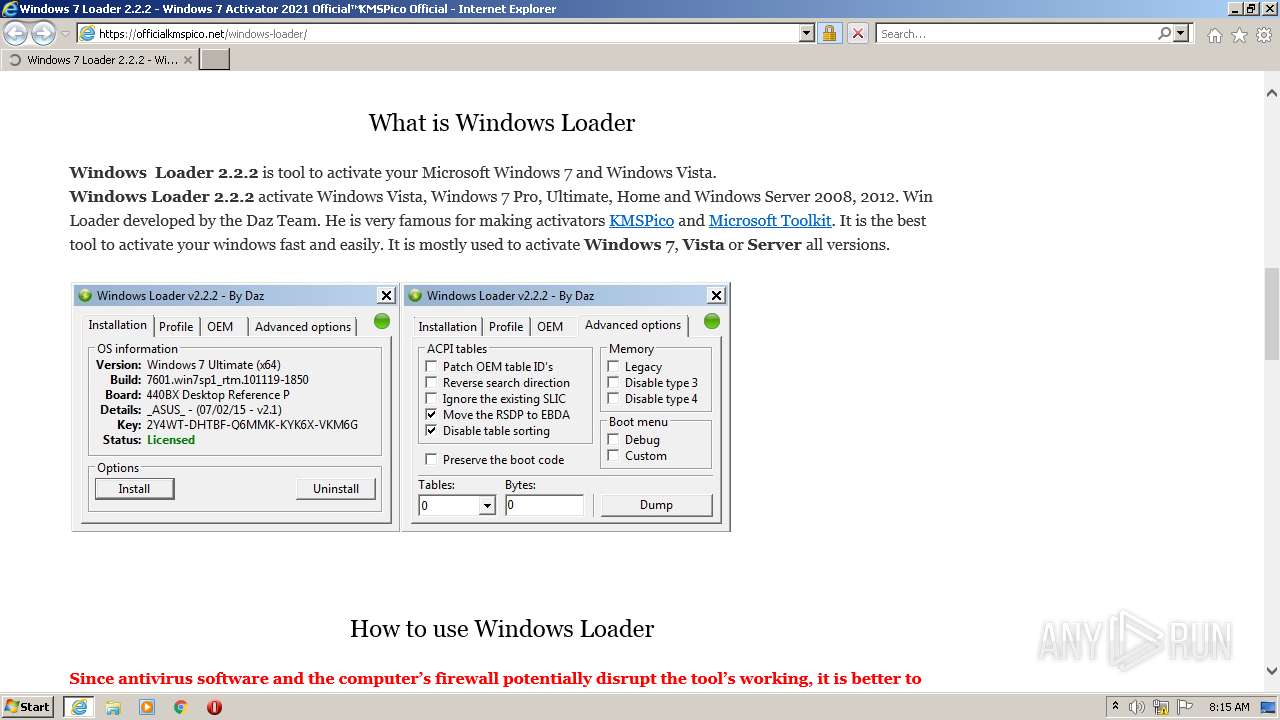
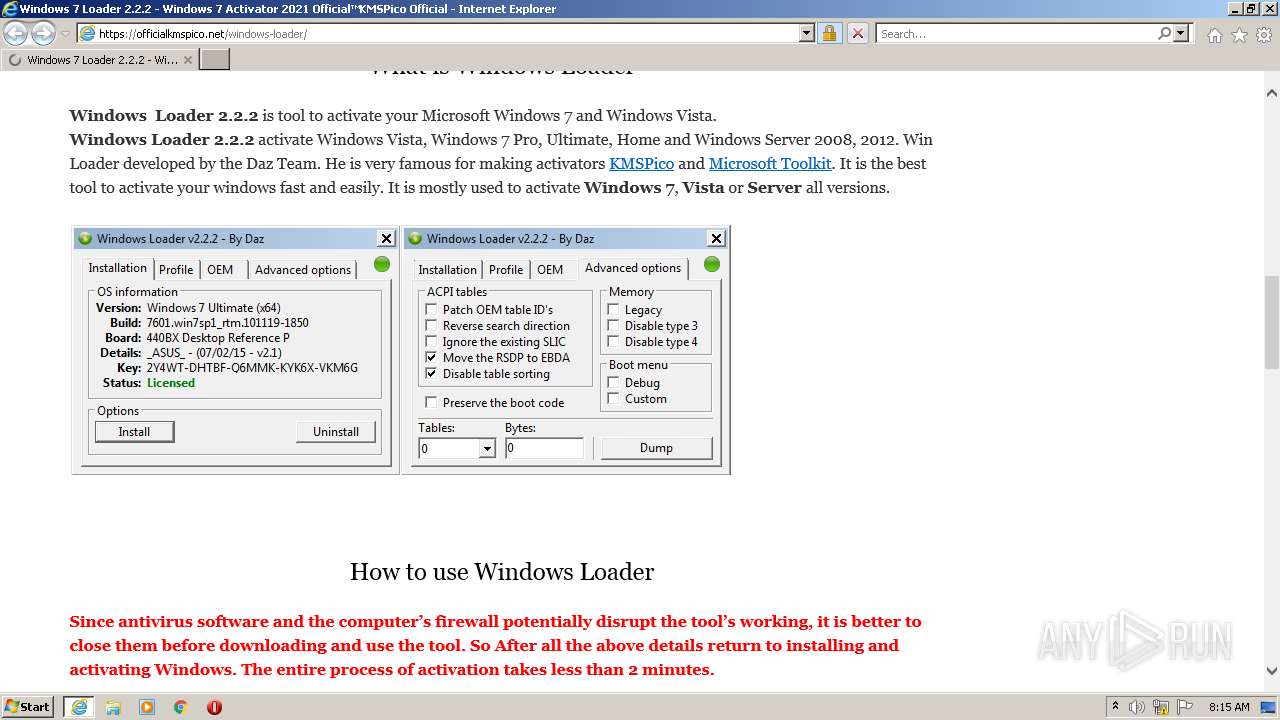
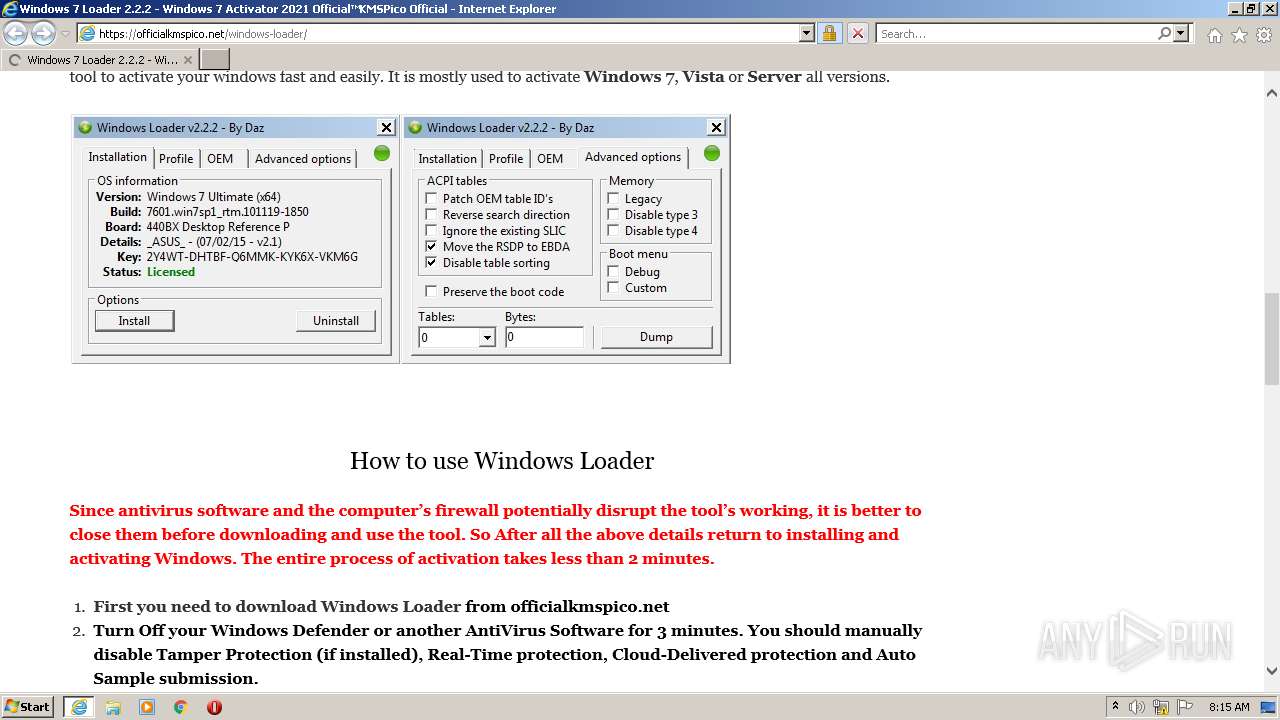
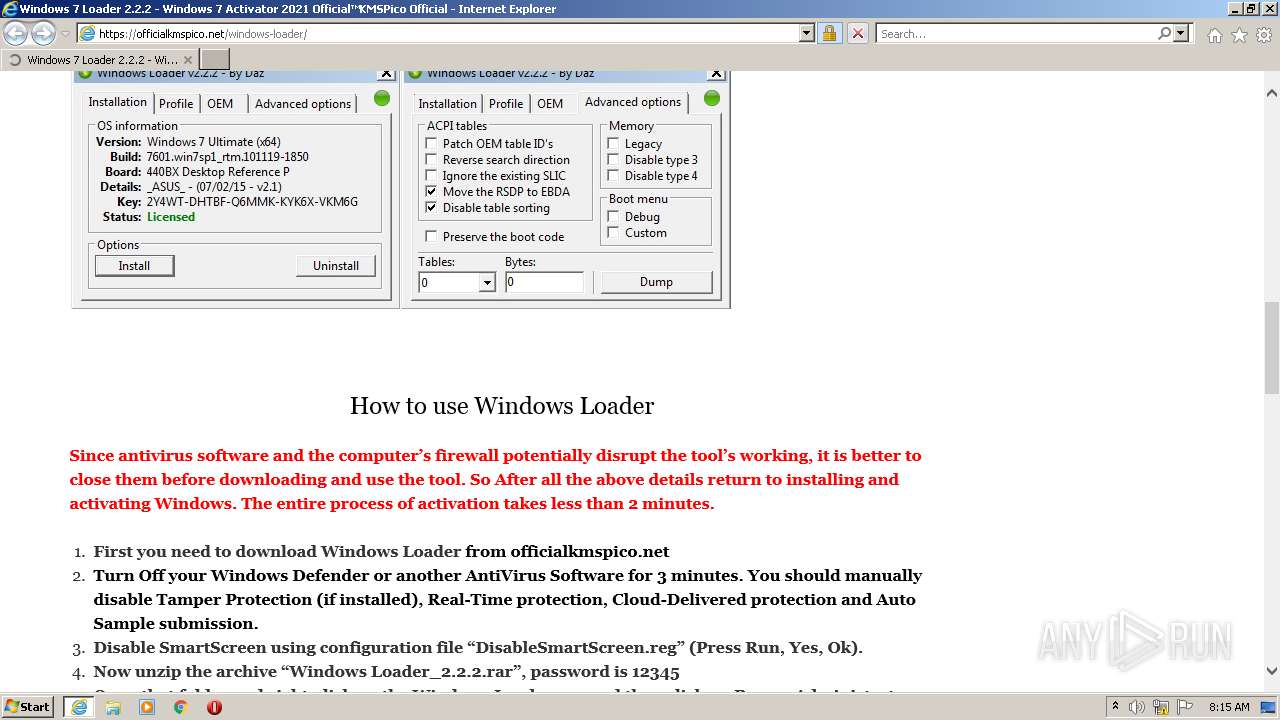
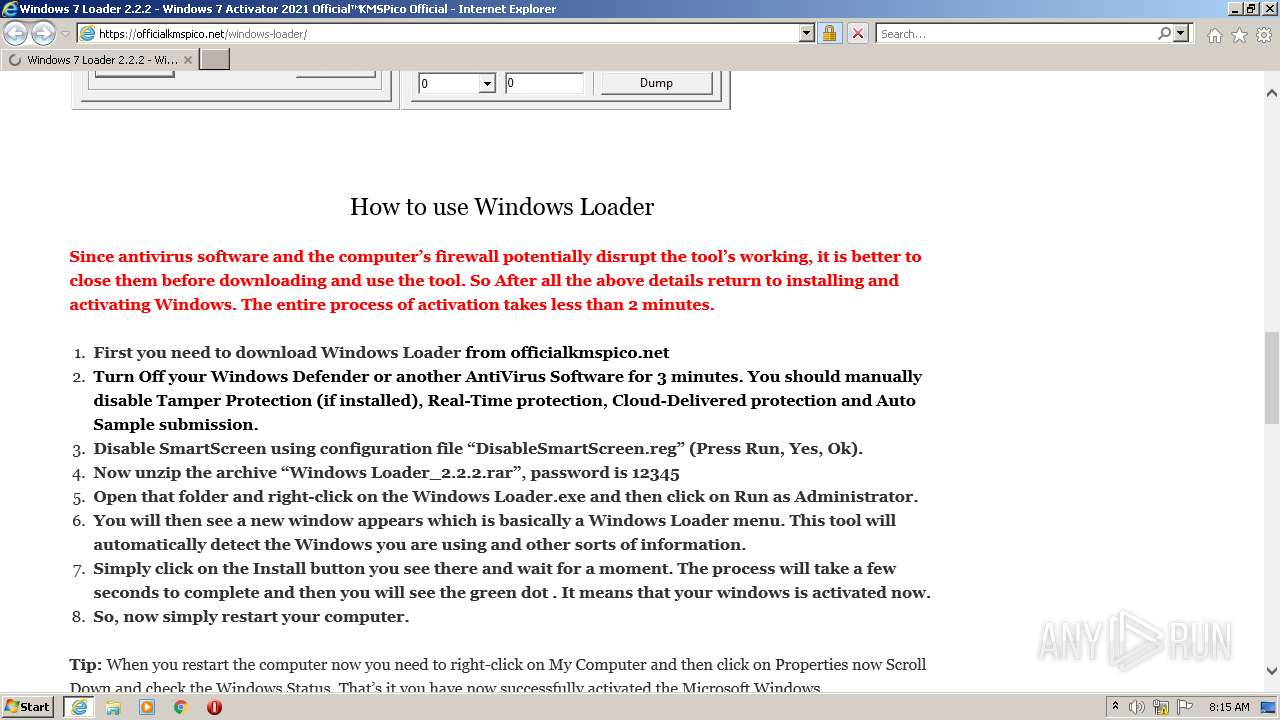
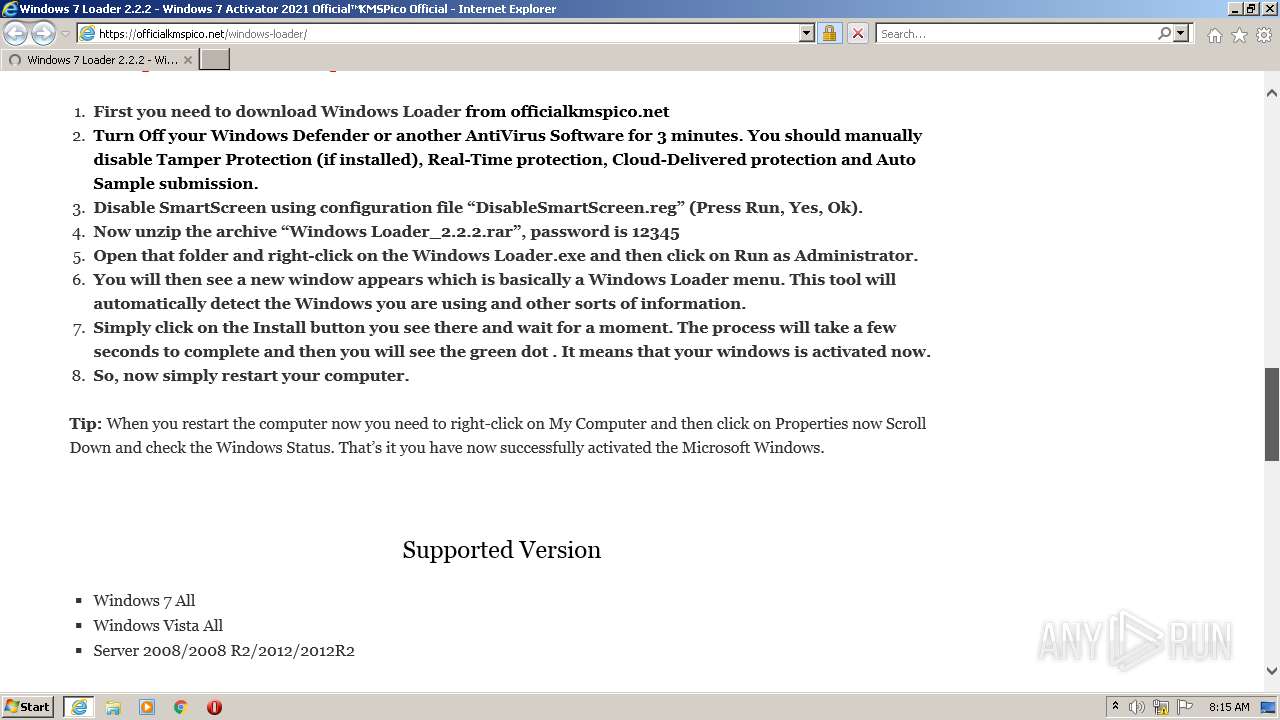
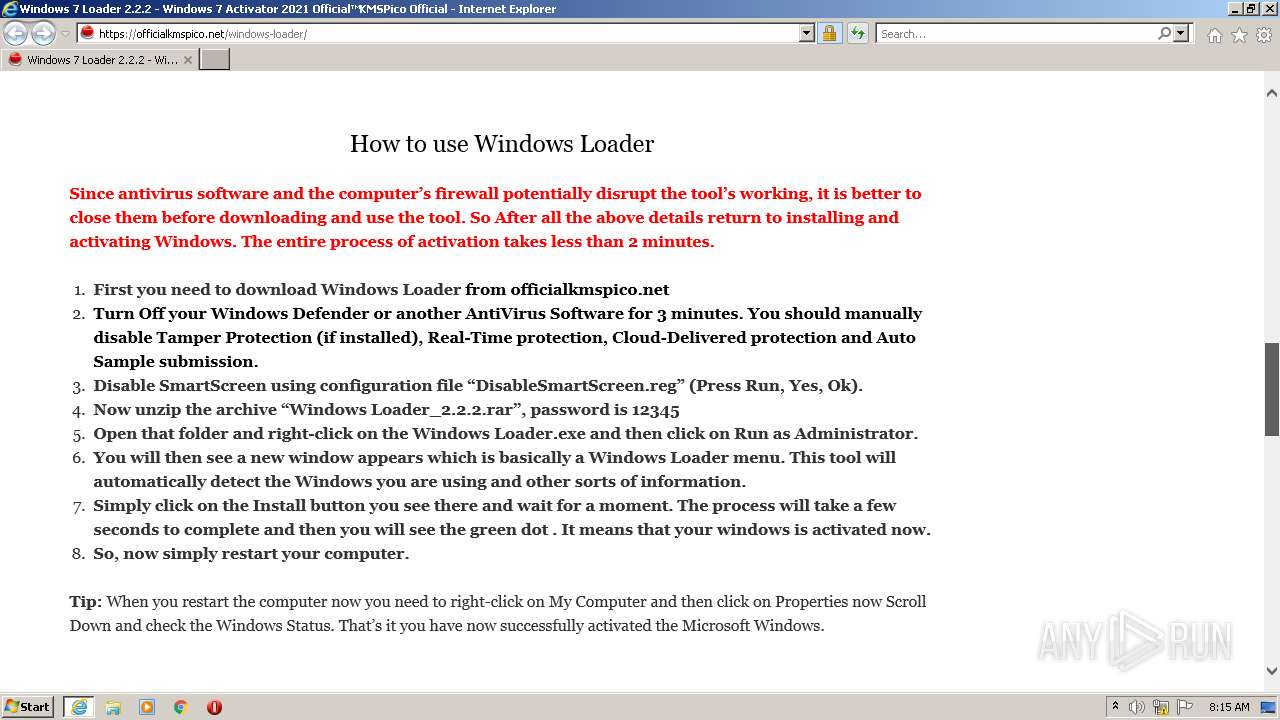
| URL: | https://officialkmspico.net/windows-loader/ |
| Full analysis: | https://app.any.run/tasks/44076fc7-6a1d-429f-856e-7a04727b3903 |
| Verdict: | Malicious activity |
| Threats: | Amadey is a formidable Windows infostealer threat, characterized by its persistence mechanisms, modular design, and ability to execute various malicious tasks. |
| Analysis date: | April 25, 2022, 07:15:15 |
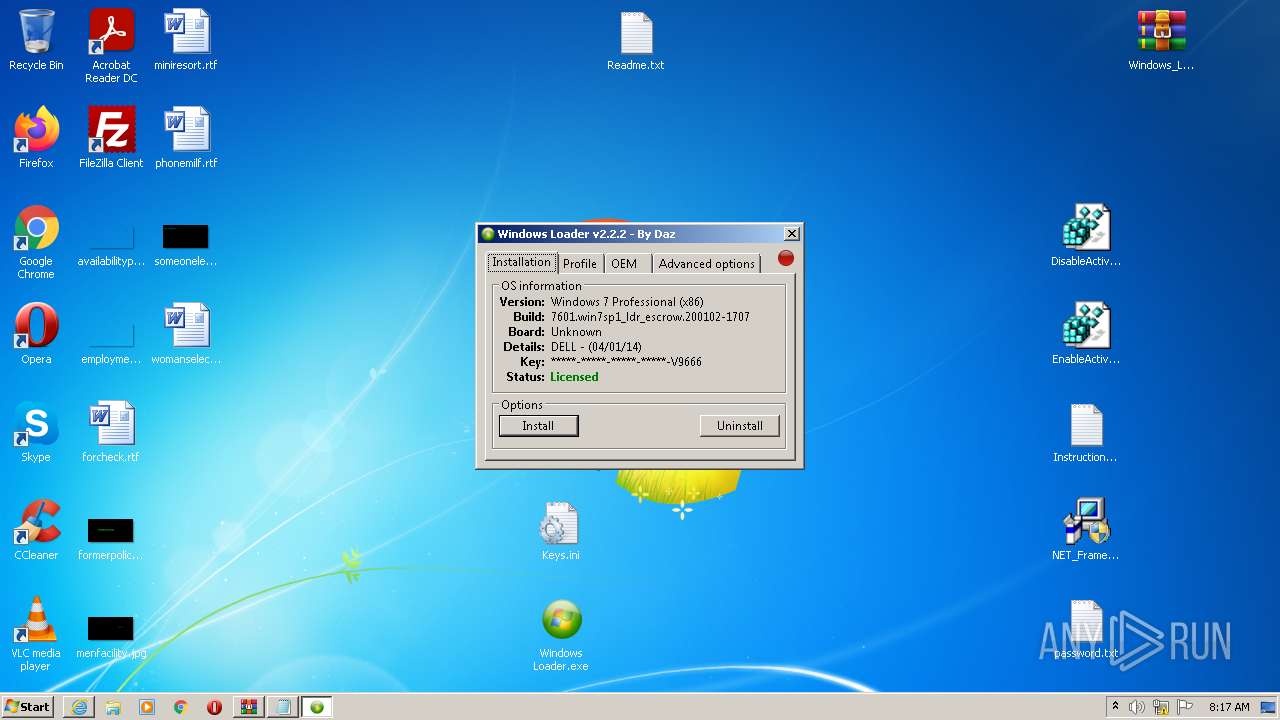
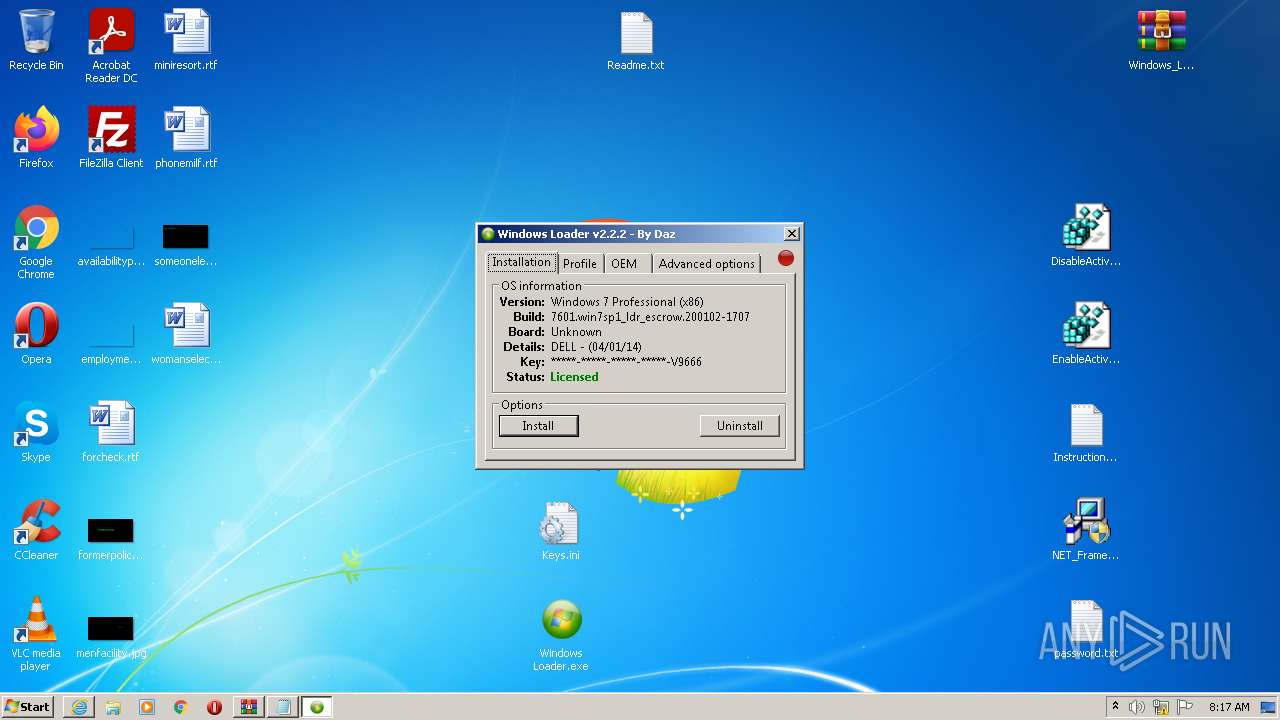
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
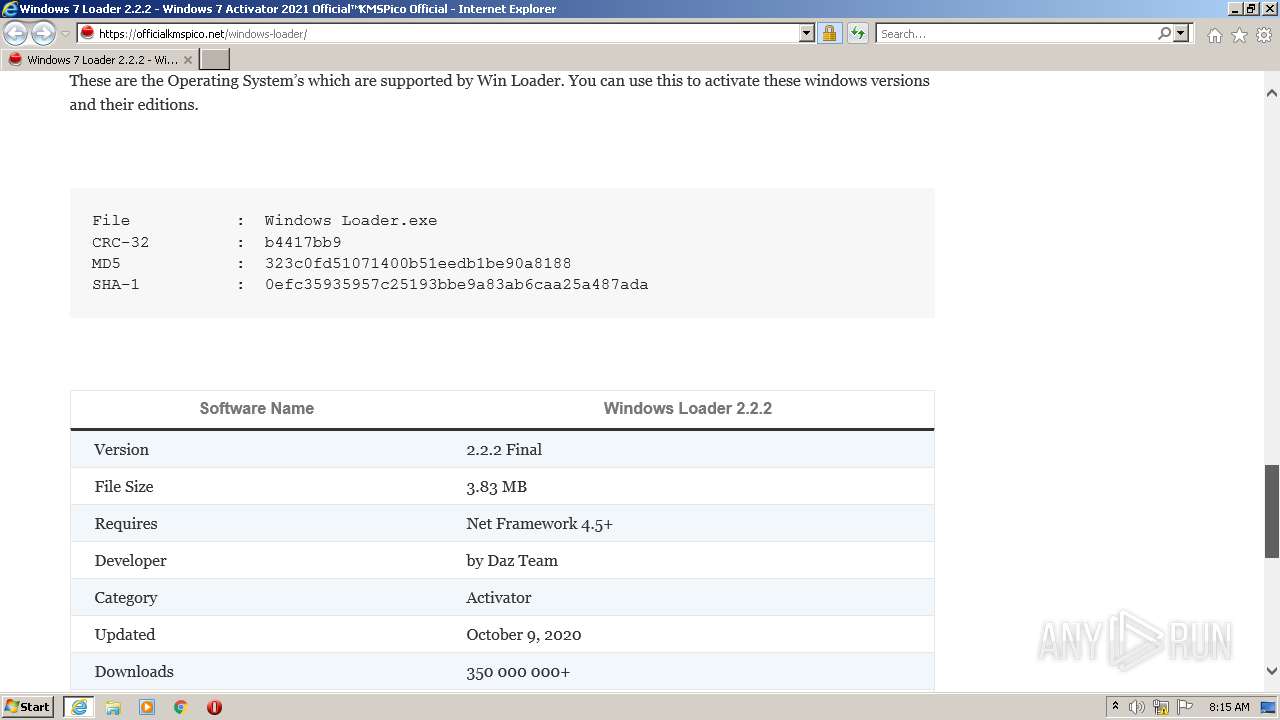
| MD5: | D1255438C0AB6A53196124A9639B7ACC |
| SHA1: | 40B3BB9DBD3B8A1891D950E7666B6F6E4A1A3E01 |
| SHA256: | 9E7CF7EDED4C0E8D251881247B4E27F730264EBDC9F976AF165715244C5AC5CE |
| SSDEEP: | 3:N8KQGMR5CryK:2KQGMe |
MALICIOUS
Drops executable file immediately after starts
- WinRAR.exe (PID: 2720)
- WinRAR.exe (PID: 1972)
- system32.exe (PID: 736)
- ftewk.exe (PID: 3480)
- Windows Loader.exe (PID: 1836)
- windows loader.exe (PID: 3608)
Application was dropped or rewritten from another process
- Windows Loader.exe (PID: 1836)
- services32.exe (PID: 3060)
- services32.exe (PID: 2244)
- svchost32.exe (PID: 2364)
- system32.exe (PID: 736)
- windows loader.exe (PID: 4036)
- windows loader.exe (PID: 3608)
- ftewk.exe (PID: 3480)
- ftewk.exe (PID: 3348)
- ftewk.exe (PID: 3844)
- Windows Loader.exe (PID: 1948)
- ftewk.exe (PID: 452)
- svchost32.exe (PID: 4088)
- system32.exe (PID: 3088)
- windows loader.exe (PID: 3216)
- services32.exe (PID: 2184)
- bootsect.exe (PID: 3088)
Changes the autorun value in the registry
- svchost32.exe (PID: 2364)
Uses Task Scheduler to run other applications
- ftewk.exe (PID: 3480)
- cmd.exe (PID: 3552)
Loads the Task Scheduler COM API
- schtasks.exe (PID: 3892)
- schtasks.exe (PID: 3396)
- schtasks.exe (PID: 1284)
- schtasks.exe (PID: 1388)
- schtasks.exe (PID: 3296)
- schtasks.exe (PID: 1564)
Executes PowerShell scripts
- cmd.exe (PID: 3552)
Changes the Startup folder
- reg.exe (PID: 1928)
AMADEY was detected
- ftewk.exe (PID: 3480)
Starts NET.EXE for service management
- cmd.exe (PID: 1968)
Connects to CnC server
- ftewk.exe (PID: 3480)
- rundll32.exe (PID: 4044)
Turns off the firewall via NETSH.EXE
- powershell.exe (PID: 2424)
Actions looks like stealing of personal data
- rundll32.exe (PID: 4044)
Loads dropped or rewritten executable
- rundll32.exe (PID: 4044)
SUSPICIOUS
Reads Microsoft Outlook installation path
- iexplore.exe (PID: 3336)
- iexplore.exe (PID: 2176)
Reads the computer name
- WinRAR.exe (PID: 2720)
- WinRAR.exe (PID: 1972)
- Windows Loader.exe (PID: 1836)
- services32.exe (PID: 2244)
- windows loader.exe (PID: 3608)
- system32.exe (PID: 736)
- ftewk.exe (PID: 3480)
- powershell.exe (PID: 3380)
- ftewk.exe (PID: 3348)
- ftewk.exe (PID: 3844)
- powershell.exe (PID: 2300)
- powershell.exe (PID: 2244)
- powershell.exe (PID: 1928)
- powershell.exe (PID: 1068)
- powershell.exe (PID: 2528)
- powershell.exe (PID: 3964)
- powershell.exe (PID: 3332)
- powershell.exe (PID: 452)
- powershell.exe (PID: 2268)
- powershell.exe (PID: 2556)
- powershell.exe (PID: 3496)
- powershell.exe (PID: 4084)
- powershell.exe (PID: 2620)
- powershell.exe (PID: 3572)
- powershell.exe (PID: 2424)
- ftewk.exe (PID: 452)
- Windows Loader.exe (PID: 1948)
- services32.exe (PID: 2184)
- cscript.exe (PID: 268)
- cscript.exe (PID: 1884)
Checks supported languages
- WinRAR.exe (PID: 2720)
- Windows Loader.exe (PID: 1836)
- services32.exe (PID: 2244)
- svchost32.exe (PID: 2364)
- system32.exe (PID: 736)
- windows loader.exe (PID: 3608)
- ftewk.exe (PID: 3480)
- cmd.exe (PID: 2996)
- powershell.exe (PID: 3380)
- ftewk.exe (PID: 3348)
- cmd.exe (PID: 3552)
- ftewk.exe (PID: 3844)
- cmd.exe (PID: 1968)
- powershell.exe (PID: 2300)
- WinRAR.exe (PID: 1972)
- powershell.exe (PID: 2244)
- powershell.exe (PID: 1928)
- powershell.exe (PID: 1068)
- powershell.exe (PID: 2528)
- powershell.exe (PID: 3964)
- powershell.exe (PID: 2556)
- powershell.exe (PID: 3332)
- powershell.exe (PID: 452)
- powershell.exe (PID: 2268)
- powershell.exe (PID: 3496)
- powershell.exe (PID: 4084)
- powershell.exe (PID: 2620)
- powershell.exe (PID: 3572)
- powershell.exe (PID: 2424)
- ftewk.exe (PID: 452)
- Windows Loader.exe (PID: 1948)
- services32.exe (PID: 2184)
- svchost32.exe (PID: 4088)
- system32.exe (PID: 3088)
- windows loader.exe (PID: 3216)
- cmd.exe (PID: 1492)
- cmd.exe (PID: 3084)
- cmd.exe (PID: 2140)
- cmd.exe (PID: 2792)
- cmd.exe (PID: 3032)
- cmd.exe (PID: 2408)
- cmd.exe (PID: 3416)
- cscript.exe (PID: 1884)
- cmd.exe (PID: 3284)
- cscript.exe (PID: 268)
- cmd.exe (PID: 2184)
- bootsect.exe (PID: 3088)
- cmd.exe (PID: 2804)
- cmd.exe (PID: 2568)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 2720)
- WinRAR.exe (PID: 1972)
- Windows Loader.exe (PID: 1836)
- system32.exe (PID: 736)
- ftewk.exe (PID: 3480)
- windows loader.exe (PID: 3608)
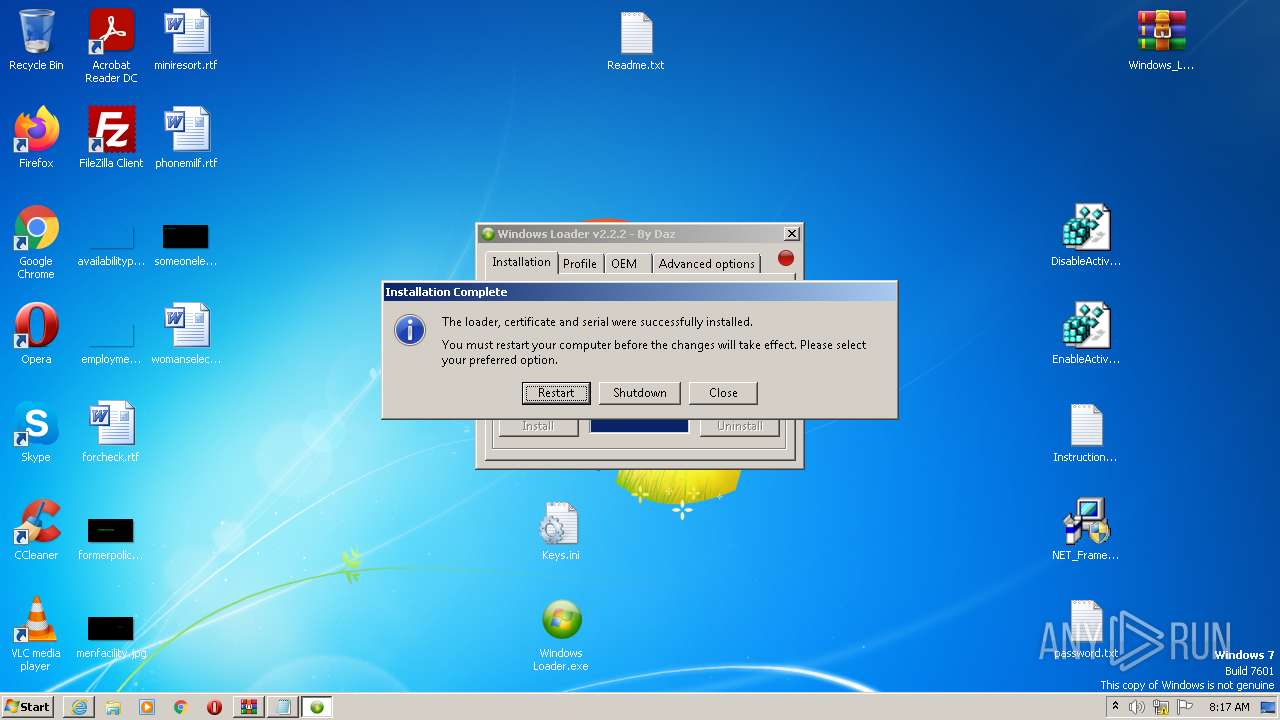
Drops a file with a compile date too recent
- WinRAR.exe (PID: 1972)
- Windows Loader.exe (PID: 1836)
- system32.exe (PID: 736)
- ftewk.exe (PID: 3480)
- WinRAR.exe (PID: 2720)
- windows loader.exe (PID: 3608)
Reads the date of Windows installation
- Windows Loader.exe (PID: 1836)
- Windows Loader.exe (PID: 1948)
Reads Environment values
- windows loader.exe (PID: 3608)
- netsh.exe (PID: 3156)
- netsh.exe (PID: 2672)
Reads Windows Product ID
- windows loader.exe (PID: 3608)
Starts itself from another location
- system32.exe (PID: 736)
Starts CMD.EXE for commands execution
- ftewk.exe (PID: 3480)
- ftewk.exe (PID: 3348)
- ftewk.exe (PID: 3844)
- cmd.exe (PID: 2792)
- cmd.exe (PID: 3084)
- windows loader.exe (PID: 3608)
Uses REG.EXE to modify Windows registry
- cmd.exe (PID: 2996)
- cmd.exe (PID: 3552)
Application launched itself
- ftewk.exe (PID: 3480)
- cmd.exe (PID: 2792)
- cmd.exe (PID: 3084)
Uses NETSH.EXE for network configuration
- cmd.exe (PID: 1968)
- powershell.exe (PID: 2424)
Executed via Task Scheduler
- ftewk.exe (PID: 452)
Uses ICACLS.EXE to modify access control list
- cmd.exe (PID: 2140)
- cmd.exe (PID: 1492)
Executes scripts
- cmd.exe (PID: 3284)
- cmd.exe (PID: 3416)
Uses RUNDLL32.EXE to load library
- ftewk.exe (PID: 3480)
Creates files in the user directory
- ftewk.exe (PID: 3480)
INFO
Checks supported languages
- iexplore.exe (PID: 1332)
- iexplore.exe (PID: 3336)
- iexplore.exe (PID: 2176)
- NOTEPAD.EXE (PID: 3044)
- reg.exe (PID: 1928)
- schtasks.exe (PID: 3892)
- net.exe (PID: 2912)
- net1.exe (PID: 3060)
- tskill.exe (PID: 2740)
- tskill.exe (PID: 2432)
- tskill.exe (PID: 3868)
- tskill.exe (PID: 2800)
- tskill.exe (PID: 2368)
- tskill.exe (PID: 2120)
- netsh.exe (PID: 3156)
- tskill.exe (PID: 3472)
- tskill.exe (PID: 2880)
- tskill.exe (PID: 2528)
- tskill.exe (PID: 752)
- tskill.exe (PID: 1836)
- tskill.exe (PID: 4092)
- tskill.exe (PID: 2120)
- tskill.exe (PID: 2548)
- tskill.exe (PID: 2832)
- tskill.exe (PID: 2604)
- tskill.exe (PID: 1760)
- tskill.exe (PID: 3488)
- tskill.exe (PID: 3220)
- tskill.exe (PID: 1020)
- tskill.exe (PID: 3316)
- tskill.exe (PID: 2532)
- tskill.exe (PID: 2432)
- tskill.exe (PID: 288)
- tskill.exe (PID: 3088)
- tskill.exe (PID: 1900)
- tskill.exe (PID: 3148)
- tskill.exe (PID: 3468)
- tskill.exe (PID: 3484)
- tskill.exe (PID: 3584)
- tskill.exe (PID: 3884)
- tskill.exe (PID: 672)
- tskill.exe (PID: 3684)
- tskill.exe (PID: 1584)
- tskill.exe (PID: 2140)
- tskill.exe (PID: 2996)
- tskill.exe (PID: 2932)
- tskill.exe (PID: 2436)
- tskill.exe (PID: 2988)
- tskill.exe (PID: 3776)
- tskill.exe (PID: 3764)
- tskill.exe (PID: 2428)
- tskill.exe (PID: 2804)
- tskill.exe (PID: 1644)
- tskill.exe (PID: 3376)
- tskill.exe (PID: 2092)
- tskill.exe (PID: 892)
- tskill.exe (PID: 2188)
- tskill.exe (PID: 1600)
- tskill.exe (PID: 2336)
- tskill.exe (PID: 2620)
- tskill.exe (PID: 2032)
- tskill.exe (PID: 2340)
- tskill.exe (PID: 3952)
- tskill.exe (PID: 2476)
- tskill.exe (PID: 2480)
- tskill.exe (PID: 3808)
- tskill.exe (PID: 3812)
- tskill.exe (PID: 3120)
- tskill.exe (PID: 3908)
- tskill.exe (PID: 2924)
- tskill.exe (PID: 2280)
- tskill.exe (PID: 1832)
- tskill.exe (PID: 588)
- tskill.exe (PID: 3412)
- tskill.exe (PID: 116)
- tskill.exe (PID: 3884)
- tskill.exe (PID: 3516)
- tskill.exe (PID: 2168)
- tskill.exe (PID: 3708)
- tskill.exe (PID: 3376)
- netsh.exe (PID: 2672)
- reg.exe (PID: 2888)
- reg.exe (PID: 116)
- reg.exe (PID: 3956)
- reg.exe (PID: 3284)
- reg.exe (PID: 2920)
- reg.exe (PID: 2776)
- reg.exe (PID: 2396)
- reg.exe (PID: 2896)
- reg.exe (PID: 3244)
- reg.exe (PID: 3760)
- reg.exe (PID: 2496)
- reg.exe (PID: 1652)
- reg.exe (PID: 2856)
- reg.exe (PID: 2948)
- reg.exe (PID: 3428)
- schtasks.exe (PID: 3396)
- schtasks.exe (PID: 1284)
- schtasks.exe (PID: 1388)
- schtasks.exe (PID: 3296)
- schtasks.exe (PID: 1564)
- reg.exe (PID: 780)
- reg.exe (PID: 1980)
- reg.exe (PID: 2448)
- reg.exe (PID: 2492)
- reg.exe (PID: 3544)
- reg.exe (PID: 3072)
- reg.exe (PID: 3364)
- reg.exe (PID: 3976)
- reg.exe (PID: 3376)
- reg.exe (PID: 1312)
- takeown.exe (PID: 3080)
- takeown.exe (PID: 3008)
- icacls.exe (PID: 4024)
- rundll32.exe (PID: 4044)
- icacls.exe (PID: 2184)
- compact.exe (PID: 3624)
- shutdown.exe (PID: 2976)
Reads the computer name
- iexplore.exe (PID: 1332)
- iexplore.exe (PID: 2176)
- iexplore.exe (PID: 3336)
- schtasks.exe (PID: 3892)
- netsh.exe (PID: 3156)
- netsh.exe (PID: 2672)
- schtasks.exe (PID: 1284)
- schtasks.exe (PID: 3396)
- schtasks.exe (PID: 3296)
- schtasks.exe (PID: 1388)
- schtasks.exe (PID: 1564)
- icacls.exe (PID: 4024)
- takeown.exe (PID: 3080)
- takeown.exe (PID: 3008)
- icacls.exe (PID: 2184)
- rundll32.exe (PID: 4044)
- shutdown.exe (PID: 2976)
Application launched itself
- iexplore.exe (PID: 1332)
Checks Windows Trust Settings
- iexplore.exe (PID: 3336)
- iexplore.exe (PID: 2176)
- iexplore.exe (PID: 1332)
- services32.exe (PID: 2244)
- powershell.exe (PID: 3380)
- powershell.exe (PID: 2300)
- powershell.exe (PID: 2244)
- powershell.exe (PID: 1928)
- powershell.exe (PID: 1068)
- powershell.exe (PID: 2528)
- powershell.exe (PID: 2268)
- powershell.exe (PID: 3964)
- powershell.exe (PID: 3332)
- powershell.exe (PID: 2556)
- powershell.exe (PID: 452)
- powershell.exe (PID: 3496)
- powershell.exe (PID: 4084)
- powershell.exe (PID: 2620)
- powershell.exe (PID: 3572)
- powershell.exe (PID: 2424)
- services32.exe (PID: 2184)
- cscript.exe (PID: 268)
- cscript.exe (PID: 1884)
Reads settings of System Certificates
- iexplore.exe (PID: 3336)
- iexplore.exe (PID: 1332)
- iexplore.exe (PID: 2176)
- services32.exe (PID: 2244)
- powershell.exe (PID: 3380)
- powershell.exe (PID: 2300)
- powershell.exe (PID: 2528)
- powershell.exe (PID: 2244)
- powershell.exe (PID: 1068)
- powershell.exe (PID: 1928)
- powershell.exe (PID: 2268)
- powershell.exe (PID: 3964)
- powershell.exe (PID: 2556)
- powershell.exe (PID: 3332)
- powershell.exe (PID: 452)
- powershell.exe (PID: 3496)
- powershell.exe (PID: 4084)
- powershell.exe (PID: 2620)
- powershell.exe (PID: 3572)
- services32.exe (PID: 2184)
Reads internet explorer settings
- iexplore.exe (PID: 3336)
- iexplore.exe (PID: 2176)
Modifies the phishing filter of IE
- iexplore.exe (PID: 1332)
Changes internet zones settings
- iexplore.exe (PID: 1332)
Creates files in the user directory
- iexplore.exe (PID: 1332)
Adds / modifies Windows certificates
- iexplore.exe (PID: 1332)
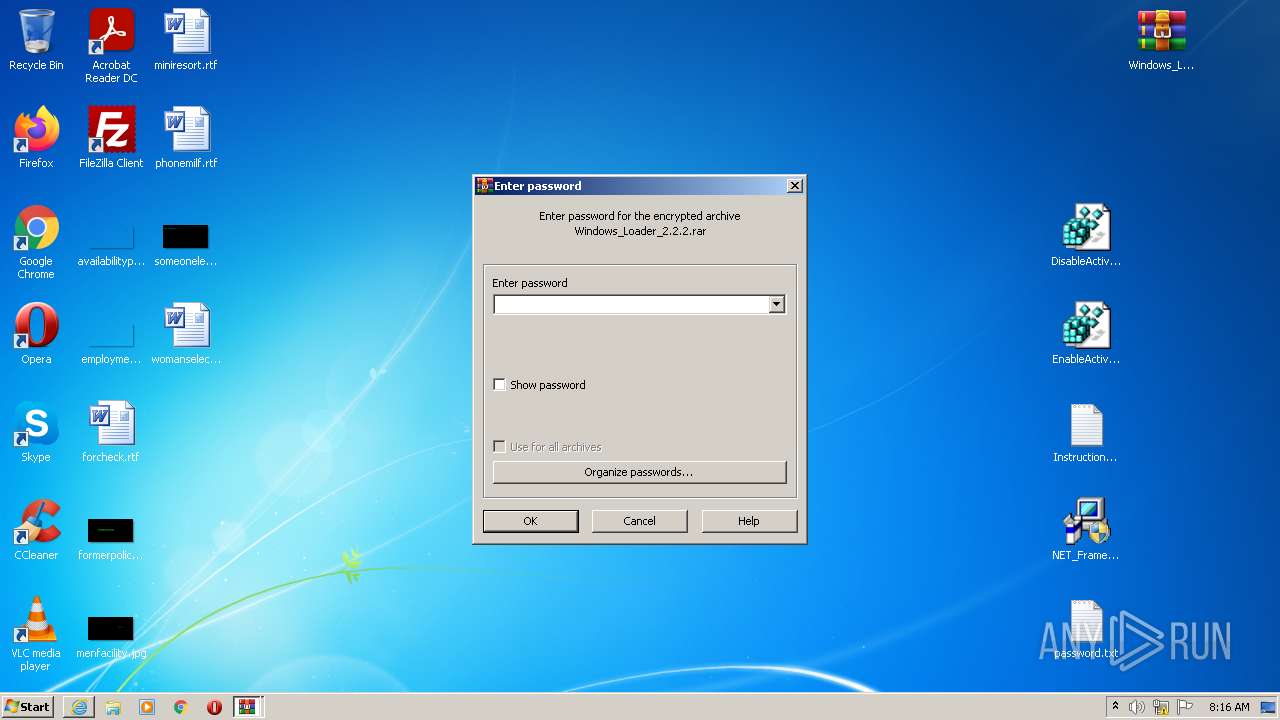
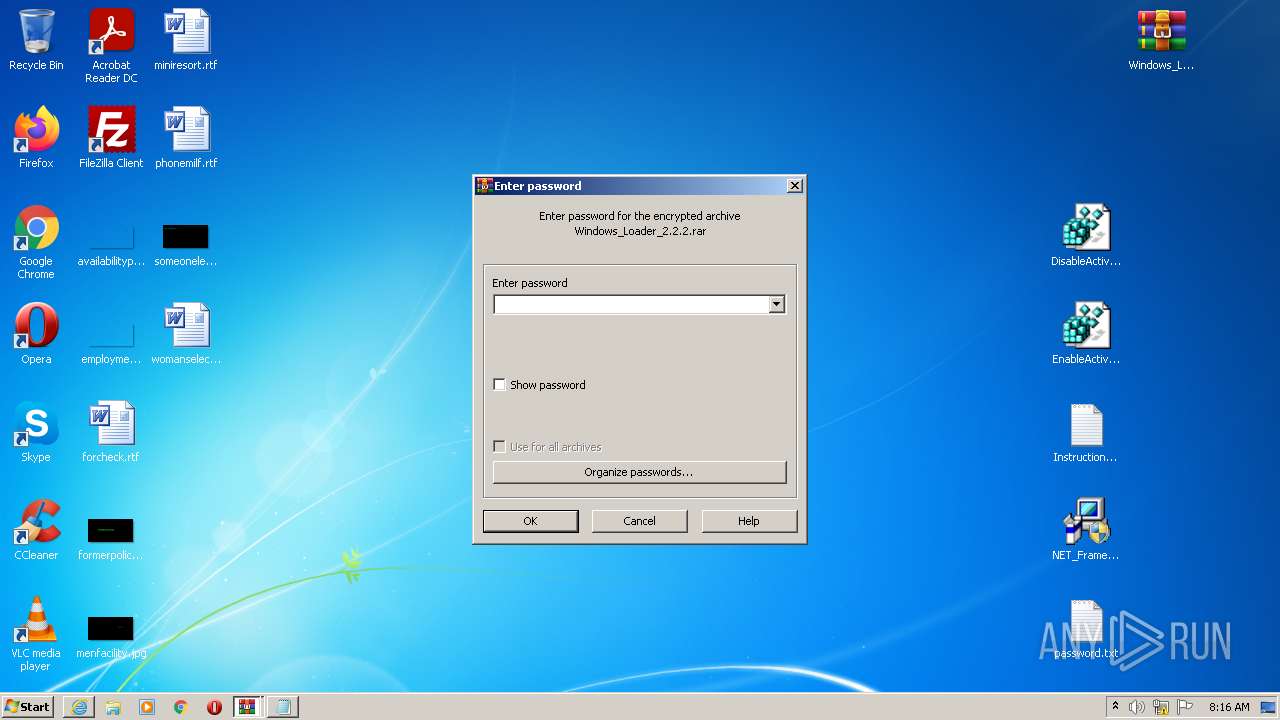
Manual execution by user
- WinRAR.exe (PID: 1972)
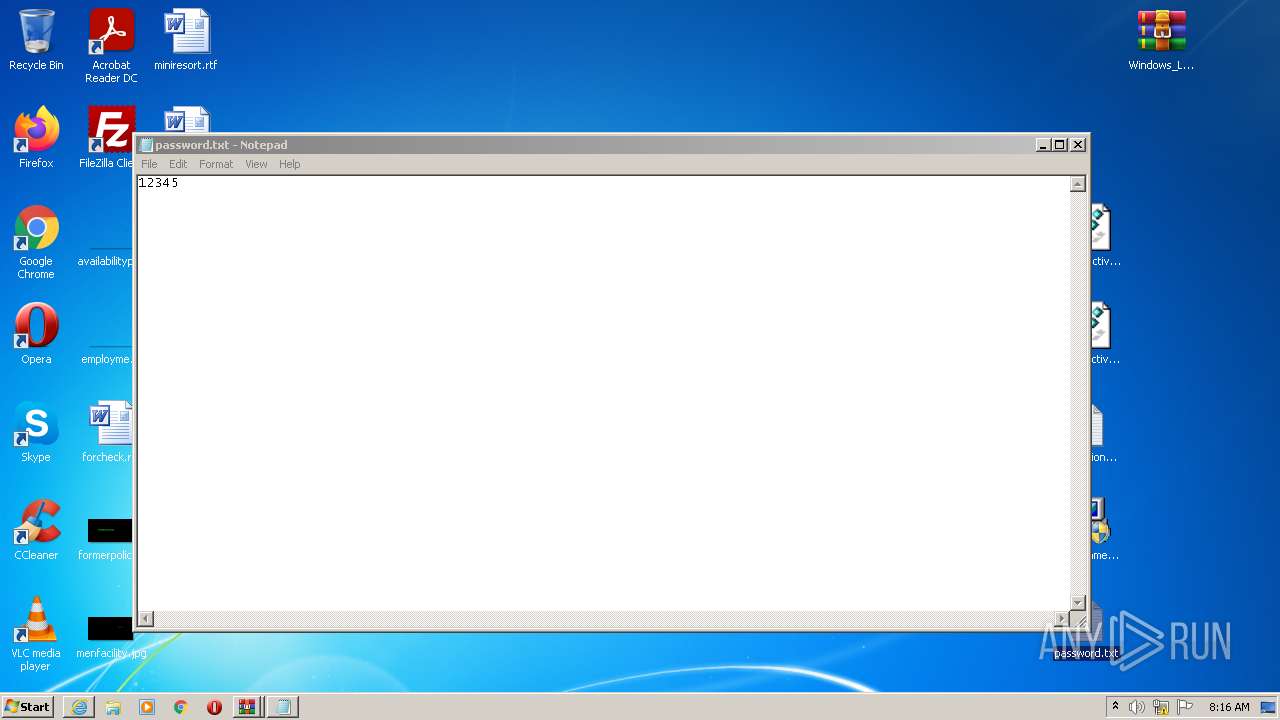
- NOTEPAD.EXE (PID: 3044)
- Windows Loader.exe (PID: 1836)
- Windows Loader.exe (PID: 1948)
Changes settings of System certificates
- iexplore.exe (PID: 1332)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
232
Monitored processes
169
Malicious processes
14
Suspicious processes
21
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 116 | tskill /A ad-* | C:\Windows\system32\tskill.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Remote Desktop Services End Process Utility Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 116 | reg add "HKLM\Software\Policies\Microsoft\Windows Defender\Real-Time Protection" /v "DisableIOAVProtection" /t REG_DWORD /d "1" /f | C:\Windows\system32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Registry Console Tool Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 268 | C:\Windows\System32\cscript.exe //nologo C:\Windows\System32\slmgr.vbs -ipk 32KD2-K9CTF-M3DJT-4J3WC-733WD | C:\Windows\System32\cscript.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft ® Console Based Script Host Exit code: 0 Version: 5.8.7600.16385 Modules
| |||||||||||||||
| 288 | tskill /A guar* | C:\Windows\system32\tskill.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Remote Desktop Services End Process Utility Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 452 | powershell.exe -command "Set-MpPreference -MAPSReporting 0" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 1 Version: 10.0.14409.1005 (rs1_srvoob.161208-1155) Modules
| |||||||||||||||
| 452 | C:\Users\admin\AppData\Local\Temp\b3dcf4c296\ftewk.exe | C:\Users\admin\AppData\Local\Temp\b3dcf4c296\ftewk.exe | — | taskeng.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Host Process for Windows Services Exit code: 0 Version: 10.0.19041.546 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 588 | tskill /A sweep* | C:\Windows\system32\tskill.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Remote Desktop Services End Process Utility Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 672 | tskill /A gcasDt* | C:\Windows\system32\tskill.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Remote Desktop Services End Process Utility Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 736 | "C:\Users\admin\system32.exe" | C:\Users\admin\system32.exe | Windows Loader.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Host Process for Windows Services Exit code: 0 Version: 10.0.19041.546 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 752 | tskill /A nav* | C:\Windows\system32\tskill.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Remote Desktop Services End Process Utility Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
94 301
Read events
93 108
Write events
1 190
Delete events
3
Modification events
| (PID) Process: | (1332) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPDaysSinceLastAutoMigration |
Value: 1 | |||
| (PID) Process: | (1332) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchLowDateTime |
Value: 950159744 | |||
| (PID) Process: | (1332) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchHighDateTime |
Value: 30955636 | |||
| (PID) Process: | (1332) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateLowDateTime |
Value: | |||
| (PID) Process: | (1332) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 30955636 | |||
| (PID) Process: | (1332) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (1332) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (1332) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (1332) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (1332) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
Executable files
13
Suspicious files
46
Text files
53
Unknown types
16
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3336 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | binary | |
MD5:— | SHA256:— | |||
| 3336 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\MFAQUS6V\blocks[1].css | text | |
MD5:— | SHA256:— | |||
| 3336 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\6BADA8974A10C4BD62CC921D13E43B18_28DEA62A0AE77228DD387E155AD0BA27 | der | |
MD5:— | SHA256:— | |||
| 3336 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\DY534W2X\windows-loader[1].htm | html | |
MD5:— | SHA256:— | |||
| 3336 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\DY534W2X\style[1].css | text | |
MD5:— | SHA256:— | |||
| 3336 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\6BADA8974A10C4BD62CC921D13E43B18_28DEA62A0AE77228DD387E155AD0BA27 | binary | |
MD5:— | SHA256:— | |||
| 3336 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\DY534W2X\official-kmspico[1].png | image | |
MD5:— | SHA256:— | |||
| 3336 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | compressed | |
MD5:F7DCB24540769805E5BB30D193944DCE | SHA256:6B88C6AC55BBD6FEA0EBE5A760D1AD2CFCE251C59D0151A1400701CB927E36EA | |||
| 3336 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\DY534W2X\gtranslate-style24[1].css | text | |
MD5:B1B4A32633503B5F5EEB86B59602E702 | SHA256:6A558670783199BB955EF7D0263B756A836CAC2B7644B263B3BA9BC43E4D21D3 | |||
| 3336 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\5IWPIAR9\icons[1].css | text | |
MD5:15D52F4600FD9D2BA180F9512AFA17D1 | SHA256:96EED42E394F5B00F1E02A12D1CE9557AAE7CD751E4A9AE2B3E8FC392B1DB945 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
20
TCP/UDP connections
49
DNS requests
15
Threats
21
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1332 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEA8Ull8gIGmZT9XHrHiJQeI%3D | US | der | 1.47 Kb | whitelisted |
3336 | iexplore.exe | GET | 200 | 142.250.185.131:80 | http://ocsp.pki.goog/gtsr1/ME4wTDBKMEgwRjAJBgUrDgMCGgUABBQwkcLWD4LqGJ7bE7B1XZsEbmfwUAQU5K8rJnEaK0gnhS9SZizv8IkTcT4CDQIDvFNZazTHGPUBUGY%3D | US | der | 724 b | whitelisted |
3336 | iexplore.exe | GET | 200 | 142.250.185.131:80 | http://ocsp.pki.goog/gsr1/MFEwTzBNMEswSTAJBgUrDgMCGgUABBS3V7W2nAf4FiMTjpDJKg6%2BMgGqMQQUYHtmGkUNl8qJUC99BM00qP%2F8%2FUsCEHe9DWzbNvka6iEPxPBY0w0%3D | US | der | 1.41 Kb | whitelisted |
3336 | iexplore.exe | GET | 200 | 142.250.185.131:80 | http://ocsp.pki.goog/gts1c3/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBTHLnmK3f9hNLO67UdCuLvGwCQHYwQUinR%2Fr4XN7pXNPZzQ4kYU83E1HScCEQCCPD%2BmI1IjpApTbalFlJFC | US | der | 472 b | whitelisted |
3336 | iexplore.exe | GET | 200 | 142.250.185.131:80 | http://ocsp.pki.goog/gts1c3/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBTHLnmK3f9hNLO67UdCuLvGwCQHYwQUinR%2Fr4XN7pXNPZzQ4kYU83E1HScCEQDZVQ0c3n%2F16xKL4oJJTrDj | US | der | 472 b | whitelisted |
3336 | iexplore.exe | GET | 200 | 142.250.185.131:80 | http://ocsp.pki.goog/gts1c3/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTHLnmK3f9hNLO67UdCuLvGwCQHYwQUinR%2Fr4XN7pXNPZzQ4kYU83E1HScCEGw1Yik%2BBw9wCsFmPcXqpzQ%3D | US | der | 471 b | whitelisted |
1096 | svchost.exe | GET | 200 | 67.27.233.126:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab?5ace26a206ec6551 | US | compressed | 59.5 Kb | whitelisted |
1332 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAqvpsXKY8RRQeo74ffHUxc%3D | US | der | 471 b | whitelisted |
3480 | ftewk.exe | GET | 200 | 193.106.191.201:80 | http://193.106.191.201/temps/KMS.exe | RU | executable | 99.9 Kb | malicious |
3480 | ftewk.exe | POST | 200 | 193.106.191.201:80 | http://193.106.191.201/panelis/index.php | RU | executable | 99.9 Kb | malicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
1332 | iexplore.exe | 131.253.33.200:443 | www.bing.com | Microsoft Corporation | US | whitelisted |
1332 | iexplore.exe | 93.184.220.29:80 | ocsp.digicert.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
3336 | iexplore.exe | 8.248.145.254:80 | ctldl.windowsupdate.com | Level 3 Communications, Inc. | US | suspicious |
3336 | iexplore.exe | 142.250.185.174:443 | translate.google.com | Google Inc. | US | whitelisted |
1332 | iexplore.exe | 152.199.19.161:443 | iecvlist.microsoft.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
3336 | iexplore.exe | 142.250.186.163:443 | www.gstatic.com | Google Inc. | US | whitelisted |
1332 | iexplore.exe | 204.79.197.200:443 | ieonline.microsoft.com | Microsoft Corporation | US | whitelisted |
3336 | iexplore.exe | 142.250.185.131:80 | ocsp.pki.goog | Google Inc. | US | whitelisted |
3336 | iexplore.exe | 216.58.212.138:443 | translate.googleapis.com | Google Inc. | US | whitelisted |
1332 | iexplore.exe | 131.253.33.203:443 | www.msn.com | Microsoft Corporation | US | malicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
officialkmspico.net |
| malicious |
ctldl.windowsupdate.com |
| whitelisted |
api.bing.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
translate.google.com |
| whitelisted |
ocsp.pki.goog |
| whitelisted |
translate.googleapis.com |
| whitelisted |
iecvlist.microsoft.com |
| whitelisted |
r20swj13mr.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
3480 | ftewk.exe | A Network Trojan was detected | ET TROJAN Amadey CnC Check-In |
3480 | ftewk.exe | A Network Trojan was detected | AV TROJAN Agent.DHOA System Info Exfiltration |
3480 | ftewk.exe | A Network Trojan was detected | ET INFO Executable Download from dotted-quad Host |
3480 | ftewk.exe | Potential Corporate Privacy Violation | AV POLICY HTTP request for .exe file with no User-Agent |
3480 | ftewk.exe | Potential Corporate Privacy Violation | ET POLICY PE EXE or DLL Windows file download HTTP |
3480 | ftewk.exe | Potentially Bad Traffic | ET INFO Executable Retrieved With Minimal HTTP Headers - Potential Second Stage Download |
3480 | ftewk.exe | Potentially Bad Traffic | ET INFO SUSPICIOUS Dotted Quad Host MZ Response |
3480 | ftewk.exe | A Network Trojan was detected | ET INFO Executable Download from dotted-quad Host |
3480 | ftewk.exe | Potential Corporate Privacy Violation | AV POLICY HTTP request for .exe file with no User-Agent |
3480 | ftewk.exe | Potentially Bad Traffic | ET INFO Executable Retrieved With Minimal HTTP Headers - Potential Second Stage Download |
6 ETPRO signatures available at the full report