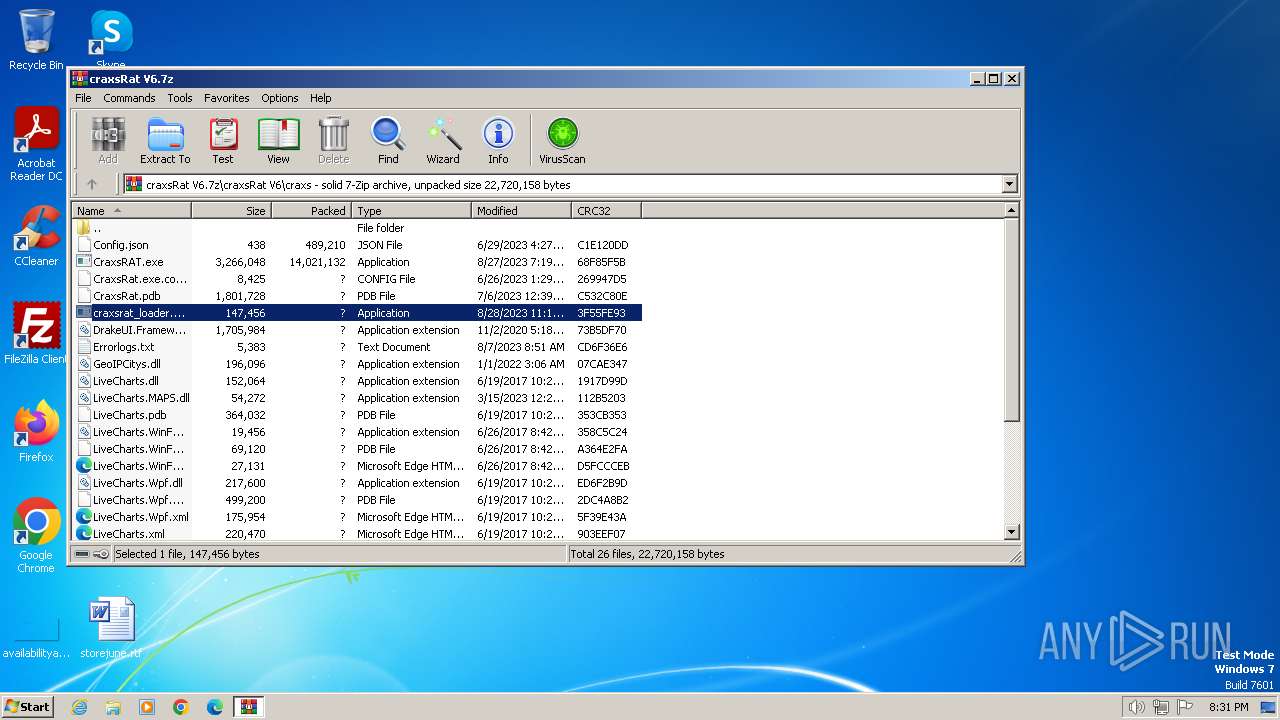
| File name: | craxsRat V6.7z |
| Full analysis: | https://app.any.run/tasks/92d6437a-0894-43b8-86cc-f1fd326f0e67 |
| Verdict: | Malicious activity |
| Threats: | Quasar is a very popular RAT in the world thanks to its code being available in open-source. This malware can be used to control the victim’s computer remotely. |
| Analysis date: | January 20, 2024, 20:29:11 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-7z-compressed |
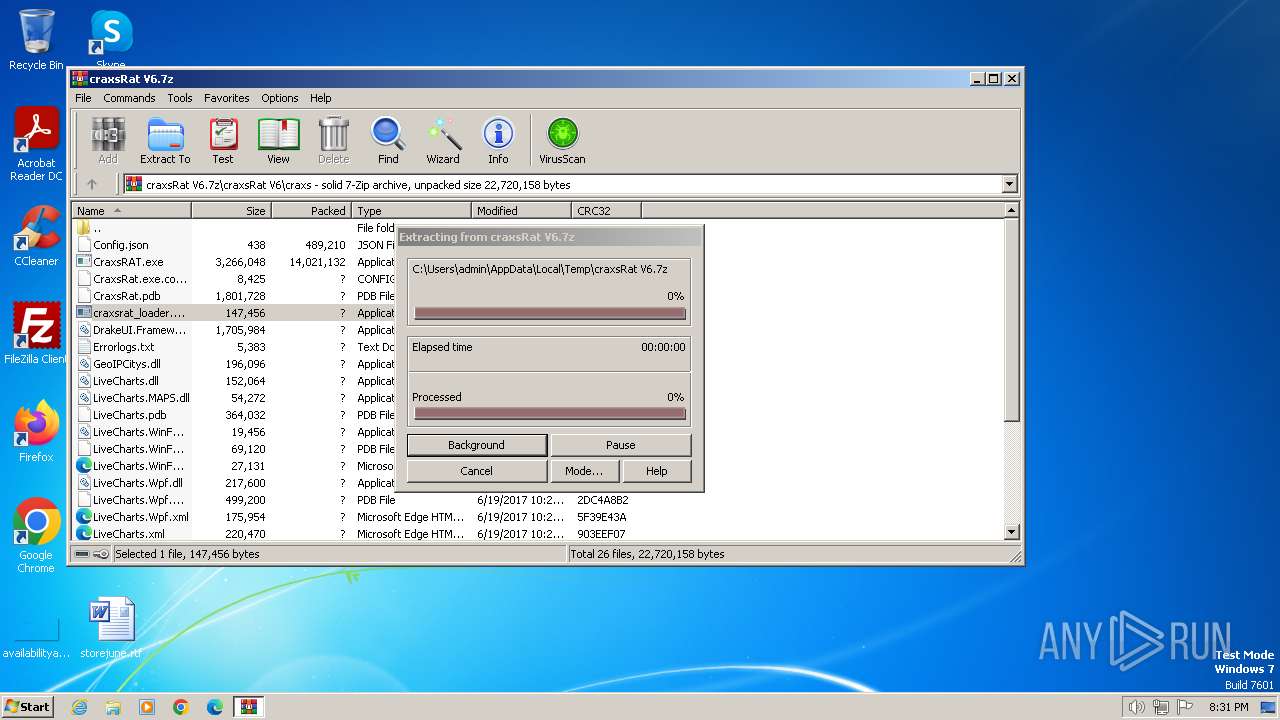
| File info: | 7-zip archive data, version 0.4 |
| MD5: | CC85AC83575E10053C1F5B14A7728E44 |
| SHA1: | 9172361508DE14B578D84F42C1FCB399123D27B0 |
| SHA256: | 9ED635587BCE97B3DD2DEC67AA1950853F72741B00682F284826932B9873E3B2 |
| SSDEEP: | 98304:uFaN86wHKWROj5binfzlhhdHwe8r6t6DJDIYFOjwFRhAMJ7gGal53PyaWsbFIeco:KmkVwQOn+glTDCaoxHsg |
MALICIOUS
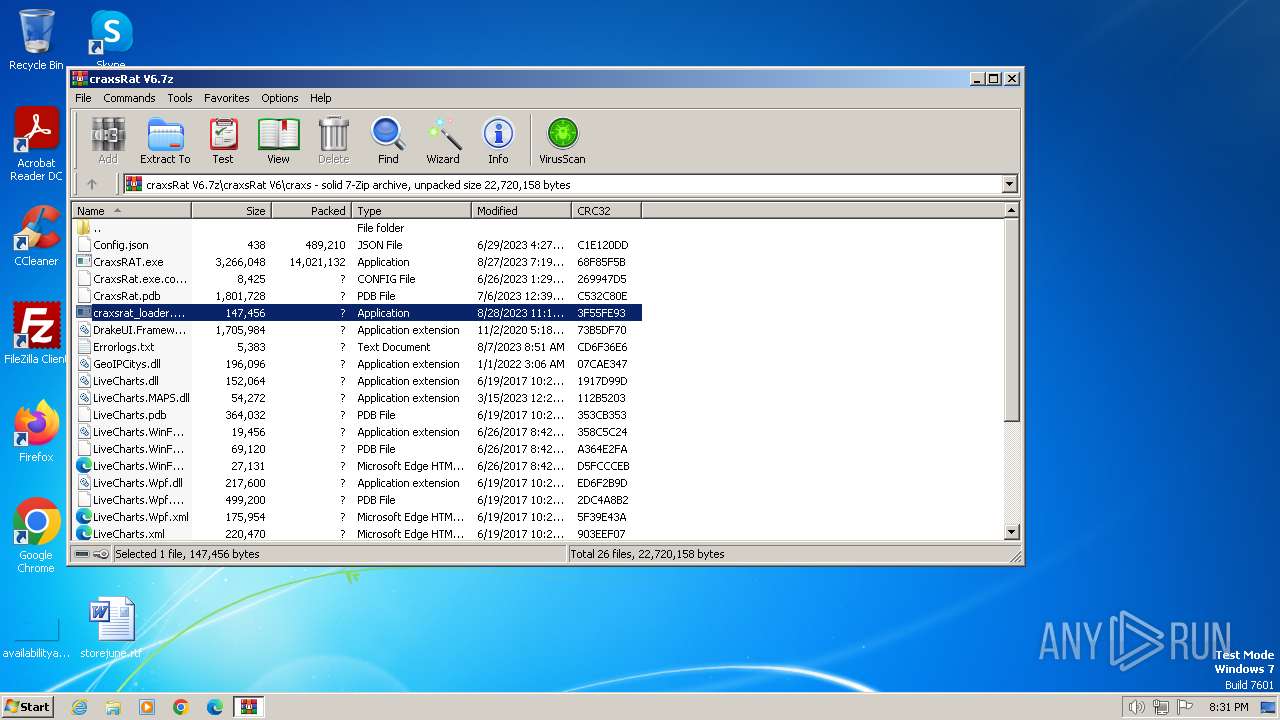
Drops the executable file immediately after the start
- WinRAR.exe (PID: 2184)
- CraxsRAT.exe (PID: 296)
Changes the autorun value in the registry
- Client.exe (PID: 2076)
QUASAR has been detected (YARA)
- Client.exe (PID: 2076)
REDLINE has been detected (YARA)
- craxsrat_loader.exe (PID: 668)
- craxsrat_loader.exe (PID: 2480)
SUSPICIOUS
Process drops legitimate windows executable
- WinRAR.exe (PID: 2184)
Executable content was dropped or overwritten
- CraxsRAT.exe (PID: 296)
Starts itself from another location
- CraxsRAT.exe (PID: 296)
Connects to unusual port
- Client.exe (PID: 2076)
- craxsrat_loader.exe (PID: 668)
- craxsrat_loader.exe (PID: 2480)
INFO
Checks supported languages
- CraxsRAT.exe (PID: 296)
- Client.exe (PID: 2076)
- craxsrat_loader.exe (PID: 668)
- CraxsRAT.exe (PID: 2444)
- craxsrat_loader.exe (PID: 2480)
Reads the computer name
- CraxsRAT.exe (PID: 296)
- Client.exe (PID: 2076)
- craxsrat_loader.exe (PID: 668)
- craxsrat_loader.exe (PID: 2480)
- CraxsRAT.exe (PID: 2444)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 2184)
Reads the machine GUID from the registry
- CraxsRAT.exe (PID: 296)
- Client.exe (PID: 2076)
- craxsrat_loader.exe (PID: 2480)
- CraxsRAT.exe (PID: 2444)
- craxsrat_loader.exe (PID: 668)
Reads Environment values
- CraxsRAT.exe (PID: 296)
- Client.exe (PID: 2076)
- CraxsRAT.exe (PID: 2444)
Creates files or folders in the user directory
- CraxsRAT.exe (PID: 296)
- Client.exe (PID: 2076)
Manual execution by a user
- craxsrat_loader.exe (PID: 2480)
- CraxsRAT.exe (PID: 2444)
- taskmgr.exe (PID: 2584)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Quasar
(PID) Process(2076) Client.exe
Version1.4.1
C2 (4)109.123.239.168:4782
45.92.1.39:4782
192.227.190.146:4782
Sub_DirGoogle Extensions
Install_NameClient.exe
Mutex10726cc3-bb08-45ab-bcfa-a1a801fe7c81
Startupmsdrvhost
TagMETRO
LogDirLogs
SignatureHAxXbimAGnaTkfgoebpxWbg+rHb9waAPcK75aNCAeHrKINdrbHOVWdMYYcnnVrVPRBgdzMwUIcFnCpoUgWeykEmJaBkX26ad9i6VhFVsAdjR8ctFLSbrSrqLKU5Laki2VZjp2AhKLca3ZRxKP47Z4AknN16f3ViOxa48A8DiGWN4goWf2lx3o7/sE/O36lnrkt63kw/kgiDTdNYhXDJh7wpETBtrgsTZuRPbMzdpCtar4FTg6y1wDxTpGTz8+d87EtHQ7mYGYHqzryJ+mfDxuL/gQlVY22W8sEKlVLJI+Qq/...
CertificateMIIE9DCCAtygAwIBAgIQAJXwinK/ak+poCze5rYYvzANBgkqhkiG9w0BAQ0FADAbMRkwFwYDVQQDDBBRdWFzYXIgU2VydmVyIENBMCAXDTIzMDgyNTE4MTUxMloYDzk5OTkxMjMxMjM1OTU5WjAbMRkwFwYDVQQDDBBRdWFzYXIgU2VydmVyIENBMIICIjANBgkqhkiG9w0BAQEFAAOCAg8AMIICCgKCAgEAjdOD746SUknaqDyFaiaG/ruicBZF669xHbCQ62NRm12SA56yGSzuqI62D04PyXXNZJCQ6Own...
TRiD
| .7z | | | 7-Zip compressed archive (v0.4) (57.1) |
|---|---|---|
| .7z | | | 7-Zip compressed archive (gen) (42.8) |
Total processes
43
Monitored processes
7
Malicious processes
5
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 296 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa2184.7175\craxsRat V6\craxs\CraxsRAT.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa2184.7175\craxsRat V6\craxs\CraxsRAT.exe | WinRAR.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Description: Quasar Client Exit code: 3 Version: 1.4.1 Modules
| |||||||||||||||
| 668 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa2184.9042\craxsRat V6\craxs\craxsrat_loader.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa2184.9042\craxsRat V6\craxs\craxsrat_loader.exe | WinRAR.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Description: Nirtro CPU Exit code: 0 Version: 15.9.1.22 Modules
| |||||||||||||||
| 2076 | "C:\Users\admin\AppData\Roaming\Google Extensions\Client.exe" | C:\Users\admin\AppData\Roaming\Google Extensions\Client.exe | CraxsRAT.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Description: Quasar Client Exit code: 0 Version: 1.4.1 Modules
Quasar(PID) Process(2076) Client.exe Version1.4.1 C2 (4)109.123.239.168:4782 45.92.1.39:4782 192.227.190.146:4782 Sub_DirGoogle Extensions Install_NameClient.exe Mutex10726cc3-bb08-45ab-bcfa-a1a801fe7c81 Startupmsdrvhost TagMETRO LogDirLogs SignatureHAxXbimAGnaTkfgoebpxWbg+rHb9waAPcK75aNCAeHrKINdrbHOVWdMYYcnnVrVPRBgdzMwUIcFnCpoUgWeykEmJaBkX26ad9i6VhFVsAdjR8ctFLSbrSrqLKU5Laki2VZjp2AhKLca3ZRxKP47Z4AknN16f3ViOxa48A8DiGWN4goWf2lx3o7/sE/O36lnrkt63kw/kgiDTdNYhXDJh7wpETBtrgsTZuRPbMzdpCtar4FTg6y1wDxTpGTz8+d87EtHQ7mYGYHqzryJ+mfDxuL/gQlVY22W8sEKlVLJI+Qq/... CertificateMIIE9DCCAtygAwIBAgIQAJXwinK/ak+poCze5rYYvzANBgkqhkiG9w0BAQ0FADAbMRkwFwYDVQQDDBBRdWFzYXIgU2VydmVyIENBMCAXDTIzMDgyNTE4MTUxMloYDzk5OTkxMjMxMjM1OTU5WjAbMRkwFwYDVQQDDBBRdWFzYXIgU2VydmVyIENBMIICIjANBgkqhkiG9w0BAQEFAAOCAg8AMIICCgKCAgEAjdOD746SUknaqDyFaiaG/ruicBZF669xHbCQ62NRm12SA56yGSzuqI62D04PyXXNZJCQ6Own... | |||||||||||||||
| 2184 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\craxsRat V6.7z" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 2444 | "C:\Users\admin\Desktop\CraxsRAT.exe" | C:\Users\admin\Desktop\CraxsRAT.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: Quasar Client Exit code: 2 Version: 1.4.1 Modules
| |||||||||||||||
| 2480 | "C:\Users\admin\Desktop\craxsrat_loader.exe" | C:\Users\admin\Desktop\craxsrat_loader.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Description: Nirtro CPU Exit code: 0 Version: 15.9.1.22 Modules
| |||||||||||||||
| 2584 | "C:\Windows\system32\taskmgr.exe" /4 | C:\Windows\System32\taskmgr.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Task Manager Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
3 927
Read events
3 860
Write events
67
Delete events
0
Modification events
| (PID) Process: | (2184) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2184) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\virtio_ivshmem_master_build.zip | |||
| (PID) Process: | (2184) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\phacker.zip | |||
| (PID) Process: | (2184) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (2184) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\curl-8.5.0_1-win32-mingw.zip | |||
| (PID) Process: | (2184) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (2184) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (2184) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (2184) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (2184) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
Executable files
30
Suspicious files
11
Text files
16
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2184 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa2184.7175\craxsRat V6\craxs\Config.json | text | |
MD5:EE3FC1A27DF0F05DF3BC938818B42F50 | SHA256:DF5E911E4EAF909E7BD6B89F7B9B679C9D928AEE34416B06E34BB7420B9D890D | |||
| 2184 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa2184.7175\craxsRat V6\craxs\Questions.url | url | |
MD5:388067B9547E513004768F0D37E6BA2D | SHA256:AE3D37A27CADBF1132178C01032E61818922CF331ABF00051F20E5B36BE10571 | |||
| 2184 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa2184.7175\craxsRat V6\craxs\LiveCharts.Wpf.pdb | pdb | |
MD5:F209A4302B929A36DD534DC48DFDC617 | SHA256:718FF471C7CCFA31E9CF905DFA01C9925D692835EA646E95754FD801A5EE4CA8 | |||
| 2184 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa2184.7175\craxsRat V6\craxs\LiveCharts.Wpf.xml | xml | |
MD5:9CBC27F6B1AFBC7F43A9ED07F784A73D | SHA256:C18A11B019A56EC8E5916042A9F23A8655EA199BF2A4319573B18B7E035E3914 | |||
| 2184 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa2184.7175\craxsRat V6\craxs\CraxsRat.exe.config | xml | |
MD5:7AE229700EFC323E33897AD95588BF2D | SHA256:DB3E864A56DEA1C786CBF5DD9CD73524259EF4CE442B27F86D6EC9F7AF581593 | |||
| 2184 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa2184.7175\craxsRat V6\craxs\LiveCharts.WinForms.pdb | pdb | |
MD5:75AC1D35A79DB3ED5810097BACD498FF | SHA256:26021AA51EAB1B7E82EFC702EF39DC6180F144415BC0A14CCACE060DAD555C77 | |||
| 2184 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa2184.7175\craxsRat V6\craxs\LiveCharts.xml | xml | |
MD5:5BE563DCD4B0F60D71384CB31D44AAE7 | SHA256:CE3283E4AFD74377D313F9C1D247AFE8164E626C95F710F928734DA6CFAB9311 | |||
| 2184 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa2184.7175\craxsRat V6\craxs\Errorlogs.txt | text | |
MD5:842CD9110FD7AC5F8FFD0403A21B2766 | SHA256:9ECAB9EEFA25DD6FA375C9940048D221029D6D532250A739DF4360400A1714CC | |||
| 2184 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa2184.7175\craxsRat V6\craxs\CraxsRat.pdb | binary | |
MD5:FE9C49EE1DF13E83BDF379D820051A8F | SHA256:D8D7BEE5AE32CBB45CD5497A465E2AD722B5E0D67D28D4505CFC5F7CE9094E2B | |||
| 2184 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa2184.7175\craxsRat V6\craxs\World.xml | xml | |
MD5:28A1E2B477EBE7DE49DF597A4117C28E | SHA256:CBD20C5CCC5B11718B782547BB5B818FE368168C1794B2254FED7333959757DA | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
72
DNS requests
1
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
2076 | Client.exe | 109.123.239.168:4782 | — | CASABLANCA INT a.s. | CZ | unknown |
2076 | Client.exe | 45.92.1.39:4782 | — | 1337 Services GmbH | BR | unknown |
668 | craxsrat_loader.exe | 45.92.1.32:20580 | — | 1337 Services GmbH | BR | malicious |
2076 | Client.exe | 192.227.190.146:4782 | — | AS-COLOCROSSING | US | unknown |
2480 | craxsrat_loader.exe | 45.92.1.32:20580 | — | 1337 Services GmbH | BR | malicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
dns.msftncsi.com |
| shared |