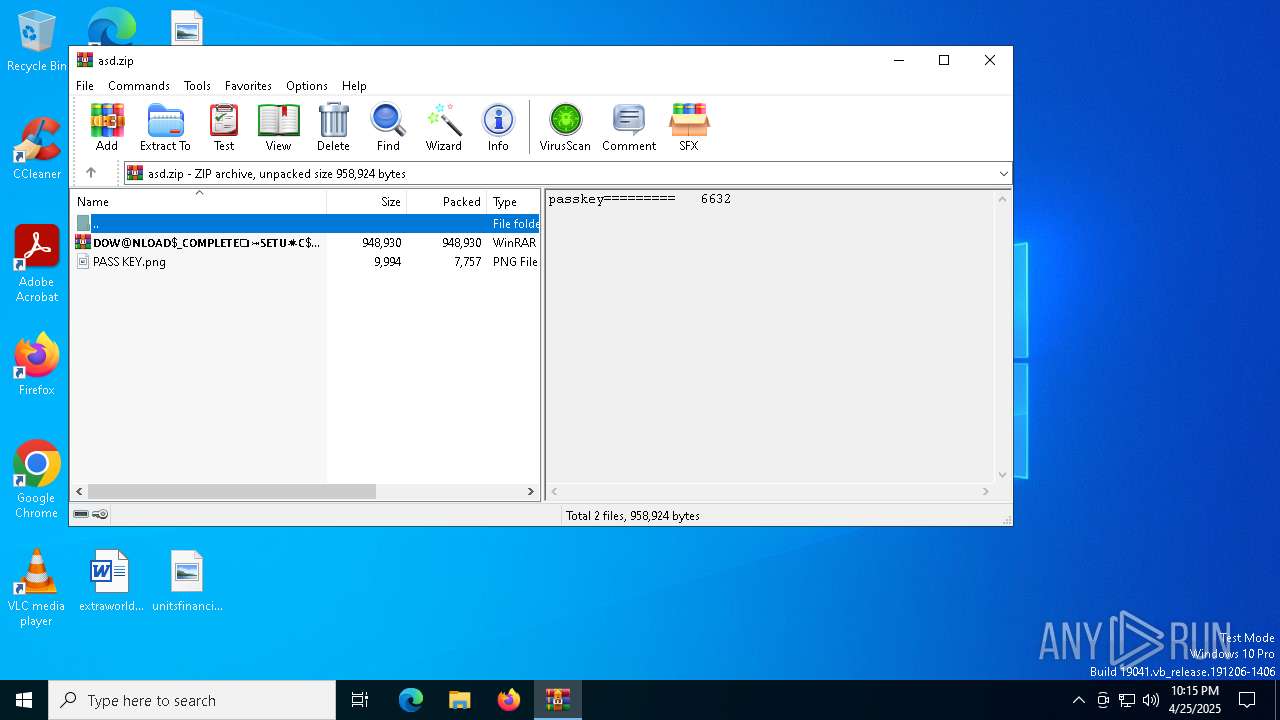
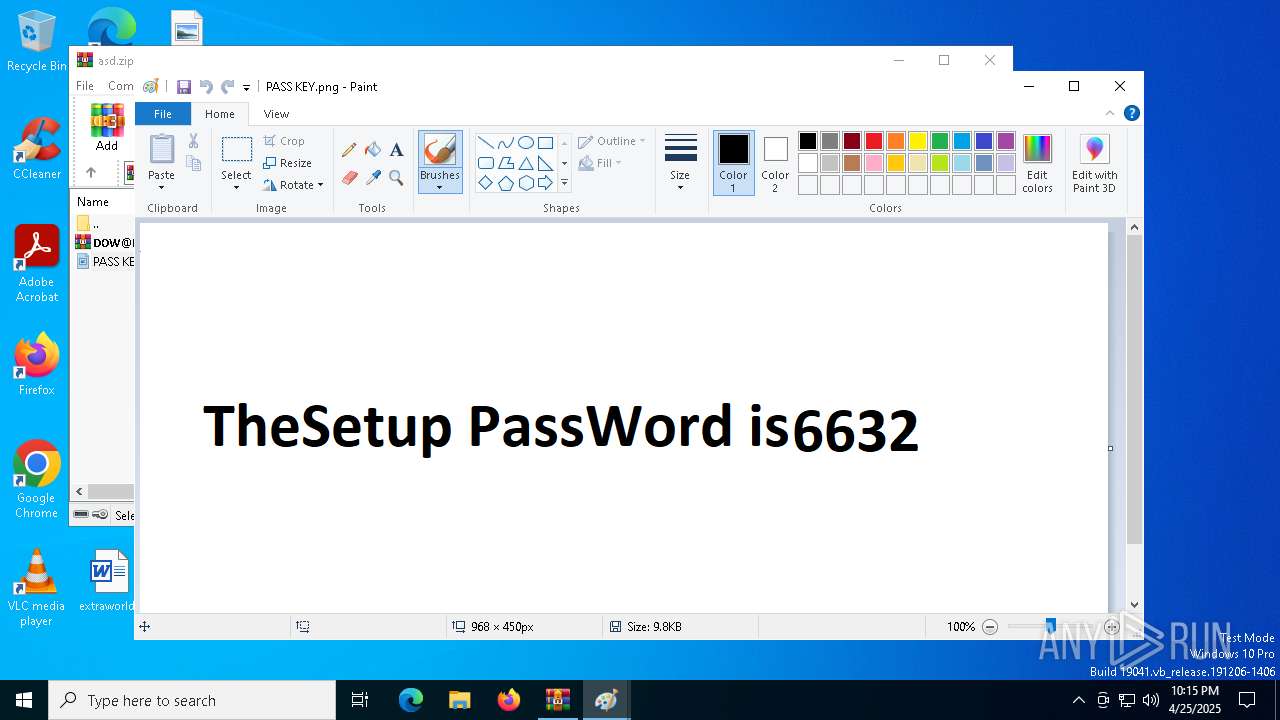
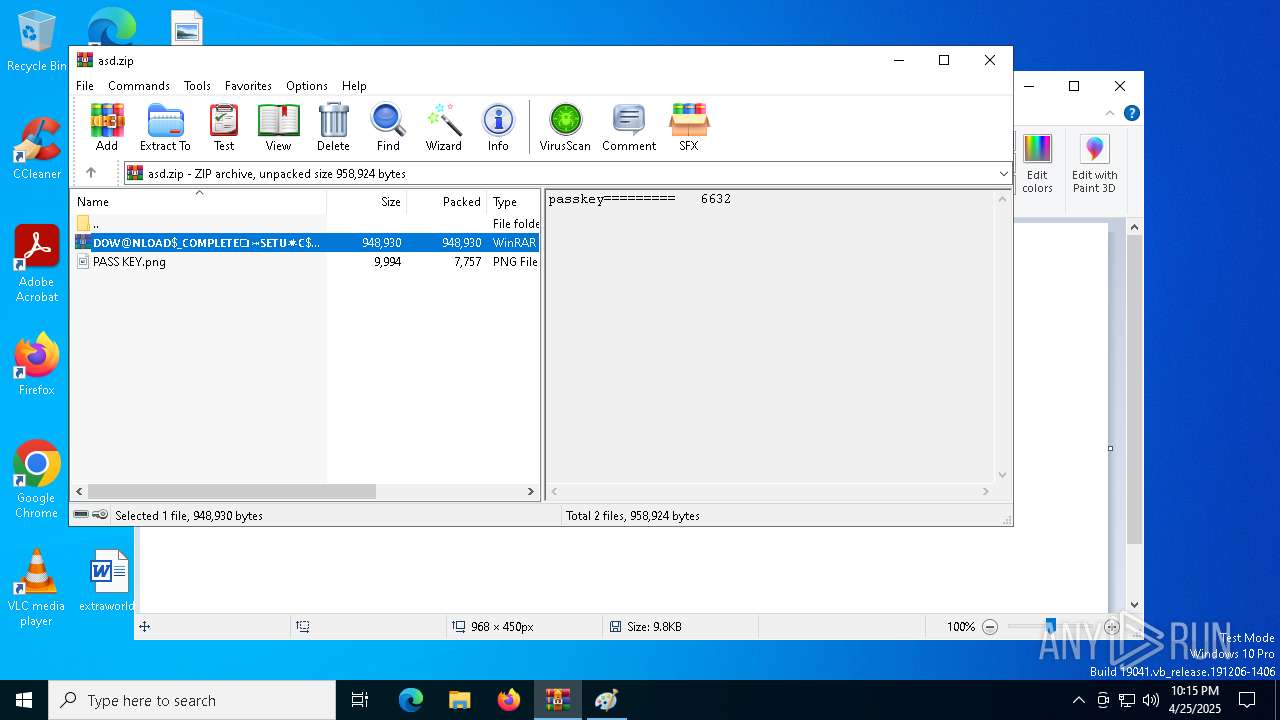
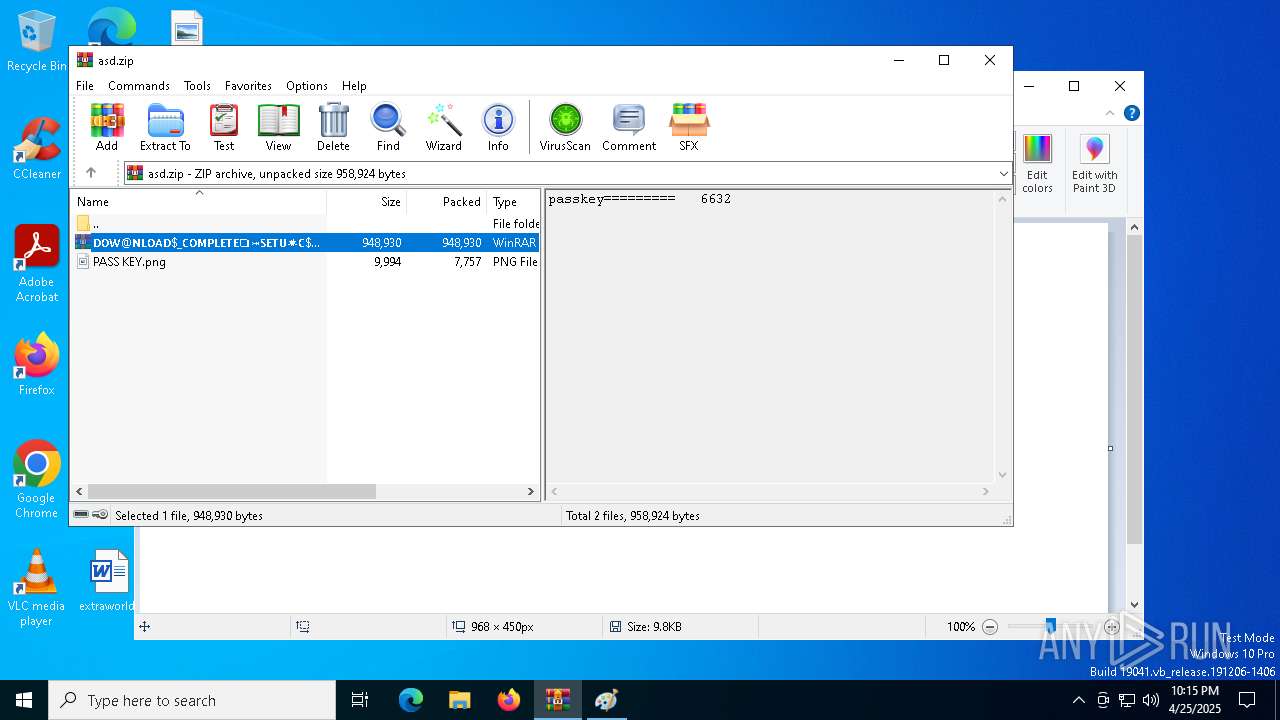
| File name: | asd.zip |
| Full analysis: | https://app.any.run/tasks/b566a5b1-76c0-4b54-9593-e1aea9d06870 |
| Verdict: | Malicious activity |
| Threats: | Lumma is an information stealer, developed using the C programming language. It is offered for sale as a malware-as-a-service, with several plans available. It usually targets cryptocurrency wallets, login credentials, and other sensitive information on a compromised system. The malicious software regularly gets updates that improve and expand its functionality, making it a serious stealer threat. |
| Analysis date: | April 25, 2025, 22:15:03 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v1.0 to extract, compression method=store |
| MD5: | 4131A5426CA1D36EC34E7A7558032C89 |
| SHA1: | D66151EAFEC5ED0A36FC8F6540B67A105ED8B265 |
| SHA256: | 9DDB514F77F98CE8D2E35BEF878FCF31073C1CB964DCFA1FFB7BFFAC3B8EE820 |
| SSDEEP: | 49152:YOI7ZTJyUgMmMpEiIzuVNEJZ8kCMbg5jlNrQVBA5DCLXO8J7S2inmvt1oNO5DMqv:YOWJgzEYzuzimxMbgTqPA5De5esnoNO5 |
MALICIOUS
Executing a file with an untrusted certificate
- Setup.exe (PID: 7744)
- Setup.exe (PID: 7776)
Steals credentials from Web Browsers
- Setup.exe (PID: 7744)
Actions looks like stealing of personal data
- Setup.exe (PID: 7744)
LUMMA mutex has been found
- Setup.exe (PID: 7744)
SUSPICIOUS
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 6488)
Searches for installed software
- Setup.exe (PID: 7744)
INFO
Manual execution by a user
- WinRAR.exe (PID: 7552)
- Setup.exe (PID: 7776)
- Setup.exe (PID: 7744)
Reads Microsoft Office registry keys
- WinRAR.exe (PID: 6488)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 7552)
Checks supported languages
- Setup.exe (PID: 7744)
- Setup.exe (PID: 7776)
The sample compiled with russian language support
- WinRAR.exe (PID: 7552)
Reads the software policy settings
- Setup.exe (PID: 7744)
Reads the computer name
- Setup.exe (PID: 7744)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 10 |
|---|---|
| ZipBitFlag: | 0x0800 |
| ZipCompression: | None |
| ZipModifyDate: | 2025:04:24 21:58:48 |
| ZipCRC: | 0xb96a9b2c |
| ZipCompressedSize: | 948930 |
| ZipUncompressedSize: | 948930 |
| ZipFileName: | 𝗗𝗢𝗪@𝗡𝗟𝗢𝗔𝗗$_𝗖𝗢𝗠𝗣𝗟𝗘𝗧𝗘❏⤖𝗦𝗘𝗧𝗨✷𝗖$#$!!!3.7z |
Total processes
139
Monitored processes
8
Malicious processes
1
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
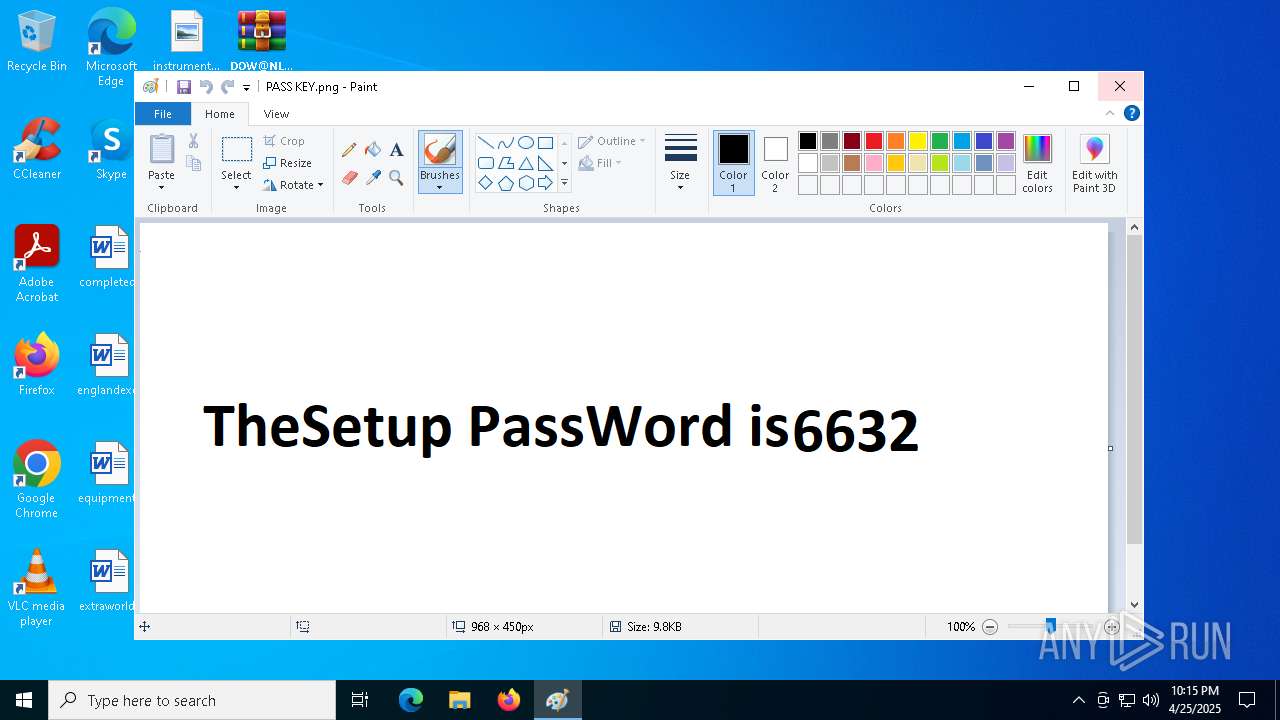
| 664 | "C:\WINDOWS\system32\mspaint.exe" "C:\Users\admin\AppData\Local\Temp\Rar$DIa6488.12205\PASS KEY.png" | C:\Windows\System32\mspaint.exe | — | WinRAR.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Paint Exit code: 0 Version: 10.0.19041.3758 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 672 | "C:\WINDOWS\system32\mspaint.exe" "C:\Users\admin\AppData\Local\Temp\Rar$DIa6488.12342\PASS KEY.png" | C:\Windows\System32\mspaint.exe | — | WinRAR.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Paint Exit code: 0 Version: 10.0.19041.3758 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2236 | "C:\WINDOWS\System32\SLUI.exe" RuleId=3482d82e-ca2c-4e1f-8864-da0267b484b2;Action=AutoActivate;AppId=55c92734-d682-4d71-983e-d6ec3f16059f;SkuId=4de7cb65-cdf1-4de9-8ae8-e3cce27b9f2c;NotificationInterval=1440;Trigger=TimerEvent | C:\Windows\System32\slui.exe | — | SppExtComObj.Exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Activation Client Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3888 | C:\WINDOWS\system32\SppExtComObj.exe -Embedding | C:\Windows\System32\SppExtComObj.Exe | — | svchost.exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: KMS Connection Broker Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6488 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\AppData\Local\Temp\asd.zip | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 7552 | "C:\Program Files\WinRAR\WinRAR.exe" x -iext -ow -ver -- "C:\Users\admin\Desktop\𝗗𝗢𝗪@𝗡𝗟𝗢𝗔𝗗$_𝗖𝗢𝗠𝗣𝗟𝗘𝗧𝗘❏⤖𝗦𝗘𝗧𝗨✷𝗖$#$!!!3.7z" C:\Users\admin\Desktop\ | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 7744 | "C:\Users\admin\Desktop\Setup.exe" | C:\Users\admin\Desktop\Setup.exe | explorer.exe | ||||||||||||
User: admin Company: Яндекс Integrity Level: MEDIUM Description: YandexDiskSetup Version: 3.2.30.4914 Modules
| |||||||||||||||
| 7776 | "C:\Users\admin\Desktop\Setup.exe" | C:\Users\admin\Desktop\Setup.exe | — | explorer.exe | |||||||||||
User: admin Company: Яндекс Integrity Level: MEDIUM Description: YandexDiskSetup Version: 3.2.30.4914 Modules
| |||||||||||||||
Total events
5 306
Read events
5 206
Write events
85
Delete events
15
Modification events
| (PID) Process: | (6488) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (6488) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (6488) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (6488) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\asd.zip | |||
| (PID) Process: | (6488) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (6488) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (6488) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (6488) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (6488) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\FileExts\.png\OpenWithProgids |
| Operation: | write | Name: | pngfile |
Value: | |||
| (PID) Process: | (672) mspaint.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Applets\Paint\View |
| Operation: | write | Name: | SnapToGrid |
Value: 0 | |||
Executable files
1
Suspicious files
1
Text files
2
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6488 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DIa6488.12205\PASS KEY.png | image | |
MD5:47BD14587DE582AC2508F4419D8951E8 | SHA256:4F6A4DFA43B7ADC183EE2AF6E16AC1D9F4CA94D132FBC8C3A566F92C6D043755 | |||
| 6488 | WinRAR.exe | C:\Users\admin\Desktop\𝗗𝗢𝗪@𝗡𝗟𝗢𝗔𝗗$_𝗖𝗢𝗠𝗣𝗟𝗘𝗧𝗘❏⤖𝗦𝗘𝗧𝗨✷𝗖$#$!!!3.7z | compressed | |
MD5:279FCBDBE626C9391529A184BD2E5A15 | SHA256:4AC6384B401A44F3462BA6D4639B9F11410BA4492C4AD689A3217287E6DDE871 | |||
| 6488 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DIa6488.12342\PASS KEY.png | image | |
MD5:47BD14587DE582AC2508F4419D8951E8 | SHA256:4F6A4DFA43B7ADC183EE2AF6E16AC1D9F4CA94D132FBC8C3A566F92C6D043755 | |||
| 7552 | WinRAR.exe | C:\Users\admin\Desktop\Setup.exe | executable | |
MD5:18343F5CBF09AF16B70E4BDB87C5FC91 | SHA256:DB3FC10F5DD5F1D577A19988E1C4E127935224CFAE35C02823F312C88CA953D8 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
5
TCP/UDP connections
23
DNS requests
14
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5496 | MoUsoCoreWorker.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | GET | 200 | 2.16.168.124:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
7608 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
7608 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2432 | RUXIMICS.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | 2.16.168.124:80 | crl.microsoft.com | Akamai International B.V. | RU | whitelisted |
5496 | MoUsoCoreWorker.exe | 23.35.229.160:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
3216 | svchost.exe | 172.211.123.249:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
6544 | svchost.exe | 40.126.31.67:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6544 | svchost.exe | 184.30.131.245:80 | ocsp.digicert.com | AKAMAI-AS | US | whitelisted |
2104 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
nodepathr.run |
| unknown |