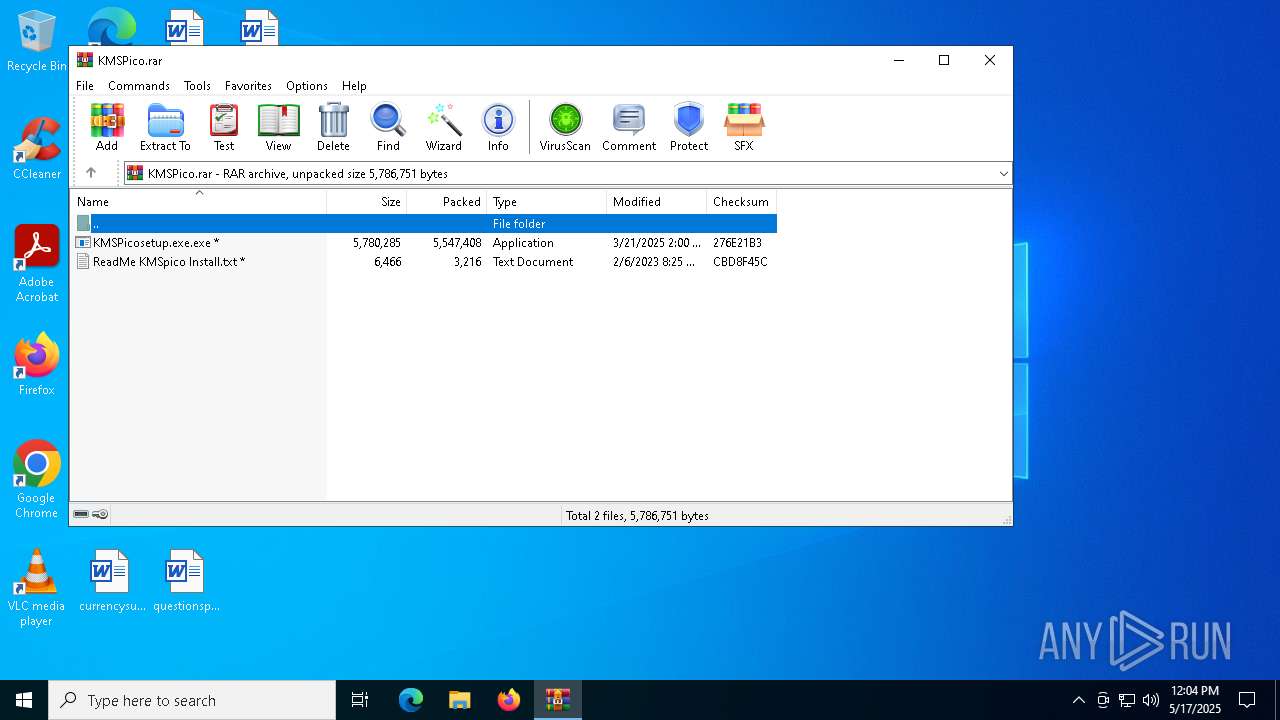
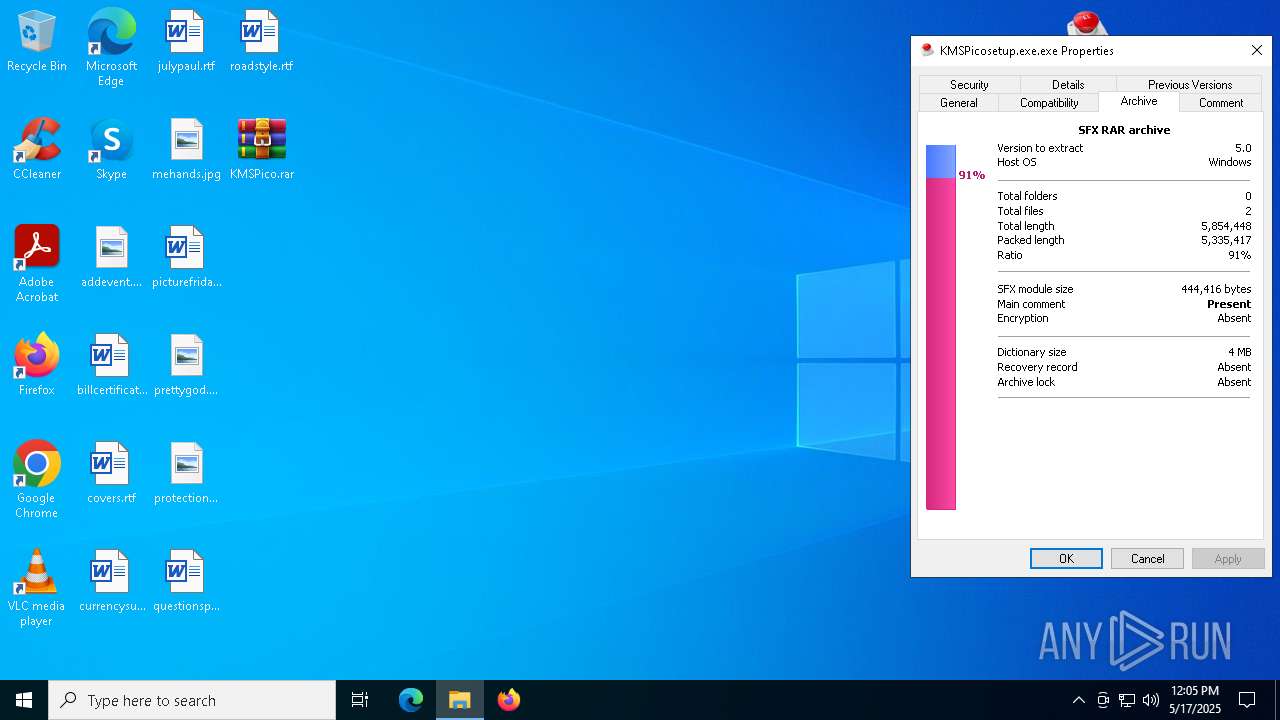
| File name: | KMSPico.rar |
| Full analysis: | https://app.any.run/tasks/2dafd440-1ae8-4262-877a-a096111db378 |
| Verdict: | Malicious activity |
| Threats: | Crypto mining malware is a resource-intensive threat that infiltrates computers with the purpose of mining cryptocurrencies. This type of threat can be deployed either on an infected machine or a compromised website. In both cases the miner will utilize the computing power of the device and its network bandwidth. |
| Analysis date: | May 17, 2025, 12:04:20 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v5 |
| MD5: | FEFF362B4F626D9D744ABEF7AAE11A4B |
| SHA1: | BAAD3957A9271347AAC0DF4C3B07B3628878B06E |
| SHA256: | 9E91922CC588EBFA9AE0BF7B28F0FDC27D4584A8E744E3EA366E6E2A6DB8C7F6 |
| SSDEEP: | 98304:CQ86L2JjkxyZXX5RTsk83tXk+yVmhQ80xAzWpkCEZjqklCGmzB0Xgq2qS0SE4AhD:+4qfWP3F |
MALICIOUS
GENERIC has been found (auto)
- WinRAR.exe (PID: 6676)
- KMSPicosetup.exe.exe (PID: 1164)
- KMSPicosetup.exe.exe (PID: 6036)
- KMSPicosetup.exe.exe (PID: 3828)
- KMSPicosetup.exe.exe (PID: 4172)
- KMSPicosetup.exe.exe (PID: 6132)
- KMSPicosetup.exe.exe (PID: 684)
- KMSPicosetup.exe.exe (PID: 1852)
- KMSPicosetup.exe.exe (PID: 680)
- KMSPicosetup.exe.exe (PID: 3016)
- KMSPicosetup.exe.exe (PID: 7280)
- KMSPicosetup.exe.exe (PID: 7832)
- KMSPicosetup.exe.exe (PID: 7820)
- KMSPicosetup.exe.exe (PID: 7560)
Executing a file with an untrusted certificate
- KMSpicosetup.exe (PID: 2908)
- KMSpicosetup.exe (PID: 6660)
- KMSELDI.exe (PID: 7012)
- AutoPico.exe (PID: 7100)
- KMSpicosetup.exe (PID: 4736)
- KMSpicosetup.exe (PID: 4068)
- KMSpicosetup.exe (PID: 1660)
- KMSpicosetup.exe (PID: 7384)
- KMSpicosetup.exe (PID: 6652)
- KMSpicosetup.exe (PID: 7712)
- KMSpicosetup.exe (PID: 8092)
- KMSpicosetup.exe (PID: 8140)
- KMSpicosetup.exe (PID: 8008)
- KMSpicosetup.exe (PID: 7980)
- KMSpicosetup.exe (PID: 8200)
- KMSpicosetup.exe (PID: 8324)
- KMSpicosetup.exe (PID: 8368)
- KMSpicosetup.exe (PID: 8428)
- KMSpicosetup.exe (PID: 8620)
- KMSpicosetup.exe (PID: 7932)
- KMSpicosetup.exe (PID: 8380)
- KMSpicosetup.exe (PID: 8956)
- KMSpicosetup.exe (PID: 8884)
- KMSpicosetup.exe (PID: 8948)
Vulnerable driver has been detected
- Registryhost.exe (PID: 6988)
- Registryhost.exe (PID: 6652)
MINER has been detected (SURICATA)
- svchost.exe (PID: 2196)
- conhost.exe (PID: 6852)
Connects to the CnC server
- conhost.exe (PID: 6852)
Uses Task Scheduler to run other applications
- cmd.exe (PID: 6940)
Changes image file execution options
- KMSELDI.exe (PID: 7012)
SUSPICIOUS
The process creates files with name similar to system file names
- WinRAR.exe (PID: 6676)
- KMSPicosetup.exe.exe (PID: 1164)
- RegistryHost.exe (PID: 1616)
Executable content was dropped or overwritten
- KMSPicosetup.exe.exe (PID: 1164)
- KMSpicosetup.exe (PID: 2908)
- KMSpicosetup.tmp (PID: 5600)
- KMSpicosetup.exe (PID: 6660)
- RegistryHost.exe (PID: 1616)
- Registryhost.exe (PID: 6988)
- KMSELDI.exe (PID: 7012)
- RegistryHost.exe (PID: 1764)
- Registryhost.exe (PID: 6652)
- KMSPicosetup.exe.exe (PID: 6036)
- KMSPicosetup.exe.exe (PID: 3828)
- KMSpicosetup.exe (PID: 4068)
- KMSPicosetup.exe.exe (PID: 6132)
- KMSpicosetup.exe (PID: 1660)
- KMSpicosetup.exe (PID: 4736)
- KMSPicosetup.exe.exe (PID: 4172)
- KMSPicosetup.exe.exe (PID: 1852)
- KMSPicosetup.exe.exe (PID: 680)
- KMSPicosetup.exe.exe (PID: 3016)
- KMSPicosetup.exe.exe (PID: 684)
- KMSpicosetup.exe (PID: 6652)
- KMSpicosetup.exe (PID: 7384)
- KMSpicosetup.exe (PID: 7712)
- KMSPicosetup.exe.exe (PID: 7280)
- KMSPicosetup.exe.exe (PID: 7832)
- KMSpicosetup.exe (PID: 8092)
- KMSpicosetup.exe (PID: 8140)
- KMSPicosetup.exe.exe (PID: 7820)
- KMSpicosetup.exe (PID: 7980)
- KMSpicosetup.exe (PID: 8008)
- KMSPicosetup.exe.exe (PID: 7560)
- KMSpicosetup.exe (PID: 8200)
- KMSpicosetup.exe (PID: 8428)
- KMSpicosetup.tmp (PID: 7012)
- KMSpicosetup.exe (PID: 7932)
- KMSpicosetup.exe (PID: 8380)
- KMSpicosetup.exe (PID: 8324)
- KMSpicosetup.tmp (PID: 8212)
- KMSpicosetup.exe (PID: 8368)
- KMSpicosetup.tmp (PID: 8656)
- KMSpicosetup.exe (PID: 8620)
- KMSpicosetup.tmp (PID: 8680)
- KMSpicosetup.tmp (PID: 8708)
- KMSpicosetup.exe (PID: 8948)
- KMSpicosetup.exe (PID: 8884)
- KMSpicosetup.exe (PID: 8956)
Starts POWERSHELL.EXE for commands execution
- RegistryHost.exe (PID: 4220)
- RegistryHost.exe (PID: 1812)
- RegistryHost.exe (PID: 1452)
- RegistryHost.exe (PID: 3124)
- RegistryHost.exe (PID: 5280)
- RegistryHost.exe (PID: 5960)
- RegistryHost.exe (PID: 7192)
- RegistryHost.exe (PID: 7488)
- RegistryHost.exe (PID: 7876)
- RegistryHost.exe (PID: 7960)
- RegistryHost.exe (PID: 8048)
- RegistryHost.exe (PID: 208)
- RegistryHost.exe (PID: 8356)
Reads security settings of Internet Explorer
- KMSpicosetup.tmp (PID: 5364)
- KMSPicosetup.exe.exe (PID: 1164)
Reads the date of Windows installation
- KMSPicosetup.exe.exe (PID: 1164)
Starts process via Powershell
- powershell.exe (PID: 4944)
- powershell.exe (PID: 1240)
- powershell.exe (PID: 6476)
- powershell.exe (PID: 5428)
- powershell.exe (PID: 728)
- powershell.exe (PID: 1512)
- powershell.exe (PID: 7224)
- powershell.exe (PID: 7520)
- powershell.exe (PID: 7972)
- powershell.exe (PID: 8016)
- powershell.exe (PID: 7580)
- powershell.exe (PID: 7252)
- powershell.exe (PID: 8516)
Reads the Windows owner or organization settings
- KMSpicosetup.tmp (PID: 5600)
Process drops legitimate windows executable
- KMSpicosetup.tmp (PID: 5600)
- KMSpicosetup.tmp (PID: 7012)
- KMSpicosetup.tmp (PID: 8212)
- KMSpicosetup.tmp (PID: 8656)
- KMSpicosetup.tmp (PID: 8708)
- KMSpicosetup.tmp (PID: 8680)
Drops a system driver (possible attempt to evade defenses)
- Registryhost.exe (PID: 6988)
- Registryhost.exe (PID: 6652)
Stops a currently running service
- sc.exe (PID: 4164)
- sc.exe (PID: 7152)
Windows service management via SC.EXE
- sc.exe (PID: 2332)
- sc.exe (PID: 1056)
- sc.exe (PID: 6424)
Executes as Windows Service
- Registryhost.exe (PID: 6988)
- Registryhost.exe (PID: 6652)
Crypto Currency Mining Activity Detected
- svchost.exe (PID: 2196)
Creates a new Windows service
- sc.exe (PID: 5384)
- sc.exe (PID: 6132)
Starts SC.EXE for service management
- RegistryHost.exe (PID: 1616)
- cmd.exe (PID: 6416)
- RegistryHost.exe (PID: 1764)
There is functionality for taking screenshot (YARA)
- KMSPicosetup.exe.exe (PID: 1164)
Modifies the phishing filter of IE
- KMSpicosetup.tmp (PID: 5600)
Starts CMD.EXE for commands execution
- KMSpicosetup.tmp (PID: 5600)
Executing commands from ".cmd" file
- KMSpicosetup.tmp (PID: 5600)
Potential Corporate Privacy Violation
- conhost.exe (PID: 6852)
INFO
Executable content was dropped or overwritten
- WinRAR.exe (PID: 4560)
- WinRAR.exe (PID: 6676)
Manual execution by a user
- WinRAR.exe (PID: 2600)
- WinRAR.exe (PID: 6676)
- KMSPicosetup.exe.exe (PID: 1164)
- RegistryHost.exe (PID: 1812)
- KMSPicosetup.exe.exe (PID: 6036)
- KMSPicosetup.exe.exe (PID: 3828)
- KMSPicosetup.exe.exe (PID: 4172)
- KMSPicosetup.exe.exe (PID: 684)
- KMSPicosetup.exe.exe (PID: 1852)
- KMSPicosetup.exe.exe (PID: 6132)
- KMSPicosetup.exe.exe (PID: 3016)
- KMSPicosetup.exe.exe (PID: 7280)
- KMSPicosetup.exe.exe (PID: 680)
- KMSPicosetup.exe.exe (PID: 7560)
- KMSPicosetup.exe.exe (PID: 7832)
- KMSPicosetup.exe.exe (PID: 7820)
The sample compiled with english language support
- WinRAR.exe (PID: 6676)
- KMSPicosetup.exe.exe (PID: 1164)
- KMSpicosetup.tmp (PID: 5600)
- RegistryHost.exe (PID: 1616)
- RegistryHost.exe (PID: 1764)
- KMSPicosetup.exe.exe (PID: 6036)
- KMSPicosetup.exe.exe (PID: 3828)
- KMSPicosetup.exe.exe (PID: 4172)
- KMSPicosetup.exe.exe (PID: 6132)
- KMSPicosetup.exe.exe (PID: 684)
- KMSPicosetup.exe.exe (PID: 1852)
- KMSPicosetup.exe.exe (PID: 680)
- KMSPicosetup.exe.exe (PID: 3016)
- KMSPicosetup.exe.exe (PID: 7280)
- KMSPicosetup.exe.exe (PID: 7832)
- KMSPicosetup.exe.exe (PID: 7820)
- KMSPicosetup.exe.exe (PID: 7560)
- KMSpicosetup.tmp (PID: 7012)
- KMSpicosetup.tmp (PID: 8212)
- KMSpicosetup.tmp (PID: 8680)
- KMSpicosetup.tmp (PID: 8656)
- KMSpicosetup.tmp (PID: 8708)
Reads the computer name
- KMSPicosetup.exe.exe (PID: 1164)
- KMSpicosetup.tmp (PID: 5364)
- KMSpicosetup.tmp (PID: 5600)
- KMSELDI.exe (PID: 7012)
Create files in a temporary directory
- KMSPicosetup.exe.exe (PID: 1164)
- KMSpicosetup.exe (PID: 2908)
- KMSpicosetup.tmp (PID: 5600)
- KMSpicosetup.exe (PID: 6660)
Checks supported languages
- KMSpicosetup.exe (PID: 2908)
- KMSpicosetup.tmp (PID: 5364)
- KMSPicosetup.exe.exe (PID: 1164)
- RegistryHost.exe (PID: 4220)
- KMSpicosetup.tmp (PID: 5600)
- RegistryHost.exe (PID: 1616)
- KMSpicosetup.exe (PID: 6660)
- Registryhost.exe (PID: 6988)
- UninsHs.exe (PID: 684)
- KMSELDI.exe (PID: 7012)
- SECOH-QAD.exe (PID: 1180)
Process checks computer location settings
- KMSpicosetup.tmp (PID: 5364)
- KMSPicosetup.exe.exe (PID: 1164)
The executable file from the user directory is run by the Powershell process
- RegistryHost.exe (PID: 1616)
Creates files in the program directory
- KMSpicosetup.tmp (PID: 5600)
- RegistryHost.exe (PID: 1616)
- KMSELDI.exe (PID: 7012)
The sample compiled with japanese language support
- Registryhost.exe (PID: 6988)
- Registryhost.exe (PID: 6652)
Detects InnoSetup installer (YARA)
- KMSpicosetup.exe (PID: 6660)
- KMSpicosetup.tmp (PID: 5364)
- KMSpicosetup.tmp (PID: 5600)
- KMSpicosetup.exe (PID: 2908)
Compiled with Borland Delphi (YARA)
- KMSpicosetup.tmp (PID: 5364)
- KMSpicosetup.tmp (PID: 5600)
Creates a software uninstall entry
- KMSpicosetup.tmp (PID: 5600)
Reads the machine GUID from the registry
- KMSELDI.exe (PID: 7012)
Reads product name
- KMSELDI.exe (PID: 7012)
Reads Environment values
- KMSELDI.exe (PID: 7012)
Reads Microsoft Office registry keys
- KMSELDI.exe (PID: 7012)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v5.0) (61.5) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (38.4) |
EXIF
ZIP
| FileVersion: | RAR v5 |
|---|---|
| CompressedSize: | 3216 |
| UncompressedSize: | 6466 |
| OperatingSystem: | Win32 |
| ArchivedFileName: | ReadMe KMSpico Install.txt |
Total processes
282
Monitored processes
135
Malicious processes
37
Suspicious processes
19
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 208 | "C:\Users\admin\AppData\Local\Temp\RarSFX8\RegistryHost.exe" | C:\Users\admin\AppData\Local\Temp\RarSFX8\RegistryHost.exe | — | KMSPicosetup.exe.exe | |||||||||||
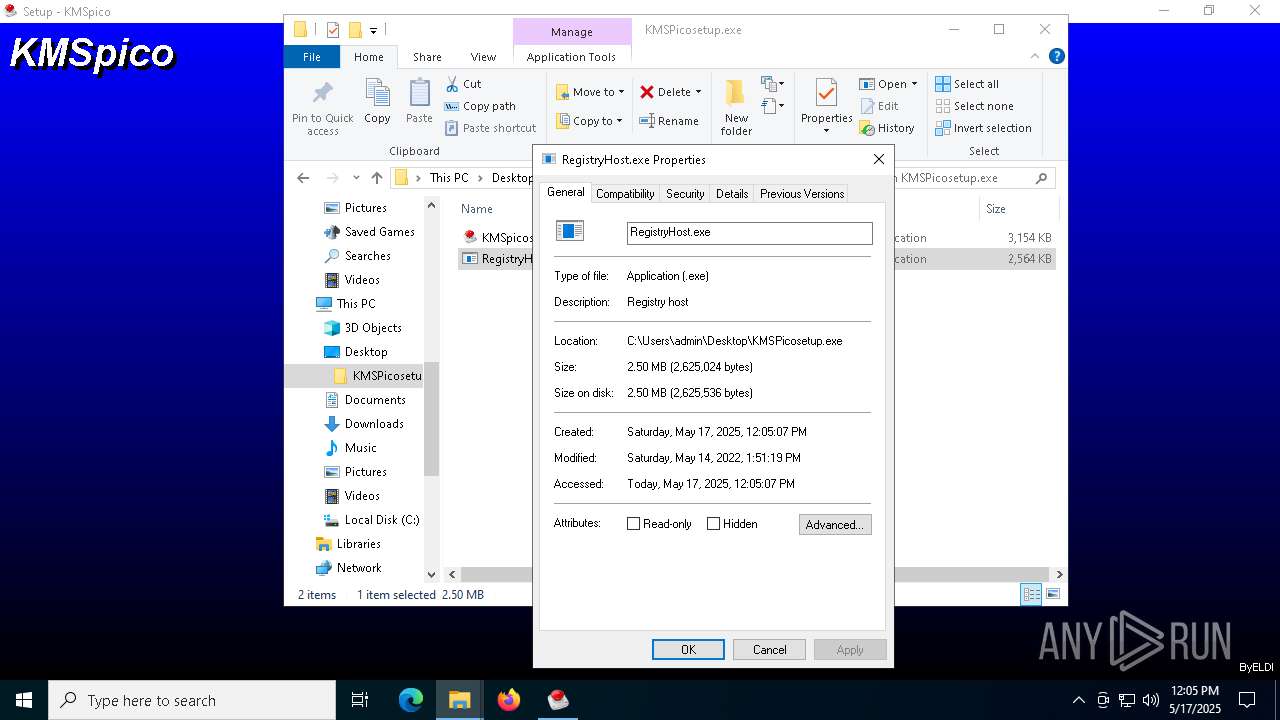
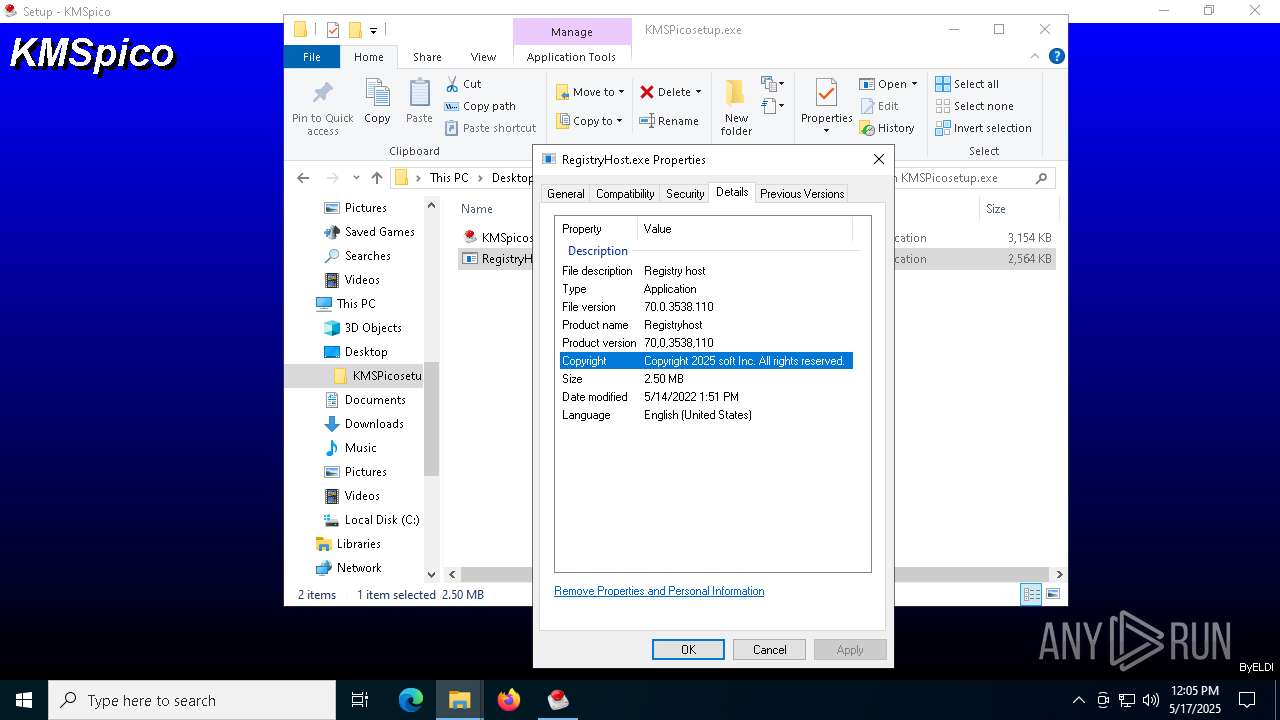
User: admin Company: Soft Inc. Integrity Level: MEDIUM Description: Registry host Exit code: 0 Version: 70,0,3538,110 Modules
| |||||||||||||||
| 632 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | sc.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 672 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 680 | "C:\Users\admin\Desktop\KMSPicosetup.exe.exe" | C:\Users\admin\Desktop\KMSPicosetup.exe.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Modules
| |||||||||||||||
| 684 | "C:\Program Files\KMSpico\UninsHs.exe" /r0=KMSpico,default,C:\Users\admin\AppData\Local\Temp\RarSFX0\KMSpicosetup.exe | C:\Program Files\KMSpico\UninsHs.exe | — | KMSpicosetup.tmp | |||||||||||
User: admin Company: Han-soft Integrity Level: HIGH Description: Uninstall for InnoSetup by Han-soft Exit code: 0 Version: 2.1.0.283 Modules
| |||||||||||||||
| 684 | "C:\Users\admin\Desktop\KMSPicosetup.exe.exe" | C:\Users\admin\Desktop\KMSPicosetup.exe.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Modules
| |||||||||||||||
| 728 | C:\WINDOWS\system32\WindowsPowerShell\v1.0\powershell.exe Start-Process '"C:\Users\admin\AppData\Local\Temp\RarSFX1\RegistryHost.exe"' -Verb runAs | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | RegistryHost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 736 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 872 | "C:\WINDOWS\System32\SLUI.exe" RuleId=eeba1977-569e-4571-b639-7623d8bfecc0;Action=AutoActivate;AppId=55c92734-d682-4d71-983e-d6ec3f16059f;SkuId=2de67392-b7a7-462a-b1ca-108dd189f588;NotificationInterval=1440;Trigger=TimerEvent | C:\Windows\System32\slui.exe | SppExtComObj.Exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1056 | C:\WINDOWS\system32\sc.exe delete "Registryhost" | C:\Windows\System32\sc.exe | — | RegistryHost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Service Control Manager Configuration Tool Exit code: 1060 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
59 214
Read events
59 109
Write events
100
Delete events
5
Modification events
| (PID) Process: | (4560) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (4560) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (4560) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (4560) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\KMSPico.rar | |||
| (PID) Process: | (4560) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (4560) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (4560) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (4560) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (4560) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface |
| Operation: | write | Name: | ShowPassword |
Value: 0 | |||
| (PID) Process: | (4560) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\MainWin |
| Operation: | write | Name: | Placement |
Value: 2C0000000000000001000000FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF3D0000002D000000FD03000016020000 | |||
Executable files
89
Suspicious files
38
Text files
735
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
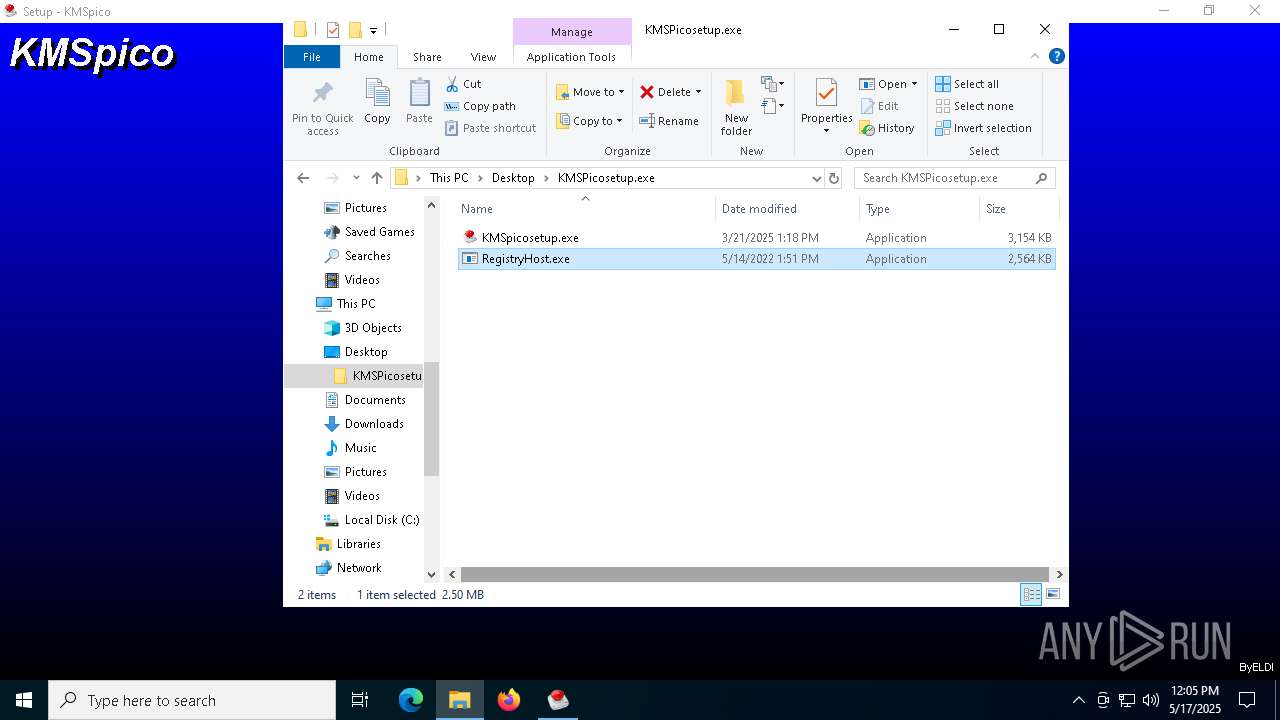
| 1164 | KMSPicosetup.exe.exe | C:\Users\admin\AppData\Local\Temp\RarSFX0\KMSpicosetup.exe | executable | |
MD5:A02164371A50C5FF9FA2870EF6E8CFA3 | SHA256:64C731ADBE1B96CB5765203B1E215093DCF268D020B299445884A4AE62ED2D3A | |||
| 4944 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_2j3oxunt.grs.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 2600 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$CS5492.30445 | binary | |
MD5:1065385D1230257C35A593CDB2D7B730 | SHA256:E274858672FFFB581537A3A9D0DEE7050552CBA6B3C03D8CEC026E9216974CDB | |||
| 2908 | KMSpicosetup.exe | C:\Users\admin\AppData\Local\Temp\is-RG2AD.tmp\KMSpicosetup.tmp | executable | |
MD5:1778C1F66FF205875A6435A33229AB3C | SHA256:95C06ACAC4FE4598840E5556F9613D43AA1039C52DAC64536F59E45A70F79DA6 | |||
| 1164 | KMSPicosetup.exe.exe | C:\Users\admin\AppData\Local\Temp\RarSFX0\RegistryHost.exe | executable | |
MD5:F821708498F6378A58138CC0588C1185 | SHA256:9ACF244976910547645131D17D2A276946E003B3ABF9C2A3A458D30399F72C1E | |||
| 6676 | WinRAR.exe | C:\Users\admin\Desktop\KMSPicosetup.exe\RegistryHost.exe | executable | |
MD5:F821708498F6378A58138CC0588C1185 | SHA256:9ACF244976910547645131D17D2A276946E003B3ABF9C2A3A458D30399F72C1E | |||
| 4944 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_5rwbxqn2.4ej.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 4560 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb4560.28967\KMSPicosetup.exe.exe | executable | |
MD5:B3982F3DA914790D18BFA2922ACB269E | SHA256:5B19E183B0ADB269CAAF8225AF38D2A7266750703780CF29E75E018310B8530F | |||
| 6676 | WinRAR.exe | C:\Users\admin\Desktop\KMSPicosetup.exe\KMSpicosetup.exe | executable | |
MD5:A02164371A50C5FF9FA2870EF6E8CFA3 | SHA256:64C731ADBE1B96CB5765203B1E215093DCF268D020B299445884A4AE62ED2D3A | |||
| 5600 | KMSpicosetup.tmp | C:\Program Files\KMSpico\is-TUGP8.tmp | executable | |
MD5:1397B23F30681F97049DF61F94F54D05 | SHA256:FA76151A783250014AC8FA55D4C833100A623FCAD1D6E2DDADCDE259F5709609 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
5
TCP/UDP connections
27
DNS requests
19
Threats
3
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5496 | MoUsoCoreWorker.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | GET | 200 | 23.48.23.158:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5176 | SIHClient.exe | GET | 200 | 23.52.120.96:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
5176 | SIHClient.exe | GET | 200 | 23.52.120.96:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | 23.48.23.158:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
5496 | MoUsoCoreWorker.exe | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
— | — | 172.211.123.250:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
6544 | svchost.exe | 20.190.159.64:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6544 | svchost.exe | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
2104 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
5176 | SIHClient.exe | 4.245.163.56:443 | slscr.update.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
pool.hashvault.pro |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2196 | svchost.exe | Crypto Currency Mining Activity Detected | ET COINMINER CoinMiner Domain in DNS Lookup (pool .hashvault .pro) |
6852 | conhost.exe | Potential Corporate Privacy Violation | ET INFO Cryptocurrency Miner Checkin |
6852 | conhost.exe | Potential Corporate Privacy Violation | ET INFO Cryptocurrency Miner Checkin |