| File name: | Setup_x32_x64.exe |
| Full analysis: | https://app.any.run/tasks/0d85380f-7dbf-4e32-95ef-712accab5bd0 |
| Verdict: | Malicious activity |
| Threats: | Amadey is a formidable Windows infostealer threat, characterized by its persistence mechanisms, modular design, and ability to execute various malicious tasks. |
| Analysis date: | March 22, 2022, 13:58:08 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | 5F7F42F26F25E4E7342C00E05C0176FA |
| SHA1: | 582EA6AA20547C8B7F83CECCBA5B3B4B1E7E4FB7 |
| SHA256: | 9E719C4DD5E1086D5197FDED7B8CDB0D3D592C0636B0D469FCDA22C9723E8E7C |
| SSDEEP: | 49152:PbA37xyPeKsyMV/mmzApSr+EHgHjCLZsMbGEpD6e3h3igtpz+vDzfvmWvoDH:PbReKyAugDmZsMwO3TpgfuWvQ |
MALICIOUS
Drops executable file immediately after starts
- Setup_x32_x64.exe (PID: 3012)
Application was dropped or rewritten from another process
- Folder.exe (PID: 1604)
- RobCleanerInstl3183813.exe (PID: 1804)
- Proxyupd.exe (PID: 4092)
- askinstall49.exe (PID: 3548)
- File.exe (PID: 708)
- soft.exe (PID: 1936)
- askinstall49.exe (PID: 2804)
- Folder.exe (PID: 2280)
- File.exe (PID: 2512)
- PW0WLh6YZ_dCLZUayMLGyWfM.exe (PID: 3864)
- NEsLEJpE0wKbPH4IWwZhky8R.exe (PID: 2784)
- yVSnPqRiWe5CswULdAN9vGHf.exe (PID: 3444)
- uUvoYU8dJrs6U_oslimV867q.exe (PID: 2288)
- FJtI2GgpnJEqRavEzo2a1FMK.exe (PID: 1816)
- f_4l3dKZ6pC1iNnv7uRNnXhe.exe (PID: 148)
- X54s7M70hFmVLNENqC_WFdeN.exe (PID: 3092)
- XVTyDggBcQCQsrnL_DCVS1iP.exe (PID: 3804)
- liBeXyQz2IRPmiQ9SL5CRMm4.exe (PID: 2364)
- uweCikF1Cr8pyOaF4lecXboQ.exe (PID: 3776)
- NEsLEJpE0wKbPH4IWwZhky8R.exe (PID: 3252)
- LU1cVXFzEPxXpAsSbaYOXnz_.exe (PID: 2020)
- gz5mJGP0o9zTrbeg89cfvWMt.exe (PID: 1208)
- Z2QT8bmXh4Yxzpm5bQgSwgTf.exe (PID: 3556)
- F6GaRp4fdSLSovjPtJ2pK5ND.exe (PID: 2252)
- ORbKVDT2Q2mnCcZRgw0hQCjJ.exe (PID: 2340)
- TCDBMQb3nWU_rqv_mo30TAym.exe (PID: 2448)
- TCDBMQb3nWU_rqv_mo30TAym.exe (PID: 2760)
- OIQ3ohNp0oi50H6WQy1uhXgW.exe (PID: 4032)
- Install.exe (PID: 3100)
- PchNaL_nYxYGcJlgr8iP0tk9.exe (PID: 2260)
- 41sAxw_EMLtldZnyfnXa1N_c.exe (PID: 1836)
- WBH27Y1LzlzgUKrYU_yyuGOi.exe (PID: 3928)
- WfLMpH8HrM4pDVtBM8YF9JeG.exe (PID: 3888)
- 7SijbG1nGYVUagKdcsW8zzna.exe (PID: 396)
- TCDBMQb3nWU_rqv_mo30TAym.exe (PID: 816)
- VBgTiPzsrJbg1BiunuWqgaJ1.exe (PID: 2160)
- 4HOldoFEqb4SeExNBuf53Kke.exe (PID: 4048)
- fohHm_OrSSocl3ne_rbZp1u0.exe (PID: 3532)
- nLsxya0gqI3yiD2BII7P7WWi.exe (PID: 2156)
- hMDGak25OXsdDytQAsjkWRBr.exe (PID: 3436)
- TCDBMQb3nWU_rqv_mo30TAym.exe (PID: 1016)
- 66695461001.exe (PID: 1996)
- build2.exe (PID: 3356)
- 56849151356.exe (PID: 1876)
- build2.exe (PID: 3756)
- neofimel.exe (PID: 1752)
- Install.exe (PID: 1980)
- Cjkcanhwcmax1.exe (PID: 2252)
Known privilege escalation attack
- DllHost.exe (PID: 2372)
Changes settings of System certificates
- askinstall49.exe (PID: 2804)
- File.exe (PID: 2512)
- yVSnPqRiWe5CswULdAN9vGHf.exe (PID: 3444)
- rundll32.exe (PID: 2104)
- LU1cVXFzEPxXpAsSbaYOXnz_.exe (PID: 2020)
REDLINE was detected
- soft.exe (PID: 1936)
- AppLaunch.exe (PID: 2168)
- uweCikF1Cr8pyOaF4lecXboQ.exe (PID: 3776)
- X54s7M70hFmVLNENqC_WFdeN.exe (PID: 3092)
- XVTyDggBcQCQsrnL_DCVS1iP.exe (PID: 3804)
- liBeXyQz2IRPmiQ9SL5CRMm4.exe (PID: 2364)
- ORbKVDT2Q2mnCcZRgw0hQCjJ.exe (PID: 2340)
- OIQ3ohNp0oi50H6WQy1uhXgW.exe (PID: 4032)
- PchNaL_nYxYGcJlgr8iP0tk9.exe (PID: 2260)
- AppLaunch.exe (PID: 3444)
- AppLaunch.exe (PID: 2584)
- AppLaunch.exe (PID: 1036)
- AppLaunch.exe (PID: 2764)
- AppLaunch.exe (PID: 3956)
- RegAsm.exe (PID: 3596)
- MSBuild.exe (PID: 3448)
- neofimel.exe (PID: 1752)
Connects to CnC server
- soft.exe (PID: 1936)
- File.exe (PID: 2512)
- AppLaunch.exe (PID: 2168)
- X54s7M70hFmVLNENqC_WFdeN.exe (PID: 3092)
- uweCikF1Cr8pyOaF4lecXboQ.exe (PID: 3776)
- XVTyDggBcQCQsrnL_DCVS1iP.exe (PID: 3804)
- liBeXyQz2IRPmiQ9SL5CRMm4.exe (PID: 2364)
- NEsLEJpE0wKbPH4IWwZhky8R.exe (PID: 3252)
- yVSnPqRiWe5CswULdAN9vGHf.exe (PID: 3444)
- ORbKVDT2Q2mnCcZRgw0hQCjJ.exe (PID: 2340)
- OIQ3ohNp0oi50H6WQy1uhXgW.exe (PID: 4032)
- PchNaL_nYxYGcJlgr8iP0tk9.exe (PID: 2260)
- AppLaunch.exe (PID: 3444)
- AppLaunch.exe (PID: 2584)
- AppLaunch.exe (PID: 1036)
- AppLaunch.exe (PID: 2764)
- AppLaunch.exe (PID: 3956)
- Z2QT8bmXh4Yxzpm5bQgSwgTf.exe (PID: 3556)
- RegAsm.exe (PID: 3596)
- neofimel.exe (PID: 1752)
- explorer.exe (PID: 3624)
- MSBuild.exe (PID: 3448)
- rundll32.exe (PID: 816)
Disables Windows Defender
- File.exe (PID: 2512)
SOCELARS was detected
- File.exe (PID: 2512)
Actions looks like stealing of personal data
- uweCikF1Cr8pyOaF4lecXboQ.exe (PID: 3776)
- X54s7M70hFmVLNENqC_WFdeN.exe (PID: 3092)
- AppLaunch.exe (PID: 2168)
- XVTyDggBcQCQsrnL_DCVS1iP.exe (PID: 3804)
- liBeXyQz2IRPmiQ9SL5CRMm4.exe (PID: 2364)
- rundll32.exe (PID: 2104)
- OIQ3ohNp0oi50H6WQy1uhXgW.exe (PID: 4032)
- LU1cVXFzEPxXpAsSbaYOXnz_.exe (PID: 2020)
- PchNaL_nYxYGcJlgr8iP0tk9.exe (PID: 2260)
- AppLaunch.exe (PID: 1036)
- AppLaunch.exe (PID: 3956)
- AppLaunch.exe (PID: 2764)
- AppLaunch.exe (PID: 2584)
- RegAsm.exe (PID: 3596)
- ORbKVDT2Q2mnCcZRgw0hQCjJ.exe (PID: 2340)
- AppLaunch.exe (PID: 3444)
- neofimel.exe (PID: 1752)
- MSBuild.exe (PID: 3448)
- rundll32.exe (PID: 816)
Steals credentials from Web Browsers
- AppLaunch.exe (PID: 2168)
- uweCikF1Cr8pyOaF4lecXboQ.exe (PID: 3776)
- X54s7M70hFmVLNENqC_WFdeN.exe (PID: 3092)
- XVTyDggBcQCQsrnL_DCVS1iP.exe (PID: 3804)
- liBeXyQz2IRPmiQ9SL5CRMm4.exe (PID: 2364)
- rundll32.exe (PID: 2104)
- LU1cVXFzEPxXpAsSbaYOXnz_.exe (PID: 2020)
- OIQ3ohNp0oi50H6WQy1uhXgW.exe (PID: 4032)
- PchNaL_nYxYGcJlgr8iP0tk9.exe (PID: 2260)
- AppLaunch.exe (PID: 2584)
- RegAsm.exe (PID: 3596)
- ORbKVDT2Q2mnCcZRgw0hQCjJ.exe (PID: 2340)
- AppLaunch.exe (PID: 3444)
- AppLaunch.exe (PID: 3956)
- AppLaunch.exe (PID: 1036)
- AppLaunch.exe (PID: 2764)
- neofimel.exe (PID: 1752)
- MSBuild.exe (PID: 3448)
Writes to a start menu file
- NEsLEJpE0wKbPH4IWwZhky8R.exe (PID: 2784)
- fohHm_OrSSocl3ne_rbZp1u0.exe (PID: 3532)
DANABOT was detected
- rundll32.exe (PID: 2104)
AMADEY was detected
- NEsLEJpE0wKbPH4IWwZhky8R.exe (PID: 3252)
Uses SVCHOST.EXE for hidden code execution
- gz5mJGP0o9zTrbeg89cfvWMt.exe (PID: 1208)
Runs app for hidden code execution
- cmd.exe (PID: 3568)
Uses TASKLIST.EXE to search for antiviruses
- cmd.exe (PID: 3108)
Uses Task Scheduler to run other applications
- yVSnPqRiWe5CswULdAN9vGHf.exe (PID: 3444)
- Install.exe (PID: 1980)
- rundll32.exe (PID: 2104)
Uses Task Scheduler to autorun other applications
- yVSnPqRiWe5CswULdAN9vGHf.exe (PID: 3444)
Loads the Task Scheduler COM API
- schtasks.exe (PID: 2432)
- schtasks.exe (PID: 3152)
- TCDBMQb3nWU_rqv_mo30TAym.exe (PID: 2760)
- schtasks.exe (PID: 2024)
- schtasks.exe (PID: 3312)
- TCDBMQb3nWU_rqv_mo30TAym.exe (PID: 1016)
- WerFault.exe (PID: 2488)
- schtasks.exe (PID: 2156)
- schtasks.exe (PID: 2108)
- schtasks.exe (PID: 1644)
- Explorer.EXE (PID: 3480)
Changes the autorun value in the registry
- TCDBMQb3nWU_rqv_mo30TAym.exe (PID: 2760)
- explorer.exe (PID: 3624)
- reg.exe (PID: 2992)
- f_4l3dKZ6pC1iNnv7uRNnXhe.exe (PID: 148)
Loads dropped or rewritten executable
- LU1cVXFzEPxXpAsSbaYOXnz_.exe (PID: 2020)
- tasklist.exe (PID: 2320)
- AppLaunch.exe (PID: 2764)
- cmd.exe (PID: 3108)
- powershell.EXE (PID: 3200)
- 7SijbG1nGYVUagKdcsW8zzna.exe (PID: 396)
- 66695461001.exe (PID: 1996)
- conhost.exe (PID: 2716)
- WfLMpH8HrM4pDVtBM8YF9JeG.exe (PID: 3888)
- conhost.exe (PID: 3232)
- conhost.exe (PID: 284)
- schtasks.exe (PID: 3312)
- ntvdm.exe (PID: 3580)
- conhost.exe (PID: 1360)
- Setup_x32_x64.exe (PID: 3012)
- AppLaunch.exe (PID: 1036)
- consent.exe (PID: 3104)
- tasklist.exe (PID: 2708)
- WerFault.exe (PID: 2488)
- iexplore.exe (PID: 2180)
- reg.exe (PID: 3108)
- TCDBMQb3nWU_rqv_mo30TAym.exe (PID: 816)
- ORbKVDT2Q2mnCcZRgw0hQCjJ.exe (PID: 2340)
- timeout.exe (PID: 2696)
- iexplore.exe (PID: 3868)
- cmd.exe (PID: 2784)
- conhost.exe (PID: 660)
- explorer.exe (PID: 3624)
- conhost.exe (PID: 2788)
- RobCleanerInstl3183813.exe (PID: 1804)
- conhost.exe (PID: 1408)
- askinstall49.exe (PID: 3548)
- WerFault.exe (PID: 3136)
- OIQ3ohNp0oi50H6WQy1uhXgW.exe (PID: 4032)
- File.exe (PID: 2512)
- DllHost.exe (PID: 3596)
- conhost.exe (PID: 3060)
- DllHost.exe (PID: 2508)
- reg.exe (PID: 3708)
- f_4l3dKZ6pC1iNnv7uRNnXhe.exe (PID: 148)
- PchNaL_nYxYGcJlgr8iP0tk9.exe (PID: 2260)
- gz5mJGP0o9zTrbeg89cfvWMt.exe (PID: 1208)
- FJtI2GgpnJEqRavEzo2a1FMK.exe (PID: 1816)
- schtasks.exe (PID: 2432)
- Folder.exe (PID: 1604)
- cmd.exe (PID: 3568)
- rundll32.exe (PID: 2836)
- uweCikF1Cr8pyOaF4lecXboQ.exe (PID: 3776)
- Sta.exe.pif (PID: 2200)
- fohHm_OrSSocl3ne_rbZp1u0.exe (PID: 3532)
- TCDBMQb3nWU_rqv_mo30TAym.exe (PID: 2448)
- DllHost.exe (PID: 3760)
- conhost.exe (PID: 2376)
- F6GaRp4fdSLSovjPtJ2pK5ND.exe (PID: 2252)
- SearchFilterHost.exe (PID: 2680)
- schtasks.exe (PID: 3152)
- DllHost.exe (PID: 2372)
- Install.exe (PID: 3100)
- iexplore.exe (PID: 3552)
- AppLaunch.exe (PID: 2168)
- conhost.exe (PID: 2208)
- liBeXyQz2IRPmiQ9SL5CRMm4.exe (PID: 2364)
- conhost.exe (PID: 2064)
- TCDBMQb3nWU_rqv_mo30TAym.exe (PID: 1016)
- cmd.exe (PID: 3568)
- svchost.exe (PID: 2916)
- find.exe (PID: 3084)
- findstr.exe (PID: 1604)
- consent.exe (PID: 2236)
- cmd.exe (PID: 1812)
- DllHost.exe (PID: 1880)
- SearchProtocolHost.exe (PID: 2256)
- AppLaunch.exe (PID: 3956)
- Z2QT8bmXh4Yxzpm5bQgSwgTf.exe (PID: 3556)
- DllHost.exe (PID: 3832)
- conhost.exe (PID: 2644)
- yVSnPqRiWe5CswULdAN9vGHf.exe (PID: 3444)
- AppLaunch.exe (PID: 2584)
- Proxyupd.exe (PID: 4092)
- forfiles.exe (PID: 3332)
- conhost.exe (PID: 1596)
- PW0WLh6YZ_dCLZUayMLGyWfM.exe (PID: 3864)
- DllHost.exe (PID: 1860)
- conhost.exe (PID: 2144)
- soft.exe (PID: 1936)
- VBgTiPzsrJbg1BiunuWqgaJ1.exe (PID: 2160)
- askinstall49.exe (PID: 2804)
- rundll32.exe (PID: 2516)
- timeout.exe (PID: 3084)
- 4HOldoFEqb4SeExNBuf53Kke.exe (PID: 4048)
- rundll32.exe (PID: 2104)
- find.exe (PID: 1568)
- DllHost.exe (PID: 2320)
- NEsLEJpE0wKbPH4IWwZhky8R.exe (PID: 3252)
- conhost.exe (PID: 3956)
- conhost.exe (PID: 932)
- icacls.exe (PID: 3356)
- 41sAxw_EMLtldZnyfnXa1N_c.exe (PID: 1836)
- XVTyDggBcQCQsrnL_DCVS1iP.exe (PID: 3804)
- nLsxya0gqI3yiD2BII7P7WWi.exe (PID: 2156)
- iexplore.exe (PID: 2928)
- conhost.exe (PID: 2444)
- uUvoYU8dJrs6U_oslimV867q.exe (PID: 2288)
- consent.exe (PID: 892)
- conhost.exe (PID: 3804)
- X54s7M70hFmVLNENqC_WFdeN.exe (PID: 3092)
- PING.EXE (PID: 1880)
- cmd.exe (PID: 3932)
- File.exe (PID: 708)
- TCDBMQb3nWU_rqv_mo30TAym.exe (PID: 2760)
- AppLaunch.exe (PID: 3444)
- DllHost.exe (PID: 3580)
- Install.exe (PID: 1980)
- DllHost.exe (PID: 3940)
- NEsLEJpE0wKbPH4IWwZhky8R.exe (PID: 2784)
- conhost.exe (PID: 2632)
- cmd.exe (PID: 2928)
- schtasks.exe (PID: 2024)
- conhost.exe (PID: 2652)
- svchost.exe (PID: 2640)
- conhost.exe (PID: 2968)
- hMDGak25OXsdDytQAsjkWRBr.exe (PID: 3436)
- cmd.exe (PID: 3648)
- DllHost.exe (PID: 3744)
- RegAsm.exe (PID: 3596)
- wmiprvse.exe (PID: 2480)
- Folder.exe (PID: 2280)
- forfiles.exe (PID: 3088)
- WBH27Y1LzlzgUKrYU_yyuGOi.exe (PID: 3928)
- conhost.exe (PID: 1036)
- cmd.exe (PID: 2388)
- conhost.exe (PID: 2328)
- build2.exe (PID: 3356)
- taskkill.exe (PID: 2804)
- cmd.exe (PID: 812)
- conhost.exe (PID: 2912)
- timeout.exe (PID: 1804)
- 56849151356.exe (PID: 1876)
- conhost.exe (PID: 3744)
- cmd.exe (PID: 3484)
- conhost.exe (PID: 3328)
- build2.exe (PID: 3756)
- taskkill.exe (PID: 3108)
- gpscript.exe (PID: 2536)
- svchost.exe (PID: 2280)
- DllHost.exe (PID: 2980)
- cmd.exe (PID: 2540)
- reg.exe (PID: 2992)
- gpupdate.exe (PID: 3368)
- neofimel.exe (PID: 1752)
- conhost.exe (PID: 576)
- SearchProtocolHost.exe (PID: 660)
- schtasks.exe (PID: 2108)
- conhost.exe (PID: 3356)
- conhost.exe (PID: 2652)
- DllHost.exe (PID: 2740)
- taskhost.exe (PID: 3088)
- conhost.exe (PID: 2324)
- schtasks.exe (PID: 744)
- MSBuild.exe (PID: 3448)
- Cjkcanhwcmax1.exe (PID: 2252)
- Explorer.EXE (PID: 3480)
- schtasks.exe (PID: 2156)
- DllHost.exe (PID: 2312)
- schtasks.exe (PID: 1644)
- Sta.exe.pif (PID: 2244)
- rundll32.exe (PID: 816)
Stealing of credential data
- LU1cVXFzEPxXpAsSbaYOXnz_.exe (PID: 2020)
- rundll32.exe (PID: 2104)
VIDAR was detected
- rundll32.exe (PID: 2104)
Runs injected code in another process
- explorer.exe (PID: 3624)
- fohHm_OrSSocl3ne_rbZp1u0.exe (PID: 3532)
Application was injected by another process
- Explorer.EXE (PID: 1100)
STOP was detected
- TCDBMQb3nWU_rqv_mo30TAym.exe (PID: 1016)
Loads the Task Scheduler DLL interface
- schtasks.exe (PID: 744)
SUSPICIOUS
Checks supported languages
- Setup_x32_x64.exe (PID: 3012)
- Proxyupd.exe (PID: 4092)
- soft.exe (PID: 1936)
- Folder.exe (PID: 1604)
- RobCleanerInstl3183813.exe (PID: 1804)
- conhost.exe (PID: 3232)
- askinstall49.exe (PID: 3548)
- askinstall49.exe (PID: 2804)
- Folder.exe (PID: 2280)
- conhost.exe (PID: 2652)
- File.exe (PID: 2512)
- wmiprvse.exe (PID: 2480)
- PW0WLh6YZ_dCLZUayMLGyWfM.exe (PID: 3864)
- yVSnPqRiWe5CswULdAN9vGHf.exe (PID: 3444)
- liBeXyQz2IRPmiQ9SL5CRMm4.exe (PID: 2364)
- uUvoYU8dJrs6U_oslimV867q.exe (PID: 2288)
- XVTyDggBcQCQsrnL_DCVS1iP.exe (PID: 3804)
- conhost.exe (PID: 932)
- AppLaunch.exe (PID: 2168)
- uweCikF1Cr8pyOaF4lecXboQ.exe (PID: 3776)
- f_4l3dKZ6pC1iNnv7uRNnXhe.exe (PID: 148)
- X54s7M70hFmVLNENqC_WFdeN.exe (PID: 3092)
- conhost.exe (PID: 2632)
- cmd.exe (PID: 2388)
- NEsLEJpE0wKbPH4IWwZhky8R.exe (PID: 2784)
- FJtI2GgpnJEqRavEzo2a1FMK.exe (PID: 1816)
- NEsLEJpE0wKbPH4IWwZhky8R.exe (PID: 3252)
- LU1cVXFzEPxXpAsSbaYOXnz_.exe (PID: 2020)
- conhost.exe (PID: 284)
- cmd.exe (PID: 2928)
- gz5mJGP0o9zTrbeg89cfvWMt.exe (PID: 1208)
- conhost.exe (PID: 2208)
- cmd.exe (PID: 3568)
- cmd.exe (PID: 3108)
- Z2QT8bmXh4Yxzpm5bQgSwgTf.exe (PID: 3556)
- ORbKVDT2Q2mnCcZRgw0hQCjJ.exe (PID: 2340)
- TCDBMQb3nWU_rqv_mo30TAym.exe (PID: 2448)
- Sta.exe.pif (PID: 2200)
- conhost.exe (PID: 1036)
- conhost.exe (PID: 1408)
- OIQ3ohNp0oi50H6WQy1uhXgW.exe (PID: 4032)
- WfLMpH8HrM4pDVtBM8YF9JeG.exe (PID: 3888)
- conhost.exe (PID: 1596)
- WBH27Y1LzlzgUKrYU_yyuGOi.exe (PID: 3928)
- 41sAxw_EMLtldZnyfnXa1N_c.exe (PID: 1836)
- conhost.exe (PID: 3956)
- PchNaL_nYxYGcJlgr8iP0tk9.exe (PID: 2260)
- conhost.exe (PID: 3060)
- TCDBMQb3nWU_rqv_mo30TAym.exe (PID: 2760)
- fohHm_OrSSocl3ne_rbZp1u0.exe (PID: 3532)
- nLsxya0gqI3yiD2BII7P7WWi.exe (PID: 2156)
- conhost.exe (PID: 2716)
- conhost.exe (PID: 660)
- VBgTiPzsrJbg1BiunuWqgaJ1.exe (PID: 2160)
- 7SijbG1nGYVUagKdcsW8zzna.exe (PID: 396)
- AppLaunch.exe (PID: 3444)
- conhost.exe (PID: 3804)
- 4HOldoFEqb4SeExNBuf53Kke.exe (PID: 4048)
- hMDGak25OXsdDytQAsjkWRBr.exe (PID: 3436)
- AppLaunch.exe (PID: 2764)
- AppLaunch.exe (PID: 2584)
- AppLaunch.exe (PID: 1036)
- AppLaunch.exe (PID: 3956)
- Install.exe (PID: 3100)
- Install.exe (PID: 1980)
- conhost.exe (PID: 2376)
- TCDBMQb3nWU_rqv_mo30TAym.exe (PID: 816)
- conhost.exe (PID: 2788)
- conhost.exe (PID: 1360)
- RegAsm.exe (PID: 3596)
- 66695461001.exe (PID: 1996)
- conhost.exe (PID: 2444)
- conhost.exe (PID: 2968)
- cmd.exe (PID: 3568)
- conhost.exe (PID: 2644)
- powershell.EXE (PID: 3200)
- TCDBMQb3nWU_rqv_mo30TAym.exe (PID: 1016)
- conhost.exe (PID: 2064)
- cmd.exe (PID: 2784)
- conhost.exe (PID: 2144)
- cmd.exe (PID: 1812)
- conhost.exe (PID: 2328)
- build2.exe (PID: 3356)
- cmd.exe (PID: 2540)
- conhost.exe (PID: 3744)
- conhost.exe (PID: 3328)
- cmd.exe (PID: 3484)
- 56849151356.exe (PID: 1876)
- conhost.exe (PID: 2912)
- build2.exe (PID: 3756)
- cmd.exe (PID: 812)
- conhost.exe (PID: 576)
- conhost.exe (PID: 3356)
- neofimel.exe (PID: 1752)
- conhost.exe (PID: 2652)
- conhost.exe (PID: 2324)
- Cjkcanhwcmax1.exe (PID: 2252)
- MSBuild.exe (PID: 3448)
- Sta.exe.pif (PID: 2244)
Reads the computer name
- Setup_x32_x64.exe (PID: 3012)
- Folder.exe (PID: 1604)
- soft.exe (PID: 1936)
- RobCleanerInstl3183813.exe (PID: 1804)
- askinstall49.exe (PID: 3548)
- askinstall49.exe (PID: 2804)
- Proxyupd.exe (PID: 4092)
- Folder.exe (PID: 2280)
- File.exe (PID: 2512)
- wmiprvse.exe (PID: 2480)
- yVSnPqRiWe5CswULdAN9vGHf.exe (PID: 3444)
- AppLaunch.exe (PID: 2168)
- uweCikF1Cr8pyOaF4lecXboQ.exe (PID: 3776)
- f_4l3dKZ6pC1iNnv7uRNnXhe.exe (PID: 148)
- X54s7M70hFmVLNENqC_WFdeN.exe (PID: 3092)
- NEsLEJpE0wKbPH4IWwZhky8R.exe (PID: 2784)
- XVTyDggBcQCQsrnL_DCVS1iP.exe (PID: 3804)
- liBeXyQz2IRPmiQ9SL5CRMm4.exe (PID: 2364)
- FJtI2GgpnJEqRavEzo2a1FMK.exe (PID: 1816)
- NEsLEJpE0wKbPH4IWwZhky8R.exe (PID: 3252)
- gz5mJGP0o9zTrbeg89cfvWMt.exe (PID: 1208)
- LU1cVXFzEPxXpAsSbaYOXnz_.exe (PID: 2020)
- ORbKVDT2Q2mnCcZRgw0hQCjJ.exe (PID: 2340)
- OIQ3ohNp0oi50H6WQy1uhXgW.exe (PID: 4032)
- Sta.exe.pif (PID: 2200)
- PchNaL_nYxYGcJlgr8iP0tk9.exe (PID: 2260)
- TCDBMQb3nWU_rqv_mo30TAym.exe (PID: 2760)
- AppLaunch.exe (PID: 3444)
- AppLaunch.exe (PID: 2764)
- AppLaunch.exe (PID: 2584)
- AppLaunch.exe (PID: 1036)
- nLsxya0gqI3yiD2BII7P7WWi.exe (PID: 2156)
- Z2QT8bmXh4Yxzpm5bQgSwgTf.exe (PID: 3556)
- AppLaunch.exe (PID: 3956)
- Install.exe (PID: 1980)
- fohHm_OrSSocl3ne_rbZp1u0.exe (PID: 3532)
- RegAsm.exe (PID: 3596)
- TCDBMQb3nWU_rqv_mo30TAym.exe (PID: 1016)
- powershell.EXE (PID: 3200)
- cmd.exe (PID: 2784)
- 66695461001.exe (PID: 1996)
- build2.exe (PID: 3756)
- 56849151356.exe (PID: 1876)
- neofimel.exe (PID: 1752)
- MSBuild.exe (PID: 3448)
Drops a file that was compiled in debug mode
- Setup_x32_x64.exe (PID: 3012)
- File.exe (PID: 2512)
- NEsLEJpE0wKbPH4IWwZhky8R.exe (PID: 2784)
- LU1cVXFzEPxXpAsSbaYOXnz_.exe (PID: 2020)
- TCDBMQb3nWU_rqv_mo30TAym.exe (PID: 2760)
- Z2QT8bmXh4Yxzpm5bQgSwgTf.exe (PID: 3556)
- fohHm_OrSSocl3ne_rbZp1u0.exe (PID: 3532)
- Sta.exe.pif (PID: 2200)
Drops a file with a compile date too recent
- Setup_x32_x64.exe (PID: 3012)
- File.exe (PID: 2512)
- NEsLEJpE0wKbPH4IWwZhky8R.exe (PID: 2784)
- AppLaunch.exe (PID: 3444)
- f_4l3dKZ6pC1iNnv7uRNnXhe.exe (PID: 148)
- AppLaunch.exe (PID: 2764)
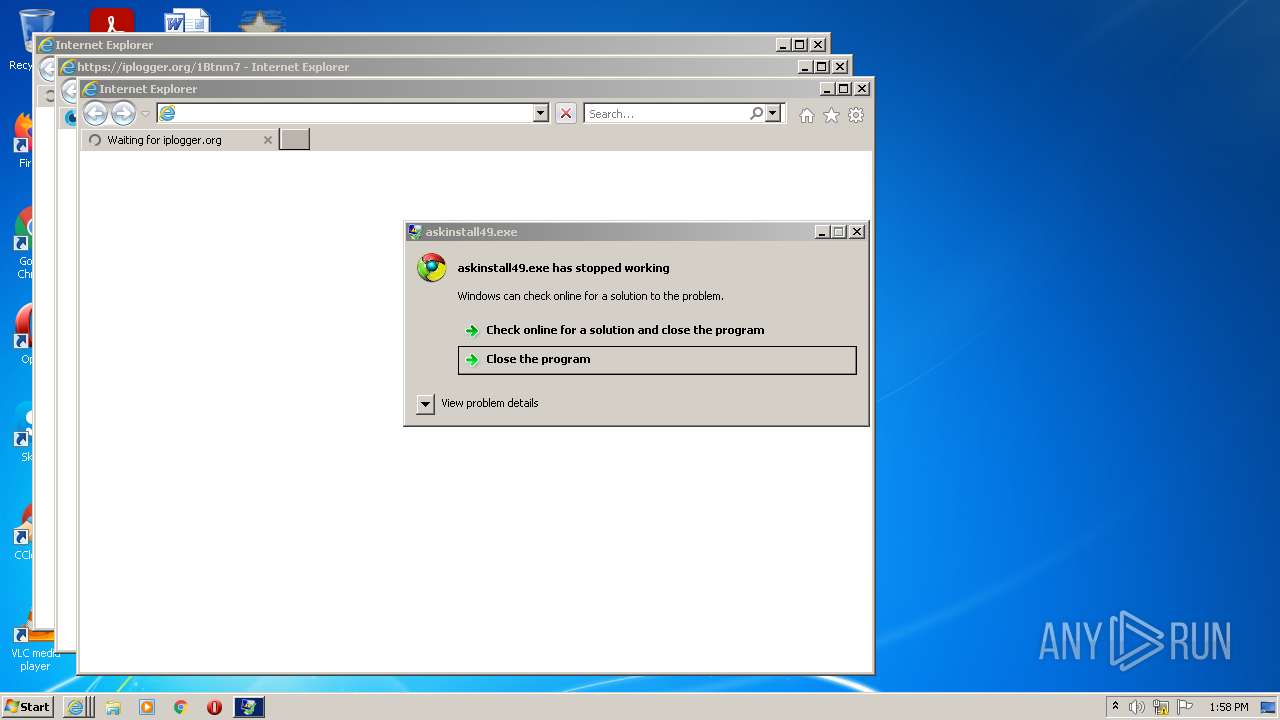
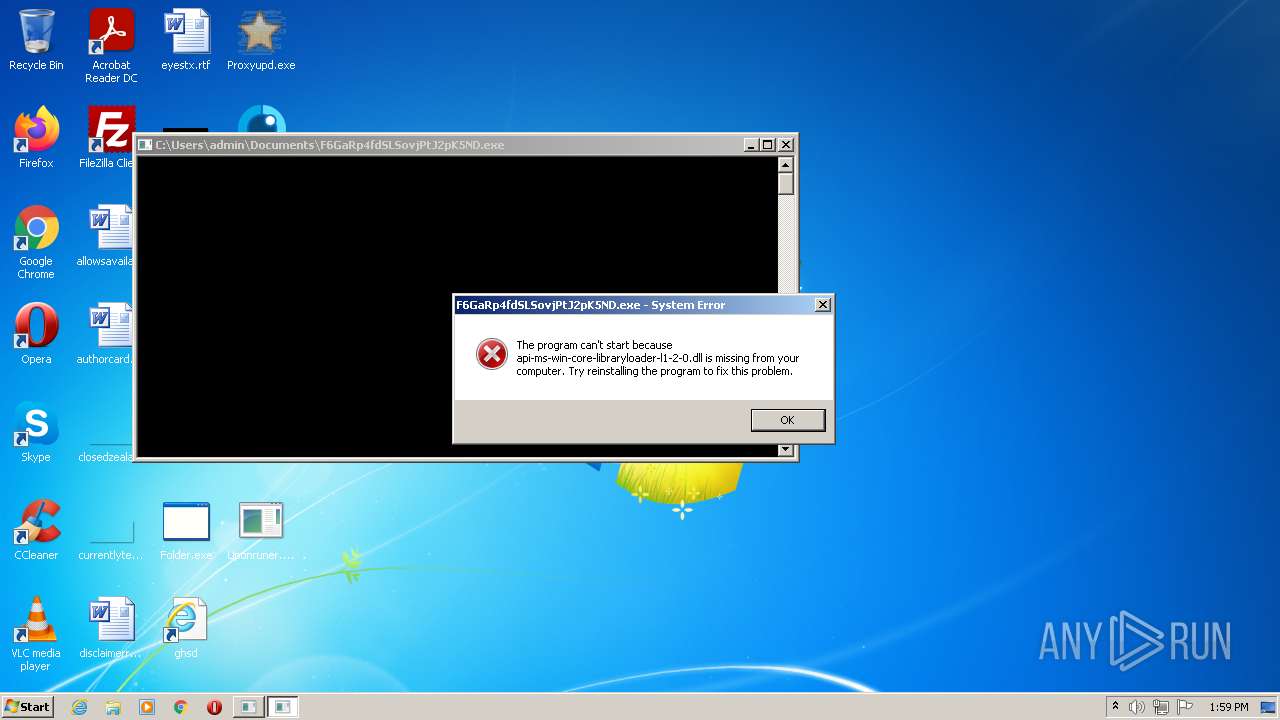
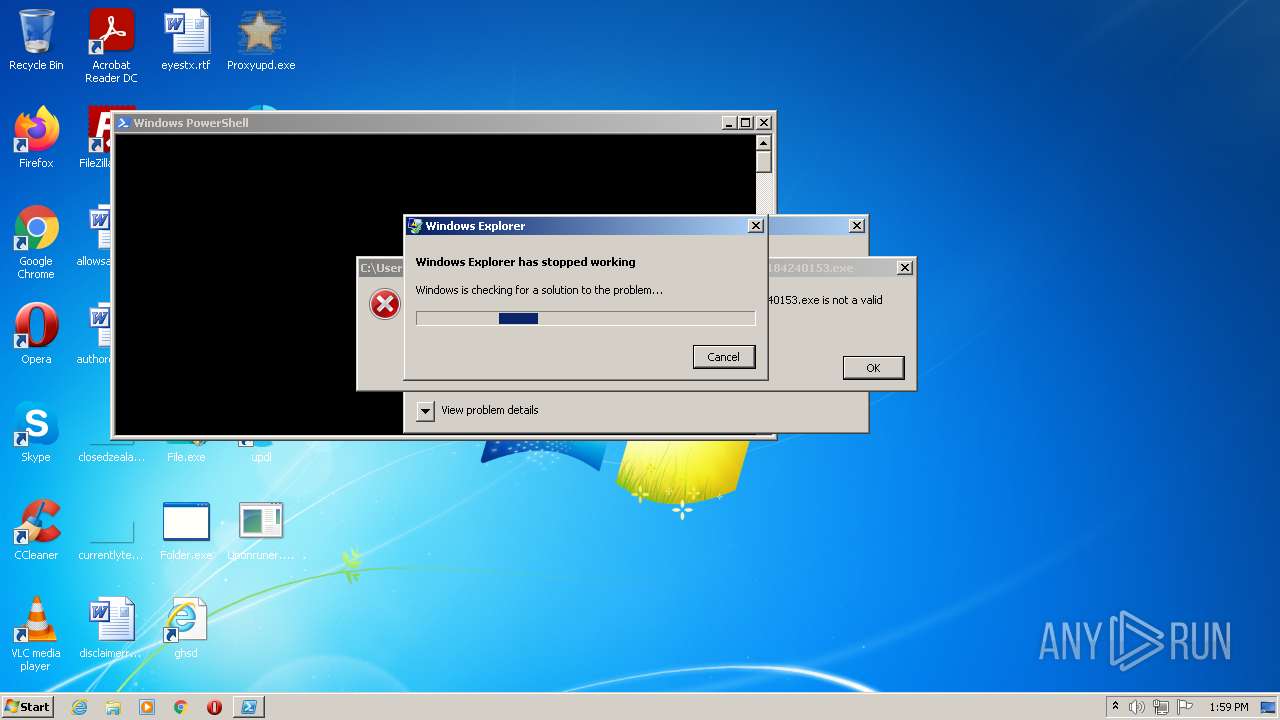
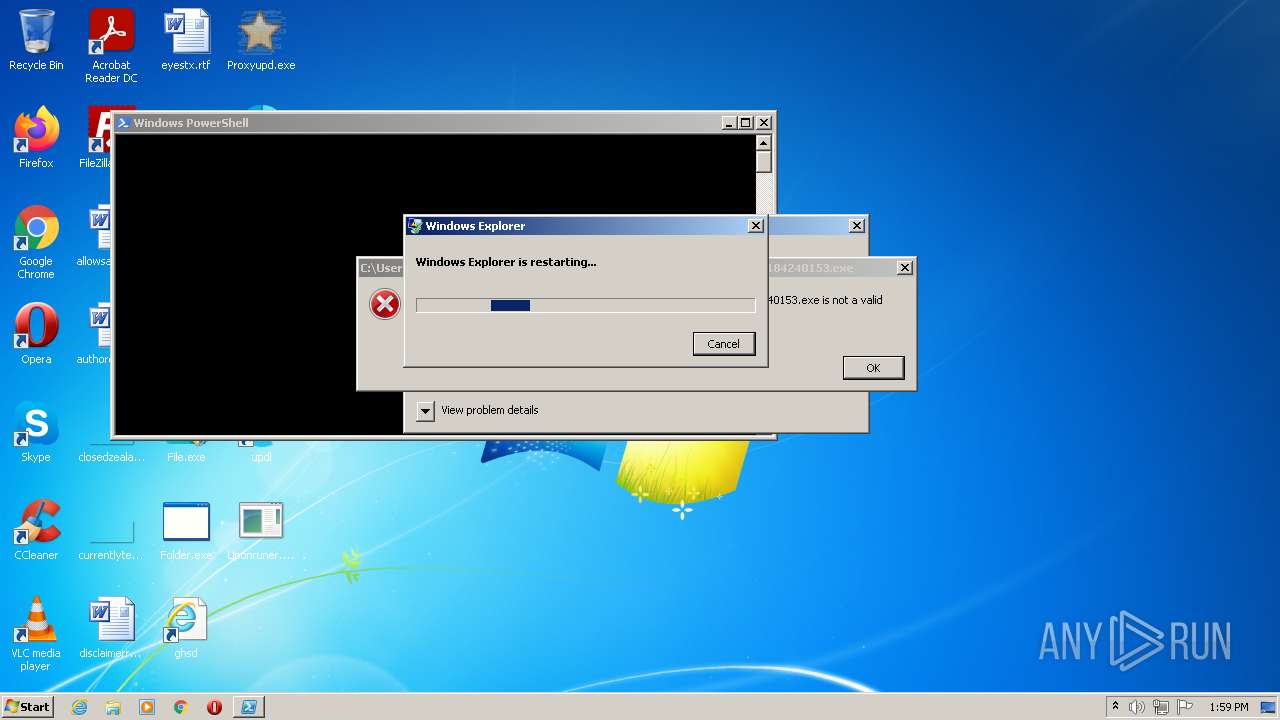
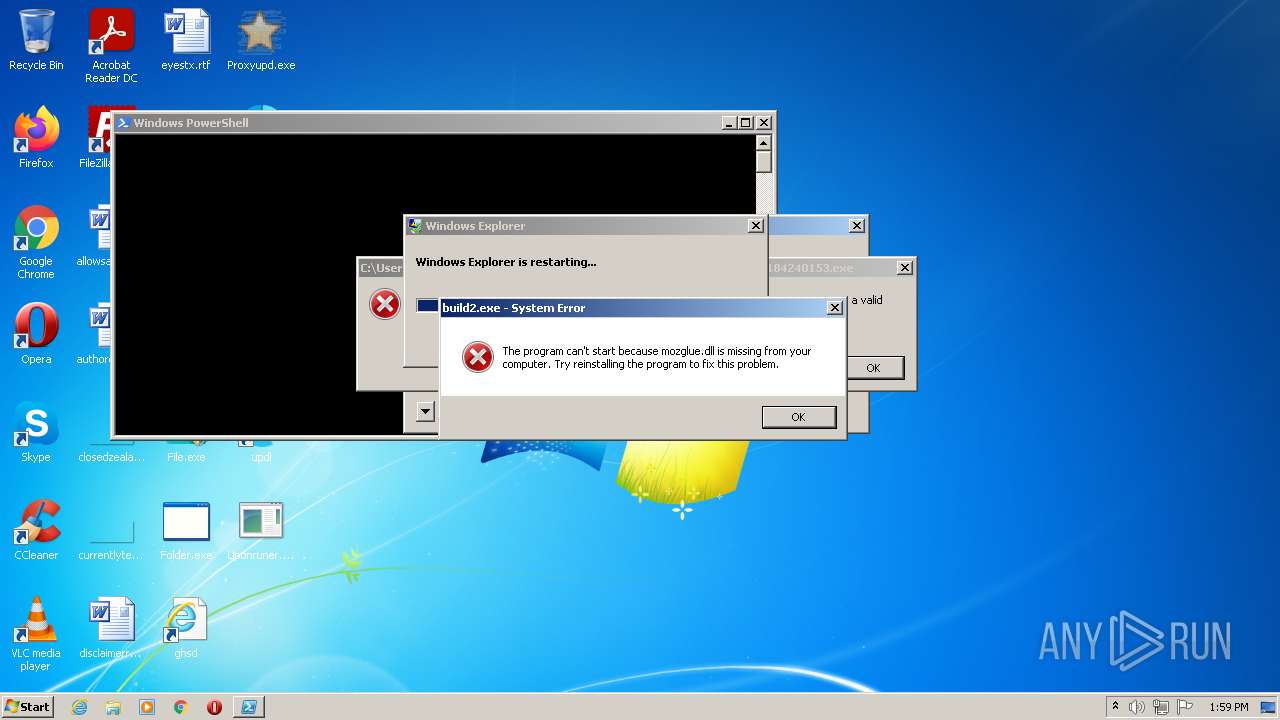
Executes application which crashes
- Setup_x32_x64.exe (PID: 3012)
Executable content was dropped or overwritten
- Setup_x32_x64.exe (PID: 3012)
- File.exe (PID: 2512)
- NEsLEJpE0wKbPH4IWwZhky8R.exe (PID: 2784)
- yVSnPqRiWe5CswULdAN9vGHf.exe (PID: 3444)
- LU1cVXFzEPxXpAsSbaYOXnz_.exe (PID: 2020)
- WfLMpH8HrM4pDVtBM8YF9JeG.exe (PID: 3888)
- TCDBMQb3nWU_rqv_mo30TAym.exe (PID: 2760)
- Z2QT8bmXh4Yxzpm5bQgSwgTf.exe (PID: 3556)
- fohHm_OrSSocl3ne_rbZp1u0.exe (PID: 3532)
- AppLaunch.exe (PID: 3444)
- Install.exe (PID: 1980)
- NEsLEJpE0wKbPH4IWwZhky8R.exe (PID: 3252)
- f_4l3dKZ6pC1iNnv7uRNnXhe.exe (PID: 148)
- Sta.exe.pif (PID: 2200)
- AppLaunch.exe (PID: 2764)
Executed via COM
- iexplore.exe (PID: 3868)
- DllHost.exe (PID: 2372)
- DllHost.exe (PID: 2312)
Reads Microsoft Outlook installation path
- iexplore.exe (PID: 3552)
- iexplore.exe (PID: 2928)
- iexplore.exe (PID: 2180)
- rundll32.exe (PID: 2104)
Reads Windows owner or organization settings
- soft.exe (PID: 1936)
- wmiprvse.exe (PID: 2480)
- FJtI2GgpnJEqRavEzo2a1FMK.exe (PID: 1816)
- rundll32.exe (PID: 2104)
Reads Environment values
- RobCleanerInstl3183813.exe (PID: 1804)
- WerFault.exe (PID: 3136)
- NEsLEJpE0wKbPH4IWwZhky8R.exe (PID: 2784)
- uweCikF1Cr8pyOaF4lecXboQ.exe (PID: 3776)
- AppLaunch.exe (PID: 2168)
- X54s7M70hFmVLNENqC_WFdeN.exe (PID: 3092)
- XVTyDggBcQCQsrnL_DCVS1iP.exe (PID: 3804)
- FJtI2GgpnJEqRavEzo2a1FMK.exe (PID: 1816)
- liBeXyQz2IRPmiQ9SL5CRMm4.exe (PID: 2364)
- rundll32.exe (PID: 2104)
- f_4l3dKZ6pC1iNnv7uRNnXhe.exe (PID: 148)
- nLsxya0gqI3yiD2BII7P7WWi.exe (PID: 2156)
- PchNaL_nYxYGcJlgr8iP0tk9.exe (PID: 2260)
- OIQ3ohNp0oi50H6WQy1uhXgW.exe (PID: 4032)
- AppLaunch.exe (PID: 3444)
- ORbKVDT2Q2mnCcZRgw0hQCjJ.exe (PID: 2340)
- LU1cVXFzEPxXpAsSbaYOXnz_.exe (PID: 2020)
- AppLaunch.exe (PID: 3956)
- AppLaunch.exe (PID: 1036)
- AppLaunch.exe (PID: 2584)
- AppLaunch.exe (PID: 2764)
- RegAsm.exe (PID: 3596)
- WerFault.exe (PID: 2488)
- 56849151356.exe (PID: 1876)
- neofimel.exe (PID: 1752)
- MSBuild.exe (PID: 3448)
Adds / modifies Windows certificates
- askinstall49.exe (PID: 2804)
- File.exe (PID: 2512)
- yVSnPqRiWe5CswULdAN9vGHf.exe (PID: 3444)
Application launched itself
- Folder.exe (PID: 1604)
- NEsLEJpE0wKbPH4IWwZhky8R.exe (PID: 2784)
- cmd.exe (PID: 3568)
- TCDBMQb3nWU_rqv_mo30TAym.exe (PID: 2448)
- TCDBMQb3nWU_rqv_mo30TAym.exe (PID: 2760)
- TCDBMQb3nWU_rqv_mo30TAym.exe (PID: 816)
- build2.exe (PID: 3356)
- Sta.exe.pif (PID: 2200)
Executed via WMI
- rundll32.exe (PID: 2836)
Creates files in the program directory
- WerFault.exe (PID: 3136)
- yVSnPqRiWe5CswULdAN9vGHf.exe (PID: 3444)
- LU1cVXFzEPxXpAsSbaYOXnz_.exe (PID: 2020)
- fohHm_OrSSocl3ne_rbZp1u0.exe (PID: 3532)
- build2.exe (PID: 3756)
Uses RUNDLL32.EXE to load library
- wmiprvse.exe (PID: 2480)
- FJtI2GgpnJEqRavEzo2a1FMK.exe (PID: 1816)
- NEsLEJpE0wKbPH4IWwZhky8R.exe (PID: 3252)
Creates files in the user directory
- File.exe (PID: 2512)
- NEsLEJpE0wKbPH4IWwZhky8R.exe (PID: 2784)
- rundll32.exe (PID: 2104)
- powershell.EXE (PID: 3200)
- fohHm_OrSSocl3ne_rbZp1u0.exe (PID: 3532)
- 56849151356.exe (PID: 1876)
- NEsLEJpE0wKbPH4IWwZhky8R.exe (PID: 3252)
- f_4l3dKZ6pC1iNnv7uRNnXhe.exe (PID: 148)
Starts CMD.EXE for commands execution
- f_4l3dKZ6pC1iNnv7uRNnXhe.exe (PID: 148)
- cmd.exe (PID: 3568)
- gz5mJGP0o9zTrbeg89cfvWMt.exe (PID: 1208)
- forfiles.exe (PID: 3332)
- forfiles.exe (PID: 3088)
- Z2QT8bmXh4Yxzpm5bQgSwgTf.exe (PID: 3556)
- fohHm_OrSSocl3ne_rbZp1u0.exe (PID: 3532)
- LU1cVXFzEPxXpAsSbaYOXnz_.exe (PID: 2020)
Checks for external IP
- File.exe (PID: 2512)
- yVSnPqRiWe5CswULdAN9vGHf.exe (PID: 3444)
Reads CPU info
- wmiprvse.exe (PID: 2480)
- FJtI2GgpnJEqRavEzo2a1FMK.exe (PID: 1816)
- LU1cVXFzEPxXpAsSbaYOXnz_.exe (PID: 2020)
- 56849151356.exe (PID: 1876)
Searches for installed software
- X54s7M70hFmVLNENqC_WFdeN.exe (PID: 3092)
- uweCikF1Cr8pyOaF4lecXboQ.exe (PID: 3776)
- XVTyDggBcQCQsrnL_DCVS1iP.exe (PID: 3804)
- AppLaunch.exe (PID: 2168)
- liBeXyQz2IRPmiQ9SL5CRMm4.exe (PID: 2364)
- PchNaL_nYxYGcJlgr8iP0tk9.exe (PID: 2260)
- LU1cVXFzEPxXpAsSbaYOXnz_.exe (PID: 2020)
- AppLaunch.exe (PID: 3956)
- AppLaunch.exe (PID: 2584)
- RegAsm.exe (PID: 3596)
- AppLaunch.exe (PID: 2764)
- ORbKVDT2Q2mnCcZRgw0hQCjJ.exe (PID: 2340)
- AppLaunch.exe (PID: 1036)
- AppLaunch.exe (PID: 3444)
- neofimel.exe (PID: 1752)
- OIQ3ohNp0oi50H6WQy1uhXgW.exe (PID: 4032)
- MSBuild.exe (PID: 3448)
- rundll32.exe (PID: 2104)
Reads the date of Windows installation
- wmiprvse.exe (PID: 2480)
- FJtI2GgpnJEqRavEzo2a1FMK.exe (PID: 1816)
- rundll32.exe (PID: 2104)
- powershell.EXE (PID: 3200)
- Explorer.EXE (PID: 3480)
Reads the Windows organization settings
- wmiprvse.exe (PID: 2480)
- FJtI2GgpnJEqRavEzo2a1FMK.exe (PID: 1816)
- rundll32.exe (PID: 2104)
Reads the cookies of Google Chrome
- AppLaunch.exe (PID: 2168)
- uweCikF1Cr8pyOaF4lecXboQ.exe (PID: 3776)
- X54s7M70hFmVLNENqC_WFdeN.exe (PID: 3092)
- XVTyDggBcQCQsrnL_DCVS1iP.exe (PID: 3804)
- liBeXyQz2IRPmiQ9SL5CRMm4.exe (PID: 2364)
- OIQ3ohNp0oi50H6WQy1uhXgW.exe (PID: 4032)
- PchNaL_nYxYGcJlgr8iP0tk9.exe (PID: 2260)
- AppLaunch.exe (PID: 2584)
- RegAsm.exe (PID: 3596)
- ORbKVDT2Q2mnCcZRgw0hQCjJ.exe (PID: 2340)
- AppLaunch.exe (PID: 3956)
- AppLaunch.exe (PID: 3444)
- AppLaunch.exe (PID: 1036)
- AppLaunch.exe (PID: 2764)
- neofimel.exe (PID: 1752)
- MSBuild.exe (PID: 3448)
Reads the cookies of Mozilla Firefox
- AppLaunch.exe (PID: 2168)
- uweCikF1Cr8pyOaF4lecXboQ.exe (PID: 3776)
- X54s7M70hFmVLNENqC_WFdeN.exe (PID: 3092)
- XVTyDggBcQCQsrnL_DCVS1iP.exe (PID: 3804)
- liBeXyQz2IRPmiQ9SL5CRMm4.exe (PID: 2364)
- OIQ3ohNp0oi50H6WQy1uhXgW.exe (PID: 4032)
- PchNaL_nYxYGcJlgr8iP0tk9.exe (PID: 2260)
- AppLaunch.exe (PID: 2584)
- RegAsm.exe (PID: 3596)
- ORbKVDT2Q2mnCcZRgw0hQCjJ.exe (PID: 2340)
- AppLaunch.exe (PID: 3444)
- AppLaunch.exe (PID: 1036)
- AppLaunch.exe (PID: 3956)
- AppLaunch.exe (PID: 2764)
- neofimel.exe (PID: 1752)
- MSBuild.exe (PID: 3448)
Reads Windows Product ID
- wmiprvse.exe (PID: 2480)
- FJtI2GgpnJEqRavEzo2a1FMK.exe (PID: 1816)
- rundll32.exe (PID: 2104)
Creates a directory in Program Files
- yVSnPqRiWe5CswULdAN9vGHf.exe (PID: 3444)
- fohHm_OrSSocl3ne_rbZp1u0.exe (PID: 3532)
Loads DLL from Mozilla Firefox
- rundll32.exe (PID: 2104)
Uses TASKLIST.EXE to query information about running processes
- cmd.exe (PID: 3108)
Starts application with an unusual extension
- cmd.exe (PID: 3108)
- Sta.exe.pif (PID: 2200)
Reads mouse settings
- Sta.exe.pif (PID: 2200)
Starts itself from another location
- WfLMpH8HrM4pDVtBM8YF9JeG.exe (PID: 3888)
Uses ICACLS.EXE to modify access control list
- TCDBMQb3nWU_rqv_mo30TAym.exe (PID: 2760)
Uses REG.EXE to modify Windows registry
- cmd.exe (PID: 3932)
- cmd.exe (PID: 3648)
- cmd.exe (PID: 1812)
PowerShell script executed
- powershell.EXE (PID: 3200)
Executed via Task Scheduler
- powershell.EXE (PID: 3200)
Starts CMD.EXE for self-deleting
- LU1cVXFzEPxXpAsSbaYOXnz_.exe (PID: 2020)
Uses TASKKILL.EXE to kill process
- cmd.exe (PID: 2540)
- cmd.exe (PID: 812)
Creates executable files which already exist in Windows
- WerFault.exe (PID: 2488)
Reads default file associations for system extensions
- Explorer.EXE (PID: 3480)
Executed as Windows Service
- taskhost.exe (PID: 3088)
Creates files in the Windows directory
- schtasks.exe (PID: 744)
Drops a file with too old compile date
- NEsLEJpE0wKbPH4IWwZhky8R.exe (PID: 3252)
INFO
Reads the computer name
- iexplore.exe (PID: 3552)
- DllHost.exe (PID: 2508)
- iexplore.exe (PID: 2928)
- iexplore.exe (PID: 2180)
- svchost.exe (PID: 2916)
- iexplore.exe (PID: 3868)
- consent.exe (PID: 892)
- consent.exe (PID: 2236)
- consent.exe (PID: 3104)
- DllHost.exe (PID: 1880)
- DllHost.exe (PID: 2372)
- SearchProtocolHost.exe (PID: 2256)
- WerFault.exe (PID: 3136)
- DllHost.exe (PID: 3832)
- DllHost.exe (PID: 3596)
- DllHost.exe (PID: 3940)
- DllHost.exe (PID: 3580)
- SearchFilterHost.exe (PID: 2680)
- rundll32.exe (PID: 2516)
- DllHost.exe (PID: 3760)
- rundll32.exe (PID: 2104)
- PING.EXE (PID: 1880)
- DllHost.exe (PID: 3744)
- tasklist.exe (PID: 2708)
- DllHost.exe (PID: 1860)
- tasklist.exe (PID: 2320)
- schtasks.exe (PID: 2432)
- schtasks.exe (PID: 3152)
- DllHost.exe (PID: 2320)
- icacls.exe (PID: 3356)
- schtasks.exe (PID: 2024)
- schtasks.exe (PID: 3312)
- explorer.exe (PID: 3624)
- WerFault.exe (PID: 2488)
- taskkill.exe (PID: 2804)
- gpupdate.exe (PID: 3368)
- taskkill.exe (PID: 3108)
- svchost.exe (PID: 2280)
- DllHost.exe (PID: 2980)
- Explorer.EXE (PID: 3480)
- schtasks.exe (PID: 2156)
- schtasks.exe (PID: 2108)
- DllHost.exe (PID: 2312)
- taskhost.exe (PID: 3088)
- schtasks.exe (PID: 1644)
- schtasks.exe (PID: 744)
- DllHost.exe (PID: 2740)
- SearchProtocolHost.exe (PID: 660)
- rundll32.exe (PID: 816)
Changes internet zones settings
- iexplore.exe (PID: 3868)
Checks supported languages
- DllHost.exe (PID: 2508)
- iexplore.exe (PID: 2928)
- iexplore.exe (PID: 2180)
- svchost.exe (PID: 2916)
- iexplore.exe (PID: 3868)
- ntvdm.exe (PID: 3580)
- iexplore.exe (PID: 3552)
- consent.exe (PID: 2236)
- consent.exe (PID: 3104)
- consent.exe (PID: 892)
- DllHost.exe (PID: 1880)
- DllHost.exe (PID: 2372)
- WerFault.exe (PID: 3136)
- DllHost.exe (PID: 3832)
- SearchProtocolHost.exe (PID: 2256)
- DllHost.exe (PID: 3596)
- DllHost.exe (PID: 3940)
- rundll32.exe (PID: 2836)
- SearchFilterHost.exe (PID: 2680)
- DllHost.exe (PID: 3580)
- timeout.exe (PID: 3084)
- rundll32.exe (PID: 2516)
- DllHost.exe (PID: 3760)
- rundll32.exe (PID: 2104)
- DllHost.exe (PID: 3744)
- PING.EXE (PID: 1880)
- timeout.exe (PID: 2696)
- svchost.exe (PID: 2640)
- tasklist.exe (PID: 2708)
- find.exe (PID: 3084)
- DllHost.exe (PID: 1860)
- tasklist.exe (PID: 2320)
- find.exe (PID: 1568)
- findstr.exe (PID: 1604)
- schtasks.exe (PID: 2432)
- schtasks.exe (PID: 3152)
- DllHost.exe (PID: 2320)
- icacls.exe (PID: 3356)
- forfiles.exe (PID: 3332)
- forfiles.exe (PID: 3088)
- cmd.exe (PID: 3932)
- reg.exe (PID: 3108)
- reg.exe (PID: 3708)
- cmd.exe (PID: 3648)
- schtasks.exe (PID: 2024)
- explorer.exe (PID: 3624)
- schtasks.exe (PID: 3312)
- WerFault.exe (PID: 2488)
- reg.exe (PID: 2992)
- taskkill.exe (PID: 2804)
- timeout.exe (PID: 1804)
- gpupdate.exe (PID: 3368)
- gpscript.exe (PID: 2536)
- svchost.exe (PID: 2280)
- taskkill.exe (PID: 3108)
- DllHost.exe (PID: 2980)
- Explorer.EXE (PID: 3480)
- schtasks.exe (PID: 2108)
- DllHost.exe (PID: 2312)
- schtasks.exe (PID: 2156)
- schtasks.exe (PID: 744)
- DllHost.exe (PID: 2740)
- taskhost.exe (PID: 3088)
- schtasks.exe (PID: 1644)
- SearchProtocolHost.exe (PID: 660)
- rundll32.exe (PID: 816)
Application launched itself
- iexplore.exe (PID: 3868)
Reads settings of System Certificates
- iexplore.exe (PID: 2928)
- consent.exe (PID: 3104)
- RobCleanerInstl3183813.exe (PID: 1804)
- iexplore.exe (PID: 3868)
- askinstall49.exe (PID: 2804)
- Folder.exe (PID: 2280)
- File.exe (PID: 2512)
- iexplore.exe (PID: 3552)
- iexplore.exe (PID: 2180)
- rundll32.exe (PID: 2516)
- yVSnPqRiWe5CswULdAN9vGHf.exe (PID: 3444)
- f_4l3dKZ6pC1iNnv7uRNnXhe.exe (PID: 148)
- rundll32.exe (PID: 2104)
- LU1cVXFzEPxXpAsSbaYOXnz_.exe (PID: 2020)
- TCDBMQb3nWU_rqv_mo30TAym.exe (PID: 2760)
- TCDBMQb3nWU_rqv_mo30TAym.exe (PID: 1016)
- WerFault.exe (PID: 2488)
- AppLaunch.exe (PID: 3444)
- build2.exe (PID: 3756)
Checks Windows Trust Settings
- iexplore.exe (PID: 2928)
- consent.exe (PID: 892)
- consent.exe (PID: 2236)
- consent.exe (PID: 3104)
- askinstall49.exe (PID: 2804)
- iexplore.exe (PID: 3868)
- File.exe (PID: 2512)
- iexplore.exe (PID: 3552)
- iexplore.exe (PID: 2180)
- rundll32.exe (PID: 2516)
- LU1cVXFzEPxXpAsSbaYOXnz_.exe (PID: 2020)
- TCDBMQb3nWU_rqv_mo30TAym.exe (PID: 2760)
- TCDBMQb3nWU_rqv_mo30TAym.exe (PID: 1016)
- powershell.EXE (PID: 3200)
- build2.exe (PID: 3756)
Reads internet explorer settings
- iexplore.exe (PID: 2928)
- iexplore.exe (PID: 2180)
- iexplore.exe (PID: 3552)
Creates files in the user directory
- iexplore.exe (PID: 2928)
- iexplore.exe (PID: 3552)
Reads the date of Windows installation
- iexplore.exe (PID: 3868)
Reads CPU info
- rundll32.exe (PID: 2104)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable (generic) (52.9) |
|---|---|---|
| .exe | | | Generic Win/DOS Executable (23.5) |
| .exe | | | DOS Executable Generic (23.5) |
EXIF
EXE
| Subsystem: | Windows GUI |
|---|---|
| SubsystemVersion: | 5.1 |
| ImageVersion: | - |
| OSVersion: | 5.1 |
| EntryPoint: | 0x1ec40 |
| UninitializedDataSize: | - |
| InitializedDataSize: | 143360 |
| CodeSize: | 201216 |
| LinkerVersion: | 14 |
| PEType: | PE32 |
| TimeStamp: | 2020:12:01 19:00:55+01:00 |
| MachineType: | Intel 386 or later, and compatibles |
Summary
| Architecture: | IMAGE_FILE_MACHINE_I386 |
|---|---|
| Subsystem: | IMAGE_SUBSYSTEM_WINDOWS_GUI |
| Compilation Date: | 01-Dec-2020 18:00:55 |
| Detected languages: |
|
| Debug artifacts: |
|
DOS Header
| Magic number: | MZ |
|---|---|
| Bytes on last page of file: | 0x0090 |
| Pages in file: | 0x0003 |
| Relocations: | 0x0000 |
| Size of header: | 0x0004 |
| Min extra paragraphs: | 0x0000 |
| Max extra paragraphs: | 0xFFFF |
| Initial SS value: | 0x0000 |
| Initial SP value: | 0x00B8 |
| Checksum: | 0x0000 |
| Initial IP value: | 0x0000 |
| Initial CS value: | 0x0000 |
| Overlay number: | 0x0000 |
| OEM identifier: | 0x0000 |
| OEM information: | 0x0000 |
| Address of NE header: | 0x00000118 |
PE Headers
| Signature: | PE |
|---|---|
| Machine: | IMAGE_FILE_MACHINE_I386 |
| Number of sections: | 6 |
| Time date stamp: | 01-Dec-2020 18:00:55 |
| Pointer to Symbol Table: | 0x00000000 |
| Number of symbols: | 0 |
| Size of Optional Header: | 0x00E0 |
| Characteristics: |
|
Sections
Name | Virtual Address | Virtual Size | Raw Size | Charateristics | Entropy |
|---|---|---|---|---|---|
.text | 0x00001000 | 0x000310EA | 0x00031200 | IMAGE_SCN_CNT_CODE, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ | 6.70808 |
.rdata | 0x00033000 | 0x0000A612 | 0x0000A800 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 5.22174 |
.data | 0x0003E000 | 0x00023728 | 0x00001000 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 3.70882 |
.didat | 0x00062000 | 0x00000188 | 0x00000200 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 3.29825 |
.rsrc | 0x00063000 | 0x00015168 | 0x00015200 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 6.24093 |
.reloc | 0x00079000 | 0x00002268 | 0x00002400 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_DISCARDABLE, IMAGE_SCN_MEM_READ | 6.55486 |
Resources
Title | Entropy | Size | Codepage | Language | Type |
|---|---|---|---|---|---|
1 | 5.25329 | 1875 | Latin 1 / Western European | English - United States | RT_MANIFEST |
7 | 3.1586 | 482 | Latin 1 / Western European | English - United States | RT_STRING |
8 | 3.11685 | 460 | Latin 1 / Western European | English - United States | RT_STRING |
9 | 3.11236 | 440 | Latin 1 / Western European | English - United States | RT_STRING |
10 | 2.99727 | 326 | Latin 1 / Western European | English - United States | RT_STRING |
11 | 3.2036 | 1094 | Latin 1 / Western European | English - United States | RT_STRING |
12 | 3.12889 | 358 | Latin 1 / Western European | English - United States | RT_STRING |
13 | 3.01704 | 338 | Latin 1 / Western European | English - United States | RT_STRING |
14 | 2.94627 | 266 | Latin 1 / Western European | English - United States | RT_STRING |
15 | 2.83619 | 188 | Latin 1 / Western European | English - United States | RT_STRING |
Imports
KERNEL32.dll |
USER32.dll (delay-loaded) |
gdiplus.dll |
Total processes
202
Monitored processes
168
Malicious processes
49
Suspicious processes
19
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 148 | "C:\Users\admin\Pictures\Adobe Films\f_4l3dKZ6pC1iNnv7uRNnXhe.exe" | C:\Users\admin\Pictures\Adobe Films\f_4l3dKZ6pC1iNnv7uRNnXhe.exe | File.exe | ||||||||||||
User: admin Company: PortableApps.com Integrity Level: HIGH Description: Dogecoin Core Portable (PortableApps.com Launcher) Exit code: 0 Version: 2.2.2.1 Modules
| |||||||||||||||
| 284 | \??\C:\Windows\system32\conhost.exe "-575800658233916951682807782-1948441376-2034091365-492119600-119824307-555964791" | \??\C:\Windows\system32\conhost.exe | — | csrss.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 396 | "C:\Users\admin\Pictures\Adobe Films\7SijbG1nGYVUagKdcsW8zzna.exe" | C:\Users\admin\Pictures\Adobe Films\7SijbG1nGYVUagKdcsW8zzna.exe | — | File.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 576 | \??\C:\Windows\system32\conhost.exe "-920358526-855616123-1196057151-6841093431058616484-1096674191-1821739550293156584" | \??\C:\Windows\system32\conhost.exe | — | csrss.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 660 | \??\C:\Windows\system32\conhost.exe "15935158481501894268-1767057840-14301783481796255274801264042896862126369233290" | \??\C:\Windows\system32\conhost.exe | — | csrss.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 660 | "C:\Windows\system32\SearchProtocolHost.exe" Global\UsGthrFltPipeMssGthrPipe_S-1-5-21-1302019708-1500728564-335382590-10004_ Global\UsGthrCtrlFltPipeMssGthrPipe_S-1-5-21-1302019708-1500728564-335382590-10004 1 -2147483646 "Software\Microsoft\Windows Search" "Mozilla/4.0 (compatible; MSIE 6.0; Windows NT; MS Search 4.0 Robot)" "C:\ProgramData\Microsoft\Search\Data\Temp\usgthrsvc" "DownLevelDaemon" "1" | C:\Windows\system32\SearchProtocolHost.exe | — | SearchIndexer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Windows Search Protocol Host Exit code: 0 Version: 7.00.7601.24542 (win7sp1_ldr_escrow.191209-2211) Modules
| |||||||||||||||
| 708 | "C:\Users\admin\Desktop\File.exe" | C:\Users\admin\Desktop\File.exe | — | Setup_x32_x64.exe | |||||||||||
User: admin Company: React Integrity Level: MEDIUM Description: React Dispatcher Exit code: 3221226540 Version: 1.11020.9.51 Modules
| |||||||||||||||
| 744 | schtasks /CREATE /TN "bnHoQpKIlSSCUFQrDN" /SC once /ST 14:01:00 /RU "SYSTEM" /TR "\"C:\Users\admin\AppData\Local\Temp\qXPJNMcRbBFEeomOU\igHnmwfRSHoqfpr\pOofixa.exe\" Sk /site_id 525403 /S" /V1 /F | C:\Windows\system32\schtasks.exe | — | Install.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Manages scheduled tasks Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 812 | "C:\Windows\System32\cmd.exe" /c taskkill /im "Z2QT8bmXh4Yxzpm5bQgSwgTf.exe" /f & erase "C:\Users\admin\Pictures\Adobe Films\Z2QT8bmXh4Yxzpm5bQgSwgTf.exe" & exit | C:\Windows\System32\cmd.exe | — | Z2QT8bmXh4Yxzpm5bQgSwgTf.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 816 | "C:\Users\admin\Pictures\Adobe Films\TCDBMQb3nWU_rqv_mo30TAym.exe" --Admin IsNotAutoStart IsNotTask | C:\Users\admin\Pictures\Adobe Films\TCDBMQb3nWU_rqv_mo30TAym.exe | — | TCDBMQb3nWU_rqv_mo30TAym.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
Total events
229 165
Read events
227 533
Write events
1 607
Delete events
25
Modification events
| (PID) Process: | (3012) Setup_x32_x64.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (3012) Setup_x32_x64.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (3012) Setup_x32_x64.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (3012) Setup_x32_x64.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (3012) Setup_x32_x64.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Shell Extensions\Cached |
| Operation: | write | Name: | {FBF23B40-E3F0-101B-8488-00AA003E56F8} {000214E4-0000-0000-C000-000000000046} 0xFFFF |
Value: 01000000000000006E2348E7F43DD801 | |||
| (PID) Process: | (3868) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPDaysSinceLastAutoMigration |
Value: 1 | |||
| (PID) Process: | (3868) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchLowDateTime |
Value: | |||
| (PID) Process: | (3868) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchHighDateTime |
Value: 30948852 | |||
| (PID) Process: | (3868) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateLowDateTime |
Value: | |||
| (PID) Process: | (3868) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 30948852 | |||
Executable files
81
Suspicious files
70
Text files
58
Unknown types
56
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2928 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\77EC63BDA74BD0D0E0426DC8F8008506 | binary | |
MD5:— | SHA256:— | |||
| 2928 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\77EC63BDA74BD0D0E0426DC8F8008506 | compressed | |
MD5:— | SHA256:— | |||
| 2928 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | binary | |
MD5:— | SHA256:— | |||
| 2928 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\Low\Tar9920.tmp | cat | |
MD5:— | SHA256:— | |||
| 1804 | RobCleanerInstl3183813.exe | C:\Users\admin\AppData\Local\Temp\Cab994E.tmp | compressed | |
MD5:— | SHA256:— | |||
| 2928 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\Low\Cab991F.tmp | compressed | |
MD5:— | SHA256:— | |||
| 1804 | RobCleanerInstl3183813.exe | C:\Users\admin\AppData\Local\Temp\Tar994F.tmp | cat | |
MD5:— | SHA256:— | |||
| 3012 | Setup_x32_x64.exe | C:\Users\admin\Desktop\updl.url | url | |
MD5:63ECA19A06A3306A8809412209B18736 | SHA256:3B36FB19771EF78578C65167A7718441208E84DDFA8C172A25DC544759B8BB31 | |||
| 3012 | Setup_x32_x64.exe | C:\Users\admin\Desktop\ghsd.url | url | |
MD5:1A83DE9519636DD32D9BFEBAB86931AE | SHA256:232F93603256C390B8C9447F2CA528BC50B859831189B0EF4E57A2E4B5A79369 | |||
| 3012 | Setup_x32_x64.exe | C:\Users\admin\Desktop\RobCleanerInstl3183813.exe | executable | |
MD5:3D84583F1C9579C143908CD10995192D | SHA256:6D42D81B33383DEC14C27239B249849101FAF172A6B3BC9C6CB460F299BD5309 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
101
TCP/UDP connections
241
DNS requests
52
Threats
525
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2512 | File.exe | HEAD | 200 | 45.144.225.57:80 | http://45.144.225.57/download/NiceProcessX32.bmp | unknown | — | — | malicious |
2512 | File.exe | HEAD | 404 | 212.193.30.29:80 | http://212.193.30.29/WW/file4.exe | RU | — | — | malicious |
2512 | File.exe | HEAD | 200 | 45.144.225.57:80 | http://45.144.225.57/download/Service.bmp | unknown | — | — | malicious |
2512 | File.exe | HEAD | 200 | 212.193.30.29:80 | http://212.193.30.29/WW/file1.exe | RU | — | — | malicious |
2512 | File.exe | HEAD | 404 | 45.144.225.57:80 | http://45.144.225.57/EU/accid125eu.exe | unknown | — | — | malicious |
2512 | File.exe | HEAD | 200 | 45.144.225.57:80 | http://45.144.225.57/EU/filename1kEu.exe | unknown | — | — | malicious |
2928 | iexplore.exe | GET | 200 | 8.248.133.254:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab?5ec9cc3ab195ab55 | US | compressed | 59.5 Kb | whitelisted |
2512 | File.exe | GET | 400 | 212.193.30.45:80 | http://212.193.30.45/proxies.txt | RU | html | 301 b | malicious |
2512 | File.exe | GET | 400 | 45.144.225.57:80 | http://45.144.225.57/server.txt | unknown | html | 301 b | malicious |
2512 | File.exe | GET | 200 | 45.144.225.57:80 | http://45.144.225.57/download/NiceProcessX32.bmp | unknown | executable | 259 Kb | malicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2928 | iexplore.exe | 148.251.234.83:443 | iplogger.org | Hetzner Online GmbH | DE | malicious |
3552 | iexplore.exe | 148.251.234.83:443 | iplogger.org | Hetzner Online GmbH | DE | malicious |
2180 | iexplore.exe | 148.251.234.83:443 | iplogger.org | Hetzner Online GmbH | DE | malicious |
2928 | iexplore.exe | 8.248.133.254:80 | ctldl.windowsupdate.com | Level 3 Communications, Inc. | US | malicious |
4092 | Proxyupd.exe | 78.46.137.240:21314 | — | Hetzner Online GmbH | DE | malicious |
1936 | soft.exe | 81.177.49.219:80 | — | JSC RTComm.RU | RU | malicious |
1804 | RobCleanerInstl3183813.exe | 188.114.96.7:443 | dpcapps.me | Cloudflare Inc | US | malicious |
2804 | askinstall49.exe | 148.251.234.83:443 | iplogger.org | Hetzner Online GmbH | DE | malicious |
3868 | iexplore.exe | 204.79.197.200:443 | www.bing.com | Microsoft Corporation | US | whitelisted |
3868 | iexplore.exe | 93.184.220.29:80 | ocsp.digicert.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
iplogger.org |
| shared |
ctldl.windowsupdate.com |
| whitelisted |
dpcapps.me |
| malicious |
api.bing.com |
| whitelisted |
www.bing.com |
| whitelisted |
www.listincode.com |
| whitelisted |
x1.c.lencr.org |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
gp.gamebuy768.com |
| malicious |
pastebin.com |
| malicious |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2512 | File.exe | A Network Trojan was detected | ET MALWARE User-Agent (???) |
2512 | File.exe | Potentially Bad Traffic | ET INFO Terse Request for .txt - Likely Hostile |
2512 | File.exe | Potentially Bad Traffic | ET INFO Terse Request for .txt - Likely Hostile |
2512 | File.exe | A Network Trojan was detected | ET MALWARE User-Agent (???) |
2512 | File.exe | Generic Protocol Command Decode | SURICATA Applayer Mismatch protocol both directions |
2512 | File.exe | A Network Trojan was detected | ET MALWARE User-Agent (???) |
2512 | File.exe | Generic Protocol Command Decode | SURICATA Applayer Mismatch protocol both directions |
2512 | File.exe | A Network Trojan was detected | ET POLICY Possible External IP Lookup Domain Observed in SNI (ipinfo. io) |
2512 | File.exe | Potential Corporate Privacy Violation | ET POLICY Possible External IP Lookup SSL Cert Observed (ipinfo.io) |
2512 | File.exe | A Network Trojan was detected | ET TROJAN Win32/Spy.Socelars.S CnC Activity M3 |
297 ETPRO signatures available at the full report