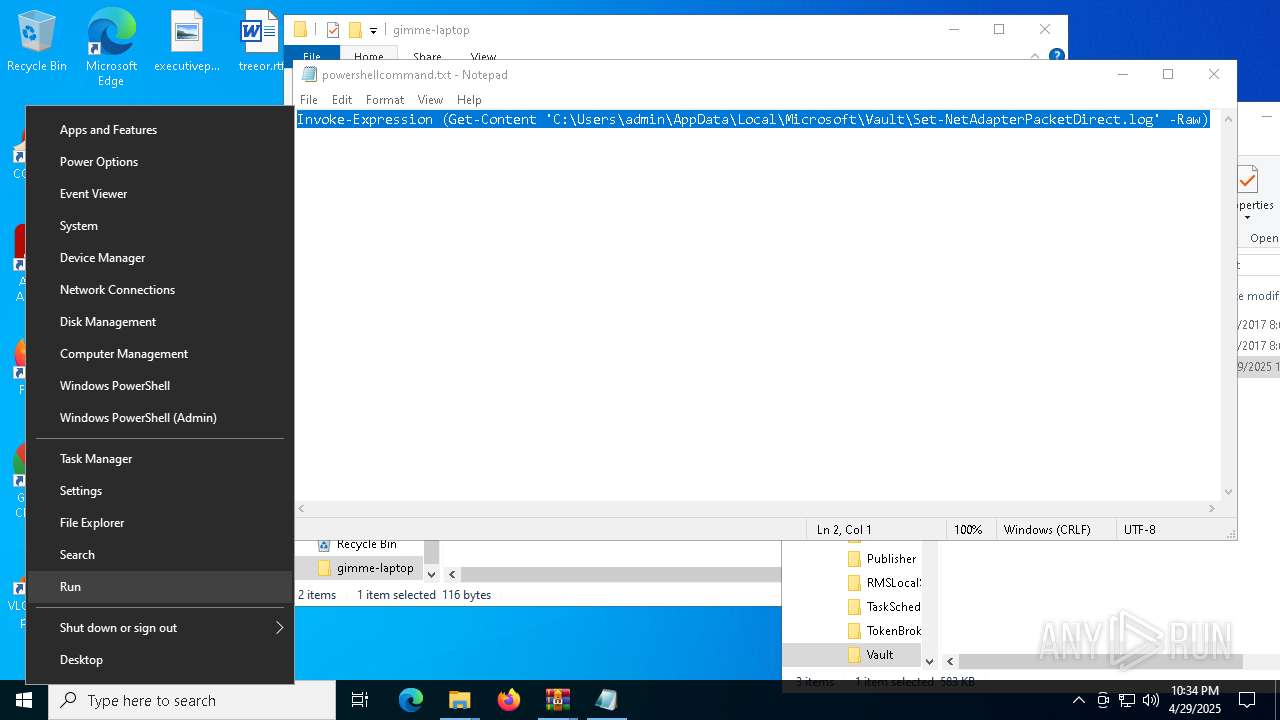
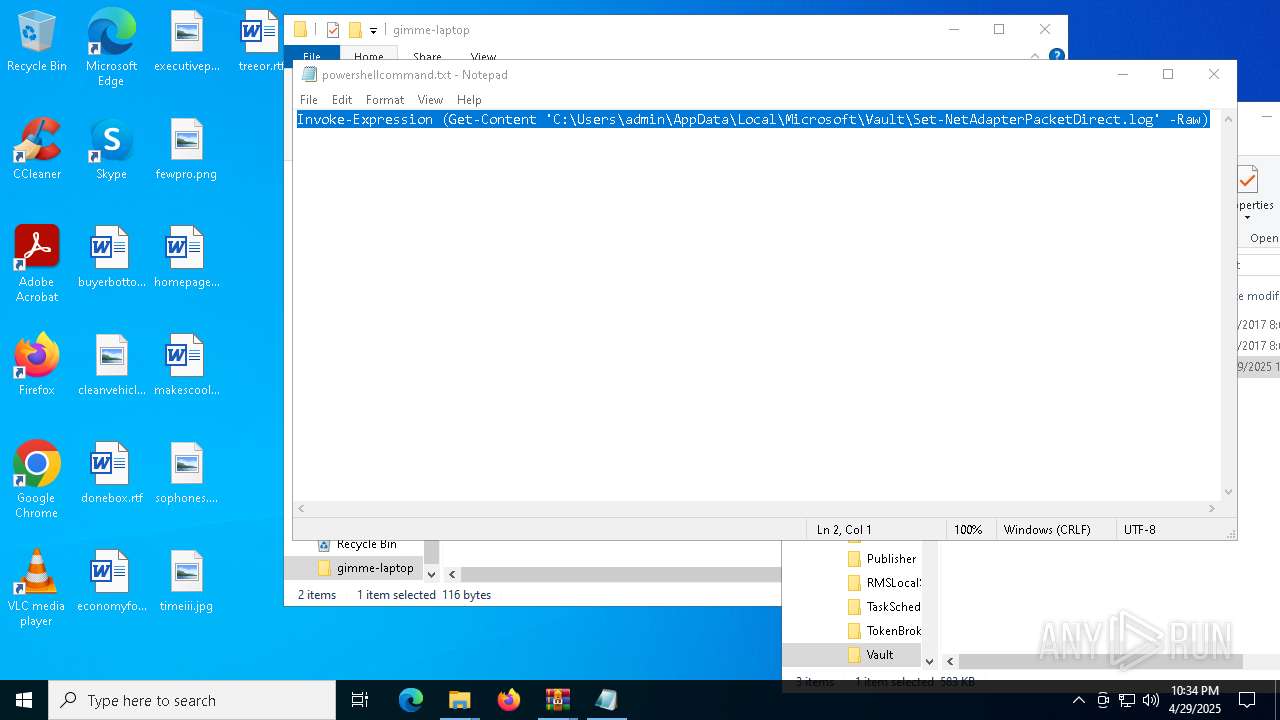
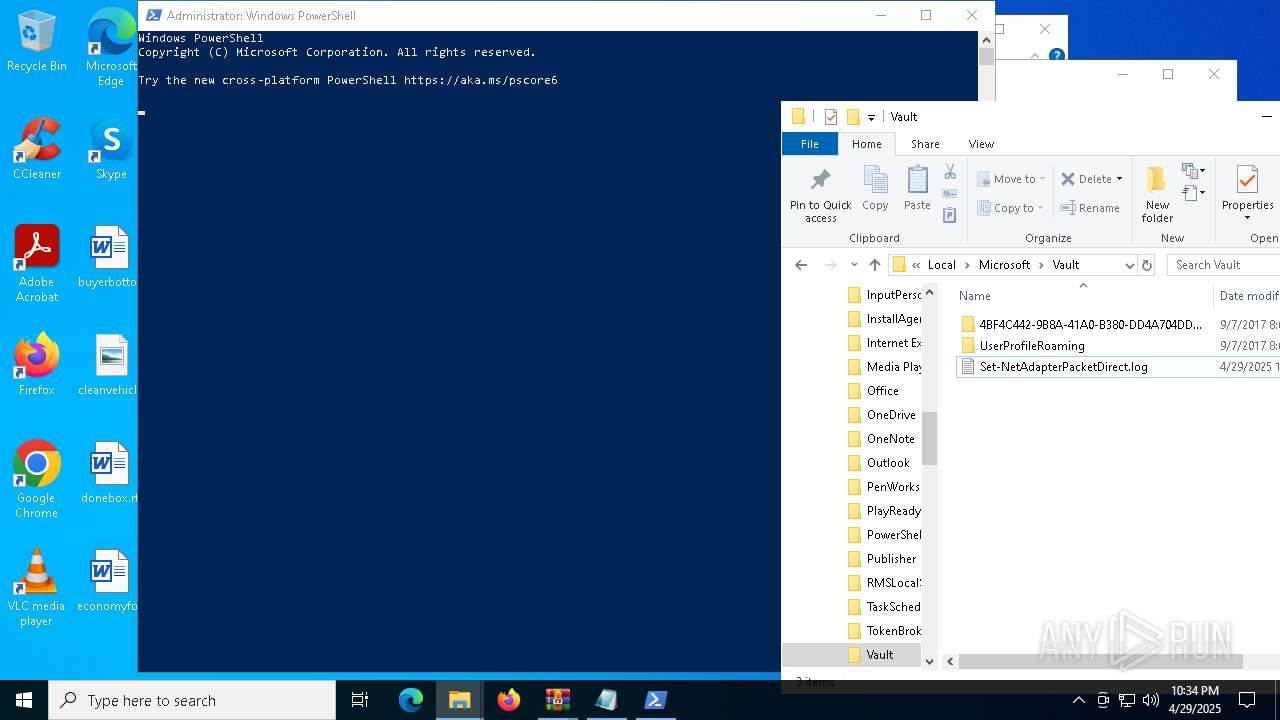
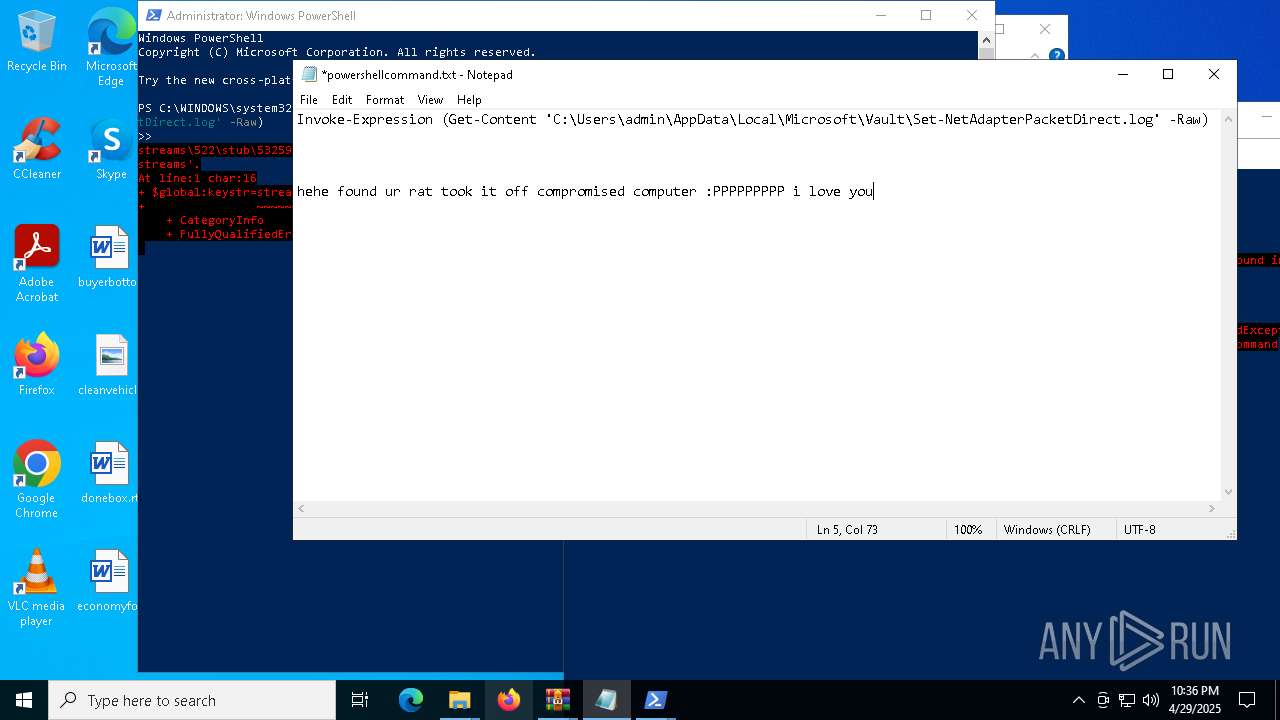
| File name: | gimme-laptop.zip |
| Full analysis: | https://app.any.run/tasks/1dc1f549-6641-4cd5-9e3f-30417dc82cd4 |
| Verdict: | Malicious activity |
| Threats: | AsyncRAT is a RAT that can monitor and remotely control infected systems. This malware was introduced on Github as a legitimate open-source remote administration software, but hackers use it for its many powerful malicious functions. |
| Analysis date: | April 29, 2025, 22:33:07 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=store |
| MD5: | 8A75155531EBB01982211BCB38547728 |
| SHA1: | 913BAF18B563831D6EAB66A7BBE21397DB449FA9 |
| SHA256: | 9E51BE4B50B7CB8BD5156EBCC43603DE7F5A8EDA22D1B269F149CB8735C2E9F8 |
| SSDEEP: | 3072:JBxCcDDi0JyLUYdf9S6ucjjS71ibvOOSRlp35ivl25:JmNnBdFS6BjGqGTP5 |
MALICIOUS
ASYNCRAT has been detected (MUTEX)
- powershell.exe (PID: 1164)
ASYNCRAT has been detected (SURICATA)
- powershell.exe (PID: 1164)
SUSPICIOUS
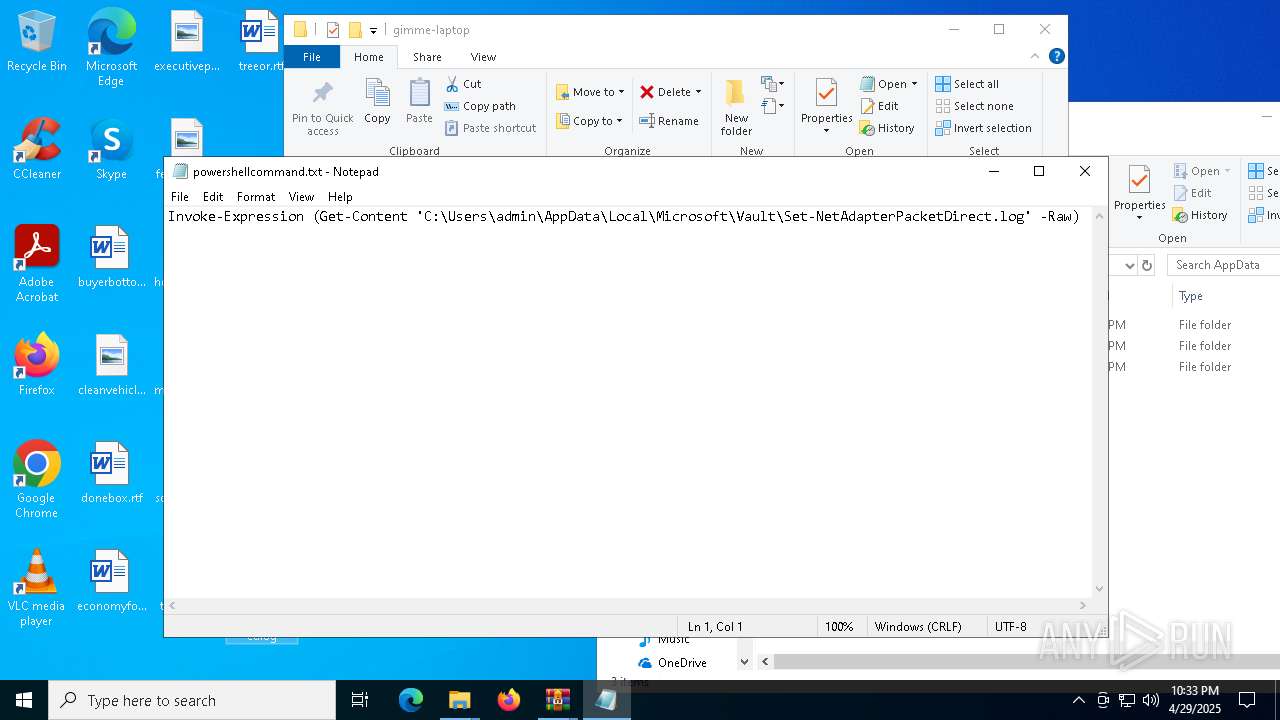
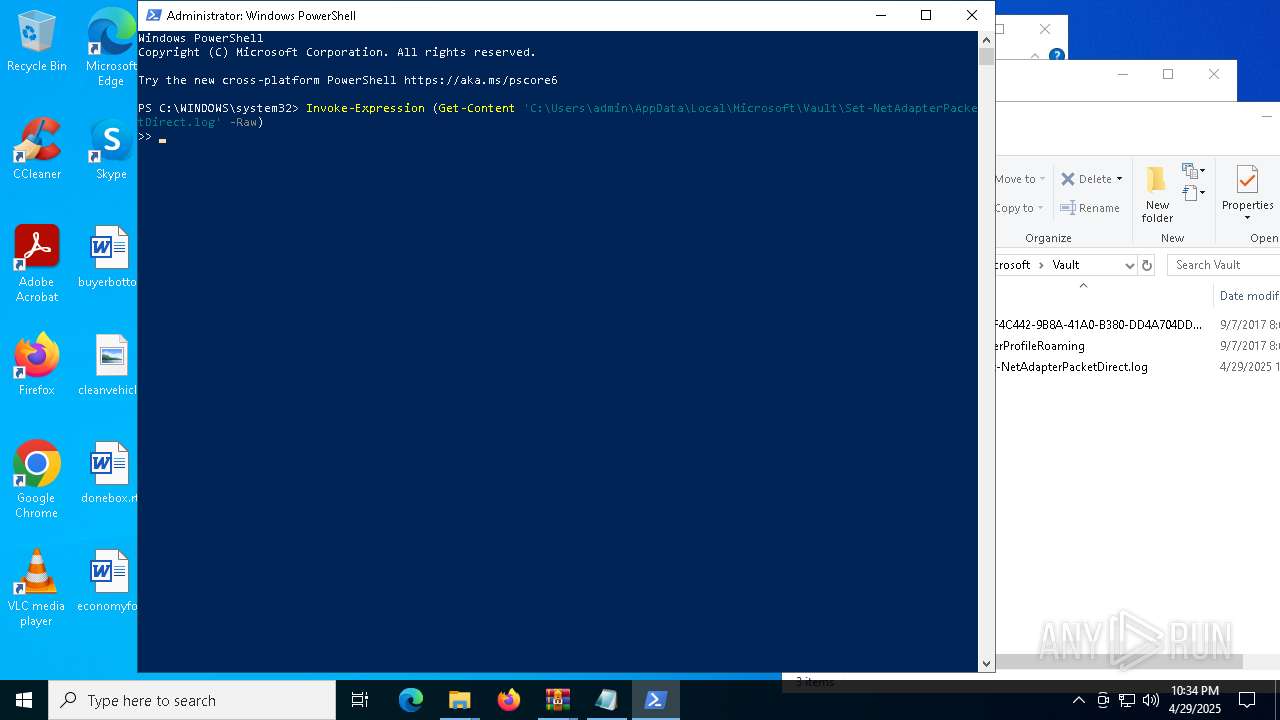
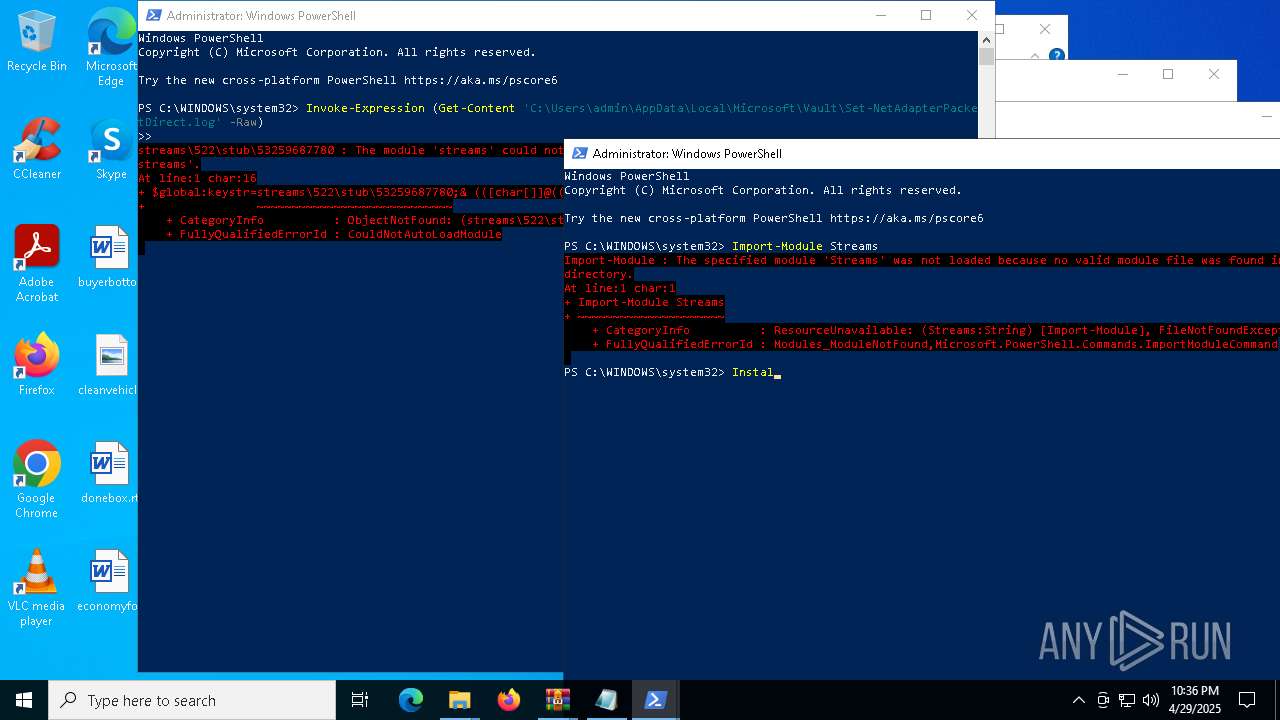
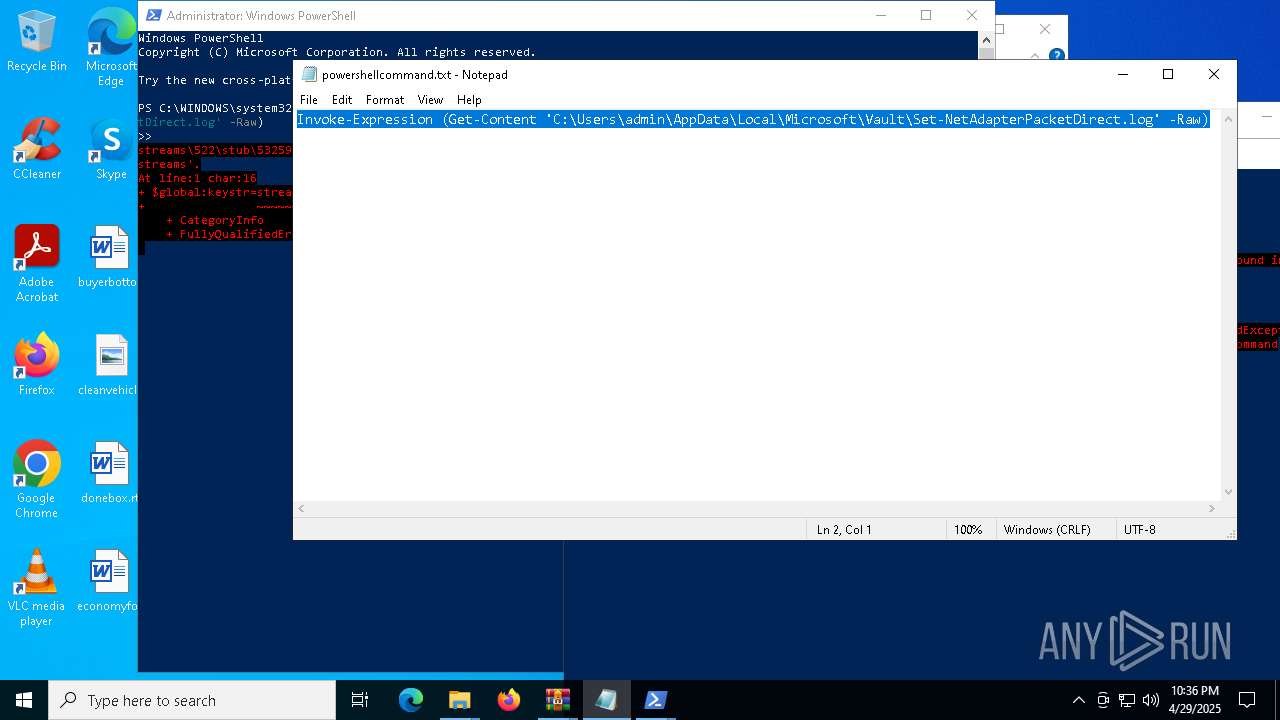
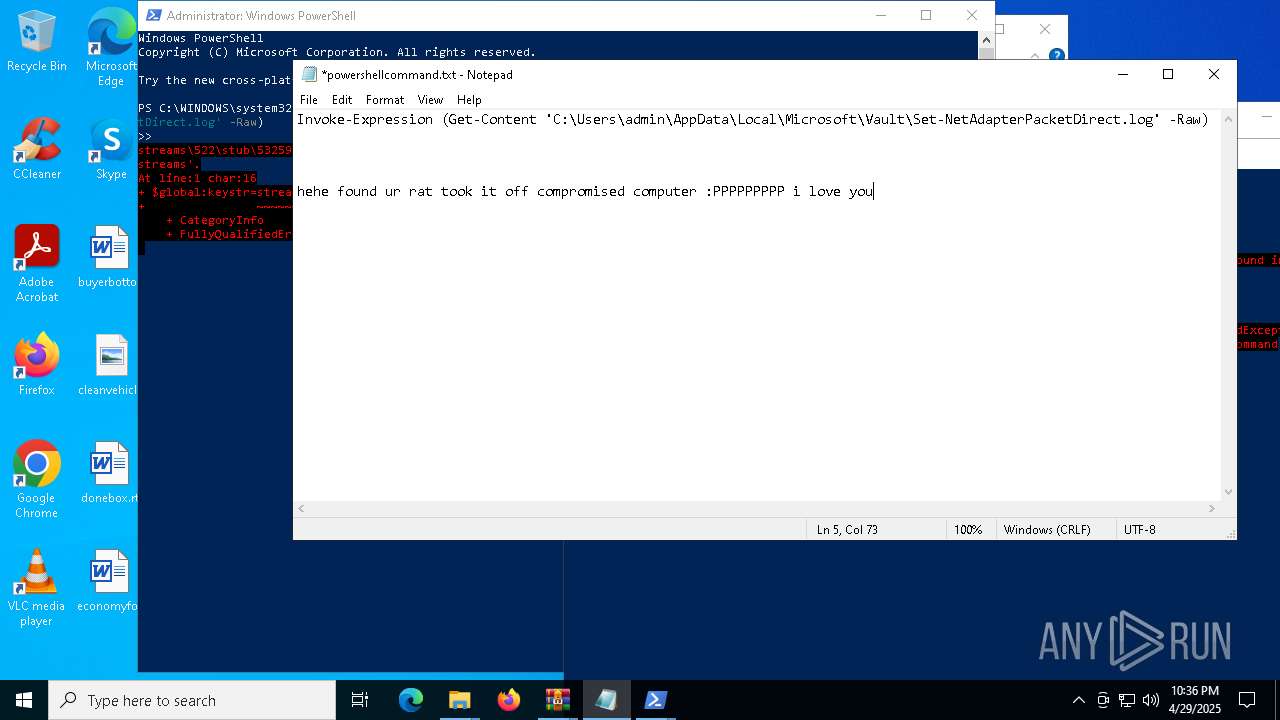
Gets content of a file (POWERSHELL)
- powershell.exe (PID: 1164)
CSC.EXE is used to compile C# code
- csc.exe (PID: 6560)
- csc.exe (PID: 7496)
Generic archive extractor
- WinRAR.exe (PID: 6032)
Executable content was dropped or overwritten
- csc.exe (PID: 6560)
- csc.exe (PID: 7496)
Connects to unusual port
- powershell.exe (PID: 1164)
Contacting a server suspected of hosting an CnC
- powershell.exe (PID: 1164)
Gets or sets the security protocol (POWERSHELL)
- powershell.exe (PID: 1164)
Checks for external IP
- svchost.exe (PID: 2196)
- powershell.exe (PID: 1164)
INFO
Manual execution by a user
- WinRAR.exe (PID: 7812)
- notepad.exe (PID: 8188)
- powershell.exe (PID: 1164)
- powershell.exe (PID: 7416)
- firefox.exe (PID: 736)
Reads security settings of Internet Explorer
- notepad.exe (PID: 8188)
Create files in a temporary directory
- cvtres.exe (PID: 2152)
- cvtres.exe (PID: 5972)
- csc.exe (PID: 7496)
- csc.exe (PID: 6560)
Reads the software policy settings
- slui.exe (PID: 7292)
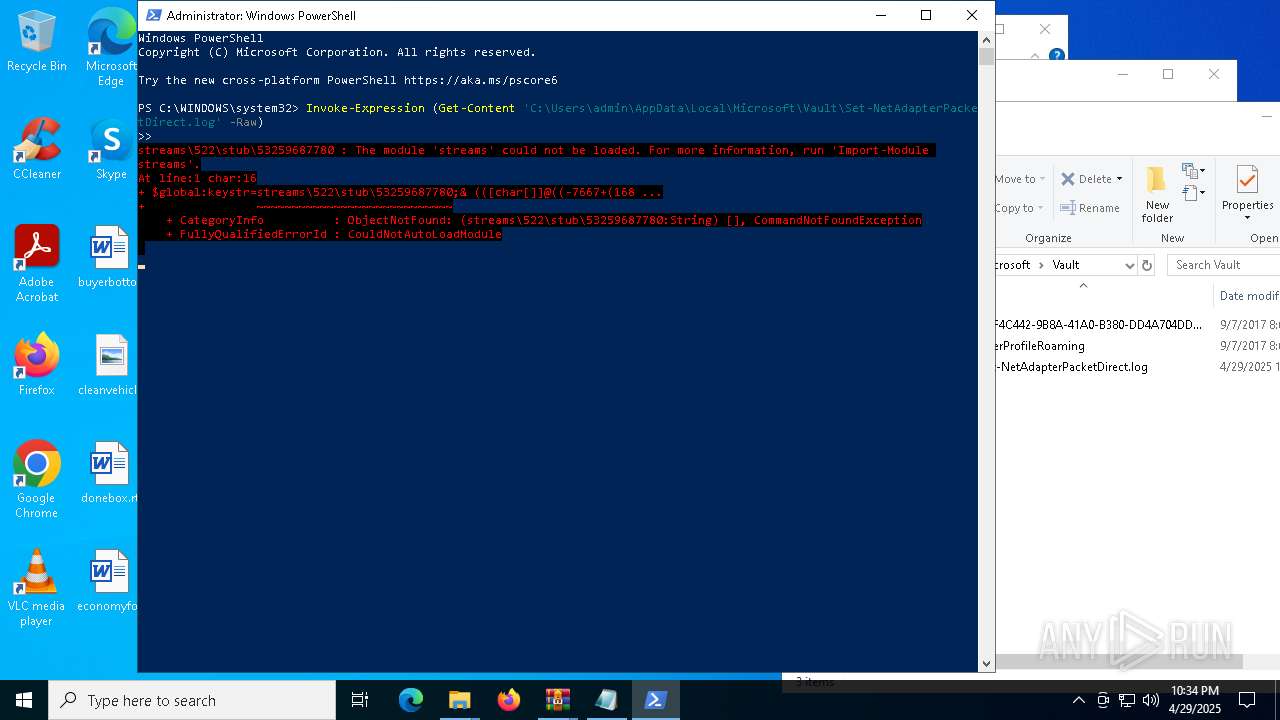
Script raised an exception (POWERSHELL)
- powershell.exe (PID: 1164)
Checks supported languages
- csc.exe (PID: 6560)
- cvtres.exe (PID: 2152)
- csc.exe (PID: 7496)
- cvtres.exe (PID: 5972)
Reads the machine GUID from the registry
- csc.exe (PID: 6560)
- csc.exe (PID: 7496)
Gets data length (POWERSHELL)
- powershell.exe (PID: 1164)
Checks proxy server information
- powershell.exe (PID: 1164)
Disables trace logs
- powershell.exe (PID: 1164)
Application launched itself
- firefox.exe (PID: 736)
- firefox.exe (PID: 6228)
Checks current location (POWERSHELL)
- powershell.exe (PID: 1164)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | None |
| ZipModifyDate: | 2025:04:29 15:25:30 |
| ZipCRC: | 0x00000000 |
| ZipCompressedSize: | - |
| ZipUncompressedSize: | - |
| ZipFileName: | gimme-laptop/ |
Total processes
178
Monitored processes
42
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 736 | "C:\Program Files\Mozilla Firefox\firefox.exe" | C:\Program Files\Mozilla Firefox\firefox.exe | — | explorer.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Exit code: 0 Version: 123.0 Modules
| |||||||||||||||
| 744 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1164 | "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1228 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel=4972 -childID 3 -isForBrowser -prefsHandle 4964 -prefMapHandle 4396 -prefsLen 31243 -prefMapSize 244583 -jsInitHandle 1540 -jsInitLen 235124 -parentBuildID 20240213221259 -win32kLockedDown -appDir "C:\Program Files\Mozilla Firefox\browser" - {ea28b8b4-93df-43f9-829c-6500ce6738e1} 6228 "\\.\pipe\gecko-crash-server-pipe.6228" 1298ce40690 tab | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Version: 123.0 Modules
| |||||||||||||||
| 1704 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel=6852 -childID 14 -isForBrowser -prefsHandle 6860 -prefMapHandle 6864 -prefsLen 31538 -prefMapSize 244583 -jsInitHandle 1540 -jsInitLen 235124 -parentBuildID 20240213221259 -win32kLockedDown -appDir "C:\Program Files\Mozilla Firefox\browser" - {1688ecac-84fc-4b90-959a-1f27d105439e} 6228 "\\.\pipe\gecko-crash-server-pipe.6228" 1298e3464d0 tab | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Version: 123.0 Modules
| |||||||||||||||
| 2152 | C:\Windows\Microsoft.NET\Framework64\v4.0.30319\cvtres.exe /NOLOGO /READONLY /MACHINE:IX86 "/OUT:C:\Users\admin\AppData\Local\Temp\RESEC9F.tmp" "c:\Users\admin\AppData\Local\Temp\3vpw4tba\CSC859AB97069664B83838E5C96E490C824.TMP" | C:\Windows\Microsoft.NET\Framework64\v4.0.30319\cvtres.exe | — | csc.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft® Resource File To COFF Object Conversion Utility Exit code: 0 Version: 14.32.31326.0 Modules
| |||||||||||||||
| 2196 | C:\WINDOWS\system32\svchost.exe -k NetworkService -p -s Dnscache | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2240 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel=7156 -childID 17 -isForBrowser -prefsHandle 7060 -prefMapHandle 7064 -prefsLen 31538 -prefMapSize 244583 -jsInitHandle 1540 -jsInitLen 235124 -parentBuildID 20240213221259 -win32kLockedDown -appDir "C:\Program Files\Mozilla Firefox\browser" - {d69d45e6-448a-442a-b398-e04672a5cc2c} 6228 "\\.\pipe\gecko-crash-server-pipe.6228" 1298e50a150 tab | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Version: 123.0 Modules
| |||||||||||||||
| 2600 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel=4796 -parentBuildID 20240213221259 -sandboxingKind 0 -prefsHandle 4892 -prefMapHandle 4872 -prefsLen 38185 -prefMapSize 244583 -win32kLockedDown -appDir "C:\Program Files\Mozilla Firefox\browser" - {adb4e04c-ba6c-49e0-9a6a-3c183d1d04a5} 6228 "\\.\pipe\gecko-crash-server-pipe.6228" 1298cfbb710 utility | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Version: 123.0 Modules
| |||||||||||||||
| 4988 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel=7072 -childID 16 -isForBrowser -prefsHandle 7100 -prefMapHandle 6956 -prefsLen 31538 -prefMapSize 244583 -jsInitHandle 1540 -jsInitLen 235124 -parentBuildID 20240213221259 -win32kLockedDown -appDir "C:\Program Files\Mozilla Firefox\browser" - {fd0774de-4c9d-4524-b939-0070d1b285fd} 6228 "\\.\pipe\gecko-crash-server-pipe.6228" 1298fd44f50 tab | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Exit code: 0 Version: 123.0 Modules
| |||||||||||||||
Total events
47 533
Read events
47 515
Write events
18
Delete events
0
Modification events
| (PID) Process: | (6032) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (6032) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (6032) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (6032) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\gimme-laptop.zip | |||
| (PID) Process: | (6032) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (6032) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (6032) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (6032) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (7812) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (7812) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
Executable files
2
Suspicious files
207
Text files
37
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1164 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_1evg1k4u.11r.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
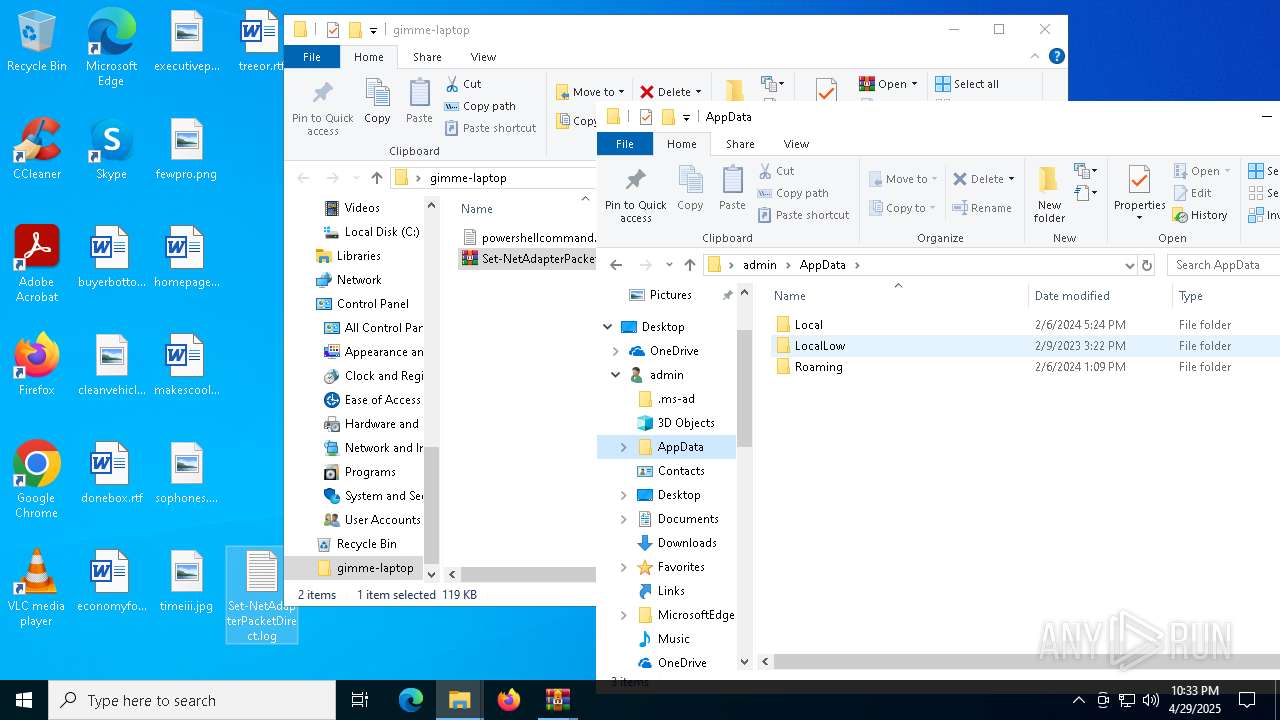
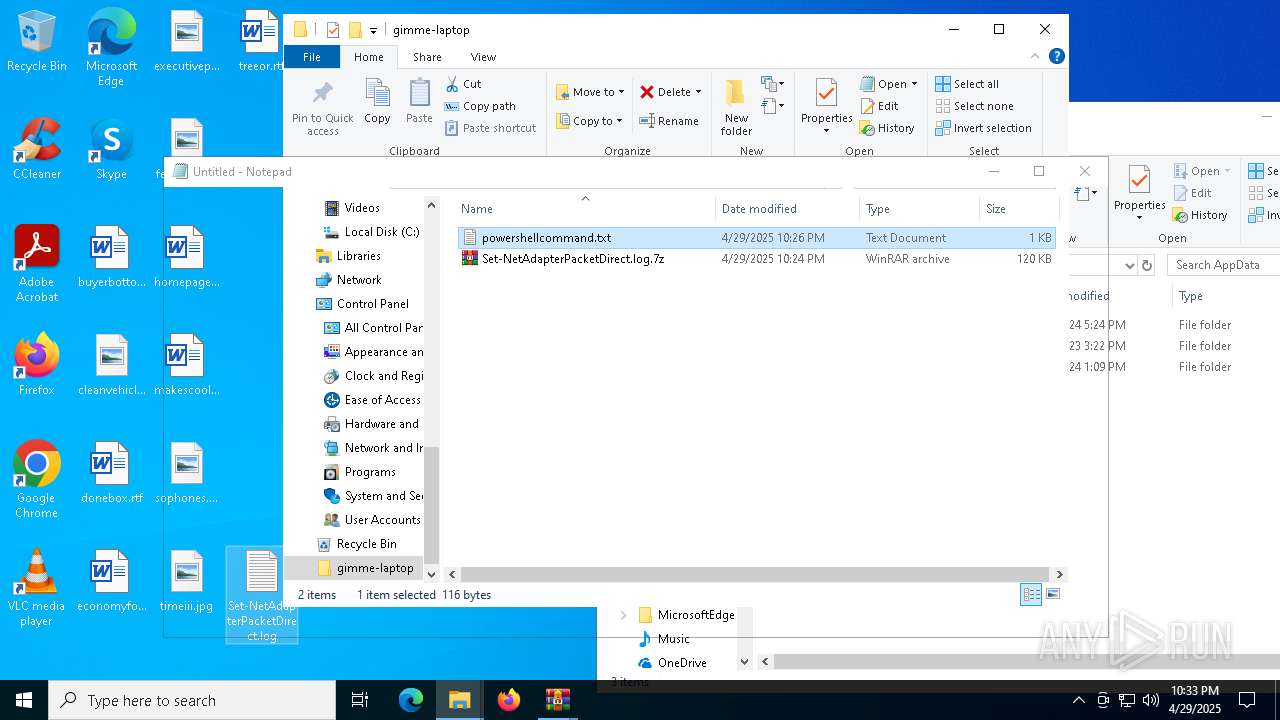
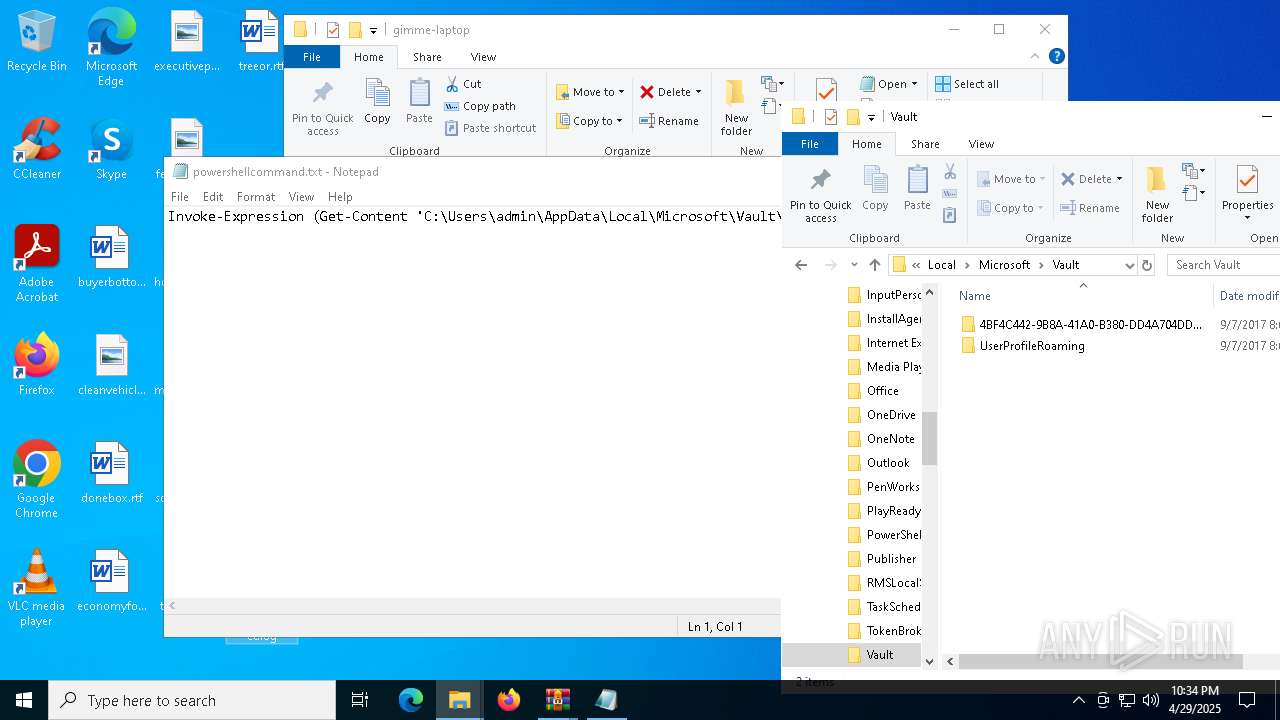
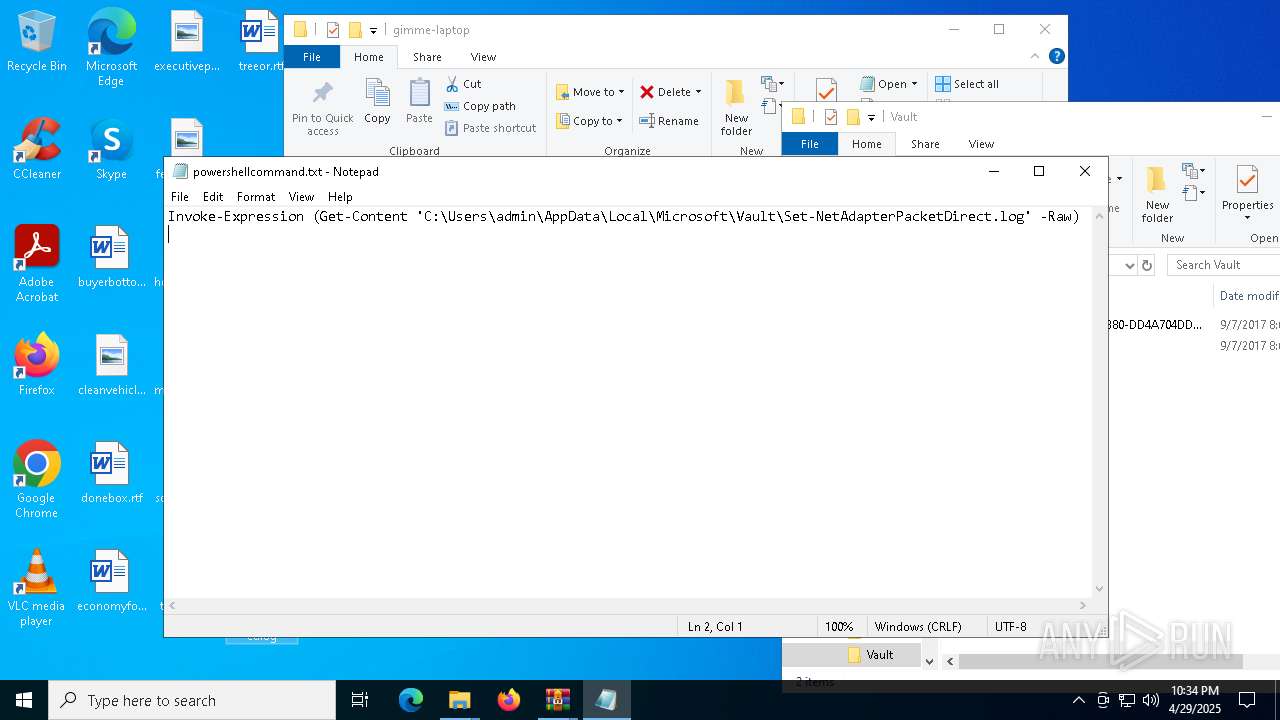
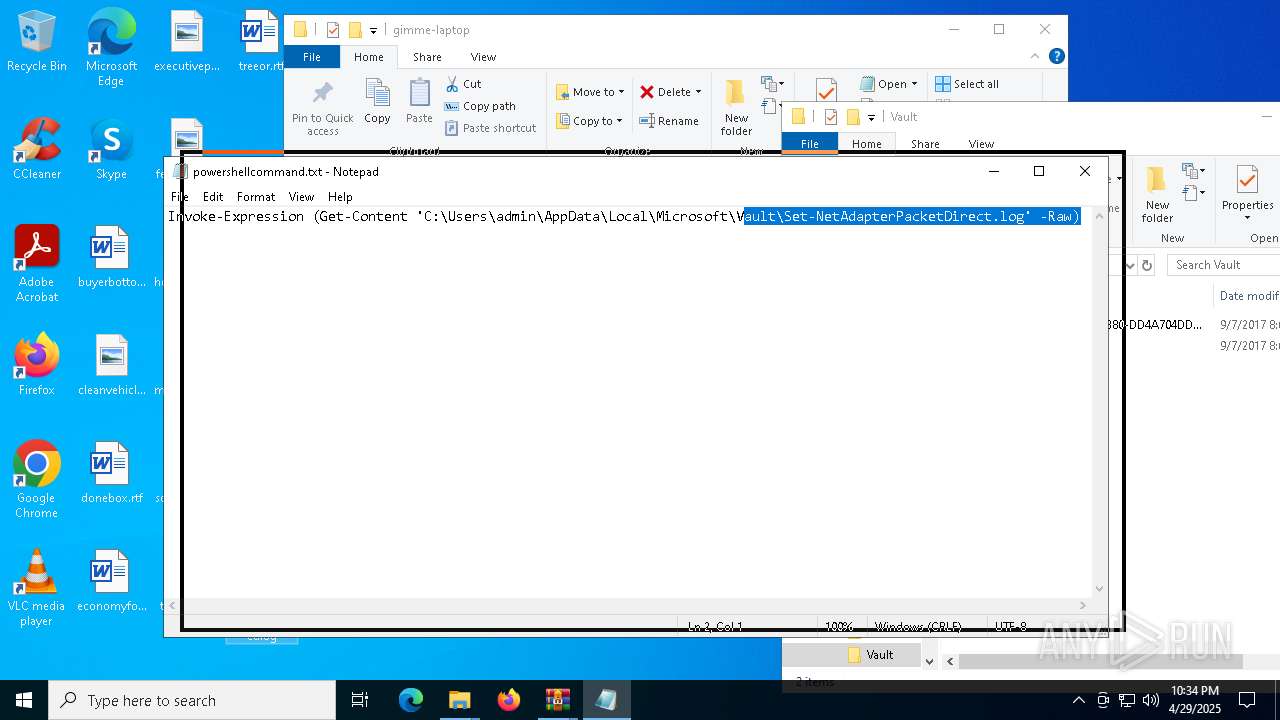
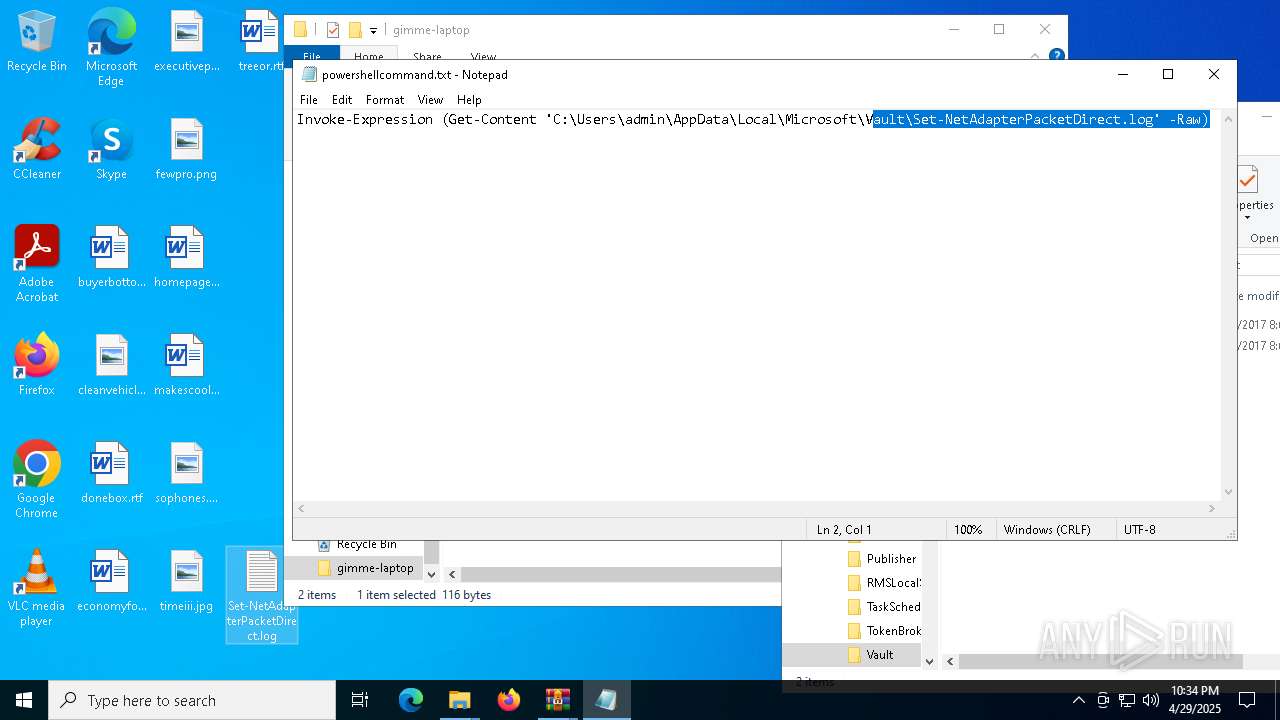
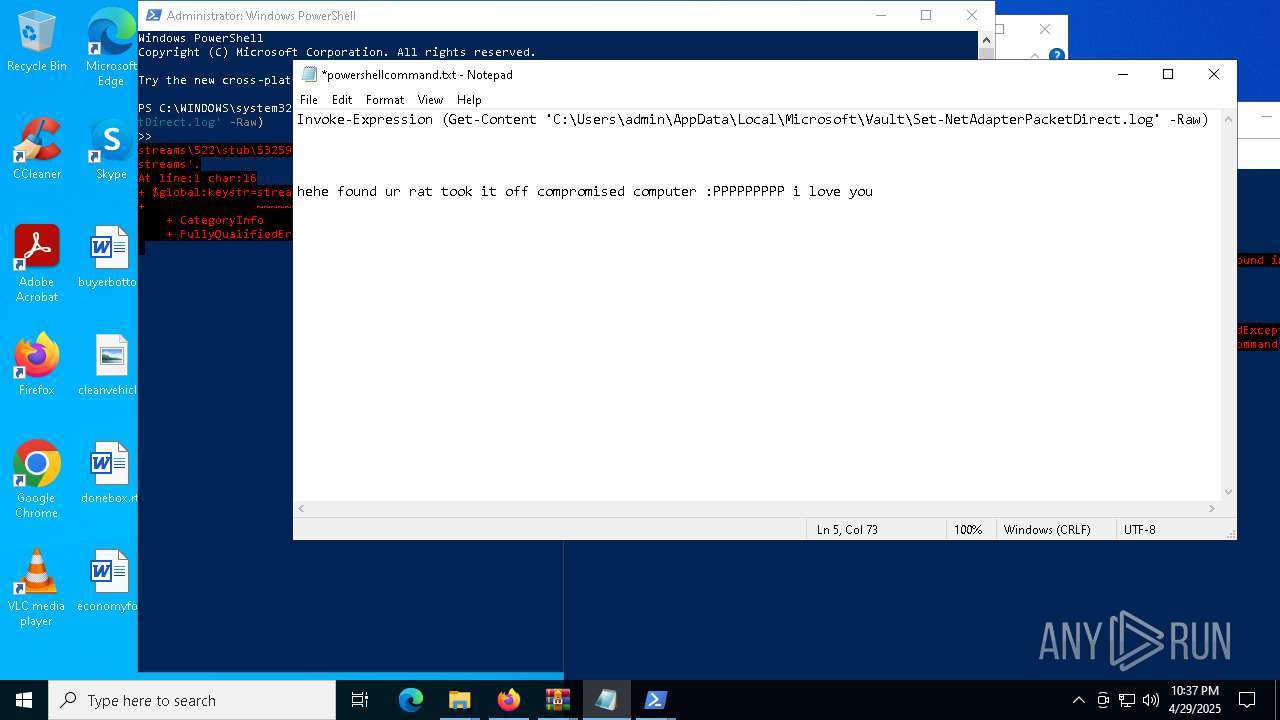
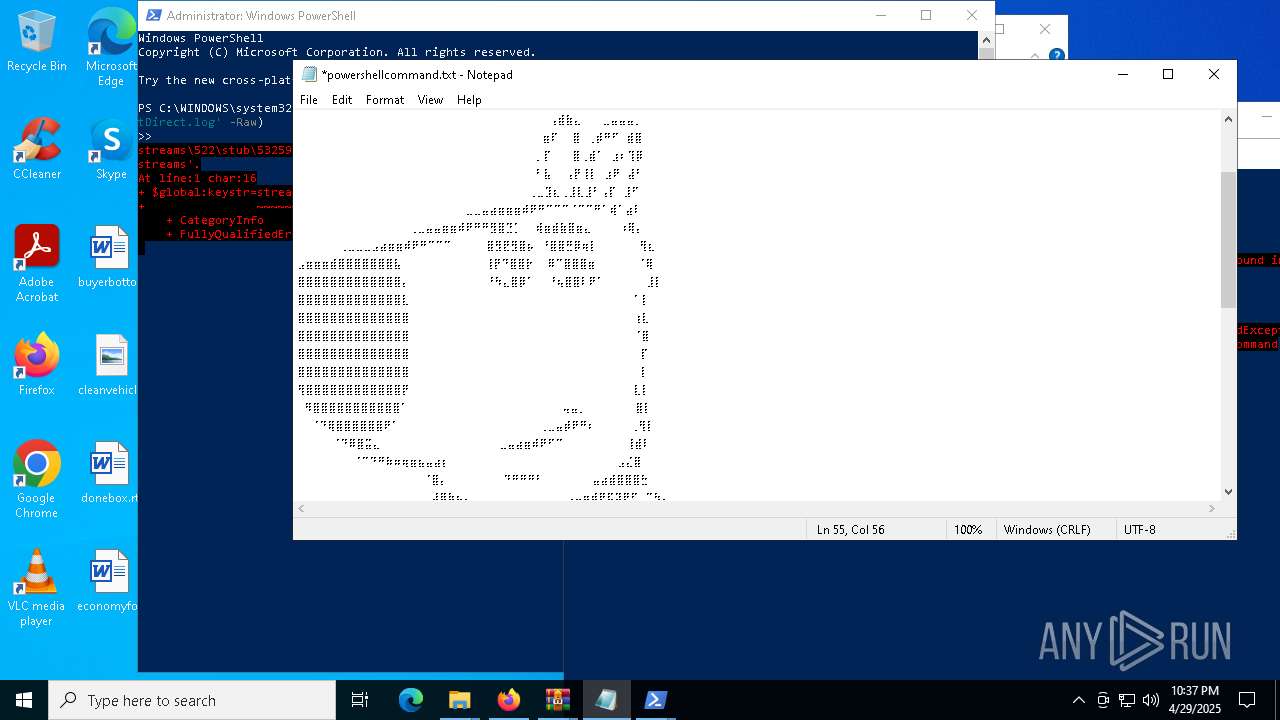
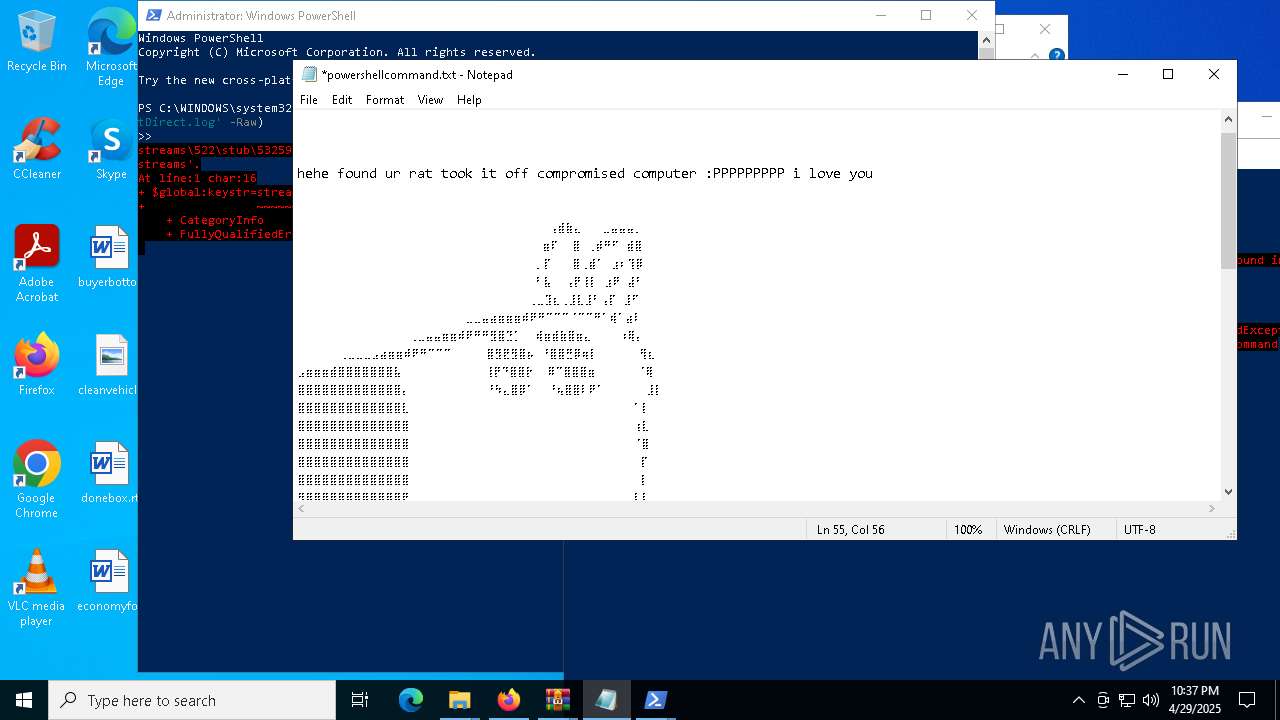
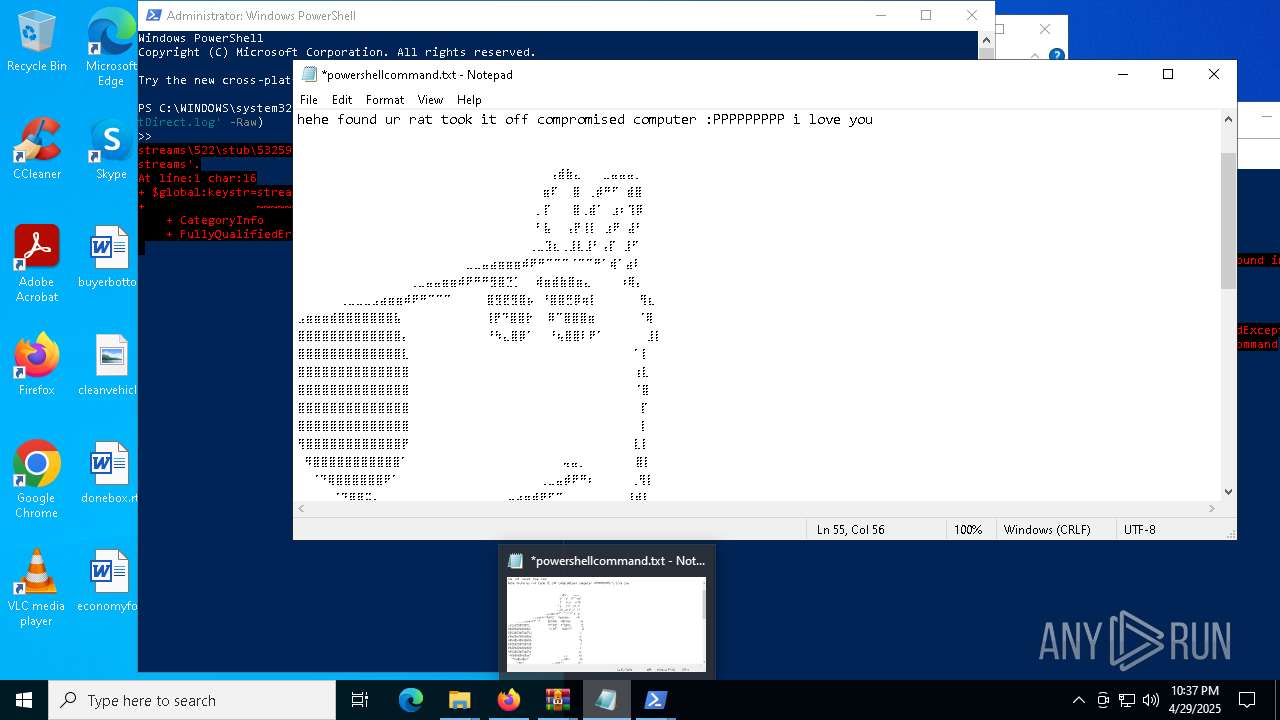
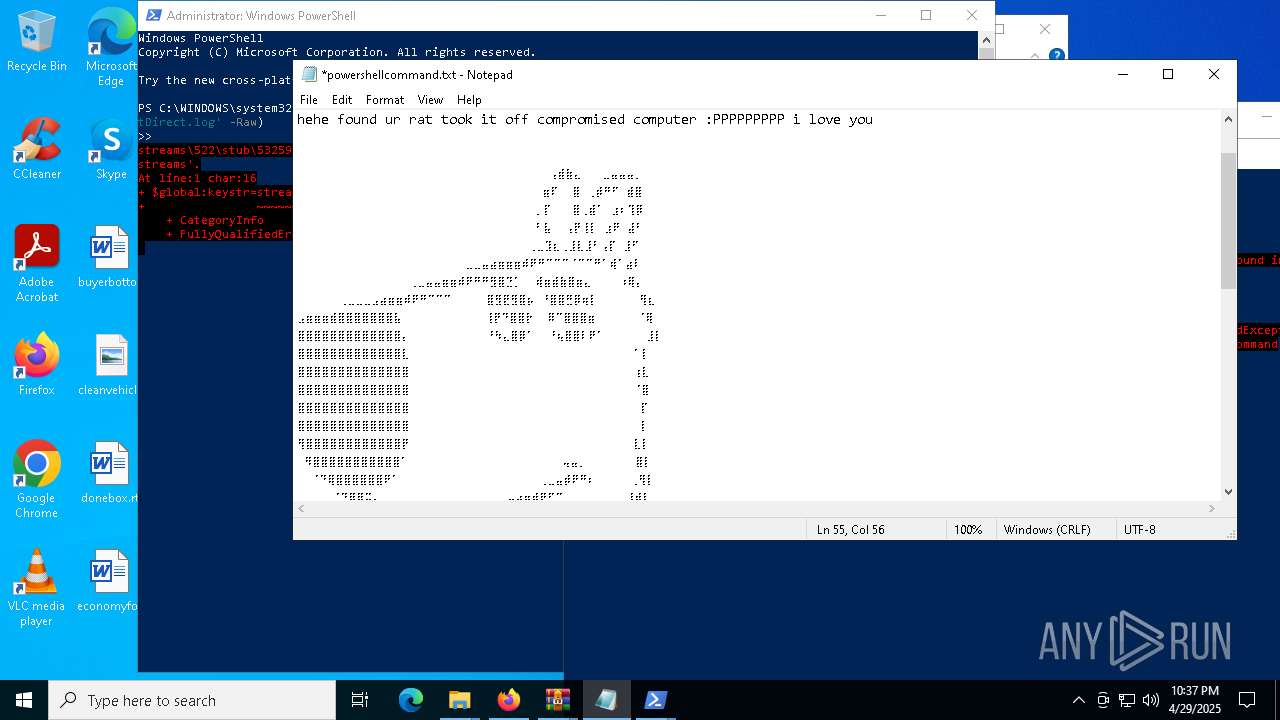
| 6032 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa6032.30767\gimme-laptop\powershellcommand.txt | text | |
MD5:8E21C6EE29857B04B624A7DCACC34955 | SHA256:AC811255542AD87B618EE37D1C3CED67E7EEC1DEEE389CF1000D54604A4B6804 | |||
| 1164 | powershell.exe | C:\Users\admin\AppData\Local\Temp\3vpw4tba\3vpw4tba.0.cs | text | |
MD5:E8C9153D97CBDE01A9659965497AA640 | SHA256:7FF5E962B406C8BCD750F7AFEAB5762011A0CEA90D327D85095B505B9B4A51F5 | |||
| 6560 | csc.exe | C:\Users\admin\AppData\Local\Temp\3vpw4tba\3vpw4tba.dll | executable | |
MD5:A95F8E16FF8DE316CC9CFACC727FCA8B | SHA256:6CF2101E6CA7C82F89EC7CAB828217568FB904707B402CCD90BEFFE376173420 | |||
| 7812 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb7812.32104\Set-NetAdapterPacketDirect.log | text | |
MD5:95E4BC853142711E748B45F8E8A73590 | SHA256:0EC0E1C5D585E3CD2ABFE9138819654916D47A13E40E2ECD32CE2CC478488E99 | |||
| 1164 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\590aee7bdd69b59b.customDestinations-ms | binary | |
MD5:65EABBBE8996F94EF065C028A52AD930 | SHA256:DC21FE0859A00C057457EEB34BE18EBF53E660335F36B45D1C3FFC7A3435A114 | |||
| 1164 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\5JWMKARDH32Z34GJPW2M.temp | binary | |
MD5:65EABBBE8996F94EF065C028A52AD930 | SHA256:DC21FE0859A00C057457EEB34BE18EBF53E660335F36B45D1C3FFC7A3435A114 | |||
| 5972 | cvtres.exe | C:\Users\admin\AppData\Local\Temp\RES4389.tmp | binary | |
MD5:ACFDE5CA7921974F9ADFF507AA01DB23 | SHA256:3257A315FBB9AF3082B7508E766494616D371E925519FE481C9125F9B32D38D4 | |||
| 1164 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\590aee7bdd69b59b.customDestinations-ms~RF11c205.TMP | binary | |
MD5:D040F64E9E7A2BB91ABCA5613424598E | SHA256:D04E0A6940609BD6F3B561B0F6027F5CA4E8C5CF0FB0D0874B380A0374A8D670 | |||
| 1164 | powershell.exe | C:\Users\admin\AppData\Local\Temp\uc3jal54\uc3jal54.cmdline | text | |
MD5:E962BE281D1B2EB4291E4D60C5788362 | SHA256:DAE502C308E0CF7F13777293FA7111C7DAC493EBACC20A5E5E8DD56FF07B6888 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
104
TCP/UDP connections
344
DNS requests
427
Threats
5
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5496 | MoUsoCoreWorker.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
8032 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
8032 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
6228 | firefox.exe | POST | 200 | 142.250.185.163:80 | http://o.pki.goog/s/wr3/3H4 | unknown | — | — | whitelisted |
6228 | firefox.exe | GET | 200 | 34.107.221.82:80 | http://detectportal.firefox.com/canonical.html | unknown | — | — | whitelisted |
6228 | firefox.exe | POST | 200 | 142.250.185.163:80 | http://o.pki.goog/we2 | unknown | — | — | whitelisted |
6228 | firefox.exe | GET | 200 | 34.107.221.82:80 | http://detectportal.firefox.com/success.txt?ipv4 | unknown | — | — | whitelisted |
6228 | firefox.exe | POST | — | 142.250.185.163:80 | http://o.pki.goog/s/wr3/FIY | unknown | — | — | whitelisted |
6228 | firefox.exe | POST | 200 | 184.24.77.83:80 | http://r11.o.lencr.org/ | unknown | — | — | whitelisted |
6228 | firefox.exe | POST | 200 | 184.24.77.83:80 | http://r11.o.lencr.org/ | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4108 | RUXIMICS.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
2104 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5496 | MoUsoCoreWorker.exe | 23.216.77.42:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
5496 | MoUsoCoreWorker.exe | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2112 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
3216 | svchost.exe | 172.211.123.249:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
6544 | svchost.exe | 40.126.31.3:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
activation-v2.sls.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1164 | powershell.exe | Potentially Bad Traffic | ET DNS Query to a *.top domain - Likely Hostile |
1164 | powershell.exe | Domain Observed Used for C2 Detected | ET MALWARE Generic AsyncRAT/zgRAT Style SSL Cert |
2196 | svchost.exe | Misc activity | ET INFO External IP Lookup Domain (ipify .org) in DNS Lookup |
1164 | powershell.exe | Misc activity | ET INFO External IP Address Lookup Domain (ipify .org) in TLS SNI |
1164 | powershell.exe | Malware Command and Control Activity Detected | REMOTE [ANY.RUN] AsyncRAT Successful Connection |