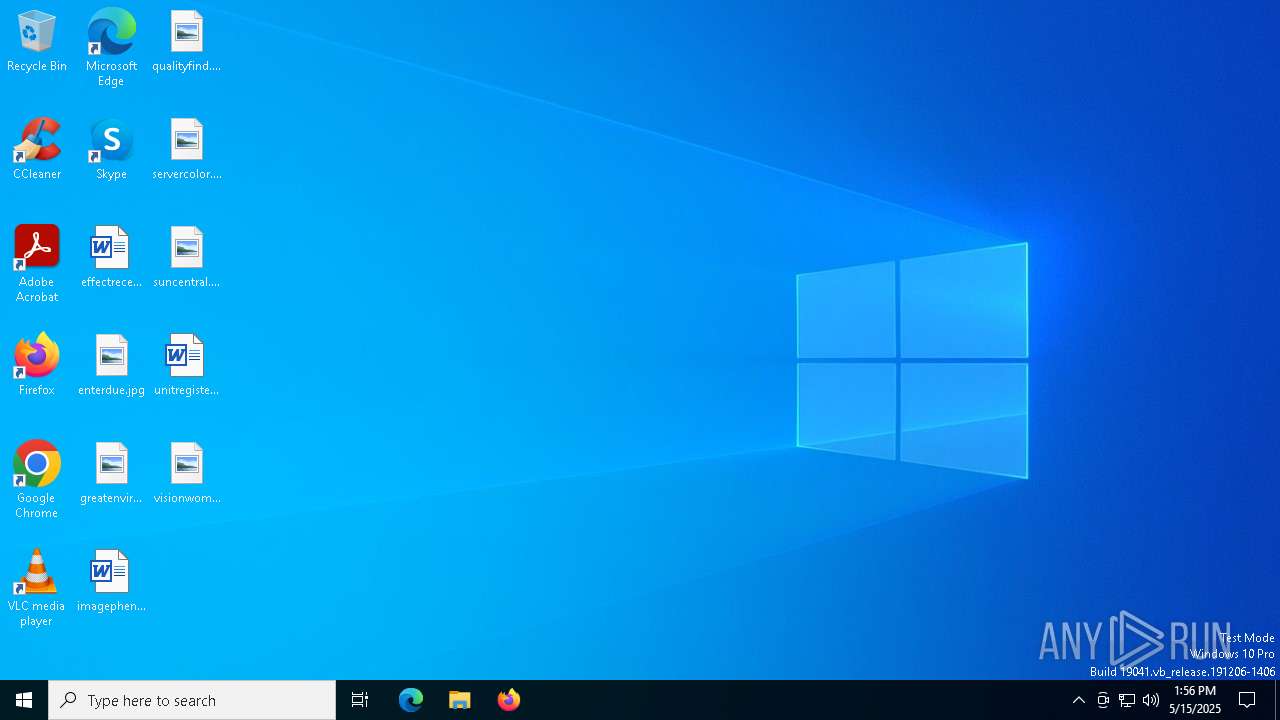
| File name: | 83d145e19e74958fc894ac46fb965b1d.exe |
| Full analysis: | https://app.any.run/tasks/8b4d941a-fe46-49f1-933c-288374bd694d |
| Verdict: | Malicious activity |
| Threats: | Amadey is a formidable Windows infostealer threat, characterized by its persistence mechanisms, modular design, and ability to execute various malicious tasks. |
| Analysis date: | May 15, 2025, 13:55:59 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, 7 sections |
| MD5: | 83D145E19E74958FC894AC46FB965B1D |
| SHA1: | 54279D302D178F5D4A2900C40EA999CF461BBB31 |
| SHA256: | 9D542D5B8579EB9E76F36EC20A3A3387748E48E7D9C1A0899A5056F60DDFFB3D |
| SSDEEP: | 98304:USKaSh01hZLOcX4abVFceP3edIQTDHnGHrhTp5sS+KlFv67pwsM4IA/uzrY0cHXD:Jk4S |
MALICIOUS
LUMMA mutex has been found
- 83d145e19e74958fc894ac46fb965b1d.exe (PID: 2320)
- MSBuild.exe (PID: 6768)
- 53d23870d6.exe (PID: 5244)
Steals credentials from Web Browsers
- 83d145e19e74958fc894ac46fb965b1d.exe (PID: 2320)
- MSBuild.exe (PID: 6768)
- 53d23870d6.exe (PID: 5244)
Actions looks like stealing of personal data
- 83d145e19e74958fc894ac46fb965b1d.exe (PID: 2320)
- MSBuild.exe (PID: 6768)
- 53d23870d6.exe (PID: 5244)
LUMMA has been detected (SURICATA)
- svchost.exe (PID: 2196)
- 83d145e19e74958fc894ac46fb965b1d.exe (PID: 2320)
- 53d23870d6.exe (PID: 5244)
Connects to the CnC server
- svchost.exe (PID: 2196)
- ramez.exe (PID: 6192)
LUMMA has been detected (YARA)
- 83d145e19e74958fc894ac46fb965b1d.exe (PID: 2320)
AMADEY mutex has been found
- 1F0ZQD6BSMS9EJVZXTNMJWJF.exe (PID: 6744)
- ramez.exe (PID: 6192)
- B9P0KZDUJ6K7OQJDYCAI8W998PFW.exe (PID: 7200)
AMADEY has been detected (SURICATA)
- ramez.exe (PID: 6192)
AMADEY has been detected (YARA)
- ramez.exe (PID: 6192)
Changes the autorun value in the registry
- ramez.exe (PID: 6192)
Adds path to the Windows Defender exclusion list
- NSudoLG.exe (PID: 4488)
- cmd.exe (PID: 4112)
Changes Windows Defender settings
- NSudoLG.exe (PID: 4488)
Possible tool for stealing has been detected
- firefox.exe (PID: 7712)
- 04f06bca58.exe (PID: 3268)
Uses Task Scheduler to run other applications
- cmd.exe (PID: 7412)
Run PowerShell with an invisible window
- powershell.exe (PID: 6424)
Request from PowerShell that ran from MSHTA.EXE
- powershell.exe (PID: 6424)
Starts SC.EXE for service management
- cmd.exe (PID: 4112)
SUSPICIOUS
Reads the BIOS version
- 83d145e19e74958fc894ac46fb965b1d.exe (PID: 2320)
- 1F0ZQD6BSMS9EJVZXTNMJWJF.exe (PID: 6744)
- ramez.exe (PID: 6192)
- 53d23870d6.exe (PID: 5244)
- B9P0KZDUJ6K7OQJDYCAI8W998PFW.exe (PID: 7200)
Contacting a server suspected of hosting an CnC
- svchost.exe (PID: 2196)
- 83d145e19e74958fc894ac46fb965b1d.exe (PID: 2320)
- ramez.exe (PID: 6192)
- 53d23870d6.exe (PID: 5244)
Searches for installed software
- 83d145e19e74958fc894ac46fb965b1d.exe (PID: 2320)
- MSBuild.exe (PID: 6768)
- 53d23870d6.exe (PID: 5244)
Potential Corporate Privacy Violation
- 83d145e19e74958fc894ac46fb965b1d.exe (PID: 2320)
- ramez.exe (PID: 6192)
- 53d23870d6.exe (PID: 5244)
- powershell.exe (PID: 6424)
Executable content was dropped or overwritten
- 83d145e19e74958fc894ac46fb965b1d.exe (PID: 2320)
- 1F0ZQD6BSMS9EJVZXTNMJWJF.exe (PID: 6744)
- ramez.exe (PID: 6192)
- 3b41e7c978.exe (PID: 680)
- 53d23870d6.exe (PID: 5244)
- 7z.exe (PID: 7220)
- Unlocker.exe (PID: 8620)
- powershell.exe (PID: 6424)
- cmd.exe (PID: 4112)
Reads security settings of Internet Explorer
- 1F0ZQD6BSMS9EJVZXTNMJWJF.exe (PID: 6744)
- ramez.exe (PID: 6192)
- 3b41e7c978.exe (PID: 680)
- nircmd.exe (PID: 856)
- Unlocker.exe (PID: 7376)
- Unlocker.exe (PID: 8620)
Connects to the server without a host name
- 83d145e19e74958fc894ac46fb965b1d.exe (PID: 2320)
- ramez.exe (PID: 6192)
- 53d23870d6.exe (PID: 5244)
- powershell.exe (PID: 6424)
Starts itself from another location
- 1F0ZQD6BSMS9EJVZXTNMJWJF.exe (PID: 6744)
Process requests binary or script from the Internet
- 83d145e19e74958fc894ac46fb965b1d.exe (PID: 2320)
- ramez.exe (PID: 6192)
- 53d23870d6.exe (PID: 5244)
- powershell.exe (PID: 6424)
Executes application which crashes
- 45d9bbde4b.exe (PID: 856)
There is functionality for enable RDP (YARA)
- ramez.exe (PID: 6192)
Process communicates with Telegram (possibly using it as an attacker's C2 server)
- MSBuild.exe (PID: 6768)
The process creates files with name similar to system file names
- 3b41e7c978.exe (PID: 680)
Executing commands from a ".bat" file
- 3b41e7c978.exe (PID: 680)
- nircmd.exe (PID: 856)
- cmd.exe (PID: 4152)
- cmd.exe (PID: 5352)
- cmd.exe (PID: 5776)
- NSudoLG.exe (PID: 4880)
Starts CMD.EXE for commands execution
- 3b41e7c978.exe (PID: 680)
- nircmd.exe (PID: 856)
- cmd.exe (PID: 4152)
- cmd.exe (PID: 5352)
- NSudoLG.exe (PID: 4880)
- cmd.exe (PID: 5776)
- cmd.exe (PID: 4112)
- e886917125.exe (PID: 7272)
- Unlocker.exe (PID: 7376)
- Unlocker.exe (PID: 8620)
- Unlocker.exe (PID: 5956)
Application launched itself
- cmd.exe (PID: 5352)
- cmd.exe (PID: 4152)
- cmd.exe (PID: 5776)
- cmd.exe (PID: 4112)
Starts application with an unusual extension
- cmd.exe (PID: 6760)
- cmd.exe (PID: 4976)
- cmd.exe (PID: 4112)
The executable file from the user directory is run by the CMD process
- nircmd.exe (PID: 856)
- NSudoLG.exe (PID: 4880)
- NSudoLG.exe (PID: 4488)
- 7z.exe (PID: 7220)
- Unlocker.exe (PID: 7376)
- Unlocker.exe (PID: 8620)
- Unlocker.exe (PID: 5956)
Reads the date of Windows installation
- nircmd.exe (PID: 856)
- Unlocker.exe (PID: 7376)
- Unlocker.exe (PID: 8620)
Uses REG/REGEDIT.EXE to modify registry
- cmd.exe (PID: 4976)
- cmd.exe (PID: 4112)
Get information on the list of running processes
- cmd.exe (PID: 4112)
- cmd.exe (PID: 6476)
Script adds exclusion path to Windows Defender
- NSudoLG.exe (PID: 4488)
PowerShell delay command usage (probably sleep evasion)
- powershell.exe (PID: 6828)
Starts POWERSHELL.EXE for commands execution
- NSudoLG.exe (PID: 4488)
- mshta.exe (PID: 7436)
Uses TASKKILL.EXE to kill Browsers
- 04f06bca58.exe (PID: 3268)
Uses TASKKILL.EXE to kill process
- 04f06bca58.exe (PID: 3268)
- cmd.exe (PID: 8276)
- cmd.exe (PID: 8264)
- cmd.exe (PID: 8148)
Using 'findstr.exe' to search for text patterns in files and output
- cmd.exe (PID: 4112)
Probably download files using WebClient
- mshta.exe (PID: 7436)
Starts process via Powershell
- powershell.exe (PID: 6424)
Found IP address in command line
- powershell.exe (PID: 6424)
Starts SC.EXE for service management
- cmd.exe (PID: 7576)
- cmd.exe (PID: 4112)
- cmd.exe (PID: 8752)
- cmd.exe (PID: 9184)
- cmd.exe (PID: 6572)
Windows service management via SC.EXE
- sc.exe (PID: 8236)
- sc.exe (PID: 8808)
- sc.exe (PID: 8508)
- sc.exe (PID: 8548)
- sc.exe (PID: 8568)
- sc.exe (PID: 7800)
- sc.exe (PID: 8480)
- sc.exe (PID: 5020)
- sc.exe (PID: 3024)
- sc.exe (PID: 8564)
- sc.exe (PID: 8256)
- sc.exe (PID: 8284)
- sc.exe (PID: 8768)
- sc.exe (PID: 5308)
- sc.exe (PID: 8756)
- sc.exe (PID: 2804)
- sc.exe (PID: 6964)
- sc.exe (PID: 4200)
- sc.exe (PID: 2424)
- sc.exe (PID: 8900)
- sc.exe (PID: 2392)
- sc.exe (PID: 1756)
- sc.exe (PID: 8696)
- sc.exe (PID: 7508)
- sc.exe (PID: 456)
- sc.exe (PID: 2416)
- sc.exe (PID: 9196)
- sc.exe (PID: 9208)
- sc.exe (PID: 9084)
- sc.exe (PID: 2800)
- sc.exe (PID: 8412)
- sc.exe (PID: 9068)
- sc.exe (PID: 8296)
- sc.exe (PID: 8672)
- sc.exe (PID: 8444)
- sc.exe (PID: 8164)
- sc.exe (PID: 9152)
- sc.exe (PID: 8744)
- sc.exe (PID: 8540)
- sc.exe (PID: 8688)
- sc.exe (PID: 8212)
Manipulates environment variables
- powershell.exe (PID: 6424)
Stops a currently running service
- sc.exe (PID: 660)
- sc.exe (PID: 8452)
- sc.exe (PID: 1748)
- sc.exe (PID: 8520)
- sc.exe (PID: 8832)
- sc.exe (PID: 2440)
- sc.exe (PID: 2428)
- sc.exe (PID: 5780)
- sc.exe (PID: 8904)
- sc.exe (PID: 8732)
- sc.exe (PID: 8232)
- sc.exe (PID: 4108)
- sc.exe (PID: 9136)
- sc.exe (PID: 2664)
- sc.exe (PID: 8752)
- sc.exe (PID: 5452)
- sc.exe (PID: 9144)
Drops a system driver (possible attempt to evade defenses)
- Unlocker.exe (PID: 8620)
Deletes scheduled task without confirmation
- schtasks.exe (PID: 8596)
- schtasks.exe (PID: 8572)
- schtasks.exe (PID: 8512)
- schtasks.exe (PID: 6268)
- schtasks.exe (PID: 8476)
Process drops legitimate windows executable
- cmd.exe (PID: 4112)
The process executes via Task Scheduler
- ramez.exe (PID: 8796)
- ramez.exe (PID: 8712)
INFO
Checks supported languages
- 83d145e19e74958fc894ac46fb965b1d.exe (PID: 2320)
- 1F0ZQD6BSMS9EJVZXTNMJWJF.exe (PID: 6744)
- ramez.exe (PID: 6192)
- MSBuild.exe (PID: 6768)
- 45d9bbde4b.exe (PID: 856)
- 53d23870d6.exe (PID: 5244)
- 3b41e7c978.exe (PID: 680)
- chcp.com (PID: 1348)
- nircmd.exe (PID: 856)
- NSudoLG.exe (PID: 4880)
- chcp.com (PID: 736)
- chcp.com (PID: 5600)
- mode.com (PID: 5352)
- NSudoLG.exe (PID: 4488)
- 04f06bca58.exe (PID: 3268)
- B9P0KZDUJ6K7OQJDYCAI8W998PFW.exe (PID: 7200)
- 7z.exe (PID: 7220)
- e886917125.exe (PID: 7272)
- Unlocker.exe (PID: 8620)
- IObitUnlocker.exe (PID: 8836)
Reads the computer name
- 83d145e19e74958fc894ac46fb965b1d.exe (PID: 2320)
- 1F0ZQD6BSMS9EJVZXTNMJWJF.exe (PID: 6744)
- ramez.exe (PID: 6192)
- MSBuild.exe (PID: 6768)
- 53d23870d6.exe (PID: 5244)
- 3b41e7c978.exe (PID: 680)
- nircmd.exe (PID: 856)
- NSudoLG.exe (PID: 4880)
- NSudoLG.exe (PID: 4488)
- 04f06bca58.exe (PID: 3268)
- 7z.exe (PID: 7220)
- e886917125.exe (PID: 7272)
- Unlocker.exe (PID: 8620)
Reads the software policy settings
- 83d145e19e74958fc894ac46fb965b1d.exe (PID: 2320)
- MSBuild.exe (PID: 6768)
- 53d23870d6.exe (PID: 5244)
Themida protector has been detected
- 83d145e19e74958fc894ac46fb965b1d.exe (PID: 2320)
- ramez.exe (PID: 6192)
Create files in a temporary directory
- 83d145e19e74958fc894ac46fb965b1d.exe (PID: 2320)
- 1F0ZQD6BSMS9EJVZXTNMJWJF.exe (PID: 6744)
- ramez.exe (PID: 6192)
- 3b41e7c978.exe (PID: 680)
Process checks computer location settings
- 1F0ZQD6BSMS9EJVZXTNMJWJF.exe (PID: 6744)
- ramez.exe (PID: 6192)
- 3b41e7c978.exe (PID: 680)
- nircmd.exe (PID: 856)
Checks proxy server information
- ramez.exe (PID: 6192)
Creates files or folders in the user directory
- ramez.exe (PID: 6192)
- WerFault.exe (PID: 680)
Attempting to use instant messaging service
- MSBuild.exe (PID: 6768)
Auto-launch of the file from Registry key
- ramez.exe (PID: 6192)
The sample compiled with english language support
- 3b41e7c978.exe (PID: 680)
- ramez.exe (PID: 6192)
- Unlocker.exe (PID: 8620)
- cmd.exe (PID: 4112)
Changes the display of characters in the console
- cmd.exe (PID: 6760)
- cmd.exe (PID: 4976)
- cmd.exe (PID: 4112)
NirSoft software is detected
- nircmd.exe (PID: 856)
Starts MODE.COM to configure console settings
- mode.com (PID: 5352)
Checks operating system version
- cmd.exe (PID: 4112)
Reads mouse settings
- 04f06bca58.exe (PID: 3268)
- e886917125.exe (PID: 7272)
Checks if a key exists in the options dictionary (POWERSHELL)
- powershell.exe (PID: 6828)
Application launched itself
- firefox.exe (PID: 7712)
- firefox.exe (PID: 7732)
Script raised an exception (POWERSHELL)
- powershell.exe (PID: 6828)
Reads the machine GUID from the registry
- Unlocker.exe (PID: 7376)
- Unlocker.exe (PID: 8620)
Auto-launch of the file from Task Scheduler
- cmd.exe (PID: 7412)
The executable file from the user directory is run by the Powershell process
- TempZAVWOIF8SVHPRSKED7T6TMQGLZAIARQ9.EXE (PID: 8104)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Lumma
(PID) Process(2320) 83d145e19e74958fc894ac46fb965b1d.exe
C2 (9)emphatakpn.bet/ladk
featurlyin.top/pdal
overcovtcg.top/juhd
laminaflbx.shop/twoq
cornerdurv.top/adwq
testcawepr.run/dsap
saxecocnak.live/manj
posseswsnc.top/akds
blackswmxc.top/bgry
Amadey
(PID) Process(6192) ramez.exe
C2185.156.72.96
URLhttp://185.156.72.96/te4h2nus/index.php
Version5.34
Options
Drop directoryd610cf342e
Drop nameramez.exe
Strings (125)lv:
msi
Kaspersky Lab
av:
|
#
"
\App
00000422
dm:
Powershell.exe
ProgramData\
ps1
rundll32
http://
Content-Disposition: form-data; name="data"; filename="
SOFTWARE\Microsoft\Windows NT\CurrentVersion
dll
SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\Shell Folders
id:
VideoID
cred.dll|clip.dll|
0000043f
cmd
00000423
SYSTEM\CurrentControlSet\Control\ComputerName\ComputerName
-executionpolicy remotesigned -File "
2022
------
2016
og:
\0000
CurrentBuild
2019
:::
S-%lu-
" && timeout 1 && del
ProductName
Panda Security
ESET
SOFTWARE\Microsoft\Windows\CurrentVersion\Run
/k
+++
?scr=1
Doctor Web
GET
SYSTEM\ControlSet001\Services\BasicDisplay\Video
/quiet
.jpg
d610cf342e
vs:
sd:
rundll32.exe
"taskkill /f /im "
pc:
random
=
360TotalSecurity
<d>
wb
Content-Type: multipart/form-data; boundary=----
Startup
Norton
&& Exit"
os:
https://
SOFTWARE\Microsoft\Windows\CurrentVersion\RunOnce
2025
Avira
%-lu
zip
POST
"
Content-Type: application/octet-stream
Rem
/te4h2nus/index.php
------
5.34
<c>
clip.dll
AVAST Software
\
shell32.dll
" && ren
e3
ramez.exe
kernel32.dll
DefaultSettings.XResolution
d1
DefaultSettings.YResolution
185.156.72.96
r=
cred.dll
--
GetNativeSystemInfo
-%lu
ComputerName
&unit=
Keyboard Layout\Preload
SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\User Shell Folders
ar:
Sophos
%USERPROFILE%
exe
e1
e2
st=s
Programs
0123456789
un:
rb
bi:
abcdefghijklmnopqrstuvwxyz0123456789-_
SYSTEM\CurrentControlSet\Control\UnitedVideo\CONTROL\VIDEO\
cmd /C RMDIR /s/q
Bitdefender
-unicode-
AVG
WinDefender
&&
shutdown -s -t 0
Comodo
00000419
Content-Type: application/x-www-form-urlencoded
/Plugins/
Main
TRiD
| .exe | | | Generic Win/DOS Executable (50) |
|---|---|---|
| .exe | | | DOS Executable Generic (49.9) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2025:05:11 18:58:30+00:00 |
| ImageFileCharacteristics: | Executable, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 14 |
| CodeSize: | 315392 |
| InitializedDataSize: | 37888 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x493000 |
| OSVersion: | 6 |
| ImageVersion: | - |
| SubsystemVersion: | 6 |
| Subsystem: | Windows GUI |
Total processes
364
Monitored processes
227
Malicious processes
17
Suspicious processes
8
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 136 | reg delete "HKLM\Software\Microsoft\Windows\CurrentVersion\WINEVT\Channels\Microsoft-Windows-Windows Defender/WHC" /f | C:\Windows\System32\reg.exe | — | cmd.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Registry Console Tool Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 456 | sc delete "WdNisDrv" | C:\Windows\System32\sc.exe | — | cmd.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Service Control Manager Configuration Tool Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 660 | sc stop IObitUnlocker | C:\Windows\System32\sc.exe | — | cmd.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Service Control Manager Configuration Tool Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 664 | reg delete "HKLM\Software\Microsoft\Windows\CurrentVersion\Run" /v "SecurityHealth" /f | C:\Windows\System32\reg.exe | — | cmd.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Registry Console Tool Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 680 | C:\WINDOWS\system32\WerFault.exe -u -p 856 -s 260 | C:\Windows\System32\WerFault.exe | — | 45d9bbde4b.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Problem Reporting Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 680 | "C:\Users\admin\AppData\Local\Temp\10118520101\3b41e7c978.exe" | C:\Users\admin\AppData\Local\Temp\10118520101\3b41e7c978.exe | ramez.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 736 | chcp 65001 | C:\Windows\System32\chcp.com | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Change CodePage Utility Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 780 | C:\WINDOWS\system32\SppExtComObj.exe -Embedding | C:\Windows\System32\SppExtComObj.Exe | — | svchost.exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: KMS Connection Broker Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 856 | "C:\Users\admin\AppData\Local\Temp\10118500101\45d9bbde4b.exe" | C:\Users\admin\AppData\Local\Temp\10118500101\45d9bbde4b.exe | ramez.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221225477 Modules
| |||||||||||||||
| 856 | nircmd elevate "C:\Users\admin\AppData\Local\Temp\gBYTeGp.bat" | C:\Users\admin\AppData\Local\Temp\Work\nircmd.exe | — | cmd.exe | |||||||||||
User: admin Company: NirSoft Integrity Level: MEDIUM Description: NirCmd Exit code: 0 Version: 2.87 Modules
| |||||||||||||||
Total events
39 122
Read events
38 956
Write events
34
Delete events
132
Modification events
| (PID) Process: | (6192) ramez.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (6192) ramez.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (6192) ramez.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (6192) ramez.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Run |
| Operation: | write | Name: | 53d23870d6.exe |
Value: C:\Users\admin\AppData\Local\Temp\10118510101\53d23870d6.exe | |||
| (PID) Process: | (856) nircmd.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\MuiCache |
| Operation: | write | Name: | C:\WINDOWS\System32\cmd.exe.FriendlyAppName |
Value: Windows Command Processor | |||
| (PID) Process: | (856) nircmd.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\MuiCache |
| Operation: | write | Name: | C:\WINDOWS\System32\cmd.exe.ApplicationCompany |
Value: Microsoft Corporation | |||
| (PID) Process: | (6192) ramez.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Run |
| Operation: | write | Name: | 3b41e7c978.exe |
Value: C:\Users\admin\AppData\Local\Temp\10118520101\3b41e7c978.exe | |||
| (PID) Process: | (6468) reg.exe | Key: | HKEY_USERS\.DEFAULT\Software\Microsoft\Windows\CurrentVersion\Themes\Personalize |
| Operation: | write | Name: | AppsUseLightTheme |
Value: 0 | |||
| (PID) Process: | (3768) reg.exe | Key: | HKEY_USERS\.DEFAULT\Software\Microsoft\Windows\CurrentVersion\Themes\Personalize |
| Operation: | write | Name: | AppsUseLightTheme |
Value: 0 | |||
| (PID) Process: | (6192) ramez.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Run |
| Operation: | write | Name: | 04f06bca58.exe |
Value: C:\Users\admin\AppData\Local\Temp\10118530101\04f06bca58.exe | |||
Executable files
24
Suspicious files
163
Text files
33
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 680 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\ReportQueue\AppCrash_45d9bbde4b.exe_3f32f0e53caabdb5a58b556f1cc7f49c3b173ef_2f979479_86caab72-2e40-43fb-8ffd-69c1bc3d145f\Report.wer | — | |
MD5:— | SHA256:— | |||
| 2320 | 83d145e19e74958fc894ac46fb965b1d.exe | C:\Users\admin\AppData\Local\Temp\1F0ZQD6BSMS9EJVZXTNMJWJF.exe | executable | |
MD5:B024F652A94D64CFFC7DBF2E54F9F680 | SHA256:0762262EE8CA6BB6FFCBB1003088ECF3C6945C2B34B818E4EA8C96F378F5017D | |||
| 680 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\Temp\WER1599.tmp.WERInternalMetadata.xml | binary | |
MD5:EDB12EEE91D590E7FAE9E84A25698829 | SHA256:DDDF7190B8D1A0BEEF0EF377D90C3948DB2E52CEFA1456777BF18AB4313436C8 | |||
| 6744 | 1F0ZQD6BSMS9EJVZXTNMJWJF.exe | C:\Windows\Tasks\ramez.job | binary | |
MD5:92733810085EC1FACE4D37FEA58AE697 | SHA256:6EB1991D4065392B1496AD2E63BEAE637362225E0BD56760BBDEE67F9D300099 | |||
| 6192 | ramez.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\IE\RR3E01RZ\random[1].exe | executable | |
MD5:B3EDC4D046207F50B2075C84430FFBC8 | SHA256:C0E19BB95FB9541F2F82FAF23AEA1B917611EF9364E82474927F5B89E32A7743 | |||
| 680 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\Temp\WER151B.tmp.dmp | binary | |
MD5:4E8DC90208A28C2D09198CF136682978 | SHA256:CF2AC0050815FC8AC5A1F0ADB0F3AE0CDC5910427FF25CEB84CAB2CB3B561422 | |||
| 6192 | ramez.exe | C:\Users\admin\AppData\Local\Temp\10118500101\45d9bbde4b.exe | executable | |
MD5:B3EDC4D046207F50B2075C84430FFBC8 | SHA256:C0E19BB95FB9541F2F82FAF23AEA1B917611EF9364E82474927F5B89E32A7743 | |||
| 6744 | 1F0ZQD6BSMS9EJVZXTNMJWJF.exe | C:\Users\admin\AppData\Local\Temp\d610cf342e\ramez.exe | executable | |
MD5:B024F652A94D64CFFC7DBF2E54F9F680 | SHA256:0762262EE8CA6BB6FFCBB1003088ECF3C6945C2B34B818E4EA8C96F378F5017D | |||
| 7732 | firefox.exe | C:\Users\admin\AppData\Local\Mozilla\Firefox\Profiles\9kie7cg6.default-release\startupCache\scriptCache-current.bin | — | |
MD5:— | SHA256:— | |||
| 680 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\Temp\WER15B9.tmp.xml | xml | |
MD5:871B73D7AA8E5DE536AC543900688F8C | SHA256:2264D326EADF1A414191780F20282D5DB12E4D985B57216AD06A608F0FAD2D1A | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
47
TCP/UDP connections
130
DNS requests
138
Threats
43
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 23.48.23.177:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
2320 | 83d145e19e74958fc894ac46fb965b1d.exe | GET | 200 | 185.156.72.2:80 | http://185.156.72.2/mine/random.exe | unknown | — | — | unknown |
6192 | ramez.exe | GET | 200 | 185.156.72.2:80 | http://185.156.72.2/files/fate/random.exe | unknown | — | — | unknown |
6192 | ramez.exe | POST | 200 | 185.156.72.96:80 | http://185.156.72.96/te4h2nus/index.php | unknown | — | — | malicious |
6192 | ramez.exe | POST | 200 | 185.156.72.96:80 | http://185.156.72.96/te4h2nus/index.php | unknown | — | — | malicious |
6192 | ramez.exe | GET | 200 | 185.156.72.2:80 | http://185.156.72.2/luma/random.exe | unknown | — | — | unknown |
4976 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 40.127.240.158:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 23.48.23.177:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
— | — | 23.35.229.160:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
5496 | MoUsoCoreWorker.exe | 23.35.229.160:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
2104 | svchost.exe | 40.127.240.158:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2320 | 83d145e19e74958fc894ac46fb965b1d.exe | 104.21.96.1:443 | cornerdurv.top | CLOUDFLARENET | — | unknown |
2320 | 83d145e19e74958fc894ac46fb965b1d.exe | 104.21.112.1:443 | cornerdurv.top | CLOUDFLARENET | — | unknown |
2320 | 83d145e19e74958fc894ac46fb965b1d.exe | 104.21.21.111:443 | emphatakpn.bet | CLOUDFLARENET | — | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
cornerdurv.top |
| unknown |
saxecocnak.live |
| unknown |
testcawepr.run |
| unknown |
emphatakpn.bet |
| unknown |
laminaflbx.shop |
| unknown |
overcovtcg.top |
| malicious |
settings-win.data.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2196 | svchost.exe | Potentially Bad Traffic | ET DNS Query to a *.top domain - Likely Hostile |
2320 | 83d145e19e74958fc894ac46fb965b1d.exe | Domain Observed Used for C2 Detected | ET MALWARE Observed Win32/Lumma Stealer Related Domain (overcovtcg .top) in TLS SNI |
2196 | svchost.exe | Domain Observed Used for C2 Detected | ET MALWARE Win32/Lumma Stealer Related CnC Domain in DNS Lookup (overcovtcg .top) |
2320 | 83d145e19e74958fc894ac46fb965b1d.exe | Domain Observed Used for C2 Detected | ET MALWARE Observed Win32/Lumma Stealer Related Domain (overcovtcg .top) in TLS SNI |
2320 | 83d145e19e74958fc894ac46fb965b1d.exe | Domain Observed Used for C2 Detected | ET MALWARE Observed Win32/Lumma Stealer Related Domain (overcovtcg .top) in TLS SNI |
2320 | 83d145e19e74958fc894ac46fb965b1d.exe | Domain Observed Used for C2 Detected | ET MALWARE Observed Win32/Lumma Stealer Related Domain (overcovtcg .top) in TLS SNI |
2320 | 83d145e19e74958fc894ac46fb965b1d.exe | Domain Observed Used for C2 Detected | ET MALWARE Observed Win32/Lumma Stealer Related Domain (overcovtcg .top) in TLS SNI |
2320 | 83d145e19e74958fc894ac46fb965b1d.exe | Domain Observed Used for C2 Detected | ET MALWARE Observed Win32/Lumma Stealer Related Domain (overcovtcg .top) in TLS SNI |
2320 | 83d145e19e74958fc894ac46fb965b1d.exe | Potentially Bad Traffic | ET INFO Executable Download from dotted-quad Host |
2320 | 83d145e19e74958fc894ac46fb965b1d.exe | Potential Corporate Privacy Violation | ET INFO PE EXE or DLL Windows file download HTTP |