| download: | IMG-872364%20NOTIFCACION%20CITACION%20POR%20FALSIFICACION%20DE%20DOCUMENTO.uu |
| Full analysis: | https://app.any.run/tasks/18c2e642-e1d9-4d22-b25c-844973316cac |
| Verdict: | Malicious activity |
| Threats: | njRAT is a remote access trojan. It is one of the most widely accessible RATs on the market that features an abundance of educational information. Interested attackers can even find tutorials on YouTube. This allows it to become one of the most popular RATs in the world. |
| Analysis date: | January 17, 2020, 17:11:16 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
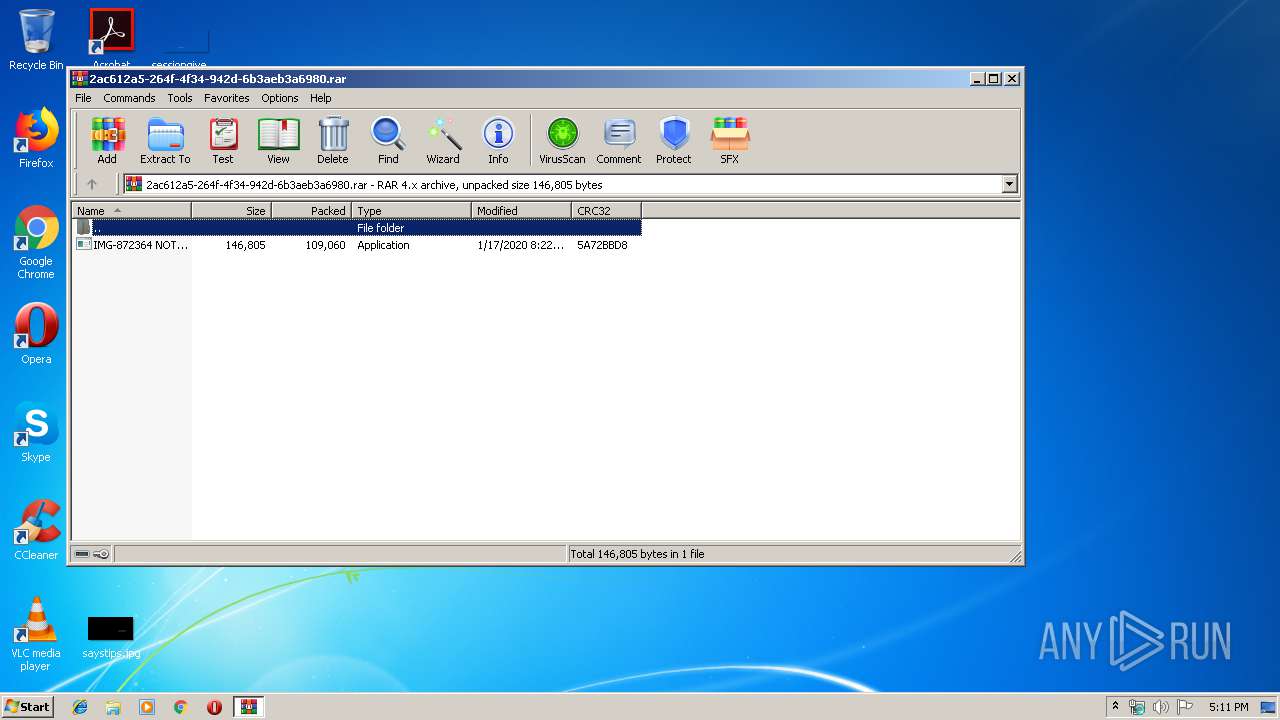
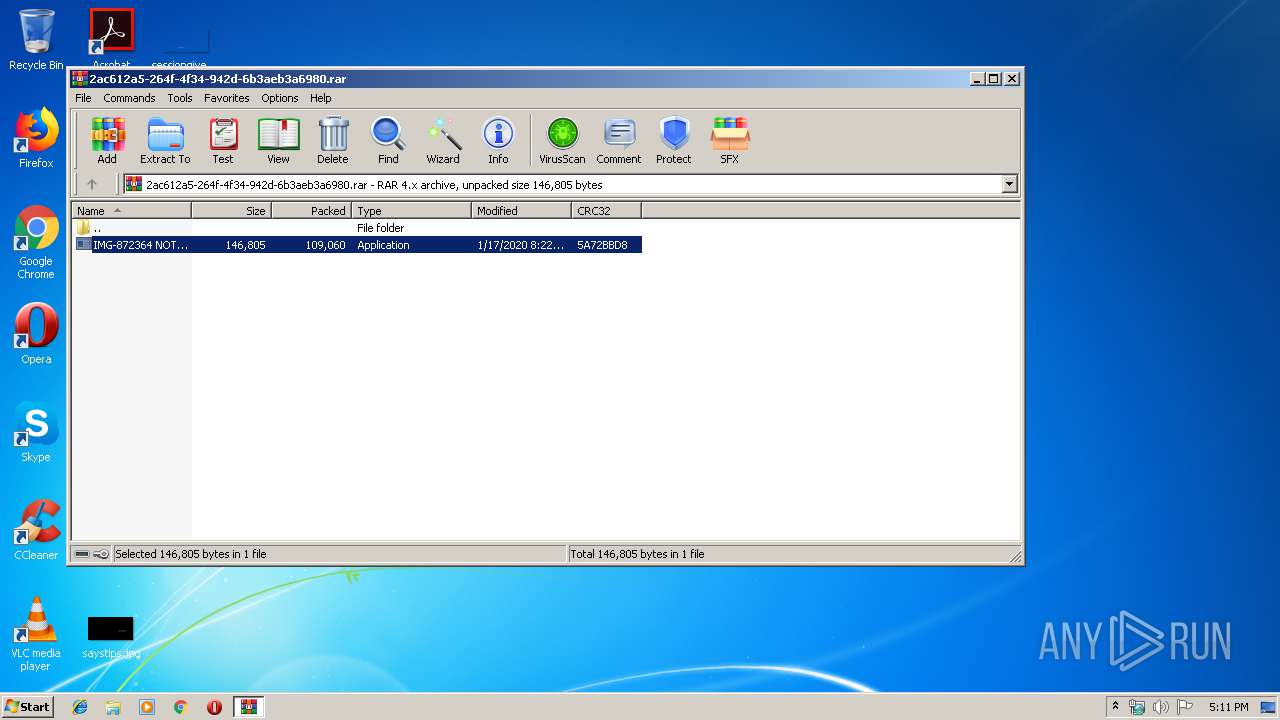
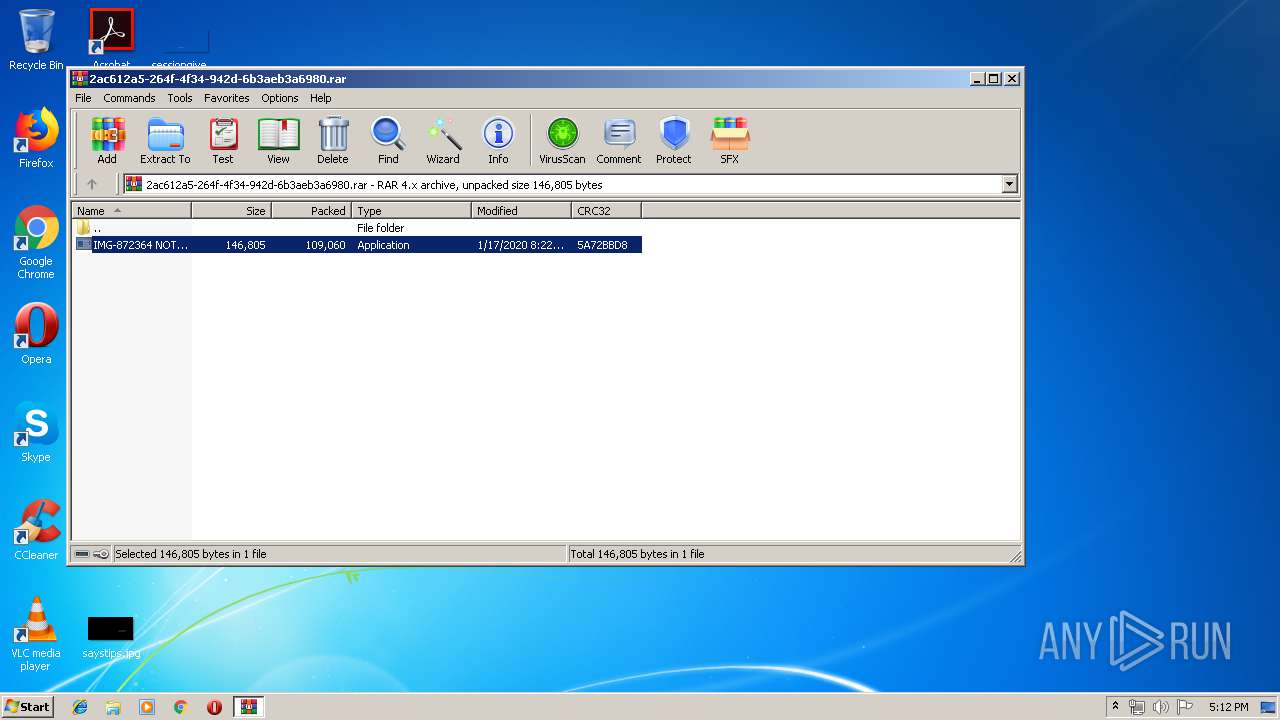
| MIME: | application/x-rar |
| File info: | RAR archive data, v4, os: Win32 |
| MD5: | E8BECCA6AEF4C1545FA181258FD8157C |
| SHA1: | F00A88B58959C28E52571AE152013320A7BF50D4 |
| SHA256: | 9E3BF48D2D51EC7A9E3B4AABA8866013B2DC5CCA85D1E9F805650E17EA728E4C |
| SSDEEP: | 3072:Lr4yQ/RMby5Isyd+8Sbz5D3viocRCFe2V44IfPGhEZ:Lr4yQ/iV5P8z5zIyZdIH4EZ |
MALICIOUS
Starts Visual C# compiler
- GWUgdpESktgsgwntma5.exe (PID: 2884)
- GWUgdpESktgsgwntma5.exe (PID: 2608)
- GWUgdpESktgsgwntma5.exe (PID: 1992)
Application was dropped or rewritten from another process
- GWUgdpESktgsgwntma5.exe (PID: 2884)
- IMG-872364 NOTIFCACION DE CITACION POR FALSIFICACION DE DOCUMENTO.exe (PID: 2836)
- GWUgdpESktgsgwntma5.exe (PID: 2608)
- IMG-872364 NOTIFCACION DE CITACION POR FALSIFICACION DE DOCUMENTO.exe (PID: 584)
- GWUgdpESktgsgwntma5.exe (PID: 1992)
Changes the autorun value in the registry
- GWUgdpESktgsgwntma5.exe (PID: 2884)
- GWUgdpESktgsgwntma5.exe (PID: 2608)
- GWUgdpESktgsgwntma5.exe (PID: 1992)
NJRAT was detected
- RegAsm.exe (PID: 2420)
Connects to CnC server
- RegAsm.exe (PID: 2420)
SUSPICIOUS
Executable content was dropped or overwritten
- IMG-872364 NOTIFCACION DE CITACION POR FALSIFICACION DE DOCUMENTO.exe (PID: 2836)
- GWUgdpESktgsgwntma5.exe (PID: 2884)
- WinRAR.exe (PID: 2104)
- csc.exe (PID: 2392)
Application launched itself
- GWUgdpESktgsgwntma5.exe (PID: 2884)
INFO
No info indicators.
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v-4.x) (58.3) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (41.6) |
EXIF
ZIP
| CompressedSize: | 109155 |
|---|---|
| UncompressedSize: | 146805 |
| OperatingSystem: | Win32 |
| ModifyDate: | 2020:01:17 08:22:19 |
| PackingMethod: | Normal |
| ArchivedFileName: | IMG-872364 NOTIFCACION DE CITACION POR FALSIFICACION DE DOCUMENTO.exe |
Total processes
64
Monitored processes
24
Malicious processes
4
Suspicious processes
3
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 252 | "C:\Windows\Microsoft.NET\Framework\v4.0.30319\RegAsm.exe" | C:\Windows\Microsoft.NET\Framework\v4.0.30319\RegAsm.exe | — | GWUgdpESktgsgwntma5.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft .NET Assembly Registration Utility Exit code: 0 Version: 4.7.3062.0 built by: NET472REL1 Modules
| |||||||||||||||
| 272 | C:\Windows\Microsoft.NET\Framework\v4.0.30319\cvtres.exe /NOLOGO /READONLY /MACHINE:IX86 "/OUT:C:\Users\admin\AppData\Local\Temp\RES75C2.tmp" "c:\Users\admin\AppData\Local\Temp\CSC143B290888EE4BF798EBCA13EE4E879.TMP" | C:\Windows\Microsoft.NET\Framework\v4.0.30319\cvtres.exe | — | csc.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft® Resource File To COFF Object Conversion Utility Exit code: 0 Version: 12.00.52519.0 built by: VSWINSERVICING Modules
| |||||||||||||||
| 444 | "C:\Windows\Microsoft.NET\Framework\v4.0.30319\RegAsm.exe" | C:\Windows\Microsoft.NET\Framework\v4.0.30319\RegAsm.exe | — | GWUgdpESktgsgwntma5.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft .NET Assembly Registration Utility Exit code: 0 Version: 4.7.3062.0 built by: NET472REL1 Modules
| |||||||||||||||
| 504 | C:\Windows\Microsoft.NET\Framework\v4.0.30319\cvtres.exe /NOLOGO /READONLY /MACHINE:IX86 "/OUT:C:\Users\admin\AppData\Local\Temp\RESE6D0.tmp" "c:\Users\admin\AppData\Local\Temp\CSC9D171738DD0E4758816E9F386E9D95C9.TMP" | C:\Windows\Microsoft.NET\Framework\v4.0.30319\cvtres.exe | — | csc.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft® Resource File To COFF Object Conversion Utility Exit code: 0 Version: 12.00.52519.0 built by: VSWINSERVICING Modules
| |||||||||||||||
| 520 | C:\Windows\Microsoft.NET\Framework\v4.0.30319\cvtres.exe /NOLOGO /READONLY /MACHINE:IX86 "/OUT:C:\Users\admin\AppData\Local\Temp\RESE7CA.tmp" "c:\Users\admin\AppData\Local\Temp\CSC6348BA366CA545938181511167D5C554.TMP" | C:\Windows\Microsoft.NET\Framework\v4.0.30319\cvtres.exe | — | csc.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft® Resource File To COFF Object Conversion Utility Exit code: 0 Version: 12.00.52519.0 built by: VSWINSERVICING Modules
| |||||||||||||||
| 584 | "C:\Windows\Microsoft.NET\Framework\v4.0.30319\csc.exe" /noconfig /fullpaths @"C:\Users\admin\AppData\Local\Temp\221uyvop.cmdline" | C:\Windows\Microsoft.NET\Framework\v4.0.30319\csc.exe | — | GWUgdpESktgsgwntma5.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Visual C# Command Line Compiler Exit code: 0 Version: 4.7.3062.0 built by: NET472REL1 Modules
| |||||||||||||||
| 584 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa2104.14871\IMG-872364 NOTIFCACION DE CITACION POR FALSIFICACION DE DOCUMENTO.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa2104.14871\IMG-872364 NOTIFCACION DE CITACION POR FALSIFICACION DE DOCUMENTO.exe | — | WinRAR.exe | |||||||||||
User: admin Company: Nota Inc. Integrity Level: MEDIUM Description: GyazoReplay Exit code: 0 Version: 4.1.0.0 Modules
| |||||||||||||||
| 736 | "C:\Windows\Microsoft.NET\Framework\v4.0.30319\RegAsm.exe" | C:\Windows\Microsoft.NET\Framework\v4.0.30319\RegAsm.exe | — | GWUgdpESktgsgwntma5.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft .NET Assembly Registration Utility Exit code: 0 Version: 4.7.3062.0 built by: NET472REL1 Modules
| |||||||||||||||
| 1400 | "C:\Windows\Microsoft.NET\Framework\v4.0.30319\RegAsm.exe" | C:\Windows\Microsoft.NET\Framework\v4.0.30319\RegAsm.exe | — | GWUgdpESktgsgwntma5.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft .NET Assembly Registration Utility Exit code: 0 Version: 4.7.3062.0 built by: NET472REL1 Modules
| |||||||||||||||
| 1800 | "C:\Windows\Microsoft.NET\Framework\v4.0.30319\csc.exe" /noconfig /fullpaths @"C:\Users\admin\AppData\Local\Temp\rwjap3fl.cmdline" | C:\Windows\Microsoft.NET\Framework\v4.0.30319\csc.exe | — | GWUgdpESktgsgwntma5.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Visual C# Command Line Compiler Exit code: 0 Version: 4.7.3062.0 built by: NET472REL1 Modules
| |||||||||||||||
Total events
1 517
Read events
1 493
Write events
24
Delete events
0
Modification events
| (PID) Process: | (2104) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (2104) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (2104) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\12B\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2104) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\2ac612a5-264f-4f34-942d-6b3aeb3a6980.rar | |||
| (PID) Process: | (2104) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (2104) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (2104) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (2104) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (2104) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (2104) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
Executable files
5
Suspicious files
0
Text files
8
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2884 | GWUgdpESktgsgwntma5.exe | C:\Users\admin\AppData\Local\Temp\221uyvop.0.cs | — | |
MD5:— | SHA256:— | |||
| 2884 | GWUgdpESktgsgwntma5.exe | C:\Users\admin\AppData\Local\Temp\221uyvop.cmdline | — | |
MD5:— | SHA256:— | |||
| 584 | csc.exe | C:\Users\admin\AppData\Local\Temp\CSC9D171738DD0E4758816E9F386E9D95C9.TMP | — | |
MD5:— | SHA256:— | |||
| 504 | cvtres.exe | C:\Users\admin\AppData\Local\Temp\RESE6D0.tmp | — | |
MD5:— | SHA256:— | |||
| 584 | csc.exe | C:\Users\admin\AppData\Local\Temp\221uyvop.dll | — | |
MD5:— | SHA256:— | |||
| 584 | csc.exe | C:\Users\admin\AppData\Local\Temp\221uyvop.out | — | |
MD5:— | SHA256:— | |||
| 2144 | csc.exe | C:\Users\admin\AppData\Local\Temp\CSC6348BA366CA545938181511167D5C554.TMP | — | |
MD5:— | SHA256:— | |||
| 2144 | csc.exe | C:\Users\admin\AppData\Local\Temp\hdzjeicf.dll | — | |
MD5:— | SHA256:— | |||
| 520 | cvtres.exe | C:\Users\admin\AppData\Local\Temp\RESE7CA.tmp | — | |
MD5:— | SHA256:— | |||
| 2144 | csc.exe | C:\Users\admin\AppData\Local\Temp\hdzjeicf.out | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
1
DNS requests
1
Threats
5
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2420 | RegAsm.exe | 181.52.109.69:1800 | zdfhsfj.duckdns.org | Telmex Colombia S.A. | CO | malicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
zdfhsfj.duckdns.org |
| malicious |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1080 | svchost.exe | Misc activity | ET INFO DYNAMIC_DNS Query to *.duckdns. Domain |
2420 | RegAsm.exe | A Network Trojan was detected | MALWARE [PTsecurity] njRAT.Gen RAT outbound connection |
3 ETPRO signatures available at the full report